Patents
Literature
183 results about "Network Endpoint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
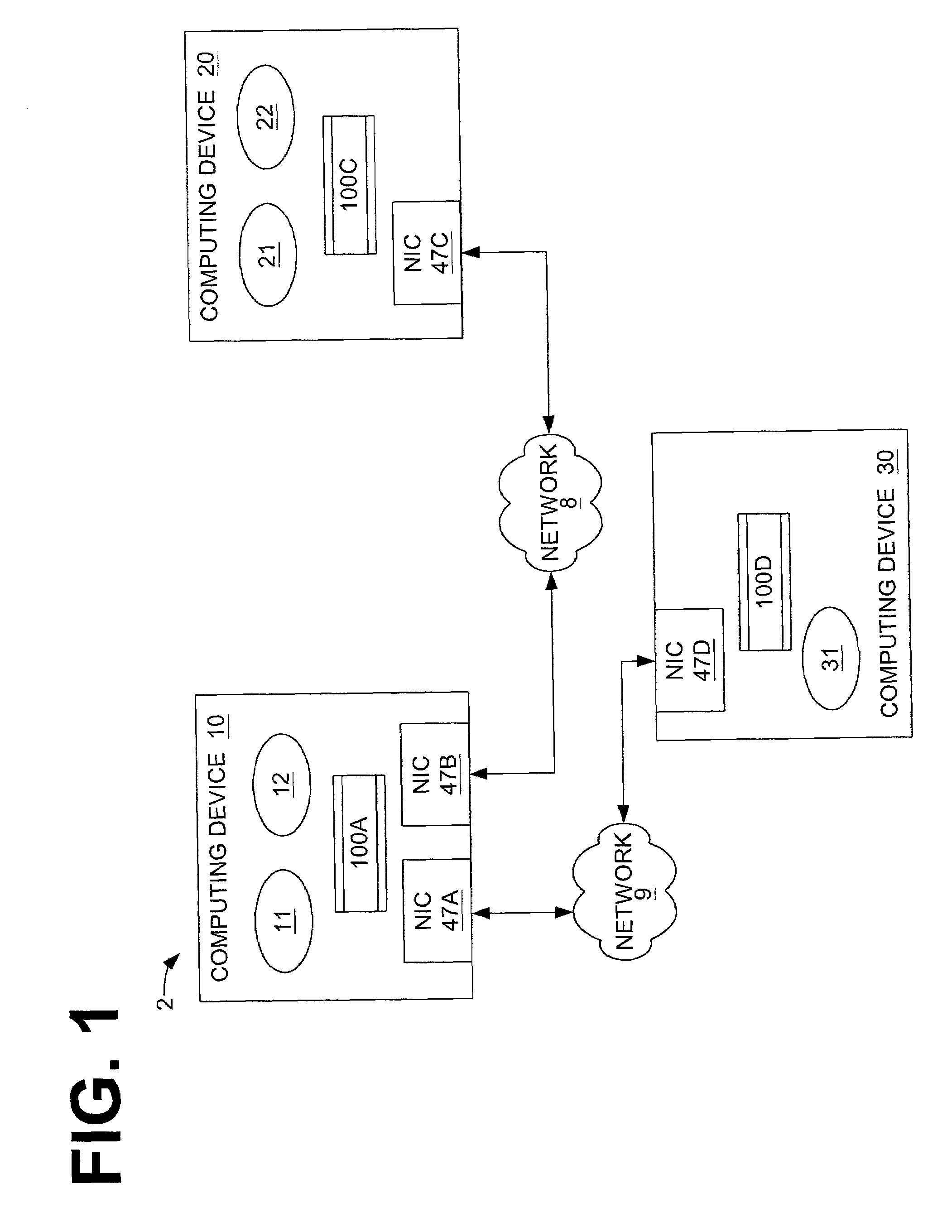
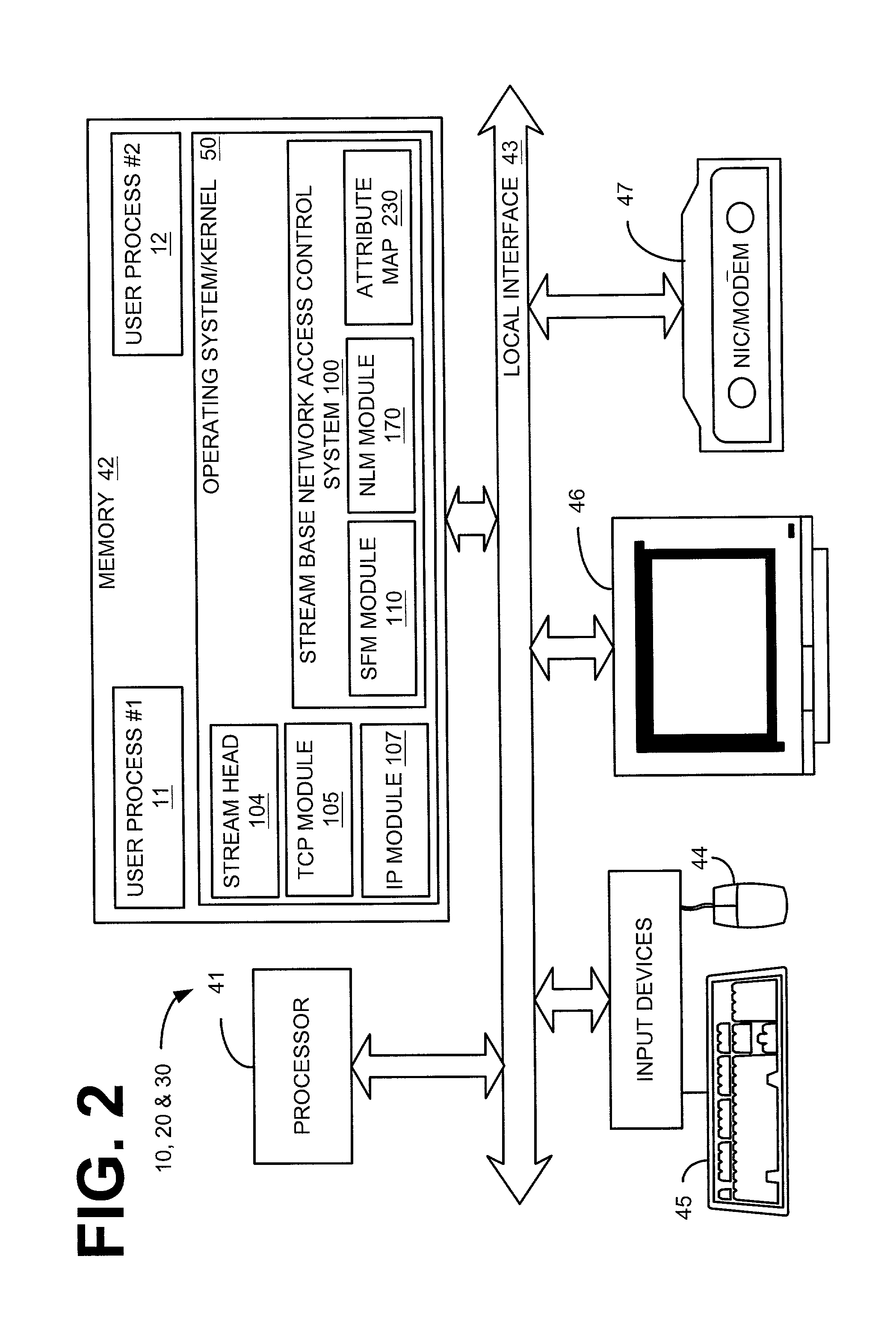
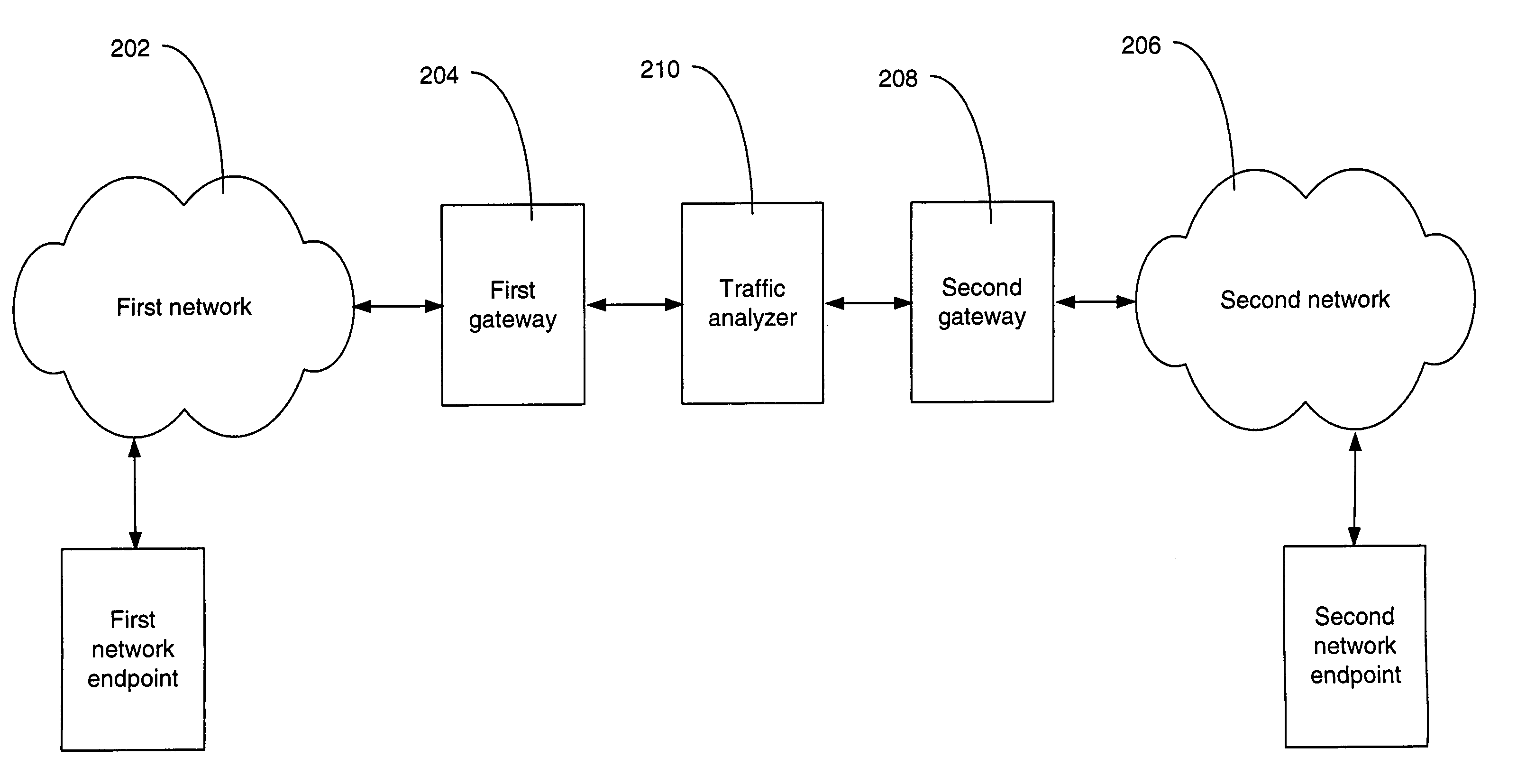
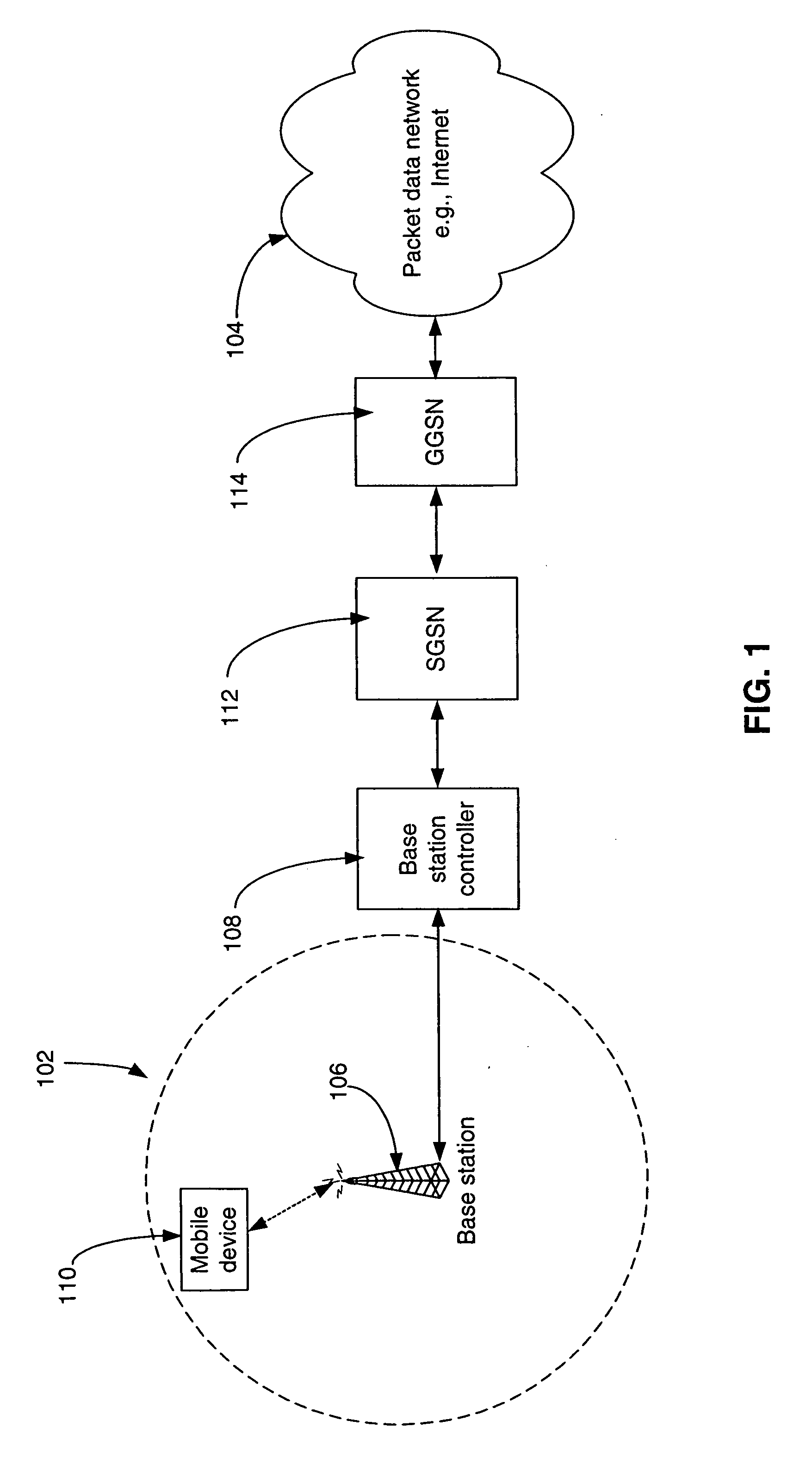
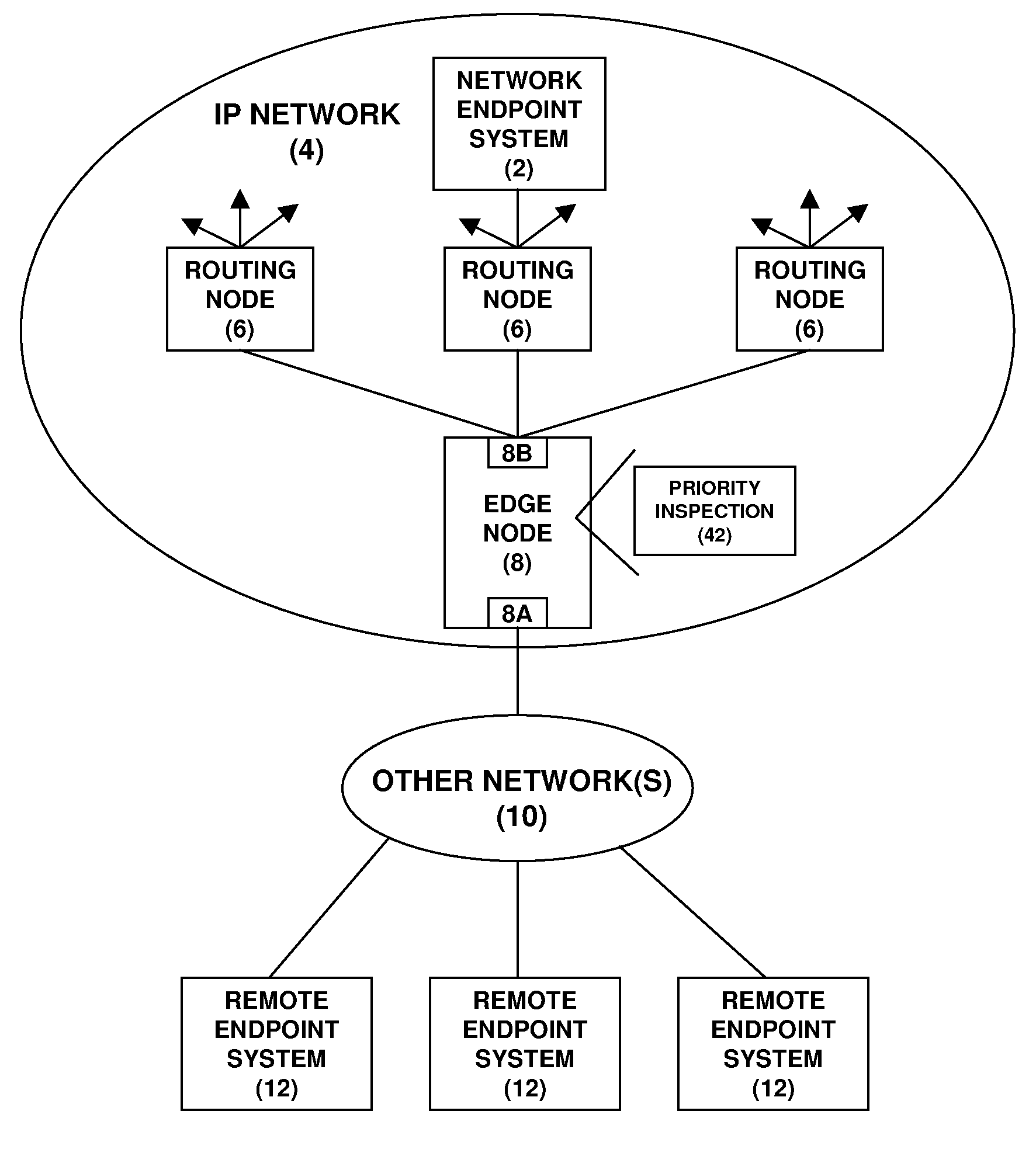
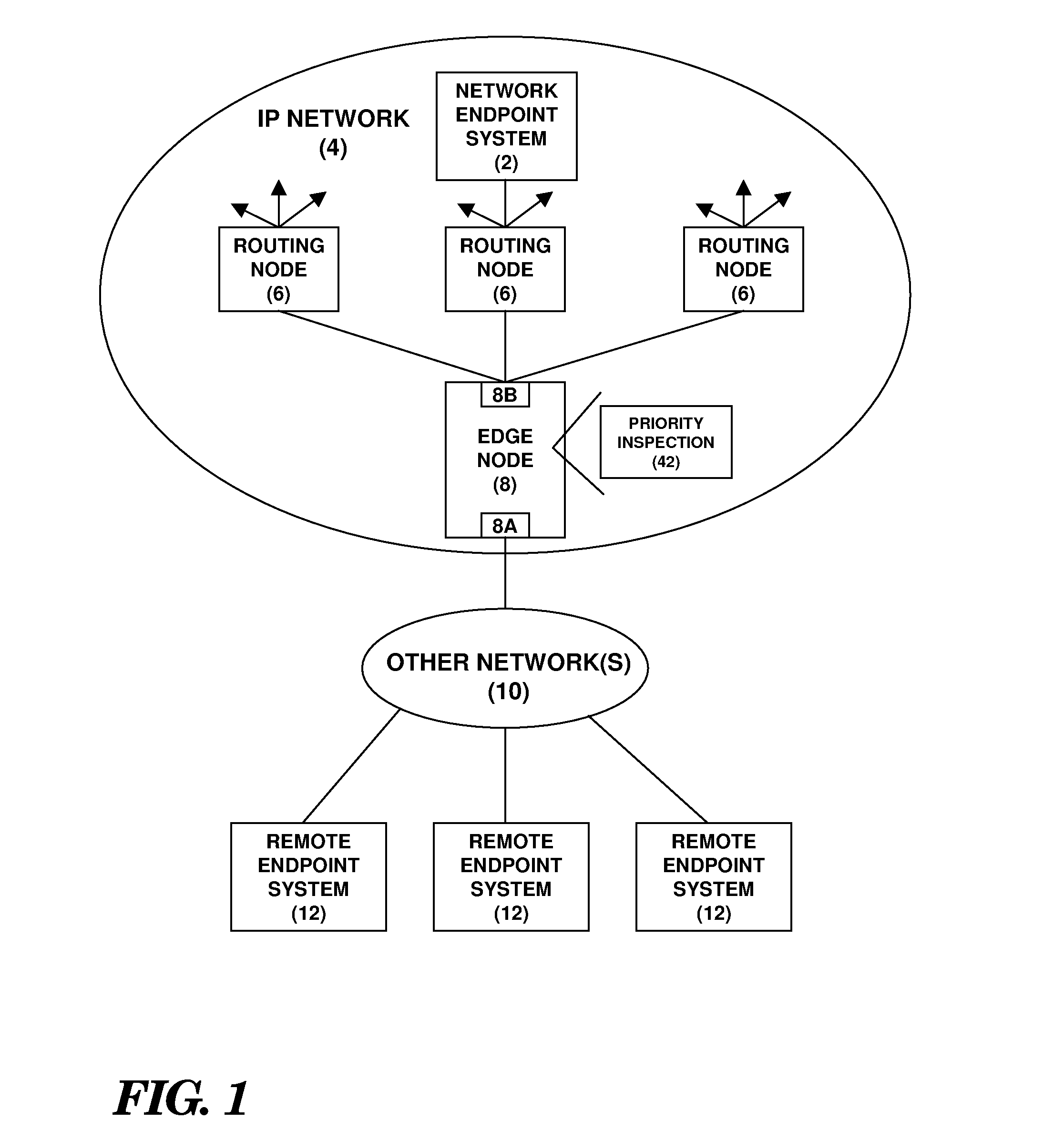
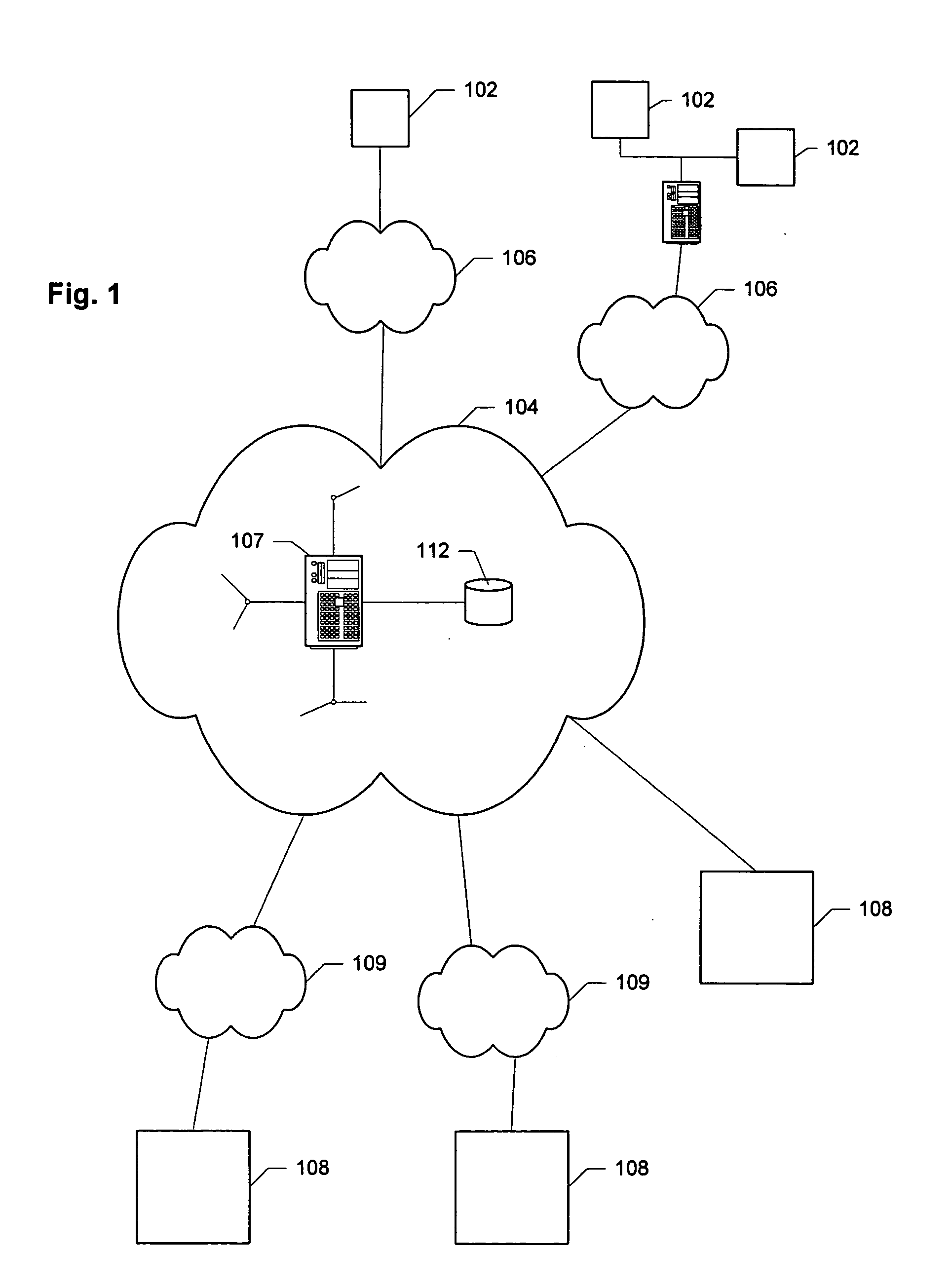
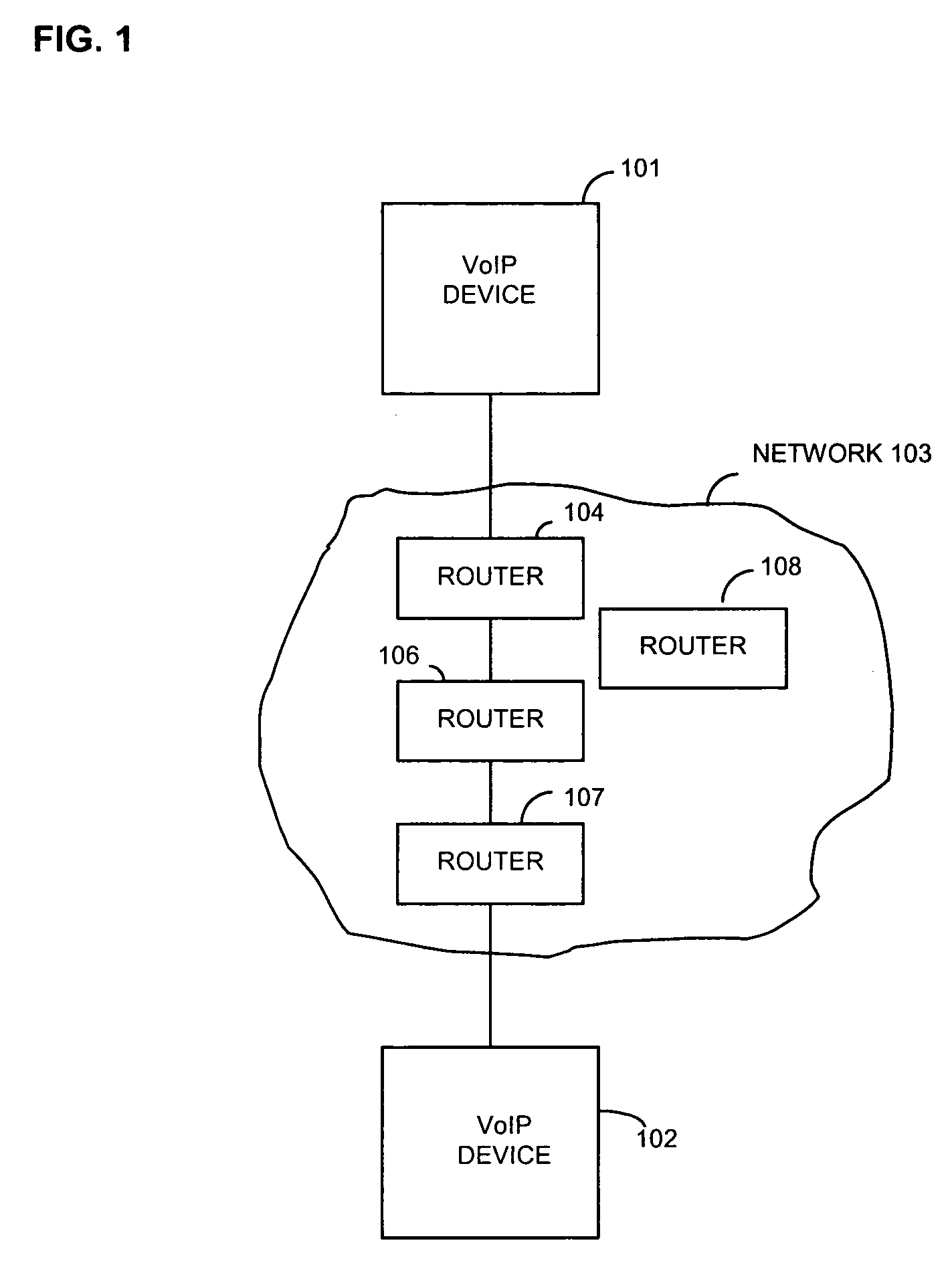
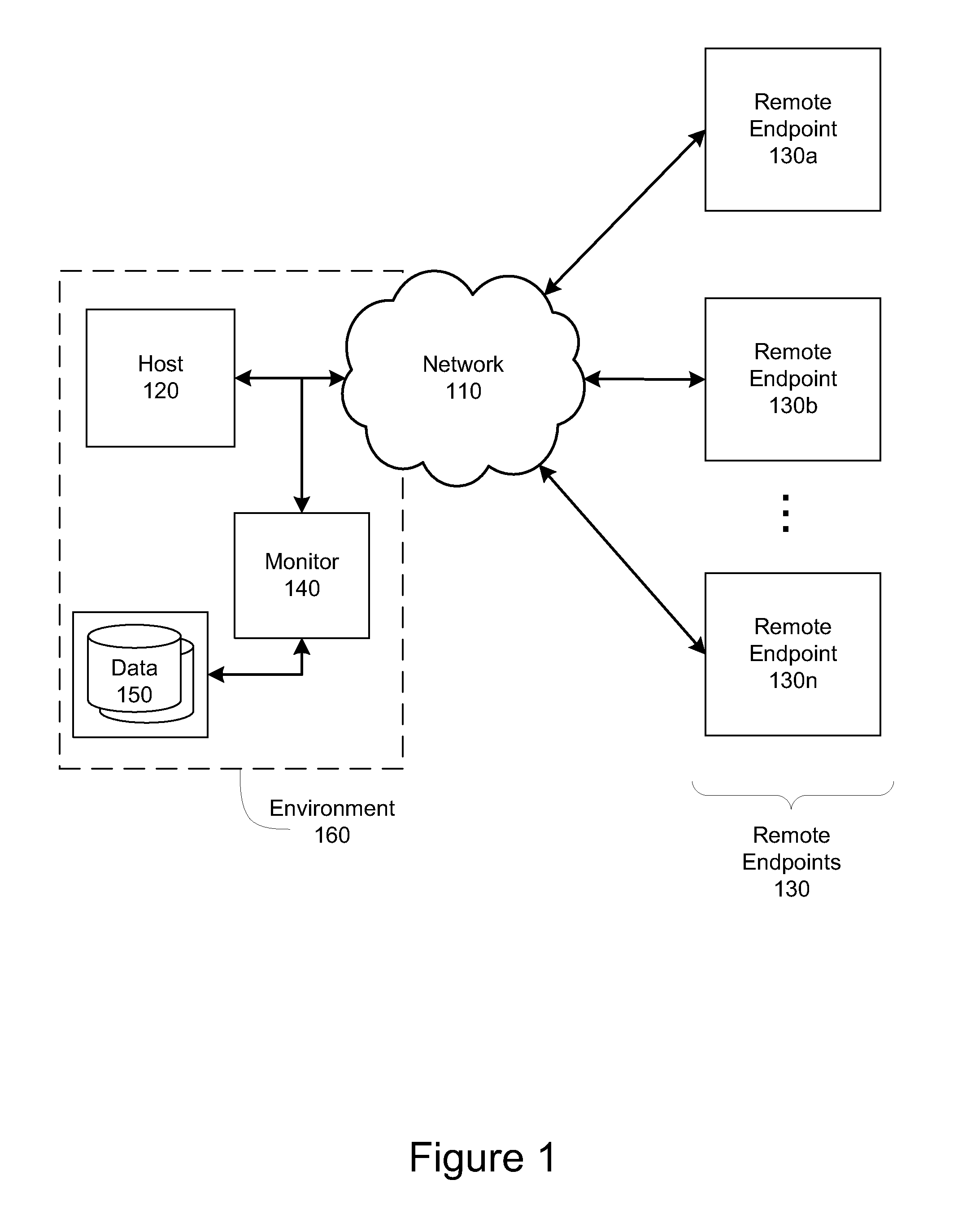
An individual user device on a data communication network.
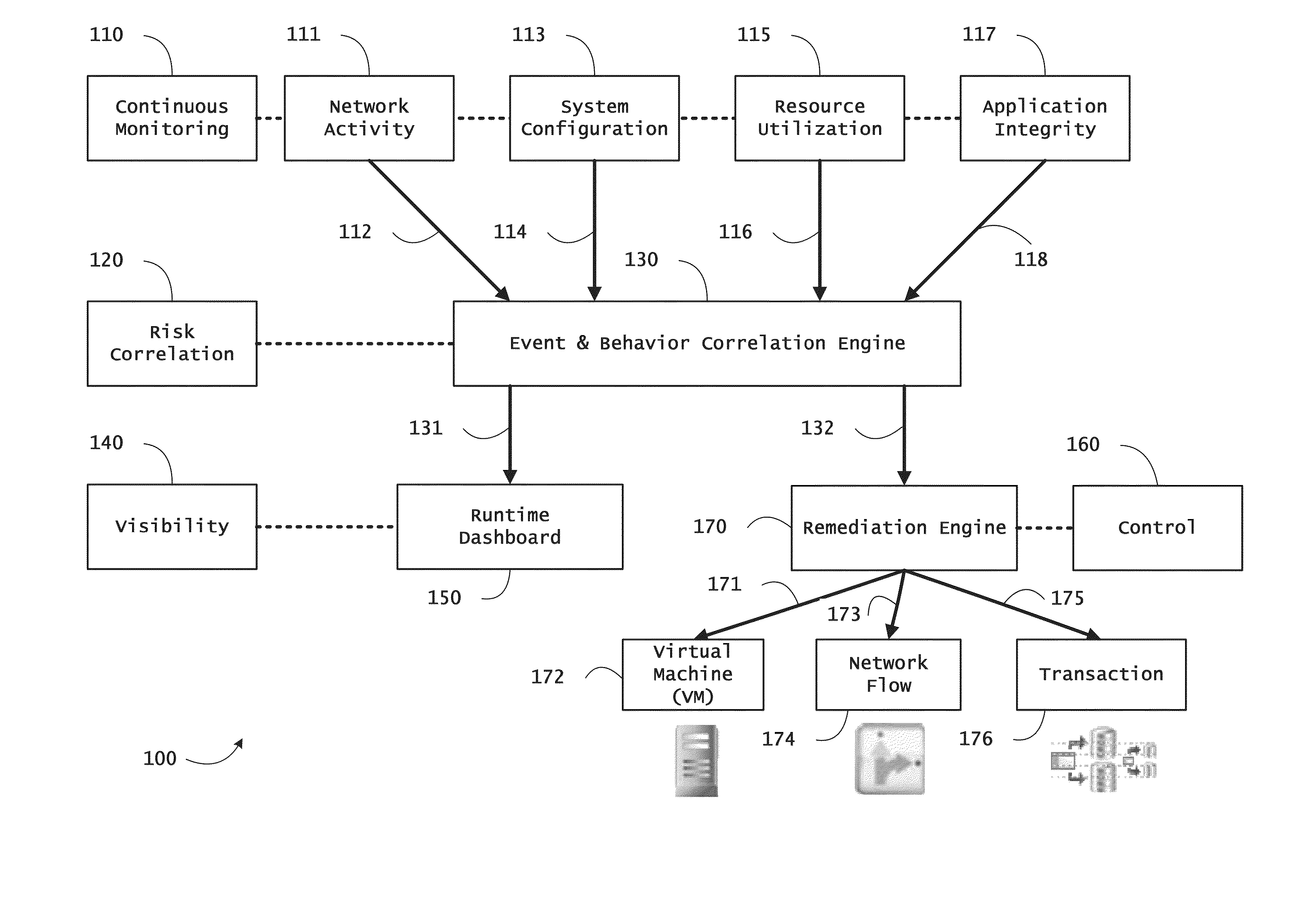
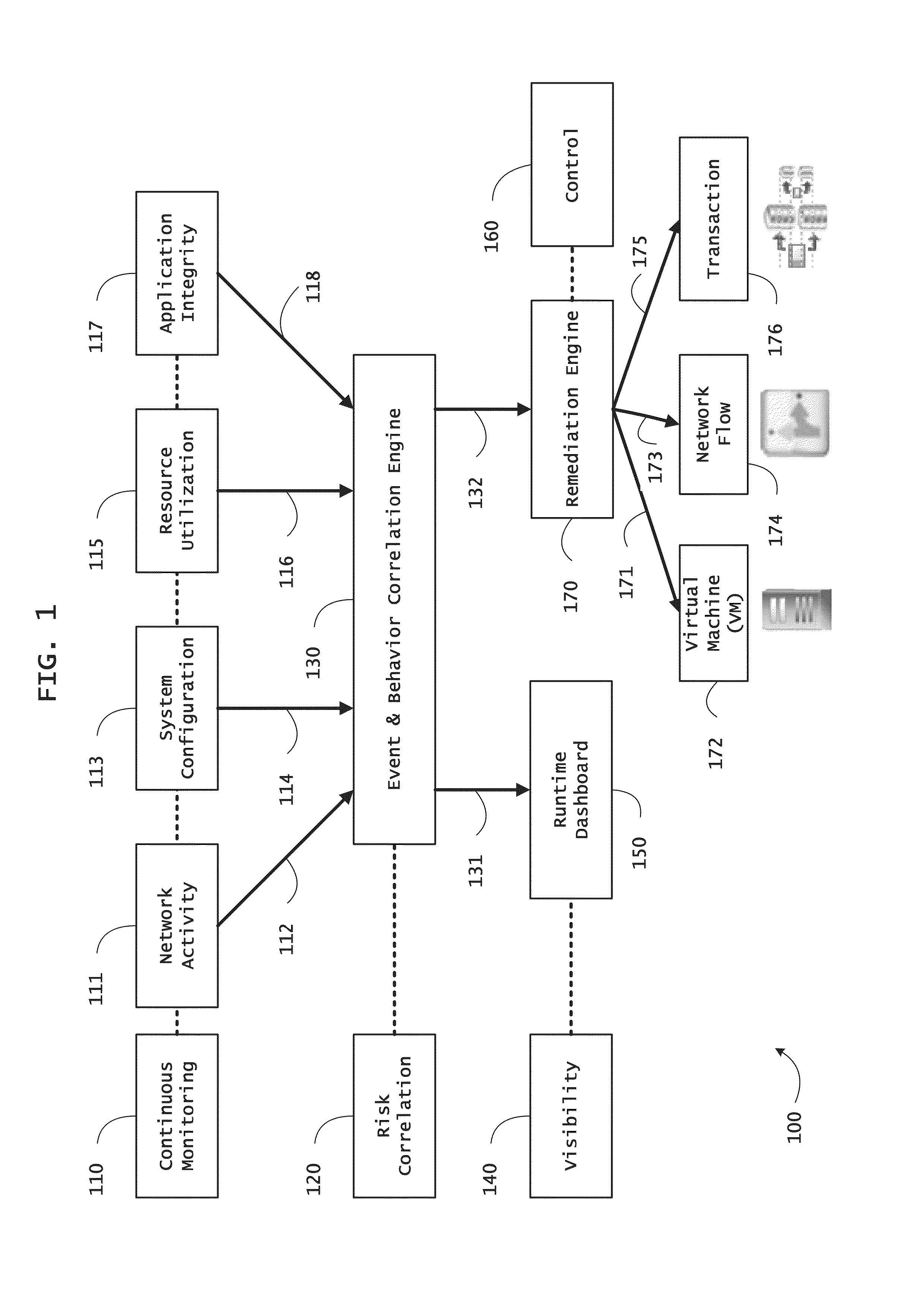
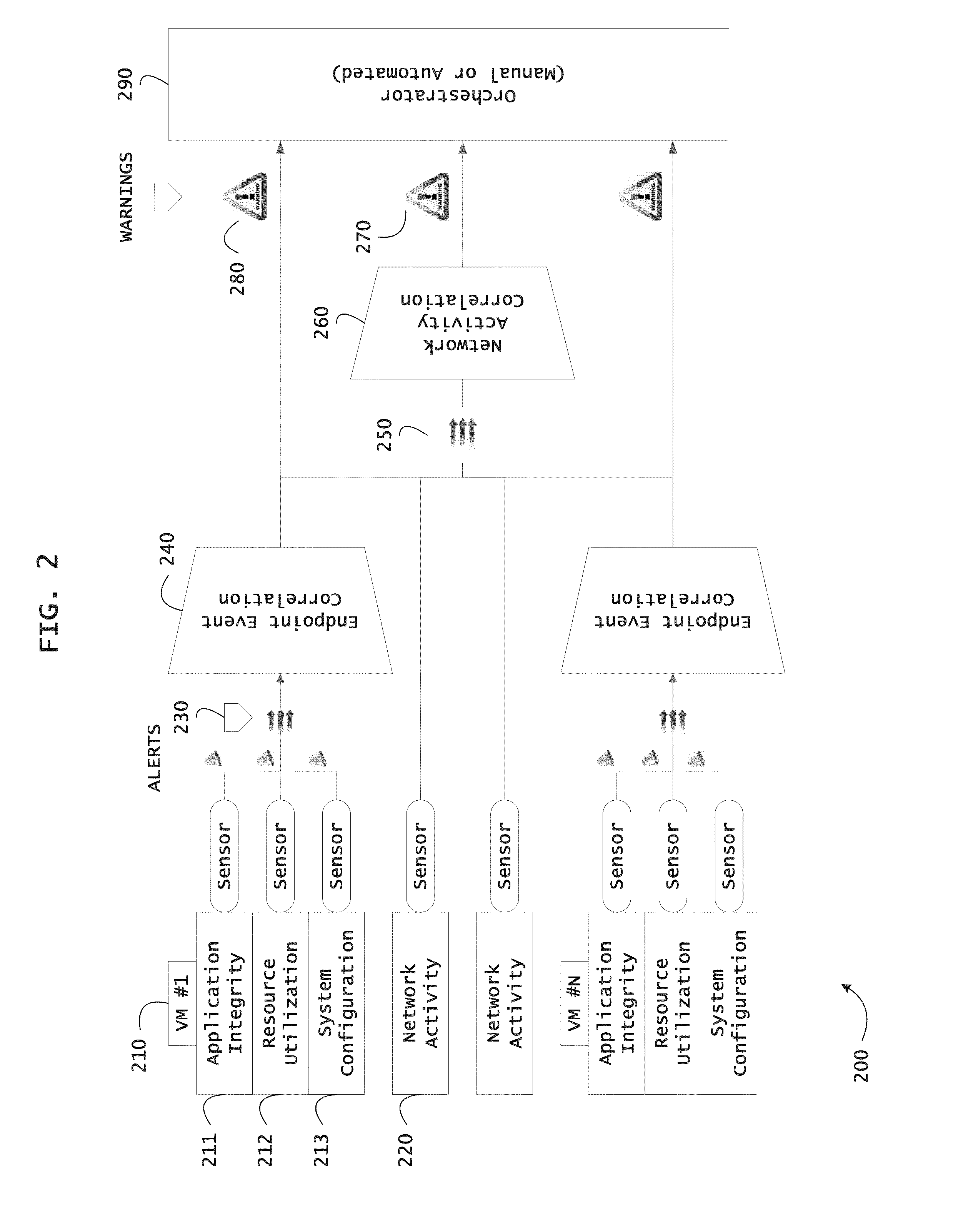
Systems and methods for threat identification and remediation
ActiveUS20130298244A1Memory loss protectionError detection/correctionOrchestrationApplication software
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Systems and methods for threat identification and remediation for computing platforms based upon reconnaissance-based intelligence correlation and network / application monitoring are disclosed. In an embodiment, a method provides runtime operational integrity of a system by receiving: a dynamic context including endpoint events; and network endpoint assessments. The method generates temporal events based on the network endpoint assessments and correlates the endpoint events and temporal events before generating an integrity profile for the system. In another embodiment, flow level remediation is provided to isolate infected or compromised systems from a computing network fabric using a network trust agent, an endpoint trust agent, and a trust orchestrator.
Owner:TAASERA LICENSING LLC
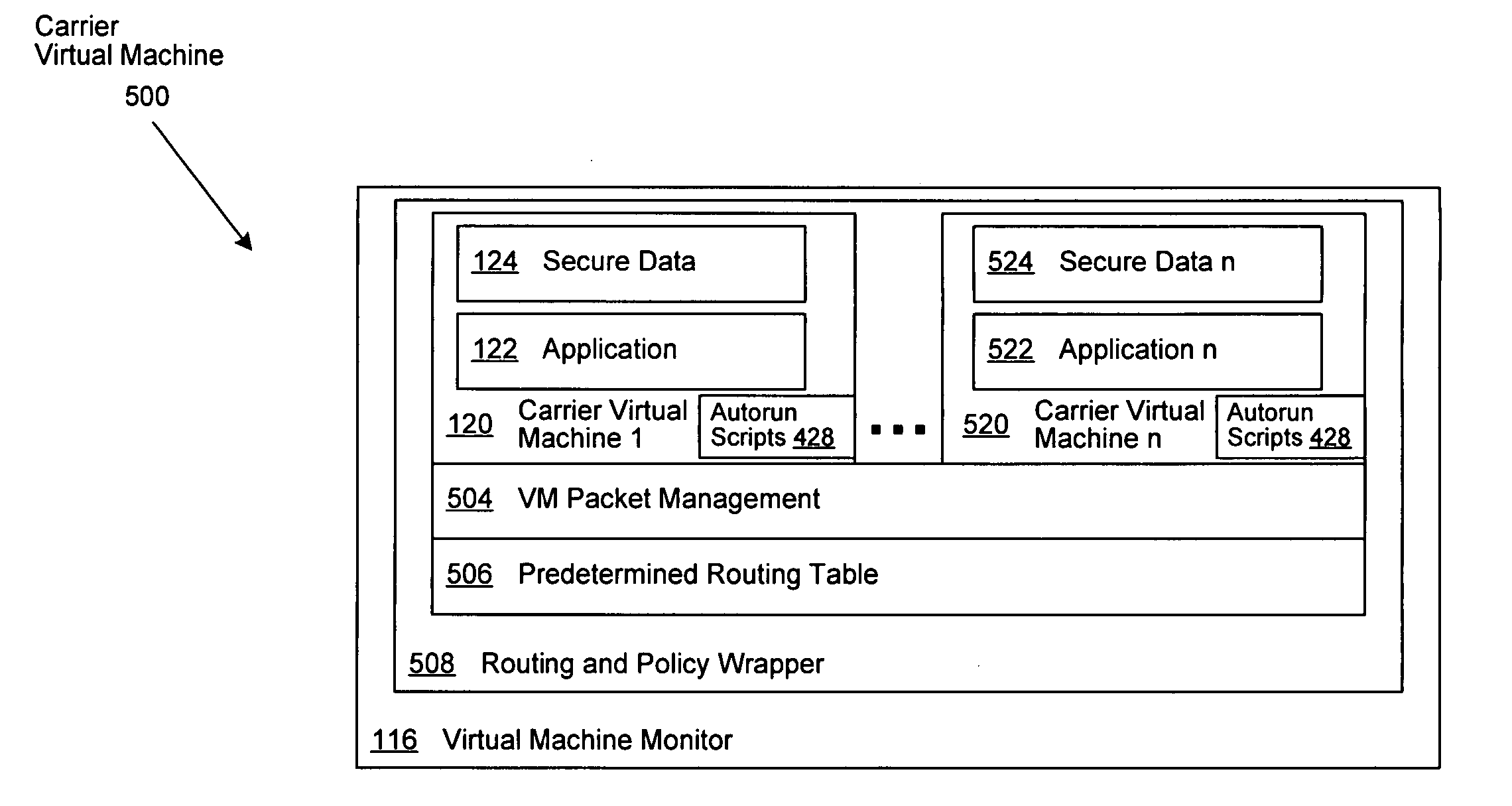
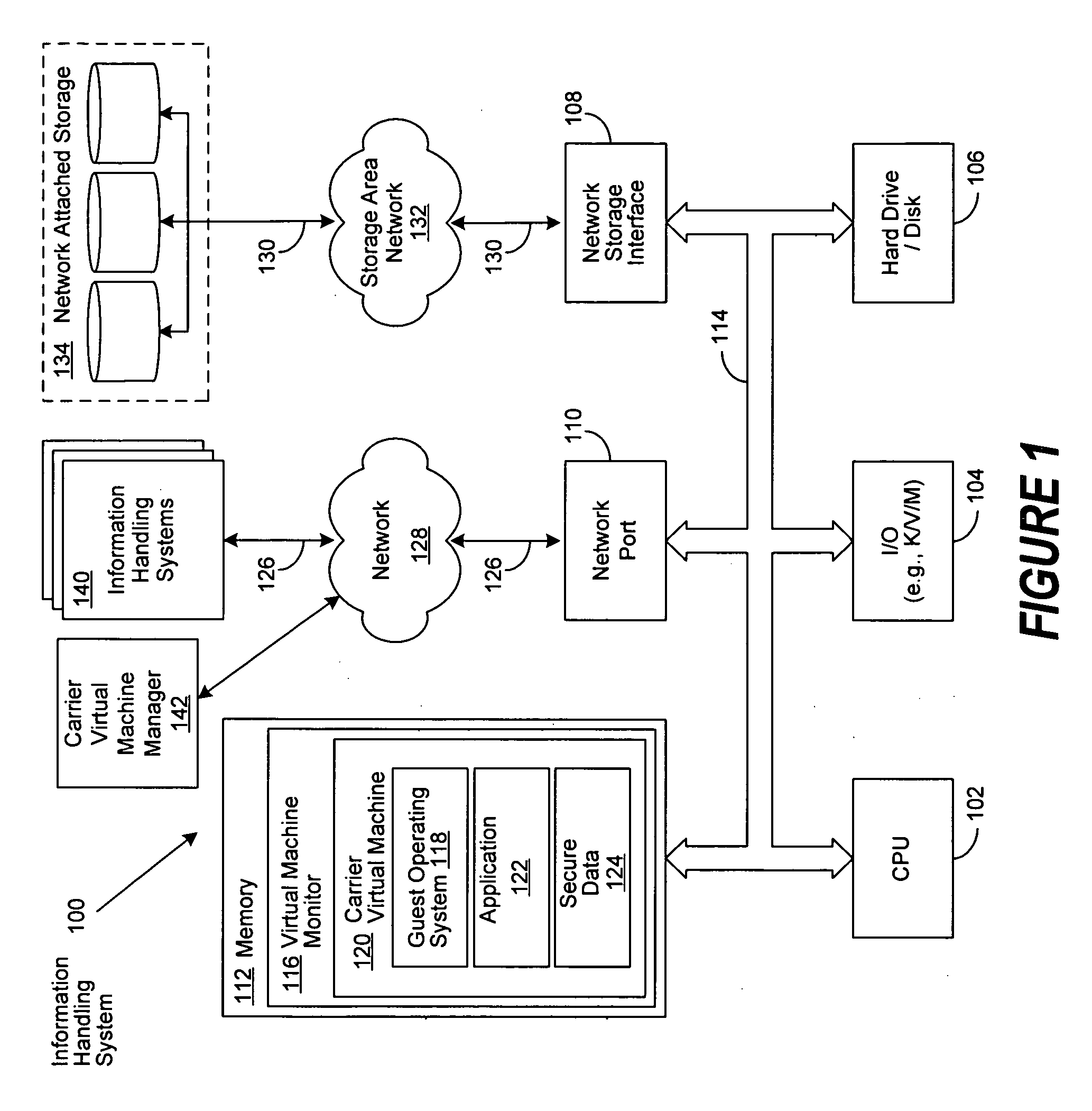
Virtual machine based network carriers
InactiveUS20070079307A1Environment safetyTransmissionSoftware simulation/interpretation/emulationData packData set
A system and method is disclosed for the secure transfer of data by carrier virtual machines between participating physical hosts through a virtual network (VNET) implemented on one or more internal and / or external networks. The method of the invention can provide additional security controls, comprising parameters that may include, but are not limited to, time-to-live (TTL), access control lists (ACLs), usage policies, directory roles, etc. Additionally, access to one or more of a plurality of carrier virtual machine payloads by security groups, individual access, subdivided individual access, and MIME-like subdivision of a VM-encapsulated payload may be controlled, thereby providing the carrier VM the ability to carry many secured payloads. In addition, VM packets, a group of packets, a single VM, or subpackets within a VM between network endpoints, or at a predetermined intermediary network point, may be quarantined to realize further security. Individual or combinations of these functionalities on carrier virtual machines, and by extension, application and / or one or more sets of secure data may be implemented.
Owner:DELL PROD LP
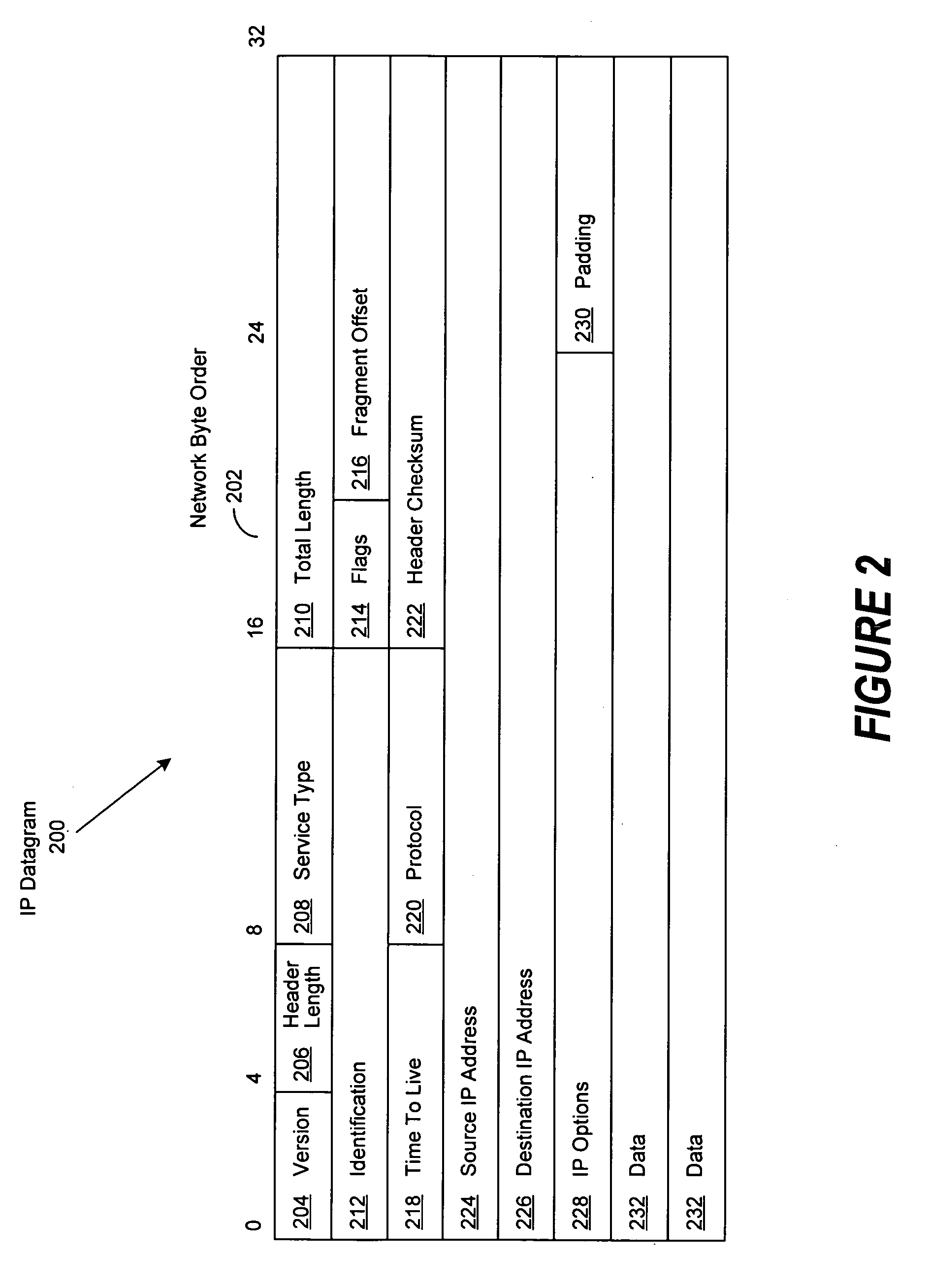
Method of determining path maximum transmission unit
ActiveUS7542471B2Digital computer detailsData switching by path configurationIP fragmentationStandard methods
Network endpoints using TCP / IP operate to determine the maximum transmission unit (MTU) of the path between them. This determination is done so as to avoid the expensive IP fragmentation that will occur when transitioning links with a smaller MTU size. The standard method of determining the path MTU (PMTU) has several known deficiencies, including: inefficient use of bandwidth as proper operation will likely result in the loss of one or more packets and difficulty of implementation as the reverse channel communication mechanism, reception of ICMP messages indicating the discarding of unfragmentable packets, is frequently blocked by firewalls and other security apparatus. A method of determining the PMTU between intermediate proxies is disclosed that does not require reception of ICMP messages or the inefficient use of bandwidth due to the presumed dropping of packets with valid data.
Owner:CITRIX SYST INC
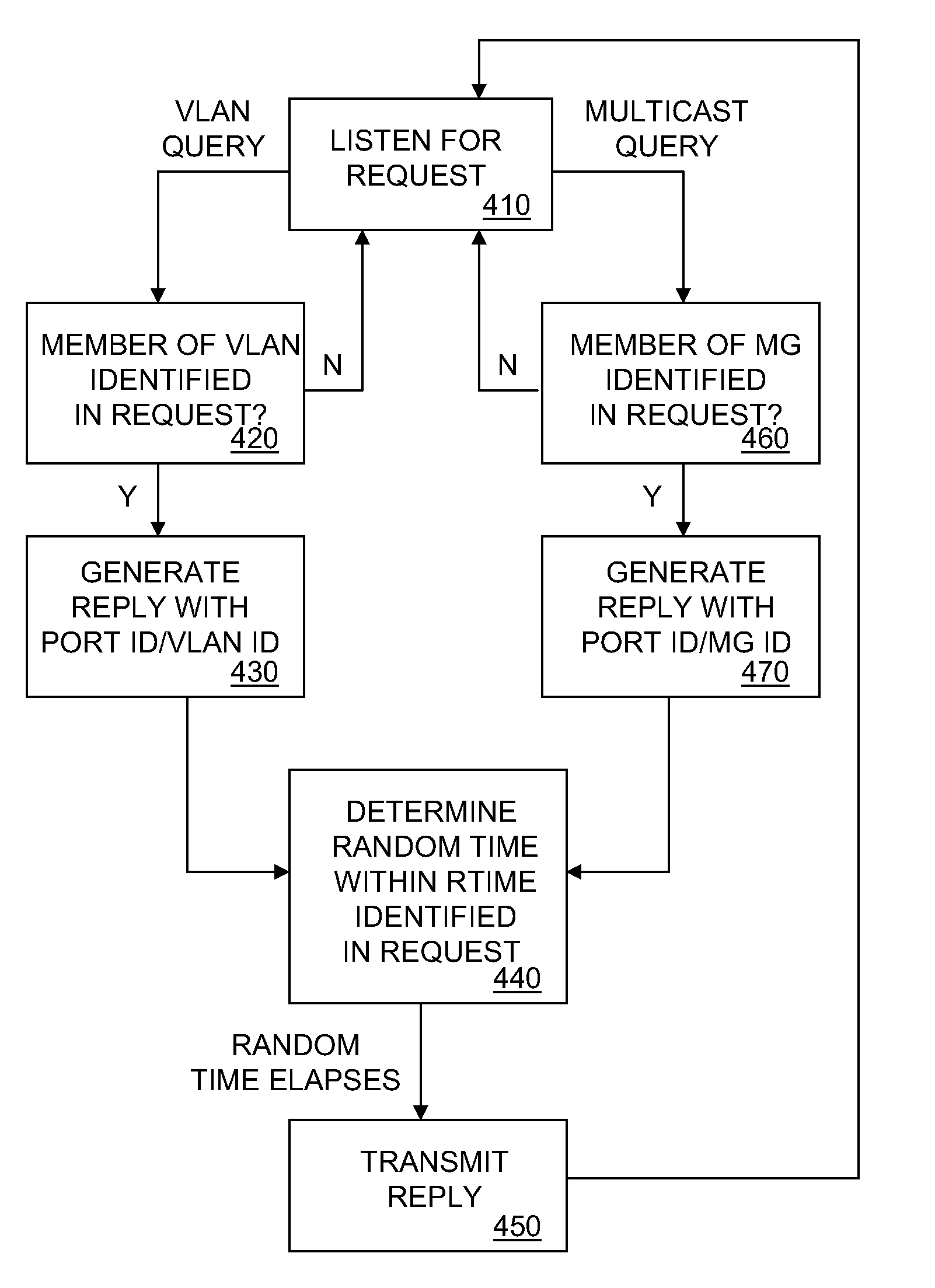
Logical Group Endpoint Discovery for Data Communication Network
InactiveUS20070223493A1Efficient learning processEfficient detectionNetworks interconnectionMulticast addressDistributed computing
A method and system for logical group endpoint discovery in a data communication network is disclosed. A network endpoint receives from a source a request identifying a logical group and determines whether a port associated with the endpoint is a member of the logical group. If a port associated with the endpoint is a member of the logical group, the endpoint transmits to the source a reply identifying the port and the logical group. The request may be multicast while the reply may be unicast. The logical group may be a VLAN or a multicast group. The source and endpoint are preferably 802.1 ag maintenance endpoints. The request may include an IEEE 802.1 ag continuity check multicast address as a destination address.
Owner:ALCATEL LUCENT SAS
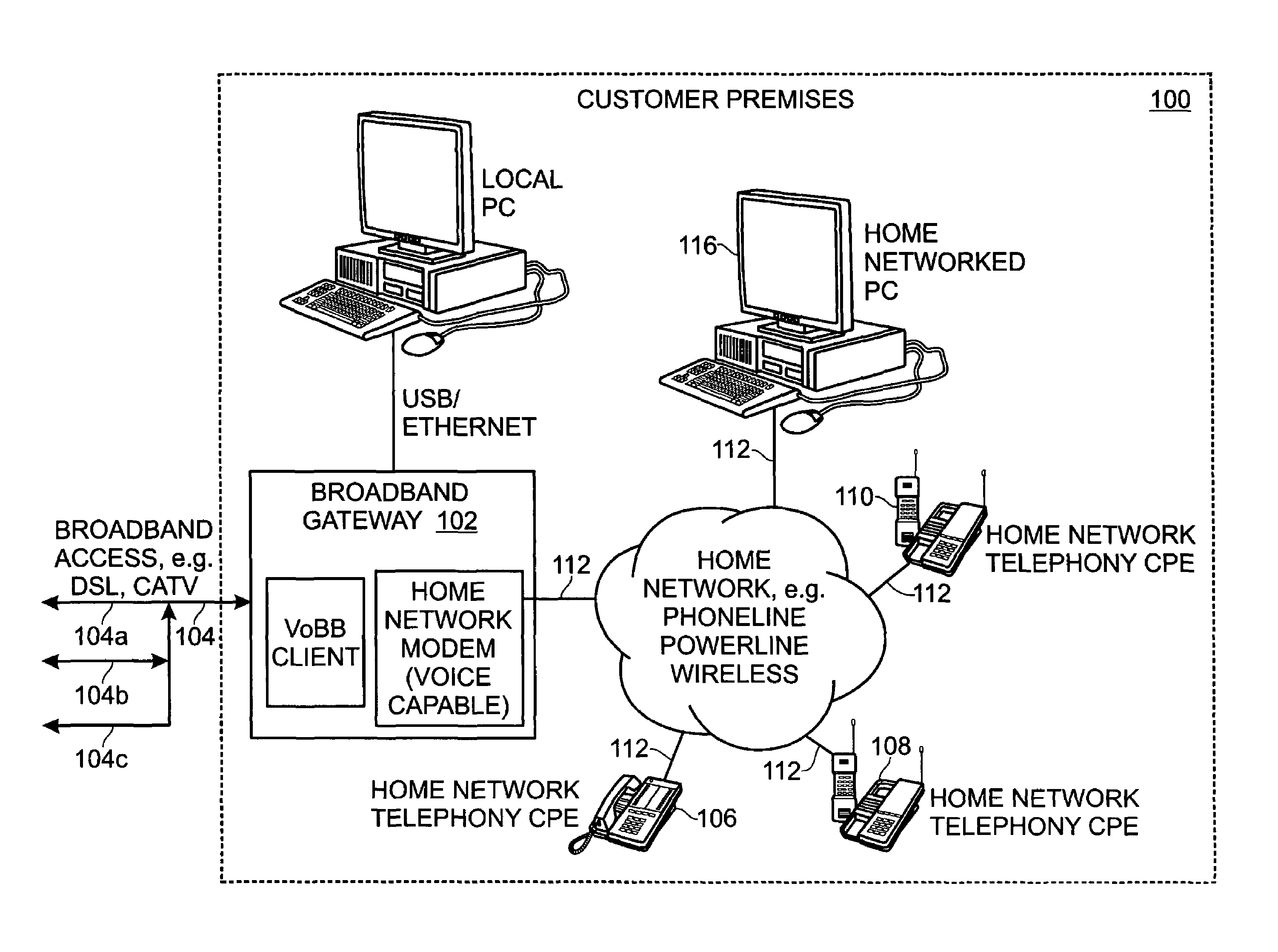
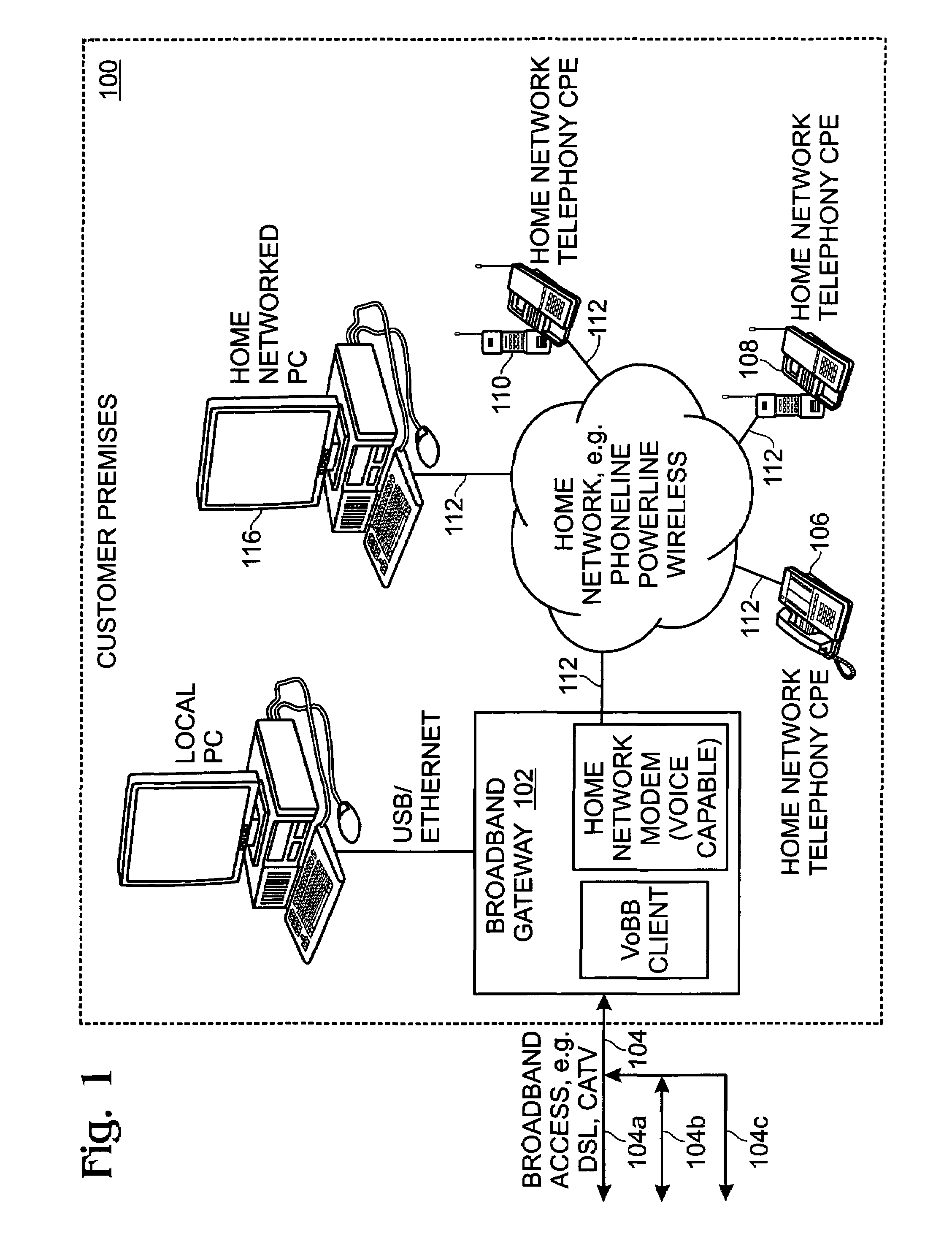
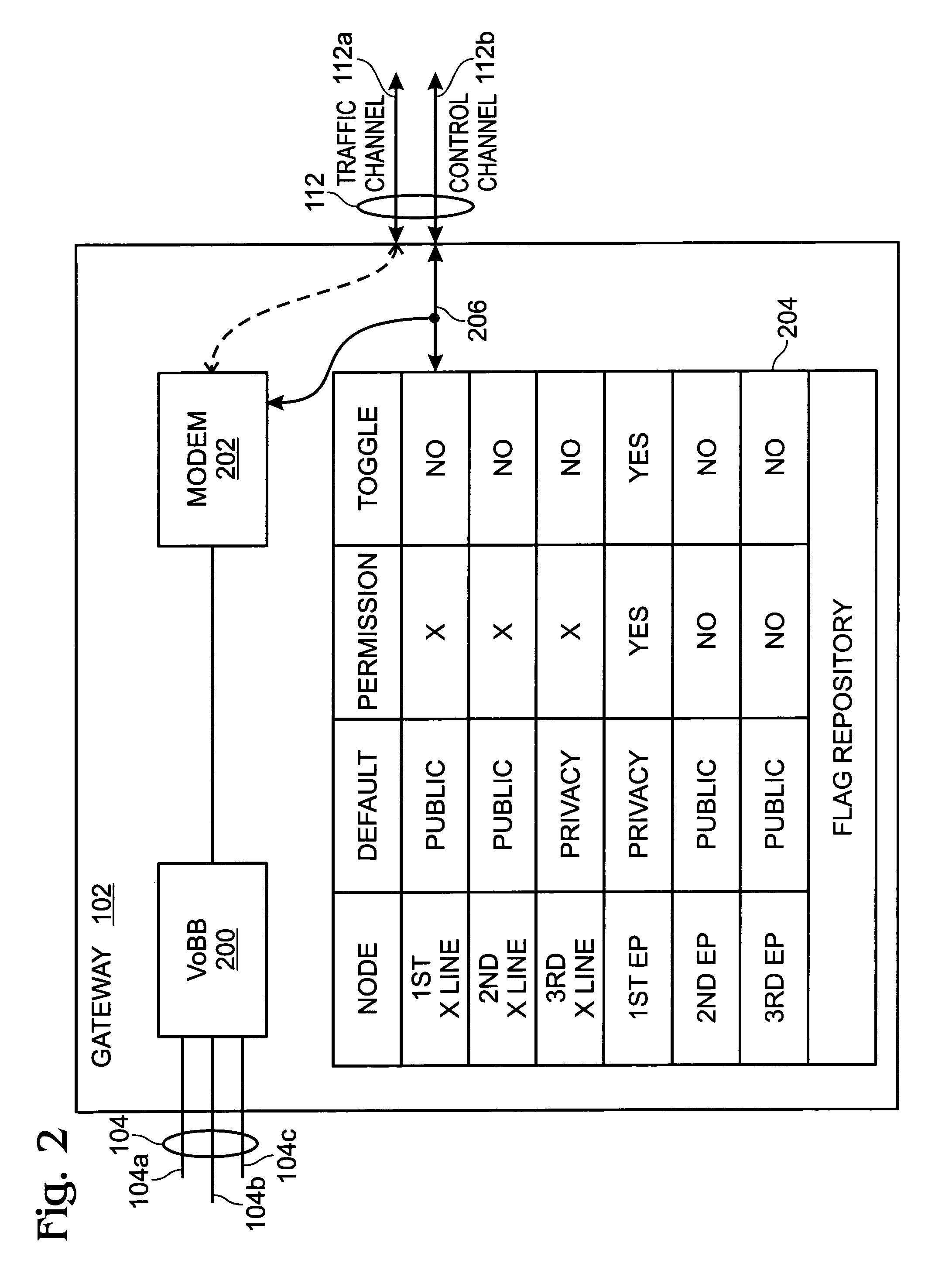
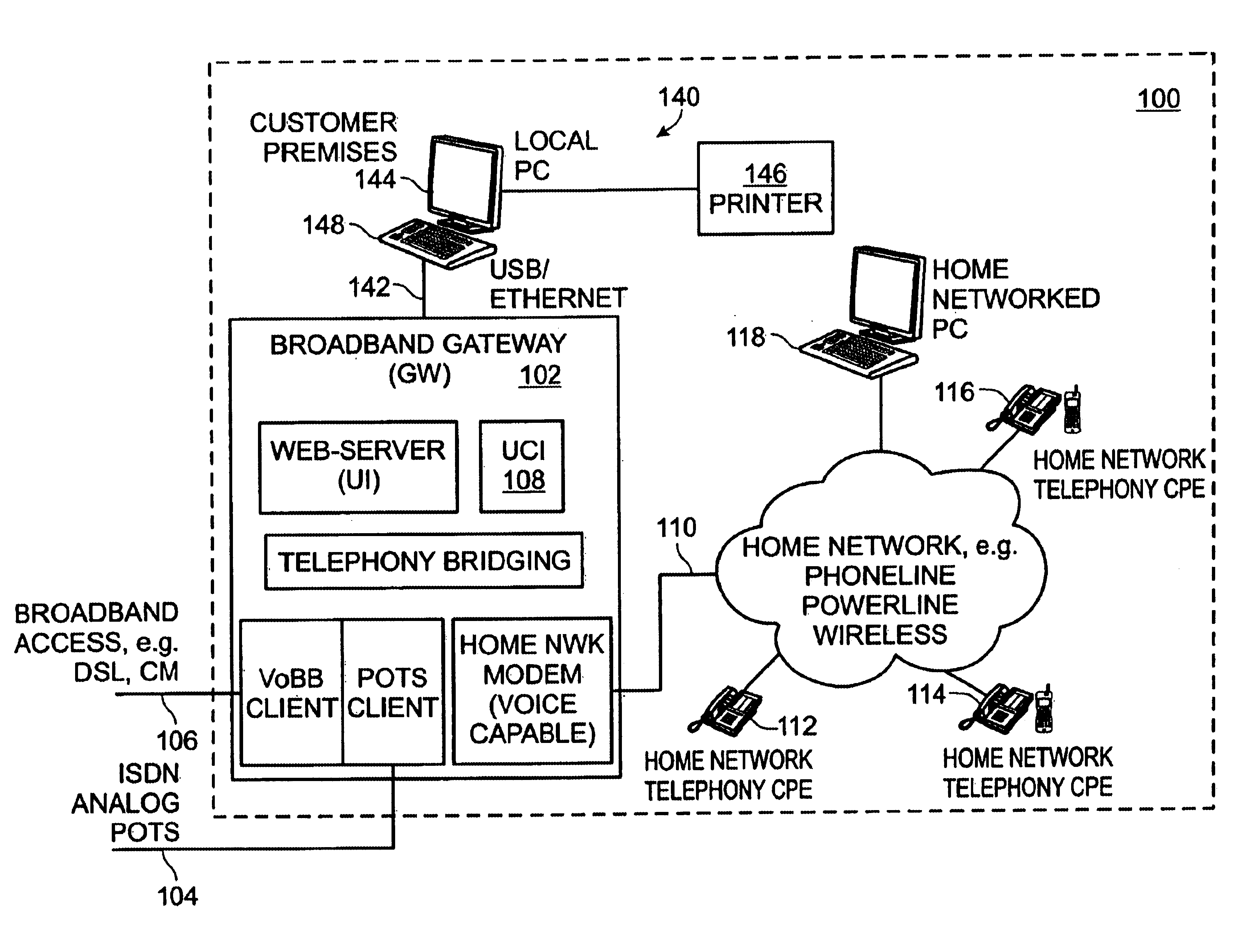
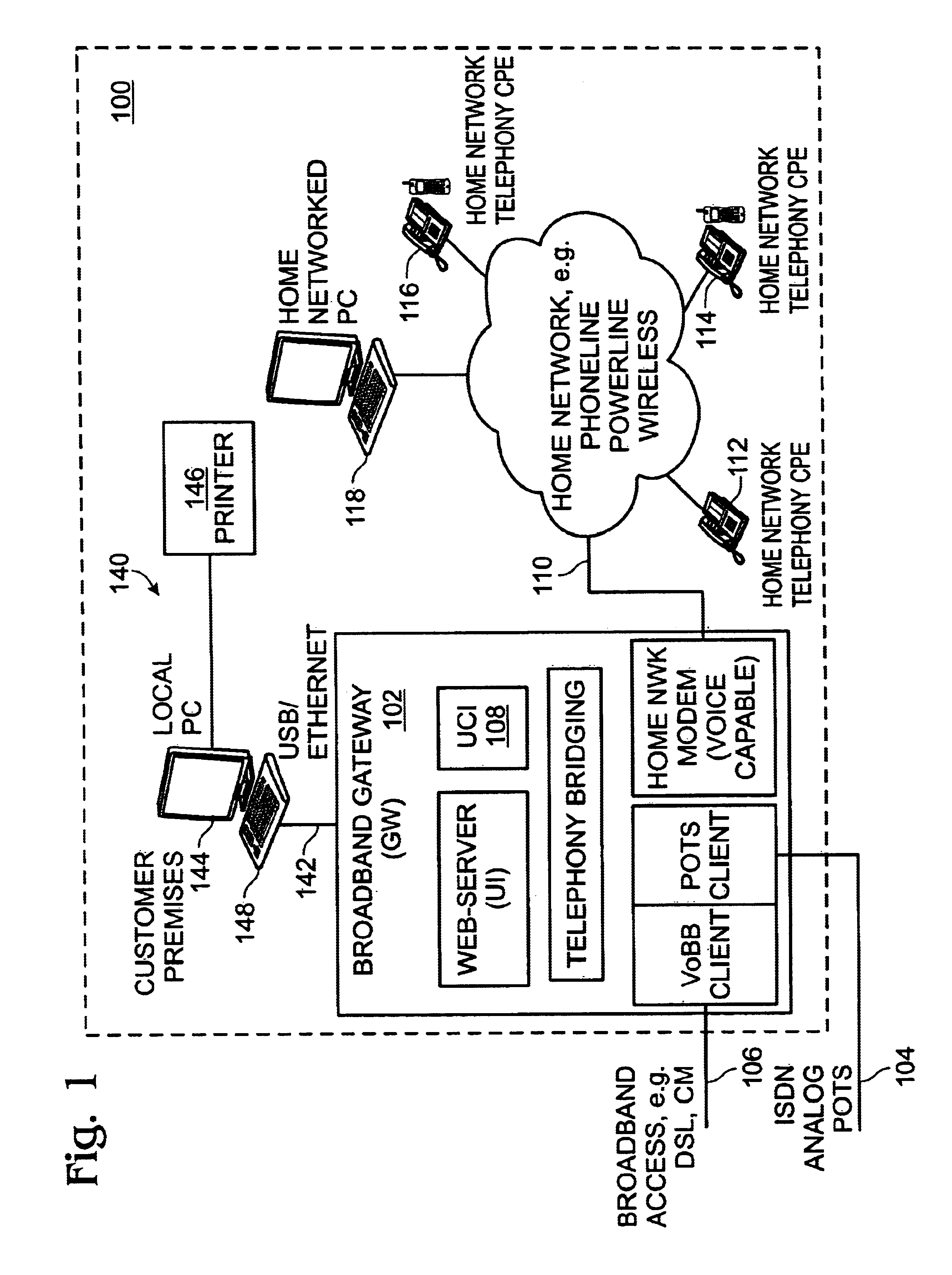
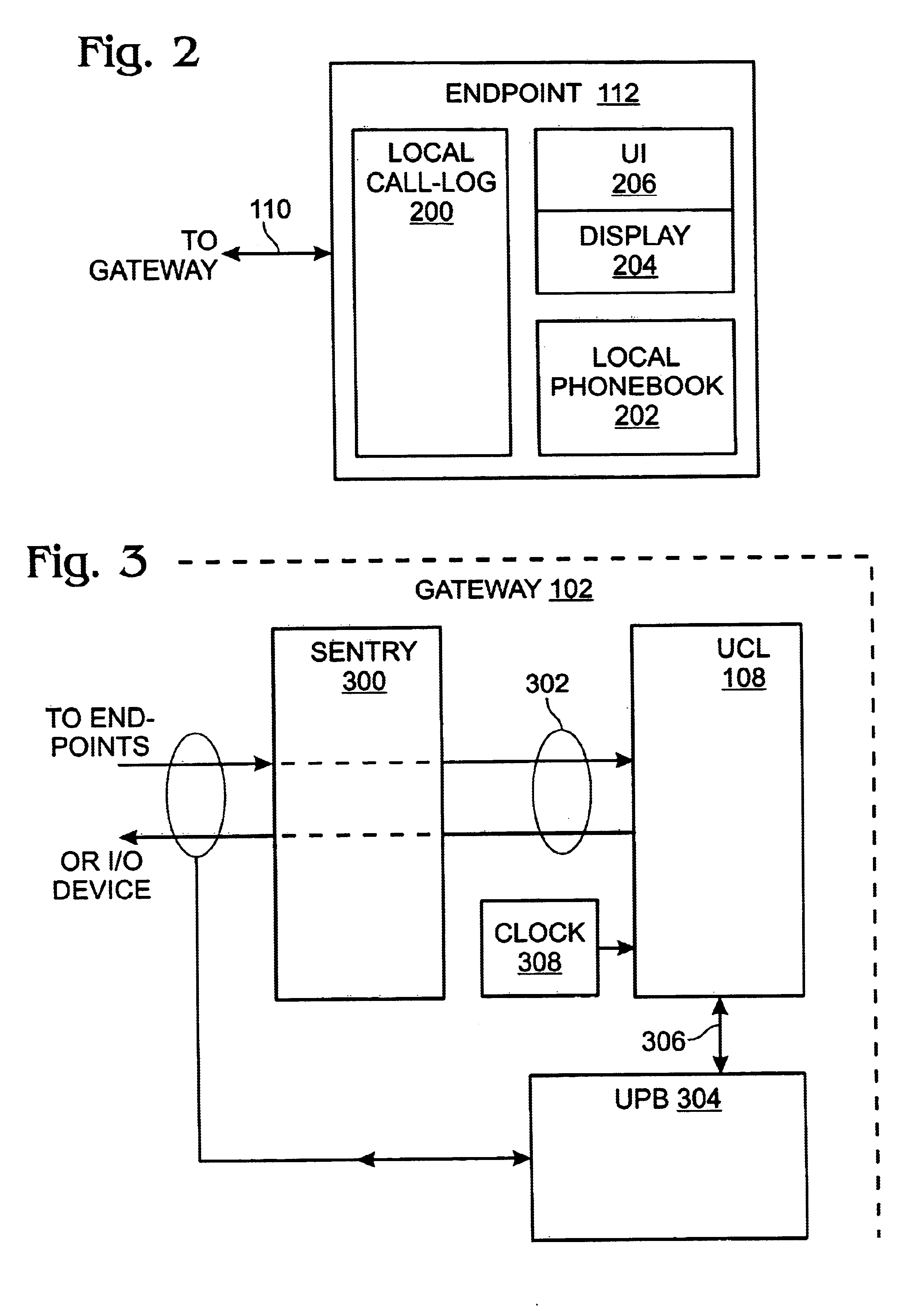
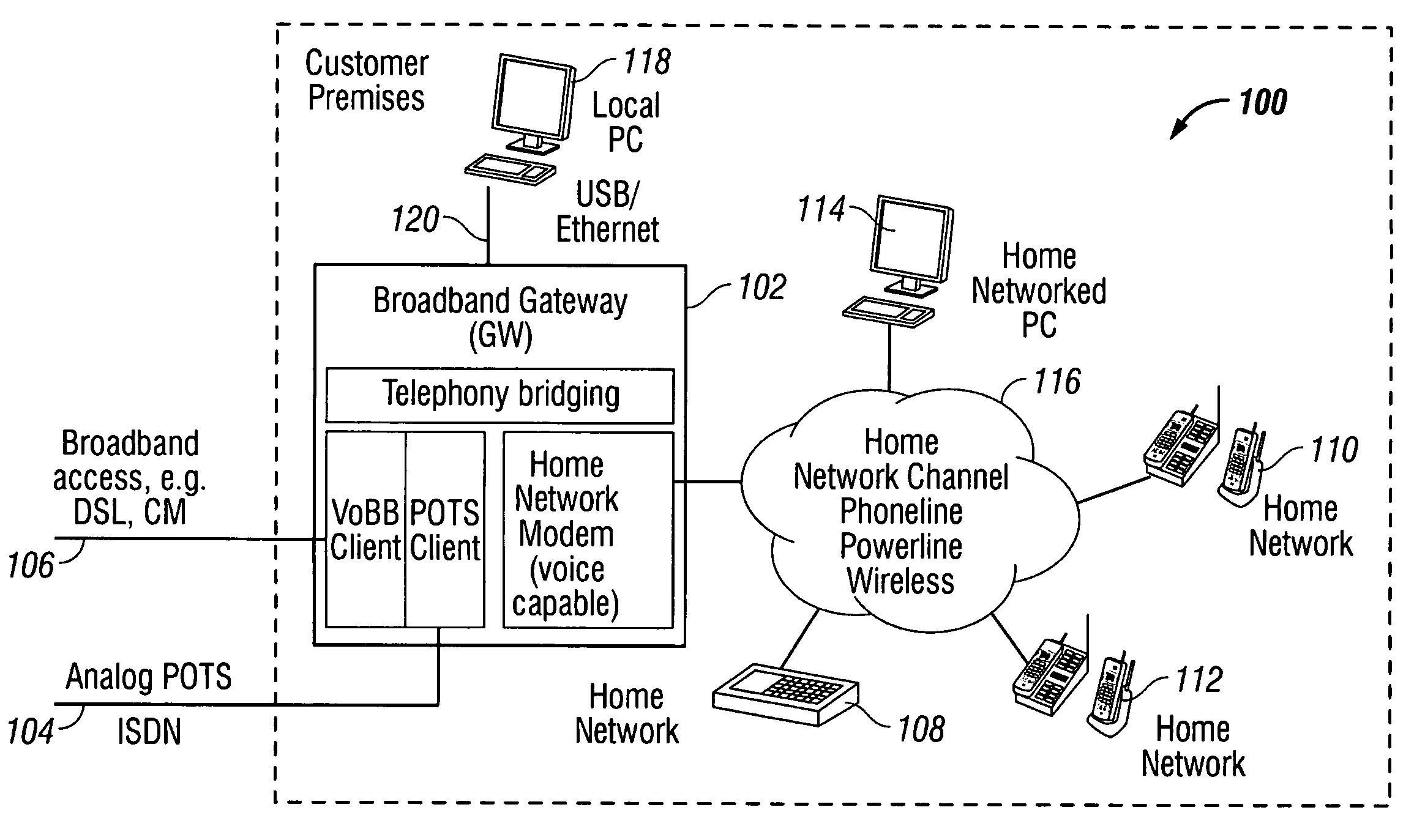
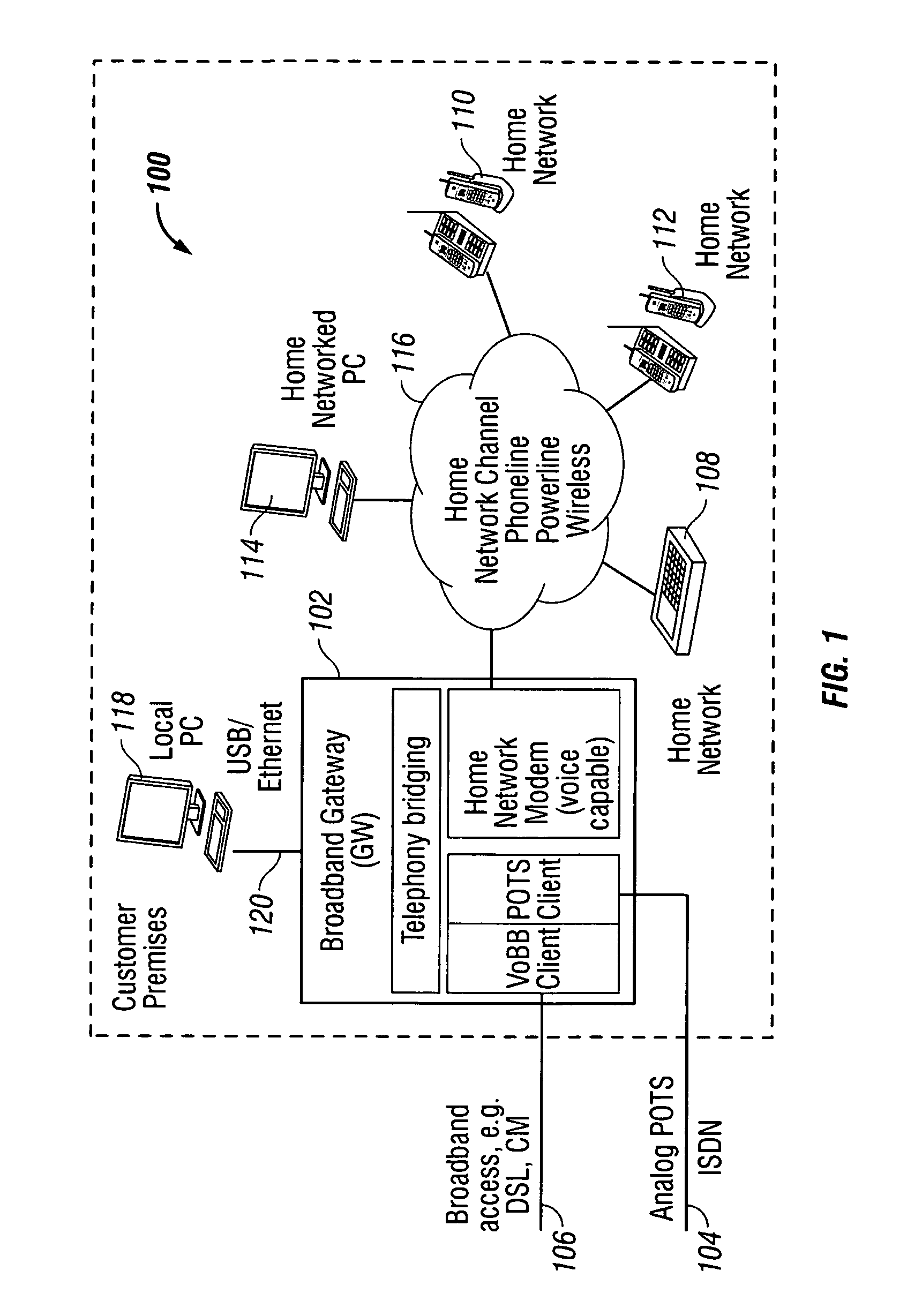
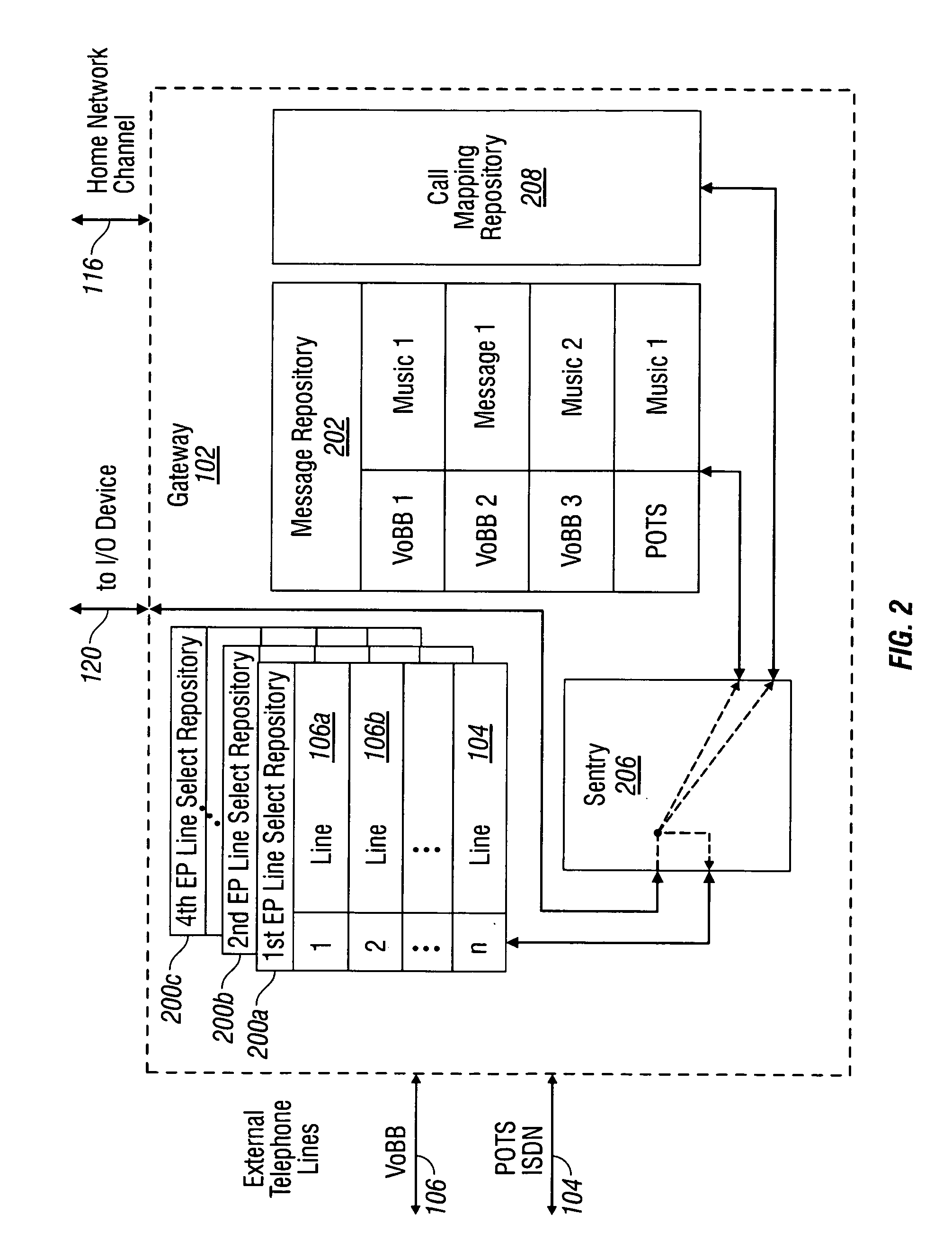
Privacy mode system and method for home network telephone
InactiveUS7023975B2Prevent bridgingInterconnection arrangementsSubstation speech amplifiersOperation modeFamily network
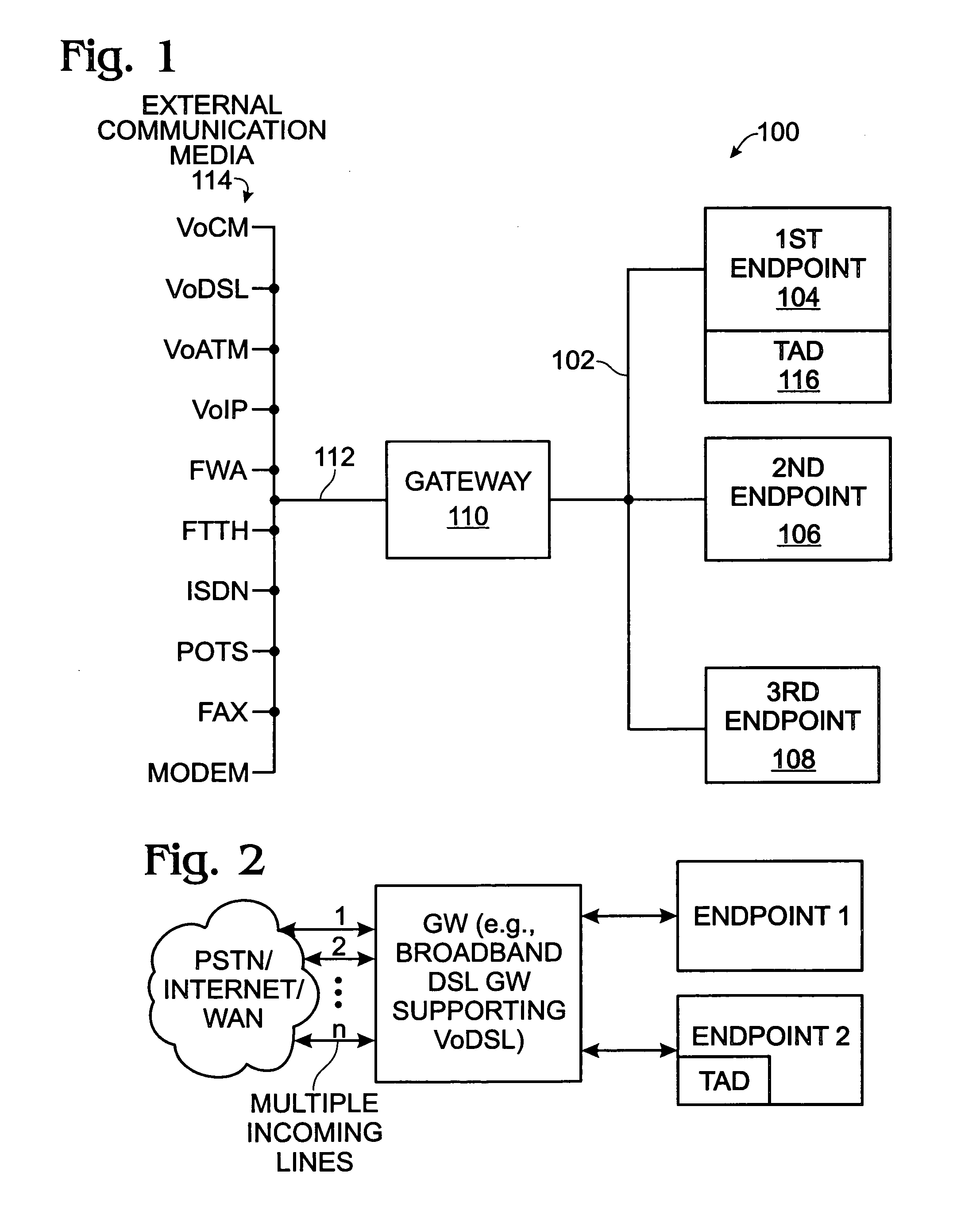
A system and method are provided for controlling communications privacy in a Home Network telephone system. The method comprises: using a gateway to send and receive calls on at least one external telephone line; supplying privacy and public mode bridging options; and, selectively excluding bridges between external telephone lines and a plurality of Home Network endpoints. In response to the privacy mode being selected, the gateway bridges a call between a first external telephone line and a first endpoint, and prevents bridges between the first external telephone line and other endpoints in the system. Alternately, when the public mode is selected, the gateway bridges a call between the first external telephone line and the first endpoint; and permits bridges between the first external telephone line and other endpoints in the system. That is, while the call is bridged to the first endpoint, a bridge is added between the first telephone line and the second endpoint. The privacy and public mode bridging options are selected with respect to nodes. A node can be an external telephone line or an endpoint. That is, a privacy or public mode of operation can be selected for a first external telephone line, whether calls are received or originated through the Home Network telephone system. Likewise, a privacy or public mode of operation can be selected for a particular endpoint, regardless of whether the endpoint receives or originates the call.
Owner:SHARP KK
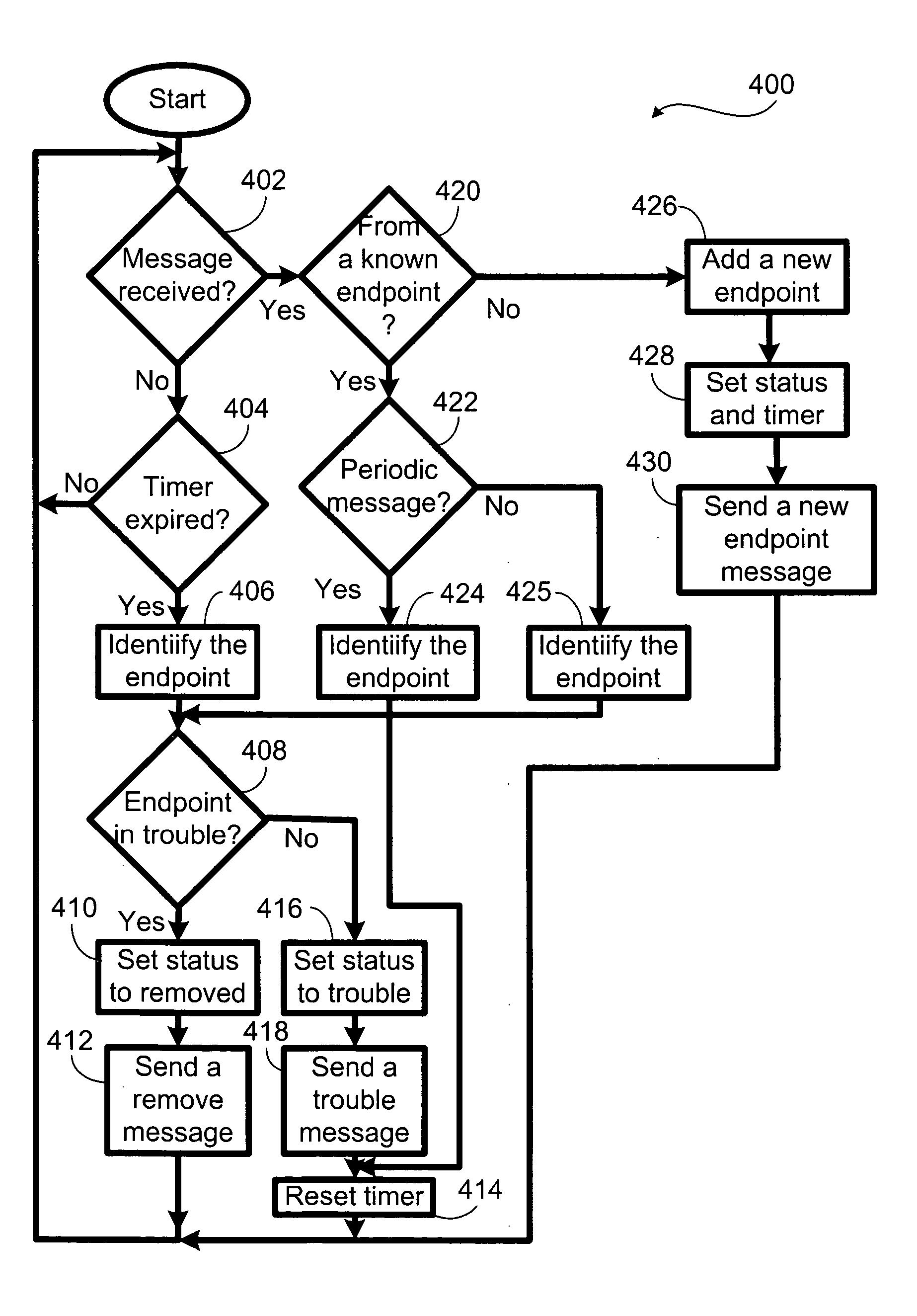
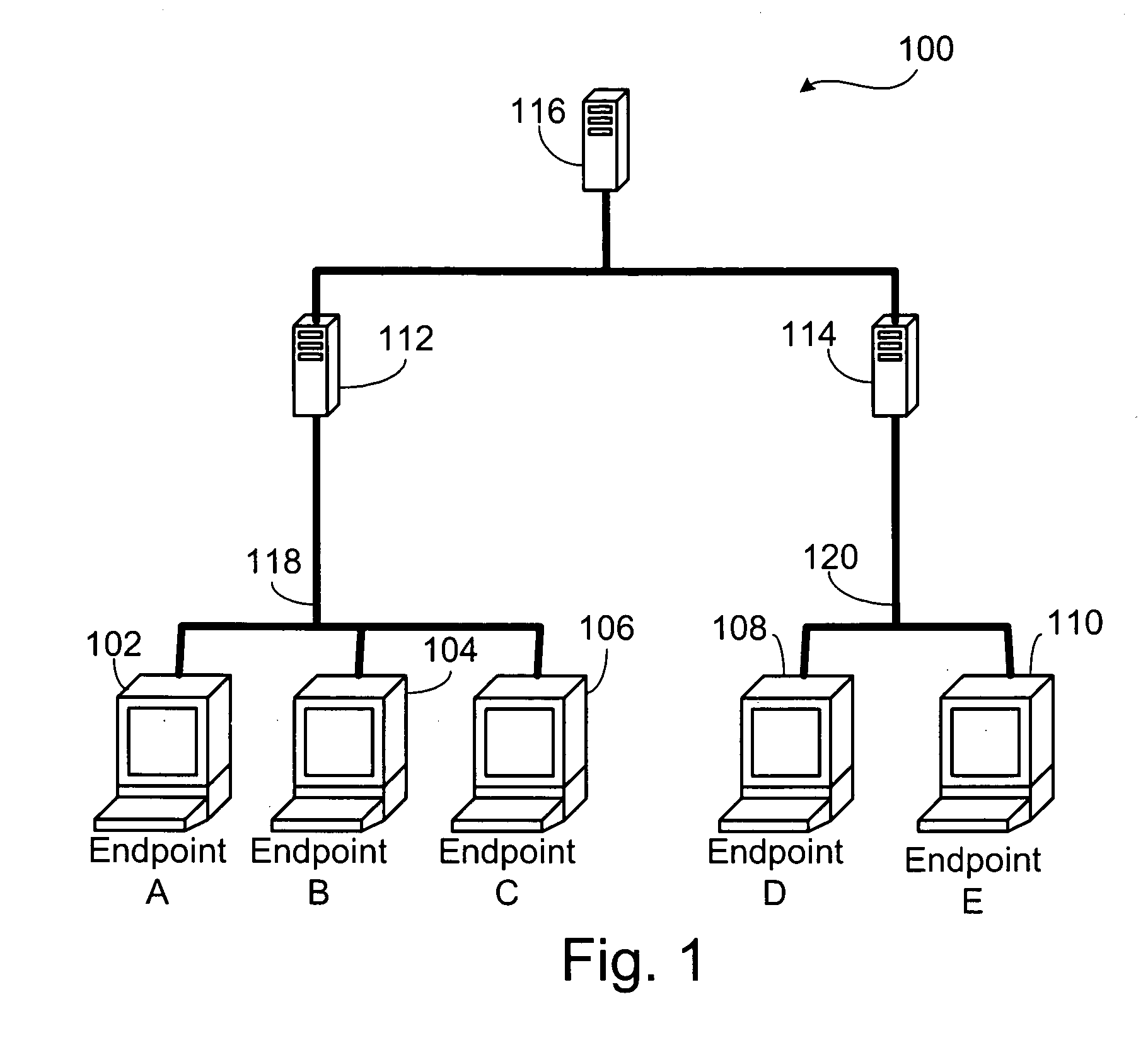
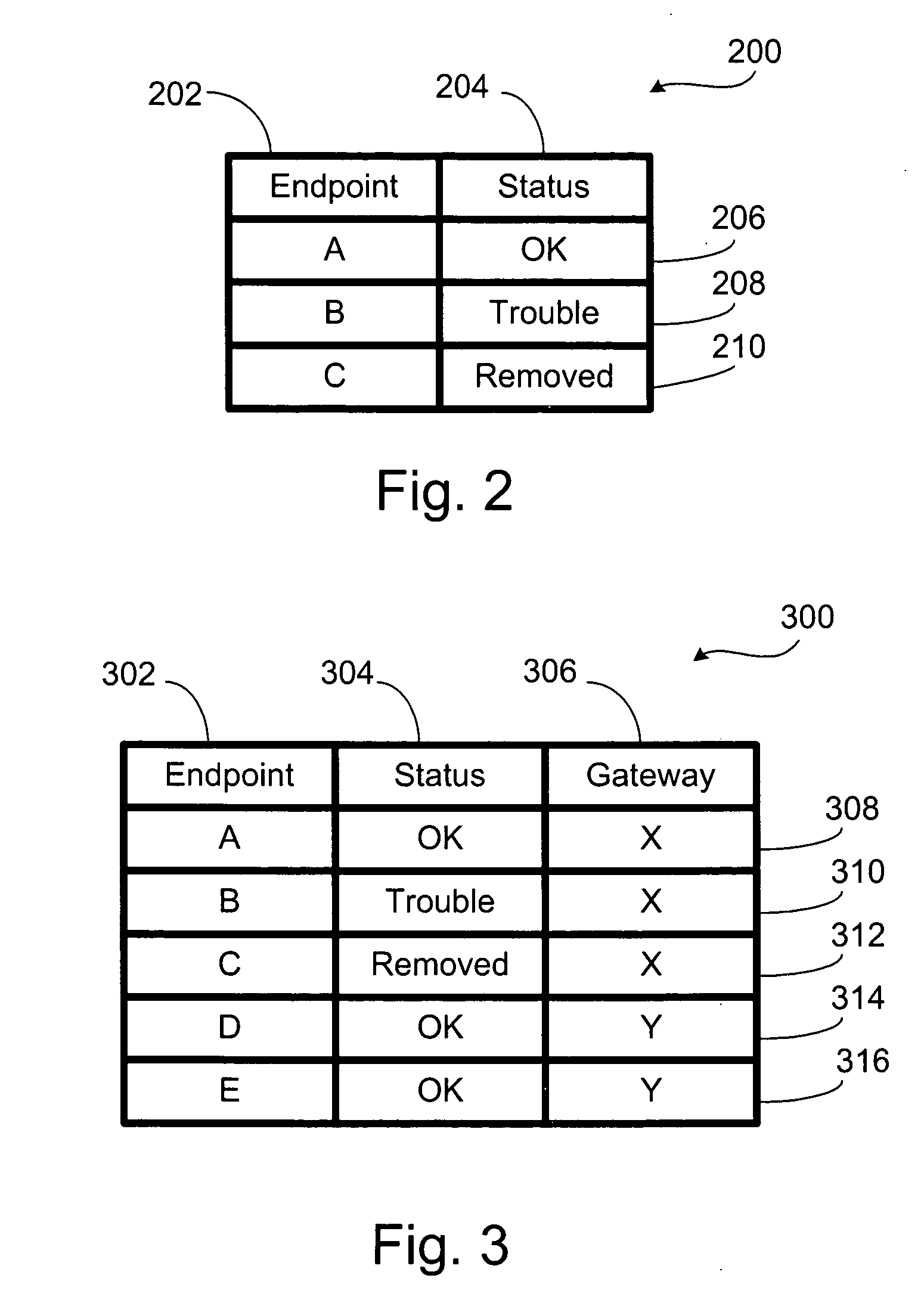
Network endpoint health check
In a system and method for monitoring the integrity of a plurality of endpoint devices in a network, each endpoint device is in communication with a gateway device and transmits a periodic message to this gateway device. When the gateway device fails to receive a periodic message from an endpoint, the gateway device marks the endpoint as in trouble. The next time the gateway device fails to receive a periodic message from the same endpoint, the gateway device marks the endpoint as removed. The gateway is in communication with a central server and sends status update messages to this central server.
Owner:IBM CORP
Universal call-log system and method for a home network telephone
InactiveUS6882714B2Easy accessCordless telephonesInterconnection arrangementsTelephone lineNetwork Endpoint
A system and method are provided for maintaining a universal call-log in a Home Network telephone system. The method comprises: transceiving calls on at least one external telephone line; bridging calls to a plurality Home Network endpoints; and, logging the bridged calls. Bridging calls to a plurality Home Network endpoints includes initiating an outgoing call from an endpoint. Then, the outgoing calls initiated from endpoints are logged. Likewise, incoming calls received on an external telephone line addressed to an endpoint and bridged, and logged. Logging the bridged calls includes cross-referencing entries such as call time, the call duration, the type of call, the external telephone involved, the external line telephone number from which an incoming call is received, the external telephone line telephone number to which an outgoing call is addressed, the endpoint to which an incoming call is addressed, and the endpoint initiating an outgoing call.
Owner:SHARP LAB OF AMERICA INC
System and method for virtual multiline telephony in a home-network telephone
InactiveUS7142560B2Provide capabilityMultiplex system selection arrangementsSpecial service for subscribersControl channelBroadband
A system and method are provided for multiline telephony in a home-network telephone system. The method comprises: establishing a gateway; using the gateway for transceiving calls on a plurality of external telephone lines; and, bridging a call between a home-network endpoint and a selected external telephone line. Transceiving calls on a plurality of external telephone lines includes the gateway communicating call information in a format such as voice-over broadband (VoBB) or POTS. Bridging a call includes the gateway: converting between the external format and a digital home-network format; establishing a traffic channel between the gateway and the endpoint to communicate information in the home-network format; and, establishing an out-of-band control channel to manage the corresponding traffic channel.
Owner:SHARP KK
Method of determining path maximum transmission unit
ActiveUS20050005024A1Digital computer detailsData switching by path configurationIP fragmentationStandard methods
Network endpoints using TCP / IP operate to determine the maximum transmission unit (MTU) of the path between them. This determination is done so as to avoid the expensive IP fragmentation that will occur when transitting links with a smaller MTU size. The standard method of determining the path MTU (PMTU) has several known deficiencies, including: inefficient use of bandwidth as proper operation will likely result in the loss of one or more packets and difficulty of implementation as the reverse channel communication mechanism, reception of ICMP messages indicating the discarding of unfragmentable packets, is frequently blocked by firewalls and other security apparatus. A method of determining the PMTU between intermediate proxies is disclosed that does not require reception of ICMP messages or the inefficient use of bandwidth due to the presumed dropping of packets with valid data.
Owner:CITRIX SYST INC
System and method for a group-based network access control for a computer
ActiveUS7032243B2Digital data processing detailsUnauthorized memory use protectionNetworking protocolControl system
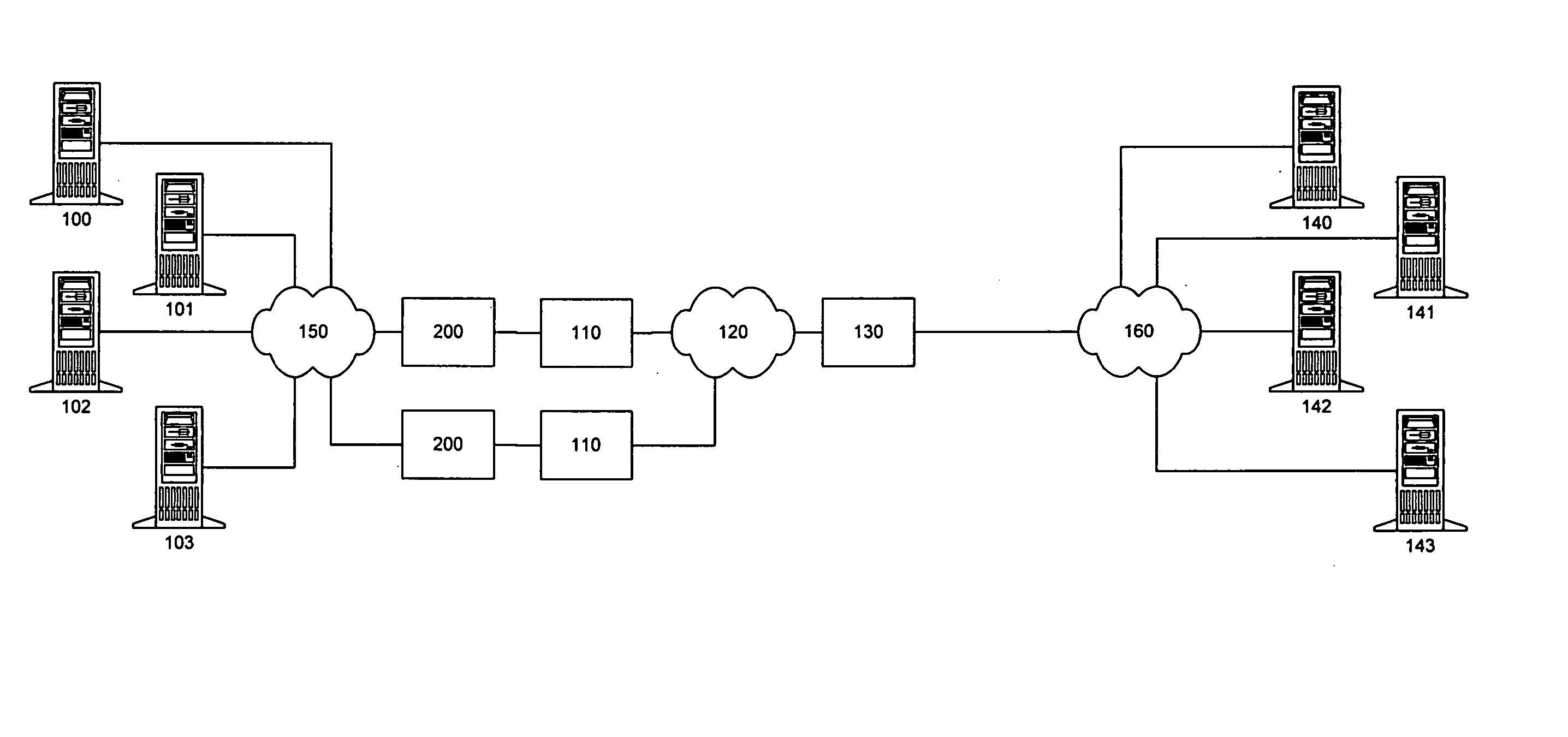
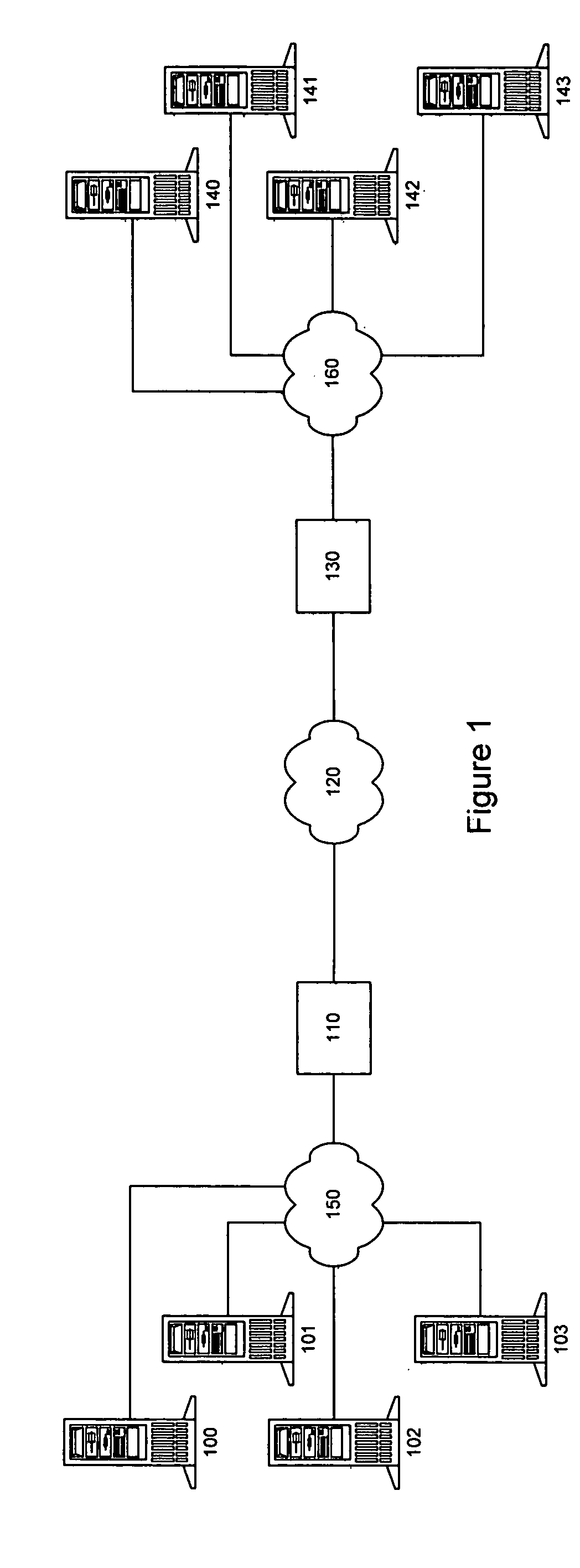
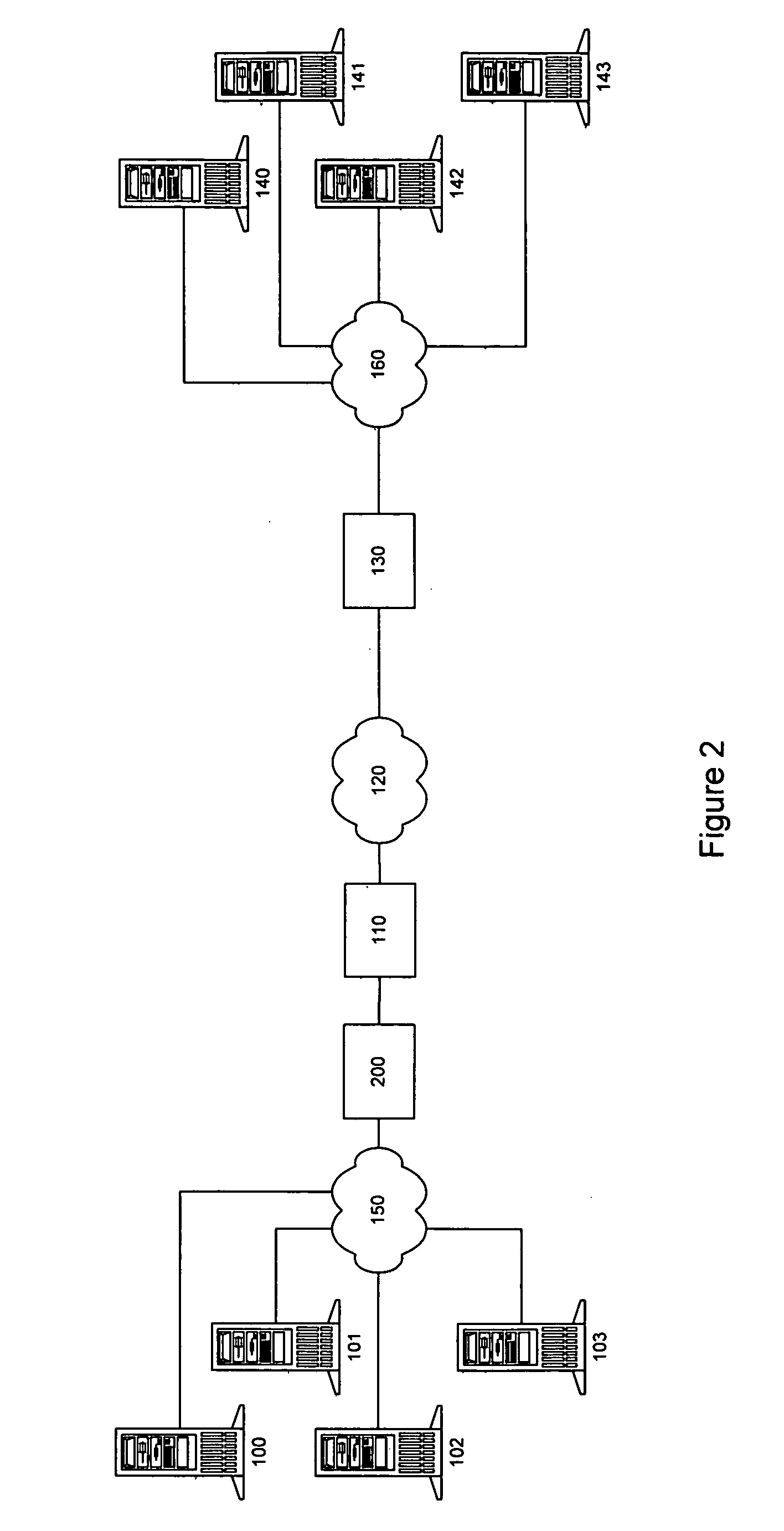
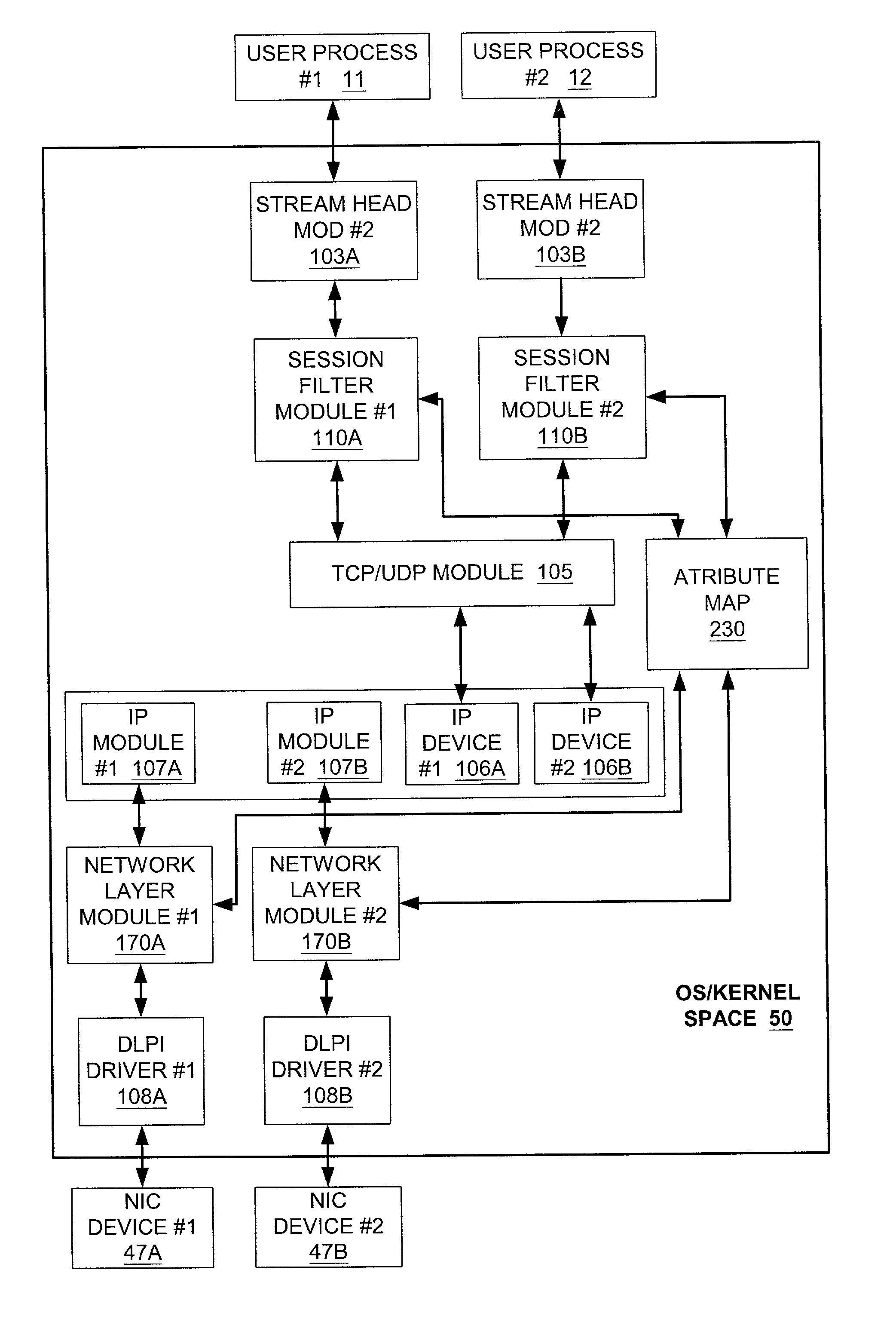
Systems and methods for group-based network access control systems are provided. The group-based network access control system includes a software process operating on a computer. The software process is configured to communicate a packet through a group-based network protocol stack to a network interface card that includes an interface attribute. A table of network attributes, associated with a session filter module and a network filter module, compares the network endpoint attribute with the interface attribute in the table of network attributes to determine whether the software process can access the network interface card. Each network endpoint attribute comprises a primary group identifier and a supplemental group identifier list, and each interface attribute comprises a network group list. The method includes the steps of operating a software process that includes a network endpoint attribute. Next, packets are communicated through a network protocol stack to a network interface card, where the network interface card includes an interface attribute. Association between the network endpoint attribute and the interface attribute is established, and both the network endpoint attribute and the interface attribute are placed in a table. The network endpoint attribute is then compared with the interface attribute to determine whether the software process can access the network interface card. Each network endpoint attribute comprises a primary group identifier and a supplemental group identifier list, and each interface attribute comprises a network group list.
Owner:VALTRUS INNOVATIONS LTD
Method and system for quality of service renegotiation
InactiveUS20070058561A1Metering/charging/biilling arrangementsError preventionQuality of serviceTelecommunications link
A method of renegotiating QoS levels of a communication link in one or more networks, the communication link having an initial QoS level prior to renegotiation, includes examining information flowing on the communication link between a first network endpoint and a second network endpoint. The method also includes determining, based on the information, a type of application being used by the first and second network endpoints for the communication link. The method further includes determining a QoS level that is suitable for the application, and negotiating with at least one of the one or more networks to procure resources associated with the network that will provide the suitable QoS level.
Owner:CISCO TECH INC
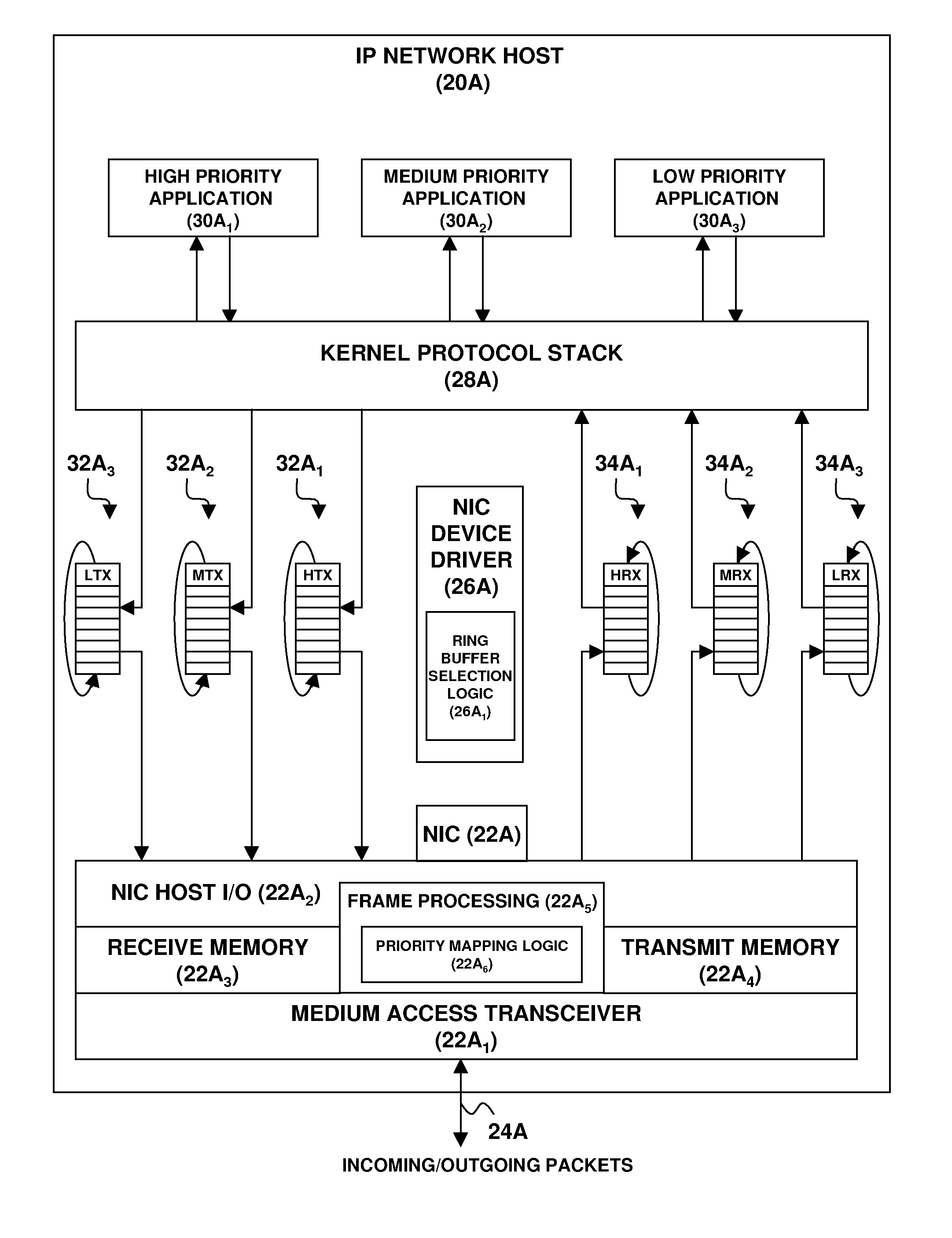
Enhancement of end-to-end network QOS
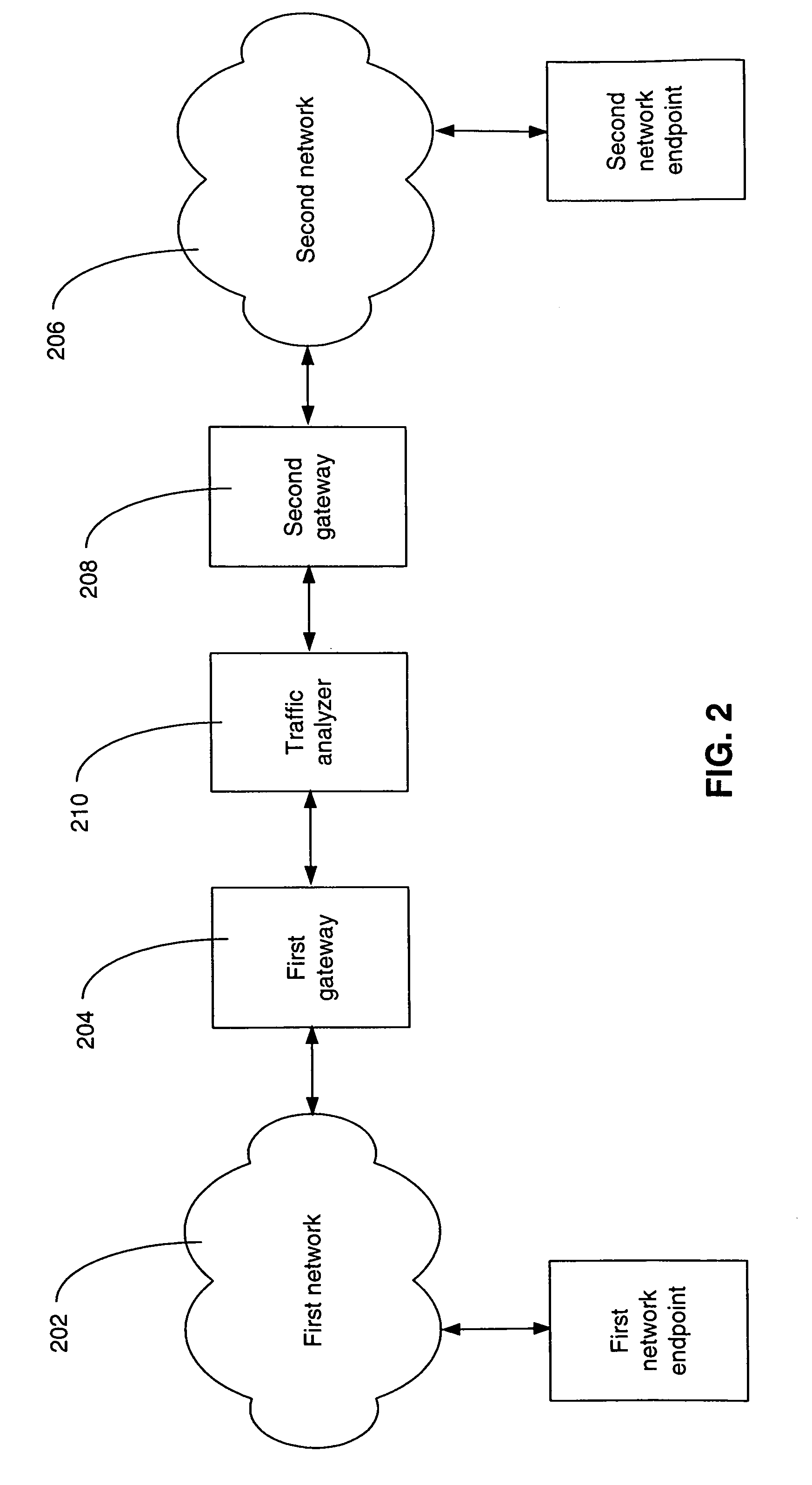
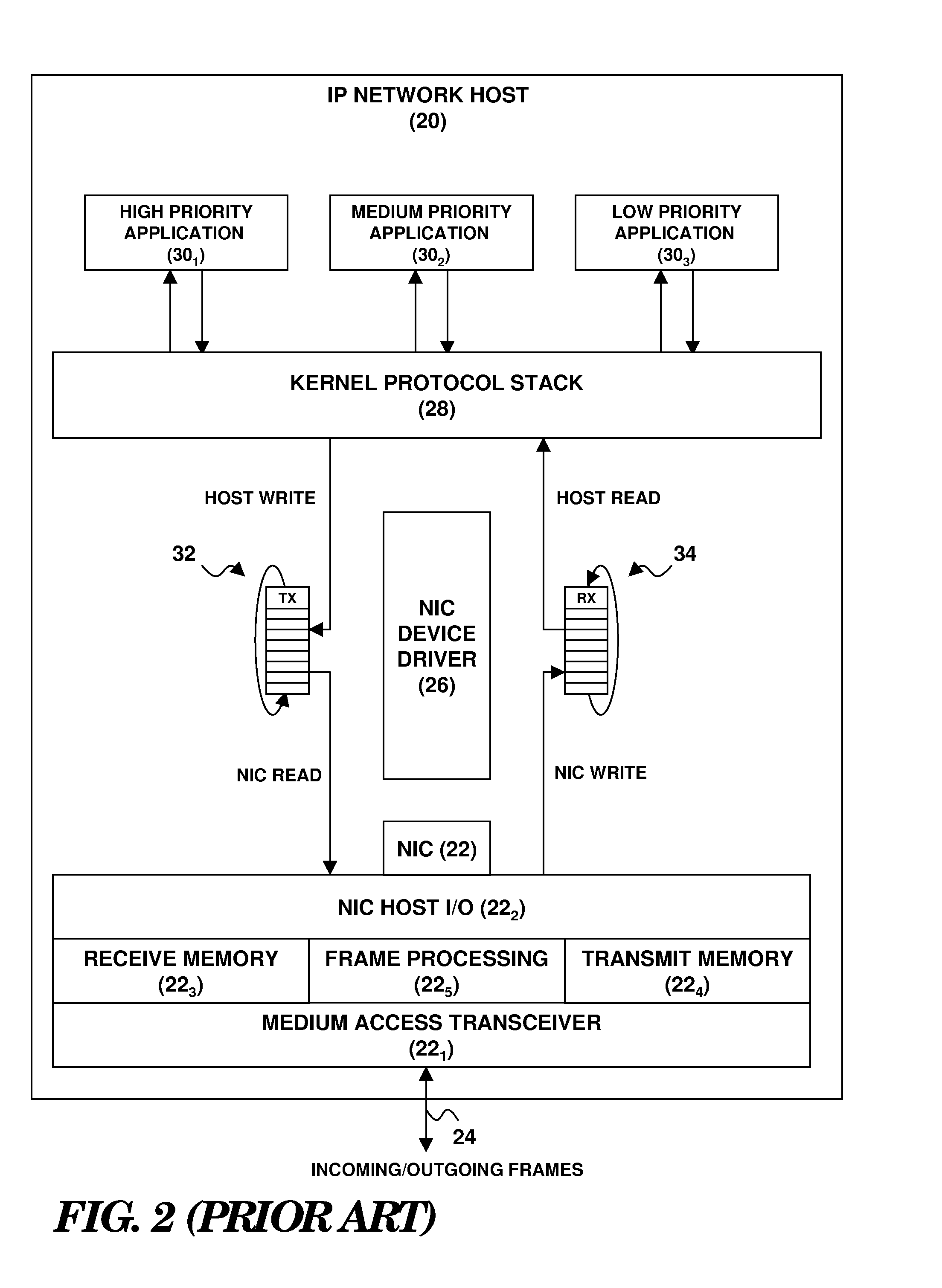
A network endpoint system and related method and computer program product for use in a network to support enhanced end-to-end QoS in the network. The network endpoint system is adapted to receive network data of varying priority on behalf of a data consumer operating at the application layer of a network protocol stack implemented by the network endpoint system. The network endpoint system includes a network interface controller adapted to receive network frames containing the network data, plural network data handling channels each having an associated priority, and priority processing logic adapted to transfer the network data from the network interface controller to the plural data handling channels on a prioritized basis according to the network data priority. Also disclosed are a network interface controller and a network node to support enhanced end-to-end QoS in a network.
Owner:IBM CORP
Home network telephone answering system and method for same
InactiveUS7162013B2Multiplex system selection arrangementsSpecial service for subscribersWeb siteService provision
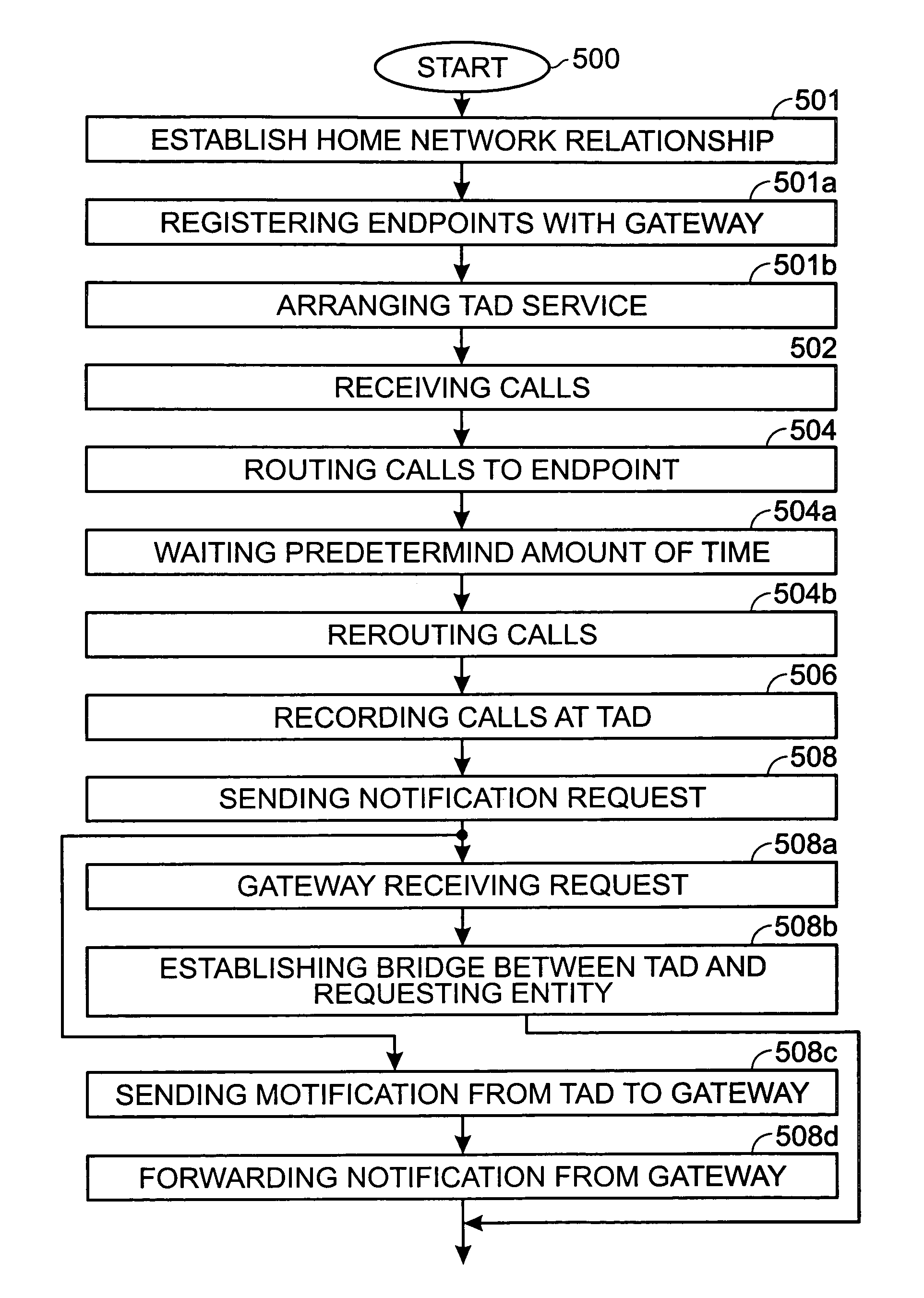
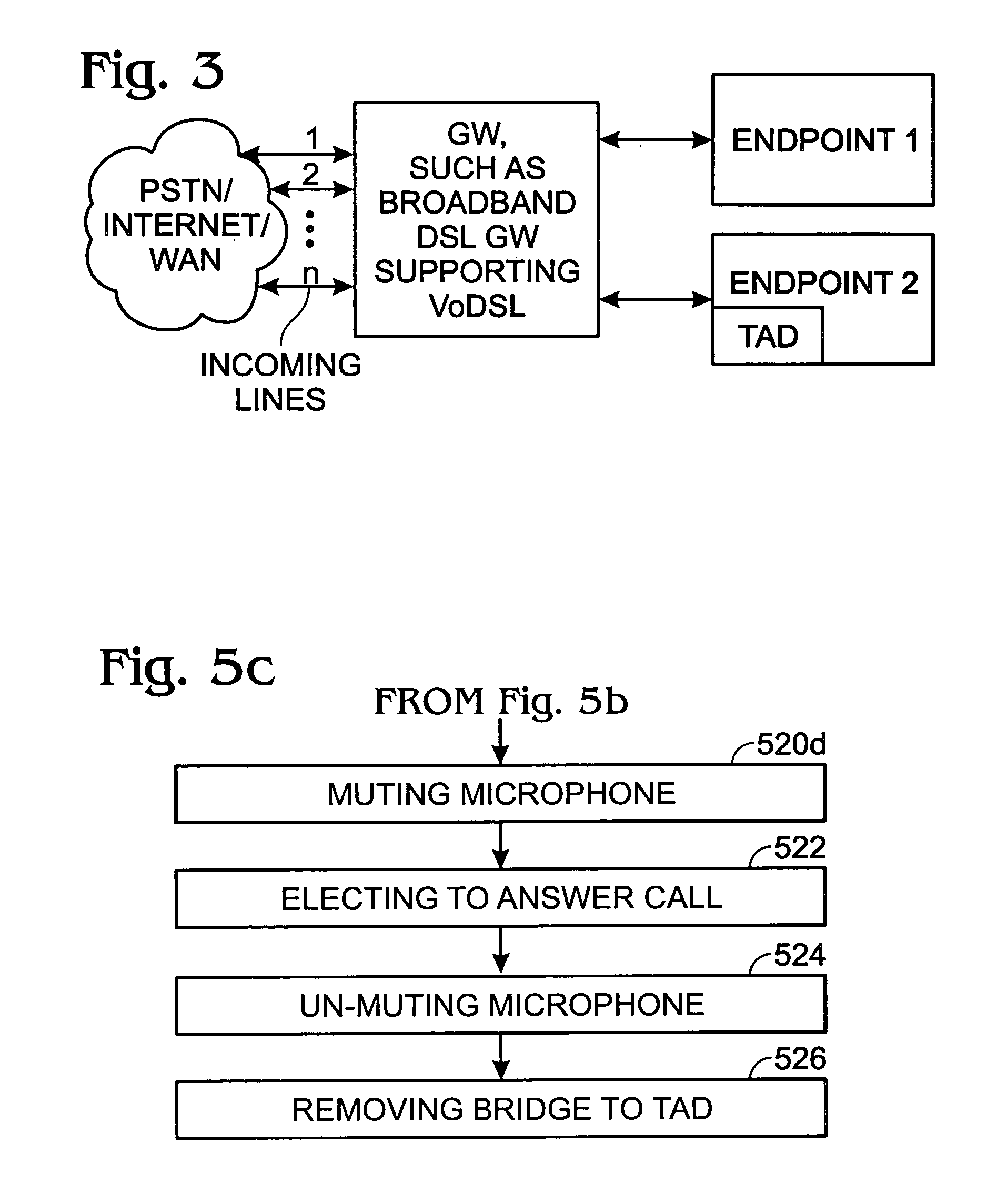
A system and method are provided for answering Home Network telephone calls. The method comprises: receiving telephone calls addressed to a Home Network endpoint; routing the received calls from a gateway to the endpoint; and, automatically recording the received call at a telephone answering device (TAD). The call can be recorded by an endpoint, the gateway, or an external line service provider facility central office or web site. Telephone calls can be addressed to an endpoint from external communication media or another endpoint. Some aspects of the method include sending notification that a message has been recorded. The gateway may initiate the notification. Alternately, the gateway may receive a request for any TAD information that may exist for an addressed endpoint, and if a message exists, the TAD creates a bridge between the TAD and a requesting entity to forward the notification.
Owner:SHARP KK
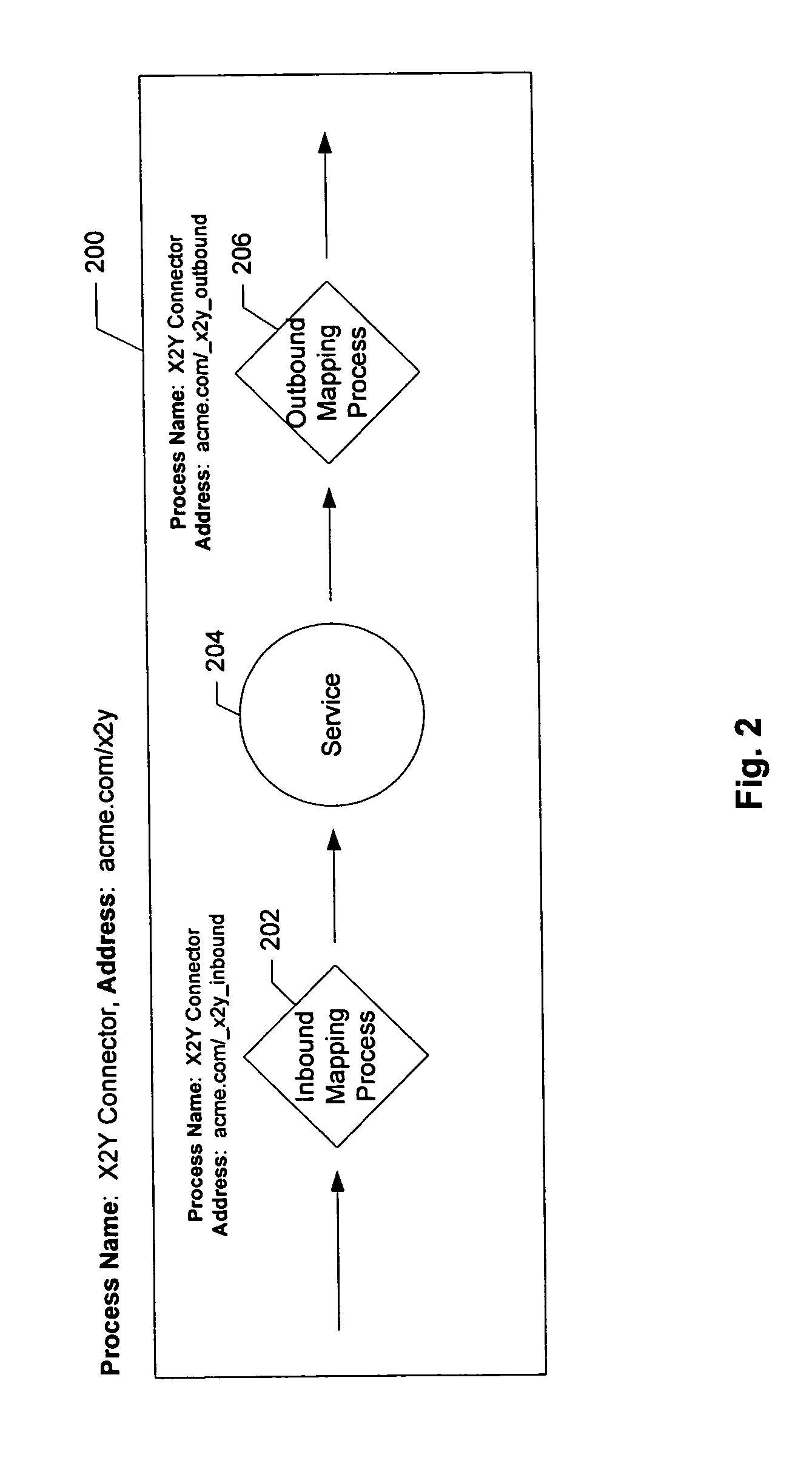
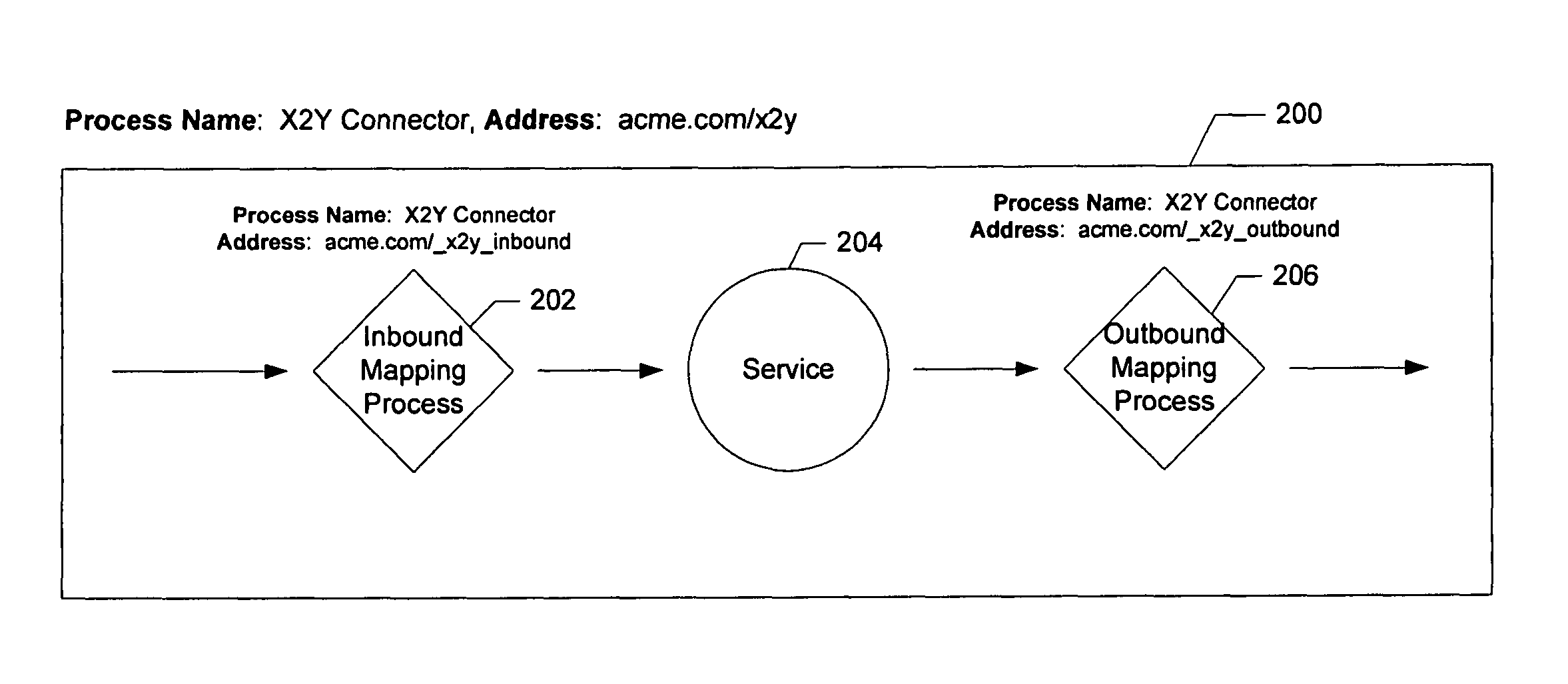
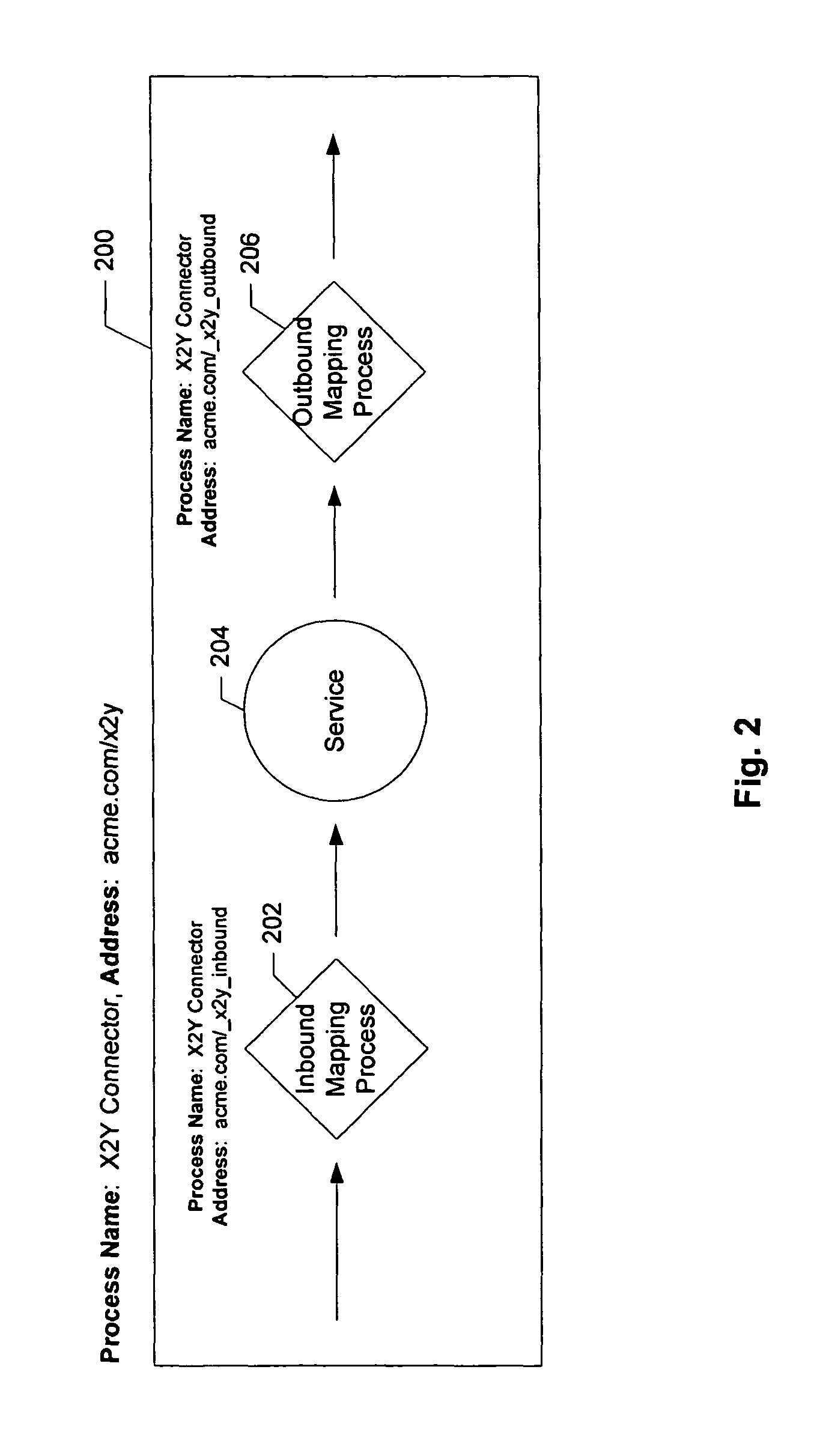
Techniques for providing connections to services in a network environment
ActiveUS20060015353A1Reduce consumptionFacilitate creation of newMultiple digital computer combinationsOffice automationBusiness policiesBusiness process
Methods and apparatus for facilitating consumption of services via a services network are described. Access is provided to a services directory which identifies a plurality of services and at least one connector for facilitating consumption of each of the services via the network. Each connector is operable to mediate communication protocol and business policy differences between a first network end point associated with the corresponding service and a second network end point associated with a consumer of the service. For each of selected ones of the connectors, information accessible via the services directory is provided regarding how to use the connector to consume the corresponding service. For each of selected ones of the services, access to a connector design process is provided via the services directory. The connector design process is operable to facilitate creation of a new connector for the corresponding service, and to specify at least one business process for mediating the business policy differences.
Owner:SALESFORCE COM INC
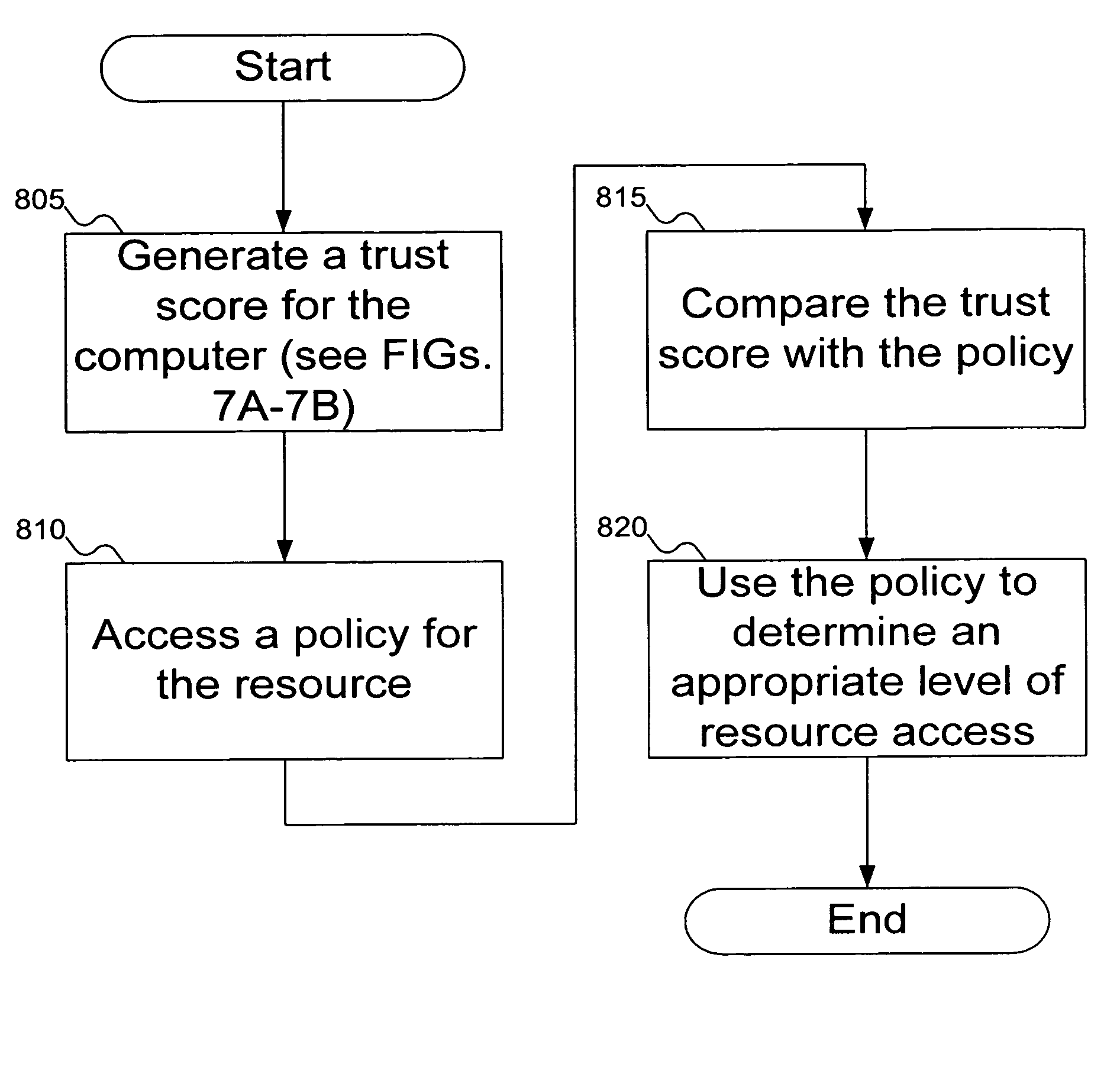
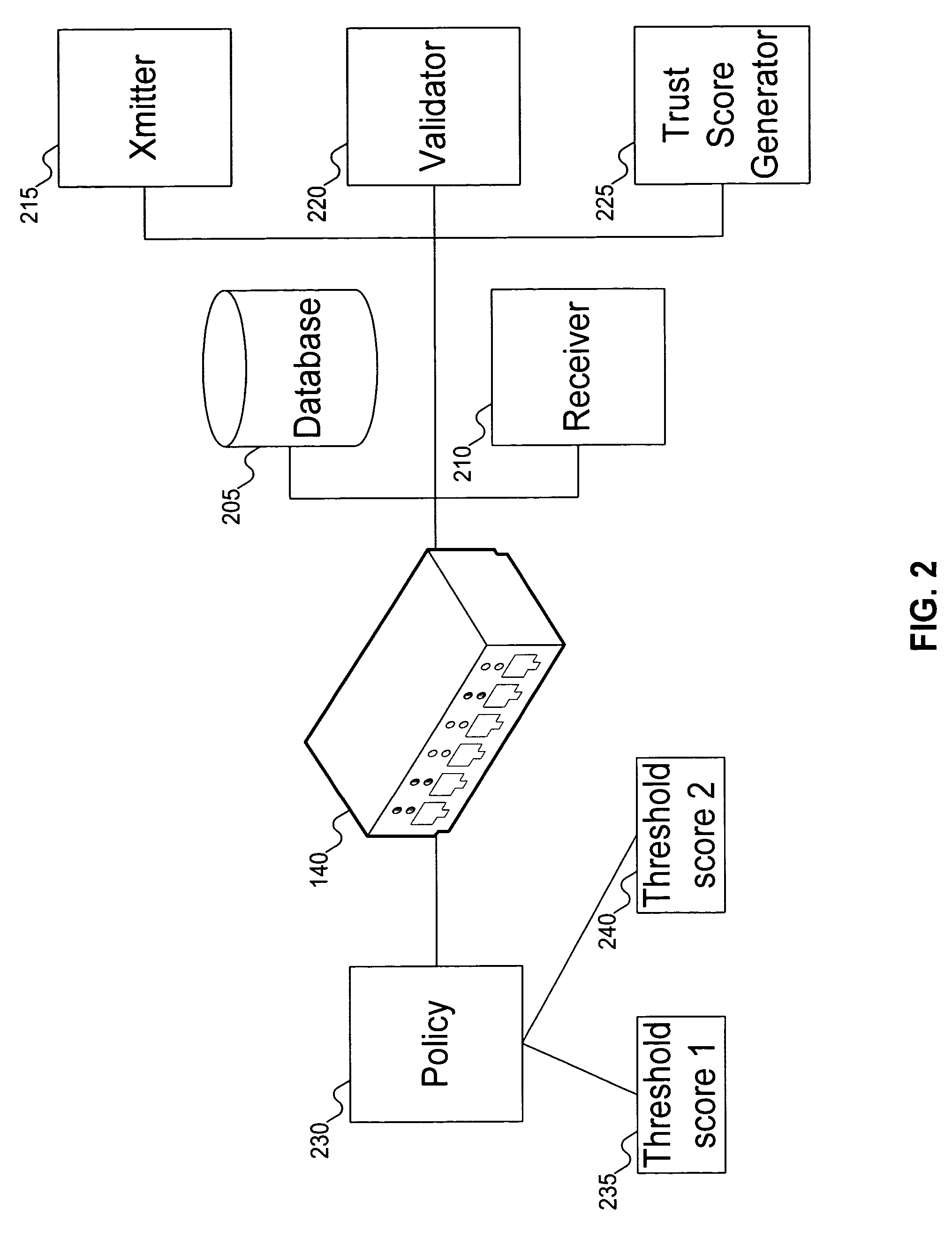
Method to control access between network endpoints based on trust scores calculated from information system component analysis
InactiveUS7272719B2Digital data processing detailsUser identity/authority verificationComputerized systemData mining
Signatures are generated for modules in a computer system. The signatures can be assembled into an integrity log. The signatures are compared with signatures in a database in an integrity validator. Once signatures are either validated or invalidated, a trust score can be generated. The trust score can then be used to determine whether the computer system should be granted access to a resource using a policy.
Owner:SILICON VALLEY BANK +1
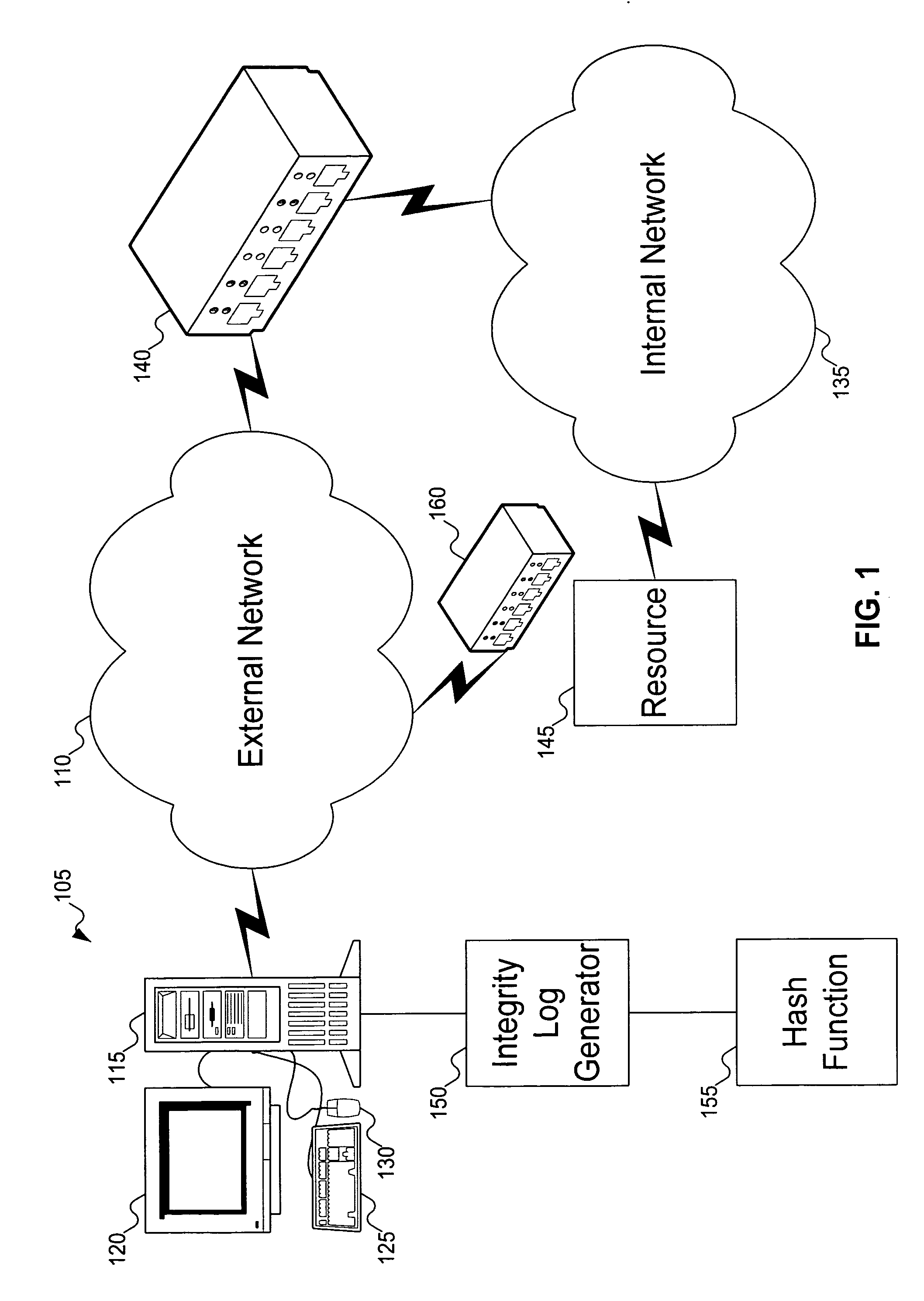
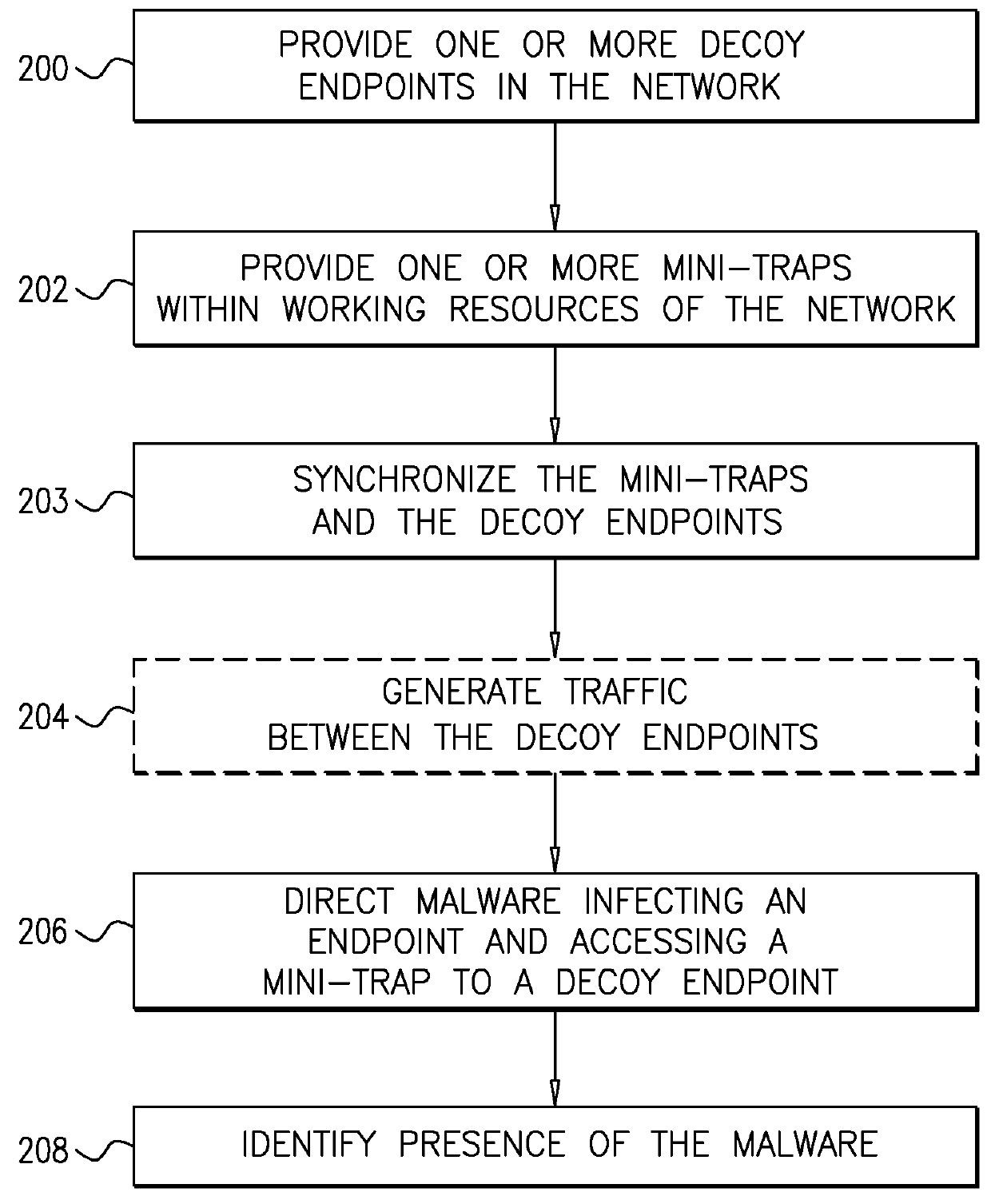
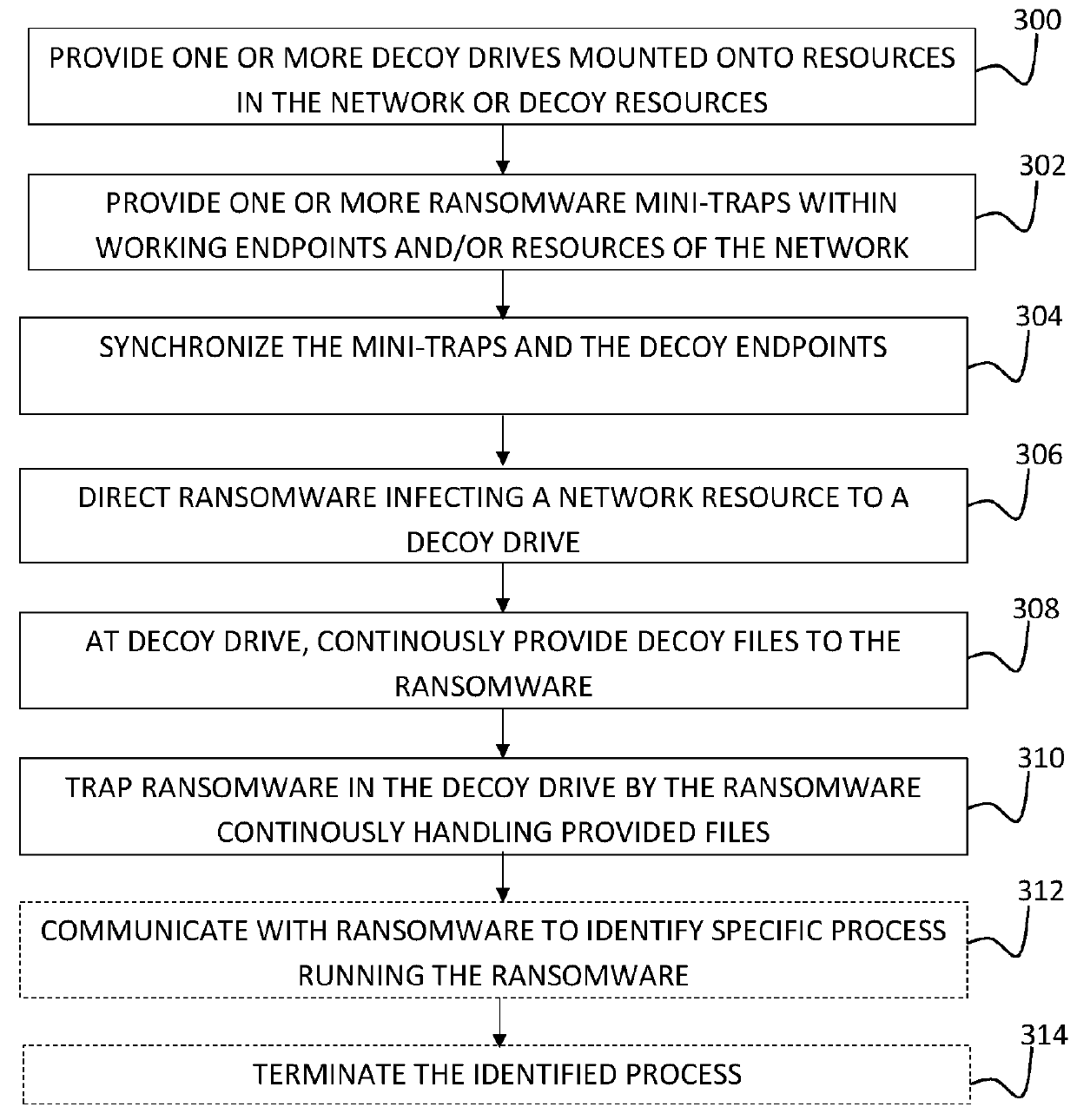
System and a method for identifying the presence of malware and ransomware using mini-traps set at network endpoints
A system and a method for identifying the presence of ransomware on a network including a plurality of resources, and for trapping the ransomware therein.
Owner:FIDELIS SECURITY LLC +1
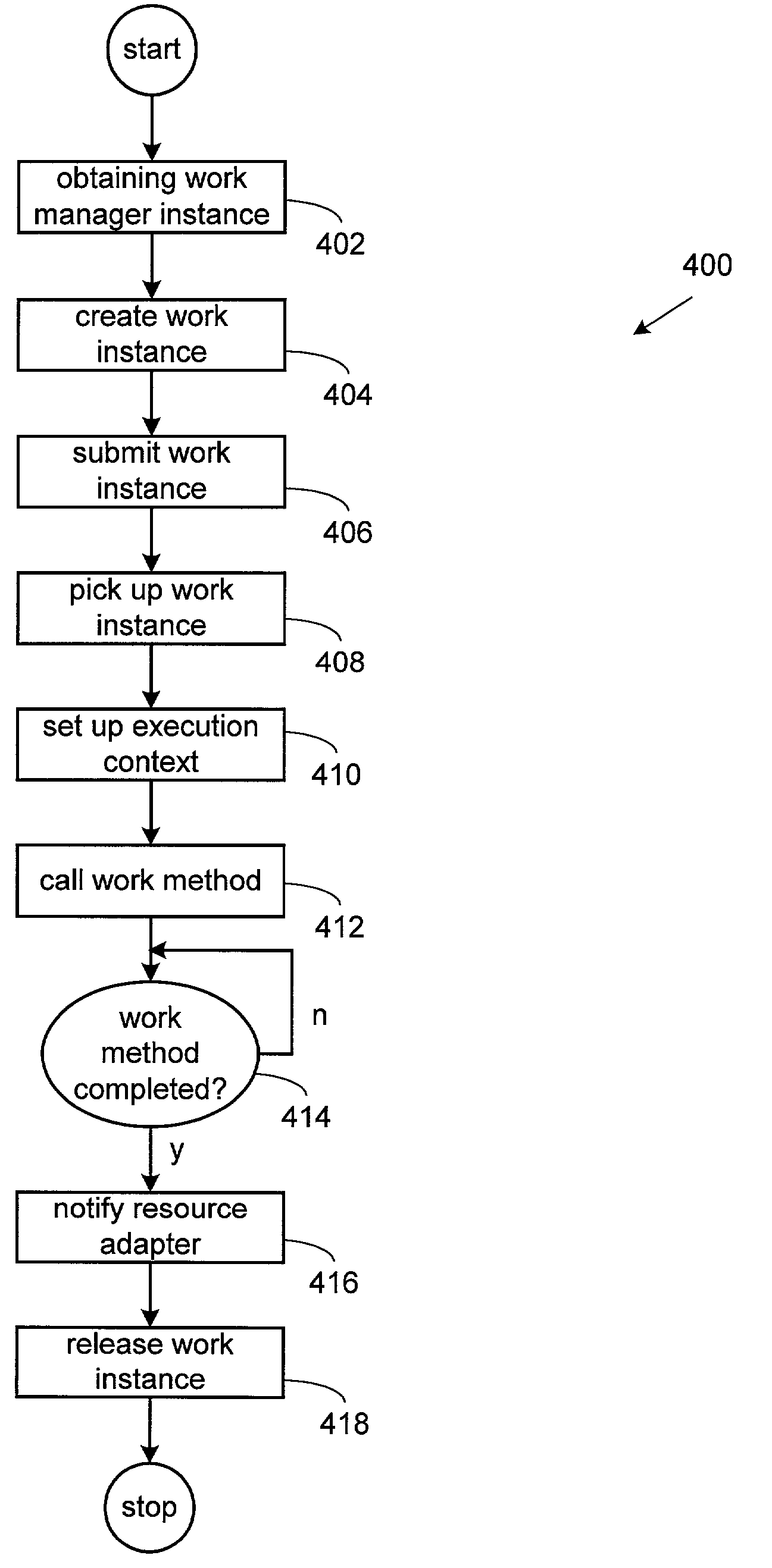
Callback event listener mechanism for resource adapter work executions performed by an application server thread
A method, apparatus and system arranged to provide a contract between an application server and a resource adapter that allows the resource adapter to do work (monitor network endpoints, call application components, etc) by submitting work instances to an application server for execution. In the described embodiment, the application server dispatches threads to execute submitted work instances thereby allowing the requesting resource adapter to avoid creating or managing threads directly. In this way, a mechanism for the resource adapter to do its work is provided as well as allowing the application server to efficiently pool threads and have more control over its runtime environment.
Owner:ORACLE INT CORP
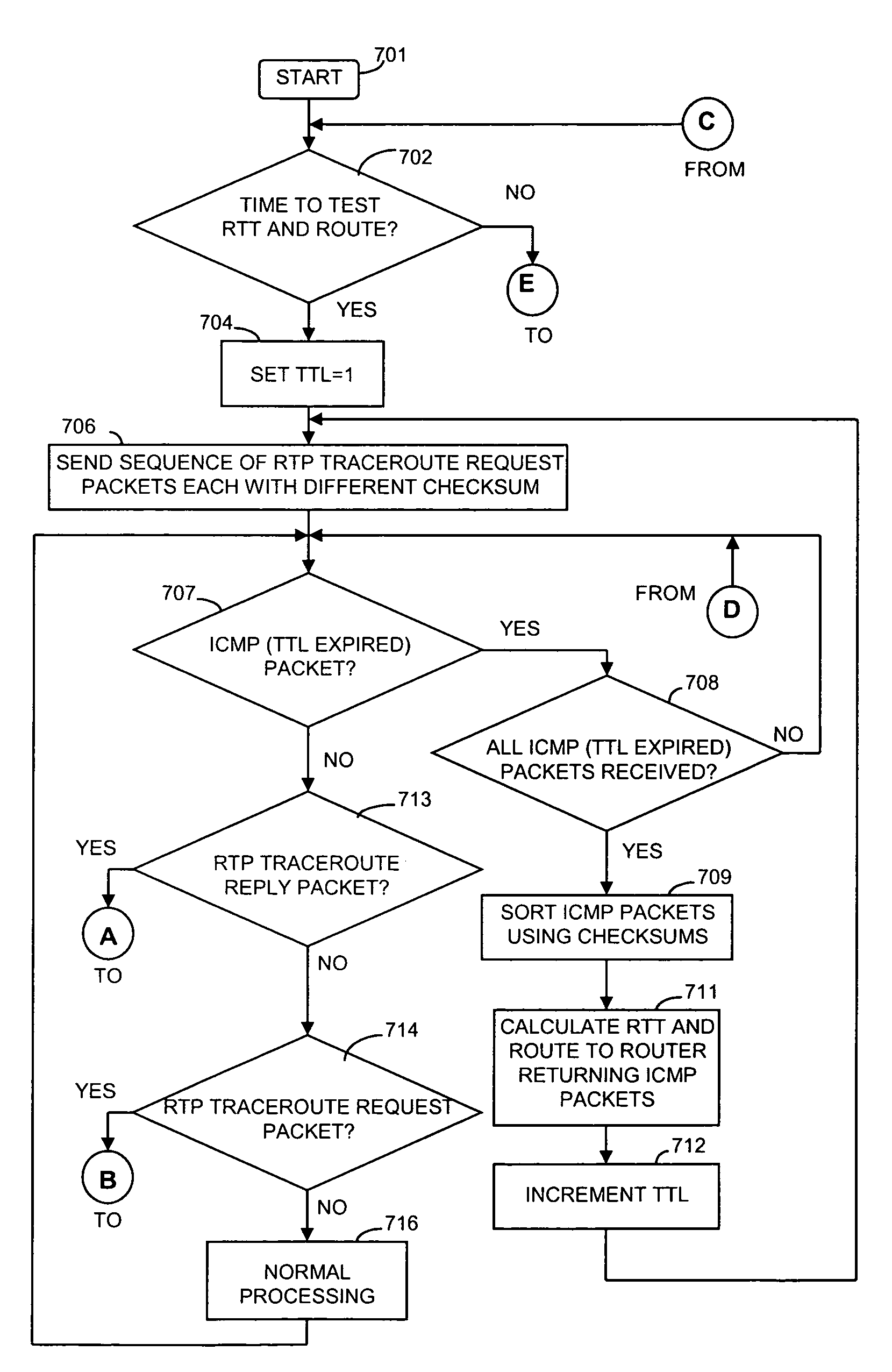
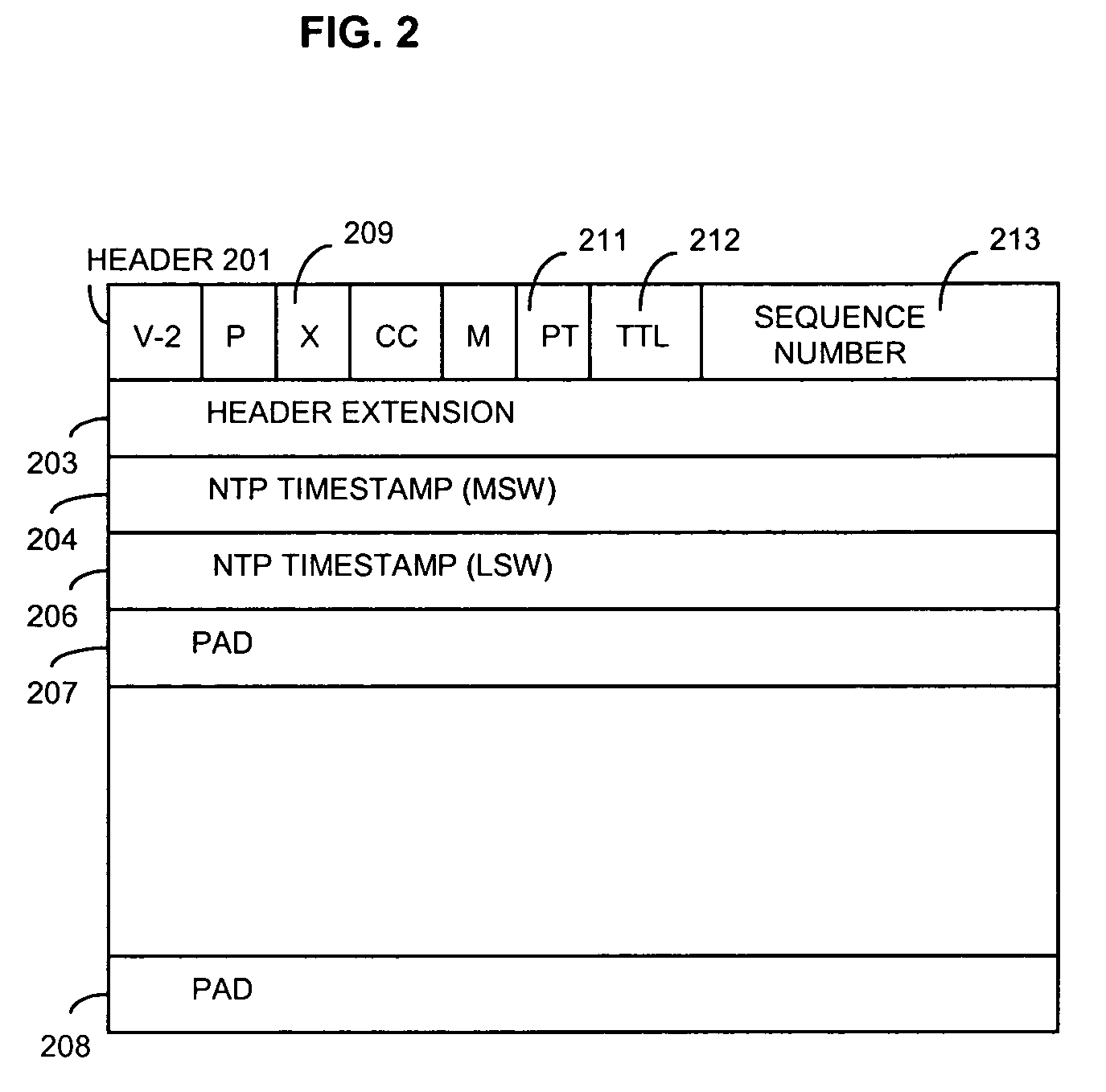
Method and apparatus for providing trace route and timing information for media streams
An apparatus and method that use media packets, such as Real-time Transport Protocol (RTP), packets with a specially define profile to determine the route and round-trip-time information. The route is determined by transmitting by a first network endpoint one or a group of media packets having a number of hops equal to a predefined number and the network address of a second endpoint, incrementing the number of hops upon a non-media packet being received in response to the one or group by a network node because the number of hops was exceeded at that network node. After recording the identification of that network node and incrementing the number of hops, the network endpoint re-transmits the one or group of media packets. The round-trip-time information is determined by timestamp information inserted into the one or group of media packets by the first network endpoint and timestamp information inserted into another one or another group of media packets transmitted from the second network endpoint to the first network endpoint in response to receipt of the one or group of media packets.
Owner:AVAYA INC
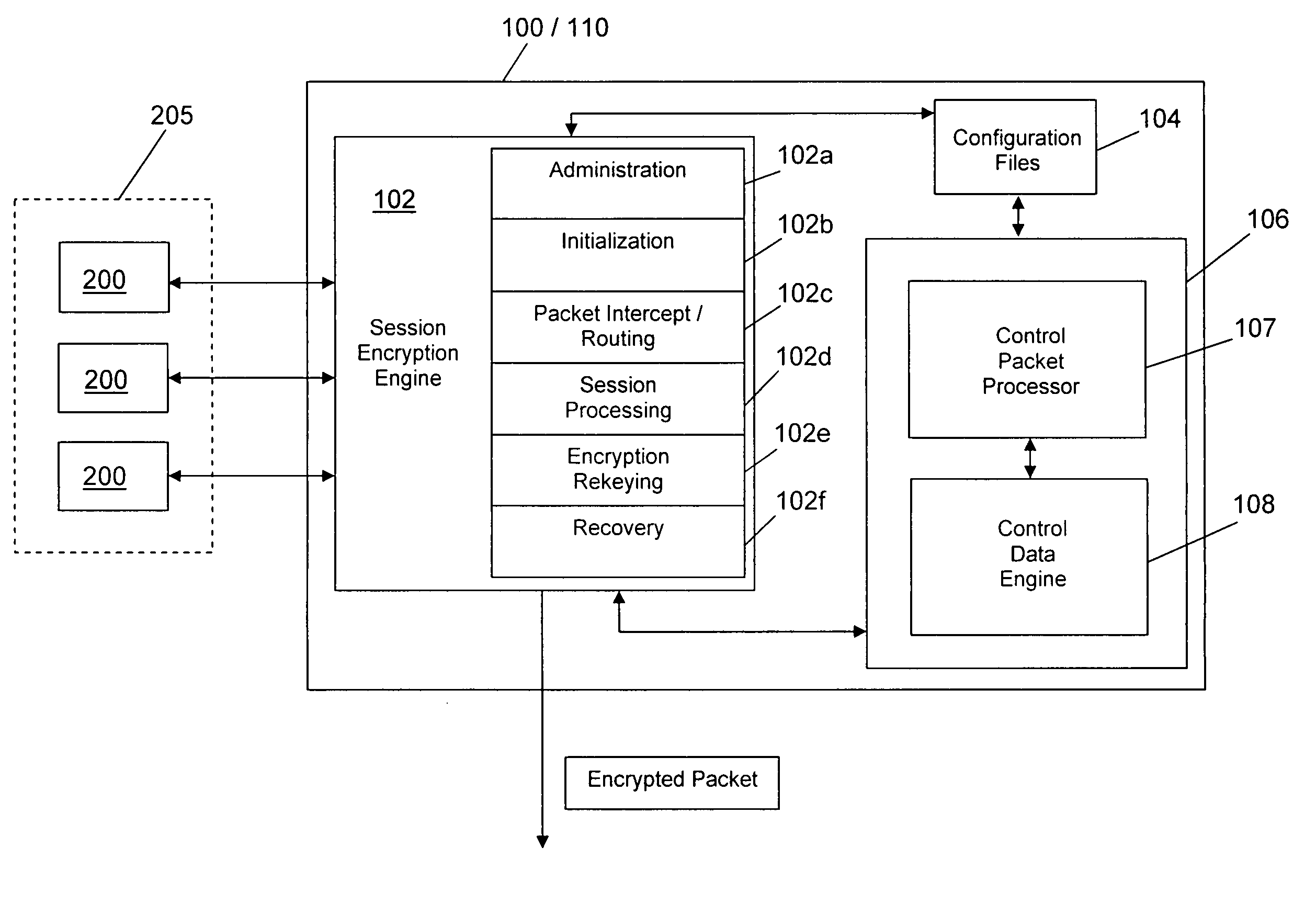
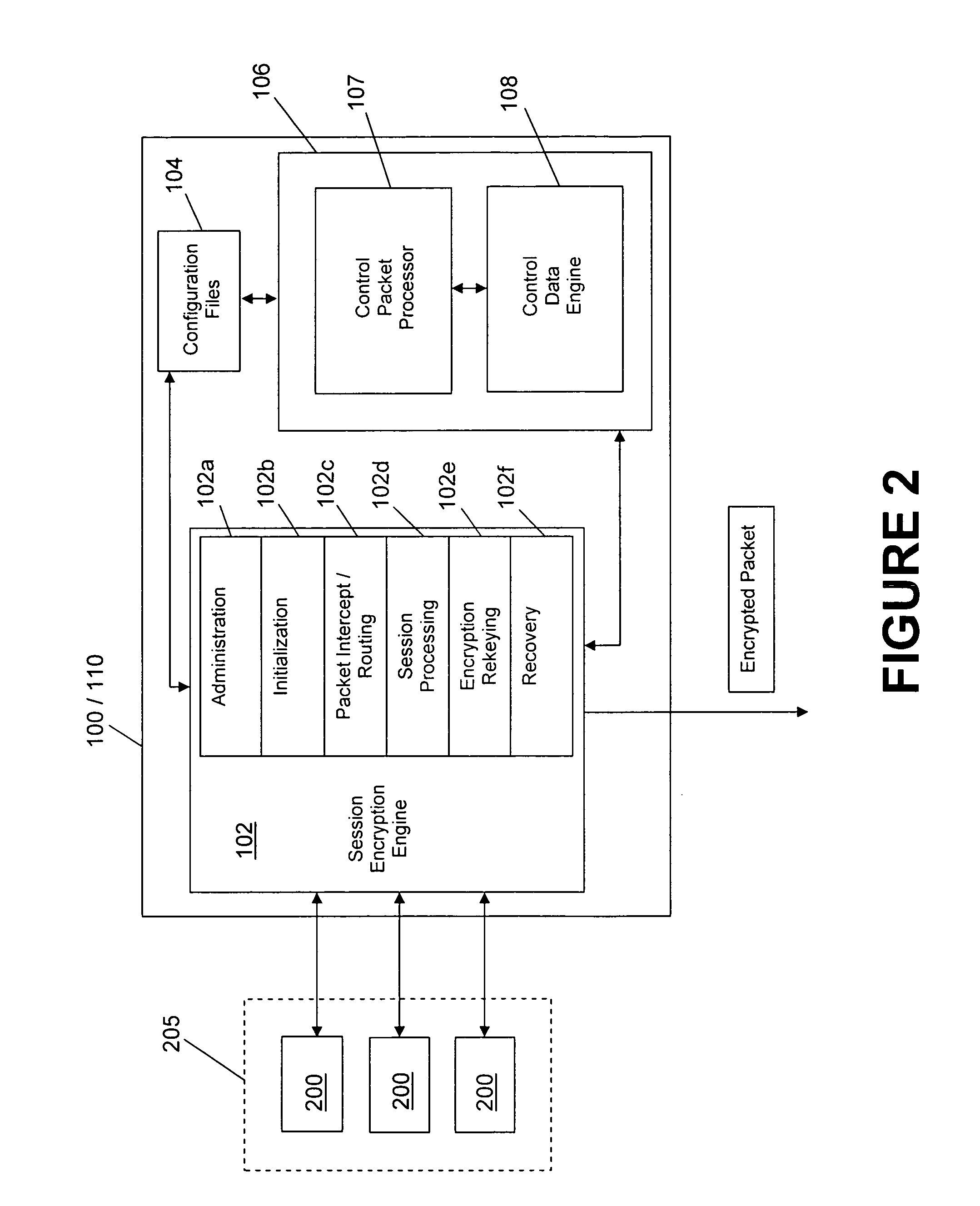
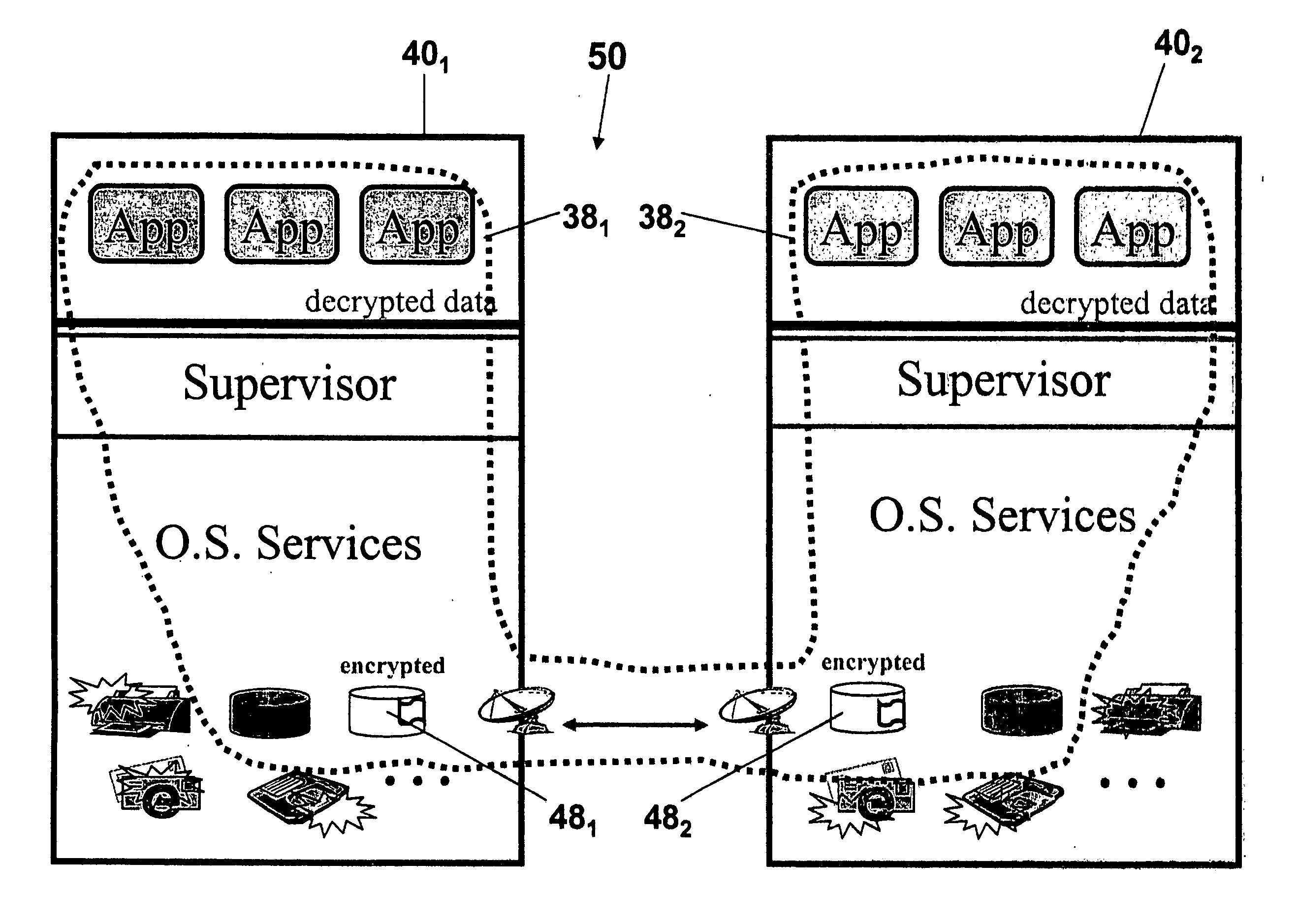
System and method for encryption rekeying
Disclosed is a system and method for maintaining a secure, encrypted networking session across a communications network by dynamically replacing encryption keys during the networking session and without terminating the session. A secure control channel is embedded within the general encrypted network connection and is used to transport encrypted control messages from one network endpoint to another. In order to hide that fact that such control messages are being transferred (as opposed to general network data traffic), the control message data packets are formatted in a way to simulate the standard general network data packets.
Owner:VELOCITE SYST
Acceleration through a network tunnel
Methods and systems for implementing acceleration through a packet encapsulation protocol tunnel, are described. The method includes establishing a packet encapsulation protocol tunnel between a first network endpoint and a second network endpoint, sending packets with a packet encapsulation protocol tunnel header from the first network endpoint to the second network endpoint, and removing the packet encapsulation protocol tunnel headers from the packets. The method further includes storing the packet encapsulation protocol tunnel headers in a storage memory, performing acceleration on the packets, and retrieving the packet encapsulation protocol tunnel headers from the storage memory. Further, the method includes replacing the packet encapsulation protocol tunnel headers on the packets, and sending the packets with the packet encapsulation protocol tunnel headers through the packet encapsulation protocol tunnel to the second endpoint.
Owner:VIASAT INC
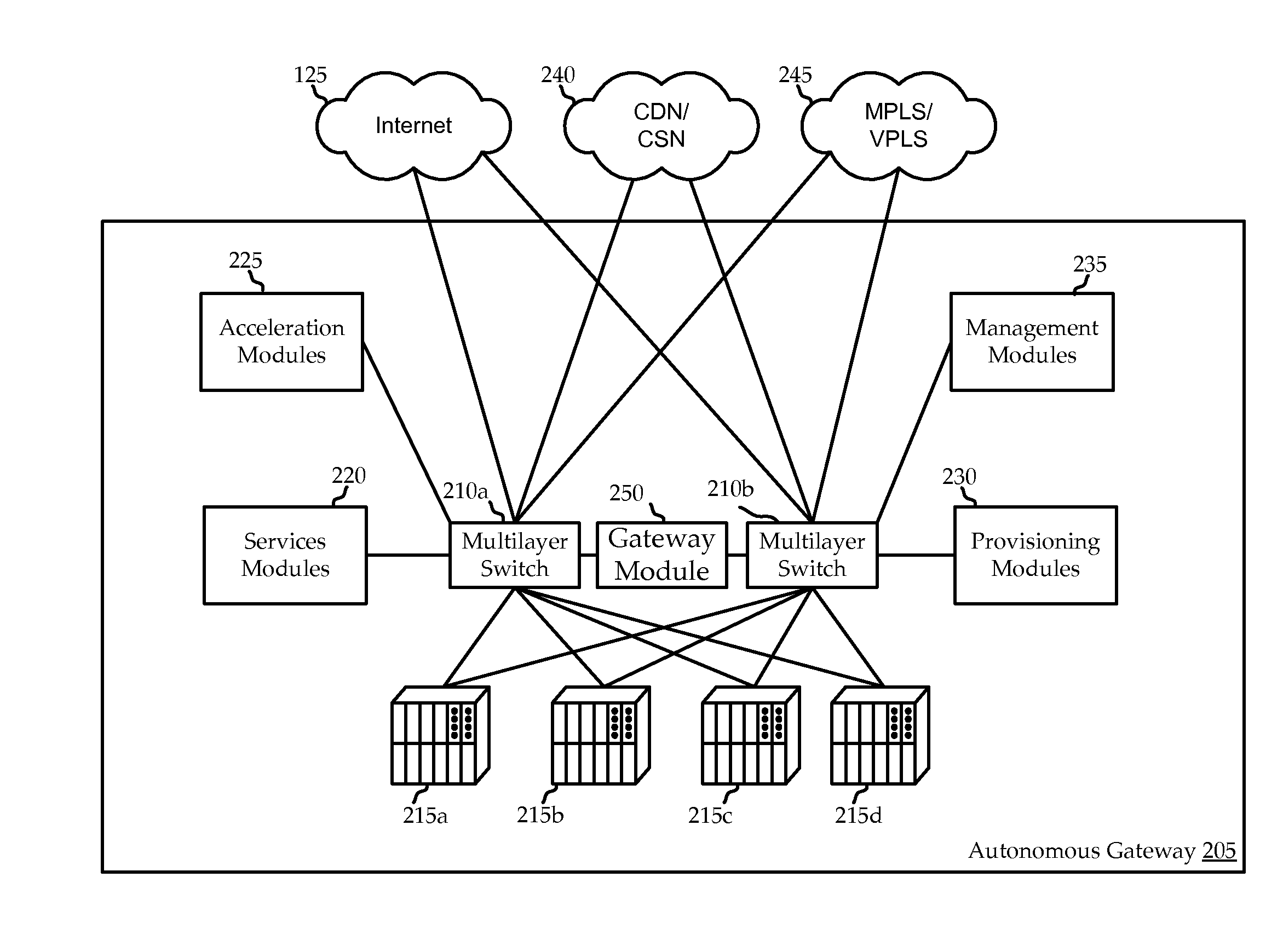
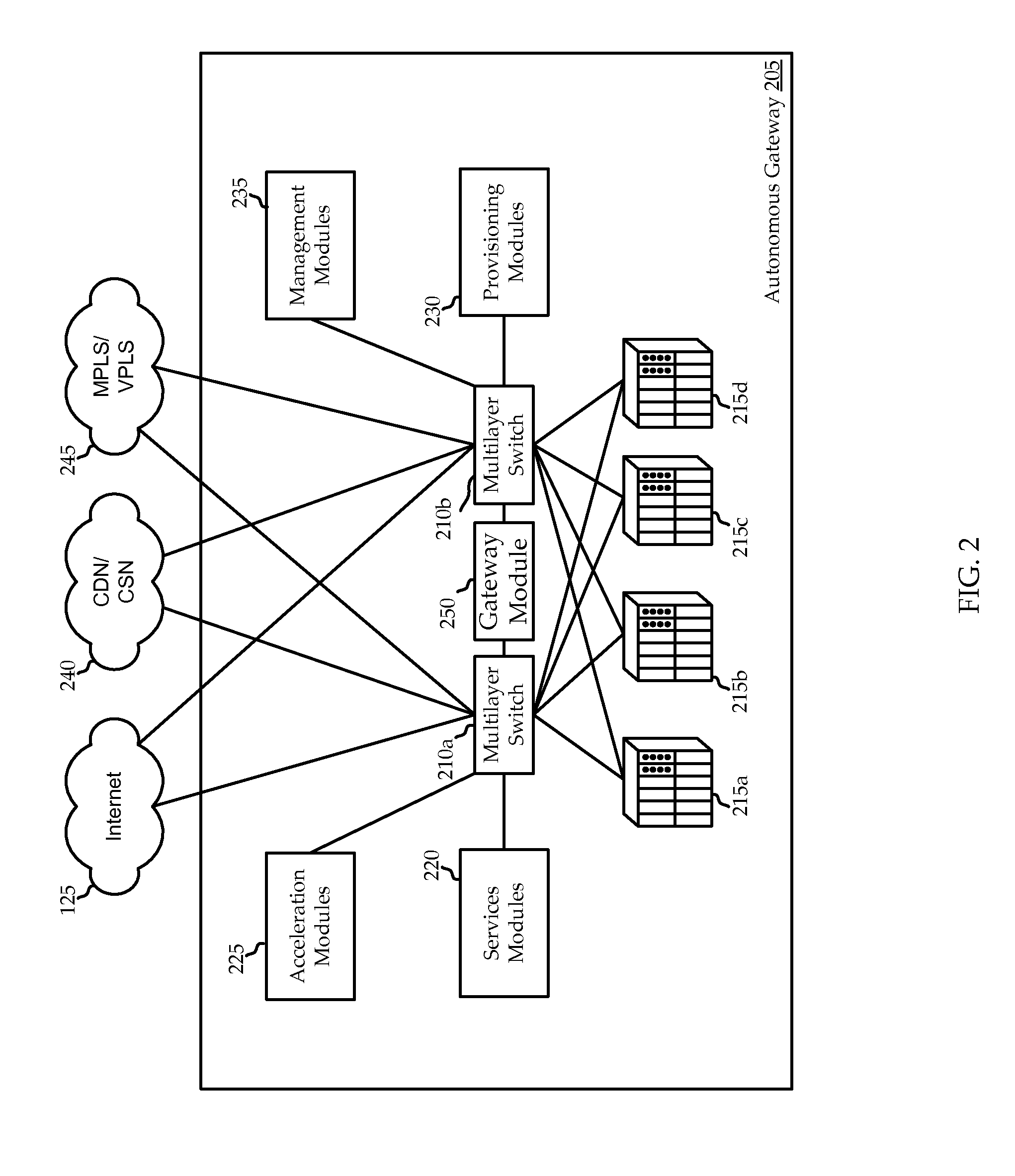
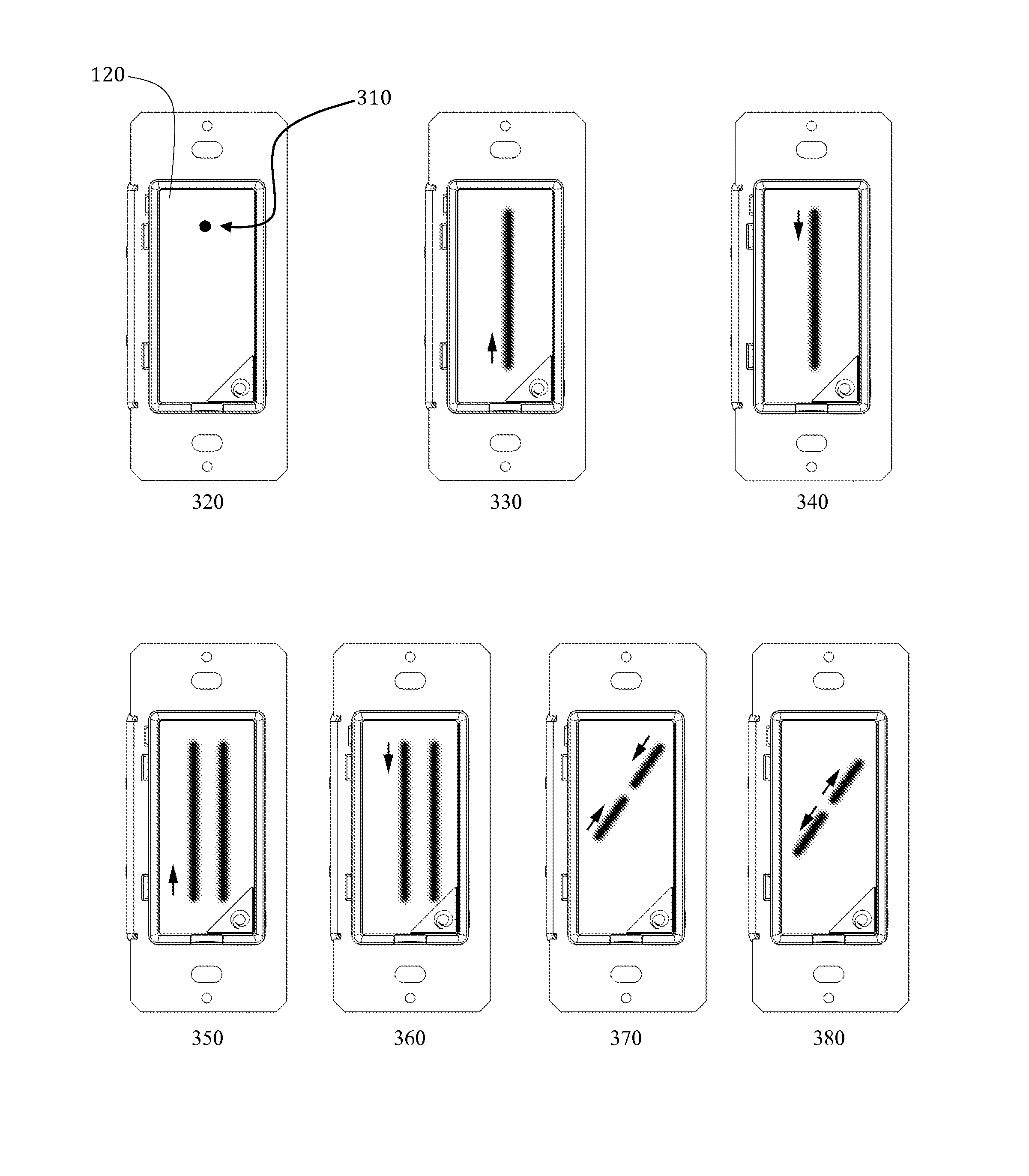
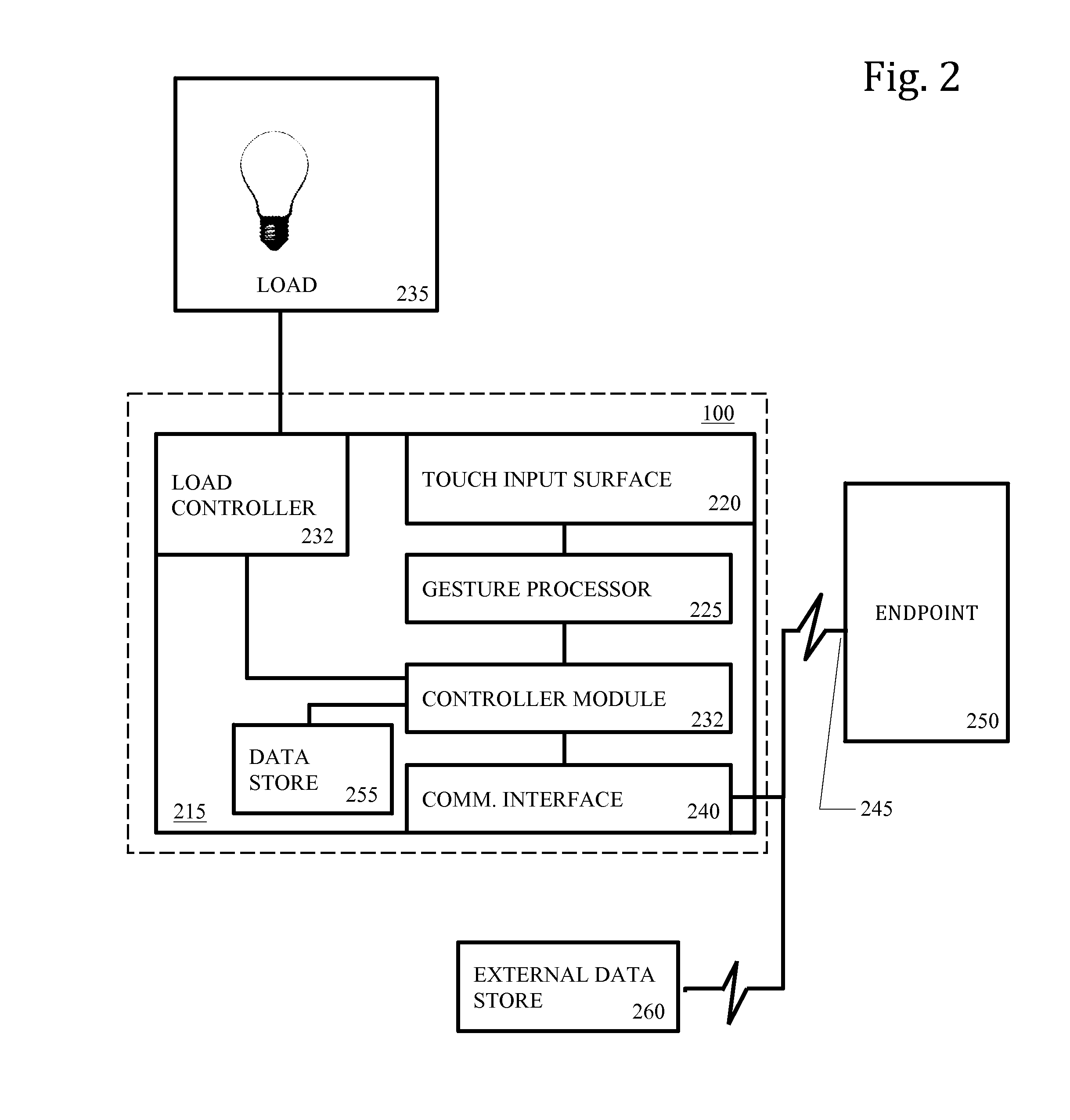
Wall-Mounted Multi-Touch Electronic Lighting- Control Device with Capability to Control Additional Networked Devices
InactiveUS20140253483A1Raises number of potentialIncrease the number ofInput/output for user-computer interactionGraph readingNetwork connectionControl signal
An in-wall, touch-actuated electronic control device makes use of gesture motions. A touch sensor permits a user to input control commands through the use of one or more one- or two-dimensional gestures such as one- or two-fingered tapping; swiping; tracing; pinching; and zooming, allowing for a significant increase in the potential number of network endpoints that can be controlled from, and also in the number of control signals that can be generated by, a single touch-control device. The touch-control device may include both a direct load controller such as a light switch or dimmer as well as a network connection to allow control of networked devices, either on a local network (for example a home WiFi network) or, for example, Web applications hosted on a remote server.
Owner:UBE INC DBA PLUM
Method and system to provide secure data connection between creation points and use points
InactiveUS20070061870A1Easy to implementDigital data processing detailsMultiple digital computer combinationsData connectionAccess method
A method and system for creating a secure network access method is provided. The system creates a secure network environment beyond the traditional network endpoints to include the contents transferred through the secure network, stored in the endpoint machine, and utilized by the applications residing on the endpoint machine.
Owner:TING ANNSHENG +1
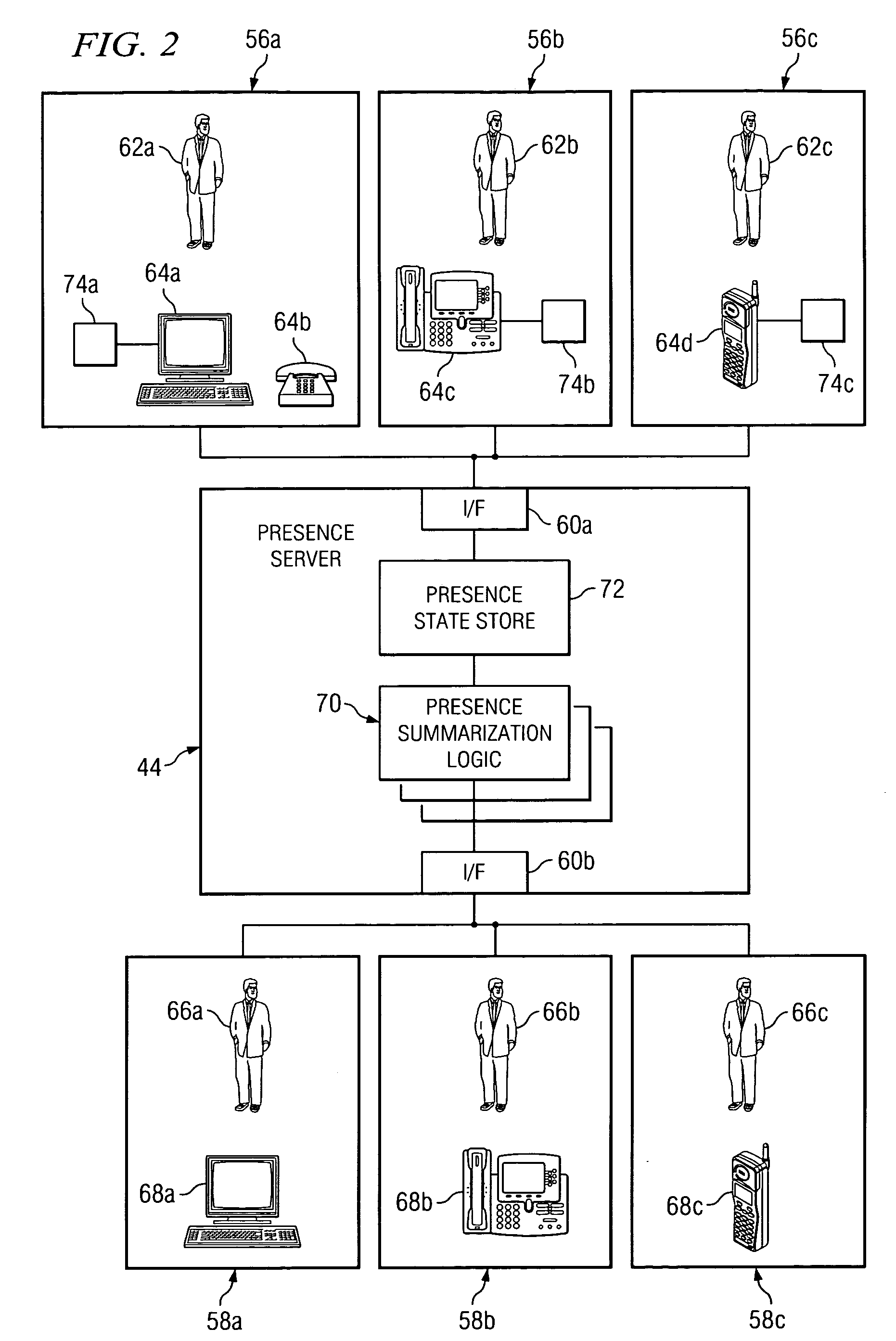
Method and system using presence information to manage network access
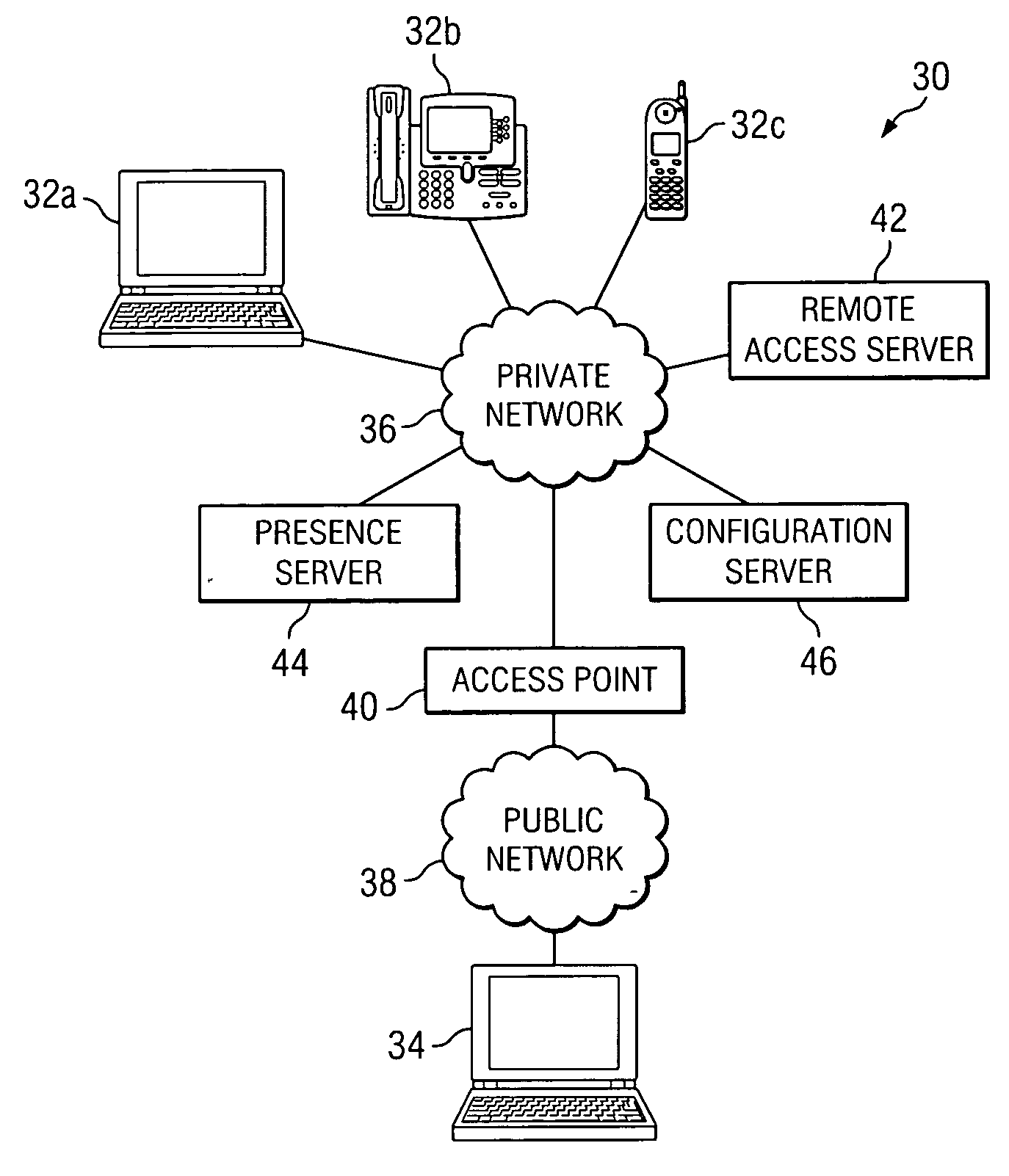
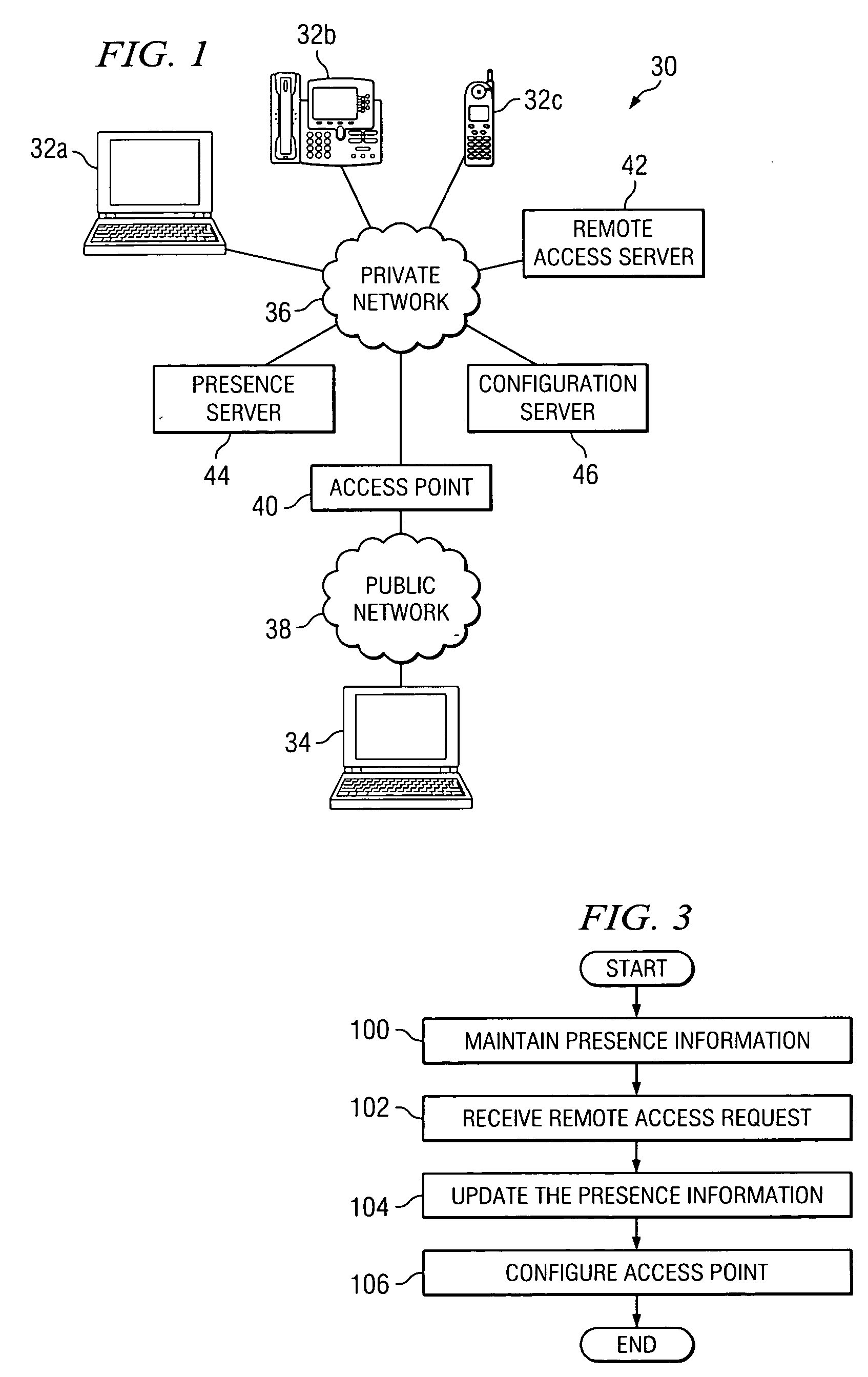
ActiveUS20060259958A1Eliminates and reduces of disadvantageEliminates and reduces of and problemDigital data processing detailsUser identity/authority verificationAuto-configurationIp address
In accordance with a particular embodiment of the present invention, a method using presence information to manage network access includes maintaining presence information for an end user. When a remote access request is received from the end user at a remote endpoint, the presence information for the end user is updated to identify the presence of the end user at one or more network endpoints associated with a private network. An access point to the private network is then automatically configured to allow any communications addressed to an IP address associated with the one or more network endpoints to pass through the access point.
Owner:CISCO TECH INC
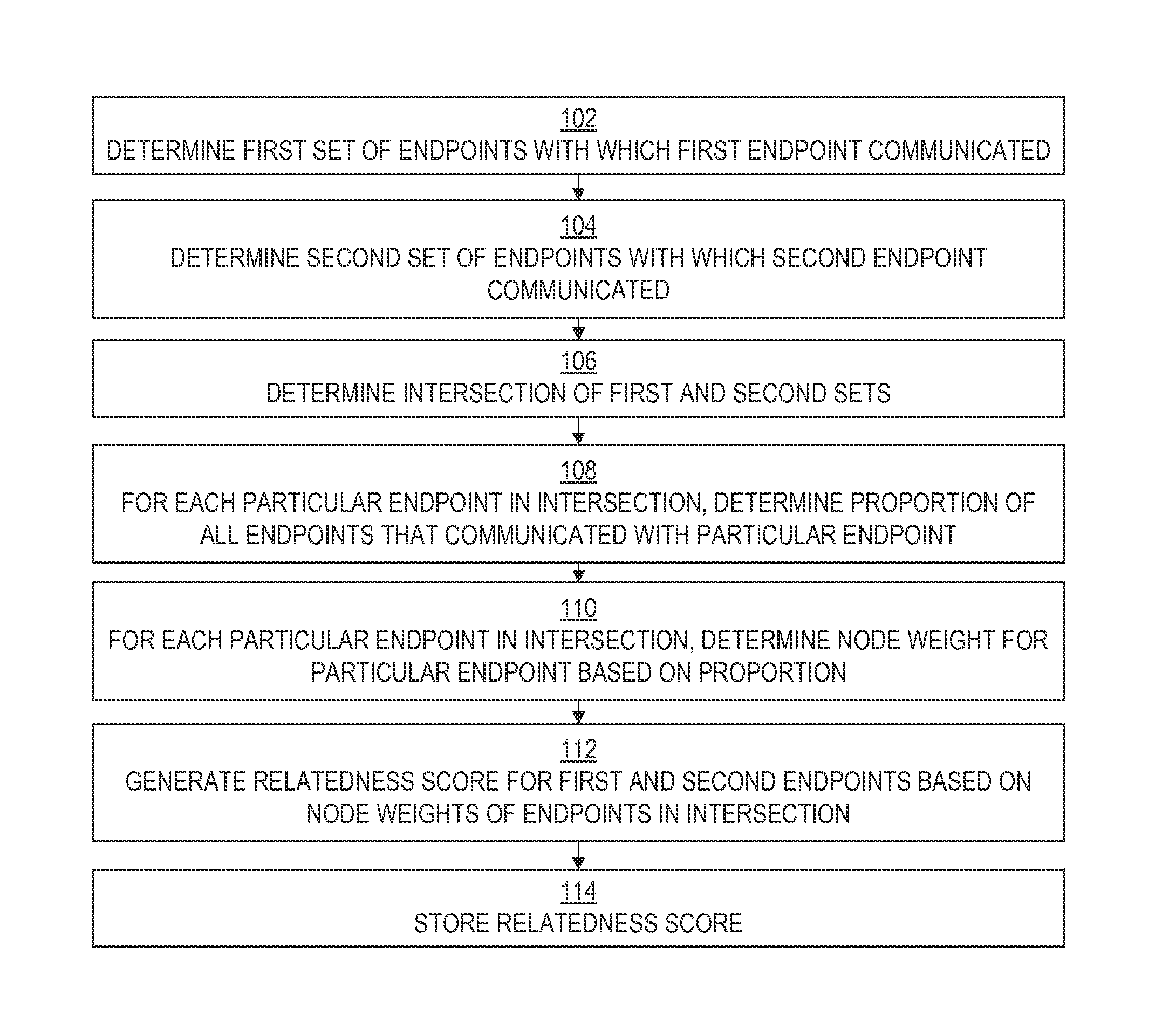
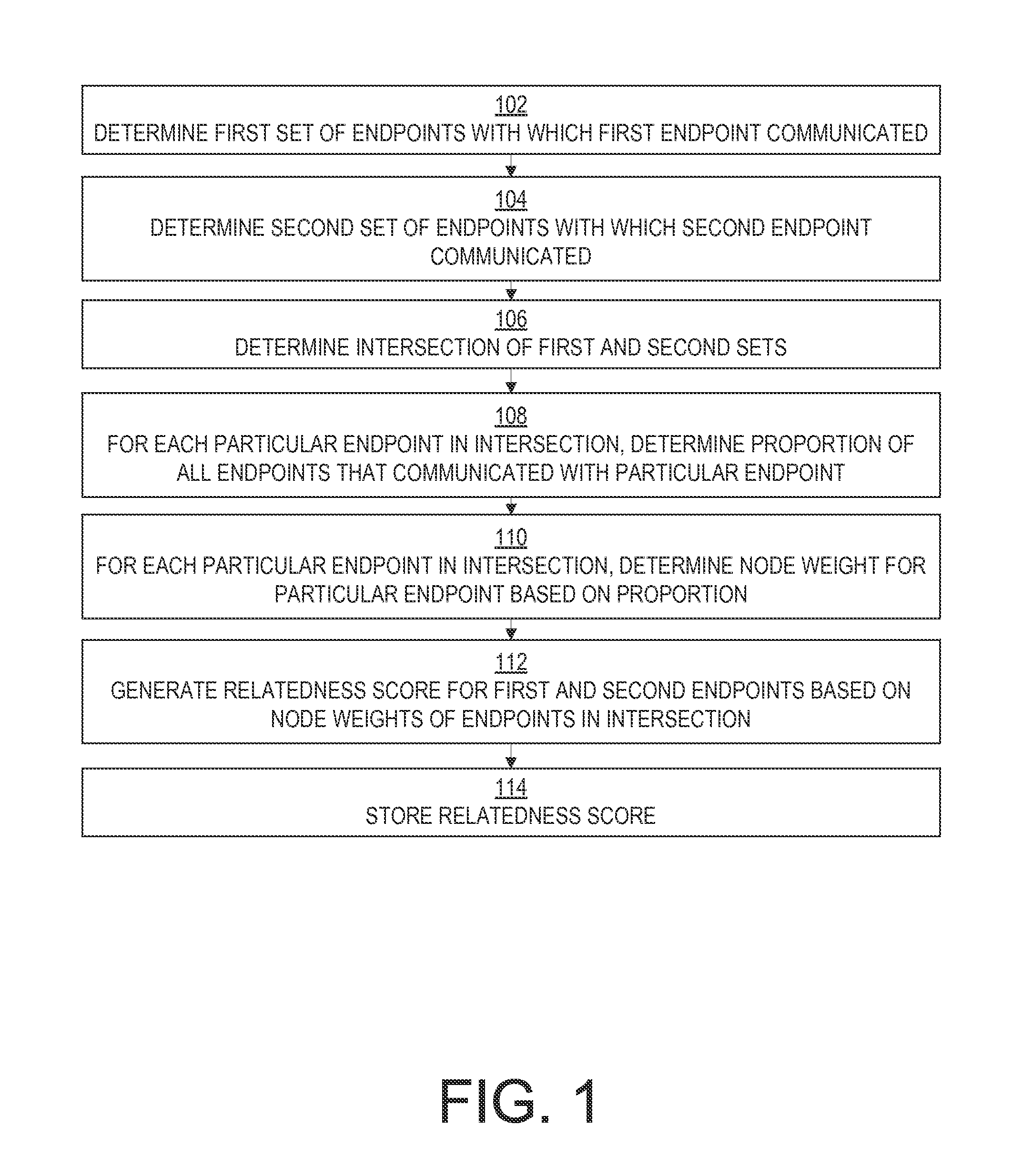
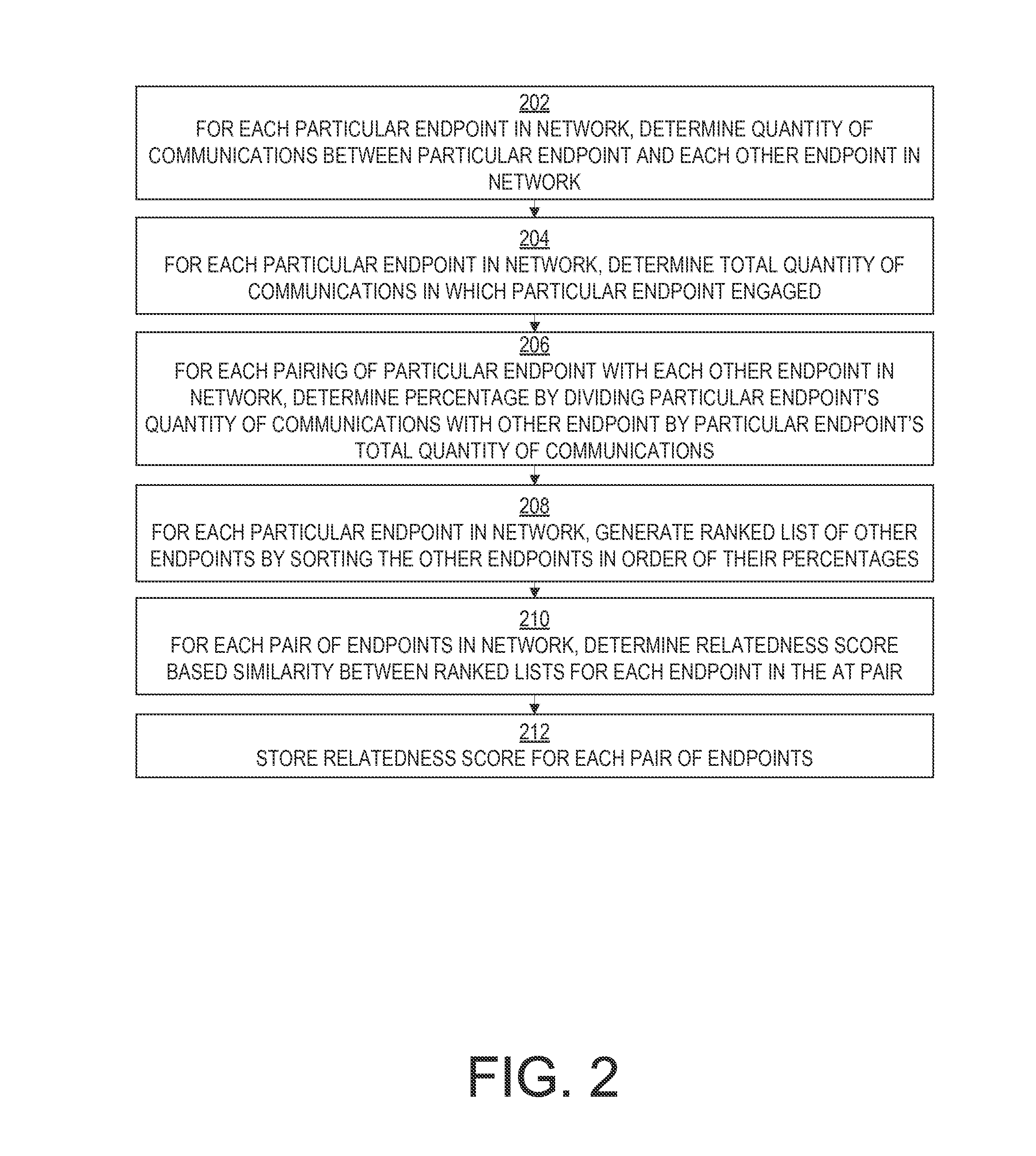
Implicit relationship discovery based on network activity profile similarities
InactiveUS20150319256A1Reduce the impactLess determineData processing applicationsTransmissionNetwork activityNetwork communication
An extent of relatedness between entities that might exhibit no express relationship is determined based on network communications with shared endpoints. Communications occurring in a network are monitored. For each particular endpoint in the network, a set of other endpoints with which that particular endpoint has communicated is determined based on the monitored communications. For each pair of endpoints in the network, the intersection of the sets determined for those endpoints is determined to be the set of shared endpoints for that pair. The endpoints in the set of shared endpoints can be inversely weighted based on their overall popularity among all of the network's endpoints. The weights of the shared endpoints in the pair's set of shared endpoints can then be multiplied together to produce a relatedness score for that pair of endpoints.
Owner:REDVECTOR NETWORKS INC
Techniques for providing connections to services in a network environment
ActiveUS7802007B2Multiple digital computer combinationsOffice automationBusiness processBusiness policies
Methods and apparatus for facilitating consumption of services via a services network are described. Access is provided to a services directory which identifies a plurality of services and at least one connector for facilitating consumption of each of the services via the network. Each connector is operable to mediate communication protocol and business policy differences between a first network end point associated with the corresponding service and a second network end point associated with a consumer of the service. For each of selected ones of the connectors, information accessible via the services directory is provided regarding how to use the connector to consume the corresponding service. For each of selected ones of the services, access to a connector design process is provided via the services directory. The connector design process is operable to facilitate creation of a new connector for the corresponding service, and to specify at least one business process for mediating the business policy differences.
Owner:SALESFORCE COM INC
Methods and systems for reciprocal generation of watch-lists and malware signatures
ActiveUS20140317735A1Avoid accessMemory loss protectionError detection/correctionNetwork activityWatch list
The present disclosure is directed to methods and systems for reciprocal generation of watch-lists and traffic models characteristic of malicious network activity. In some aspects, the described methods and systems relate to maintaining data for recognition of malicious network activity. In general, the methods include monitoring network traffic; comparing endpoint data from monitored data packets to endpoints in a watch-list of network endpoints and comparing packet data from monitored data packets to traffic models in a catalog of traffic models characterizing malicious network activity; and determining, based on the comparisons, that a set of data packets comprise suspect network activity. The methods include adding a network endpoint to the watch-list when the determination is based on comparing packet data to a traffic model or adding a traffic model to the catalog when the determination is based on comparing endpoint data.
Owner:VMWARE INC
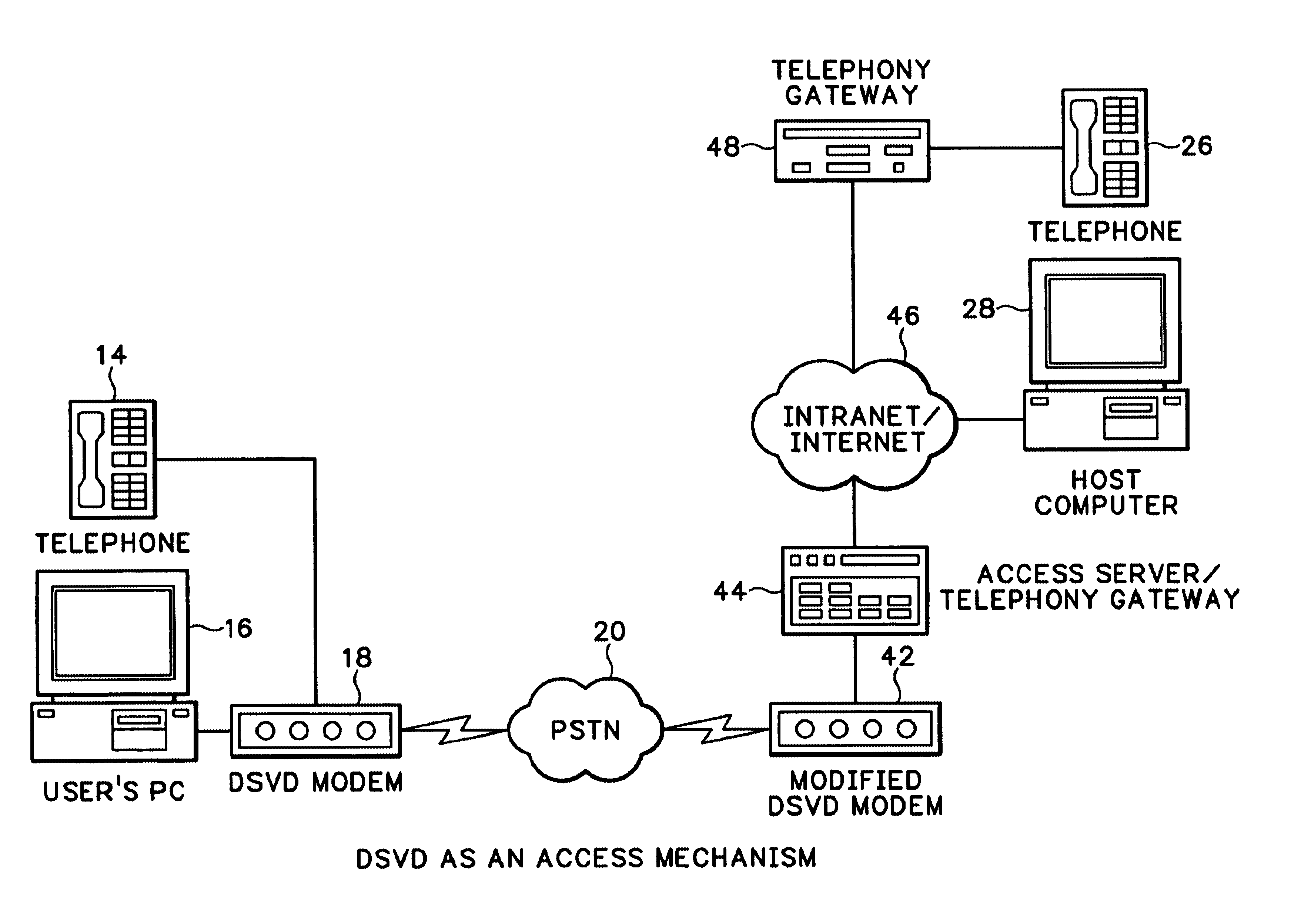
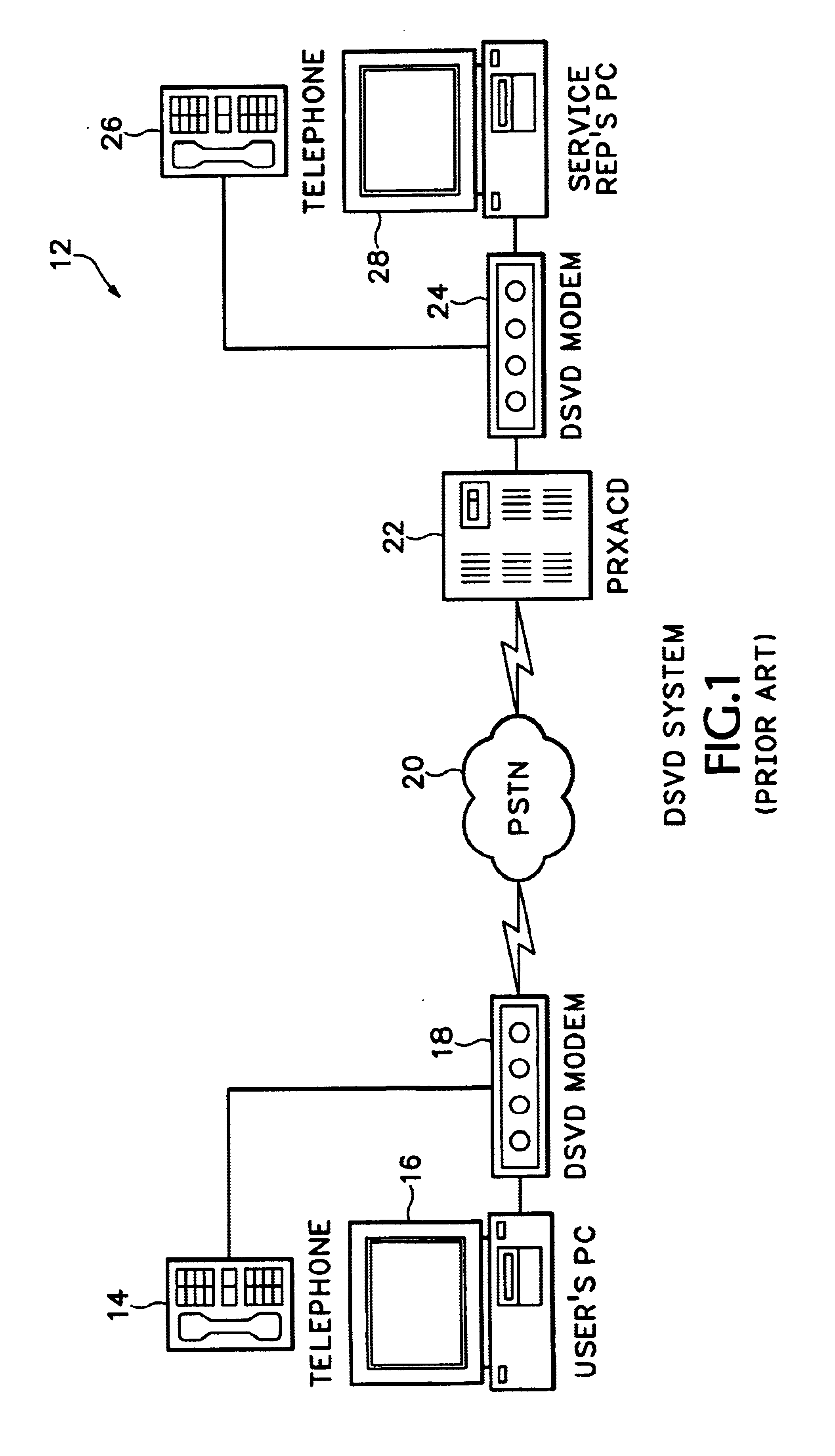
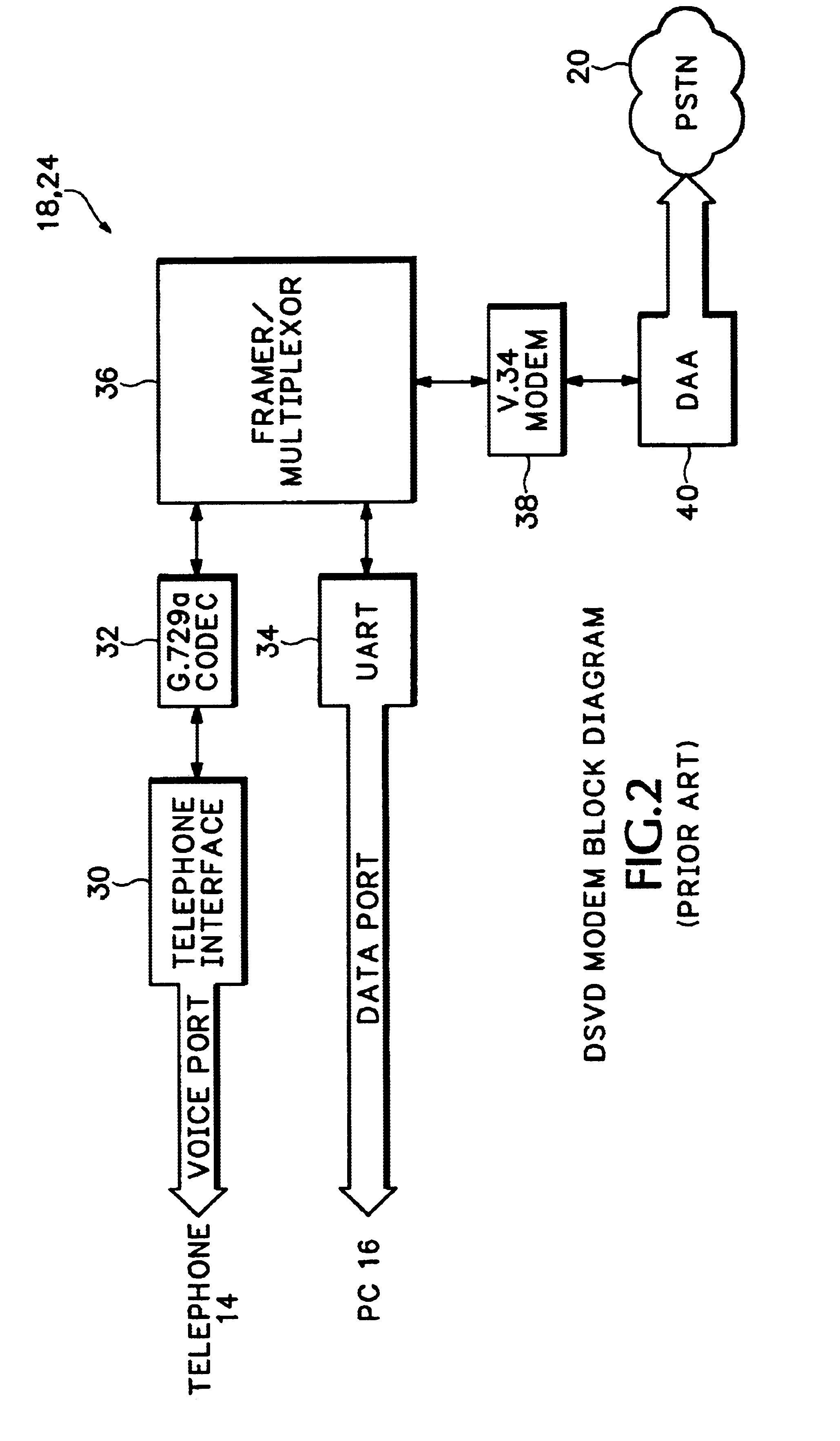
Asymmetric implementation of DSVD for voice/data internet access
InactiveUS6904037B2More dataEfficient routingTime-division multiplexData switching by path configurationNetwork access serverCable Internet access
Voice and data streams transmitted from a conventional DSVD modem are interfaced directly to a network access server through a modified DSVD modem according to the invention. The voice and data is formatted into network data packets that are then routed directly to different endpoints through the network access server. The modified DSVD modem includes a packet framer that removes conventionally transmitted V.76 DSVD framing formats and stuffs bytes into the voice and data to form network packets. The network access server then routes the voice and data packets to the different endpoints identified in a packet header. Since the voice and data are output from the DSVD modem in data packets, the voice and data can be routed more efficiently to different network endpoints.
Owner:CISCO TECH INC
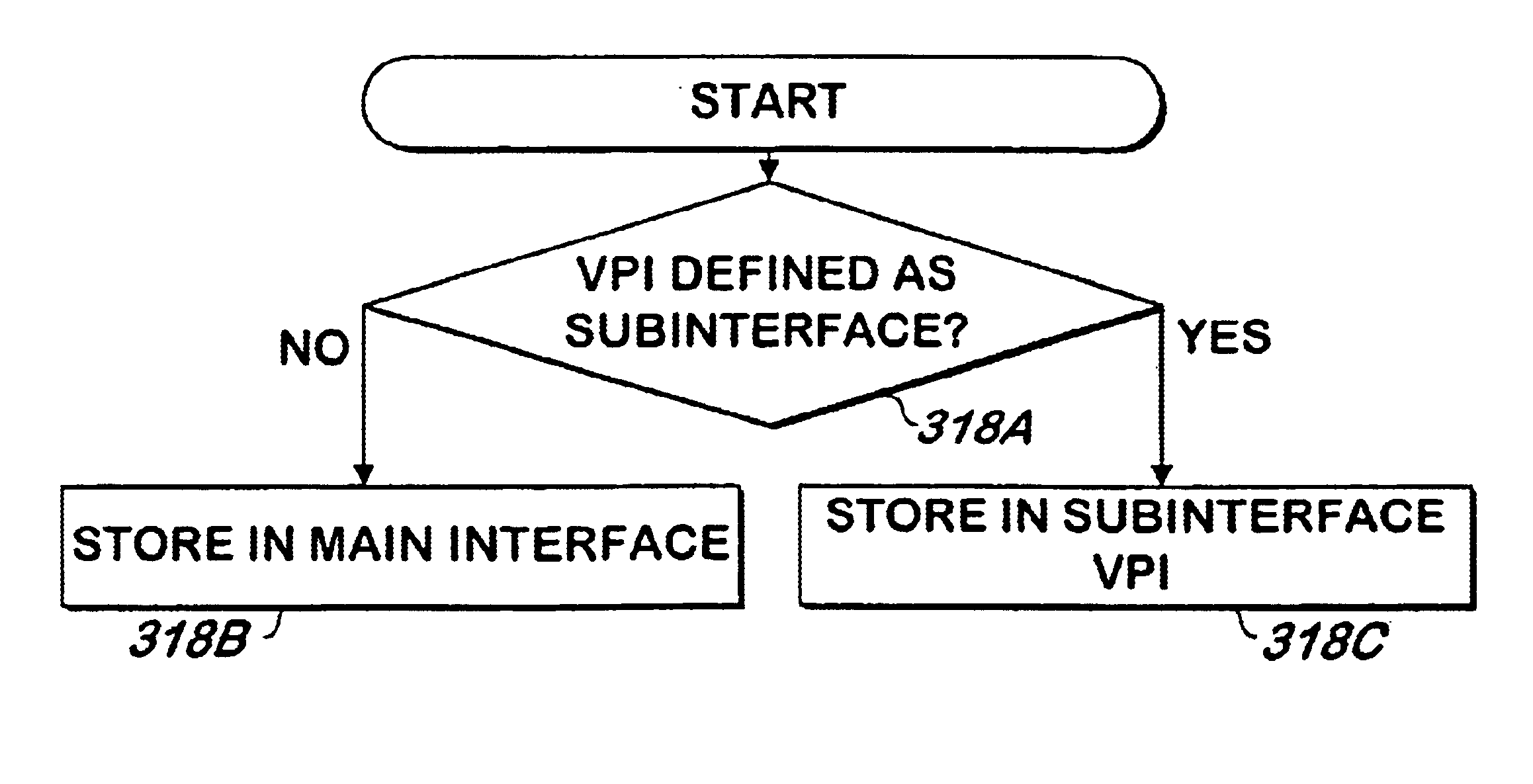
Method and apparatus for configuring permanent virtual connection (PVC) information stored on network devices in an ATM network logically configured with subnetworks
InactiveUS6700890B1Avoid mistakesShorten the timeDigital computer detailsData resettingPermanent virtual connectionComputer science
A method and apparatus retrieves and stores configuration information for network endpoint devices from other devices in the network, such as a switch adjacent to the endpoint device. When the endpoint device establishes a connection with the network, it generates a sequence of SNMP getnext commands using the ILMI interface to obtain the configuration information from the network device. If the network device sends a trap to the endpoint device indicating a change has been made to the configuration parameters stored in the network device for a PVC, a series of SNMP getrequest commands are made using the ILMI interface to retrieve the configuration information for that PVC from the network device. If the endpoint device detects an interruption in communication with the network device, the endpoint device discards the information retrieved previously.
Owner:CISCO TECH INC
Enhancement of end-to-end network QoS
InactiveUS7936772B2Data switching by path configurationNetwork connectionsEnd to end qosNetworking protocol
A network endpoint system and related method and computer program product for use in a network to support enhanced end-to-end QoS in the network. The network endpoint system is adapted to receive network data of varying priority on behalf of a data consumer operating at the application layer of a network protocol stack implemented by the network endpoint system. The network endpoint system includes a network interface controller adapted to receive network frames containing the network data, plural network data handling channels each having an associated priority, and priority processing logic adapted to transfer the network data from the network interface controller to the plural data handling channels on a prioritized basis according to the network data priority. Also disclosed are a network interface controller and a network node to support enhanced end-to-end QoS in a network.
Owner:INT BUSINESS MASCH CORP
Method for reducing congestion in packet-switched networks
InactiveUS7227843B2Reduce congestionReduce usageMetering/charging/biilling arrangementsError preventionExchange networkThe Internet
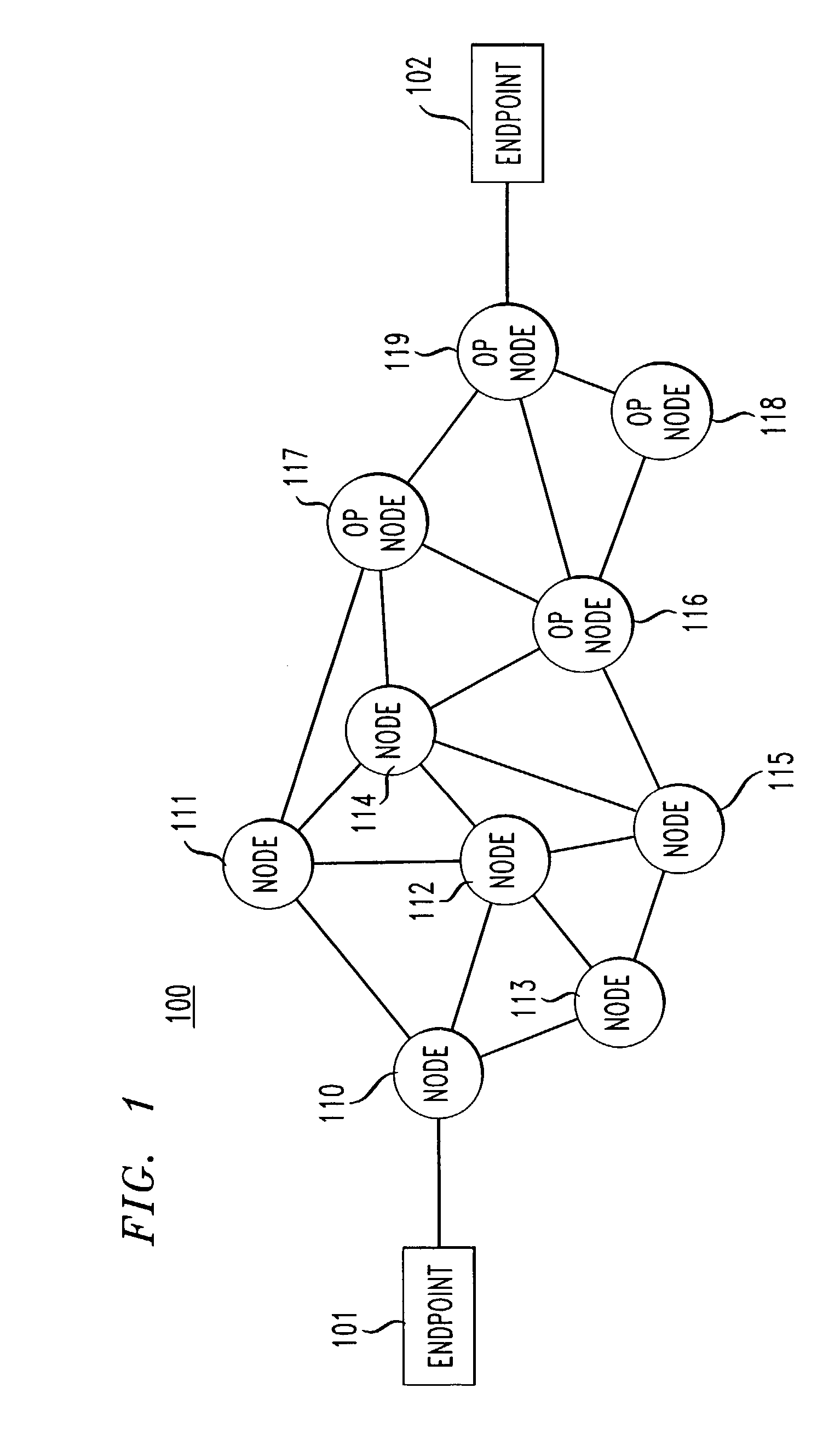
The present invention permits a network service provider to detect an operational condition—such as congestion—in a packet-switched network and to alleviate such congestion by providing customer incentives to avoid use of the network. The detection mechanism triggers an incentive such as the modification of the user's access charges and the customer can be immediately notified of either the occurrence of the congestion or of information regarding the incentive. Usage of the network during congested periods can be deterred by imposing additional access charges during such periods—similarly, customers can be given a discount to encourage usage during periods of low congestion. An incentive schedule can be tailored to dynamically change the usage patterns of the customers of the network to accommodate the operational conditions in the network. The present invention has application in the Internet, where a detection / notification mechanism, for example, can be implemented in a network node such as a router or in a network endpoint such as a client machine or a proxy or mail server.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com