Patents
Literature
751 results about "System change" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
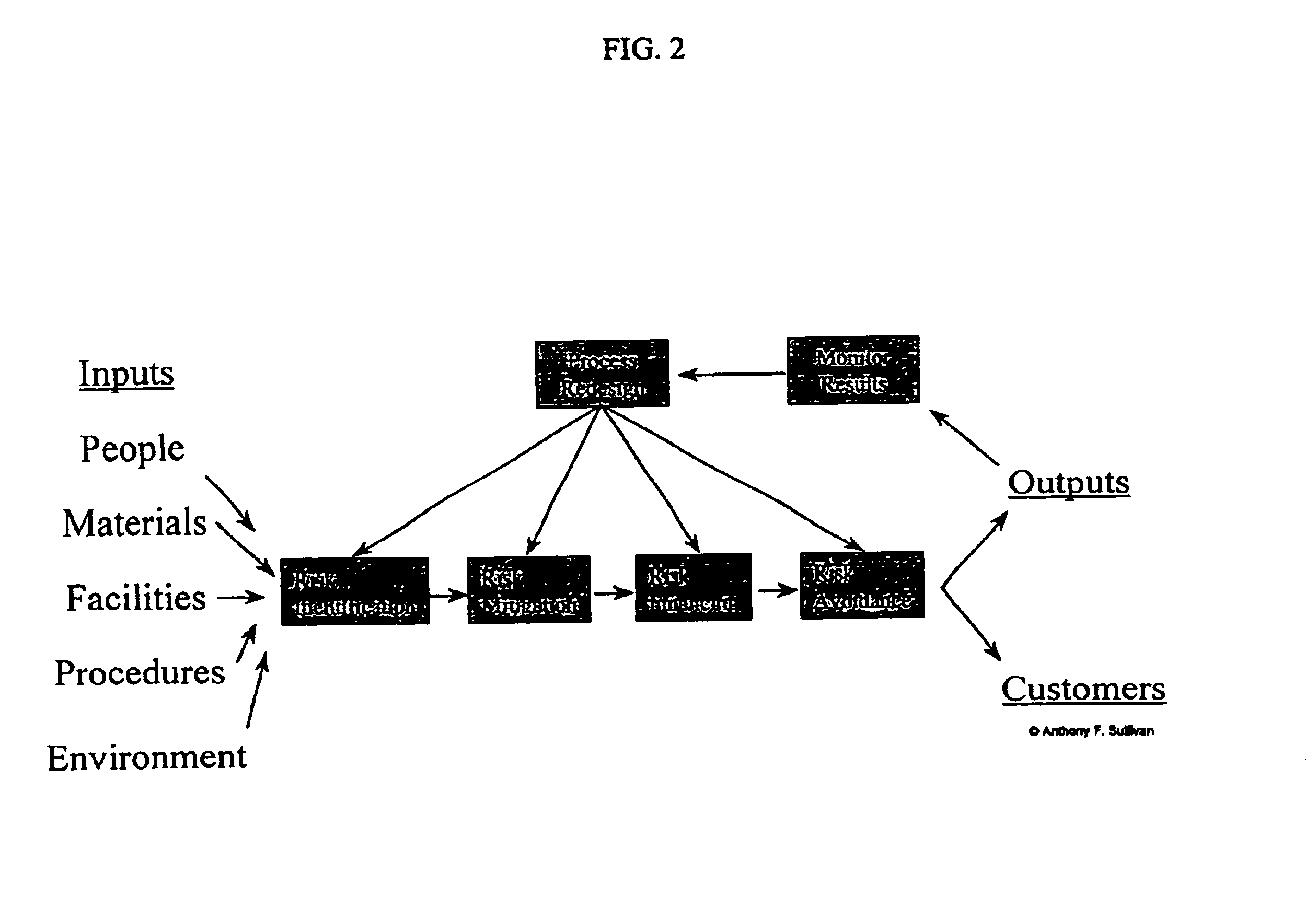
Systems change is about addressing the root causes of social problems, which are often intractable and embedded in networks of cause and effect. It is an intentional process designed to fundamentally alter the components and structures that cause the system to behave in a certain way.
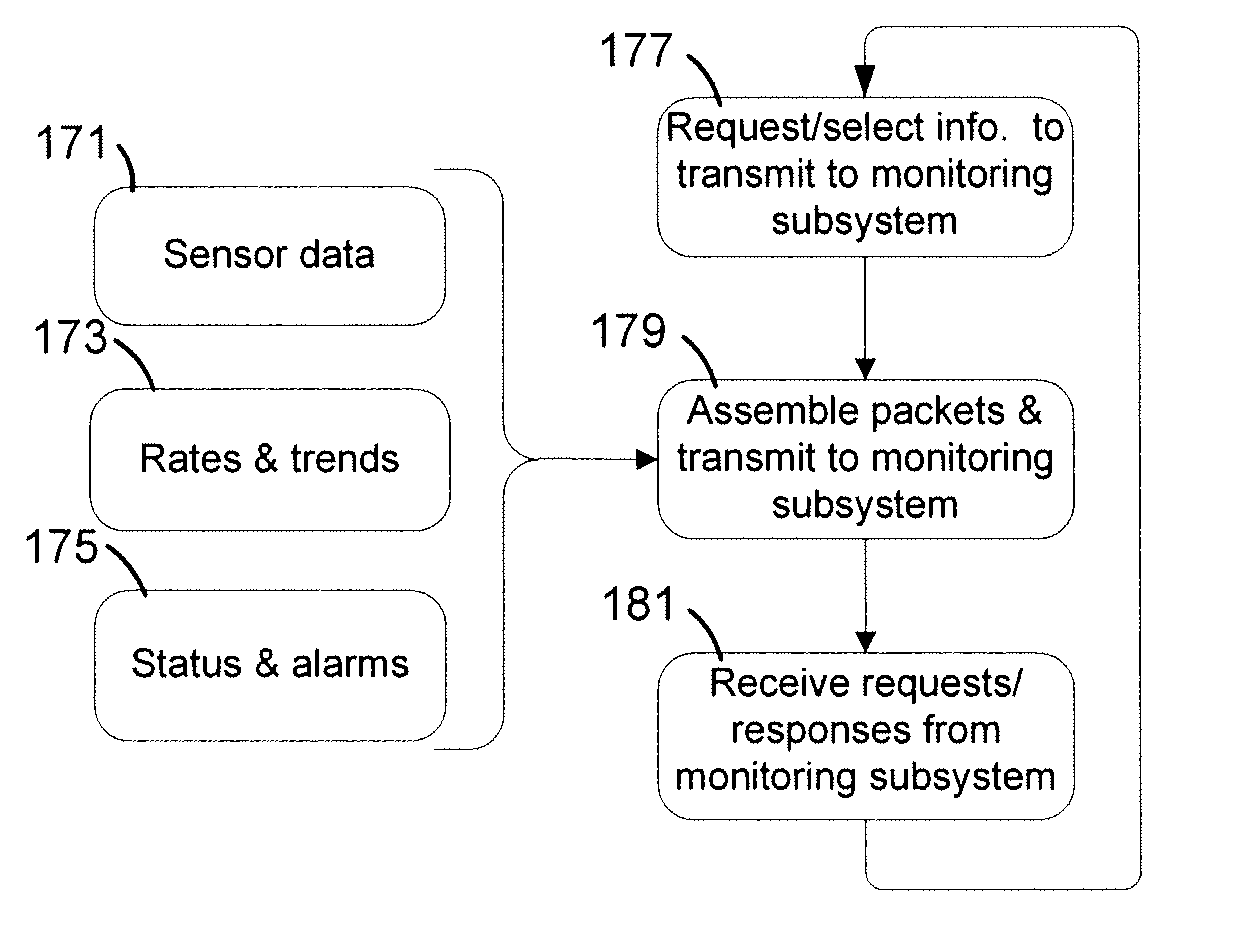
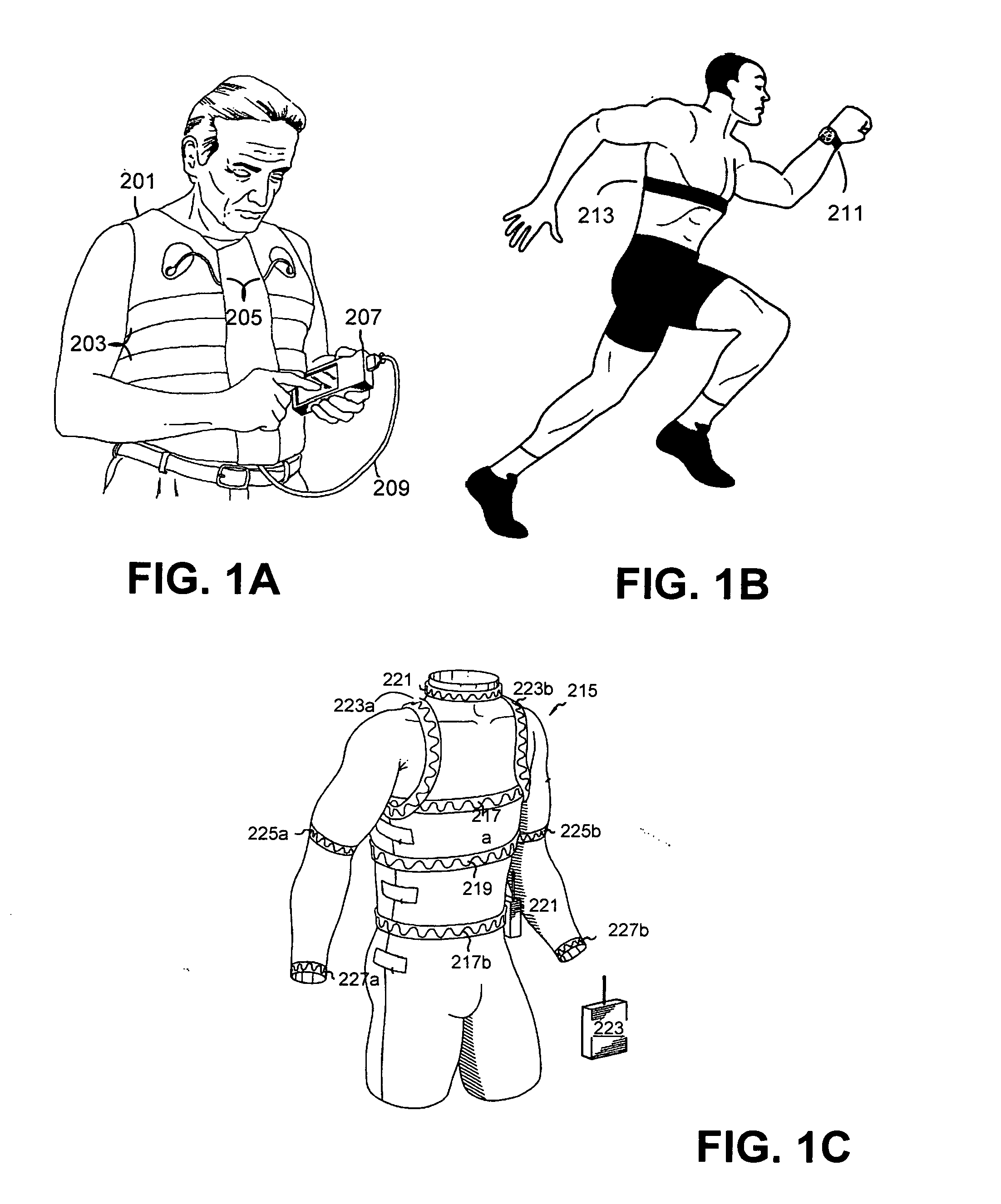
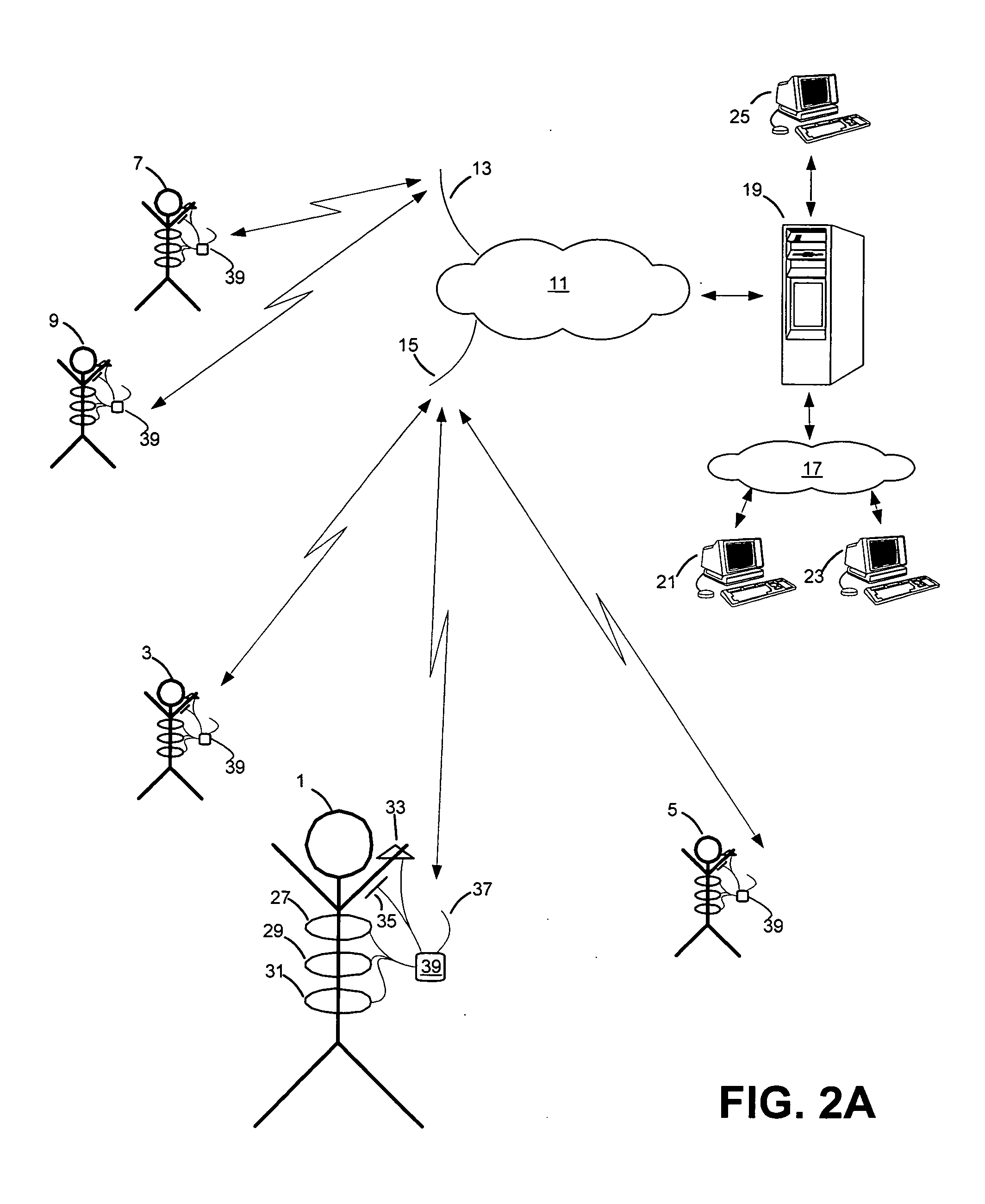
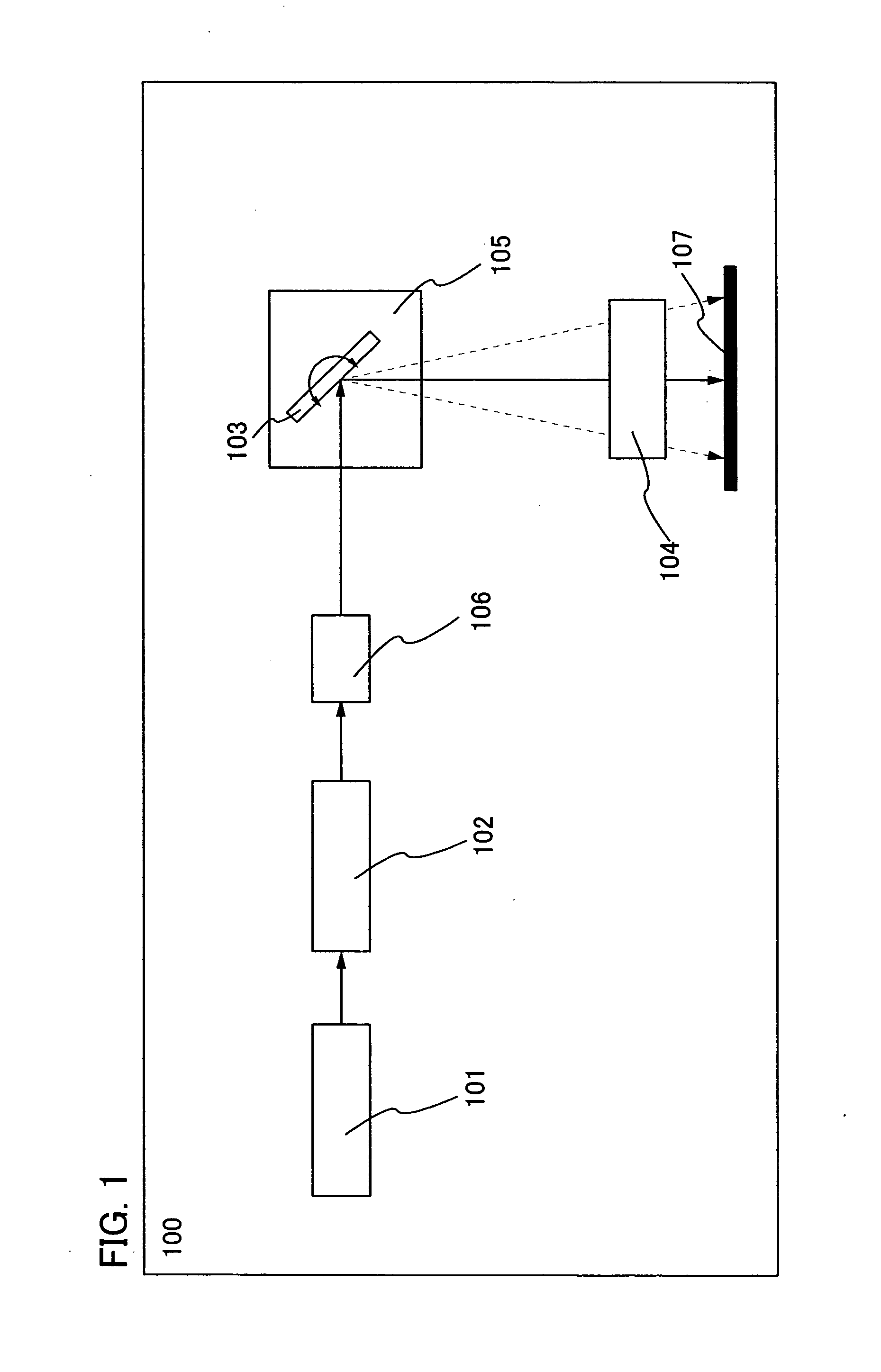
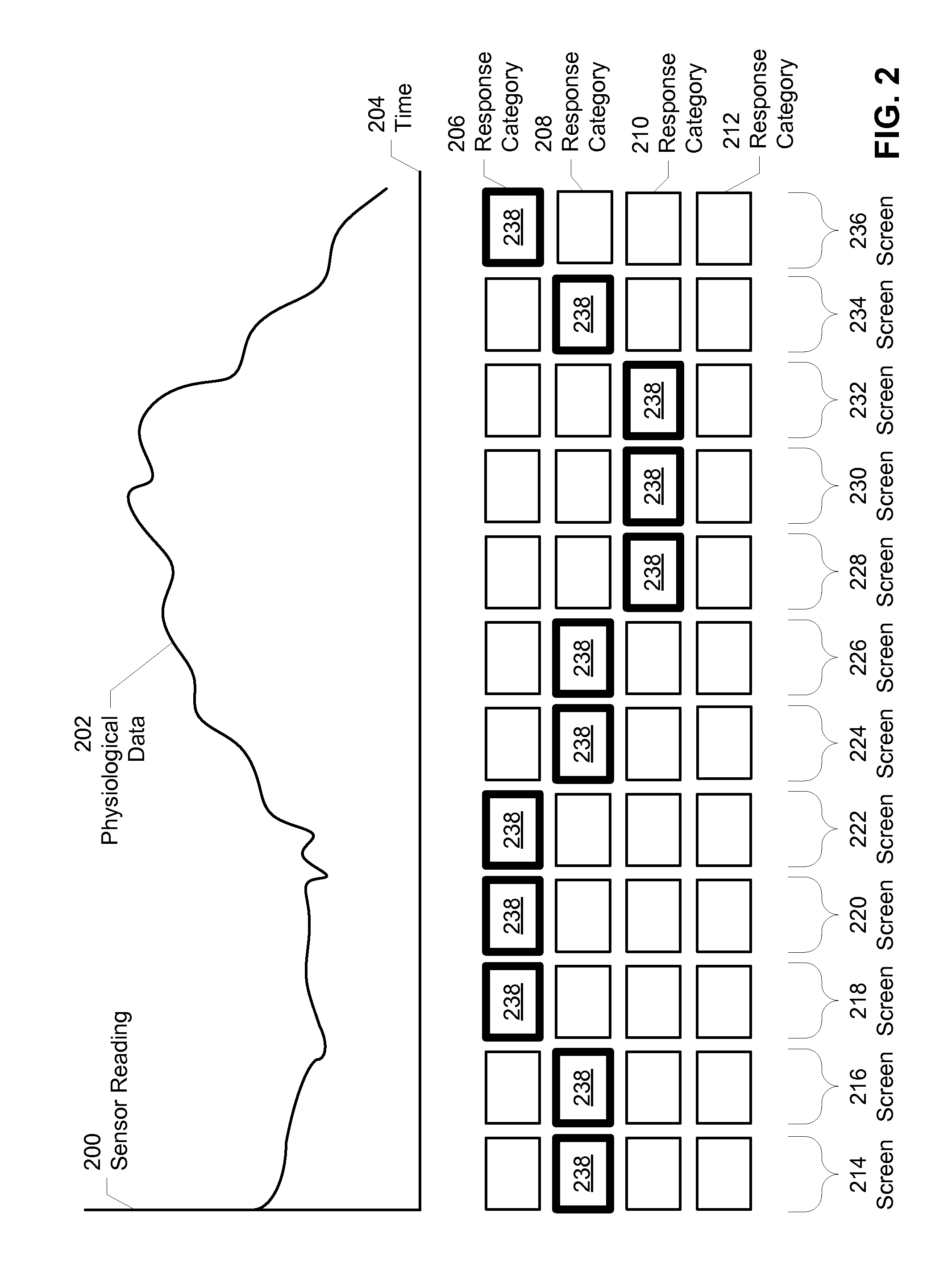
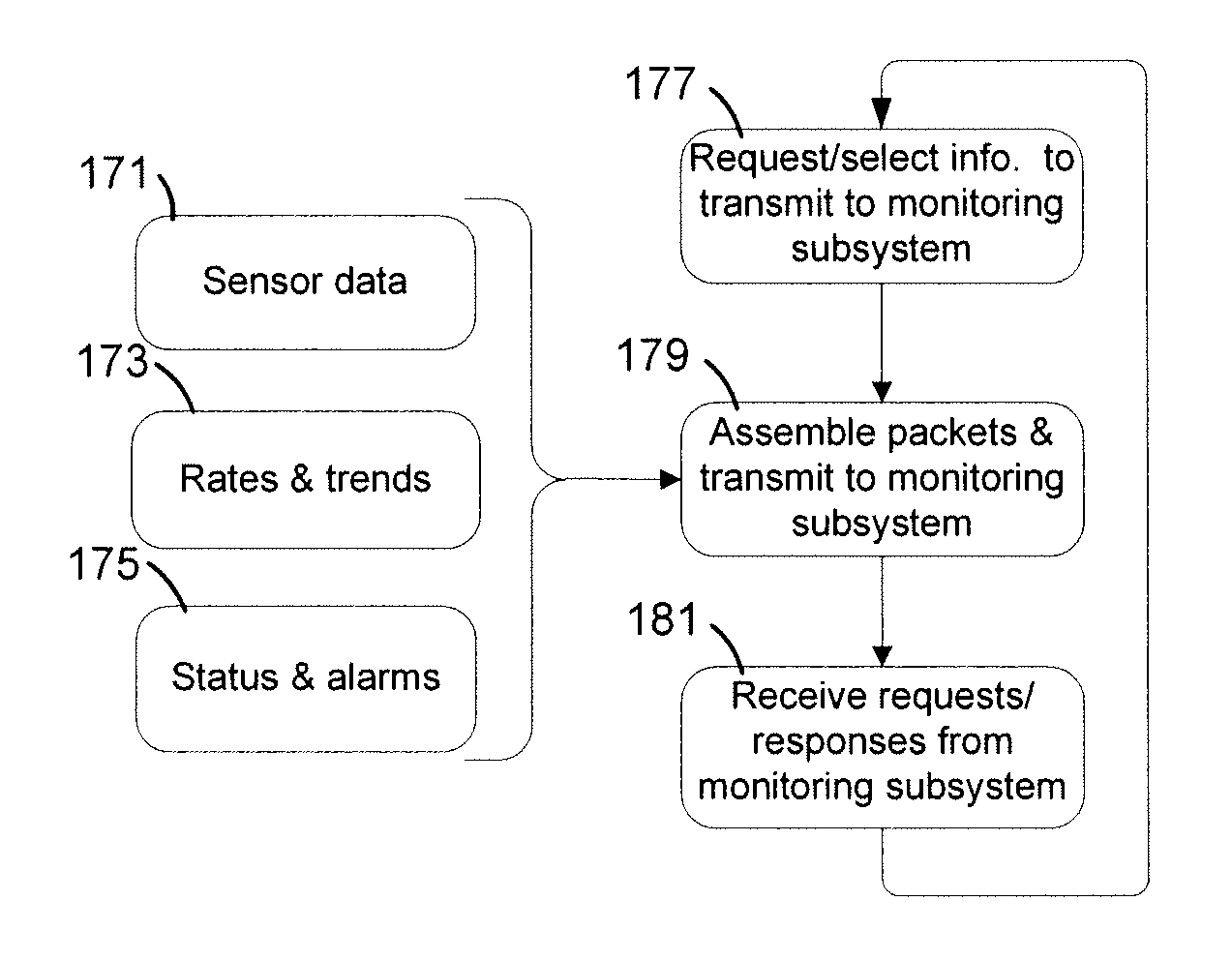
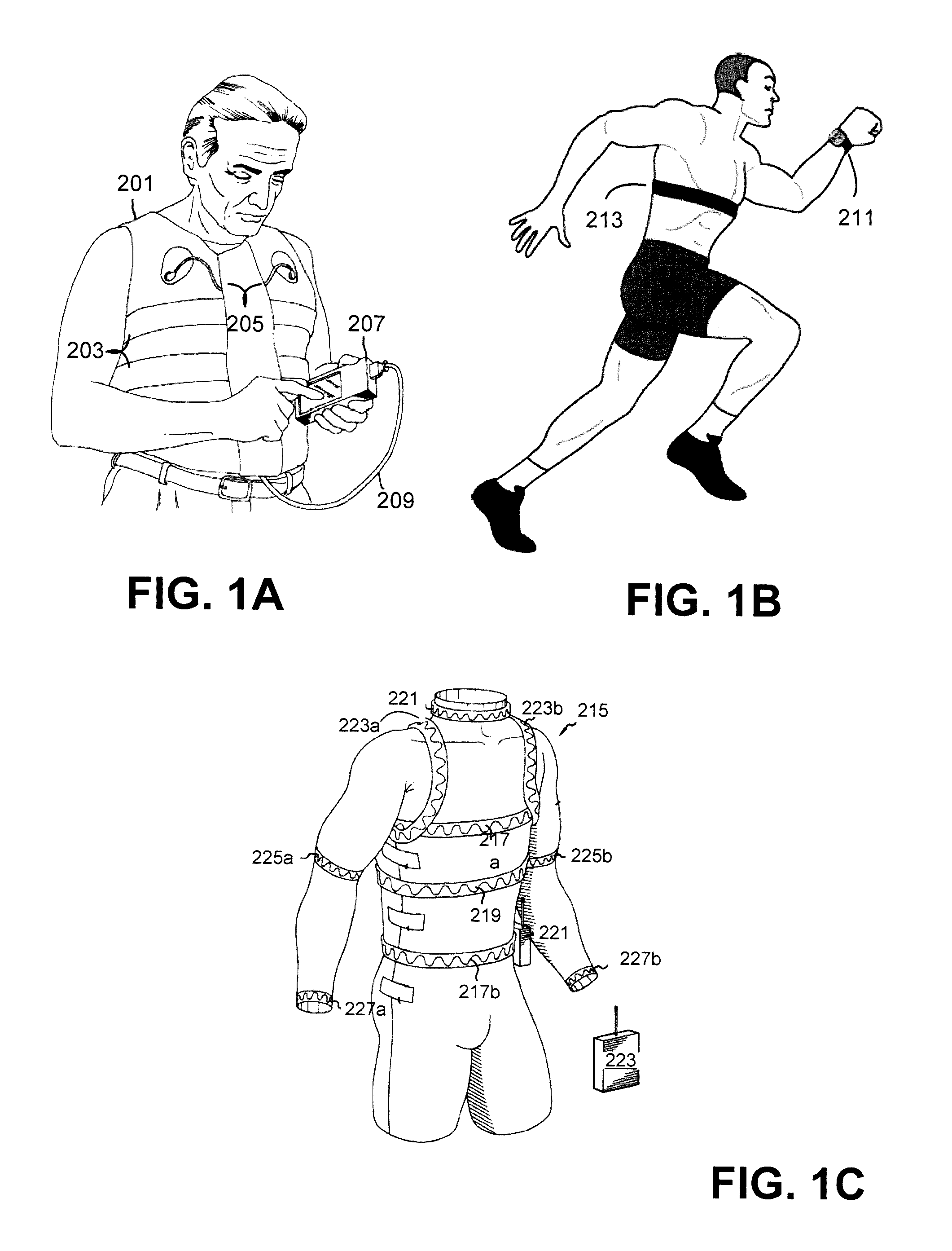
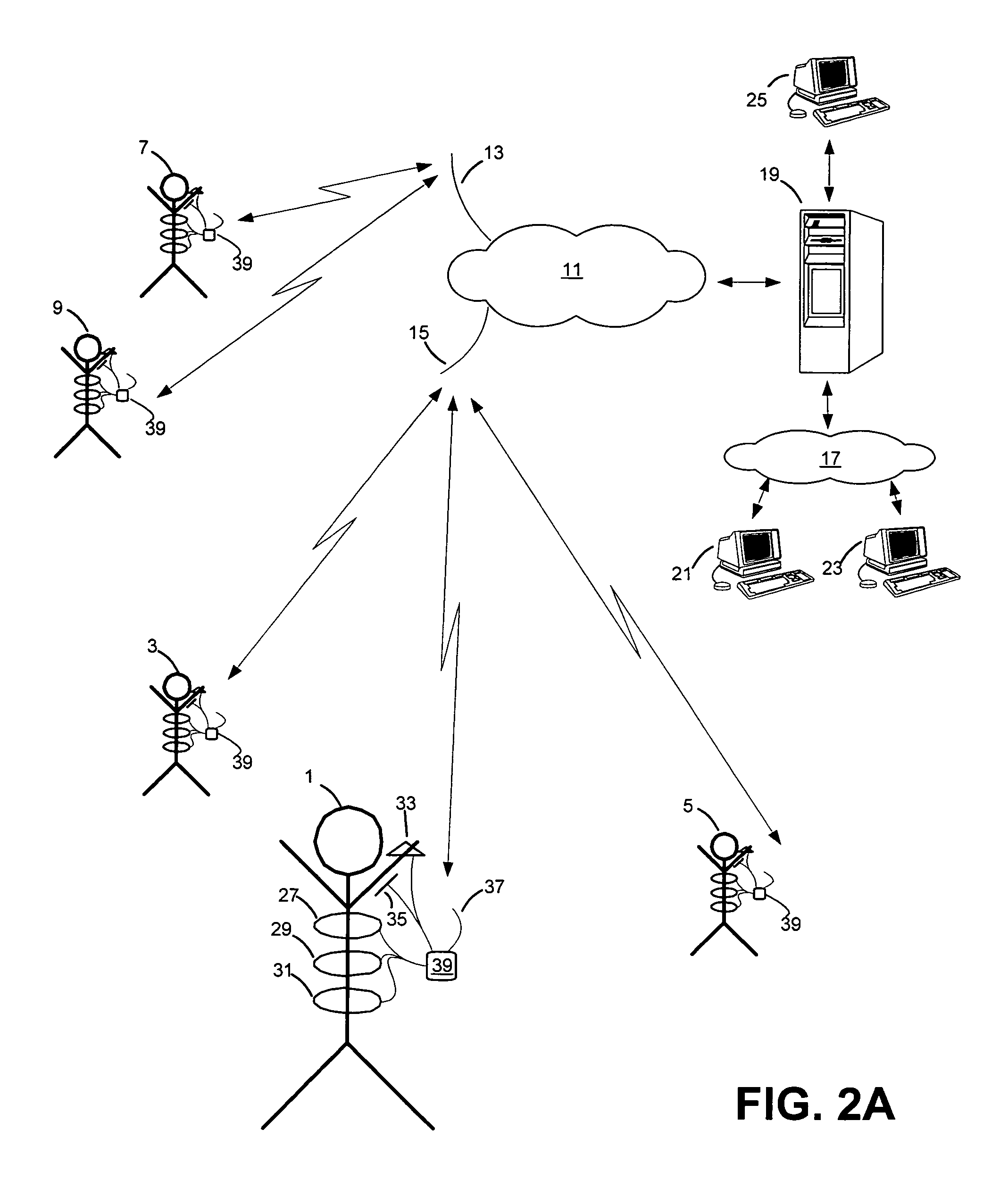
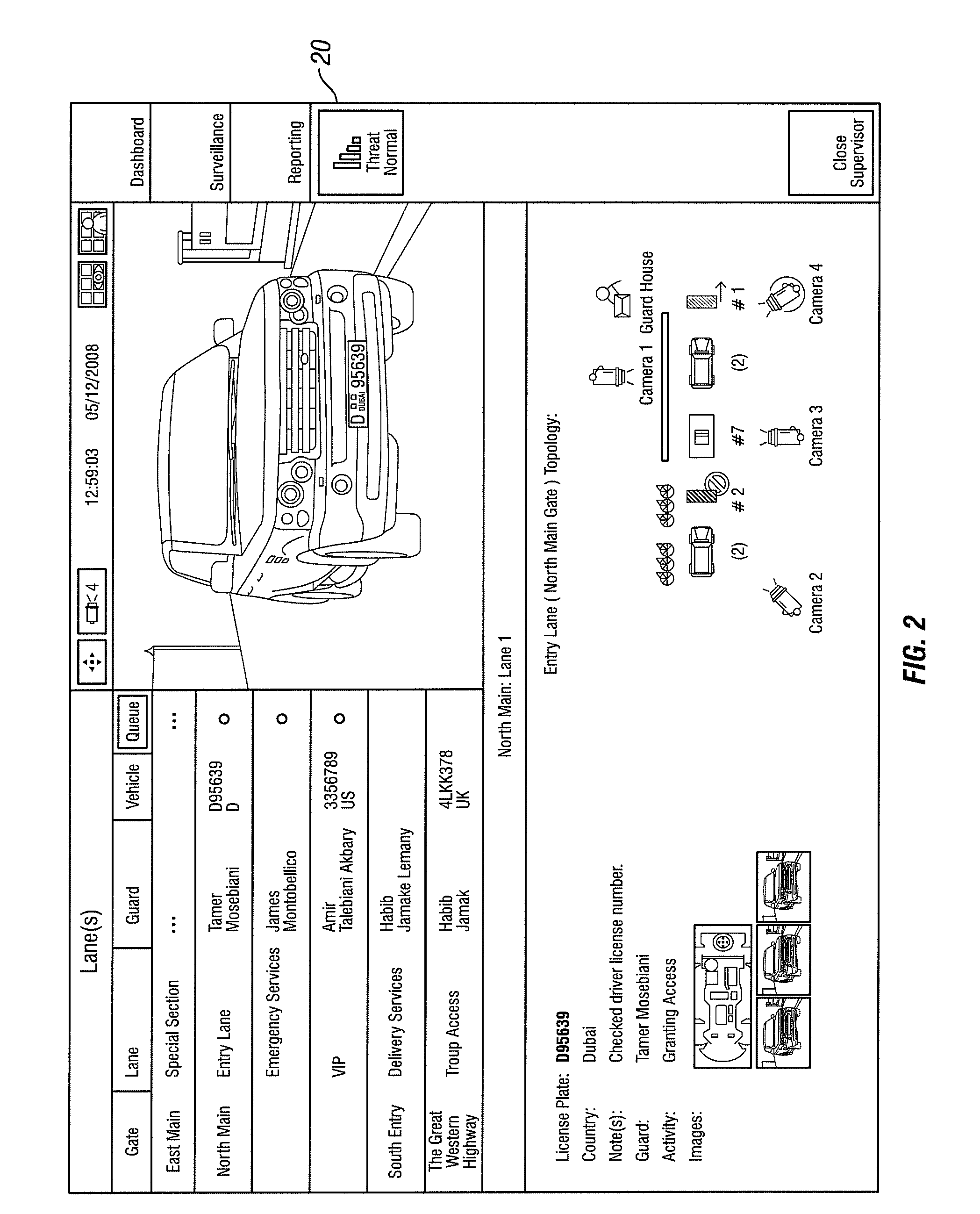
Systems and methods for monitoring subjects in potential physiological distress
ActiveUS20100274100A1Medical communicationPhysical therapies and activitiesPhysiologic StatesSubject matter
The present invention provides systems and methods for monitoring in real time the physiological status of one or more subjects, especially subject engaged in potentially hazardous or dangerous activities. Systems include wearable items with one or more physiological sensors and a local data unit (LDU) operatively coupled to the sensors. The LDUs digitize and filter sensor data, extract physiological parameters, determine abnormal or not acceptable physiological conditions, and communicate to external monitoring facilities. The external facilities display status and data concerning monitored subjects. In preferred embodiments, communication between the LDUs and the external monitoring facilities dynamically adjusts to the condition of the subjects and to system changes such as subjects and external facilities entering and leaving and / or moving from place to place. The invention also provides program products for performing this invention's methods.
Owner:ADIDAS
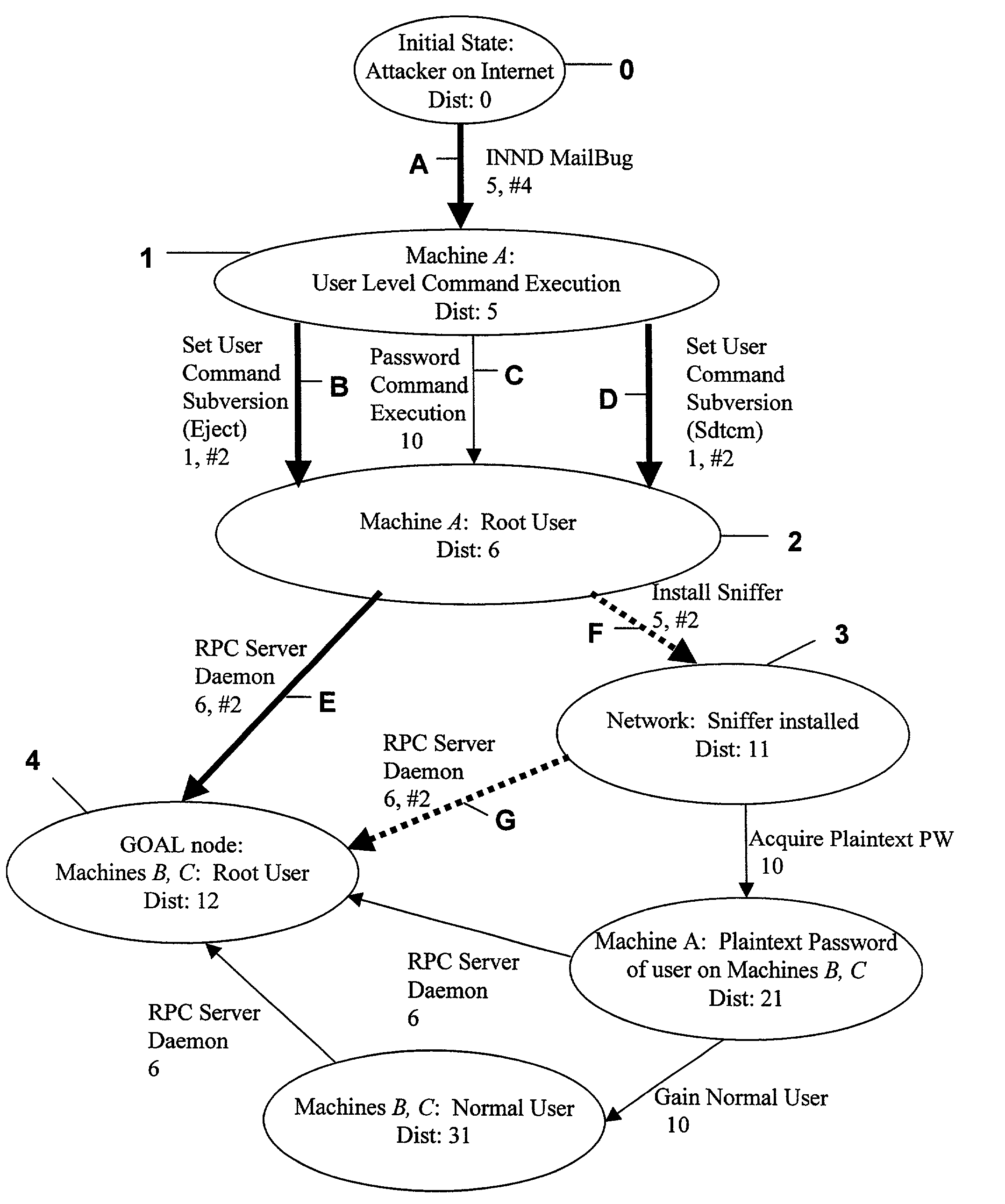
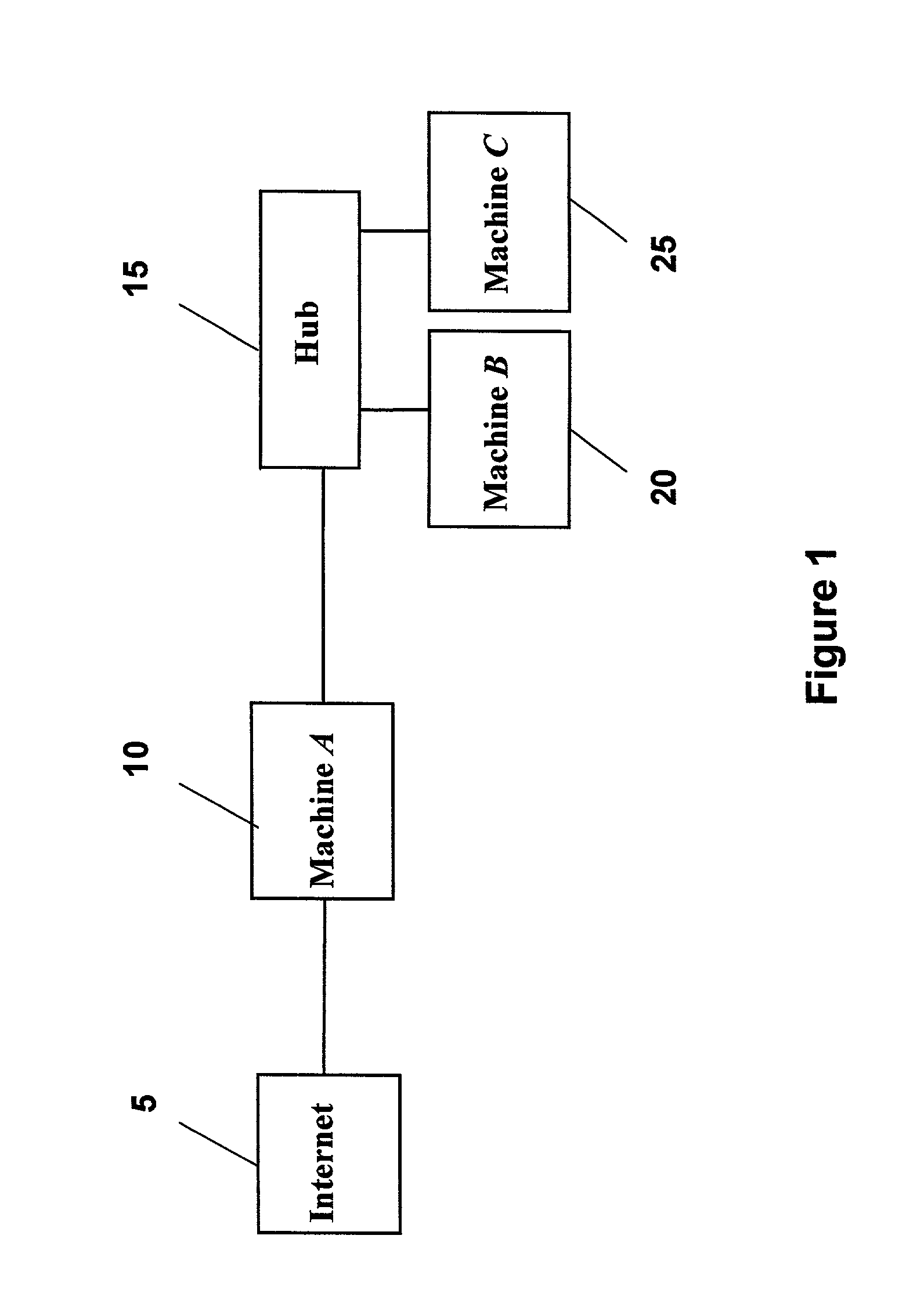
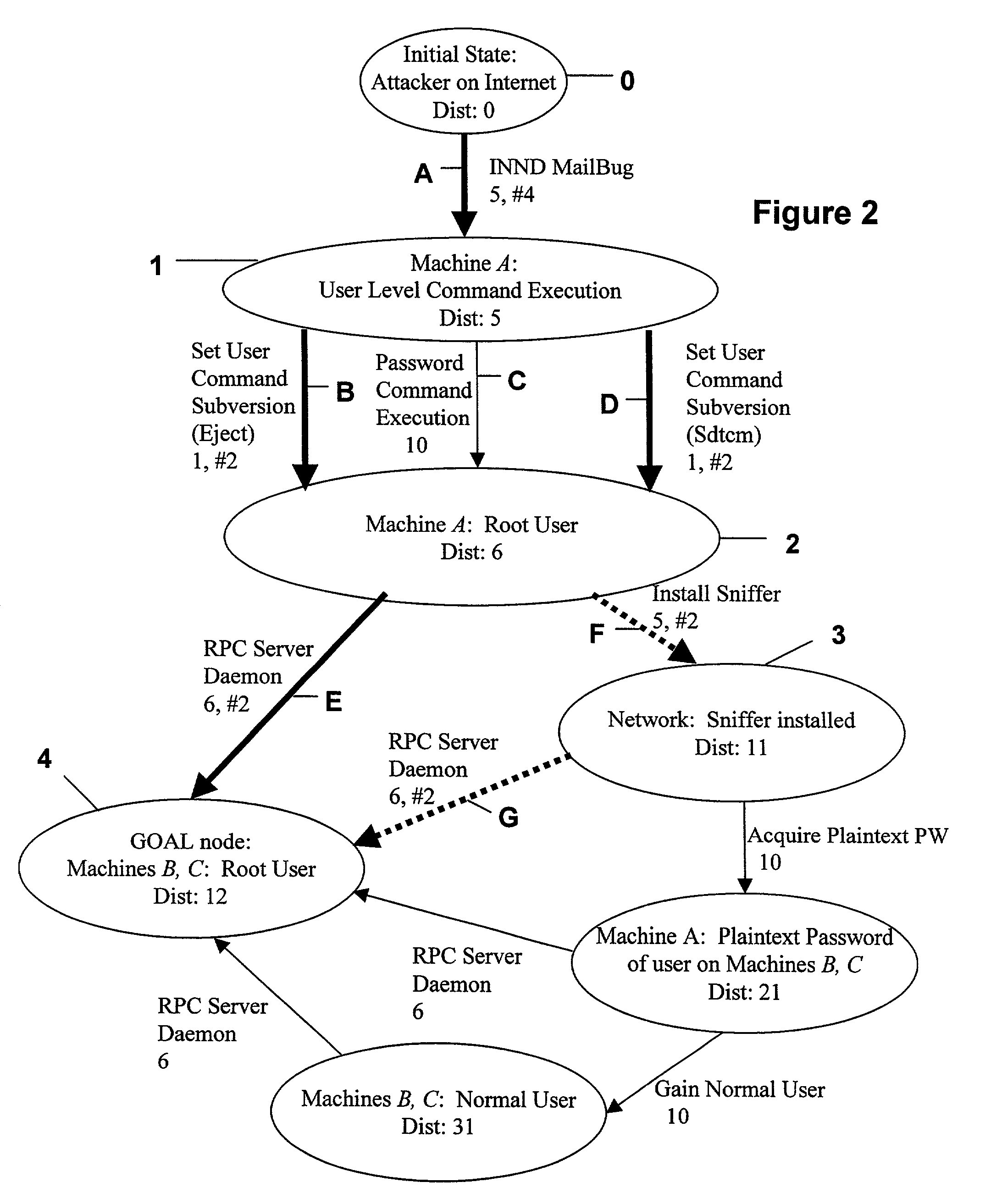
Method and tool for network vulnerability analysis
InactiveUS7013395B1Avoid low successLow “ effort ” costMemory loss protectionUnauthorized memory use protectionLimited resourcesCountermeasure
A computer system analysis tool and method that will allow for qualitative and quantitative assessment of security attributes and vulnerabilities in systems including computer networks. The invention is based on generation of attack graphs wherein each node represents a possible attack state and each edge represents a change in state caused by a single action taken by an attacker or unwitting assistant. Edges are weighted using metrics such as attacker effort, likelihood of attack success, or time to succeed. Generation of an attack graph is accomplished by matching information about attack requirements (specified in “attack templates”) to information about computer system configuration (contained in a configuration file that can be updated to reflect system changes occurring during the course of an attack) and assumed attacker capabilities (reflected in “attacker profiles”). High risk attack paths, which correspond to those considered suited to application of attack countermeasures given limited resources for applying countermeasures, are identified by finding “epsilon optimal paths.”
Owner:SANDIA NAT LAB
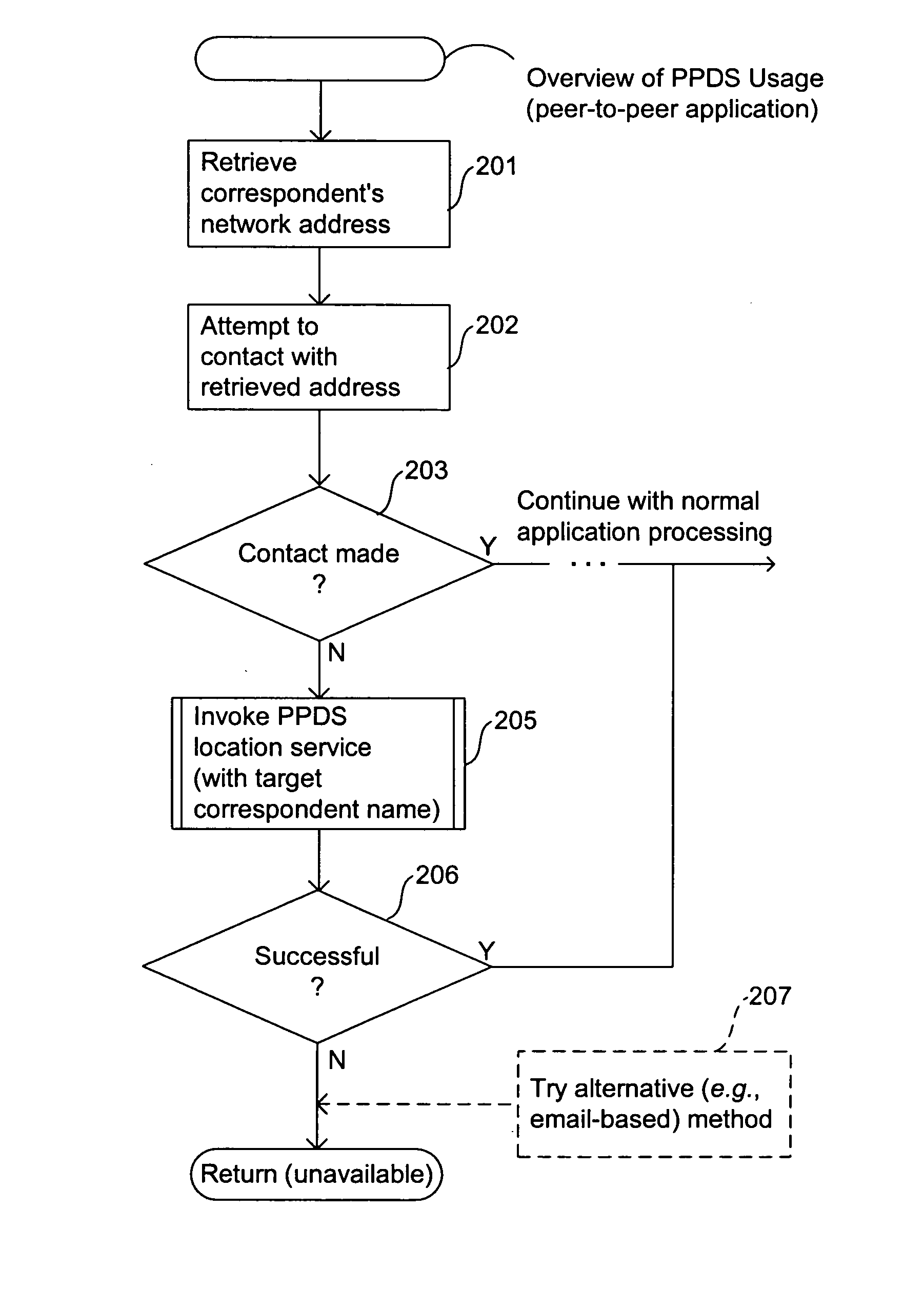
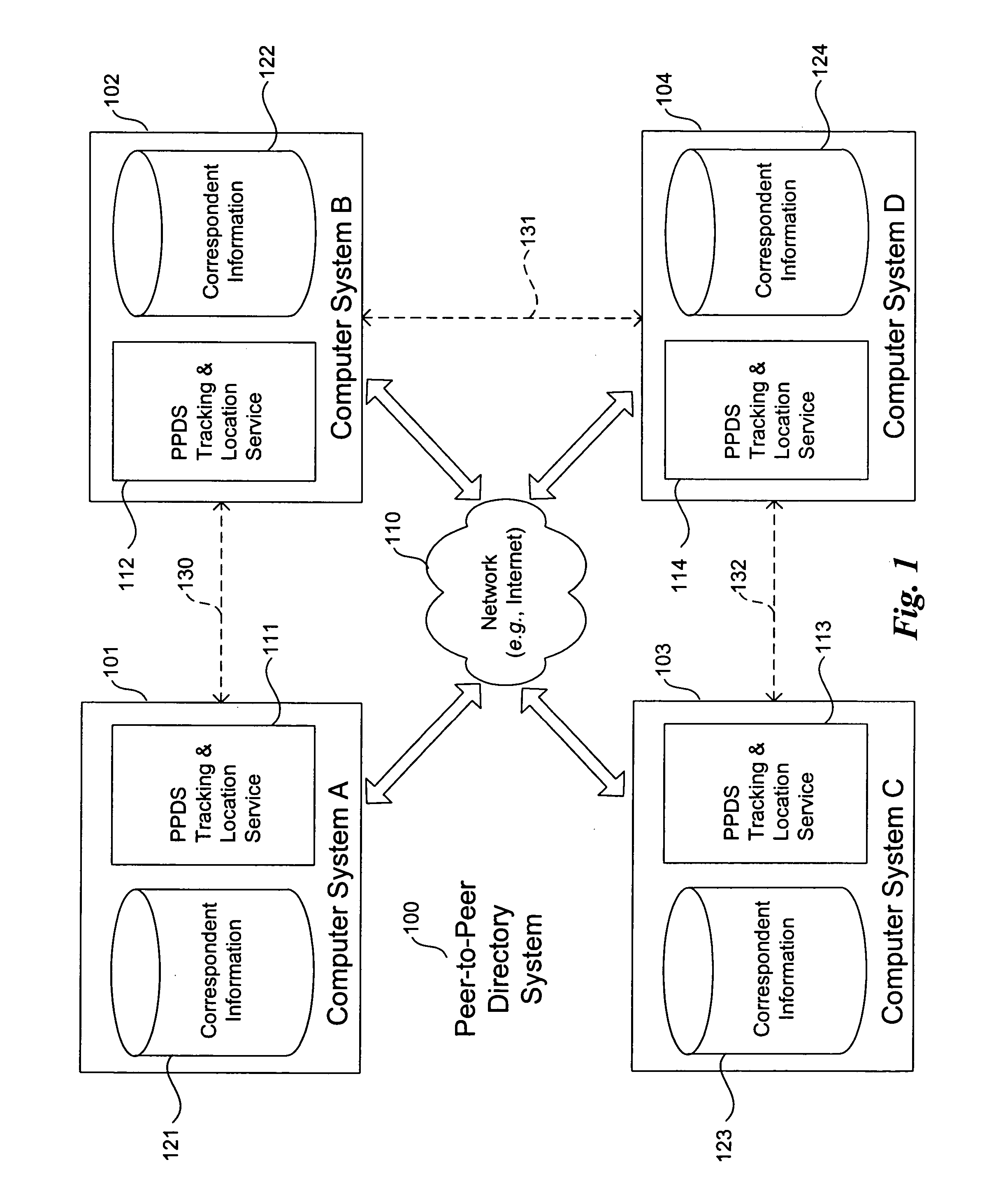
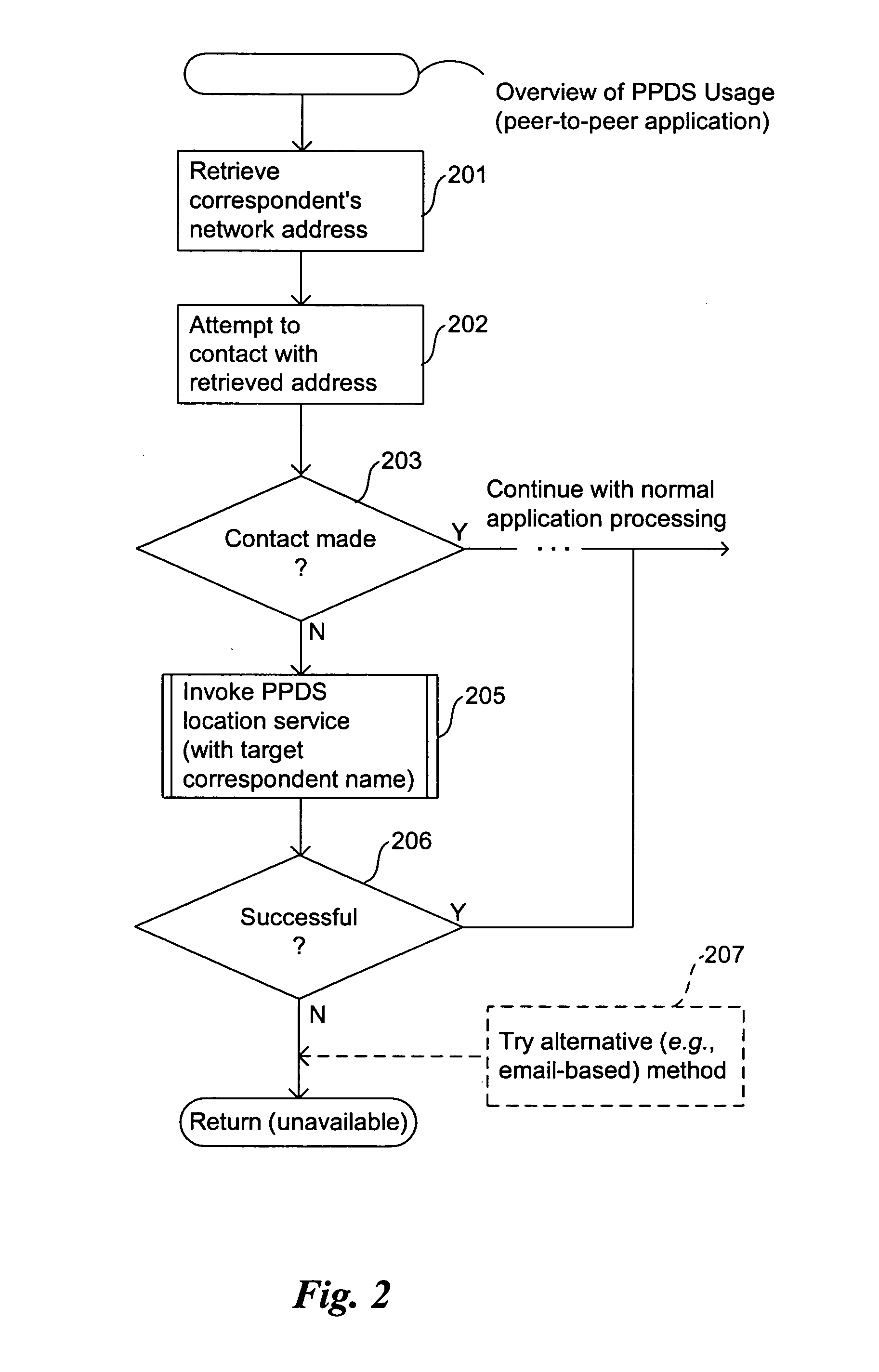
Method and system for peer-to-peer directory services
InactiveUS20050050227A1Multiple digital computer combinationsTransmissionCommunity basedNetwork addressing
Methods and systems for providing directory services for peer-to-peer systems and applications are provided. Example embodiments provide a Peer-to-Peer Directory System (“PPDS”), which enables applications, especially those using peer-to-peer technology that desire to communicate directly with one another on different peer computer systems, to automatically discover working (current) network addresses for each other even when the network addresses of their respective computer systems change dynamically. The PPDS provides a community-based tracking system, a portion of which is implemented on each computer system that is a member of the community, to mutually track and store the network addresses of the other computer systems to which it has an associated relationship. The PPDS also provides a query mechanism that takes advantage of the relationship paths between the various computer systems to search for a current network address of a designated computer system.
Owner:CASCADE BASIC RES CORP
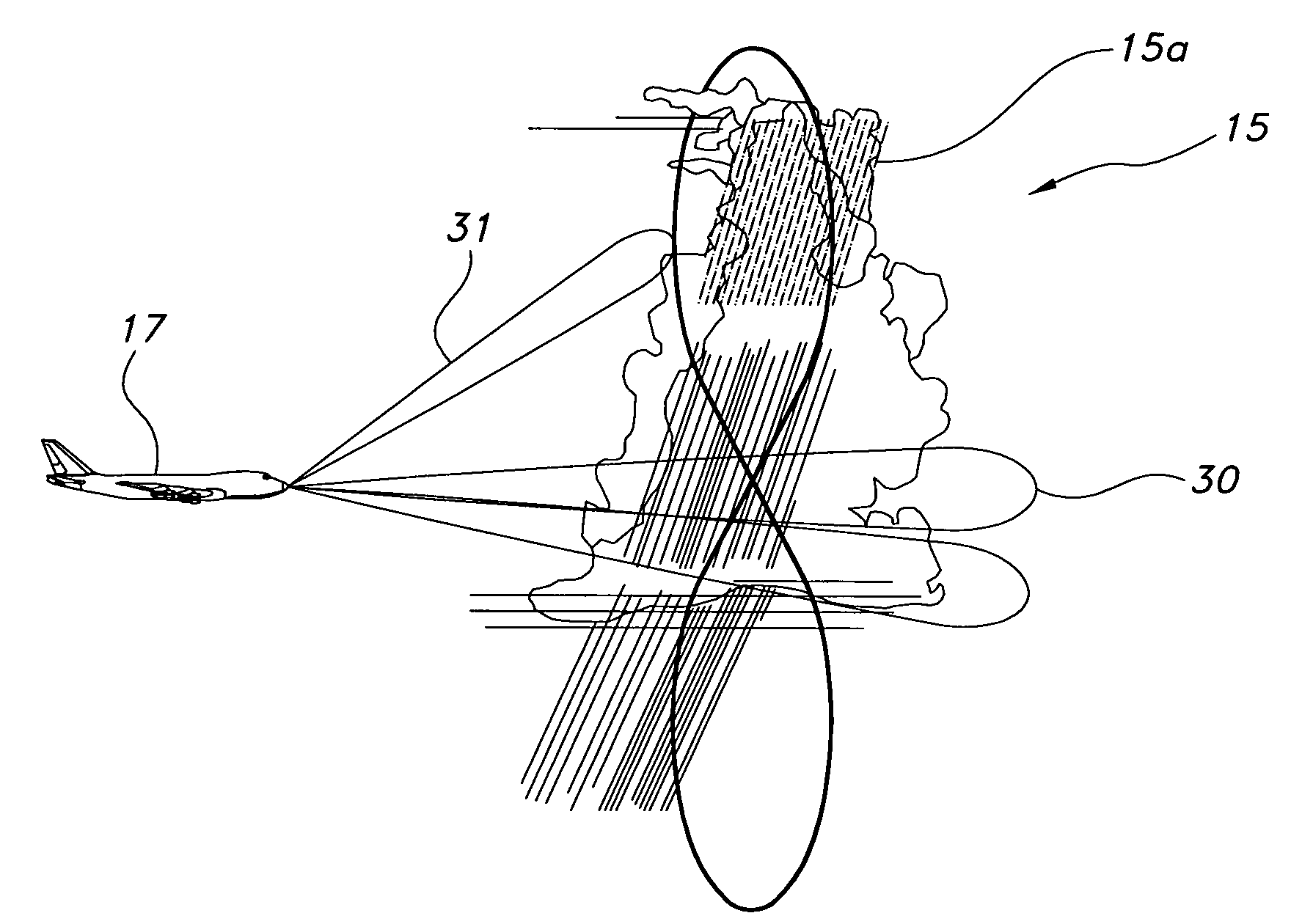
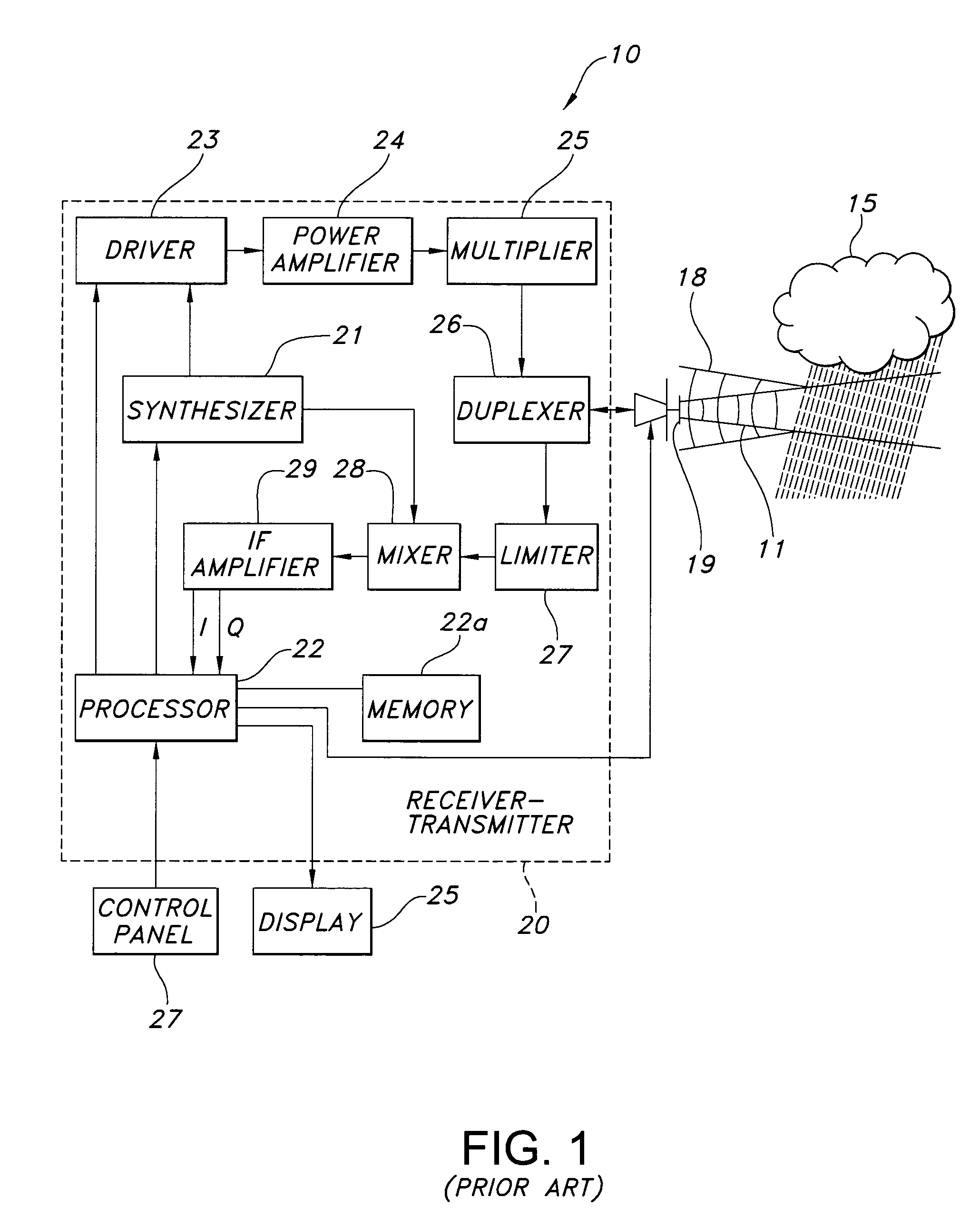
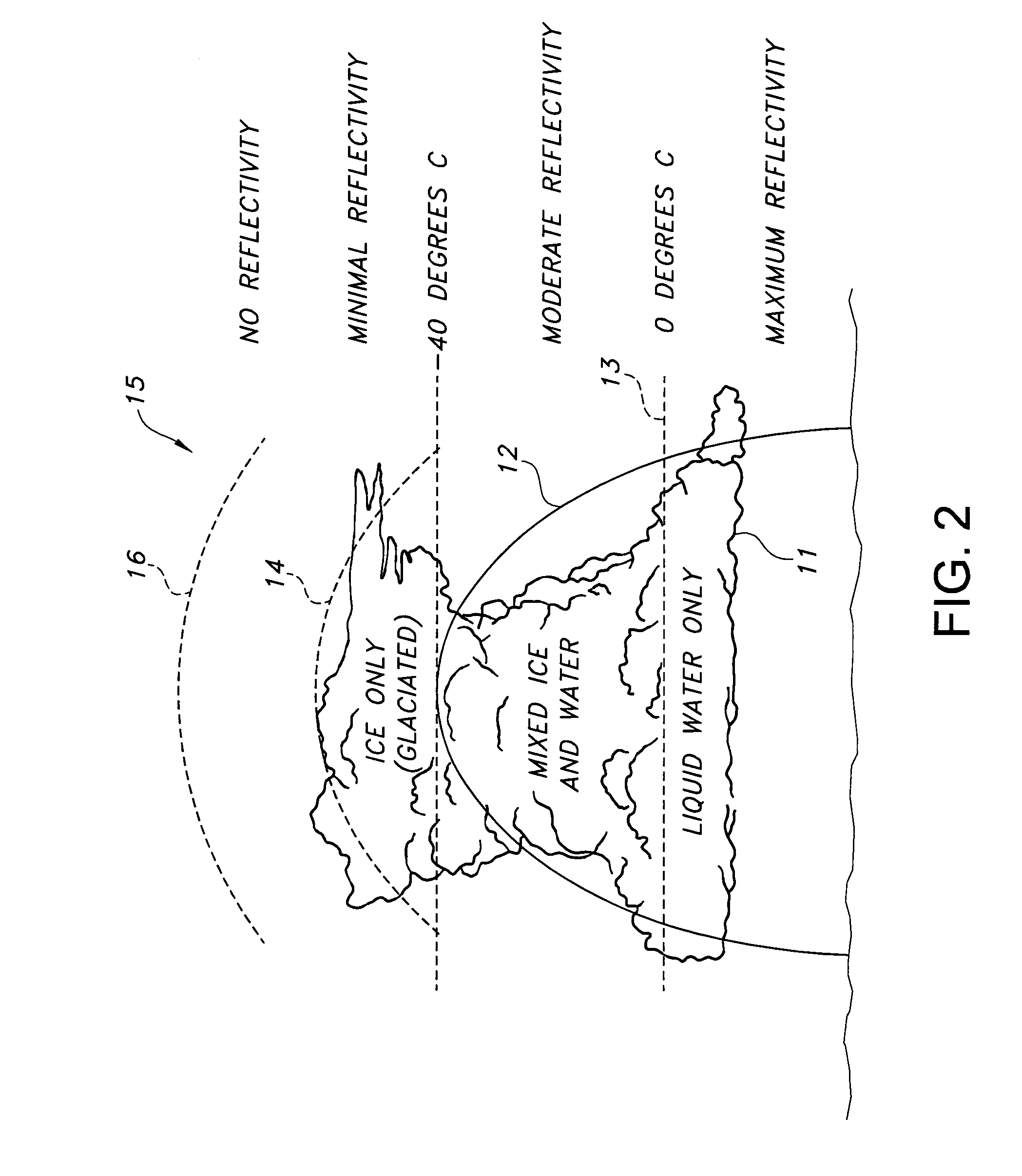
Directed sequential hazard assessment weather radar
ActiveUS7242343B1Process is inferiorDetectable turbulenceRadio wave reradiation/reflectionICT adaptationWeather radarLatency (engineering)
A directed sequential hazard assessment weather radar system detects weather and hazards with low latency and high confidence in a hazard detection mode to detect a region of reflectivity and changes to an assessment mode after detecting the region of reflectivity. The weather radar system scans a volume in front of an aircraft to detect the region of reflectivity in the hazard detection mode using a multiscan process and a reflectivity pulse pattern. The weather radar system determines presence of a hazard in the region of reflectivity after detecting the region. The weather radar system changes to a turbulence pulse pattern in the assessment mode and scans the region of reflectivity with an auxiliary sweep to determine turbulence. The directed sequential hazard assessment weather radar system performs a qualification process by scheduling an additional radar scanning auxiliary sweep to determine if the turbulence is real.
Owner:ROCKWELL COLLINS INC
System and method for maintaining translation look-aside buffer (TLB) consistency
InactiveUS6105113AMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryMemory address
A system and method for maintaining consistency between translational look-aside buffers (TLB) and page tables. A TLB has a TLB table for storing a list of virtual memory address-to-physical memory address translations, or page table entries (PTES) and a hardware-based controller for invalidating a translation that is stored in the TLB table when a corresponding page table entry changes. The TLB table includes a virtual memory (VM) page tag and a page table entry address tag for indexing the list of translations The VM page tag can be searched for VM pages that are referenced by a process. If a referenced VM page is found, an associated physical address is retrieved for use by the processor. The TLB controller includes a snooping controller for snooping a cache-memory interconnect for activity that affects PTEs. The page table entry address tag can be searched by a search engine in the TLB controller for snooped page table entry addresses. The TLB controller includes an updating module for invalidating or updating translations associated with snooped page table entry addresses. Translations in TLBs are thus updated or invalidated through hardware when an operating system changes a PTE, without intervention by an operating system or other software.
Owner:RPX CORP +1
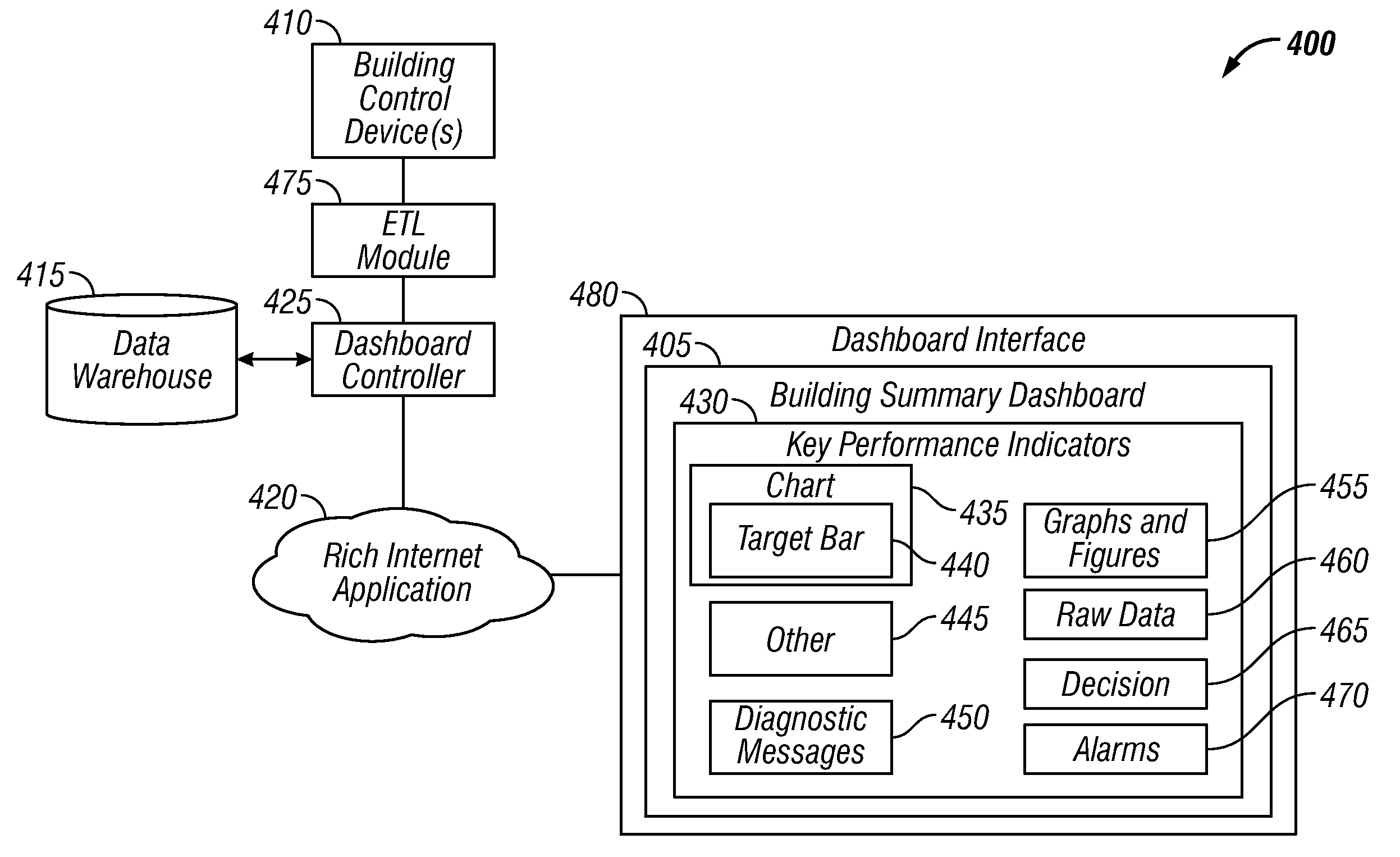
Method and System for Providing an Integrated Building Summary Dashboard
InactiveUS20100318200A1Improve energy efficiencyProtect environmentLevel controlTemperatue controlDashboardData warehouse
A method and system for providing an integrated building summary dashboard application. The dashboard can be implemented, for example, as a Rich Internet Application (RIA), which integrates with multiple data sources. A data warehouse can be utilized to consolidate and store the data related to a particular dashboard. The dashboard can be configured by integrating high-level metrics with key performance indicators to provide an overview, which can then be granularized to provide detailed information. The dashboard can also be configured to include a data chart that provides a “glimpse” of information associated with key performance indicators. The data chart can be configured to utilize a target bar as input to an interactive what-if analysis, and an output can be utilized to automatically drive control automation system changes.
Owner:HONEYWELL INT INC
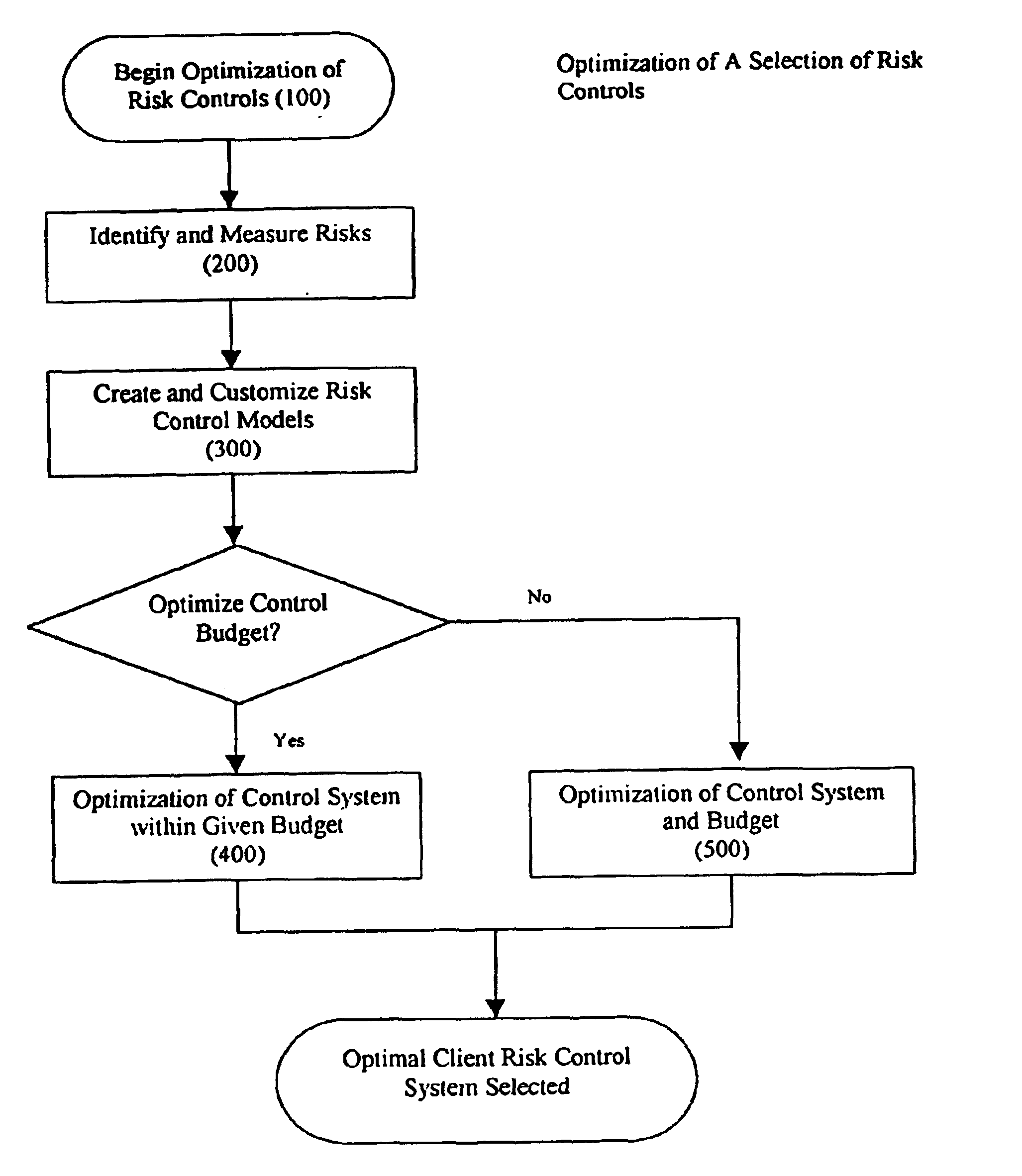
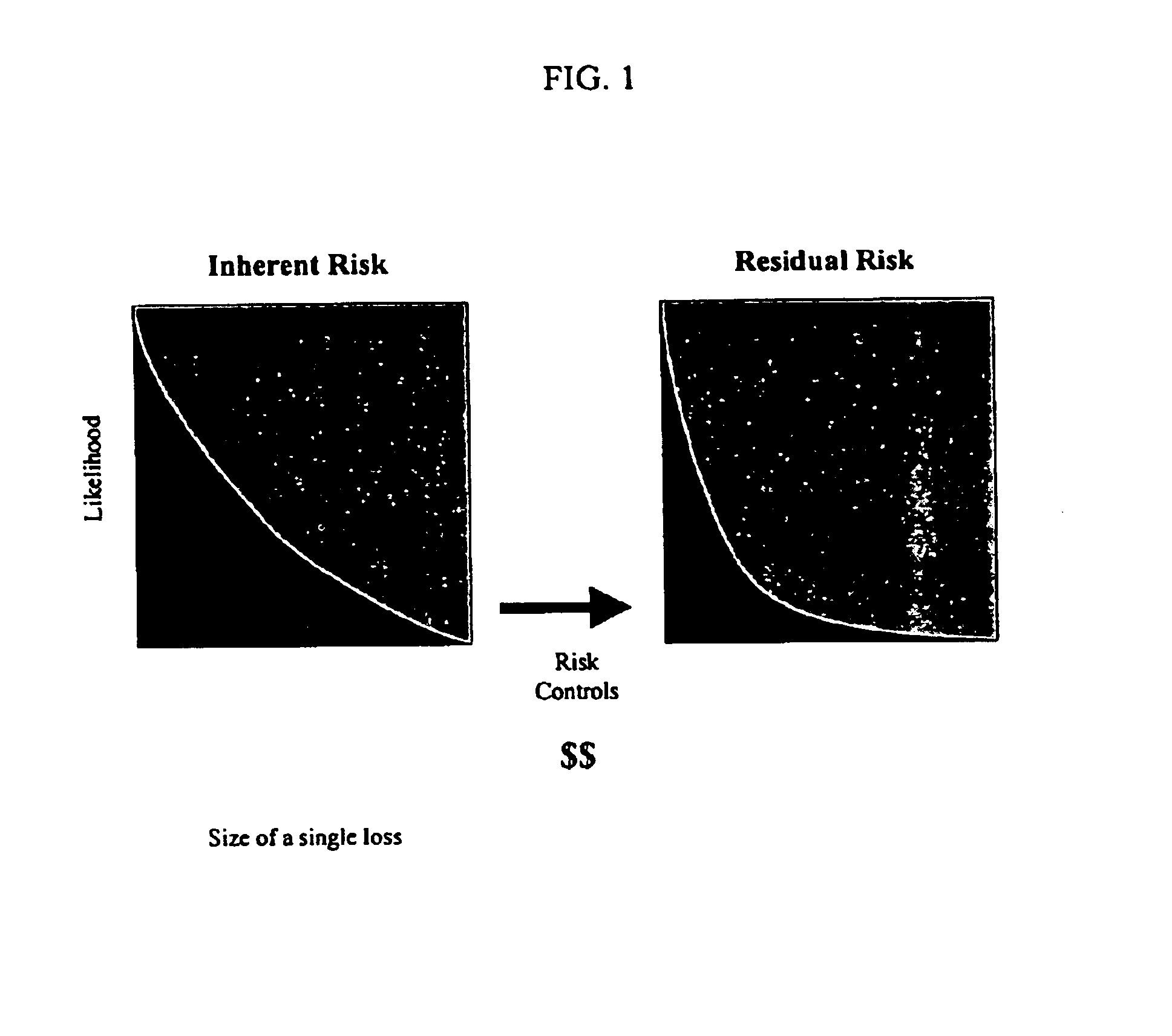
Method and system for risk control optimization
InactiveUS6876992B1Economic value maximizationHigh economic valueFinanceComputation using non-denominational number representationRisk exposureRisk Control
A method and system for selecting an optimal set of management and risk controls for a given set of risks within a variable control budget. Specifically, optimization according to the present invention is defined using a method and system to calculate the greatest reduction in an organization's risk exposure with the minimum investment in cost and time as measured by the economic value added of the risk system change. Risk control models and management risk control models are client customized into a risk control system specifically addressing a clients applicable risks and their associated exposures. An operator is able to determine which risk control system maximizes available resources while also reducing an organization's total risk exposure.
Owner:WILLIS NORTH AMERICA
Self-tuning link aggregation system
InactiveUS6498781B1Error preventionFrequency-division multiplex detailsData processing systemSelf-tuning
A data processing system and method in a computer network are disclosed for improving performance of a link aggregation system included in the network. Parameters are established which are utilized to determine performance criteria of the link aggregation system. A performance of the link aggregation system is determined by determining the performance criteria. The performance of the link aggregation system changes in response to a flow traffic burden on the link aggregation system changing. The link aggregation system dynamically modifies the parameters in response to the changing performance of the link aggregation system. The link aggregation system is self-tuning and capable of automatically adjusting to a changing flow traffic burden on the link aggregation system.
Owner:IBM CORP
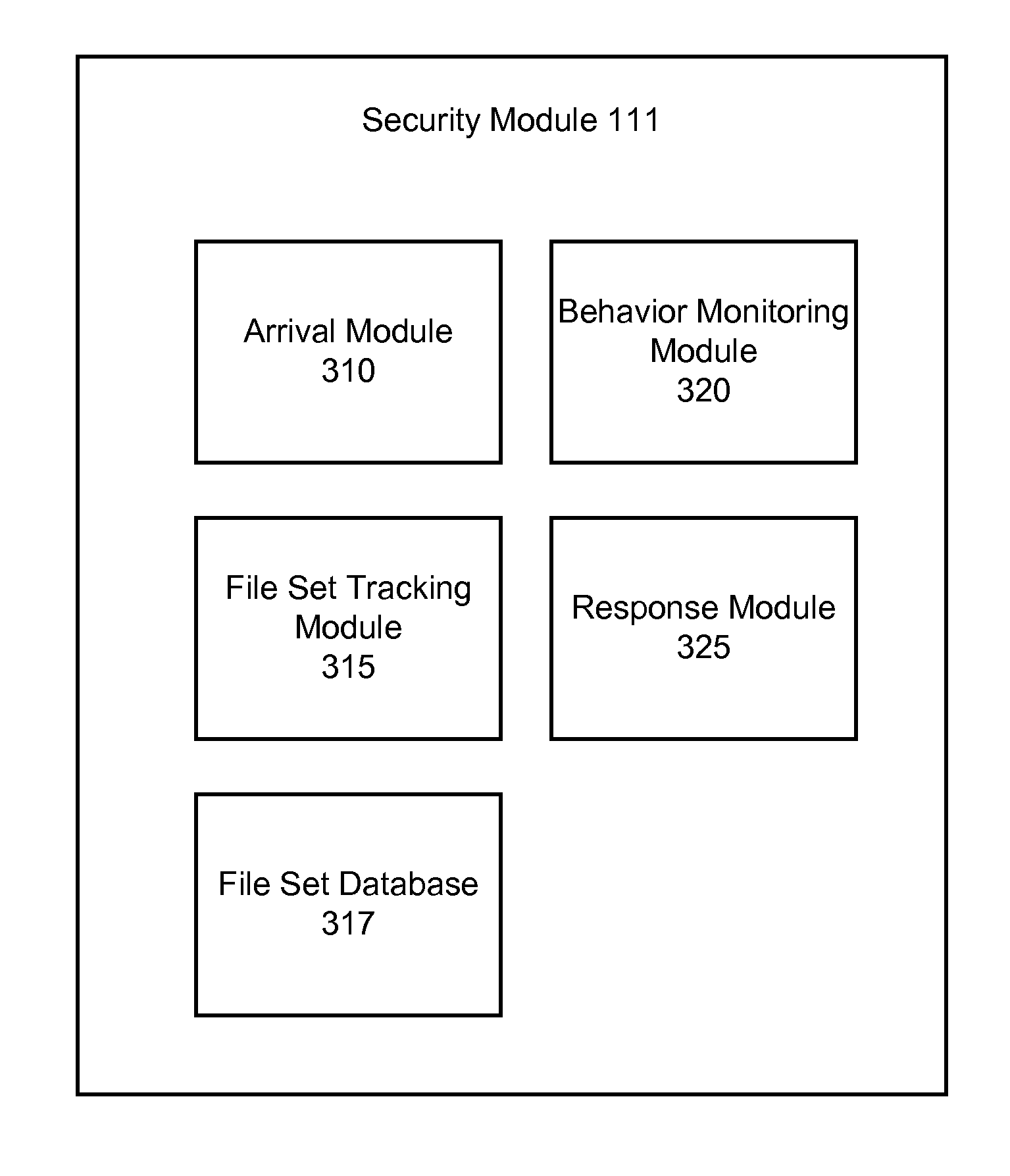
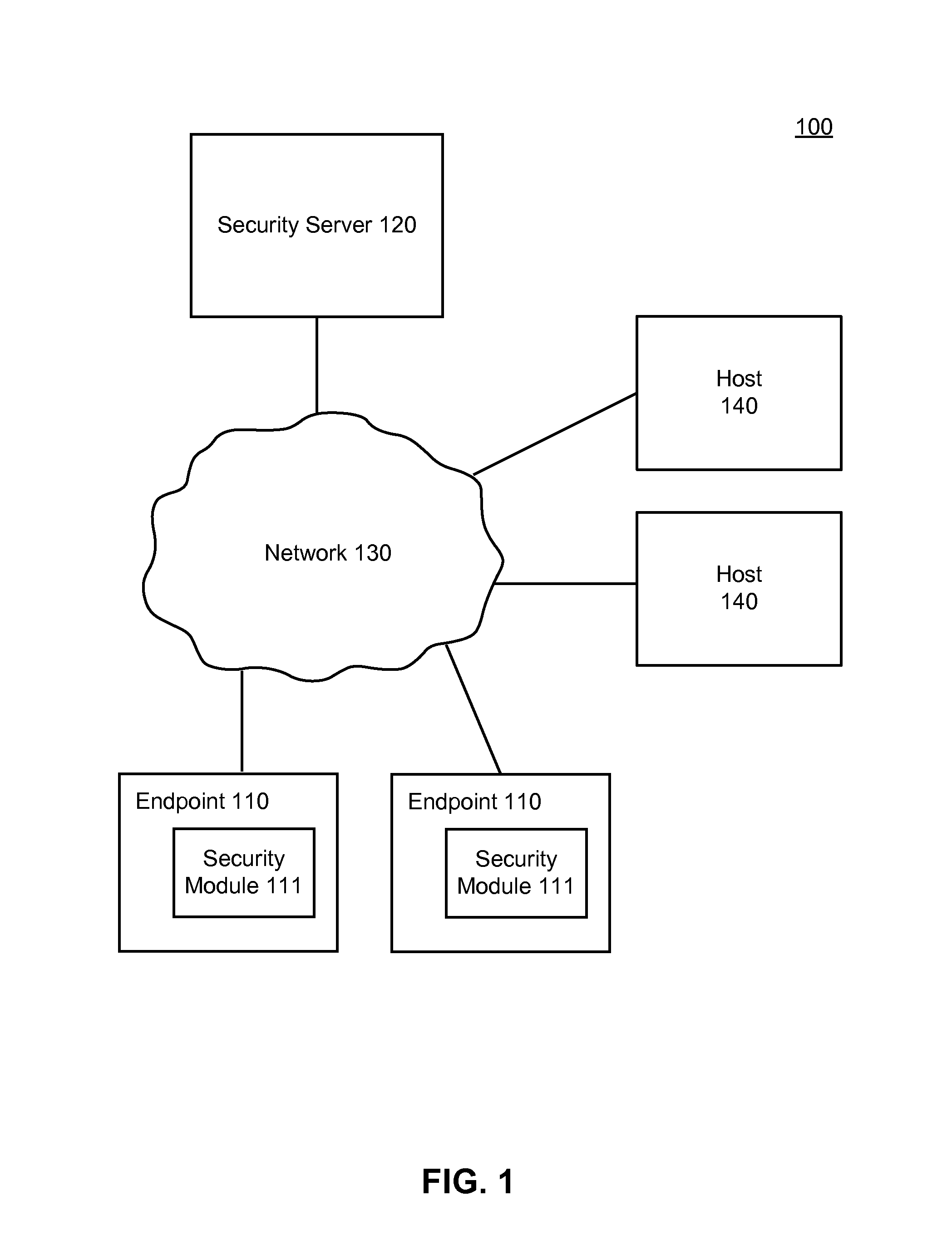
Detecting and remediating malware dropped by files
A security module detects and remediates malware from suspicious hosts. A file arrives at an endpoint from a host. The security module detects the arrival of the file and determines the host from which the file arrived. The security module also determines whether the host is suspicious. If the host is suspicious, the security module observes the operation of the file and identifies a set of files dropped by the received file. The security module monitors the files in the set using heuristics to detect whether any of the files engage in malicious behavior. If a file engages in malicious behavior, the security module responds to the malware detection by remediating the malware, which may include removing system changes caused by the set.
Owner:CA TECH INC
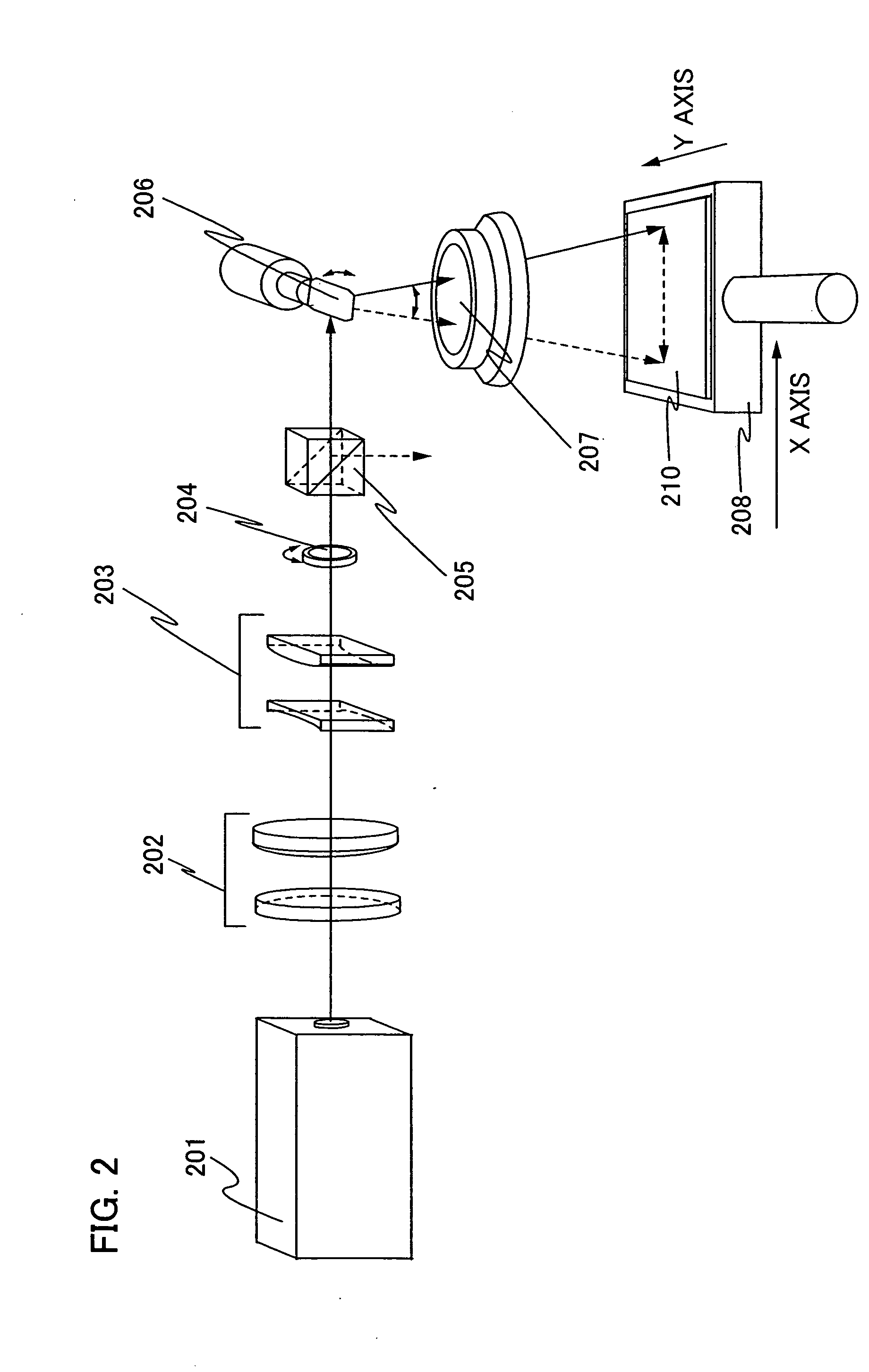
Laser irradiation apparatus and method of manufacturing semiconductor device by using the laser irradiation apparatus
InactiveUS20040074881A1Offset changeSuppress fluctuationsTransistorSolid-state devicesEnergy variationLight beam
The present invention provides the laser irradiation apparatus that has a galvanometer mirror and an f-theta lens optical system, can offset the change of the energy due to the transmittance change of the f-theta lens, and can scan a laser beam while the change of the energy on a substrate is suppressed. Further, the laser beam energy that is incident on the lens is controlled in advance by combining the optical system changing the branching ratio of polarization of the laser beam and the optical system having dependence on direction of polarization of the laser beam and changed continuously according to the transmittance of the lens on which the laser beam is incident. The laser energy is controlled to offset the transmittance of the lens, and thereby energy fluctuation of the laser beam irradiation of a substrate can be prevented.
Owner:SEMICON ENERGY LAB CO LTD
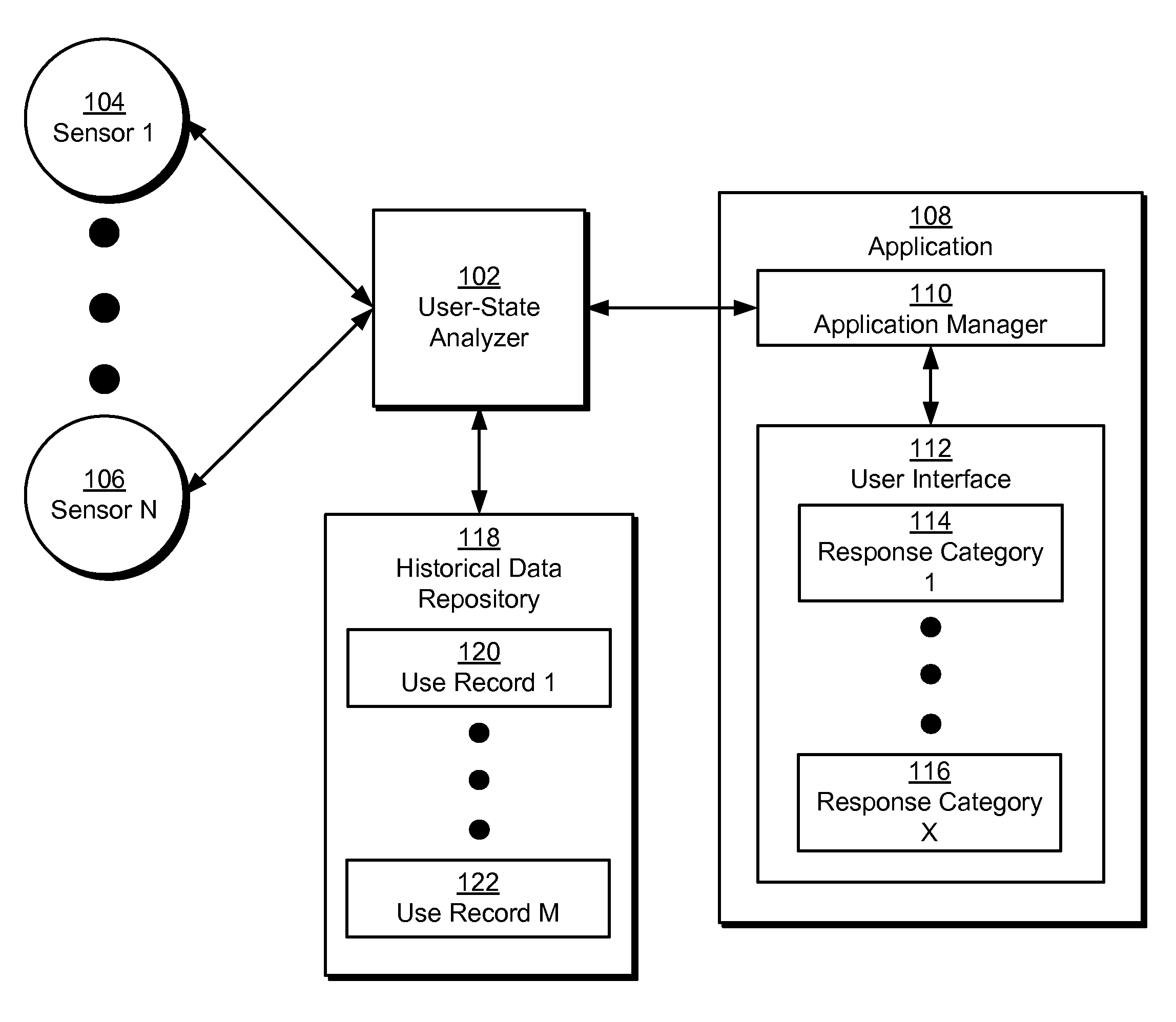
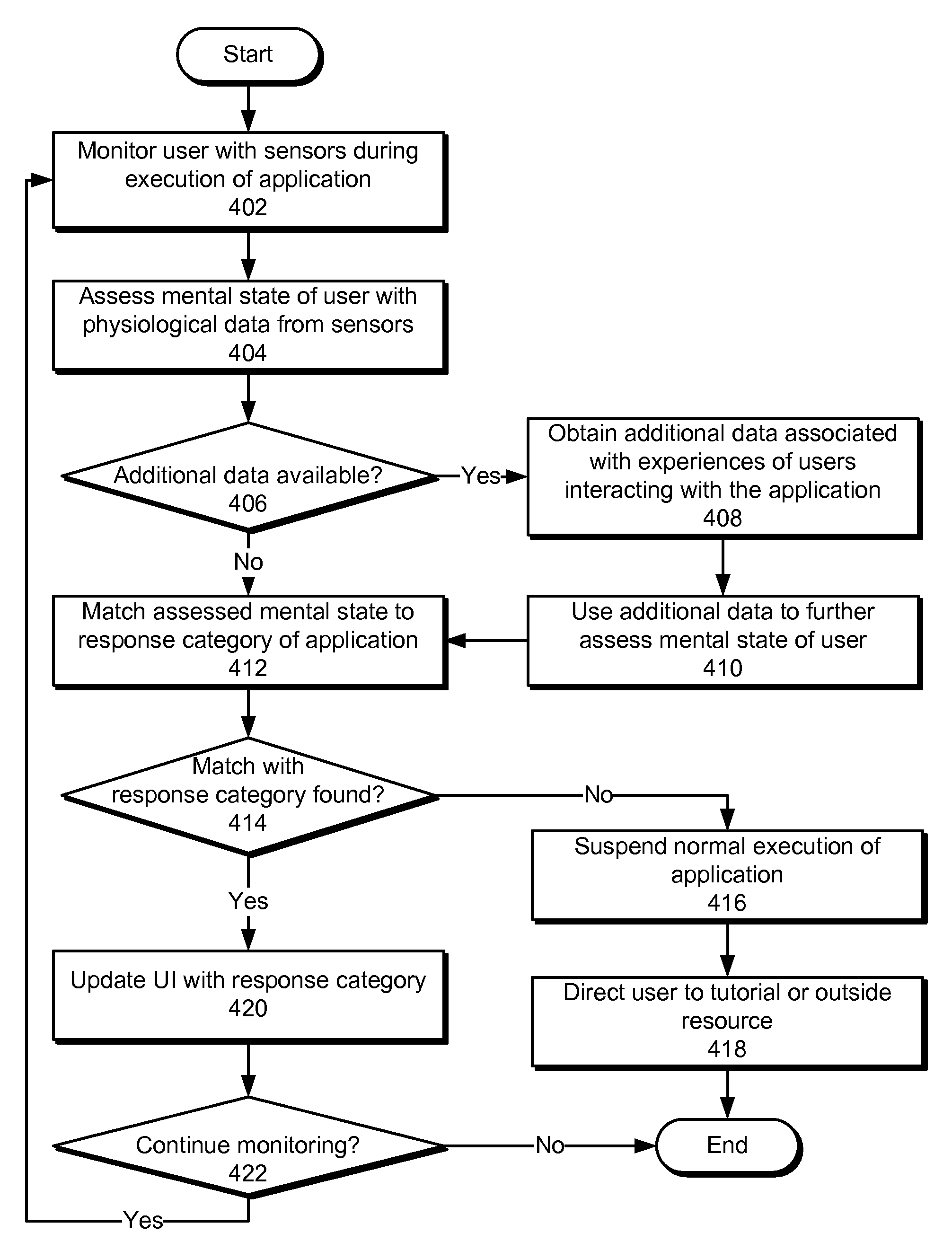
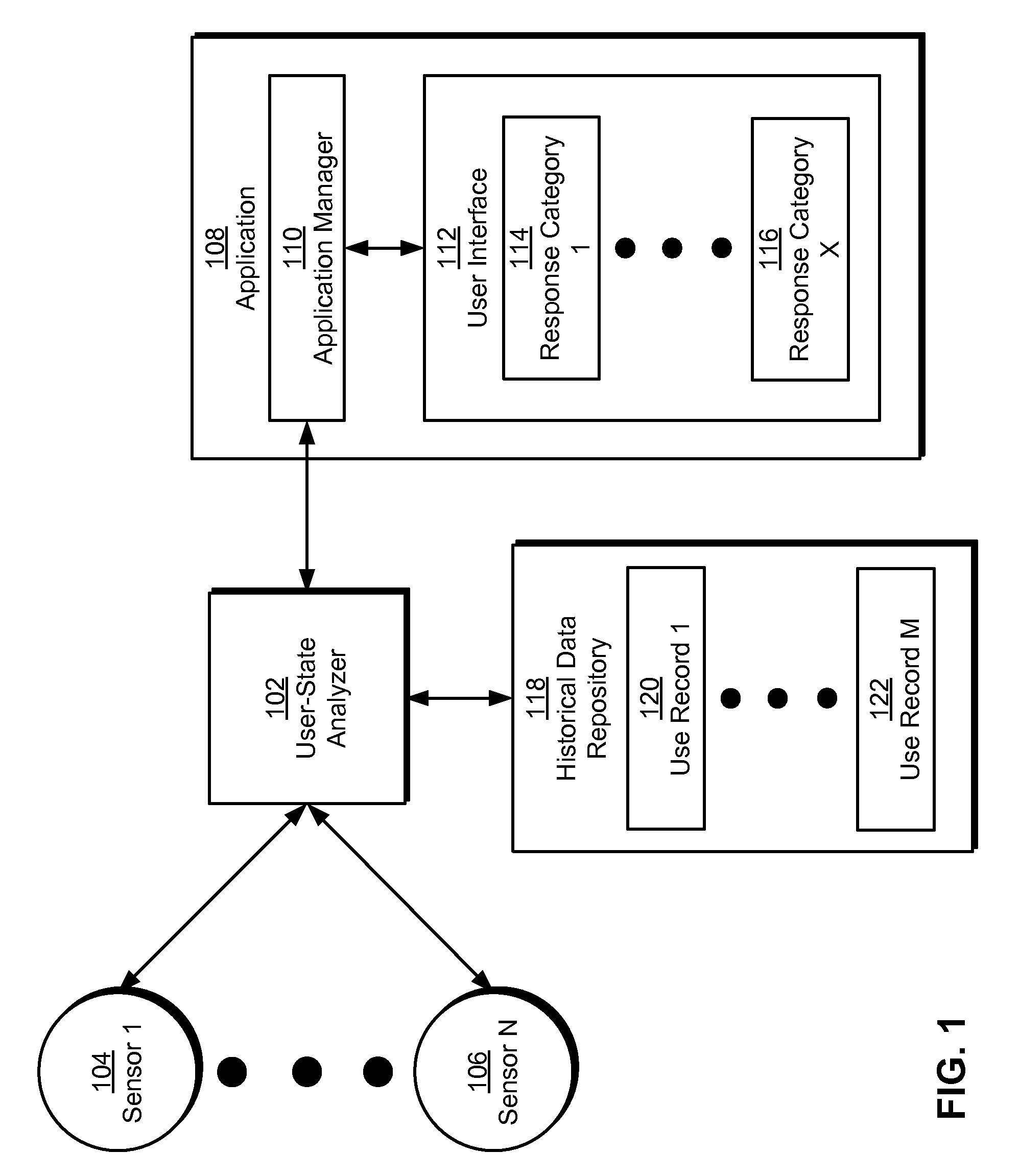
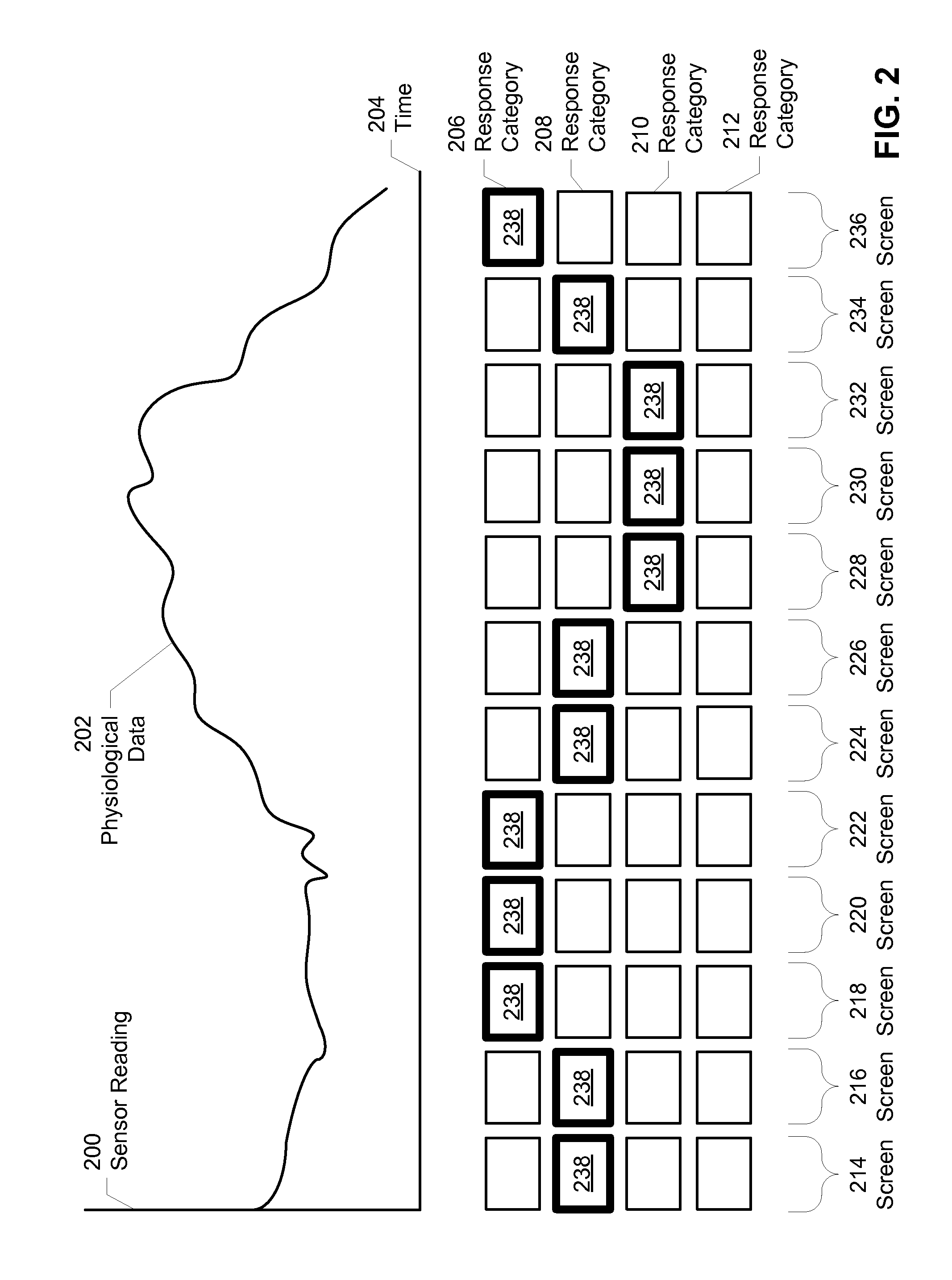
Method and system for dynamic adaptation of user experience in an application
ActiveUS20090248594A1Easy to useExecution for user interfacesSpecial data processing applicationsMental stateComputer science
Some embodiments of the present invention provide a system that executes an application. During operation, the system physiologically monitors a user of the application with a set of sensors as the application executes. Next, the system assesses a mental state of the user based on physiological data collected from the sensors. Finally, the system changes the behavior of the application based on the assessed mental state to facilitate use of the application by the user.
Owner:INTUIT INC
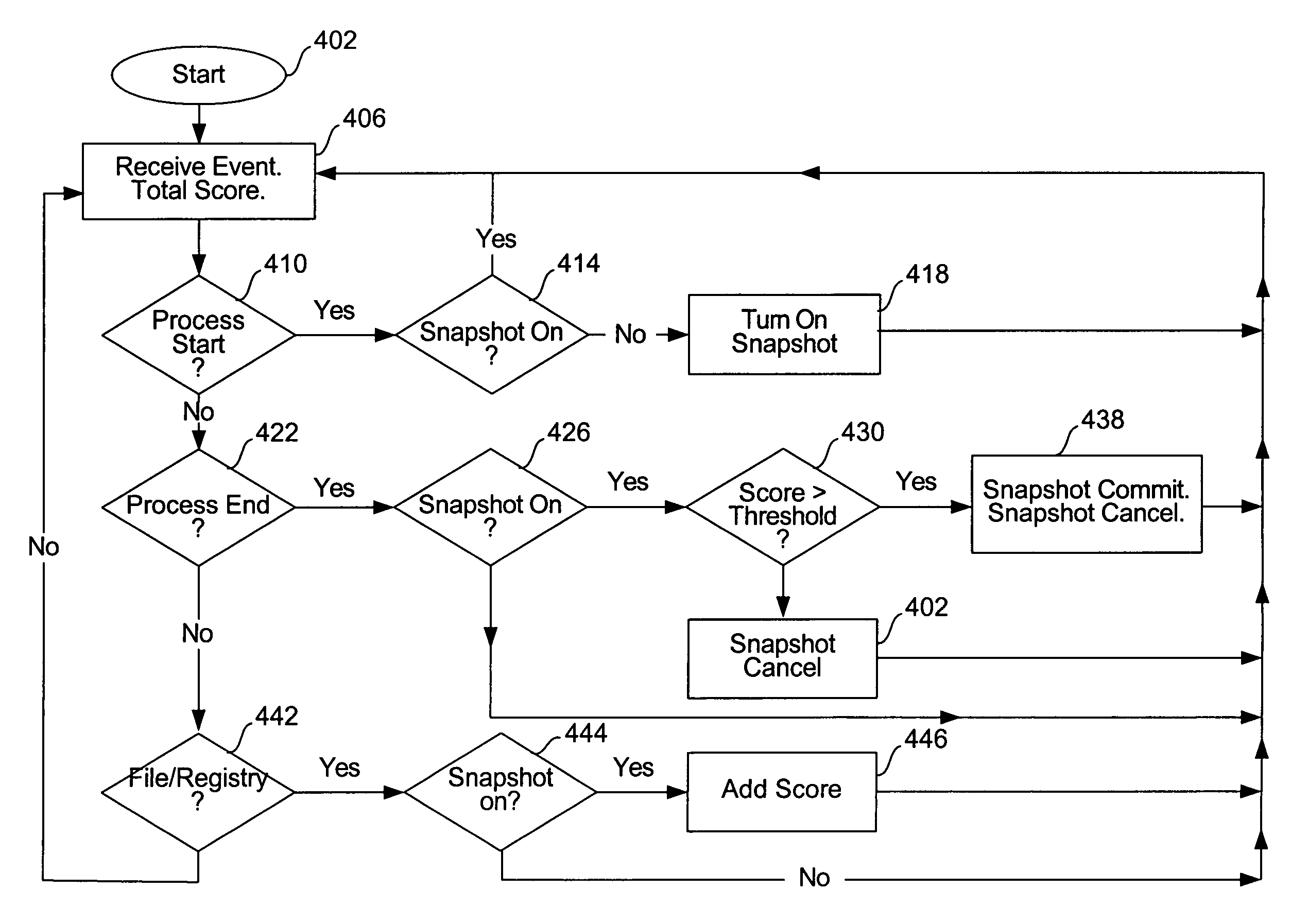
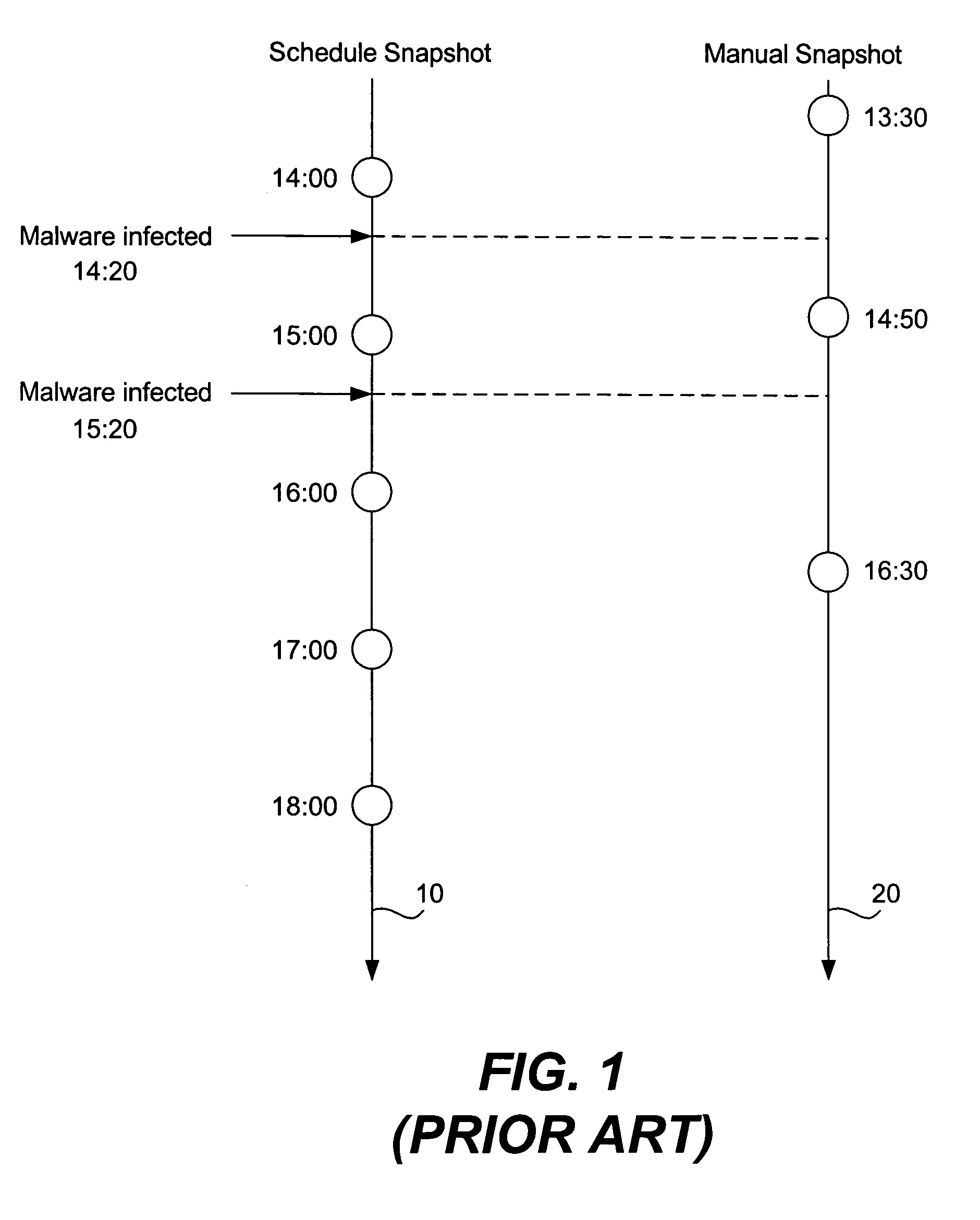
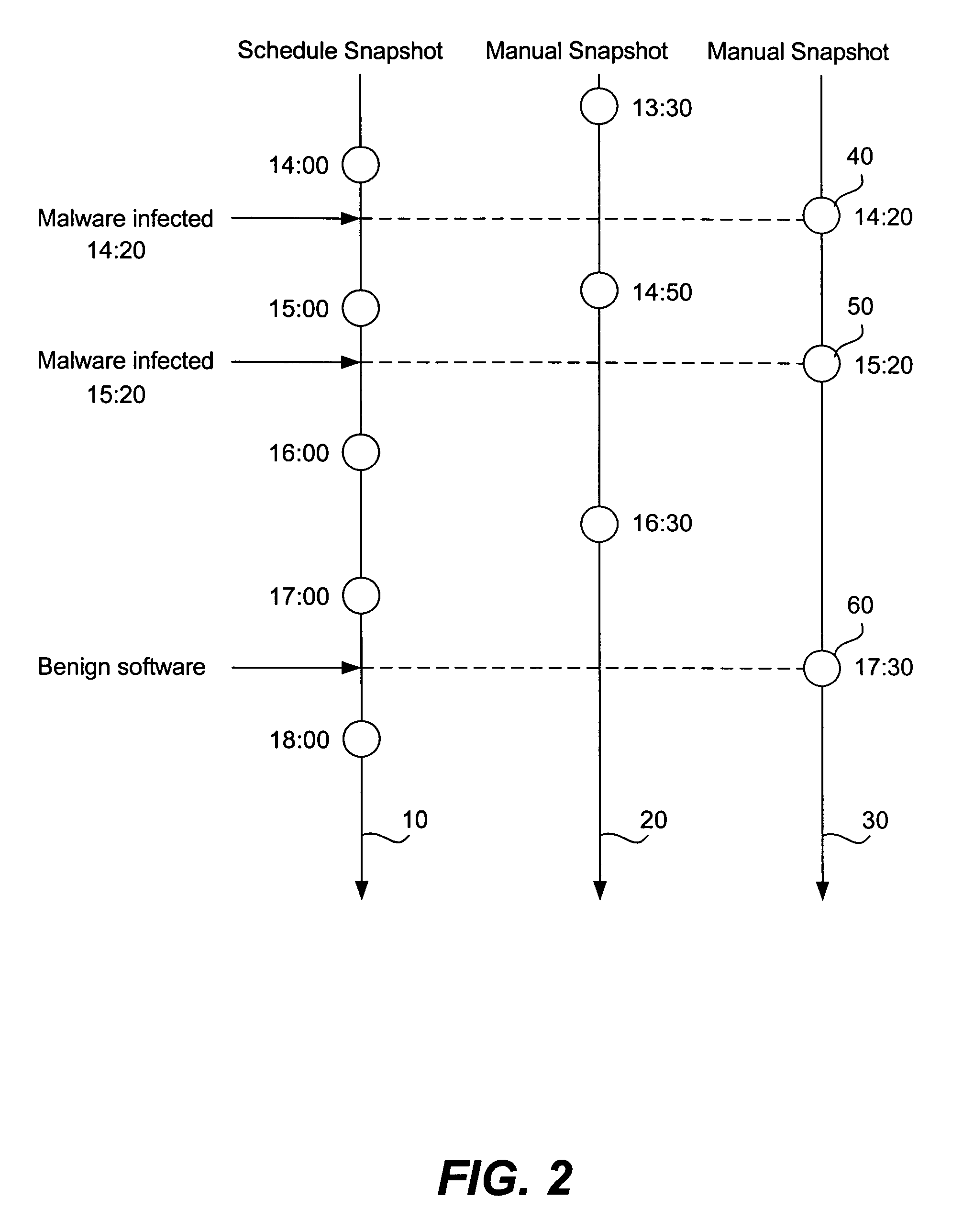
Snapshot and restore technique for computer system recovery
A computer system operation registers as an event when an operation potentially characteristic of malware occurs. Events are scored and when a threshold is reached indicative of a possible malware infection a restore point is created. Many restore points are created. When a user decides to restore the system because of the presence of malware a malware report is retrieved. The malware report describes characteristics of a particular piece of malware. The malware report is compared to the restore point logs that had been created earlier. Any number of malware reports are compared to the restore point logs. A restore point log that shares many of the same system changes or other effects also present in a malware report is likely to be an indication of the beginning of a malware infection. The matched restore point log is recommended to the user as the best restore point.
Owner:TREND MICRO INC
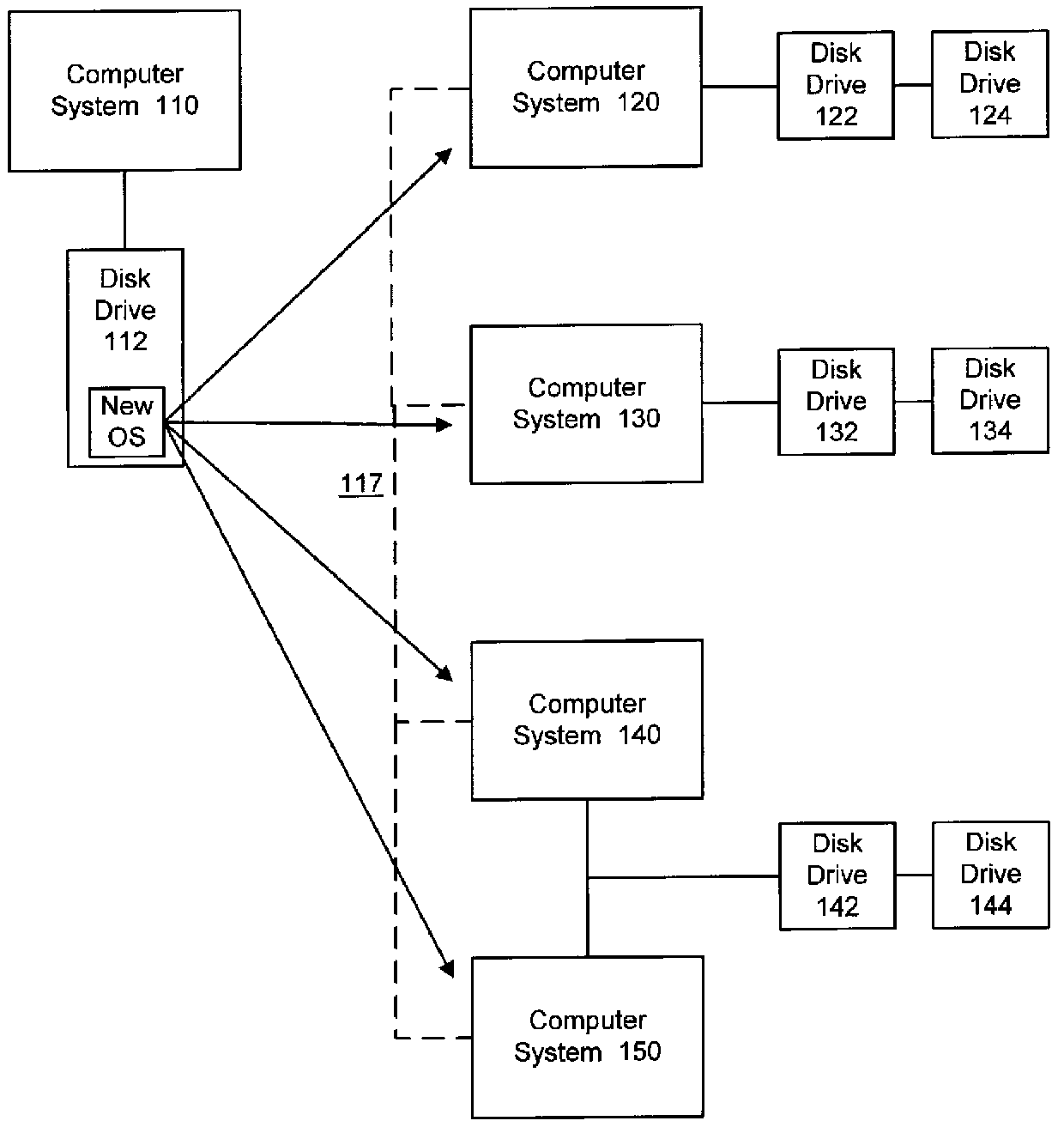
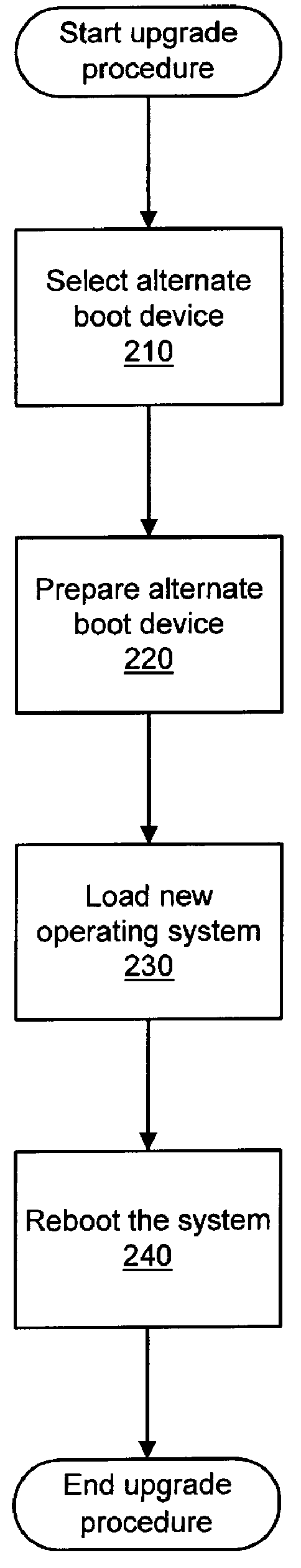
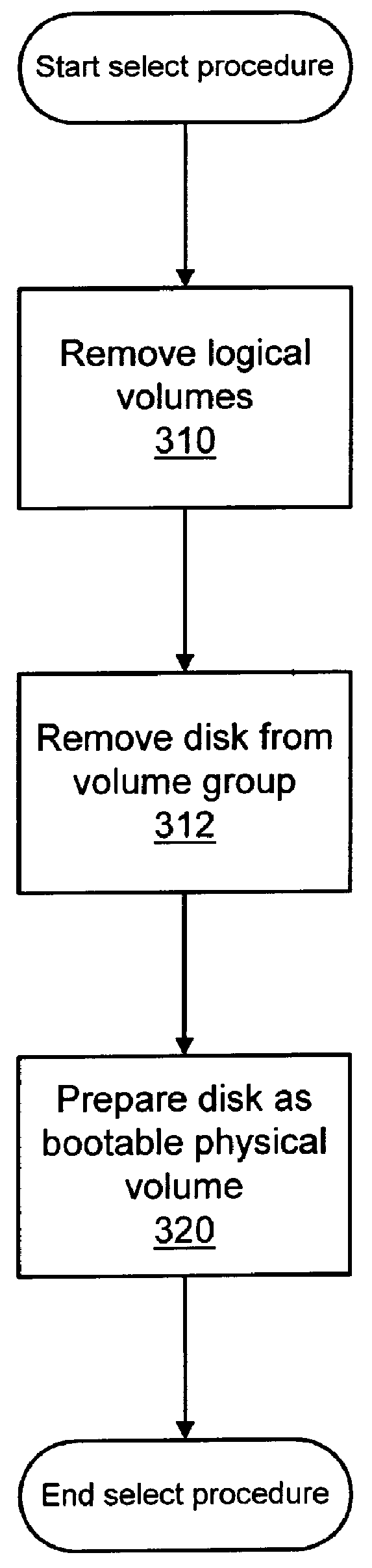
Installing operating systems changes on a computer system
A computer system is upgraded while the computer system is functioning. The computer system has a first boot device with a first operating system and a second device. The method includes: preparing the second device within the computer system as a bootable device while the computer system is functioning under control of the first operating system; preparing the second device within the computer system to receive a second operating system while the computer system is functioning under control of the first operating system; loading the second operating system onto the second device while the computer system is functioning under control of the first operating system; and, rebooting the computer system such that the computer system is under control of the second operating system on the second device.
Owner:GLOBALFOUNDRIES INC
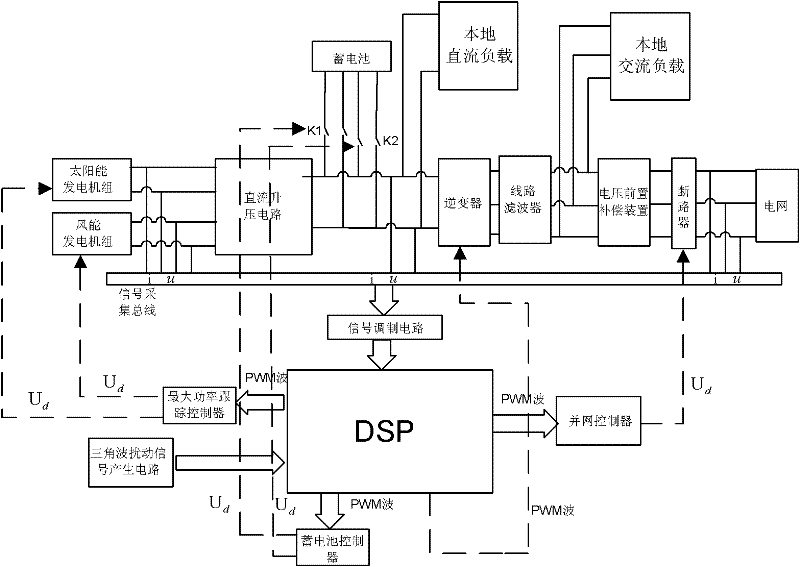
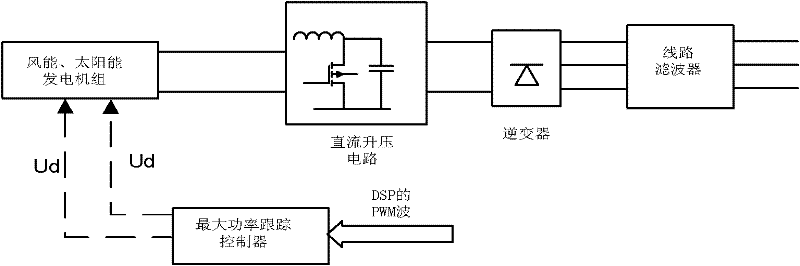
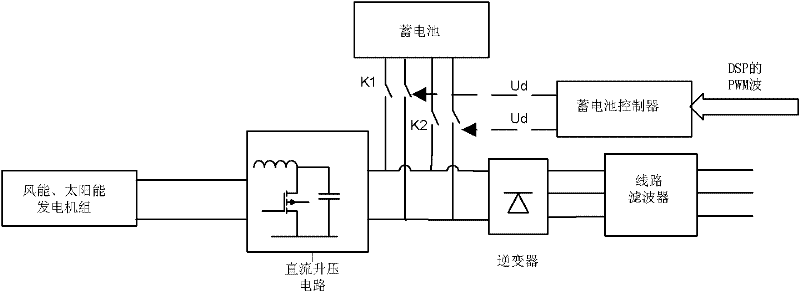
Wind energy and solar energy grid-connected generation system and control method thereof
InactiveCN102237691AImprove energy efficiencyGood synchronizationBatteries circuit arrangementsSingle network parallel feeding arrangementsState parameterAlternating current
The invention provides a wind energy and solar energy grid-connected generation system and a control method thereof. The wind energy and solar energy grid-connected generation system comprises a generation unit, an inversion unit, a grid-connecting unit, a main control unit and a detection unit. Each unit is effectively controlled by an integrated control unit which is formed by a digital signal processor (DSP), and operating state parameters of the system are predicted by a neural network, so the defect that the grid-connected system changes due to execution delaying of a control instructionis overcome, and the operating stability of the system is improved. Island detection adopts an active and passive detection mode, so the capacity for anti-island operation of the system is improved. The invention has the advantages that: inverted electric energy is supplied to an electricity grid and can be locally supplied to local alternating current and direct current loads, so the load pressure of the electricity grid is reduced, and the capacity for stable operation of the electricity grid can be improved; and when the output electric energy of the system is smaller than a local load, the electricity grid can supply power to the local load of the system, so the local load is supplied with power doubly by power supplies of the system and the electricity grid, and the time for uninterrupted power supply of the power supplies is prolonged.
Owner:NORTHEASTERN UNIV
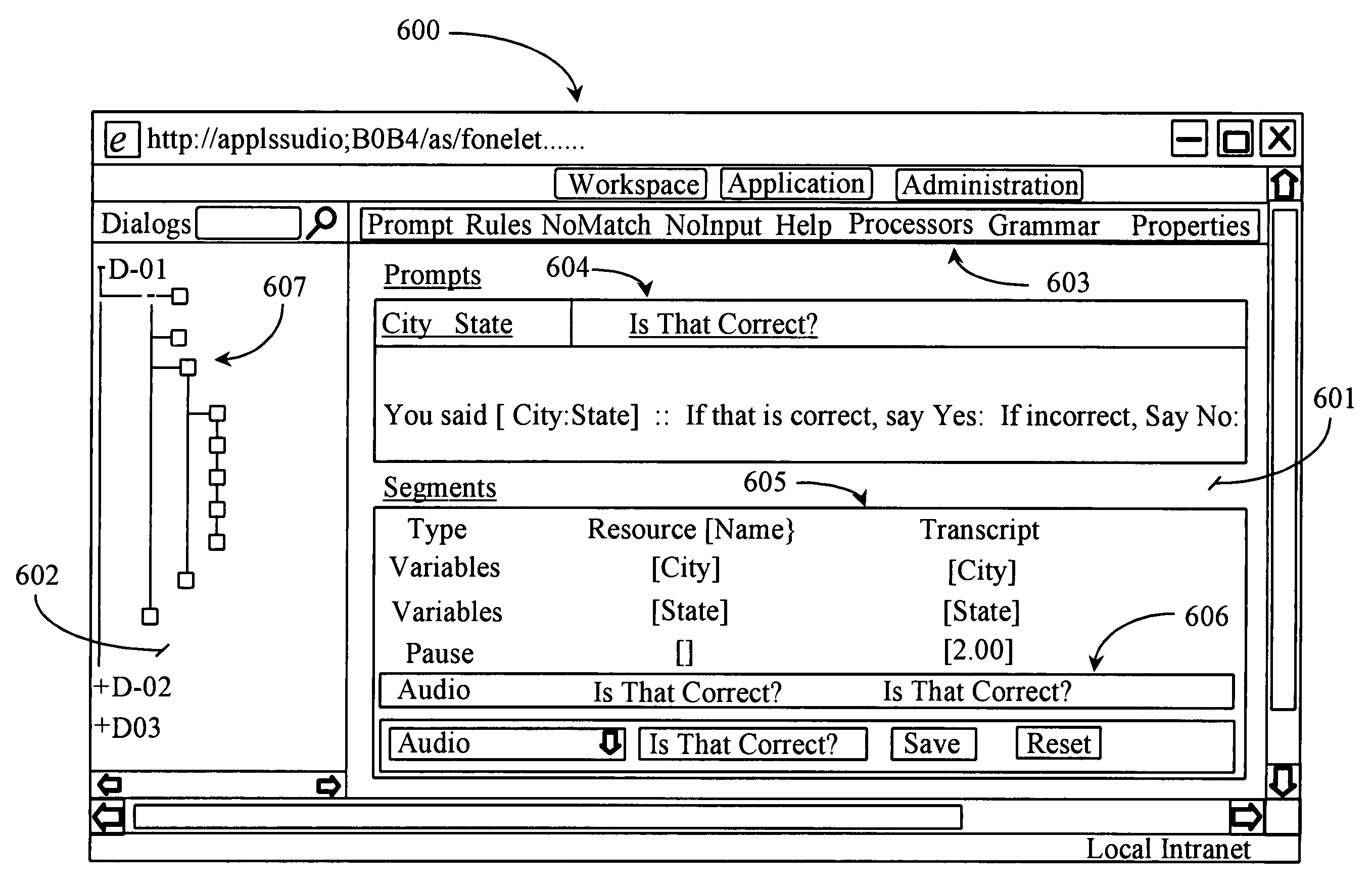
Method for creating and deploying system changes in a voice application system
ActiveUS20050135338A1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingSpeech applicationsSoftware
A system for configuring and implementing changes to a voice application system has a first software component and host node for configuring one or more changes; a second software component and host node for receiving and implementing the configured change or changes; and a data network connecting the host nodes. In a preferred embodiment, a pre-configured change-order resulting from the first software component and host node is deployed after pre-configuration, deployment and execution thereof requiring only one action.
Owner:HTC CORP
Automatic holographic management system integrating detection of electric energy meter and warehousing management
ActiveCN101539617ARealize automatic feeding processAchieve contactRadiation pyrometryElectrical measurementsTemperature monitoringEngineering
The invention discloses an automatic holographic management system integrating detection of an electric energy meter and warehousing management, comprising an automatic pipelining standard device for detection of the electric energy meter, an unboxing machine, a boxing machine and a three-dimensional table library; wherein the three-dimensional table library is respectively connected with the boxing machine and the unboxing machine; and the boxing machine and the unboxing machine are respectively connected with the automatic pipelining standard device for detection of the electric energy meter by a conveying belt. The system changes large amount of repeated and mechanical manual modes in the whole process of the operation of the electric energy meter, and has the automatic functions of automatic delivery from the warehouse, automatic distribution, automatic feeding, automatic positioning, automatic wire connection, automatic image recognition, automatic temperature monitoring, automatic wire disconnection, automatic discharging, automatic boxing, automatic disc packing and automatic warehouse entry.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD SHAOXING POWER SUPPLY CO +1
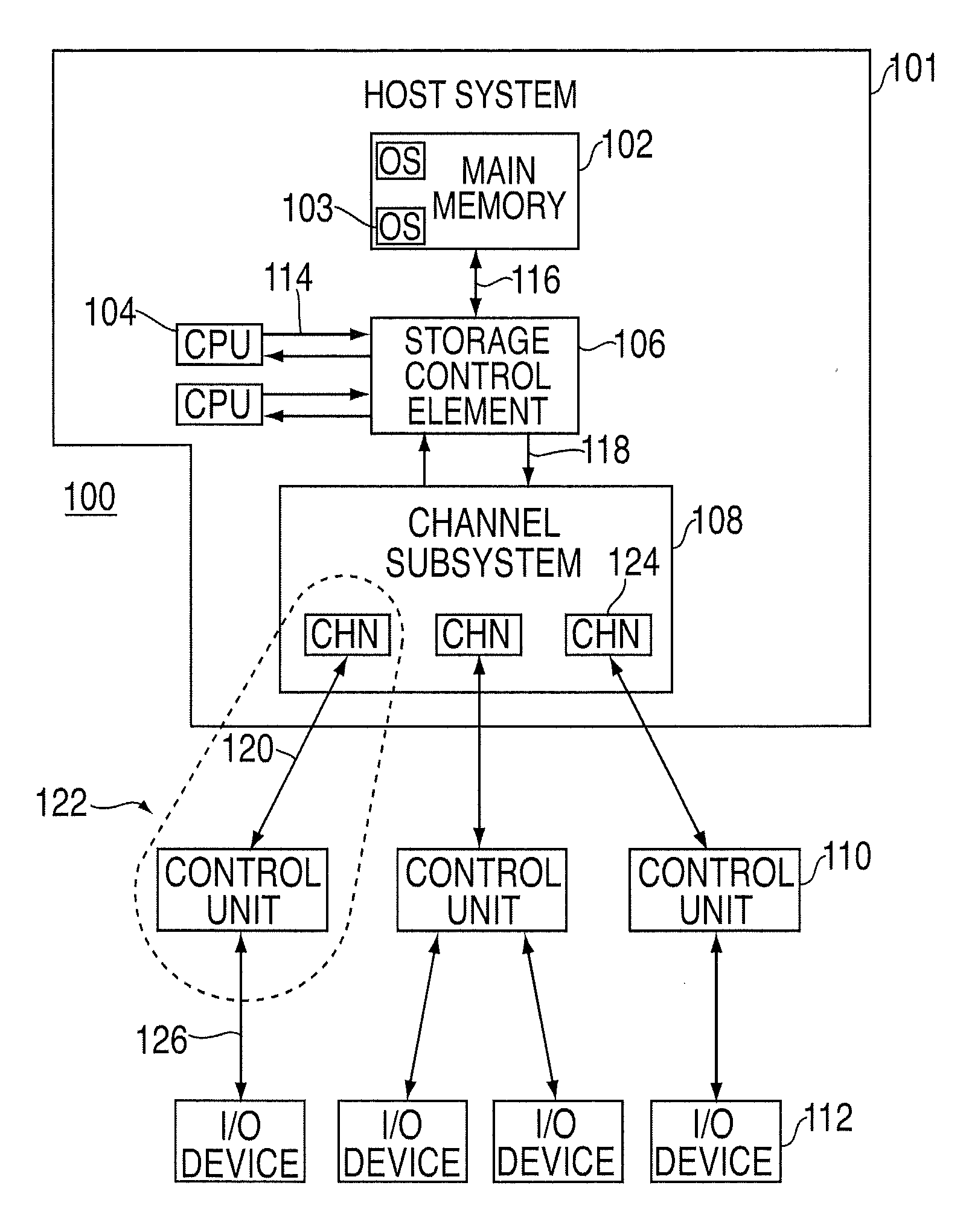
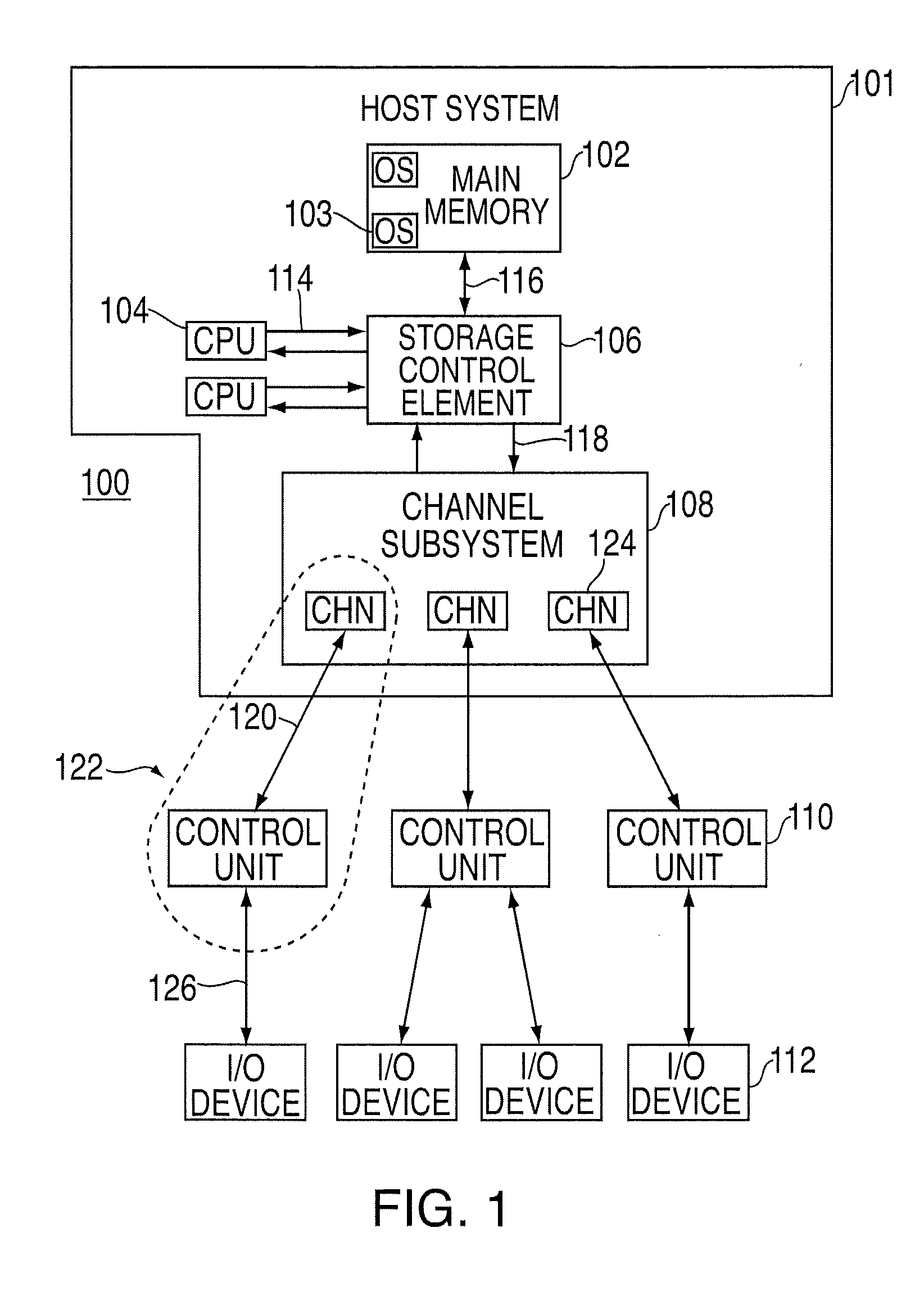
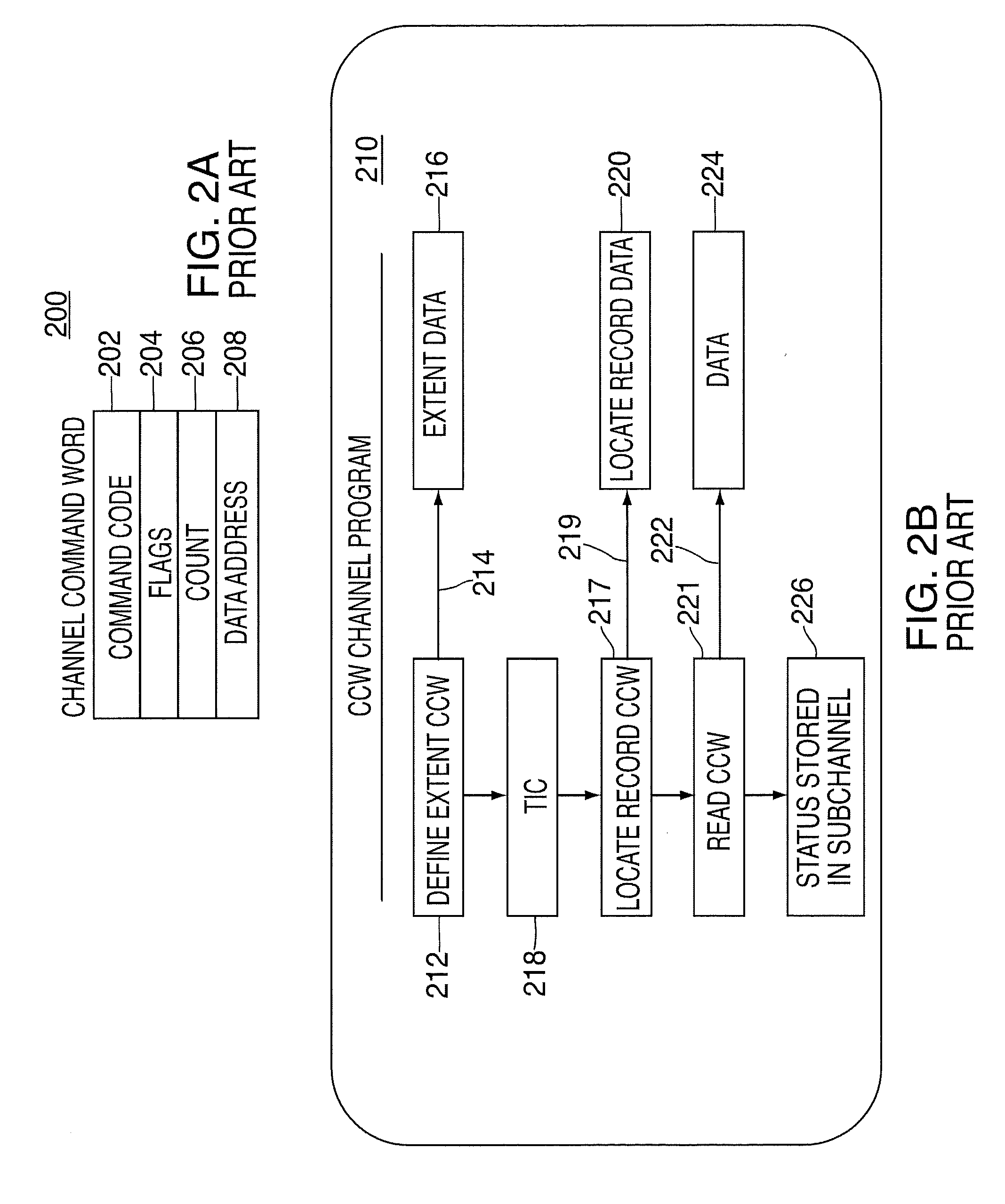
Processing of data to perform system changes in an input/output processing system
ActiveUS20090210561A1Multiplex system selection arrangementsError preventionProcess communicationComputer science
A computer program product, an apparatus, and a method for processing communications between a target and an initiator an input / output processing system are provided. The computer program product includes a tangible storage medium readable by a processing circuit and storing instructions for execution by the processing circuit for performing a method. The method includes: sending a message from the initiator to the target, the message requesting suspension of input / output operations between the initiator and the target for a period of time, the period of time being defined by the message; responsive to the message, suspending input / output operation messages for the period of time; performing a system change comprising at least one of: at least one update, a computer program installation, a recovery, and a change in operating parameters; and initiating new input / output operations after at least one of: expiration of the period of time and initiation of new input / output operations by the initiator.
Owner:IBM CORP
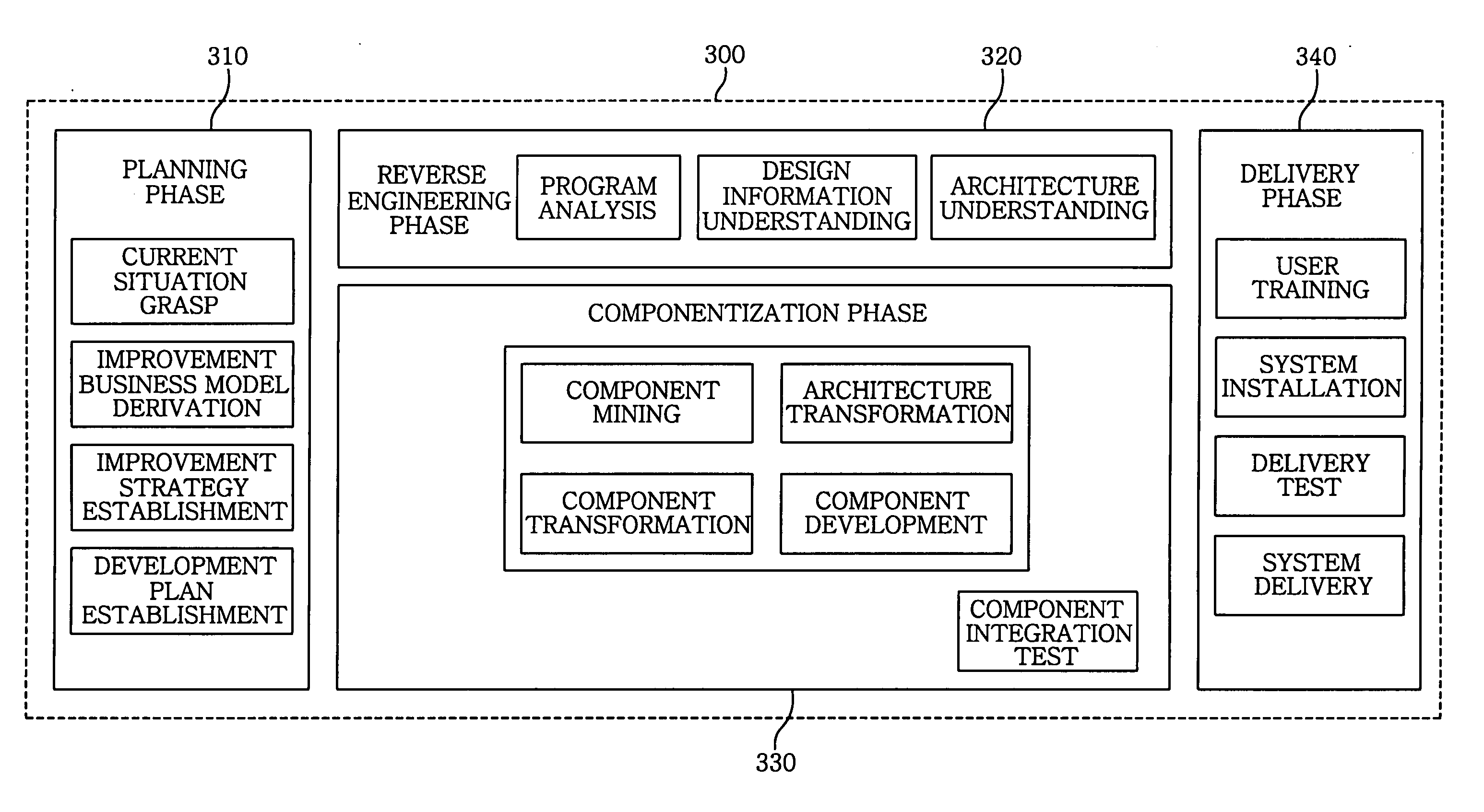
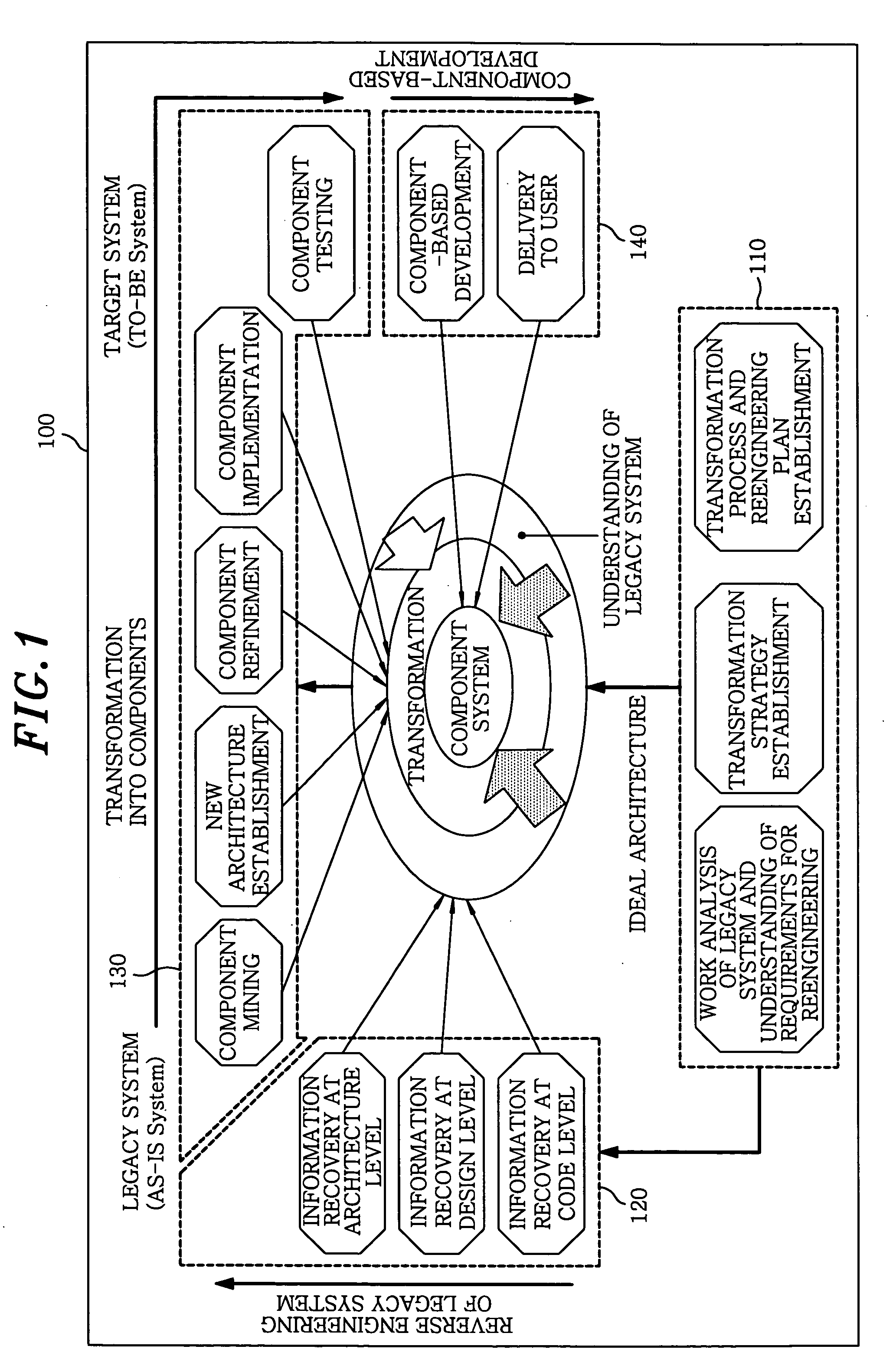
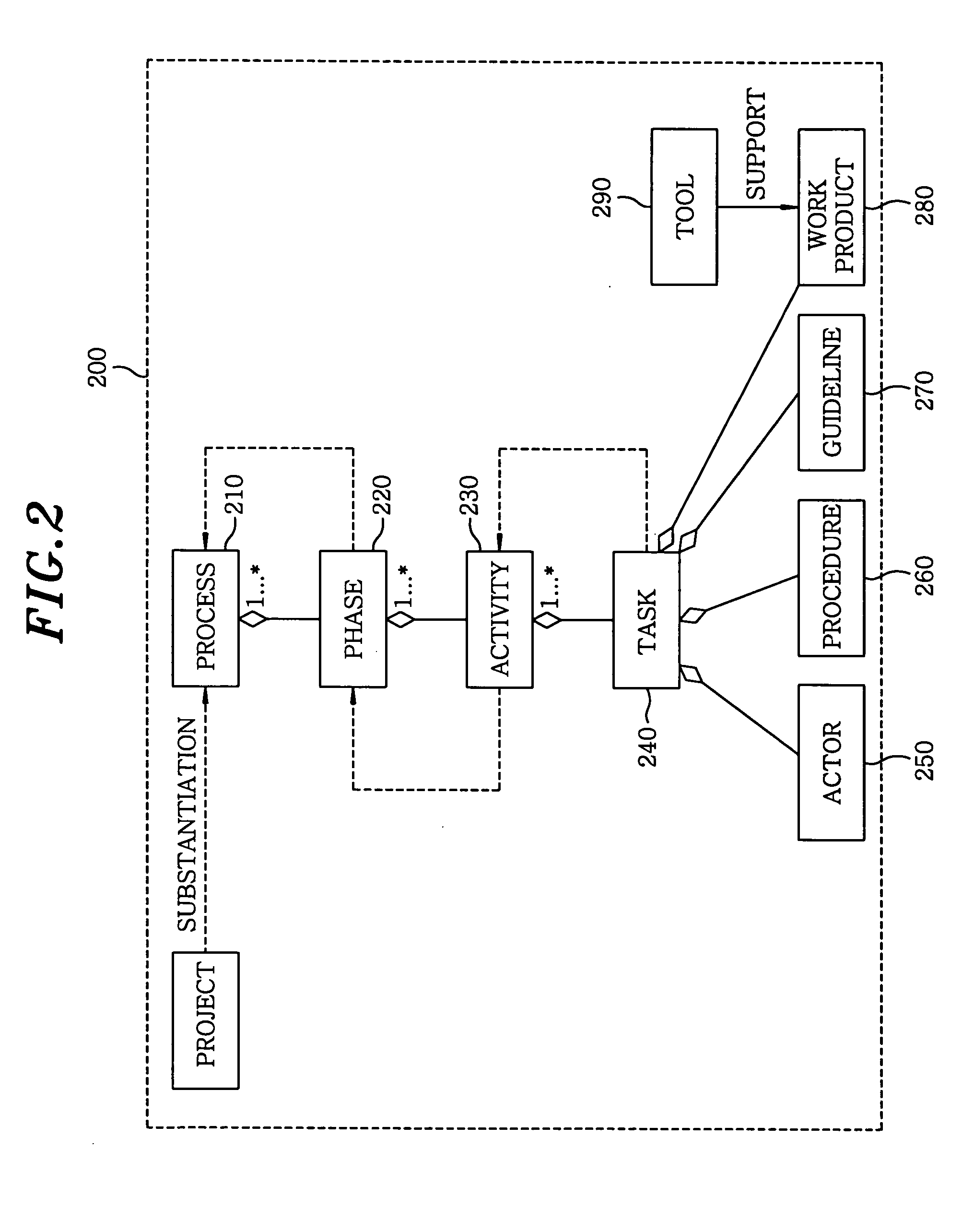
Componentization method for reengineering legacy system
InactiveUS20050138603A1Minimizing semantic differenceIncrease valueDecompilation/disassemblyReverse engineeringProduction rateSoftware engineering
The present invention proposes a Magic and Robust Methodology Integrated-Reengineering (MaRMI-RE), which is a reengineering methodology defining a process including procedures and techniques for a componentization of legacy systems and work products generated during the process. A continuous evolution model for the legacy systems proposed in the present invention enables the legacy systems to be systematically transformed into component systems capable of smoothly complying with new requirements, thus maximizing productivity and efficiency of the legacy systems with respect to potential business and system change requirements.
Owner:ELECTRONICS & TELECOMM RES INST
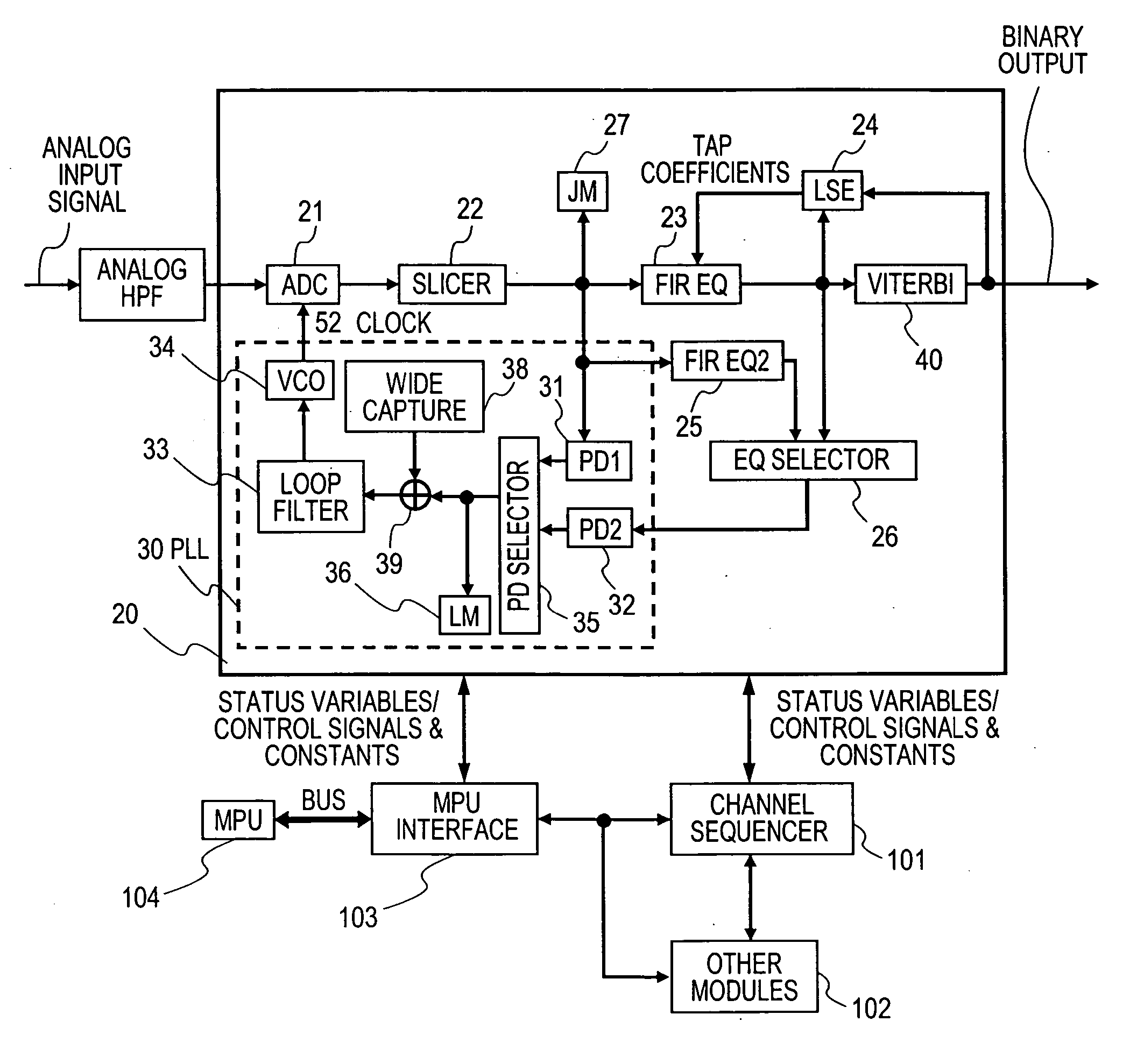
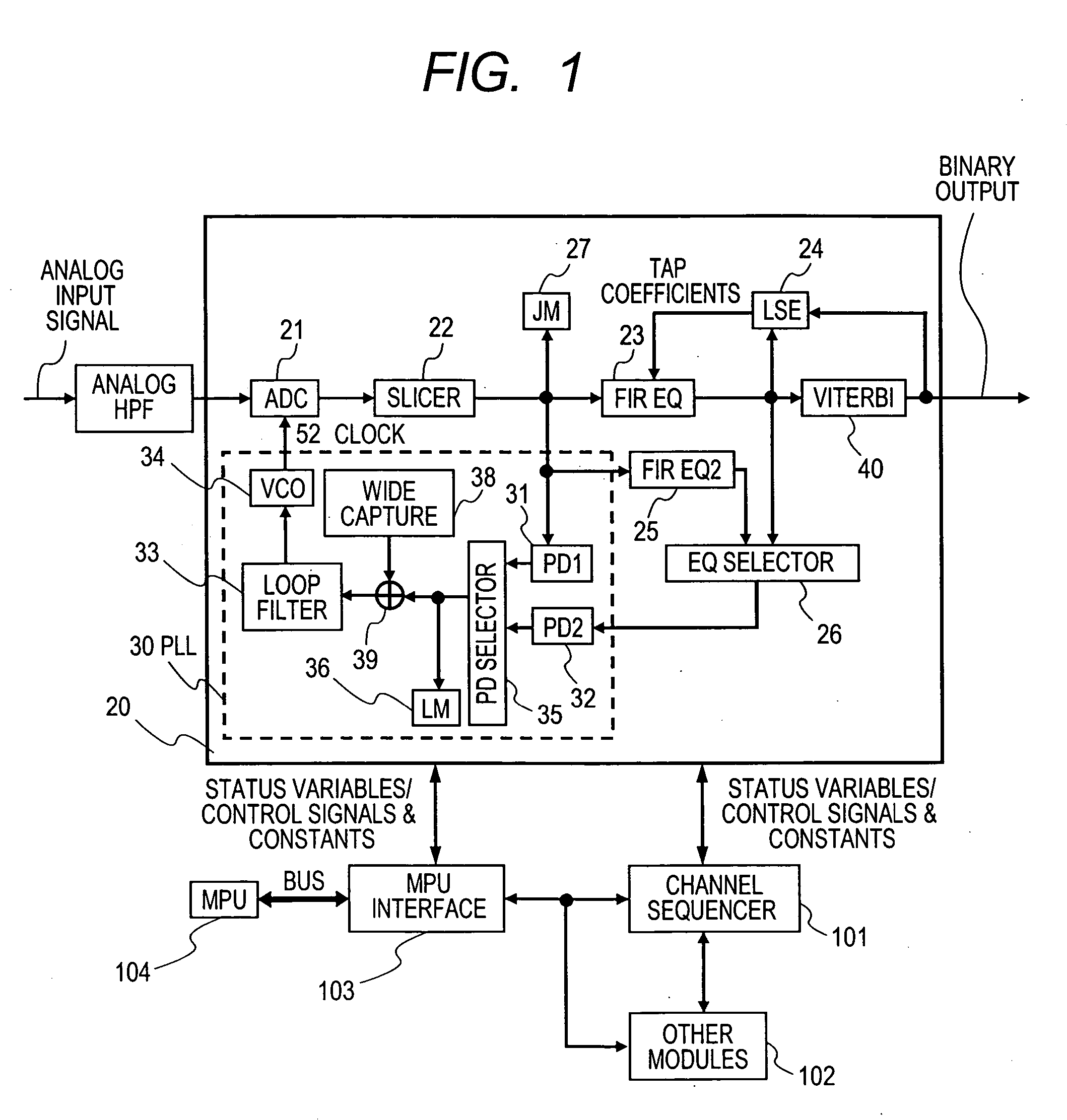
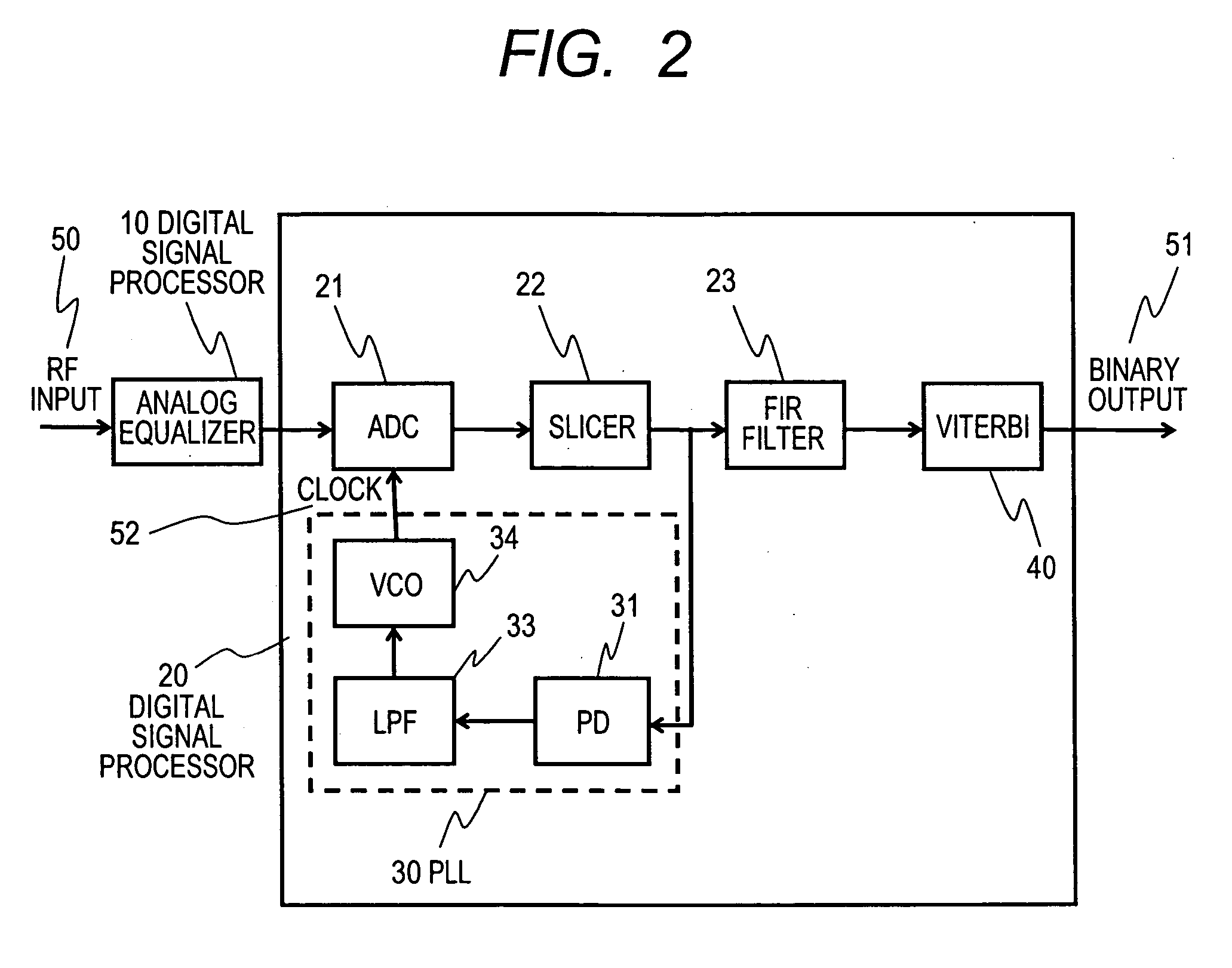
Information read device and read signal processing circuit
ActiveUS20060280240A1High error rateSatisfied with the effectMultiple-port networksFilamentary/web record carriersSignal processing circuitsSignal-to-noise ratio (imaging)
An optical disk read signal processing system for Blu-ray disc systems to ensure stable phase-locked locked operation even with a low signal-to-noise ratio. This system changes a loop configuration of a phase lock loop circuit according to the operating state, and utilizes a FIR equalizer for phase detection. This system attains a low error rate even when the signal-to-noise ratio of an input signal is low, and avoids pulse edges with low phase detection accuracy or signal pulse streams with a high possibility of being mistakenly detected as an edge in conventional methods, and also supports diverse types of input signals.
Owner:HITACHI CONSUMER ELECTRONICS CORP
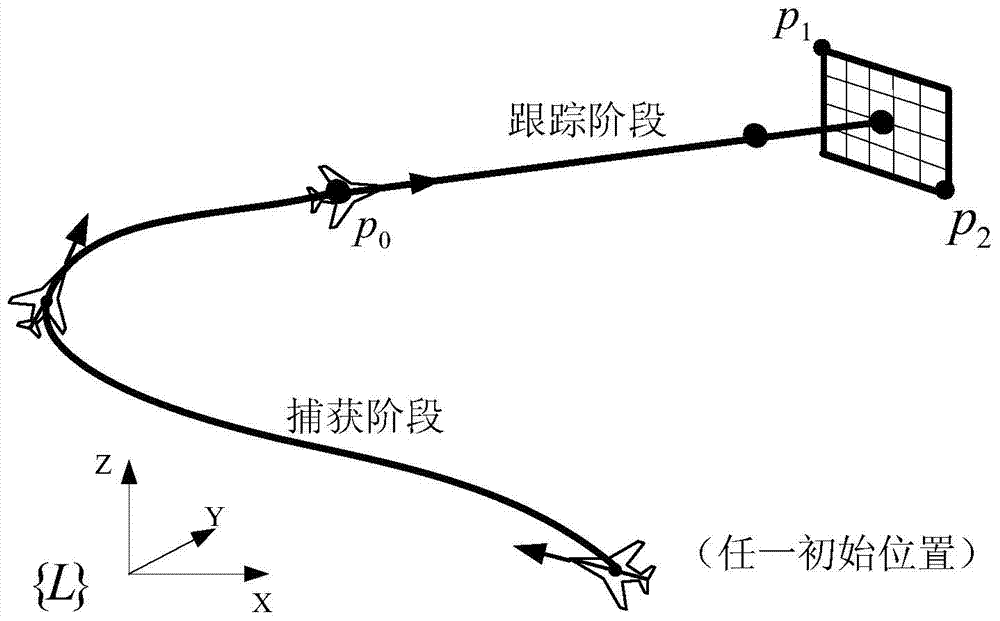
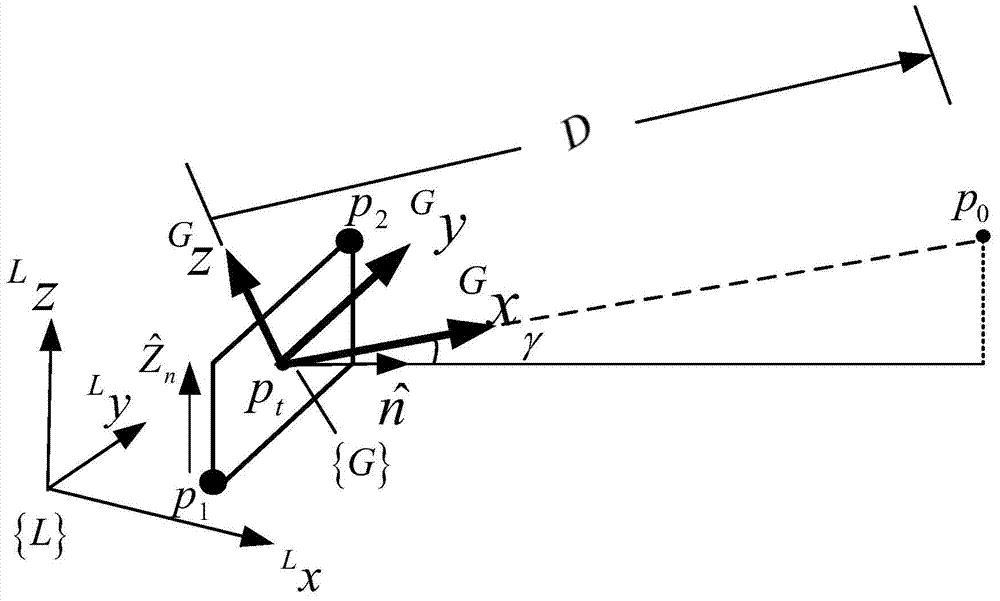
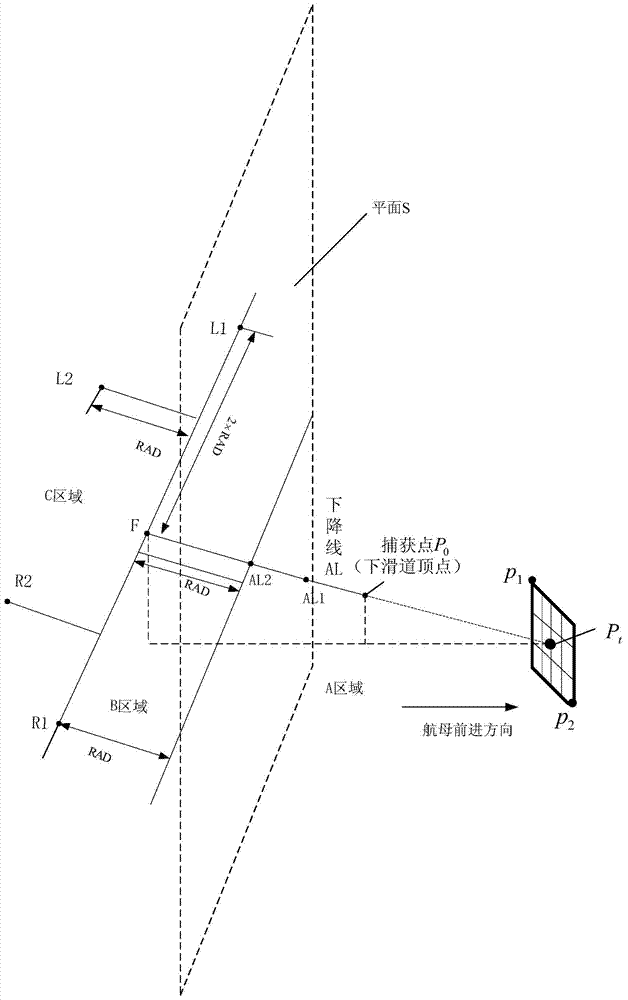
Automatic carrier-landing guiding method of carrier-borne unmanned aircraft
InactiveCN103700286AImprove landing performanceImprove reliabilityAutomatic aircraft landing aidsLanding performanceControl signal
The invention discloses an automatic carrier-landing guiding method of a carrier-borne unmanned aircraft and belongs to the technical field of automatic carrier-landing guiding for carrier-borne aircrafts. The method comprises the following steps of determining a reference flight path at a capturing phase according to the initial course information and the positional information of the unmanned aircraft, determining a reference flight path at a tracking phase by considering the influence of deck movement, acquiring a flight-path error at the capturing phase by adopting a direct sightline method, and obtaining a flight-path error at the tracking phase by adopting a dynamic coordinate-system changing method; calculating longitudinal and transverse control-signal instruction values according to the flight-path errors, and guiding the carrier-borne unmanned aircraft to fly along the reference flight paths. The automatic carrier-landing guiding method of the carrier-borne unmanned aircraft provided by the invention has high realizability and operability, so that the carrier-landing performance of the unmanned aircraft under a specific carrier-landing environment is improved; the deck movement is directly led into a carrier-landing tracking-phase guiding algorithm, so that the addition of a deck-movement compensator to a controller is avoided, the complexity of a flight control system is lowered, and the reliability of a carrier-landing system is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
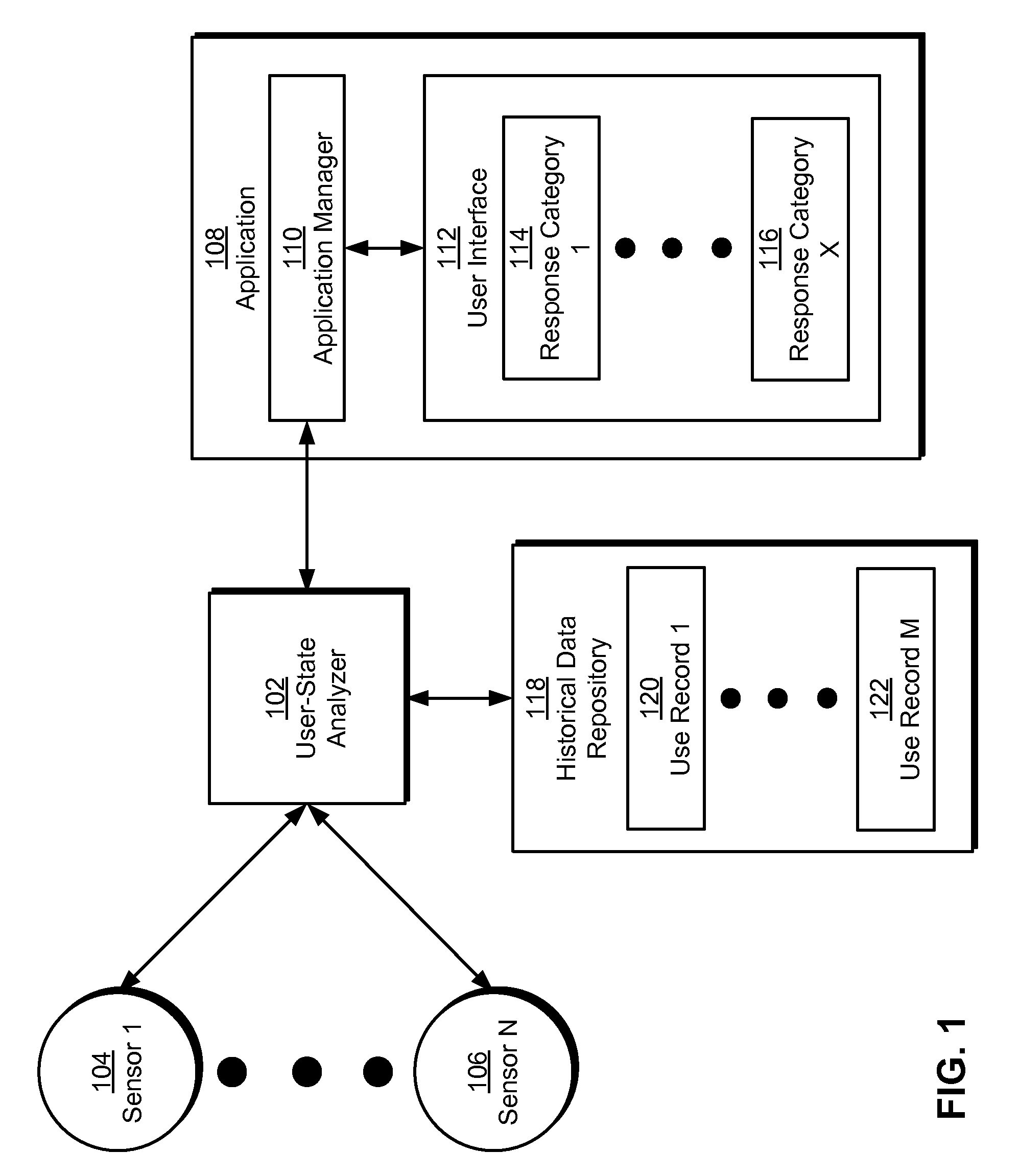
Method and system for dynamic adaptation of user experience in an application
ActiveUS8346680B2Execution for user interfacesSpecial data processing applicationsMental stateService experience
Some embodiments of the present invention provide a system that executes an application. During operation, the system physiologically monitors a user of the application with a set of sensors as the application executes. Next, the system assesses a mental state of the user based on physiological data collected from the sensors. Finally, the system changes the behavior of the application based on the assessed mental state to facilitate use of the application by the user.
Owner:INTUIT INC
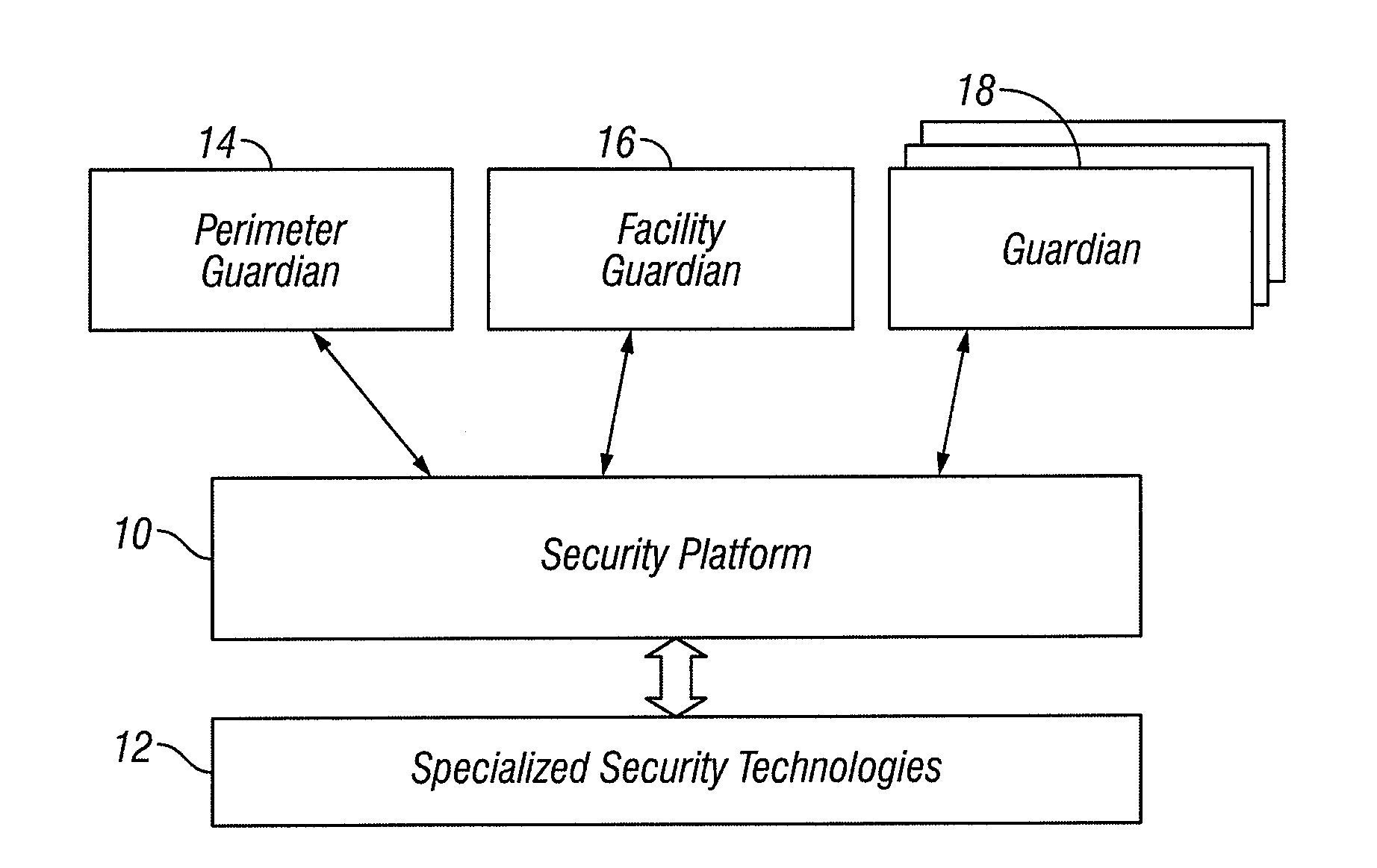
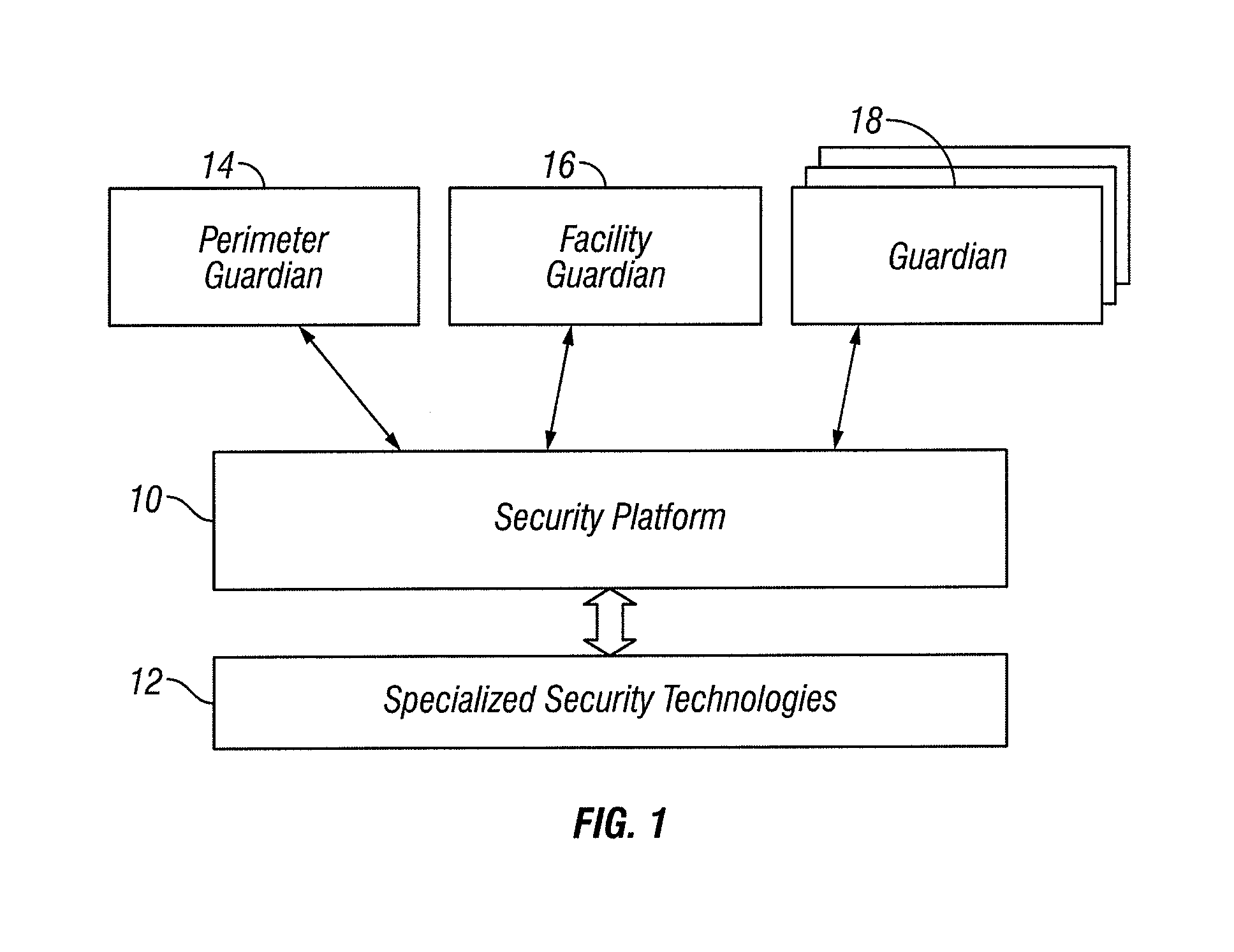
Automated Adaption Based Upon Prevailing Threat Levels in a Security System
InactiveUS20100156628A1Easy to adjustHigh riskIndication of parksing free spacesIndividual entry/exit registersRisk levelThreat level
Four threat levels reflect a prevailing risk and can be adjusted, for example, when local authorities advise of an increased likelihood of terrorist activity. Thus, a higher threat level in such system indicates a higher level of risk to a particular facility. In an embodiment of the invention, the behavior of the system changes with a simple adjustment to the threat level.
Owner:TITAN HLDG
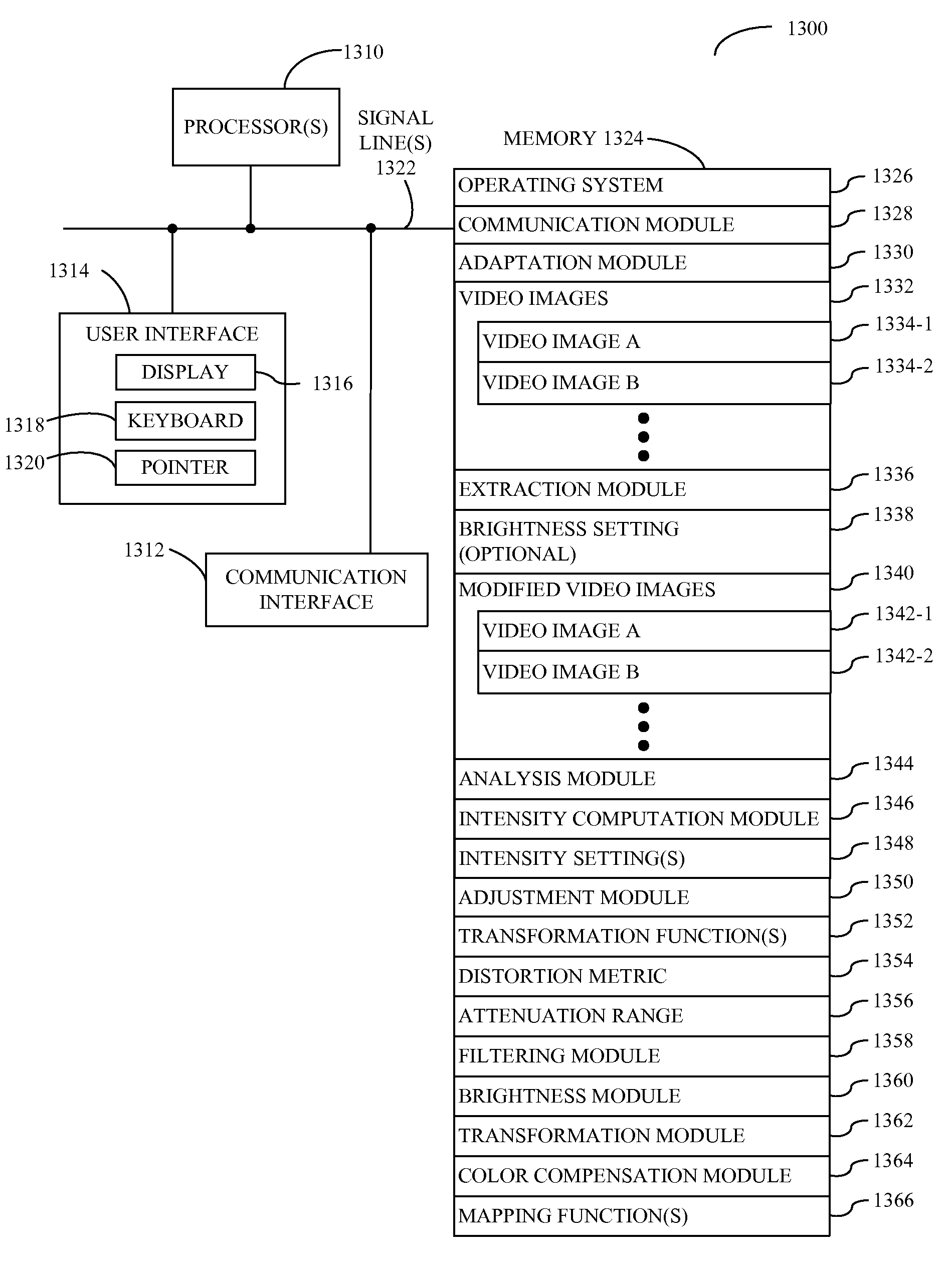
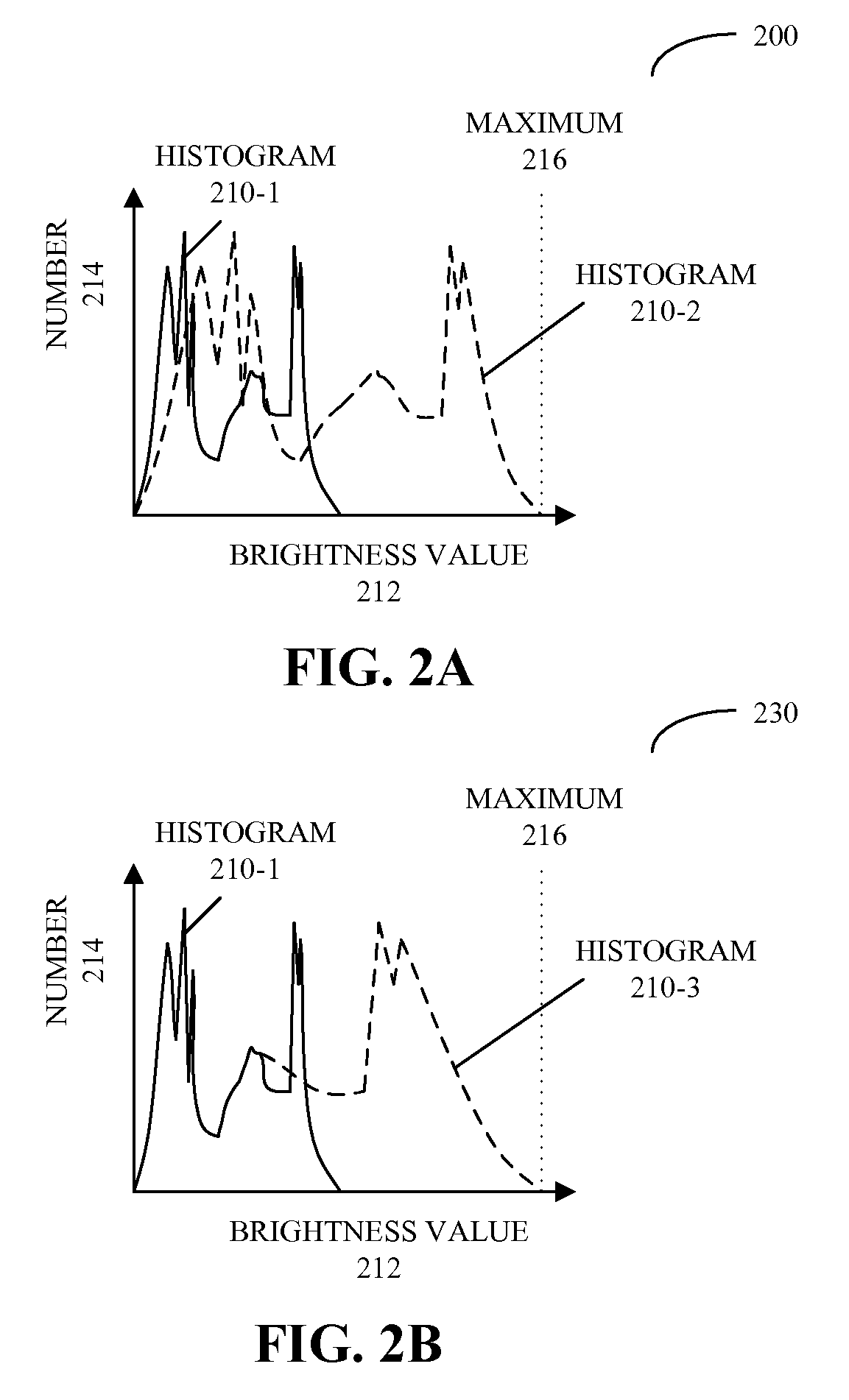
Technique for adjusting a backlight during a brightness discontinuity
InactiveUS20090002564A1Reduce noiseReduce power consumptionTelevision system detailsStatic indicating devicesDisplay deviceVideo image
Embodiments of a system that includes one or more integrated circuits are described. During operation, the system receives a sequence of video images, and calculates brightness metrics associated with the video images in the sequence of video images. Then, the system determines an intensity setting of a light source, which illuminates a display that is configured to display the sequence of video images, and scales brightness values of a given video image in the sequence of video images based on a given brightness metric associated with the given video image. Next, the system changes the intensity setting and scaling the brightness values when there is a discontinuity in the brightness metrics between two adjacent video images in the sequence of video images.
Owner:APPLE INC
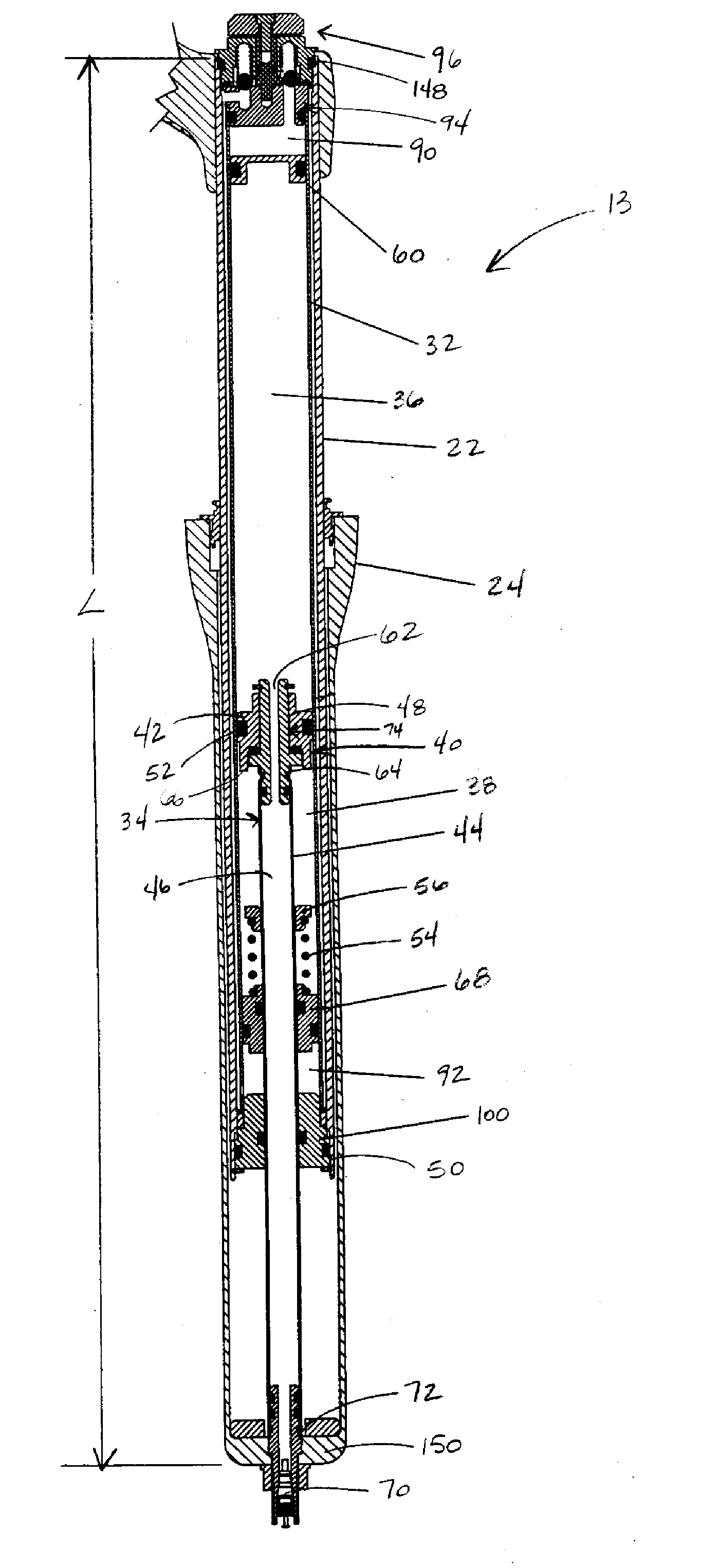
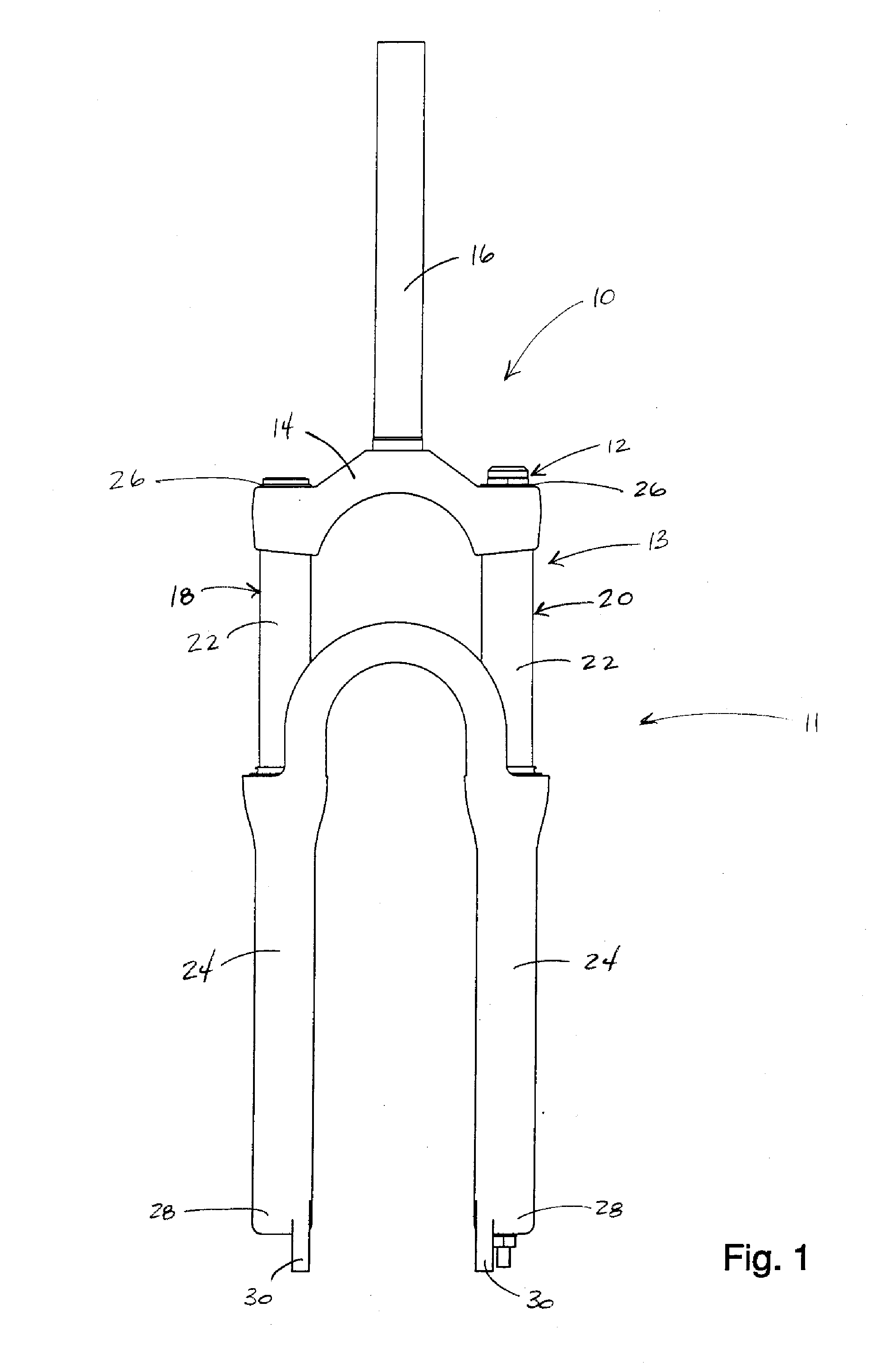
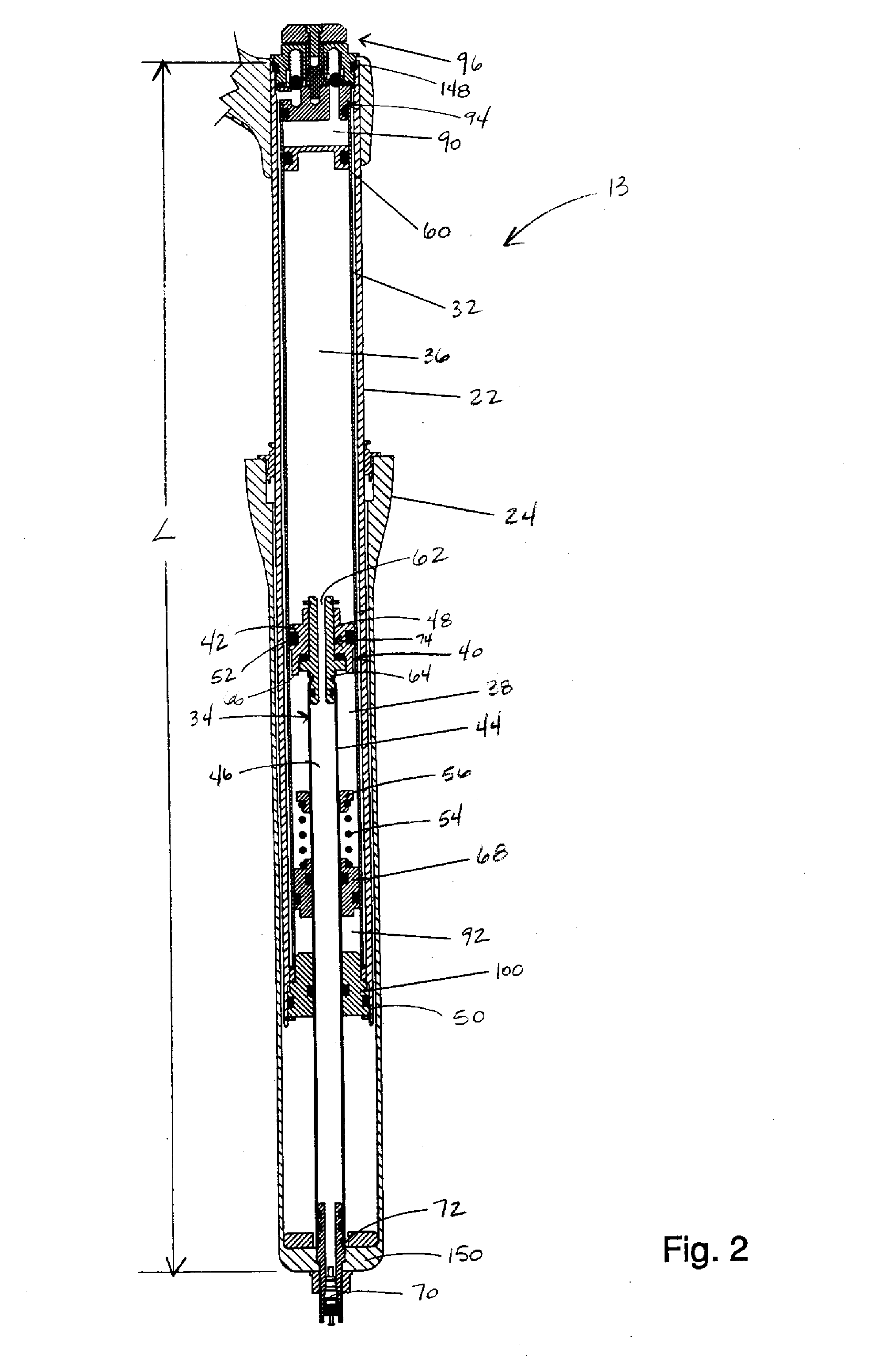
Bicycle suspension system
InactiveUS20080041681A1Wheel based transmissionFrictional rollers based transmissionEngineeringPiston
A bicycle suspension system including a travel adjustment apparatus. The bicycle suspension system includes a piston tube and a piston assembly slidably disposed in the piston tube forming a shock-absorbing mechanism. The piston assembly is in contact with the piston tube. The travel adjustment apparatus includes first and second fluid chambers, a fluid valve mechanism for controlling fluid flow between the first and second fluid chambers, and an actuating assembly operatively connected to the fluid valve mechanism operable between at least two rider-selectable travel settings to operate the fluid valve mechanism between at least two valve settings corresponding to the rider-selectable travel settings. The first and second fluid chamber are configured such that operation of the fluid valve mechanism between two of the at least two valve settings permits the piston assembly to be moved from a first initial position relative to the piston tube to a second initial position relative to the piston tube such that the suspension system changes from a first of the at least two amounts of travel to a second of the at least two amounts of travel.
Owner:SRAM CORPORATION
Dynamic modification of application behavior in response to changing environmental conditions
InactiveUS20030135638A1Multiple digital computer combinationsData switching networksComputer scienceMultiple methods
Methods, systems, and computer program products for dynamically modifying an application program's behavior in response to changing environmental conditions (such as network changes, system changes, and so forth). The application may solicit such information, and / or may receive unsolicited environmental change notifications. In response to a change notification, the application may take one or more of the following approaches to adapt to the changing conditions: (1) alter its execution; (2) modify its use of, or control of, other cooperating application; and (3) modify the selection of application execution threads. (An application might also decide to make no changes in its behavior.)
Owner:IBM CORP
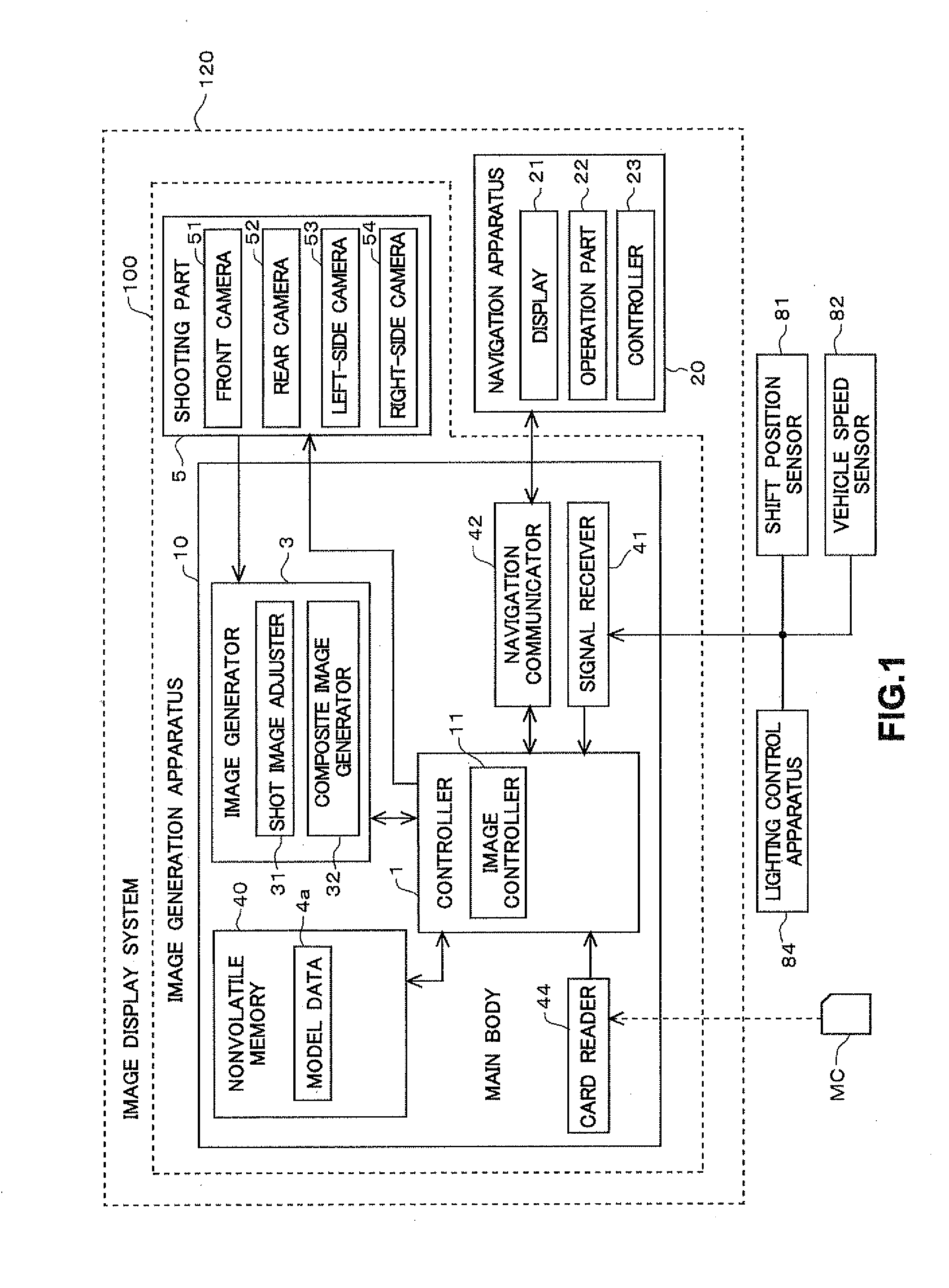
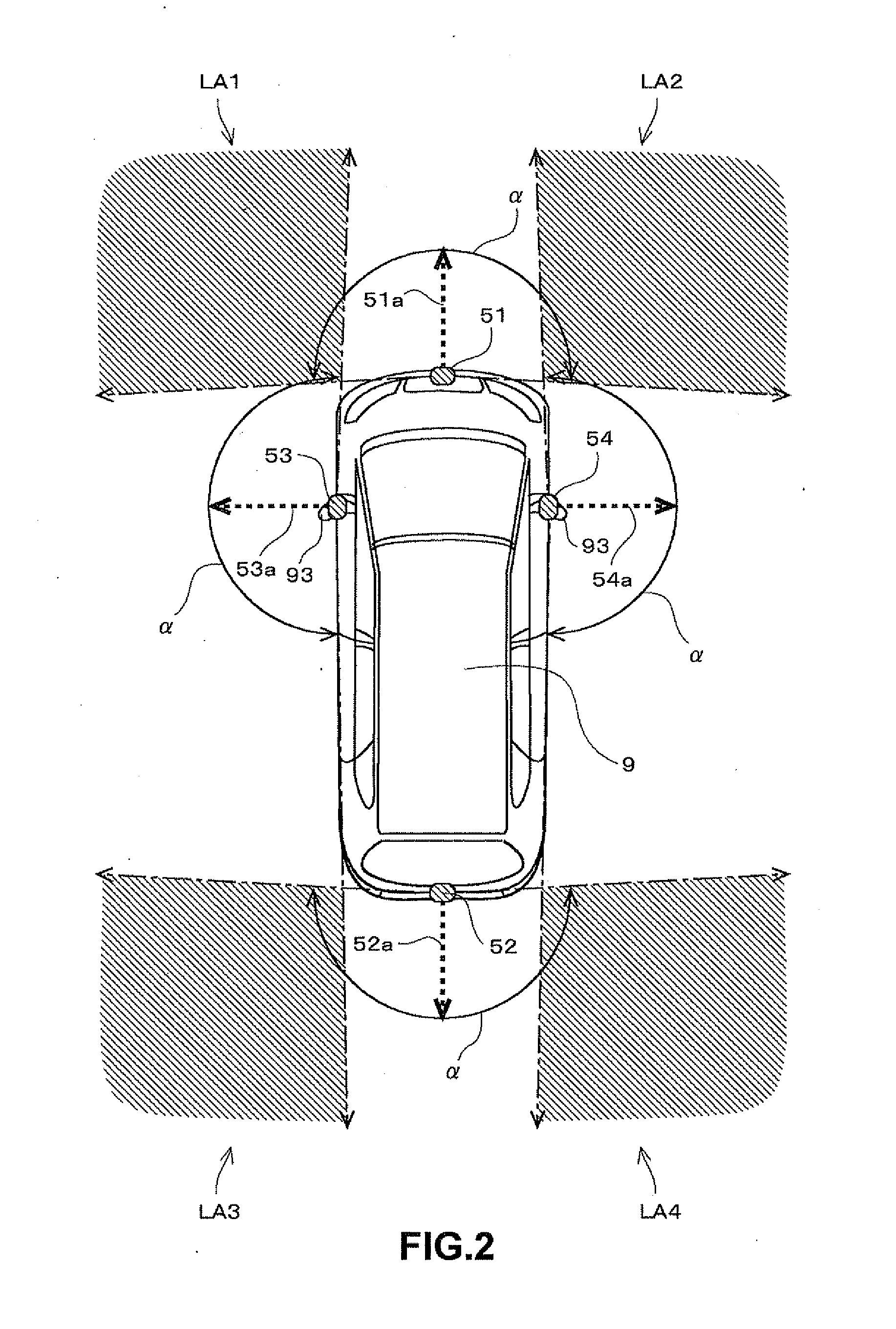
Image generation apparatus
ActiveUS20110234801A1Lighting problemReduce decreaseTelevision system detailsColor television detailsViewpointsComputer graphics (images)
An image display system is capable of generating a composite image that shows a surrounding area of a vehicle viewed from virtual viewpoints, by combining a plurality of shot images taken by a plurality of on-vehicle cameras that are disposed at different locations on the vehicle. The image display system changes data volumes of two shot images taken by two of the on-vehicle cameras based on a lighting mode of a lighting apparatus, the data volumes being used for an overlap area of the composite image that corresponds to the surrounding area of the vehicle where the two on-vehicle cameras can shoot in overlap. This reduces problems caused by lighting of the lighting apparatus in the overlap area of the composite image.
Owner:FUJITSU GENERAL LTD
Method for creating and deploying system changes in a voice application system
ActiveUS7206391B2Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingSpeech applicationsSoftware
A system for configuring and implementing changes to a voice application system has a first software component and host node for configuring one or more changes; a second software component and host node for receiving and implementing the configured change or changes; and a data network connecting the host nodes. In a preferred embodiment, a pre-configured change-order resulting from the first software component and host node is deployed after pre-configuration, deployment and execution thereof requiring only one action.
Owner:HTC CORP
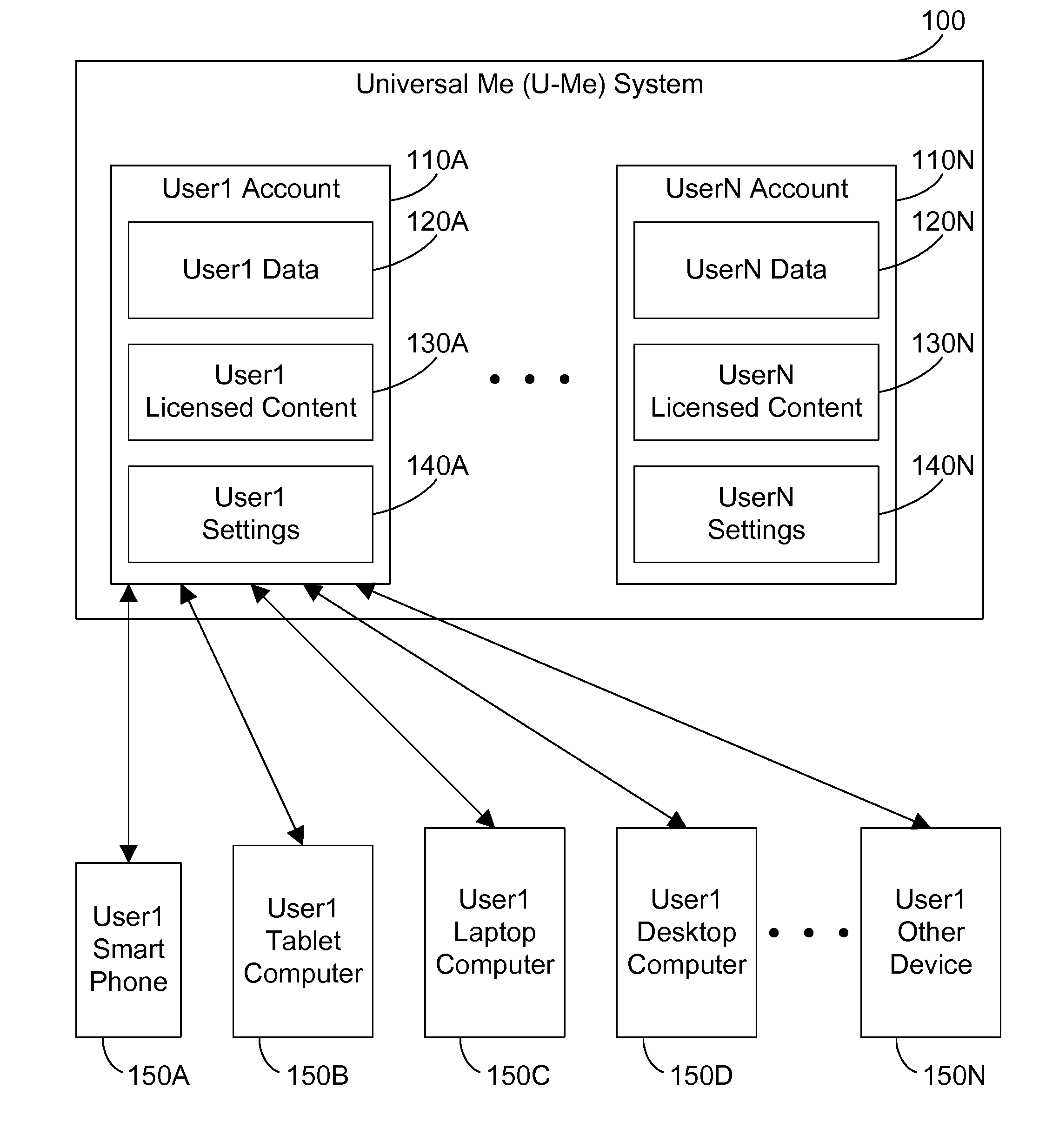
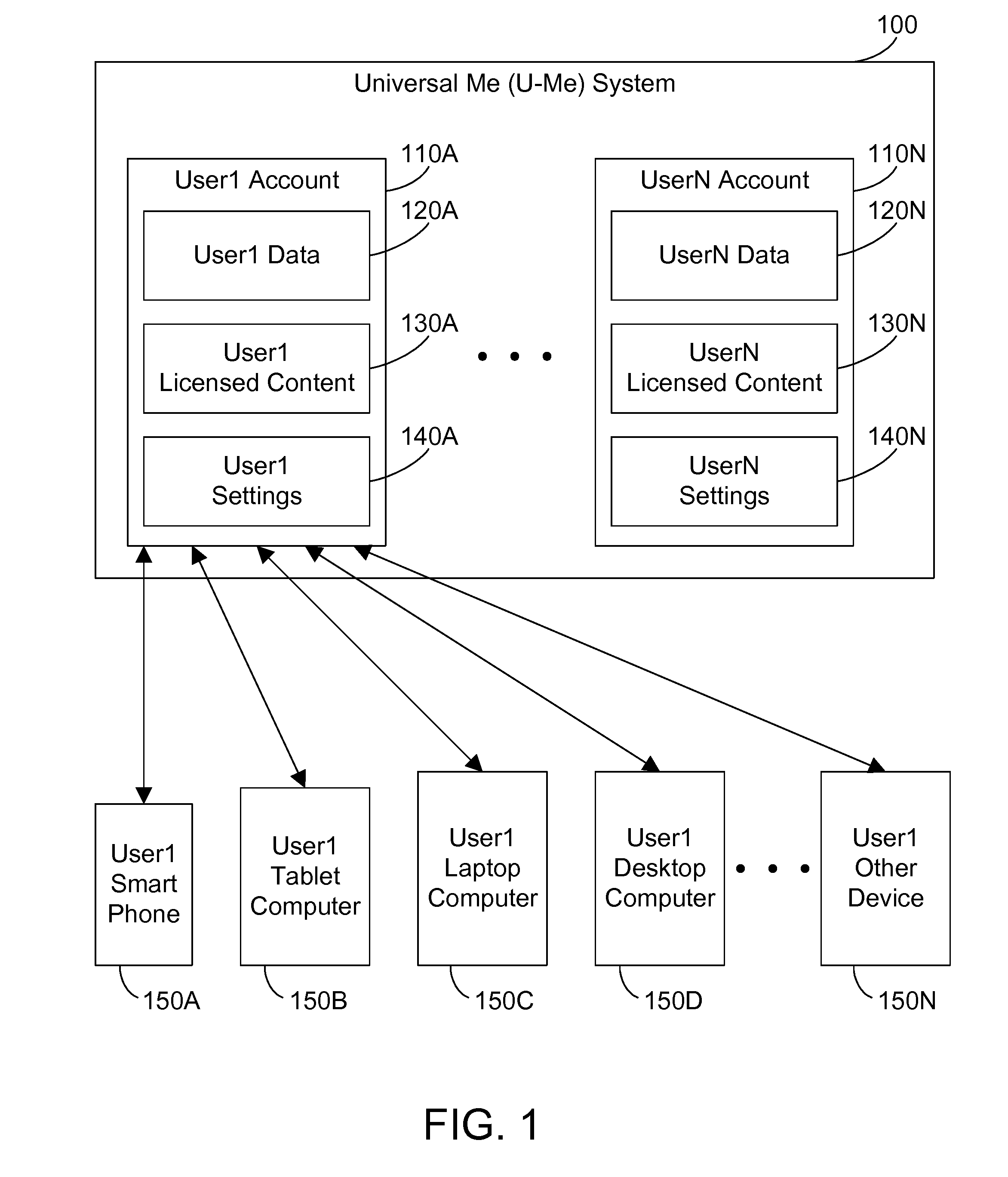
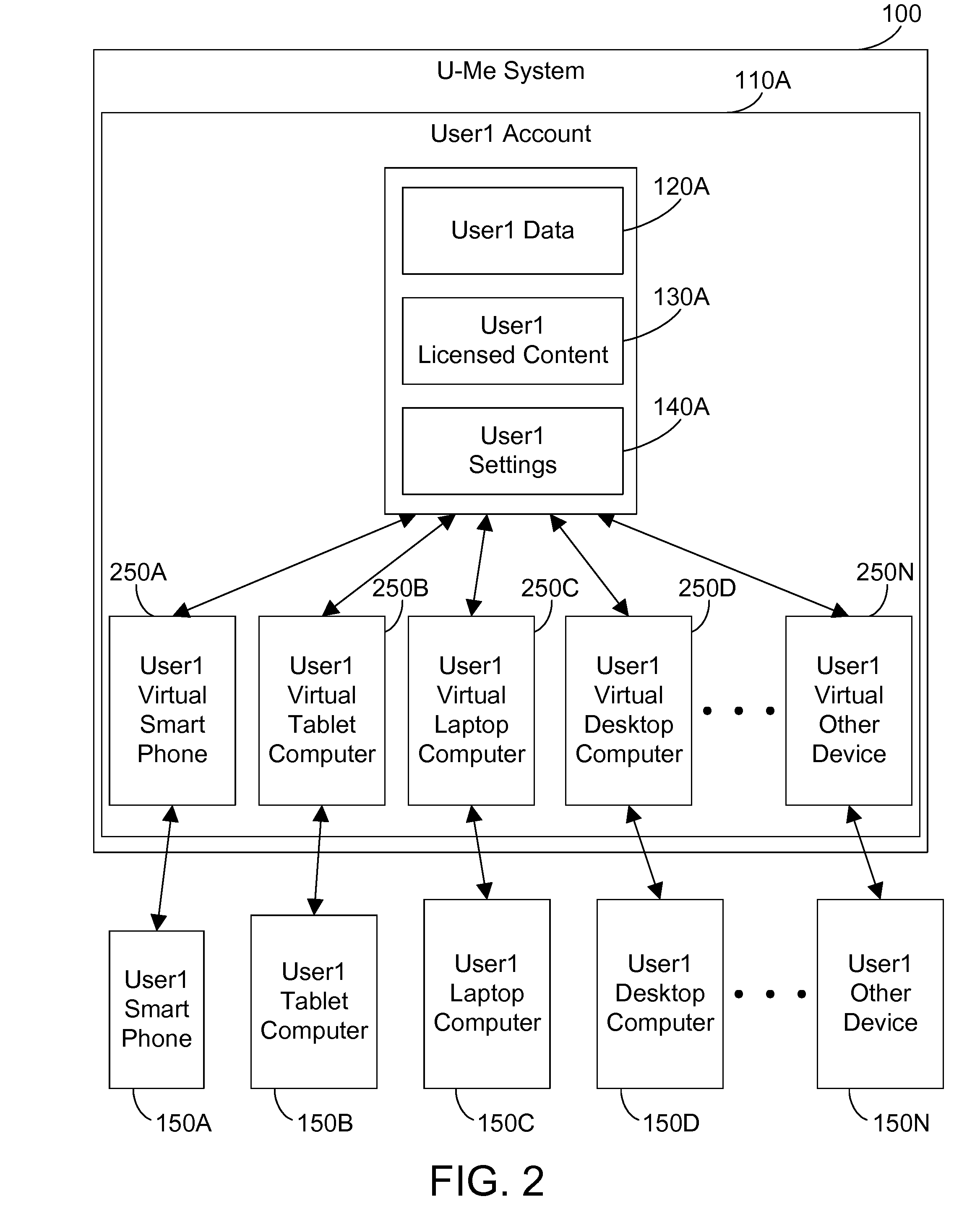
Making a user's data, settings, and licensed content available in the cloud
InactiveUS20150067805A1Digital data processing detailsDatabase distribution/replicationDevice typeRelevant information
A cloud-based computer system changes the modern paradigm from being device-centric to being person-centric. The system makes all user data, software settings, device settings, and licensed content for a user available in the cloud. The system includes a conversion mechanism that can convert information intended for one device type to a different device type. Thus, a user changing smart phone platforms can convert their current smart phone settings to equivalent settings on the new phone platform, and their new phone can then be configured using the user's converted settings stored in the cloud. By storing all the user's relevant information in the cloud, this information may be accessed anywhere and may be used to configure a large number of different devices according to the user's settings.
Owner:U ME HLDG
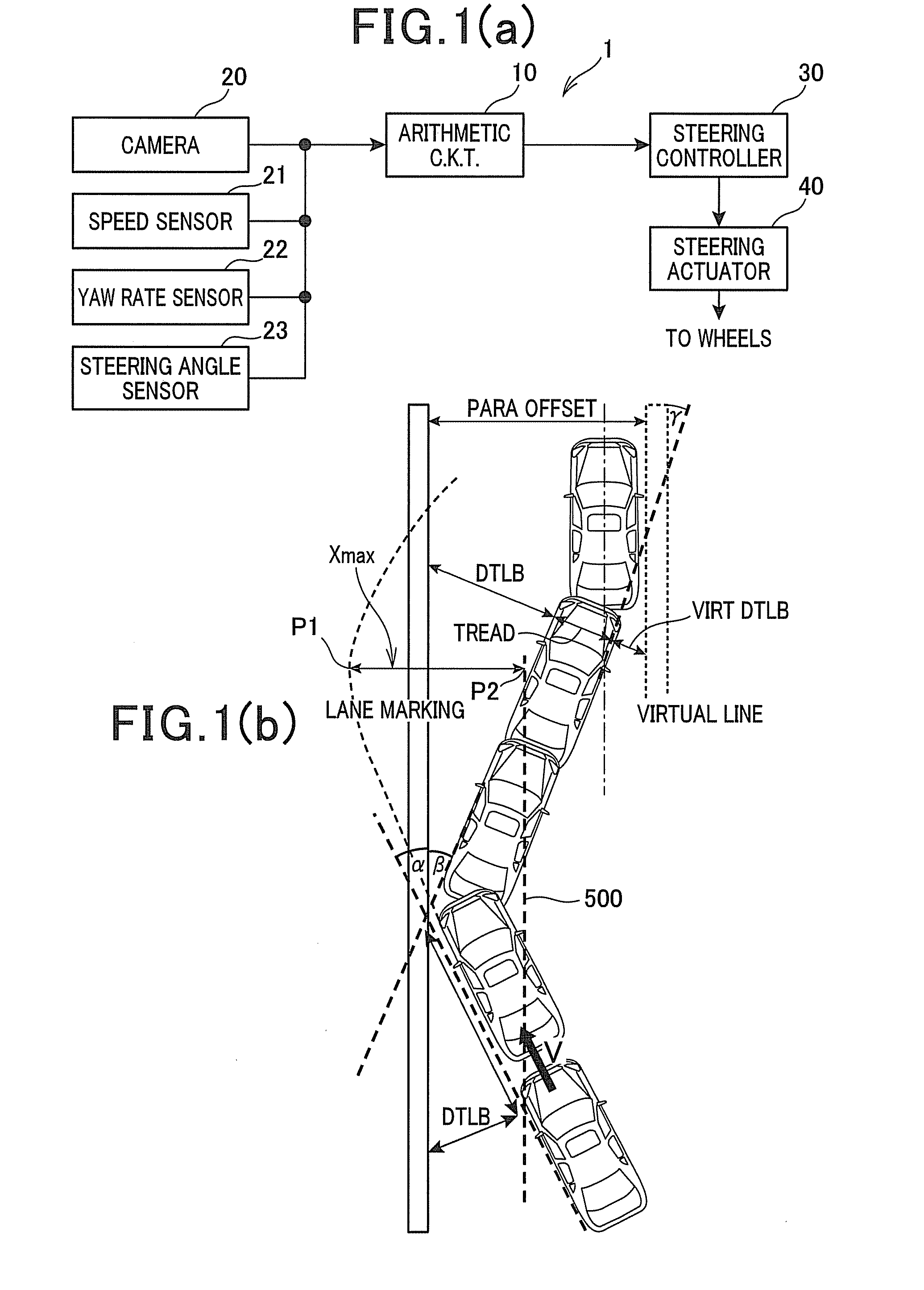
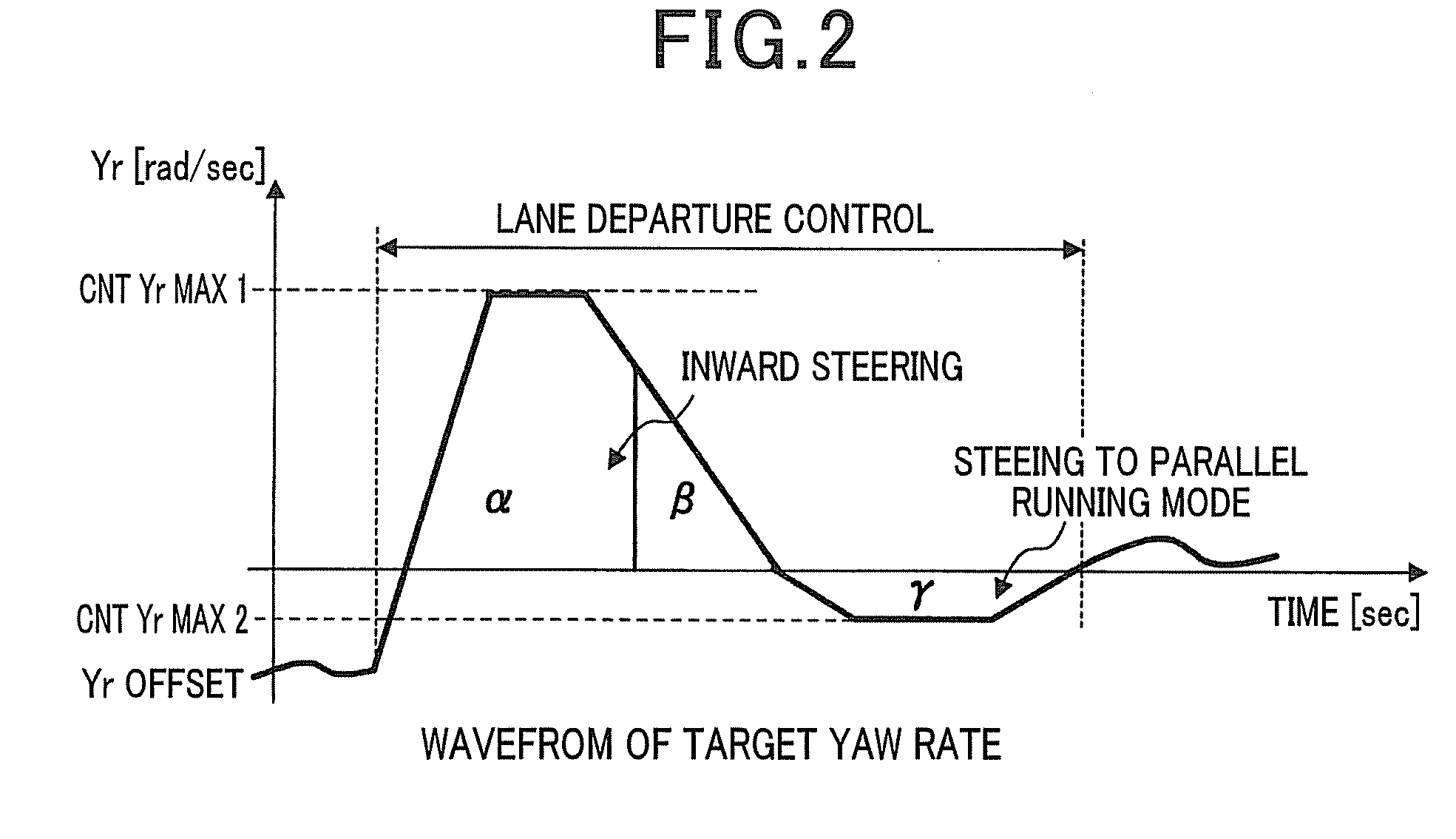
Lane departure control system
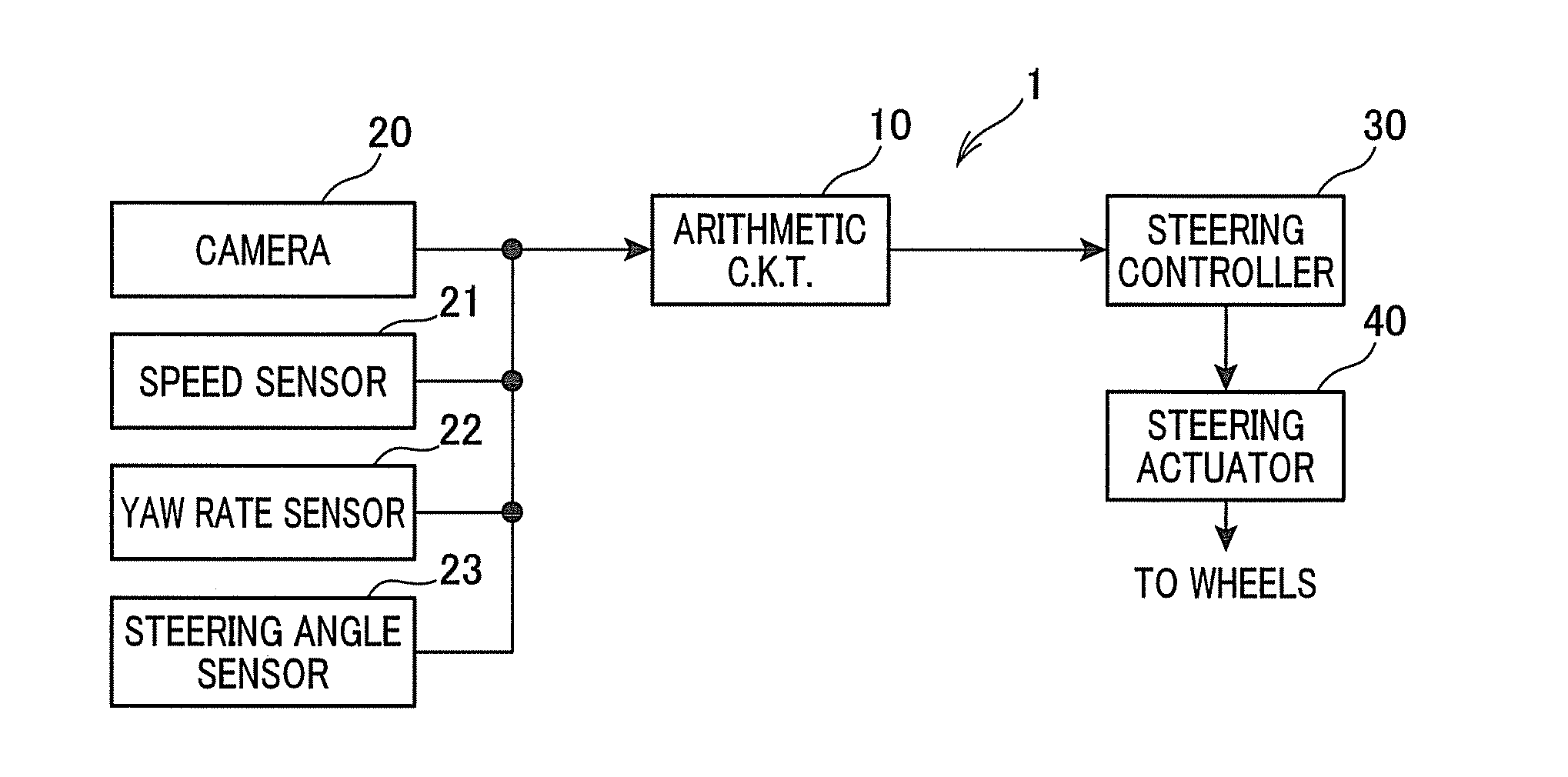
ActiveUS20130190982A1Easy to operateSteering initiationsDigital data processing detailsPhysical loadControl system
A lane departure control system is provided which steers a vehicle toward the center of a lane of a road at a first yaw rate by a controlled angle when the vehicle is determined to be about to deviate from the lane. Afterwards, when the vehicle is determined to be traveling toward a virtual line defined near a lane boundary, the system steers the vehicle by a correction angle so as to orient the vehicle parallel to the virtual line at a second yaw rate. The system changes the value of the first yaw rate at a first rate within the controlled angle and also changes the value of the second yaw rate at a second rate within the correction angle. An absolute value of the second rate is set smaller than that of the first rate, thereby minimizing an undesirable physical load on a driver of the vehicle.
Owner:DENSO CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com