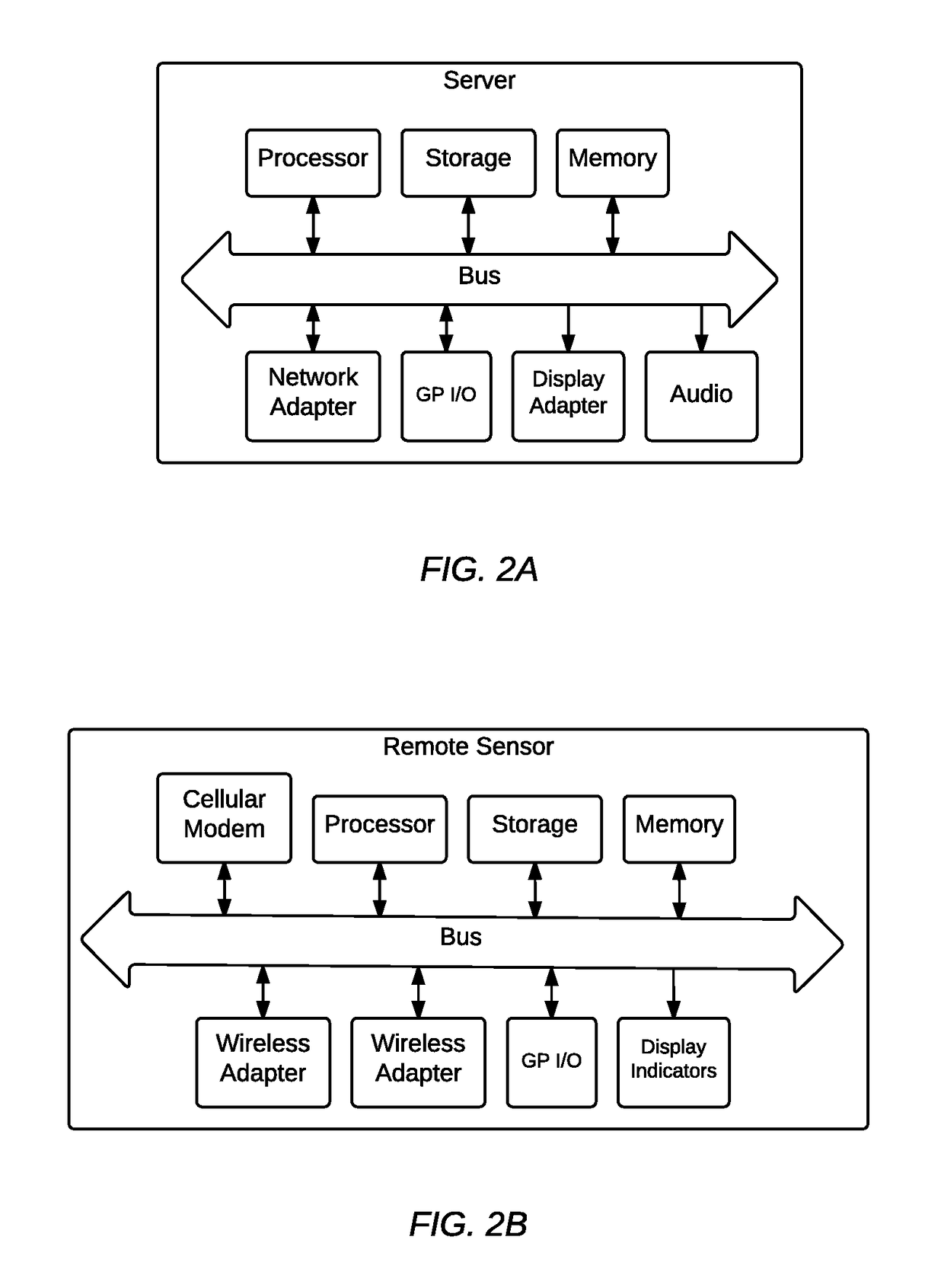
Patents
Literature
322 results about "Threat level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
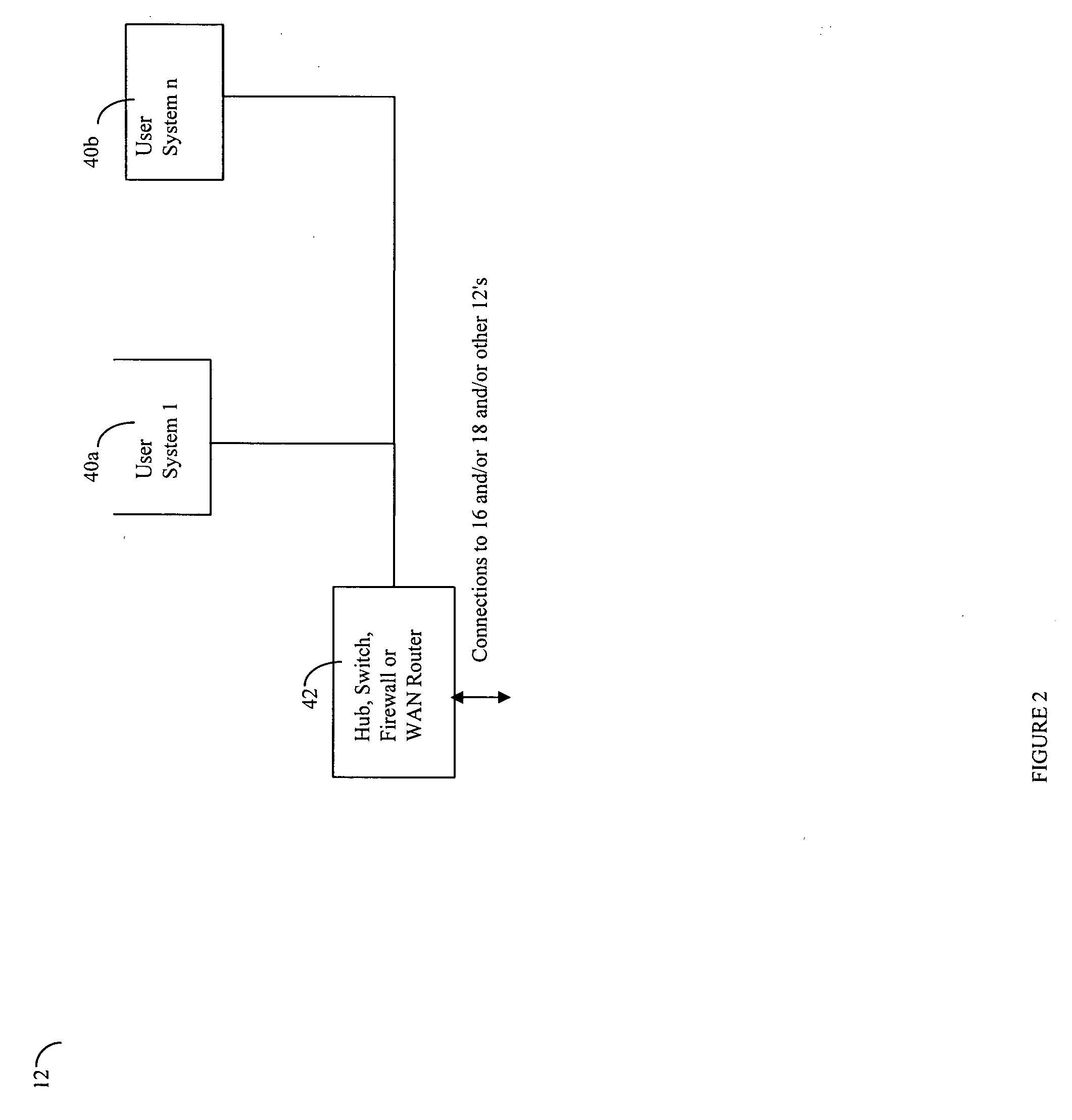
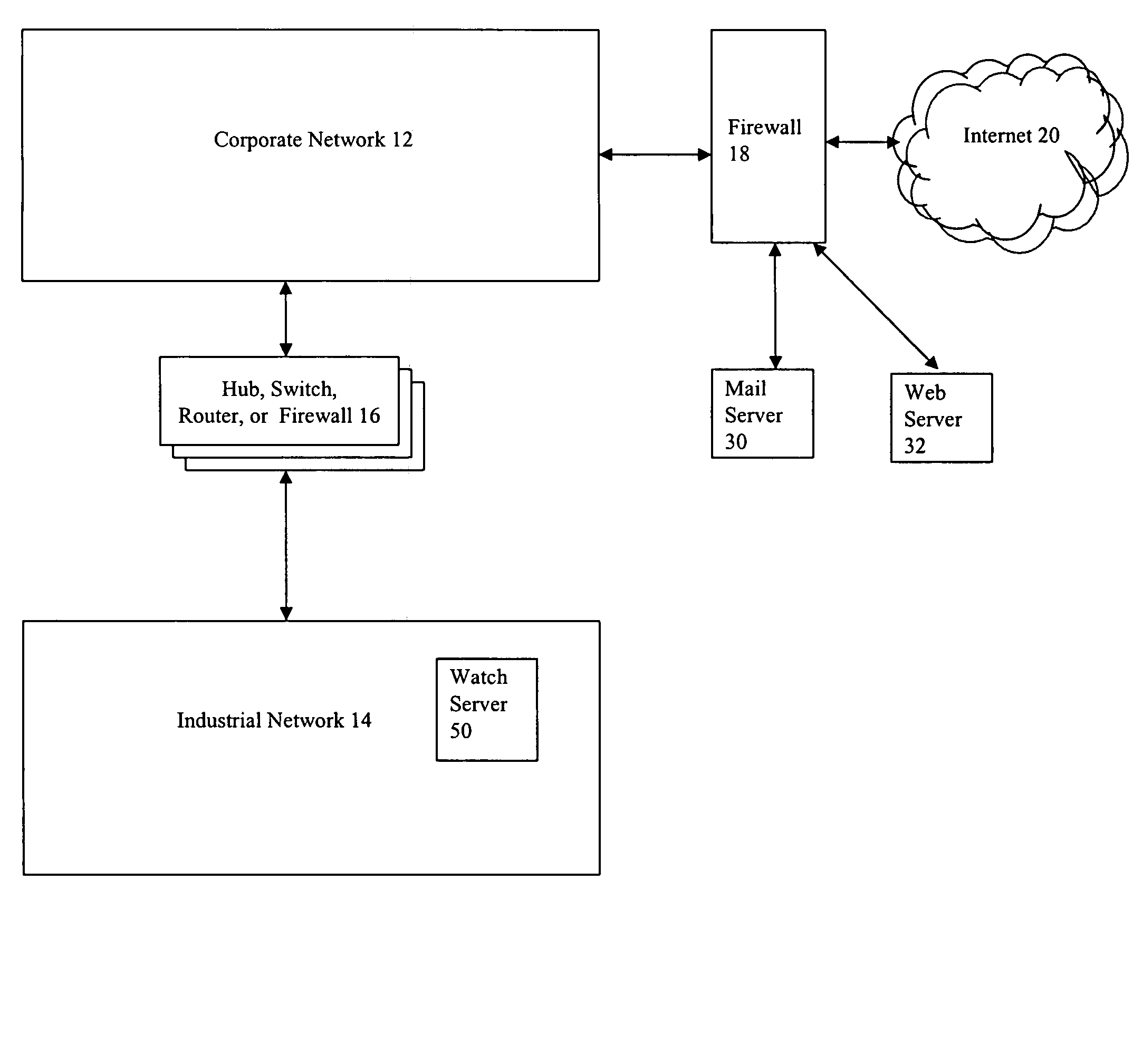
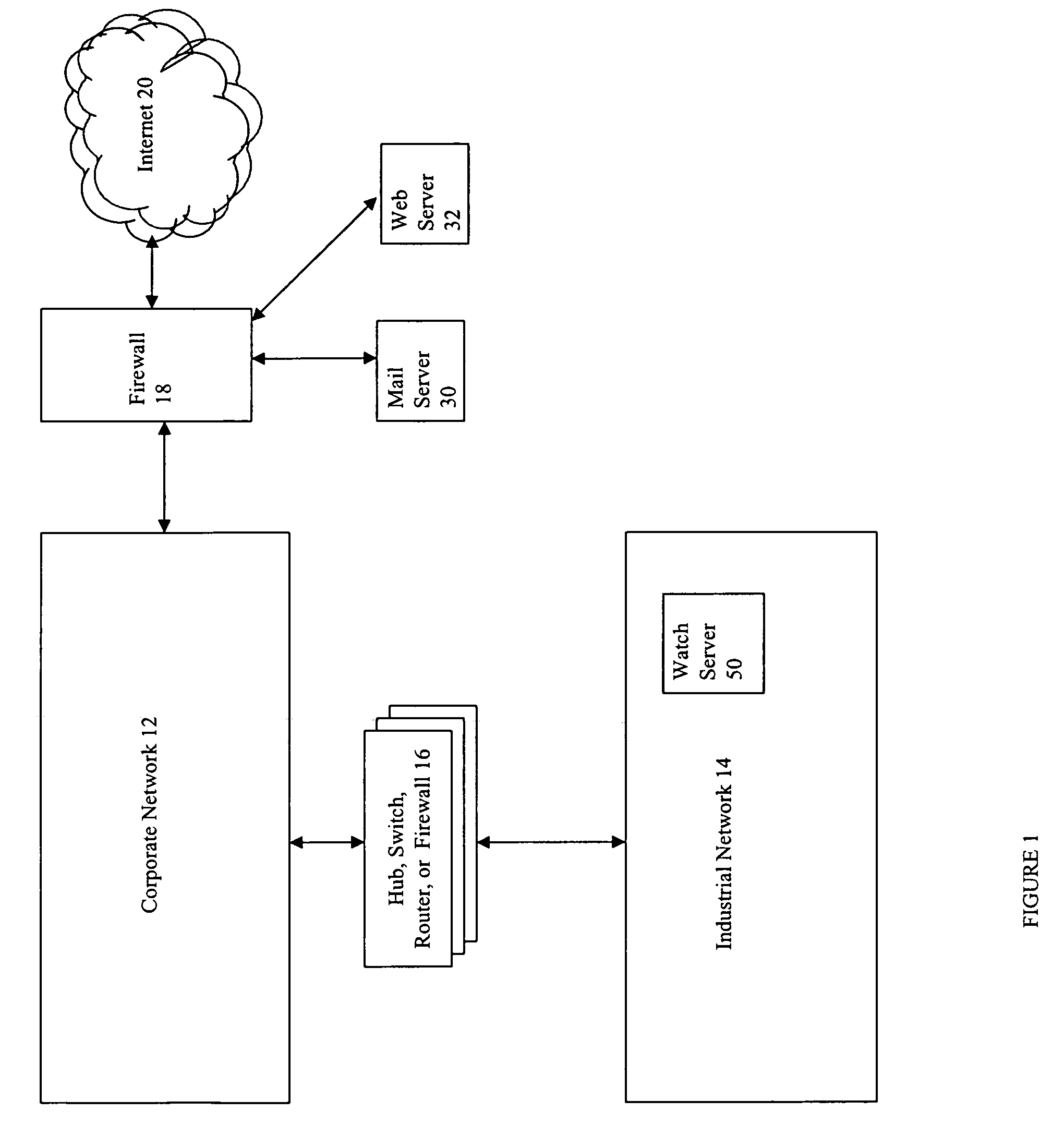
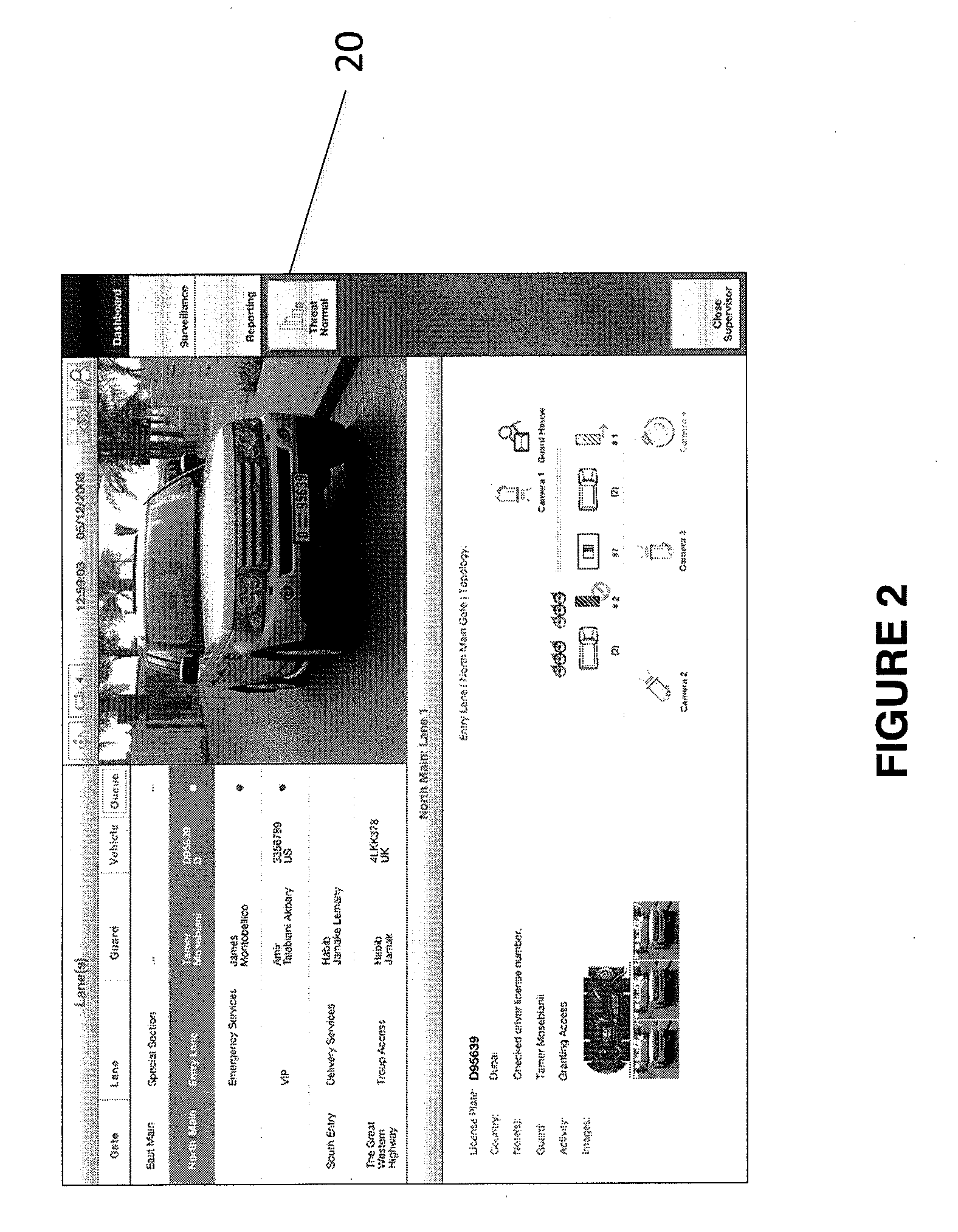
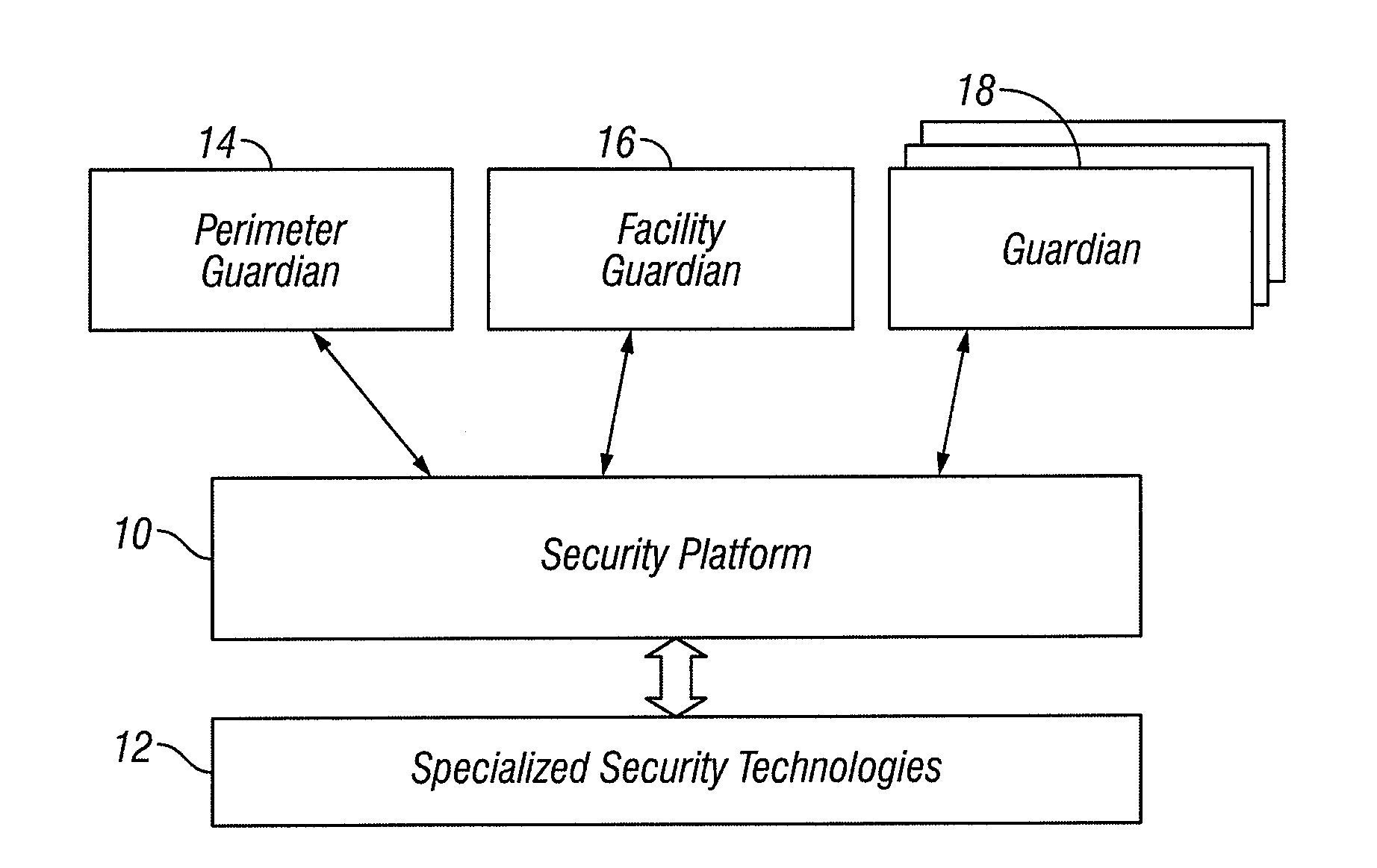
Event monitoring and management
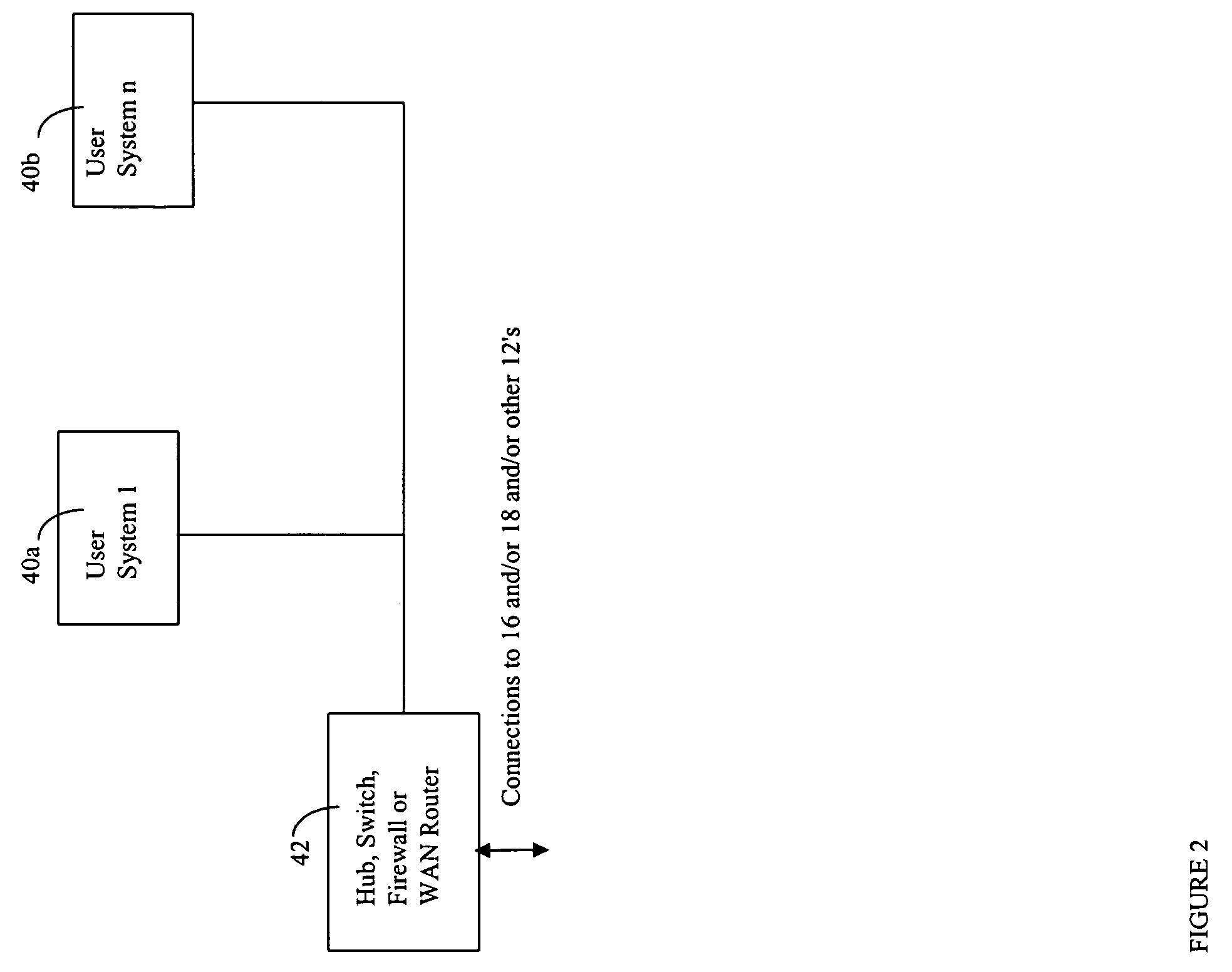
ActiveUS20050015624A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionThermostat
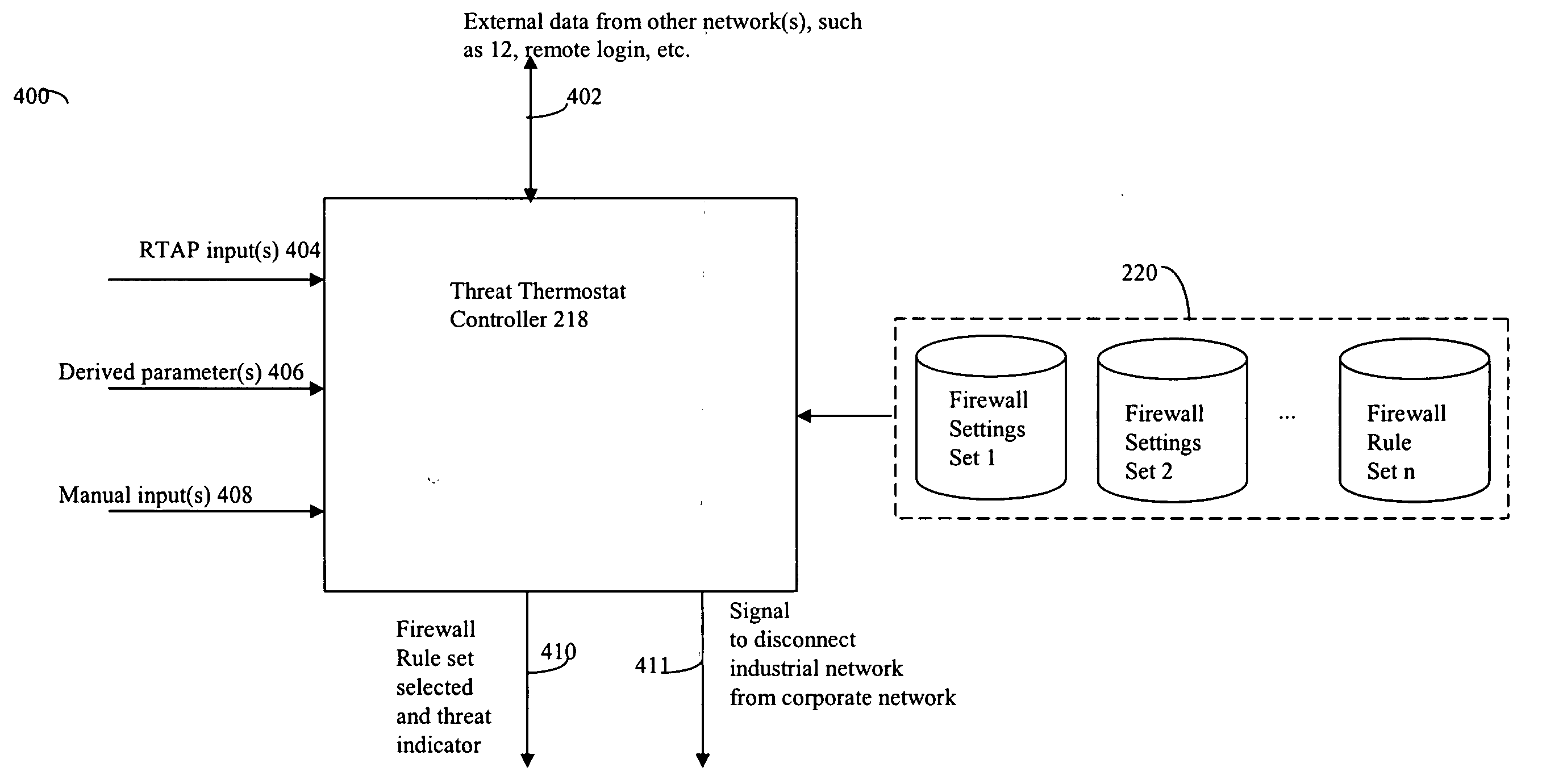
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
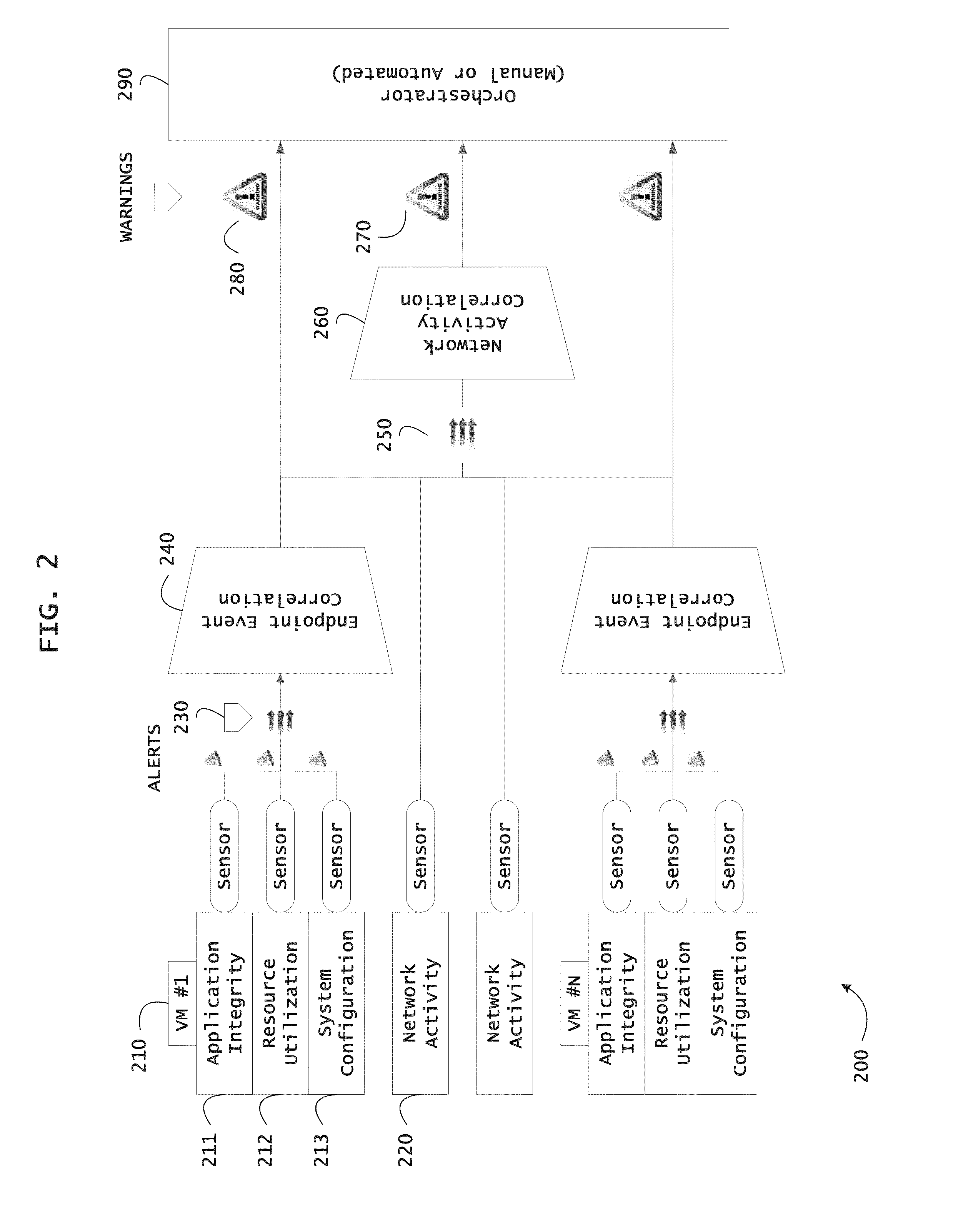
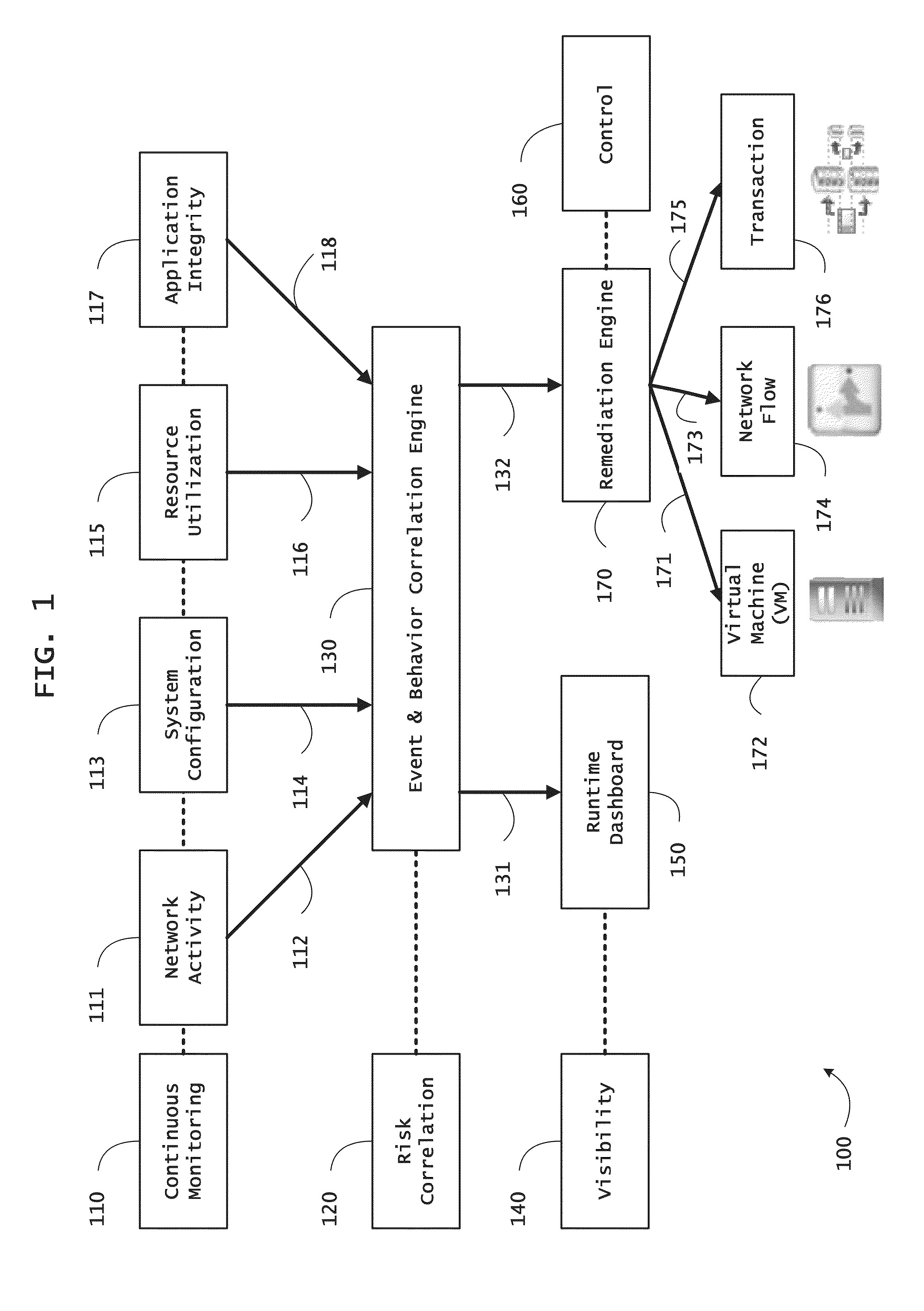
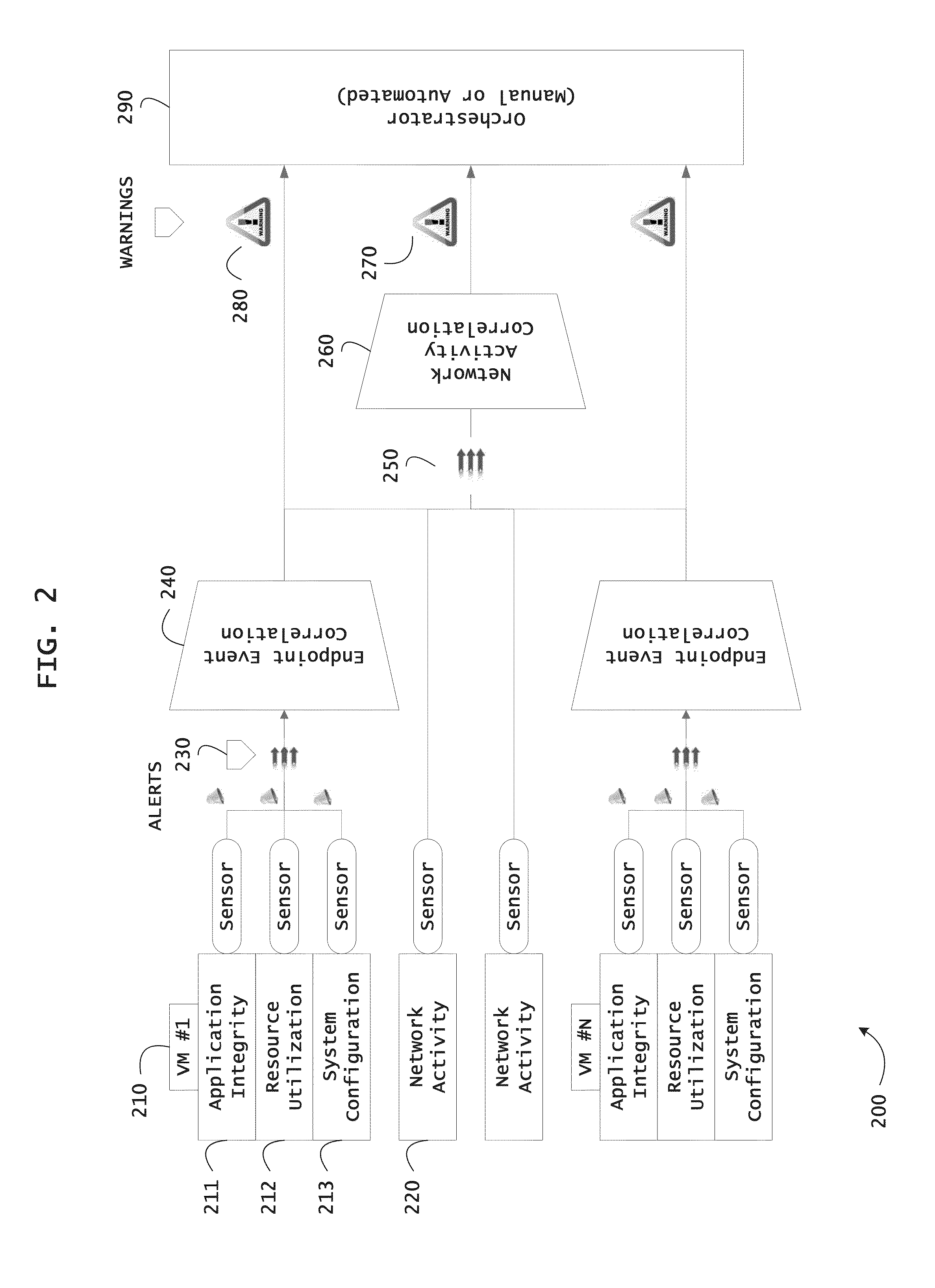
Systems and methods for threat identification and remediation
ActiveUS20130298244A1Memory loss protectionError detection/correctionOrchestrationApplication software
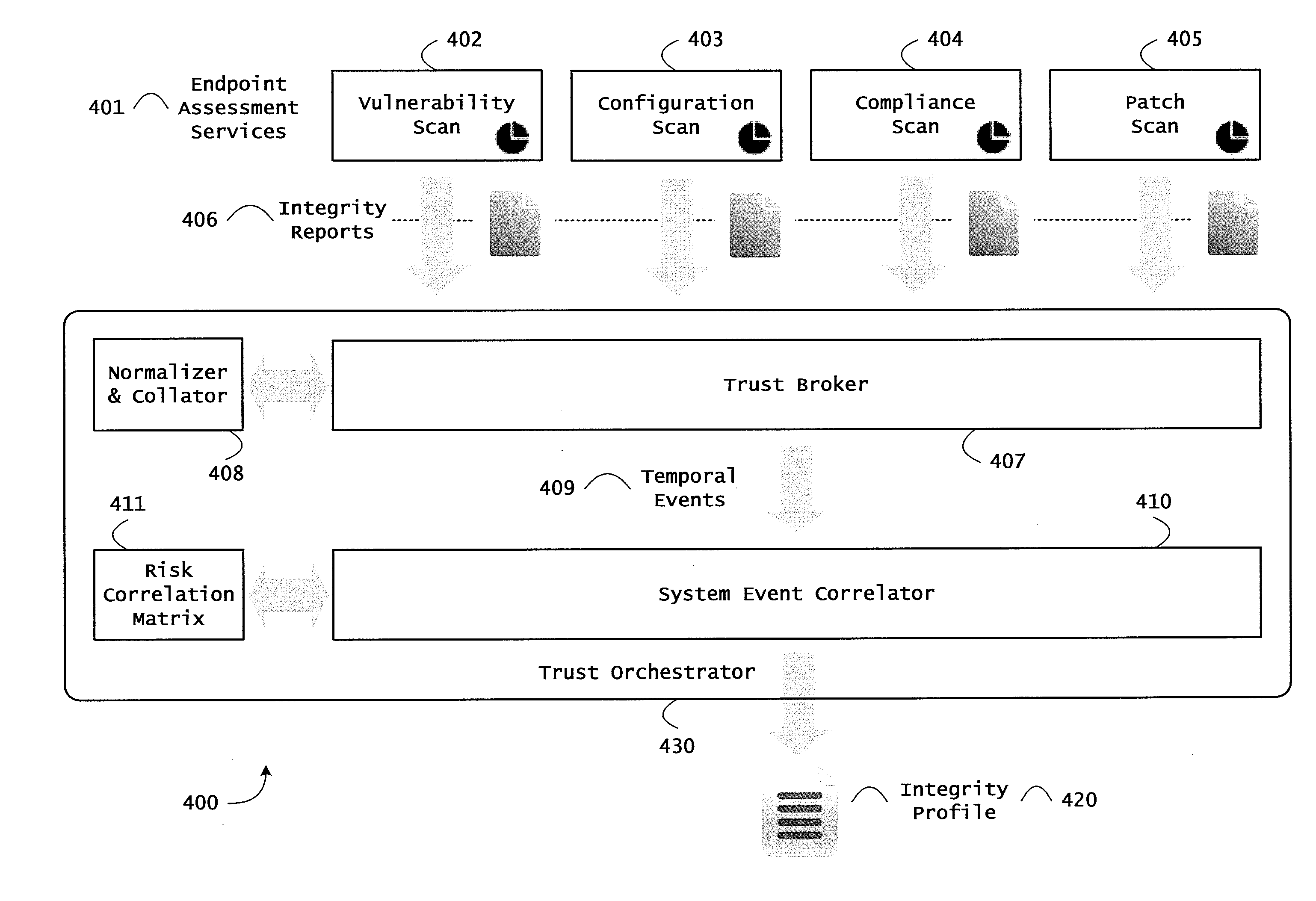
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Systems and methods for threat identification and remediation for computing platforms based upon reconnaissance-based intelligence correlation and network / application monitoring are disclosed. In an embodiment, a method provides runtime operational integrity of a system by receiving: a dynamic context including endpoint events; and network endpoint assessments. The method generates temporal events based on the network endpoint assessments and correlates the endpoint events and temporal events before generating an integrity profile for the system. In another embodiment, flow level remediation is provided to isolate infected or compromised systems from a computing network fabric using a network trust agent, an endpoint trust agent, and a trust orchestrator.
Owner:TAASERA LICENSING LLC
Duration of alerts and scanning of large data stores
InactiveUS20070050777A1Multiprogramming arrangementsNon-redundant fault processingThermostatEmbodied agent
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
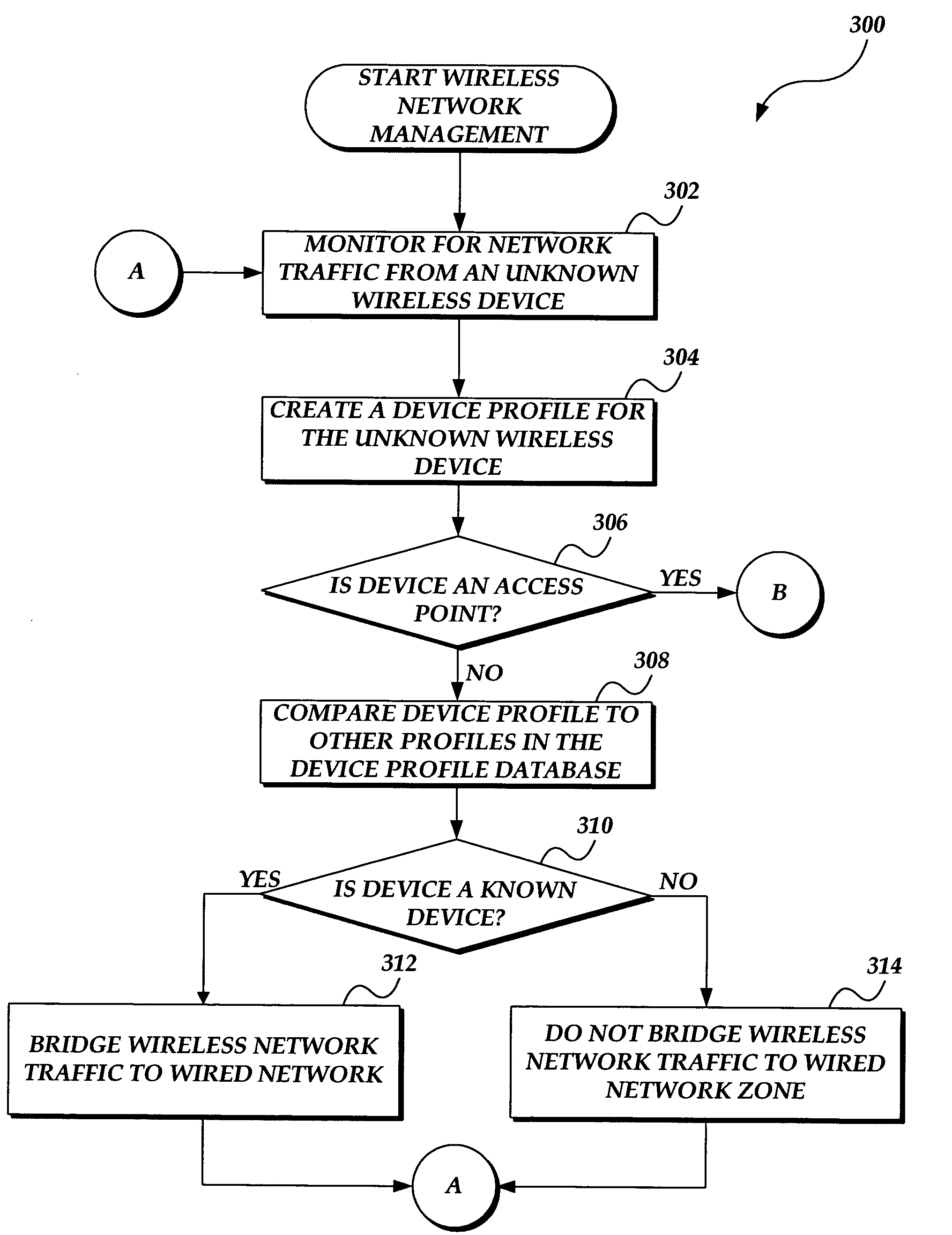
System and method for wireless local area network monitoring and intrusion detection
InactiveUS7340768B2Memory loss protectionDigital data processing detailsThreat levelNotification system
The present invention provides a system and method for providing real-time wireless network monitoring and intrusion detection. The present invention profiles wireless devices and maintains a database of known / authorized wireless device profiles. Wireless devices are analyzed to determine the threat level they pose to the network, and if the threat level exceeds a predetermined threshold, the invention refuses to bridge the network traffic from the wireless devices to the wired network. The present invention provides reporting of the wireless network activity, the known and unknown wireless devices, and the threat levels posed by the wireless devices. If an unknown wireless device is determined to be, or may be, a wireless access point, an alert is generated, such as notifying a system administrator to take appropriate action.
Owner:WIMETRICS CORP
Adjusting security level of mobile device based on presence or absence of other mobile devices nearby
ActiveUS8095112B2Unauthorised/fraudulent call preventionDigital data processing detailsSecure stateGeolocation
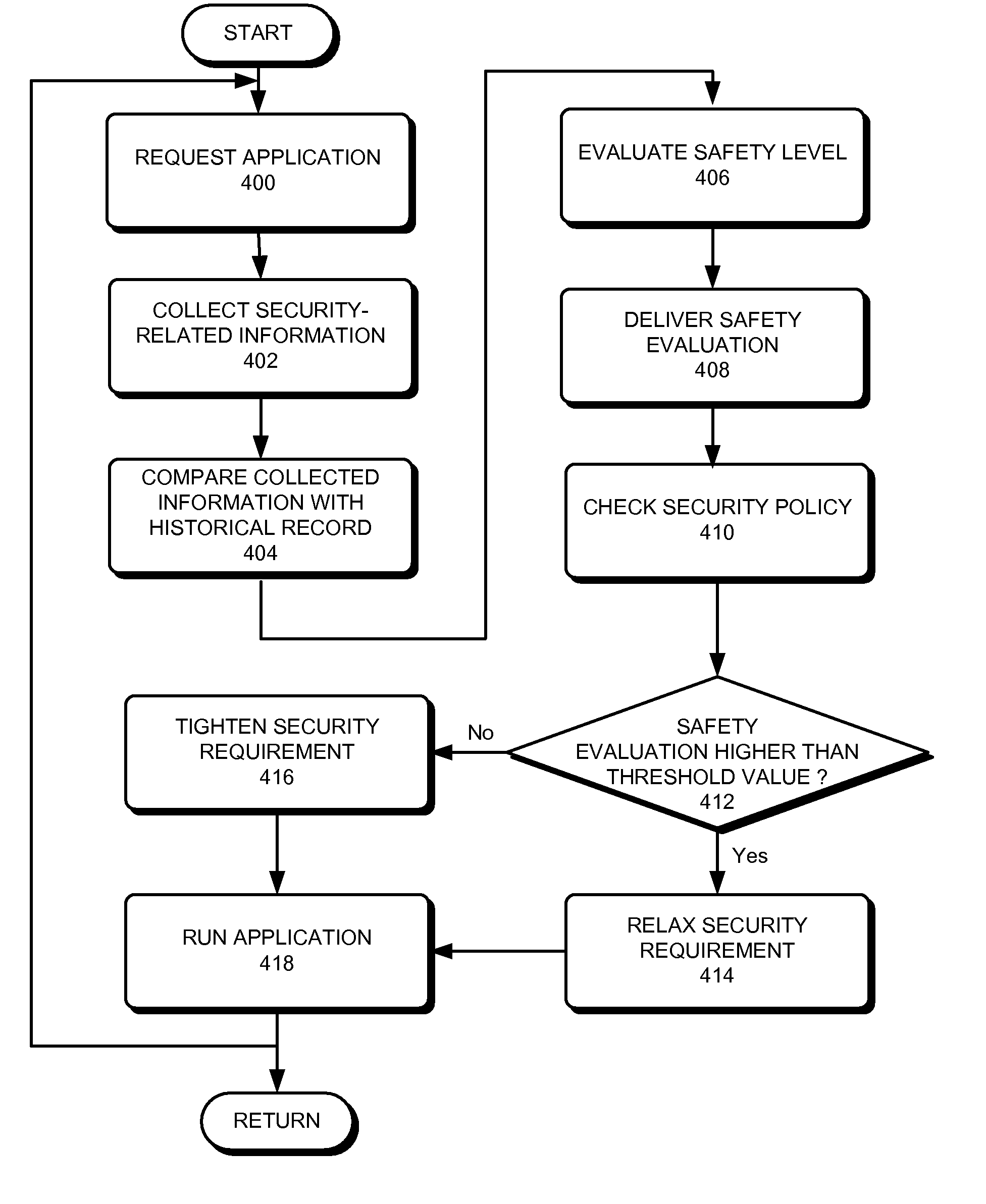
One embodiment of the present invention provides a method for adjusting security status on a mobile device, the method comprising: collecting security-related contextual information which includes information of nearby mobile devices and / or the geographic location of the intelligent mobile device; evaluating a threat level based on the collected security-related contextual information; invoking a security policy; and adjusting the security status of the mobile device based on the threat level and the security policy.
Owner:XEROX CORP
Systems and methods for providing mobile security based on dynamic attestation
ActiveUS20130298242A1Memory loss protectionError detection/correctionMobile securityApplication software
Instrumented networks, machines and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects (including mobile devices) and applications on the instrumented target platform. Methods and systems are disclosed for dynamic attestation of mobile device integrity based upon subject reputation scores. In an embodiment, a method scores trustworthiness of a mobile device based on reputation scores for users associated with the device and / or a device reputation score. The method generates runtime integrity alerts regarding execution anomalies for applications executing on the device, calculates risks based on a ruleset, and determines a calculus of risk for the device. The method sends endpoint events comprising data and content of the integrity warnings to a trust orchestrator, which generates an integrity profile based on the endpoint events.
Owner:TAASERA LICENSING LLC
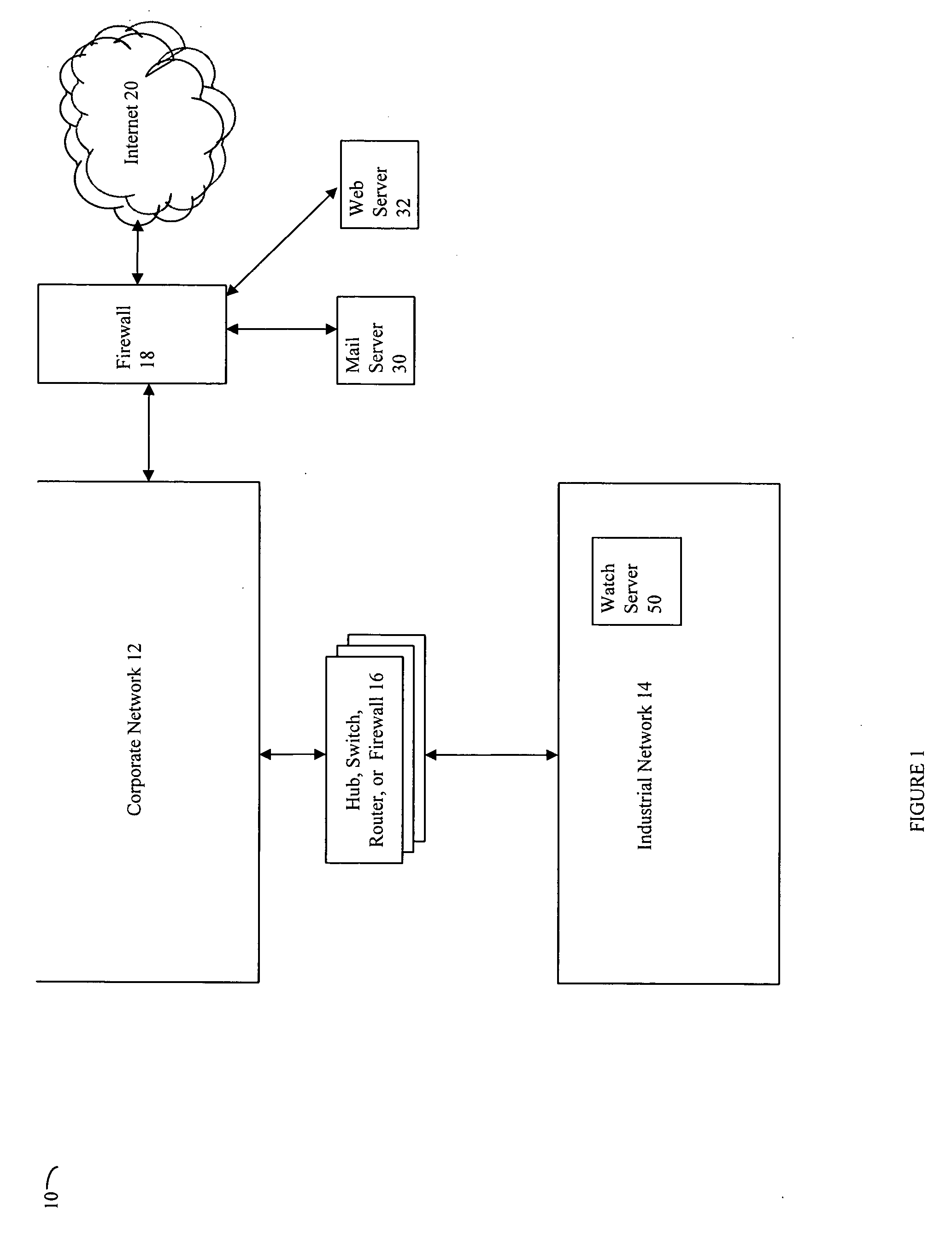
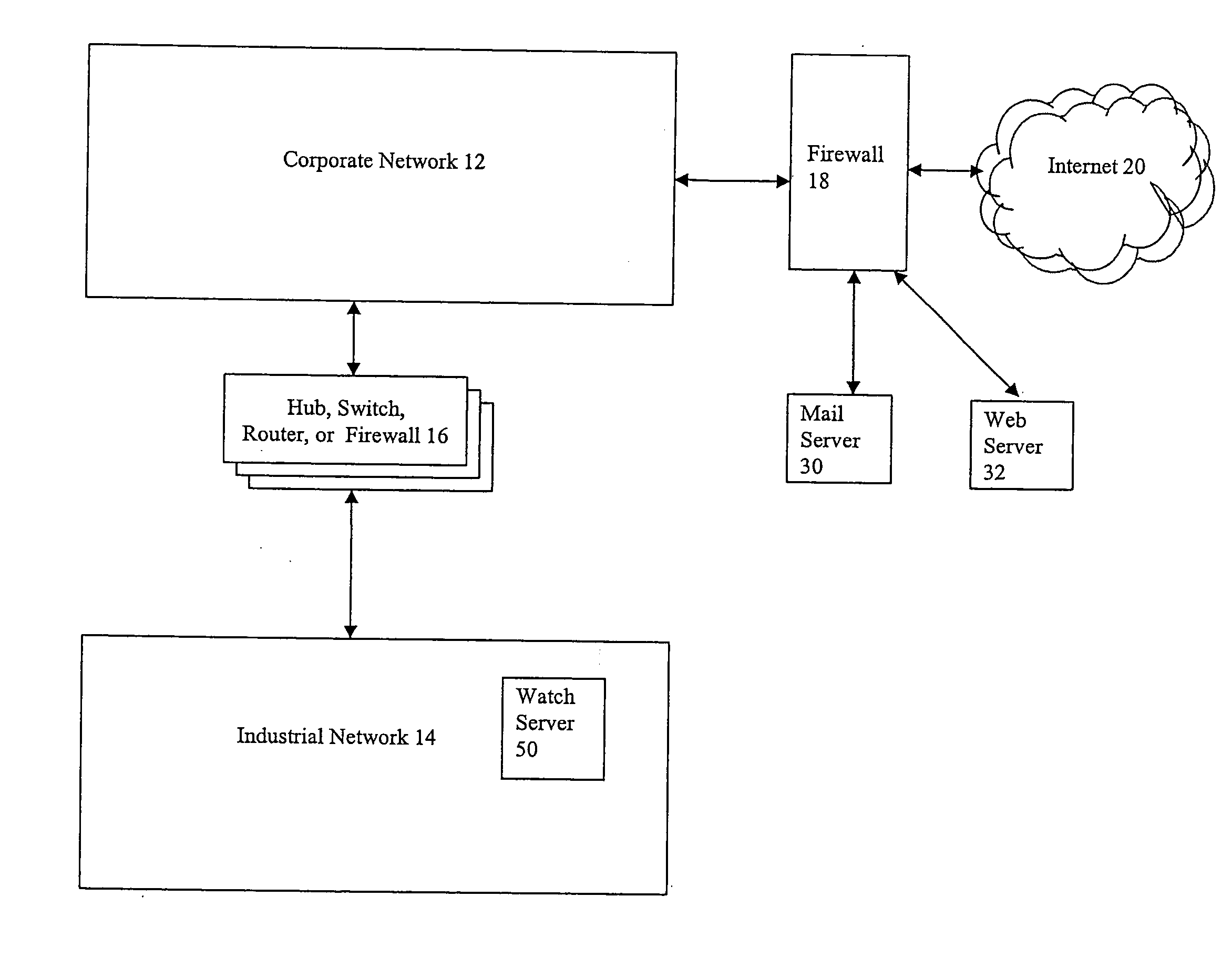
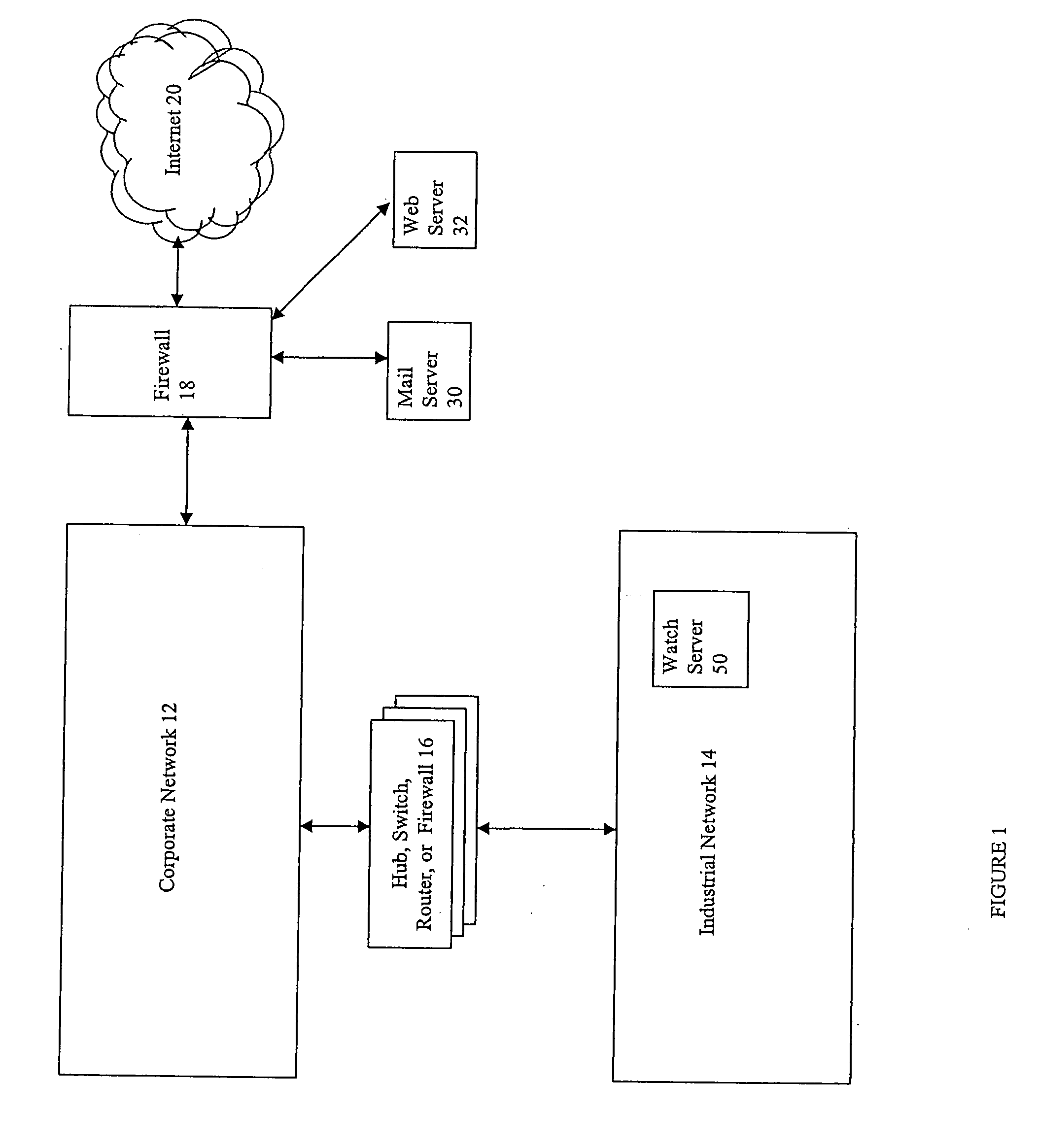
Method and computer program product for monitoring an industrial network
ActiveUS7246156B2Digital data processing detailsMultiple digital computer combinationsEmbodied agentThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
Adjusting security level of mobile device based on presence or absence of other mobile devices nearby
ActiveUS20100048167A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure stateGeolocation
One embodiment of the present invention provides a method for adjusting security status on a mobile device, the method comprising: collecting security-related contextual information which includes information of nearby mobile devices and / or the geographic location of the intelligent mobile device; evaluating a threat level based on the collected security-related contextual information; invoking a security policy; and adjusting the security status of the mobile device based on the threat level and the security policy.
Owner:XEROX CORP
Using location capabilities of a mobile device to permit users to avoid potentially harmful interactions
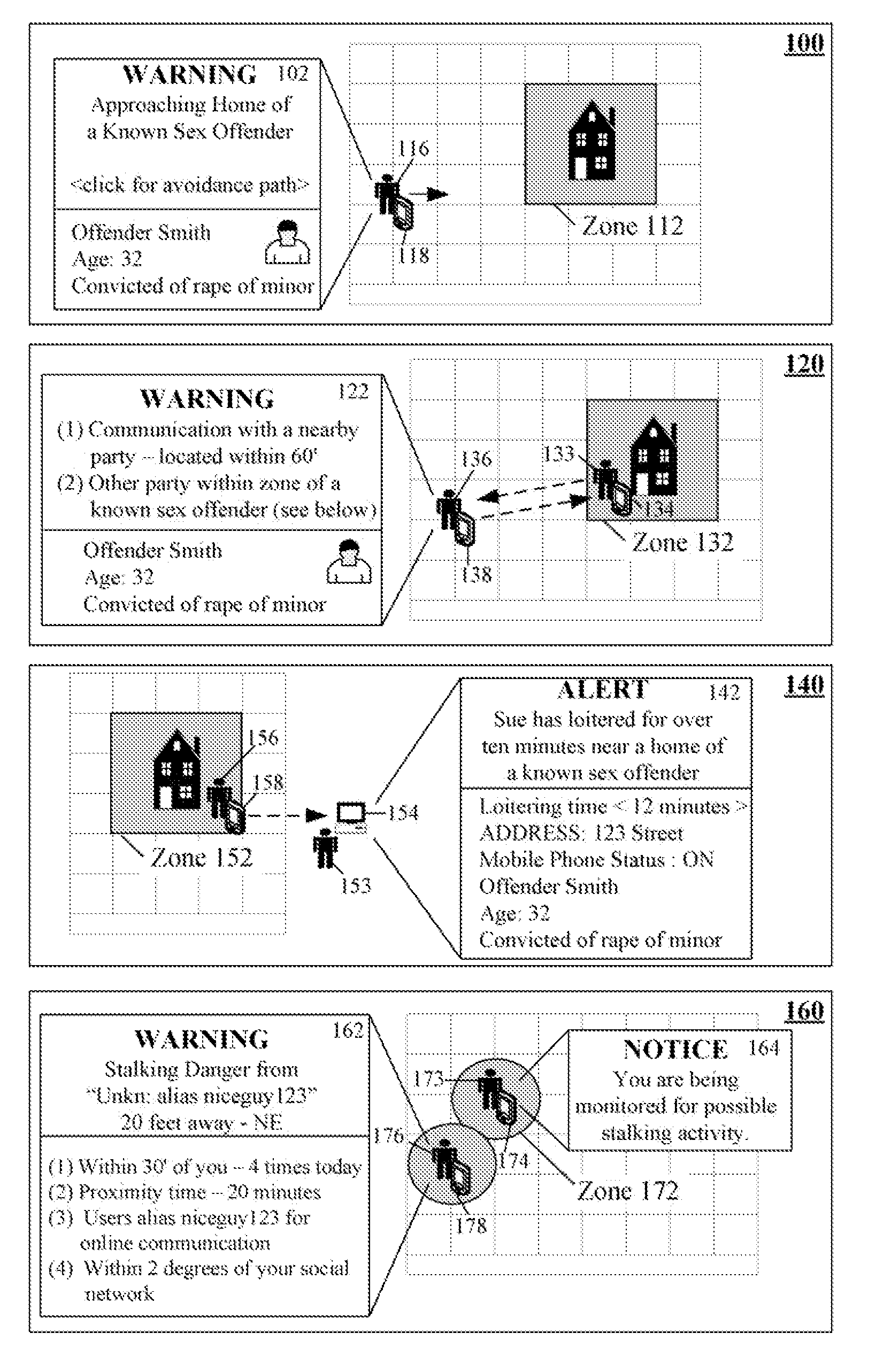
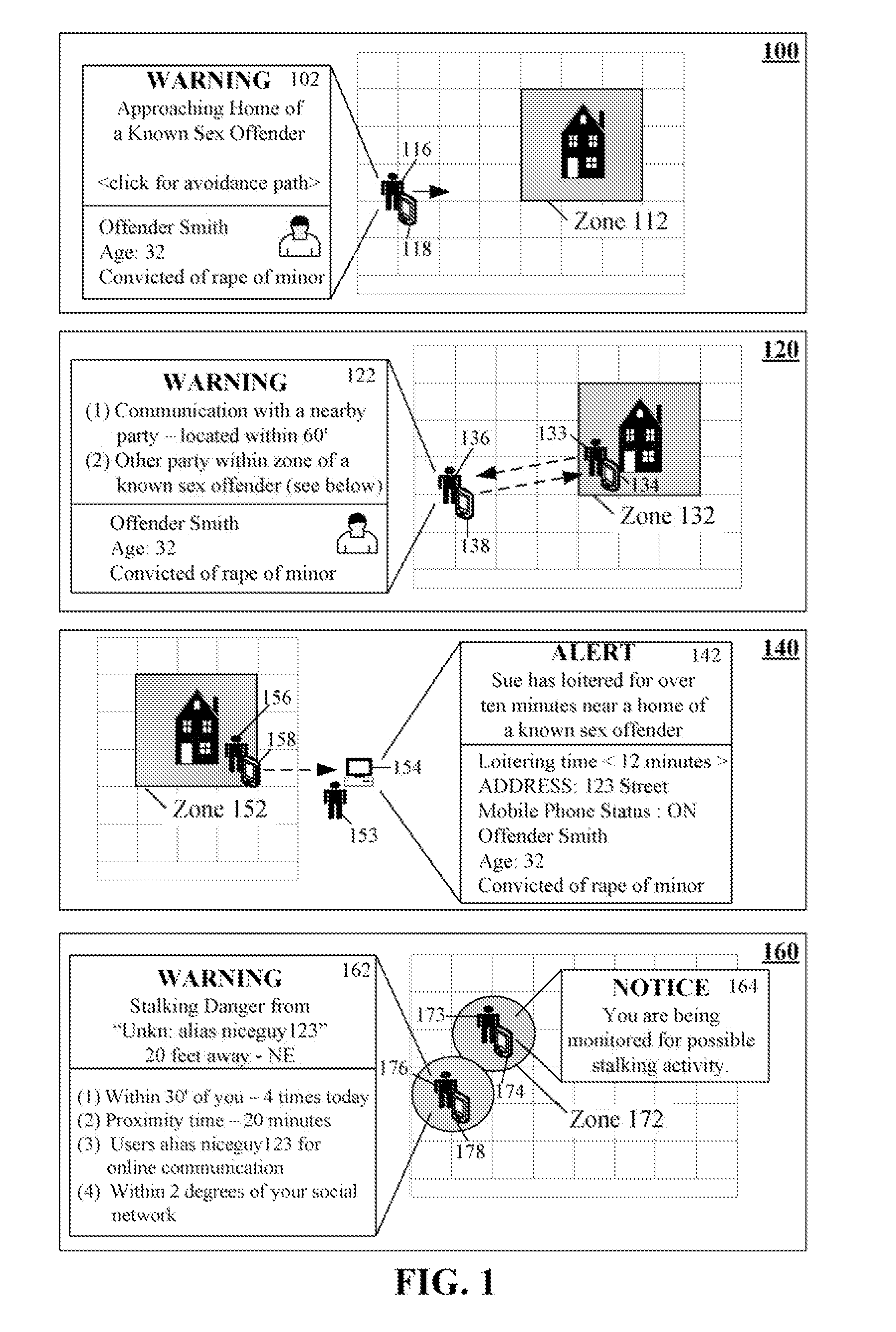
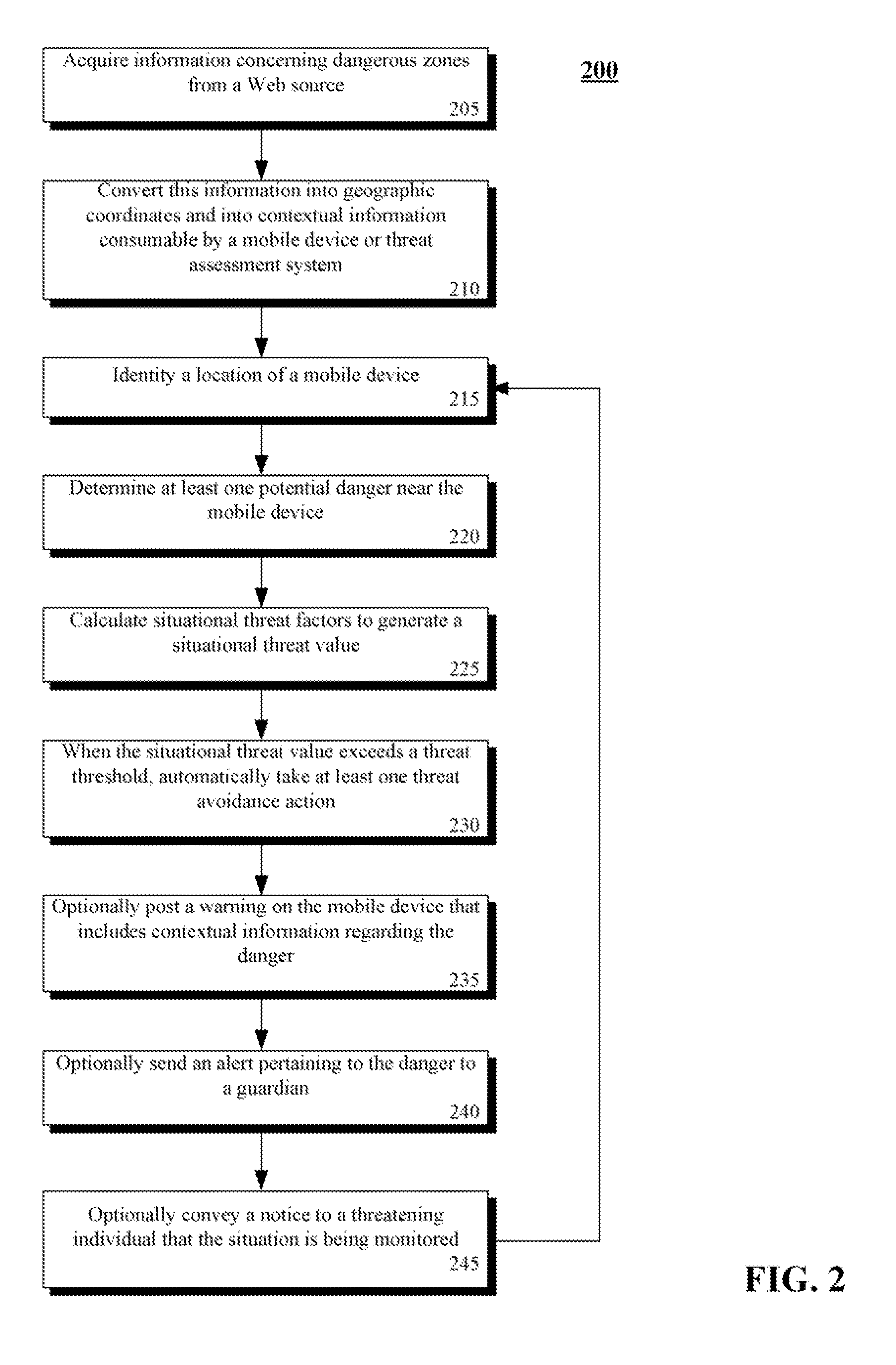
InactiveUS20080094230A1Enhanced Situational AwarenessAvoid harmAlarmsElectric signalling detailsProximateSimulation
The present invention automatically increases situational awareness relating to potential sexual predators, criminals, and / or stalkers located near a mobile device user. A location of the mobile device can be determined by device location electronics, such as a Global Positioning System (GPS). The location can be compared against at least one zone believed to be associated with a sexual predator, a criminal, and / or a stalker. Zones can be static or dynamic. A threat level associated with a zone can be computed from multiple factors, which are compared against one or more thresholds. When the threat level exceeds a thresholds, an associated threat avoidance action can be automatically initiated. One threat avoidance action is to present a warning upon a user's mobile device along with contextual information about a proximate danger.
Owner:MOTOROLA INC
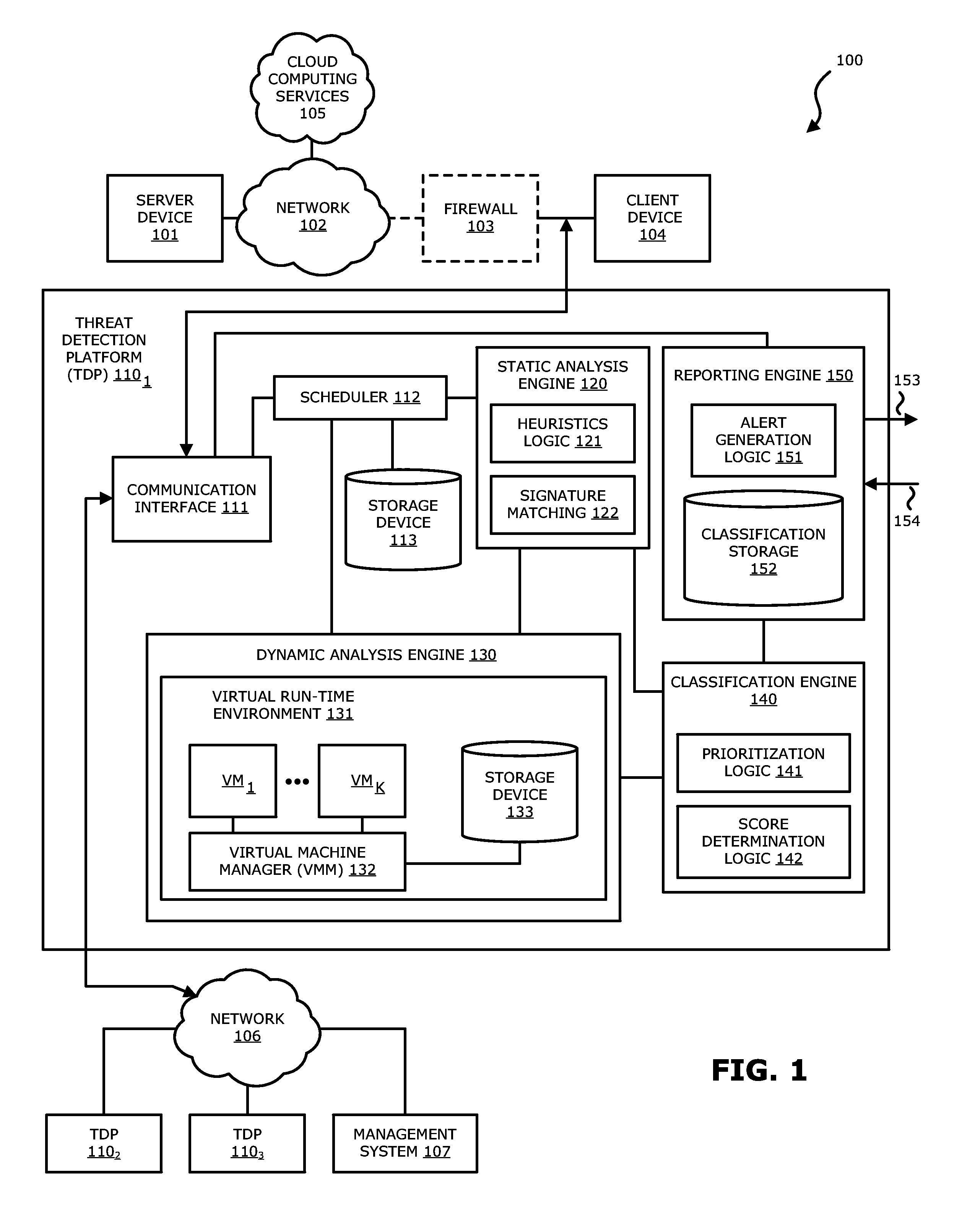
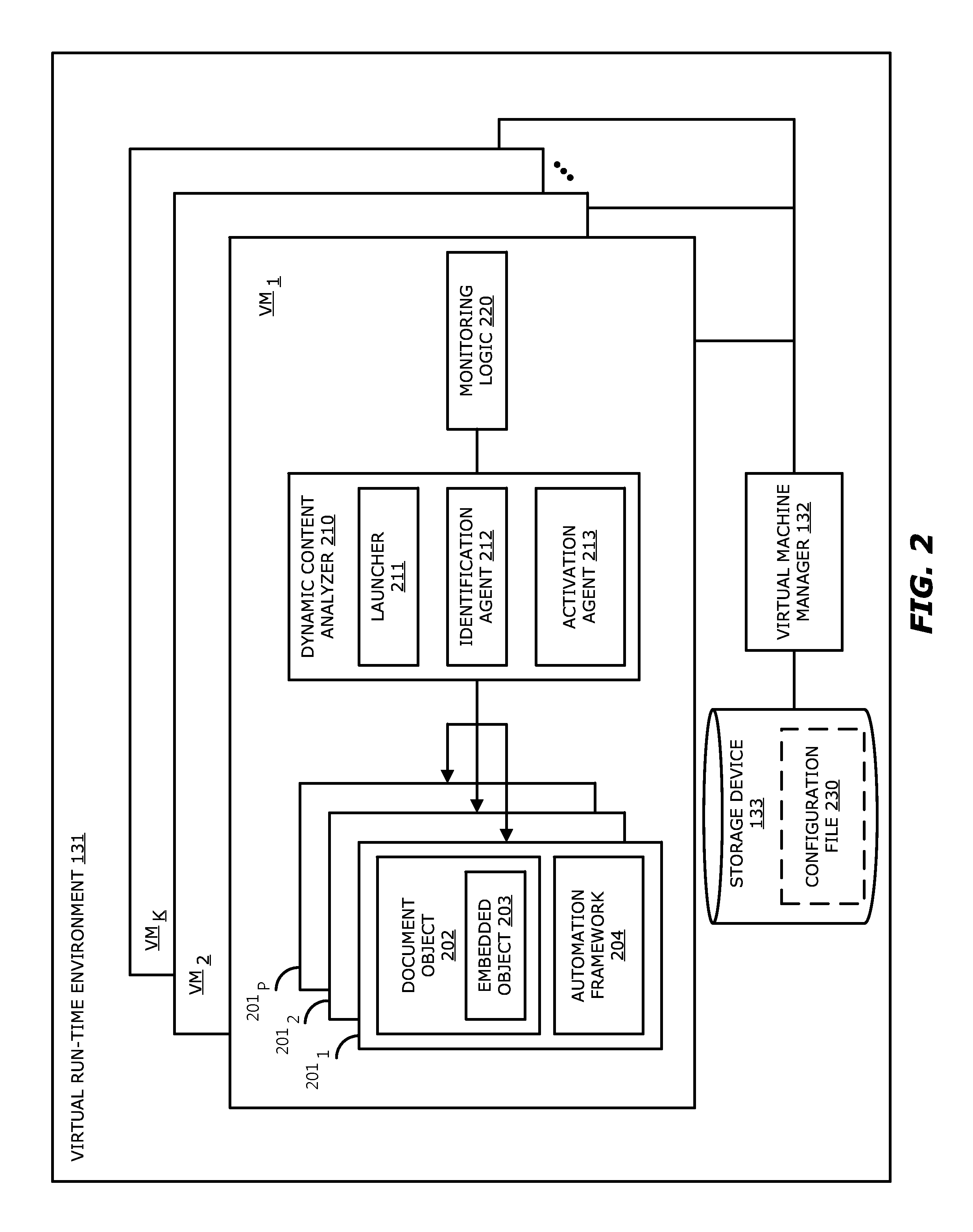
Dynamic content activation for automated analysis of embedded objects
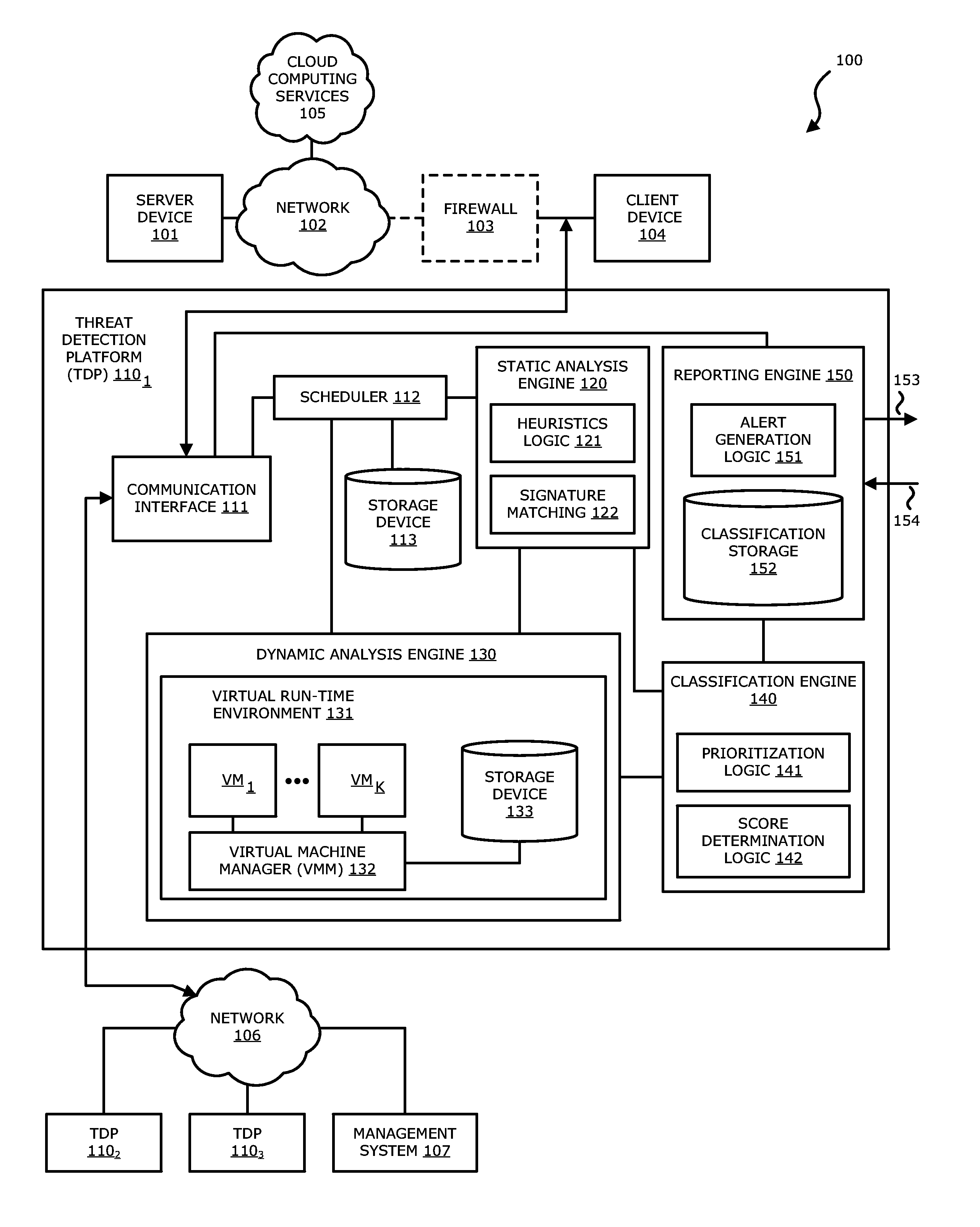
According to one embodiment, a threat detection platform is integrated with at least one virtual machine that automatically performs a dynamic analysis of a received document object and monitors the processing during the dynamic analysis. The dynamic analysis includes a detection of embedded objects and may automatically process the embedded objects, while maintaining a context of the embedding, within the virtual machine processing the document object. The virtual machine may monitor the processing of both the document object and the embedded object. The results of the processing may be analyzed to determine whether the document object includes malware and / or a threat level of the document object.
Owner:FIREEYE SECURITY HLDG US LLC
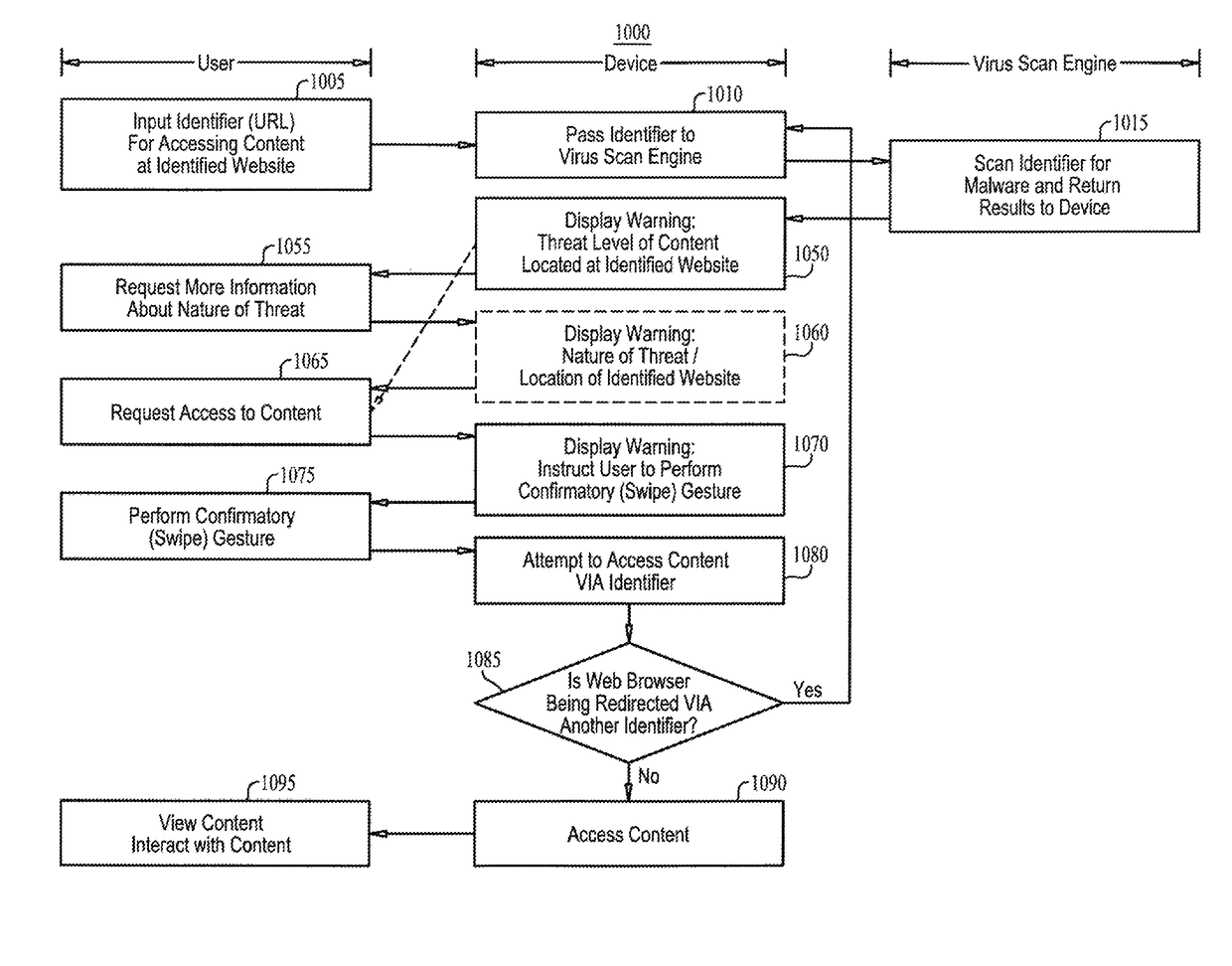
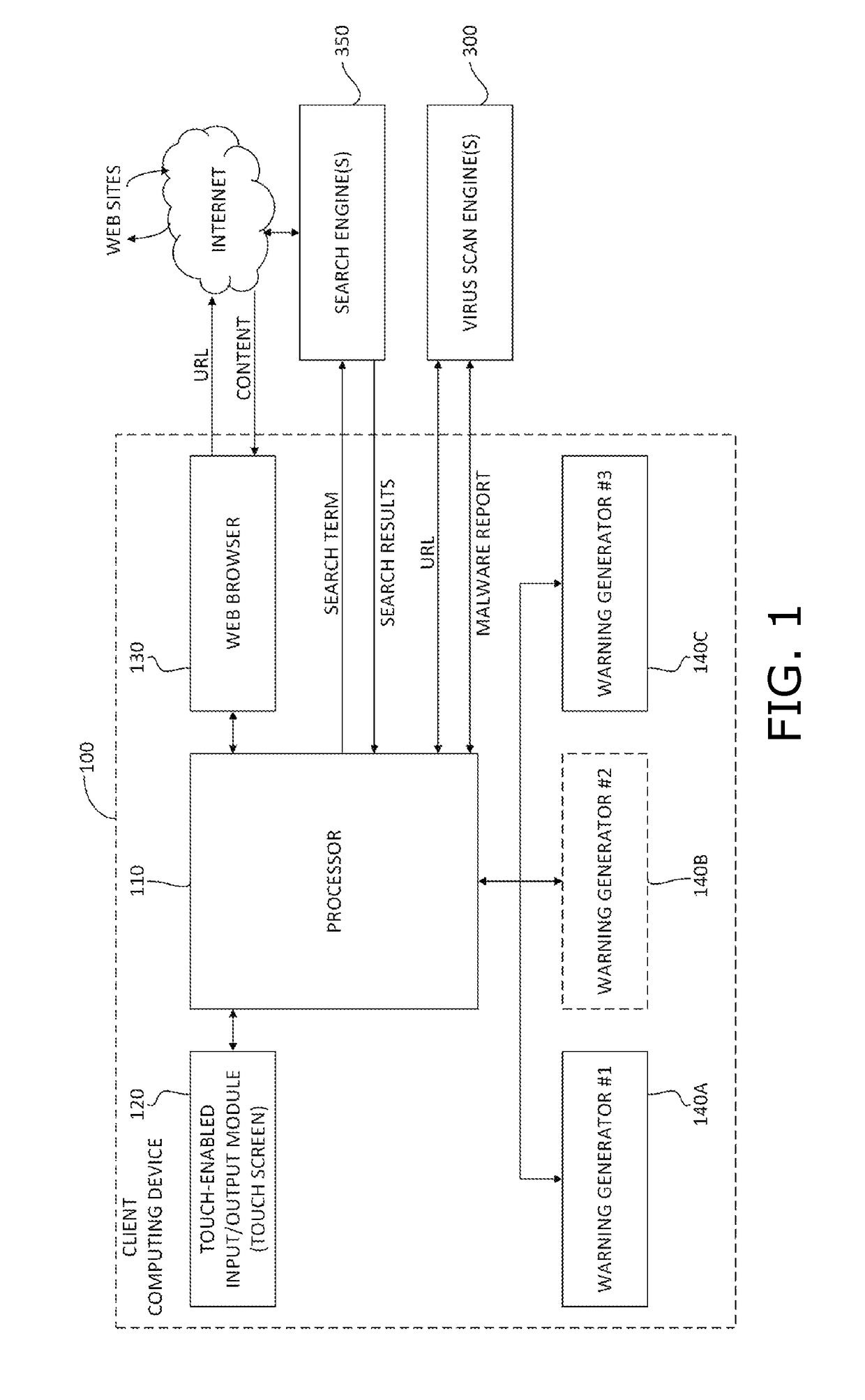
Malware warning
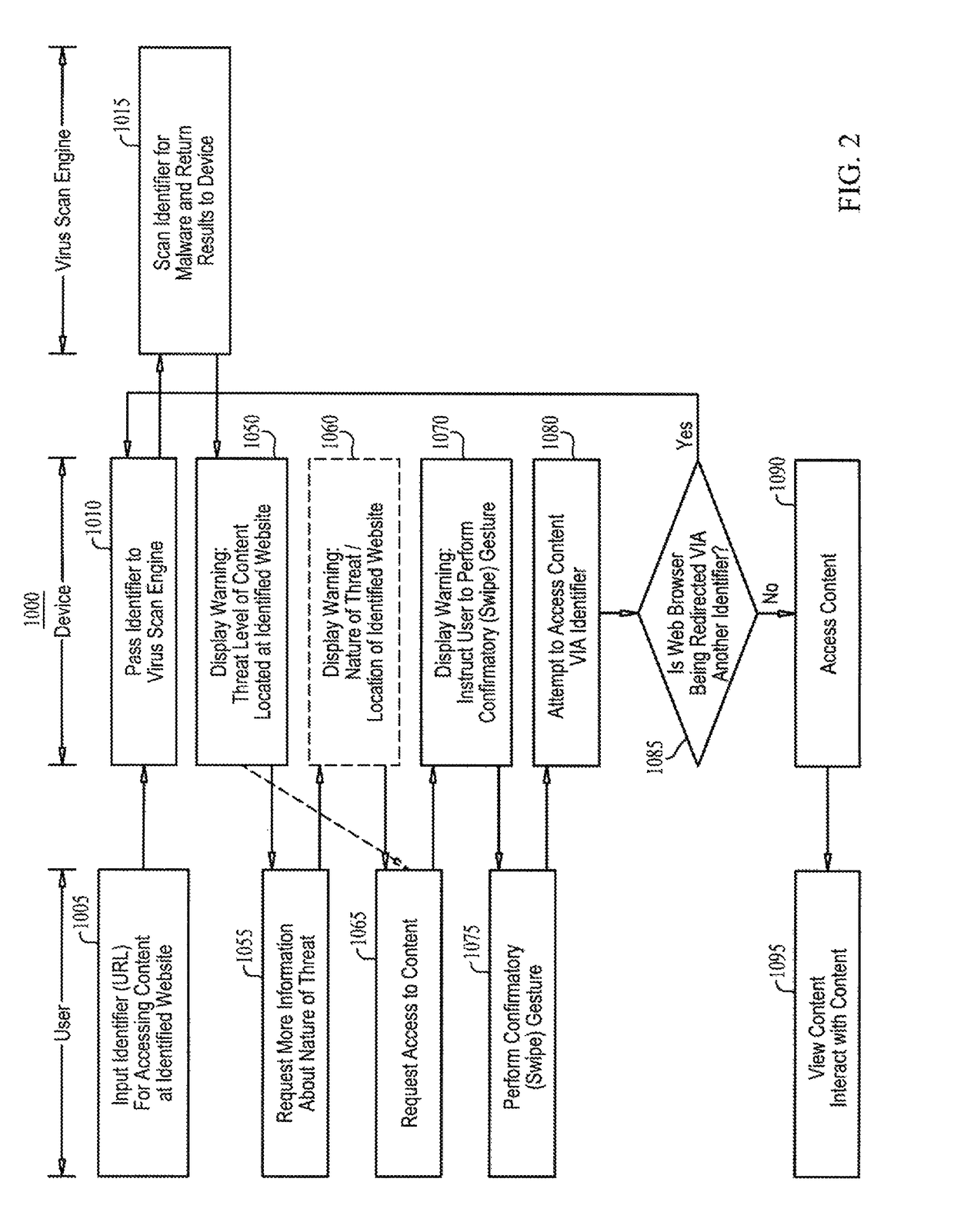
A malware warning system, including a client sending requests to and receiving replies from a server, and a server, including a first warning generator sending to the client a warning including a threat level of content located at a web site, in response to receiving from the client a URL for accessing content at the web site, a second warning generator sending to the client a warning including information about at least one of the nature of the threat of the content located at the web site and a location of the web site, in response to receiving from the client a request for more information about the nature of the threat, and a third warning generator, sending to the client a warning including an instruction to perform a swipe gesture to confirm a request to access the URL, in response to receiving that request from the client.
Owner:FINJAN MOBILE LLC
Volume sensor: data fusion-based, multi-sensor system for advanced damage control
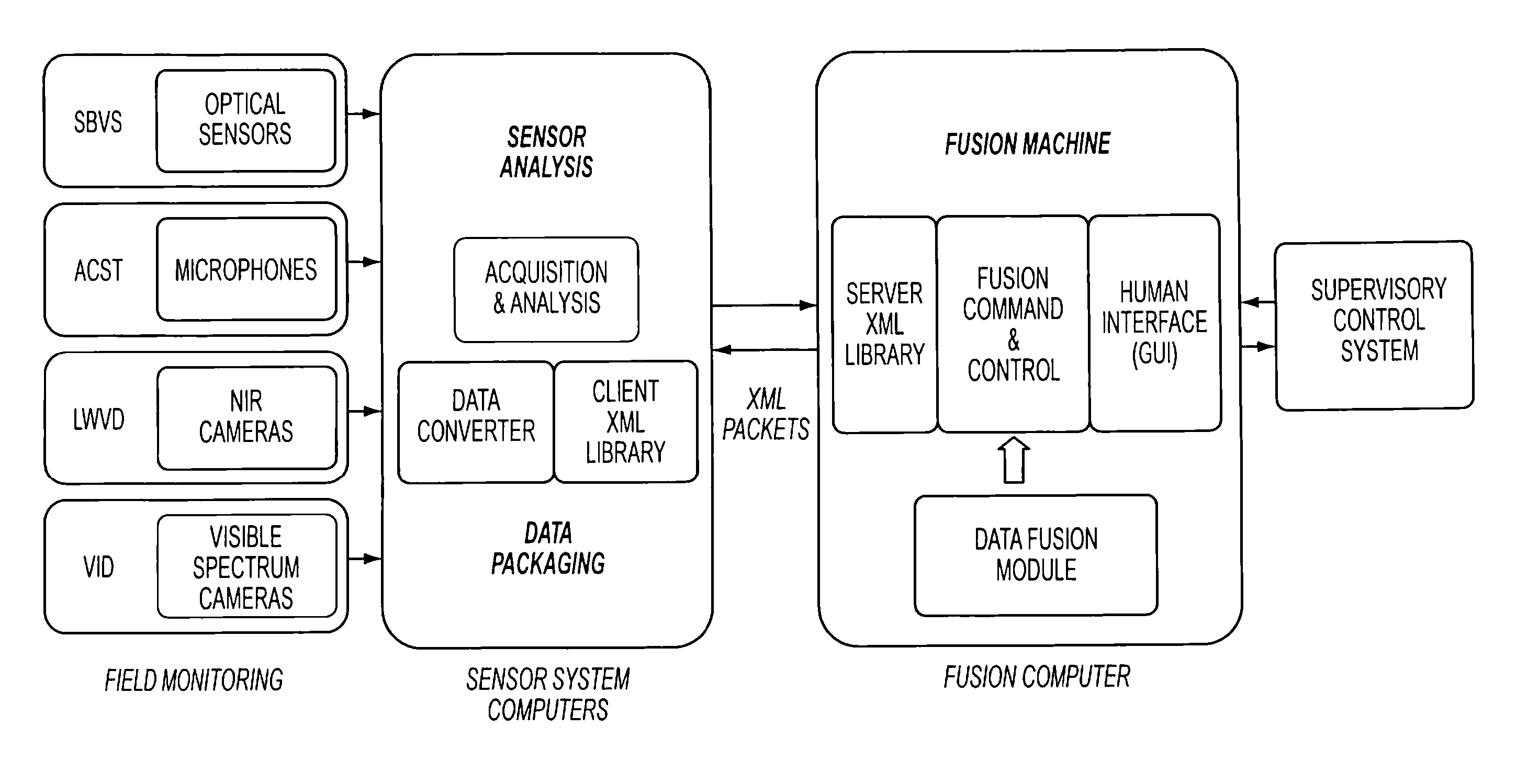
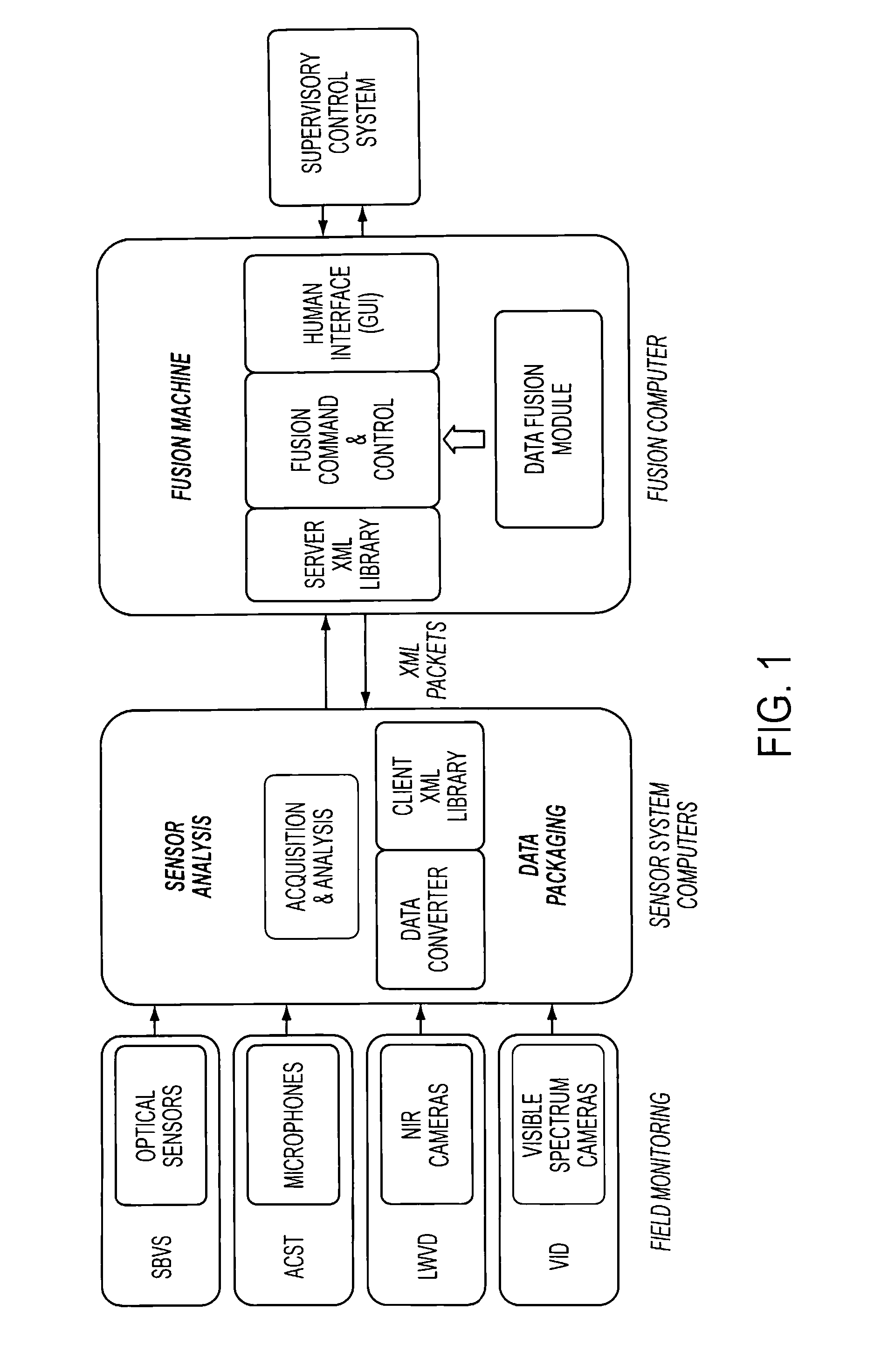
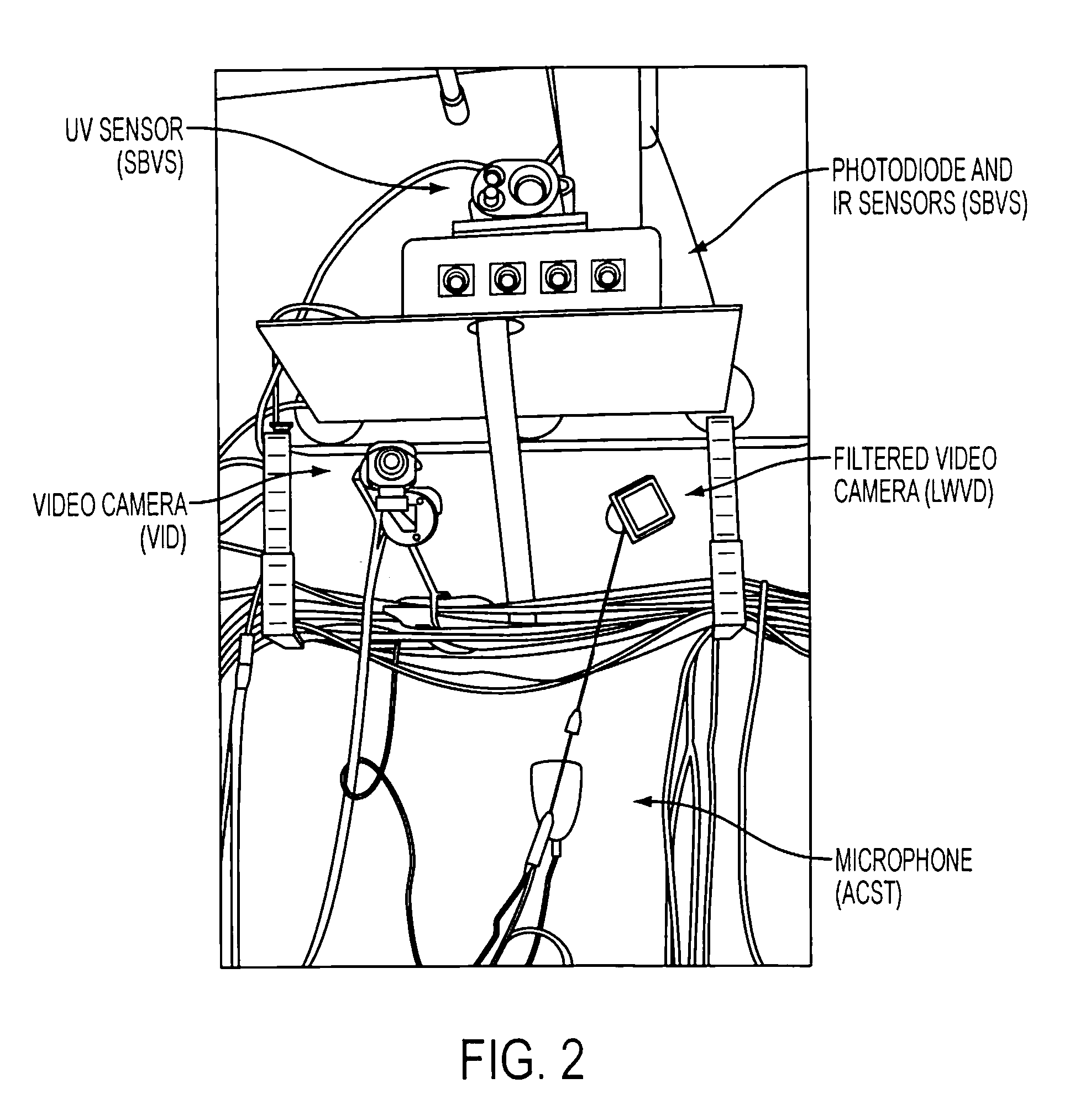
Provided a system and method for detecting an event while discriminating against false alarms in a monitored space using at least one sensor suite to acquire signals, transmitting the signals to a sensor system device where the signal is processed into data packets, transmitting the data packets to a data fusion device, where the data packets are aggregated and algorithmic data fusion analysis is performed to generate threat level information. The threat level information is distributed to a supervisory control system where an alarm level can be generated when predetermined criteria are met to indicate the occurrence of an event in the monitored space.
Owner:UNITED STATES OF AMERICA
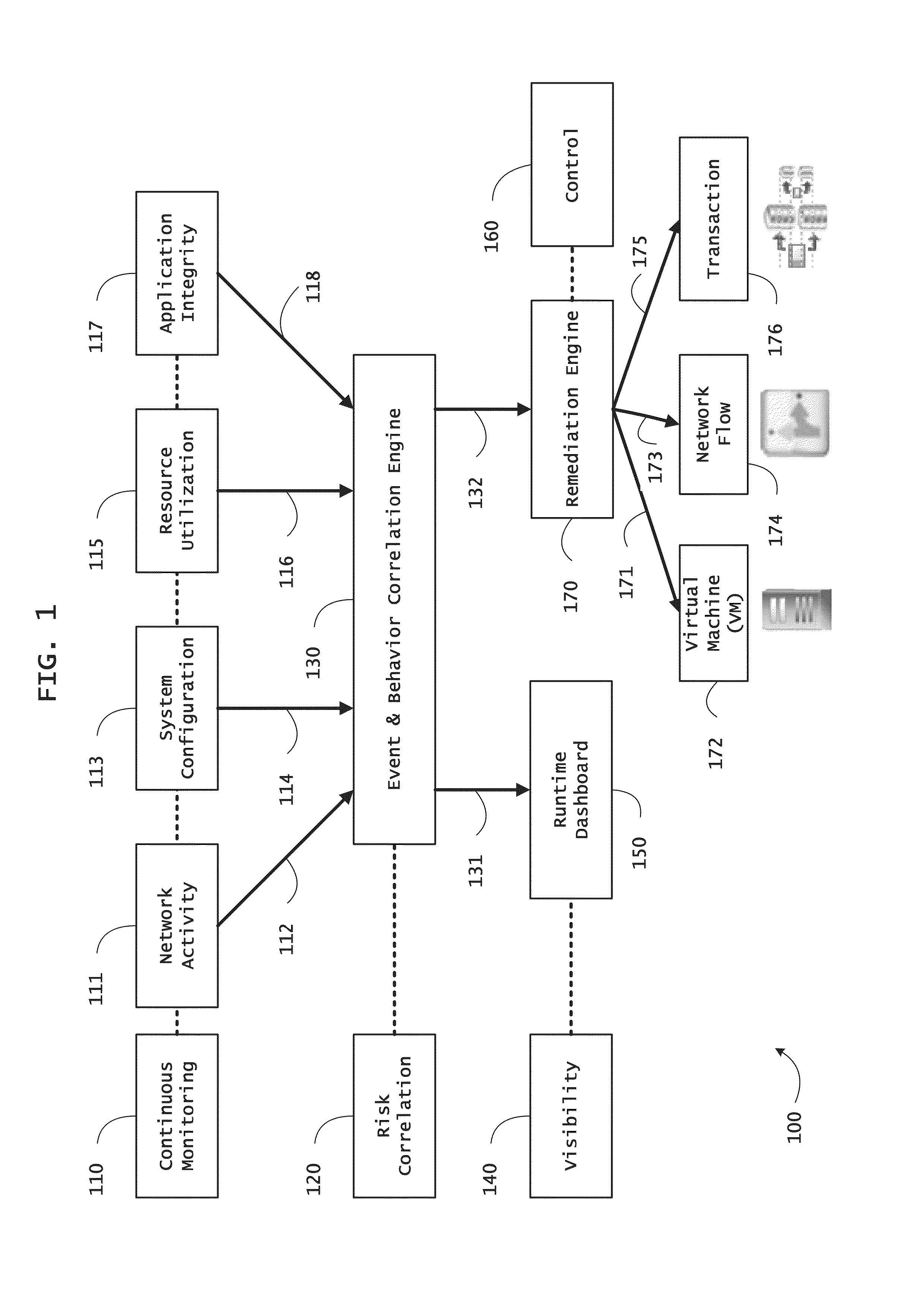
Systems and methods for network flow remediation based on risk correlation
ActiveUS20130298230A1Memory loss protectionError detection/correctionResource utilizationSystem configuration
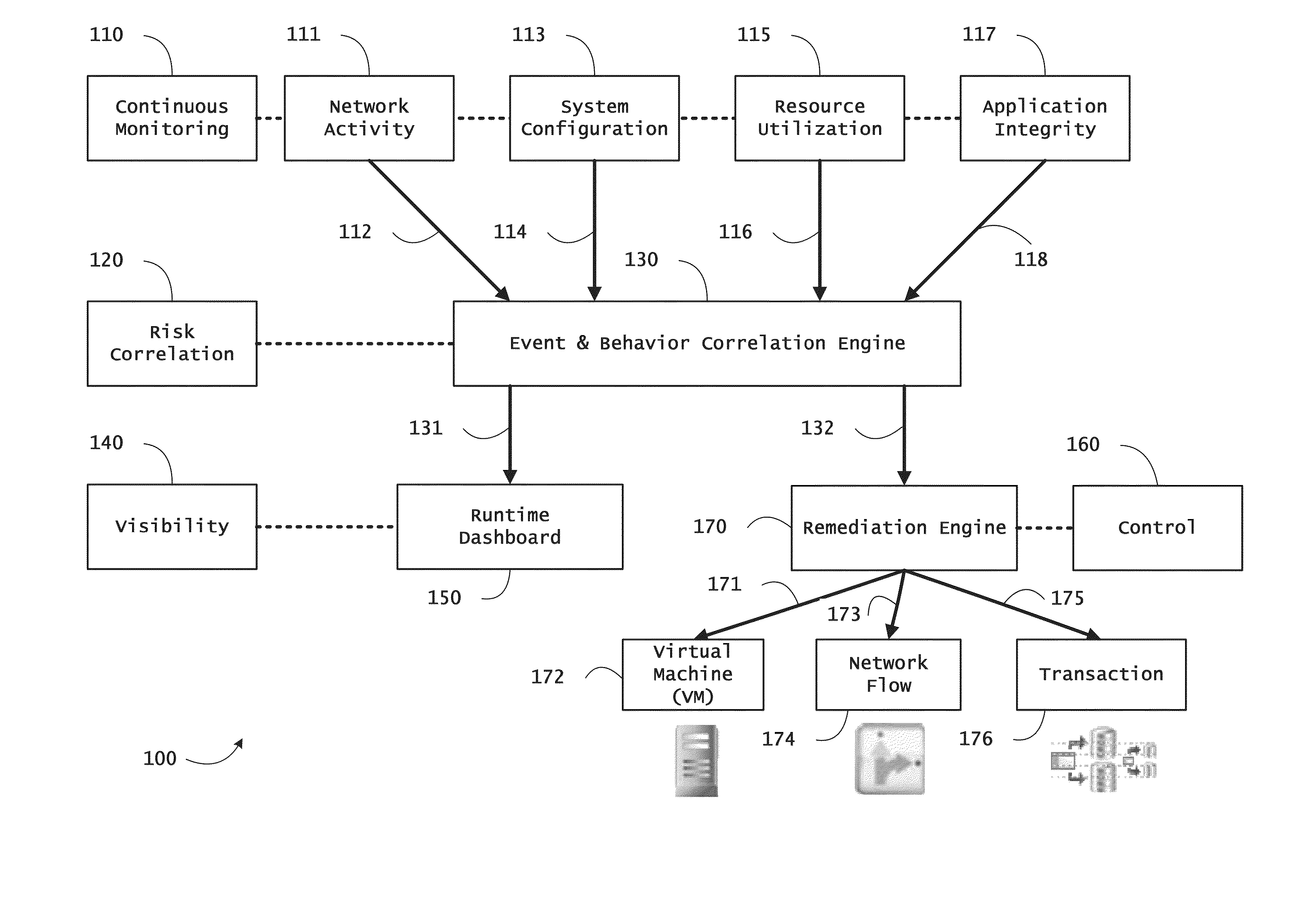
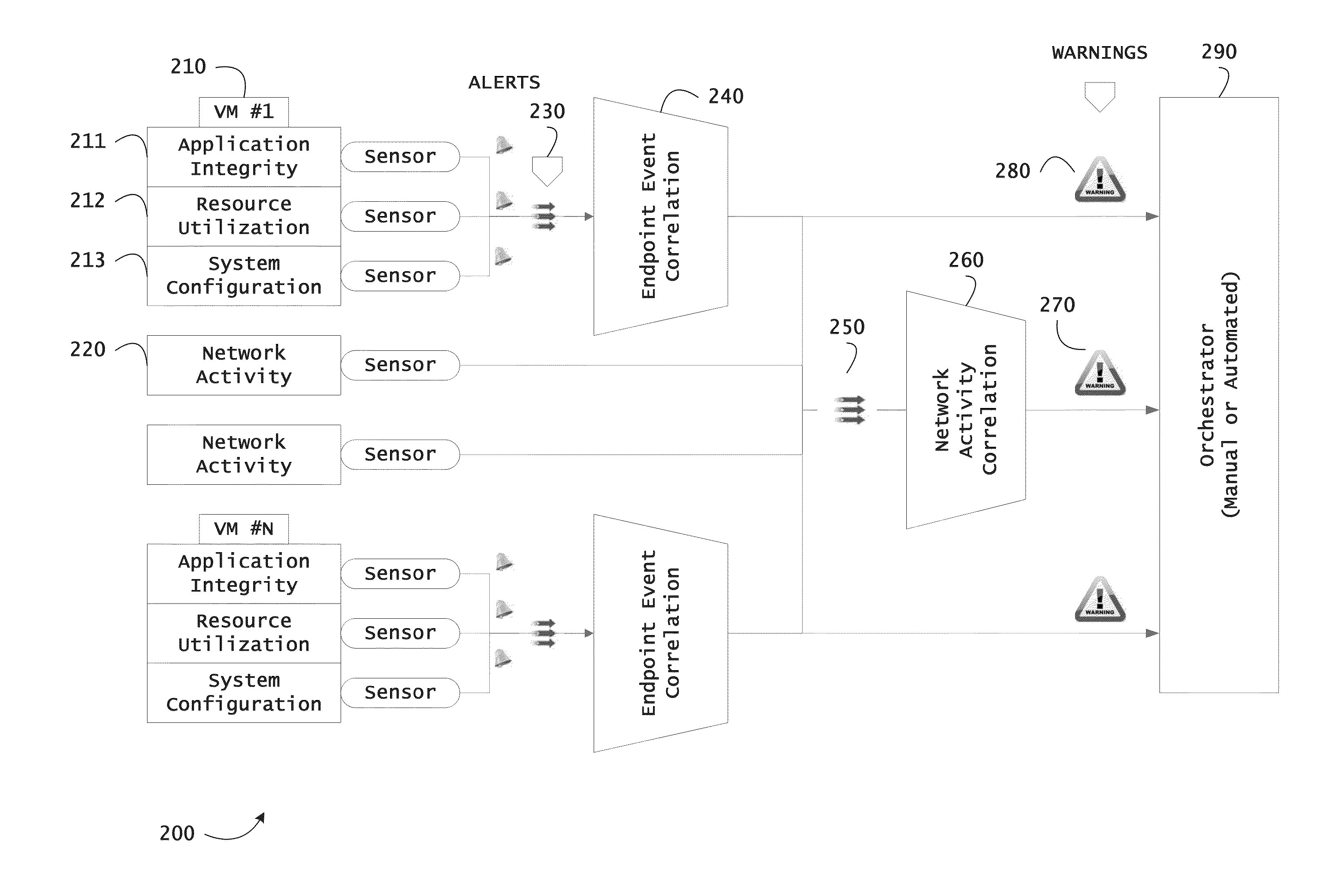
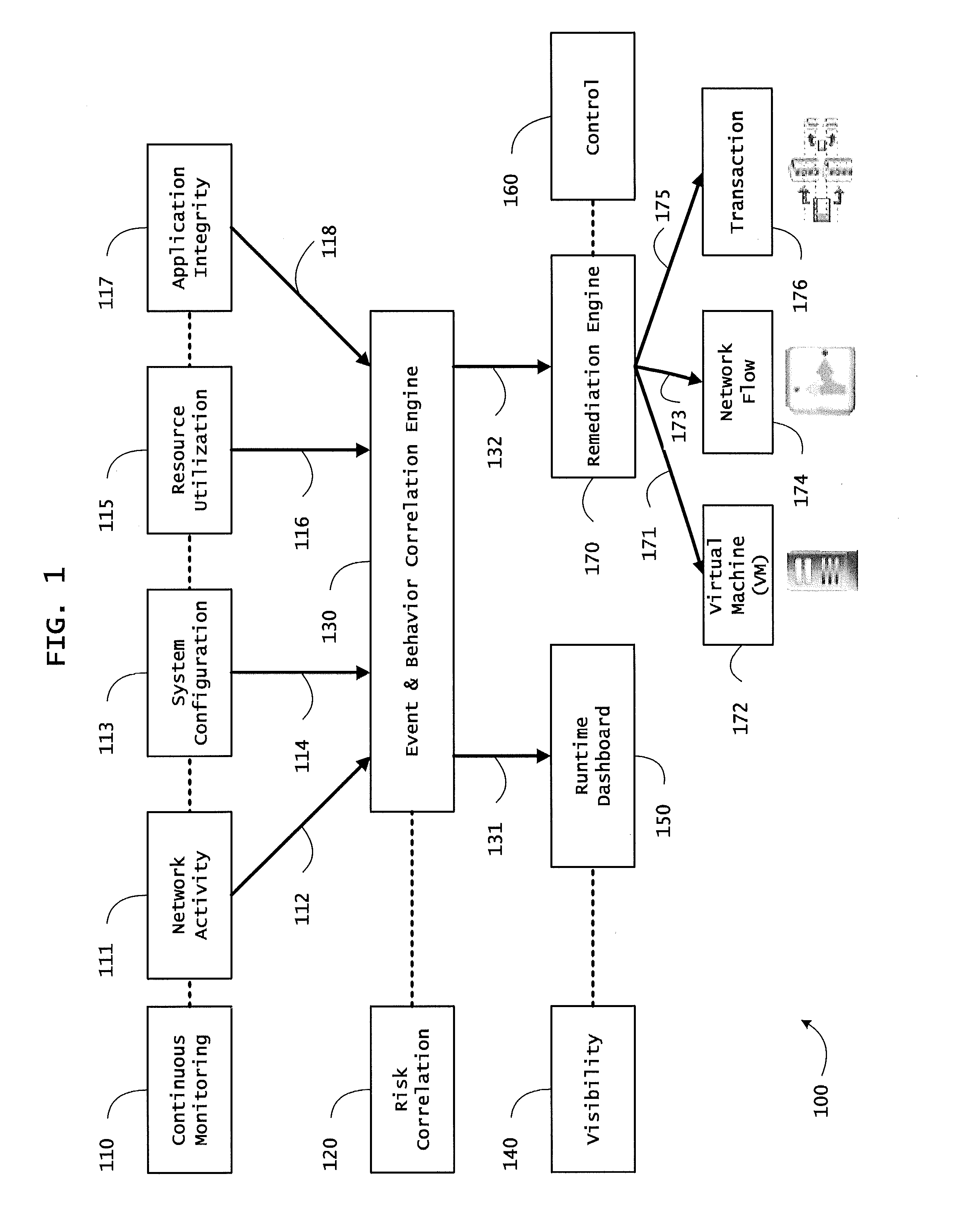
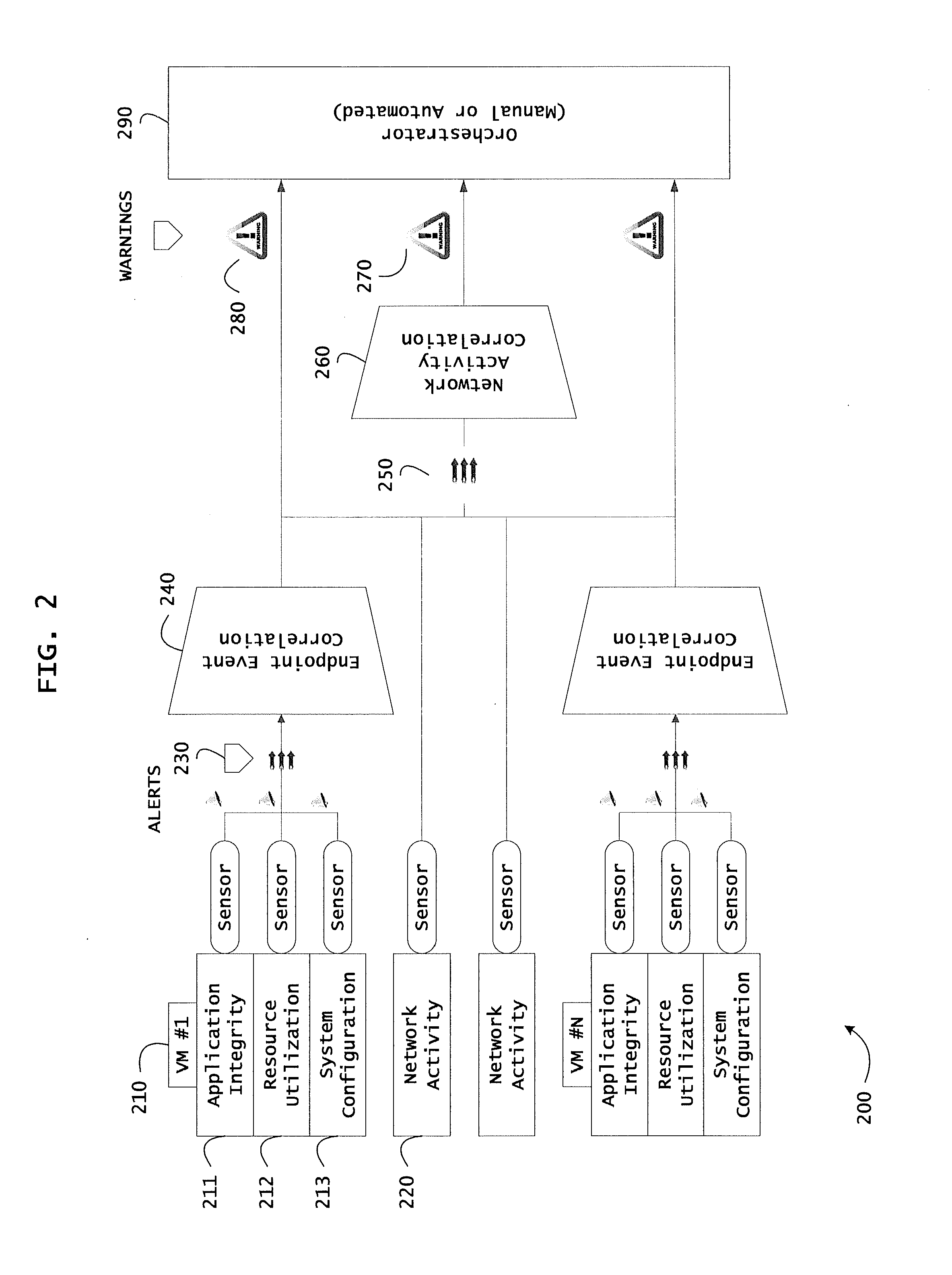
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for network flow and device / platform remediation in response to reconnaissance-based intelligence correlation based on network monitoring, to accomplish network flow remediation and device / platform remediation. In an embodiment, a system receives system warnings and endpoint threat intelligence. The system correlates risk based on inputs from sensory inputs that monitor network activity, system configuration, resource utilization, and device integrity. The system then performs a calculus of risk on a global security context including endpoint assessment reports and sends system warnings based upon the endpoint threat intelligence. The system includes a remediation engine for receiving real time directives to control the device.
Owner:TAASERA LICENSING LLC
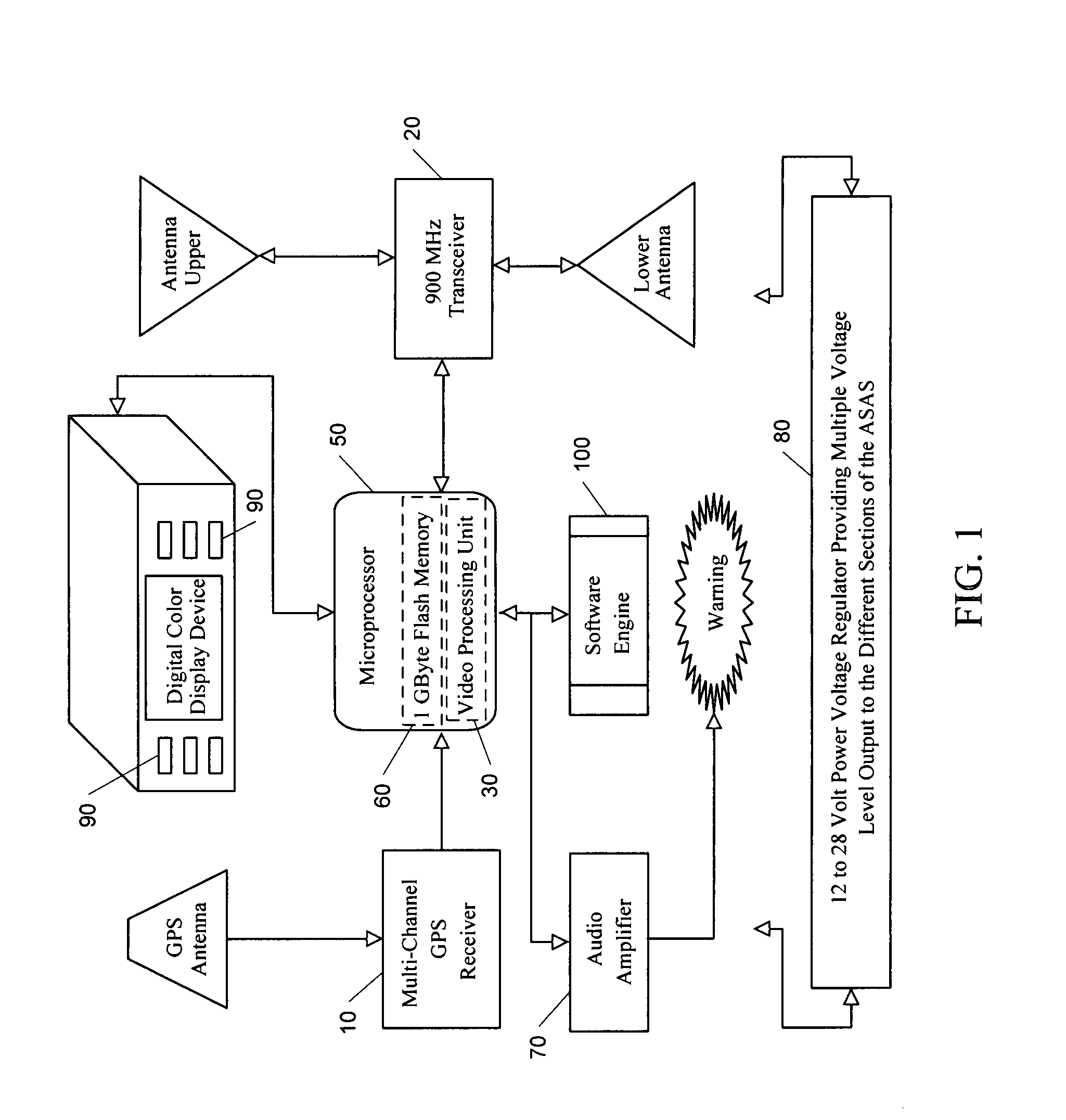
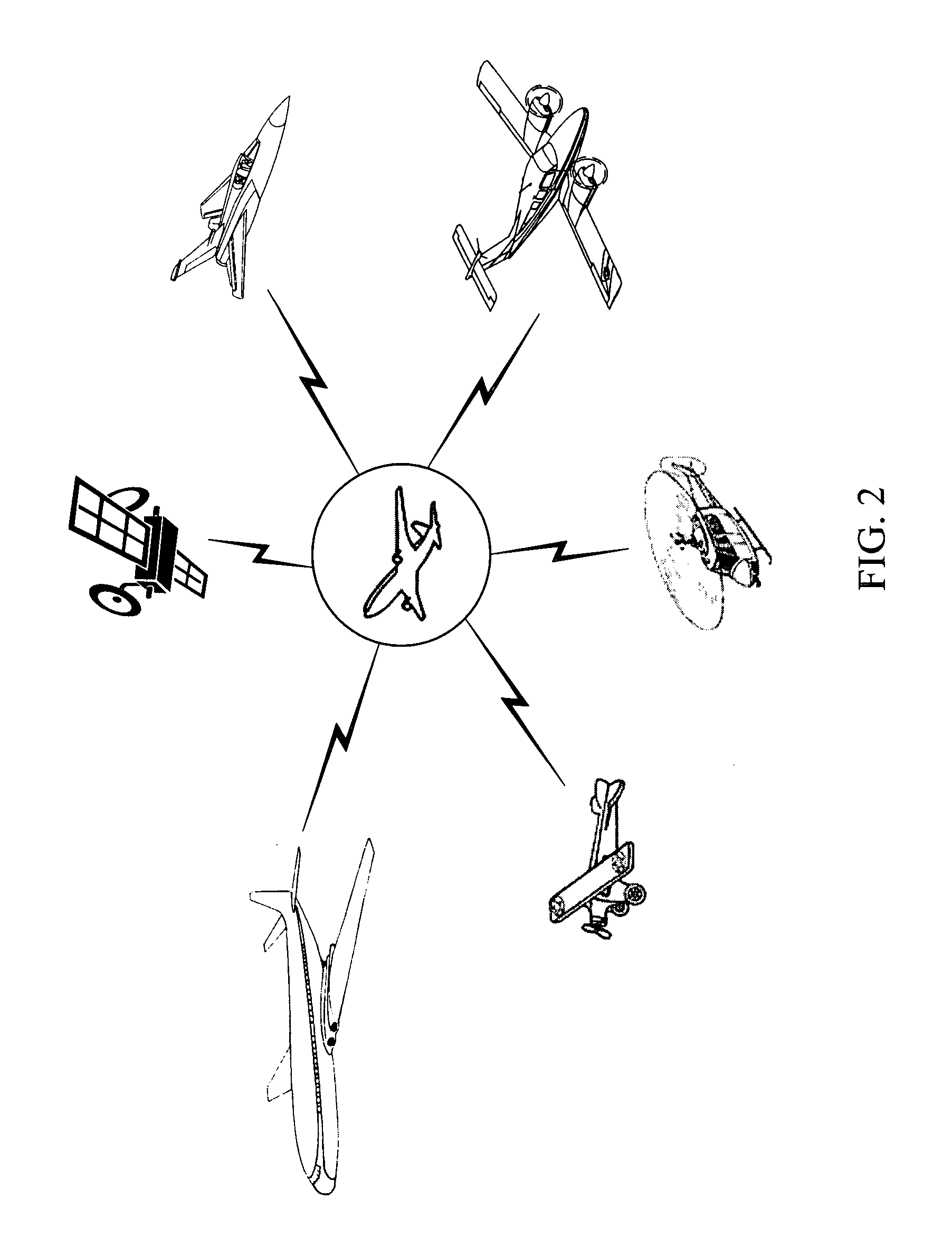
Airborne Situational Awareness System
InactiveUS20070222665A1Satellite radio beaconingRadio wave reradiation/reflectionData packTransceiver
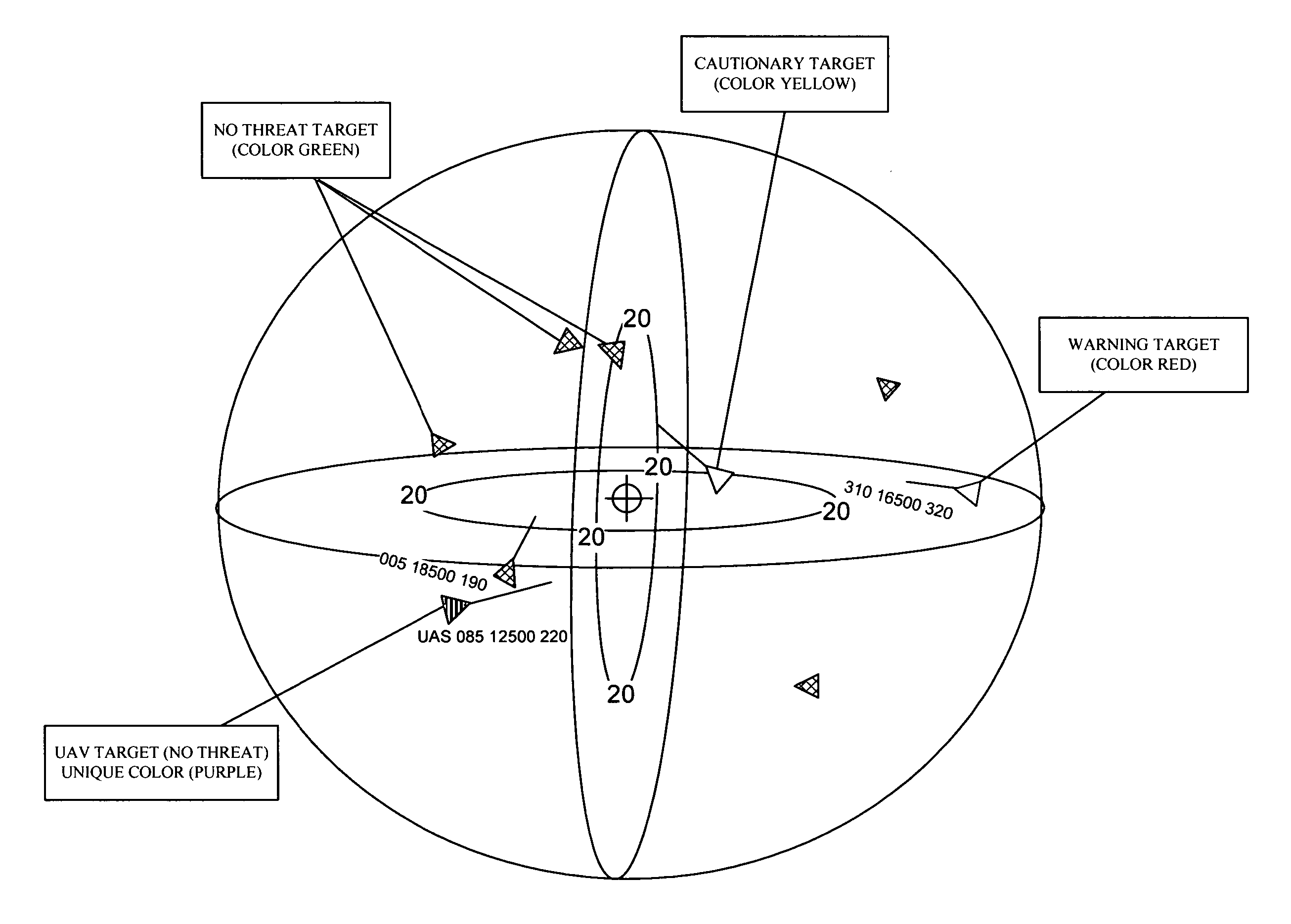
A digital airborne situational awareness system and method. The system is installed on multiple aircraft to generate an airborne network providing collision avoidance without ground control. A global positioning system (GPS) receiver unit is coupled to a microprocessor in each aircraft equipped with the system. A software engine receives the raw GPS data and determines location, speed, flight path direction, and altitude. The software engine conditions the GPS data for display on a cockpit display panel. The conditioned data orients the display with the heading, speed, and altitude data of the host system aircraft. A transceiver section provides data transmission to other airborne receiving units within the approximately forty mile range of the airborne network. The transceiver transmits data packets including reconditioned location (track), altitude, and an aircraft class identifier to other aircraft in the network. The transceiver receives data from other airborne vehicles equipped with the system within the network range. Once the computations of positional data for other aircraft are performed, the positional data is sent to the display processing section for appropriate cockpit display. The software engine develops a set of projections that are compared to the relative speed, flight path direction and altitude of the all other units in the airborne network. These projections determine the threat levels of converging flight paths with limits that provide warning data to the pilot of any pending flight path conflict situation.
Owner:DIMENSIONAL RES
Event monitoring and management
InactiveUS20070294369A1Multiple digital computer combinationsPlatform integrity maintainanceNetwork connectionThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
Apparatus and method for providing environmental predictive indicators to emergency response managers
ActiveUS20140324351A1Good effectIncrease probabilityWeather condition predictionAlarmsAtmospheric sciencesPrediction system
A method of predicting weather-exacerbated threats, said method comprising inputting localized weather measurement data into a weather threat prediction system; predicting future localized weather conditions based on said localized weather measurement data combined with modeling from large scale weather data including National Weather Service Data; inputting natural environment and infrastructure data into said weather threat prediction system; correlating said infrastructure data with said predicted future localized weather conditions; and determining a threat level index over a region, a threat level indicating an area having a certain probabilistic likelihood of being harmed by said future weather conditions.
Owner:SAINT LOUIS UNIVERSITY
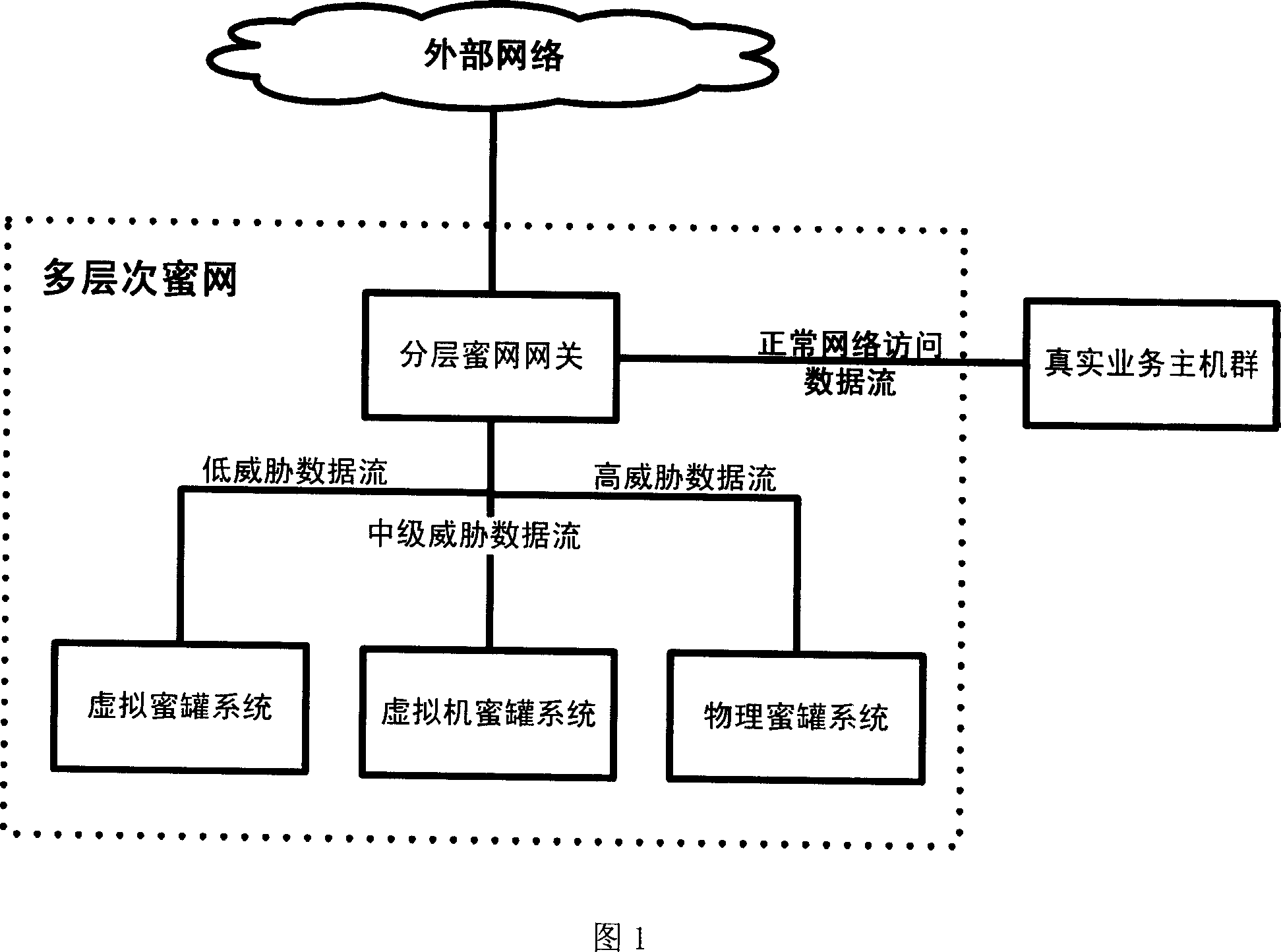
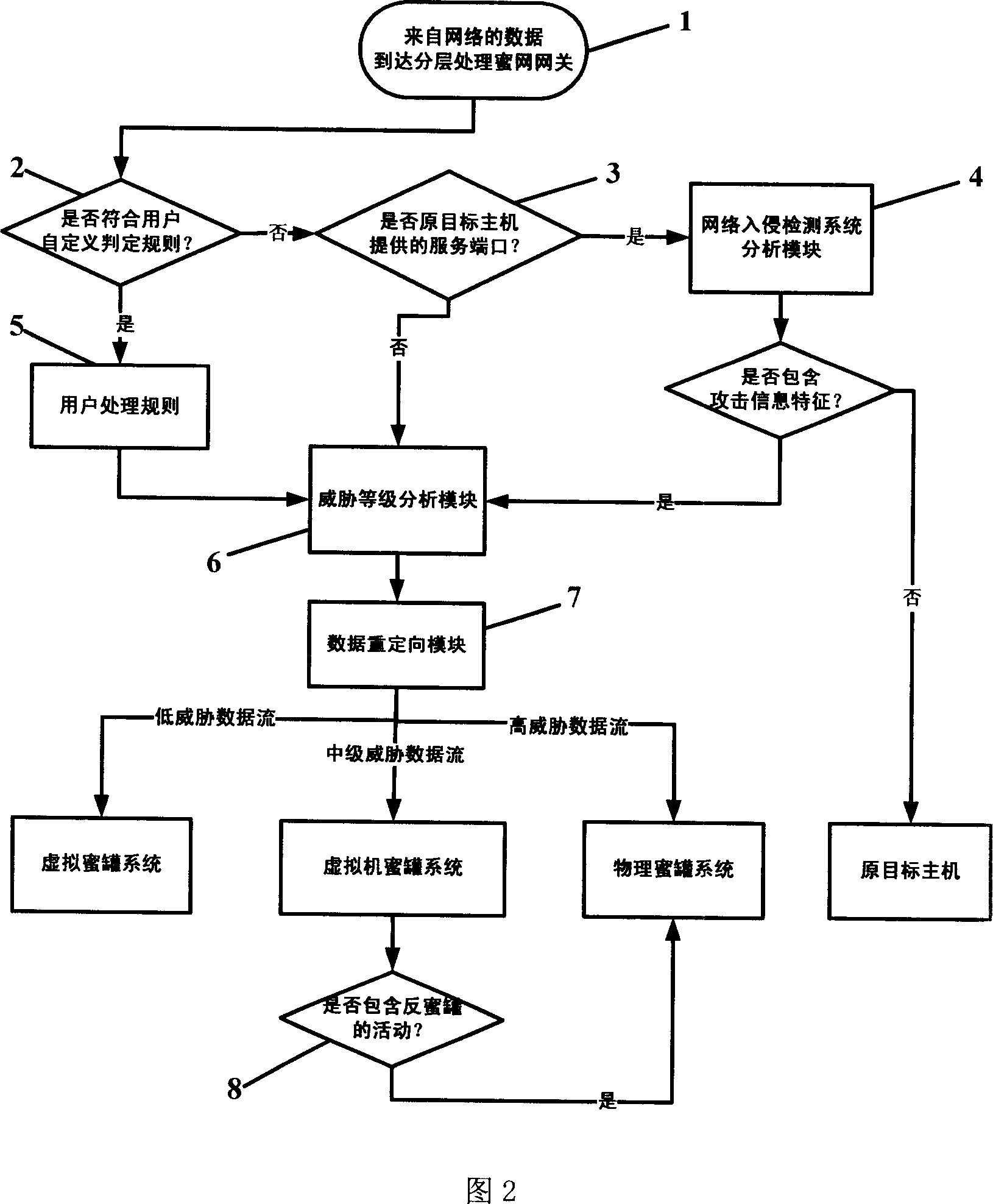
Multi-layer honey network data transmission method and system
InactiveCN101087196AIncrease reachSave resourcesNetwork connectionsSecuring communicationData streamNonnormal data
The invention relates to multilayer honey-net data transmission method and system, and the gateway of honey-net receives the data flow of external network; the gateway of honey-net detects the network intrusion for the received data flow; the normal data flow can pass, which is sent to the target host computer; and the informal data flow is divide into high, middle and low according to dangerous level; and the data flow with high level is sent to physical honey-tank system, the data flow with middle level is sent to virtual machine honey-tank system, and the data floe with low level is sent to virtual honey-tank system. The invention can utilize the advantages of low interactive honey-tank system and high interactive honey-tank system, save system source, and improve the covering area of honey-tank system and the ability of obtaining the movable information of network attack and capturing the malice code; it can defeat the anti-honey tank technique. And it can be used in security field of computer network.
Owner:PEKING UNIV
Contextual Risk Indicators in Connection with Threat Level Management
InactiveUS20100156630A1Easy to adjustHigh riskIndication of parksing free spacesIndividual entry/exit registersCountermeasureInternet privacy
A system is provided that that allows users to define factors that uniquely affect the security risk of certain events at a certain locale. The system can then change its behavior based on these custom risks and invoke various counter measures when threats are more likely. Accordingly, one embodiment of the invention provides for the use of contextual risk indicators in connection with threat level management.
Owner:TITAN HLDG
Context-aware threat response arbitration
ActiveUS20150057891A1Reduce probabilityImprove convenienceAnalogue computers for trafficSteering initiationsThreat levelThrottle
A method for prioritizing potential threats identified by vehicle active safety systems. The method includes providing context information including map information, vehicle position information, traffic assessment information, road condition information, weather condition information, and vehicle state information. The method calculates a system context value for each active safety system using the context information. Each active safety system provides a system threat level value, a system braking value, a system steering value, and a system throttle value. The method calculates an overall threat level value using all of the system context values and all of the system threat level values. The method then provides a braking request value to vehicle brakes based on all of the system braking values, a throttle request value to a vehicle throttle based on all of the system throttle values, and a steering request value to vehicle steering based on all of the system steering values.
Owner:GM GLOBAL TECH OPERATIONS LLC
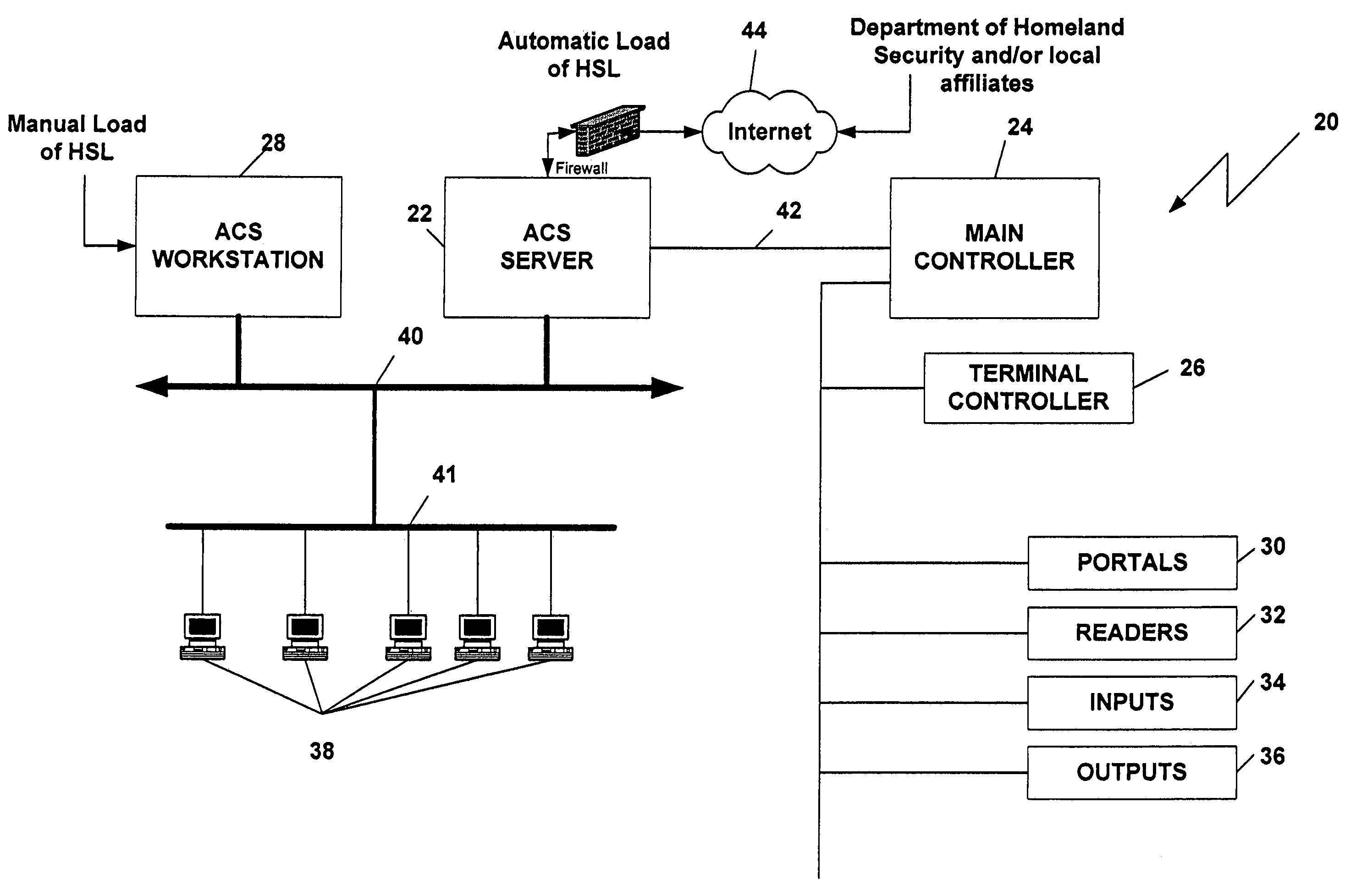
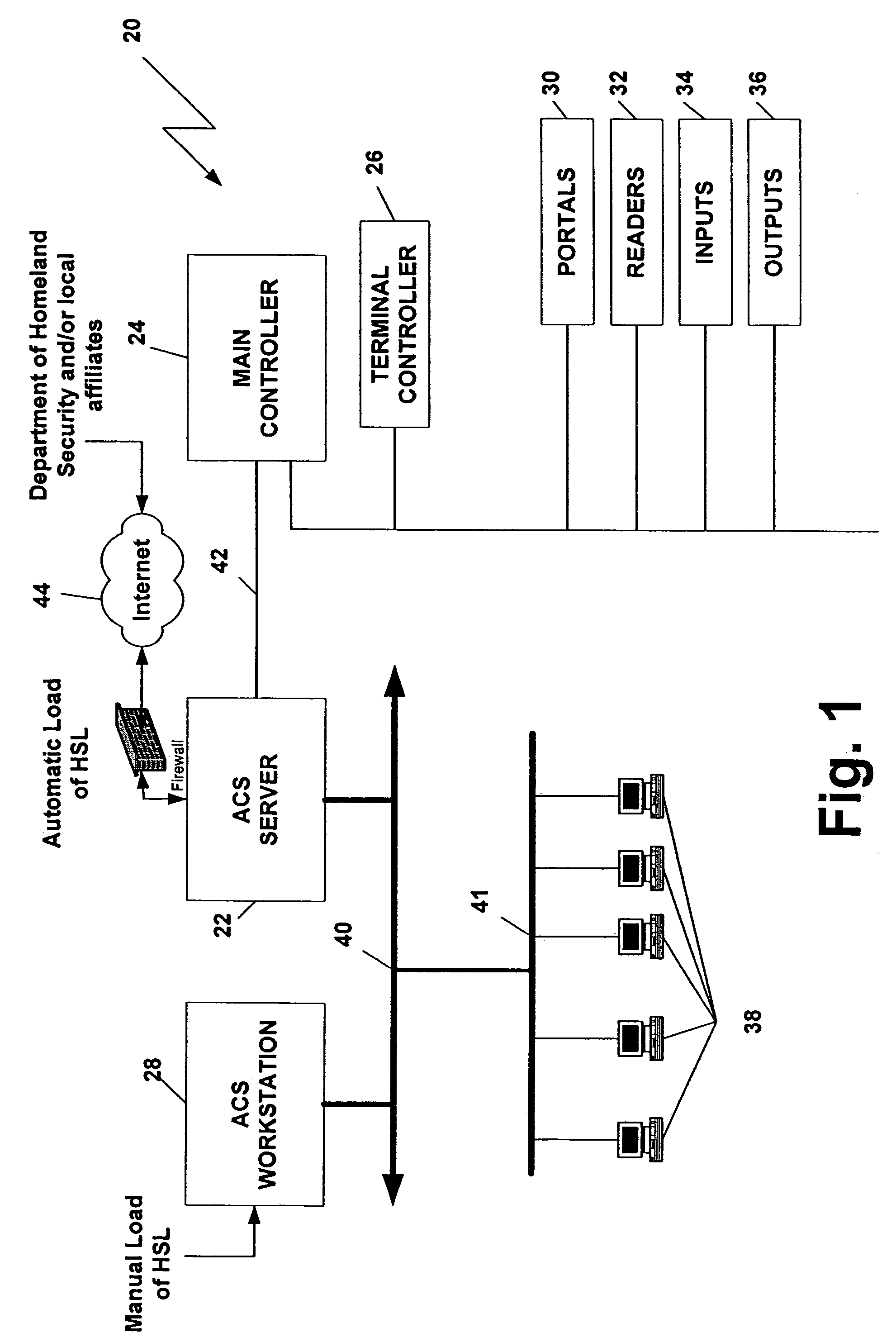
System and method for adjusting access control based on homeland security levels
ActiveUS7280030B1Electric signal transmission systemsMultiple keys/algorithms usageControl systemHomeland security
A system and method for automatically regulating access control levels in an access control system based on the threat level as determined by the Department of Homeland Security and / or their corresponding local offices.
Owner:HGW ACQUISITION COMPANY
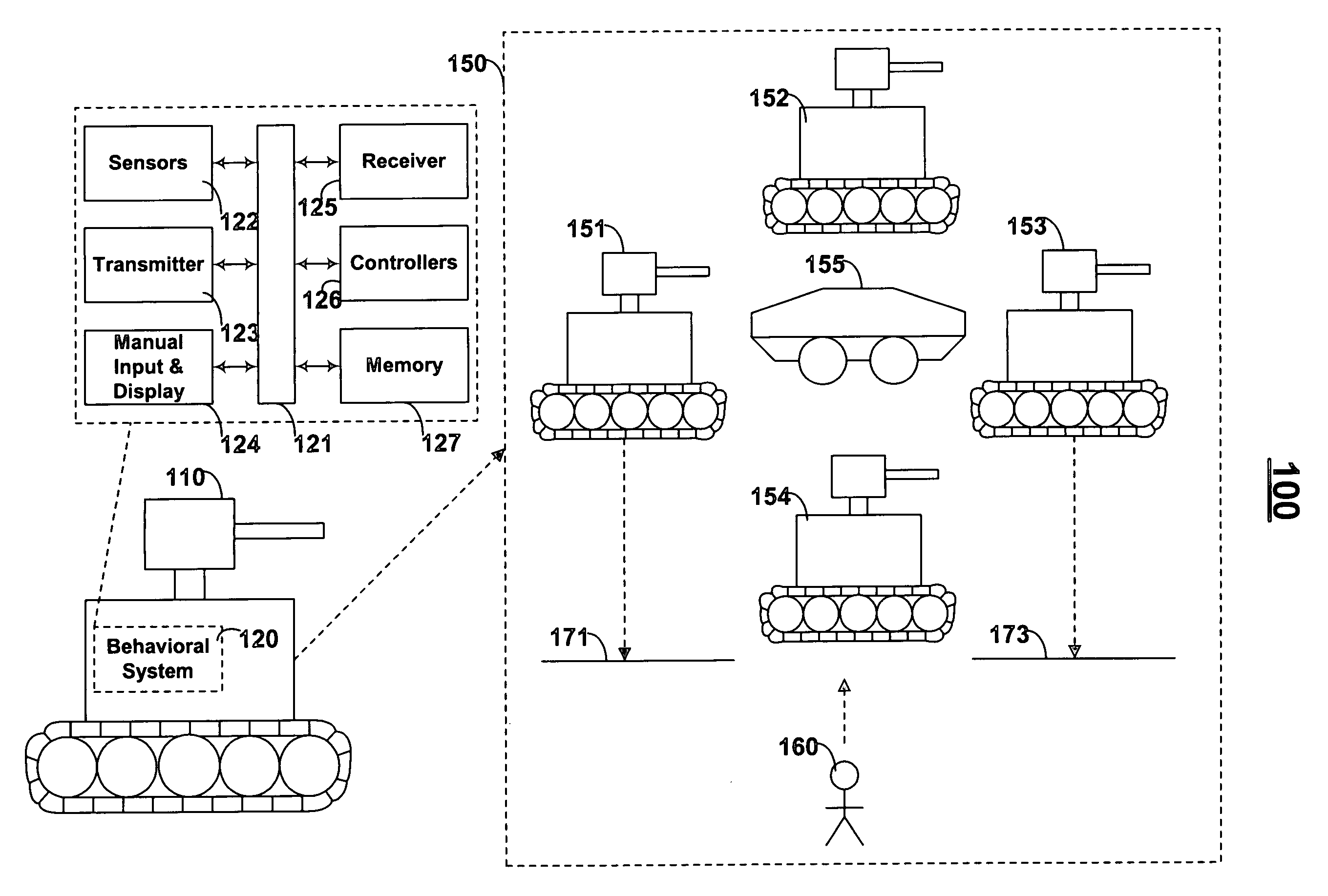
Advanced cooperative defensive military tactics, armor, and systems
This invention provides impact detection and vehicle cooperation to achieve particular goals and determine particular threat levels. For example, an impact / penetration sensing device may be provided on a soldier's clothing such that when this clothing is impacted / penetrated (e.g., penetrated to a particular extent) a medical unit (e.g., a doctor or medical chopper) may be autonomously, and immediately, provided with the soldiers location (e.g., via a GPS device on the soldier) and status (e.g., right lung may be punctured by small-arms fire).
Owner:MULLEN JEFFREY D
Active attack detection system
Owner:MEADOW HILLS
Rapid disaster notification system
InactiveUS20080088434A1Remove restrictionsQuickly and efficiently transmit useful informationAlarmsElectric signalling detailsField conditionsEngineering
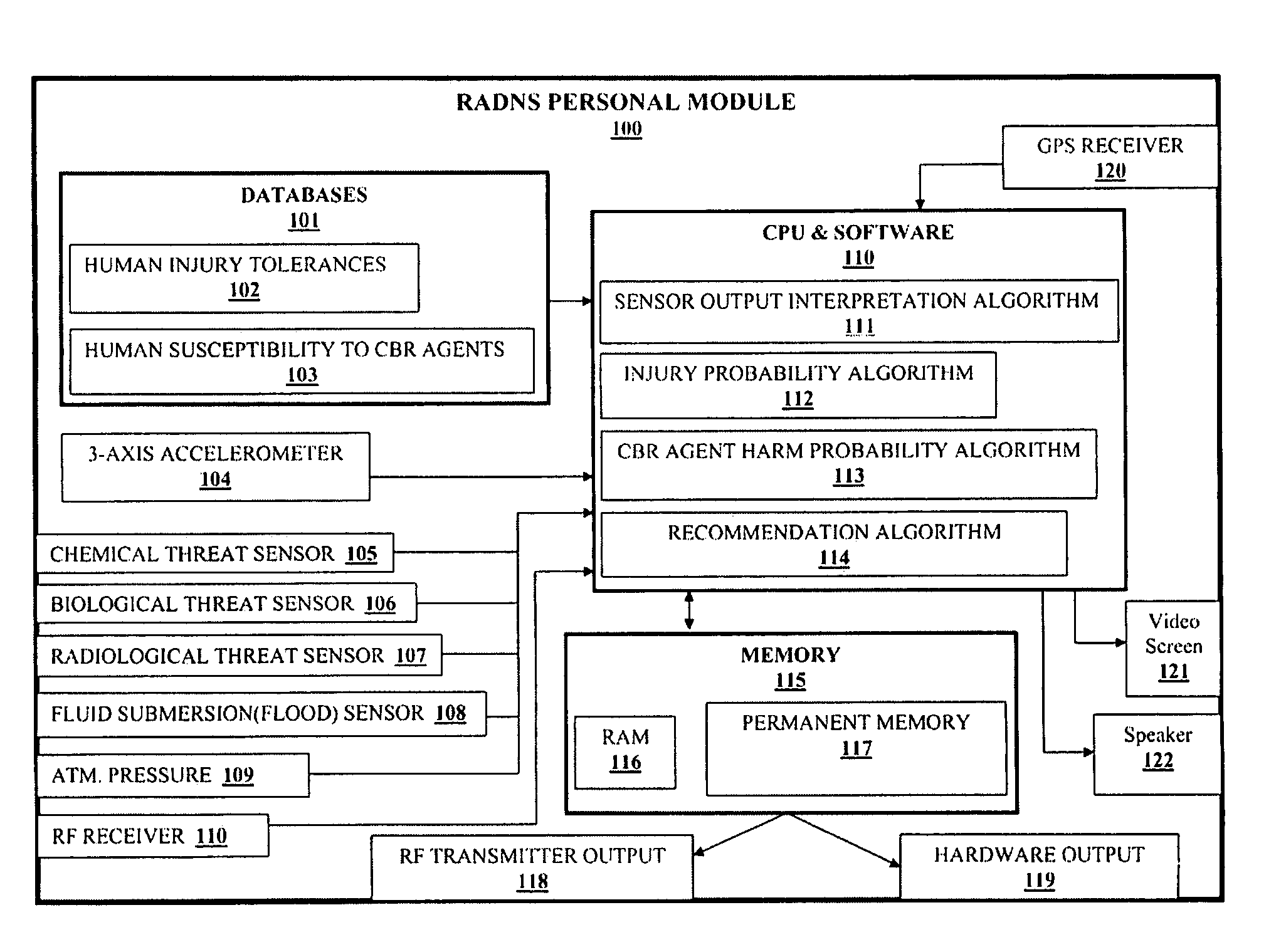
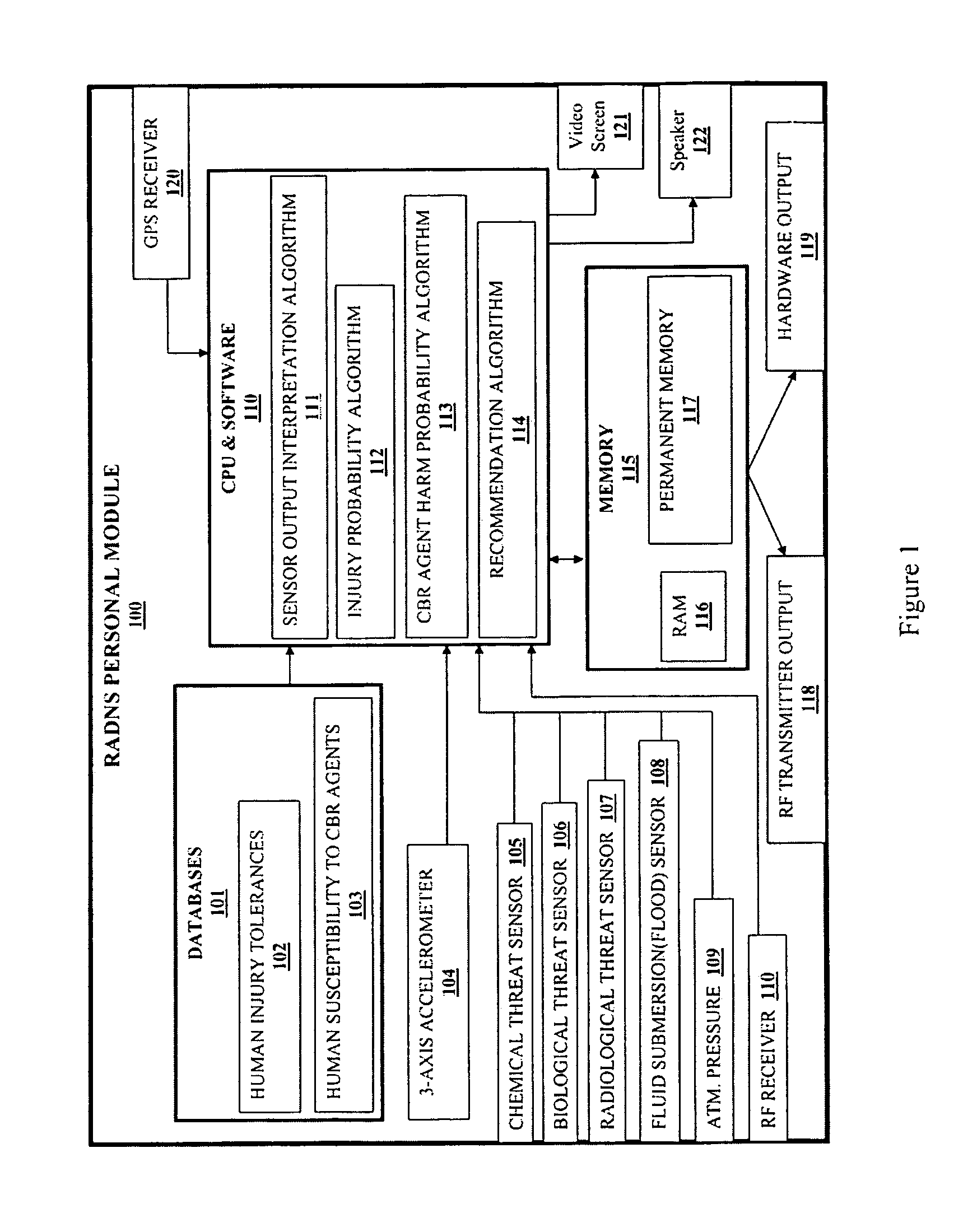
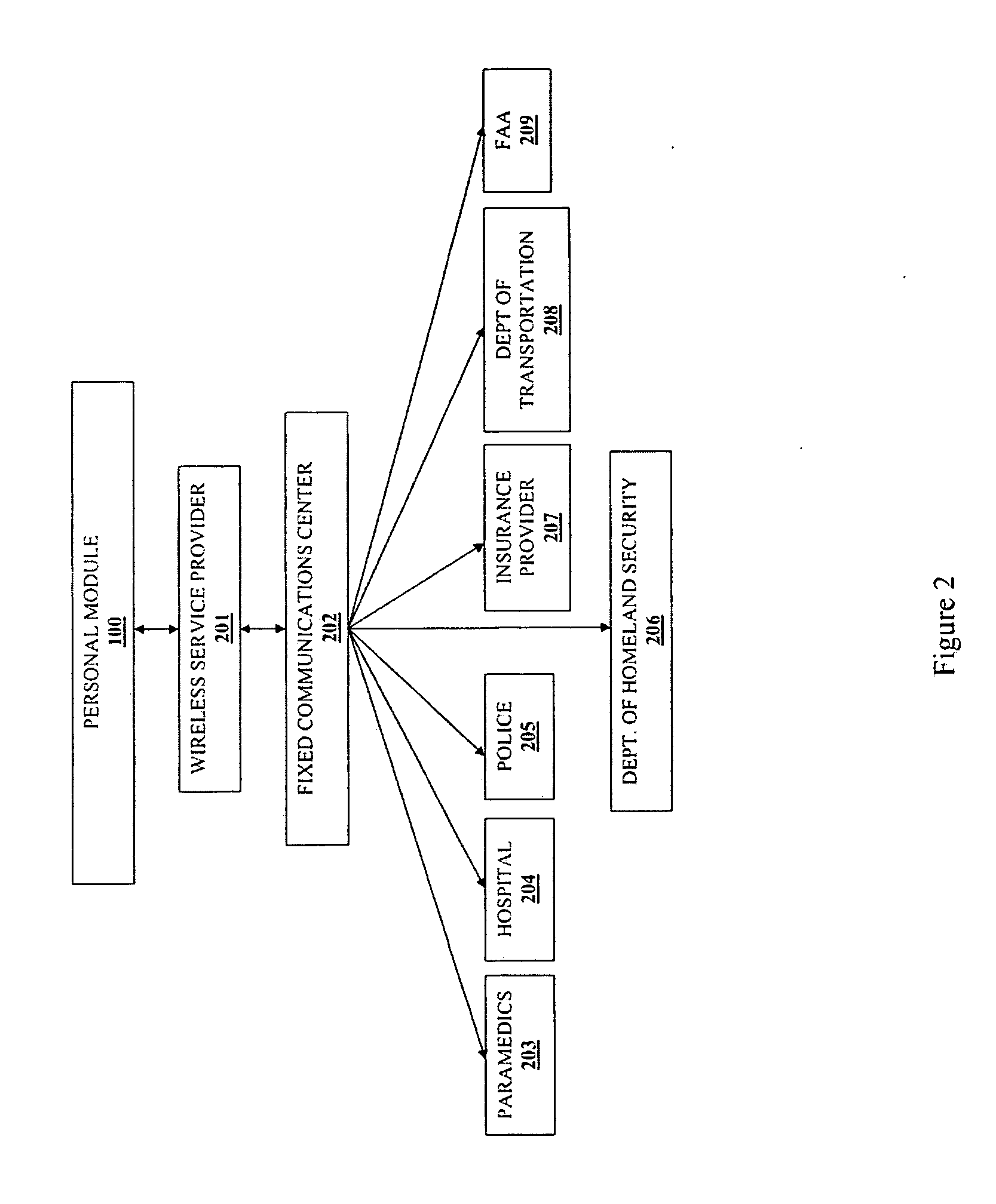
A system operable for detecting the exposure of a person or persons to a plurality of different hazards. The system comprises at least one wearable personal module, a fixed communication center and wireless linking means operable for providing wireless communication between a personal module and the communication center and between a personal module and other personal modules comprising the system. The personal module is operable for detecting exposure of the wearer to a hazard and includes computer means operable for evaluating the threat level of the hazard to the wearer. The personal module further includes telemetry means operable for communicating the threat level to the fixed communication center and / or other personal modules. The personal module includes a plurality of detectors operable for detecting the exposure of the wearer to one or more chemical, physical, biological or radiological hazards under field conditions. The fixed communication center is operable for receiving exposure data from one or more personal modules and communicating the exposure data to first responders.
Owner:SAFETY DESIGN ANANYSIS
Multithreat safety and security system and specification method thereof
ActiveUS20090207020A1Easy to controlImprove efficiencyMarine craft traffic controlBurglar alarmRadarDependability
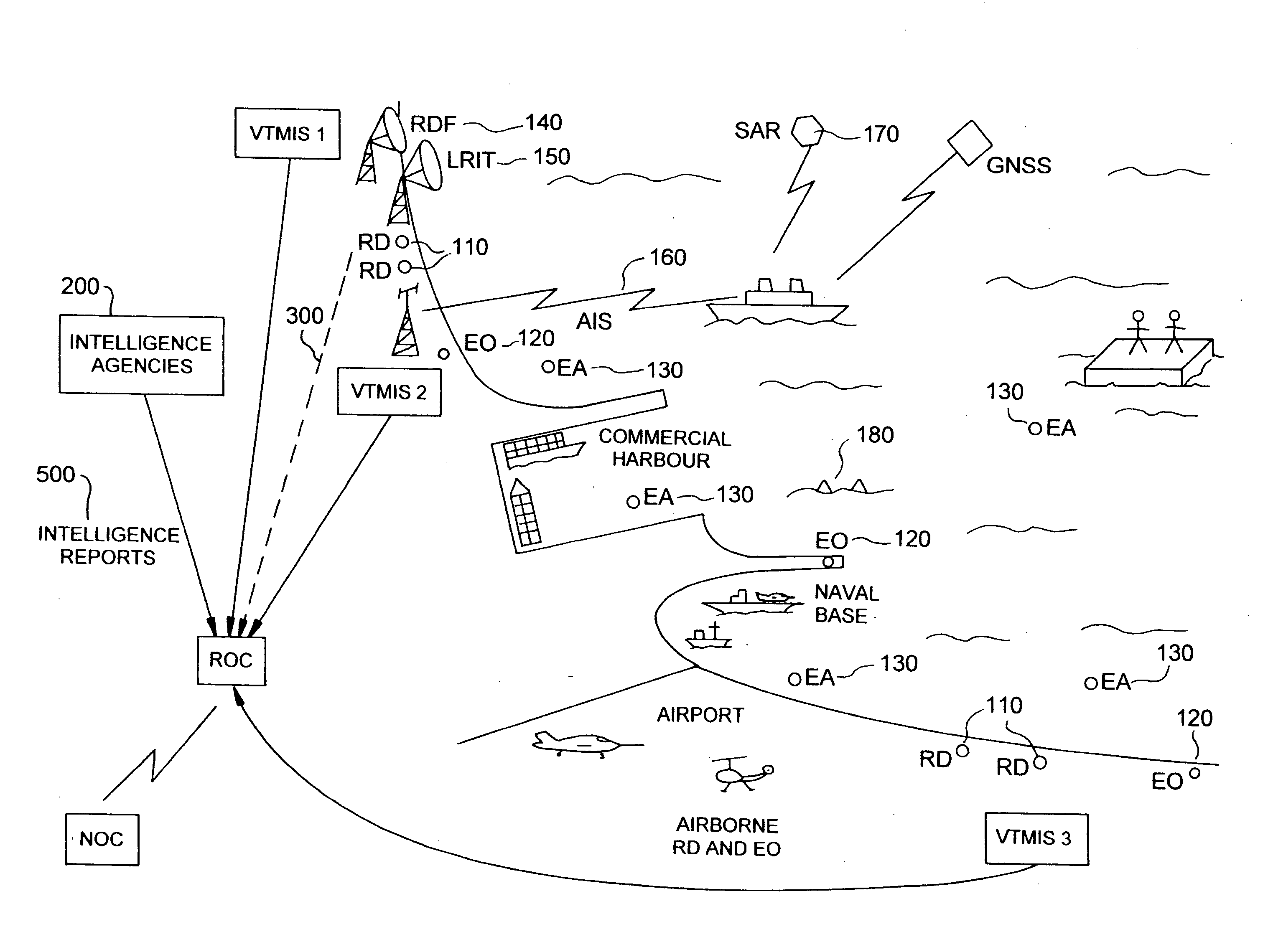
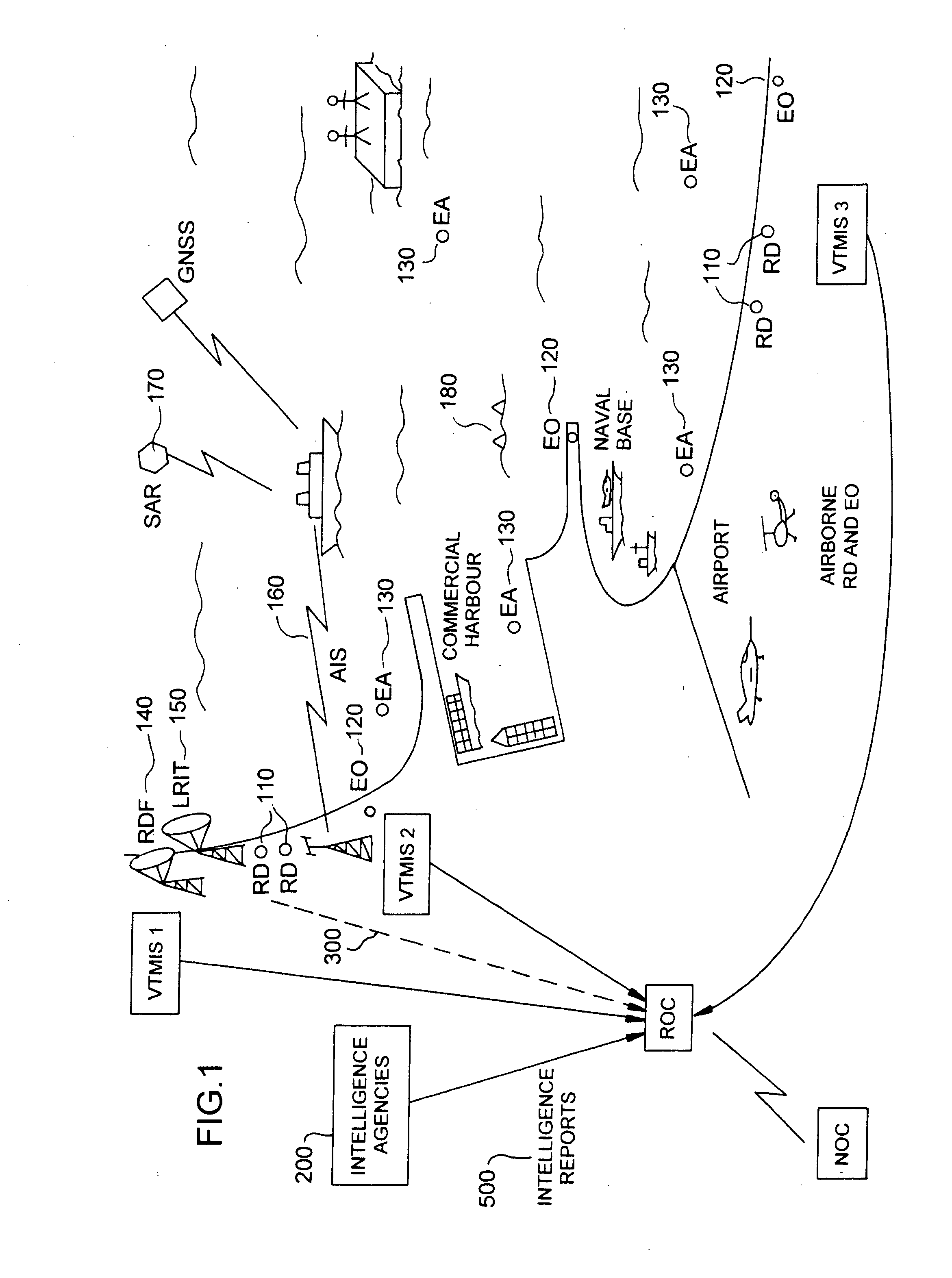
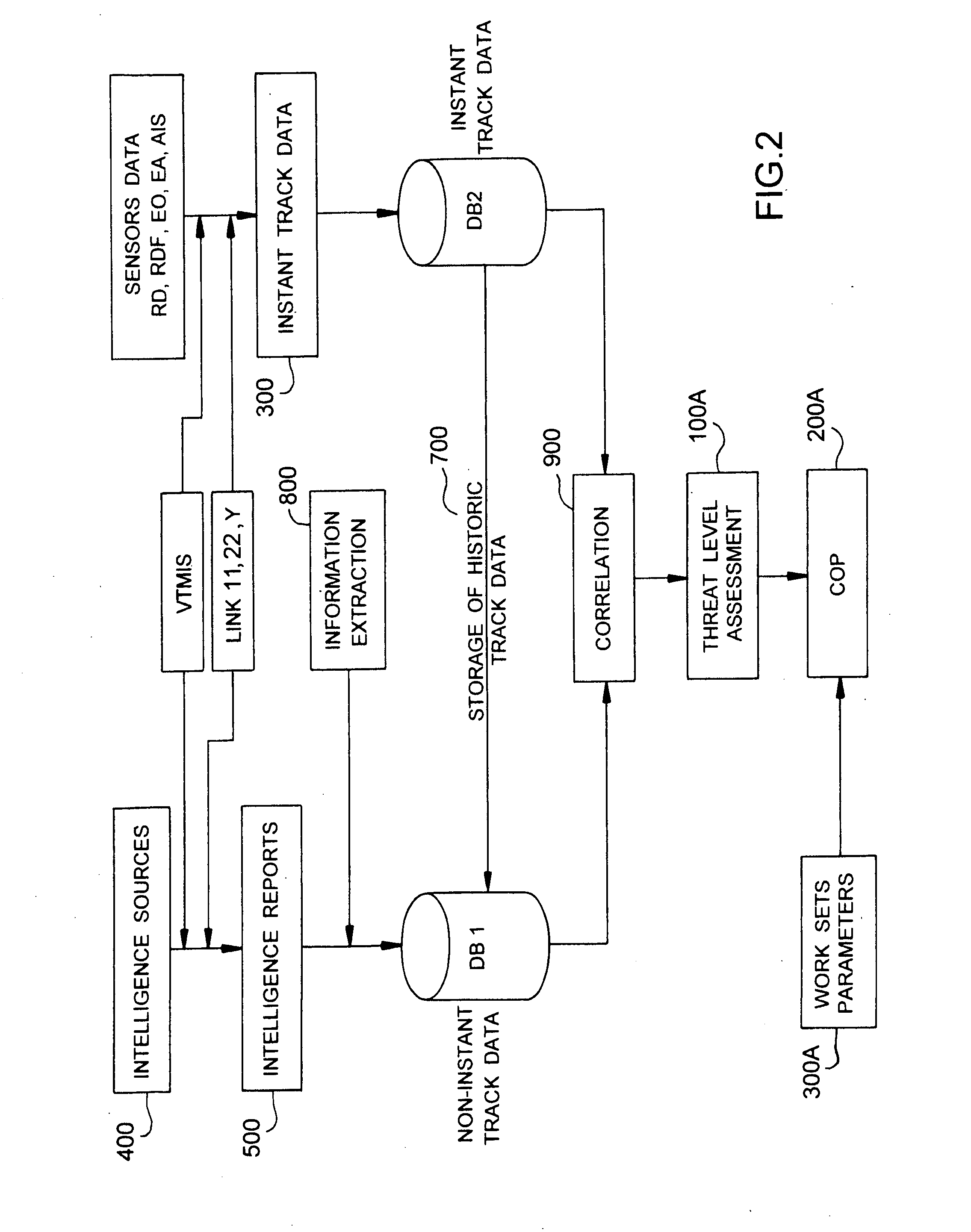
The invention relates to a safety and security system designed to protect a designated area. The system comprises sensors of various types (radars, infrared detectors for instance) and sources of intelligence. Correlation is run between instant-track data and non-instant-track data before the level of threat of the tracks is analysed. Reliability of this analysis is thus greatly enhanced. Also a method is provided to develop systems of this type which provides an integrated specification and design method which covers technical and human factors.
Owner:THALES NEDERLAND BV
Emergency Lighting System with Projected Directional Indication
InactiveUS20120092183A1Enable two-way communicationEfficiently projectedLight source combinationsPoint-like light sourceLight equipmentEffect light
An emergency lighting device for providing a directional indication on a recipient surface with first and second guidance indication light sources retained relative to a housing to emit beams of light, each with a directional indication, onto a recipient surface. The light sources can be individually operable and can have directional indications, such as arrows, pointing in first and second different directions. An illumination light source without a guidance indication can illuminate an adjacent area. Guidance indication light sources, which can be lasers, can emit beams in different colors to provide threat level indications. Plural emergency lighting devices can cooperate to guide a building occupant by providing directional indications on recipient surfaces.
Owner:EGRESSLITE
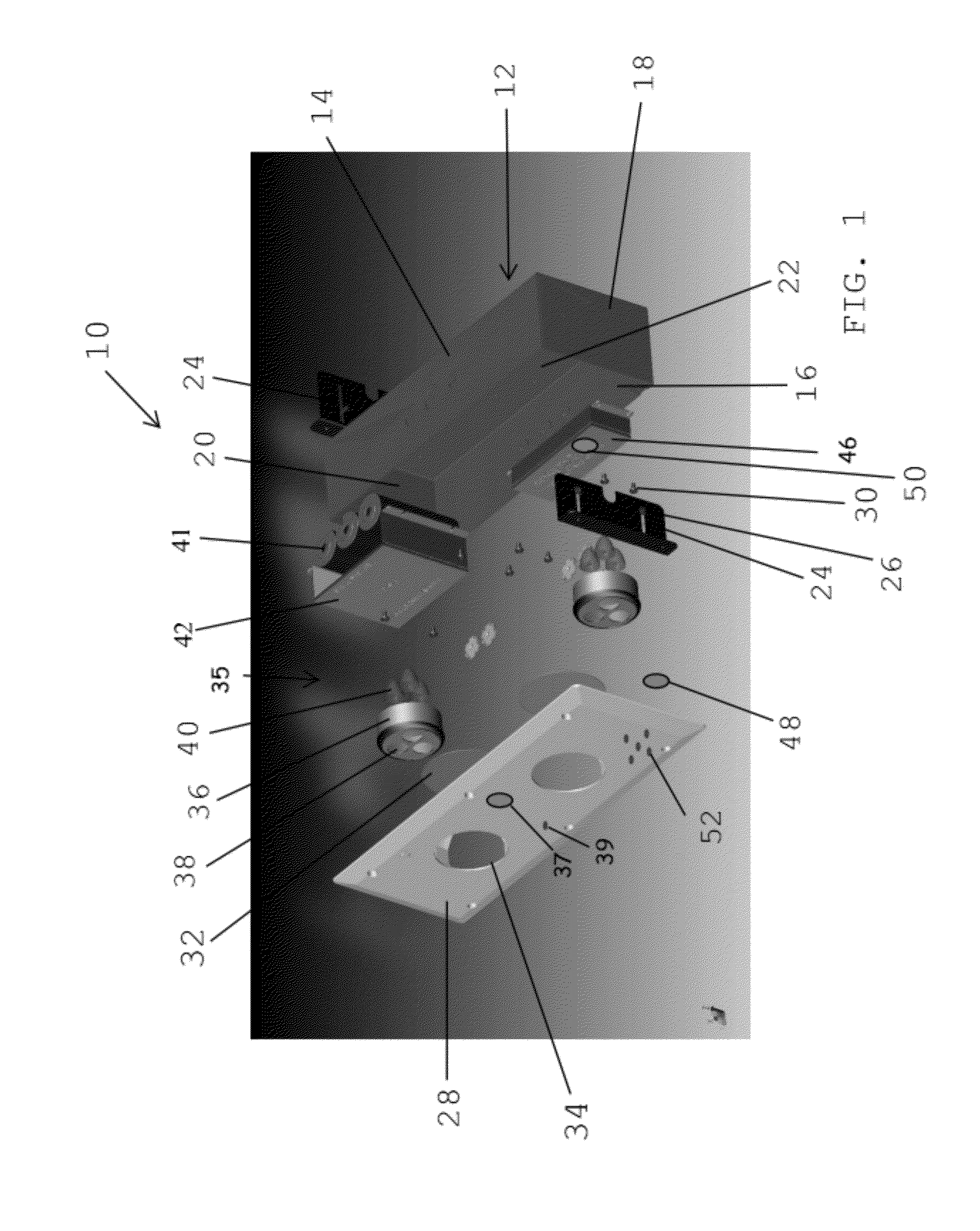
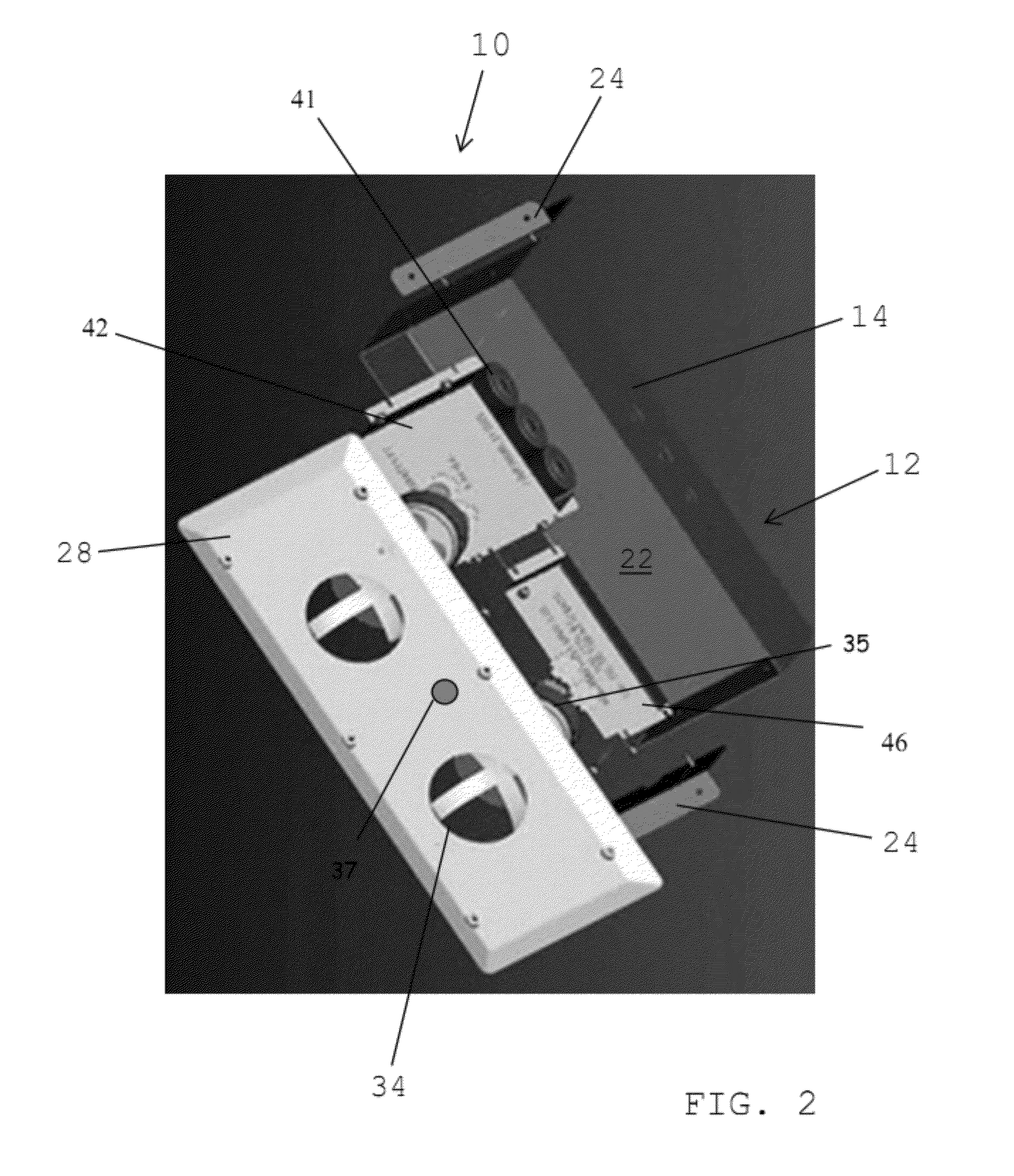
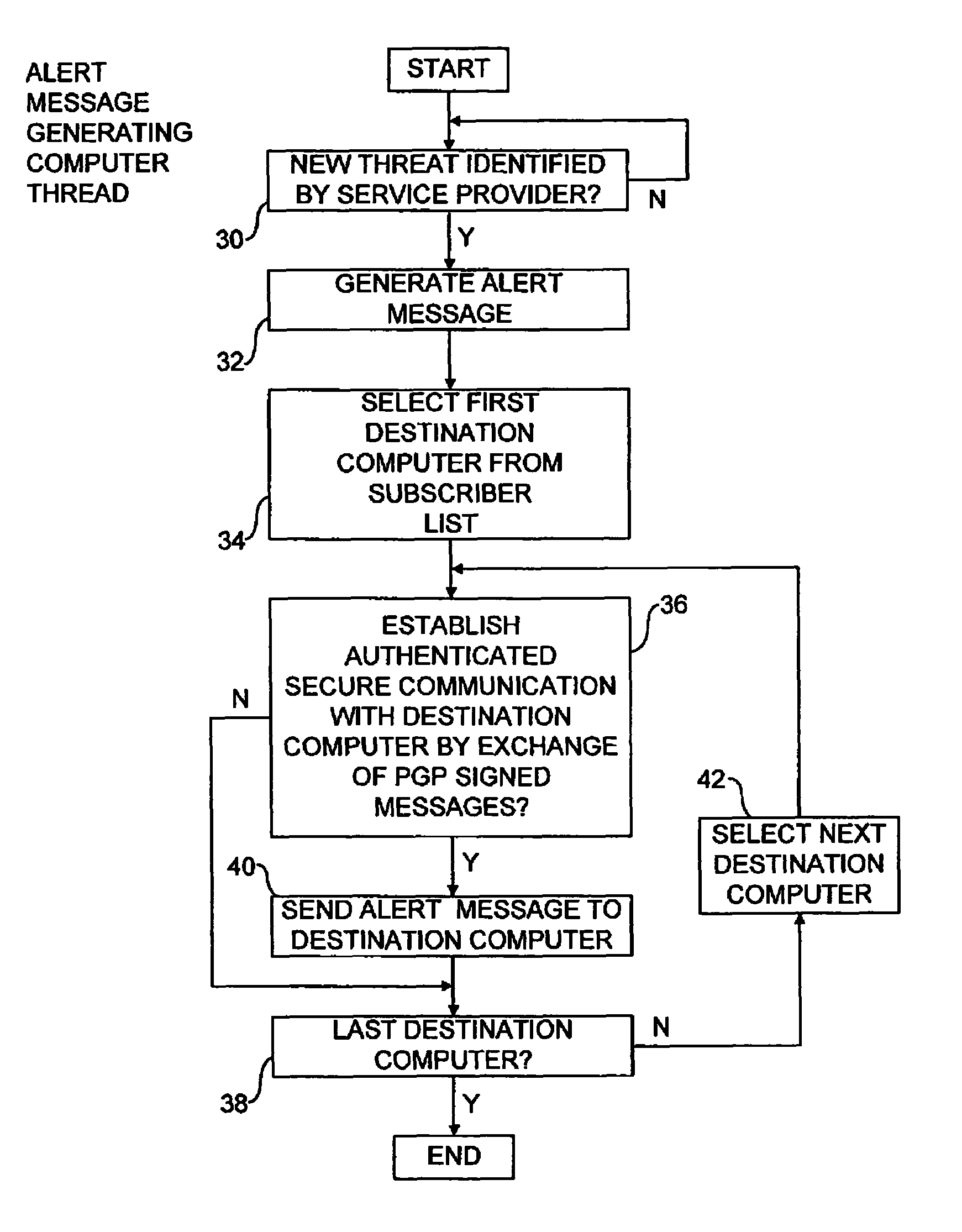
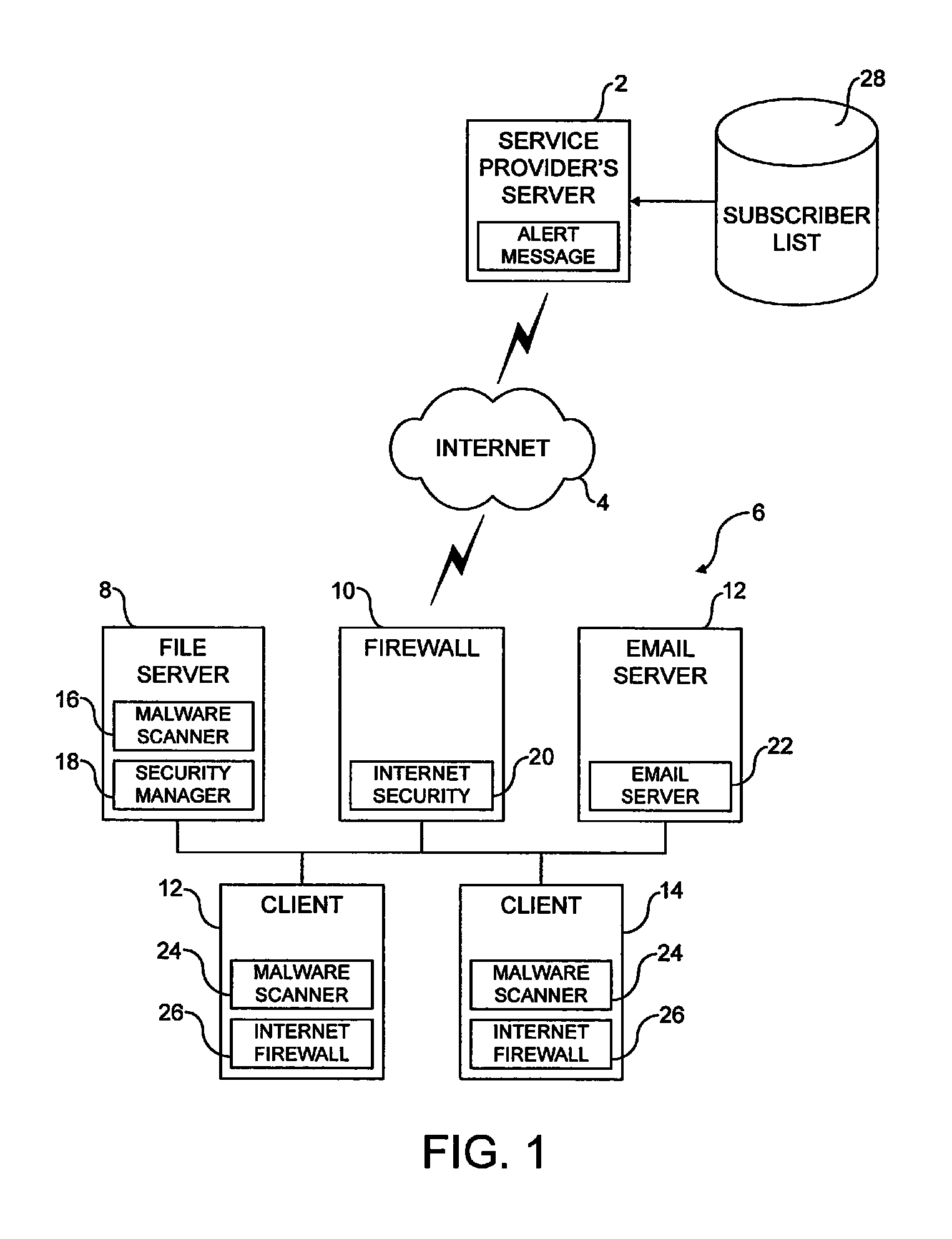
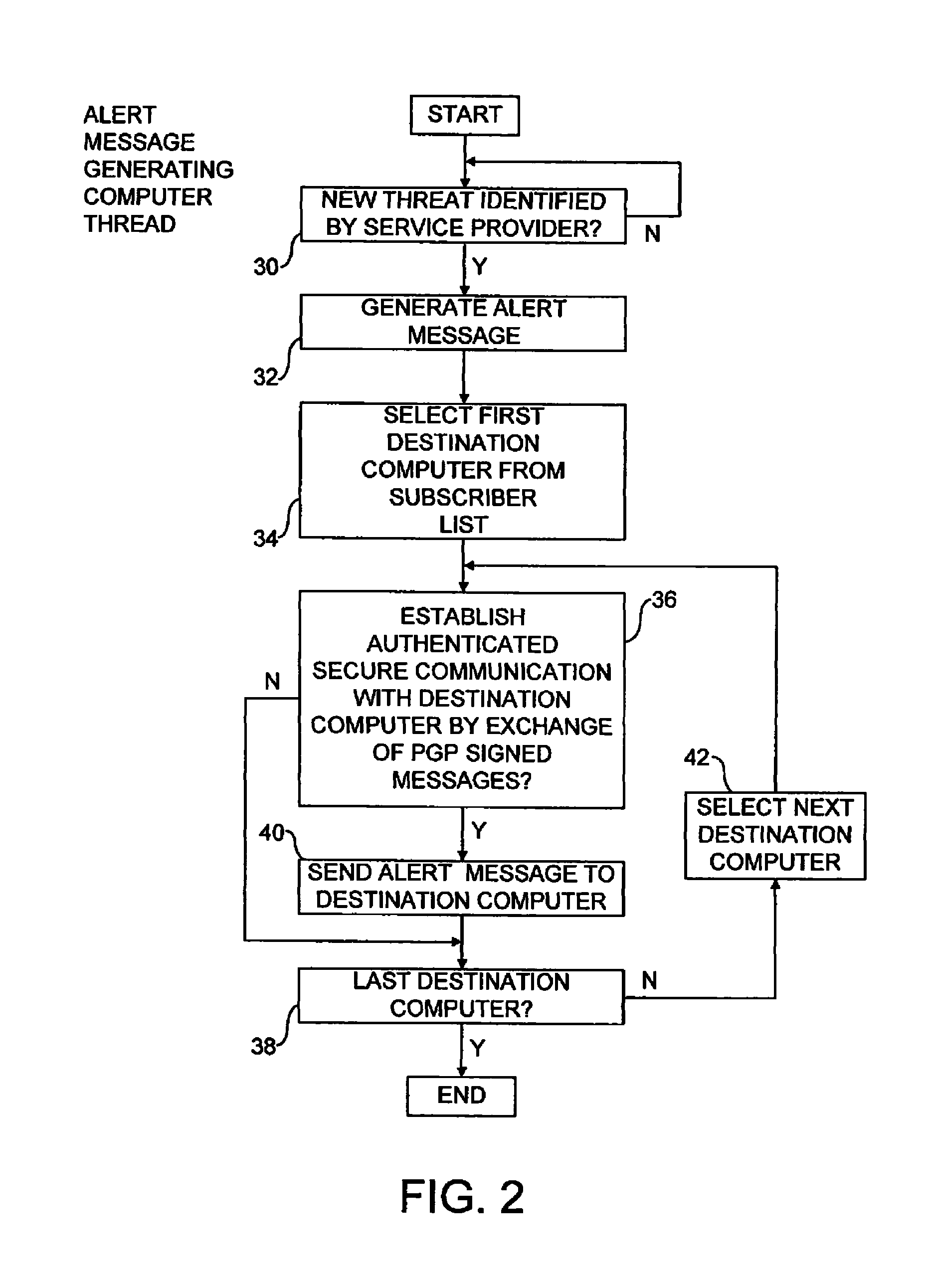
Alert message control of security mechanisms in data processing systems
ActiveUS8042178B1Memory loss protectionError detection/correctionData processing systemCountermeasure
An authenticated secure network communication link is established between an alert message generating computer 2 and a destination data processing system 6. The alert message sent specifies a risk threat level and a suggested countermeasure amongst other data. The destination computer 6 automatically responds to the alert message as controlled by its local response configuration parameters to trigger security actions of one or more security mechanisms, such as malware scanners, firewall scanners, security policy managers and the like.
Owner:MCAFEE LLC
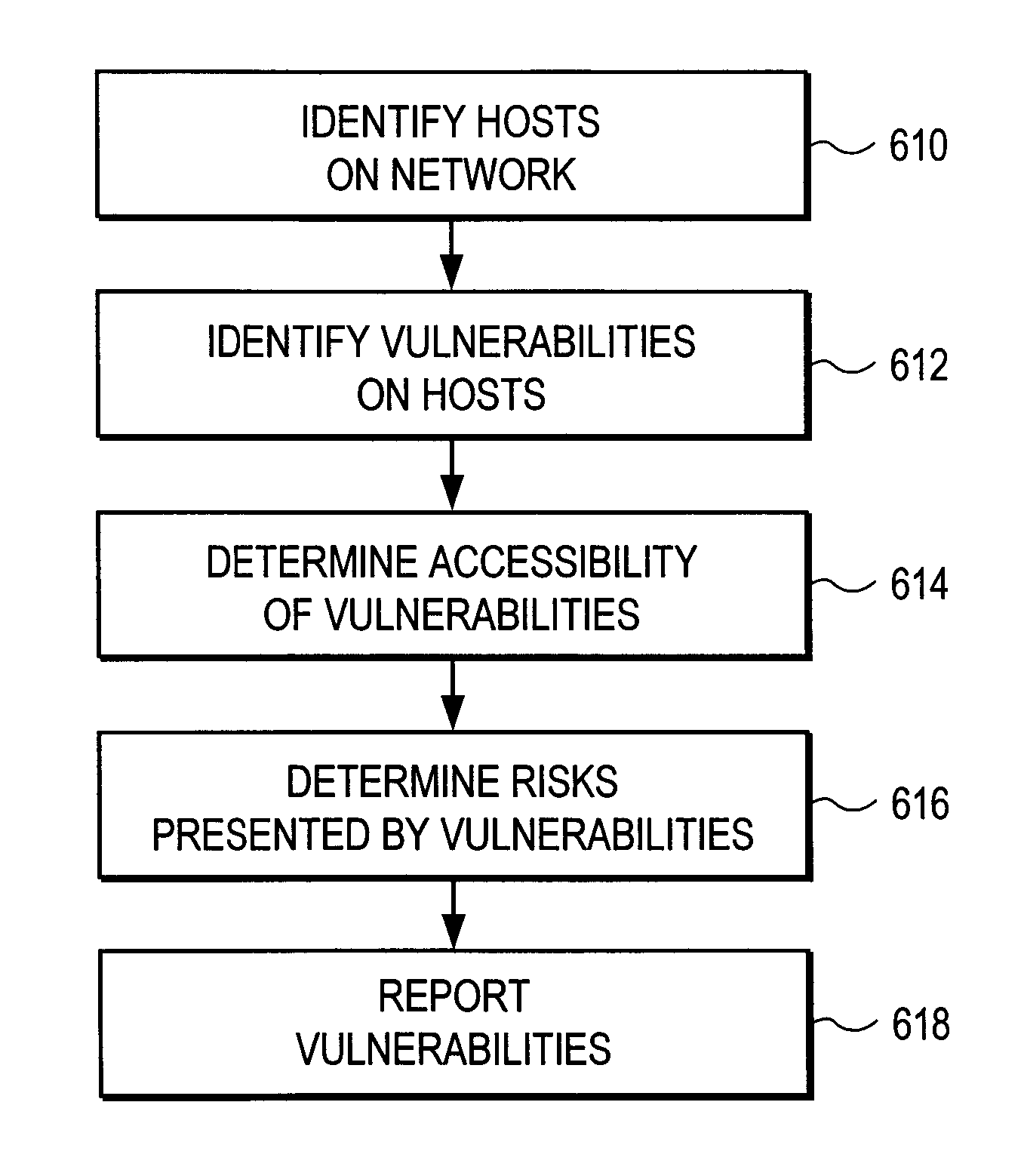
Prioritizing network security vulnerabilities using accessibility
ActiveUS8918883B1Memory loss protectionError detection/correctionInternet privacyBusiness enterprise
An enterprise network includes hosts running services. Some of the services have security vulnerabilities. There are one or more threat zones associated with the network. For example, a firewall may create two threat zones, one internal to the firewall and one external to it. A device profiler in the first threat zone profiles the hosts on the network and identifies the vulnerabilities that are present. A device profiler in the second threat zone determines which of the identified vulnerabilities are accessible from its zone. A risk module calculates the risk associated with a vulnerability based on the vulnerability's severity, threat level metrics for the threat zones, and an asset value of the host with the vulnerability. A reporting module prioritizes the vulnerabilities based on their risks.
Owner:TRIPWIRE
Automated Adaption Based Upon Prevailing Threat Levels in a Security System
InactiveUS20100156628A1Easy to adjustHigh riskIndication of parksing free spacesIndividual entry/exit registersRisk levelThreat level
Four threat levels reflect a prevailing risk and can be adjusted, for example, when local authorities advise of an increased likelihood of terrorist activity. Thus, a higher threat level in such system indicates a higher level of risk to a particular facility. In an embodiment of the invention, the behavior of the system changes with a simple adjustment to the threat level.
Owner:TITAN HLDG
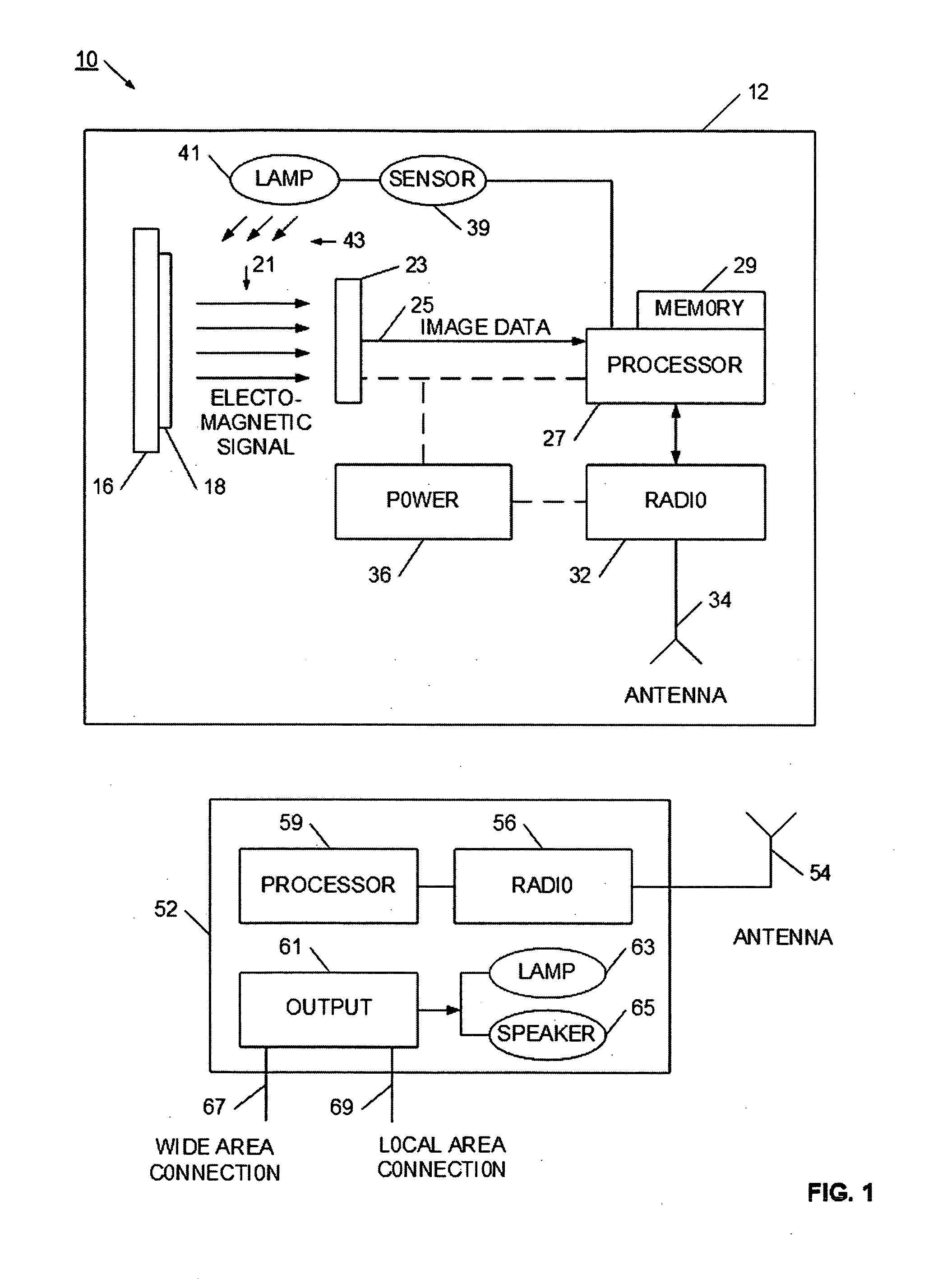
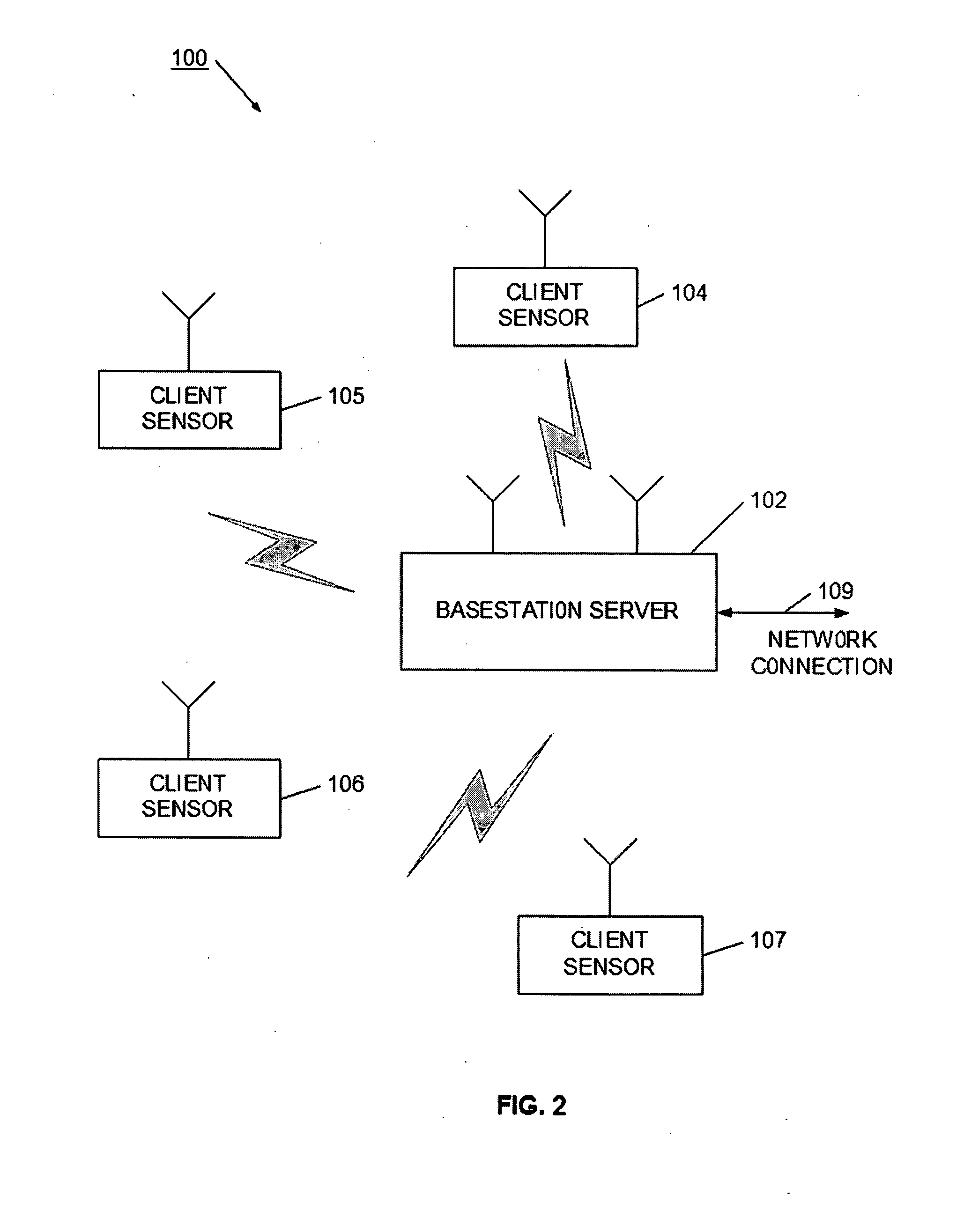
Remote biological, chemical and explosive detector
InactiveUS20060249683A1EffectiveRapid deploymentMaterial analysis by observing effect on chemical indicatorMicrobiological testing/measurementOptical propertyThreat level
A distributed detector system is provided for remotely detecting agents indicating the presence of particular biological, explosive, or chemical targets. The distributed detector system may be used for security threat detection, manufacturing or environmental monitoring, or medical assaying. In the detection system, a central server or base station wirelessly communicates with a set of distributed detectors. In this way, the central server or base station is able to aggregate detection information, as well as apply additional processing and analysis to data collected at the detectors. Each detector has a reactive material, such as a silicon-polymer, that changes an optical property in the presence of a target agent. A camera is positioned to take images of the reactive material from time to time, and has local processing to determine when the reactive material has likely changed. In some cases, the detector may have sufficient processing power to classify the change according to its urgency or threat level. The detector wirelessly communications to the central server or base station, and appropriate alerts or notifications can be generated.
Owner:AVAAK
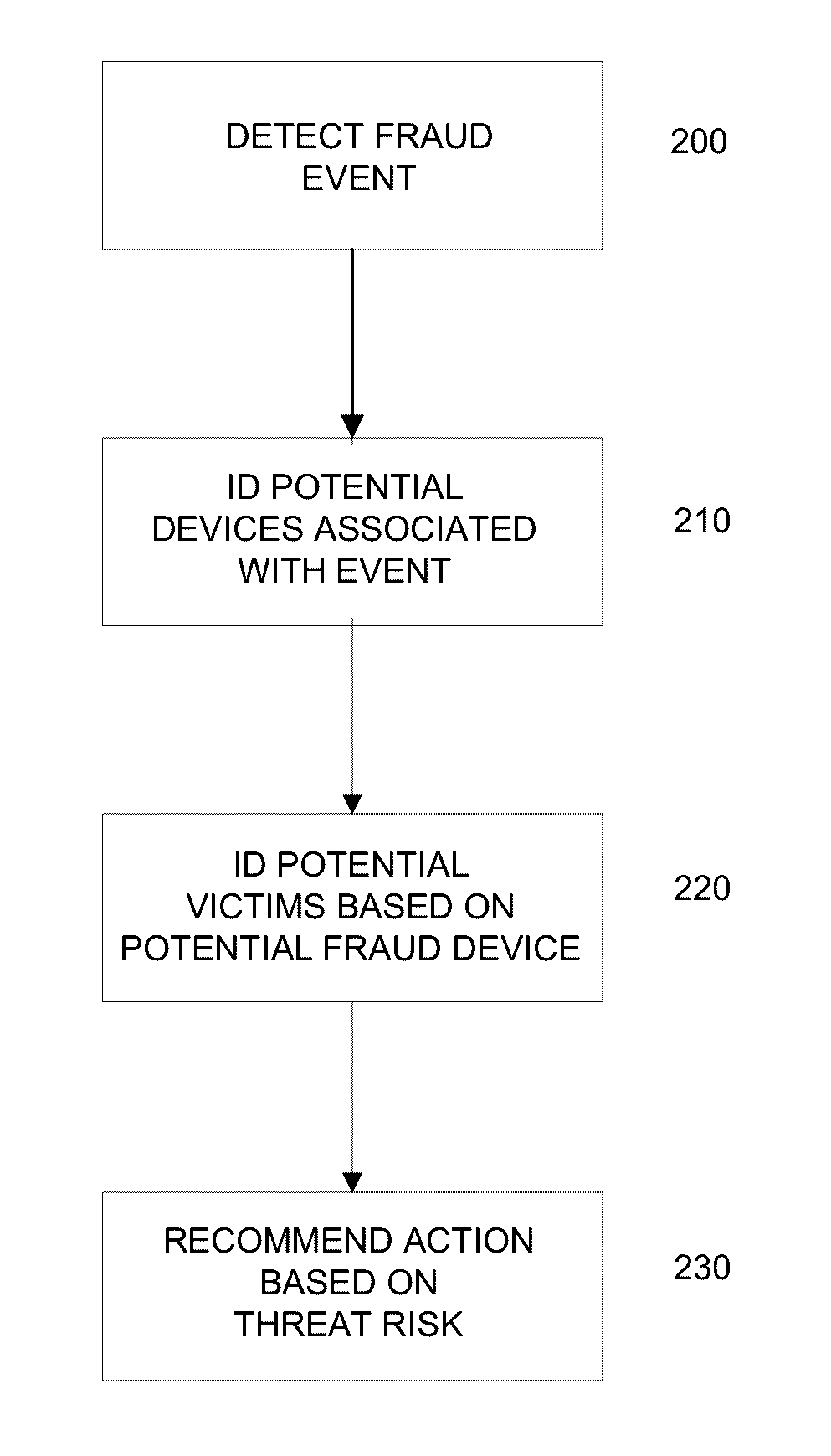
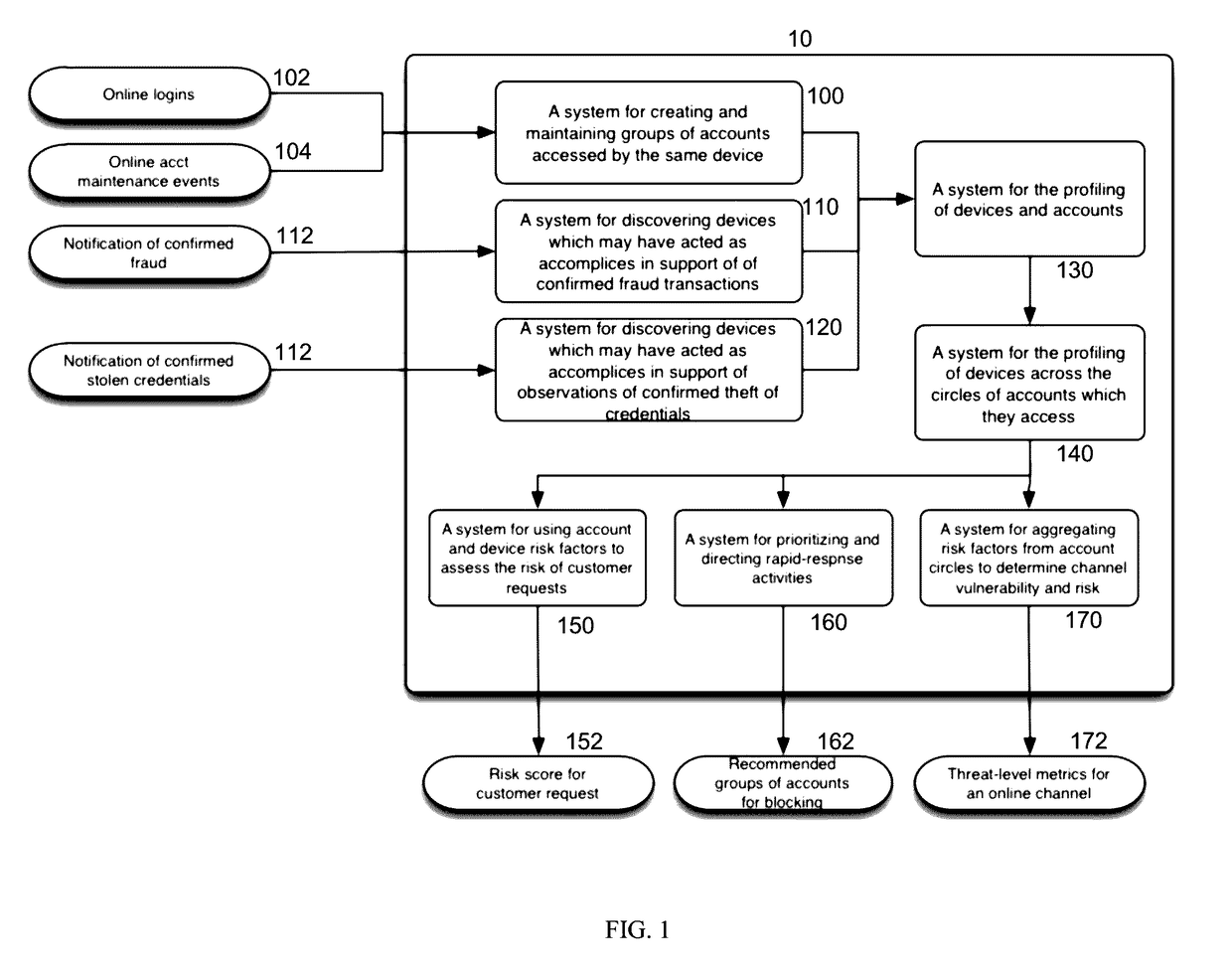
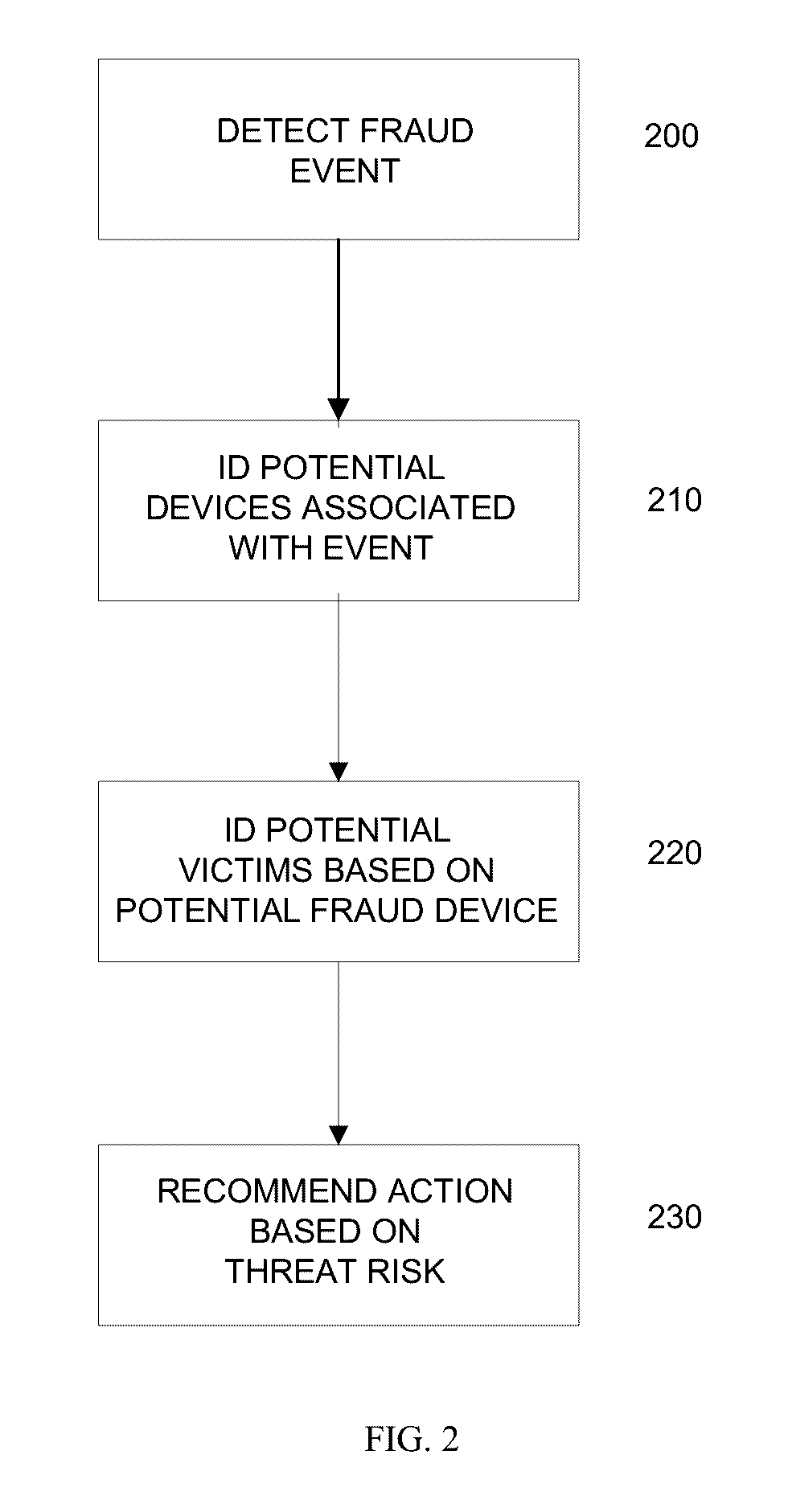
Methods and systems for fraud containment
Systems and methods for fraud containment are provided in accordance with an embodiment of the invention. A fraud event may be detected. One or more devices that may be used in perpetrating the fraud event may be detected. Additionally one or more potential fraud victims, who may be grouped into victim circles may be detected. The threat level to the victims and / or victim circles may be assessed. In some instances, behavioral profiles may be utilized to make fraud assessments. Based on the threat level, recommendations for fraud containment responses may be provided.
Owner:THE 41ST PARAMETER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com