Method for protecting SUPI through utilization of 5G-AKA
A 5G-AKA and authentication vector technology, applied in the field of SUPI protection using 5G-AKA, can solve the problem of not being able to hide user identity, location, business, etc. The effect of low cost of renovation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0066] A method for protecting SUPI using 5G AKA is disclosed. This method is applied to the network side (including network elements AMF (Access and Mobility Management Function) and UDM / ARPF), such as Figure 5 shown, including the following steps:
[0067] Step S101, the core network receives the authentication request initiated by the terminal, decrypts the SUCI reported by the terminal, and obtains the SUPI;
[0068] Step S102, determine whether the identity information needs to be replaced; when it is determined that the identity information does not need to be replaced, use SUPI for authentication; when it is determined that the identity information needs to be replaced, randomly select a SUPI from the alternative SUPI resource pool as the new "in-use" of the terminal. "Identity ID SUPI';
[0069] Step S103, encrypt the above-mentioned "in use" identity, put the encrypted "in use" identity into the authentication vector AV', and send the authentication parameters in t...
Embodiment 2
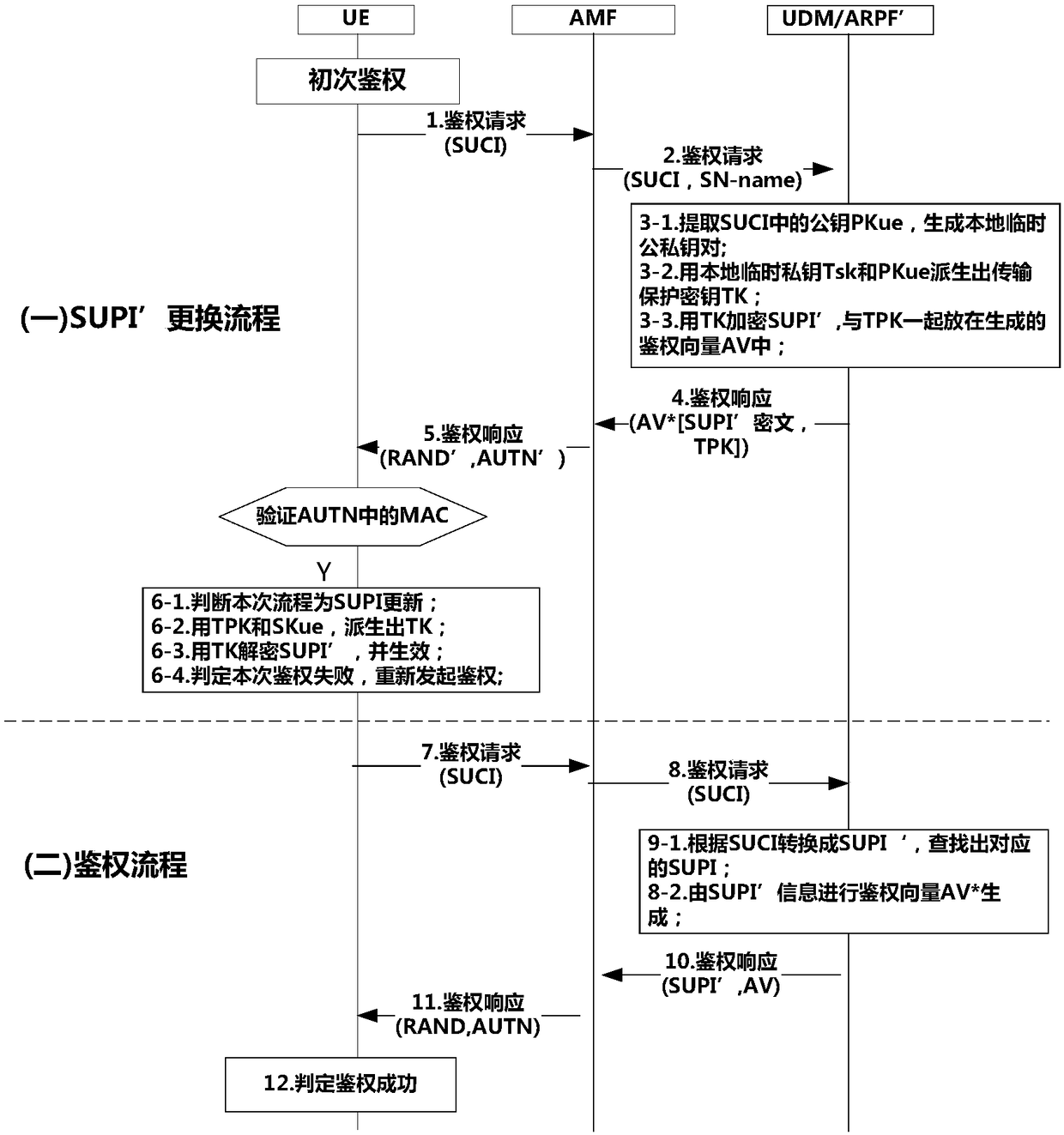
[0098] A method for protecting SUPI using 5G AKA is disclosed. Applied to the user terminal side, such as Figure 6 shown, including the following steps:
[0099] Step S201, sending an authentication request to the core network, encrypting SUPI to obtain SUCI, and reporting SUCI and the temporary public key to the core network;
[0100] Step S202, receiving and verifying the authentication response information issued by the core network, when the verification is successful, performing a normal authentication process; when the verification fails, performing SUPI' replacement;
[0101] Step S203, initiate a second authentication, and obtain a second authentication response for verification.
[0102] Compared with the prior art, this embodiment provides a method for protecting SUPI by using the 5G-AKA protocol. The cost of network transformation is low, users are indifferent, high in efficiency, and the original security of network authentication is maintained; on the premise ...
Embodiment 3
[0116] A method for protecting SUPI by using 5G-AKA is disclosed, which is implemented interactively by the user terminal side and the network side, including the following steps:
[0117] Step S301, the terminal sends an authentication request to the core network, encrypts SUPI to obtain SUCI, and reports SUCI and the temporary public key to the core network; the core network receives the authentication request initiated by the terminal, decrypts the SUCI reported by the terminal, and obtains SUPI;
[0118] Step S302, the core network judges whether identity information needs to be replaced according to the level and sensitivity of the terminal; when it is determined that the identity information does not need to be replaced, use SUPI for authentication; when it is determined that the identity information needs to be replaced, randomly select from the alternative SUPI resource pool SUPI' serves as the new "in use" identity of the terminal;
[0119] Step S303, the core networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com