Network access control system and its control method
A technology for network access control and access request, applied in the direction of user identity/authority verification, instrument, character and pattern recognition, etc., can solve the problems of easy to forget passwords, hidden dangers, inconvenient use, etc., to achieve the effect of confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
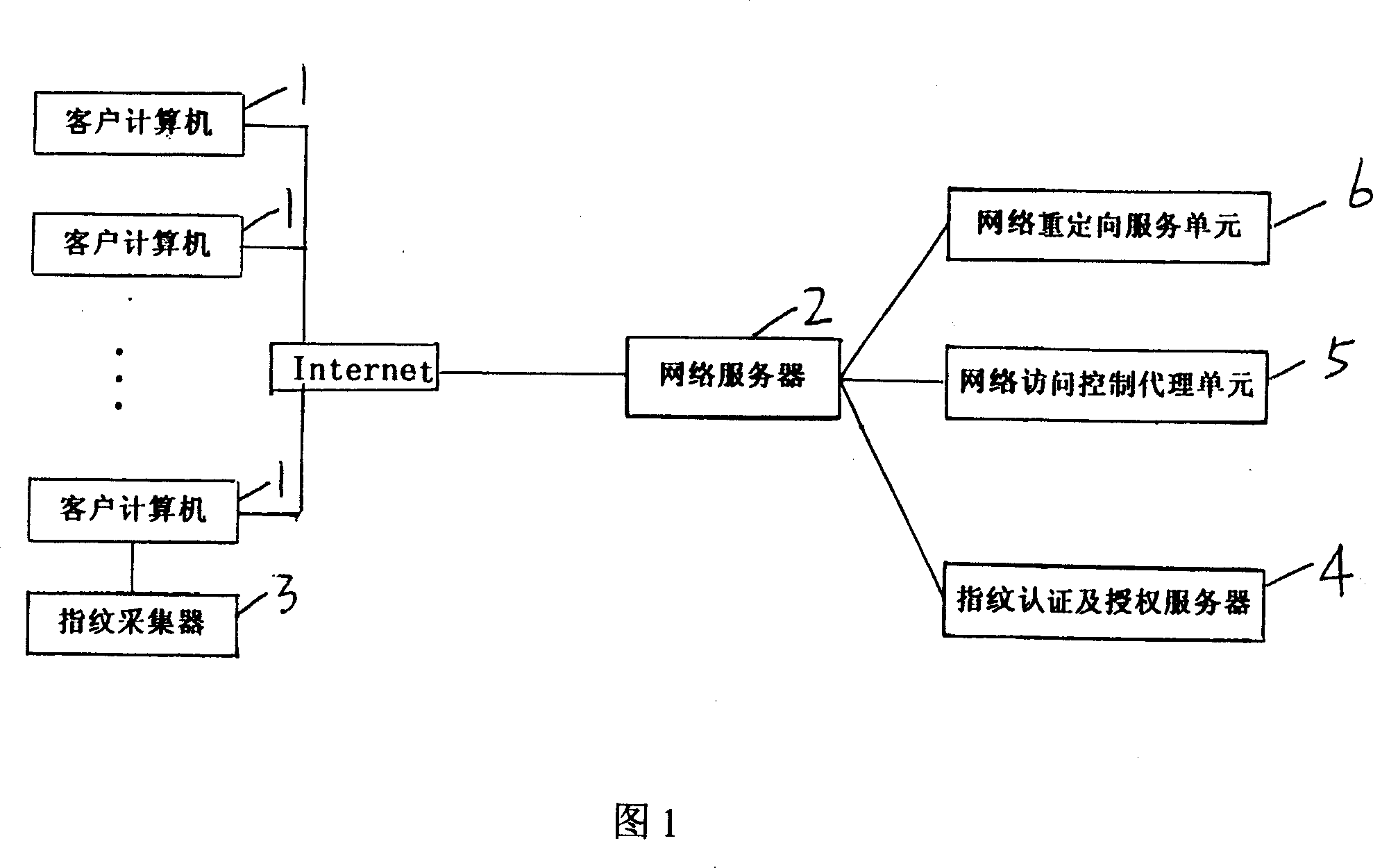
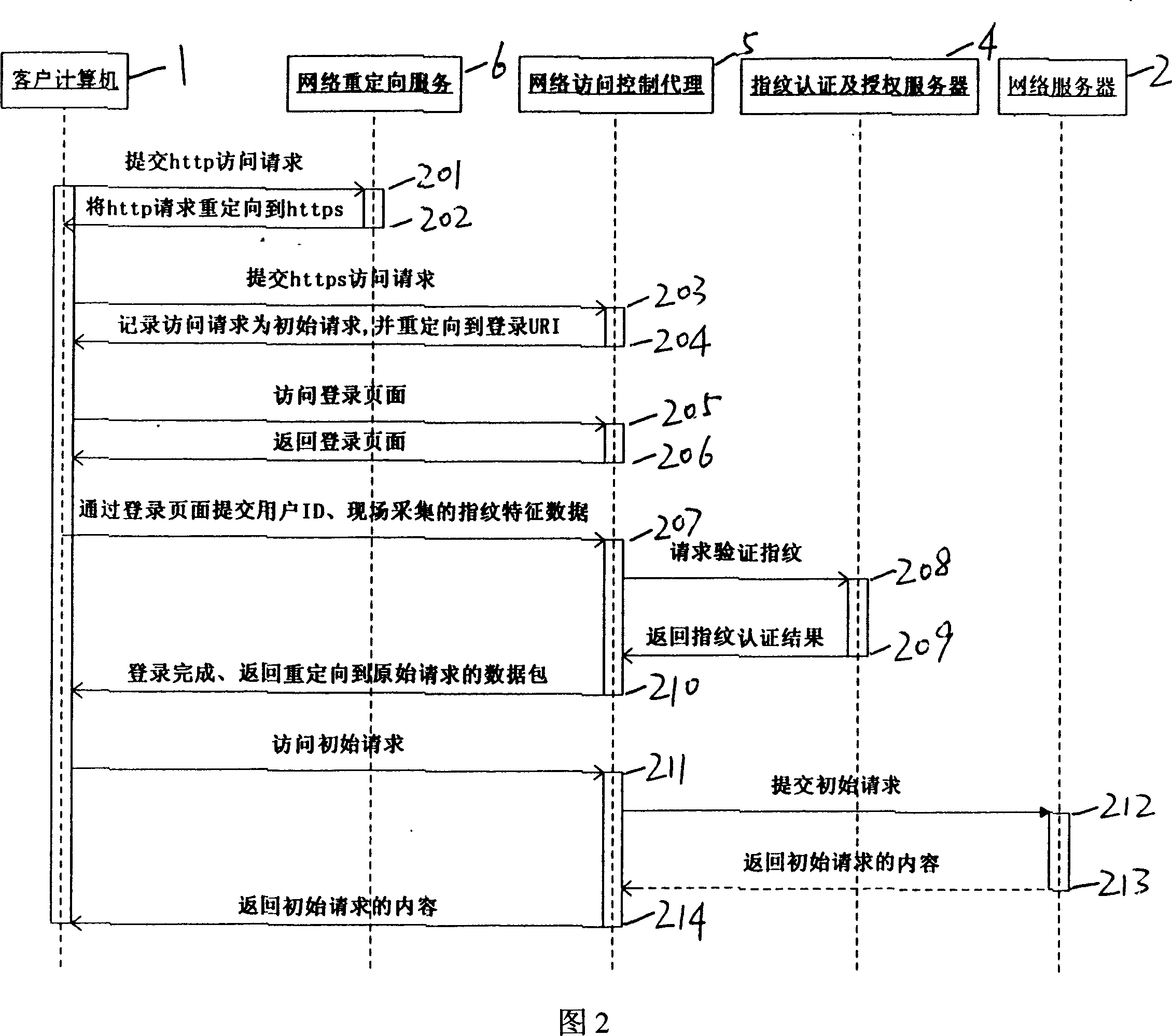
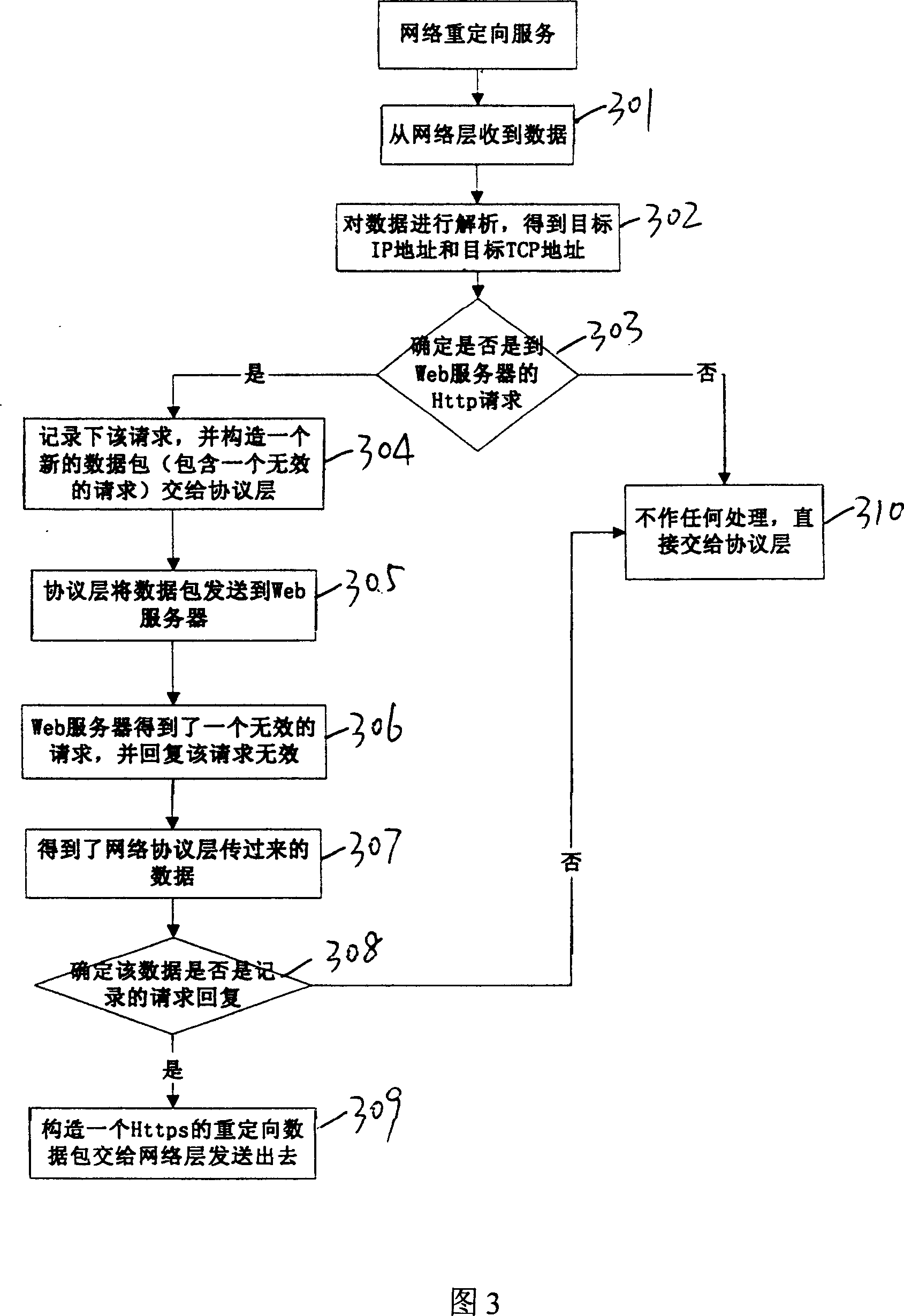
[0019] A network access control system, comprising a client personal computer 1, a server-side network server 2, characterized in that the network access control system also includes a fingerprint collector 3, the fingerprint collector 3 is installed on the client personal computer 1, used To collect fingerprint information; fingerprint authentication and authorization server 4 is connected with network server 2, is used for depositing user's fingerprint data and access authority list, and the fingerprint information that the fingerprint collector 3 that transmits by network server 2 newly collects is authenticated; The network access control agent unit 5 is installed on the network server 2 and is connected with the fingerprint authentication and authorization server 4; the network redirection service unit 6 is installed on the network server 2 to force...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com