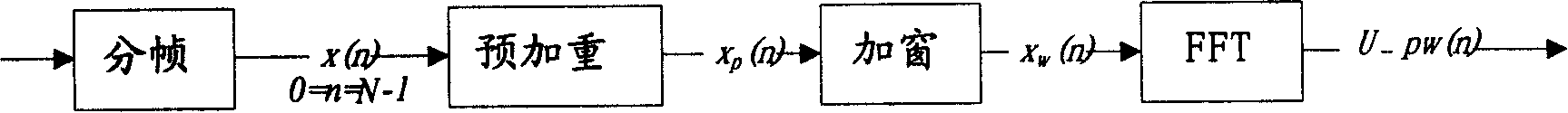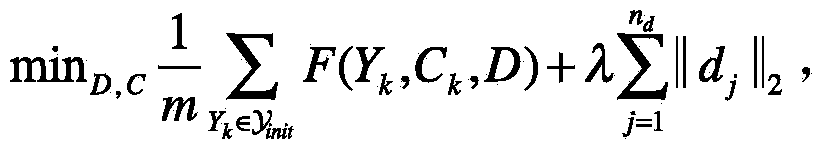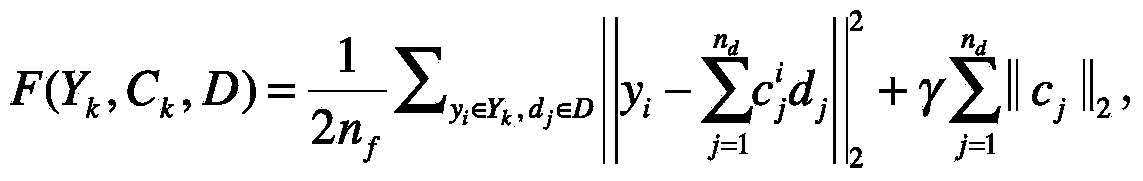Patents
Literature
487 results about "Code algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An algorithm in code looks like a food recipe or set of assembly instructions in English. The difference is that an algorithm in code is written in a programming language rather than in English (or some other human written language).
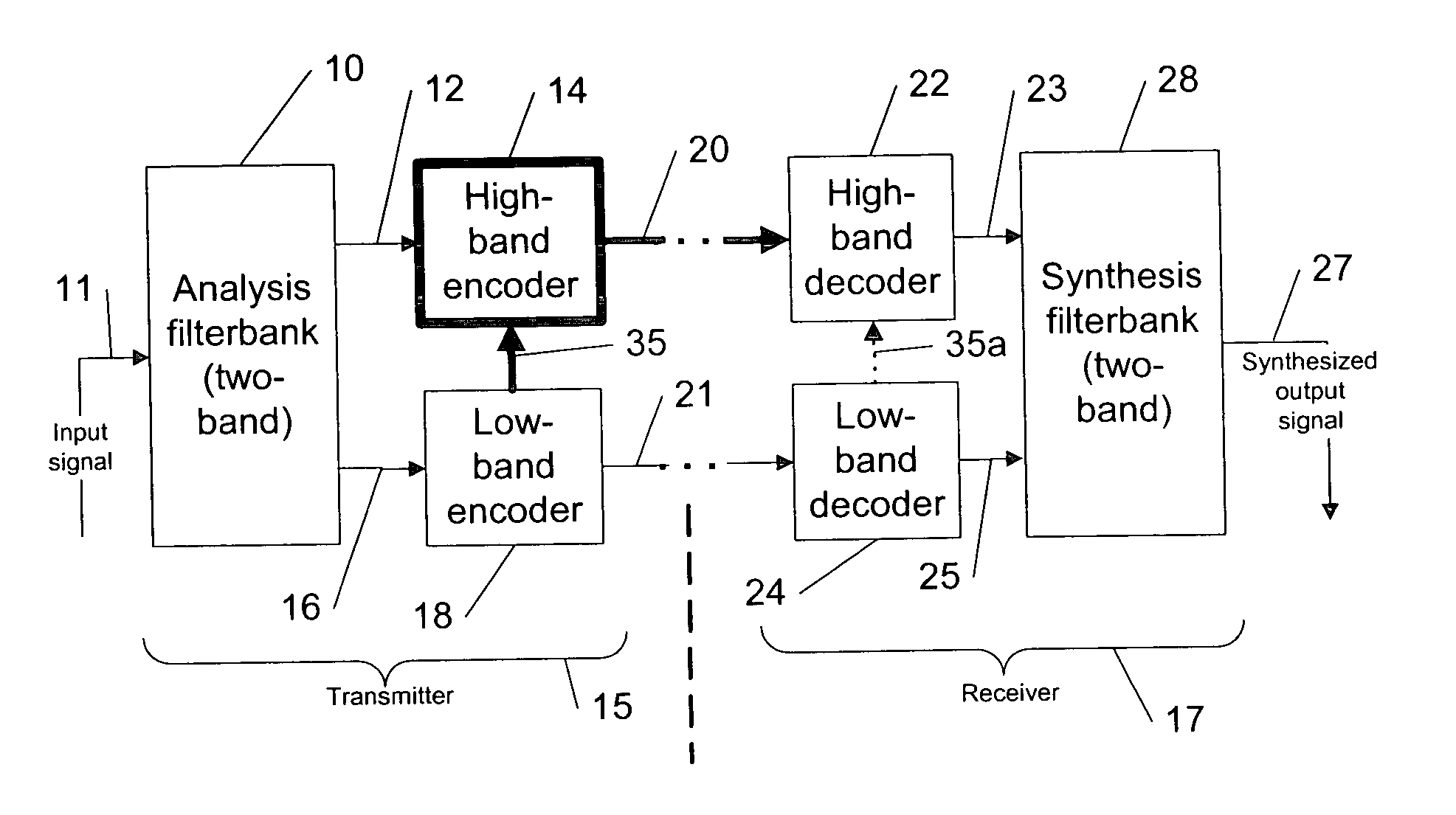
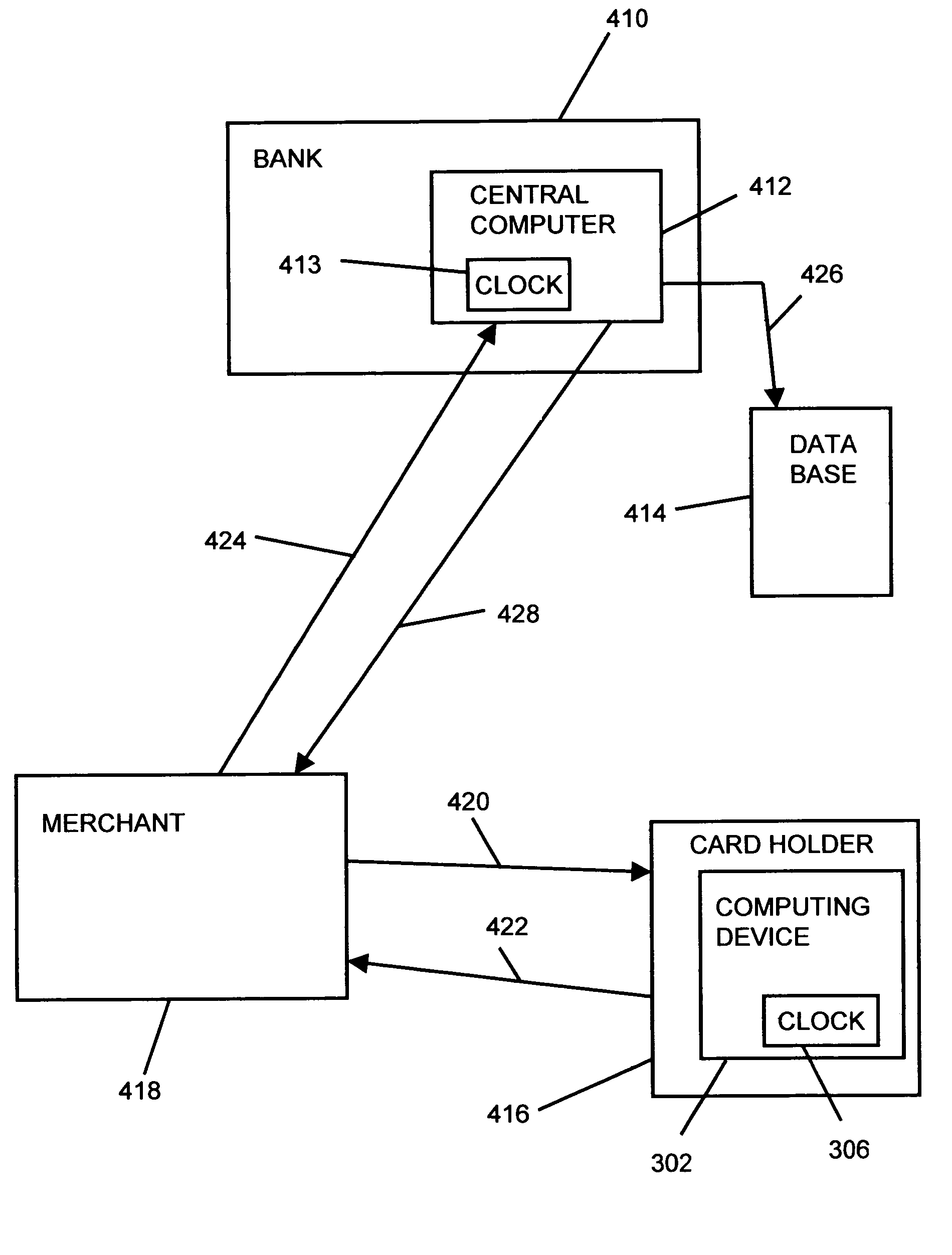
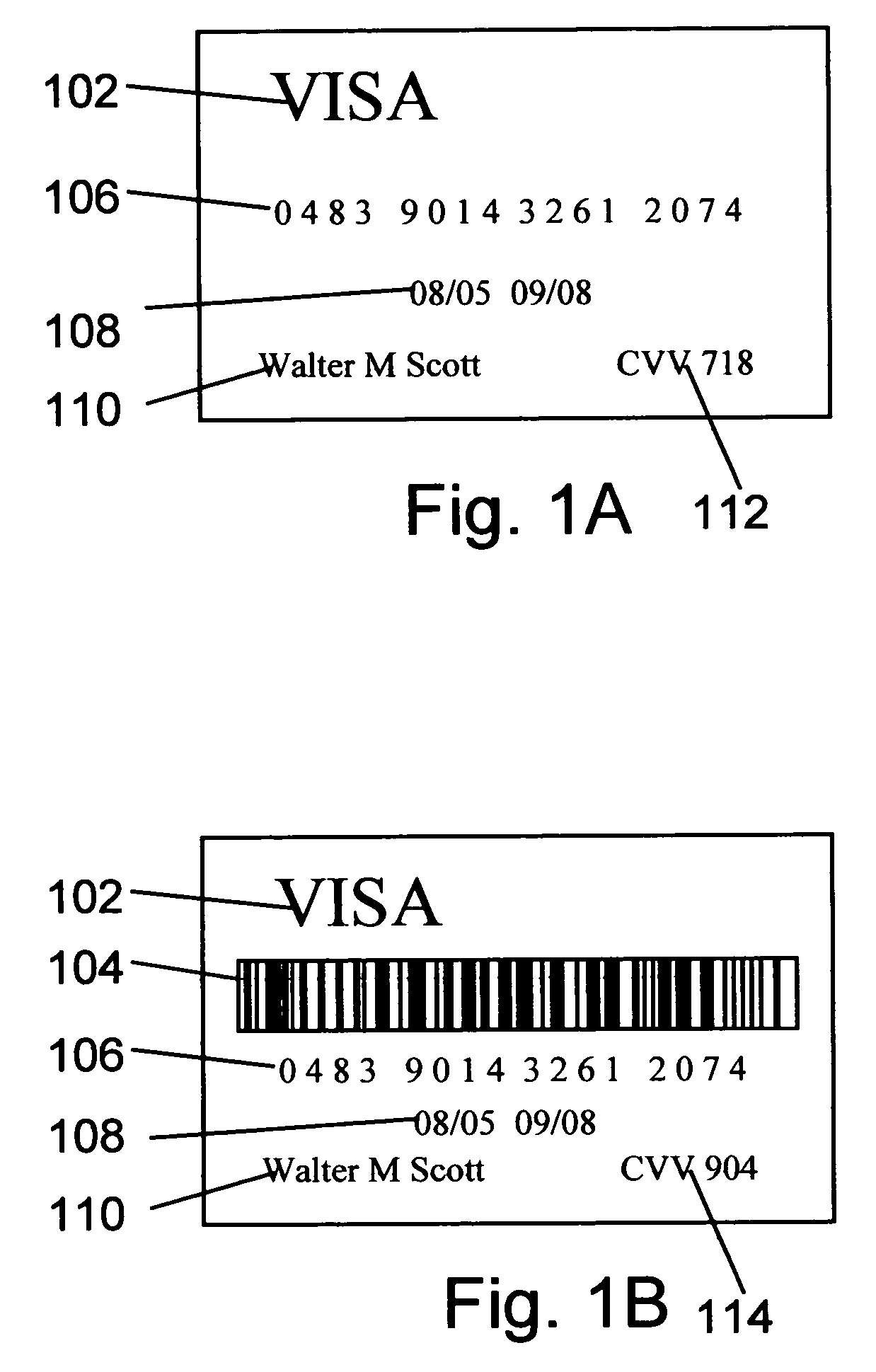
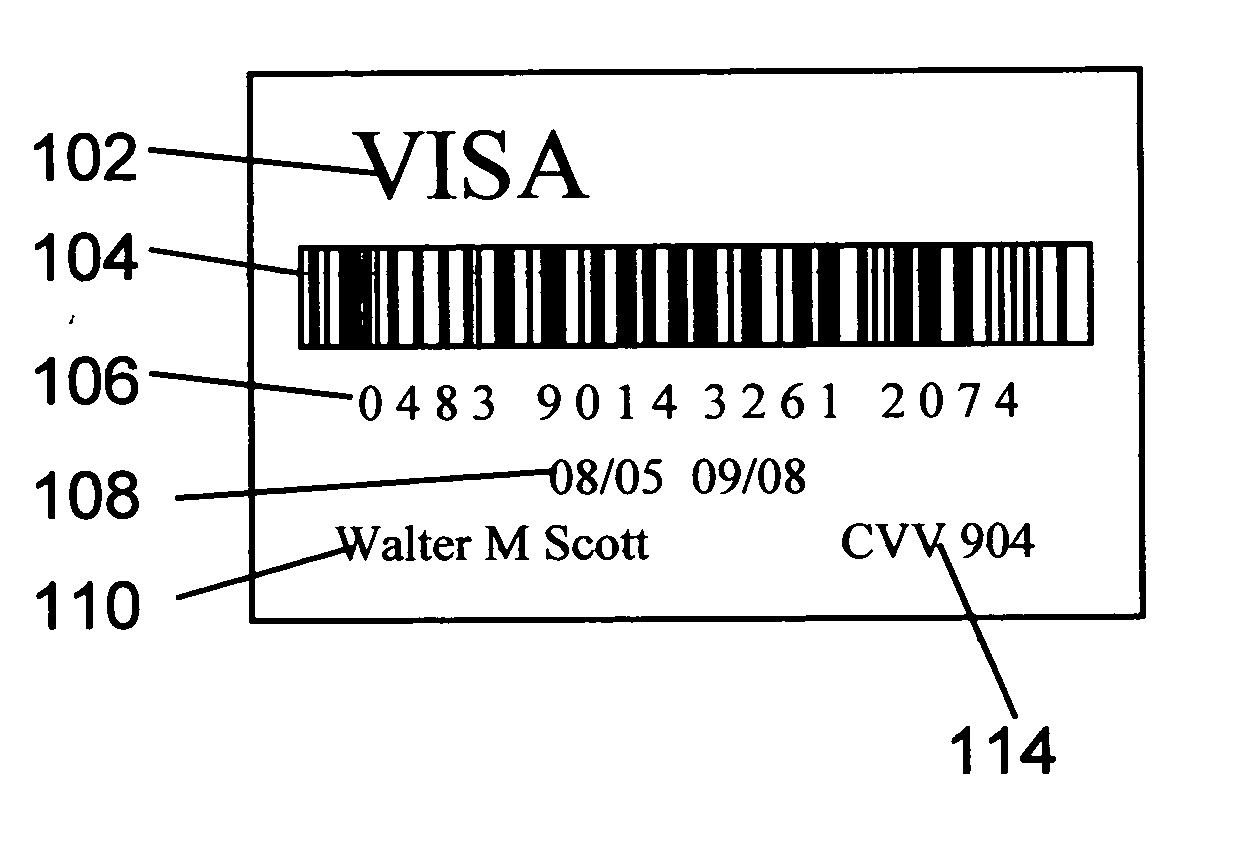
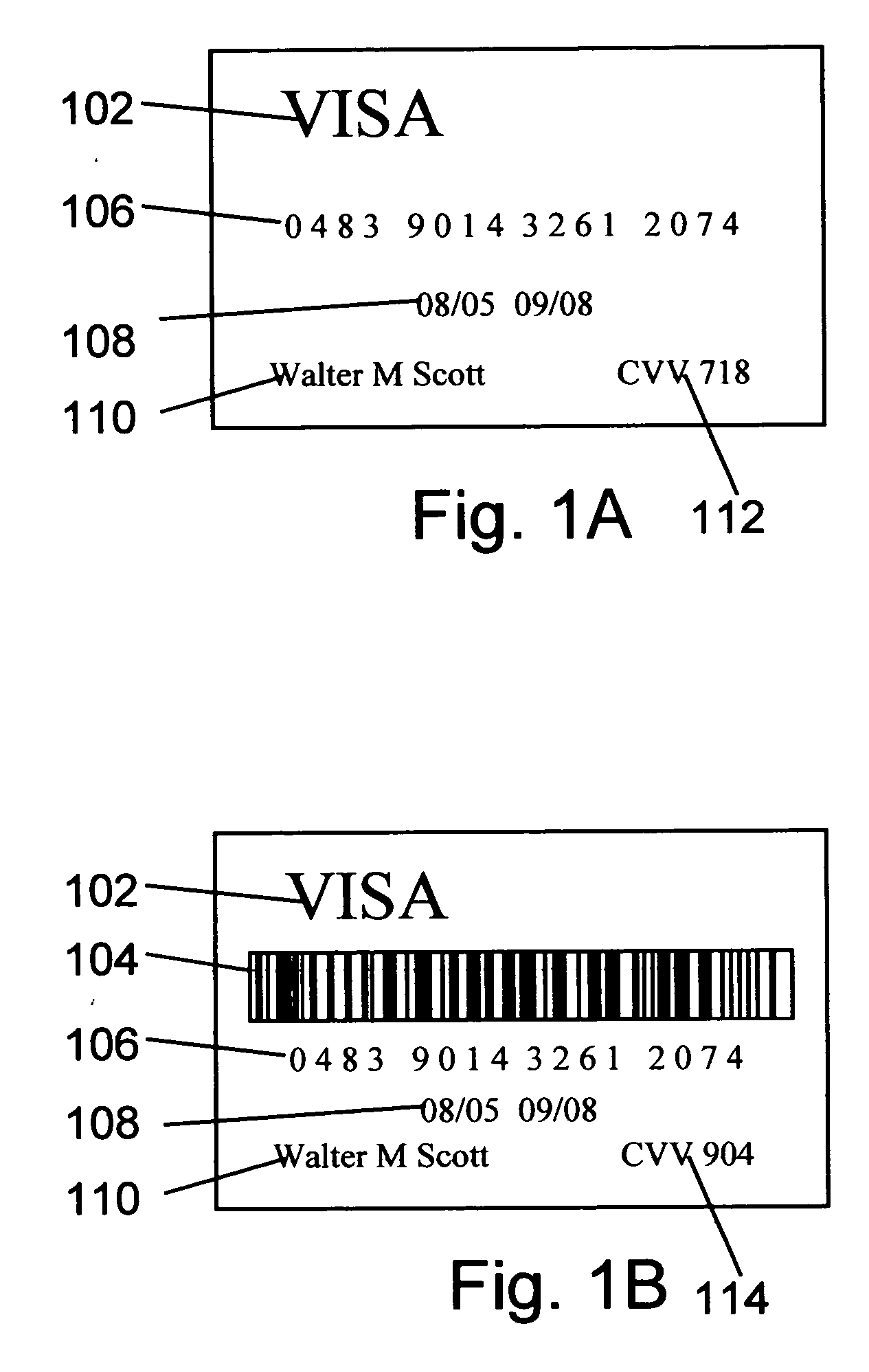
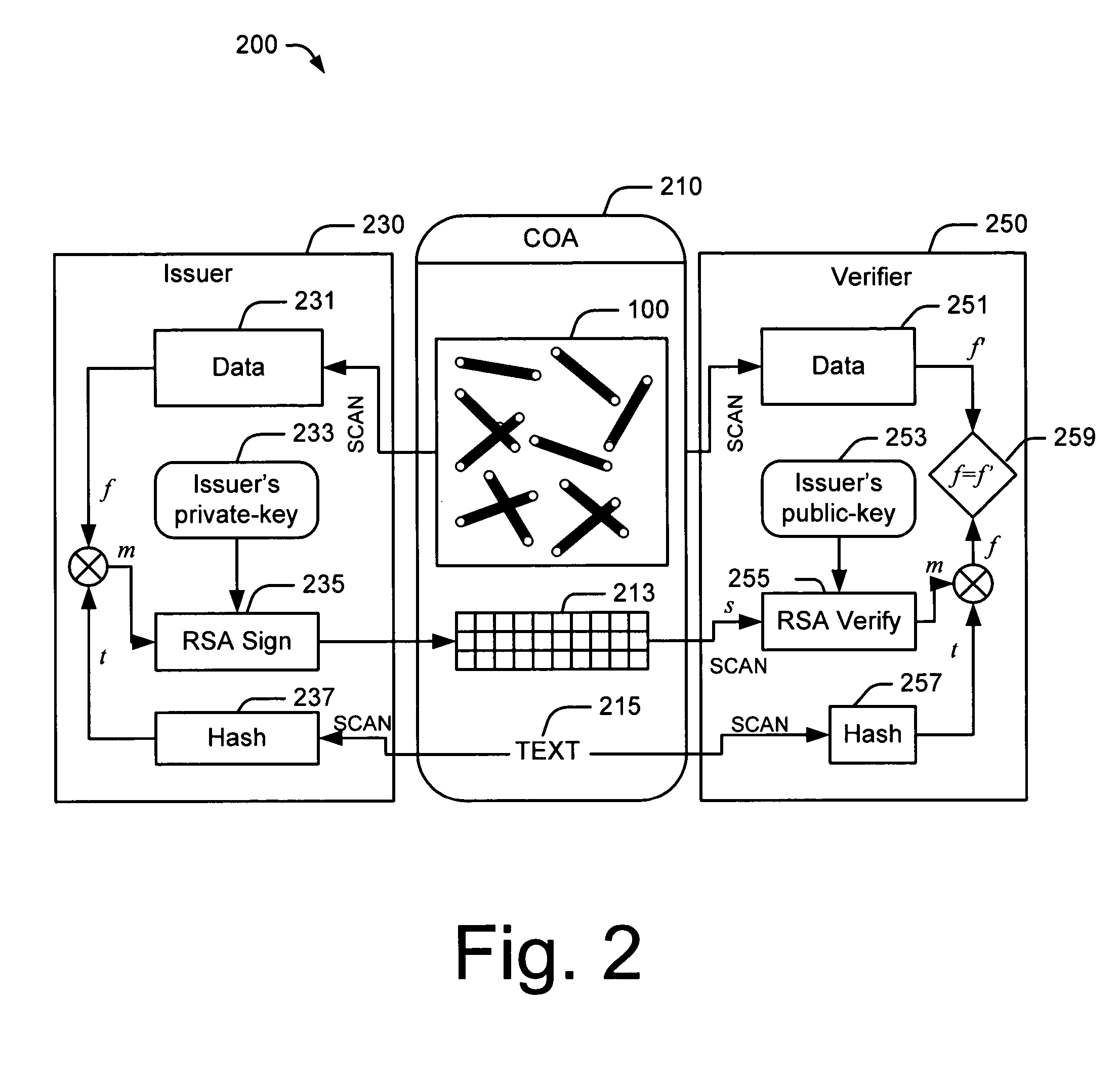
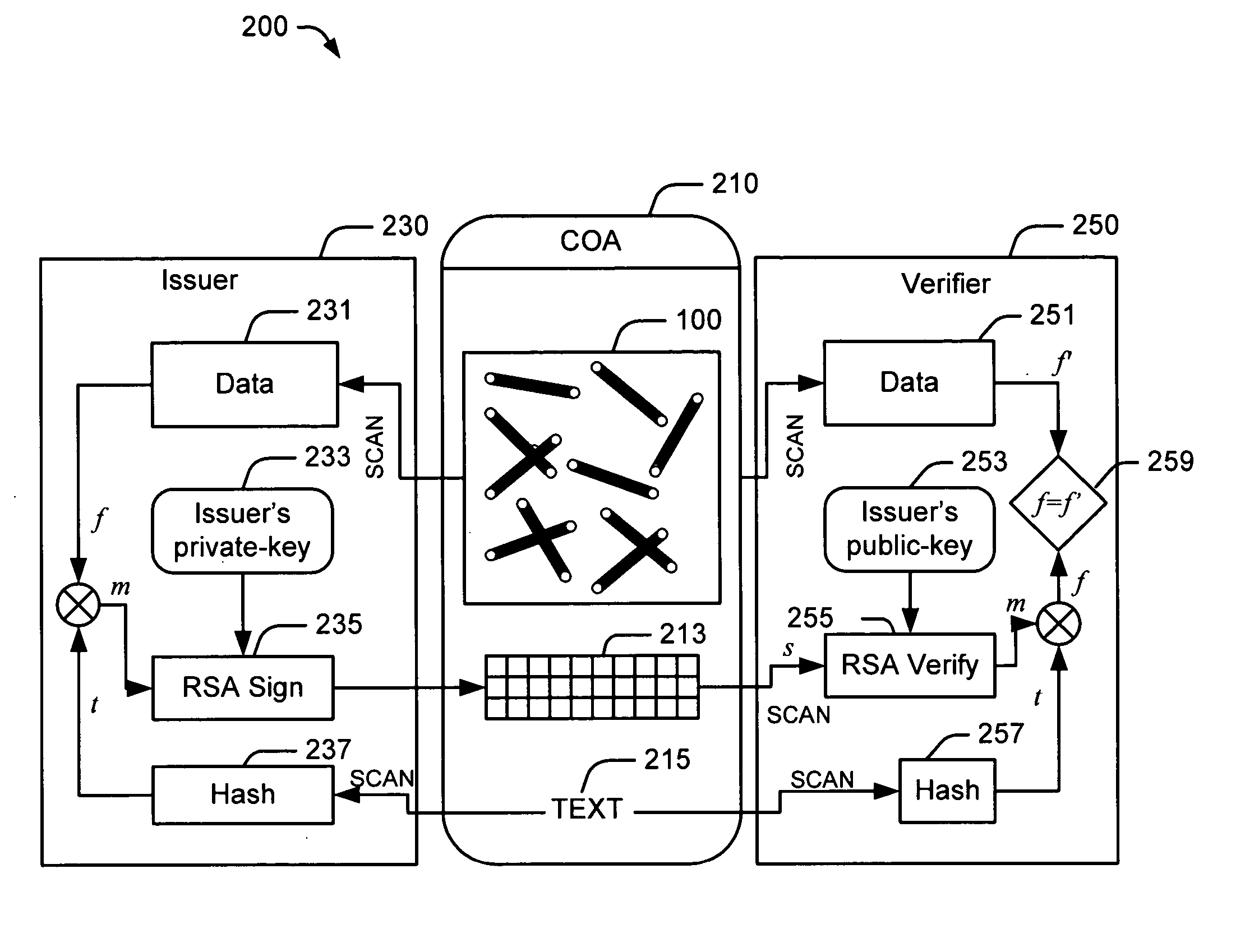
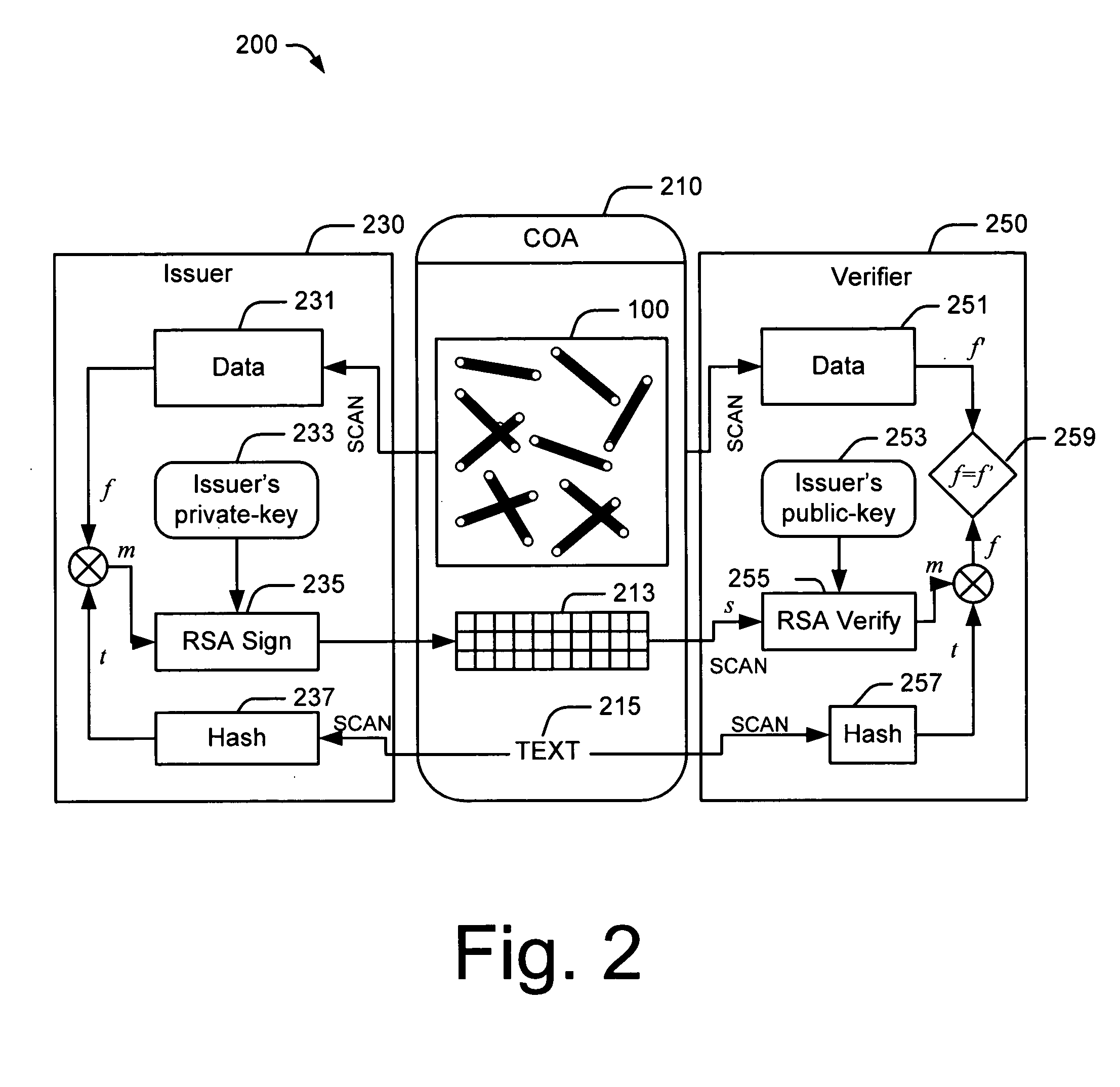
System, method and program product for account transaction validation
ActiveUS7347361B2Low costEasy to manufactureFinanceCredit schemesTransaction dataFinancial transaction
Owner:LOVETT ROBERT
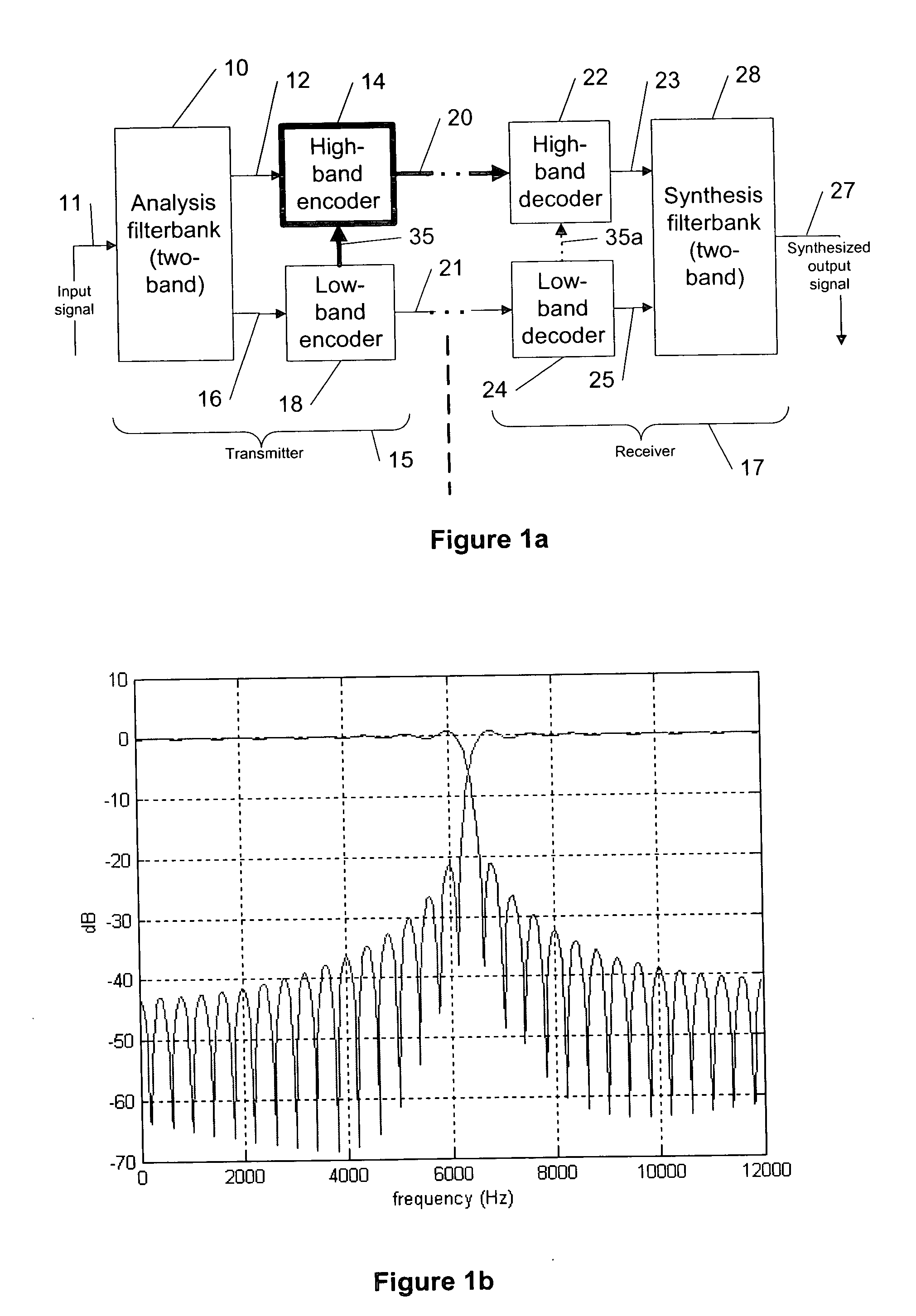
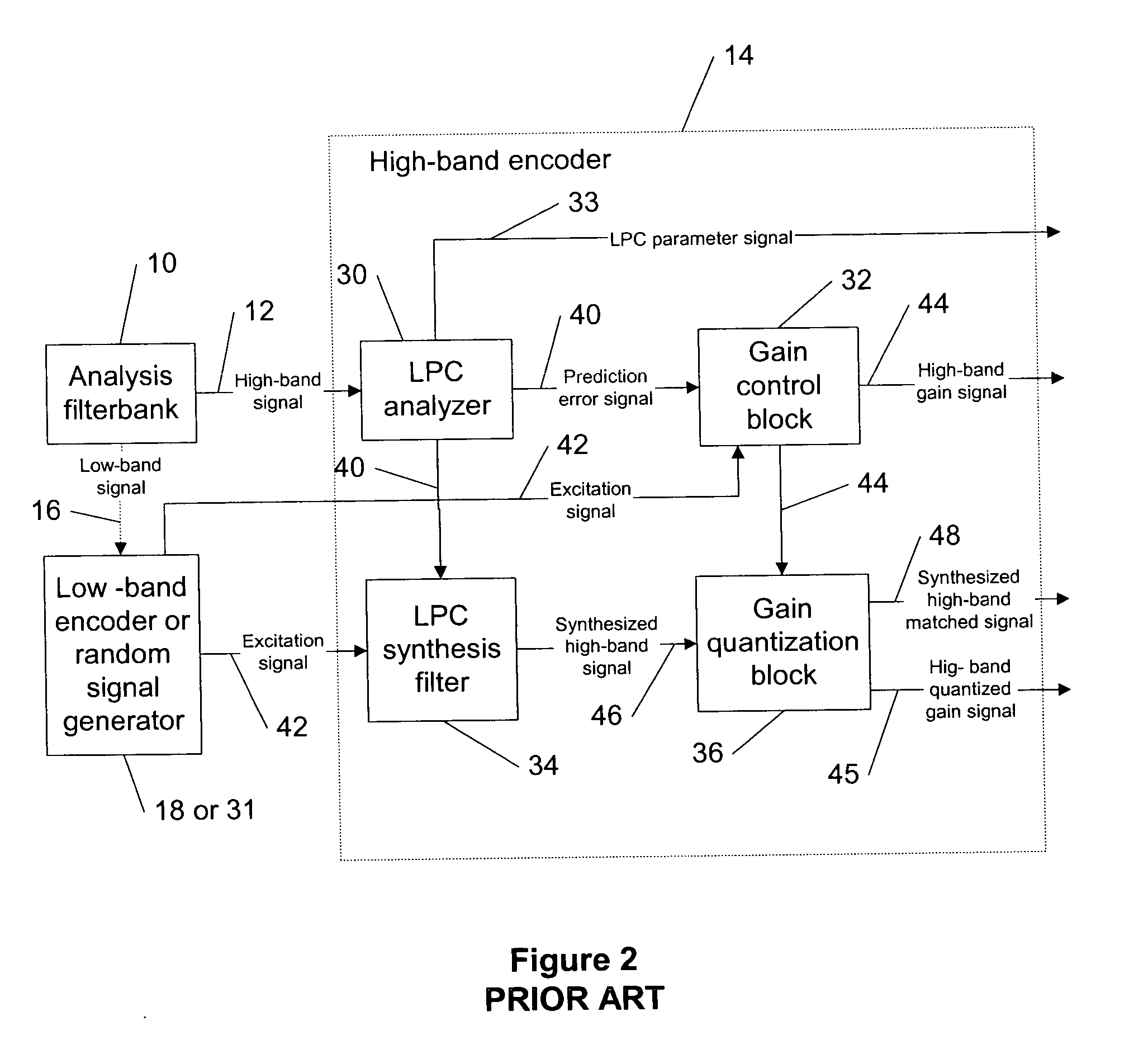
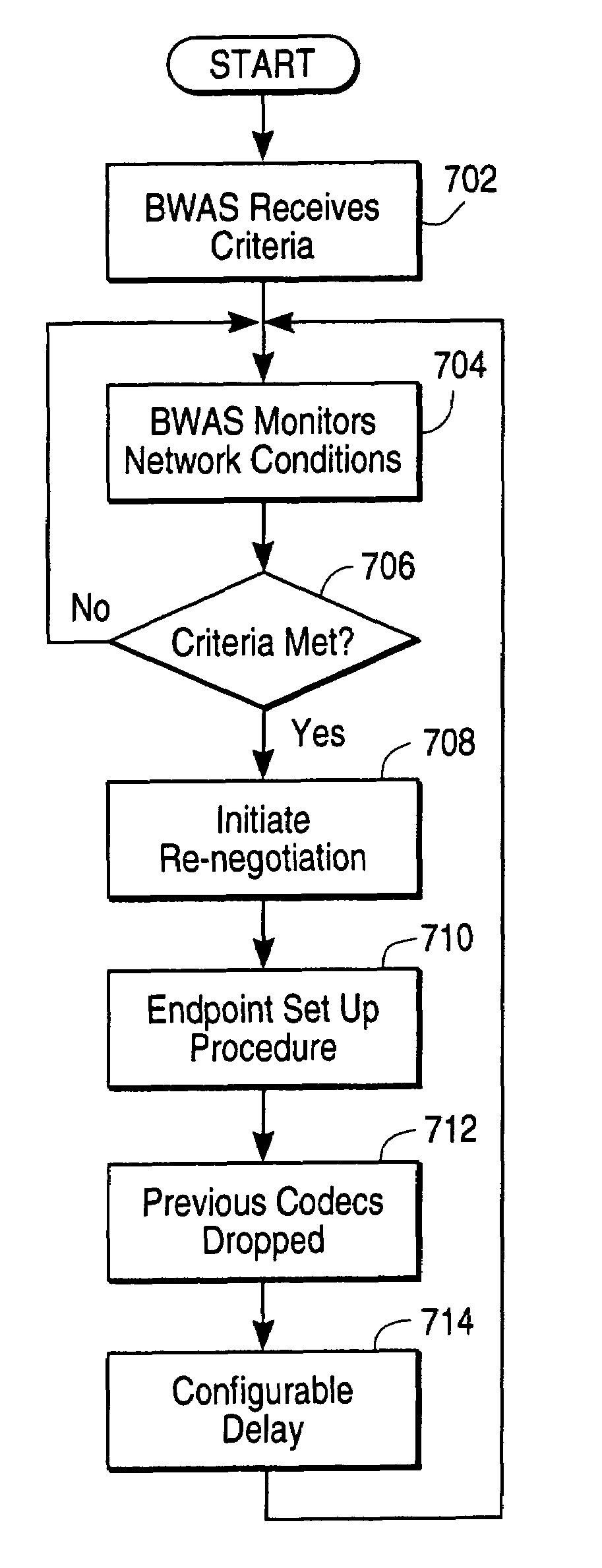
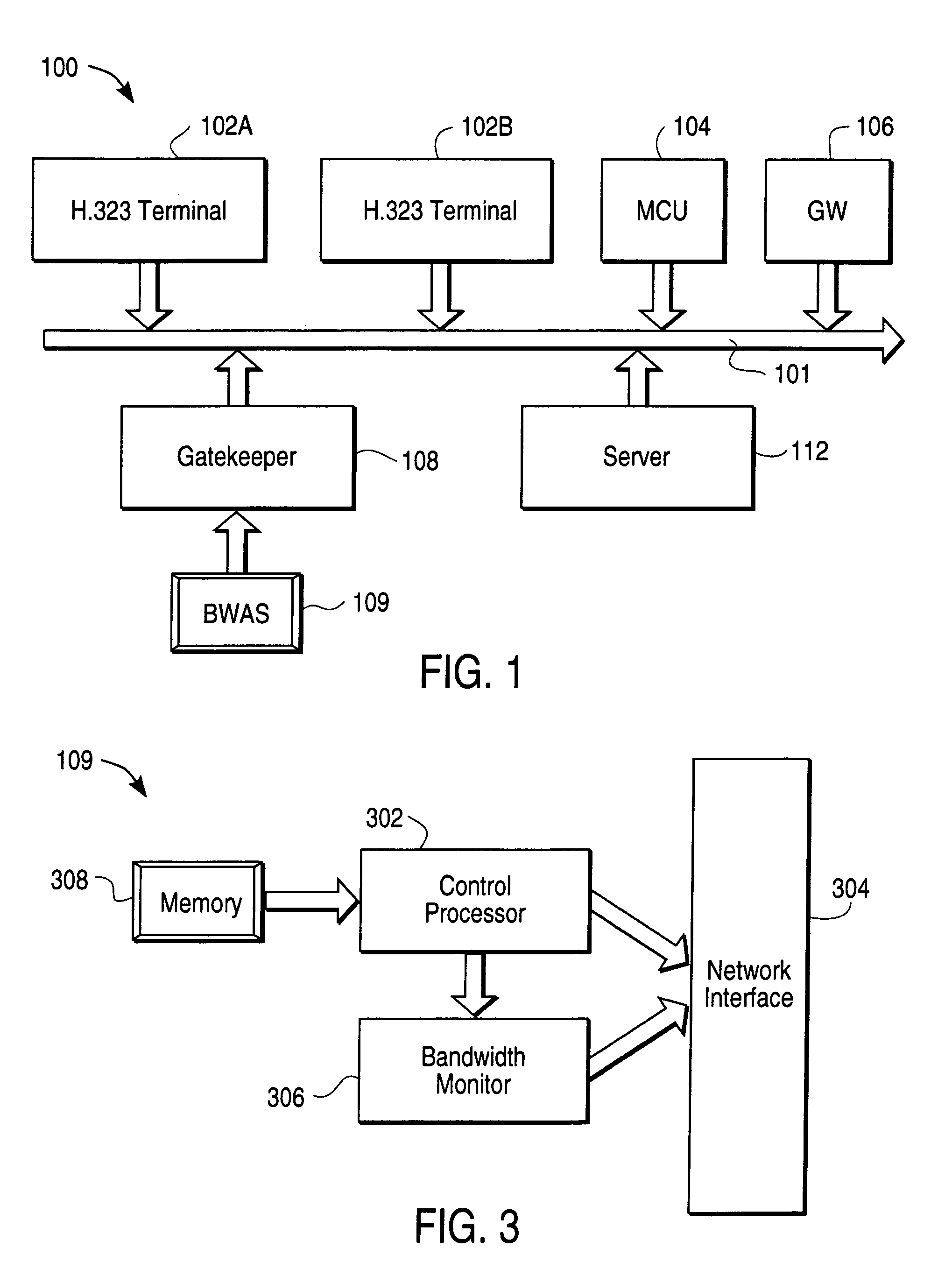
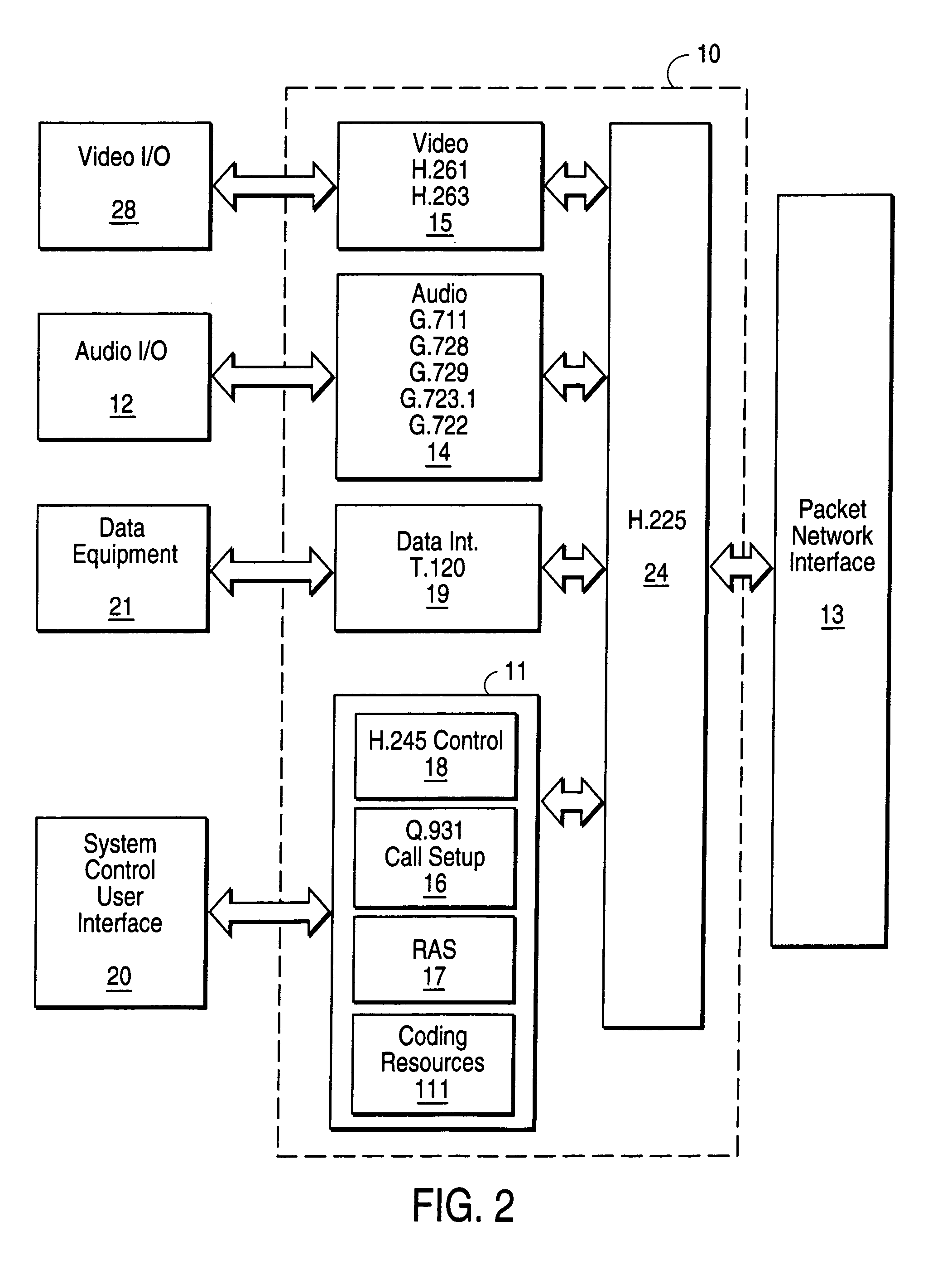
System and method for dynamic codec alteration
InactiveUS7023839B1Increase system bandwidthLess bandwidth-intenseTelephone data network interconnectionsTime-division multiplexHigh bandwidthMonitoring system
A bandwidth adjustment server (BWAS) (109) is provided which monitors system bandwidth usage, sends requests to terminals (102A, 102B and / or 106), to identify their coding capabilities, and directs each of the terminals to adjust their coding algorithms based on system bandwidth usage. If system bandwidth usage is high, the BWAS (109) requires the terminals to employ a less bandwidth intensive coding algorithm; similarly, when system bandwidth usage is low, the BWAS (109) will allow the terminals to employ higher bandwidth use coding algorithms. Codec renegotiation may be initiated if there is a disparity between the bandwidth allocated to new connections versus ongoing connections or an increase in data traffic.
Owner:SIEMENS ENTERPRISE COMM GMBH & CO KG
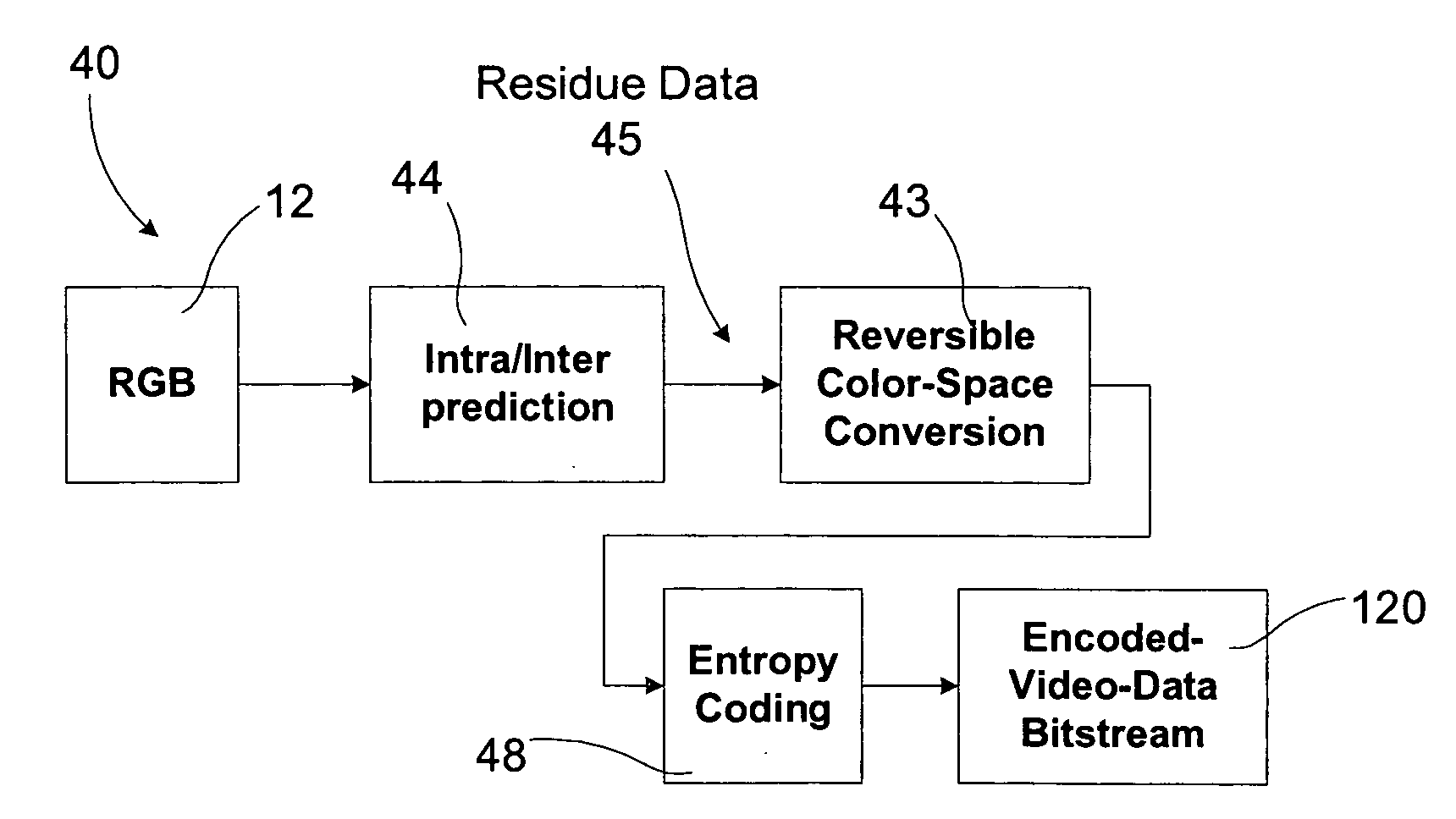
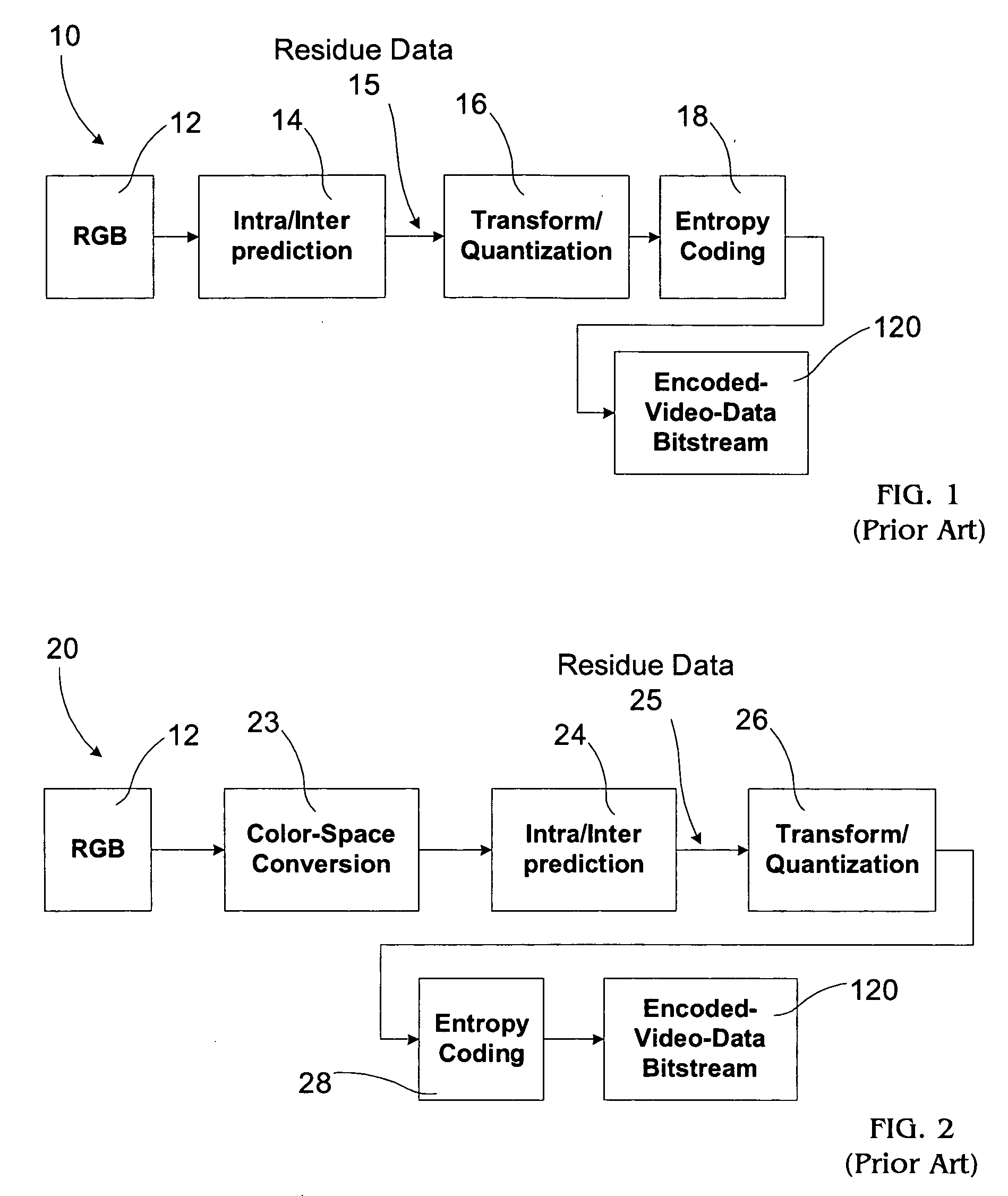
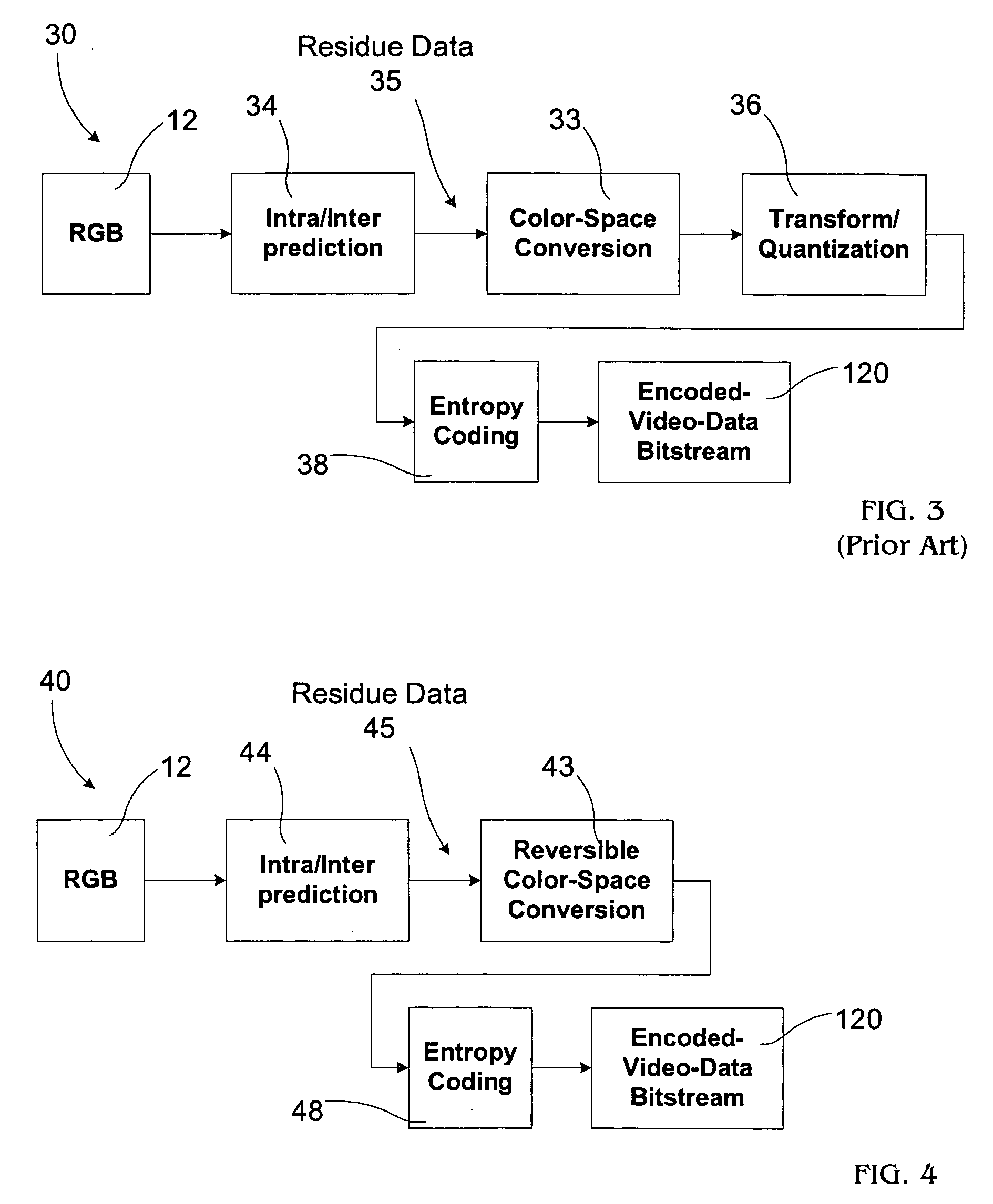
Video coding with residual color conversion using reversible YCoCg
InactiveUS20050259730A1Improve coding efficiencyHigh color fidelityColor television with pulse code modulationColor television with bandwidth reductionLossless codingFrame based
A video coding algorithm supports both lossy and lossless coding of video while maintaining high color fidelity and coding efficiency using an in-loop, reversible color transform. Accordingly, a method is provided to encode video data and decode the generated bitstream. The method includes generating a prediction-error signal by performing intra / inter-frame prediction on a plurality of video frames; generating a color-transformed, prediction-error signal by performing a reversible color-space transform on the prediction-error signal; and forming a bitstream based on the color-transformed prediction-error signal. The method may further include generating a color-space transformed error residual based on a bitstream; generating an error residual by performing a reversible color-space transform on the color-space transformed error residual; and generating a video frame based on the error residual.
Owner:SHARP LAB OF AMERICA INC
System, method and program product for account transaction validation
A system, method and program product for account transaction validation which may be downloaded or otherwise installed on a networked computing device such as a cell phone or other networked computing device. The networked computing device provides an encrypted validation code to a merchant for each transaction. The validation code is uniquely computed for each transaction and may be based on transaction time and / or other transaction data. The code algorithm is unique for each cardholder. Only the bank transaction center has knowledge of the particular algorithm for each cardholder. When transaction details such as transaction dollar amount are included in the generation of the code, the code may be used to validate the reported transaction dollar amount. An algorithm is disclosed for generating a unique code based on time and / or transaction dollar amount.
Owner:LOVETT ROBERT
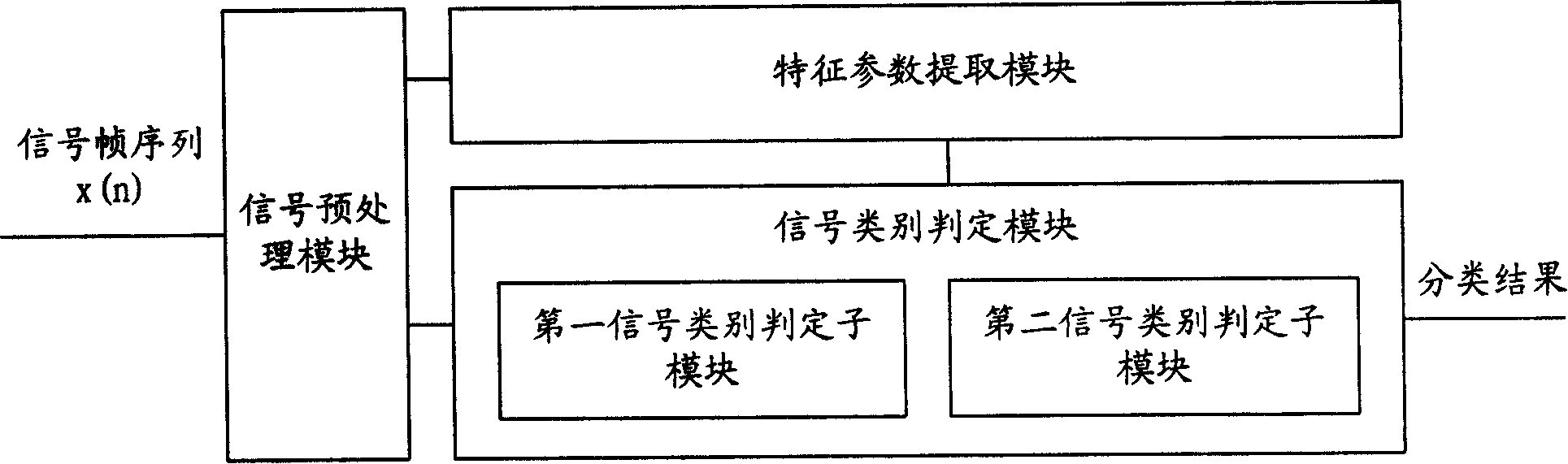
Sound activity detecting method and detector thereof
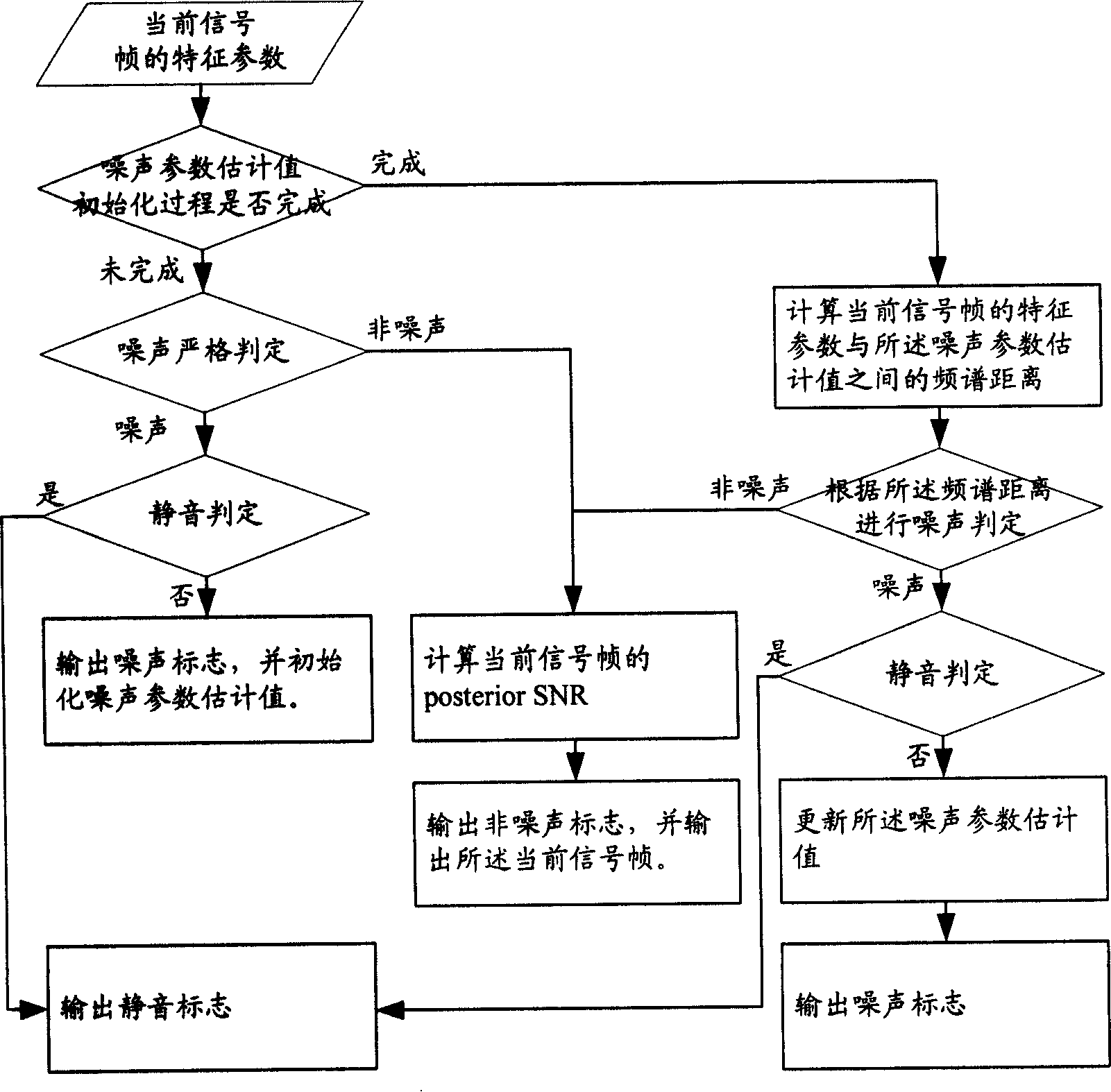
The invention discloses a sound activation detecting method and a sound activation detector, the core of which is: extracting the feature parameters of the current signal frame when the sound activation detection is needed; and determining the sound type of the current signal frame according to the feature parameters and the set parameter threshold. By the invention, the specific coding algorithm is not relied on when the used feature parameters in the classifying process are extracted, thus being convenient for maintenance and updating, and classifying the input signals into more sound types. When being used in the sound coding technical field, the invention can not only be used as new-opened variable rate sound frequency coding algorithm and standard rate selection foundation, but also provide foundation of rate selection for prior variable rate voice or sound frequency coding standard without VAD algorithm. The invention can be applicable to voice boosting, voice recognition, recognition of spoken person and other voice signal processing fields with strong commonality.
Owner:HUAWEI TECH CO LTD
Scratch protection in tape data storage system
InactiveUS6282039B1Improve protectionEvenly distributedDigital data storage formatRecord information storageData setMagnetic tape
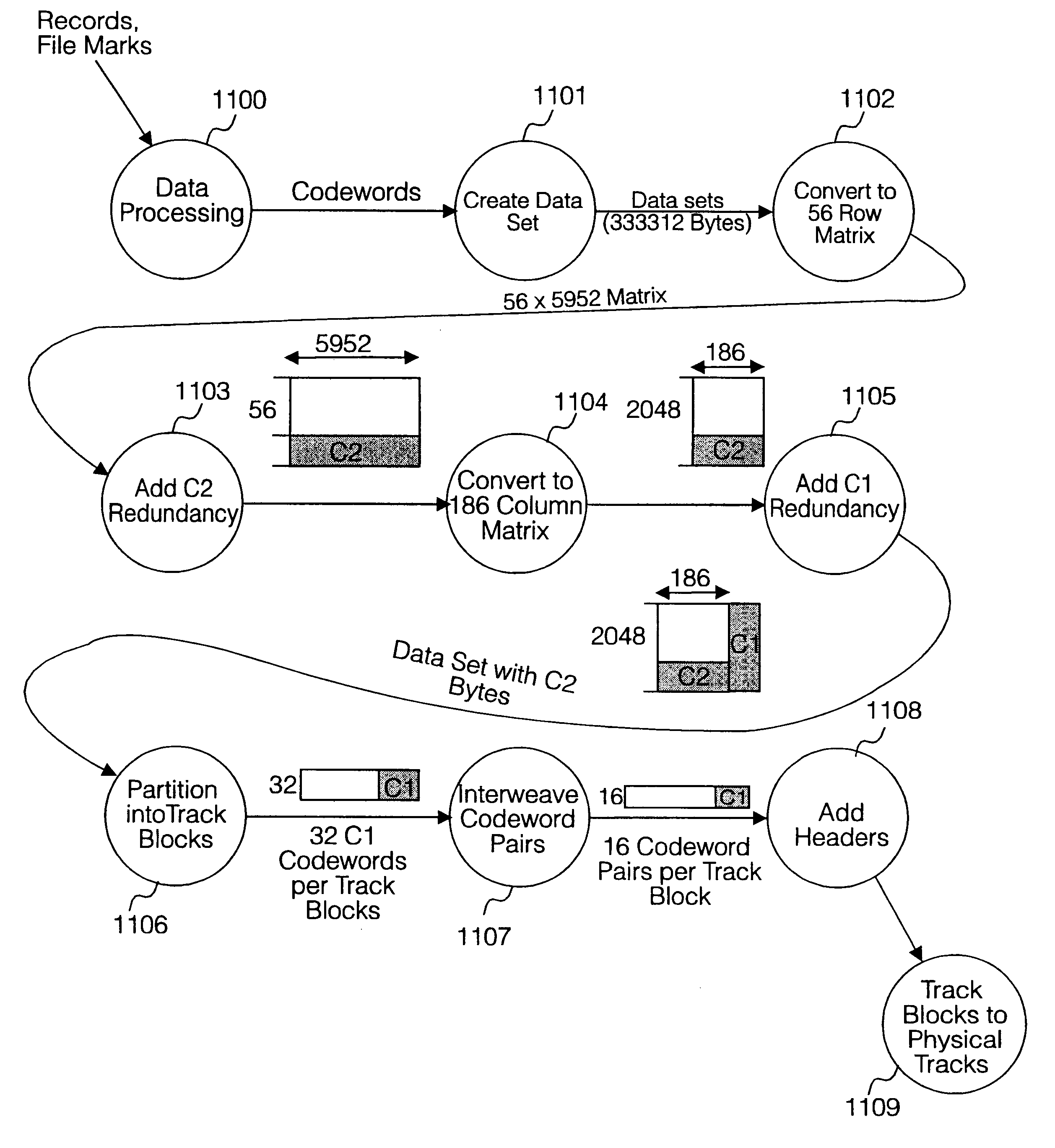
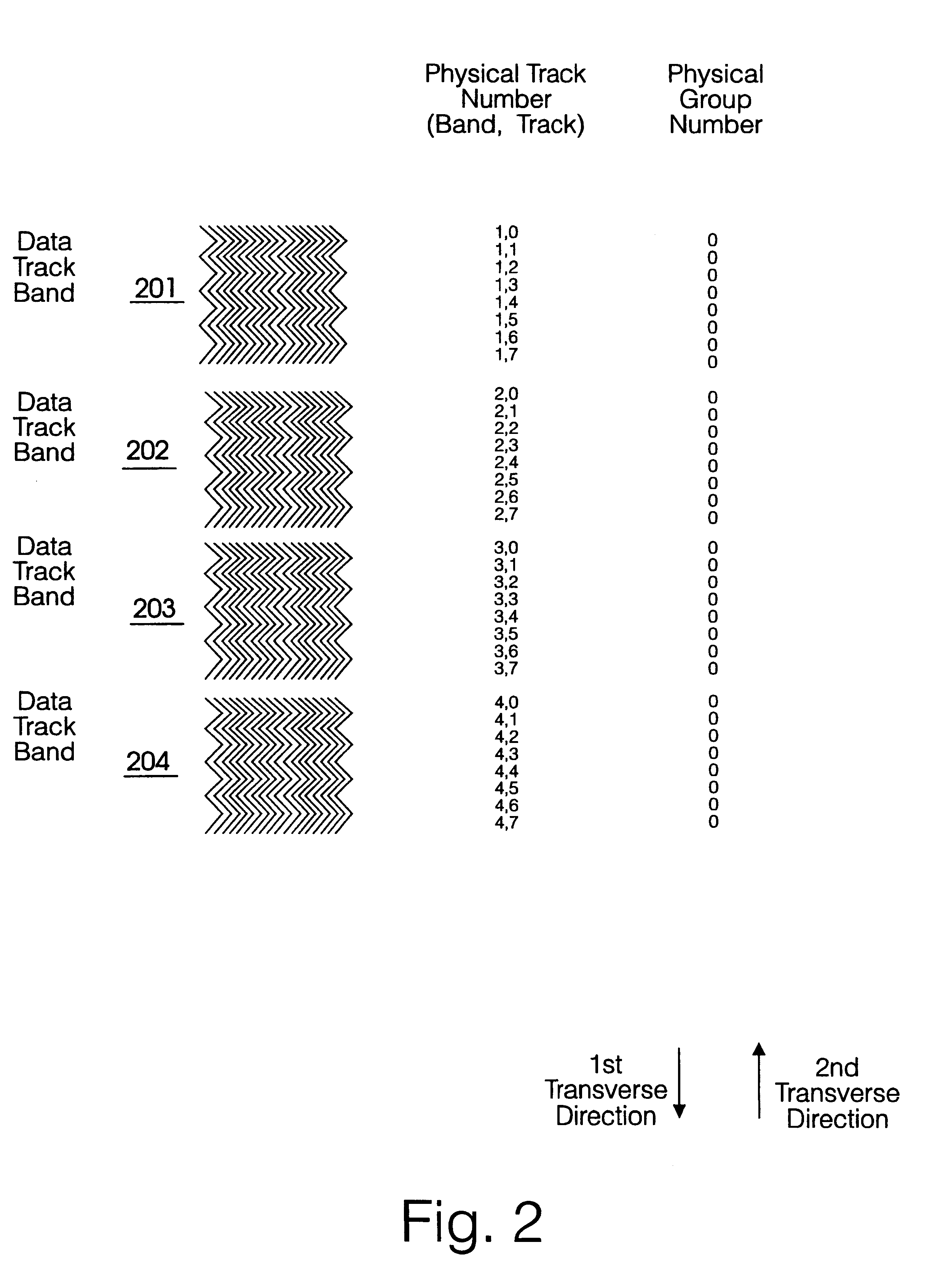
A method of redundancy coding of user data received from a host apparatus and storage of said coded data on a magnetic tape data storage medium comprises inputting a byte stream of user data into a buffer and assembling a plurality of data sets in the buffer; for each data set assembling a data set into a two-dimensional data array and (1103) applying a second redundancy coding algorithm (C2 parity) to the two-dimensional data set in a second dimension; applying (1105) a first redundancy coding (C1 parity) algorithm to the second redundancy coded data array in a first dimension to form a two-dimensional data frame having second and first redundancy coding in respective second and first dimensions, the two-dimensional data frame comprising a plurality of rows, each row comprising a first codeword and a plurality of columns, each column comprising a second codeword; partitioning the two-dimensional data frame into a plurality of logical track blocks (1106) each comprising a plurality of first codewords; and recording (1110) each logical track block to a corresponding respective physical track on the magnetic tape data storage medium. Redundancy coding of a data frame is distributed across a plurality of other data frames along the tape, and redundancy bytes of each data frame are distributed across a plurality of data tracks. Redundancy coding may be distributed diagonally across a width of the tape. Data obliterated due to damage to individual physical recorded tracks or sections of tracks on the tape may be recovered from redundant coding data distributed across other adjacent parallel physical tracks on the tape.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Coding of animated 3-D wireframe models for internet streaming applications: methods, systems and program products
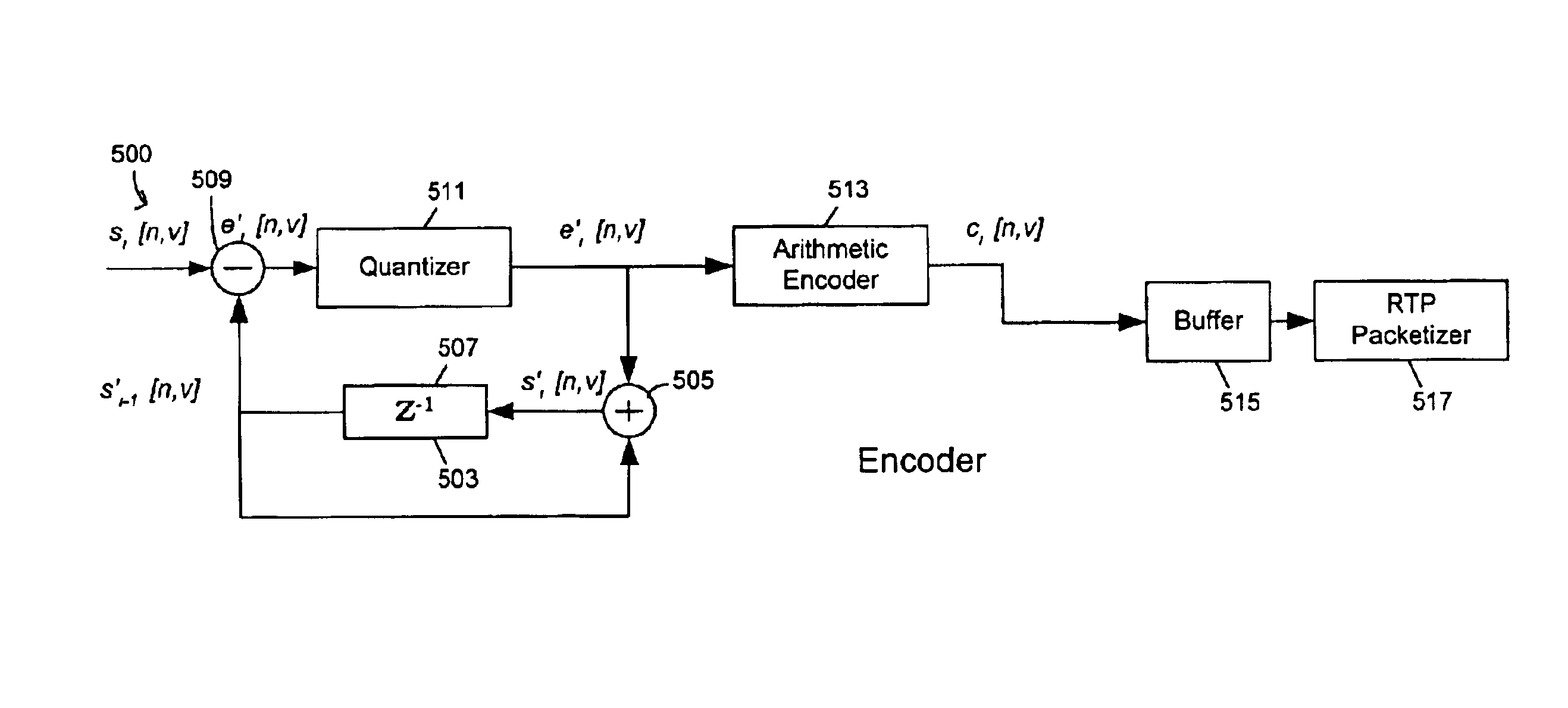
A 3-D wireframe model expressed in terms of nodes and vertices receives a 3-D video or like signal representative of a scene expressed in terms of a reference model, I frames and P frames. A DPCM coder takes advantage of the temporal correlation of the displacement of each vertex along every axis in the 3-D space. The 3-D signal is a set of non-zero displacements of all vertices and all nodes (sl[n, v]) at time tl. The decoded set (animation frame) of the previous instance is used as the predicted value (si-l[n, v]). The prediction error el[n, v], i.e. the difference between the current displacement set and the predicted one, is computed and quantised (el[n, v]). Finally, the quantised samples are entropy coded (ci[n, v]) using an adaptive arithmetic coding algorithm to handle the unknown data statistics. The predictive scheme described above prevents quantization error accumulation. A DPCM decoder first decodes arithmetically the received samples (‘e’ [n, v]) and computers the decoded samples (si′ [n, v]).
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Code compression algorithms and architectures for embedded systems
InactiveUS7095343B2Increase the compression ratioSimple designCode conversionProbit modelAdaptive coding
Code compression techniques and decompression architectures for embedded systems are disclosed, providing good compression ratio while improving decompression time for VLIW instructions and reducing bus power consumption. The invention includes two fixed-to-variable (F2V) length code compression schemes based on a reduced arithmetic code compression algorithm combining arithmetic coding with probability models; a static probability model using static coding and semi-adaptive coding using a Markov model. Multi-bit decompression methods for the F2V techniques are presented, together with a parallel decompression scheme that tags and divides a compressed block into smaller sub-blocks. The Markov model provides better compression ratio, but the static model has a less complicated decompression unit design. The invention also includes two variable-to-fixed (V2F) length coding algorithms, one based on Tunstall coding and another on arithmetic coding. The V2F algorithms are also combined with a static model and a Markov model.
Owner:THE TRUSTEES FOR PRINCETON UNIV
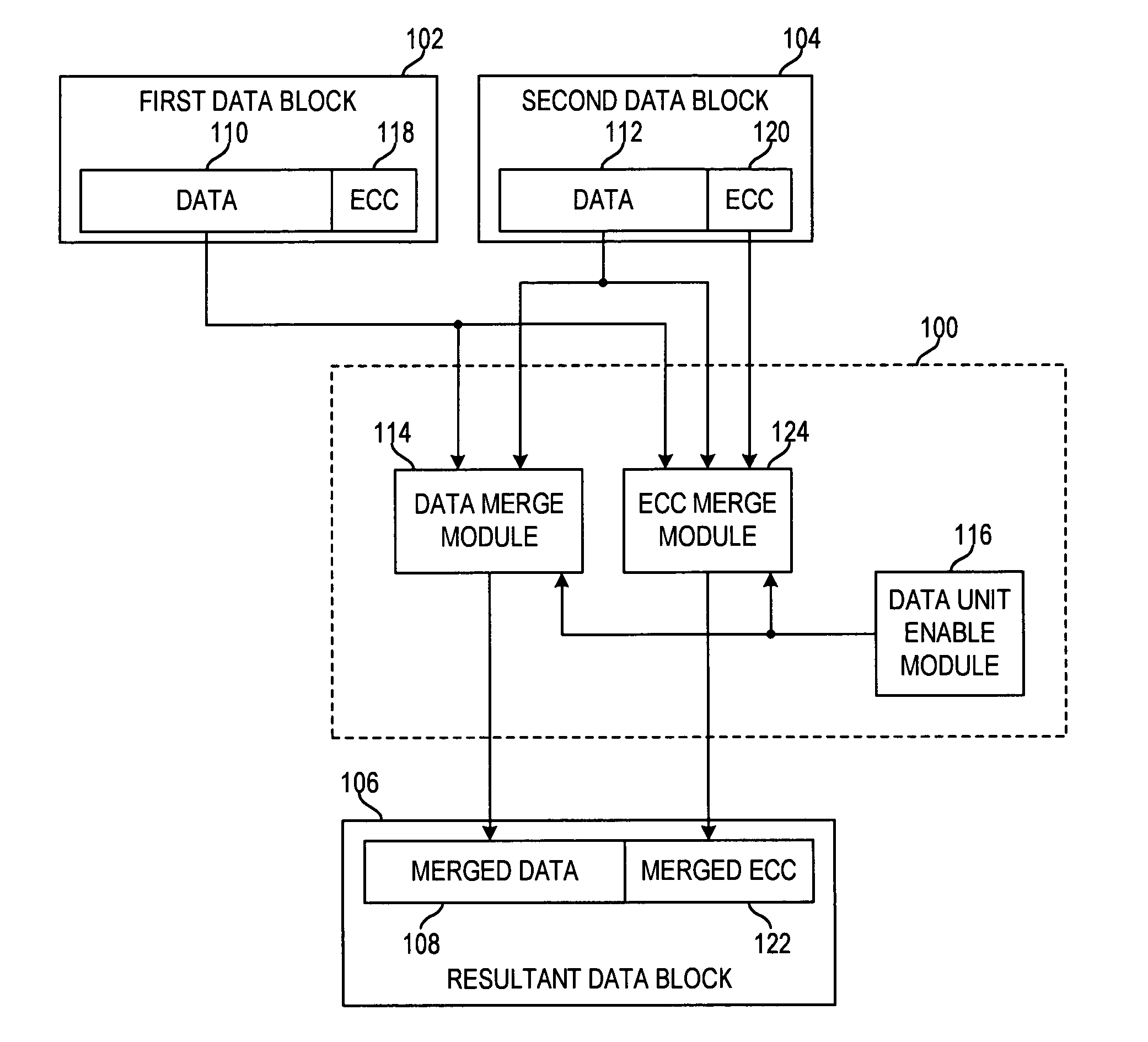
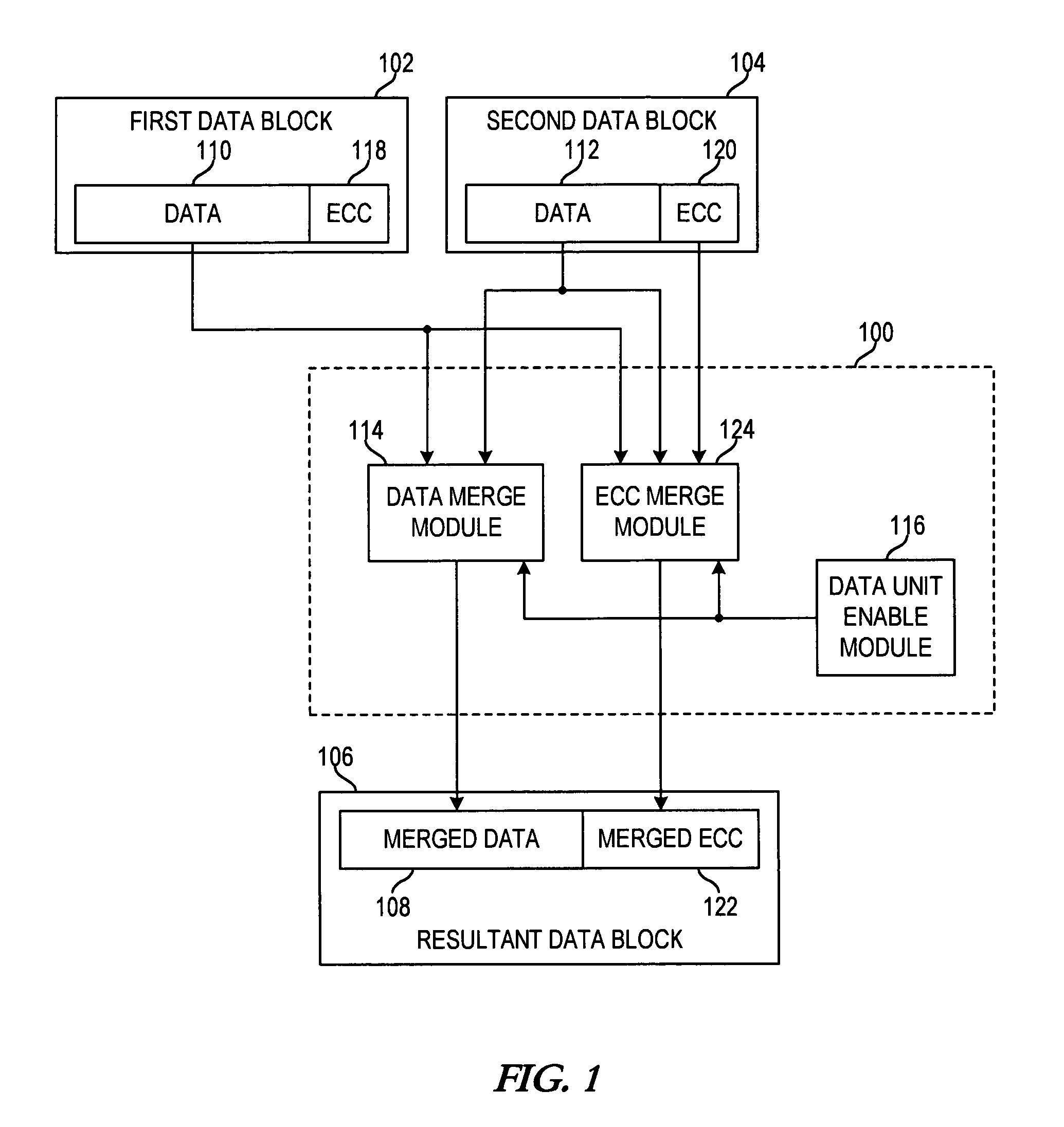
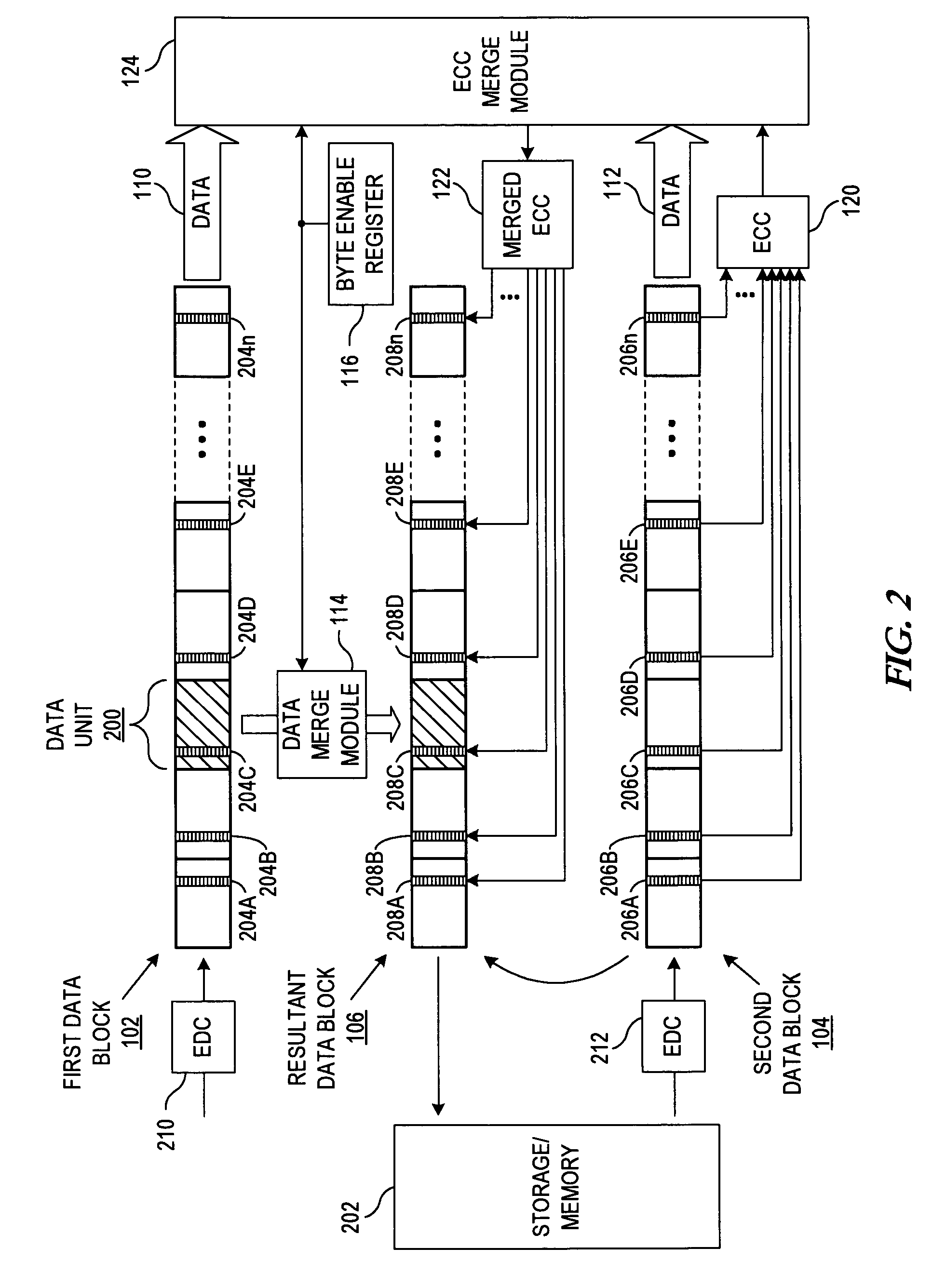
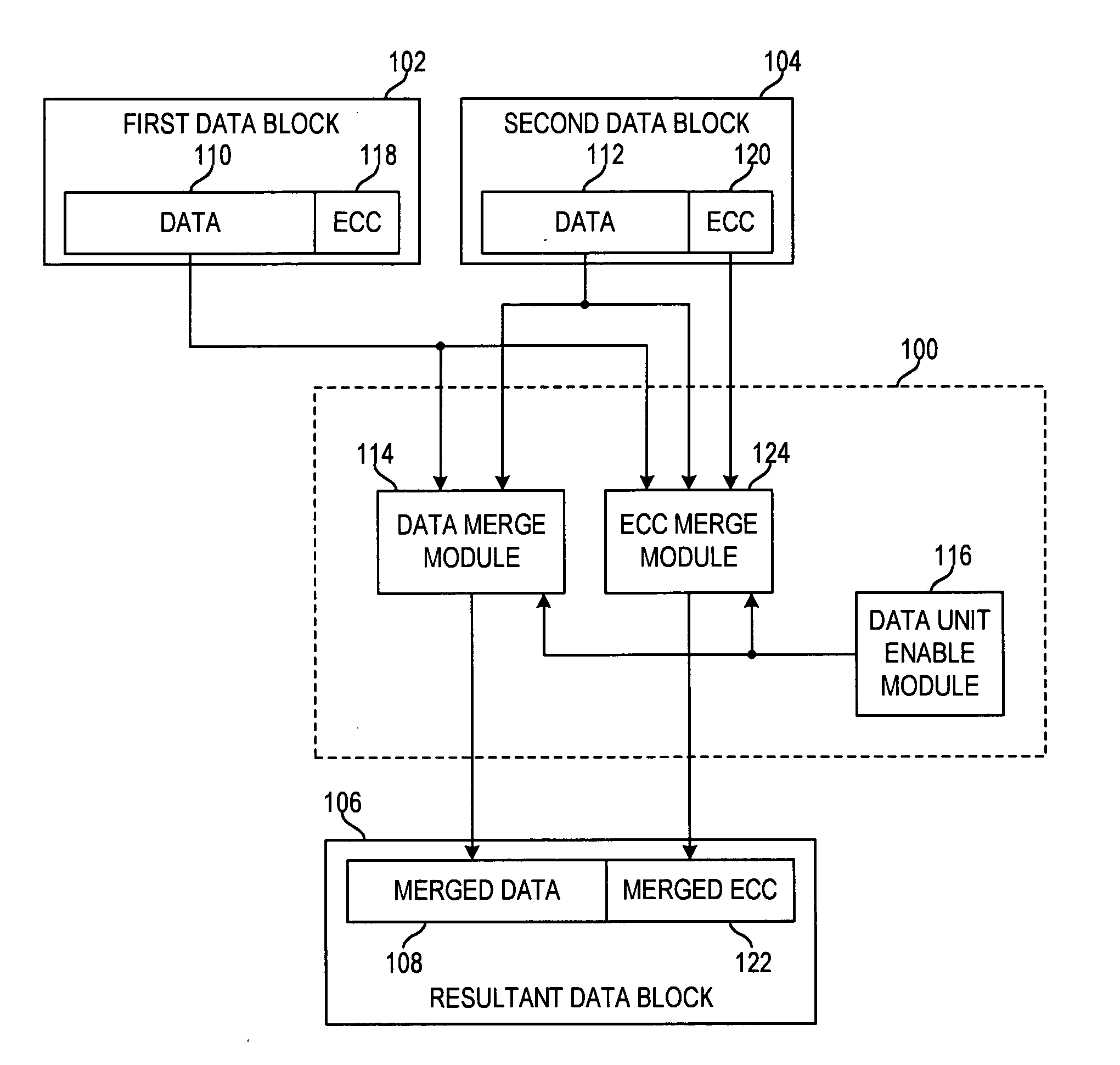
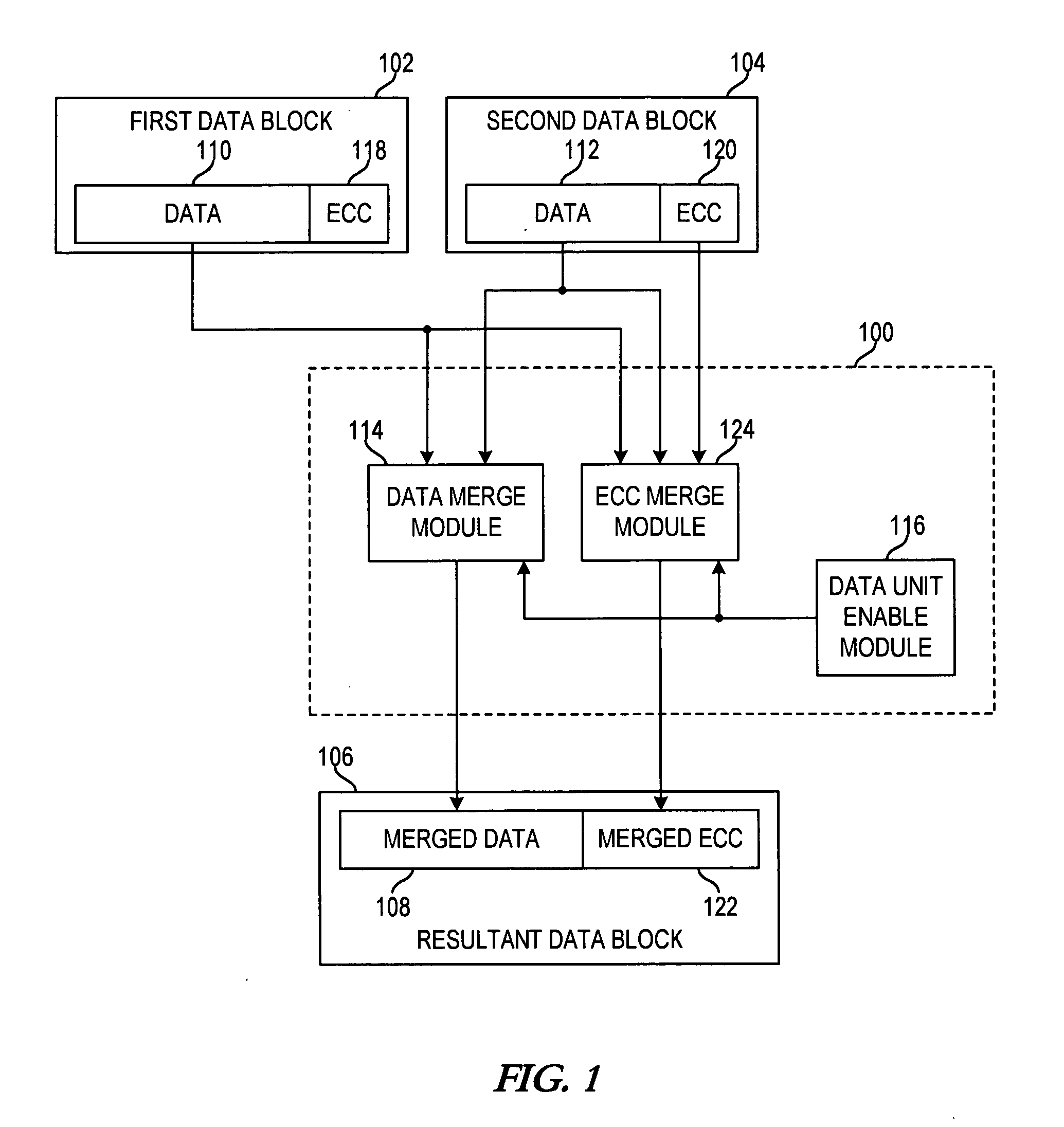
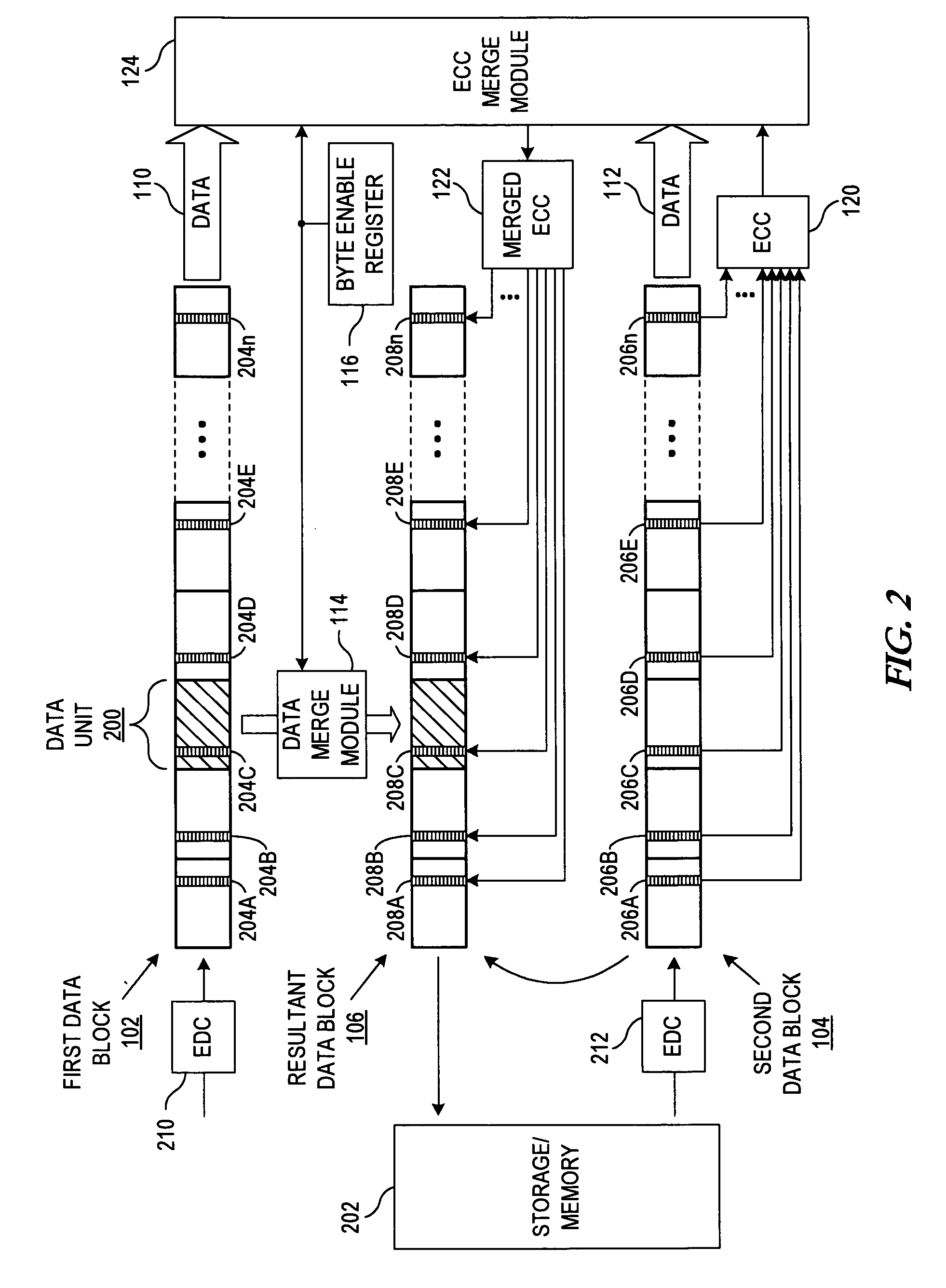
Apparatus and method for merging data blocks with error correction code protection
An apparatus and method for selectively deriving Error Correction Codes (ECCs) or other data integrity information for integration into merged data blocks. First data is merged into second data that is error-protected using an ECC generated by a coding algorithm. Bytes or other data units are identified in the first data to be merged into the second data. It is determined whether each of the check bits of the ECC will differ from its original state in response to merging the first and second data. The check bits of the ECC that have been determined to differ from their respective original states are modified to create a “merged ECC.” The resulting data block includes the merged data and the merged ECC.
Owner:UNISYS CORP
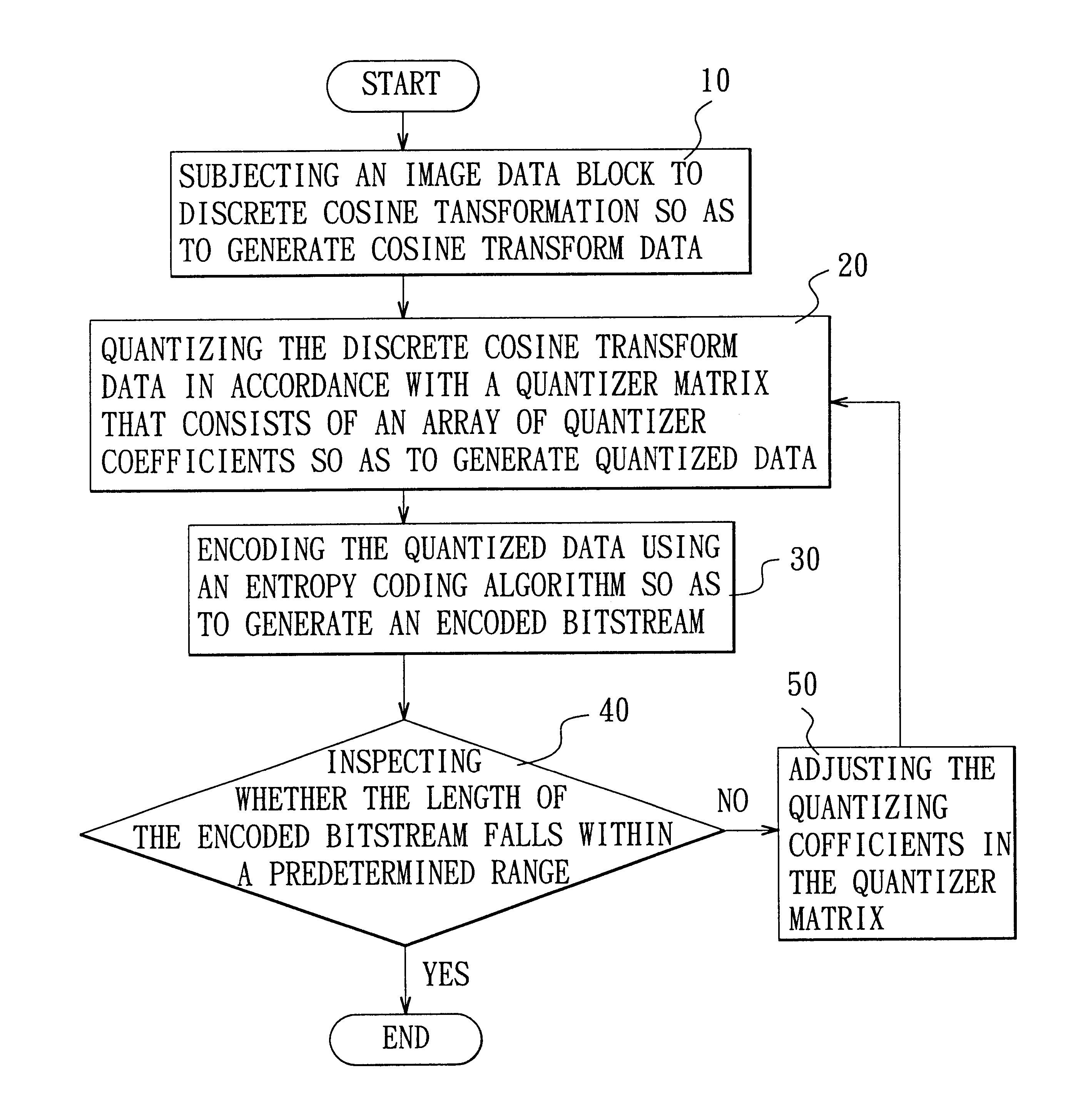
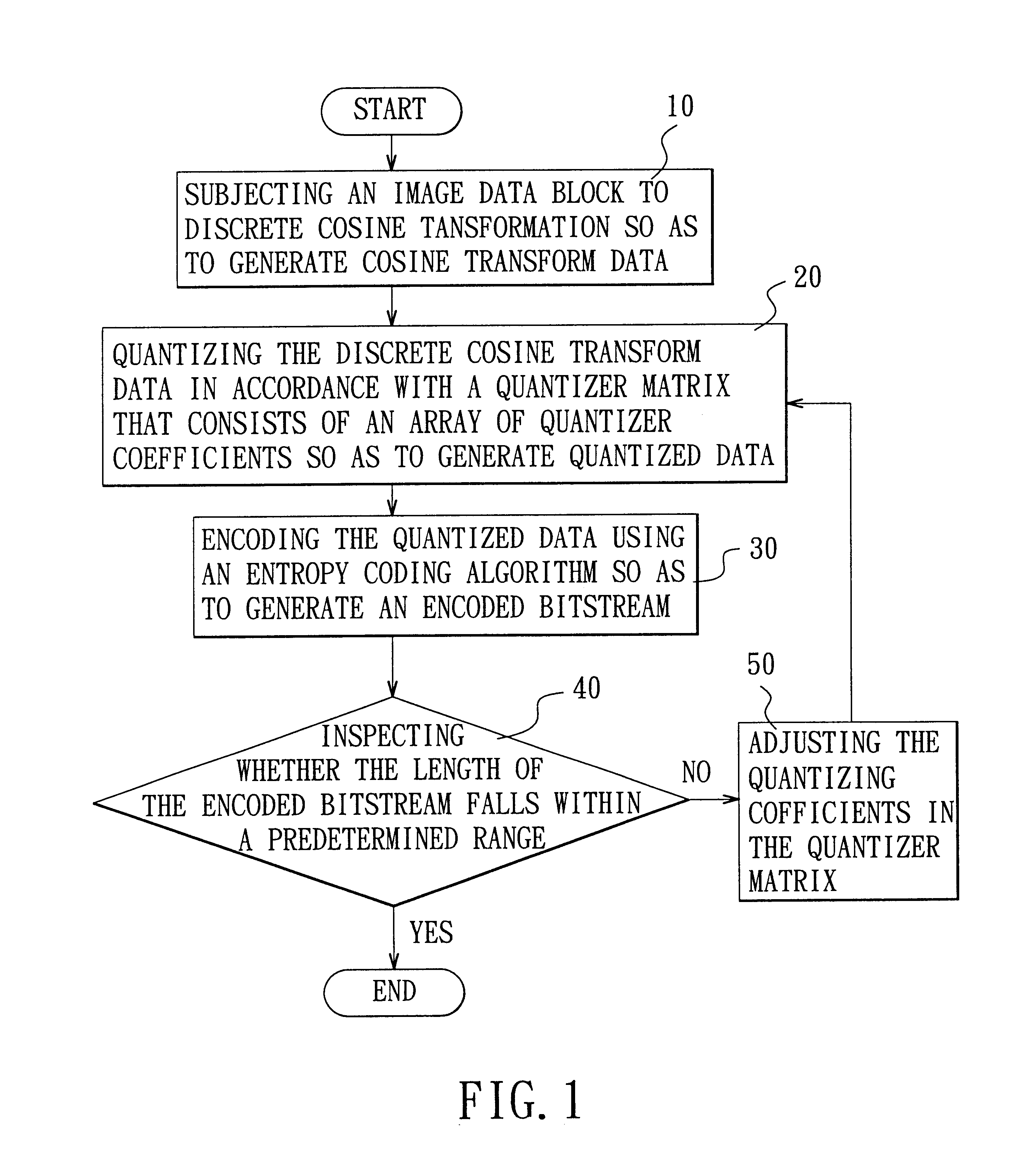
Adaptive quantization using code length in image compression
InactiveUS6882753B2Low memory and bus bandwidth requirementImprove processing efficiencyPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningPattern recognitionLandau quantization
A method is adapted for compressing an image data block, and includes the steps of:(a) subjecting the image data block to discrete cosine transformation so as to generate discrete cosine transform data;(b) quantizing the discrete cosine transform data in accordance with a quantizer matrix that consists of an array of quantizing coefficients so as to generate quantized data;(c) encoding the quantized data using an entropy coding algorithm so as to generate an encoded bitstream; and(d) when the length of the encoded bitstream does not fall within a predetermined range, adjusting the quantizing coefficients in the quantizer matrix and repeating steps (b) and (c) until the length of the encoded bitstream falls within the predetermined range.
Owner:SILICON INTEGRATED SYSTEMS
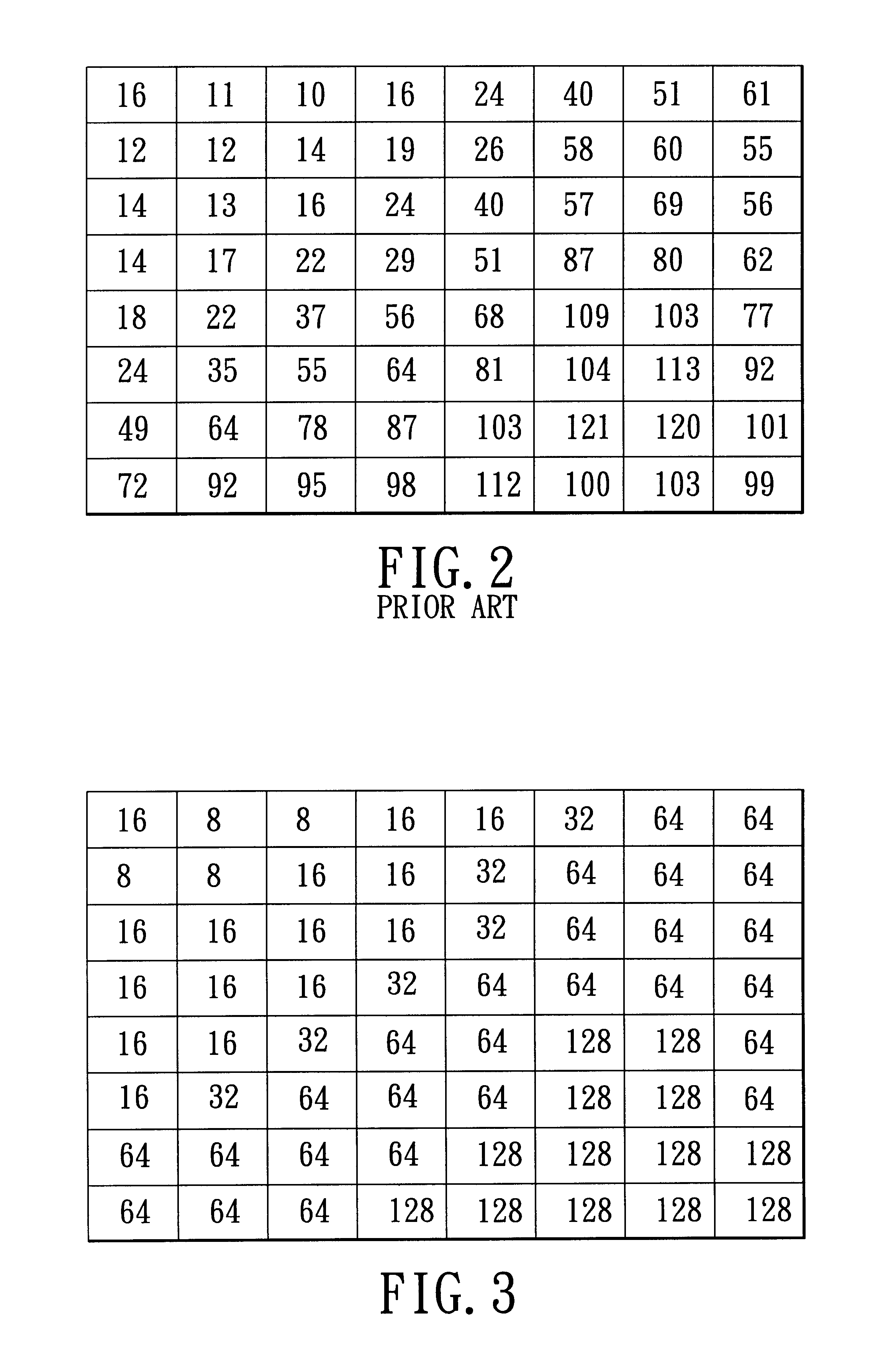
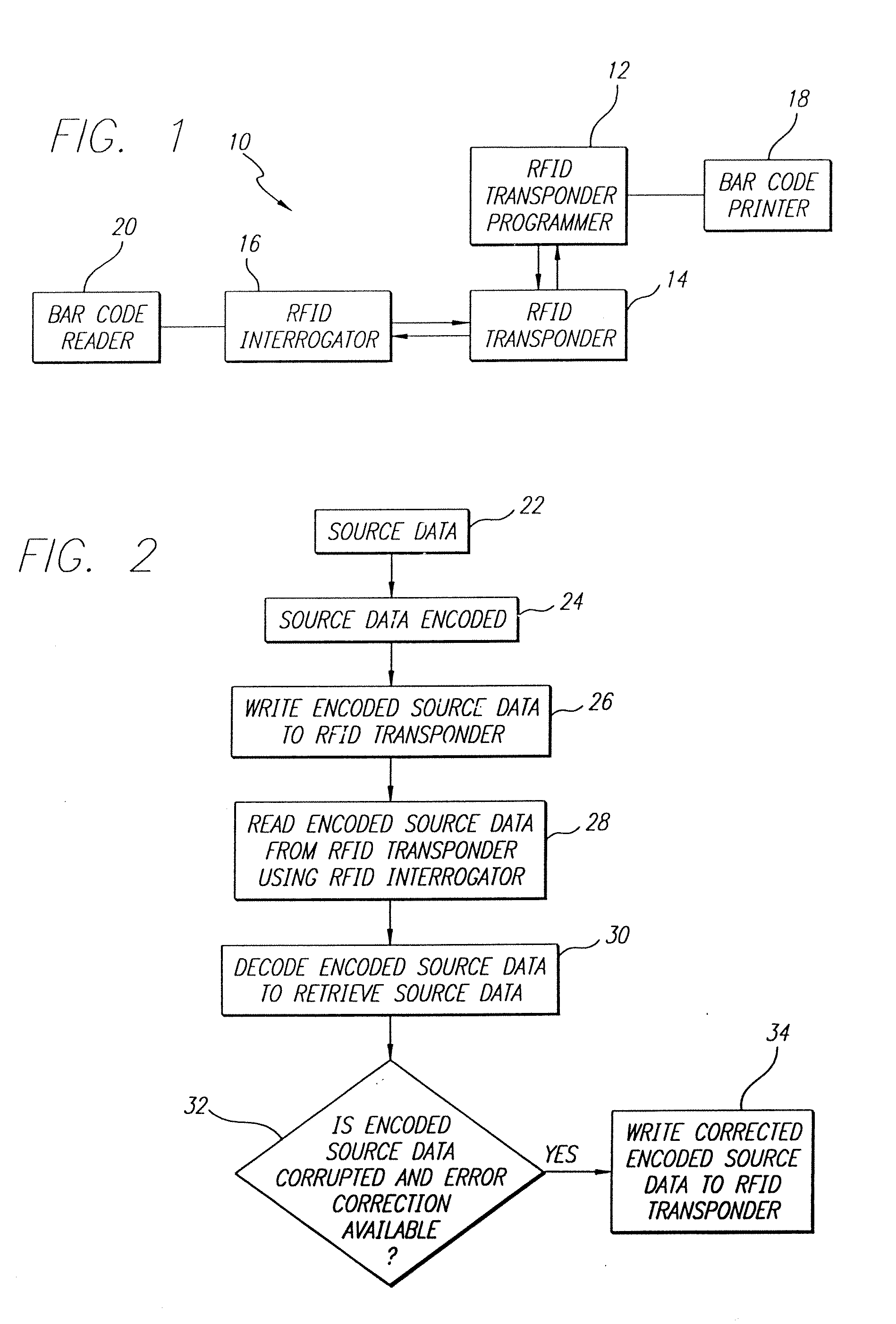
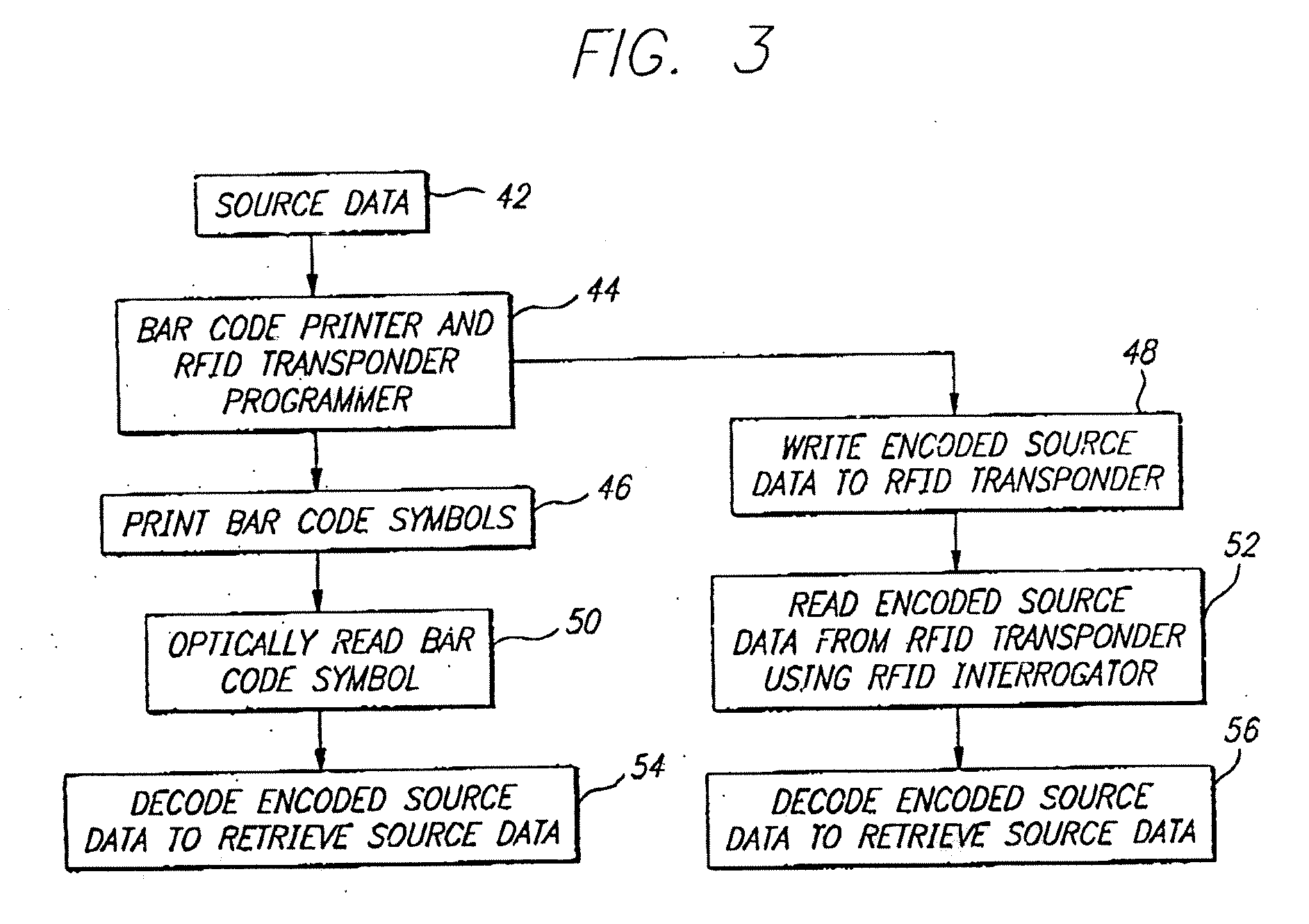
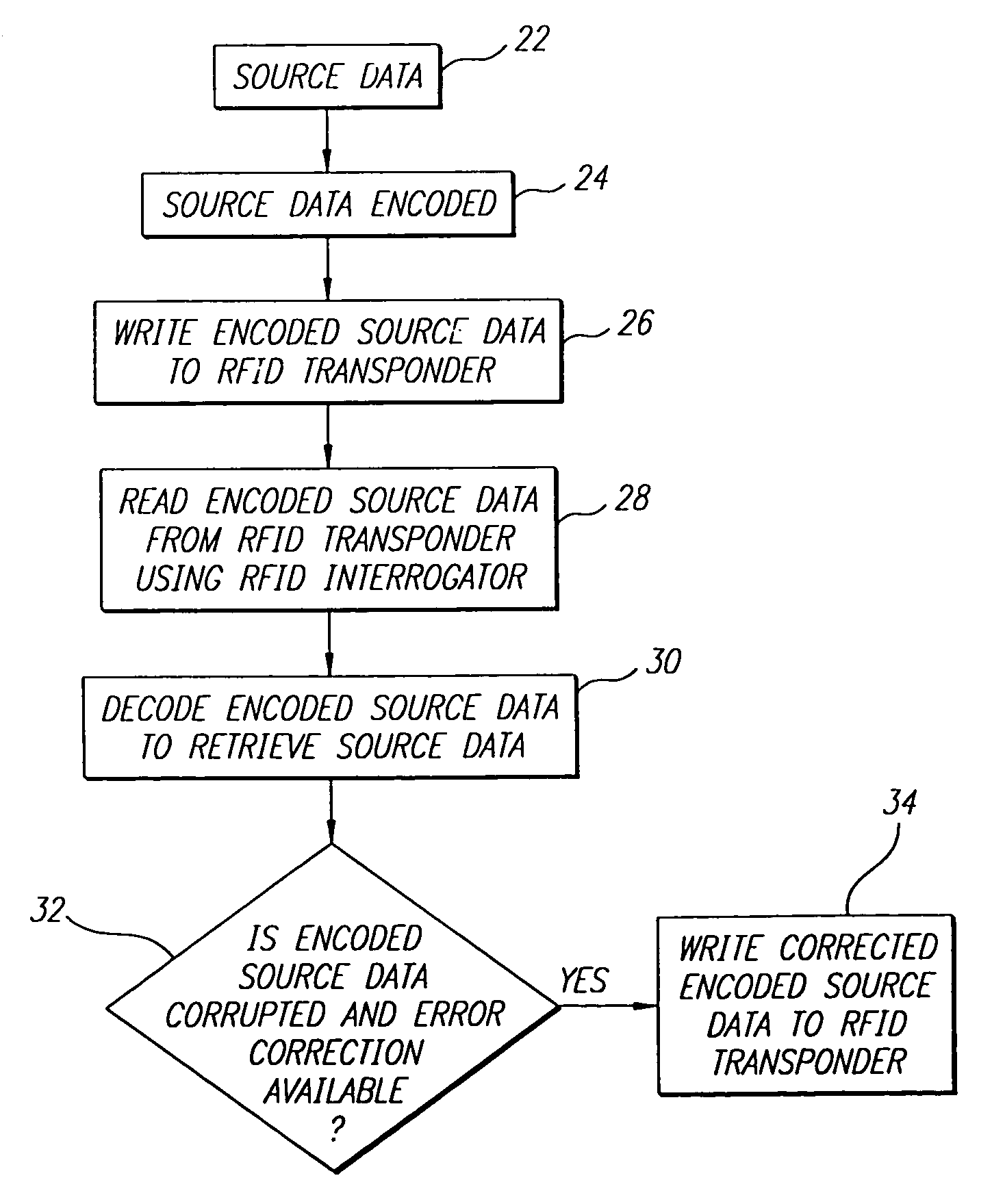
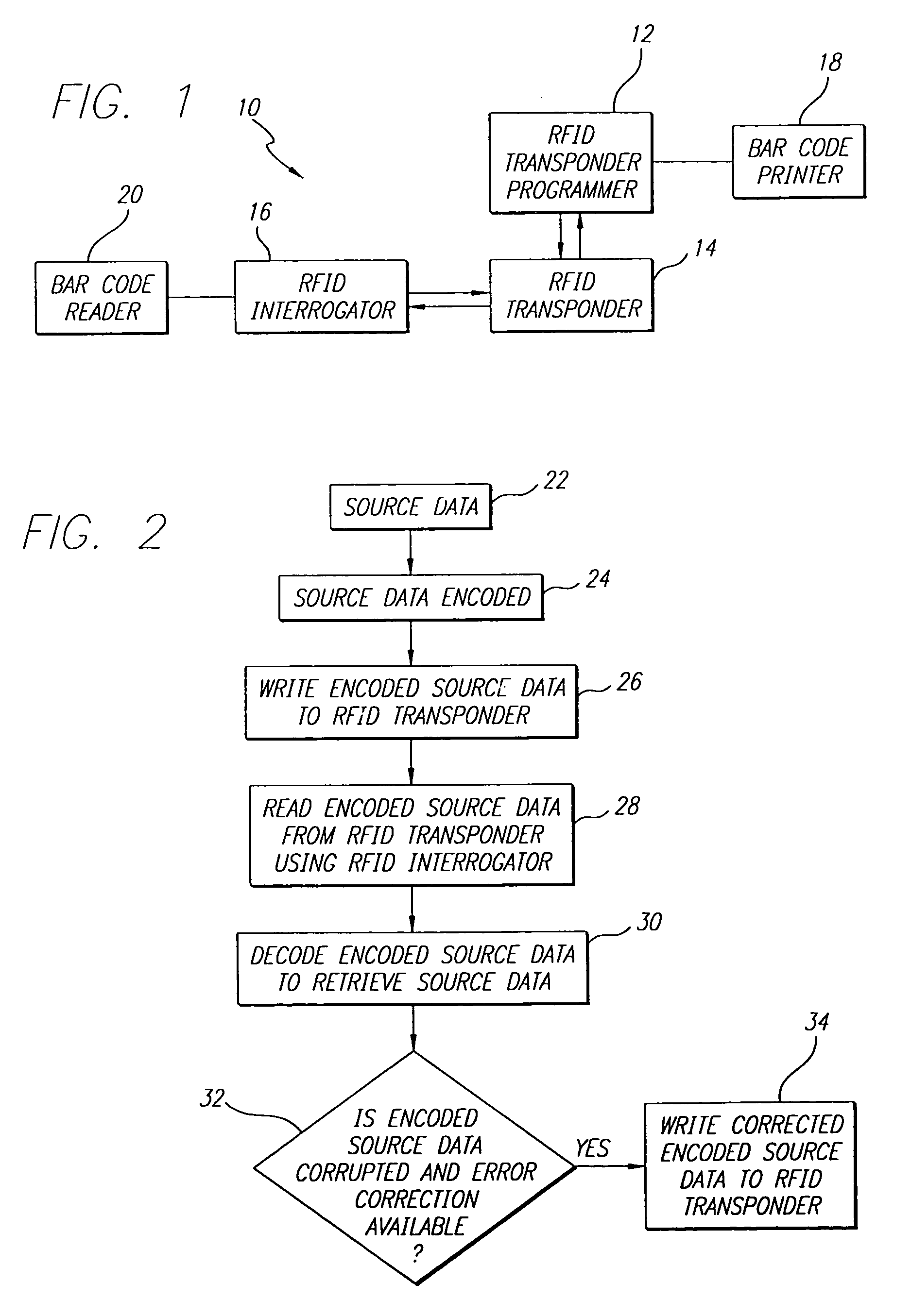
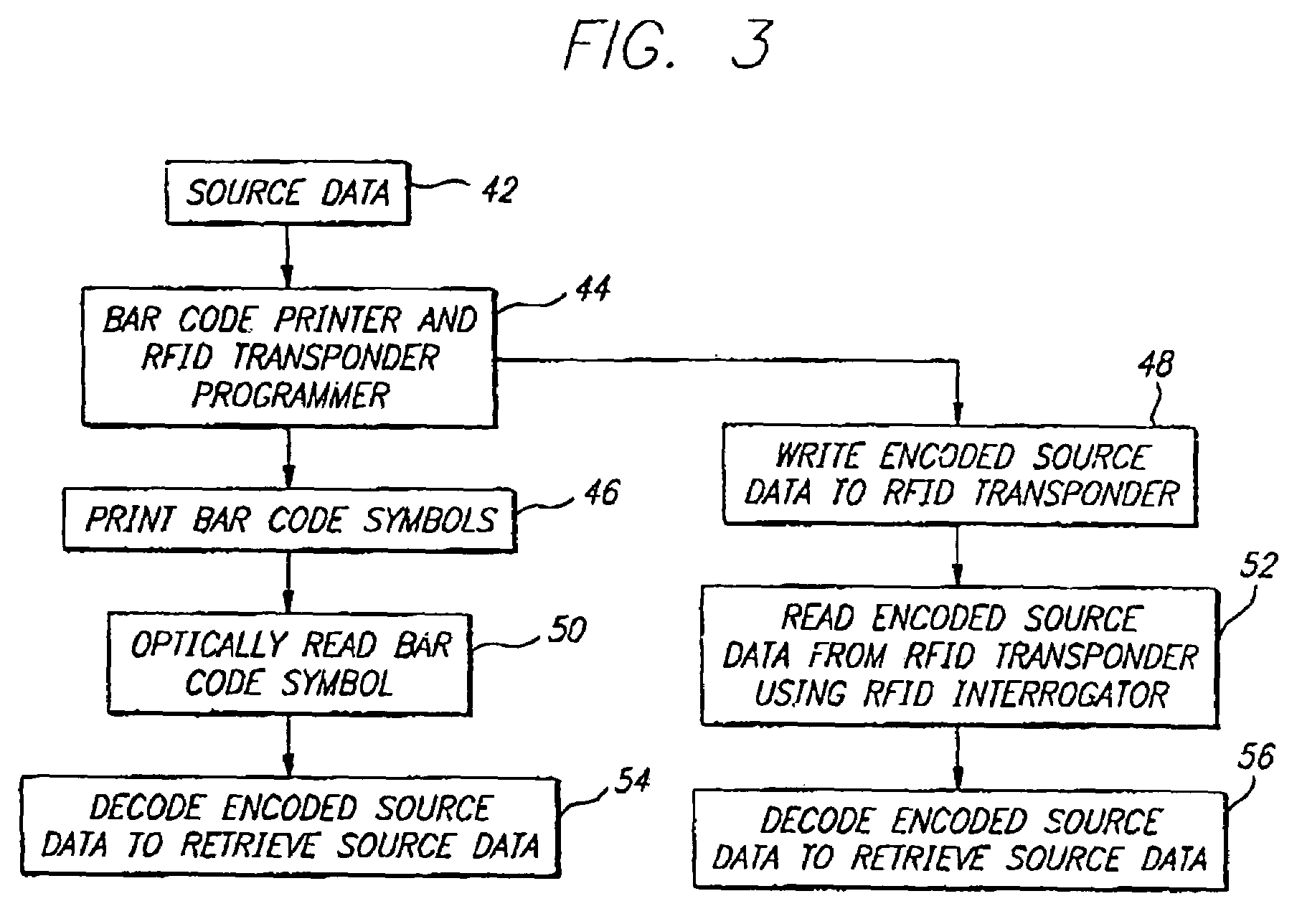
Data encoding in radio frequency identification transponders
InactiveUS20070075841A1Improve system performanceMemory record carrier reading problemsCo-operative working arrangementsComputer printingBarcode
A method and apparatus are provided for efficiently encoding source data in radio frequency identification (RFID) systems. The encoded source data may also provide additional functionality such as data error detection and correction. A source data encoding and decoding method for a RFID system having a RFID transponder comprises the steps of obtaining the source data, encoding to provide more efficient data encodation that may also include data error detection and error correction, writing the encoded source data to a RFID transponder, reading the encoded source data from the RFID transponder, and decoding the encoded source data to recover the original source data. The encoding may utilize bar code symbology algorithms or a non-Full ASCII enhanced functionality character set. A source data encoding device and a decoding device for a RFID system may comprise a memory, a processor for running a program stored in the memory, a bar code printer for printing a bar code, a RFID transponder programmer for writing the data to the RFID transponder, a RFID interrogator for interrogating the RFID transponder, and a bar code reader to read a bar code. The data may be provided encoded or the device may encode / decode the data using coding algorithms. The RFID transponder stores the encoded source data, that may utilize a non-Full ASCII enhanced functionality character set, and the encoded data may be retrieved to recover the original source data.
Owner:INTERMEC IP
Data encoding in radio frequency identification transponders
InactiveUS7190257B2Improve system performanceMemory record carrier reading problemsCo-operative working arrangementsBarcodeData encoding
A method and apparatus are provided for efficiently encoding source data in radio frequency identification (RFID) systems. The encoded source data may also provide additional functionality such as data error detection and correction. A source data encoding and decoding method for a RFID system having a RFID transponder comprises the steps of obtaining the source data, encoding to provide more efficient data encodation that may also include data error detection and error correction, writing the encoded source data to a RFID transponder, reading the encoded source data from the RFID transponder, and decoding the encoded source data to recover the original source data. The encoding may utilize bar code symbology algorithms or a non-Full ASCII enhanced functionality character set. A source data encoding device and a decoding device for a RFID system may comprise a memory, a processor for running a program stored in the memory, a bar code printer for printing a bar code, a RFID transponder programmer for writing the data to the RFID transponder, a RFID interrogator for interrogating the RFID transponder, and a bar code reader to read a bar code. The data may be provided encoded or the device may encode / decode the data using coding algorithms. The RFID transponder stores the encoded source data, that may utilize a non-Full ASCII enhanced functionality character set, and the encoded data may be retrieved to recover the original source data.
Owner:INTERMEC IP
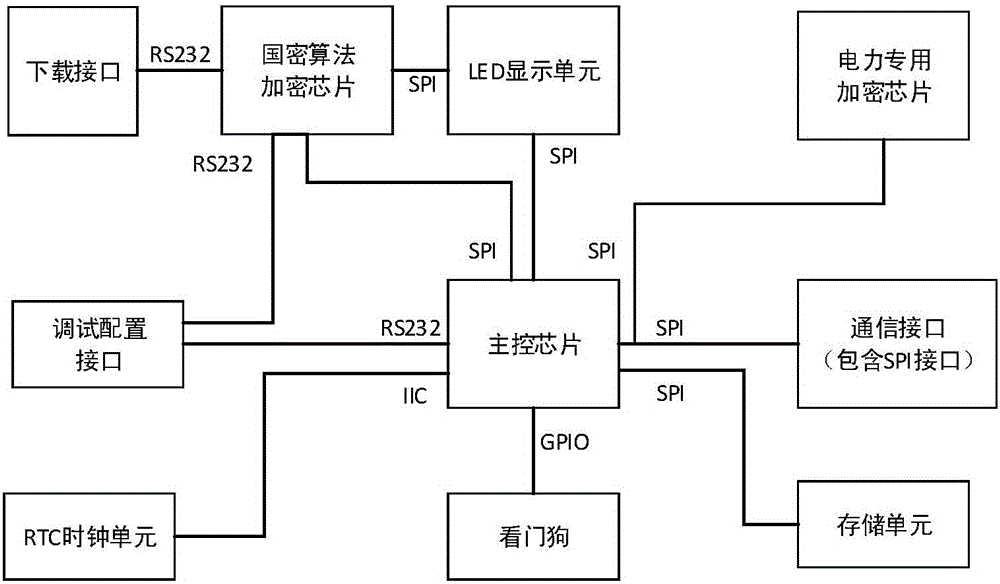
Security encryption authentication module for power distribution terminal communication and method thereof
InactiveCN105871873ASpeed up encryption/decryption timeReduce dependenceKey distribution for secure communicationUser identity/authority verificationCommunication interfaceCommunications security
The invention discloses a security encryption authentication module for power distribution terminal communication and a method thereof. The security encryption authentication module comprises a main control chip, a commercial code algorithm encryption chip, a communication interface and a storage unit; the main control chip is connected with the commercial code algorithm encryption chip, the communication interface and the storage unit and receives message information of a front-end processor of a distribution master station and a distribution terminal through safe interface software of the distribution terminal to overall manages the other modules, and the commercial code algorithm encryption chip encrypts or decrypts the message information received by the main control chip. The special encryption chip is adopted in the security encryption authentication module, response speed is increased, and dependence on a CPU and an internal storage is reduced. Besides, communication security is greatly improved by means of bidirectional authentication of verifying each other's identity between the security encryption authentication module and a distribution security interaction gateway.
Owner:STATE GRID CORP OF CHINA +4
Method and apparatus for transcoding coded video image data
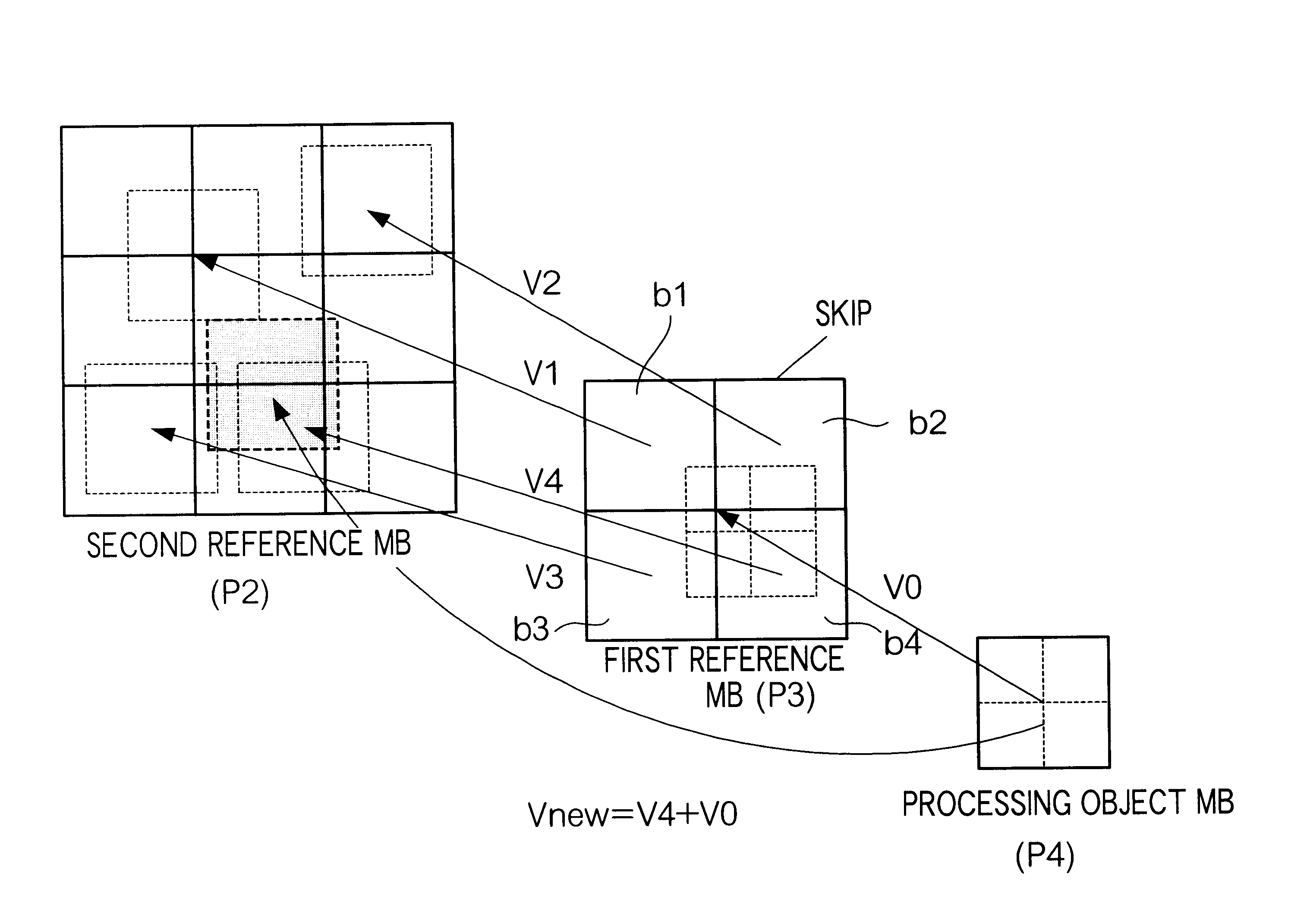
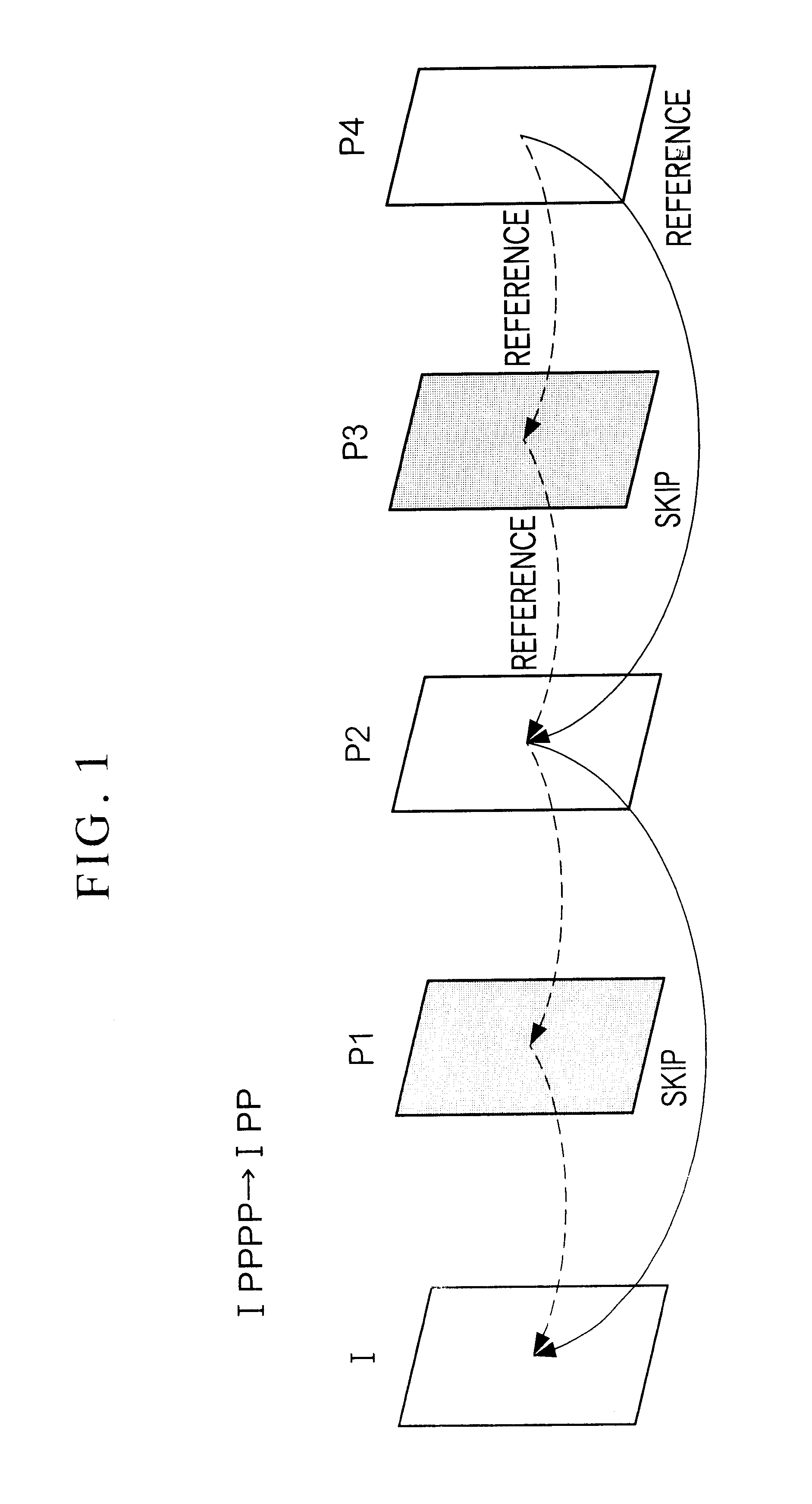
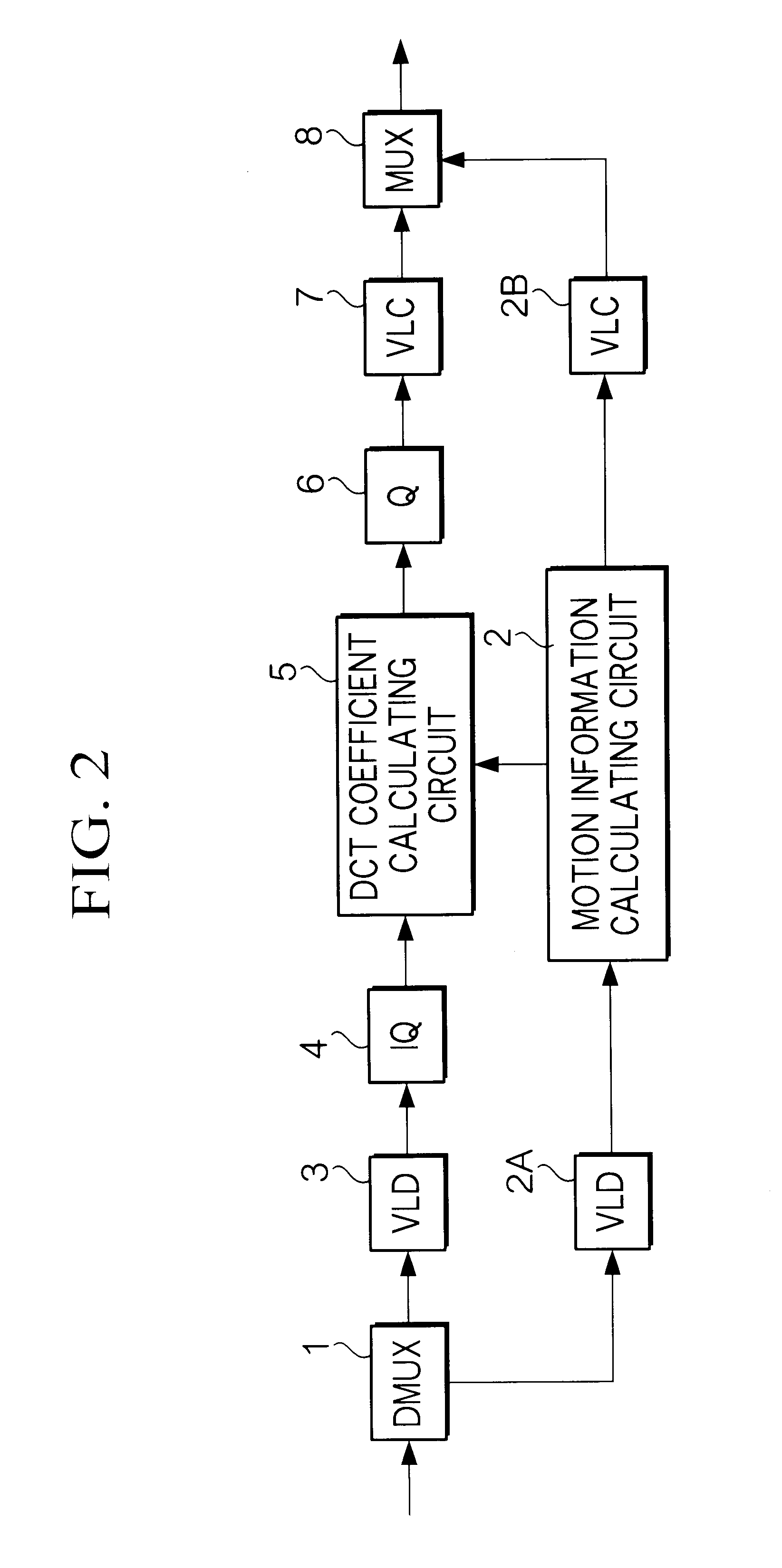
InactiveUS6912253B1Less caliculation processColor television with pulse code modulationColor television with bandwidth reductionInter frameCode algorithm
A transcoding apparatus converts first coded data obtained from a plurality of frames forming a video image by means of a coding algorithms including an interframe prediction coding algorithm with motion compensation into second coded data having a different structure. More specifically, the transcoding apparatus takes a portion of frames which have had the interframe prediction coding and are included in the plurality of frames forming the video image as processing object frames, and from at least the first coded data corresponding to the processing object frames, generates the second coded data corresponding to coded data which are to be obtained when performing the interframe prediction coding on the processing object frames with reference to second reference frames which are different from first reference frames referenced in the interframe prediction coding of the processing object frames. In order to the second coded data, the transcoding apparatus has a motion information calculating portion for calculating motion information to be included in the second coded data using at least motion information contained in said processing object data.
Owner:NTT DOCOMO INC
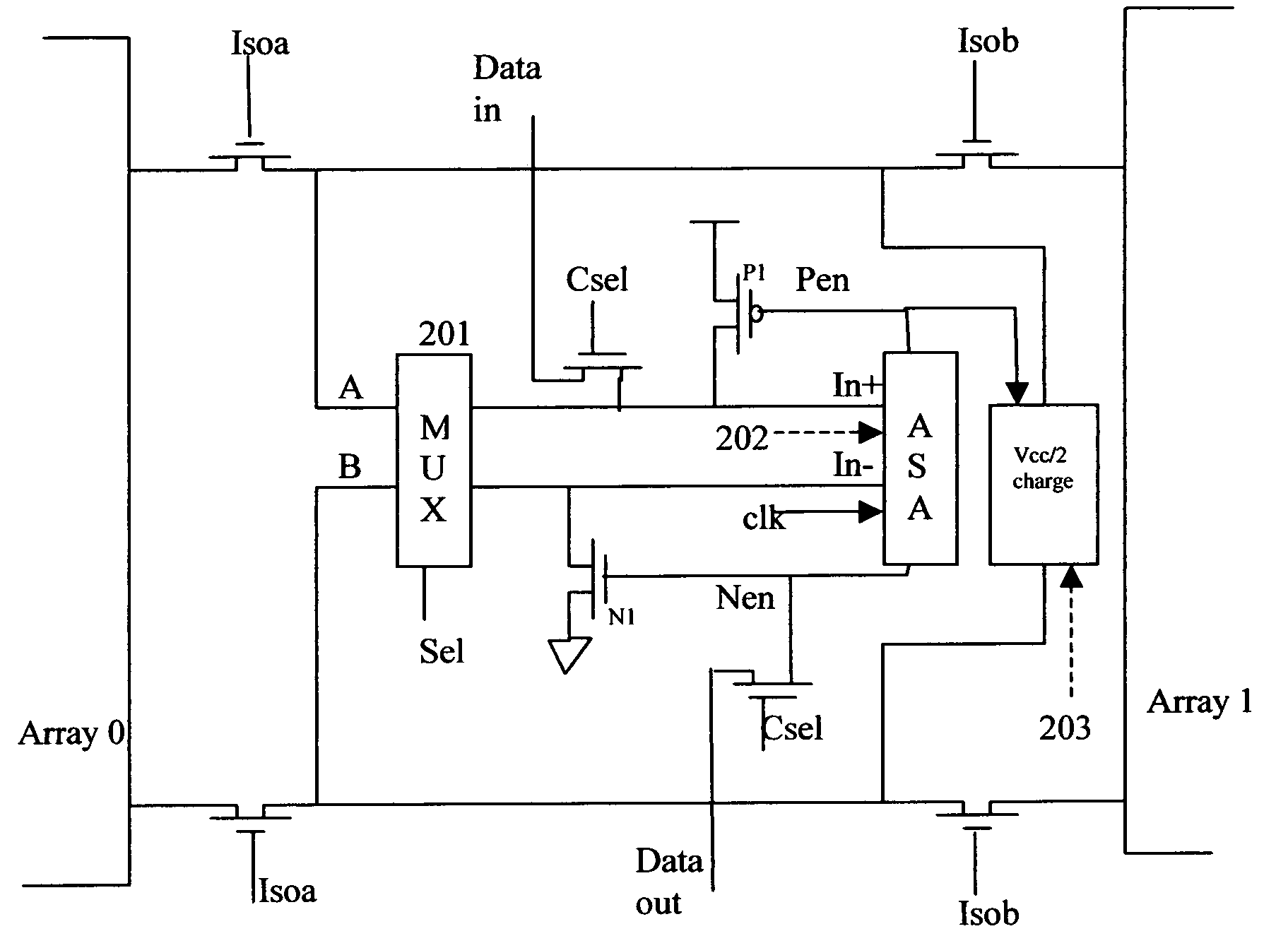
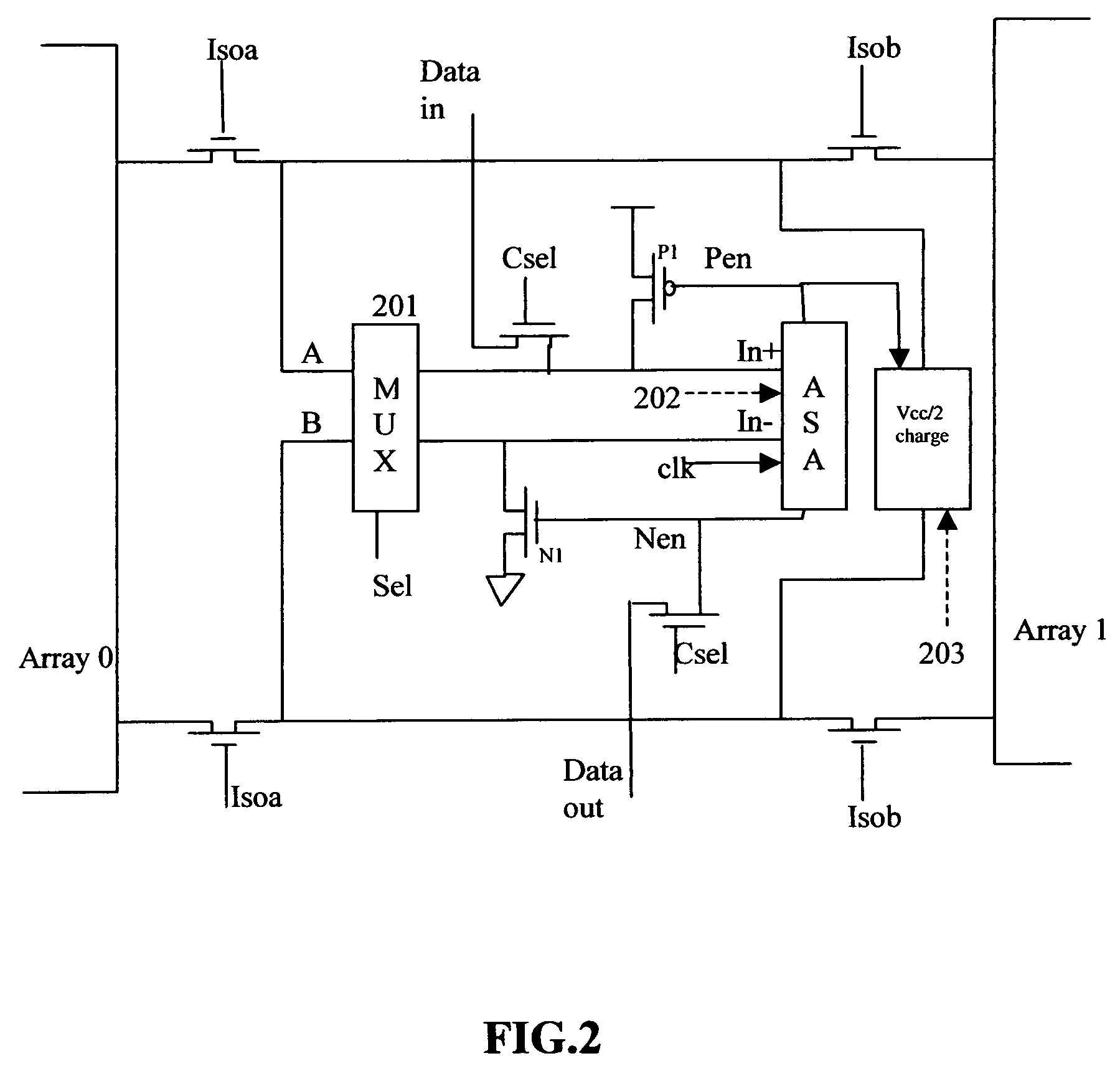
Low power, high speed read method for a multi-level cell DRAM
A method of storing, sensing and restoring three voltage levels (1.5 bit per cell) of a plurality of memory cells in Dynamic random access memory is disclosed. An asymmetrical sense amplifier, ASA, together with a 2 to 2 multiplex, will be used to detect the voltage difference on the bit lines and transfer the voltage difference to digital data. ASA is designed to have one input stronger than the other input. The multiplex is controlled by a signal so that the connection between bit line pair and two inputs of ASA is switched at different time and logical address. Other transistors and circuits are also used to store and restore the voltage levels into memory cells. Coding algorithms are used to get fast read speed of this multi-level cell DRAM.
Owner:LIU BO
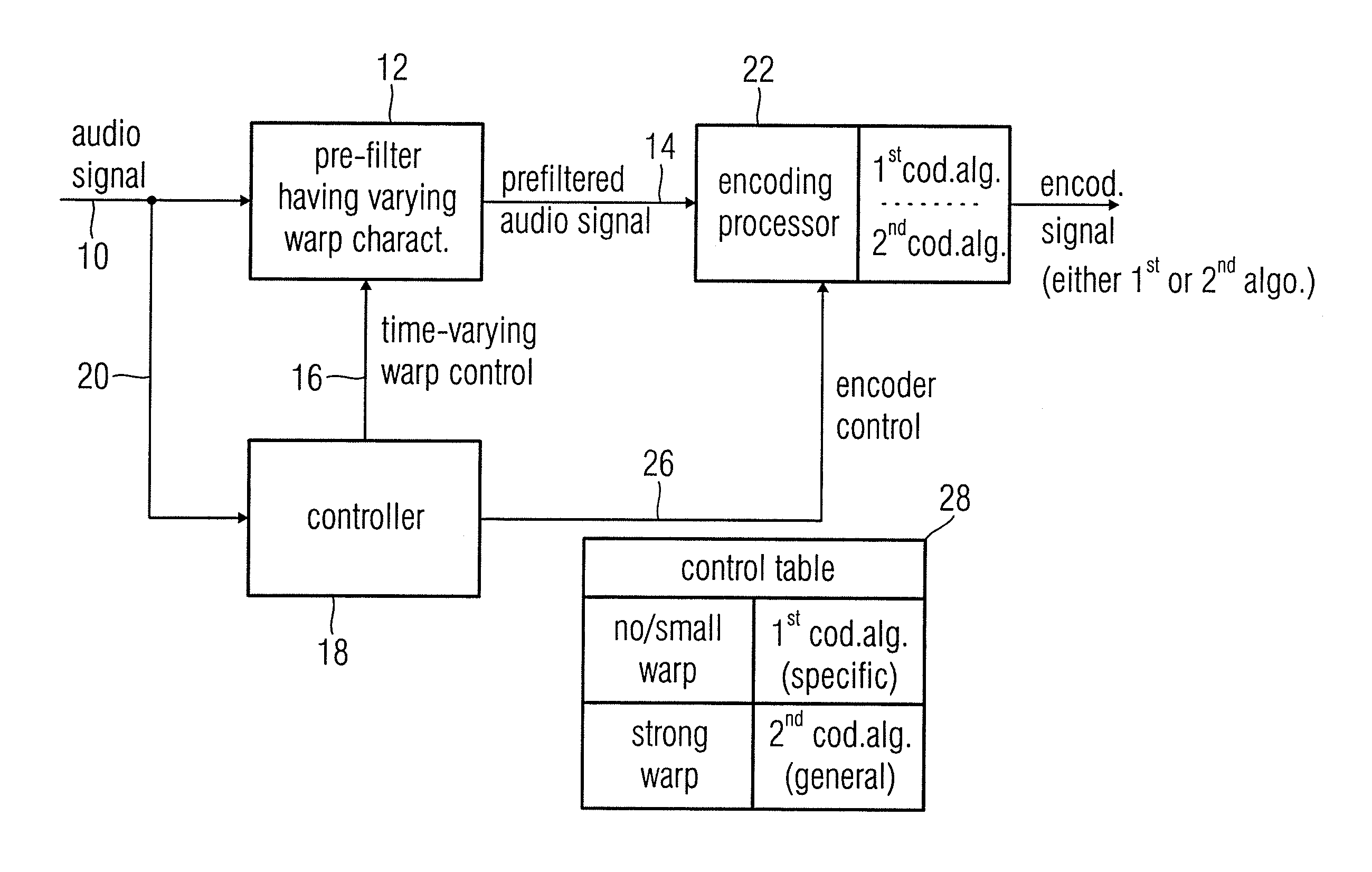
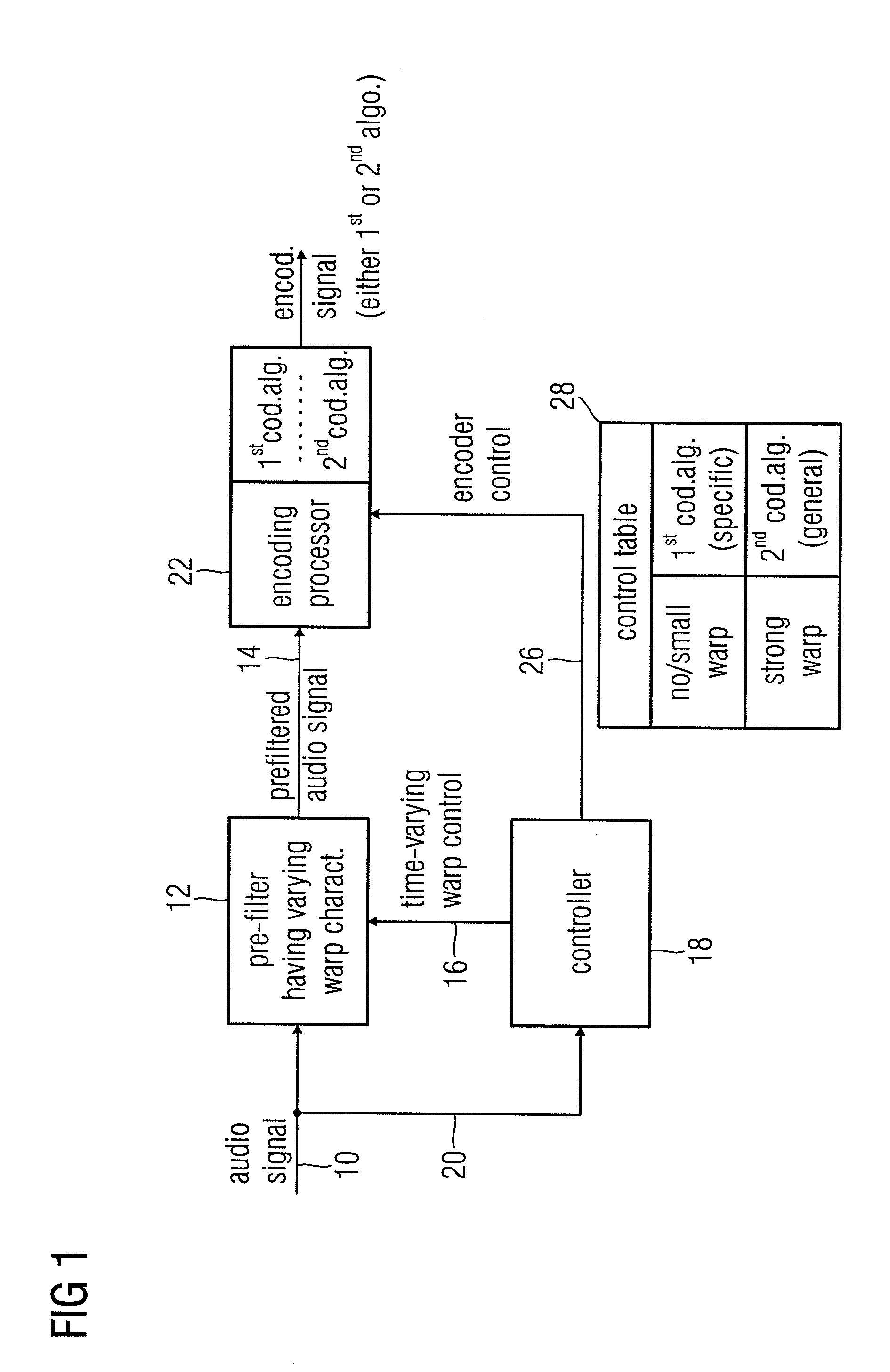
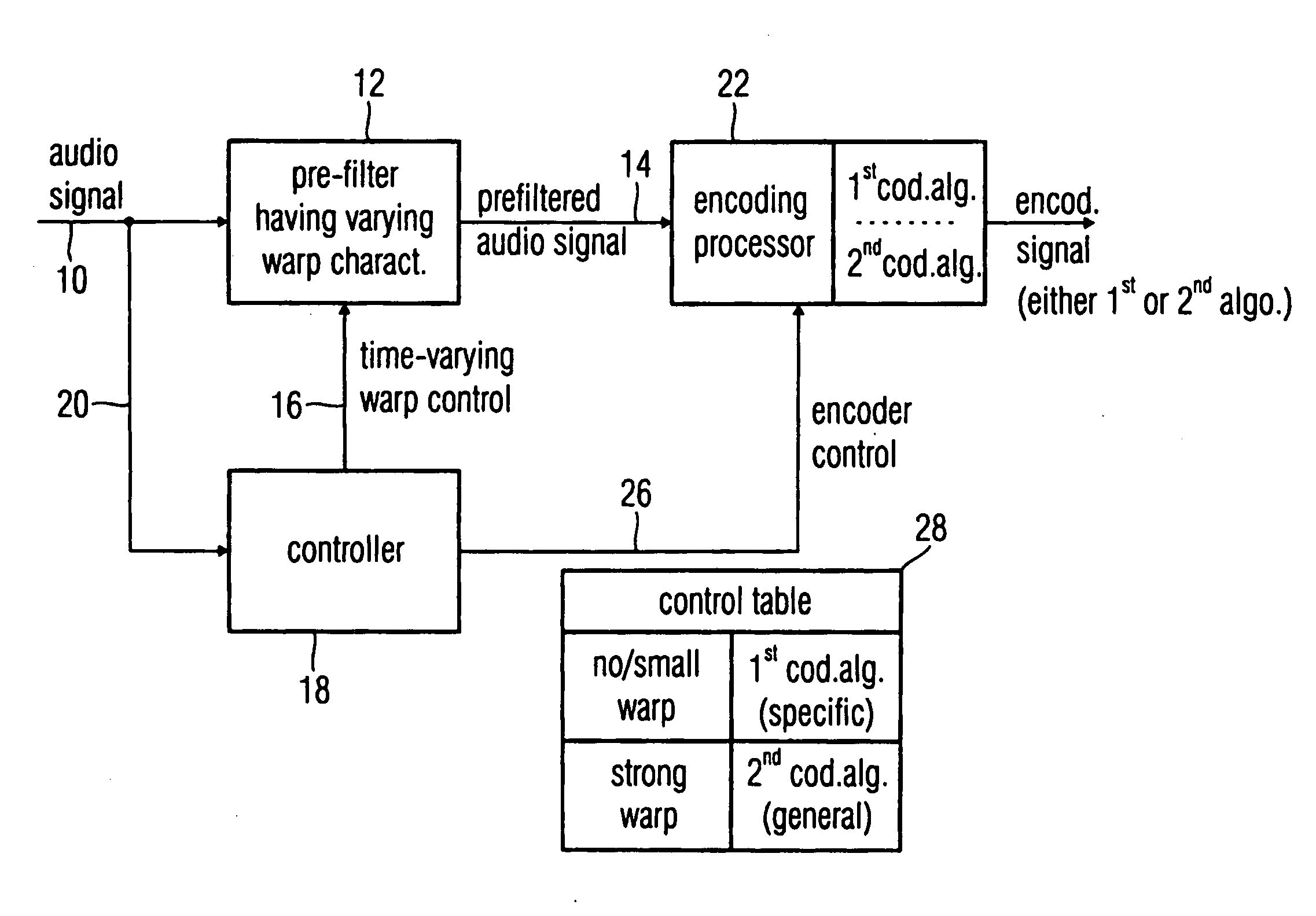
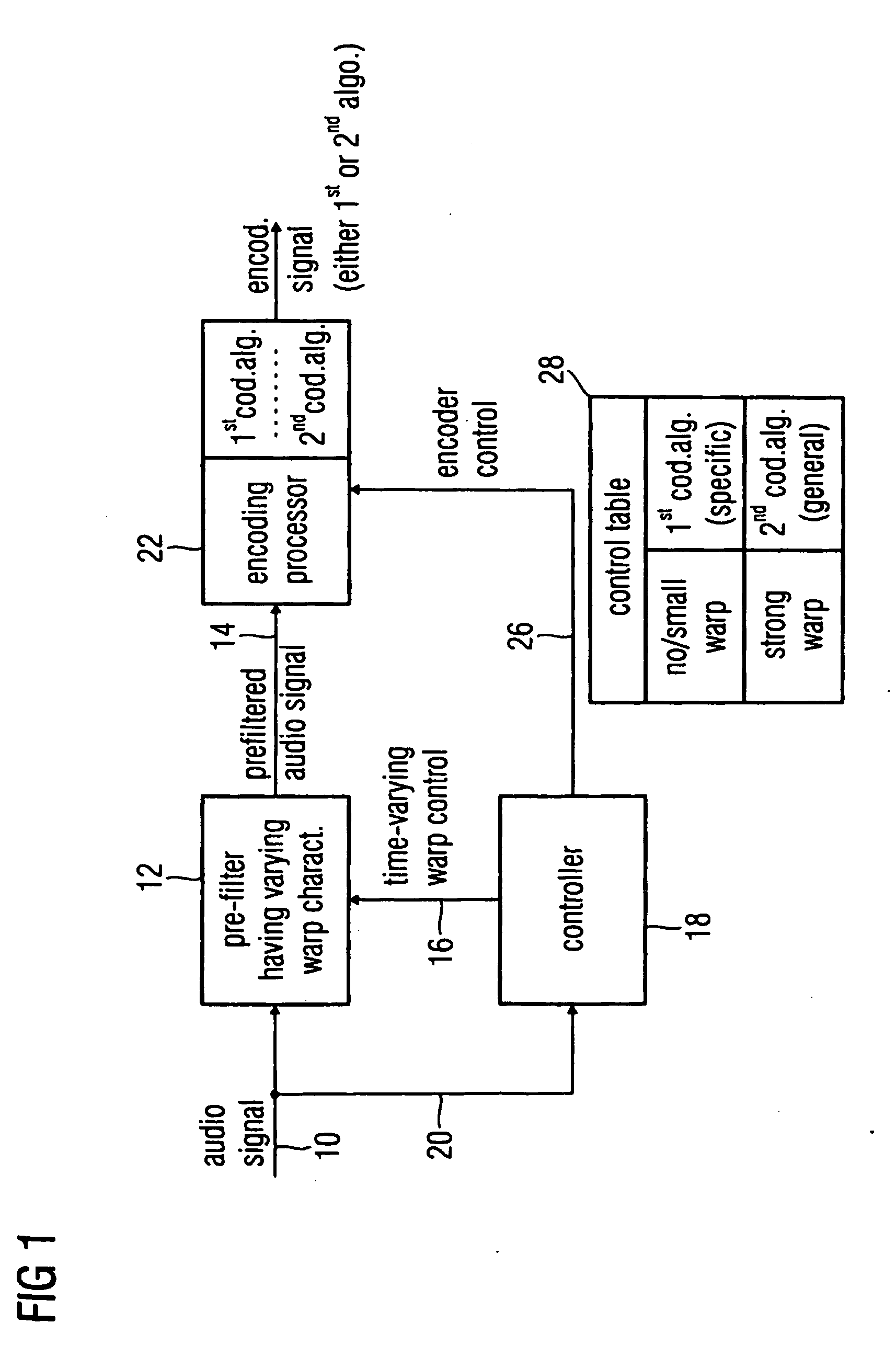
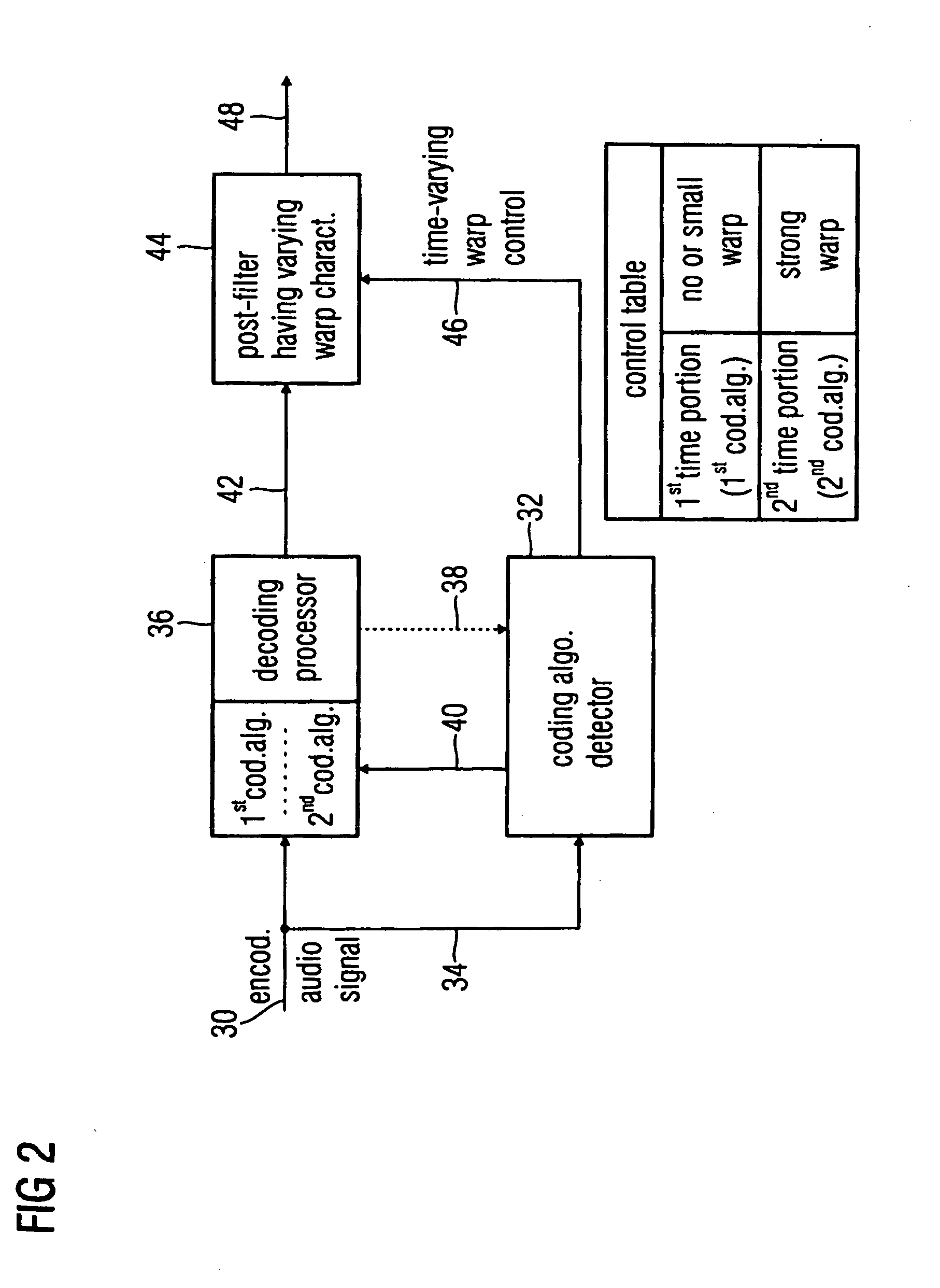
Audio encoder, audio decoder and audio processor having a dynamically variable warping characteristic
An audio encoder, an audio decoder or an audio processor includes a filter for generating a filtered audio signal, the filter having a variable warping characteristic, the characteristic being controllable in response to a time-varying control signal, the control signal indicating a small or no warping characteristic or a comparatively high warping characteristic. Furthermore, a controller is connected for providing the time-varying control signal, which depends on the audio signal. The filtered audio signal can be introduced to an encoding processor having different encoding algorithms, one of which is a coding algorithm adapted to a specific signal pattern. Alternatively, the filter is a post-filter receiving a decoded audio signal.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
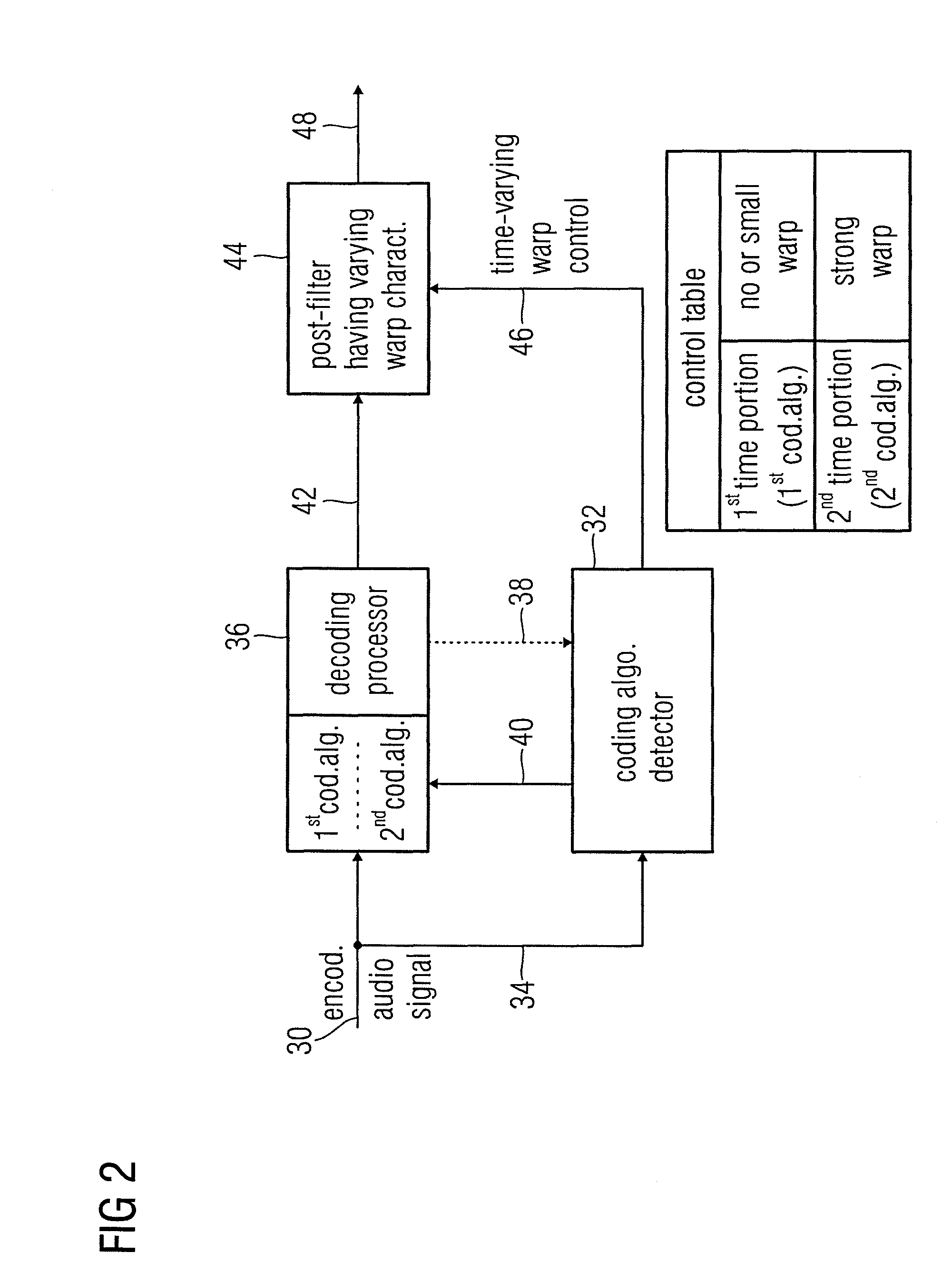
Audio encoder, audio decoder and audio processor having a dynamically variable warping characteristic
ActiveUS20100241433A1Quality improvementReduce bitrateSpeech analysisEncoding algorithmControl signal
An audio encoder, an audio decoder or an audio processor includes a filter (12) for generating a filtered audio signal, the filter having a variable warping characteristic, the characteristic being controllable in response to a time-varying control signal (16), the control signal indicating a small or no warping characteristic or a comparatively high warping characteristic. Furthermore, a controller (18) is connected for providing the time-varying control signal, which depends on the audio signal. The filtered audio signal can be introduced to an encoding processor (22) having different encoding algorithms, one of which is a coding algorithm adapted to a specific signal pattern. Alternatively, the filter is a post-filter receiving a decoded audio signal.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Systems and methods for encoding randomly distributed features in an object
The described systems and methods described are directed at encoding randomly distributed features in an object. Randomly distributed features in an authentication object are determined. Data representing the randomly distributed features is compressed and encoded with a signature. A label is created and includes the authentication object and the encoded data. The data may be compressed by determining a probability density function associated with the authentication object. Vectors associated with the randomly distributed attributes are determined based, at least in part, on the probability density function. The vectors are encoded using an arithmetic coding algorithm.
Owner:MICROSOFT TECH LICENSING LLC
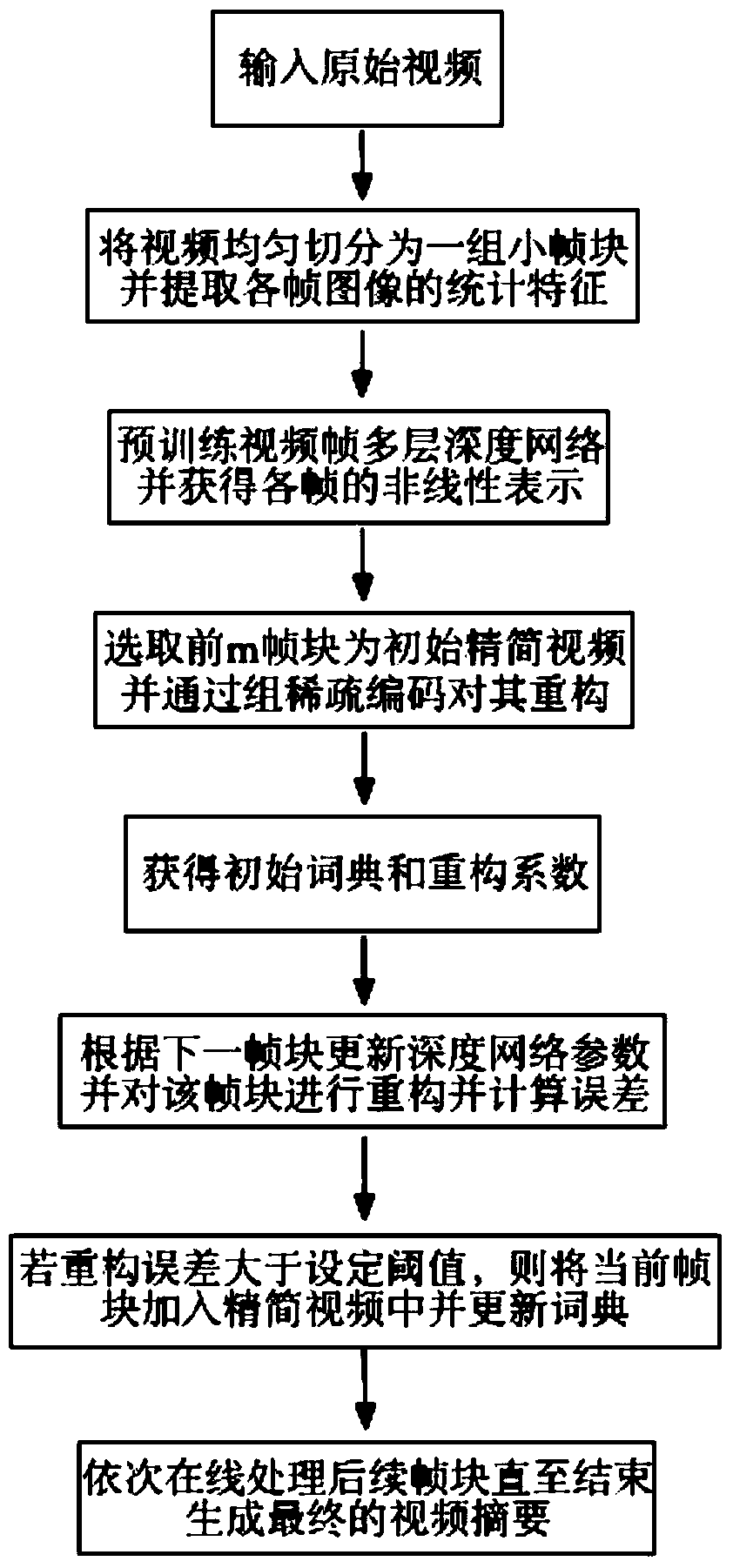
On-line video abstraction generation method based on depth learning
ActiveCN104113789AShorten the timeImprove visual experienceSelective content distributionSpecial data processing applicationsVisual perceptionReconstruction error
The invention relates to an on-line video abstraction generation method based on depth learning. An original video is subjected to the following operation: 1) cutting the video uniformly into a group of small frame blocks, extracting statistical characteristics of each frame image and forming corresponding vectorization expressions; 2) pre-training video frame multilayer depth network and obtaining the nonlinearity expression of each frame; 3) selecting the front m frame blocks being as an initial concise video, and carrying out reconstruction on the concise video through a group sparse coding algorithm to obtain an initial dictionary and reconstruction coefficients; 4) updating depth network parameters according to the next frame block, carrying out reconstruction and reconstruction error calculation on the frame block, and adding the frame block to the concise video and updating the dictionary if the error is larger than a set threshold; and 5) processing new frame blocks till the end in sequence on line according to the step 4), and the updated concise video being generated video abstraction. With the method, latent high-level semantic information of the video can be excavated deeply, the video abstraction can be generated quickly, time of users is saved, and visual experience is improved.
Owner:HANGZHOU HUICUI INTELLIGENT TECH CO LTD
Lock
ActiveUS20120229251A1Easy to operateResistant to tamperingElectric signal transmission systemsVehicle locksLocking mechanismEngineering
An electro-mechanical lock for cargo containers or similar enclosed spaces such as storage units. The locking mechanism includes a dual-ratcheting mechanism, which is normally in the locked position, and which firmly secures doors of a container or other enclosure. To unlock the device, the user obtains a temporary access code and unlocks the device, either by a wireless interface or by, for example, a key pad. The device incorporates a rolling access code algorithm that changes the access code based upon a pre-defined customer selected time period during which the code is valid. Once the validity period expires the user must obtain a new access code from a secure access code source to unlock the device. When access is desired, the user contacts a remote secure access code source, which provides the access code for the associated lock and time period.
Owner:SECURITY ENHANCEMENT SYST
Apparatus and method for merging data blocks with error correction code protection
ActiveUS20090313526A1Code conversionError correction/detection using block codesData integrityEncoding algorithm
An apparatus and method for selectively deriving Error Correction Codes (ECCs) or other data integrity information for integration into merged data blocks. First data is merged into second data that is error-protected using an ECC generated by a coding algorithm. Bytes or other data units are identified in the first data to be merged into the second data. It is determined whether each of the check bits of the ECC will differ from its original state in response to merging the first and second data. The check bits of the ECC that have been determined to differ from their respective original states are modified to create a “merged ECC.” The resulting data block includes the merged data and the merged ECC.
Owner:UNISYS CORP
Procedure for exchanging useful information generated according to different coding laws between at least 2 pieces of user terminal equipment
InactiveUS20050008030A1Efficient coding/decodingInterconnection arrangementsTime-division multiplexTerminal equipmentCode conversion
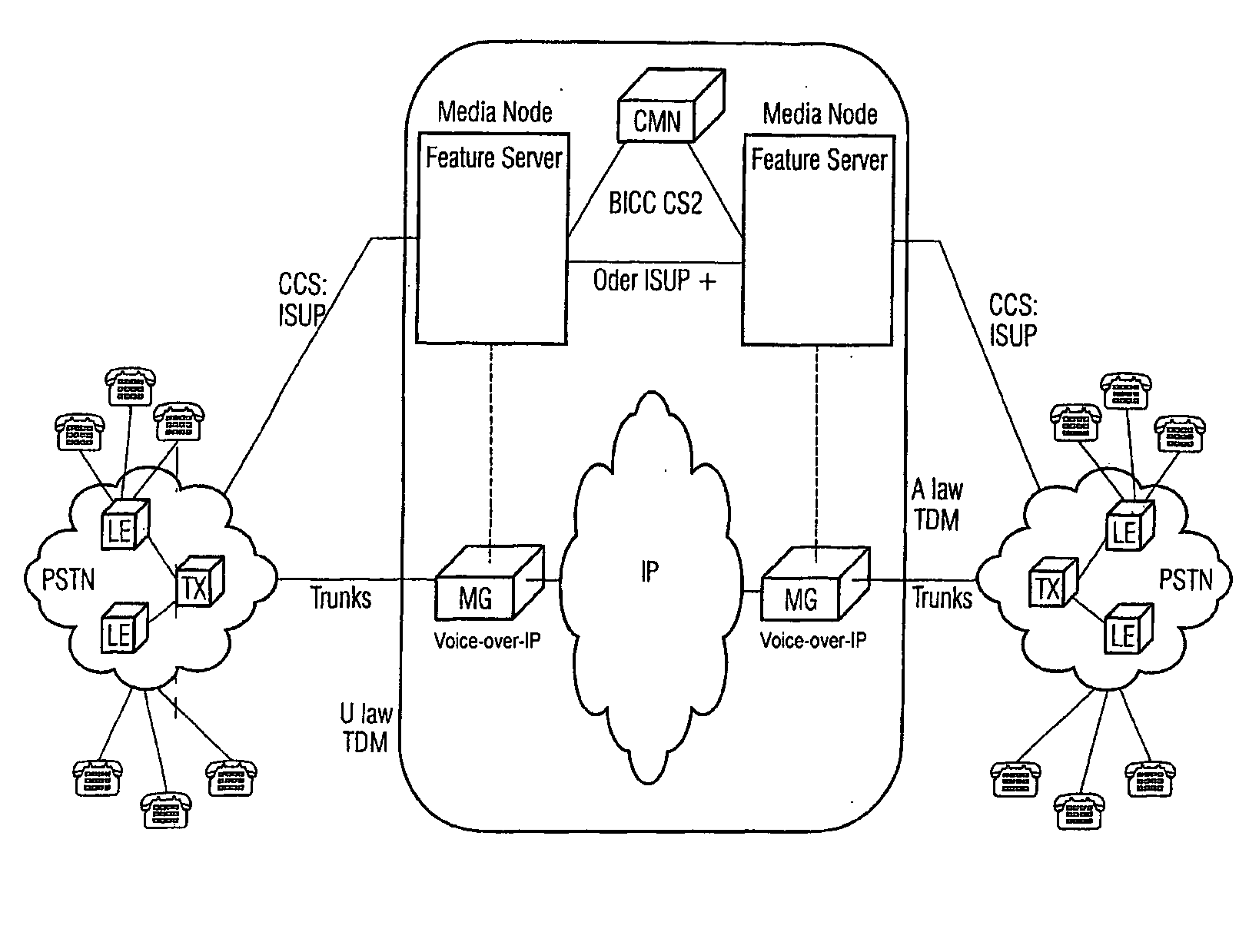
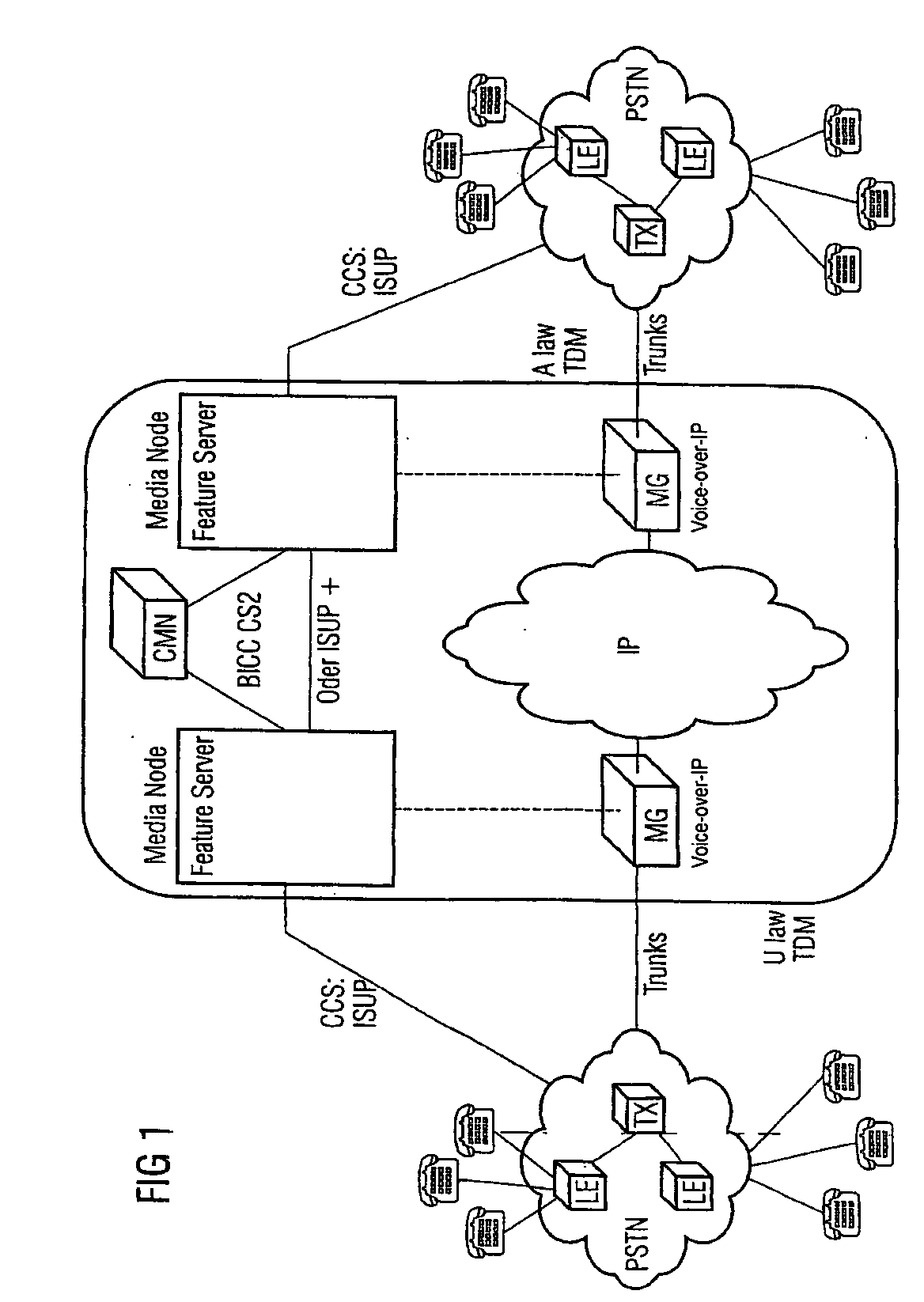
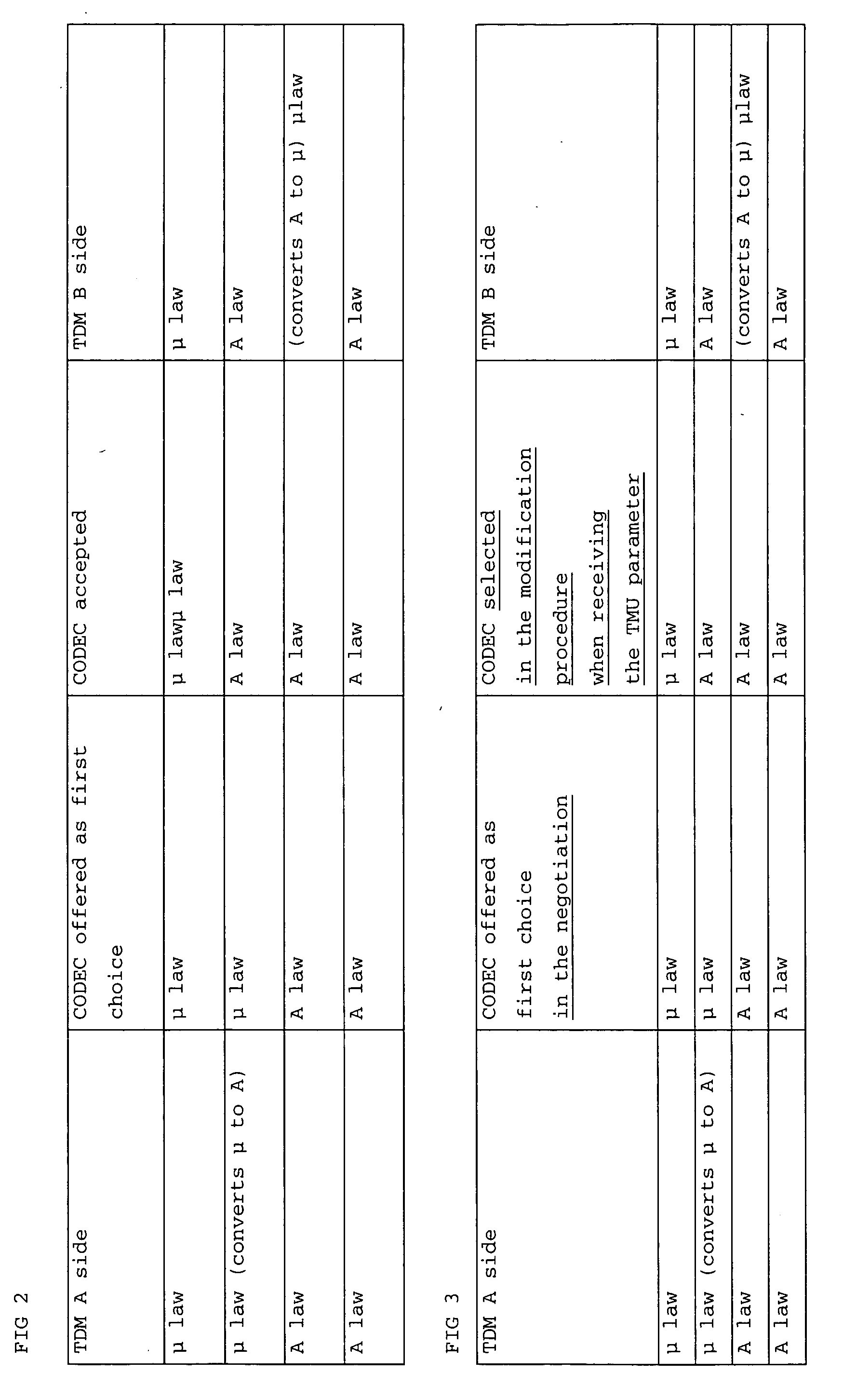
If TDM connections are through-connected from the originating TDM network to the target TDM network via a data network in the form of backbone, e.g. VoIP, the switchover between the TDM network and the data network takes place via media gateways. As is the case with connections exclusively between TDM, the coding algorithms of the A face and the B face have to be identical. In TDM networks, coding is done according to A Law and μ Law. When switching from an A Law network to a μ Law network, the coding specifications have to be converted. In order to carry out a conversion in a TDM environment, at the switchover point the μ Law face has to convert to A Law. The same applies to VoIP. The invention relates to the integration of this switchover conversion rule in the codec negotiation procedure so that in principle a μ Law A face offers μ Law and, alternatively, A-Law to the B face; a μ Law B face accepts μ Law whereas an A-Law B face acknowledges A-Law. Furthermore, 64 kBit / s unrestricted preferred connections are considered in fall back mode, wherefore an additional logic is integrated into the codec modification procedure by means of which in principle μ Law and, as an alternative, A-Law are offered to the B face in addition to the transparent CODEC or instead of offering a μ Law A face to the TMR only. The B face first accepts the transparent CODEC on the basis of the list or the TMR ‘64 kBit / s unrestricted preferred’. When receiving the TMU, the B face selects the Codec to satisfy the code conversion rule.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
Method and apparatus for scalable video encoding and decoding
InactiveUS20050117640A1Color television with pulse code modulationPulse modulation television signal transmissionComputer graphics (images)Video encoding
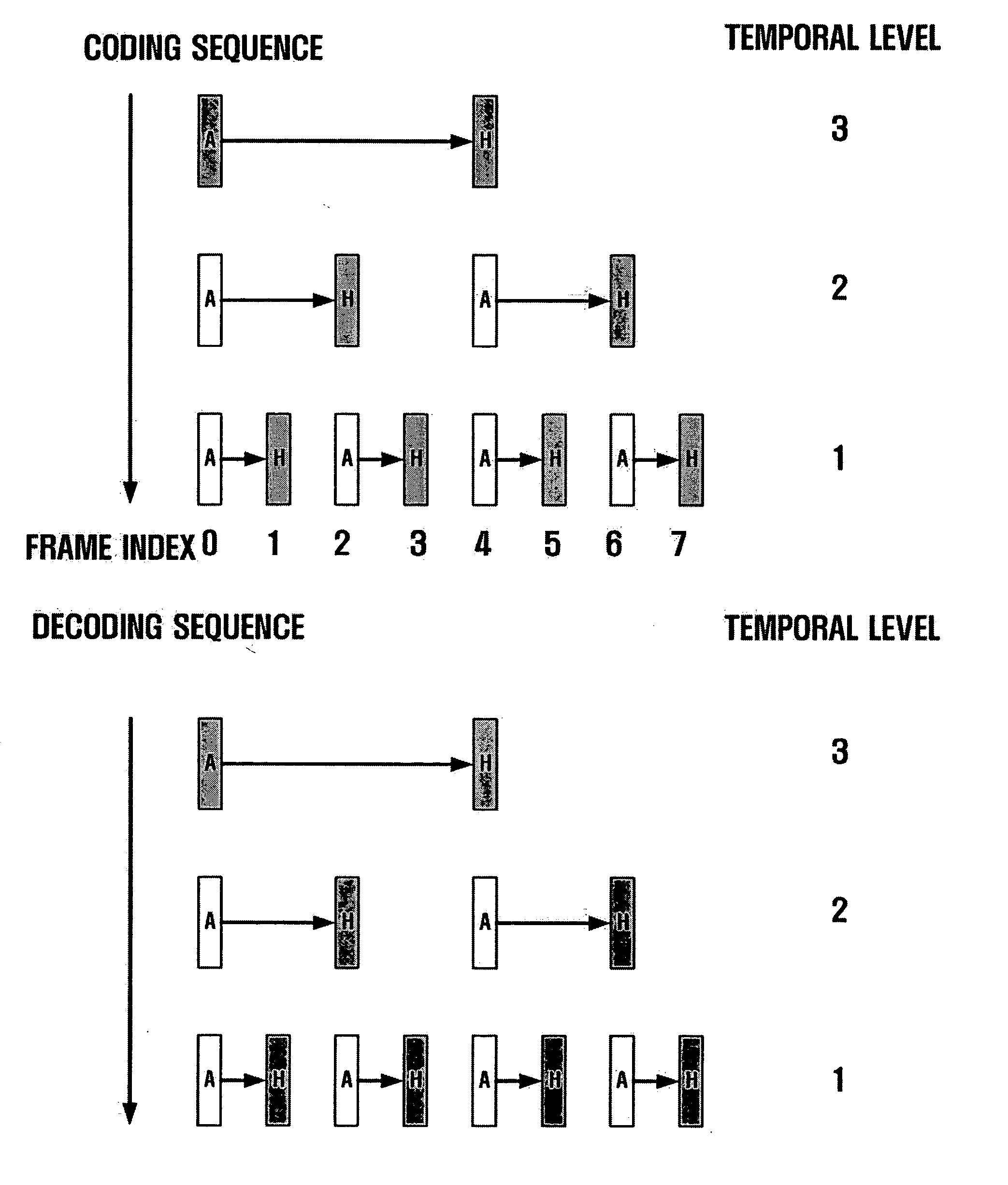
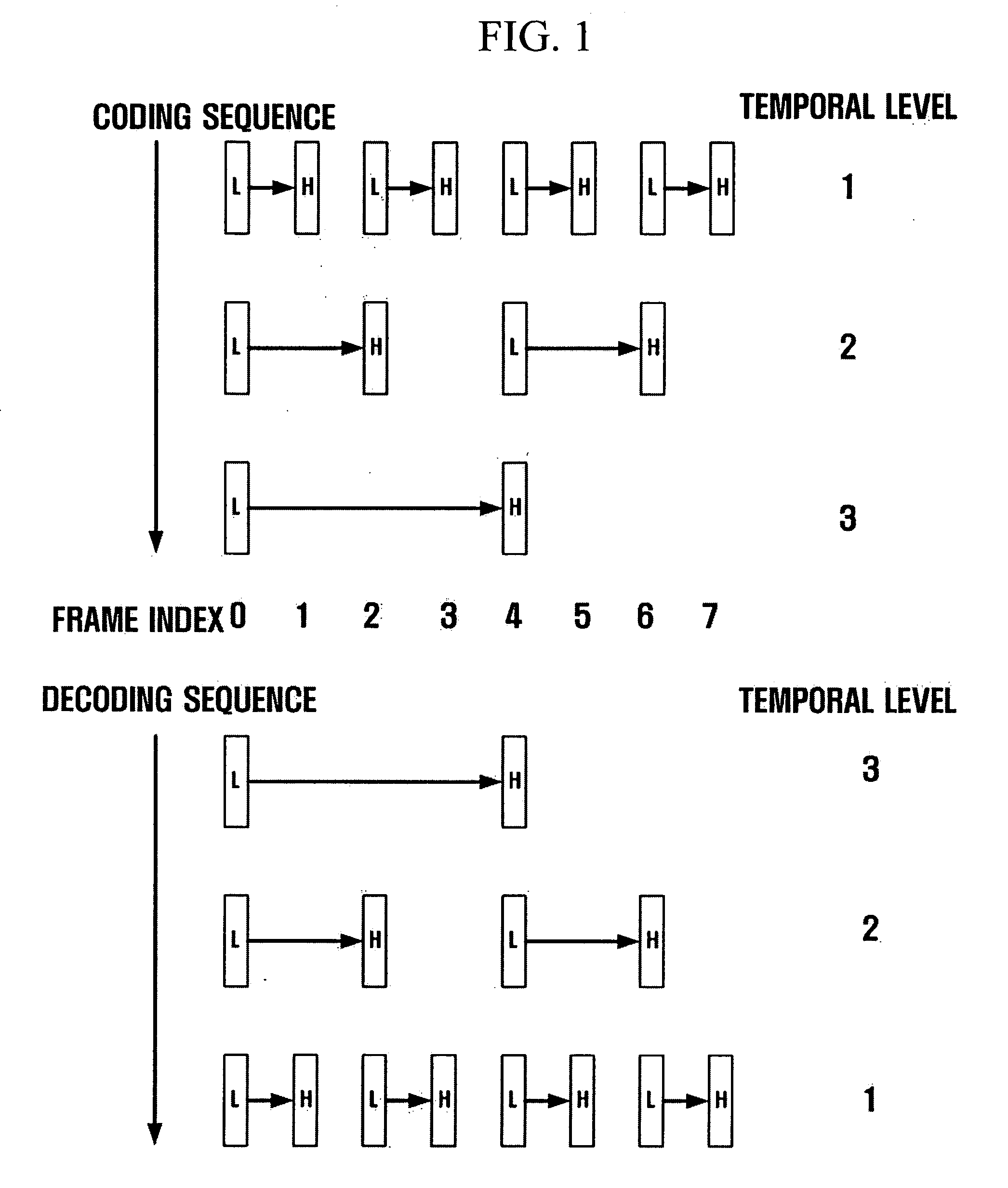
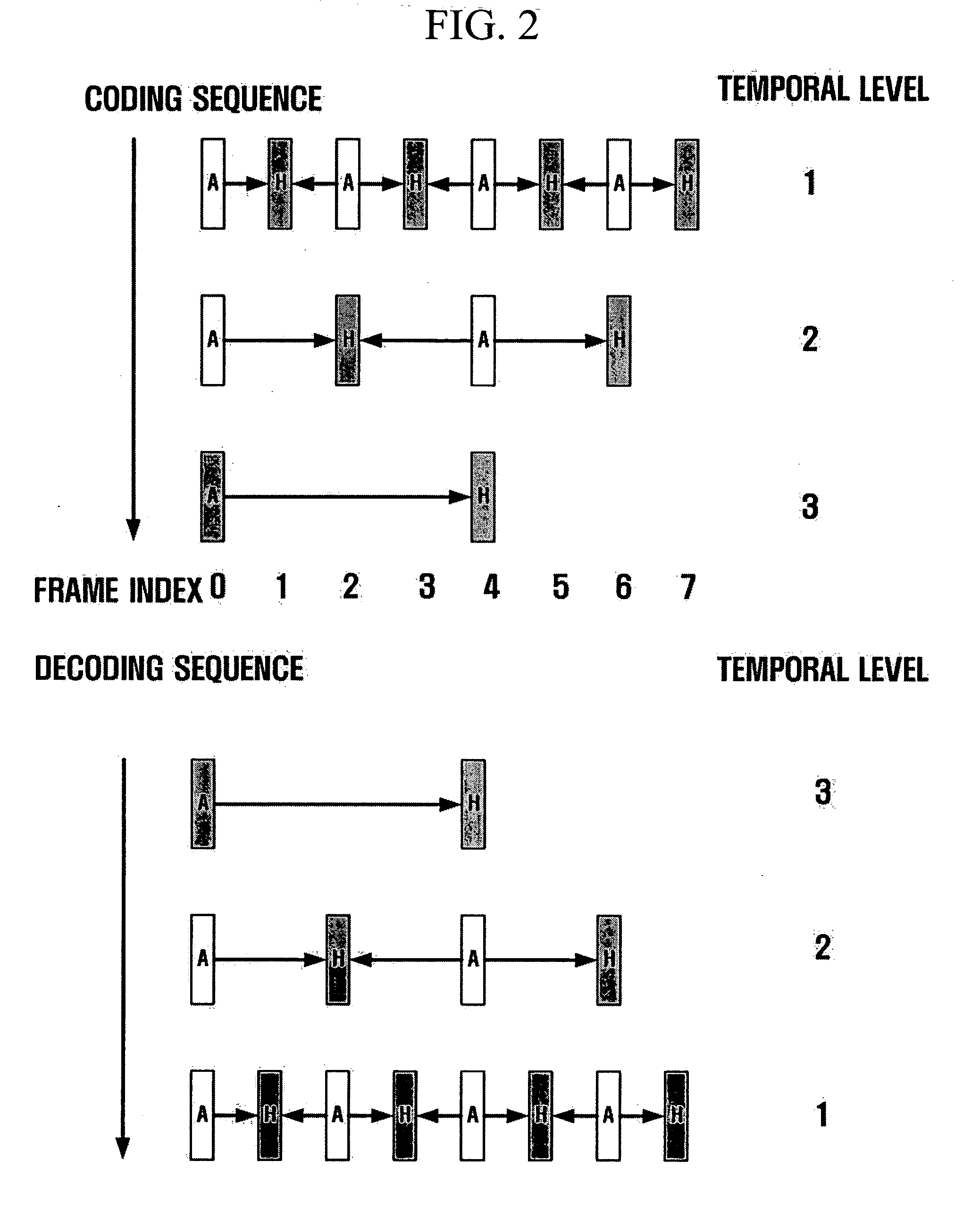
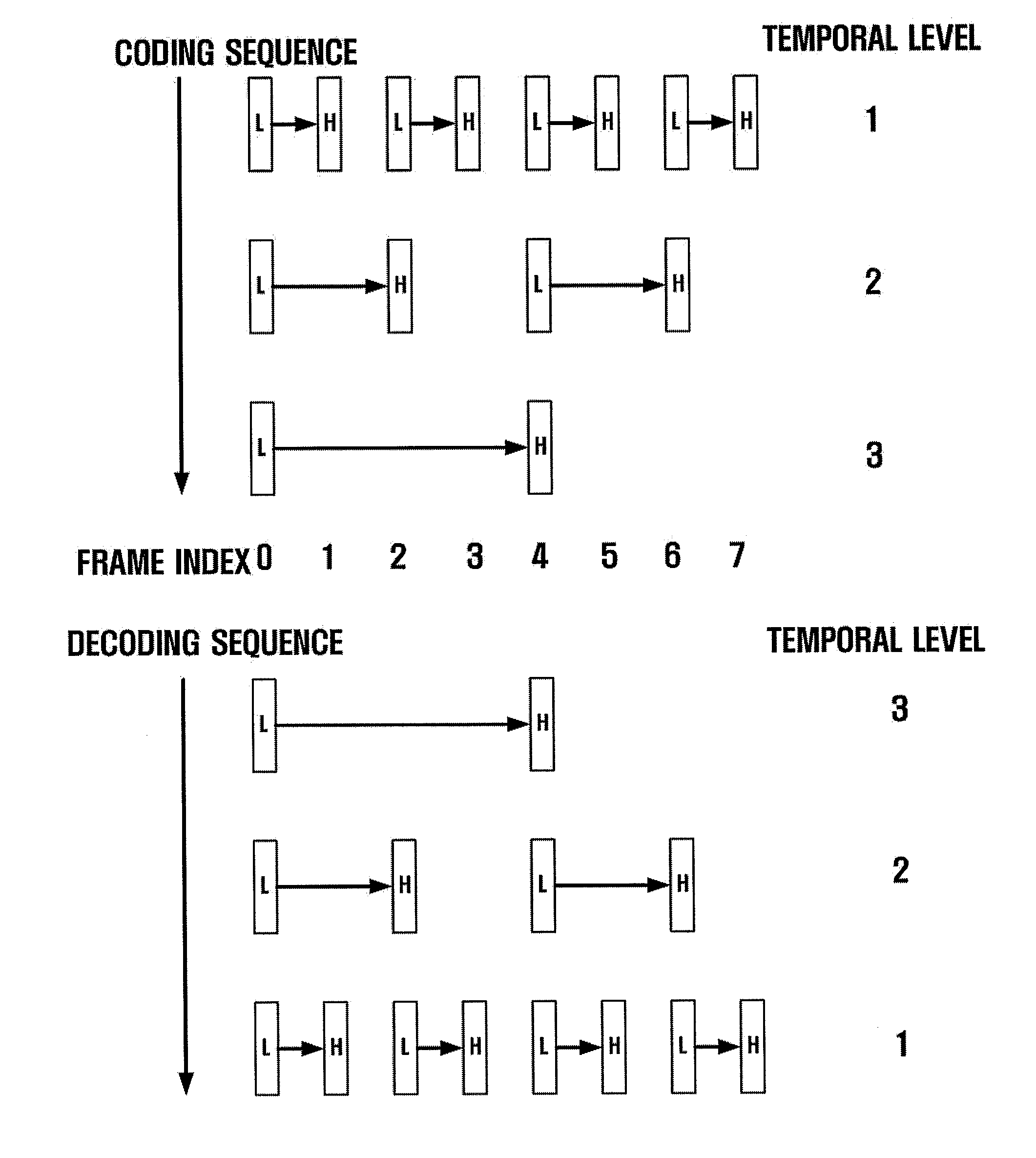
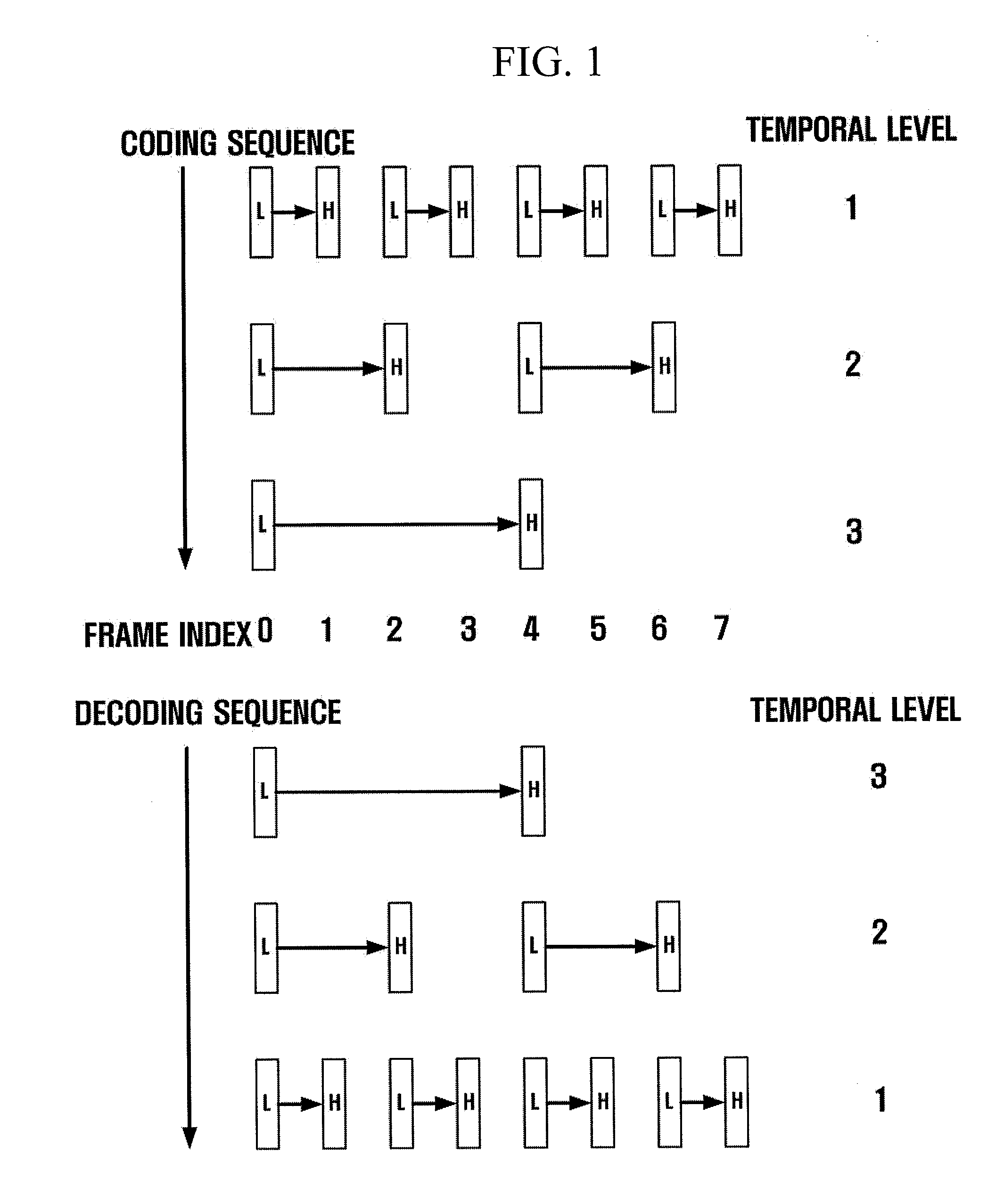
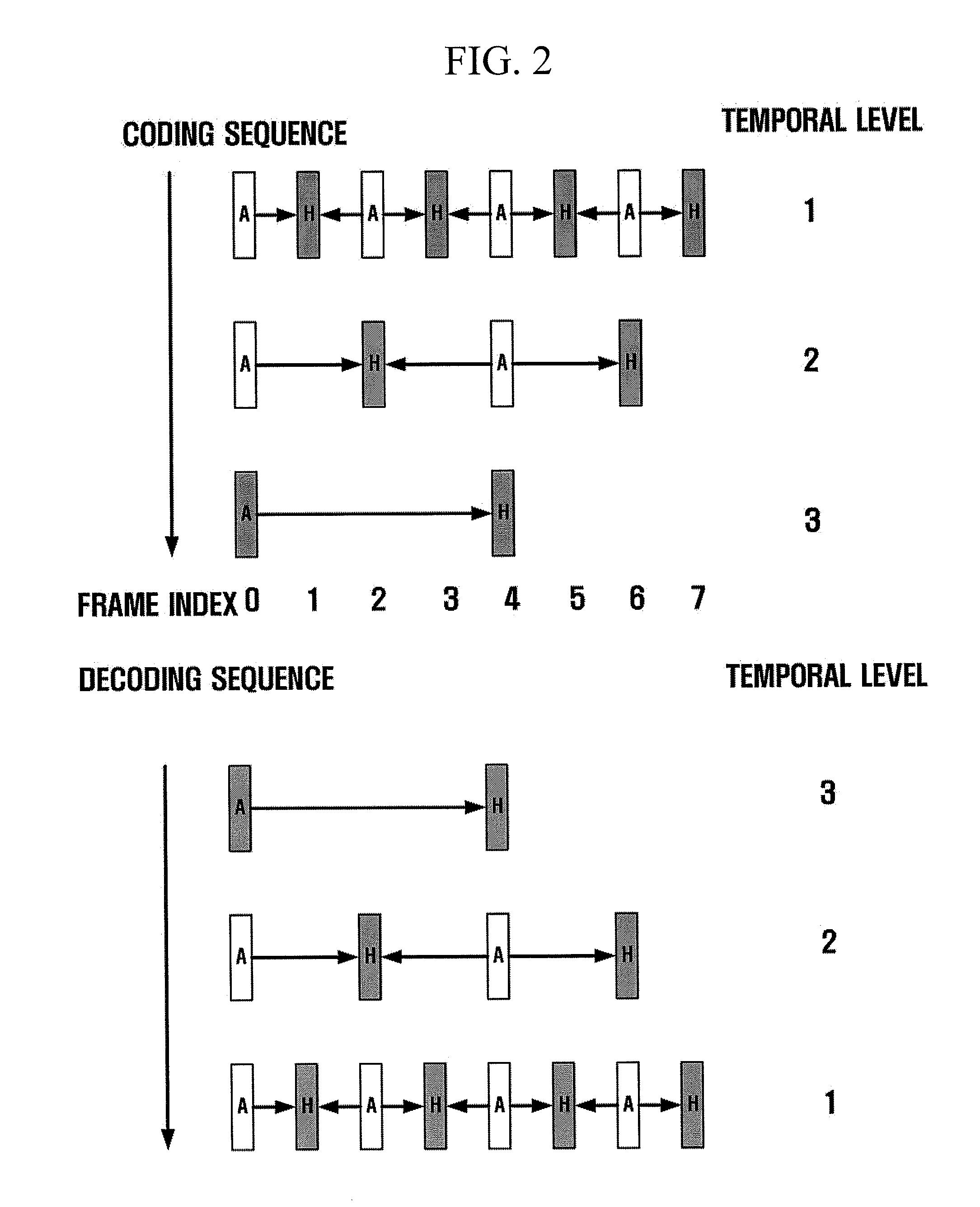
Disclosed is a scalable video coding algorithm. A method for video coding includes temporally filtering frames in the same sequence to a decoding sequence thereof to remove temporal redundancy, obtaining and quantizing transformation coefficients from frames whose temporal redundancy is removed, and generating bitstreams. A video encoder comprises a temporal transformation unit, a spatial transformation unit, a quantization unit and a bitstream generation unit to perform the method. A method for video decoding is basically reverse in sequence to the video coding. A video decoder extracts information necessary for video decoding by interpreting the received bitstream and decoding it. Thus, video streams may be generated by allowing a decoder to decode the generated bitstreams, while maintaining the temporal scalability on an encoder-side.
Owner:SAMSUNG ELECTRONICS CO LTD
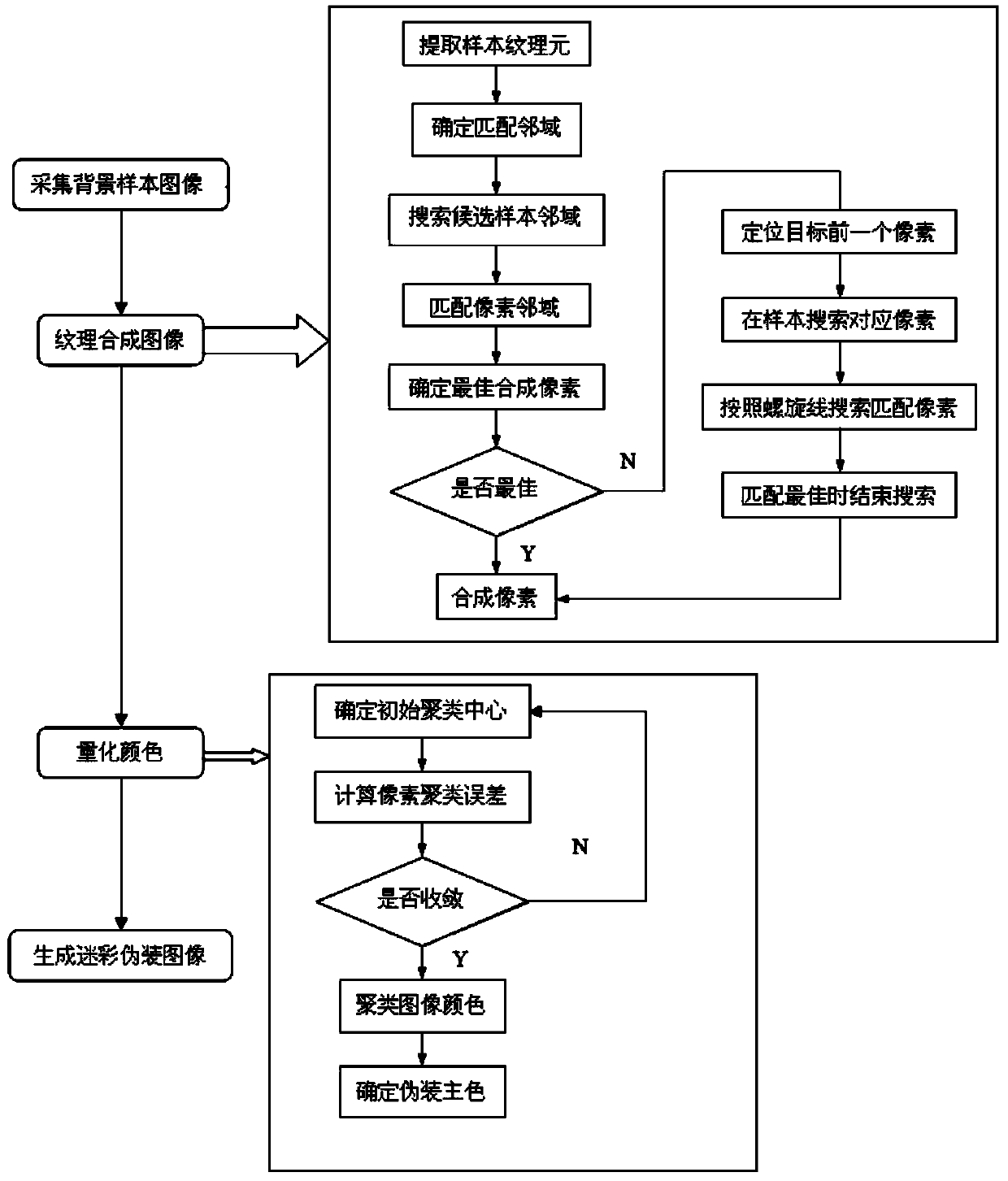
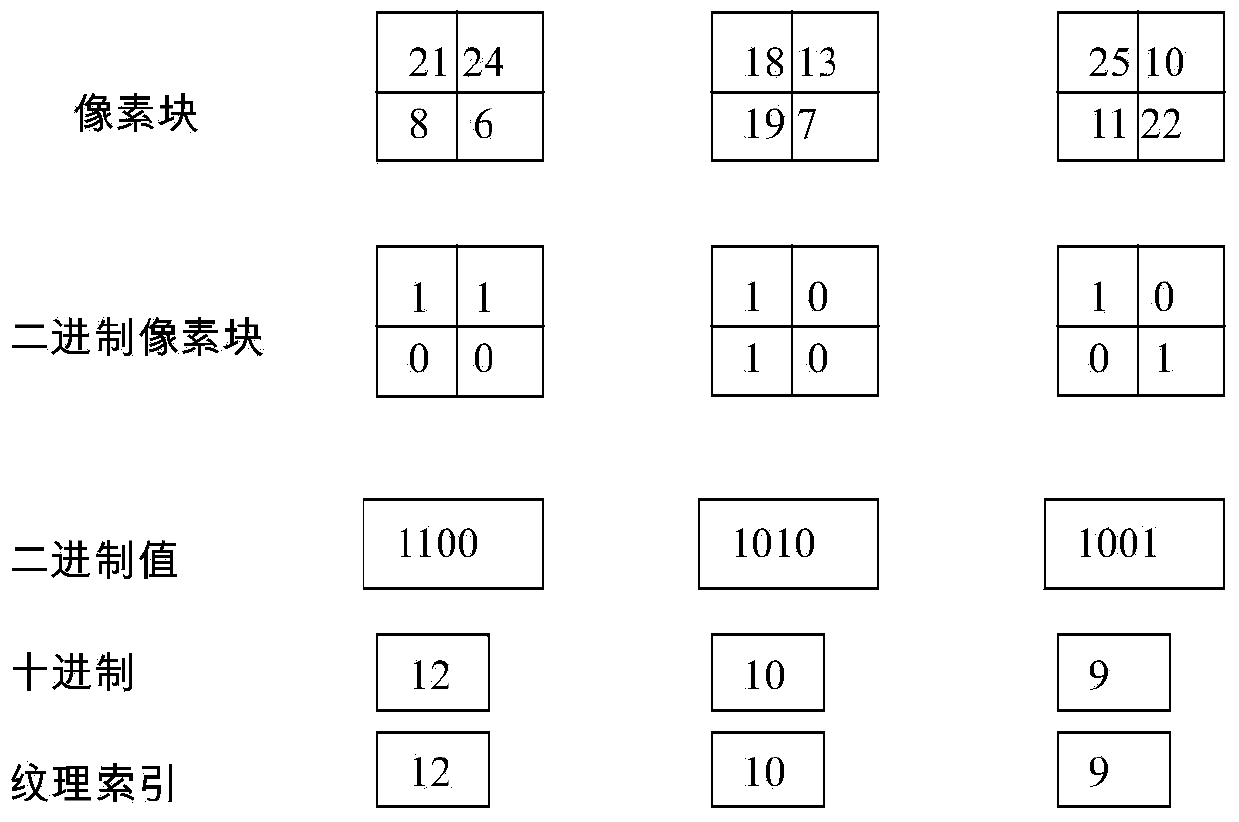
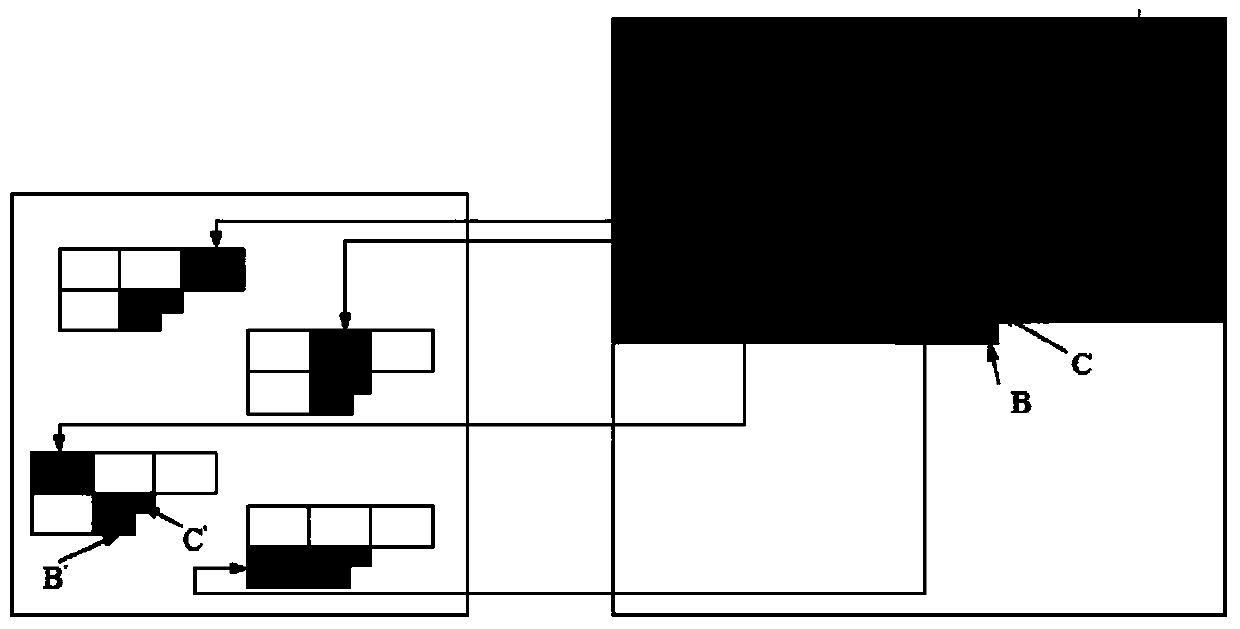
Self-adaptation camouflage design method based on background
InactiveCN104318570AHigh synthesis efficiencyQuality assuranceImage analysisTexturing/coloringCluster algorithmSelf adaptive
The invention discloses a self-adaptation camouflage design method based on a background. According to the method, on the basis of a texture synthesis algorithm based on pixels, a whole camouflage image is synthesized pixel by pixel; in the synthesis process, a self coding algorithm is adopted to extract a texture primitive containing background sample complete texture features, and a neighborhood of the pixels to be synthesized is determined; by means of the neighboring correlation principle and a helix supplement search mechanism, a neighborhood matched with a target pixel neighborhood is searched for in a background sample; similarity matching is carried out through a pixel and texture similarity matching rule, pixels in the neighborhoods which are most similar in the sample are selected to serve as synthesis pixels, pixels of a target image are synthesized according to the sequence of scanning lines, and after synthesis, color quantization is carried out on the image by means of the clustering algorithm to generate a final camouflage image. By means of the method, similar camouflage images can be synthesized quickly according to the background, and the application aim of quickly camouflaging a target in a self-adaptation mode can be achieved.
Owner:SHENYANG JIANZHU UNIVERSITY
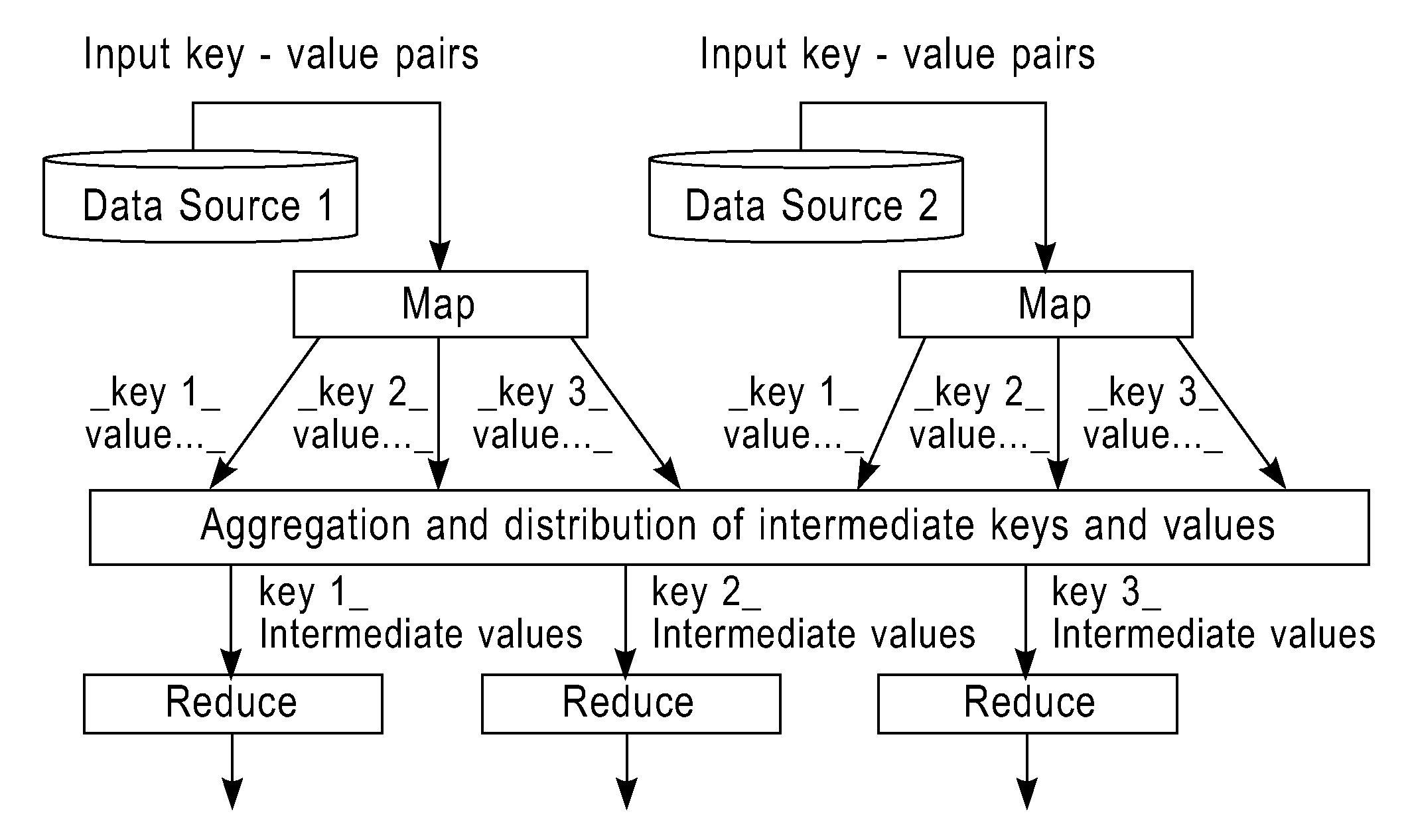
System and Method for Simplifying Transmission in Parallel Computing System
InactiveUS20110208947A1Easy transferSimplified intermediate resultDigital data information retrievalCode conversionParallel computingAverage size
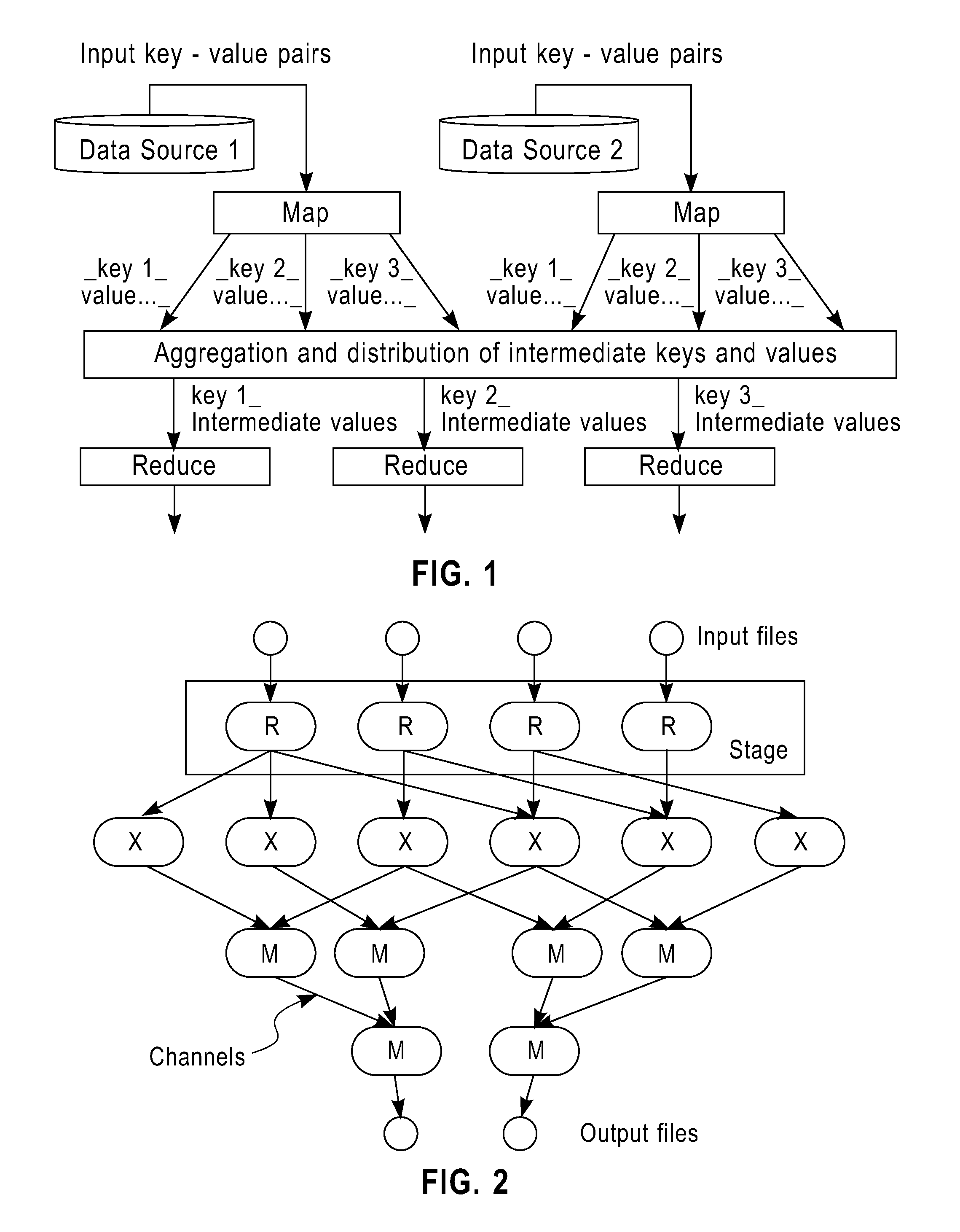
Simplifying transmission in a distributed parallel computing system. The method includes: identifying at least one item in a data input to the parallel computing unit; creating a correspondence relation between the at least one item and indices thereof according to a simplification coding algorithm, where the average size of the indices is less than the average size of the at least one item; replacing the at least one item with the corresponding indices according to the correspondence relation; generating simplified intermediate results by the parallel computing unit based on the indices; and transmitting the simplified intermediate results. The invention also provides a system corresponding to the above method.
Owner:IBM CORP
Method and apparatus for scalable video encoding and decoding
InactiveUS20100142615A1Color television with pulse code modulationPulse modulation television signal transmissionComputer graphics (images)Video encoding
Disclosed is a scalable video coding algorithm. A method for video coding includes temporally filtering frames in the same sequence to a decoding sequence thereof to remove temporal redundancy, obtaining and quantizing transformation coefficients from frames whose temporal redundancy is removed, and generating bitstreams. A video encoder comprises a temporal transformation unit, a spatial transformation unit, a quantization unit and a bitstream generation unit to perform the method. A method for video decoding is basically reverse in sequence to the video coding. A video decoder extracts information necessary for video decoding by interpreting the received bitstream and decoding it. Thus, video streams may be generated by allowing a decoder to decode the generated bitstreams, while maintaining the temporal scalability on an encoder-side.
Owner:SAMSUNG ELECTRONICS CO LTD
Frequency-domain scalable coding without upsampling filters
InactiveUS6370507B1Easy to operateSpeech analysisIndividual digits conversionFrequency spectrumImage resolution
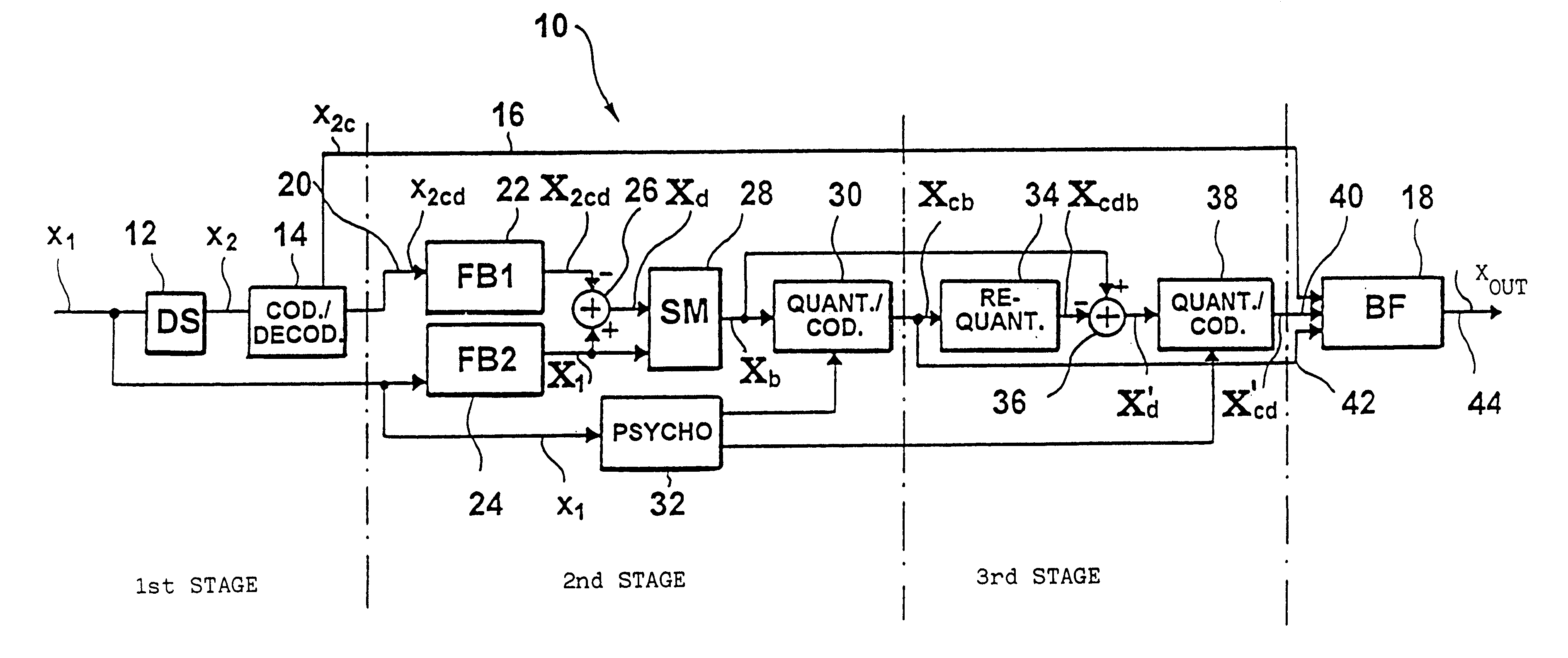
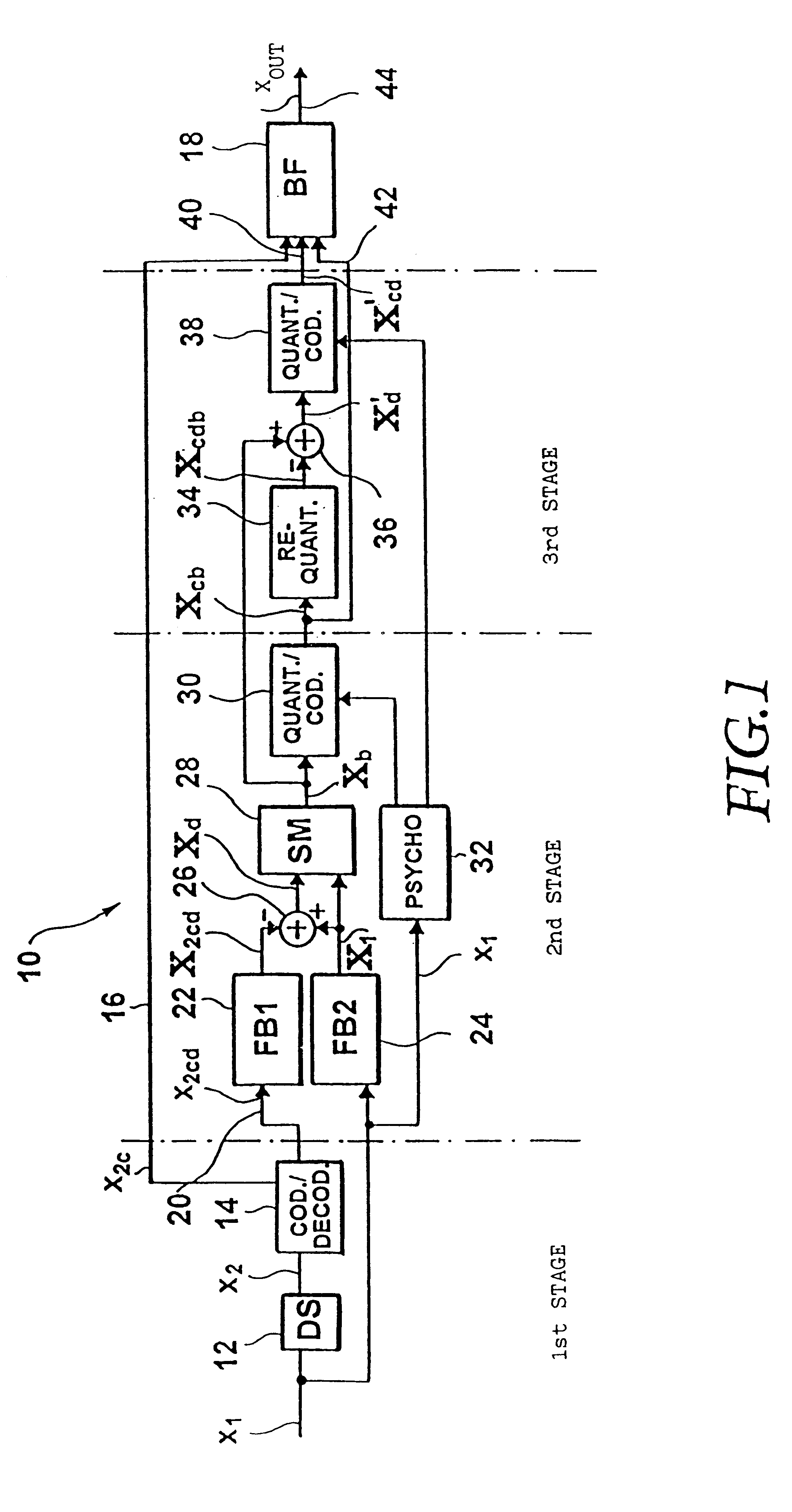
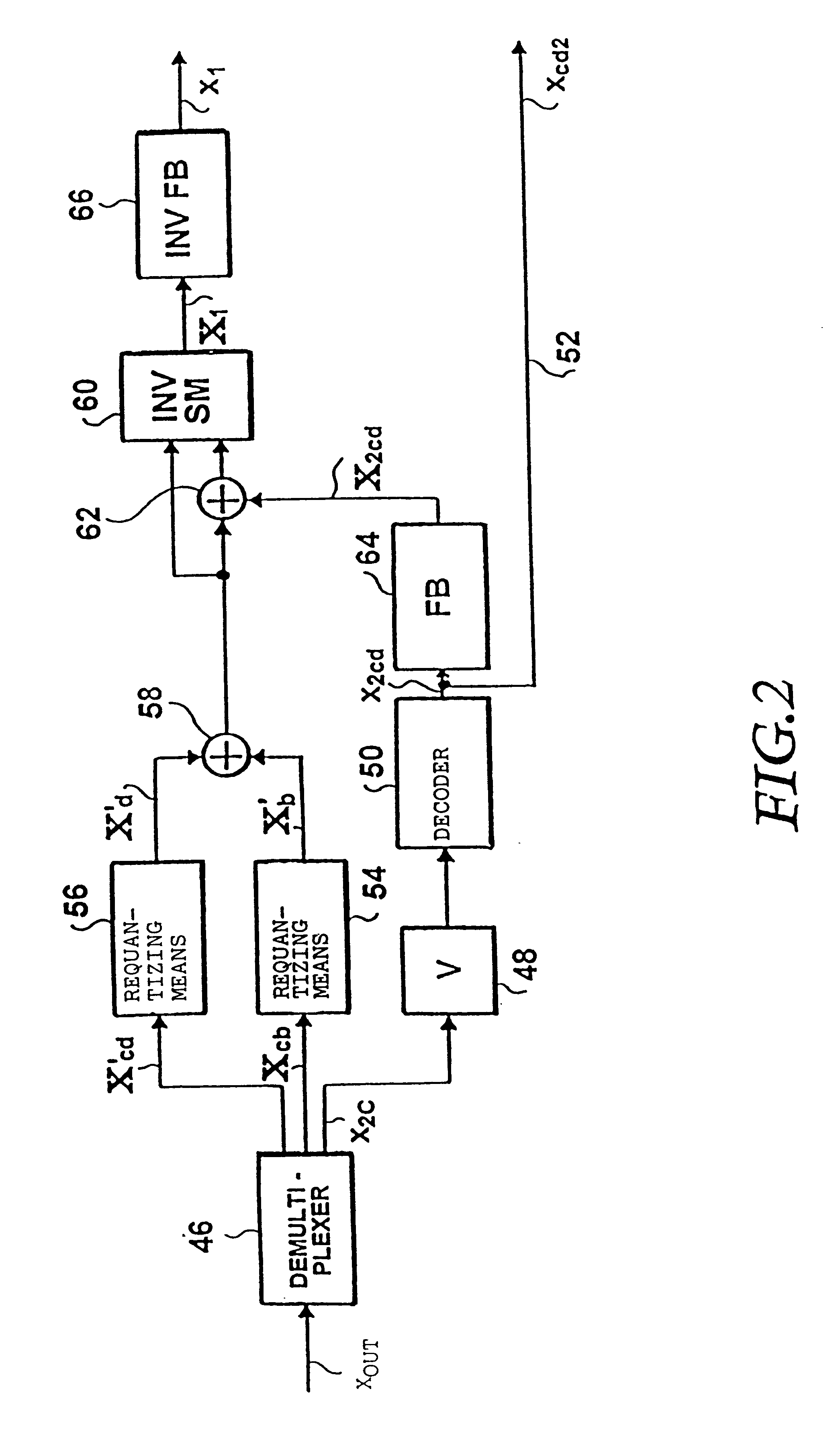
In a method of coding discrete time signals (X1) sampled with a first sampling rate, second time signals (x2) are generated using the first time signals having a bandwidth corresponding to a second sampling rate, with the second sampling rate being lower than the first sampling rate. The second time signals are coded in accordance with a first coding algorithm. The coded second signals (X2c) are decoded again in order to obtain coded / decoded second time signals (X2cd) having a bandwidth corresponding to the second sampling frequency. The first time signals, by frequency domain transformation, become first spectral values (X1). Second spectral values (X2cd) are generated from the coded / decoded second time signals, the second spectral values being a representation of the coded / decoded time signals in the frequency domain. To obtain weighted spectral values, the first spectral values are weighted by means of the second spectral values, with the first and second spectral values having the same frequency and time resolution. The weighted spectral values (Xb) are coded in accordance with a second coding algorithm in consideration of a psychoacoustic model and written into a bit stream. Weighting the first spectral values and the second spectral values comprises the subtraction of the second spectral values from the first spectral values in to obtain differential spectral values.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Systems and methods for encoding randomly distributed features in an object
The described systems and methods described are directed at encoding randomly distributed features in an object. Randomly distributed features in an authentication object are determined. Data representing the randomly distributed features is compressed and encoded with a signature. A label is created and includes the authentication object and the encoded data. The data may be compressed by determining a probability density function associated with the authentication object. Vectors associated with the randomly distributed attributes are determined based, at least in part, on the probability density function. The vectors are encoded using an arithmetic coding algorithm.
Owner:MICROSOFT TECH LICENSING LLC
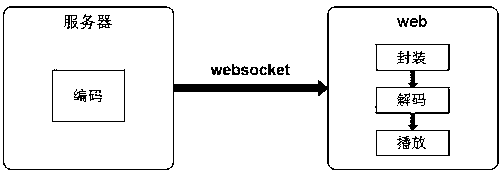
Virtual desktop remote method and system applicable to mobile terminal or Web side
InactiveCN107613029AReduce trafficImprove interactive experienceTransmissionSelective content distributionHTML5Traffic capacity
The invention discloses a virtual desktop remote method and system applicable to a mobile terminal or a Web side and belongs to the technical field of network. A VDI (virtual device interface) remotescreen is encapsulated into a coded streaming supported by a browser, the coded streaming is encapsulated into a video streaming capable of being recognized by the browser through a video streaming extension protocol of MSE (media source extensions), and the video streaming is displayed by the aid of an HTML5 video tag. Transmission flow can be lowered by adopting a more efficient frame-related video coding algorithm, use of computing sources can be reduced by making full use of the decoding function of hardware of the browser, and interactive experience is improved.
Owner:深圳市青葡萄科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com