Dependable computing unit based on homemade TCM and operation method thereof
A credible computing and credible technology, applied in computing, computer security devices, instruments, etc., can solve problems such as hardware integrity protection, malicious programs cannot be prevented, and operation security cannot be guaranteed, etc., to achieve wide system application potential, concurrent The effect of large working capacity and perfect functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
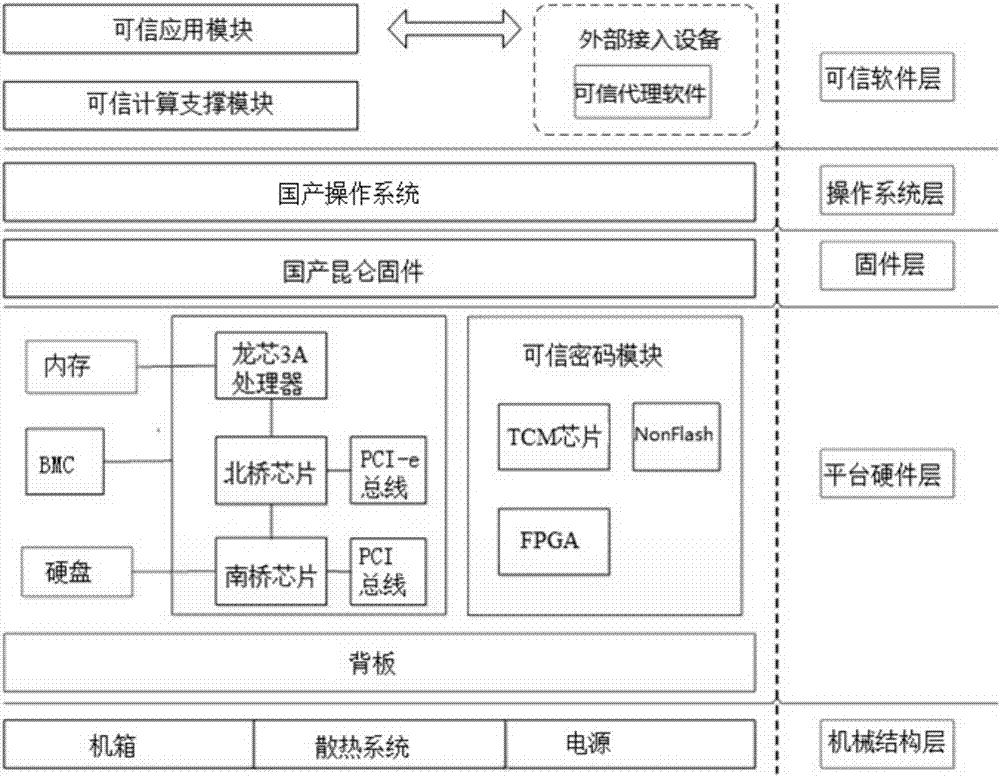
[0044] A trusted computing unit based on domestic TCM, including a mechanical structure layer, a platform hardware layer, a firmware layer, an operating system layer, and a trusted software layer;
[0045] The mechanical structure layer includes the chassis, cooling system, and power supply; the firmware layer includes Kunlun firmware; the operating system layer includes the operating system; the platform hardware layer includes the backplane, the computing unit module, and the trusted password module; the trusted software layer includes the trusted application module, Trusted computing support module; such as figure 1 shown;
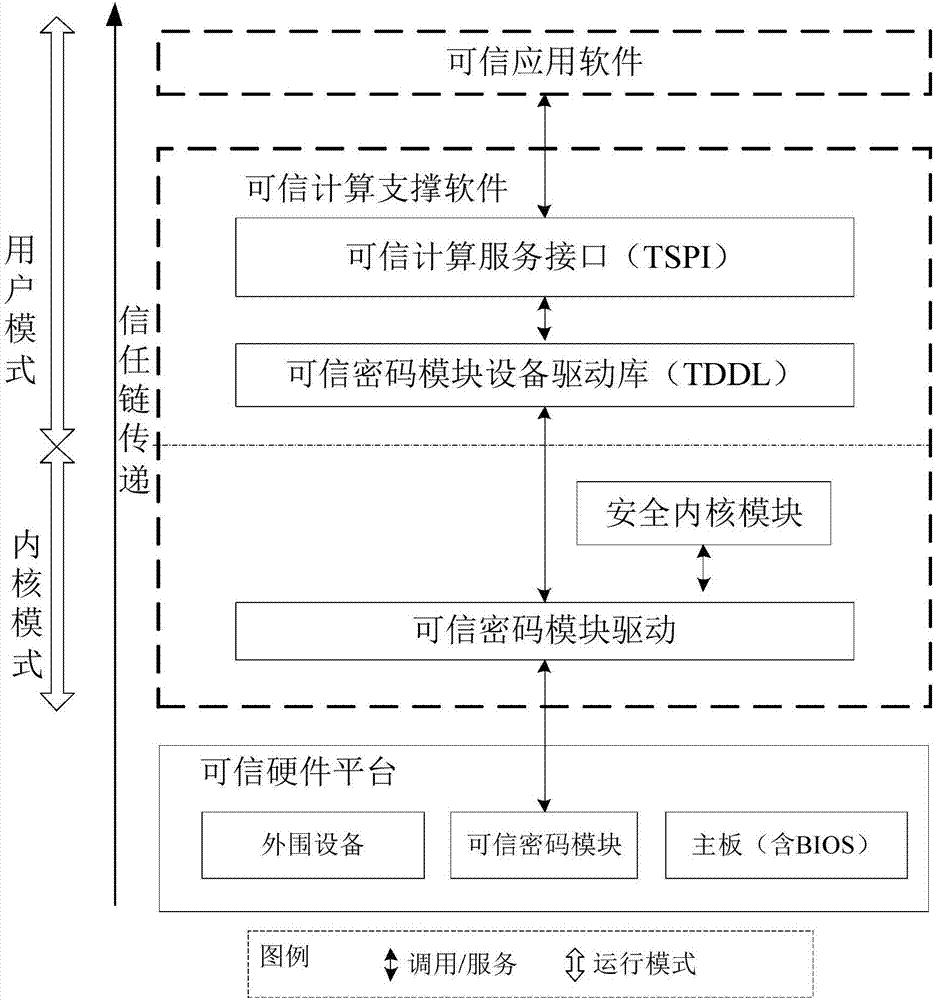
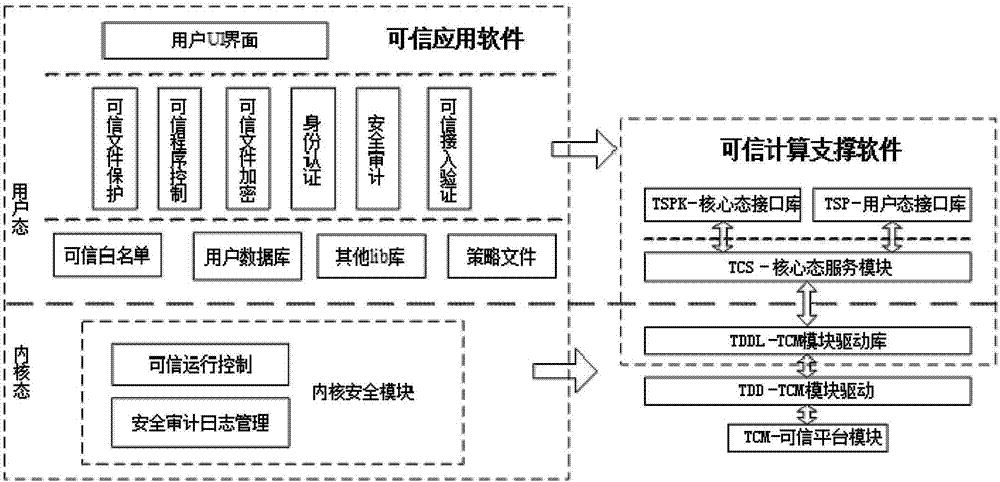
[0046] The trusted computing support module is a bridge for the trusted application module to access the trusted cryptographic module. The trusted application module uses the security functions provided by the trusted cryptographic module by calling the interface of the trusted software base and the trusted software service. The security functions inclu...
Embodiment 2
[0057] A kind of operation method of the trusted computing unit based on domestic TCM described in embodiment 1, comprises the steps as follows:
[0058] (1) After the system is turned on, measure the integrity of the BIOS of the whole machine;
[0059] (2) Authenticate users;
[0060] (3) Measure the integrity of optical drives, hard disks, graphics card hardware and key kernel files;
[0061] (4) After the integrity measurement is completed, the system loads, enters the login interface, and invokes the USBKey and TCM chip to complete the identity authentication together;
[0062] (5) The access control of files is realized through trusted file encryption and trusted file protection during system operation; illegal program interception and application program tampering are prevented through trusted program control;
[0063] (6) The trusted access control function is mainly to realize the access control of the client. By collecting and judging the software and hardware infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com