Patents
Literature
203results about How to "Implement interception" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
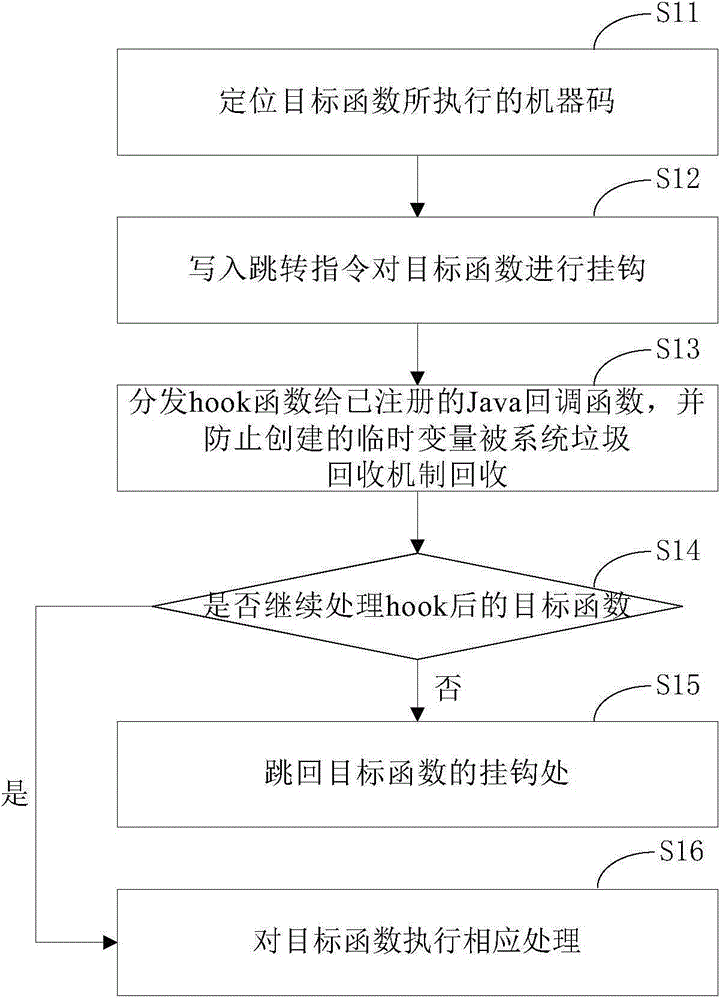
Program monitoring method and defending method thereof, as well as relevant device
ActiveCN104598809AHook implementationAvoid markingPlatform integrity maintainanceTemporary variableProgram monitoring
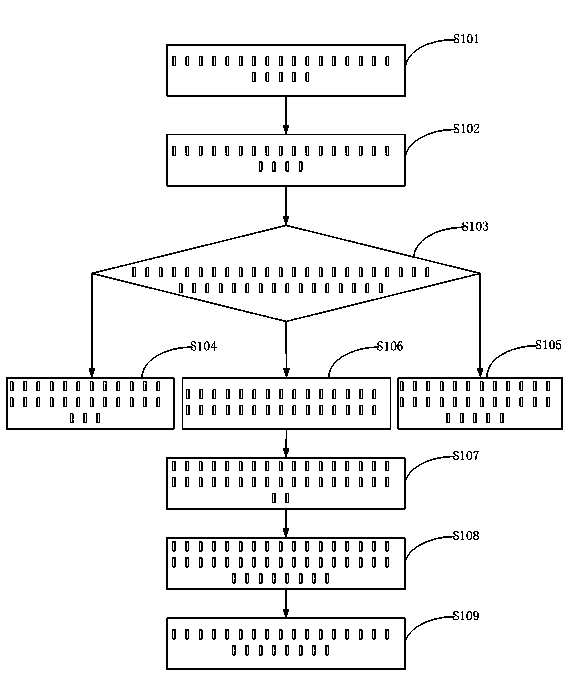
The invention provides a program monitoring method and device. The program monitoring method comprises the following steps: writing in a skip instruction for positioned objective functions so as to perform a hook operation; distributing hook functions to registered Java callback functions, and preventing created temporary variables from being collected by a garbage collection mechanism of a system; enabling the objective functions which are not processed to skip back to hook positions, or else, continuing to process the objective functions. Through the adoption of the program monitoring method disclosed by the invention, any Java function of an Android system under an ART mode can be monitored without destroying the stack of the objective functions, so that the garbage collection mechanism of the ART can perform normal memory collection. The invention further provides a program defending method and device, which realize a defending mechanism of the Android system under the ART mode by adopting the program monitoring method disclosed by the invention.
Owner:BEIJING QIHOO TECH CO LTD
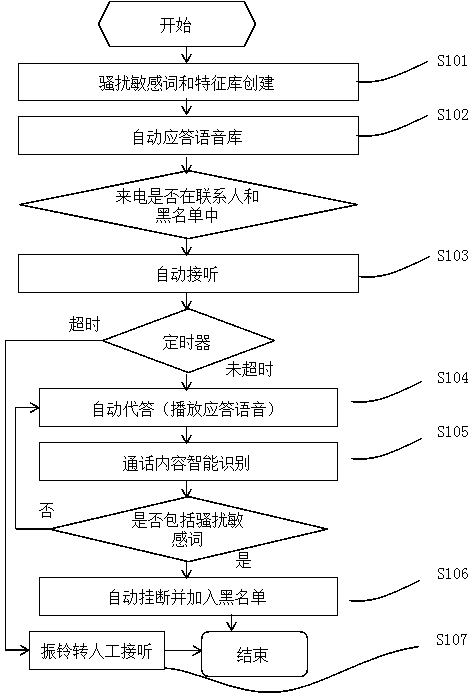
Crank call preventing mobile phone achieving method based on conversation content
InactiveCN104184872AEasy to detectImplement interceptionSubstation equipmentTelecommunicationsMobile phone
The invention discloses a crank call preventing mobile phone achieving method based on conversation content. The technology of auto-answering at the forepart of calling, the intelligent crank call sensitive word recognizing technology, the intelligent sensitive word feature matching technology, the automatic crank call hanging up and recording technology, the non-crank-call manual switching over reminding technology and other key technologies are adopted, the crank call detection and interception at the conversation stage are achieved, the accurate crank call defense based on the true conversation content is achieved, the single mode that traditionally, whether the phone call is the crank call or not is judged only based on the phone number before conversation is avoided, and an accurate and efficient crank call preventing effect is achieved.
Owner:陈桂芳
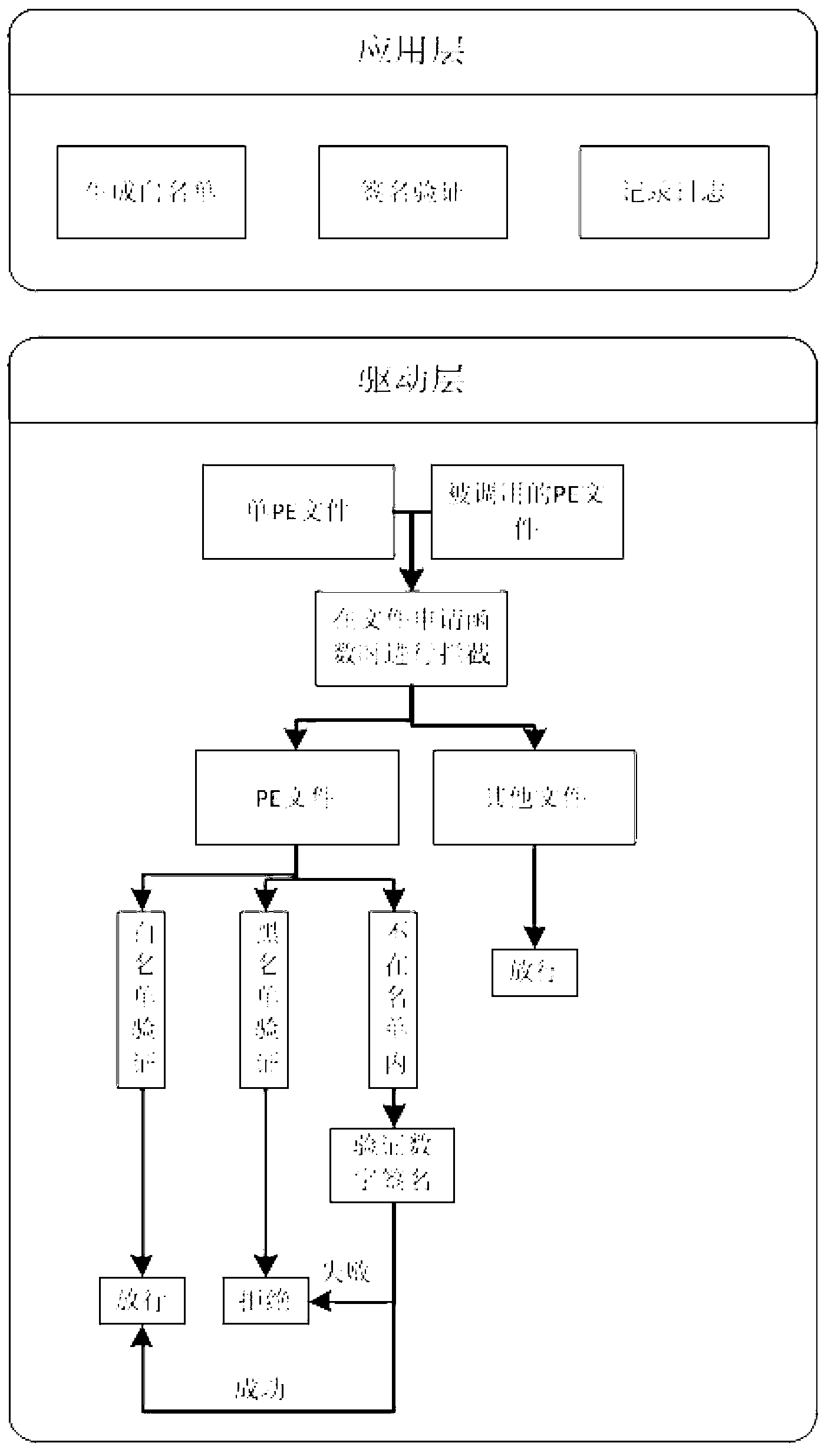
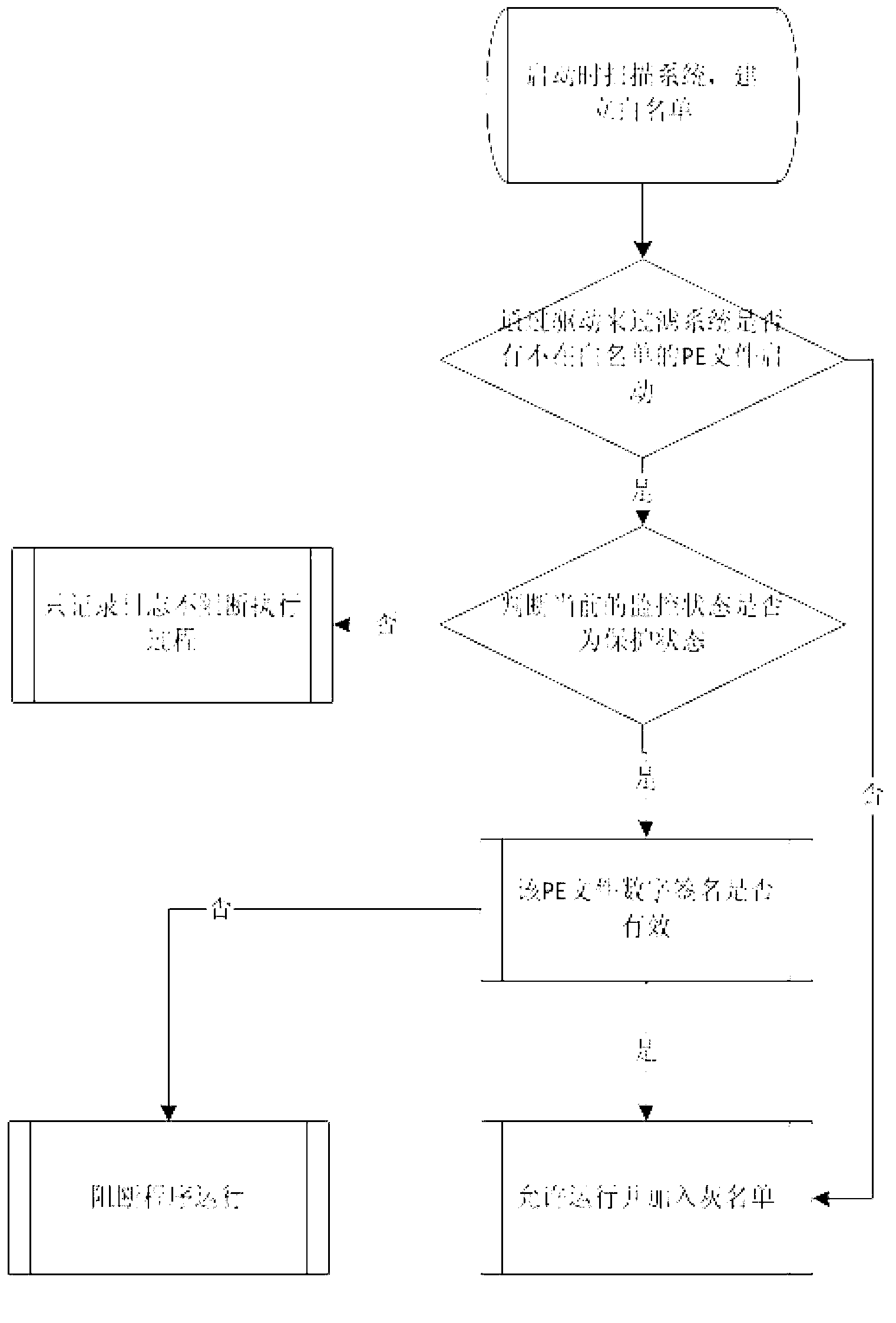
Method for intercepting operating of suspicious programs
ActiveCN103065092AImplement interceptionAchieve acquisitionPlatform integrity maintainanceBlack listVirus
The invention discloses a method for intercepting operating of suspicious programs. The method includes the steps of: (1) under the condition that a protected computer has no Trojan horse viruses and when a system is operated for the first time, recording all PE (Portable Execute) file information existing in the computer and generating a white list, (2) intercepting requests of memory application in file loading and screening out the PE files in a operating system nucleus, (3) comparing with a black list and the white list to judge whether the file is suspicious. The method for intercepting operating of suspicious programs has the advantages that the method effectively intercepts the enablement of suspicious programs and obtains Trojan horse virus samples by intercepting all the PE files loaded by an operating system and comparing with the white list to judge the PE files, intercepts known Trojan horse viruses by making the black list, provides detailed log reports to analyze and monitor running status of all processes in a current system so that the safety of the system is greatly improved, and overcomes the great defect that existing antivirus software can not intercept unknown Trojan horse viruses by using feature contrasting mode.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
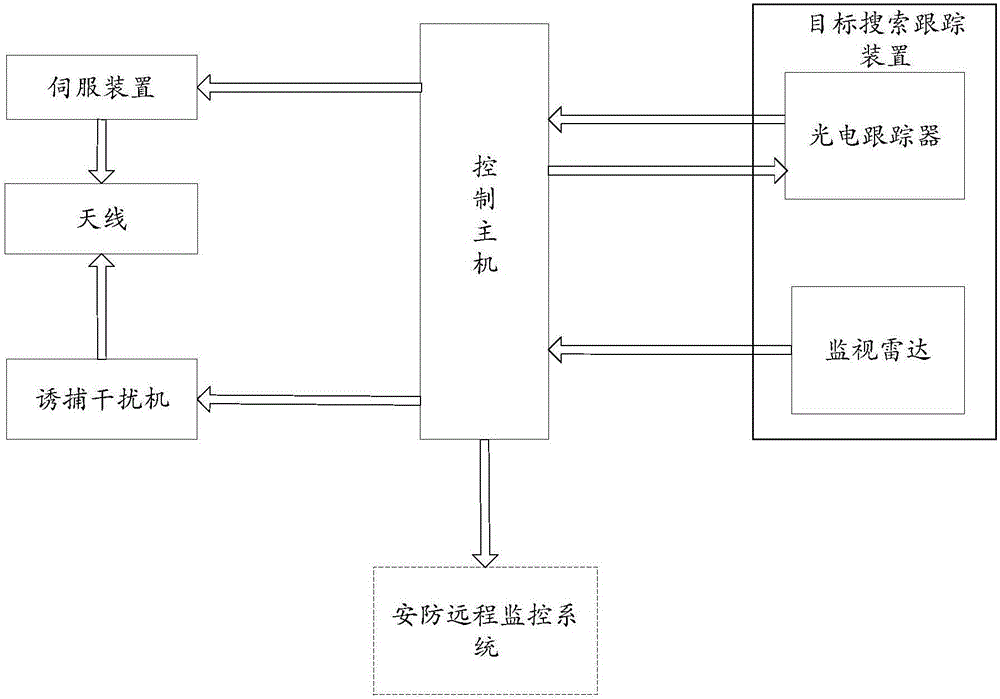
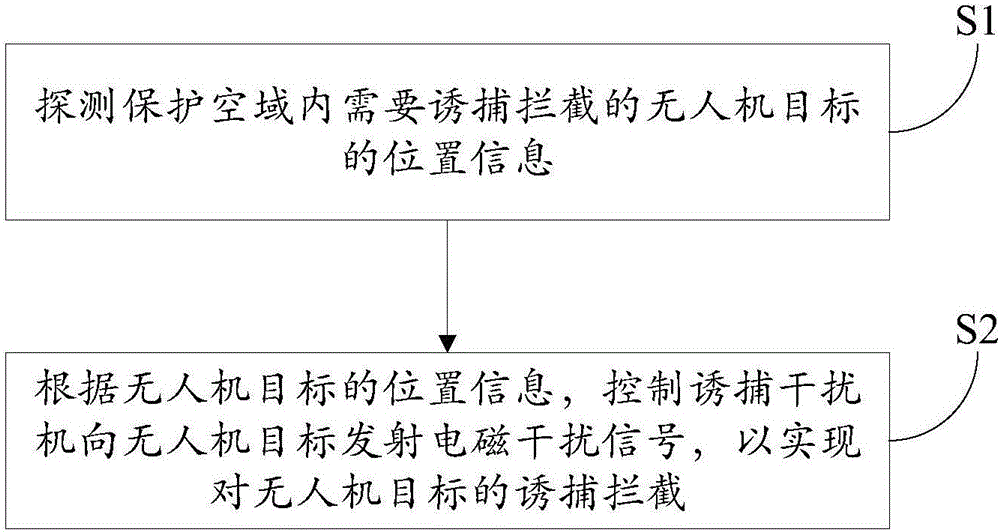
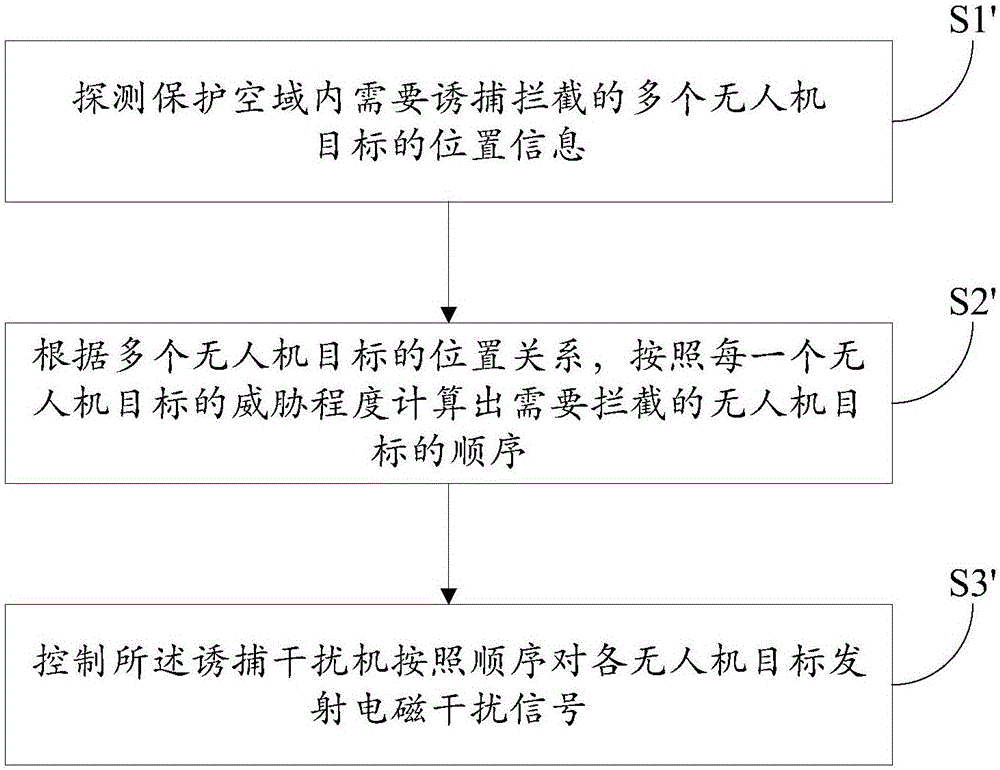
Unmanned aerial vehicle trapping interception system based on electromagnetic interference and trapping interception method thereof
InactiveCN106569511ARealize decoy interceptionRealize soft killing, trapping and interceptionControl using feedbackSatellite radio beaconingTrappingElectromagnetic interference
The invention discloses an unmanned aerial vehicle trapping interception system based on electromagnetic interference and a trapping interception method thereof. The trapping interception system comprises a control host, a target searching tracking device and a trapping jammer. The target searching tracking device is used for detecting position information of a suspicious target in a protection airspace and video information and sending to the control host. The control host is used for determining whether the suspicious target is an unmanned aerial vehicle target according to the video information. If the suspicious target is the unmanned aerial vehicle target, according to the position information of the unmanned aerial vehicle target, the trapping jammer is controlled to emit an electromagnetic interference signal to the unmanned aerial vehicle target so as to realize trapping interception to the unmanned aerial vehicle target. In the invention, through using the electromagnetic interference signal, the trapping interception to the unmanned aerial vehicle is realized and soft killing trapping interception of the unmanned aerial vehicle is realized too. New defense means are provided for relieving a security threat caused by a low, slow and small unmanned aerial vehicle. And a secondary damage caused through using a traditional interception net, a laser and other hard killing interception modes is avoided.
Owner:BEIJING INST OF RADIO MEASUREMENT
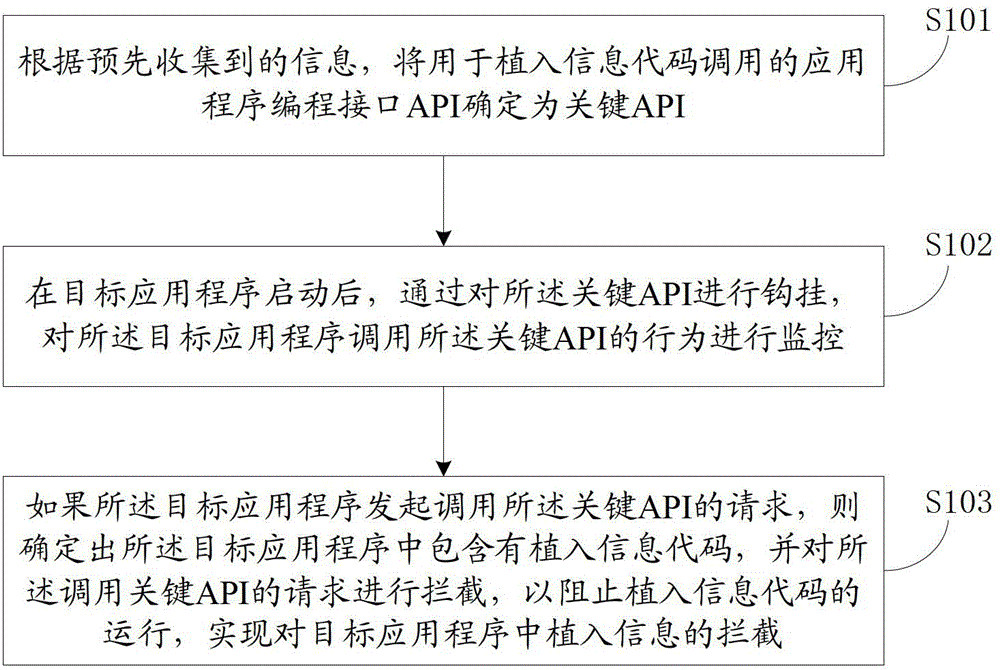
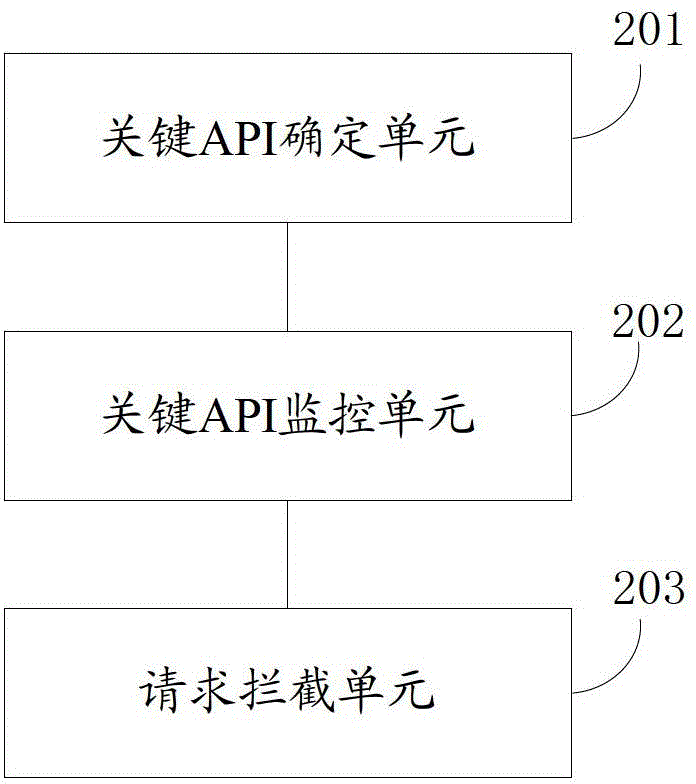
Method and device for intercepting embedded information in application program
ActiveCN103150513AImplement interceptionStop runningInterprogram communicationHardware monitoringOperational systemApplication programming interface
The invention discloses a method and a device for intercepting embedded information in an application program. The method comprises the following steps of determining an application programming interface (API) called by an embedded information code as a key API according to the pre-collected information, wherein the key API is an API provided by an information provider; after a target application program is started up, monitoring the behavior that the target application program calls the key API by hooking the key API; and if the target application program requests to call the key API, determining that the target application program comprises the embedded information code, and intercepting the request of calling the key API to prevent the embedded information code from running, thereby realizing the interception of the embedded information in the target application program. Through the method and the device provided by the invention, the interception of the embedded information in the application program can be effectively realized, and meanwhile, the running of an operating system can not be interfered, and the accuracy of interception is improved.
Owner:BEIJING QIHOO TECH CO LTD
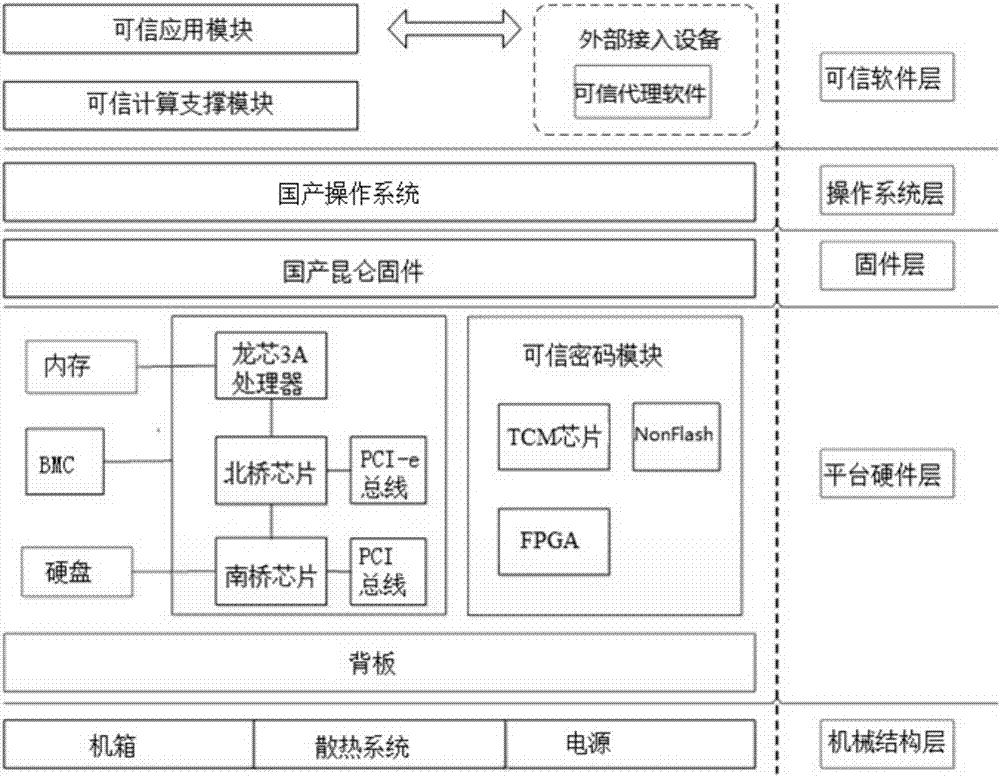
Dependable computing unit based on homemade TCM and operation method thereof
InactiveCN106991329AImprove computing speedVersatilePlatform integrity maintainanceOperational systemInformation security
The invention relates to a dependable computing unit based on a homemade TCM and an operation method thereof. The dependable computing unit comprises a mechanical structure layer, a platform hardware layer, a firmware layer, an operation system layer and a dependable software layer; the mechanical structure layer comprises a case, a heat dissipating system and a power source; the firmware layer comprises firmware; the operation system layer comprises an operation system; the platform hardware layer comprises a backboard, a computing unit module and a dependable code module; the dependable software layer comprises a dependable application module and a dependable computing supporting module. The dependable computing unit is complete in function, high in algorithm computing efficiency and large in concurrence work capacity; serving as the dependable computing unit, the unit can provide high-performance data encryption / decryption service for an information safety transmission system and serve as main code equipment and core member of a host data safety storage system, an identity authentication system and a symmetric and asymmetrical secret key management system, and has wide system application potentiality.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
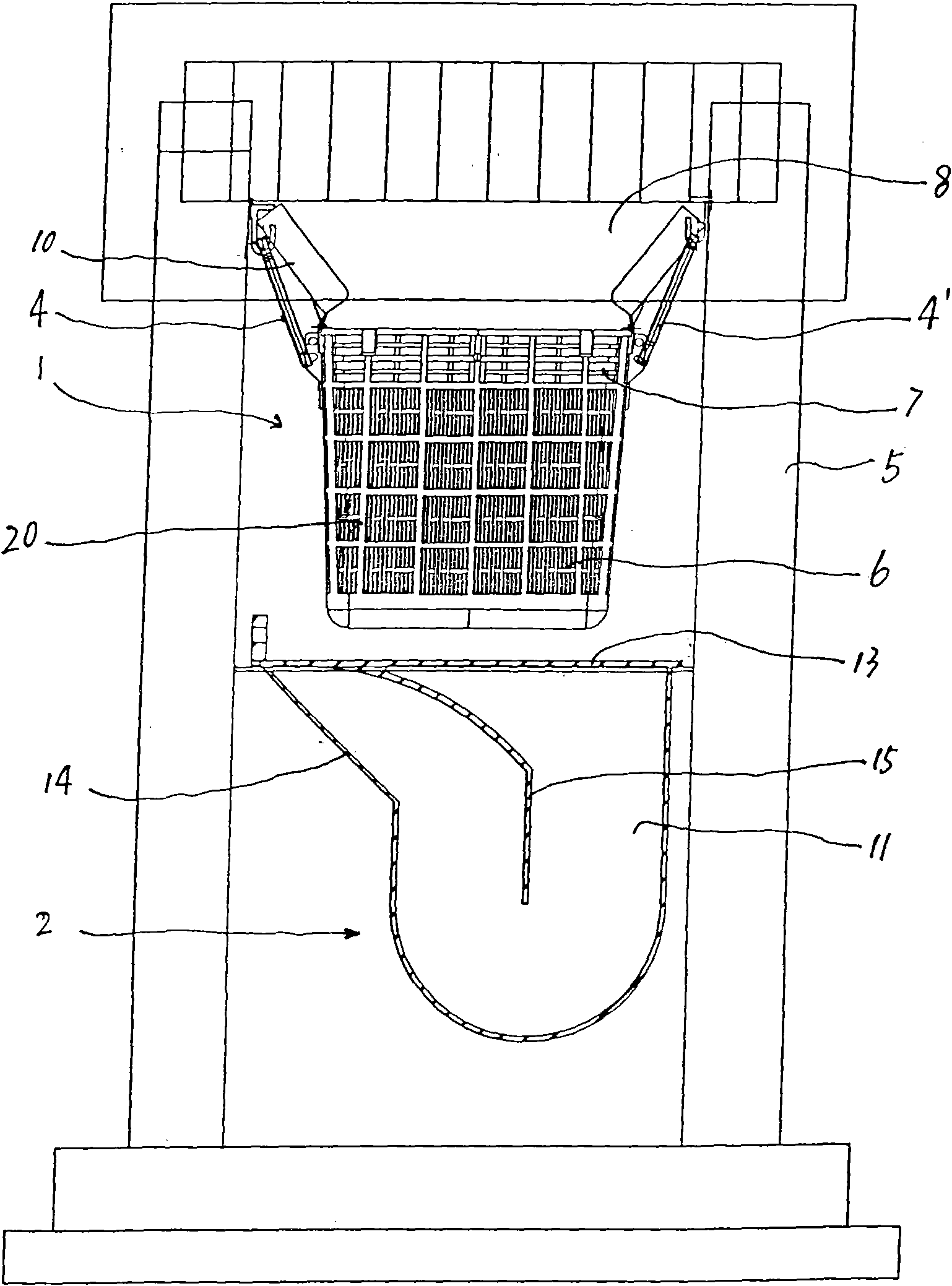
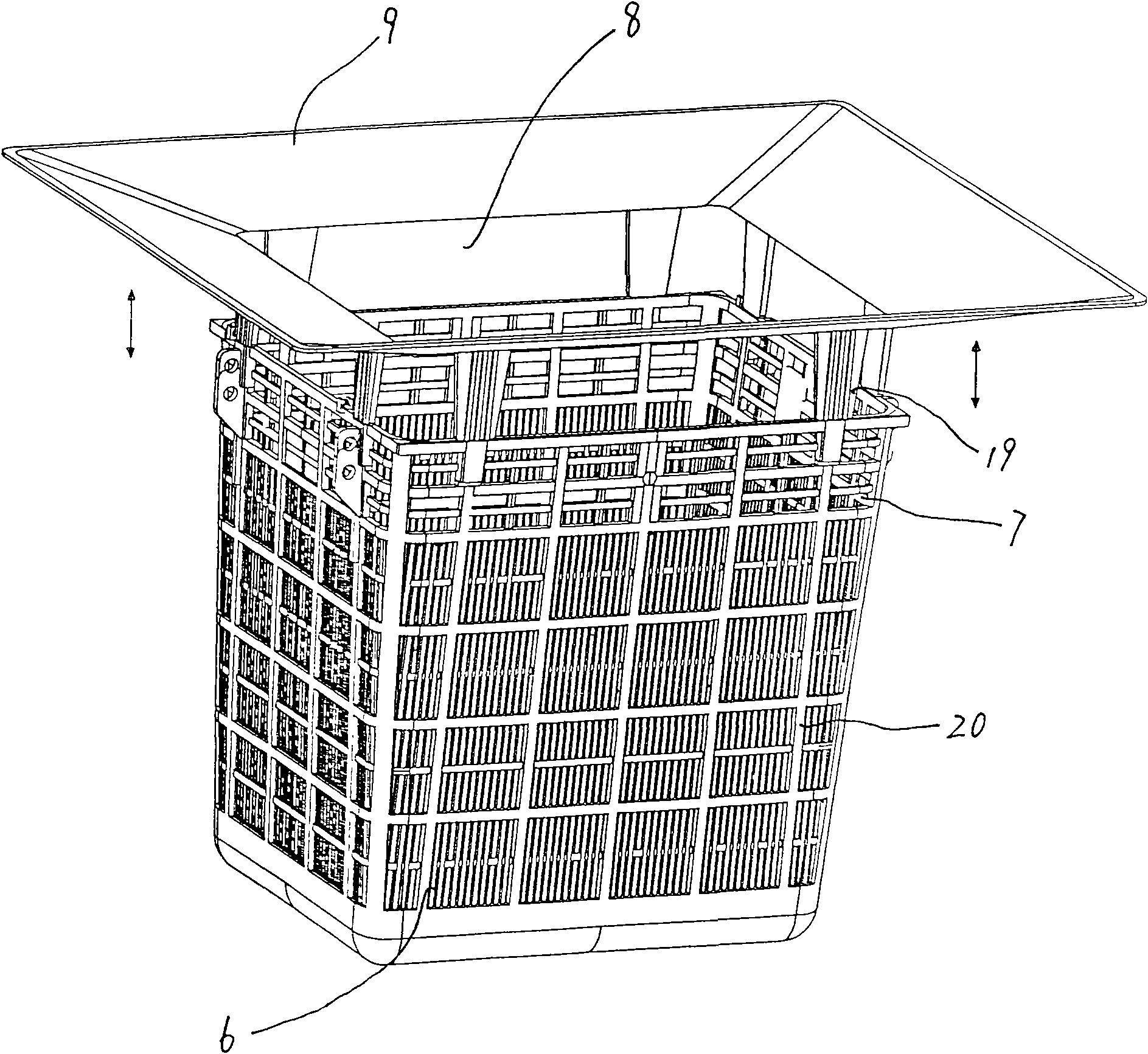
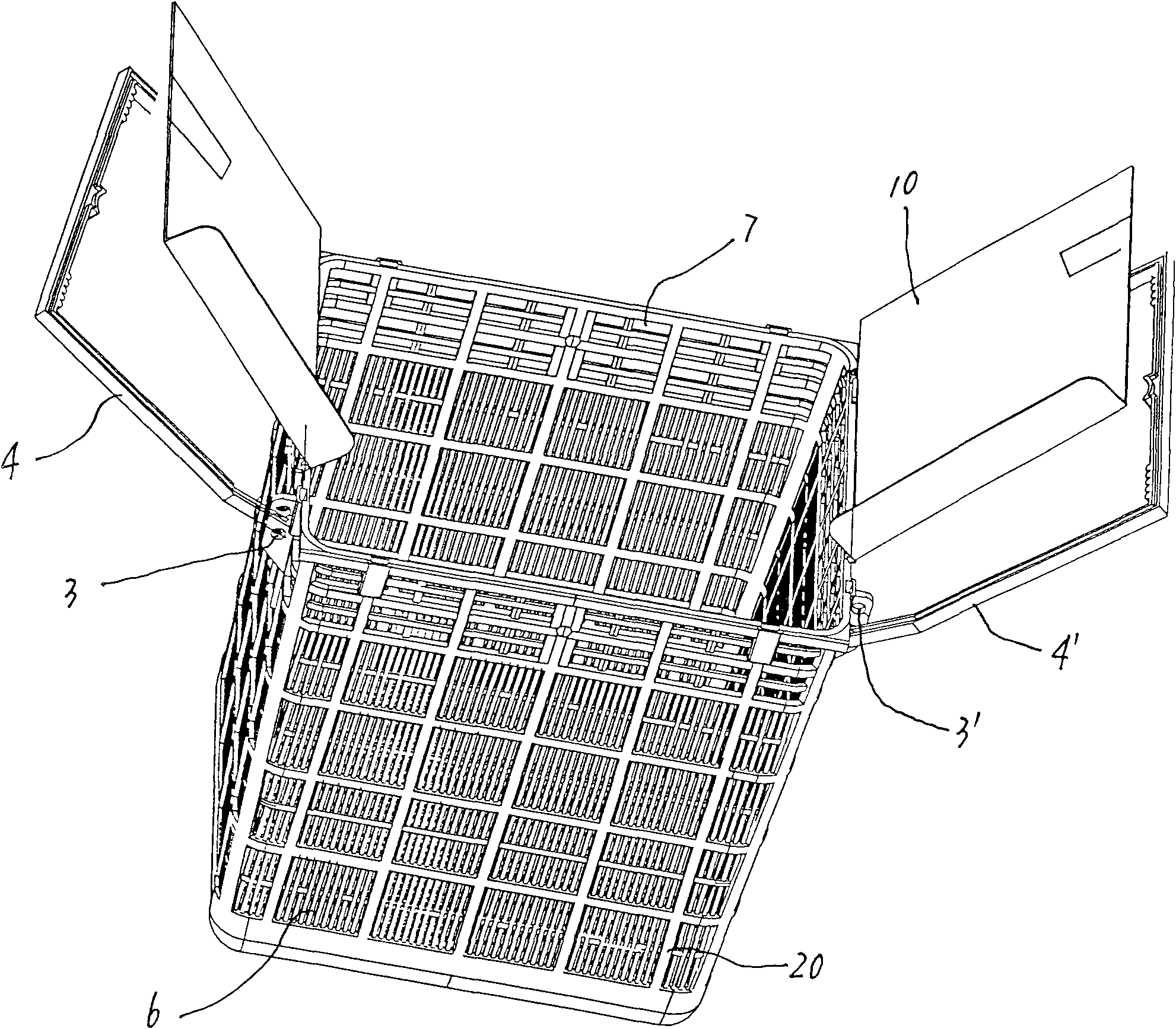
Device for intercepting and deodorizing waste at road gully
The invention discloses a device for intercepting and deodorizing waste at a gully; a solid waste intercepting device is arranged at a gully wall chamber, a deodorizing device is arranged at the lower part of the solid waste intercepting device, the solid waste intercepting device is a grating type framework with an opening at the upper end thereof, the grating type framework hangs at a fixed stainless steel hanger of the inner wall of the gully wall chamber by two handles at the two sides thereof, filtering areas with uniform density are respectively arranged at the middle and lower part of the lateral side of the grating type framework, a flooded zone is arranged at the upper part of the lateral side thereof, a drainage area is arranged at the upper part of the flooded zone, a tremie-type priming frame or a tremie-type priming frame is connected on the grating type framework; the deodorizing device is a water-holding bent deodorizing water seal or a self equilibrating turnover plate water seal. Considering the defect of complex structure of the existing solid waste treatment device, the invention provides a solid waste intercepting and deodorizing device featuring simple structure and low cost. As the device is simple in structure, convenient in both installation and use, thus being beneficial for promotion and popularization.
Owner:上海天予实业有限公司
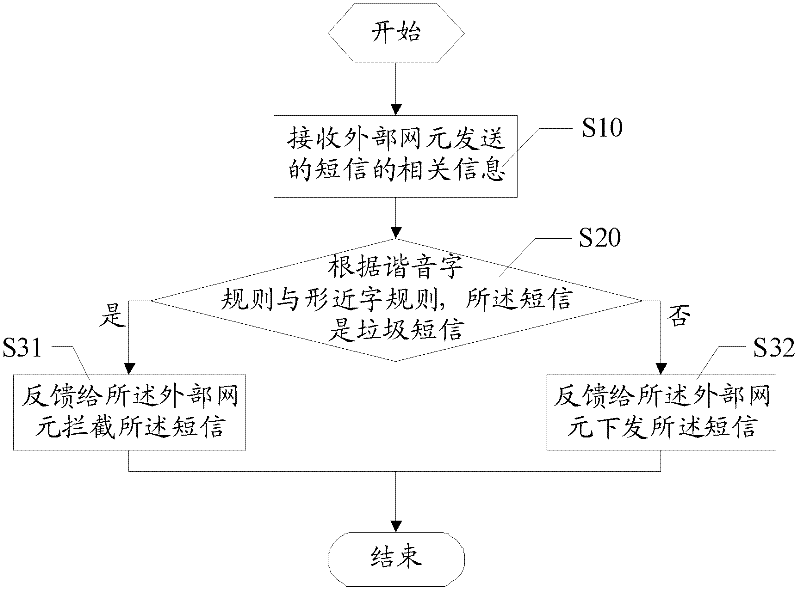
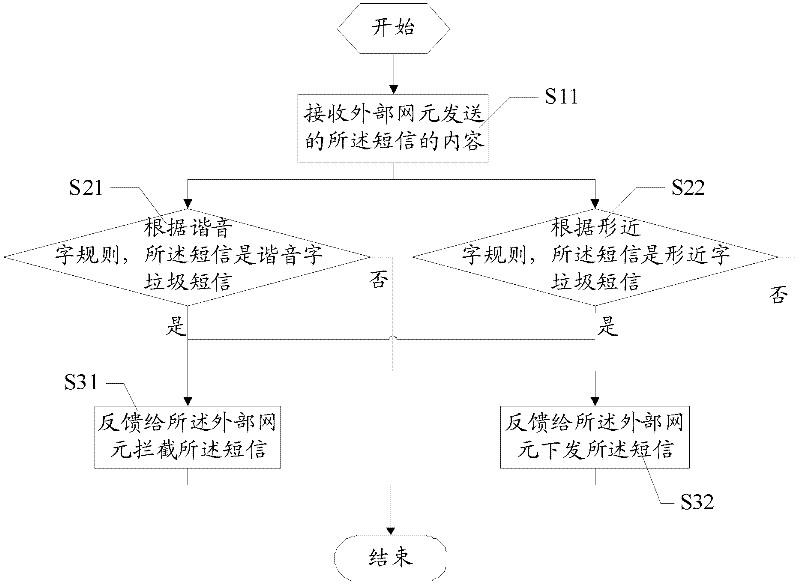
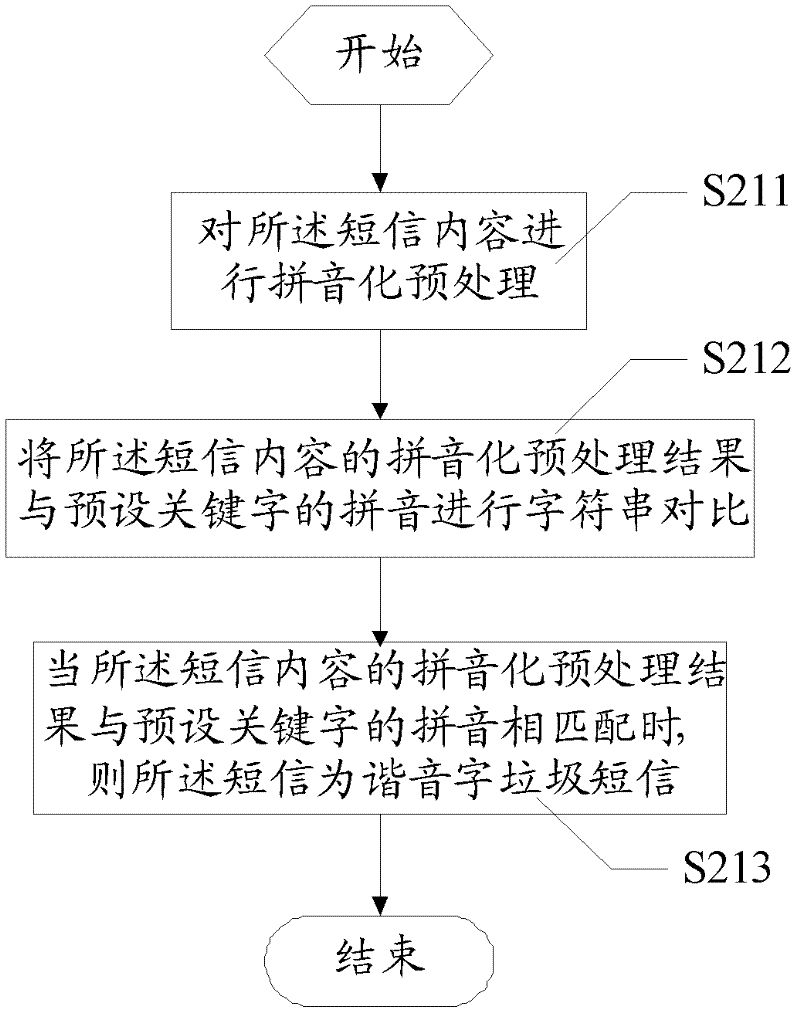
Method and system for monitoring garbage message and monitor processing apparatus
InactiveCN102231873AAchieve discriminationImplement interceptionMessaging/mailboxes/announcementsTransmissionMessage flowRelevant information
The invention discloses a method and a system for monitoring garbage messages and a monitor processing apparatus. The method for monitoring garbage messages comprises the steps of receiving relevant information of the message sent by an external network element, determining the message is a garbage message or not based on a homophonic tone character rule or a homographic character rule, sending a feedback to the external network element to intercept the message if the message is a garbage message and sending a feedback to the external network element to issue the message if the message is not a garbage message. According to the invention, a character coupling is carried out with the pinyin of the message to be monitored and the pinyin of keywords to realize discriminating and intercepting garbage messages using homophonic tone characters and another character coupling is carried out with the message to be monitored and the variation fonts of the keywords to realize discriminating and intercepting garbage messages. Meanwhile, an acceptance and rejection list and short message flow control are combined to make the monitor more comprehensive so that the phenomenon of missing examinations is effectively prevented.
Owner:ZTE CORP
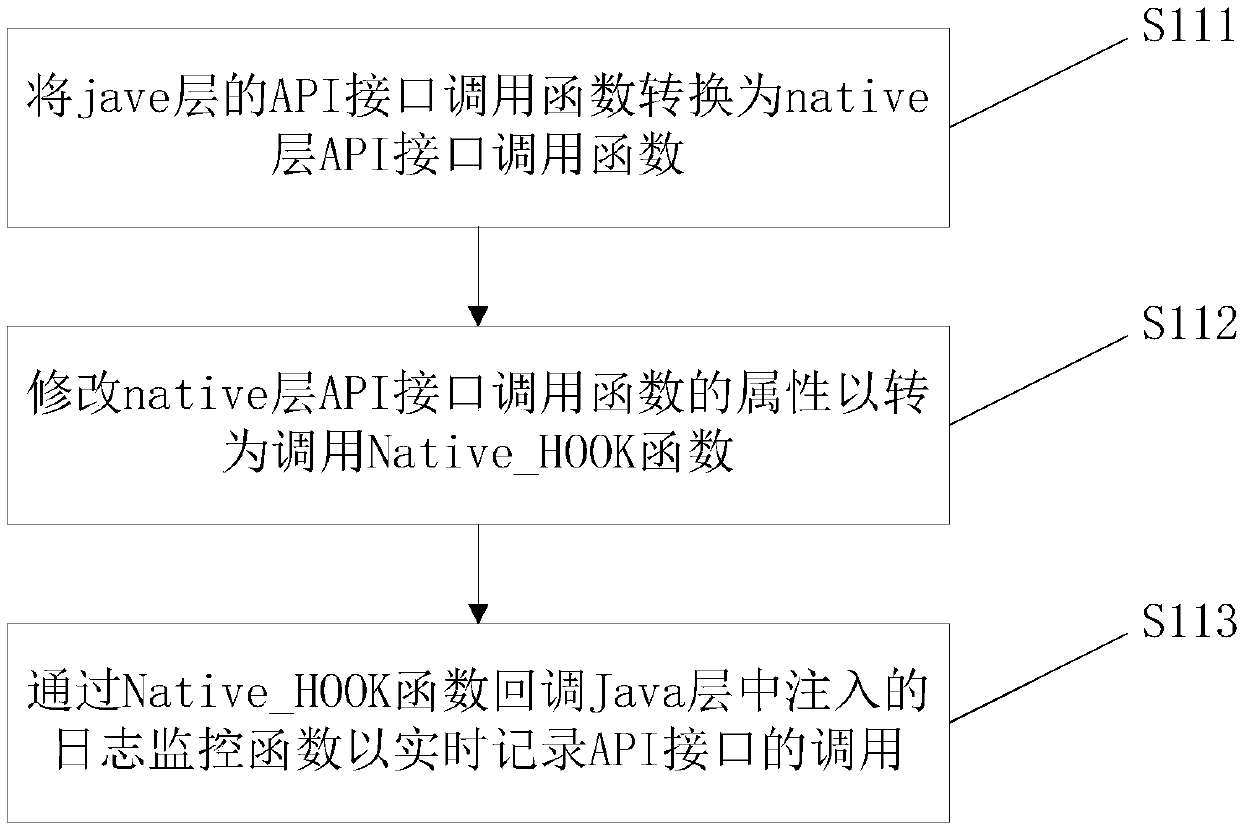
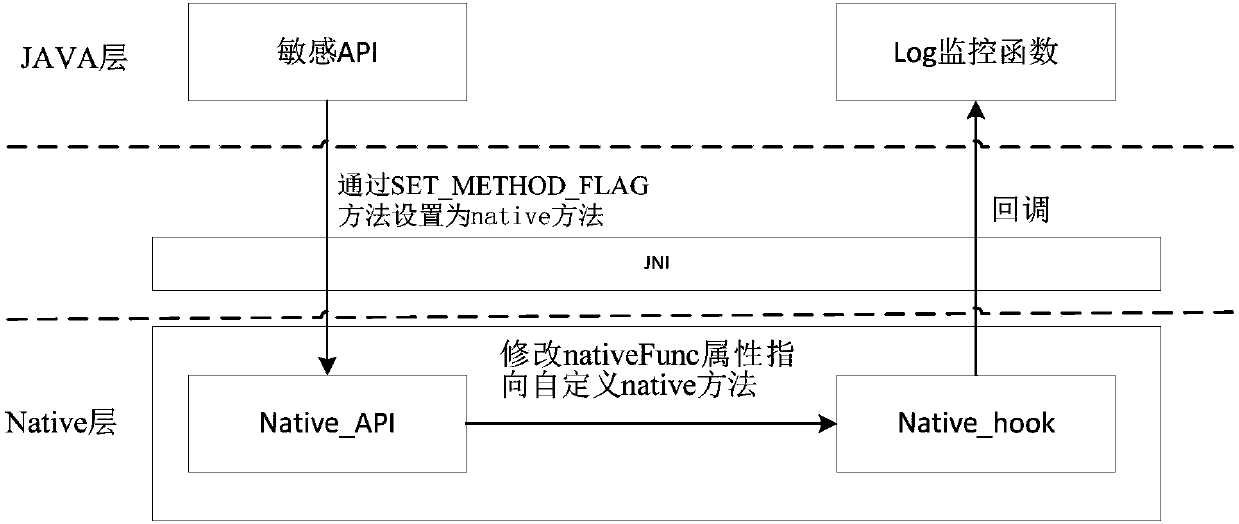
Monitoring method for App behaviors in Android system
InactiveCN105844157AImprove the protective effectTo achieve the purpose of security protectionPlatform integrity maintainanceRelevant informationAddress book
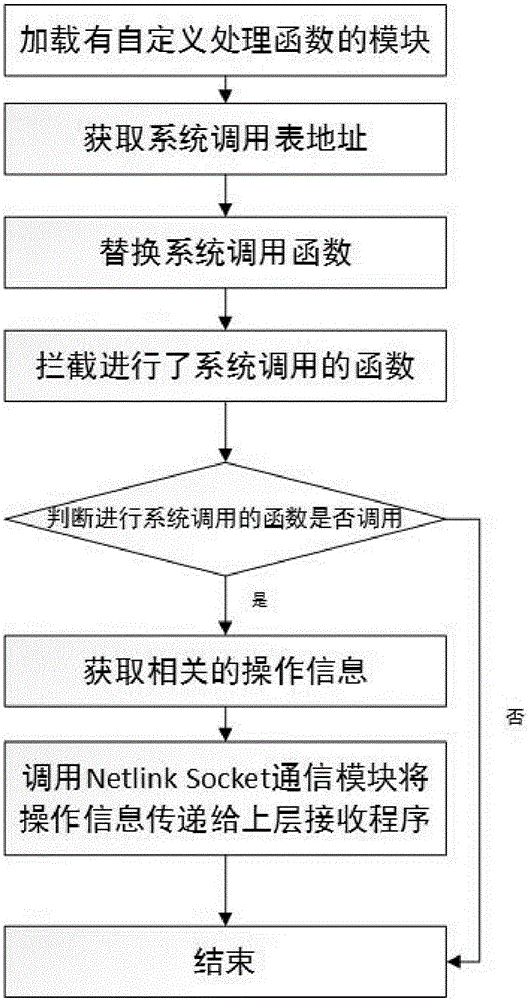
The invention discloses a monitoring method for App behaviors in an Android system. The method comprises the steps as follows: firstly, writing a kernel module, and performing cross compilation by writing of own Android kernel module; secondly, loading the module into the Android system, and intercepting specific functions (such as functions for reading related information of address books and the like) to obtain corresponding system call information including information about reading through which process and the like; thirdly, returning the corresponding recorded information to an application layer and forming corresponding monitoring log files to achieve system calling interception and monitoring of the whole Android system. According to the monitoring method, monitoring can be performed on system calling generated in both the application layer and a Native layer, and compared with existing monitoring methods for the application layer, the monitoring method has the advantages that protection can be more thorough, and the security protective property on mobile phones is higher; users are enabled to know behaviors of installed software thoroughly, thereby being capable of discovering malicious acts of the software timely.
Owner:北京鼎源科技有限公司
Two-dimensional frequency-phase scanning small target detection system
ActiveCN106291477AStrong anti-interference abilityGood high reliability performanceWave based measurement systemsVIT signalsTiming generator
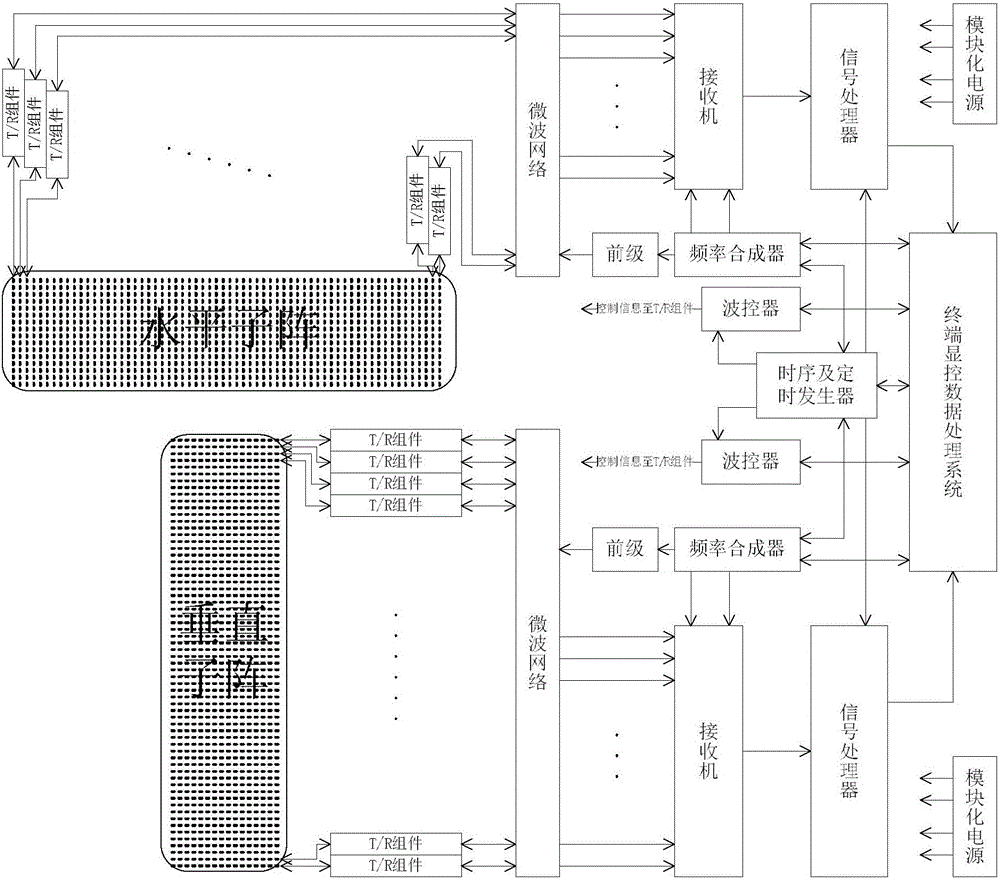
The invention provides a two-dimensional frequency-phase scanning small target detection system, aiming to provide a target detection system which is high in discovery rate, optimal in low-attitude detection performance, and high in anti-interference capability. The antennas of a horizontal sub-array and a vertical sub-array are connected with their respective microwave networks through their respective T / R components, the microwave networks are connected with receivers via n channels, the control information is sent to the T / R components via wave controllers through a time sequence and timing generator, frequency synthesizers are controlled by the time sequence and timing generator to generate excitation signals, the excitation signals are sent to the microwave networks via pre-amplifiers, the microwave networks radiate the beam through the T components to the antennas to the specified detection airspace and control the R components in the arrays to receive the radar echoes specified by emission, the radar echoes are sent to the receivers to signal processors for target detection after being amplified by each column of R components, the target detection data of the horizontal sub-array and the vertical sub-array are integrated, so that the high angle detection accuracy of orientation and pitching is achieved.
Owner:LINGBAYI ELECTRONICS GRP
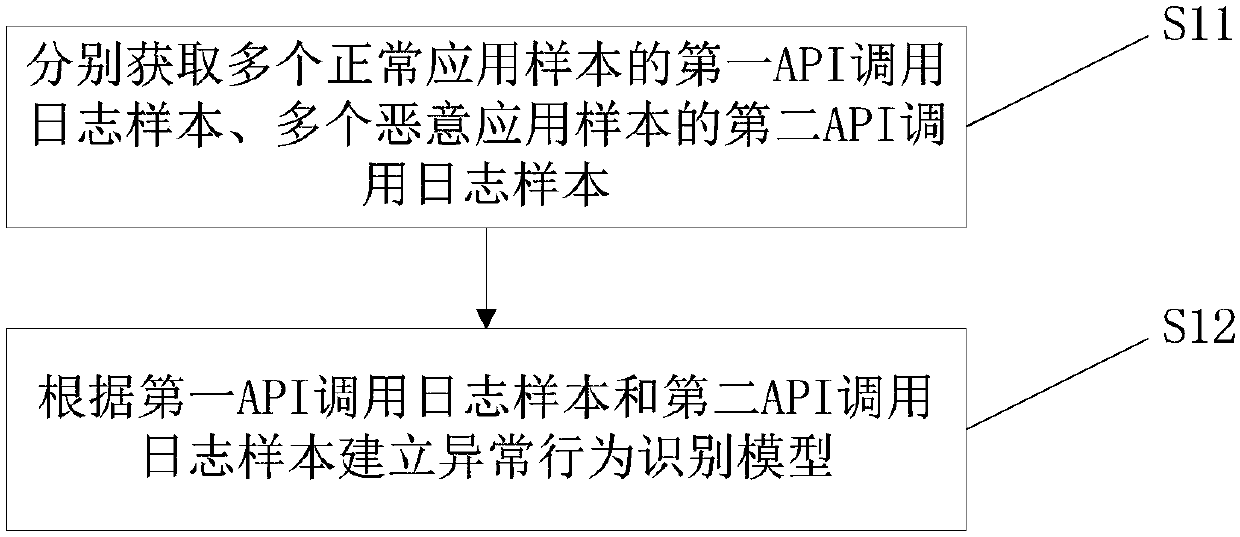
Application abnormal behavior identification model building method and apparatus, and application abnormal behavior identification method and apparatus
InactiveCN107045607AImplement interceptionRealize monitoringCharacter and pattern recognitionPlatform integrity maintainanceActual useApplication security
The invention discloses an application abnormal behavior identification model building method and apparatus, and an application abnormal behavior identification method and apparatus, and relates to the technical field of application security. The application abnormal behavior identification model building method comprises the steps of obtaining a first API call log sample of multiple normal application samples and a second API call log sample of multiple malicious application samples; and building an abnormal behavior identification model according to the first API call log sample and the second API call log sample. According to the method, the application abnormal behavior identification model can be built; and the identification model can identify whether a behavior of an application is abnormal or not according to an API call log collected during actual operation of the application in a real machine in real time, so that the behavior of the application in actual use can be detected in real time. The methods and the apparatuses can be suitable for power enterprise-oriented mobile applications.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
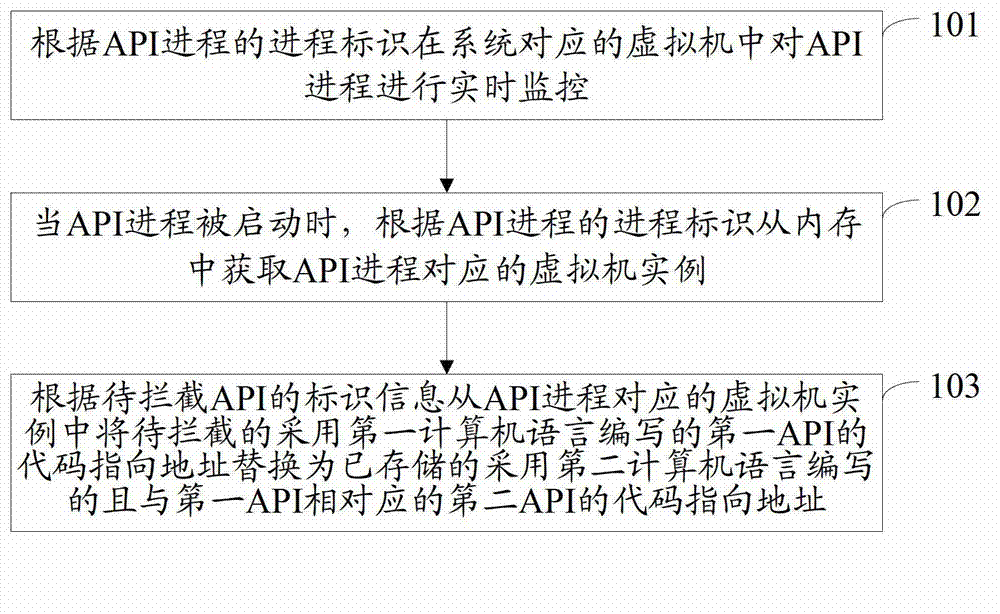
Application program interface (API) intercepting method and device and mobile terminal
ActiveCN102855138AImplement interceptionError identificationSpecific program execution arrangementsApplication programming interfaceHuman language
The invention discloses an application program interface (API) intercepting method, an API intercepting device and a mobile terminal and belongs to the field of mobile terminals. The method comprises the following steps of: monitoring an API progress in a virtual machine corresponding to the system in real time according to a progress identifier of the API progress; acquiring a virtual machine instance which corresponds to the API progress from a memory according to the progress identifier of the API progress when the API progress is started; replacing a code directing address of the intercepted first API written by the first computer language into a code directing address of the stored second API which is written by the second computer language and corresponds to the first API from the virtual machine instance which corresponds to the API progress according to the identification information of the intercepted API, wherein the second language is different from the first code; and controlling the API progress through a second function. The device comprises a monitoring module, an acquisition module and a replacement module. The application function can be expanded or modified.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
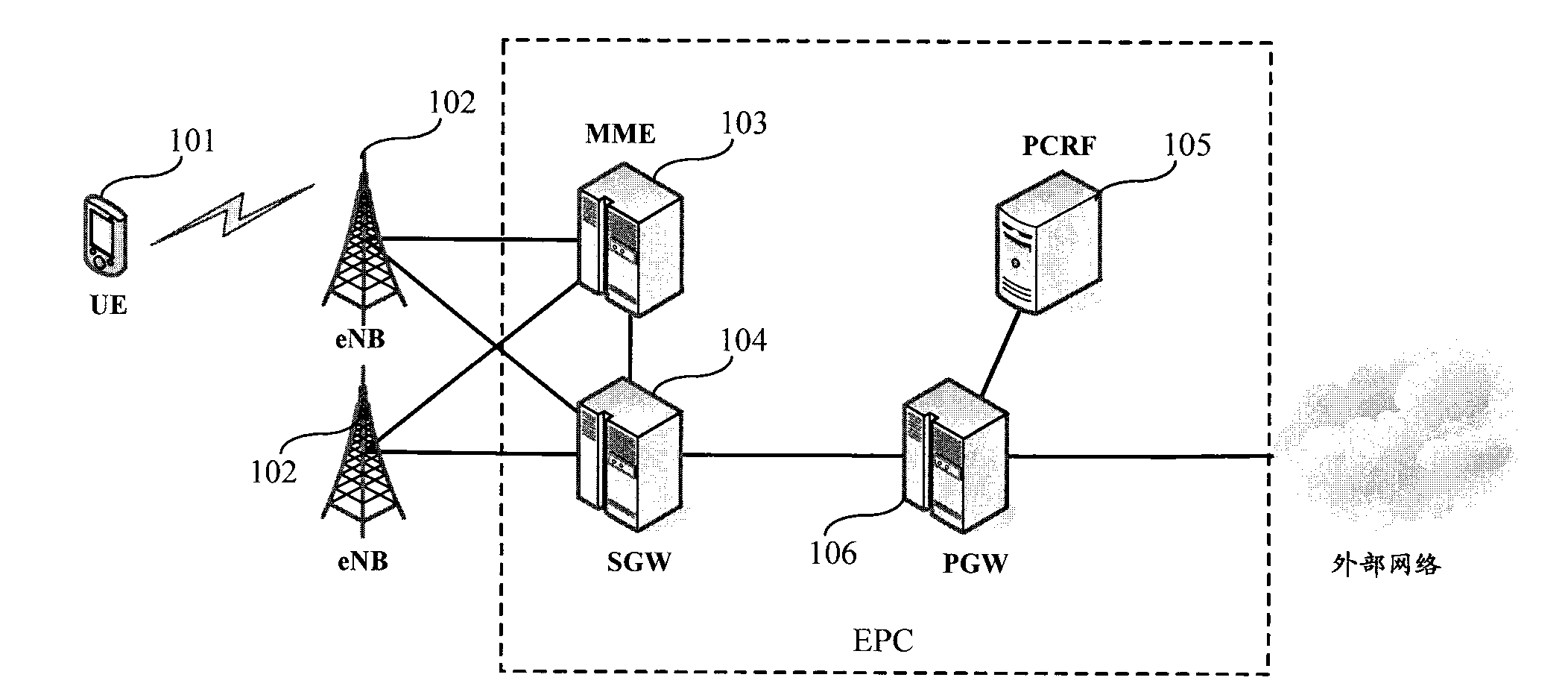
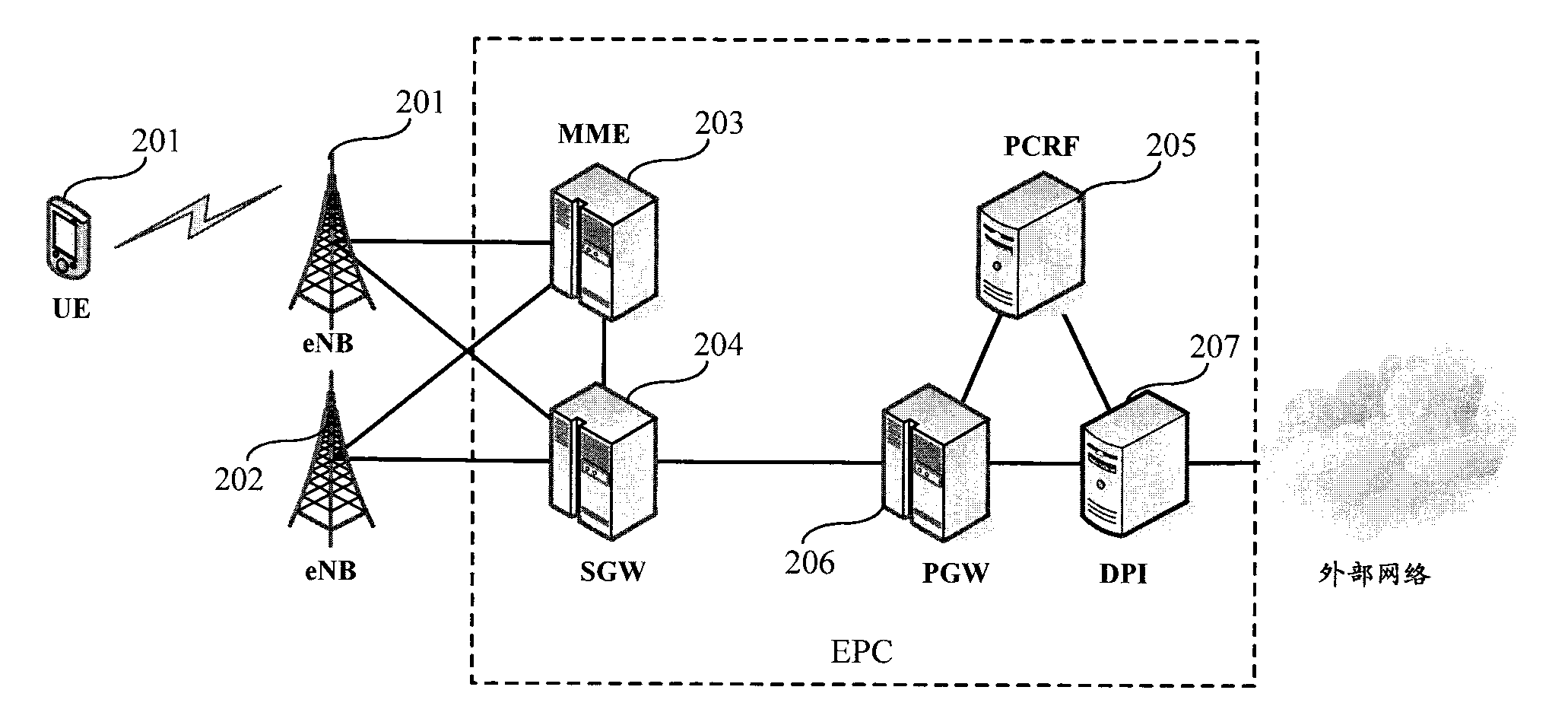
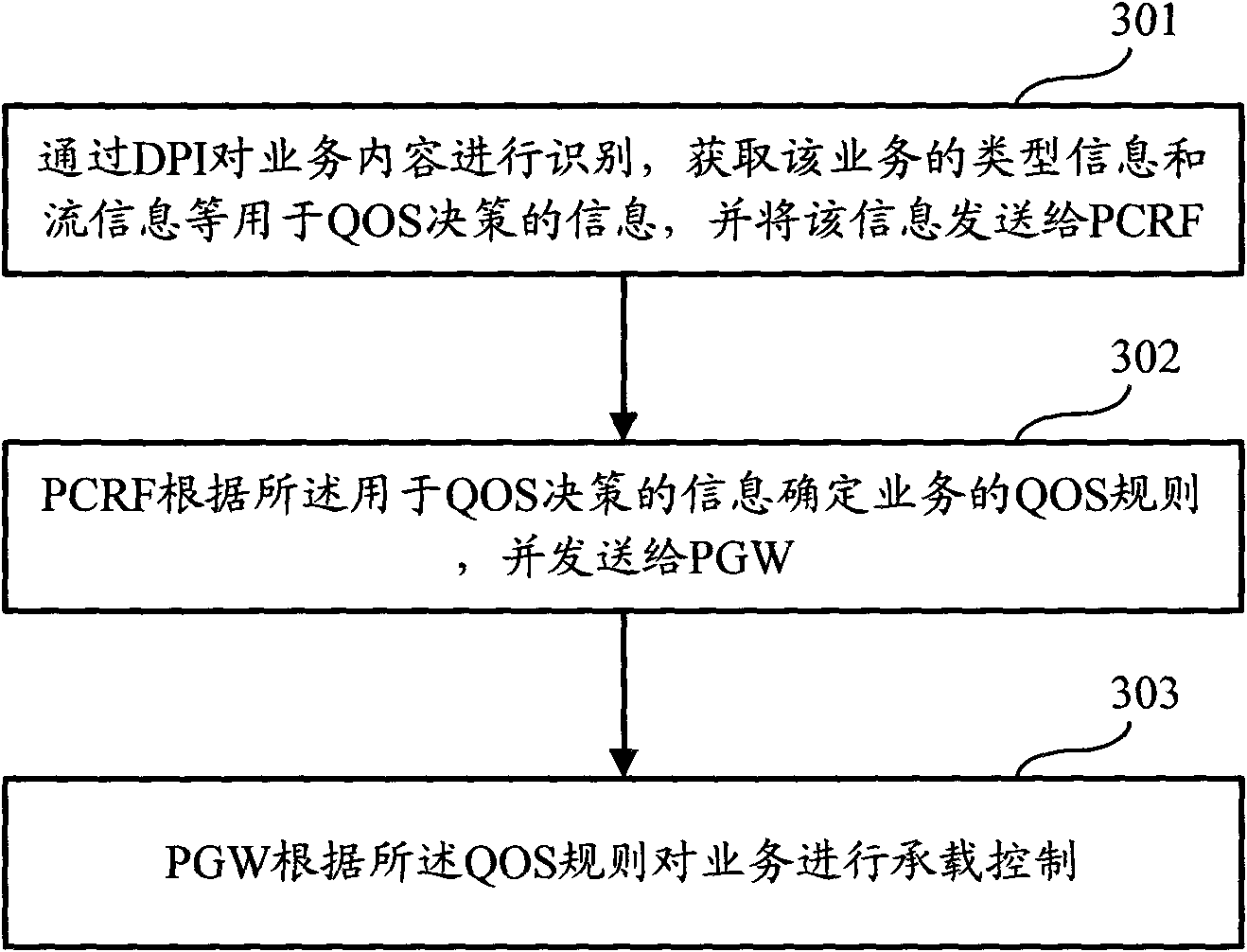
Load-bearing control system in evolved packet core based on depth package inspection and method
InactiveCN102811204AImplement interceptionImplement access controlData switching networksControl systemPolicy and charging rules function
The invention discloses a load-bearing control system in EPC (evolved packet core) based on DPI (depth package inspection). The system comprises a DPI module, a PCRF (policy and charging rules function) and a PGW (packet gateway). The DPI module is used for identifying service content through the DPI, acquires information used for service quality QoS decision-making of a service, and sends the information to the PCRF. According to a pre-established control policy and DPI module report information used for QoS decision-making, the PCRF is used for the QoS decision-making, and sends determined QoS rules to the PGW. When exchanging data with UE (mobile terminal), the PGW sends all exchanged data with the UE to the DPI module for recognition. According to the QoS rules sent by the PCRF, bearing control process to the service is initiated. The invention further discloses a load-bearing control method in the EPC based on the DPI. With the system and the method, load-bearing control to different PS (packet domains) services is achieved, intercepting and visiting control to the different PS services can be achieved, and realization cost is lower.
Owner:POTEVIO INFORMATION TECH CO LTD
Website-filtering method based on mobile Internet and cloud computing
InactiveCN103532917AImprove filtering effectImplement interceptionTransmissionCloud computingComputer security
The application discloses a website-filtering method and system based on a mobile Internet and cloud computing. The method includes: acquiring a data packet, which requests access of the mobile Internet, sent out by a mobile terminal; analyzing out a website to be accessed from the data packet; comparing the website to be accessed with websites stored in a local website database of the mobile terminal and if information of the website to be accessed does not exist and content affirmation of a webpage corresponding to the website to be accessed is evaluated to be unsafe by a user, sending the evaluation to a monitoring server; the monitoring server storing a corresponding relation of the website to be accessed and the evaluation into a cloud-end website database in the monitoring server; and at the same time, updating the local website database and the cloud-end website database at a set time. The scheme of the application is capable of integrating website access rules set by different users and sharing the rules to a local website database of each mobile terminal so that offensive websites can be filtered and intercepted timely and comprehensively.
Owner:GREEN NET WORLD FUJIAN NETWORK TECH
Kitchen waste recovery and utilization device
InactiveCN109108051AFast separationImplement interceptionSievingSolid waste disposalOil waterWaste recovery
The invention discloses a kitchen waste recovery and utilization device which comprises a base and a waste simple treatment tank body installed on the upper end of the base; the waste simple treatmenttank body is provided with a plurality of partition plates through an inner cavity to divide the inner cavity into a feeding chamber, a left feeding channel, a right reaming cutting chamber, a solid-liquid separation chamber and an oil-water separation chamber sequentially from top to bottom; the upper side of the feeding chamber is provided with a feeding funnel, a feeding cylinder and a simplerotation device; an inner cavity of the feeding chamber is provided with an inclined mesh screen, a first discharge hole, a second discharge hole and a material guide device; an inner cavity of the right reaming cutting chamber is provided with a crushing device and a roller cylinder grinding device; and the solid-liquid separation chamber is internally provided with a solid-liquid separation device. The kitchen waste recovery and utilization device has the beneficial effects of simple structure and strong practicability.
Owner:SHANGHAI ZHENGYU MACHINERY CO LTD
Method for intercepting target progress with self-protection
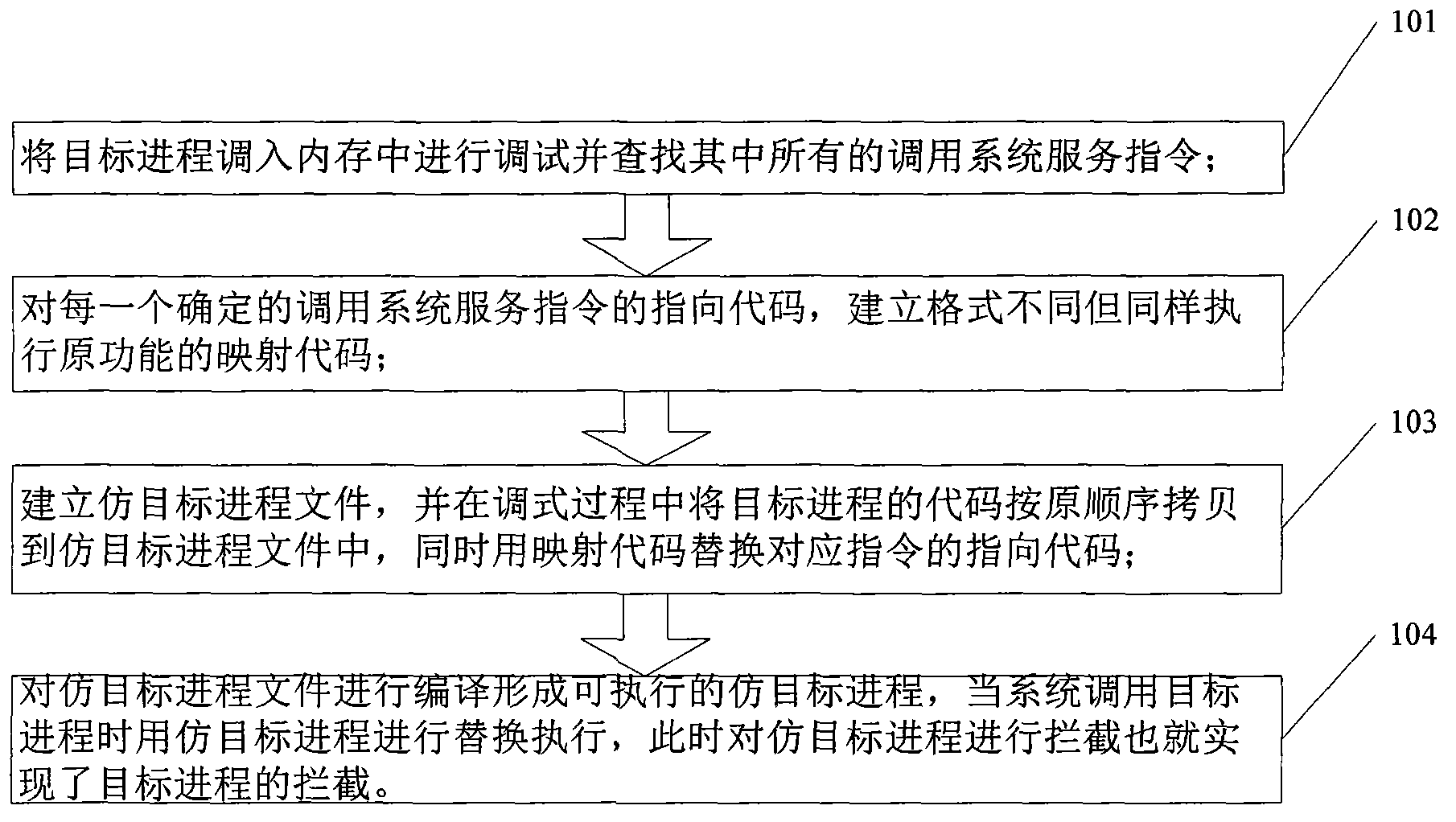
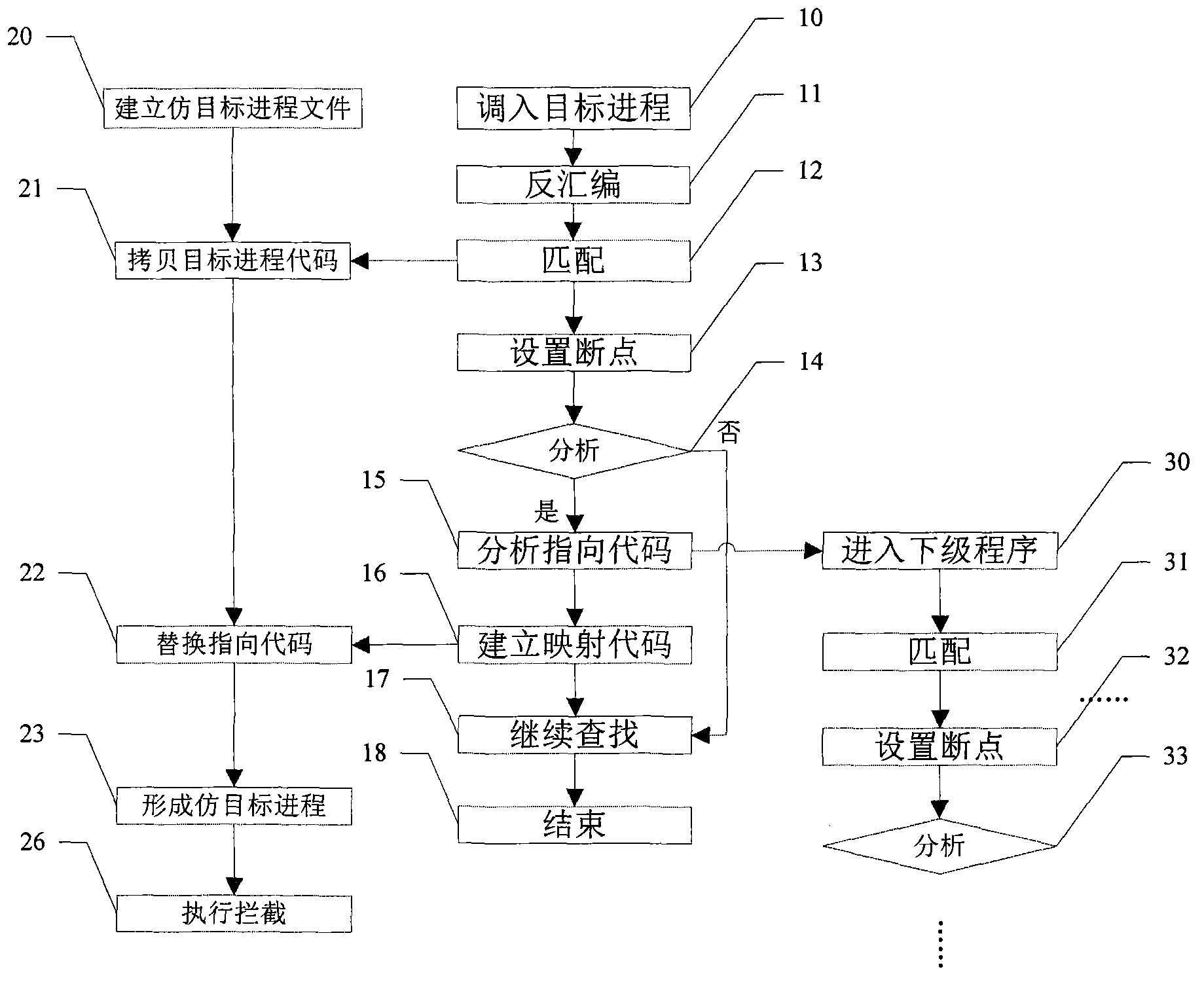
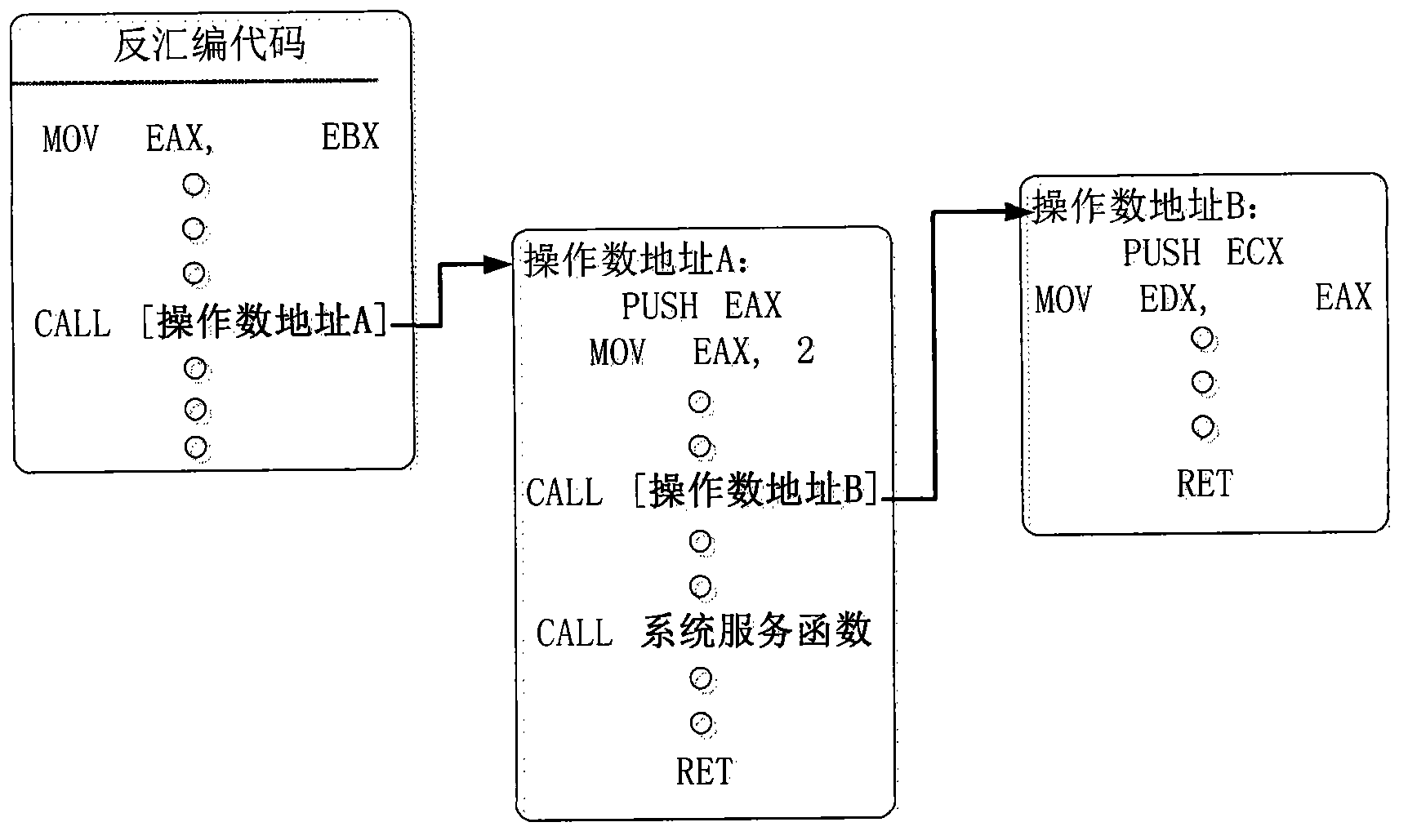
InactiveCN102799493AAvoid inspectionShield to avoidError detection/correctionProgram controlParallel computingSystem call
The invention discloses a method for intercepting a target progress with self-protection. The method comprises the following steps of: calling the target progress into a memory to debug and searching all calling system service instructions; building mapping codes with different forms and same execution original functions for a directing code of each determined calling system service instruction; building a simulating target progress document and copying the codes of the target progresses to the simulating target progress document in the debugging process, and replacing the directing codes of the corresponding instructions by the mapping codes; compiling the simulating target progress document to form an executive simulating target progress; replacing the target progress by the simulating target progress when the system calls the target progress and executing; and intercepting the simulating target progress to realize the interception of the target progress. By the method, a corresponding relation between the target progress and the simulating target progress is built, and since the target progress is replaced by the simulating target progress, so an application program interface (API) hook can be used for interception.
Owner:北京伸得纬科技有限公司 +1
Crank call interception method, device and equipment and storage medium
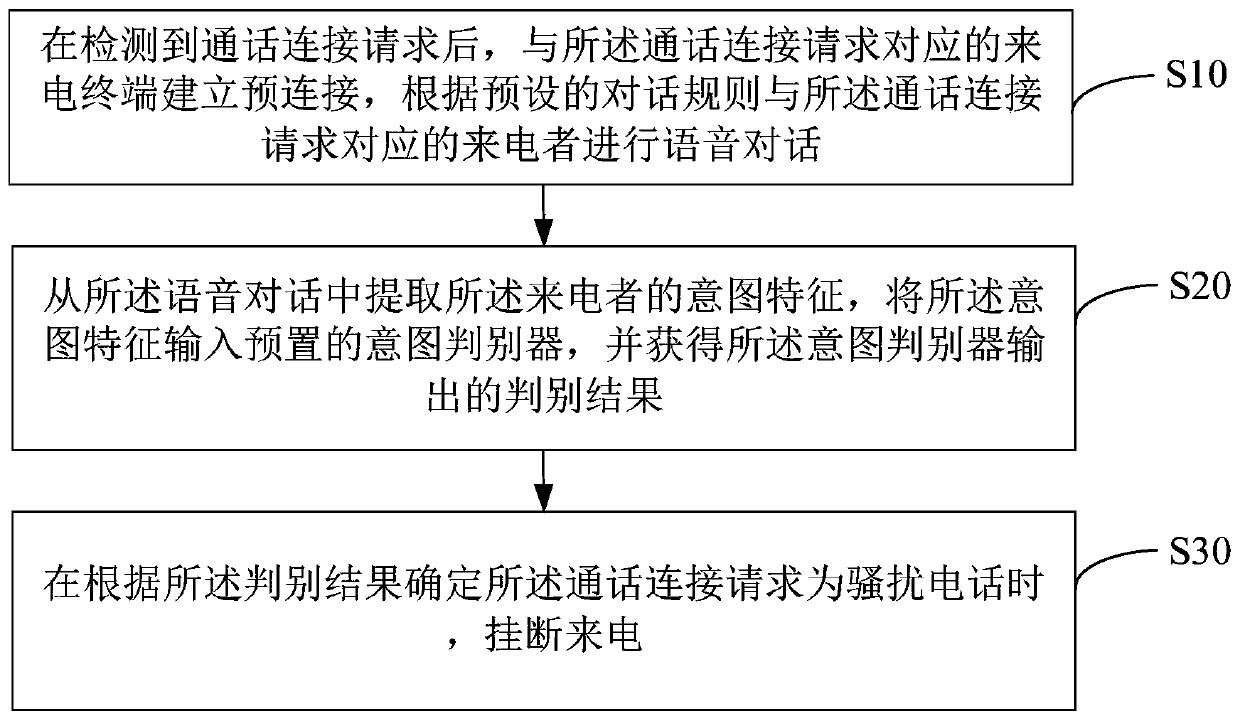
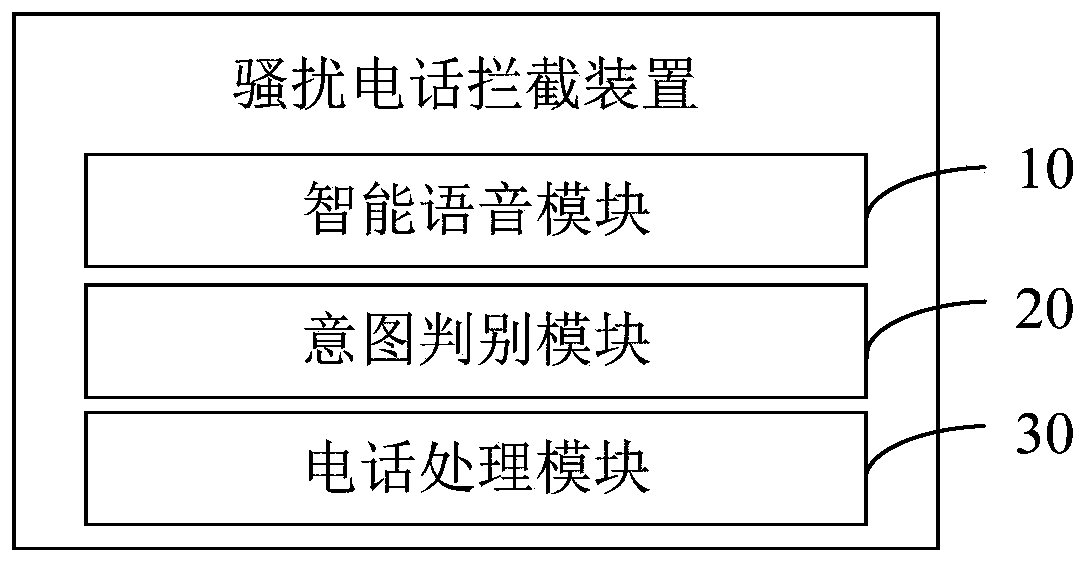
InactiveCN110149441AImplement interceptionAvoid Harassing and Scamming CallsDevices with voice recognitionSubstation equipmentDiscriminatorSpoken dialog
The invention provides a crank call interception method and device based on a classification model, equipment and a storage medium, and the method comprises the steps: building a pre-connection with an incoming call terminal corresponding to a call connection request after detecting the call connection request, and carrying out the voice conversation with an incoming caller corresponding to the call connection request according to a preset conversation rule; extracting intention characteristics of the caller from the voice conversation, inputting the intention characteristics into a preset intention discriminator, and obtaining a discrimination result output by the intention discriminator; and hanging up an incoming call when the call connection request is determined to be a crank call according to the judgment result. According to the method and the device, intelligent interception of crank calls can be realized.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
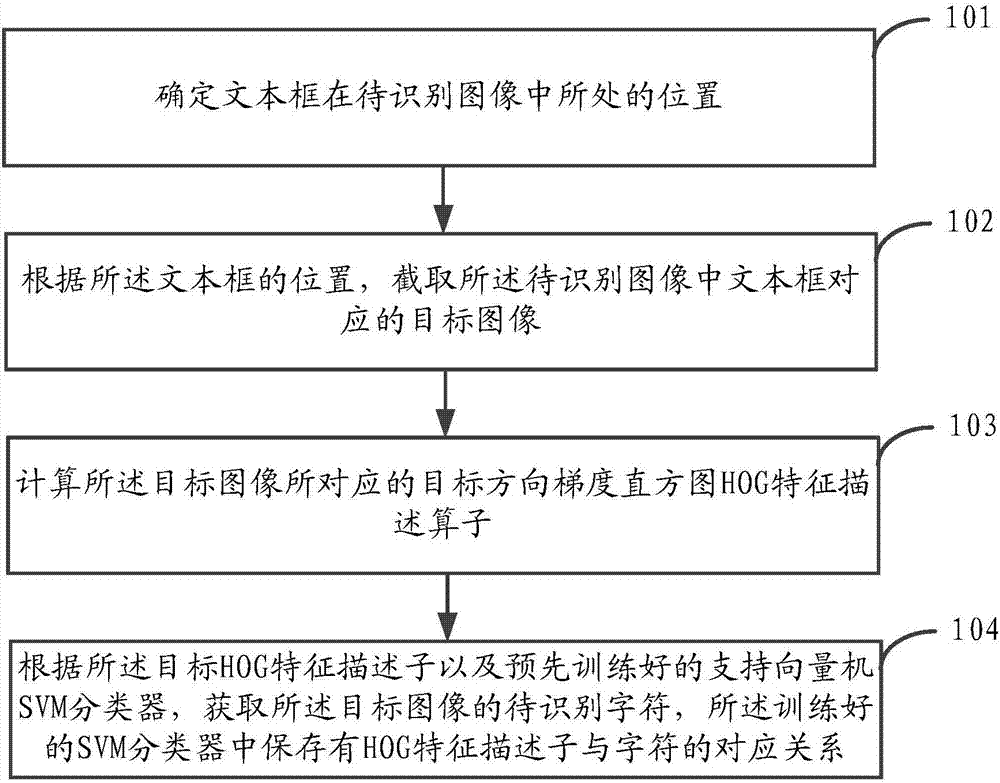
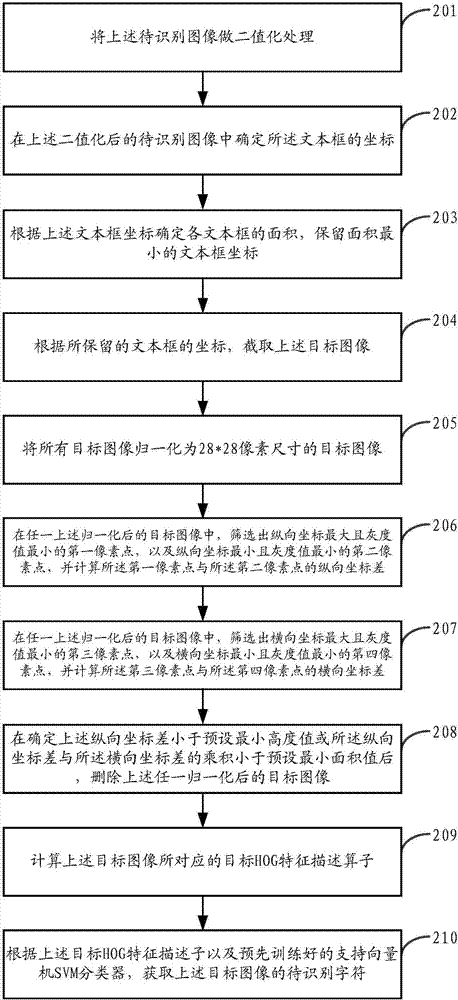
Character recognition method and device
InactiveCN107016417AAchieve positioningImplement interceptionCharacter and pattern recognitionSupport vector machine svm classifierHistogram of oriented gradients
The invention provides a character recognition method and device. The character recognition method is applied to recognition for a character in an image. The image comprises a text box with the position being uncertain, and the character is filled in the text box. The character recognition method comprises the steps of determining the position of the text box in an image to be recognized; intercepting a target image corresponding to the text box in the image to be recognized according to the position of the text box; calculating a target histogram of oriented gradient (HOG) feature description operator corresponding to the target image; acquiring a character to be recognized of the target image according to the target HOG feature description operator and a pre-trained support vector machine (SVM) classifier. By applying the embodiment of the invention, the position of the text box is determined in the image to be recognized, and a target image corresponding to the text box in the image to be recognized is intercepted according to the position of the text box, so that active positioning and interception for the target image are realized, an error occurred when a target image area is intercepted according to preset fixed coordinates is avoided, and the recognition accuracy is improved.
Owner:青岛伟东云教育集团有限公司
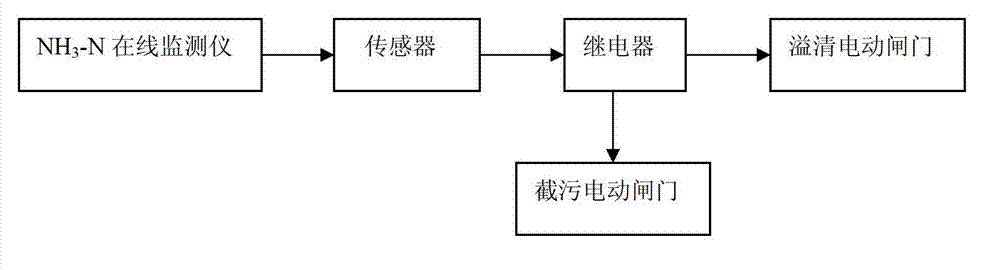
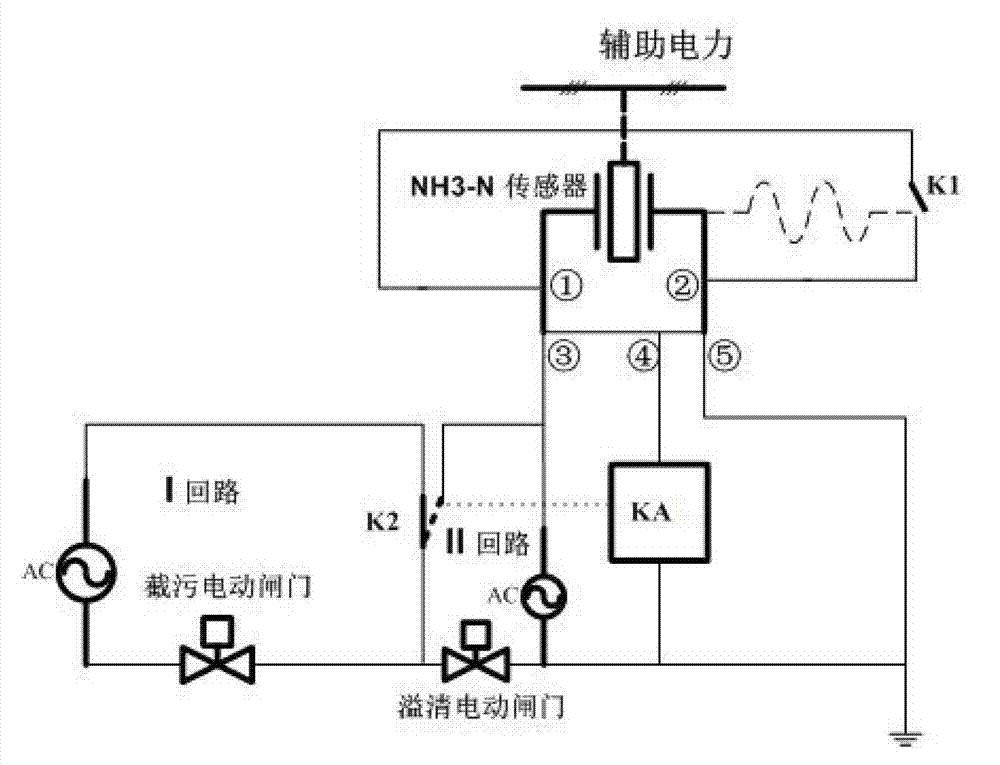
Control device for performing impurity blocking and clean water overflowing on combined sewage
InactiveCN102736641AIncrease pollution identification-intelligent control technology for sewage interception and overflow cleaningImplement interceptionControlling ratio of multiple fluid flowsHigh concentrationSewage
The invention discloses a control device for performing impurity blocking and clean water overflowing on combined sewage. The control device comprises an NH3-N on-line monitoring instrument, a sensor, a relay, an impurity blocking electric gate and a clean water overflowing electric gate, wherein the NH3-N on-line monitoring instrument, the sensor and the relay are sequentially connected with one another; the impurity blocking electric gate and the clean water overflowing electric gate are respectively connected with the relay; the NH3-N on-line monitoring instrument senses and identifies the NH3-N concentration in the sewage; the sensor converts the NH3-N concentration sensed and identified by the NH3-N on-line monitoring instrument into an electric signal; the electric signal is transmitted to the relay; and the relay controls the turn-on or turn-off of the impurity blocking electric gate and the clean water overflowing electric gate according to the electric signal. By the control device, impurities of high-concentration-charge sewage are blocked and purified, and clean water of low-concentration-charge sewage overflows, so that high-efficiency impurity blocking and clean water overflowing on the sewage are realized, and intelligent flow division control is realized.
Owner:SOUTH CHINA INST OF ENVIRONMENTAL SCI MEP
Method for intercepting business object and browser client
InactiveCN104346457AImplement interceptionEffective interceptionSpecial data processing applicationsWeb data browsing optimisationClient-sideApplication software
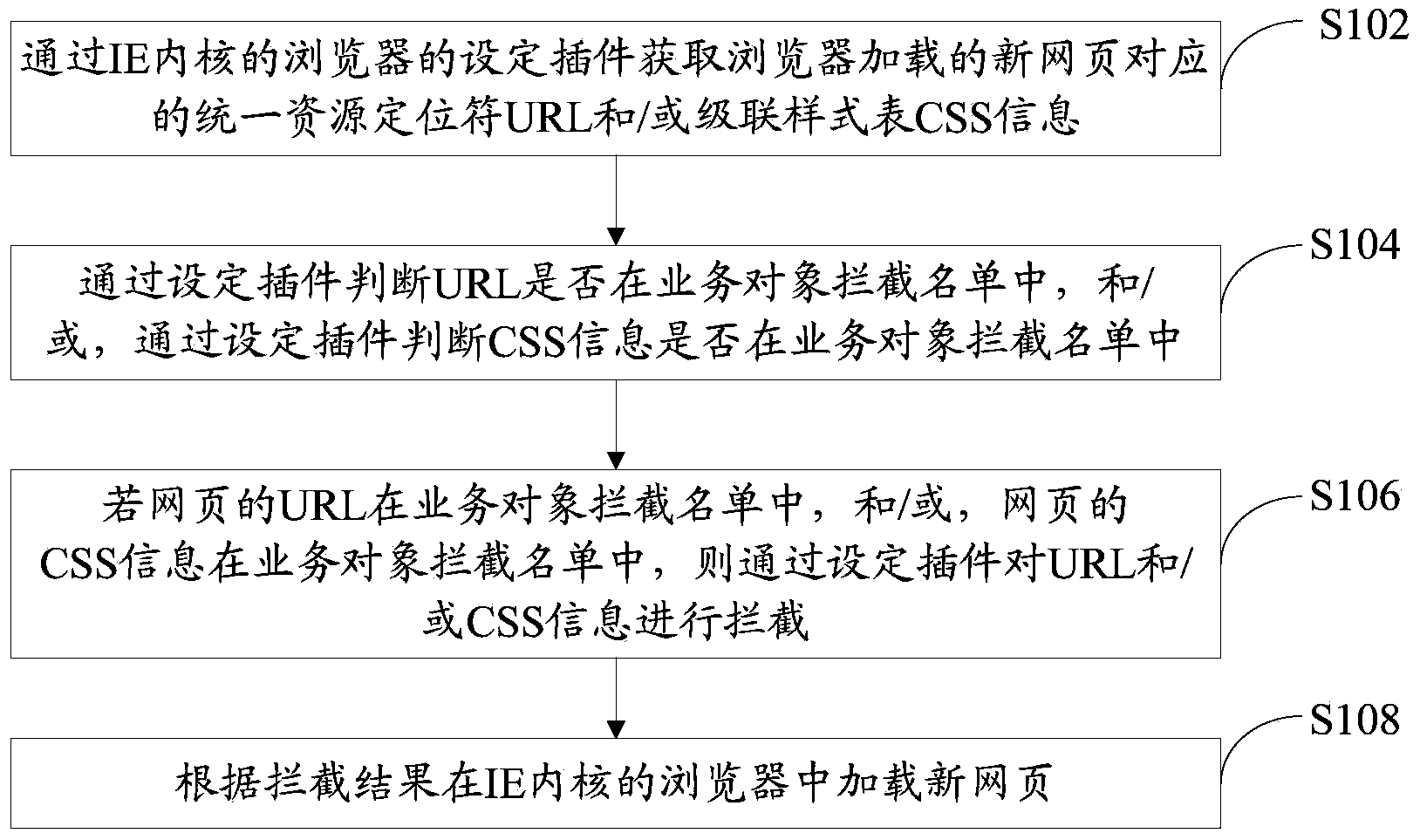
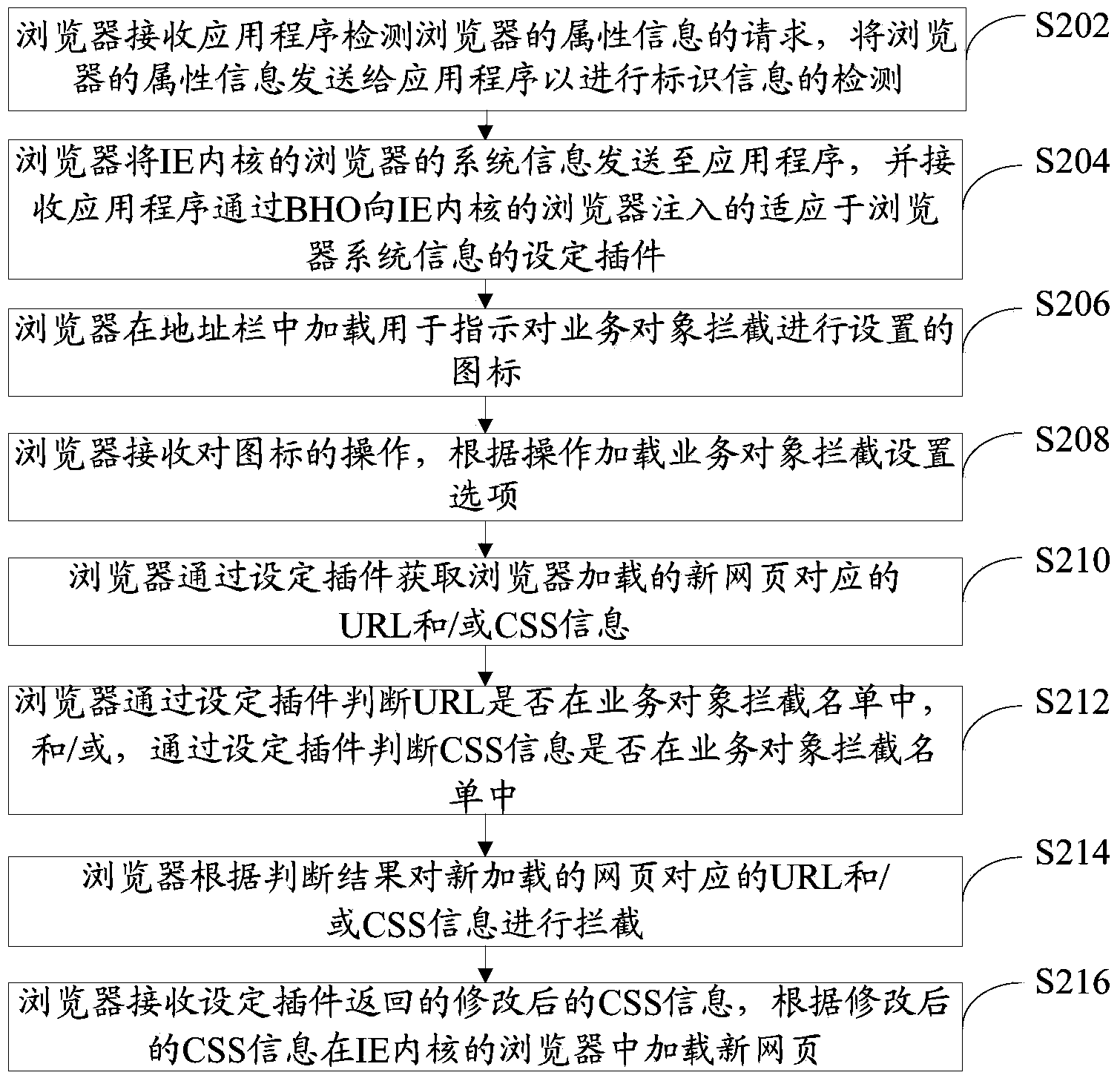
The invention provides a method for intercepting a business object and a browser client. The method comprises the following steps: acquiring URL and / or CSS information corresponding to a new webpage loaded by a browser through a set plug-in of the browser with an IE kernel, wherein the set plug-in is input into the browser with the IE kernel through BHO by an application program which is independent from the browser; judging whether URL is in a business object interception list according to the set plug-in, and / or judging whether the CSS information is in the business object interception list according to the set plug-in; if URL is in the business object interception list and / or the CSS information is in the business object interception list, intercepting the URL and / or the CSS information through the set plug-in; and loading the new webpage into the browser according to the interception result. By adopting the method, the business object can be effectively intercepted when a webpage is loaded to the browser.
Owner:BEIJING QIHOO TECH CO LTD +1
Automatic tray arranging machine
ActiveCN105129339AImplement interceptionAchieve releaseJigging conveyorsConveyor partsEngineeringTransfer mechanism
The invention relates to an automatic tray arranging machine which comprises a rack, a feeding mechanism, a transferring mechanism and a receiving mechanism, wherein materials arrive at the receiving mechanism from the feeding mechanism through the transferring mechanism; the feeding mechanism comprises an interception mechanism, a grab hook is arranged in the interception mechanism, and the materials are intercepted and released by the interception mechanism by virtue of the grab hook; the transferring mechanism comprises a manipulator and a manipulator guide rail; the receiving mechanism comprises a plurality of parallel receiving devices, a plurality of receiver grooves are formed in the receiving devices and are used for placing the materials, and the materials are grabbed by the manipulator in the transferring mechanism after passing through the grab hook in the feeding mechanism and are transmitted to the receiver grooves in the receiving devices along the manipulator guide rail. By using the automatic swinging machine, manpower can be greatly saved, the production efficiency can be improved, and the stable operation of a system can be guaranteed.
Owner:SHENZHEN MATHENTECH INTELLIGENT TECH
Integrated cooking utensil and control method thereof
ActiveCN111189086ASlow down the flowNo need to destroyDomestic stoves or rangesLighting and heating apparatusProcess engineeringMechanical engineering
The invention discloses an integrated cooking utensil. The integrated cooking utensil includes a stove body, a stove arranged at the top of the stove body, and a range hood. The range hood includes anair inlet assembly, an air outlet assembly, a filter assembly and a draught fan system. The draught fan system respectively communicates with the air inlet assembly and the air outlet assembly. The air inlet assembly includes an air inlet channel and an air inlet formed in the air inlet channel. The integrated cooking utensil is characterized in that the filter assembly is arranged in the air inlet channel, and in an oil fume flowing path, the filter assembly includes a first stage oil fume filter module for filtering first particles, a second stage oil fume filter module for filtering secondparticles and a third stage oil fume filter module for filtering third particles, wherein the first stage oil fume filter module, the second stage oil fume filter module and the third stage oil fumefilter module are arranged in sequence from upstream to downstream, and the particle sizes of the first particles, the second particles and the third particles decrease gradually. The invention further discloses a control method of the integrated cooking utensil.
Owner:NINGBO FOTILE KITCHEN WARE CO LTD
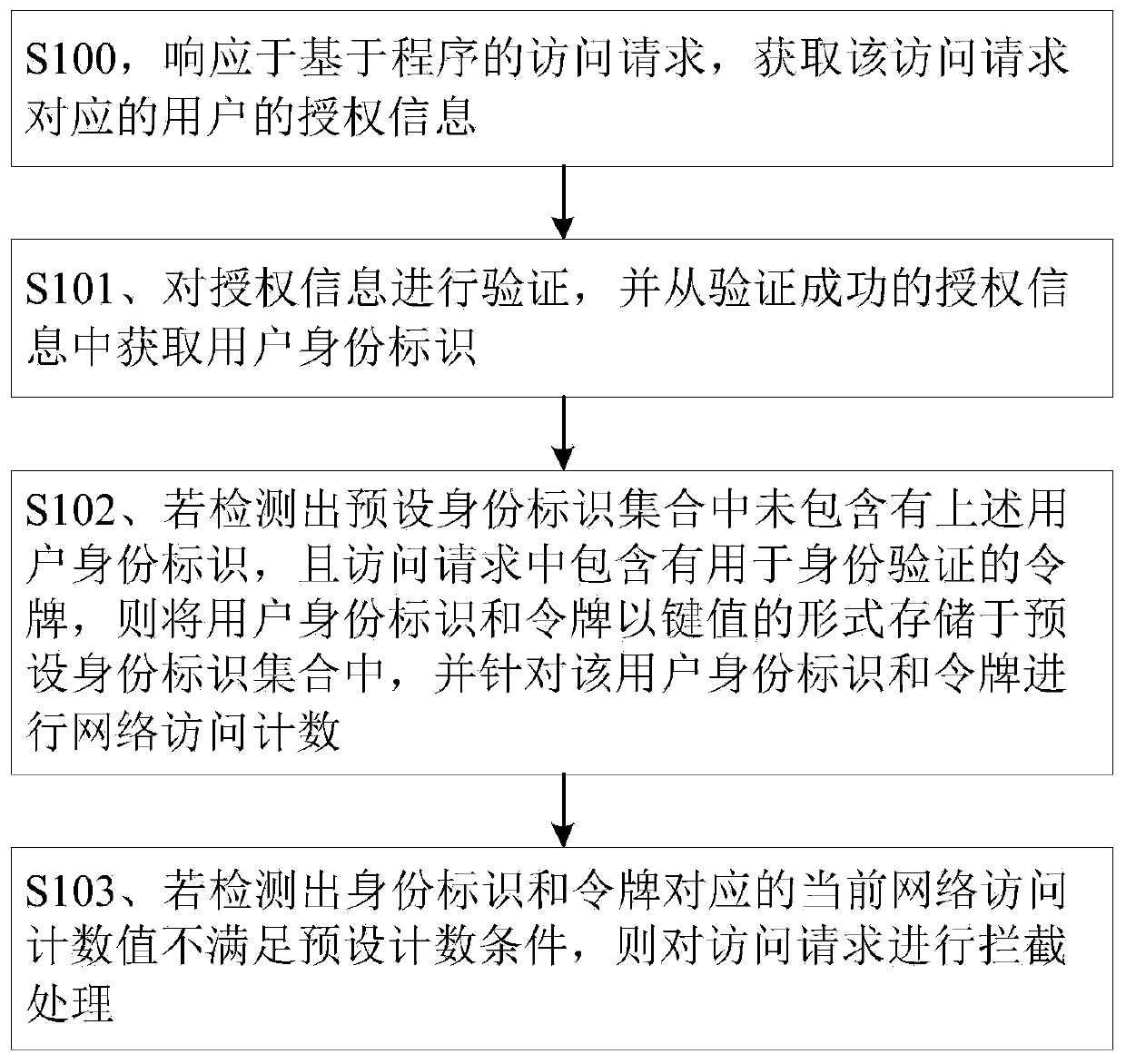
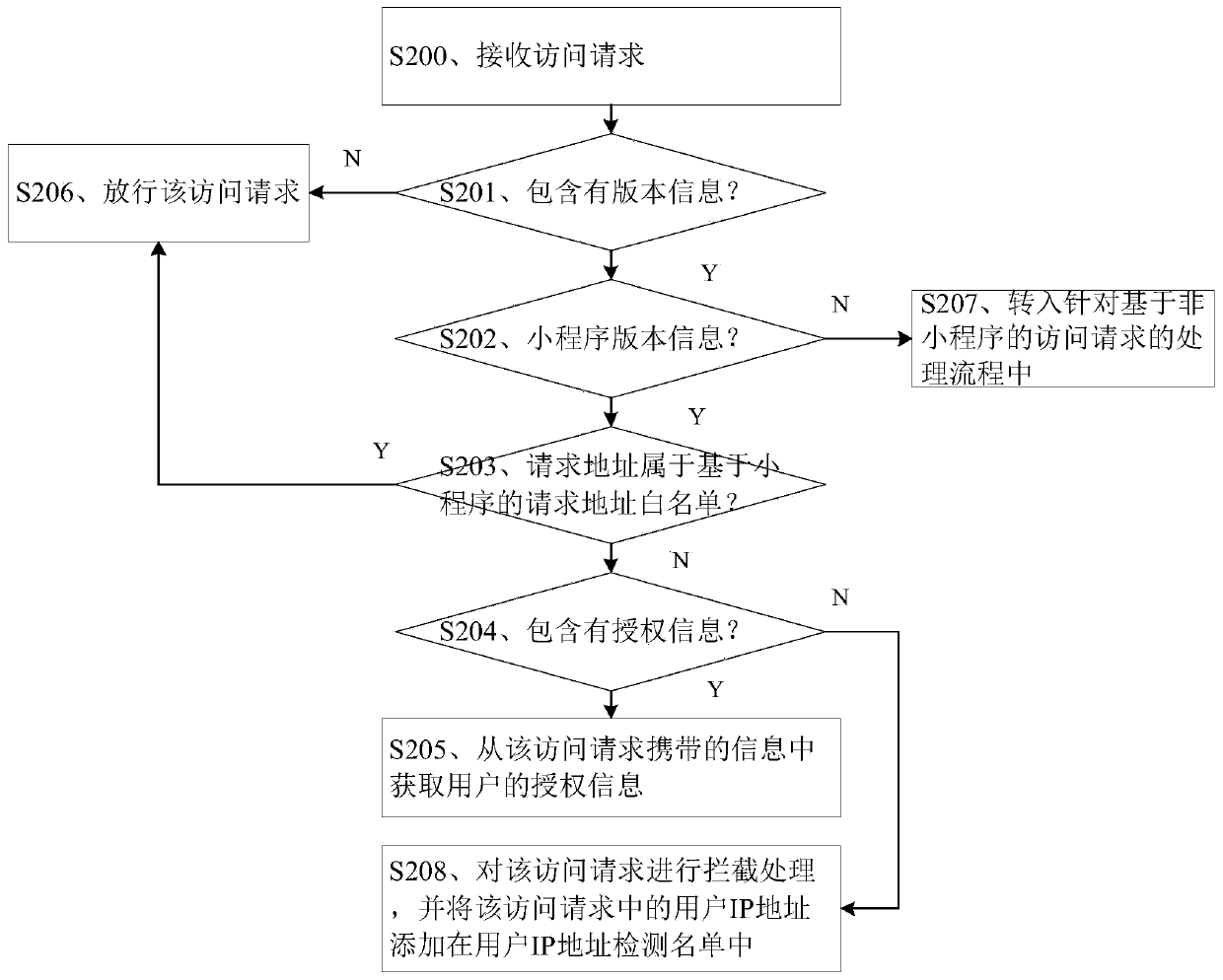
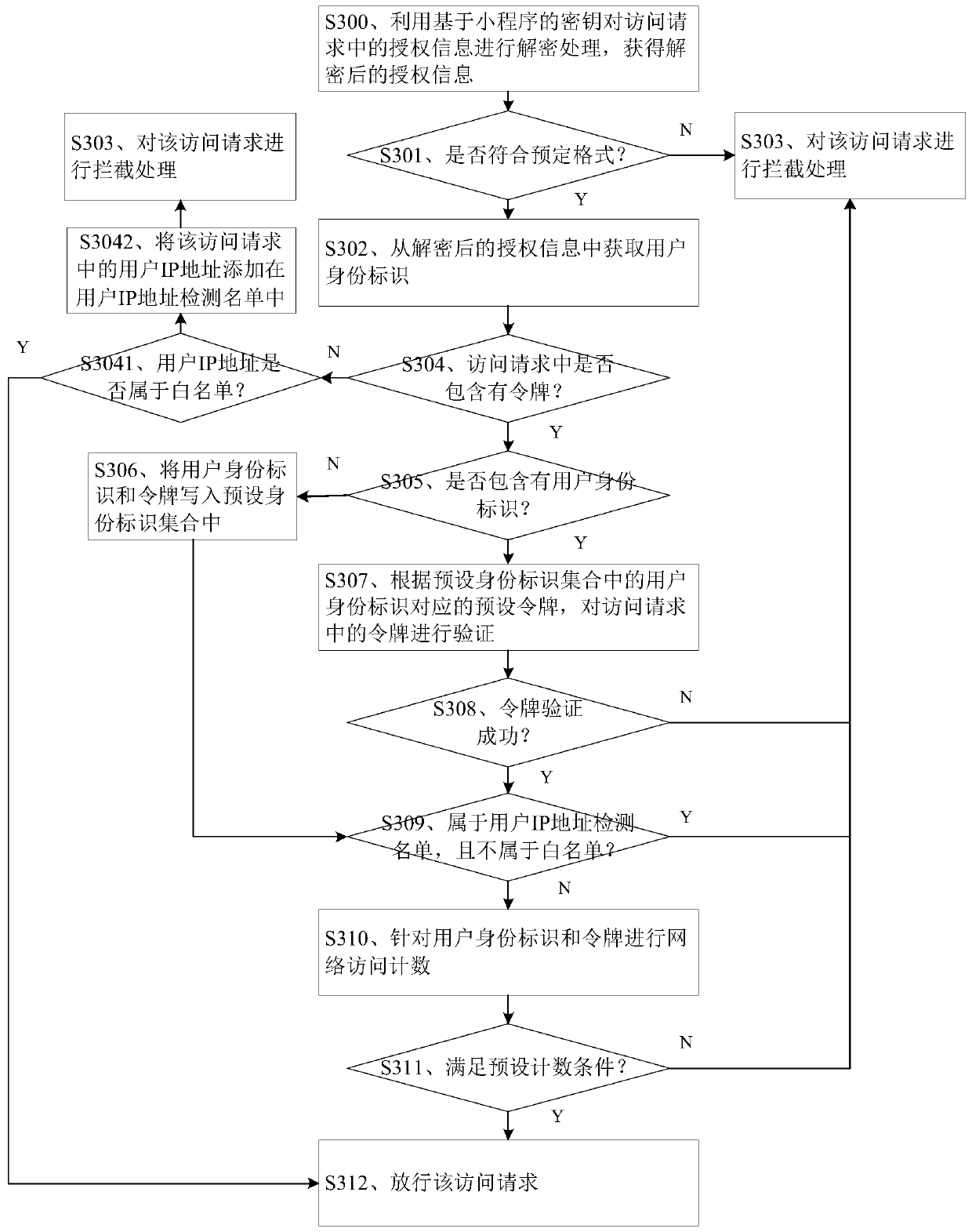
User identity authentication method and device, electronic equipment and storage medium
The embodiment of the invention discloses a user identity authentication method and device, electronic equipment and a storage medium, and the method comprises the steps: responding to an access request based on a program, and obtaining the authorization information of a user corresponding to the access request; verifying the authorization information, and obtaining a user identity identifier fromthe successfully verified authorization information; if it is detected that a preset identity identifier set does not contain the user identity identifier and the access request contains a token foridentity authentication, storing the user identity identifier and the token in the preset identity identifier set in a key value form, and performing network access counting for the user identity identifier and the token; and if it is detected that the identity identifier and the current network access count value corresponding to the token do not meet the preset counting condition, intercepting the access request. According to the method and the device, the harm of network access of illegal users to program and data security can be reduced, and the robustness of the program can be improved.
Owner:BEIJING JINTI TECH CO LTD
System and method for monitoring multimedia message content based on content recognition technology
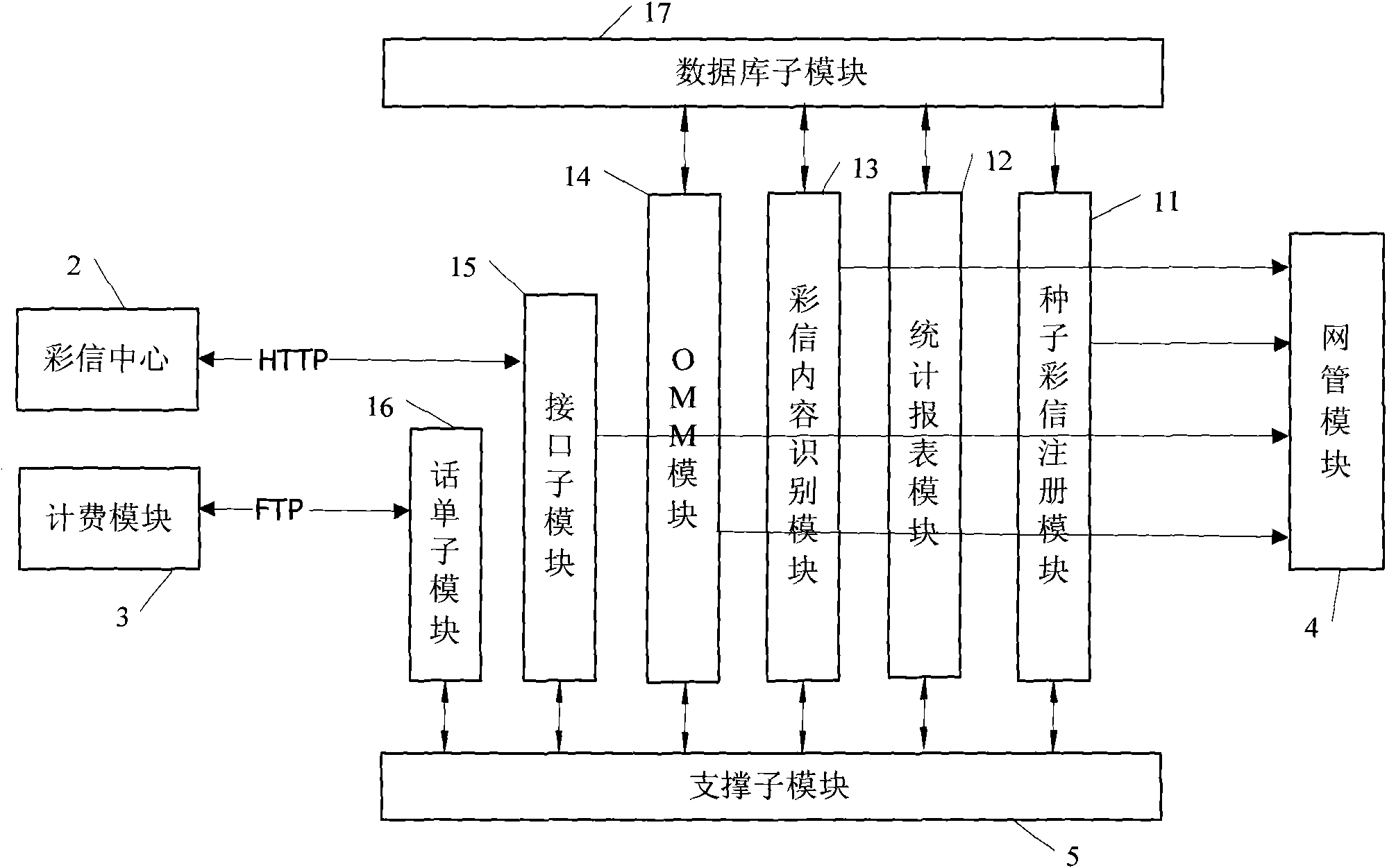
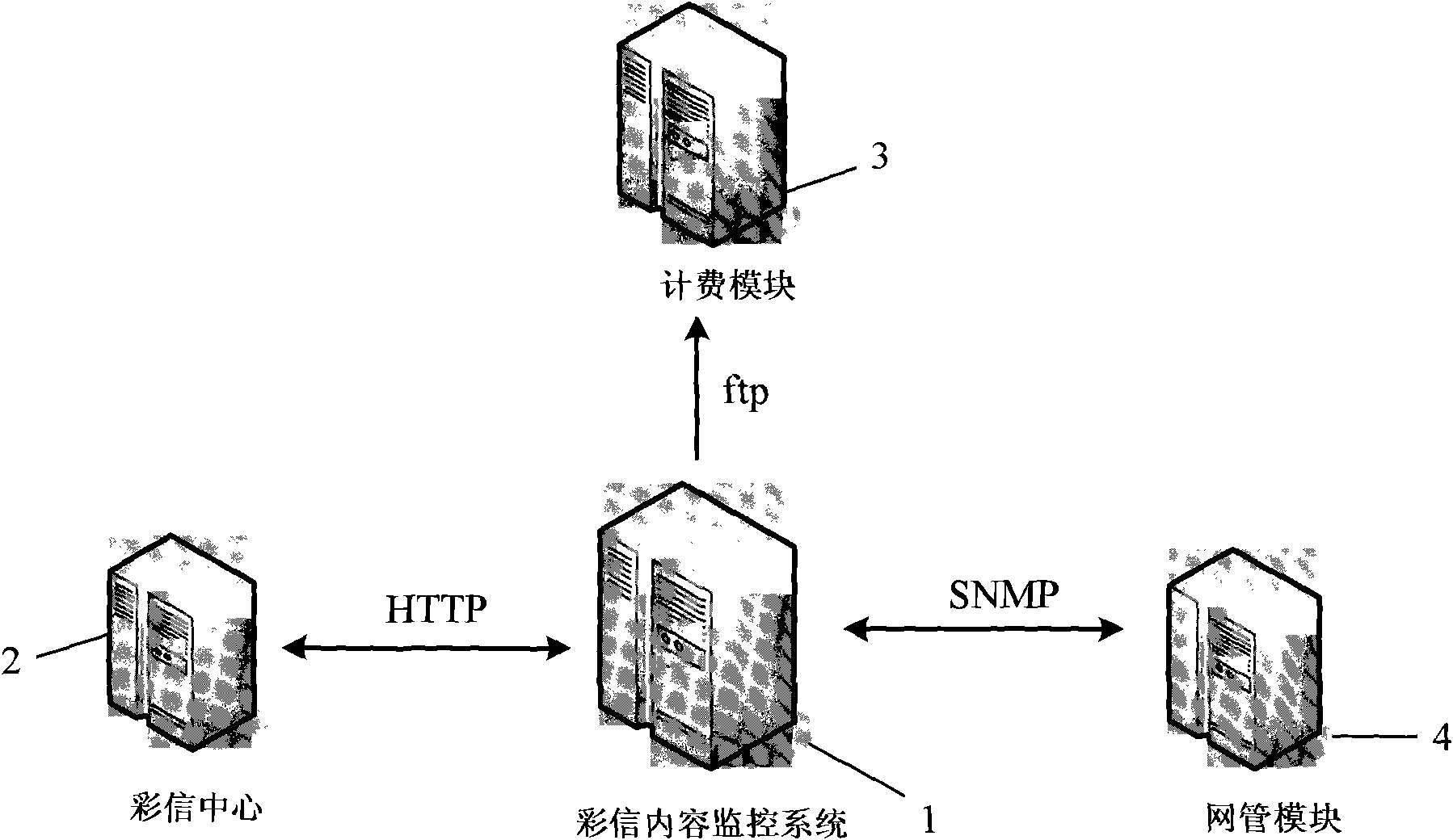
ActiveCN101656927APremium MMS serviceChange processMessaging/mailboxes/announcementsTransmissionStatistical ReportMessage service
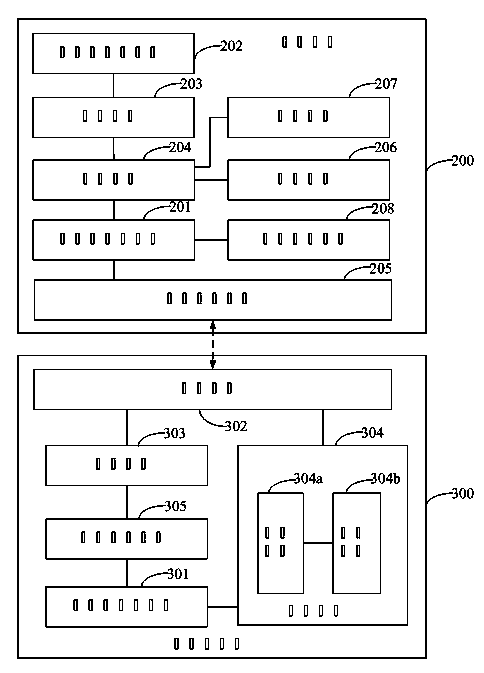
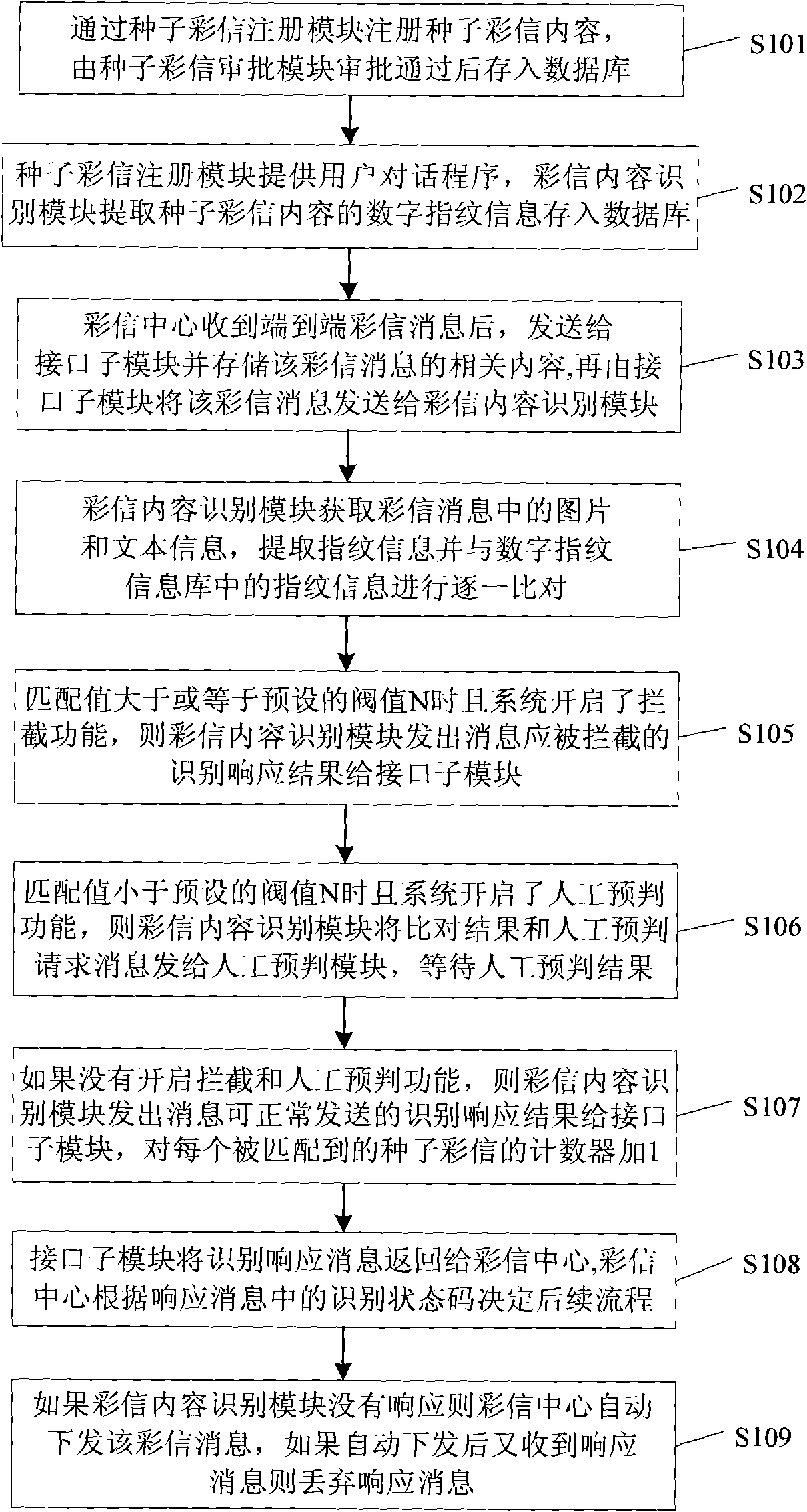
The invention discloses a system and a method for monitoring multimedia message content based on a content recognition technology. Before a multimedia message center transmits multimedia message content to a destination user, the multimedia message content is recognized by the system for monitoring a multimedia message; then, according to a recognition result, legal multimedia messages are transmitted or illegal multimedia messages are intercepted; and a counter is arranged to count the transmitting times of a certain specific multimedia message to release a multimedia message ranking list. The system for monitoring multimedia message content comprises a seed multimedia message register module (11), a multimedia message content recognition module (13), a databank submodule (17), a statistical report module (12), an interface submodule (15) and a telephone bill submodule (16). The method and the system change a multimedia message service process, intercept illegal multimedia messages bycomparing a multimedia message to be recognized with the seed multimedia message and can count the multimedia message content in order to supply good multimedia message service.
Owner:王志强 +1
High risk vehicle real-time alarm releasing system
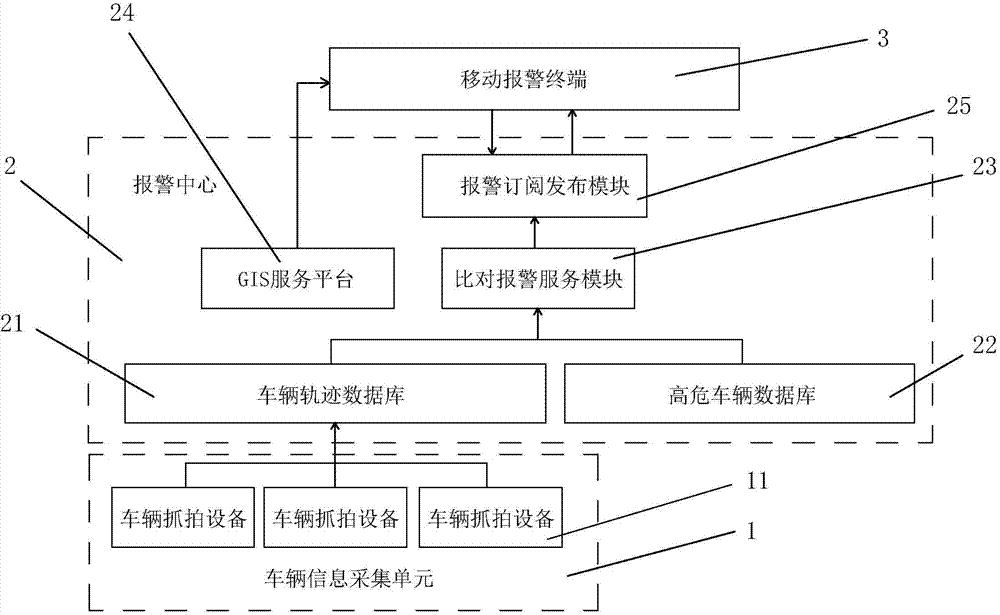
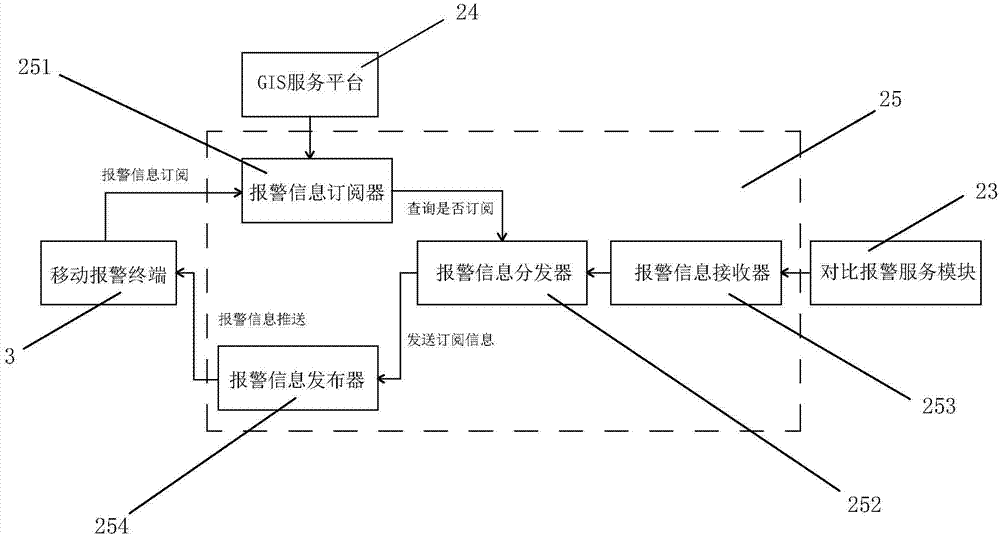
InactiveCN104732770AHave diversityImplement interceptionRoad vehicles traffic controlAlarm messageTrajectory database
The invention provides a high risk vehicle real-time alarm releasing system, and belongs to the technical field of vehicle comprehensive management and control systems. The high risk vehicle real-time alarm releasing system comprises a vehicle information collection unit, an alarm center and a mobile alarm terminal; the alarm center comprises a vehicle track database, a high risk vehicle database, a comparison alarm service module, a GIS service platform and an alarm subscription releasing module; an APP alarm client is arranged on the mobile alarm terminal, alarm services are subscribed through the APP alarm client, the alarm subscription releasing module receives the alarm services subscribed by all the mobile alarm terminals and pushes high risk vehicle alarm information to all the mobile alarm terminals in real time. The high risk vehicle real-time alarm releasing system has the advantages that the high risk vehicle alarm information can be pushed in a targeted mode according to the alarm service subscribed by the mobile alarm terminals, alarm releasing and vehicle intercepting can be quickly achieved, and therefore the vehicle management efficiency is improved; the mobile alarm terminal adopts the additionally loaded APP alarm client, therefore, the alarm means are diverse, and the improvement of the alarm timeliness is facilitated.
Owner:SUZHOU XUNCHUANG INFORMATION TECH CO LTD
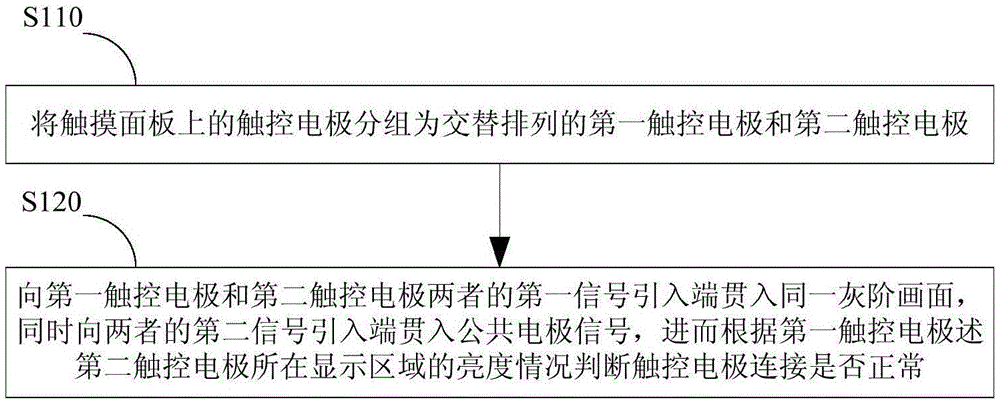
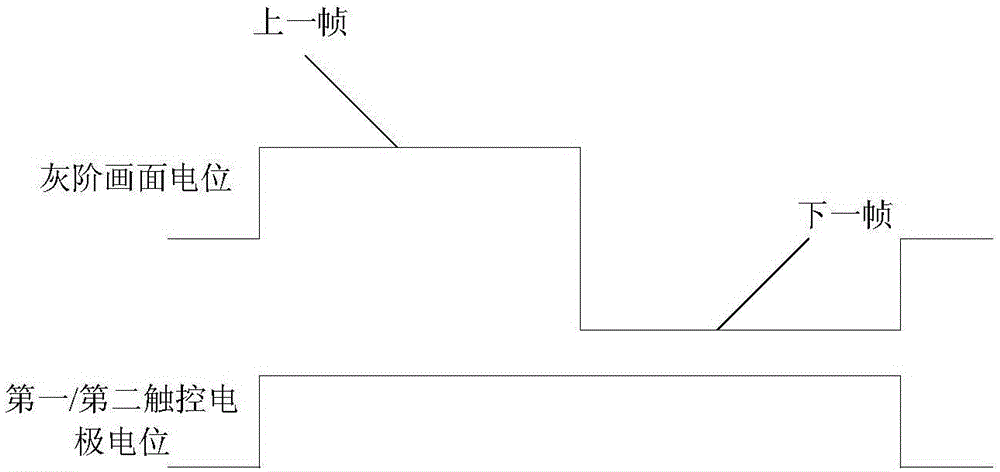
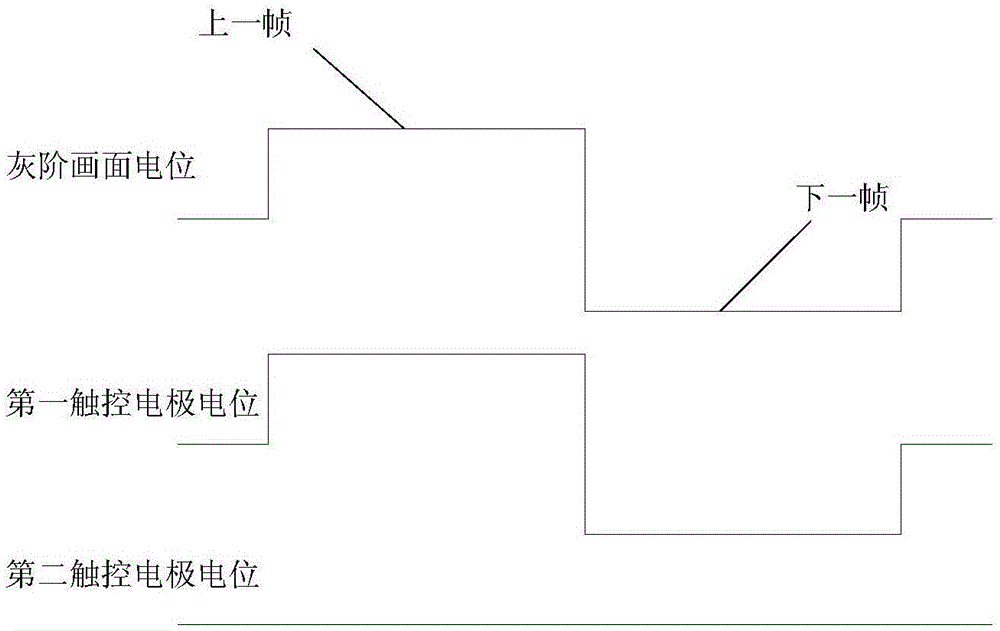
Self-contained embedded touch panel and detection method
ActiveCN105159511AImplement interceptionPrevent waste of resourcesInput/output processes for data processingElectrical polarityComputer science
The invention discloses a self-contained embedded touch panel and a detection method. The method comprises the following steps of grouping touch electrodes on a touch panel into a first touch electrode and a second touch electrode which are alternatively arranged; penetrating pictures of the same gray scale into first signal leading-in ends of the first touch electrode and the second touch electrode, and penetrating corresponding public electrode signals into second signal leading-in ends of the first touch electrode and the second touch electrode so as to judge whether the touch electrodes are normal, wherein when penetrating the pictures of the same gray scale, driving signals with alternative positive and negative polarities are adopted. According to the self-contained embedded touch panel and the detection method, the normal state, the short-circuit condition and the breaker status for connection of the touch electrodes can be detected, so that non-performing products are intercepted to prevent resource waste caused after inflowing the non-performing products, and thus the production cost is reduced.
Owner:WUHAN CHINA STAR OPTOELECTRONICS TECH CO LTD
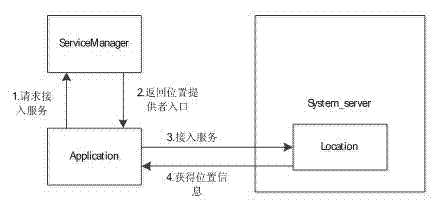
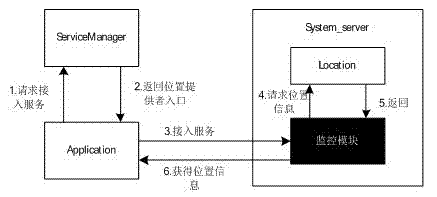
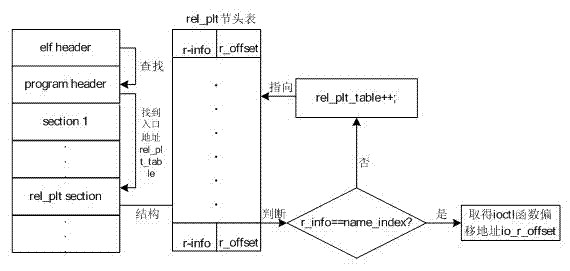
Android platform based GPS (global positioning system) data intercepting control method
InactiveCN103049707AImplement interceptionInterception control implementationDigital data protectionPrivacy protectionTwo step
The invention belongs to the technical field of location privacy protection and provides an Android platform based GPS (global positioning system) data intercepting control method. Without impacting Android system performances, an own location service monitoring module is inserted into a system_server process to achieve intercepting control of GPS data. For achieving GPS data intercepting control of an Android platform, the method includes the two steps of firstly, finding an entry address of an ioctl function during operation of the system_server process, and secondly, loading the own monitoring module at the entry address of the ioctl function in the system_server process so that GPS datagram is intercepted on the bottom layer.
Owner:WUHAN UNIV +1
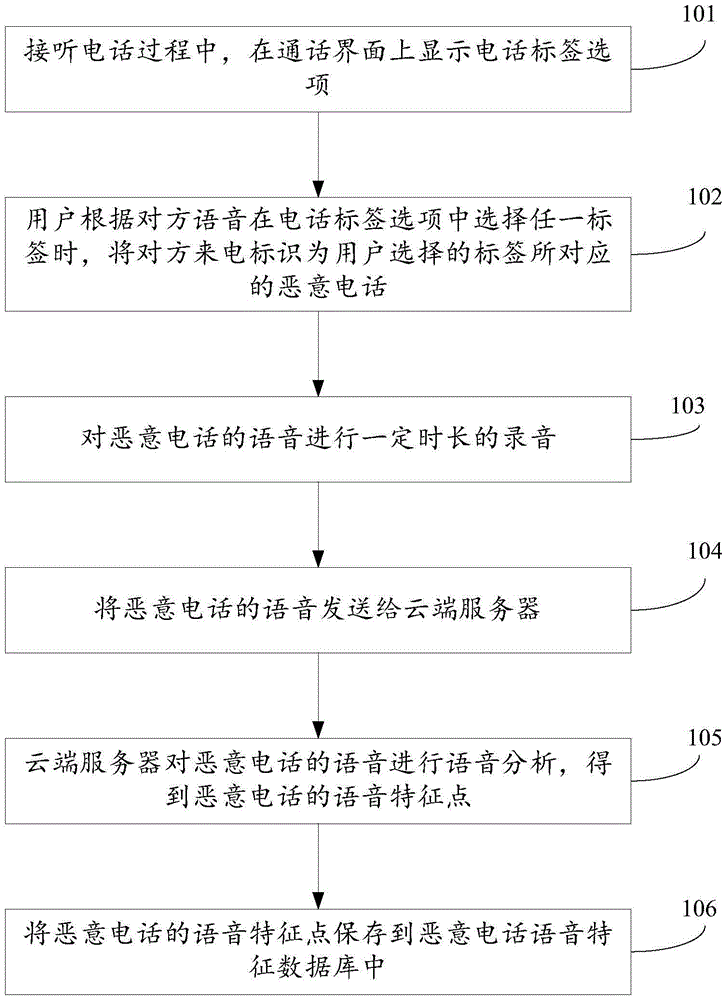
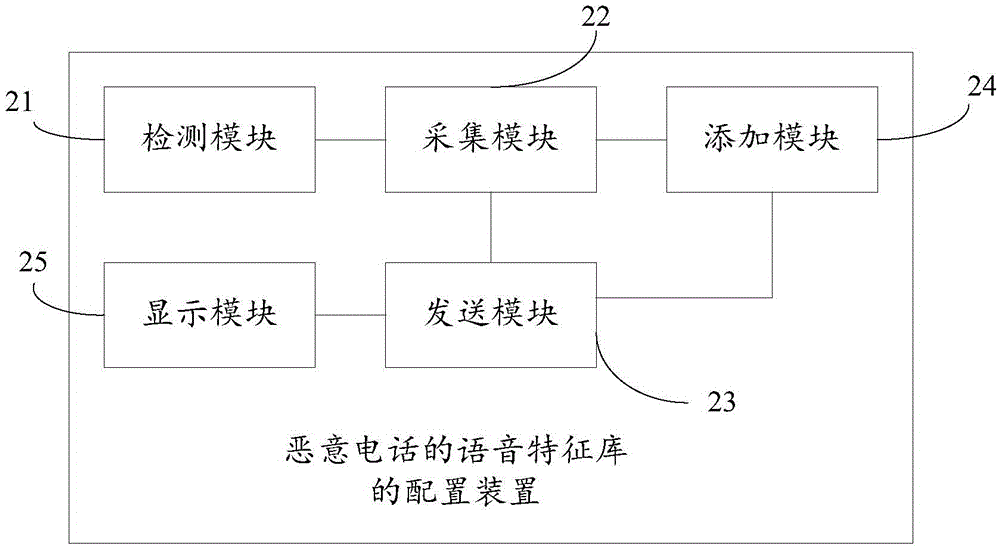
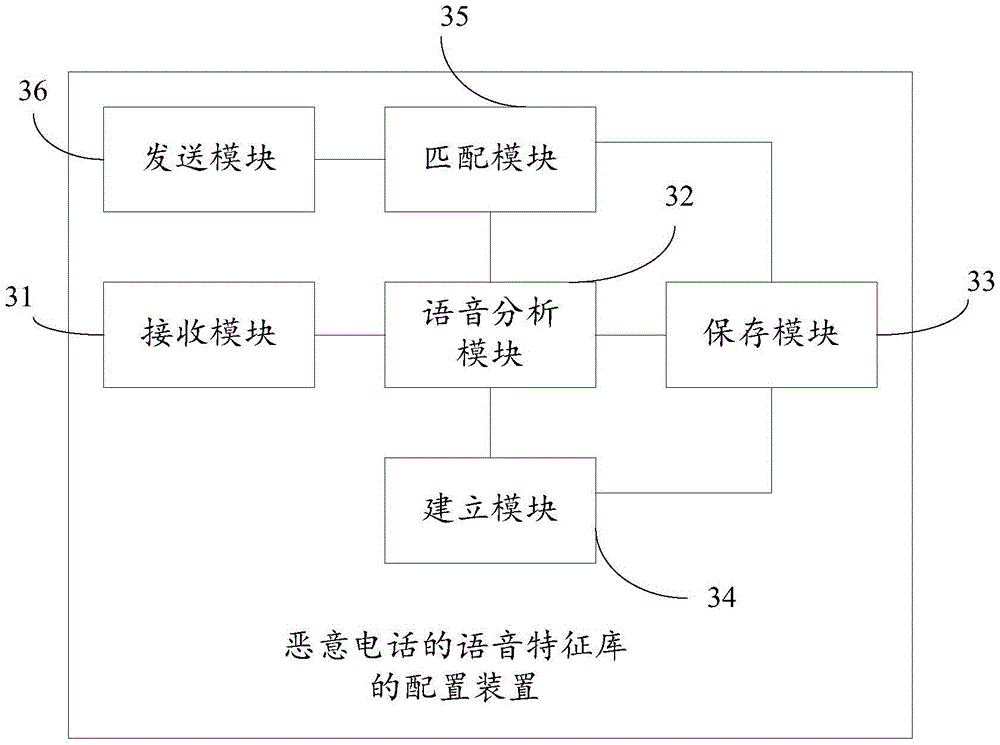
Configuration method and device of speech feature library of malicious calls
InactiveCN106790949AImplement interceptionSupervisory/monitoring/testing arrangementsSubstation equipmentSpeech soundData library
The invention discloses a configuration method and device of a speech feature library of malicious calls. When it is detected that a user selects a malicious call item according to the a user instruction in a call answering process, an incoming call of a calling party is marked as a malicious call, and a speech of the malicious call is recorded for a certain time length; and the speech of the malicious call is sent to a cloud-end server so that the cloud-end server carries out speech analysis on the speech of the malicious call, and obtains speech feature points of the malicious call, and the speech feature points of the malicious call are stored in a speech feature database of malicious calls. Thus, a malicious call which matches the speech feature points can be intercepted.
Owner:BEIJING QIHOO TECH CO LTD +1
Intelligent community access control system with adjustment function and capable of preventing checking omission
ActiveCN107893390AWith adjustment functionImprove securityTraffic restrictionsEngineeringEmbedded system
The invention relates to an intelligent community access control system with an adjustment function and capable of preventing checking omission. The system includes a door frame, a central plate and two monitoring units, the two sides of the central plate are provided with intercepting mechanisms, each intercepting mechanism includes a retractable assembly and two intercepting assemblies, each intercepting assembly comprises a driving unit, a lifting unit and an access control rod, and each retractable unit includes an air pump, an air cylinder, two pistons and two connection units. Accordingto the intelligent community access control system with the adjustment function and capable of preventing the checking omission, through the intercepting mechanisms, vehicle intercepting can be achieved, more convenience is provided for safety check, and when vehicles are allowed to pass, the intercepting mechanisms let the vehicles allowed to pass go at first and then allow following vehicles toenter the door frame for check; in this way, the function of checking vehicles one by one can be achieved, the checking omission can be avoided, and therefore the safety of the access control system is improved; moreover, through the retractable assemblies, the distance of the intercepting assemblies can be flexibly adjusted according to the length of each vehicle to achieve safety check of different types of vehicles, and the practicability is improved.
Owner:华泰智能科技有限公司
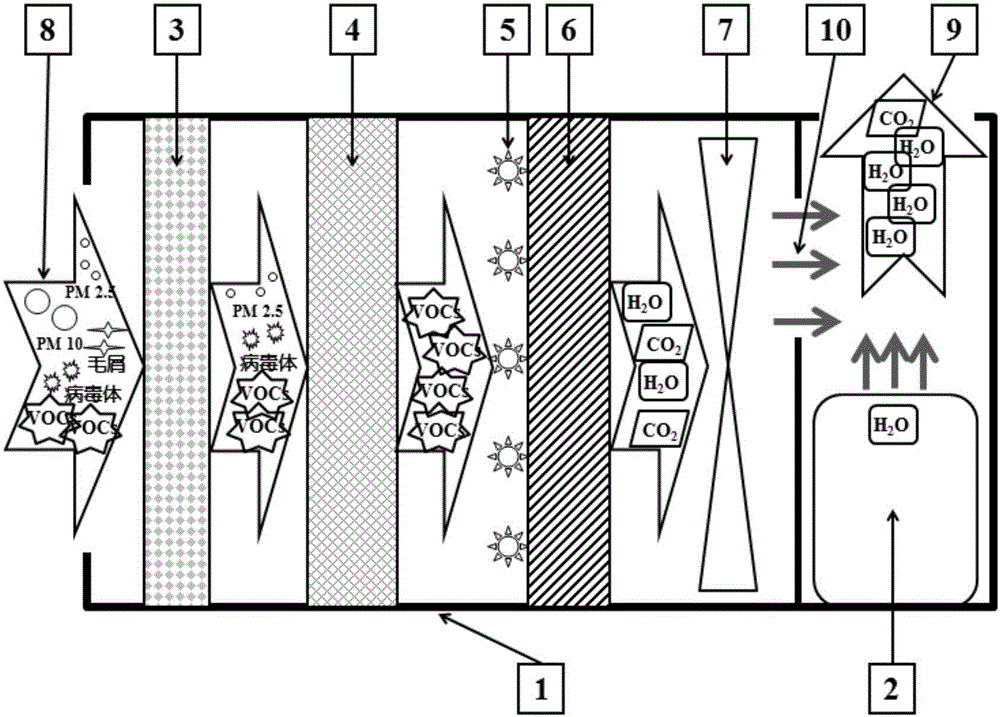
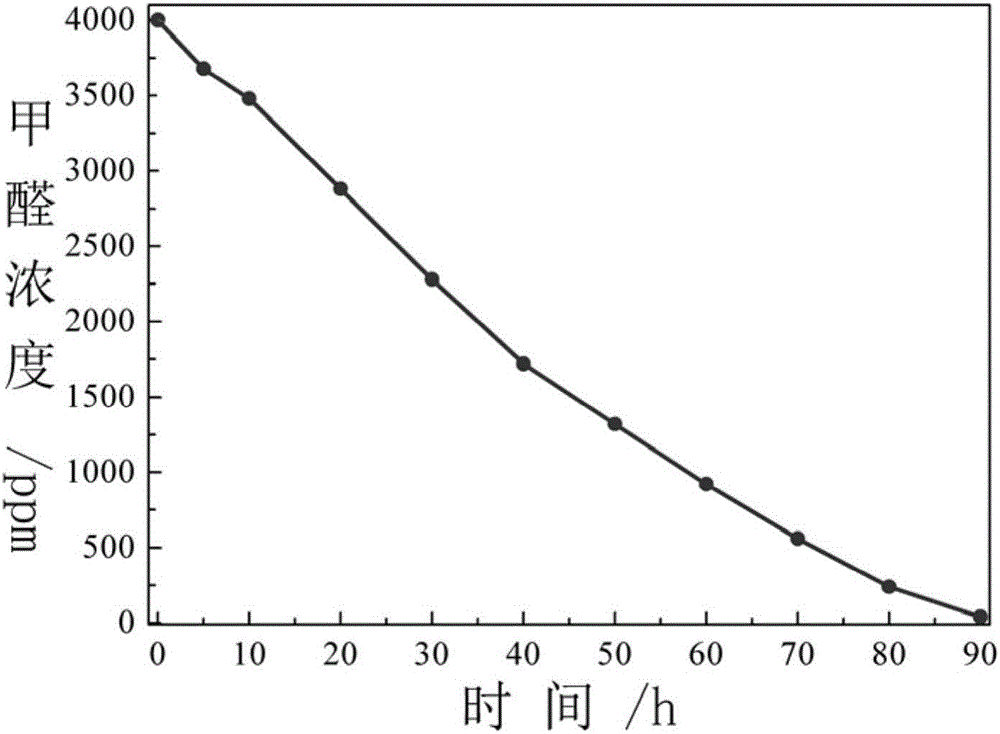
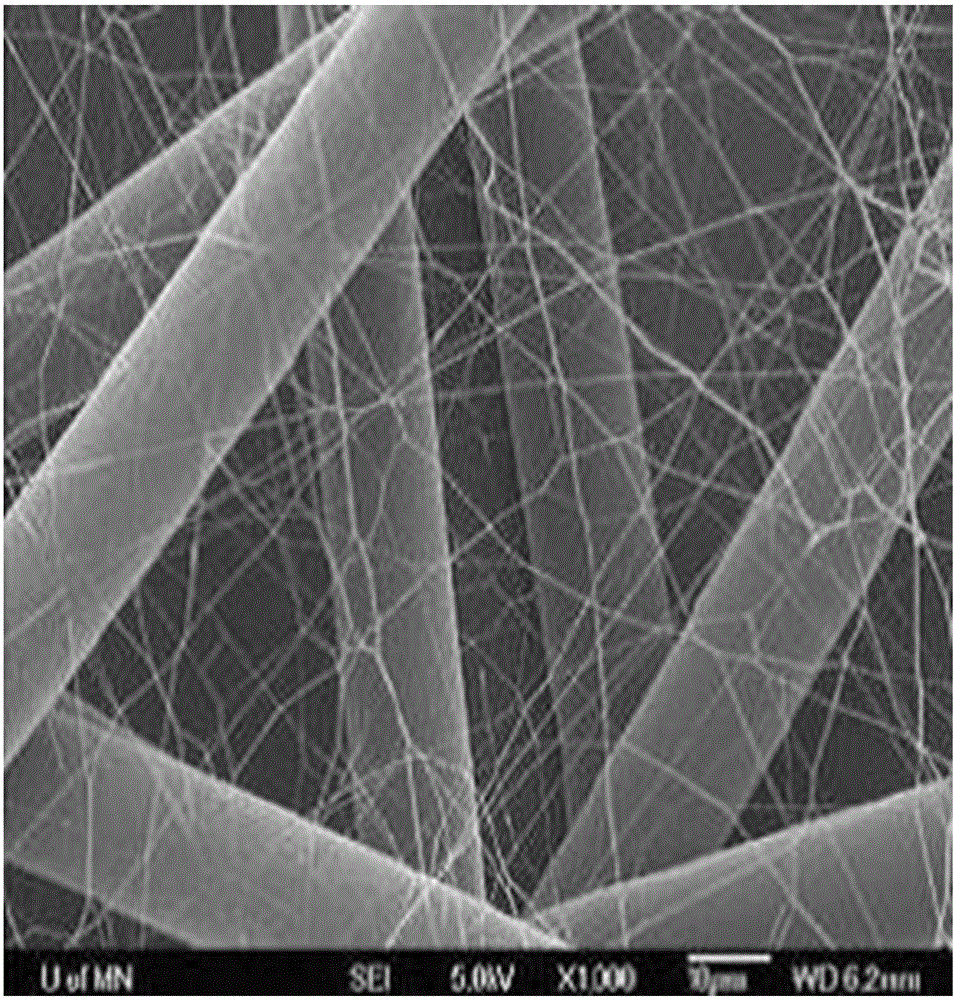
Novel photocatalytic air purifier and method for purifying air
InactiveCN106196321AImplement filteringImplement interceptionMechanical apparatusLighting and heating apparatusAir purifiersNanofiber
The invention discloses a novel photocatalytic air purifier which comprises an air purifier body. The air purifier body comprises a shell. The shell is provided with an air inlet and an air outlet. A primarily efficient filter screen, a high-performance nanofiber filter screen, a visible LED light source, a visible light response photocatalyst filter screen, a circulation fan and a humidification device are sequentially arranged in the shell in the air flowing direction. The air inlet is formed in the side wall of the shell, and the air outlet is formed in the top of the shell. The humidification device is arranged below the air outlet. An electrical circuit and an external power line are further arranged in the shell. According to the purifier, particulate pollutants and virosome of different sizes in air can be efficiently filtered out and intercepted, VOCs of different kinds in the air can be effectively degraded and mineralized, and the humidity of the purified air can be adjusted.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com