Patents
Literature
2950 results about "Transformation unit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
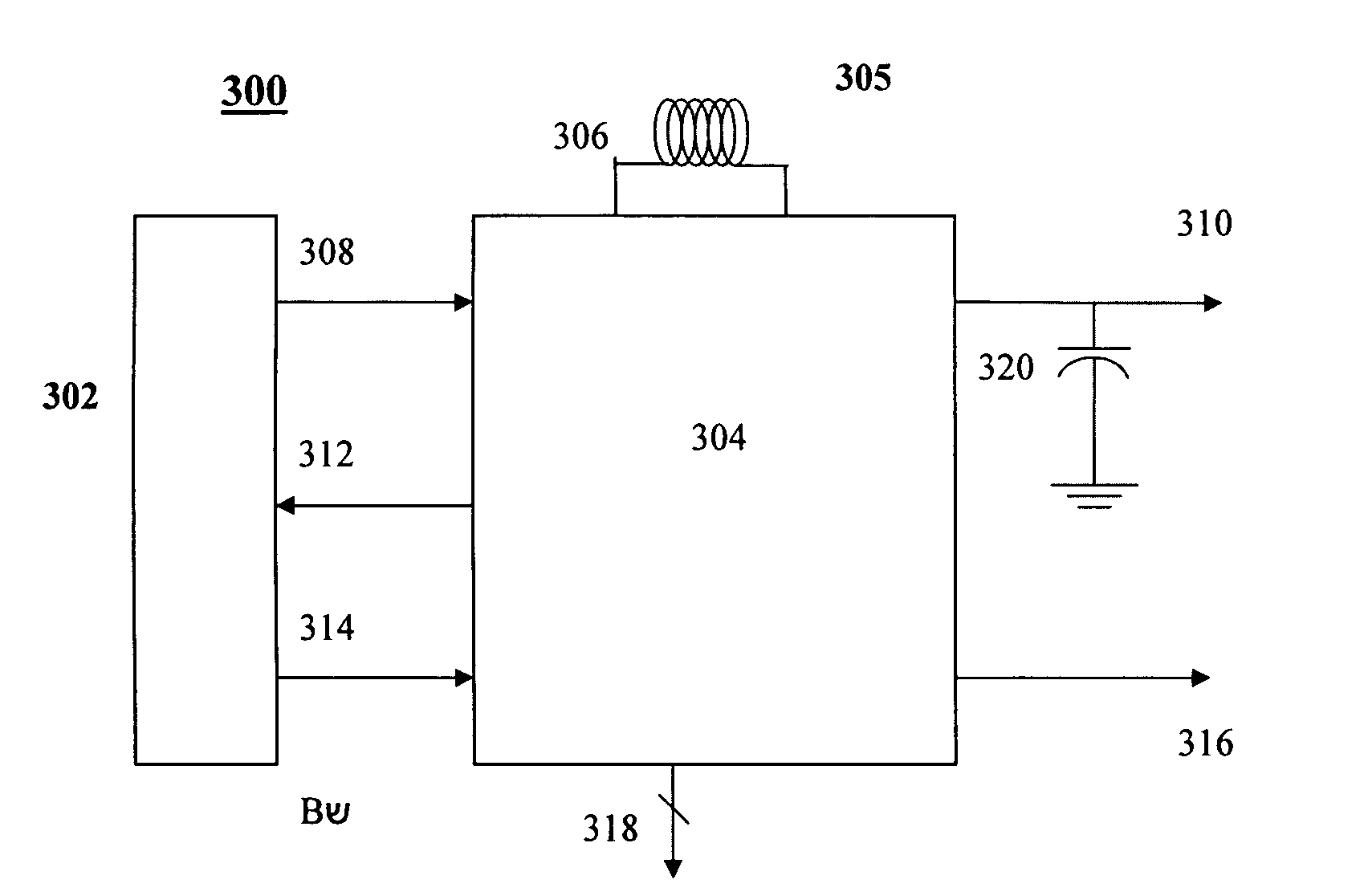
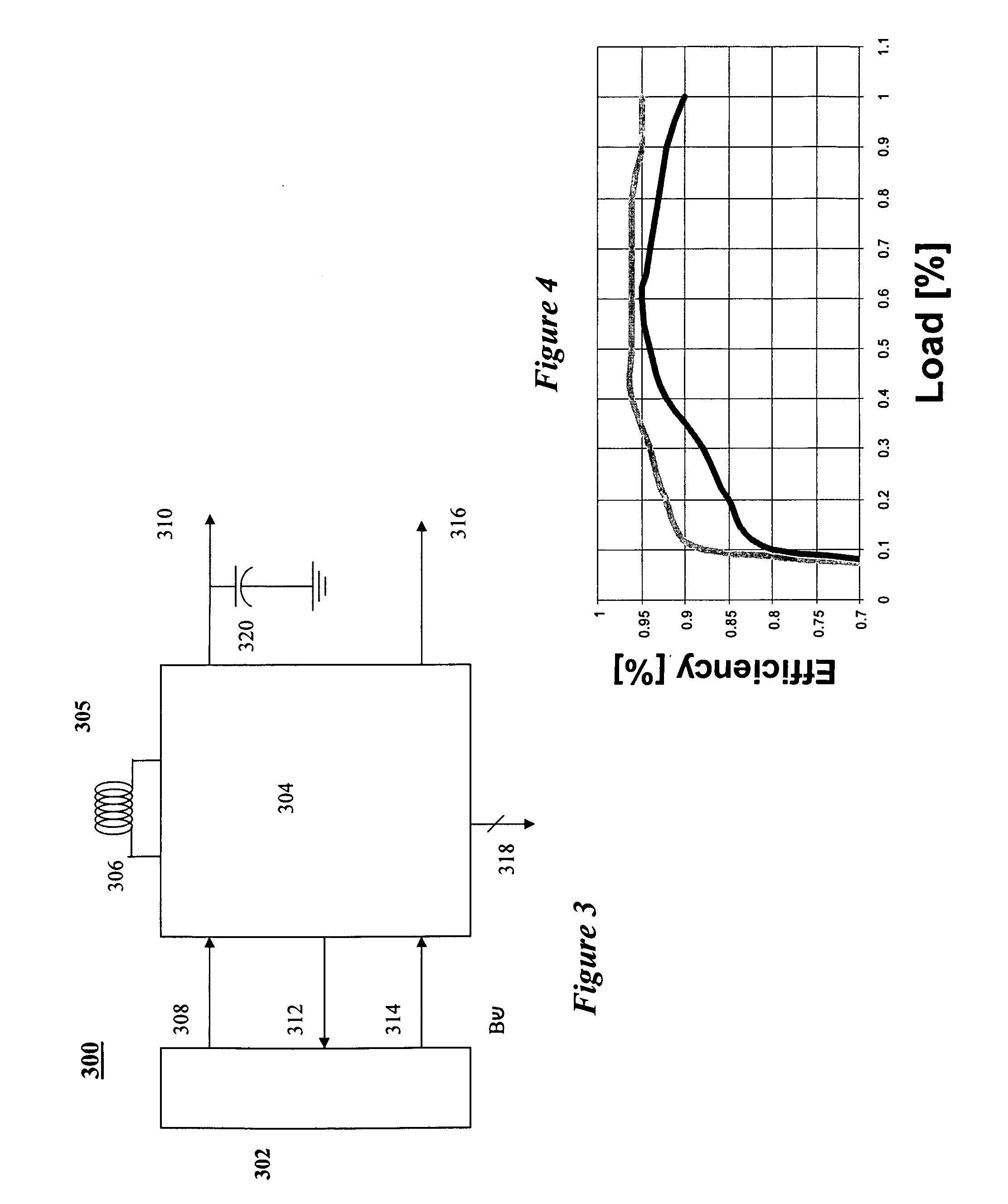
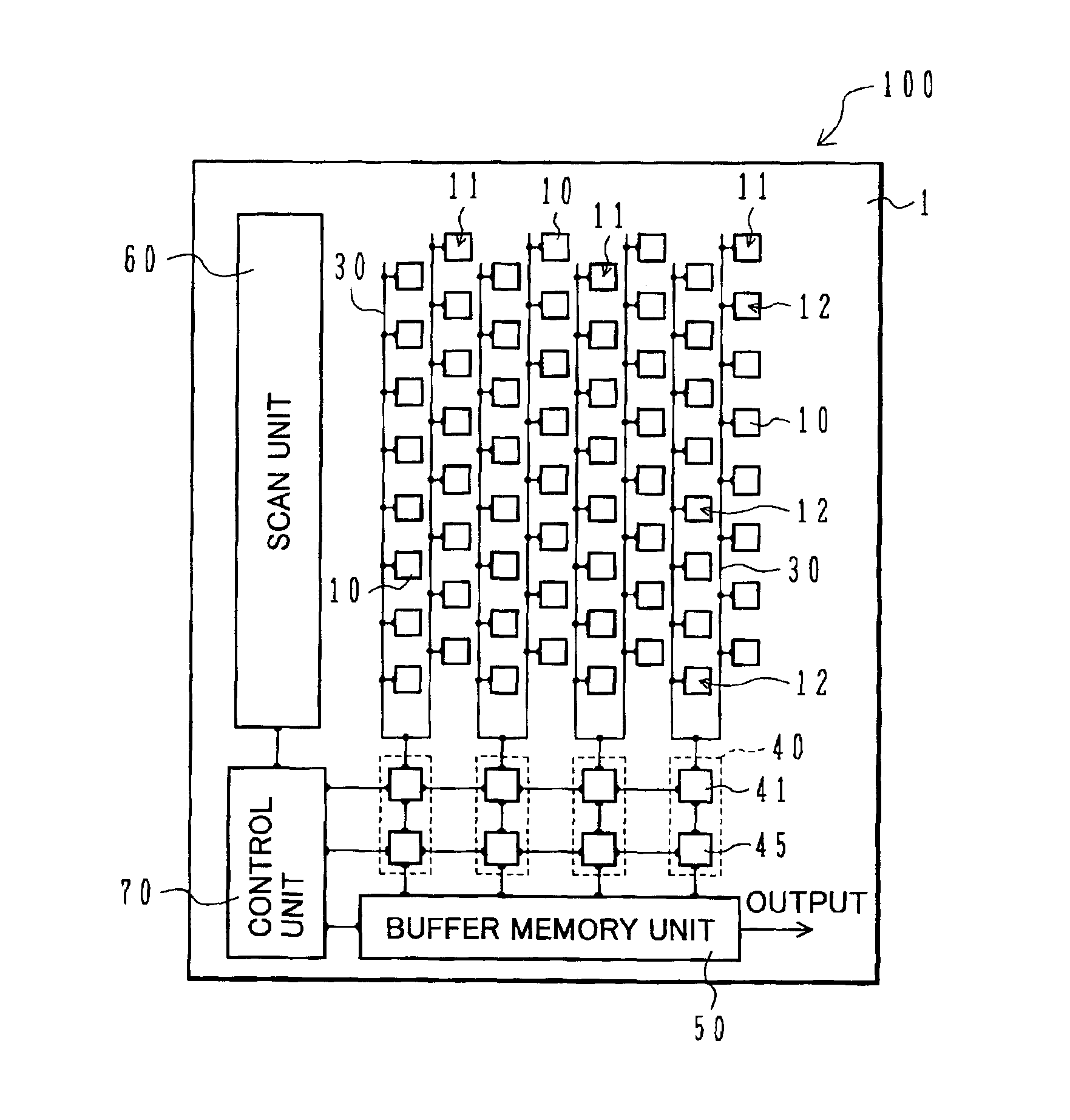
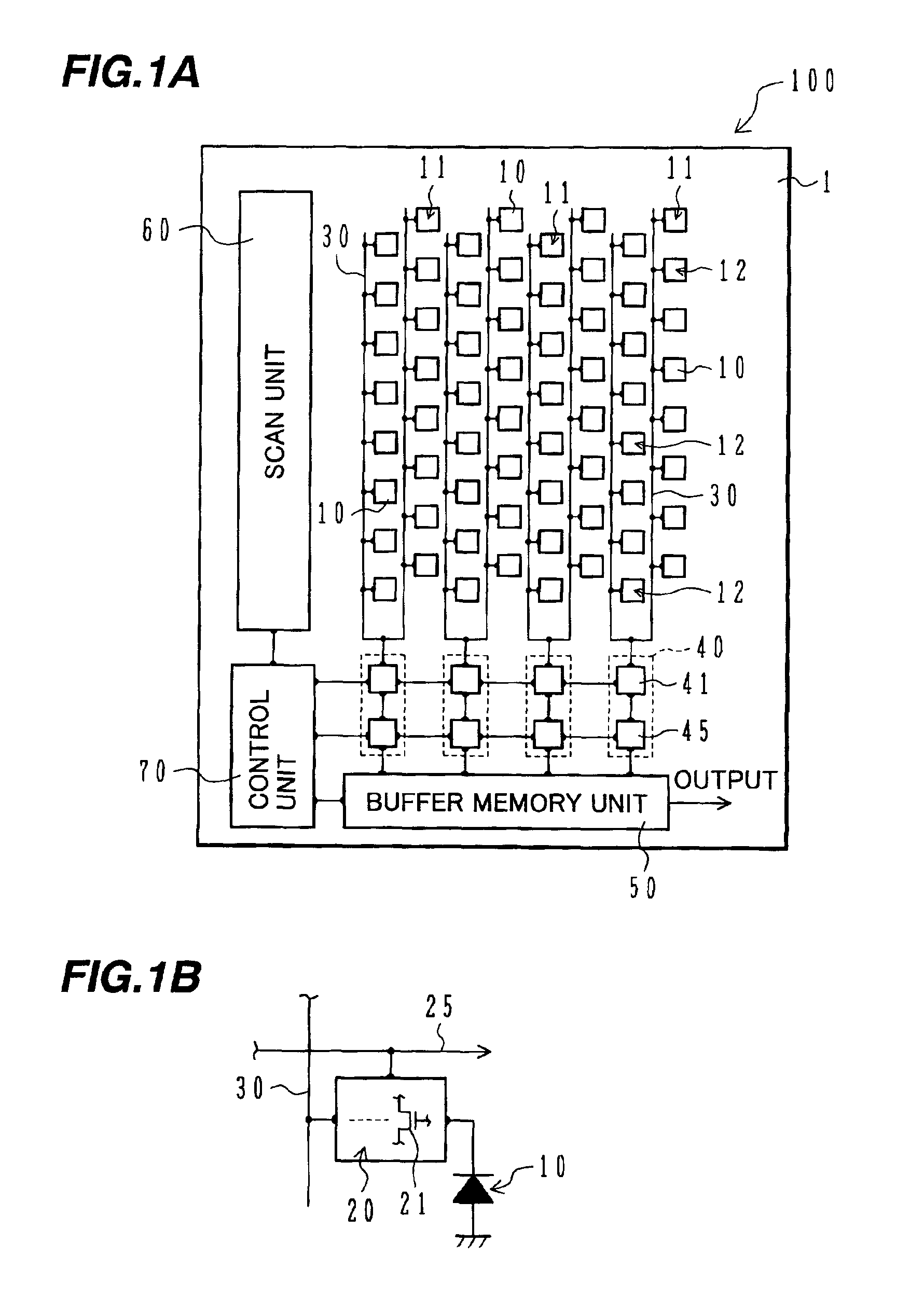
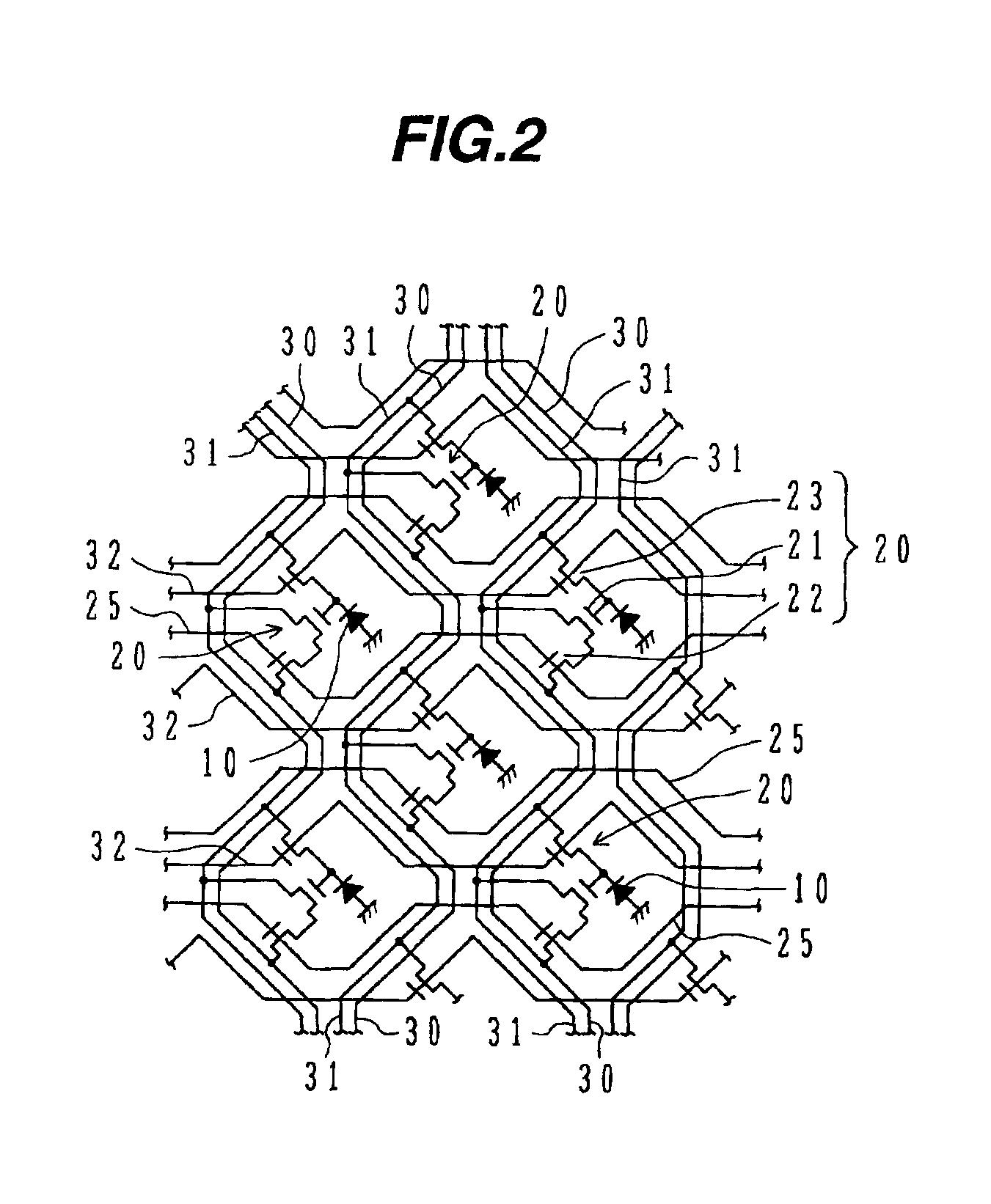
Battery power delivery module
ActiveUS20080136367A1Semiconductor/solid-state device detailsEmergency protective circuit arrangementsCharge and dischargeFuel gauge
A system and method for digital management and control of power conversion from battery cells. The system utilizes a power management and conversion module that uses a CPU to maintain a high power conversion efficiency over a wide range of loads and to manage charge and discharge operation of the battery cells. The power management and conversion module includes the CPU, a current sense unit, a charge / discharge unit, a DC-to-DC conversion unit, a battery protection unit, a fuel gauge and an internal DC regulation unit. Through intelligent power conversion and charge / discharge operations, a given battery type is given the ability to emulate other battery types by conversion of the output voltage of the battery and adaptation of the charging scheme to suit the battery.
Owner:SOLAREDGE TECH LTD
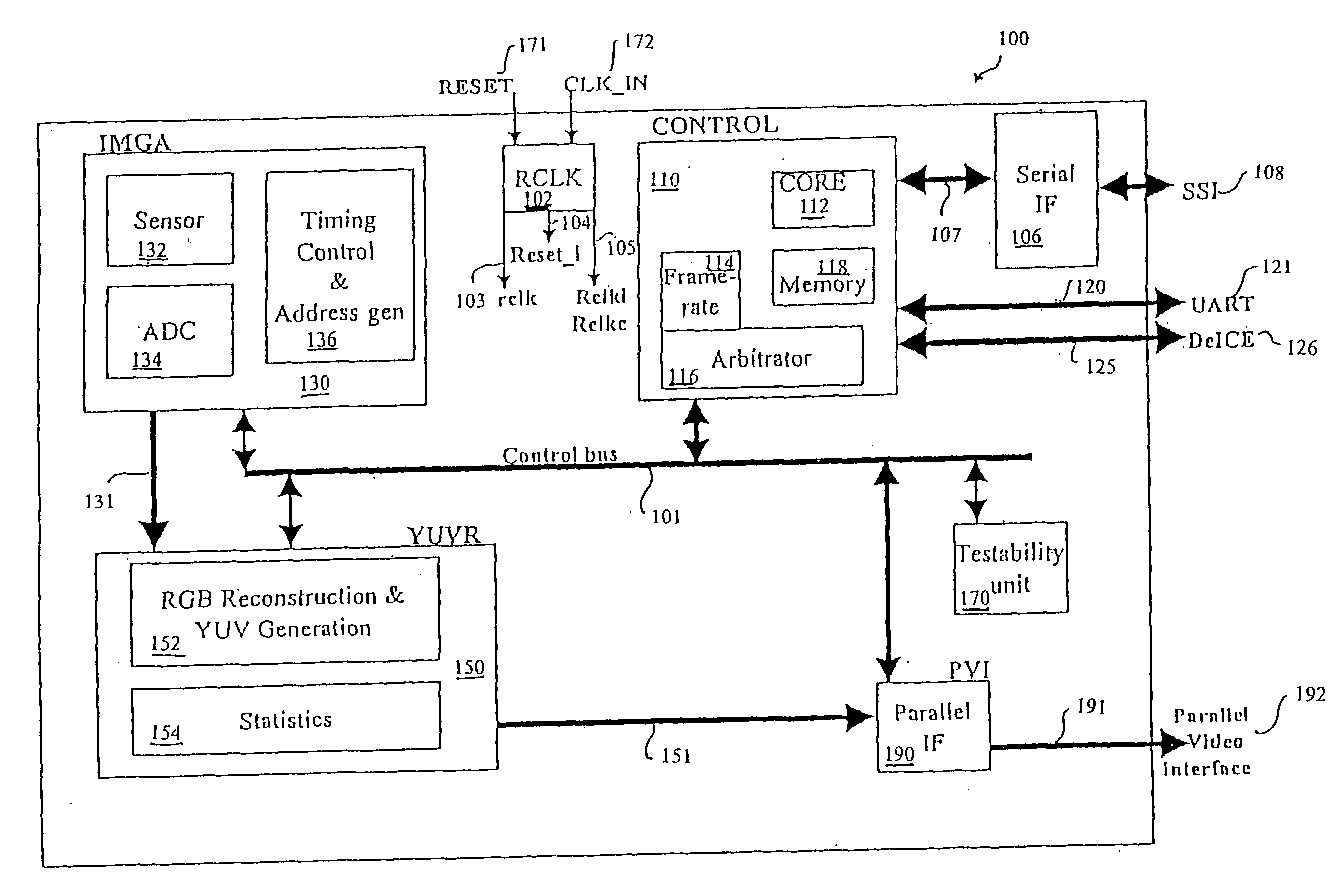
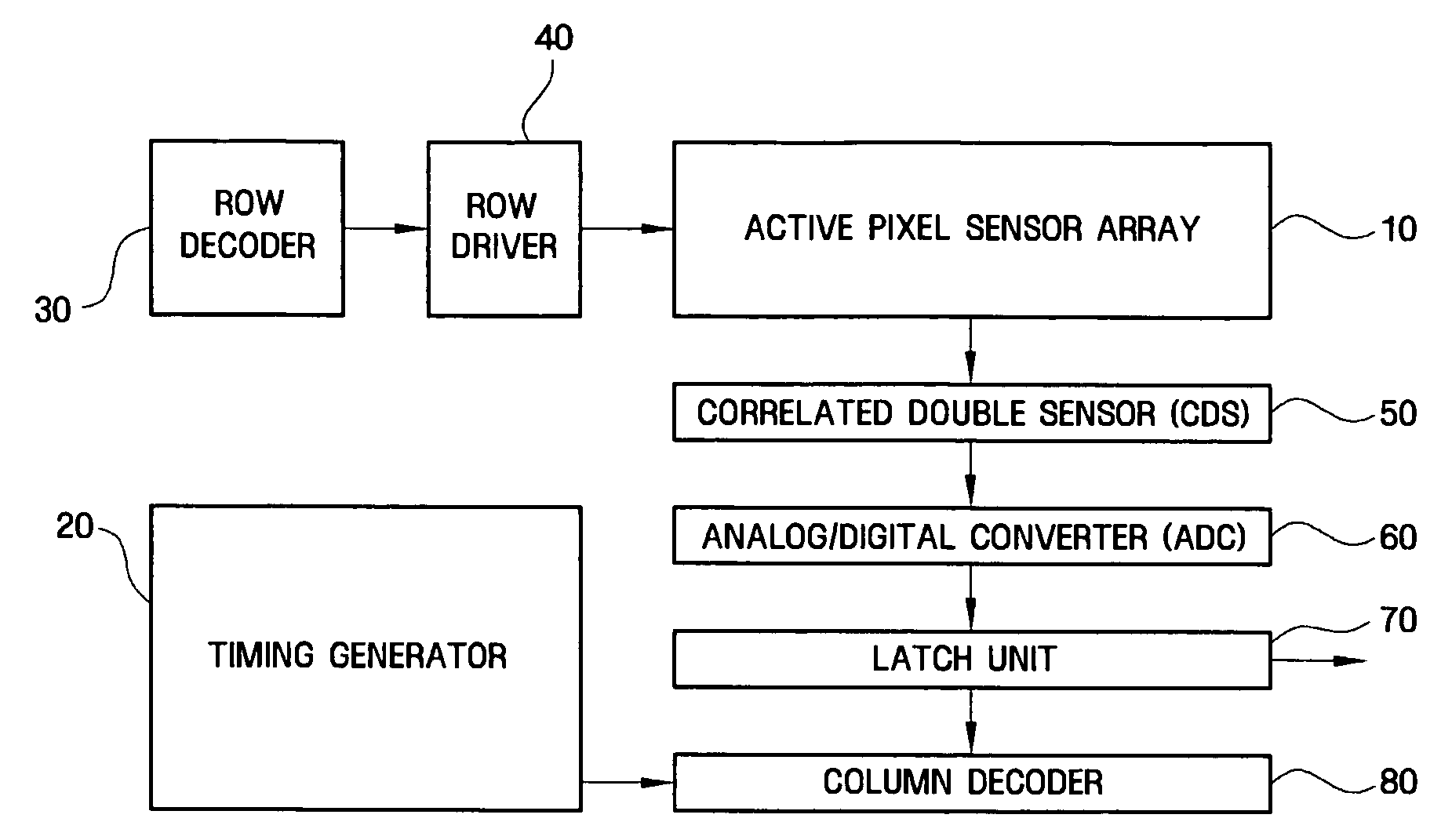
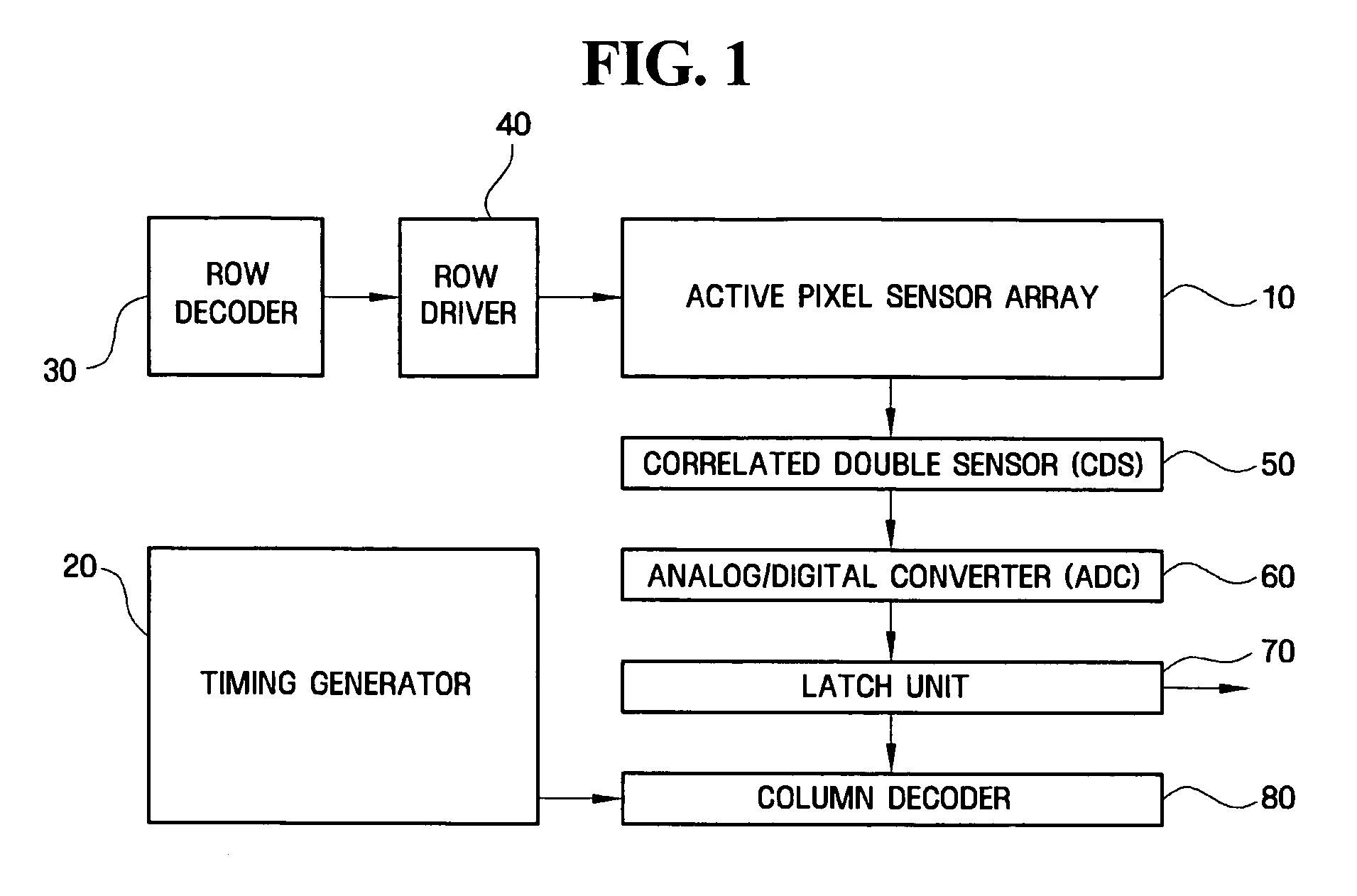
CMOS imager for cellular applications and methods of using such
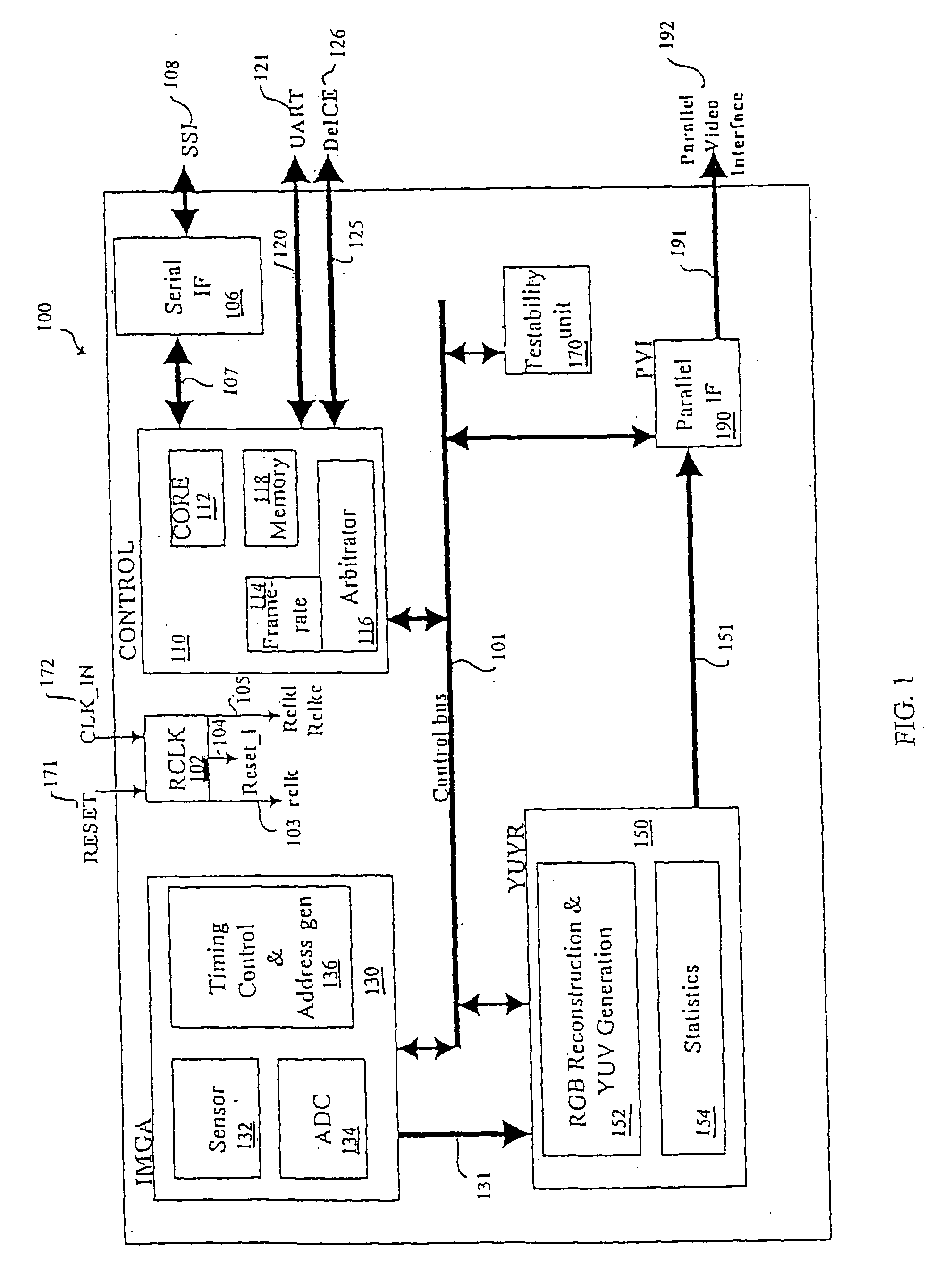
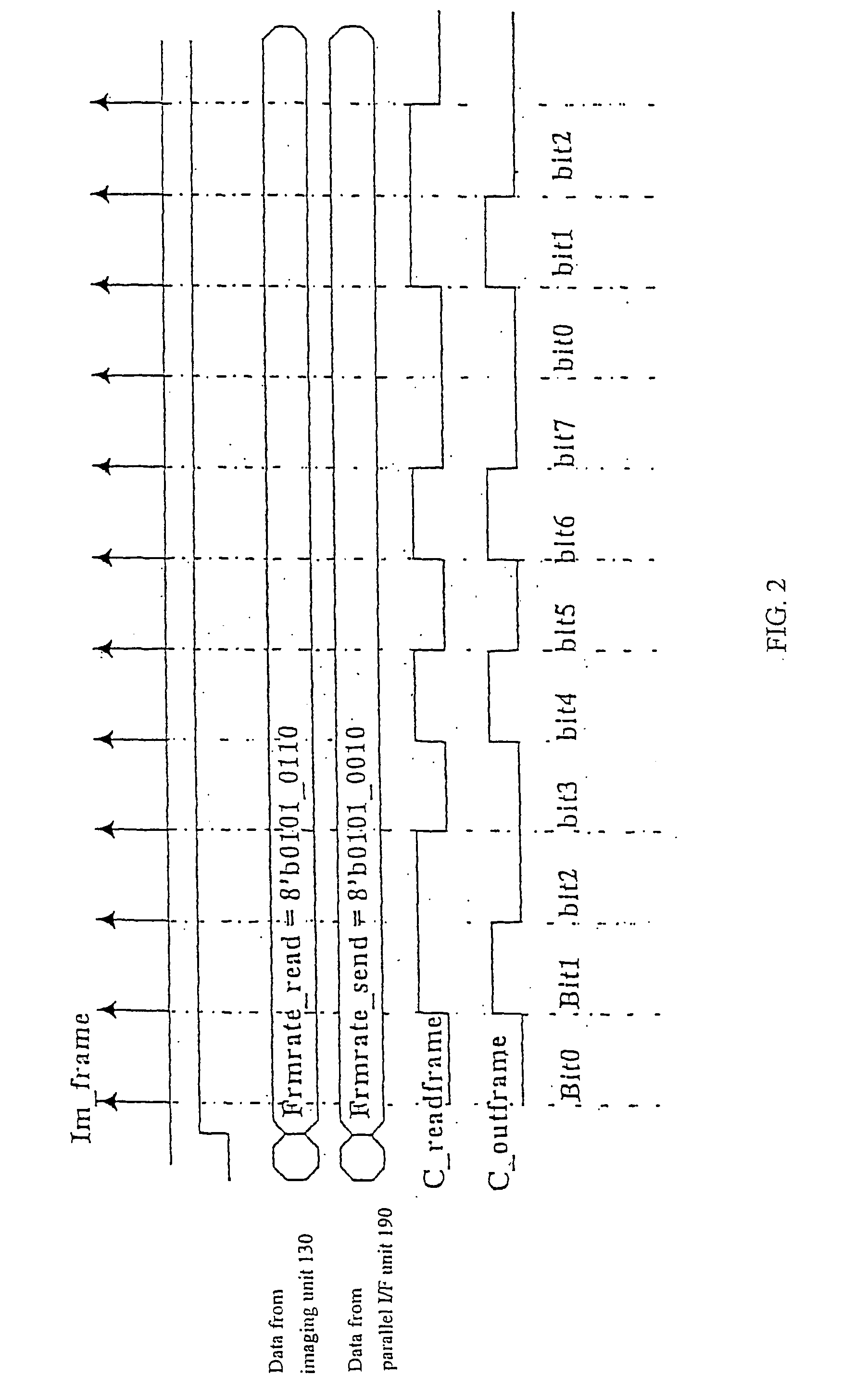
ActiveUS20050068436A1Reduce power consumptionMeet the noiseTelevision system detailsColor signal processing circuitsCMOSTransformation unit
Systems, methods and devices related to detecting and transmitting images. Imaging system and devices, as well as methods of using such that are provided herein include flicker detection and / or correction; and / or built-in self test (170) associated with various analog circuitry in the imaging devices; and / or power reduction ability; and / or pixels with charge evacuation functionality; and / or parallel to serial conversion (190) unit and associated serial output interface (106); and / or other advanced functionality.
Owner:TRANSCHIP ISRAEL
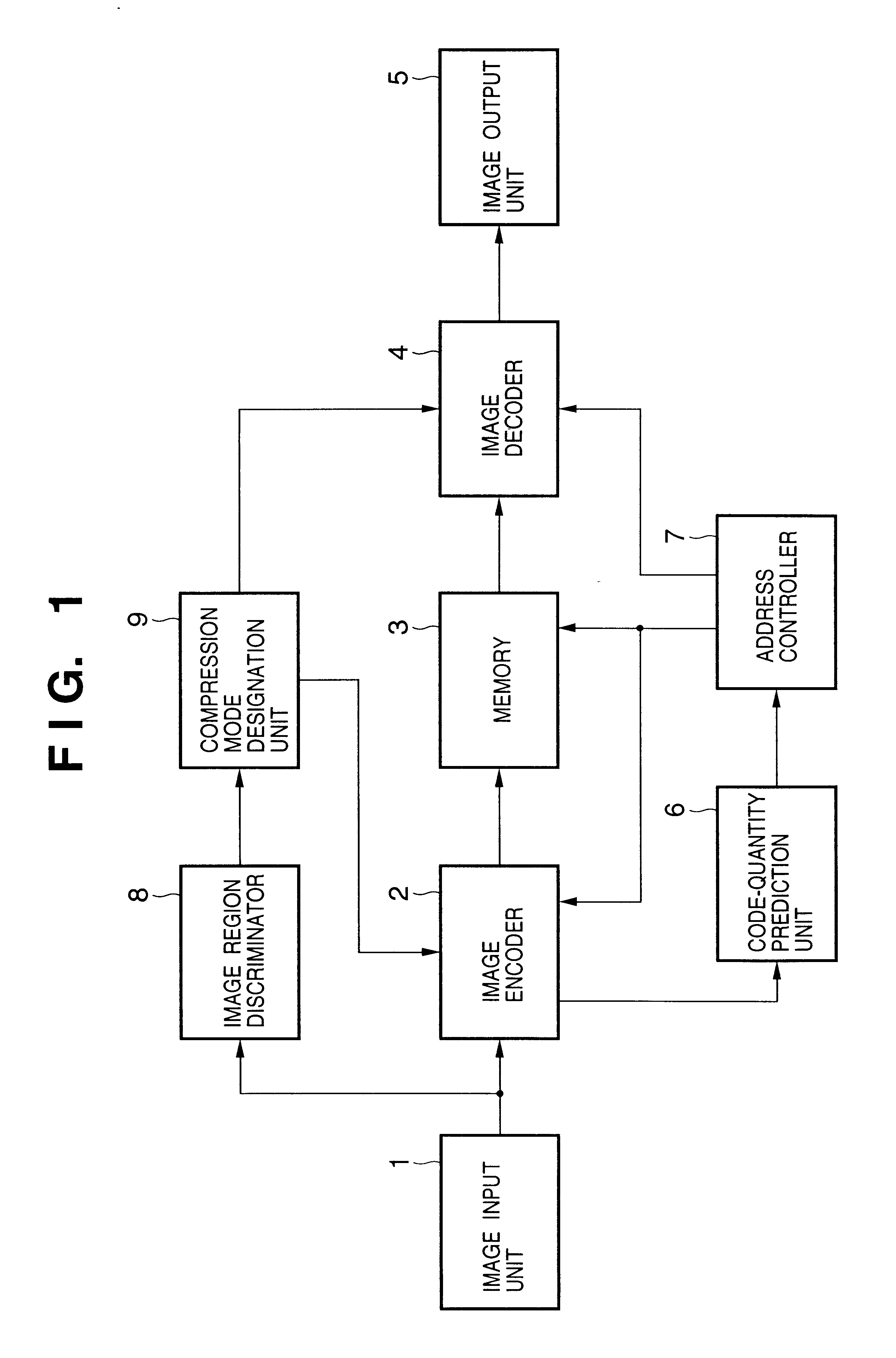
Image encoding method and apparatus
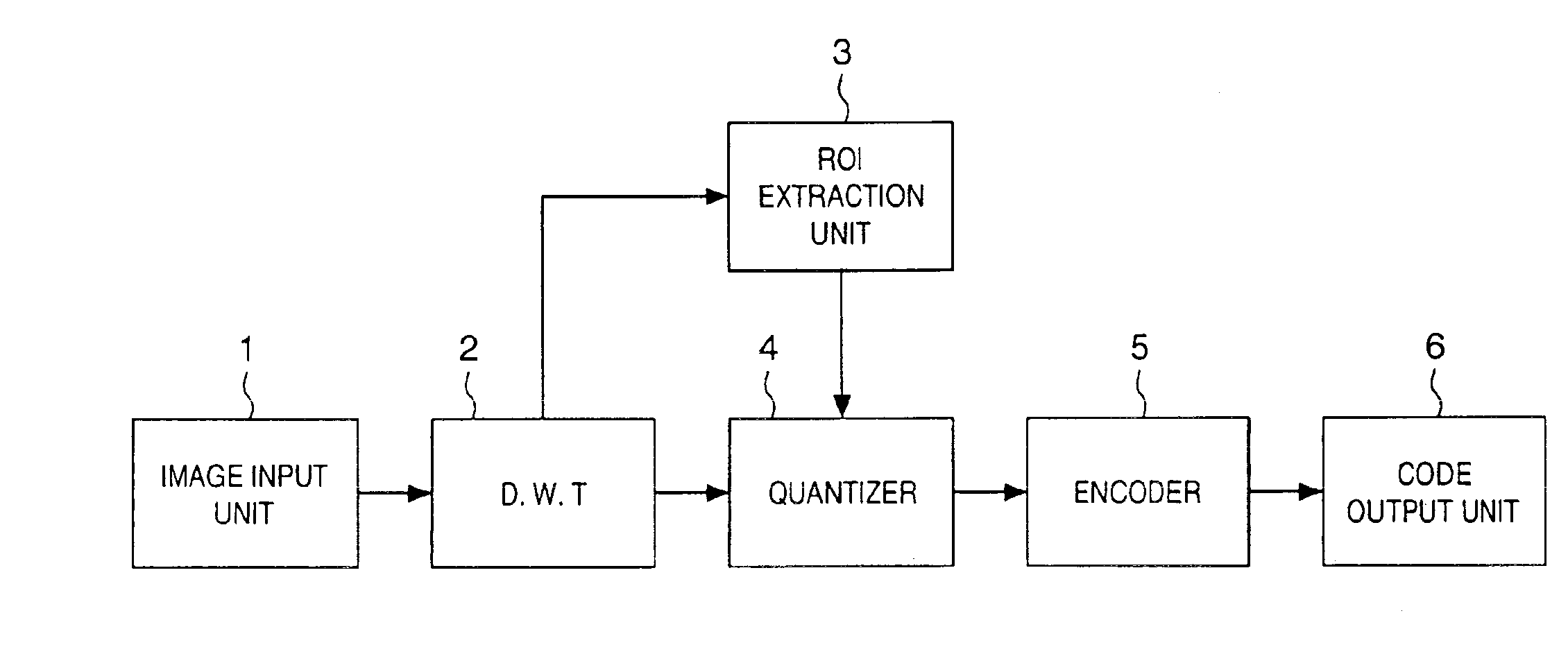
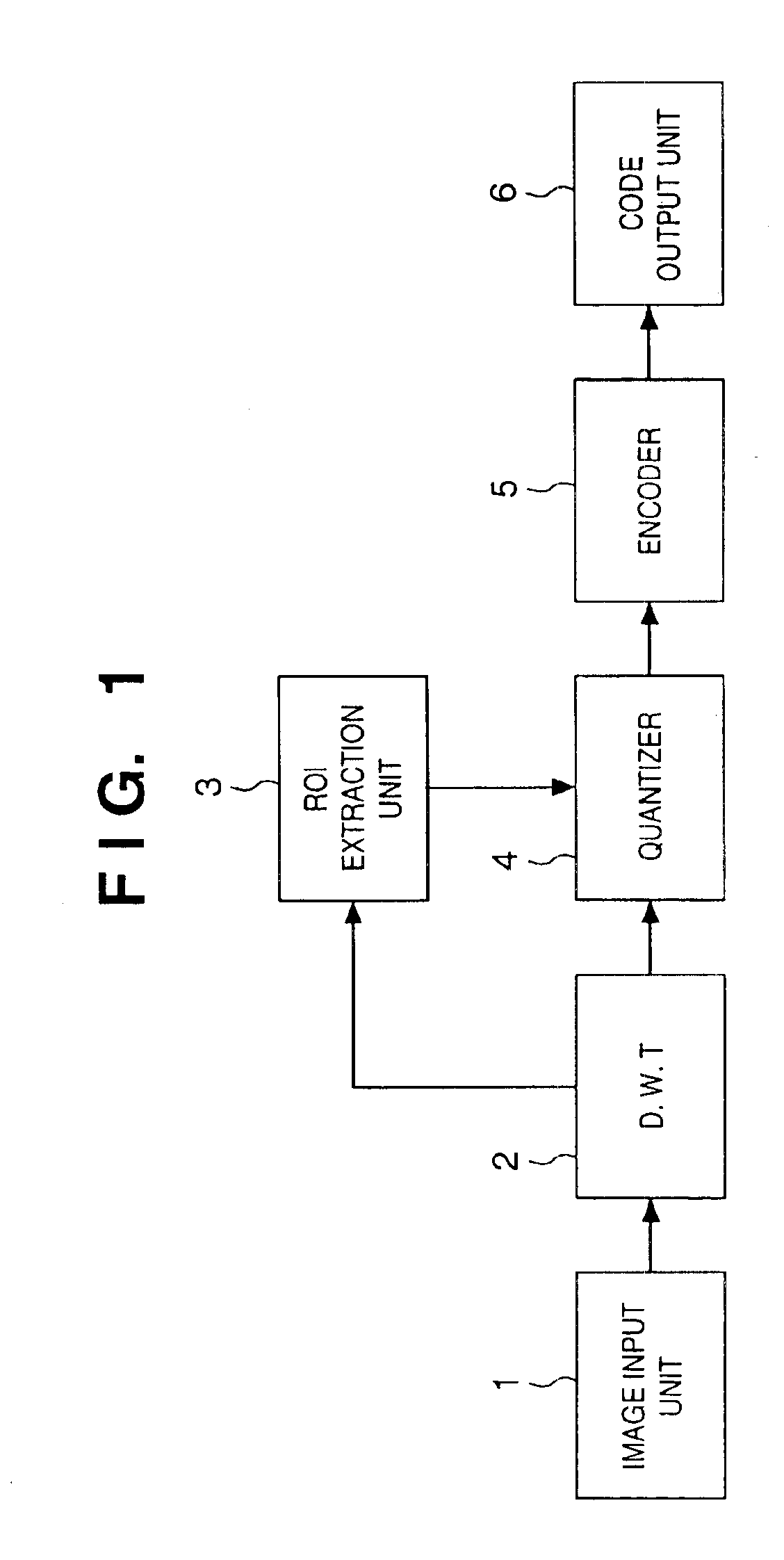
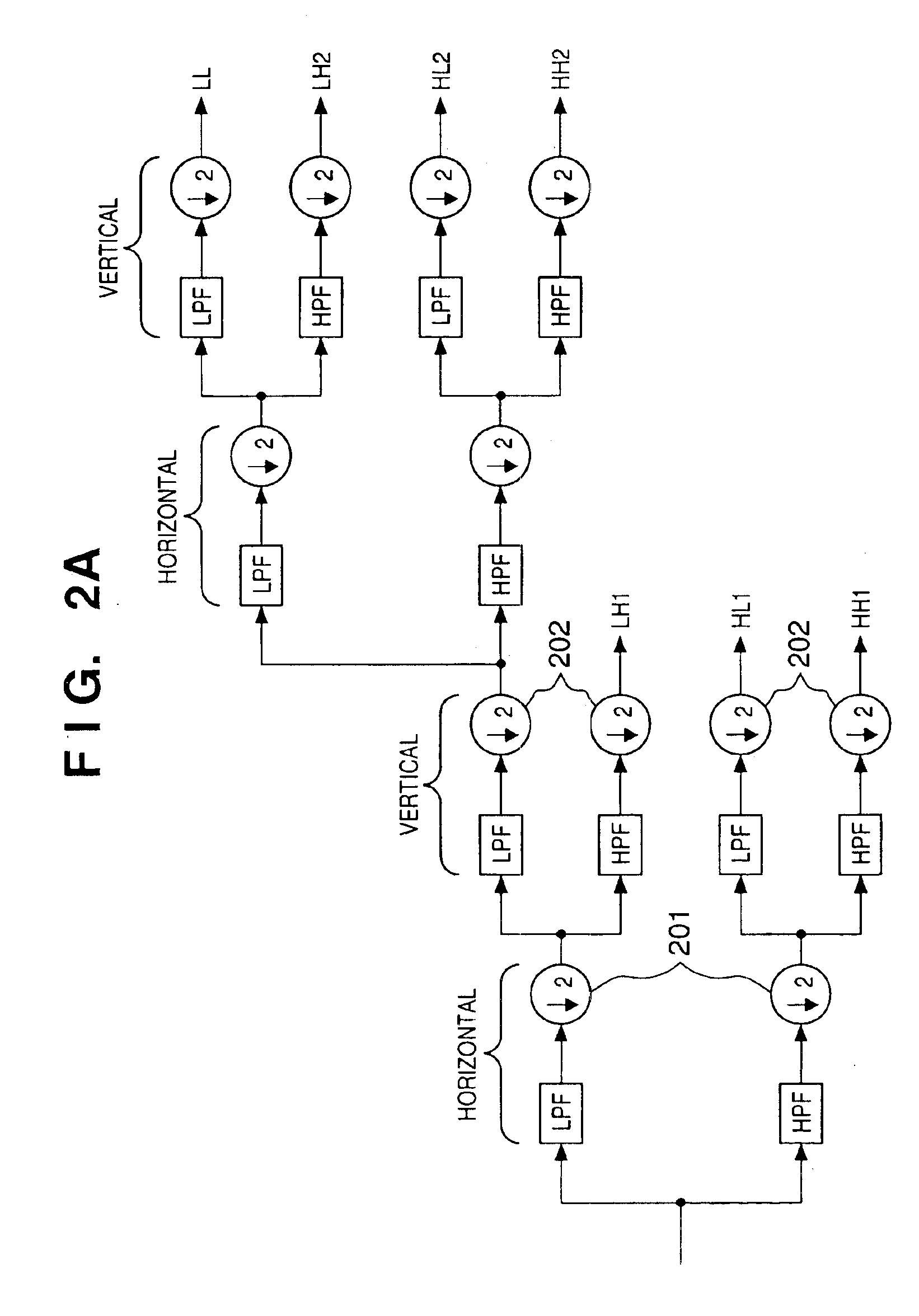
InactiveUS6937773B1Without placing a burden upon the userColor television with pulse code modulationColor television with bandwidth reductionMotion vectorTransformation unit
An image signal is input from an image input unit and is divided into different spatial frequency bands by applying a discrete wavelet transform thereto using a discrete wavelet transformation unit. On the basis of values of spatial frequency components, a region-of-interest extracts a region of interest by obtaining a distribution of motion vectors in the input image. A quantization unit applies quantization processing to the extracted region of interest and different quantization processing to other regions, and an encoder encodes the quantized image signal. Alternatively, motion of an image contained in the input image may be detected and the region of interest may be obtained based upon motion of this image.
Owner:CANON KK
3D input apparatus and method thereof
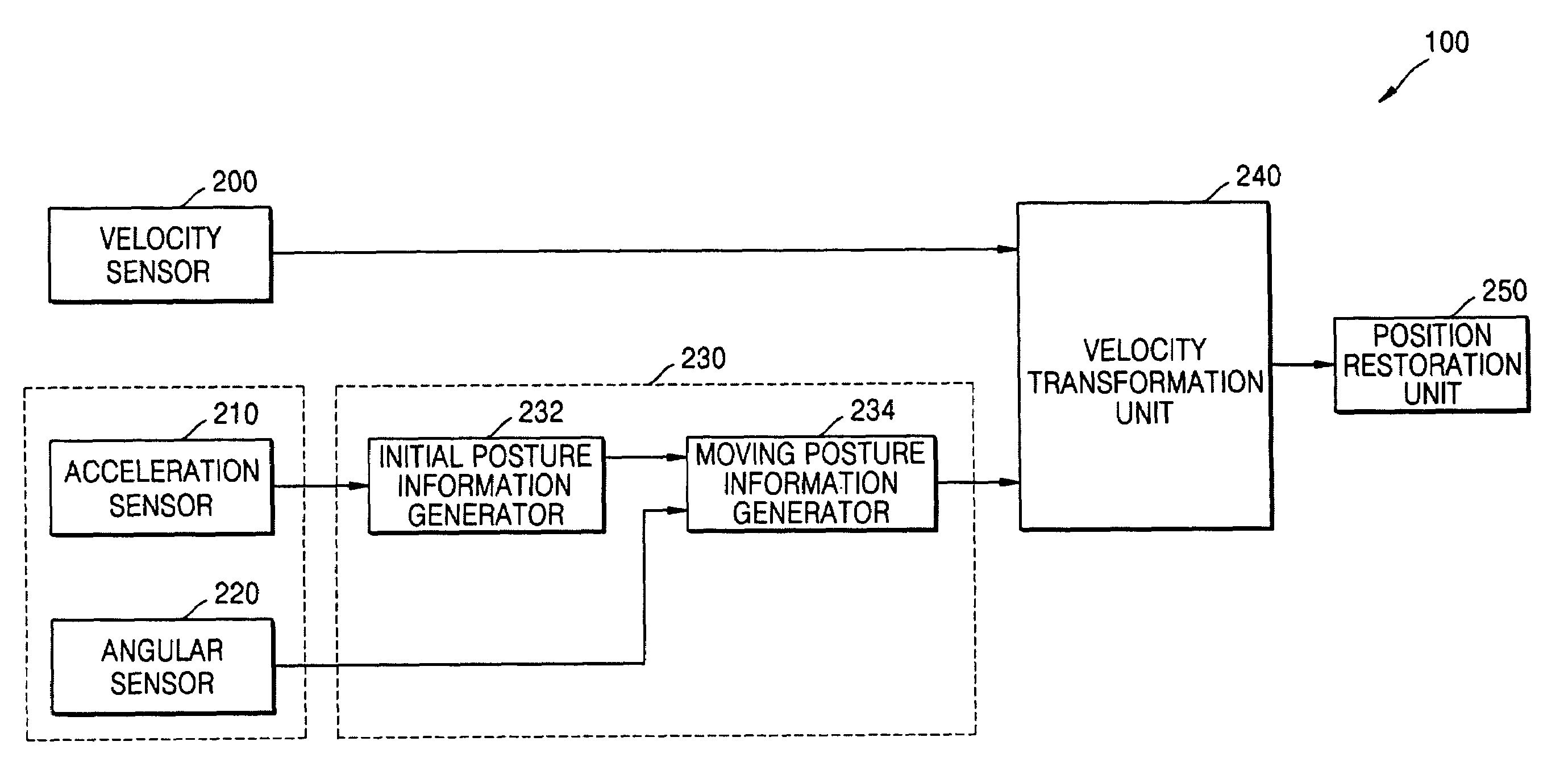
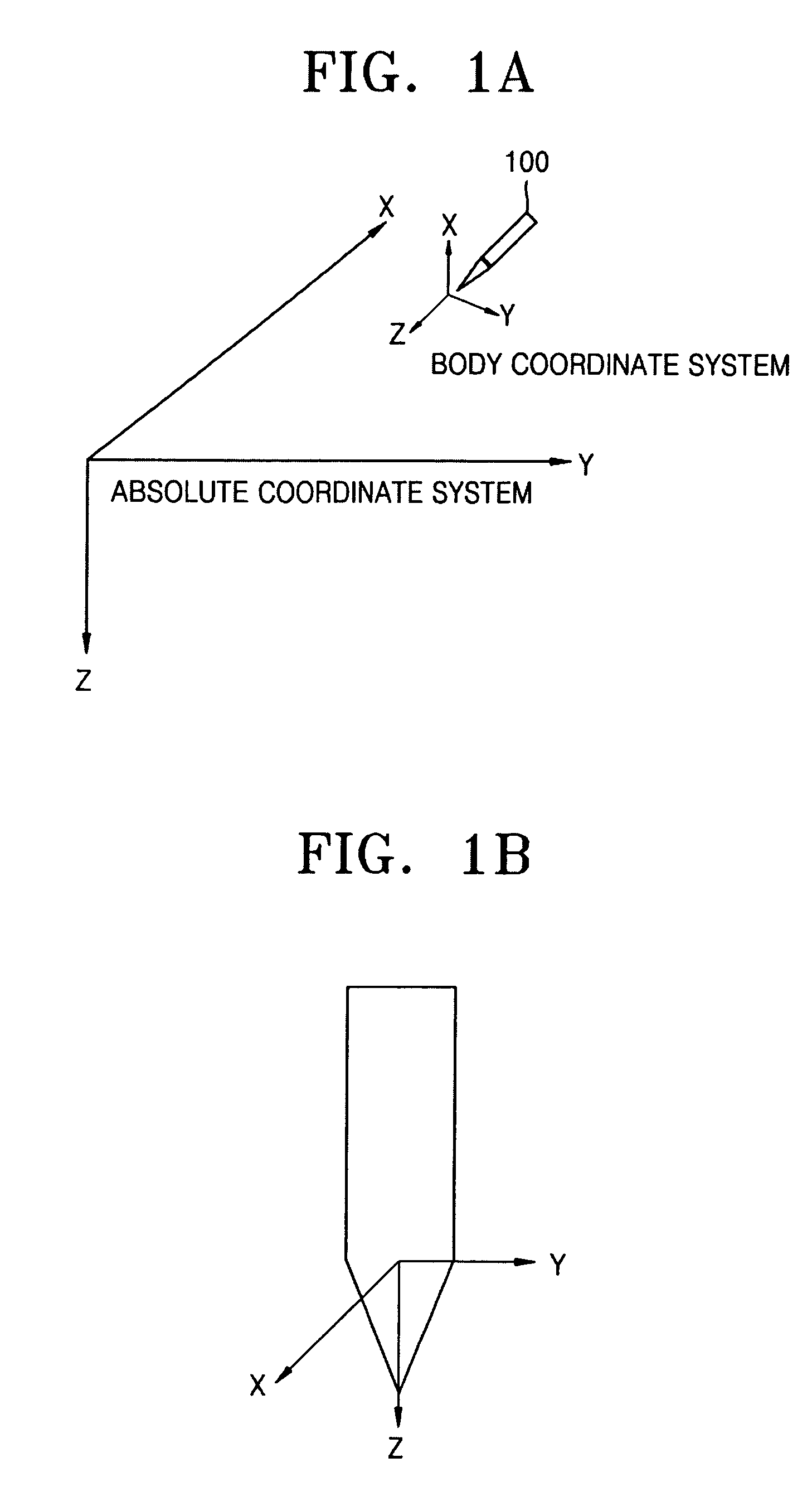
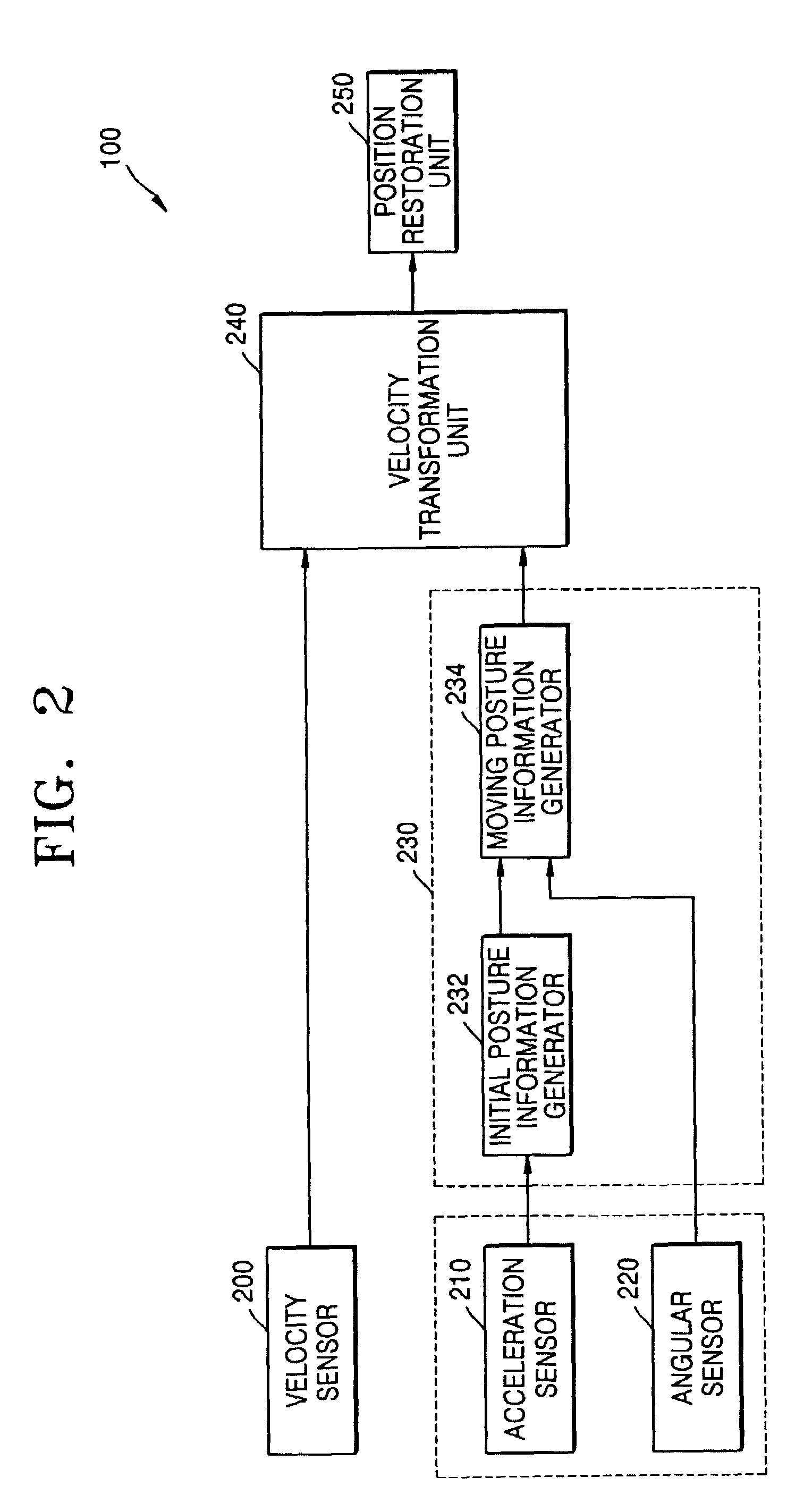
ActiveUS6993451B2Accurate detectionInput/output for user-computer interactionDigital computer detailsAngular velocityTransformation unit
Provided are a 3D input apparatus and method for precisely detecting a position of the 3D input apparatus. The 3D input apparatus includes a sensor package which measures a first velocity an acceleration, and an angular velocity of the 3D input apparatus in a relative body coordinate system; a posture information generating unit, which generates posture information of the 3D input apparatus using the measured acceleration and angular velocity; a velocity transformation unit, which transforms the measured first velocity into a second velocity in an absolute coordinate system using the posture information; and a position restoration unit, which determines a position of the 3D input apparatus by integrating the second velocity.
Owner:SAMSUNG ELECTRONICS CO LTD
Image generation apparatus and image generation method
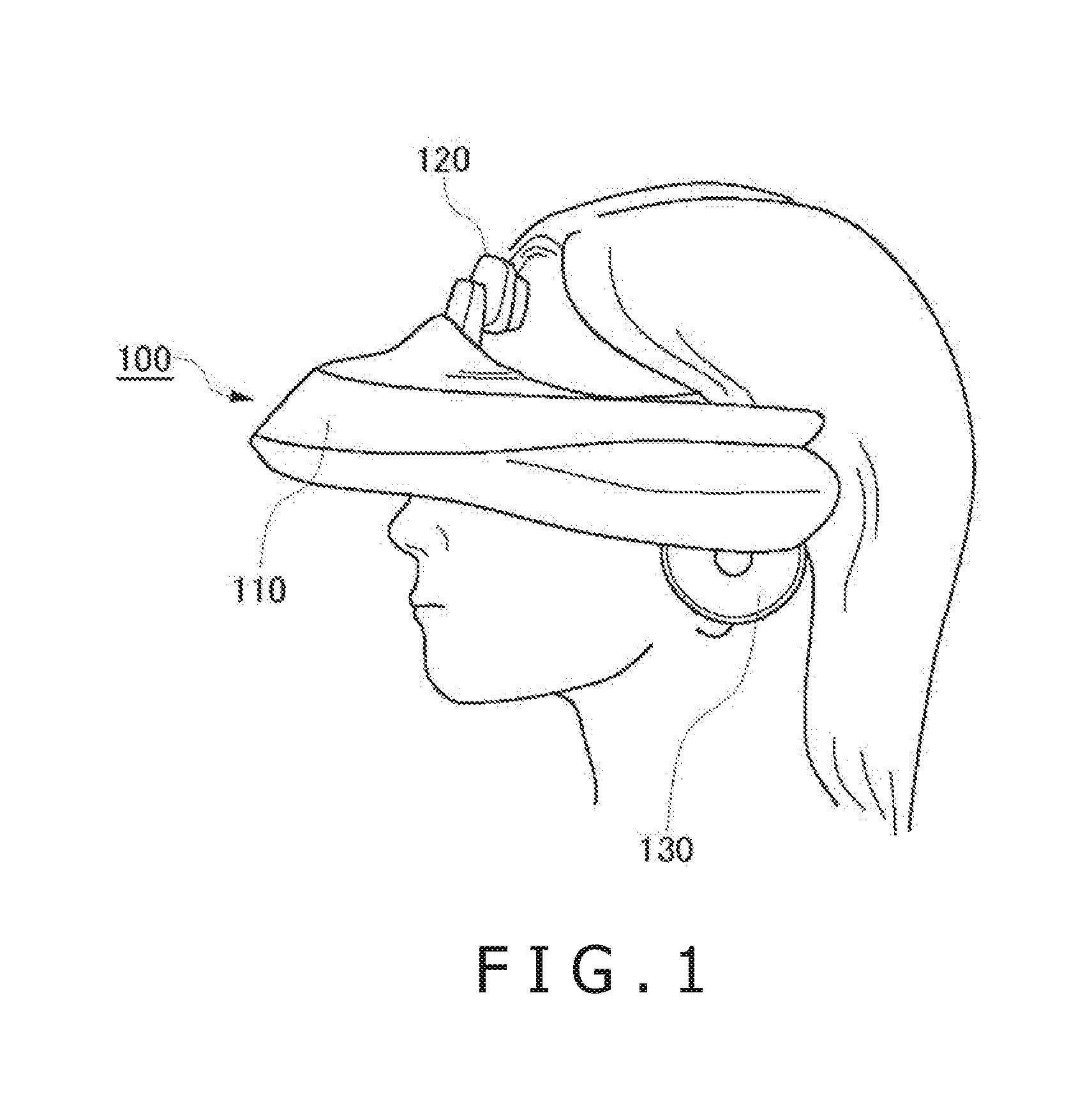
ActiveUS20160282619A1Degradation of image displayLower latencyVideo gamesInput/output processes for data processingImaging processingTransformation unit
A position and rotation information acquisition unit 730 acquires information relating to a position and a rotation of the head of a user who wears a head-mounted display unit 100. A coordinate transformation unit 740 and a panorama image processing unit 750 generate an image to be displayed on the head-mounted display unit using the information relating to the position and the rotation acquired at a certain point of time by the position and rotation information acquisition unit 730. A correction processing unit 780 corrects the generated image using updated information relating to the position and the rotation at a different point of time.
Owner:SONY COMPUTER ENTERTAINMENT INC +1
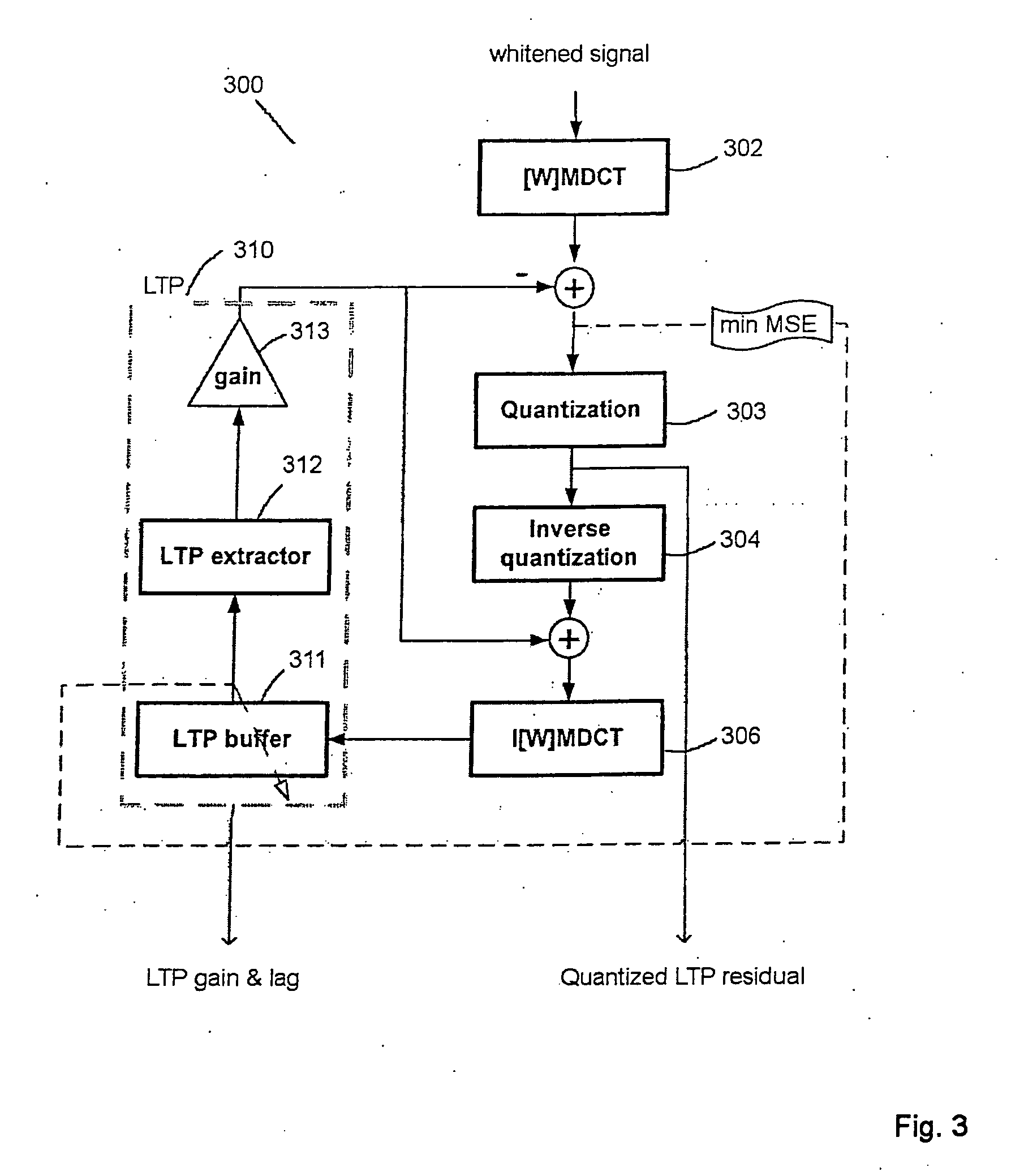
Audio encoder and decoder
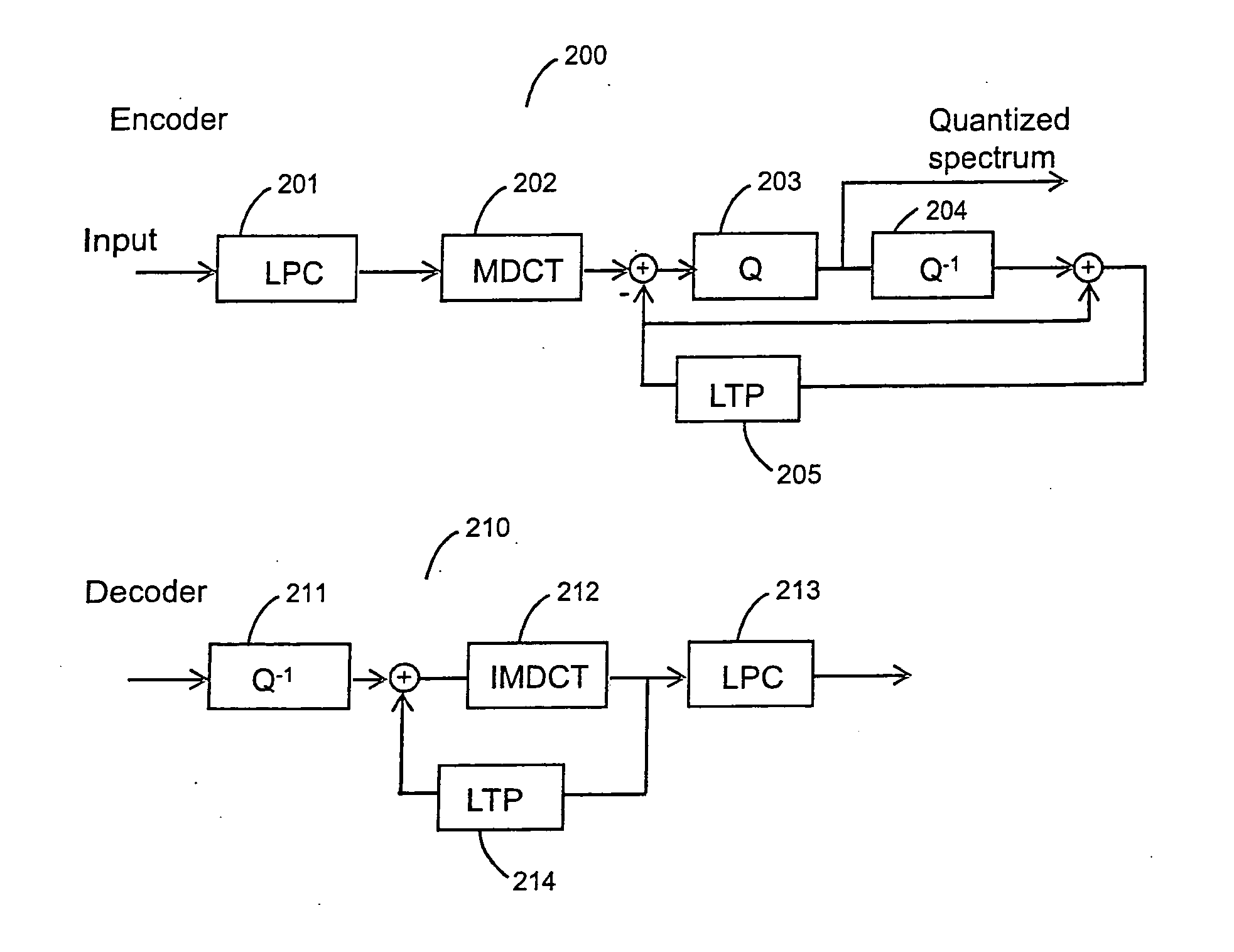
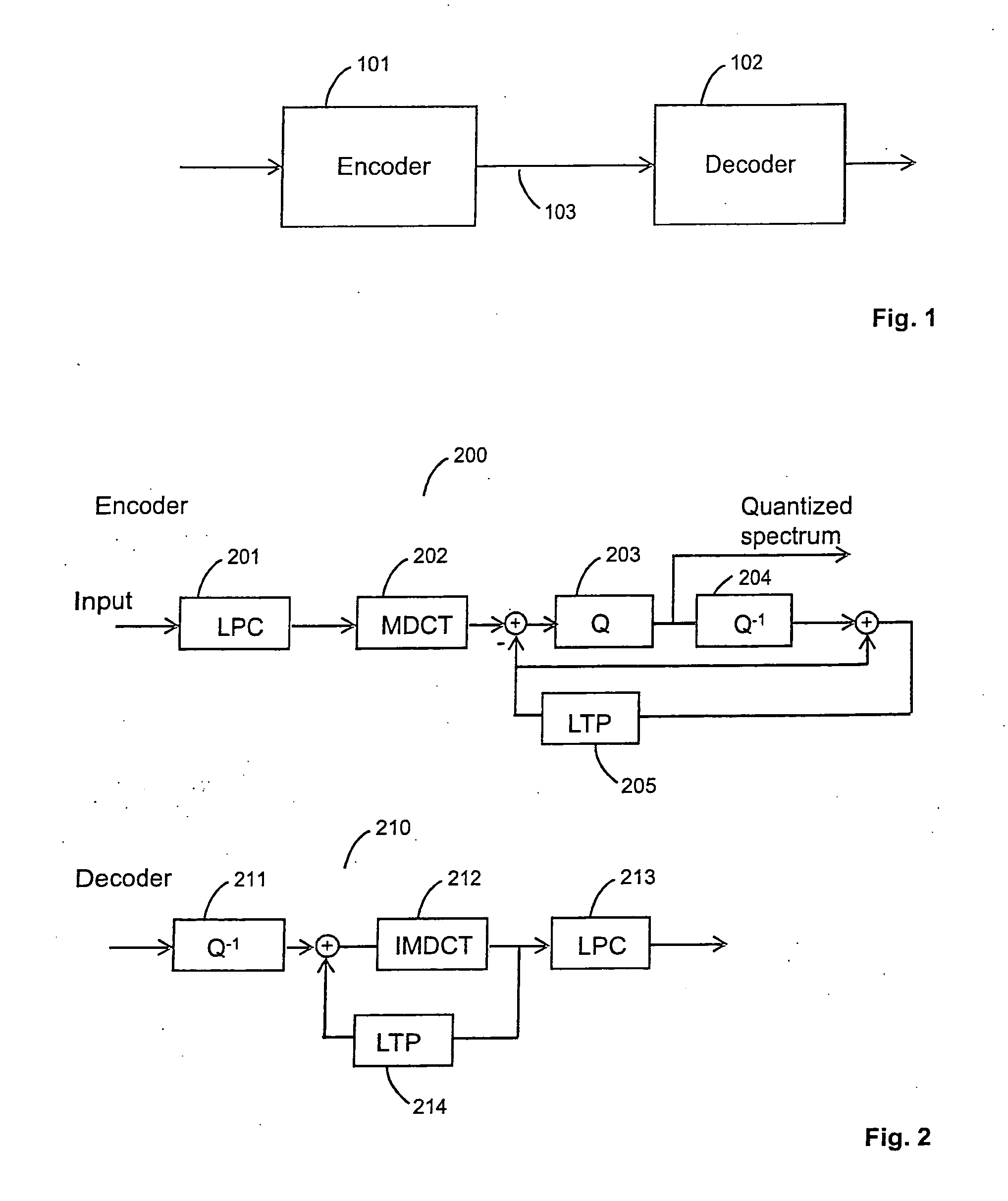
The present invention teaches a new audio coding system that can code both general audio and speech signals well at low bit rates. A proposed audio coding system comprises a linear prediction unit for filtering an input signal based on an adaptive filter; a transformation unit for transforming a frame of the filtered input signal into a transform domain; a quantization unit for quantizing a transform domain signal; a long term prediction unit for determining an estimation of the frame of the filtered input signal based on a reconstruction of a previous segment of the filtered input signal; and a transform domain signal combination unit for combining, in the transform domain, the long term prediction estimation and the transformed input signal to generate the transform domain signal.
Owner:DOLBY INT AB
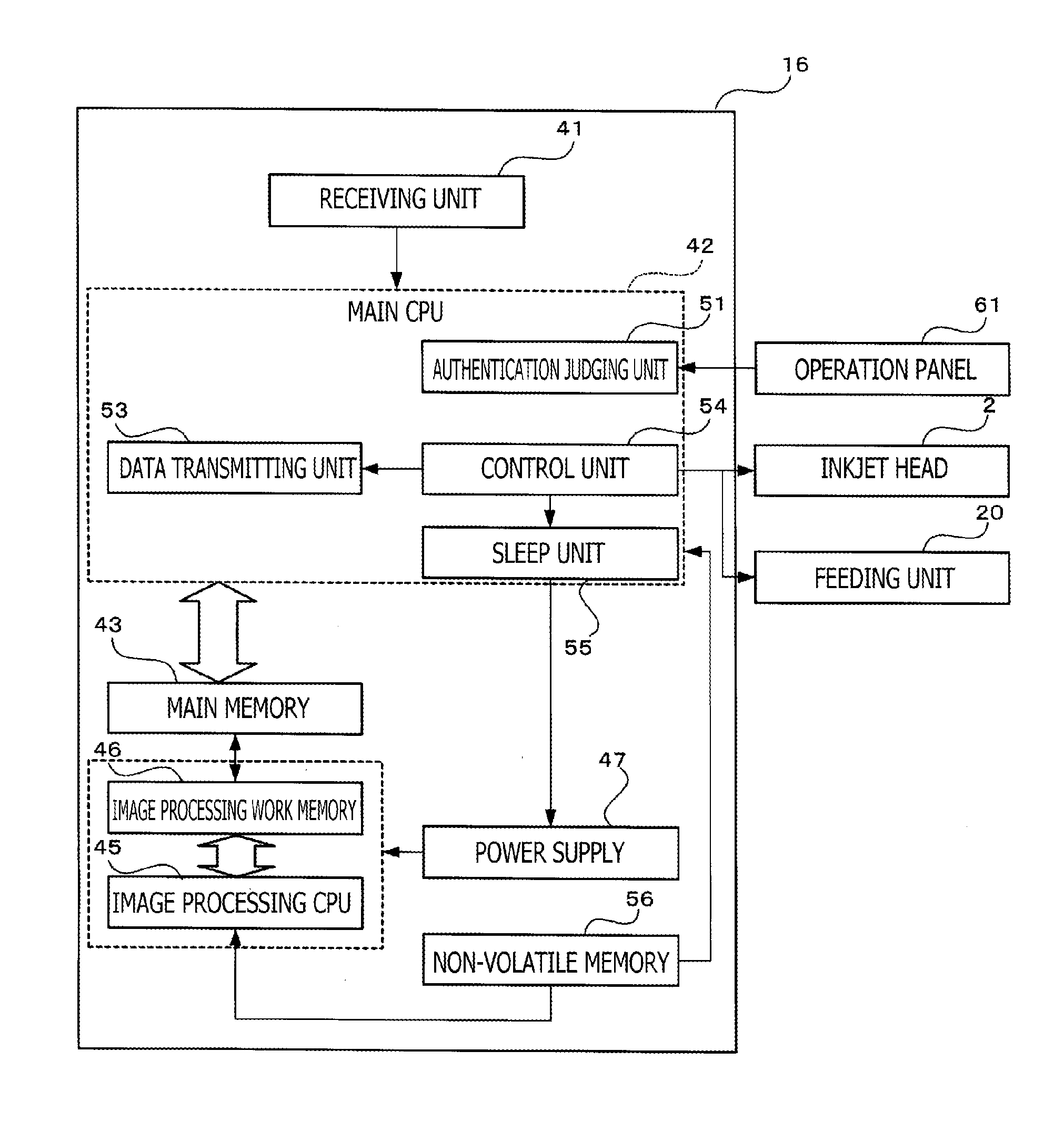
Image recording device and computer accessible storage storing program therefor
ActiveUS20120162693A1Save powerImprove performanceVisual presentation using printersComputer hardwareImage recording
An image recording device is provided with a first memory which is a volatile memory, a second memory, an input unit through which authentication information is input, an authentication judging unit. The recording unit is controlled to print an image on the printing sheet based on the drive data, which is converted from the image data stored in the first memory or the second memory and is stored in the first memory or the second memory. The drive data or the image data is stored in each of the first memory and the second memory is transmitted therebetween. The image recording device further includes a restricting unit capable of restricting power supply to the converting unit and the first memory in a sleep mode.
Owner:BROTHER KOGYO KK
Small form-factor device implementing protocol conversion
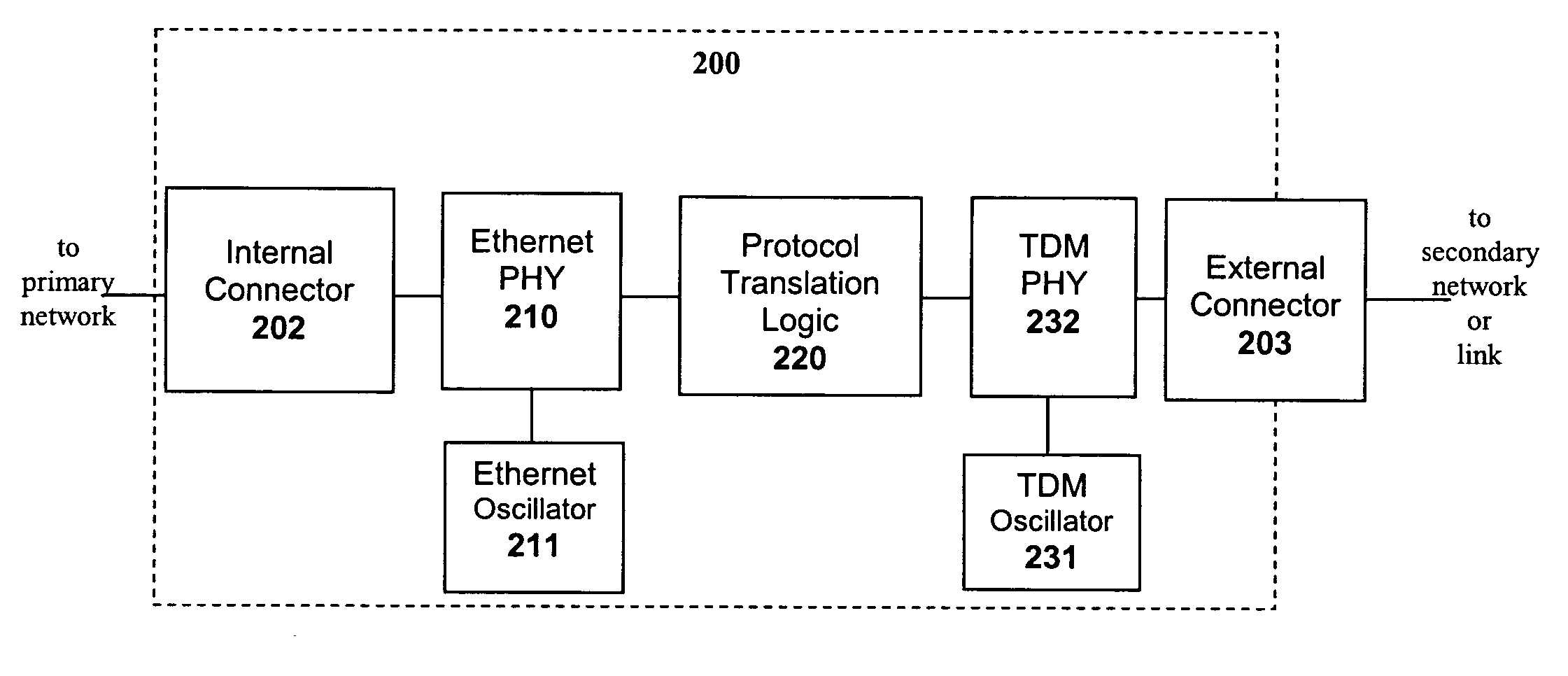
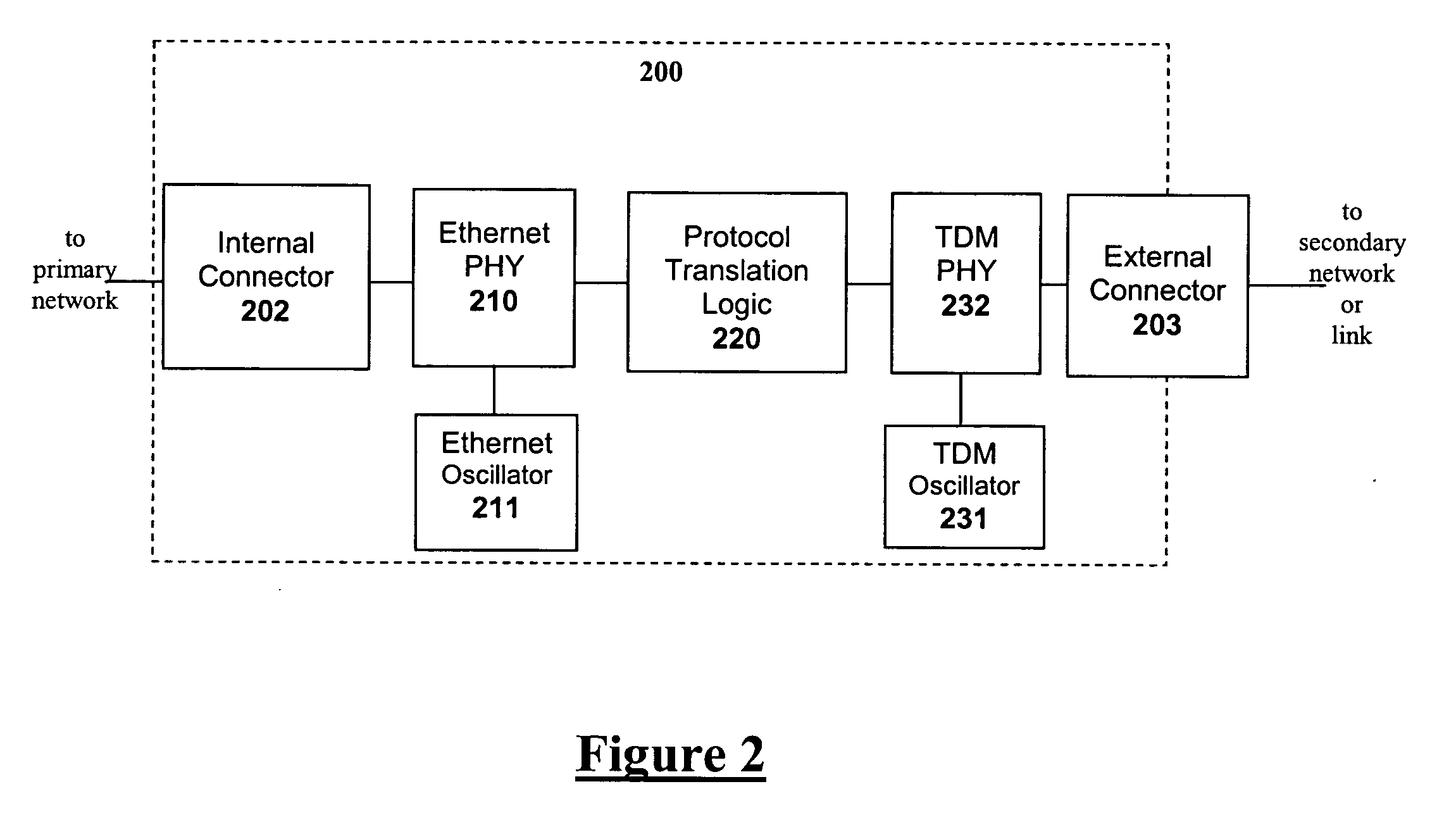
InactiveUS20060209886A1Network connectorsTime-division multiplexGigabit interface converterSmall form factor
A small form-factor transceiver module performs protocol translation, in addition to the conventional electrical and / or optical transmission media conversion. Such protocol conversion may enable transport of traffic from limited-range primary networks over long-range secondary networks, such as extension of Ethernet networks over low-rate TDM links. Additionally, such protocol conversion may enable interworking between different networks of differing technologies, such as transport of ATM traffic over Ethernet networks. The transceiver module may be a Small Form Factor transceiver (SFF), Small Form Factor pluggable module (SFP), Gigabit Interface Converter (GBIC) or any similar small form-factor module consisting of a housing, internal electronic circuitry and optionally optical components, and associated electrical or optical connectors. The transceiver module performs protocol translation by means of an integral protocol translation unit that performs standards-based or proprietary conversion between network protocols.
Owner:RAD DATA COMMUNICATIONS
Information processing apparatus, its control method, and program
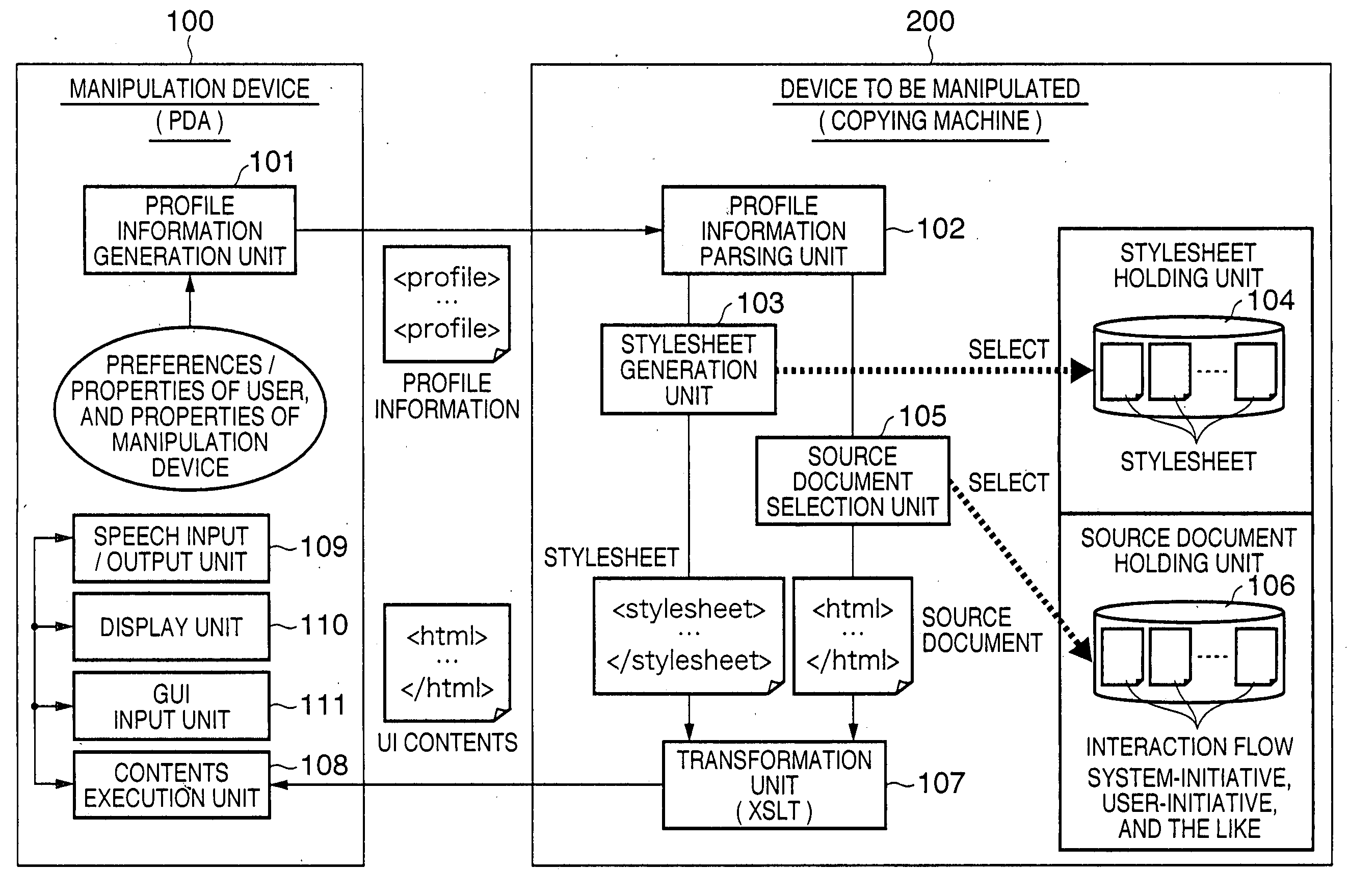
InactiveUS20050060046A1Improve usabilityComputer controlSoftware engineeringInformation processingTransformation unit
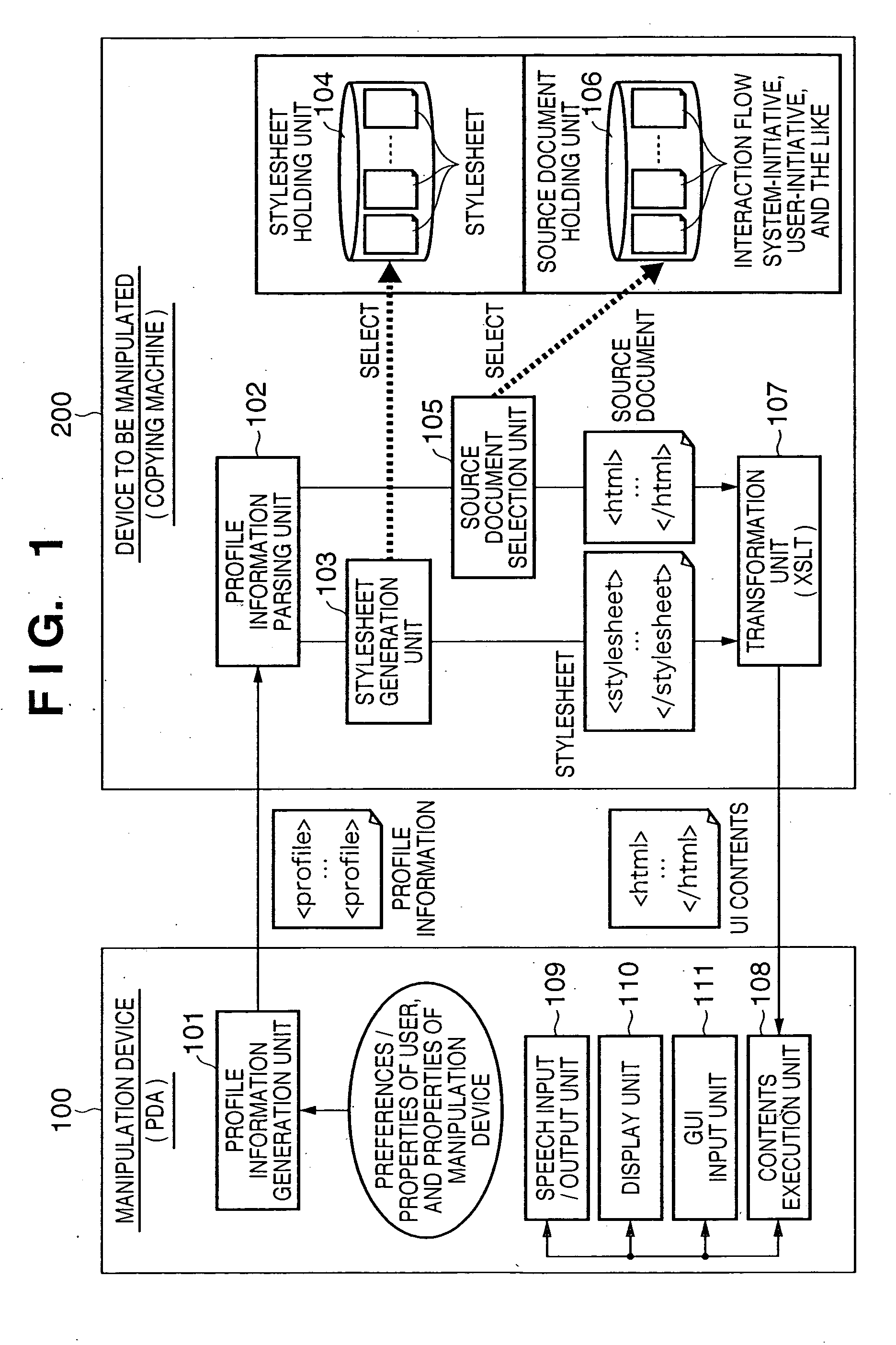
A profile information parsing unit receives profile information which includes property information indicating the properties of a manipulation device, and user information associated with a user who manipulates the manipulation device. A source document selection unit selects a source document from a source document holding unit in accordance with the received profile information. A stylesheet generation unit generates transformation description components from a stylesheet holding unit in accordance with the profile information, and generates a transformation description by integrating the selected transformation description components. A transformation unit transforms the selected source document using the generated transformation description, thus generating contents of a user interface that implements manipulations of the device to be manipulated by the manipulation device. The contents of the user interface are transmitted to the manipulation device.
Owner:CANON KK
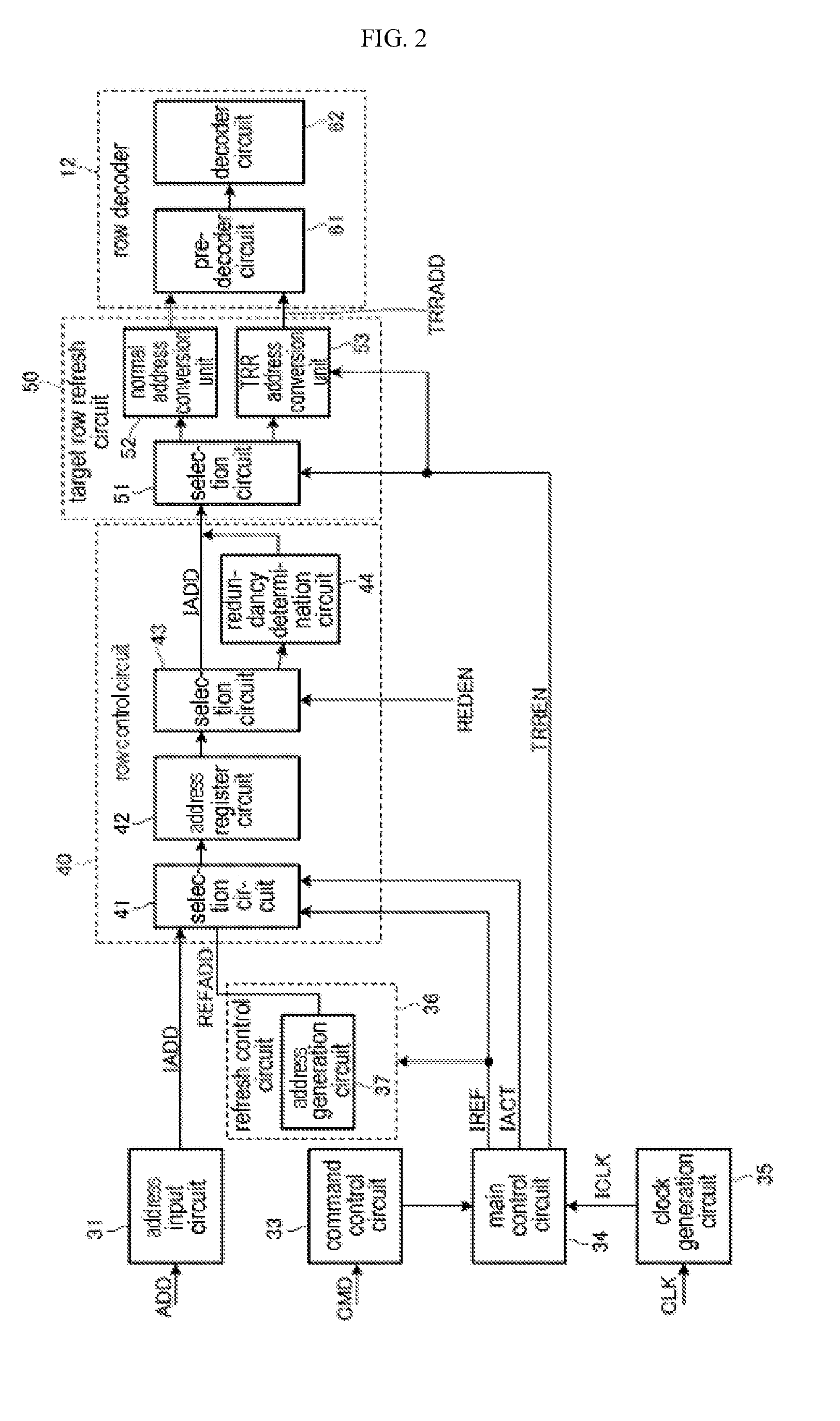
Semiconductor storage device and system provided with same
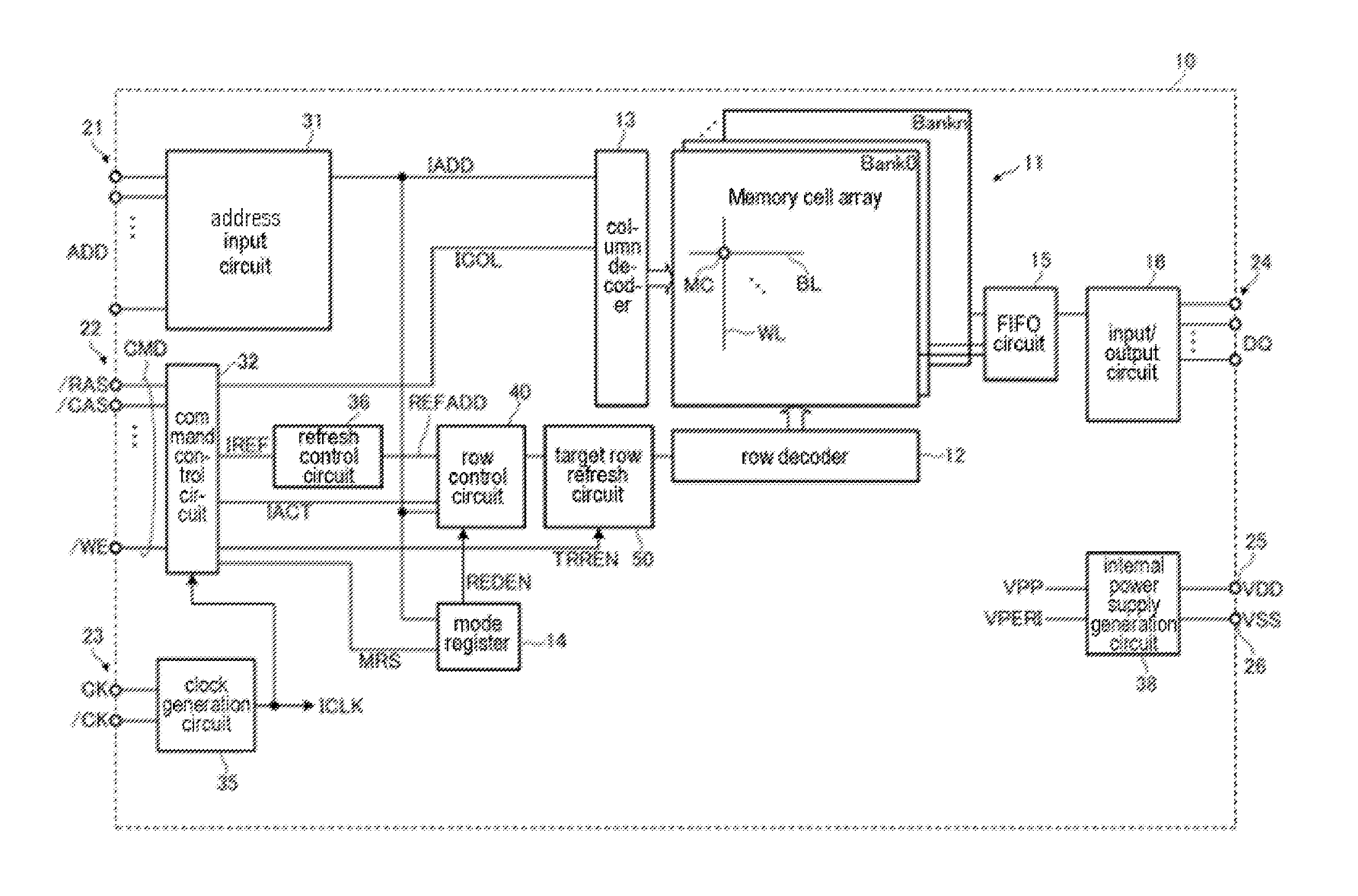
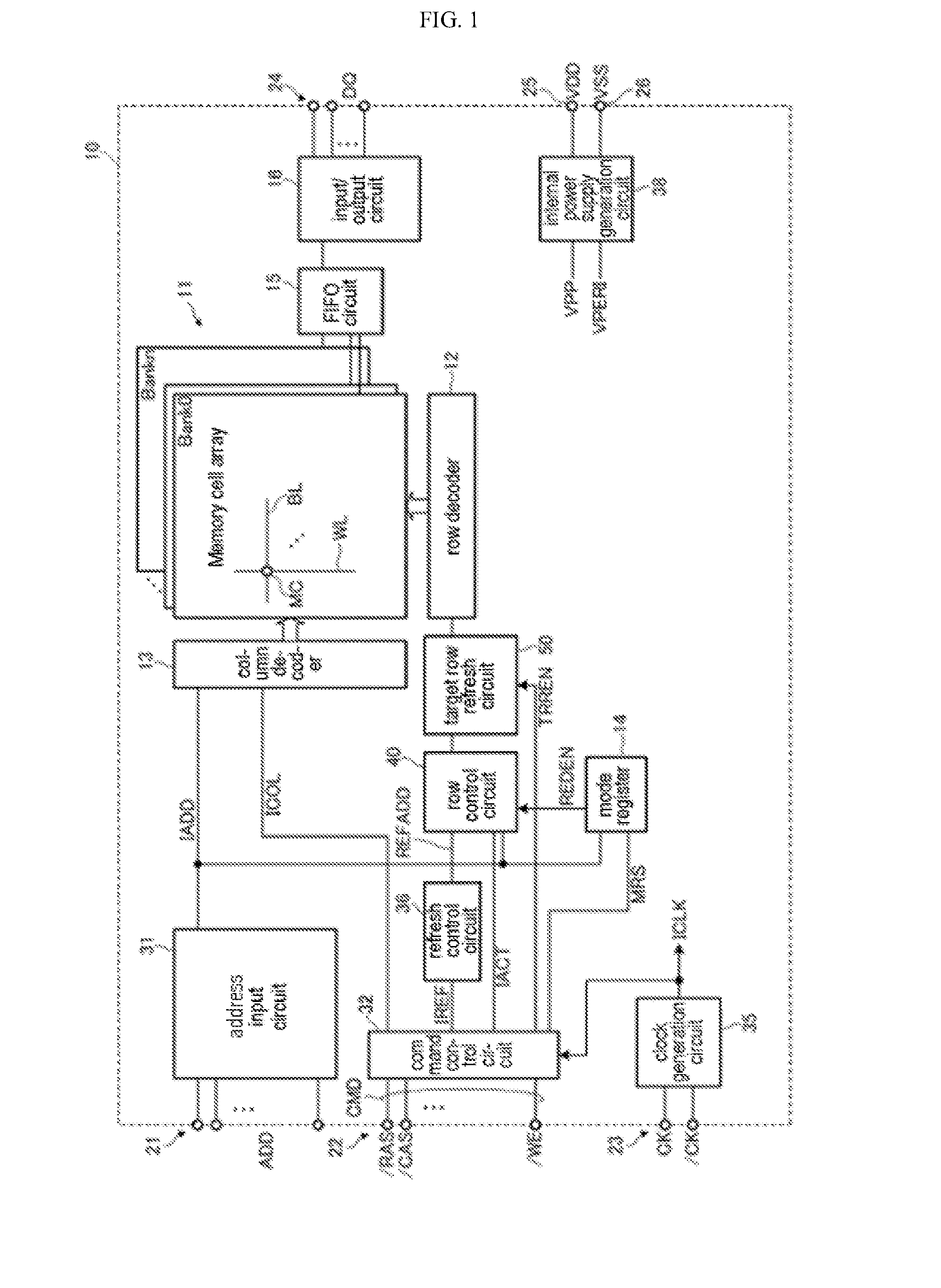
[Problem] To regenerate the charge of a memory cell having reduced information retention characteristics using a target row refresh operation. [Solution] A semiconductor storage device is provided with a memory cell array (11) comprising a plurality of word lines including word lines (WLI, WL2) that are adjacent to one another; and a TRR address conversion unit (53) that selects the word line (WL1) in response to the input of an address signal (IADD) indicating a first value while in a first operation mode and selects the word line (WL2) in response to the input of an address signal indicating a first value while in a target row refresh mode. Due to the fact that address conversion is performed on the semiconductor storage device side in the present invention, it is sufficient for a control device to output, for example, the address of a word line having a high access count to the semiconductor storage device during a target row refresh operation. As a result, control of the target row refresh operation on the control device side is facilitated.
Owner:LONGITUDE LICENSING LTD
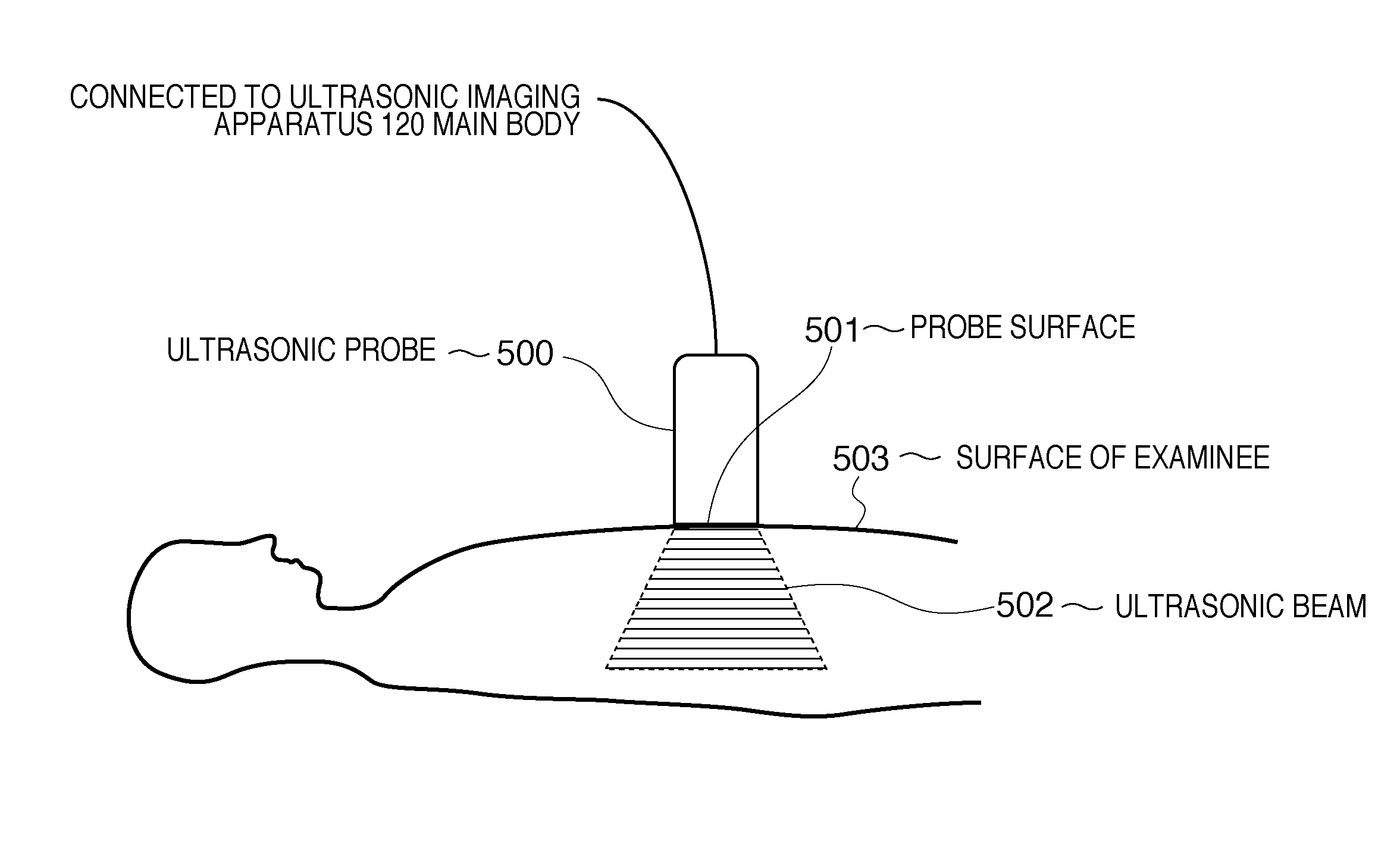
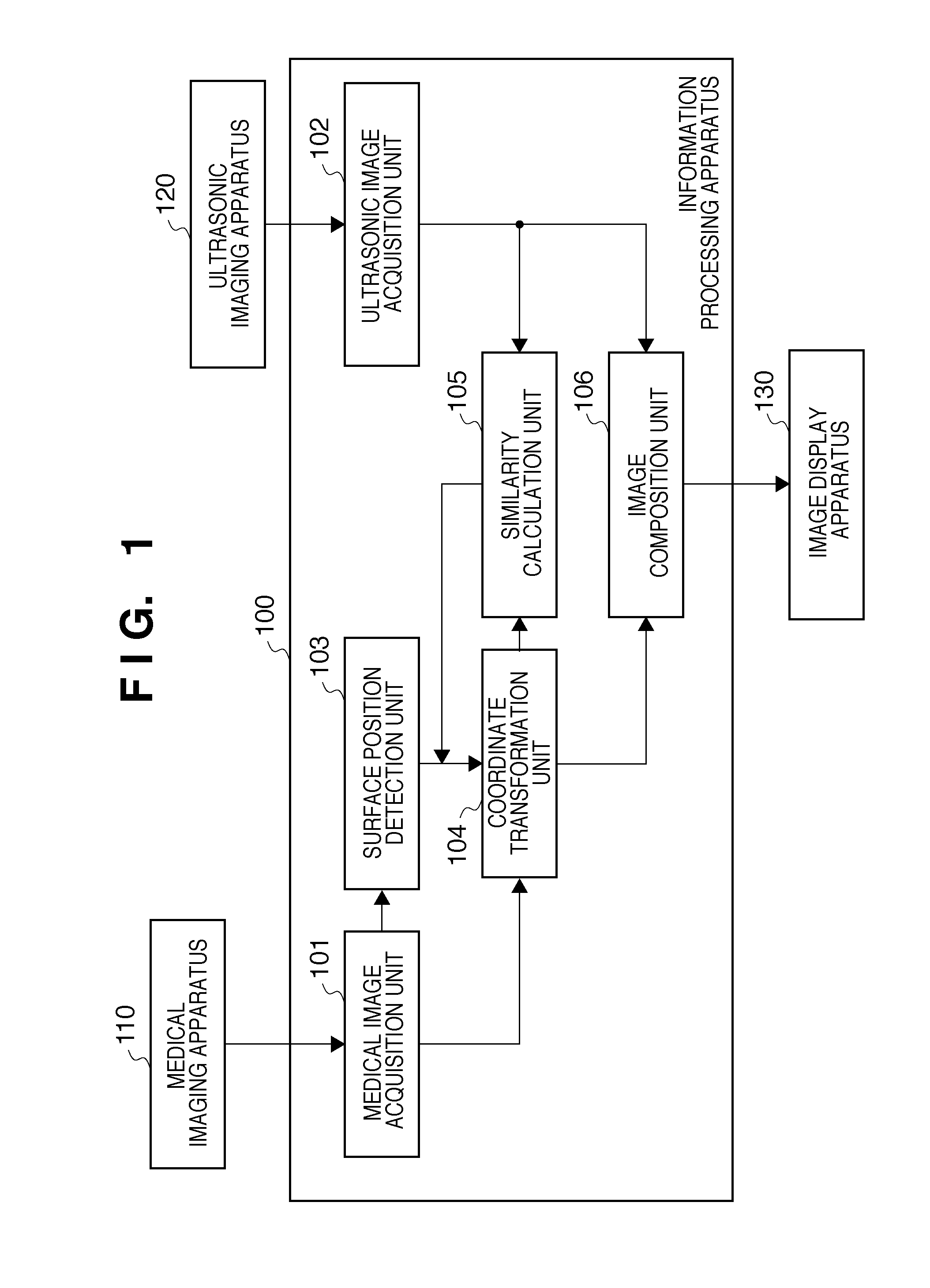
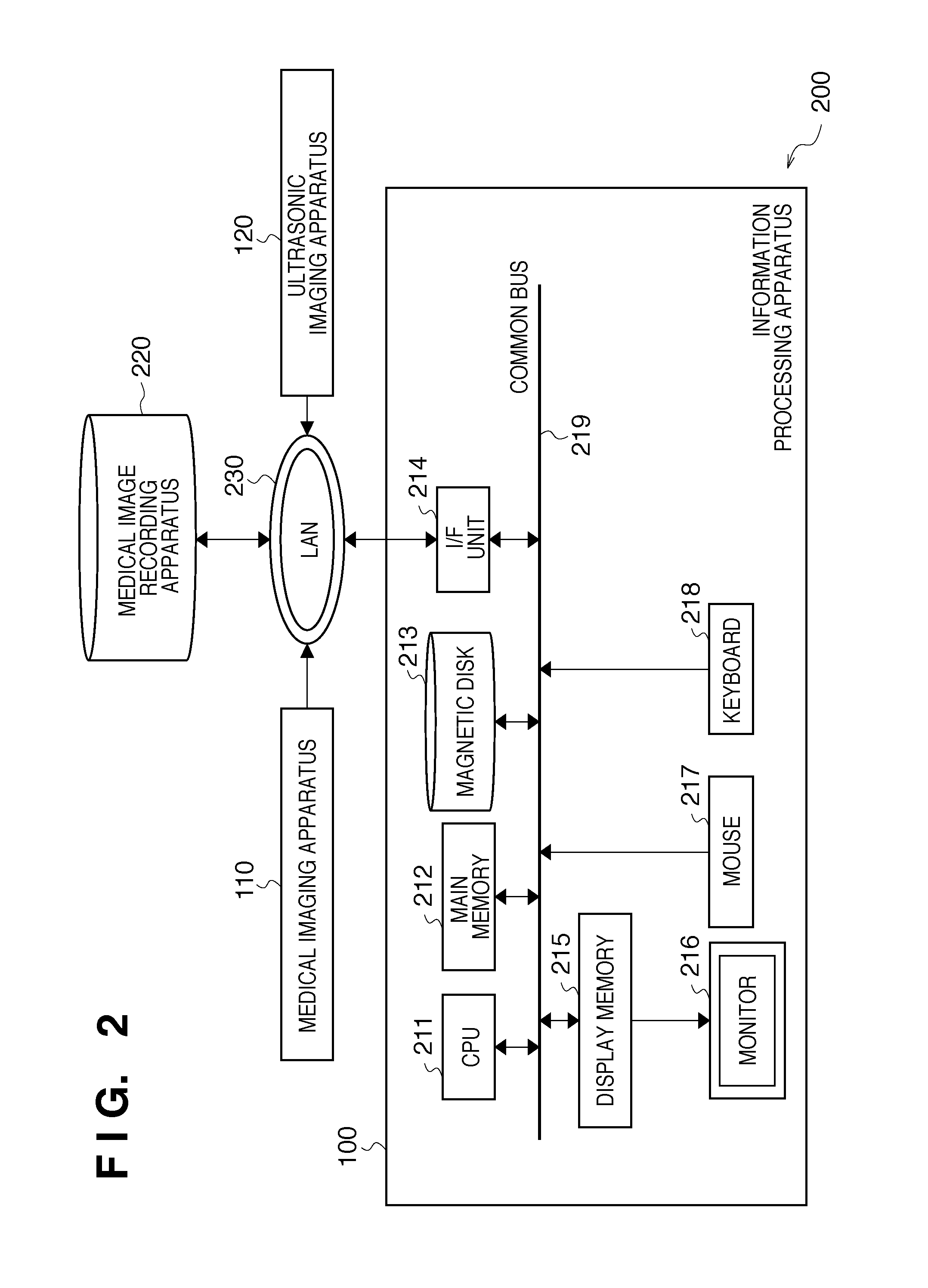
Information processing apparatus for registrating medical images, information processing method and program
ActiveUS20100239150A1Improve accuracyIncrease speedImage enhancementImage analysisInformation processingSonification
An information processing apparatus to register an ultrasonic image and a three-dimensional medical image at high speed is disclosed. The information processing apparatus includes: a medical image acquisition unit which acquires a medical image captured by a medical imaging apparatus in which an imaging unit captures an image of an object at a non-contact position with respect to the object, an ultrasonic image acquisition unit which acquires an ultrasonic image captured by an ultrasonic imaging apparatus in which an ultrasonic probe captures an image of the object at a position in contact with a surface of the object, and a coordinate transformation unit which transforms coordinates of the medical image or ultrasonic image with reference to the contact position on the ultrasonic image, so that image information of the medical image matches that of the ultrasonic image.
Owner:CANON KK
Radio communication system, radio communication method, radio transmitter and radio receiver
InactiveUS7688909B2Reduce throughputPolarisation/directional diversityMultiplex communicationRadio receiverRadio reception
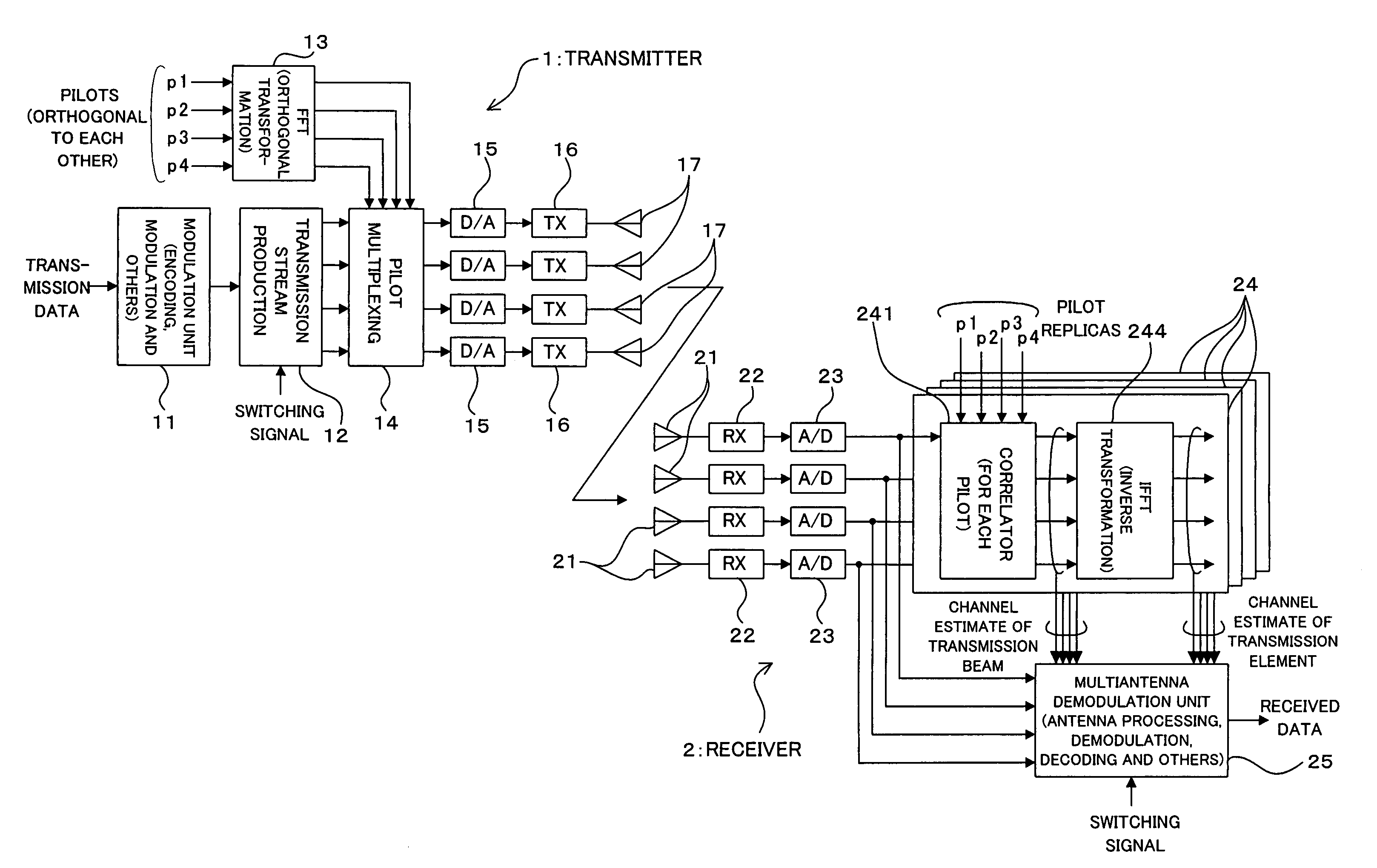
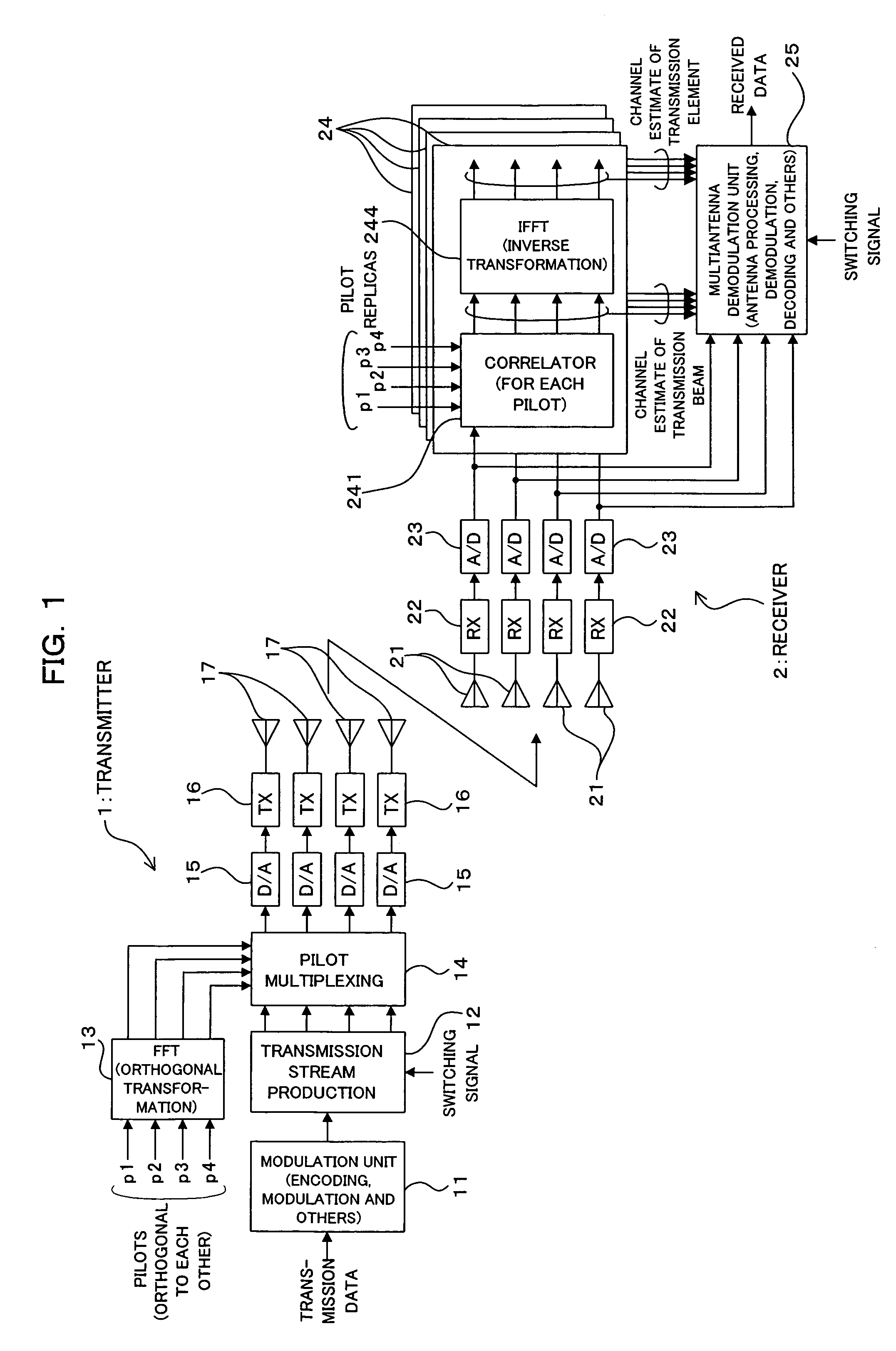
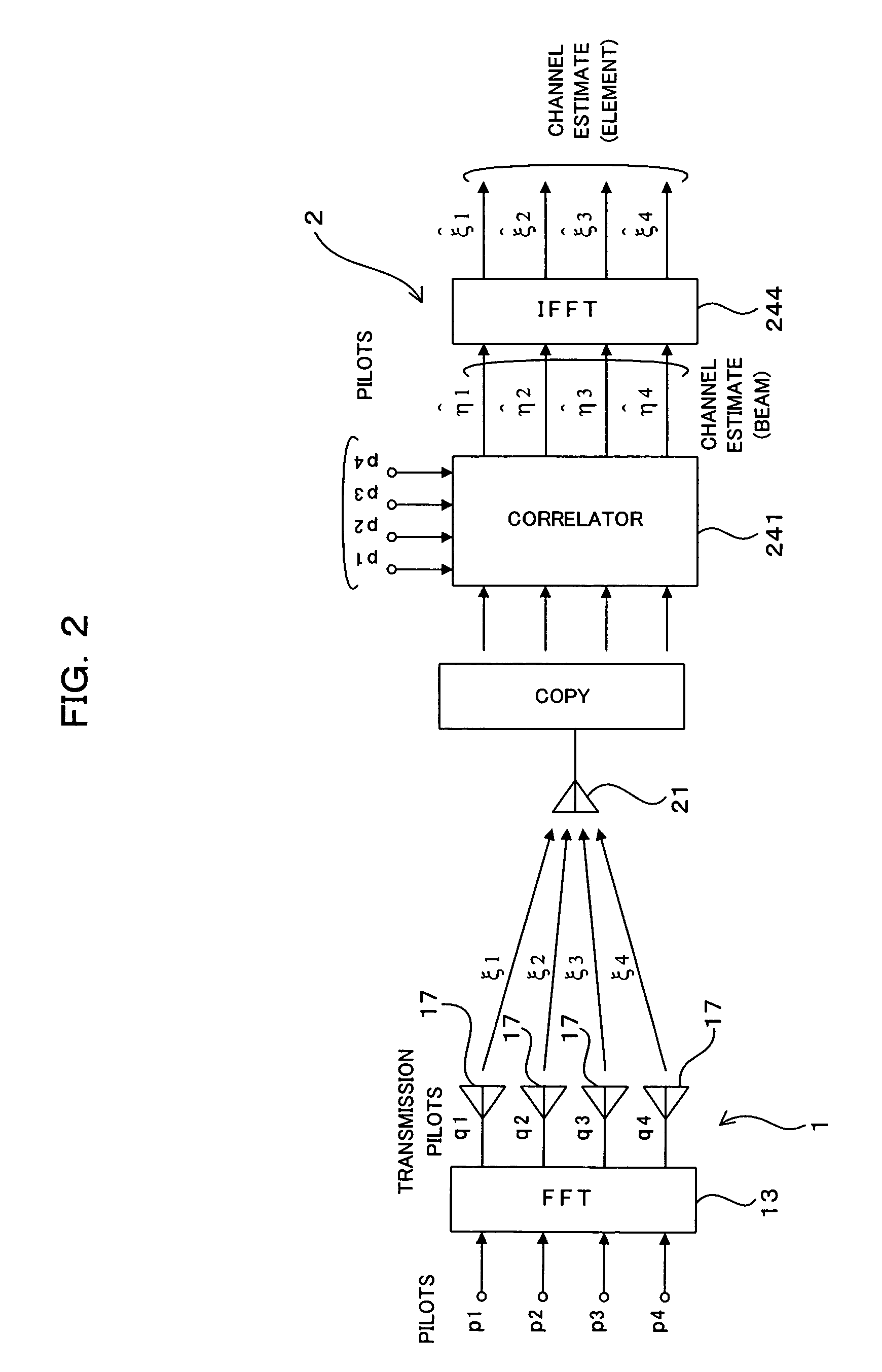
A radio transmitter includes an orthogonal transformation unit for carrying out an orthogonal transformation on pilot signals having orthogonal relation to each other between transmission antennas and a pilot multiplexing unit multiplexing the pilot signals and transmission data, and a radio receiver includes a channel estimation unit obtaining a channel estimate of a directive multibeam for each of reception antennas, an inverse transformation unit carrying out an inverse transformation of the orthogonal transformation on the obtained channel estimate and a received signal processing unit selectively conducting first processing based on the beam channel estimate in the first mode or second processing based on the channel estimate obtained by the inverse transformation unit in the second mode. This commonizes a common pilot for MIMO (second mode) and individual pilots for AAA (first mode), thus realizing the coexistence of MIMO and AAA without leading to a reduction of throughput.
Owner:FUJITSU LTD
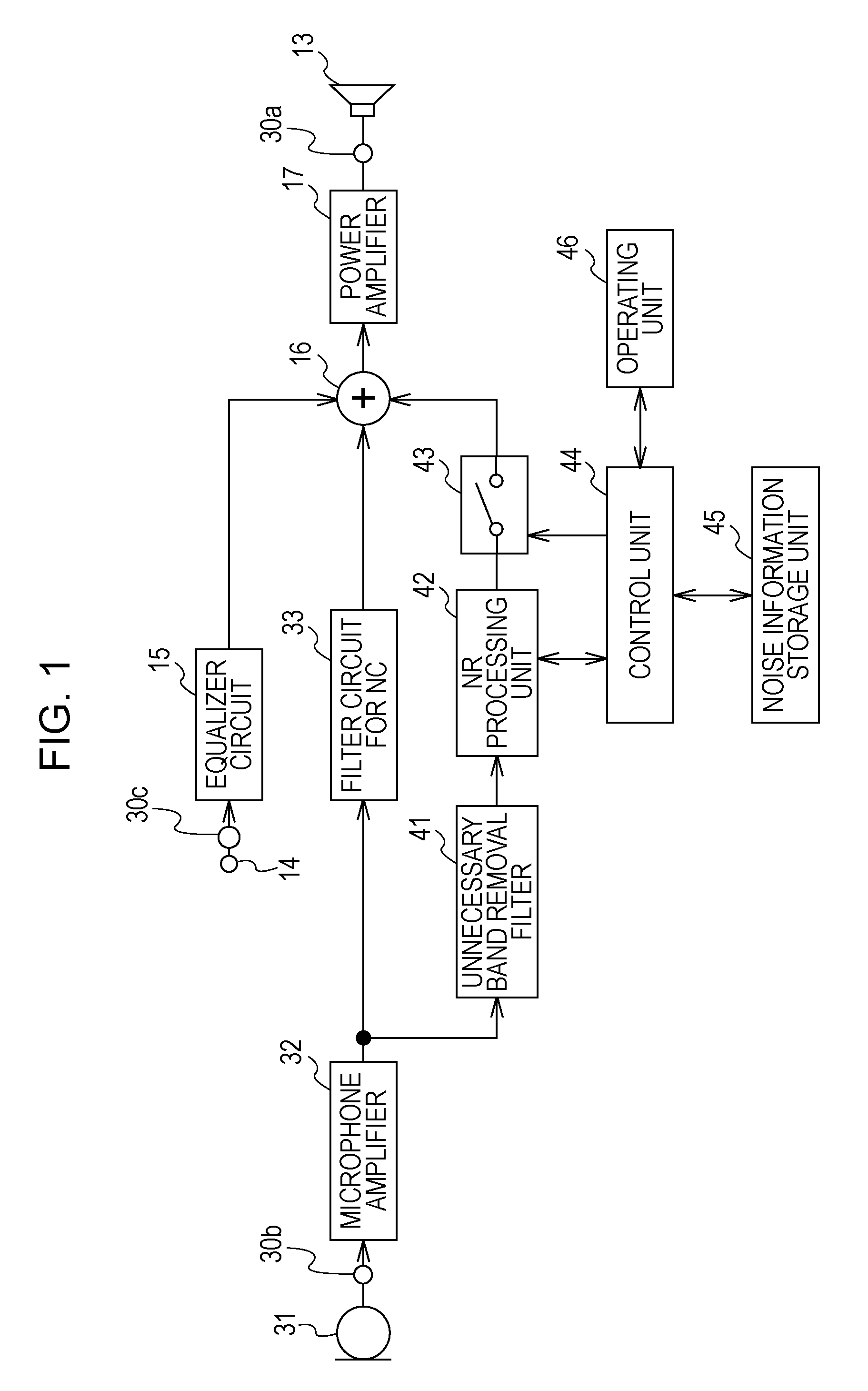
Noise reduction audio reproducing device and noise reduction audio reproducing method
ActiveUS20090323976A1Improve clarityReduce the environmentEar treatmentHearing device active noise cancellationControl signalNoise reduction
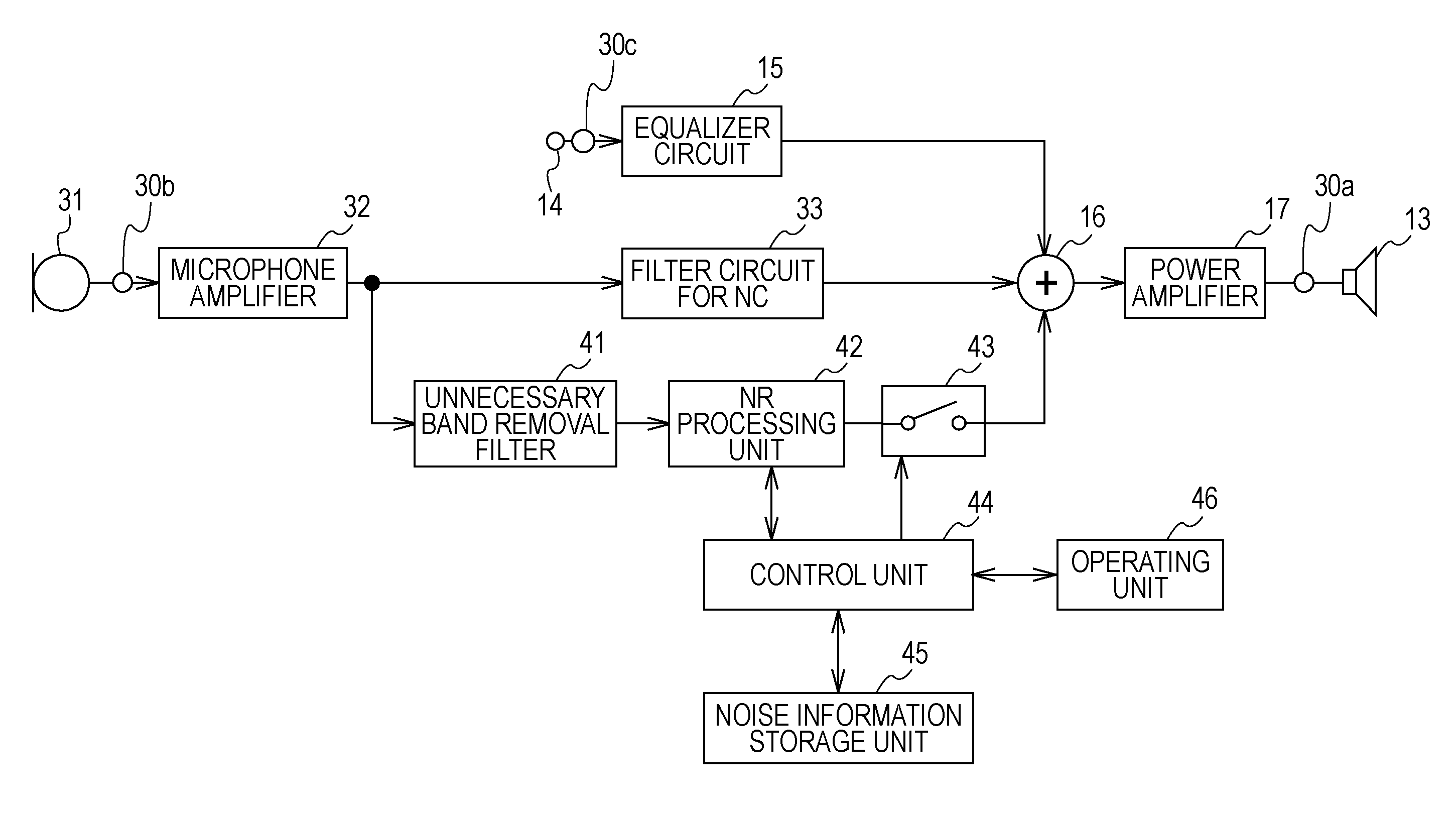
A noise reduction audio reproducing method includes the steps of: generating, from an audio signal of collected and obtained noise, an audio signal for noise cancellation to cancel the noise by synthesizing the audio signal for noise cancellation and the noise in an acoustic manner, reproducing the audio signal for noise cancellation acoustically to synthesize this with the noise in an acoustic manner; emphasizing an audio component to be listened to, of collected audio; synthesizing an audio signal with the audio component to be listened to being emphasized, and the audio signal for noise cancellation to supply the synthesized signal thereof to an electro-acoustic converting unit; and controlling so as to supply an audio signal, with the audio component to be listened to having been emphasized, to a synthesizing unit, regarding only a section based on a control signal.
Owner:SONY CORP
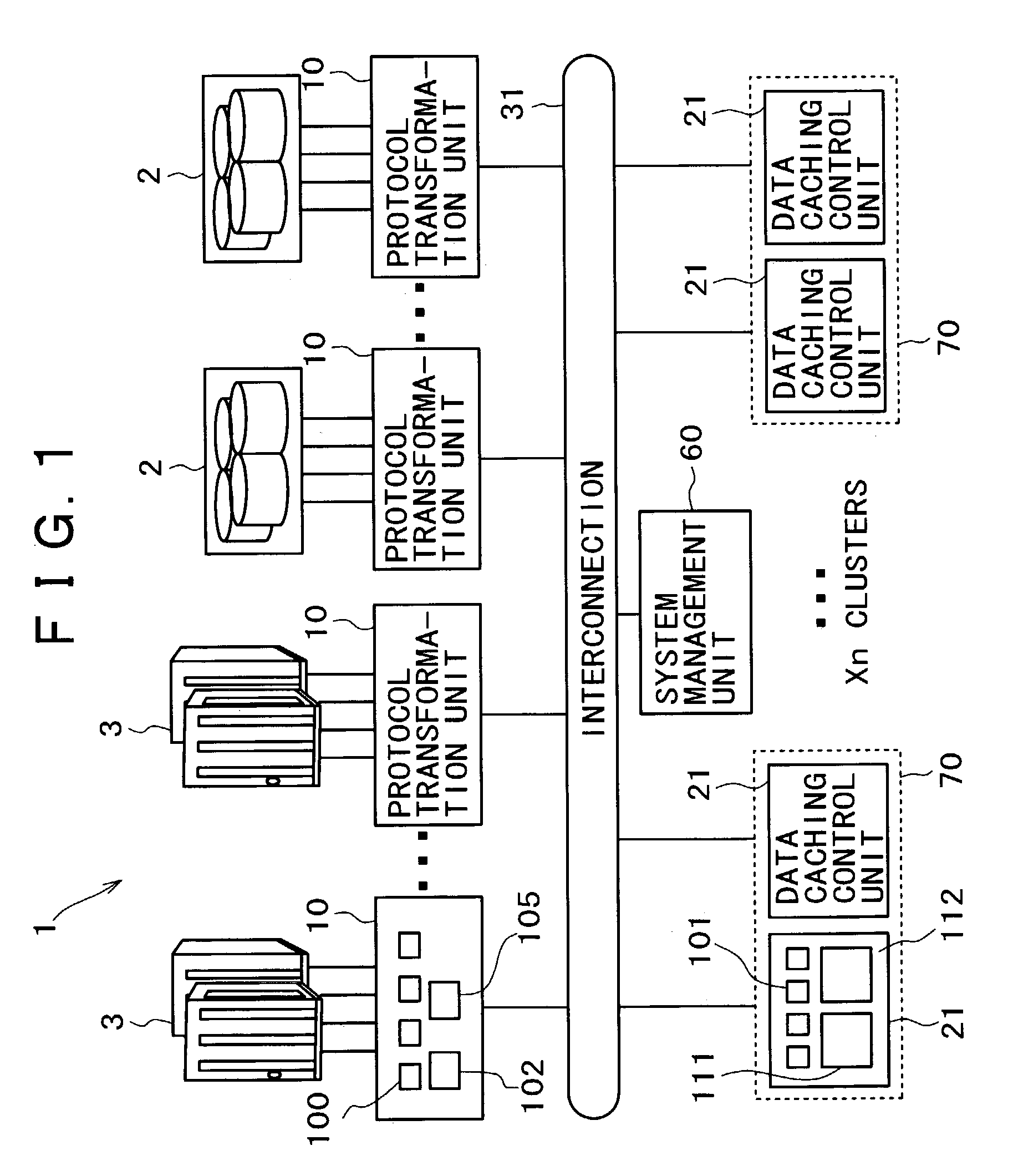
System and Managing method for cluster-type storage
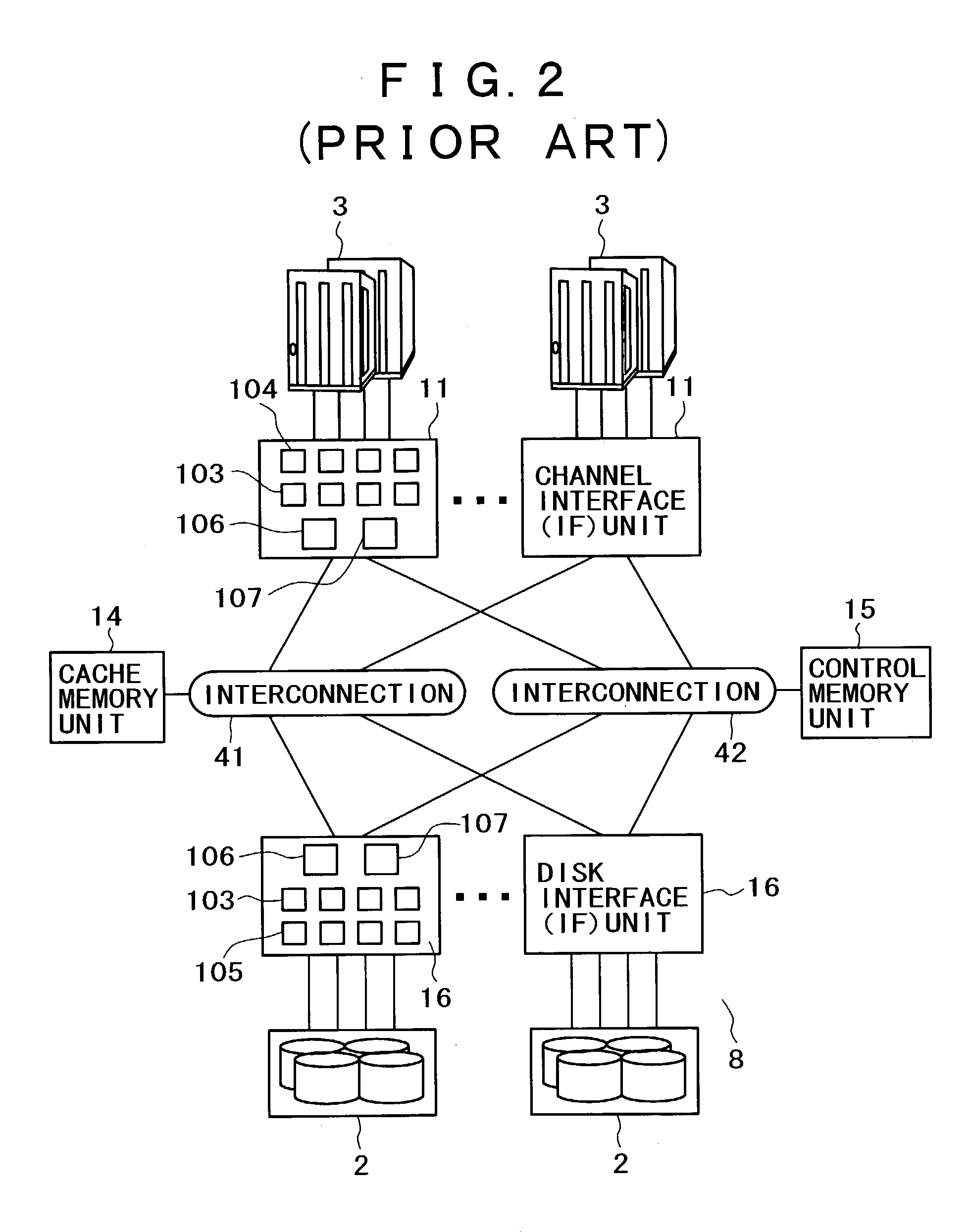
ActiveUS20040103244A1Input/output to record carriersMemory adressing/allocation/relocationHard disc driveSystems management
A system and managing method for cluster-type storage is provided. In one example of the system, the storage system is configured so as to expand from small to large configurations at a reasonable cost with performance decided appropriately to the target system scale. The storage system has an interface with a server or hard drives, a plurality of protocol transformation units, each used for transforming a read or write protocol of the data to be exchanged with the server or hard drives and a plurality of data caching control units, each having a cache memory unit for storing data to be read from or written in the server or hard drives and a function for controlling the cache memory unit. An interconnection is used for the connection between the plurality of the protocol transformation units and the plurality of the data caching control units. In the storage system, the plurality of the data caching control units are divided into a plurality of control clusters while the cache memory unit is controlled only in its corresponding control cluster independently while the system management unit is connected to the interconnection, so that the system management unit manages the plurality of protocol transformation units and so that the plurality of control clusters are managed integrally as one system.
Owner:HITACHI LTD
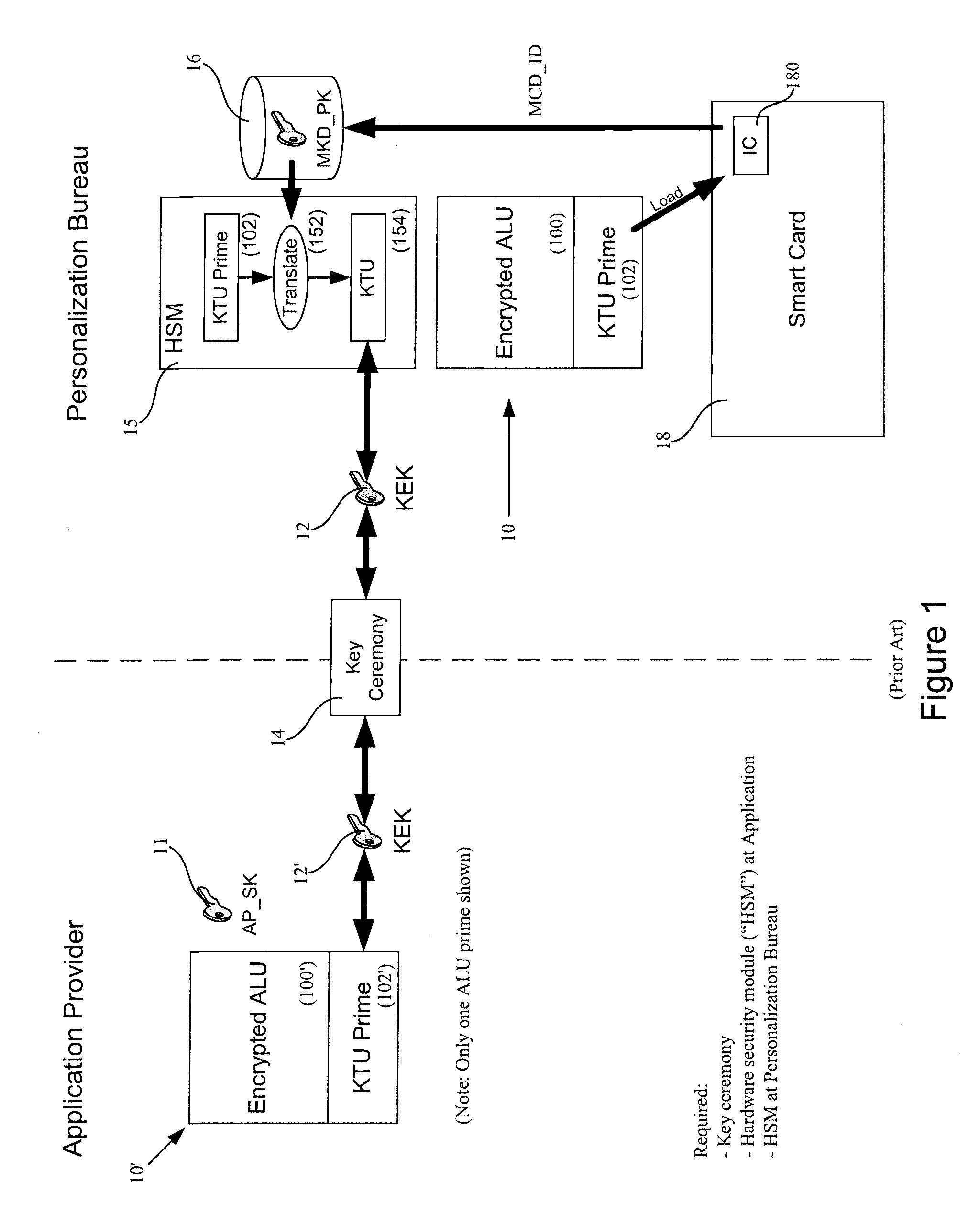
Tamper resistant module having separate control of issuance and content delivery
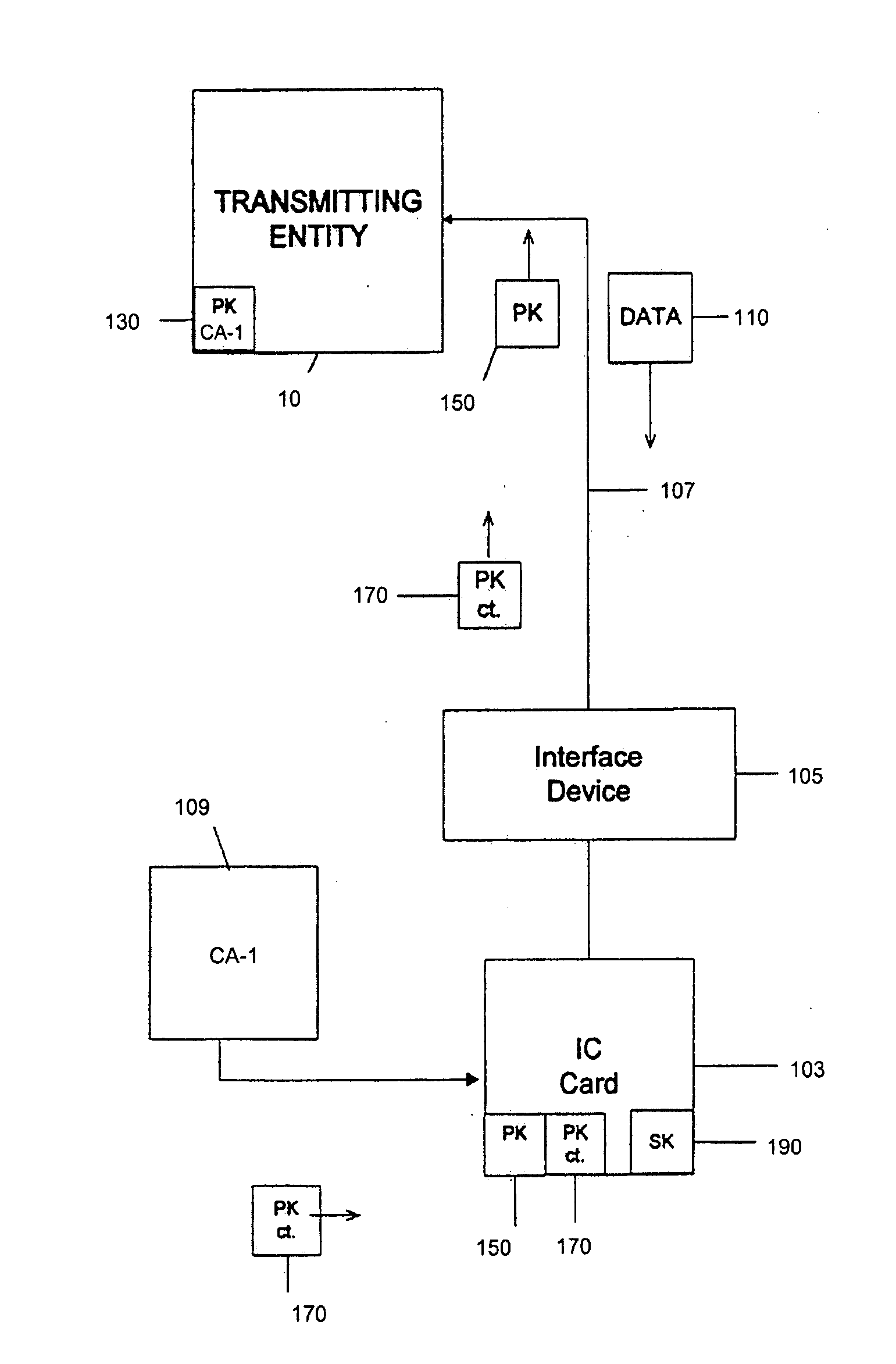
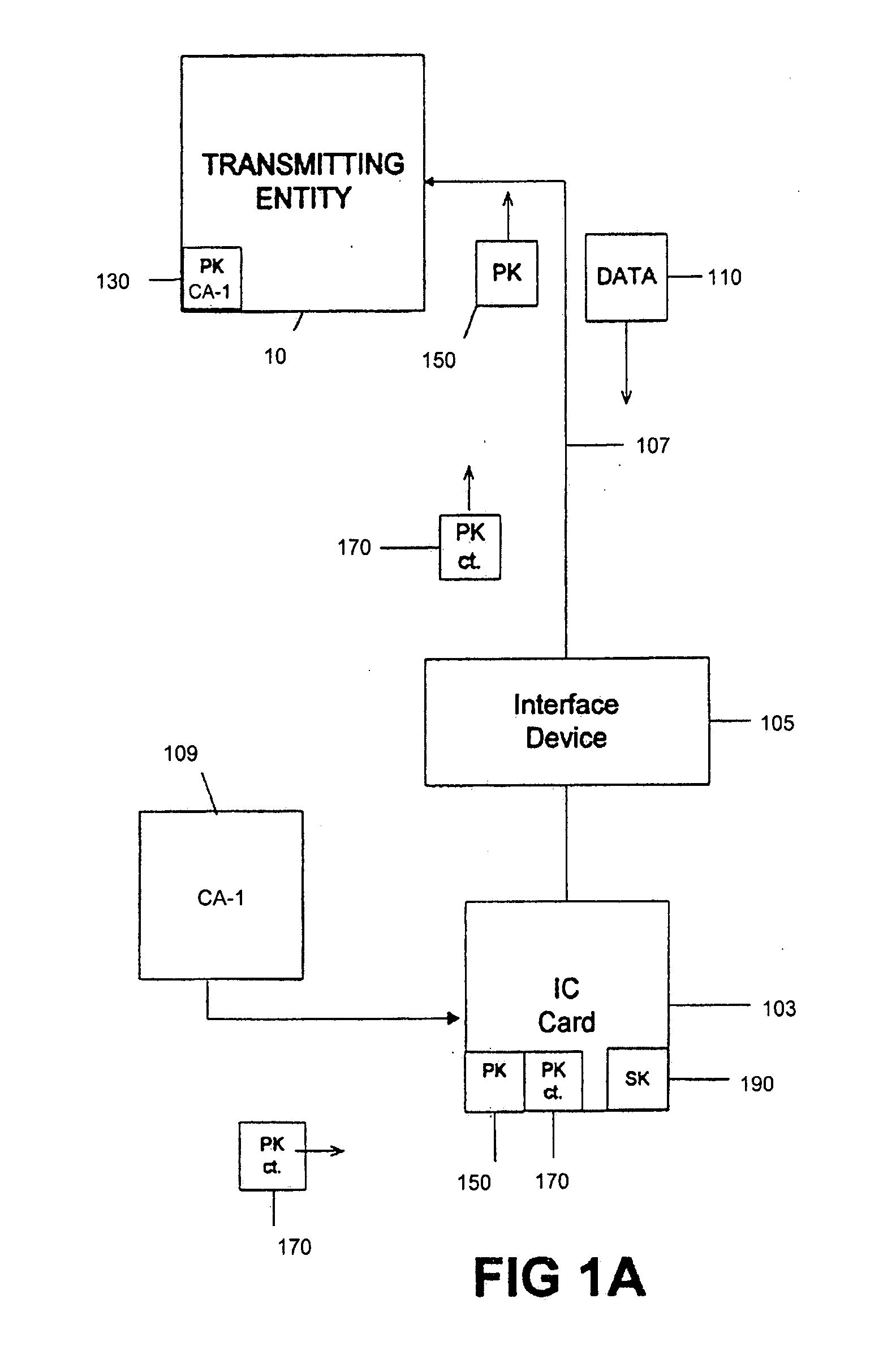
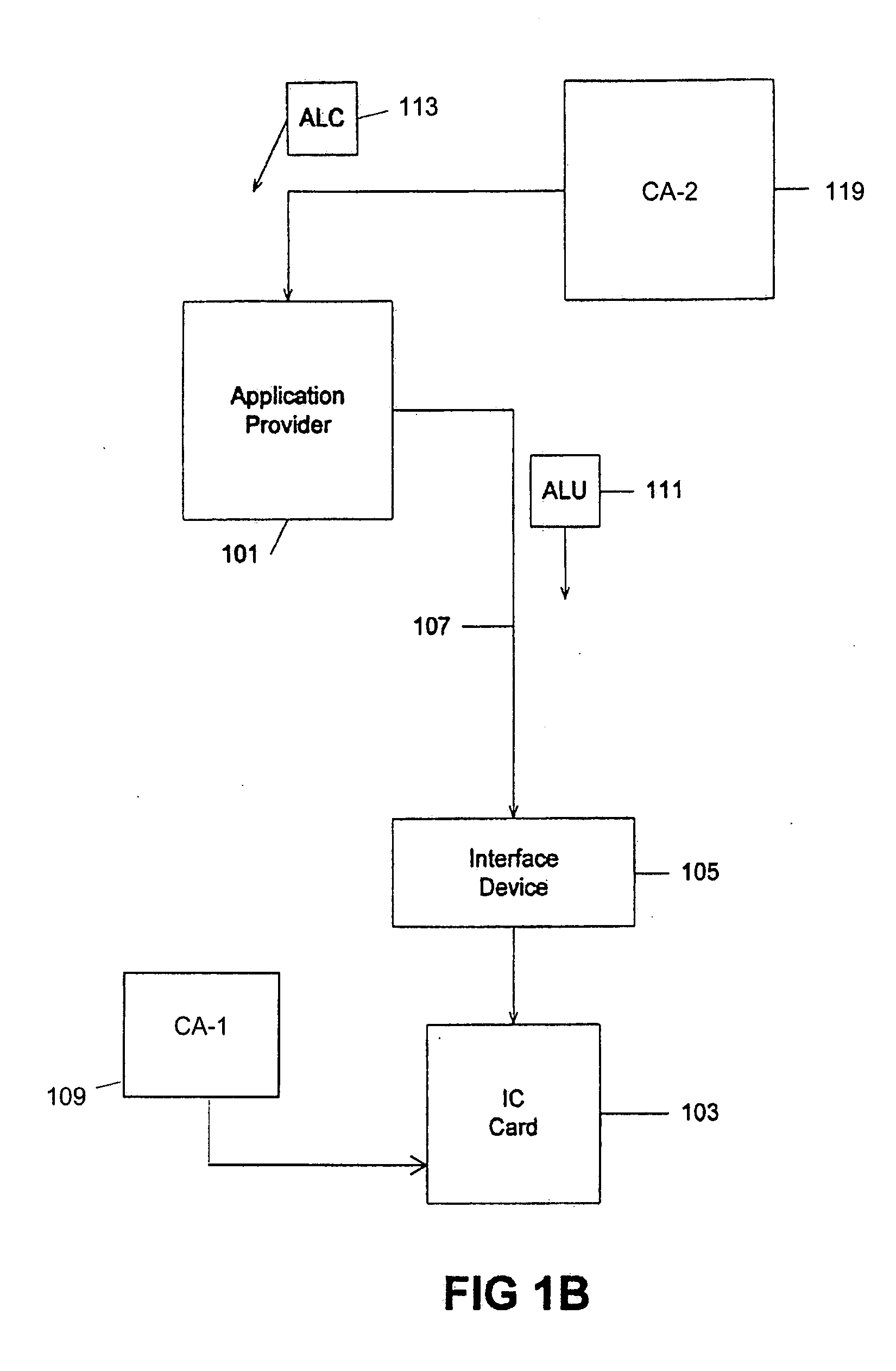
InactiveUS20080010470A1Acutation objectsUser identity/authority verificationDigital signatureTransformation unit
Methods, apparati, and computer-readable media for securely loading a software module over a communications network from a software provider (SP) (101) onto a tamper resistant module (TRM) (103). A method embodiment of the present invention comprises: the SP (101) encrypting, using at least one transport key, at least one portion of the software module, each portion having an indication of location of the portion; the SP (101) encrypting each transport key and each indication using an asymmetric TRM public key, thereby forming a key transformation unit (KTU) (207), the TRM public key (150) having a corresponding TRM private key (190), the TRM public key (150) and corresponding TRM private key (190) being certified by a first certification authority (CA-1) (109); the SP (101) digitally signing the encrypted portion(s) with at least one asymmetric SP private key, each said SP private key having a corresponding SP public key, to produce a signed software module, each SP public key being certified by a second certification authority (CA-2) (119), CA2 (119) being different than CA-1 (109); and the SP (101) transmitting the portion(s), the KTU (207), and the signed software module to the TRM (103) over the communications network; and the TRM (103) recovering the transport key(s) and the indication(s) by decrypting the KTU (207) using the TRM private key (190); the TRM identifying the portion(s) using the recovered indication(s), verifying the certified SP public key using the public key of CA-2, authenticating the portion(s) using the certified SP public key; and decrypting the portion(s) using the recovered transport key(s).
Owner:MULTOS
MOS type image pickup device having pixel interleaved array layout and one analog to digital conversion unit provided per each pair of adjacent photoelectric conversion columns
InactiveUS6933972B2Highly integratedSuppression of manufacturing cost increaseTelevision system detailsTelevision system scanning detailsPhotoelectric conversionEngineering
A number of photoelectric conversion elements are disposed in a plurality of rows and columns in a pixel shift layout, and an analog / digital conversion unit is provided per two photoelectric conversion element columns to form a MOS type solid-state image pickup device. It is possible to suppress an increase in the manufacture cost of MOS type solid state image pickup devices with built-in A / D conversion units and improve the integration degree of photoelectric conversion elements.
Owner:FUJIFILM CORP
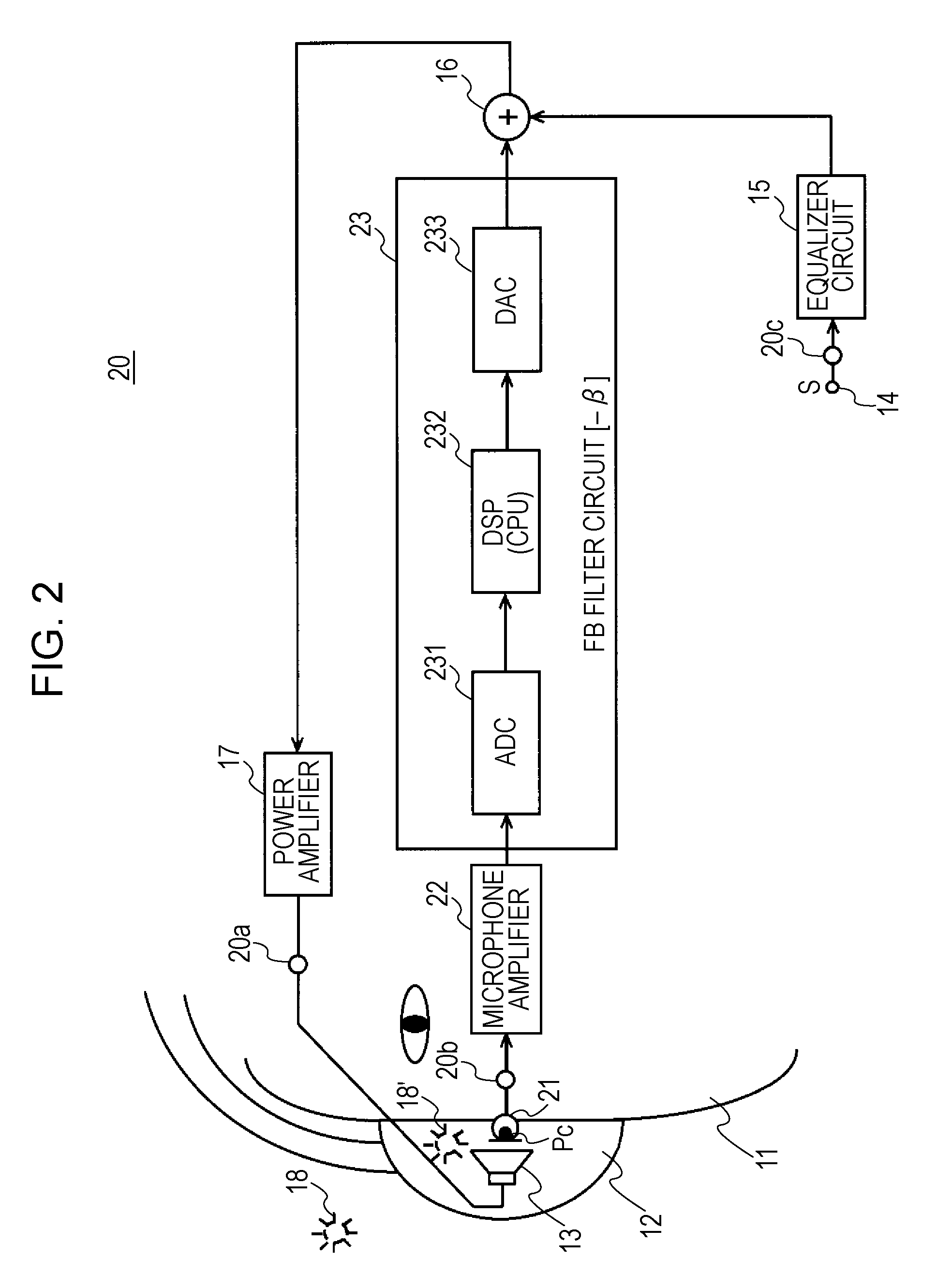
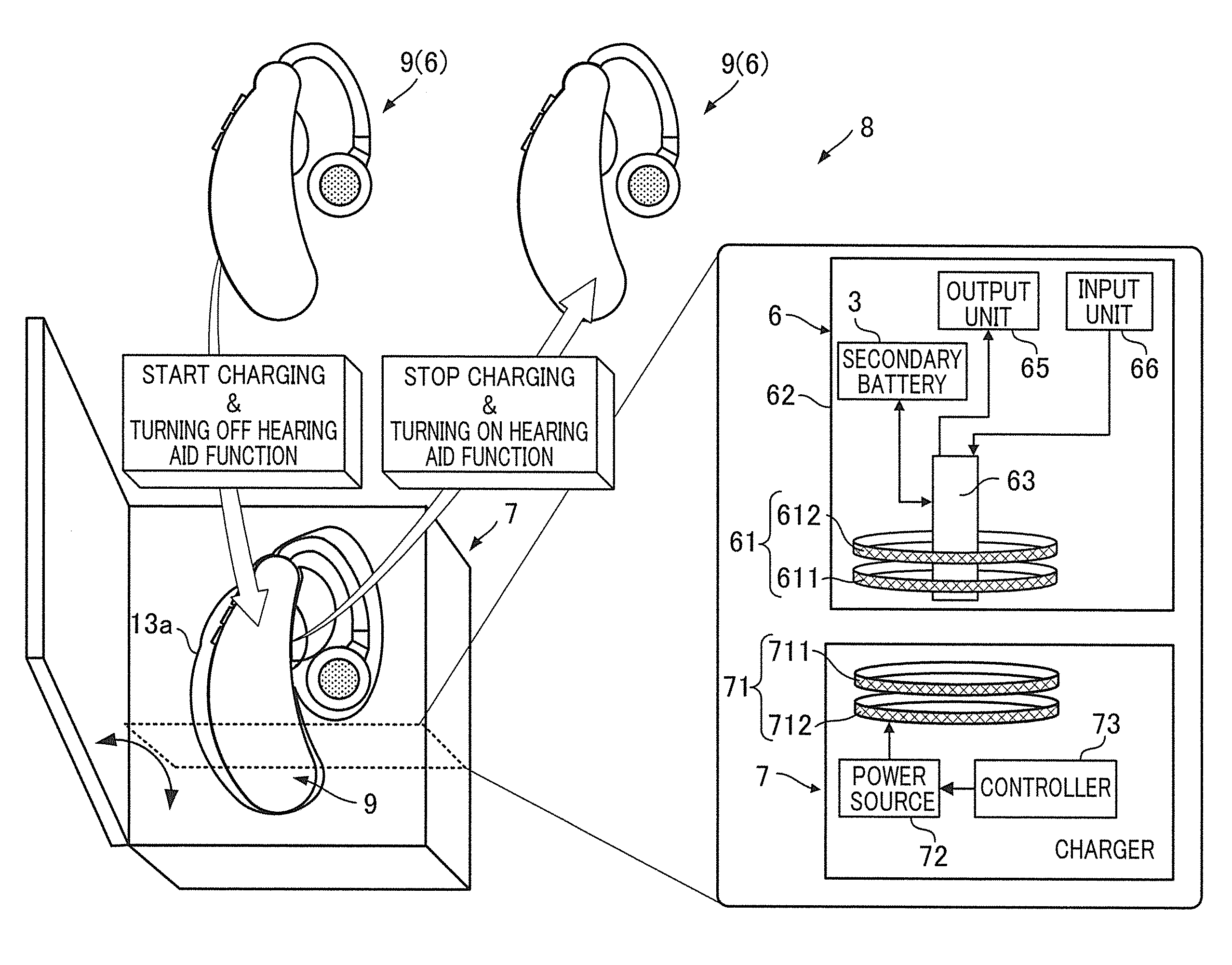
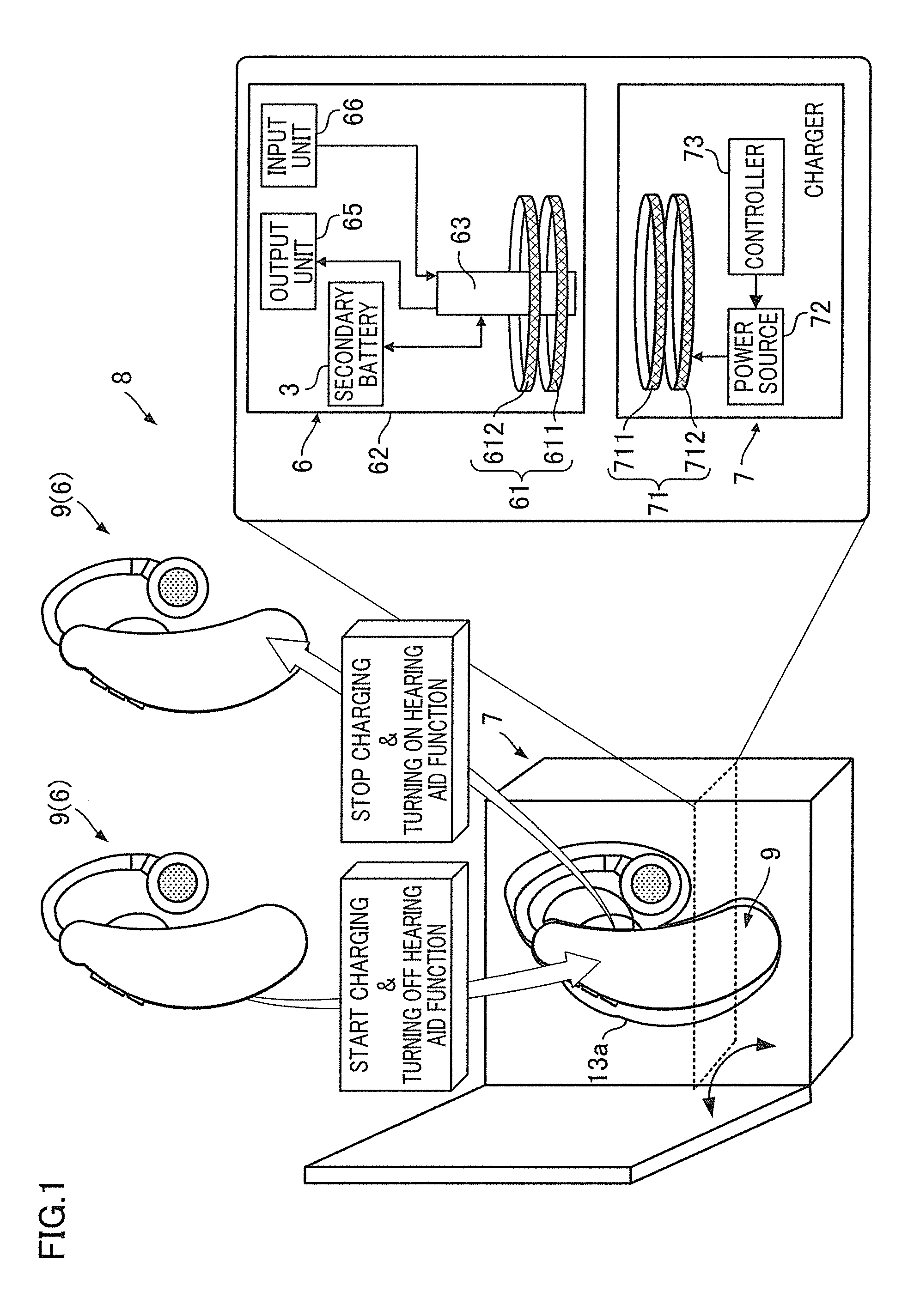
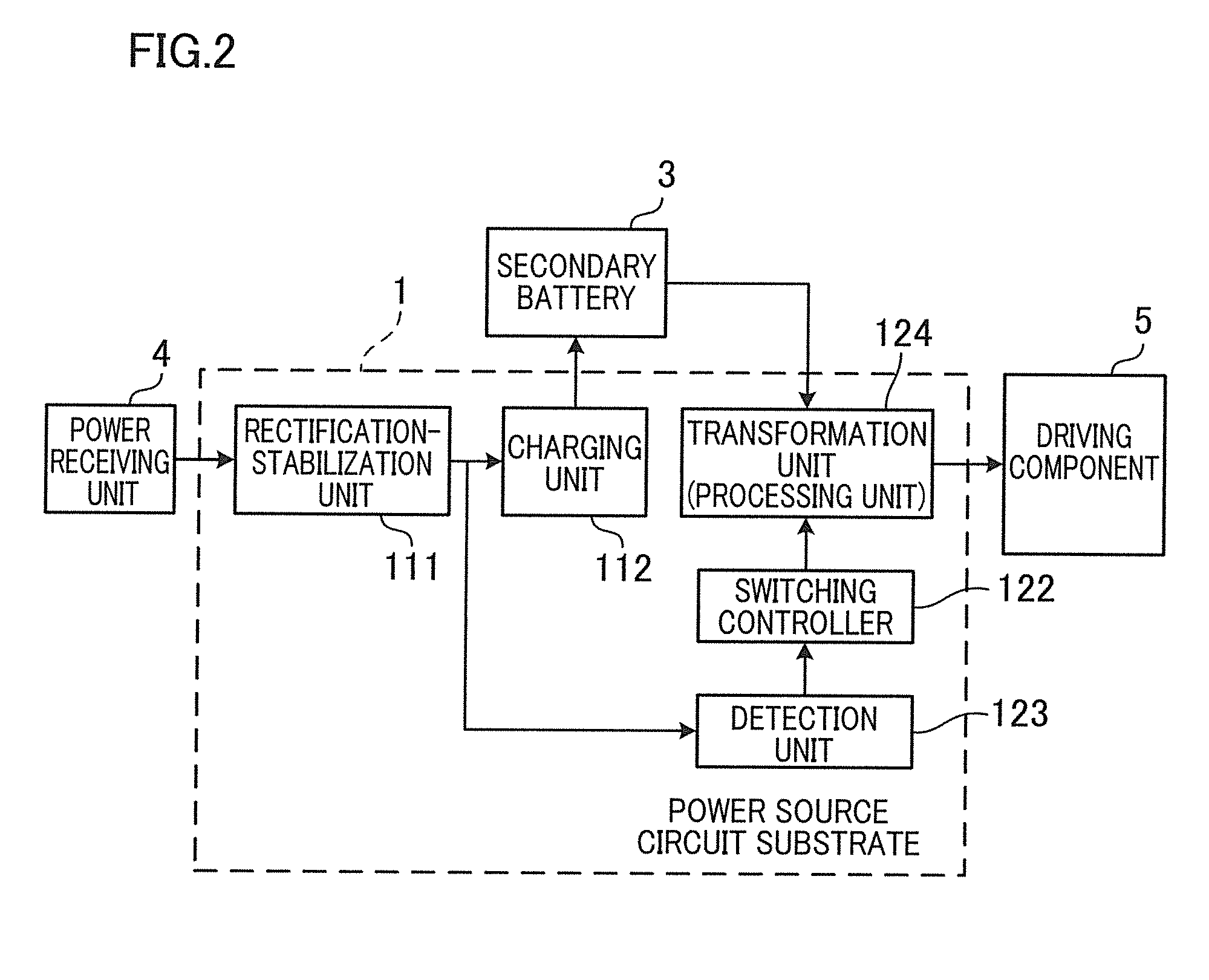
Portable device, charging system, and power source circuit substrate
A portable device is arranged to include a secondary battery, a driving component driven by charged power of the secondary battery, a charging unit configured to charge the secondary battery by outside power, a transformation unit (processing unit) configured to output the charged power of the secondary battery at a driving voltage of the driving component, a detection unit configured to detect the input of the outside power to the charging unit, and a switching controller configured to switch the state of the transformation unit from an operation state to a stopped state only when the input of the outside power to the charging unit is detected by the detection unit.
Owner:HIMPP
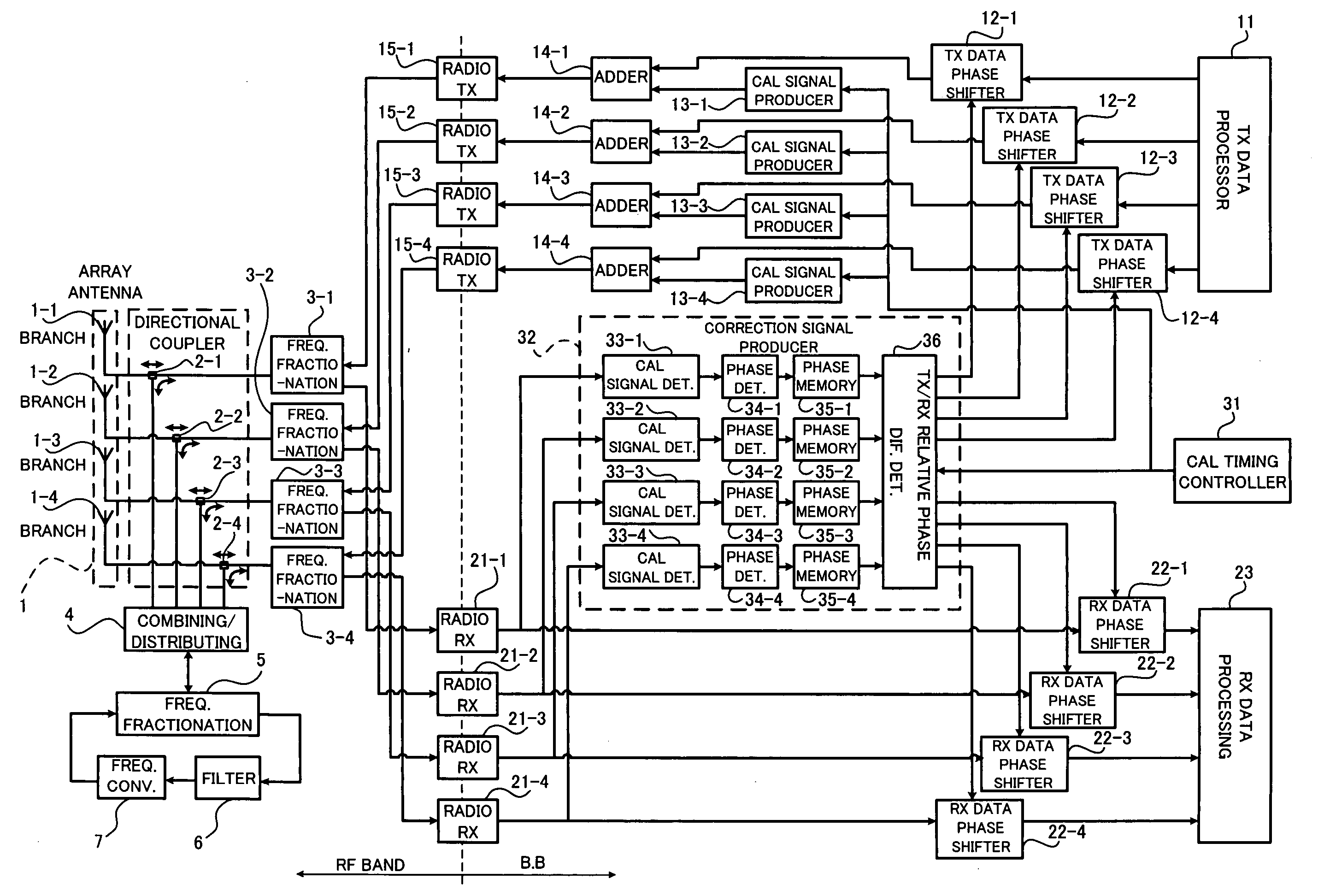
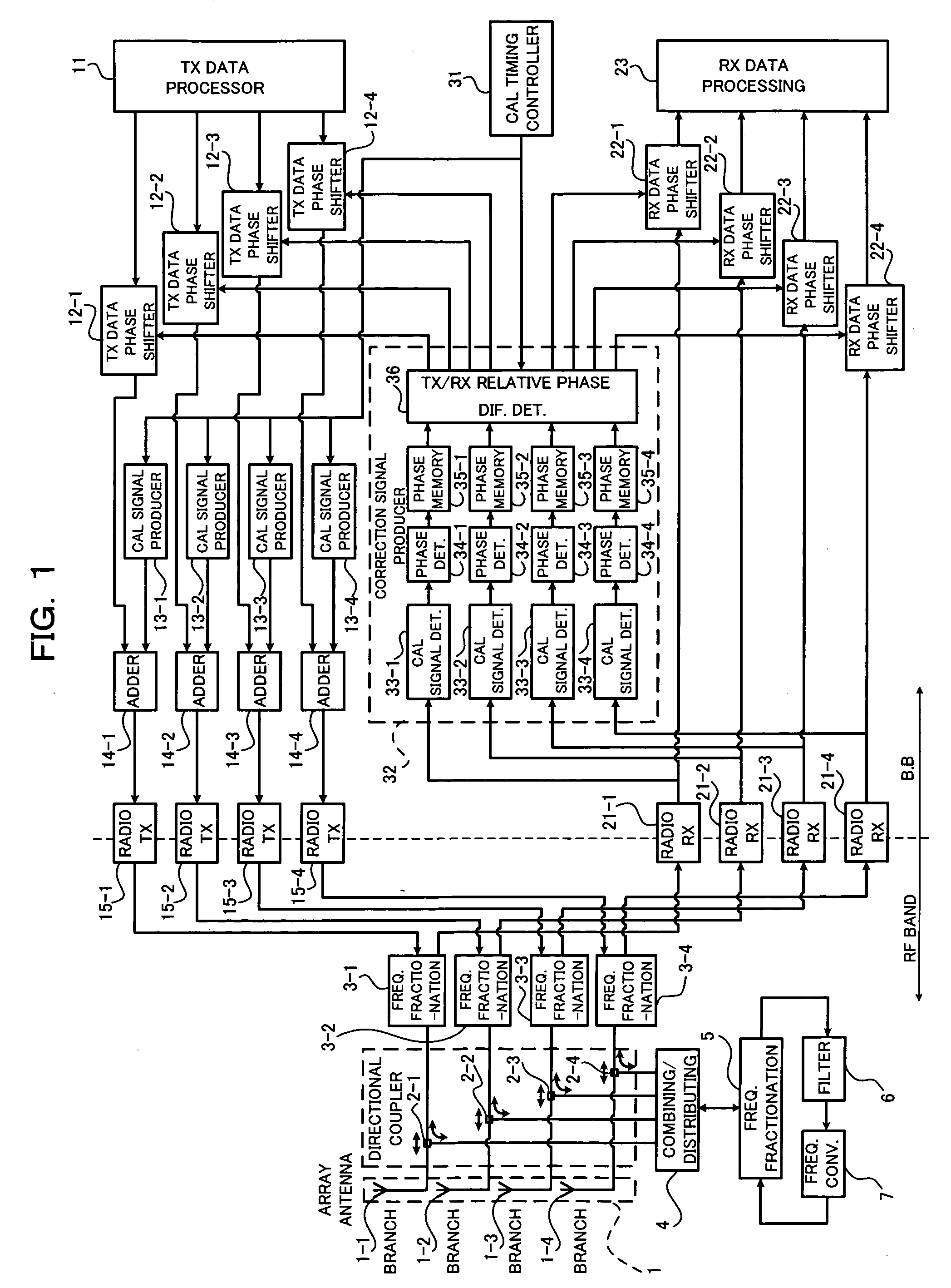
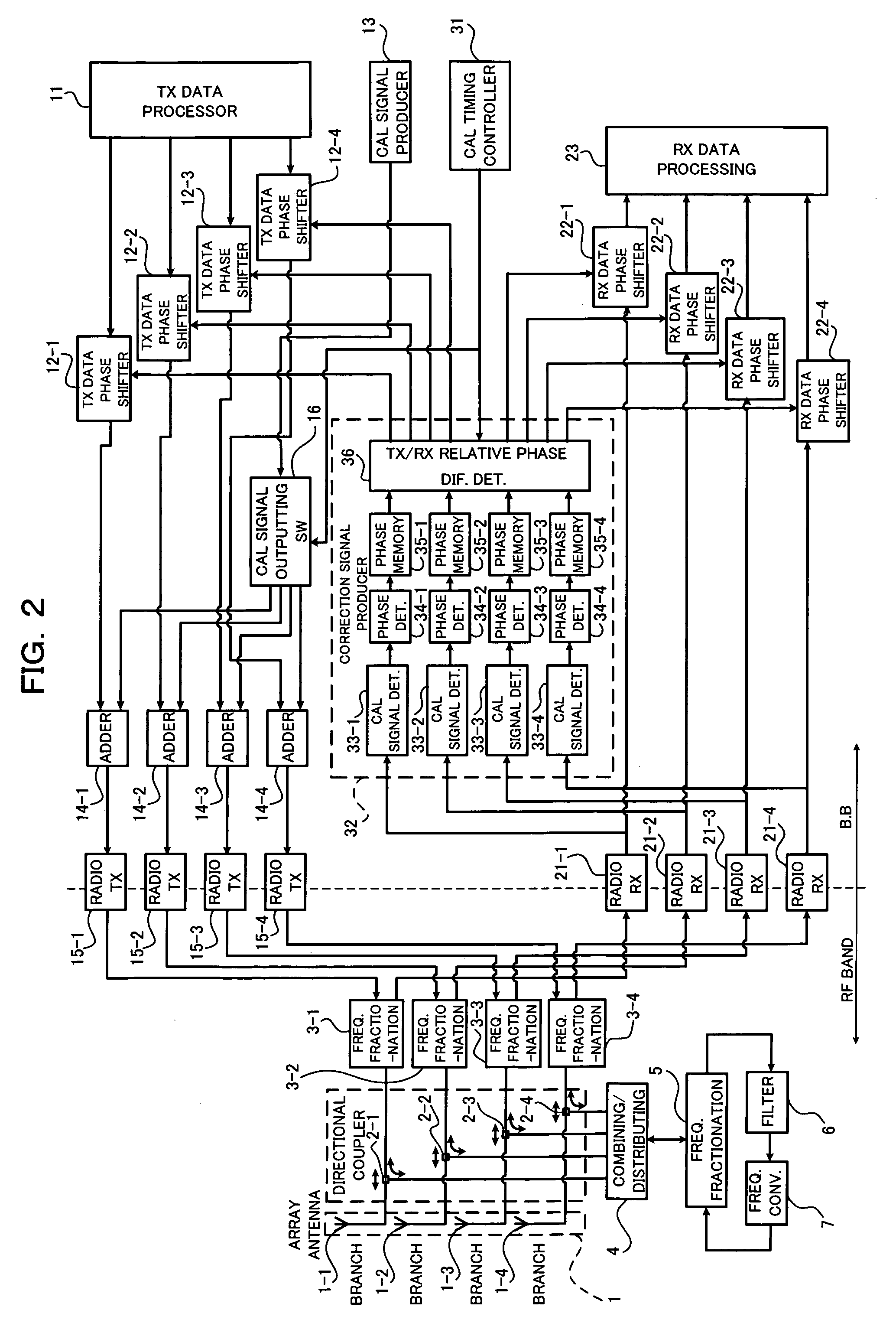
Calibration apparatus and method for array antenna
InactiveUS20060279459A1Eliminate needEasy CalibrationPolarisation/directional diversityTransmission monitoringPhase differenceRelative phase
The present invention relates to a calibration apparatus for an array antenna having a plurality of antenna elements. The calibration apparatus comprises a conversion unit detecting a calibration signal from an output of a transmission unit to convert the detected calibration signal into a predetermined reception radio frequency and outputting the converted calibration signal together with a reception main signal to a reception unit, a detecting unit detecting the calibration signal from an output of the reception unit for each of the antenna elements to obtain a relative phase difference between the calibration signals, and a phase correcting unit correcting a phase difference with respect to one of or both a transmission main signal and a reception main signal based on the obtained relative phase difference. This configuration can eliminate the need for a radio transmitter-receiver dedicated to a calibration signal, thus facilitating the calibrations.
Owner:FUJITSU LTD
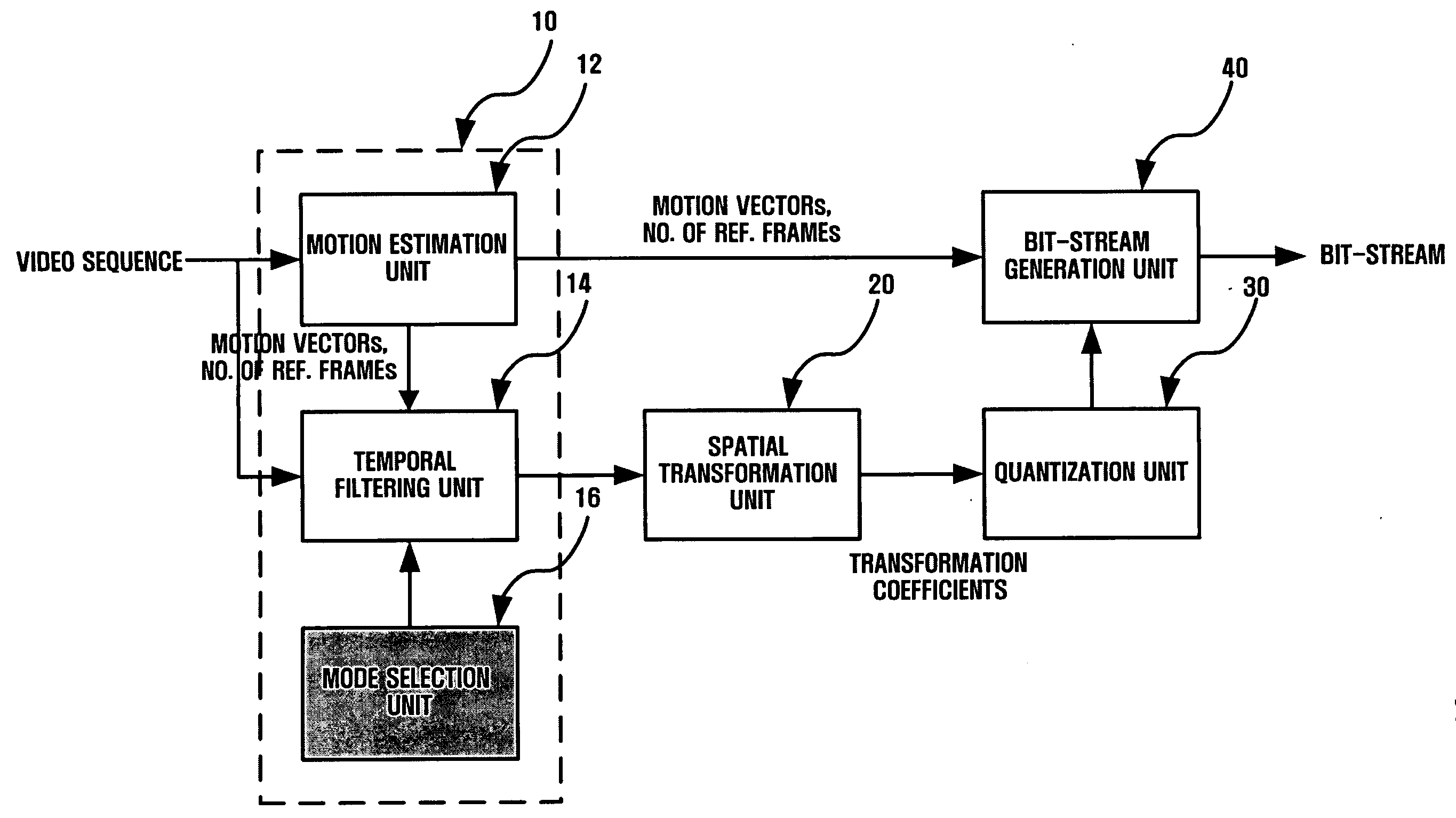
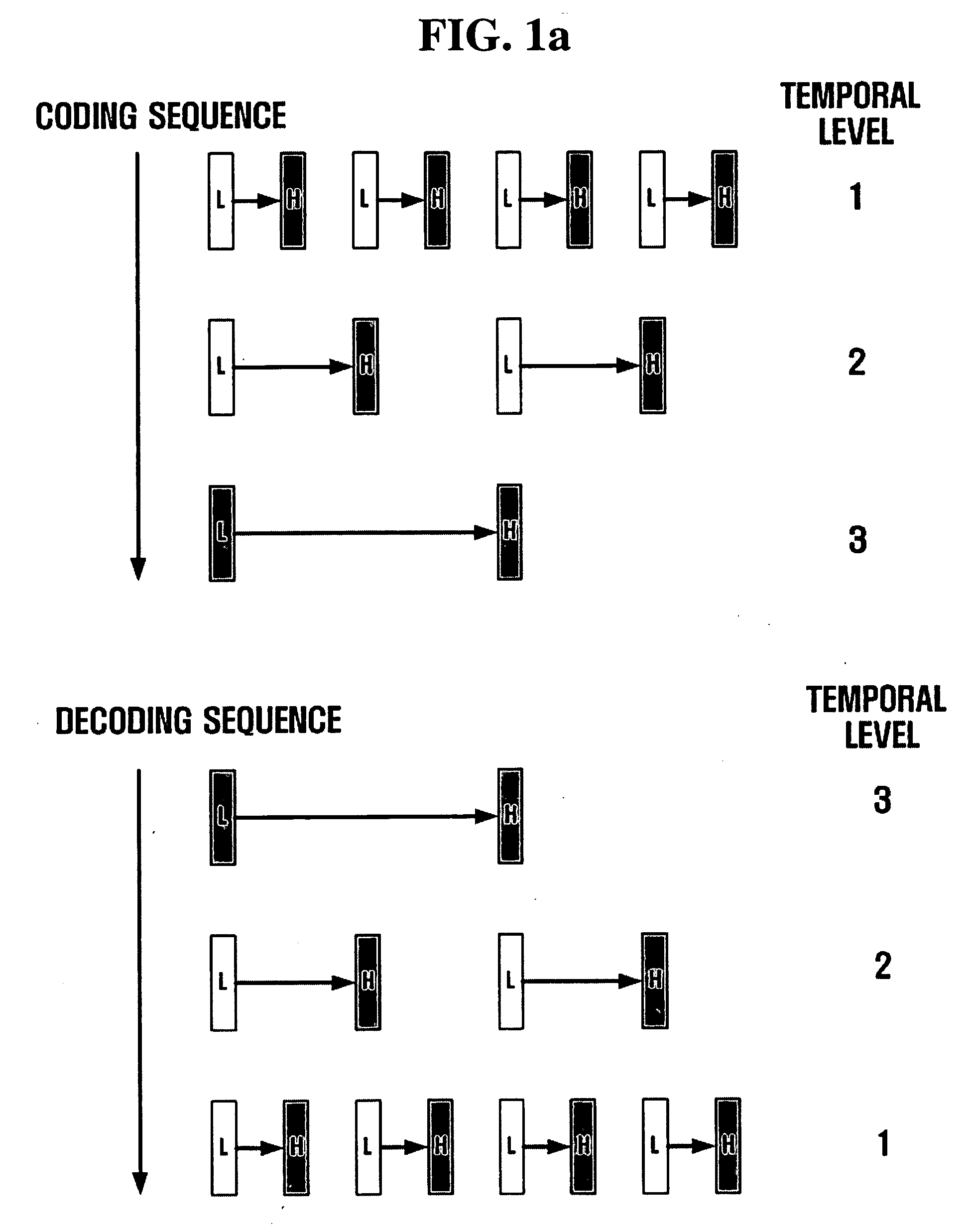
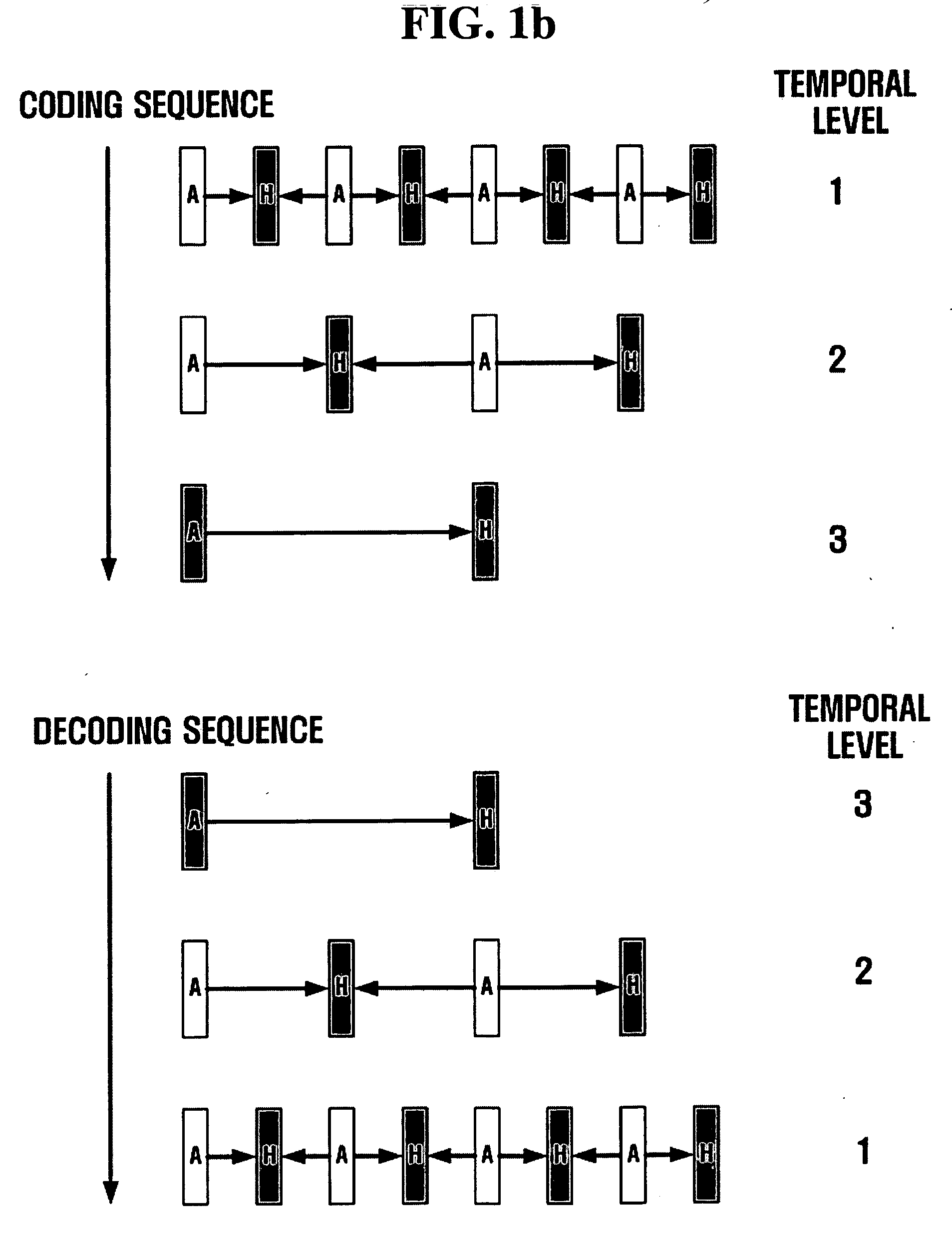
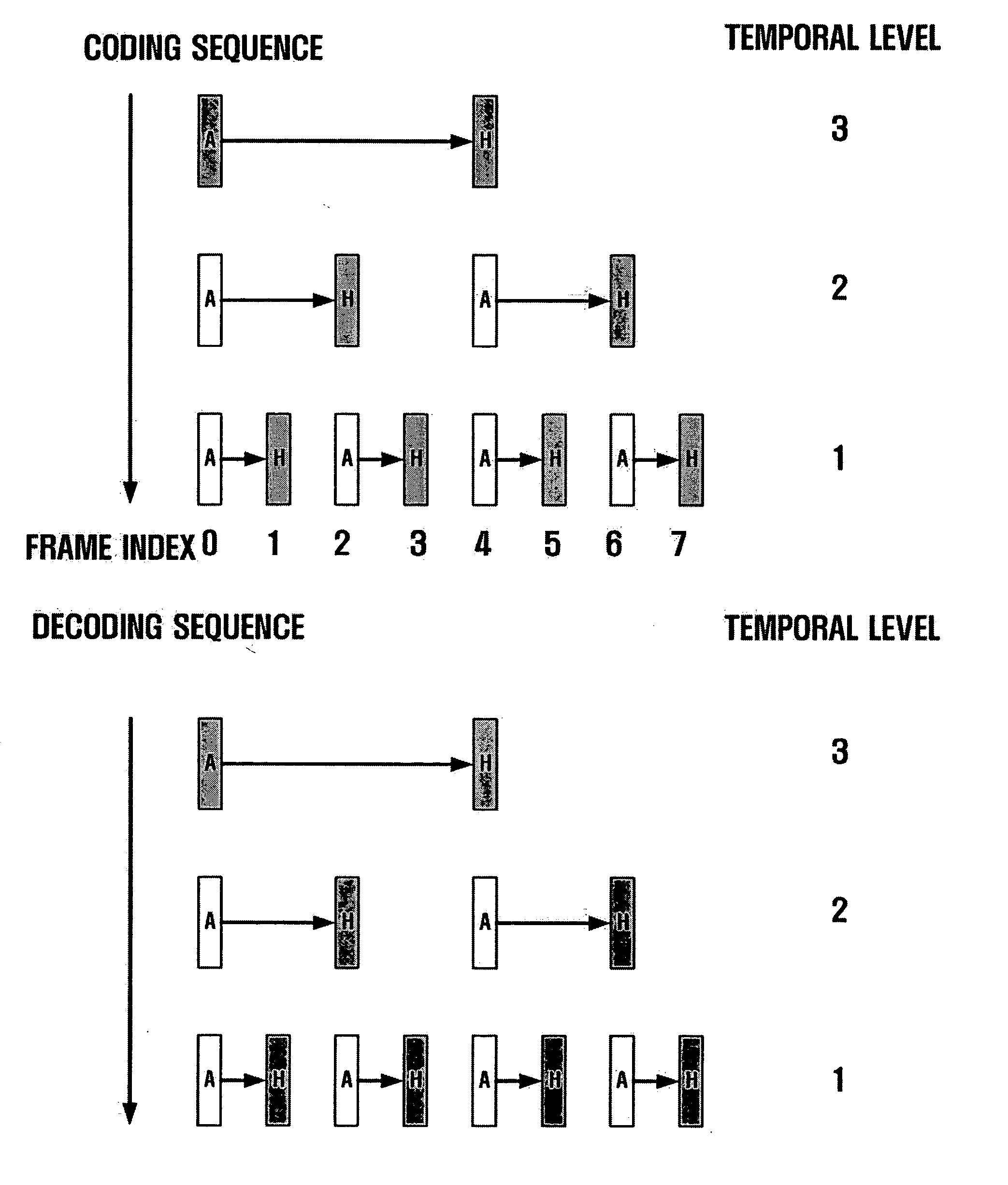
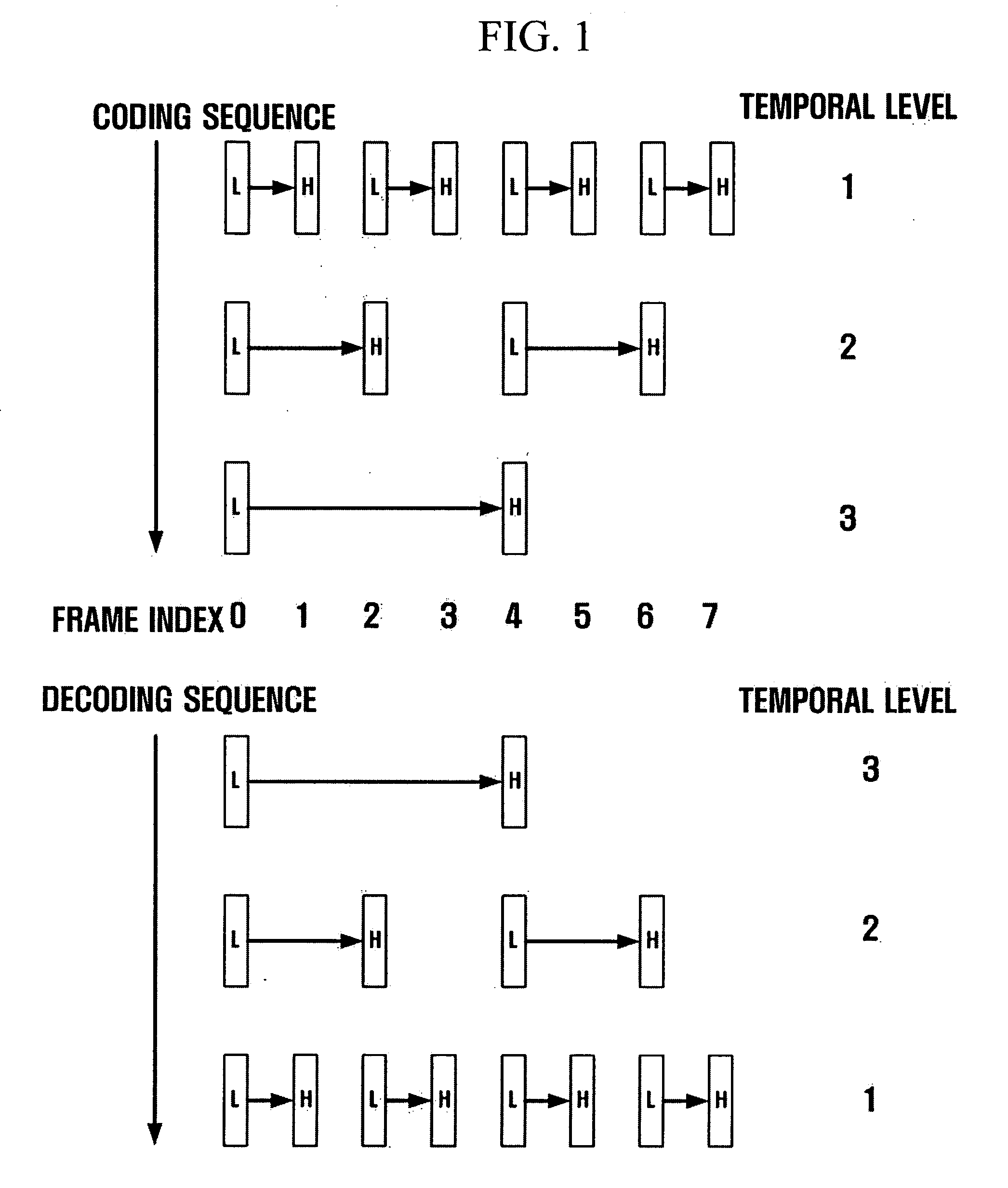
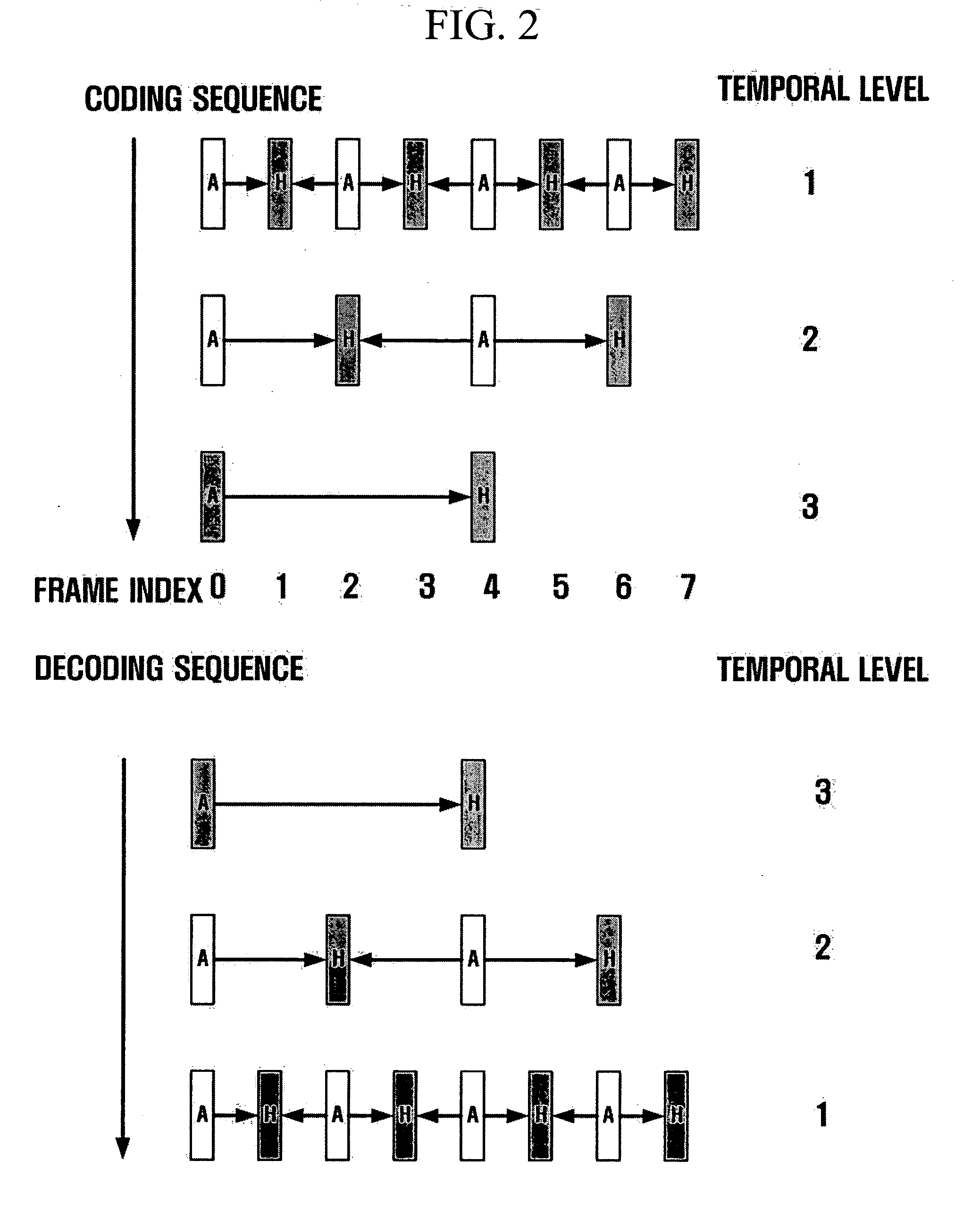
Method and apparatus for scalable video encoding and decoding
InactiveUS20050117647A1Eliminate spaceColor television with pulse code modulationColor television with bandwidth reductionComputer graphics (images)Video encoding
A method and apparatus for scalable video and decoding are provided. A method for video coding includes eliminating temporal redundancy in constrained temporal level sequence from a plurality of frames constituting a video sequence input, and generating a bit-stream by quantizing transformation coefficients obtained from the frames whose temporal redundancy has been eliminated. A video encoder for performing the encoding method includes a temporal transformation unit, a spatial transformation unit, a quantization unit, and a bit-stream generation unit. A video decoding method is in principle performed inversely to the video coding sequence, wherein decoding is performed by extracting information on encoded frames by receiving bit-streams input and interpreting them.
Owner:SAMSUNG ELECTRONICS CO LTD
Multimedia content delivery system
ActiveUS20130024545A1High degree of controlHigh degree of flexibilityDetails involving 3D image dataImage codingGraphicsManagement unit
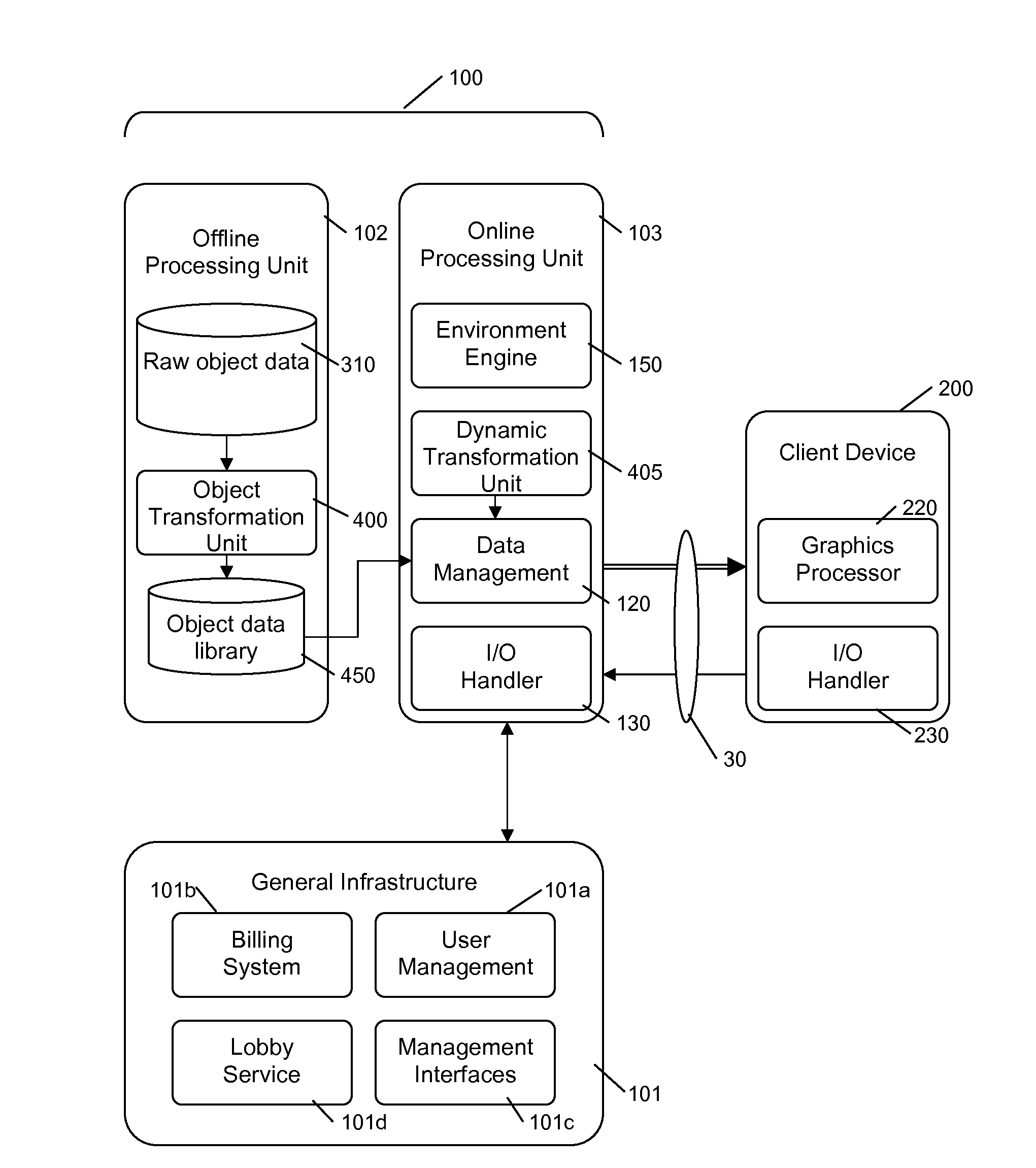
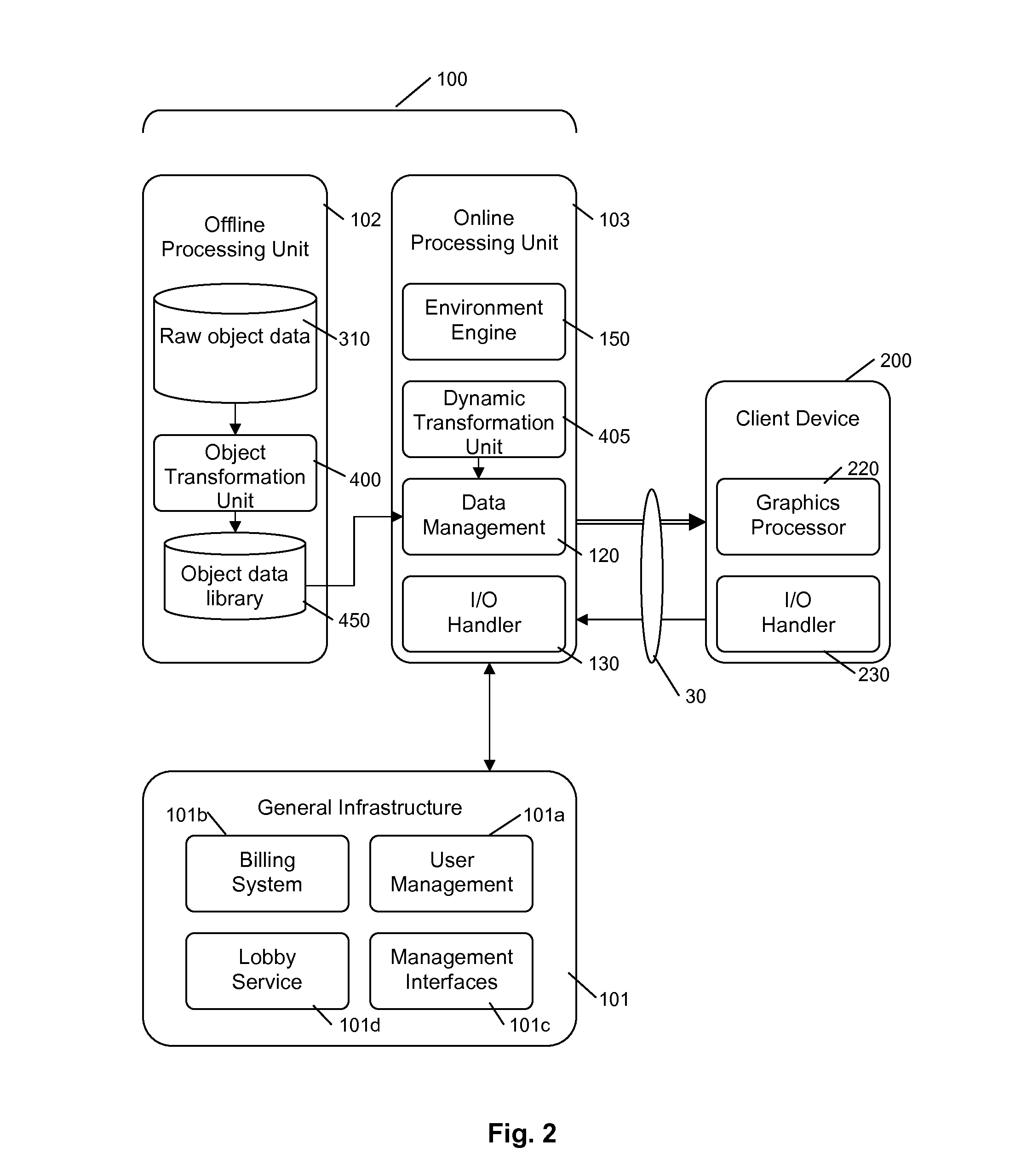
A multimedia content delivery system includes a server apparatus (100) for delivering graphical information across a network (30) to a client device (200). An environment engine (150) controls a virtual environment responsive to user commands. An object transformation unit (400, 405) transforms original object data (310) relating to a plurality of objects into compressed object data (350). A data management unit (120) transmits the compressed object data to the client device (200). The compressed object data (350) is decompressed and rendered by the client device (200) to output images to represent the virtual environment on a visual display device. Server-side and client side I / O handler units (130, 230) provide the user commands from the client device (200). The compressed object data (360) may comprise coefficients of a solution to a partial differential equation. Methods and apparatus are described relating to polygon-based object geometry (510) and pixel-based image files (600) which are transformed and regenerated using coefficients (540, 606) of a solution to a partial differential equation.
Owner:ANTI MATTER GAMES LTD
Image processing method, apparatus and storage medium
InactiveUS6879726B2Quality improvementTelevision system detailsCode conversionImaging processingTransformation unit
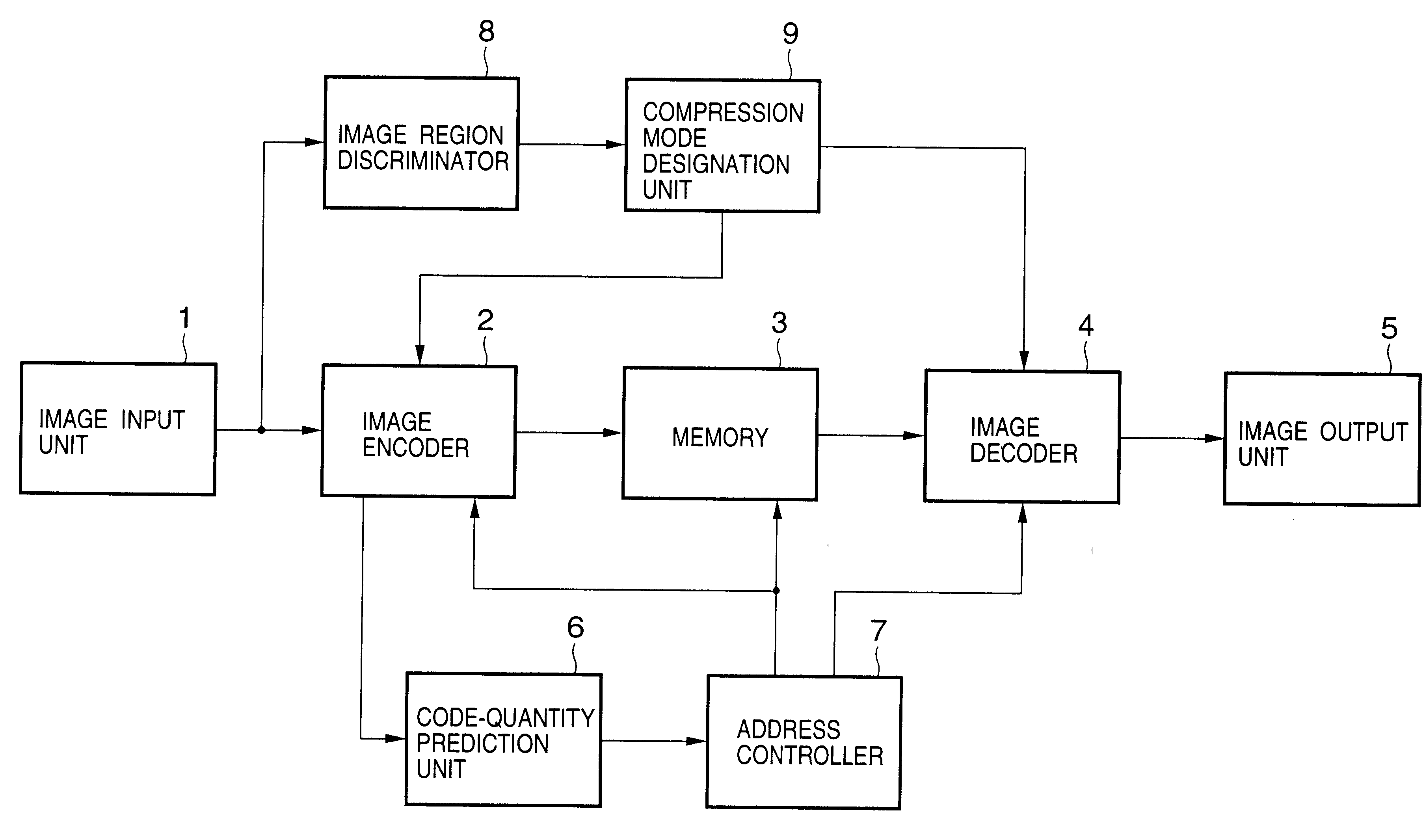
An image processing apparatus includes a wavelet transformation unit for wavelet-transforming input image data on a per-image basis, and an encoder for changing transformation coefficients, which have been obtained by the transformation, to bit planes from higher- to lower-order bits, and encoding the bit planes one bit plane at a time. A code-quantity prediction unit determines whether all encoded data of each of the image data that have been encoded can be stored in the memory when the encoded data obtained by the encoder is stored in the memory image by image. If all of the encoded data cannot be stored, the encoded data that overflows the memory is divided and the divided encoded data is stored in the memory by writing the divided encoded data equally over storage areas of the lower-order bit planes of each of the image.
Owner:CANON KK
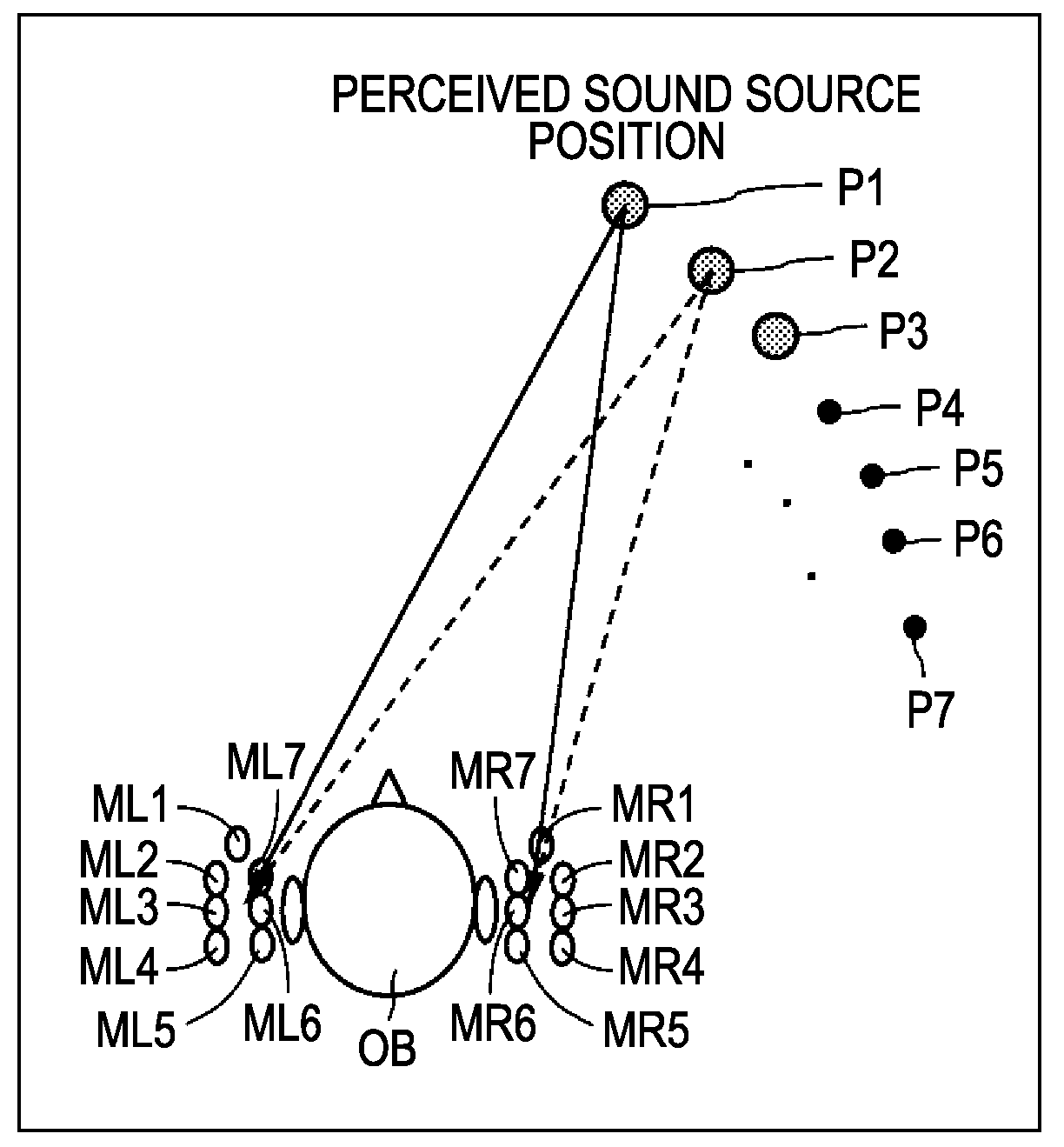
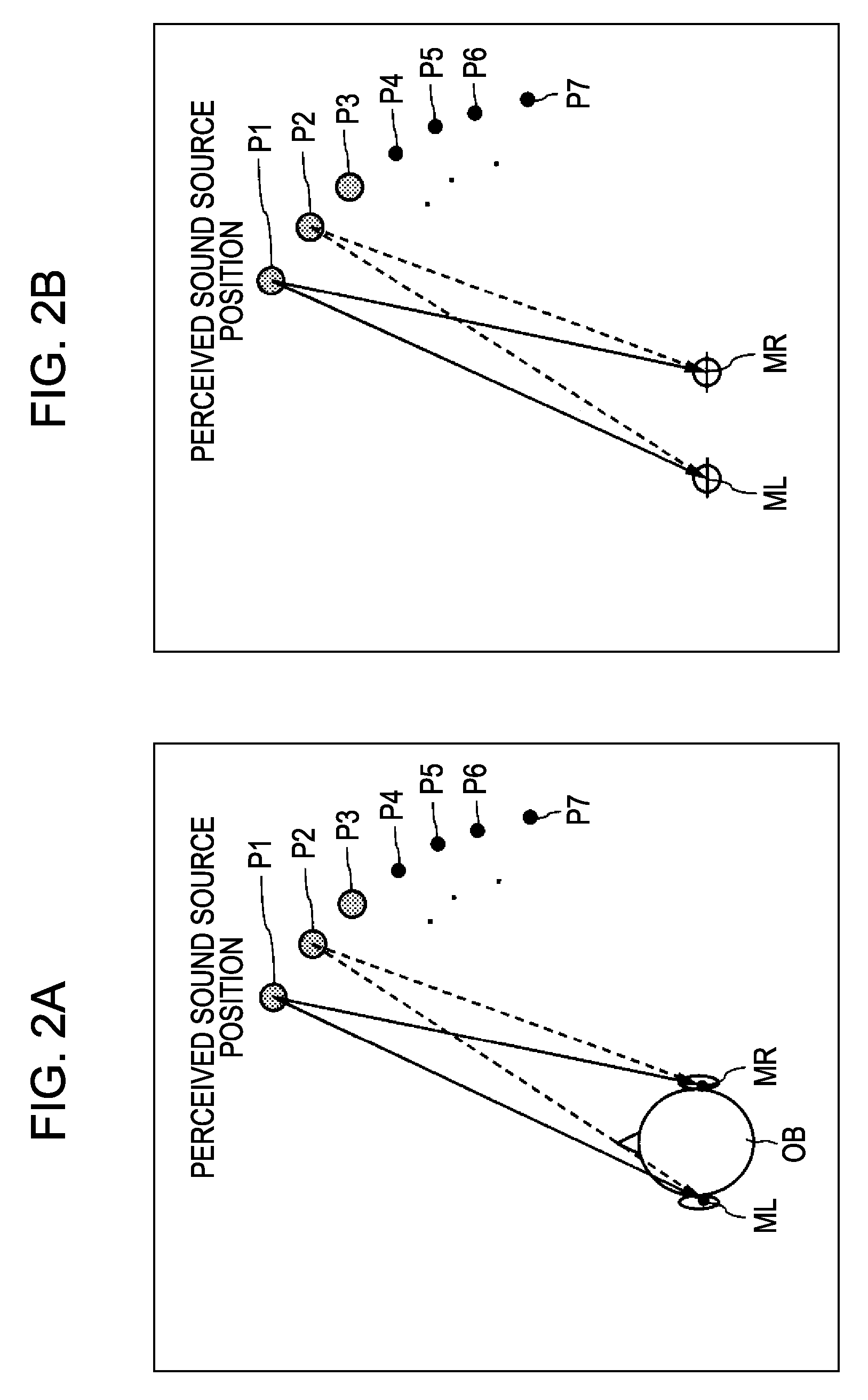
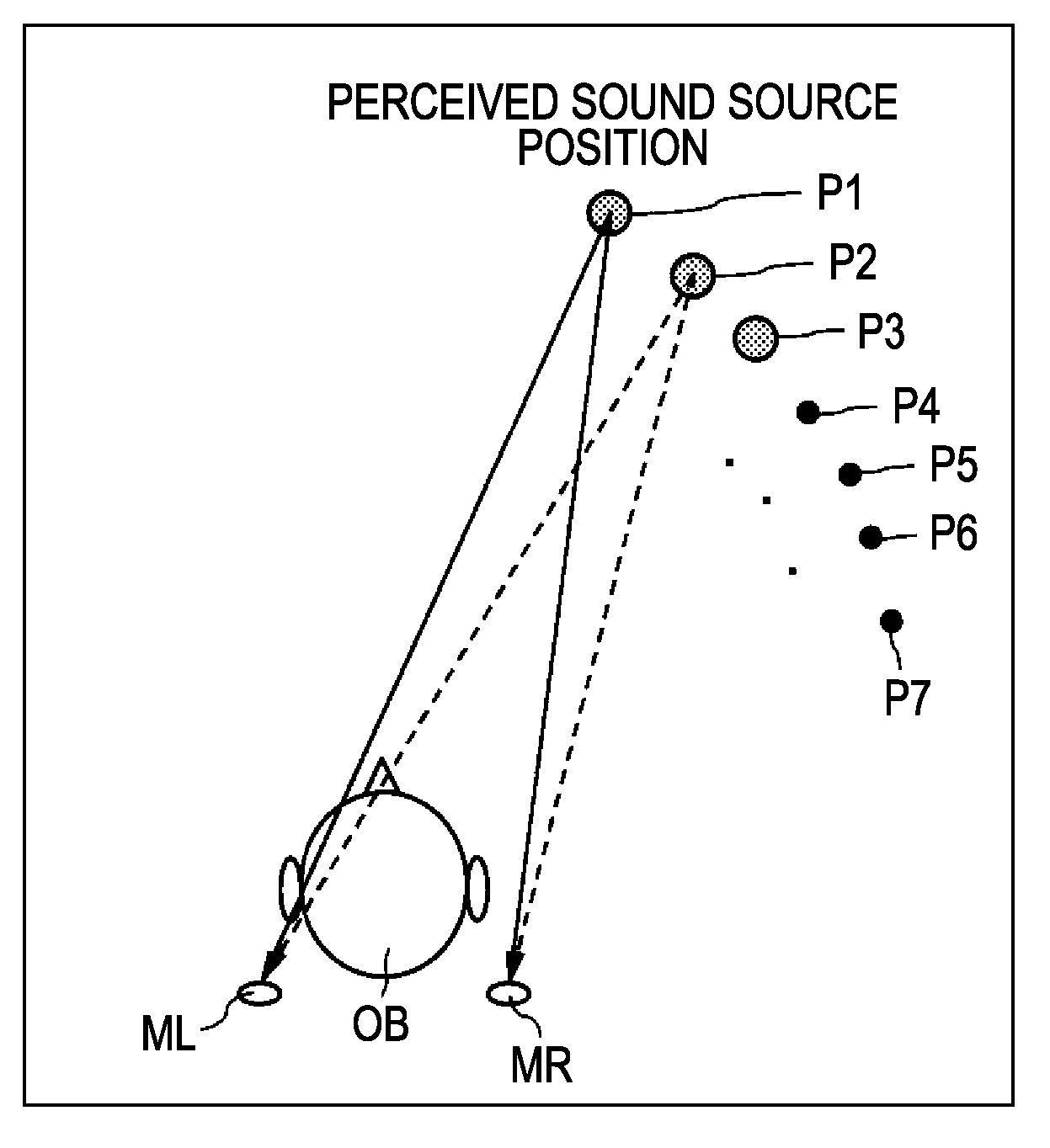
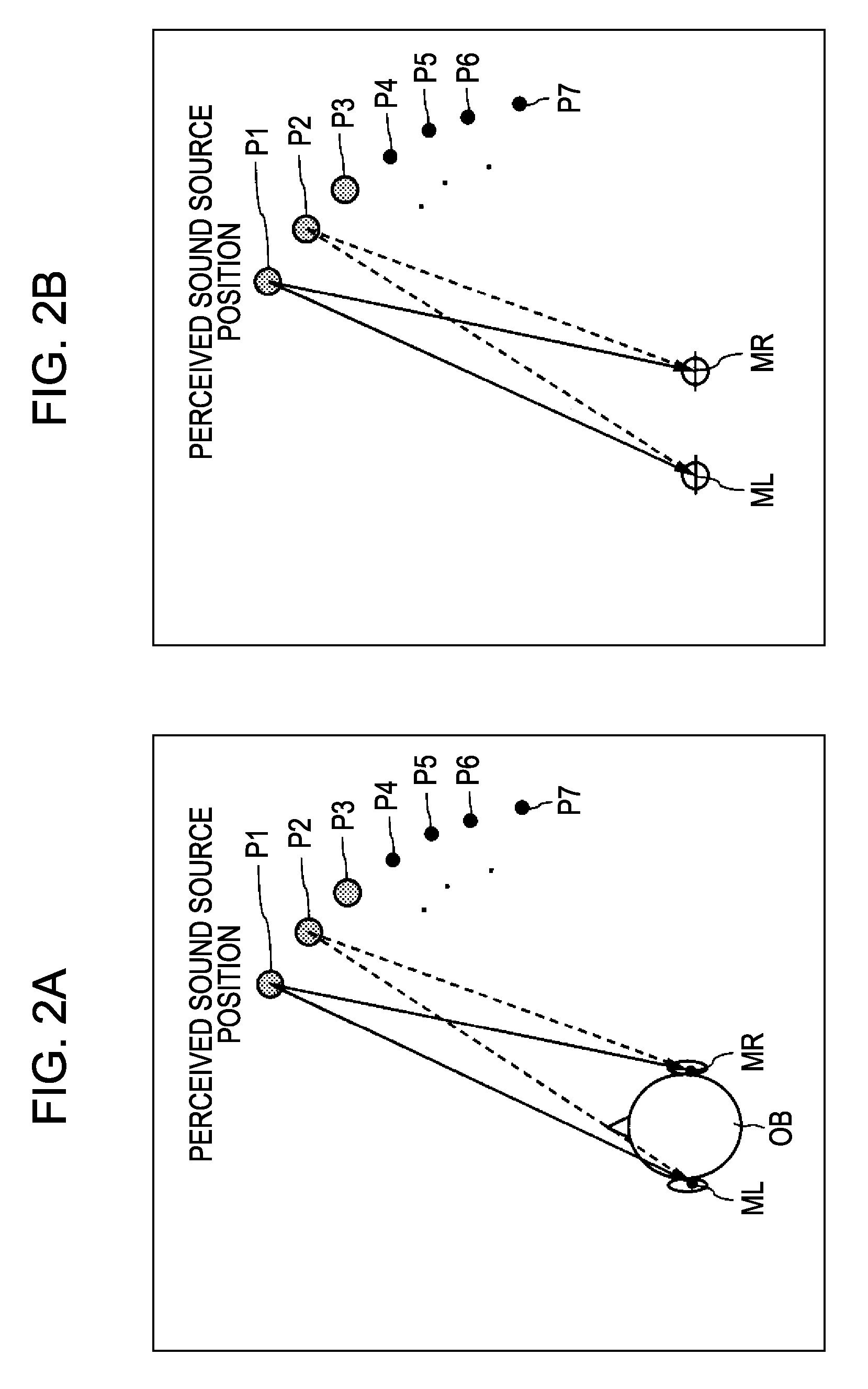
Head-related transfer function convolution method and head-related transfer function convolution device
A head-related transfer function (HRTF) convolution method arranged, when an audio signal is reproduced acoustically by an electro-acoustic conversion unit disposed in a nearby position of both ears of a listener, to convolute an HRTF into the audio signal, which allows the listener to listen to the audio signal such that a sound image is localized in a perceived virtual sound image localization position, the method including the steps of: measuring, when a sound source is disposed in the virtual sound image localization position, and a sound-collecting unit is disposed in the position of the electro-acoustic conversion unit, a direct-wave direction HRTF regarding the direction of a direct wave, and reflected-wave direction HRTFs regarding the directions of selected one or more reflected waves, from the sound source to the sound-collecting unit, separately beforehand; and convoluting the obtained direct-wave direction HRTF, and the reflected-wave direction HRTFs into the audio signal.
Owner:SONY CORP
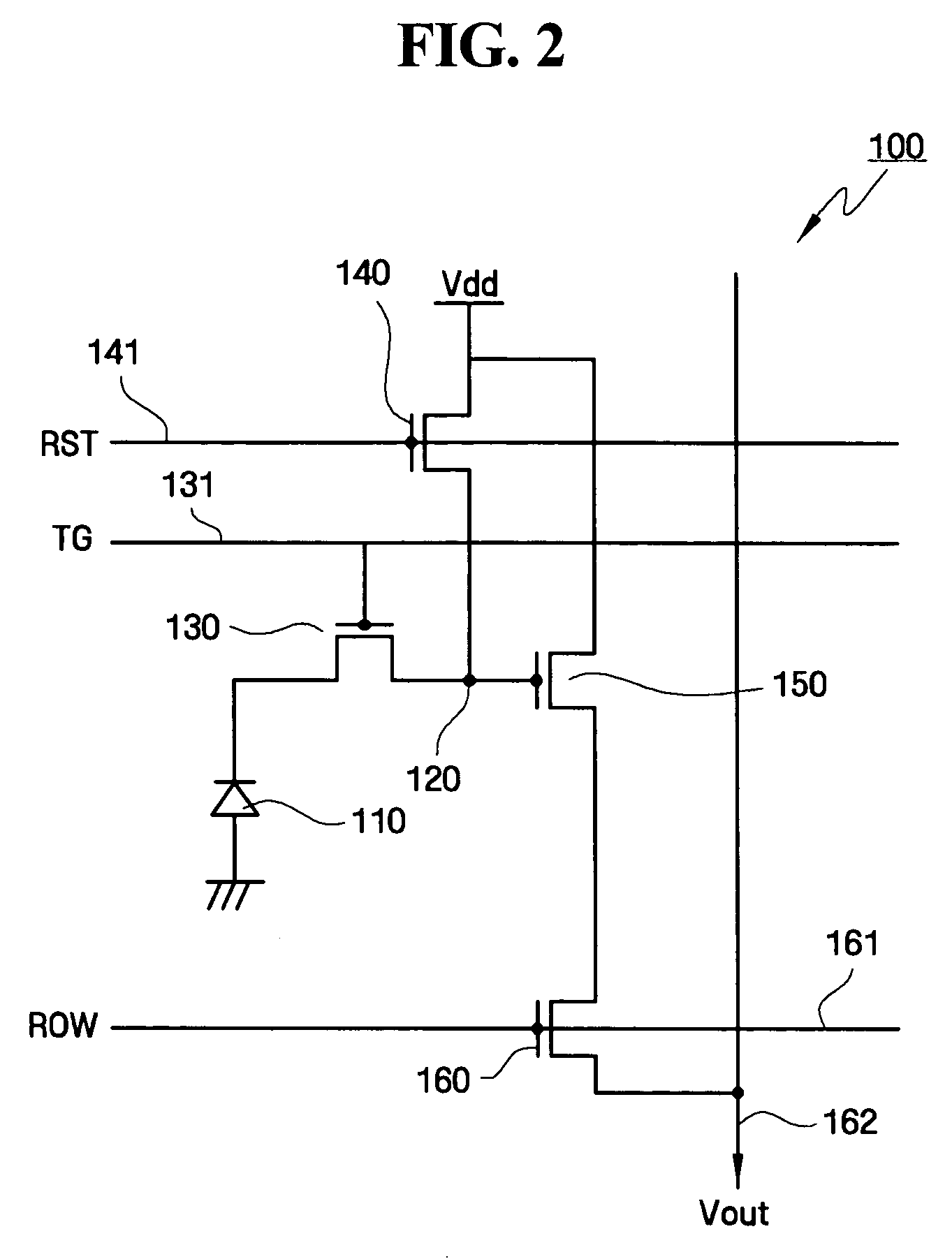
Image sensor and method of fabricating the same
InactiveUS20070153337A1Decrease pixel crosstalkDecrease and prevent pixel crosstalkSolid-state devicesRadiation controlled devicesEngineeringTransformation unit
An example embodiment is directed to an image sensor including a photoelectric transformation unit, an opening formed above the photoelectric transformation unit, and a barrier layer on a side surface of the opening to prevent or reduce crosstalk. The photoelectric transformation unit may be in a semiconductor substrate, and an interlayer insulating layer may cover a surface of the semiconductor substrate. A light transmission unit may fill the opening, and a color filter and a micro-lens on the color filter may be on top of the light transmission unit.
Owner:SAMSUNG ELECTRONICS CO LTD
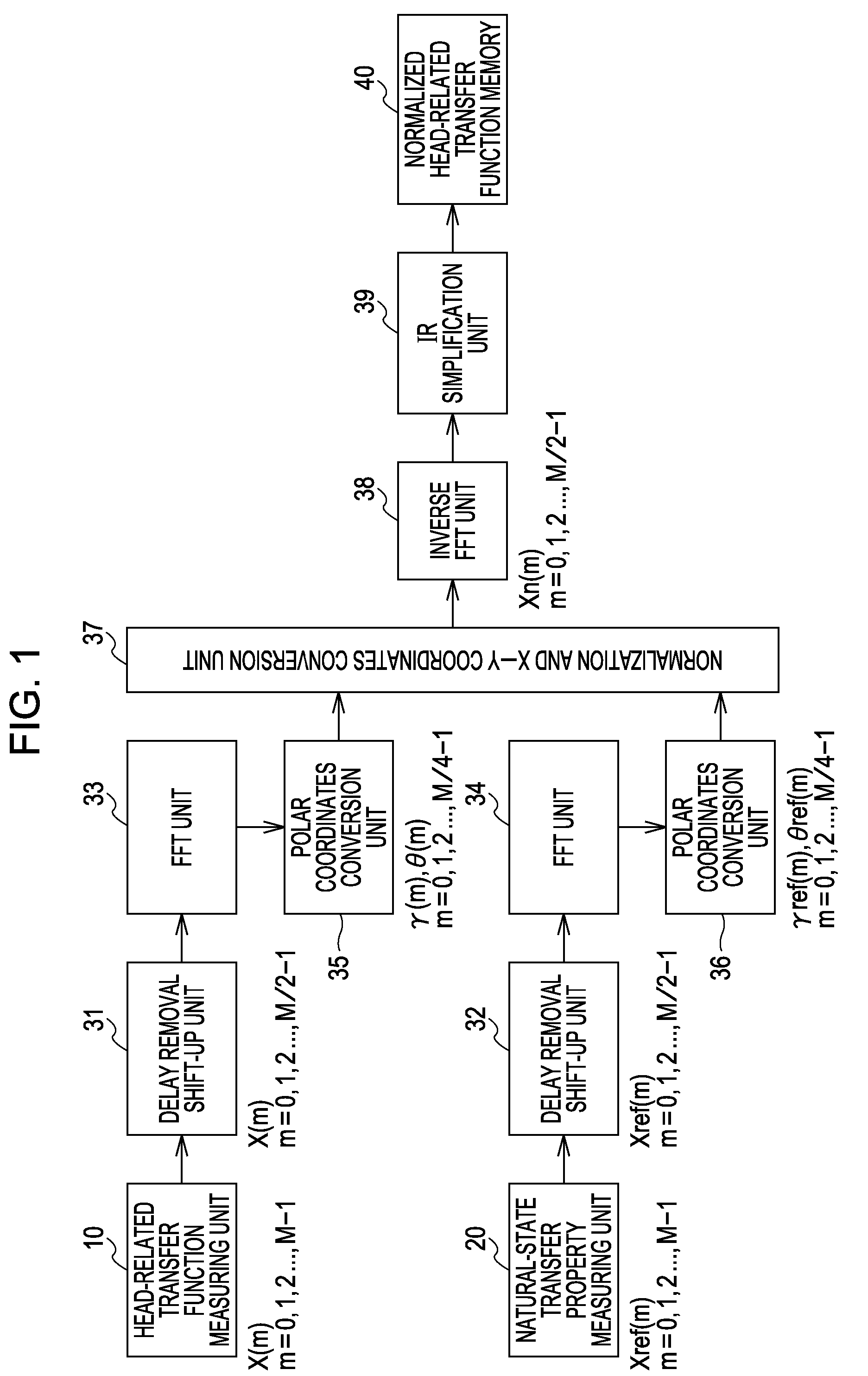
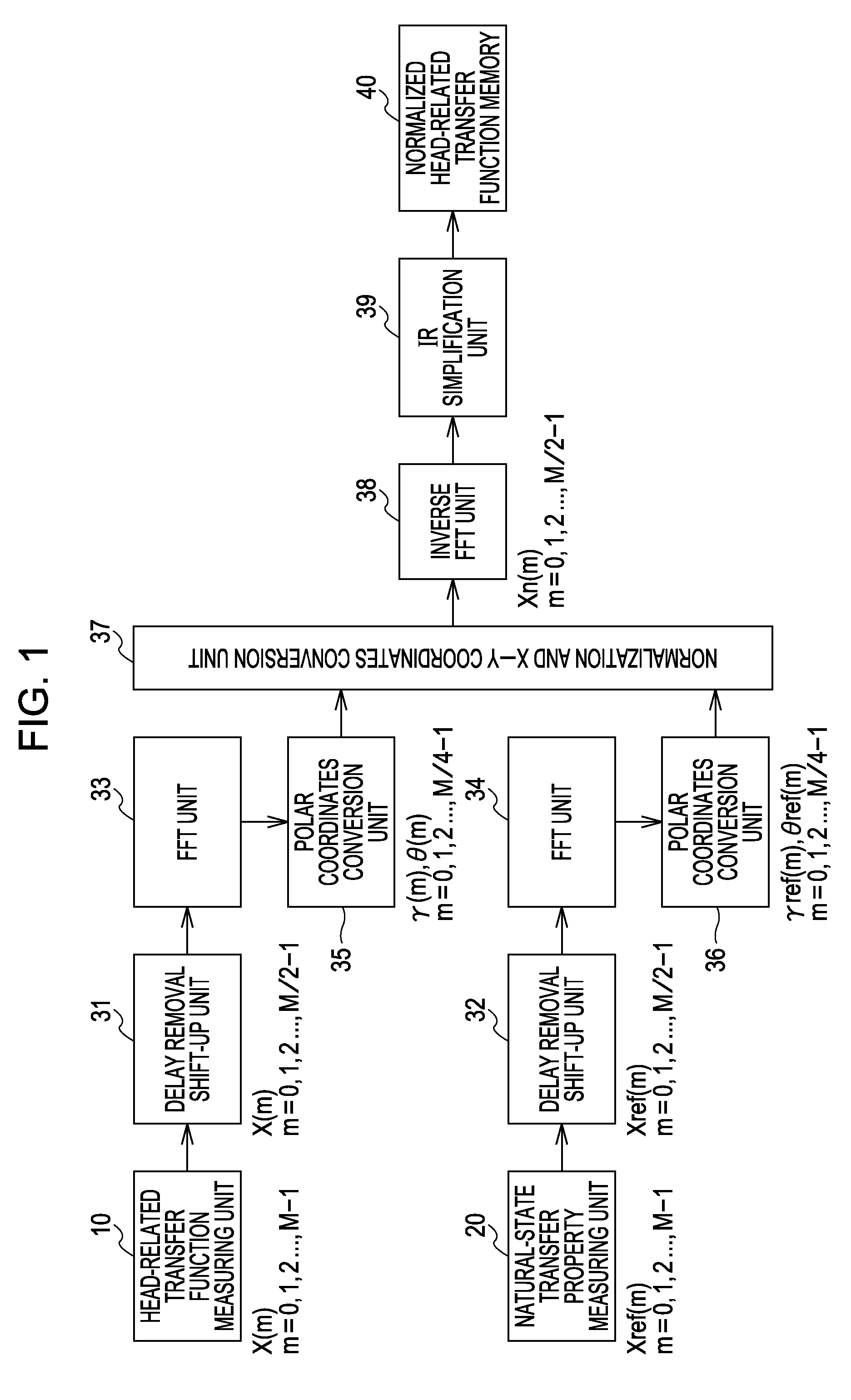
Head-related transfer function measurement method, head-related transfer function convolution method, and head-related transfer function convolution device
ActiveUS20090208022A1Headphones for stereophonic communicationSpeech analysisElectricitySound sources
A head-related transfer function measurement method includes the steps of: first measuring, including placing an acousto-electric conversion unit nearby both ears of a listener where placement of an electro-acoustic conversion unit is assumed, picking up sound waves emitted at a perceived sound source position with the acousto-electric conversion unit in a state with a dummy head or a human at the listener position, and measuring a head-related transfer function from only the sound waves directly reaching the acousto-electric conversion unit; second measuring, including picking up sound waves emitted at a perceived sound source position with the acousto-electric conversion unit, with no dummy head or human at the listener position, and measuring a natural-state transfer property from only the sound waves directly reaching the acousto-electric conversion unit; normalizing the head-related transfer function with the natural-state transfer property to obtain a normalized head-related transfer function; which is stored in a storage unit.
Owner:SONY CORP
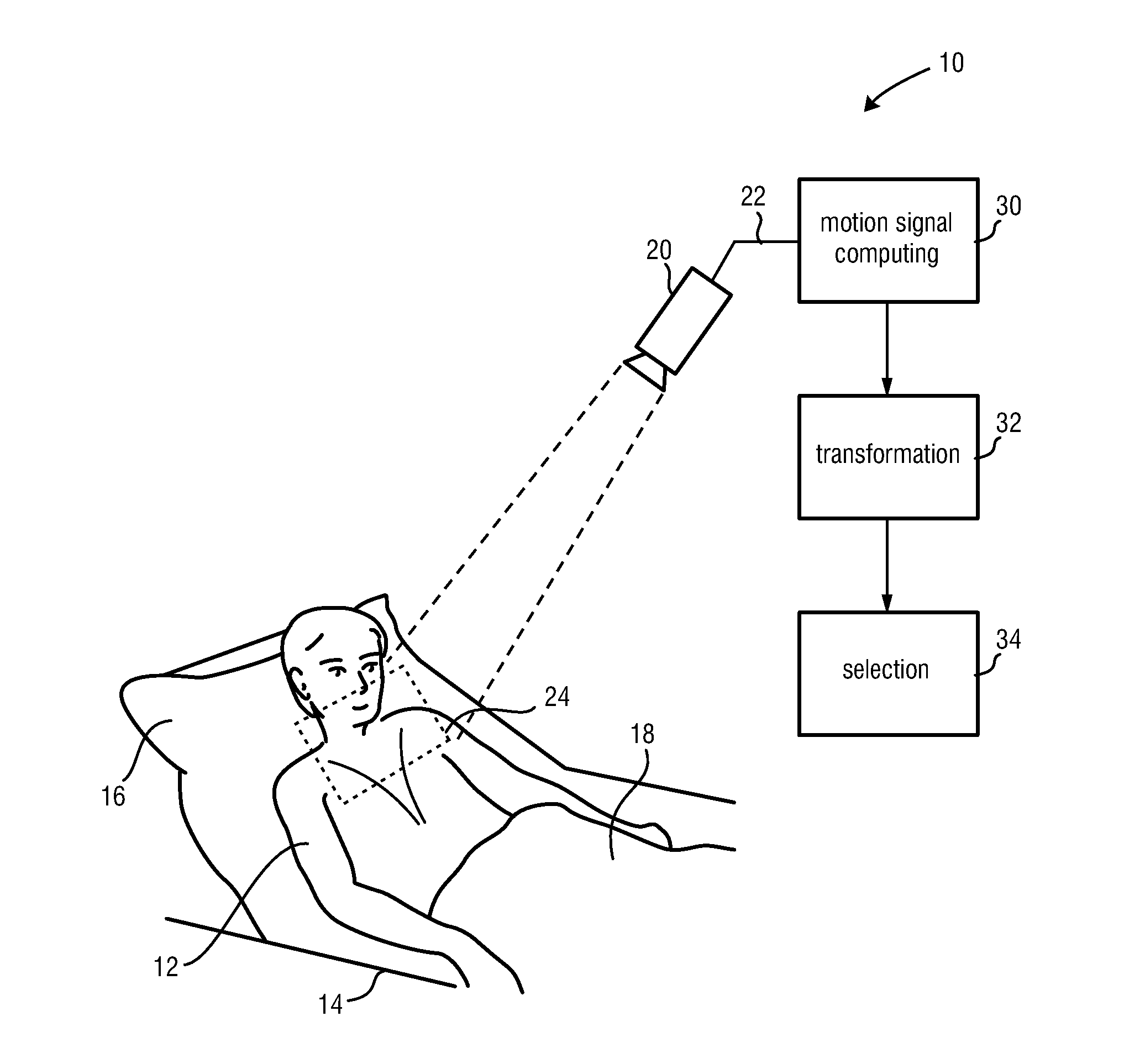
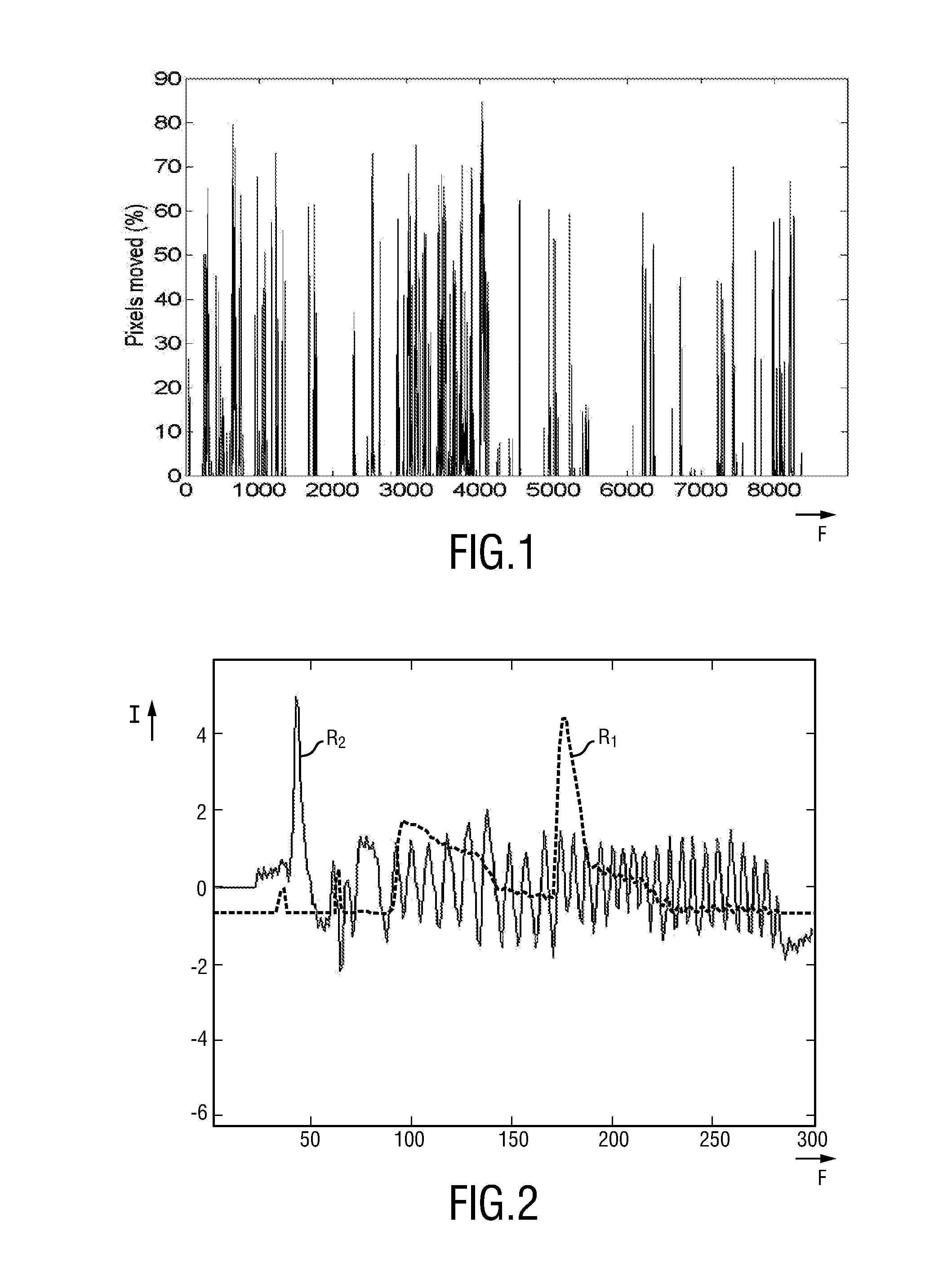
Device for obtaining respiratory information of a subject
InactiveUS20140236036A1High accuracy and robustnessReliable and accurate informationImage enhancementMedical imagingIndependent motionTransformation unit
A device and method for reliably and accurately obtaining respiratory information of a subject despite motion of the subject are disclosed. The proposed device comprises a motion signal computing unit for computing a number M of motion signals for a plurality of pixels and / or groups of pixels of at least a region of interest for a number N of image frames of a subject, a transformation unit for computing, for some or all M motion signals, a number of source signals representing independent motions within said images by applying a transformation to the respective motion signals to obtain source signals representing independent motions within said N image frames, and a selection unit for selecting a source signal from among said computed source signals representing respiration of said subject by examining one or more properties of said source signals for some or all of said computed source signals.
Owner:KONINKLJIJKE PHILIPS NV
Method and apparatus for scalable video encoding and decoding
InactiveUS20050117640A1Color television with pulse code modulationPulse modulation television signal transmissionComputer graphics (images)Video encoding
Disclosed is a scalable video coding algorithm. A method for video coding includes temporally filtering frames in the same sequence to a decoding sequence thereof to remove temporal redundancy, obtaining and quantizing transformation coefficients from frames whose temporal redundancy is removed, and generating bitstreams. A video encoder comprises a temporal transformation unit, a spatial transformation unit, a quantization unit and a bitstream generation unit to perform the method. A method for video decoding is basically reverse in sequence to the video coding. A video decoder extracts information necessary for video decoding by interpreting the received bitstream and decoding it. Thus, video streams may be generated by allowing a decoder to decode the generated bitstreams, while maintaining the temporal scalability on an encoder-side.
Owner:SAMSUNG ELECTRONICS CO LTD
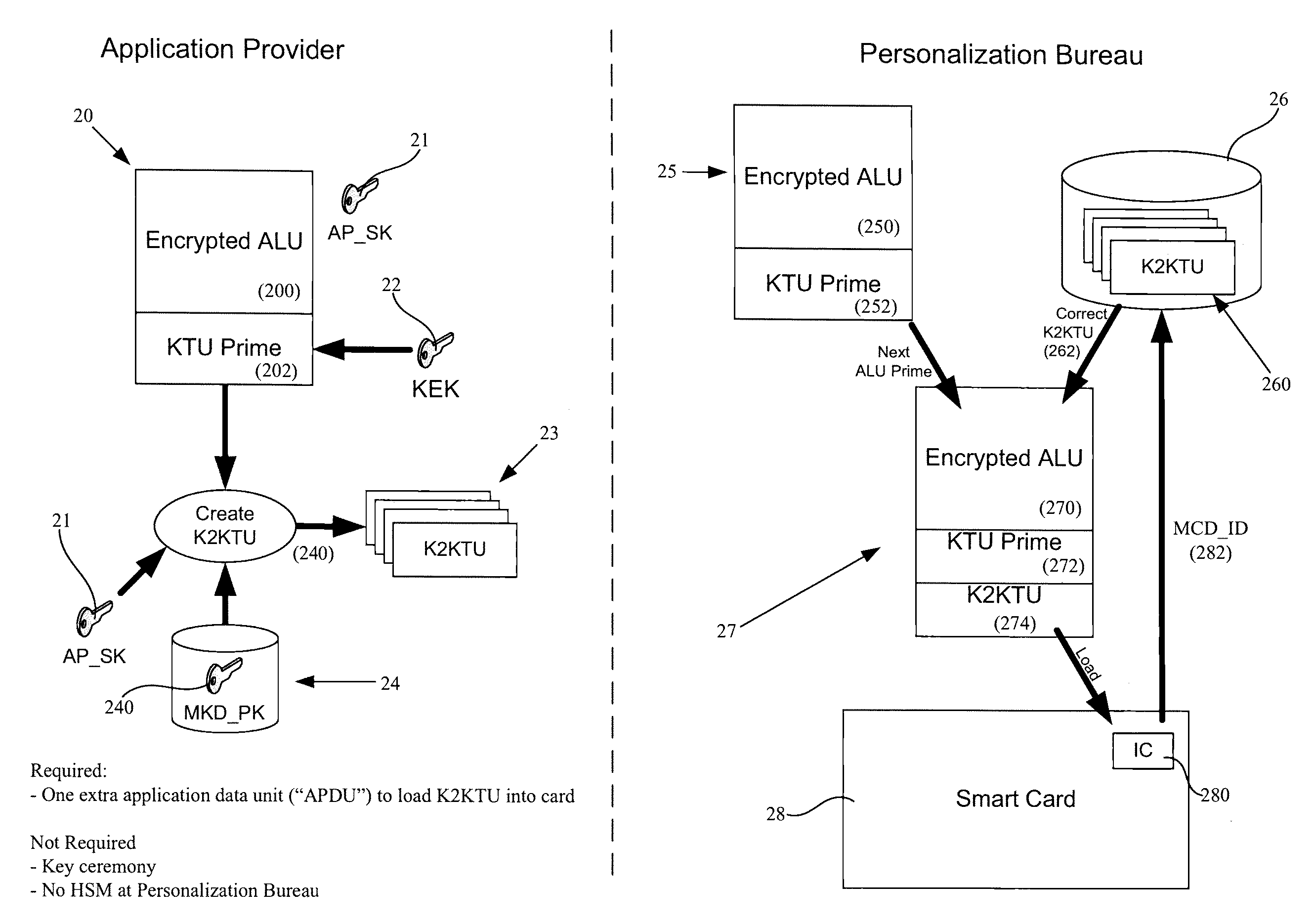
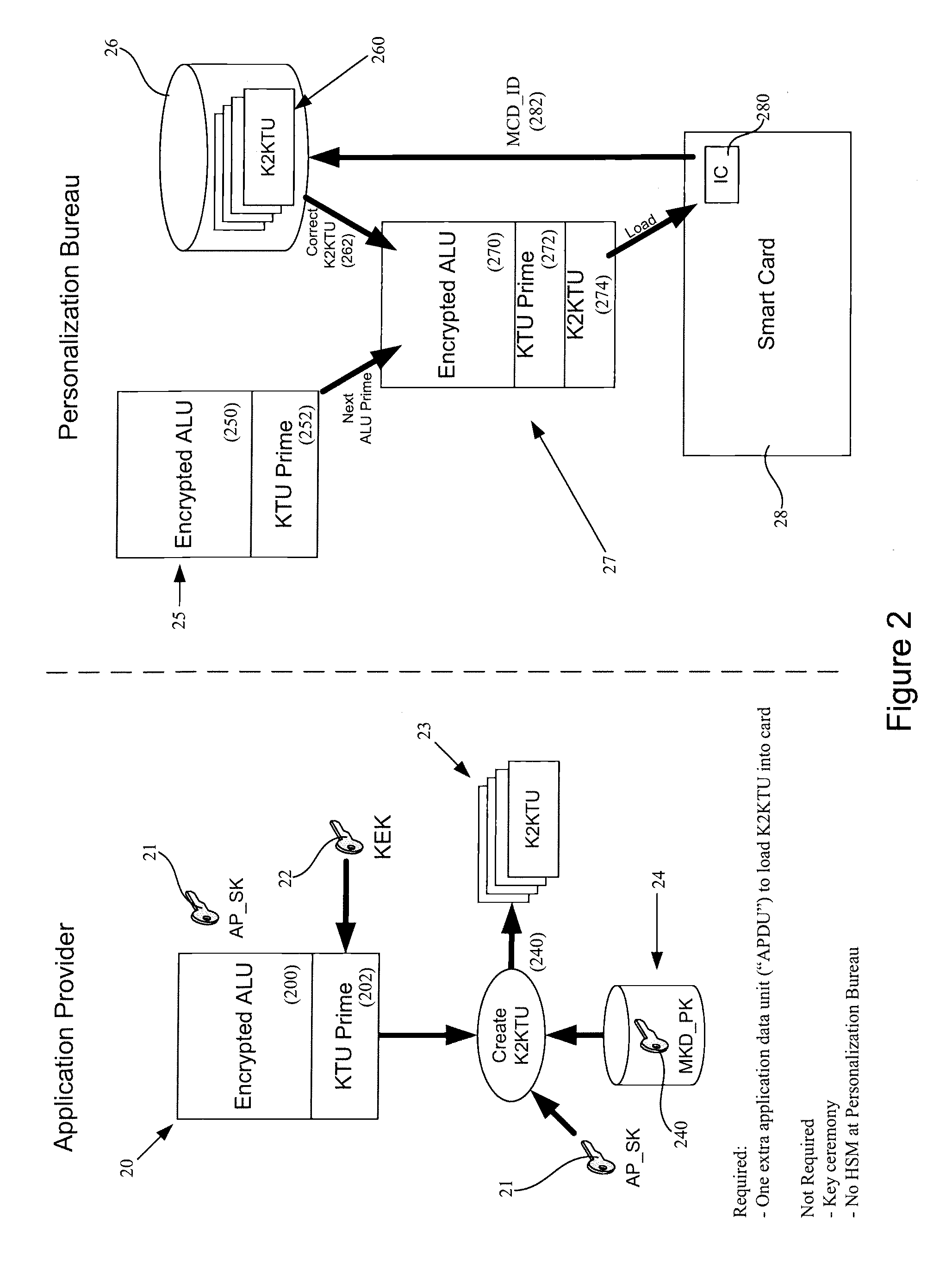
Methods and systems for IC card application loading
Systems and methods are described that provide a new type of application load unit for use in the secure loading of applications and / or data onto integrated circuit cards or smart cards. Plaintext key transformation units can be created for each of a plurality of smart cards that are to be loaded with a desired or selected application. A plaintext key transformation unit may be individually encrypted using the public keys associated with target smart cards. An application provider can create one or more application load unit using known means and can then create one or more additional plaintext key transformation unit, one for each target smart card using corresponding public keys which can be obtained taken from a database of card public keys.
Owner:MULTOS
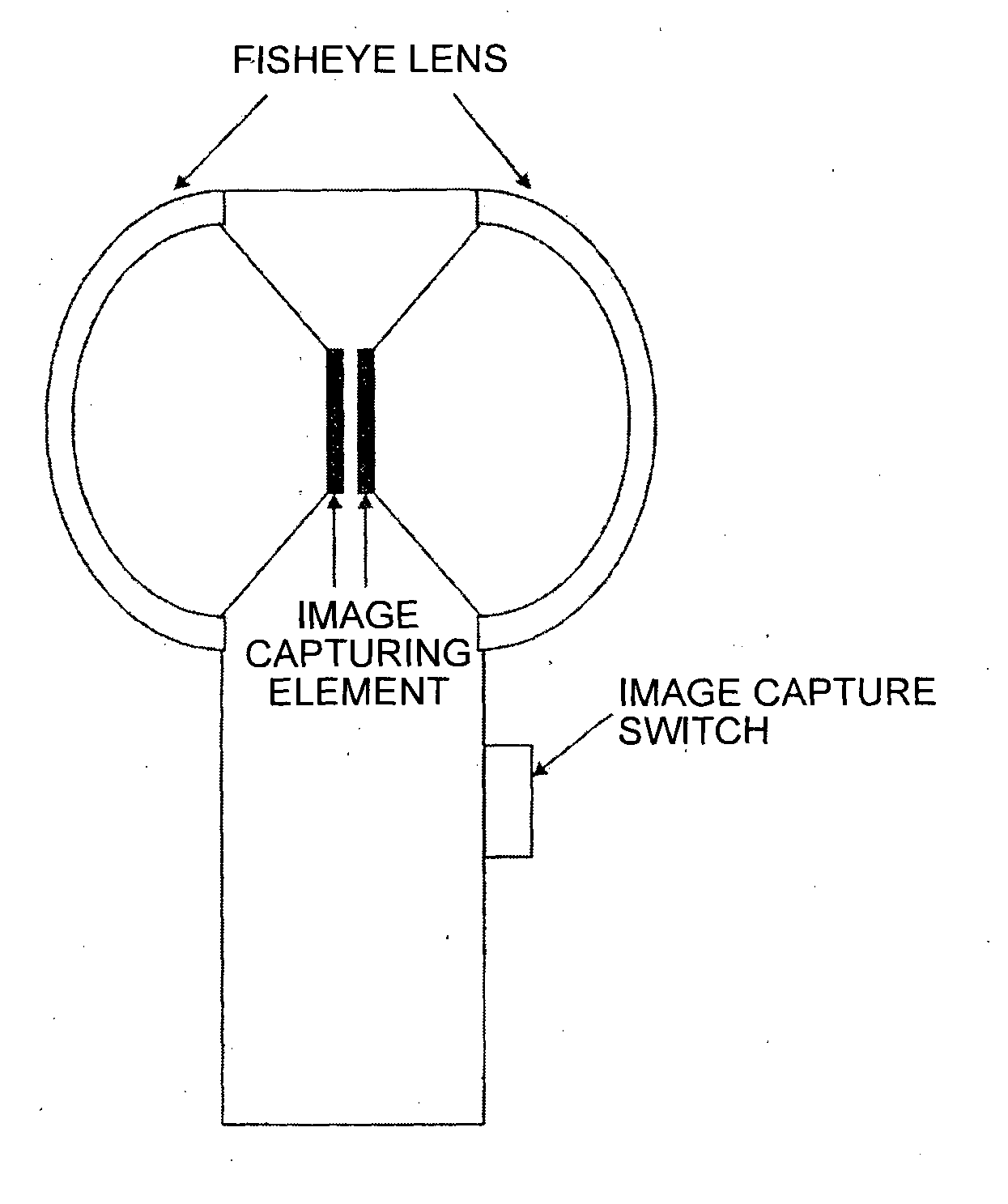
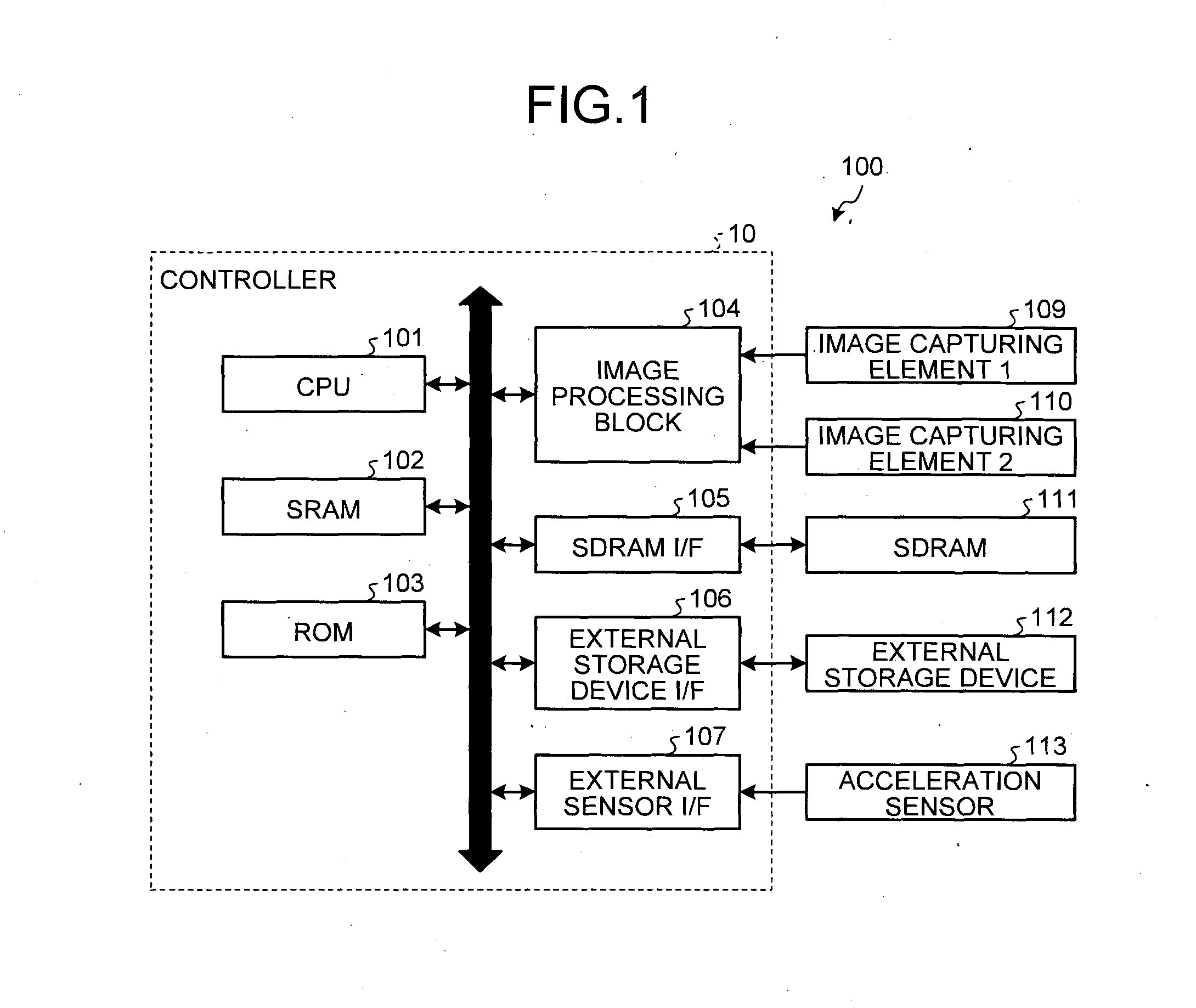
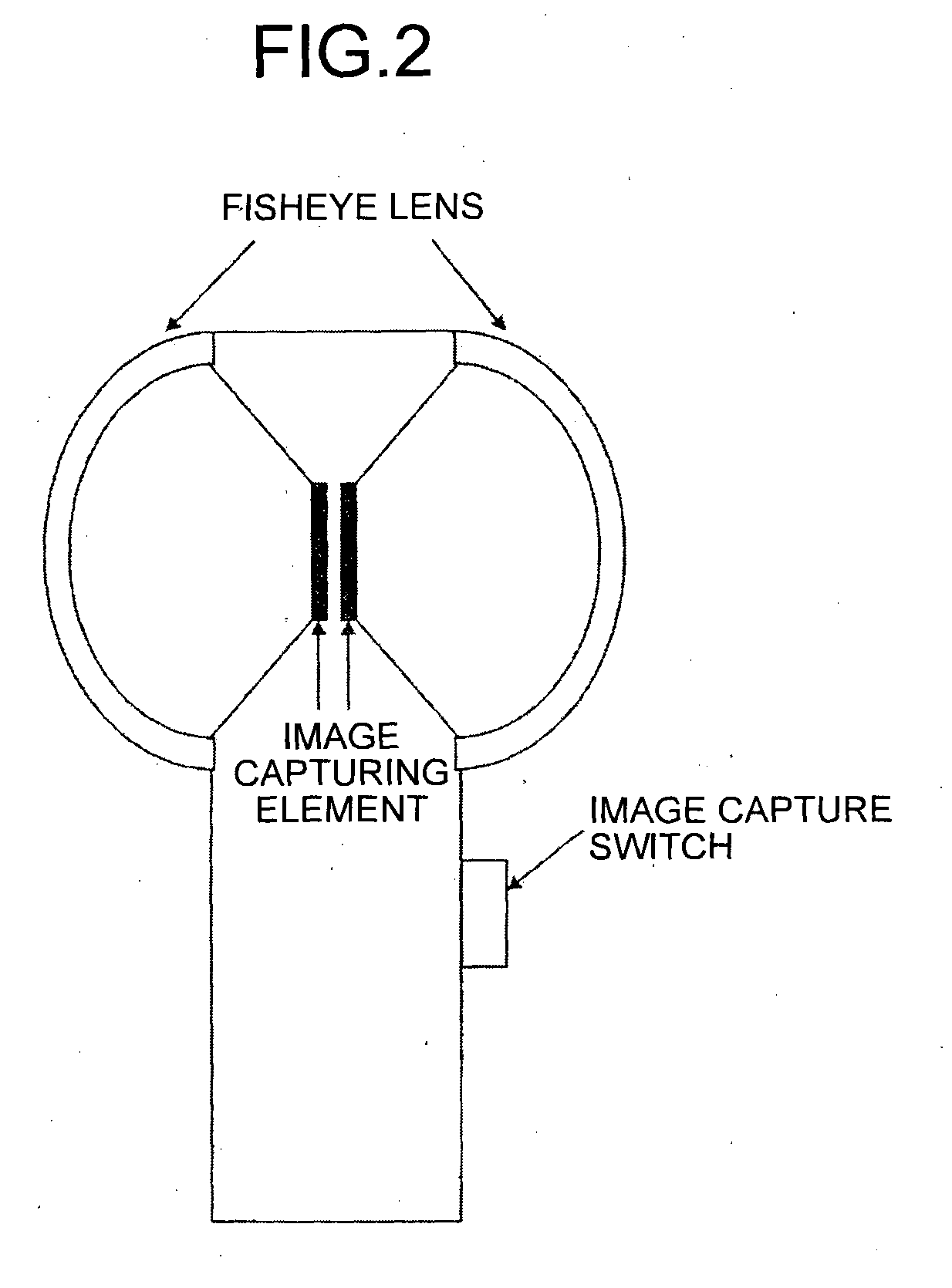
Image capturing apparatus, image capture system, image processing method, information processing apparatus, and computer-readable storage medium
ActiveUS20150062363A1Solve problemsTelevision system detailsGeometric image transformationInformation processingImaging processing
An image capturing apparatus includes a tilt detection unit that detects a tilt in the vertical direction, conversion data used for transforming plane coordinates into spherical coordinates, a correction unit that corrects the conversion data according to the tilt, a plurality of image capturing units, a coordinate transformation unit that transforms plane coordinates of a plurality of pixels included in images captured by the image capturing units into spherical coordinates according to the conversion data corrected by the correction unit, and a combining unit that combines the images including the pixels transformed into spherical coordinates by the coordinate transformation unit.
Owner:RICOH KK
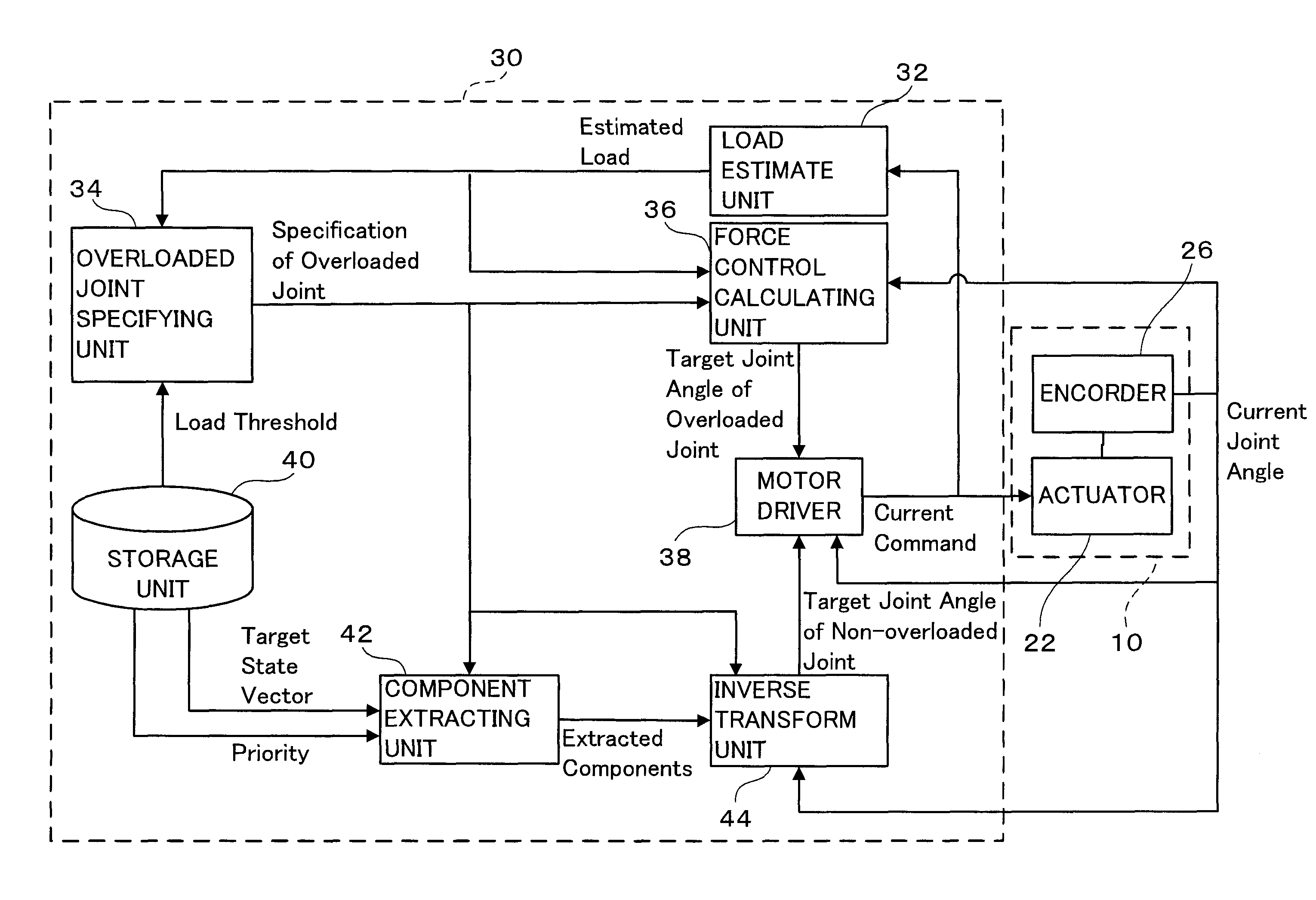
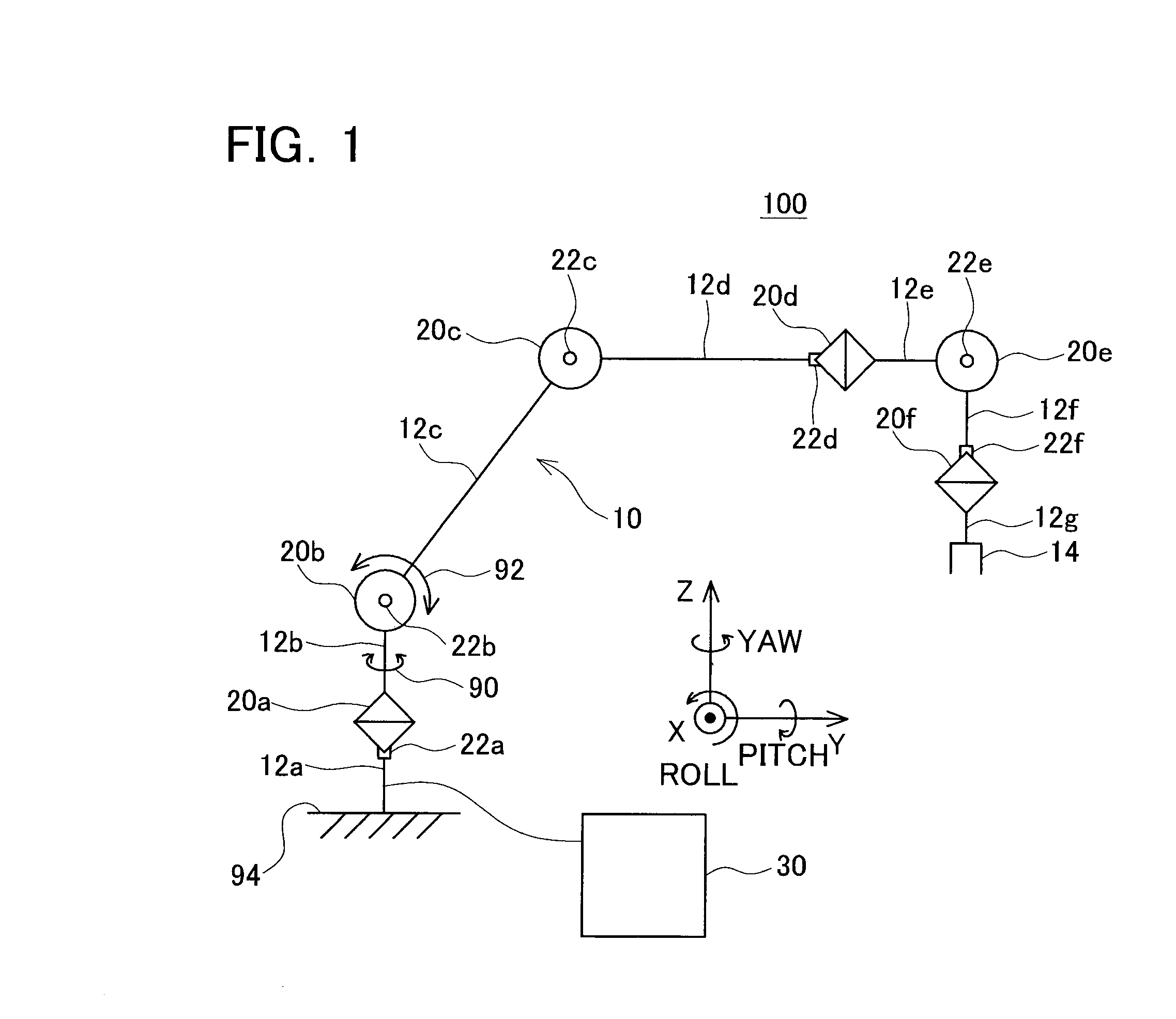
Multi-joint robot and control program thereof
InactiveUS20100234999A1Easing overloaded stateFollow exactlyProgramme controlProgramme-controlled manipulatorTransformation unitArthrobotrys
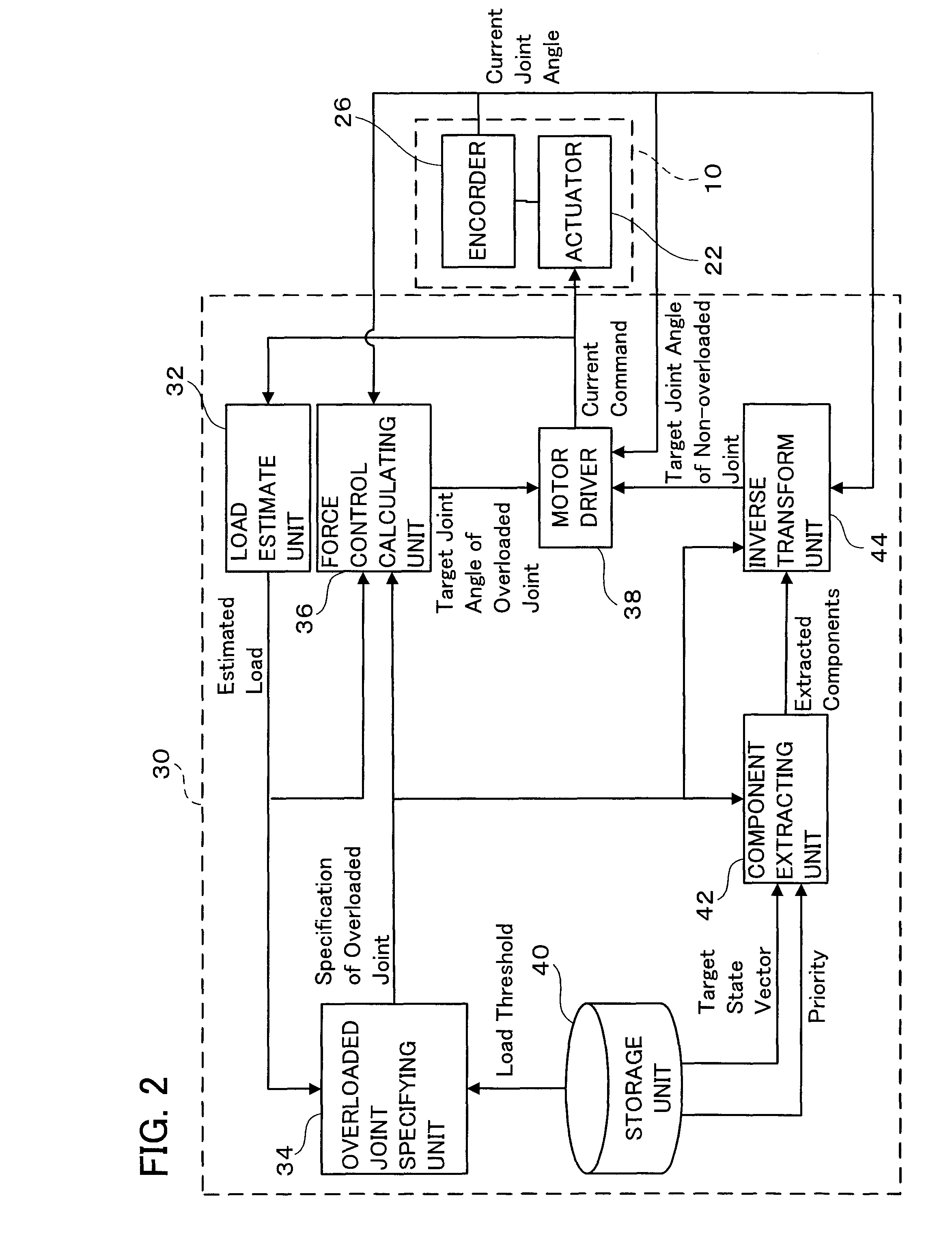
The present invention provides a multi-joint robot that, when the loads acting on some of joints are overloaded, controls the joints so as to continue the work as far as possible while easing the overloaded state. The load estimate unit (32) estimates the load acting on each joint, and the overloaded joint specifying unit (34) specifies an overloaded joint of which the estimated load is greater than a threshold. The storage unit (40) stores a target state vector of an end link of the robot and stores a predetermined priority with respect to the components of the vector. The component extracting unit (42) extracts the same number of components as that of non-overloaded joints from the target state vector in order of a higher priority. The force control calculating unit (36) determines the target drive quantity for driving the overloaded joint in the same direction as that of the load. The inverse transformation unit determines the target drive quantities with respect to the non-overloaded joints so as to realize the extracted components. Thus, the non-overloaded joints can be controlled so as to follow the target state vector as far as possible, while the overloaded joints are controlled in a direction to reduce the load.
Owner:TOYOTA JIDOSHA KK
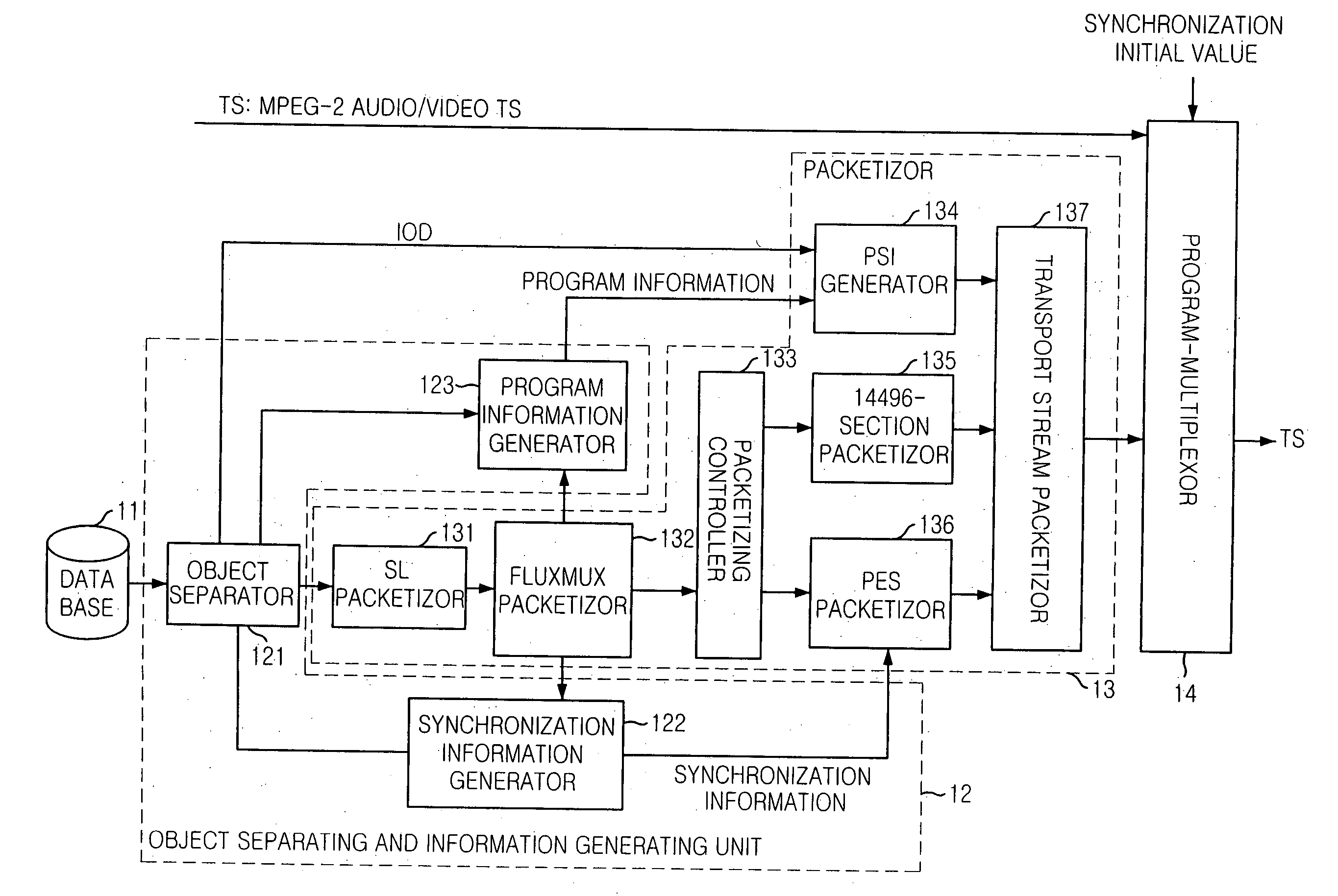
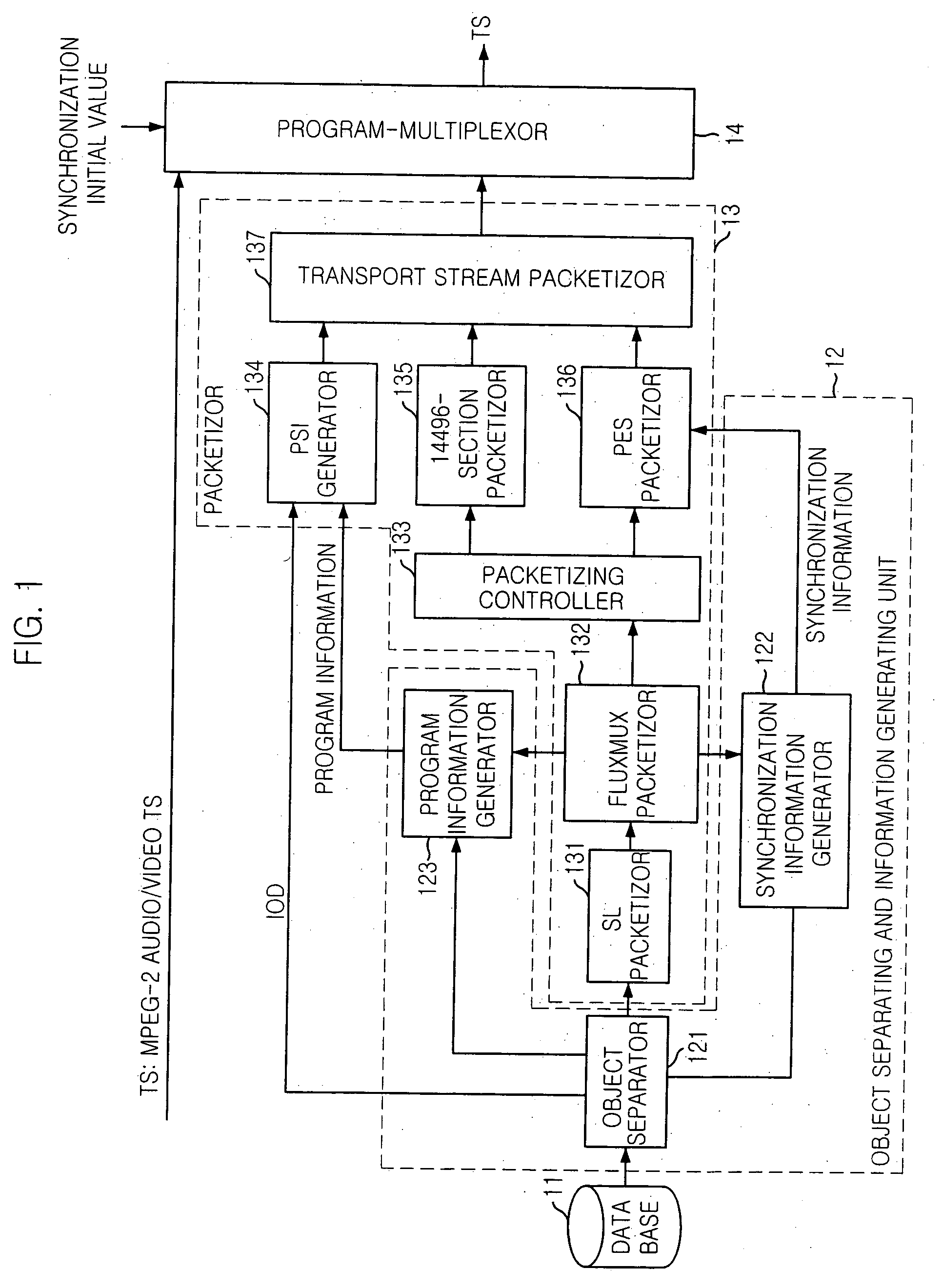
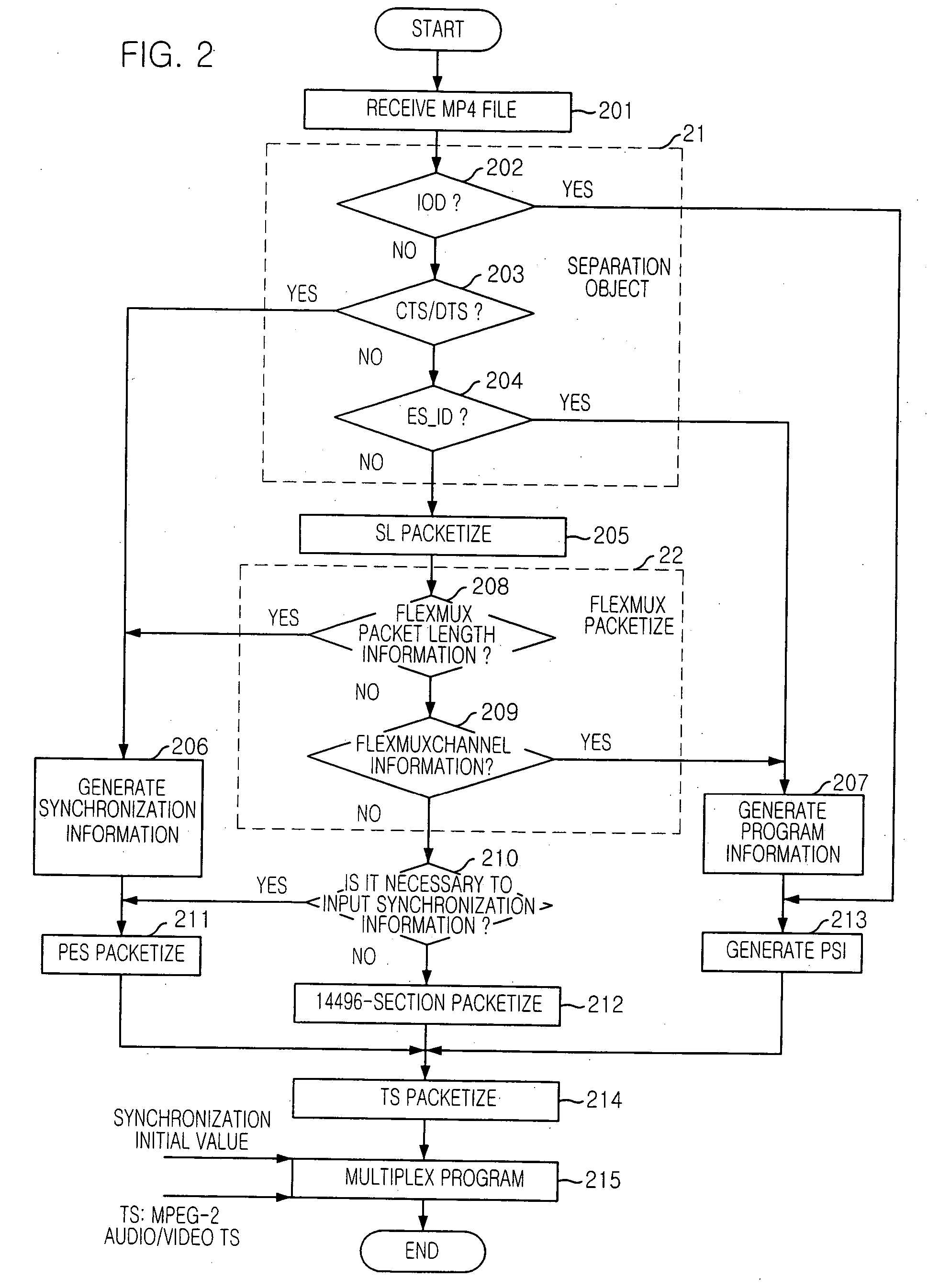
Apparatus and method for transmitting mpeg-4 data synchronized with mpeg-2 data
An apparatus and method for transmitting MPEG-4 data synchronized to MPEG-2 data is disclosed. The apparatus for transmitting MPEG-4 data synchronized to MPEG-2 data includes: an object separation unit for extracting MPEG-4 object data from MP4 data, separating meta information from the object data, and generating program information and synchronization information; a conversion unit for converting the MPEG-4 object data to MPEG-4 packets of which data structure is the same as that of MPEG-2 data, based on the program information and synchronization information; and a multiplexing unit for multiplexing the MPEG-4 packets with the MPEG-2 data.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com