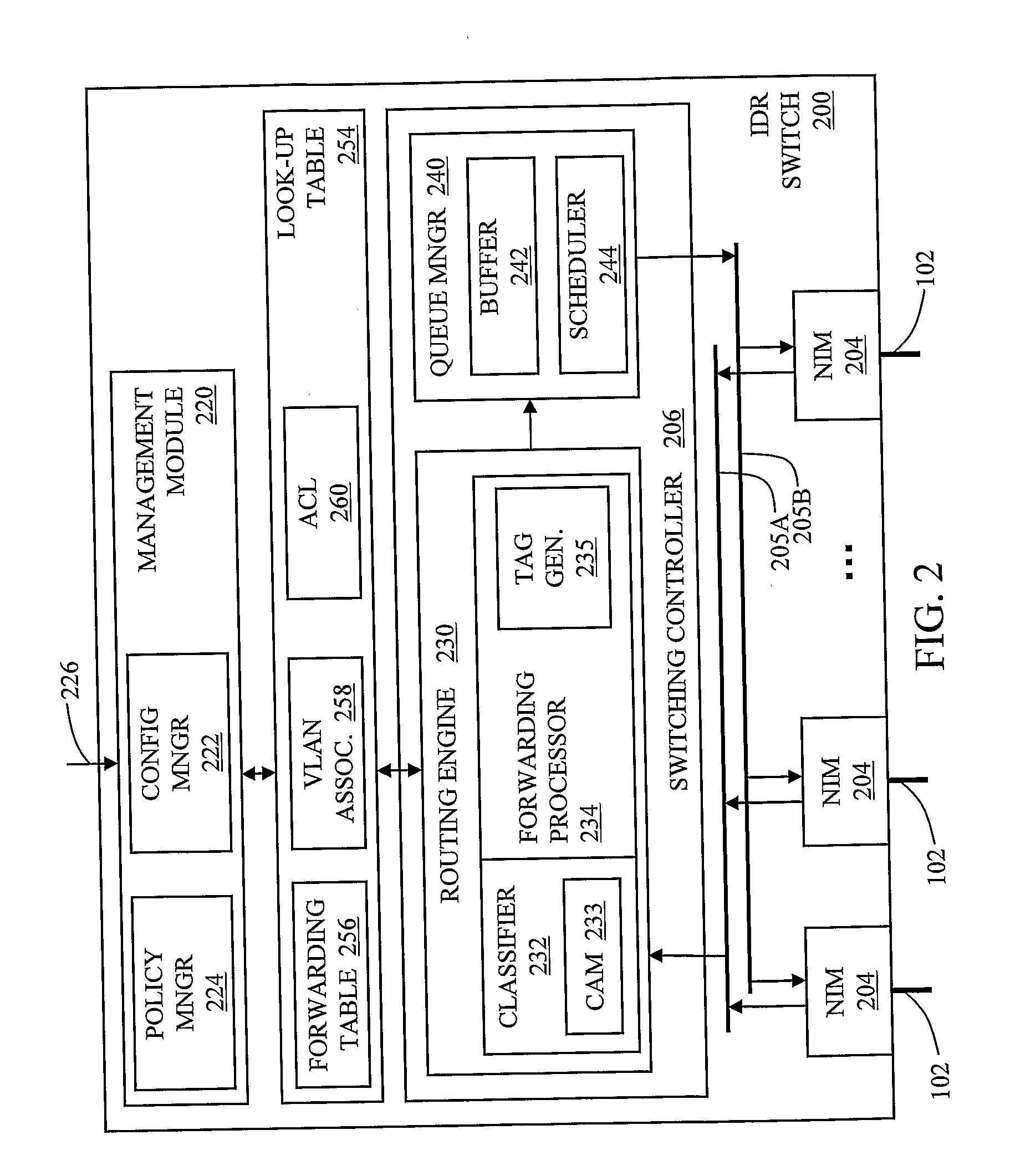
Patents
Literature
1101 results about "Access control list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
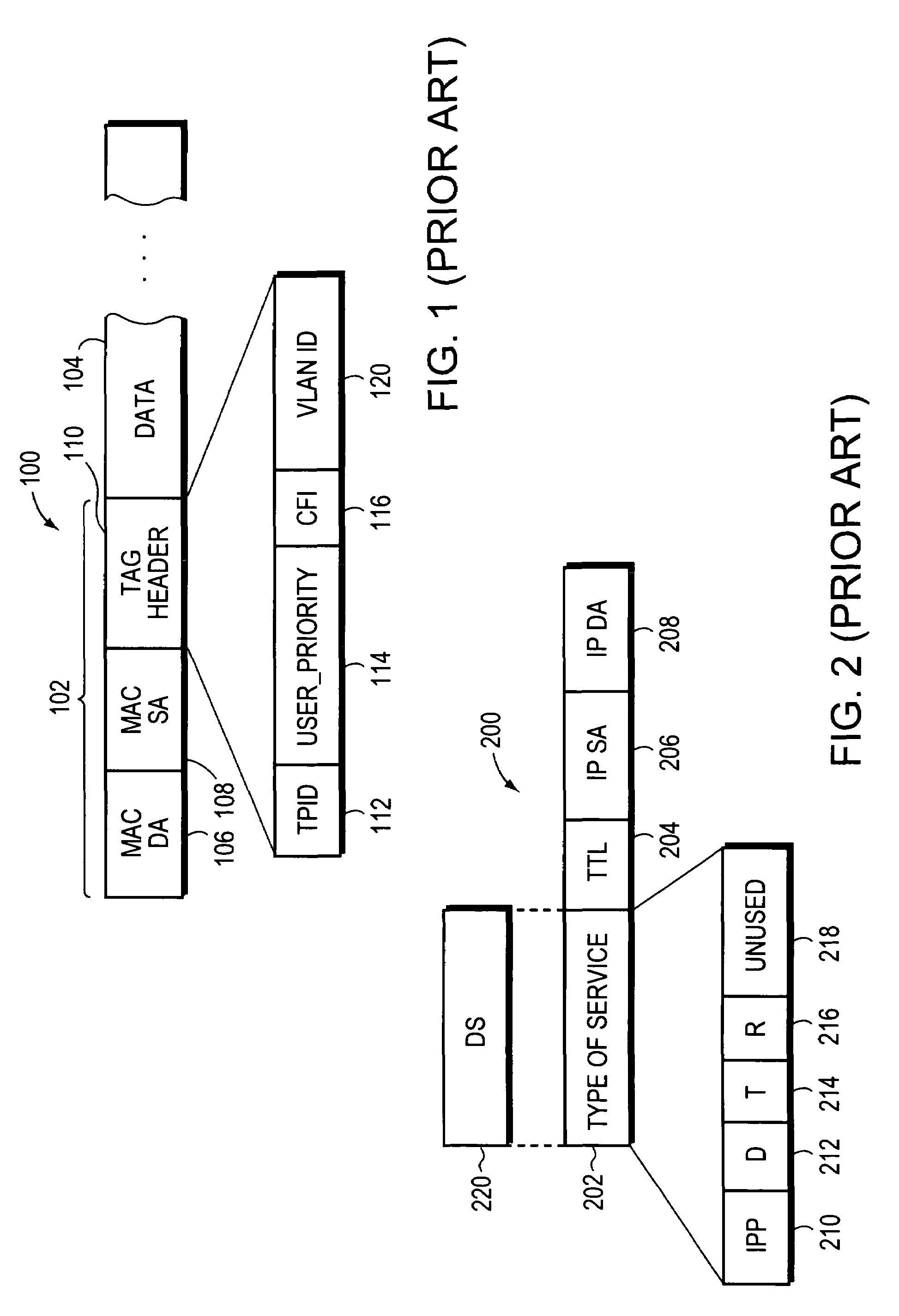
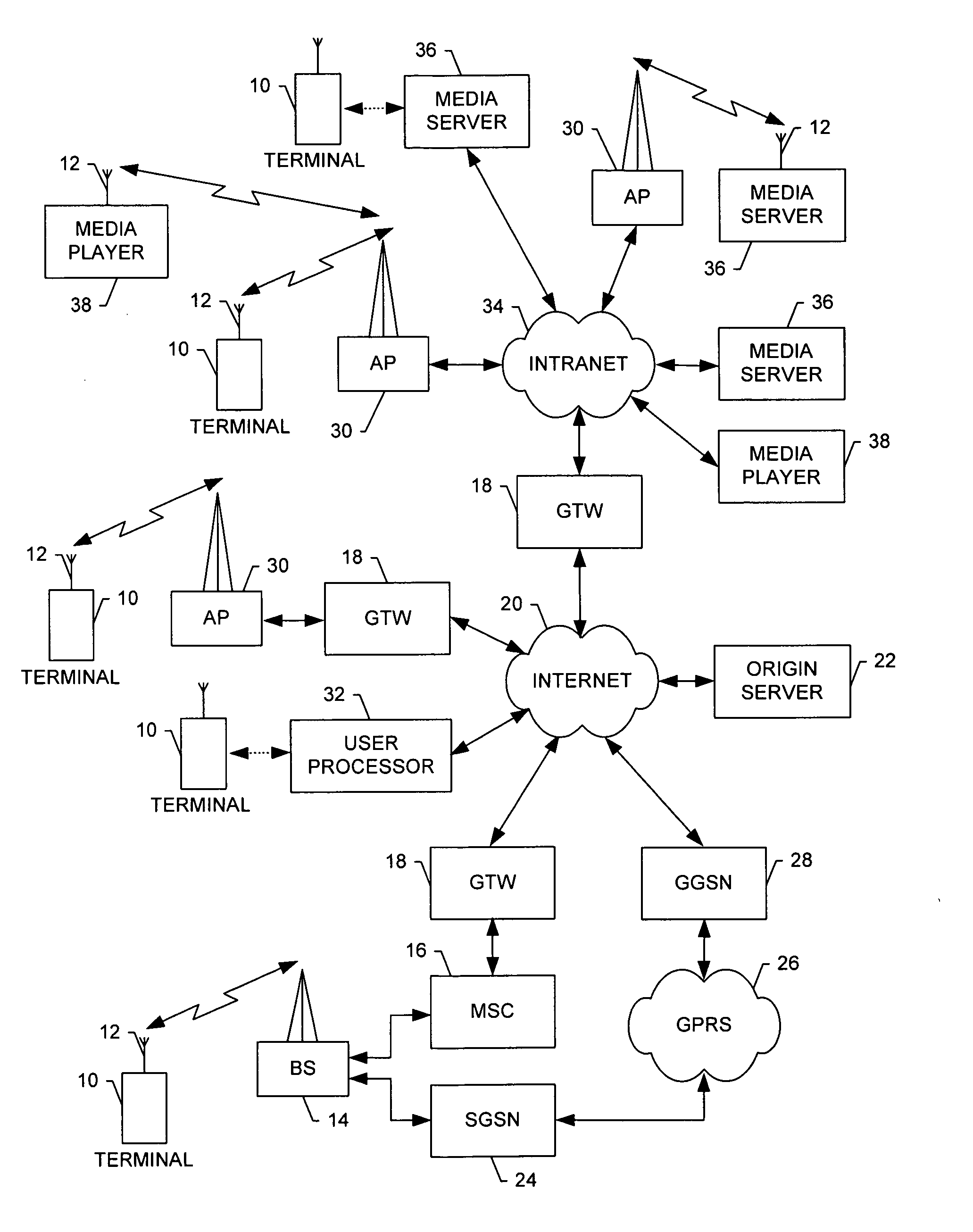
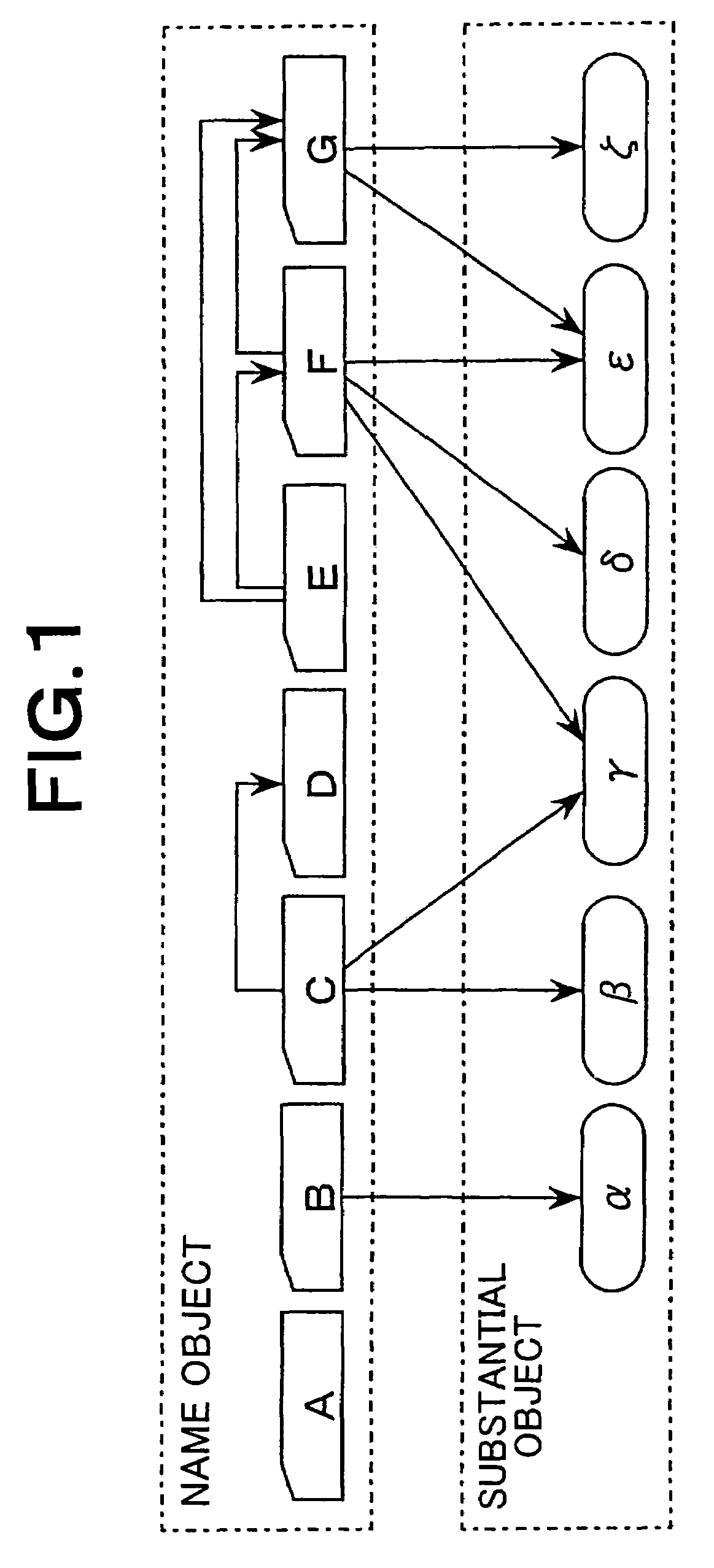
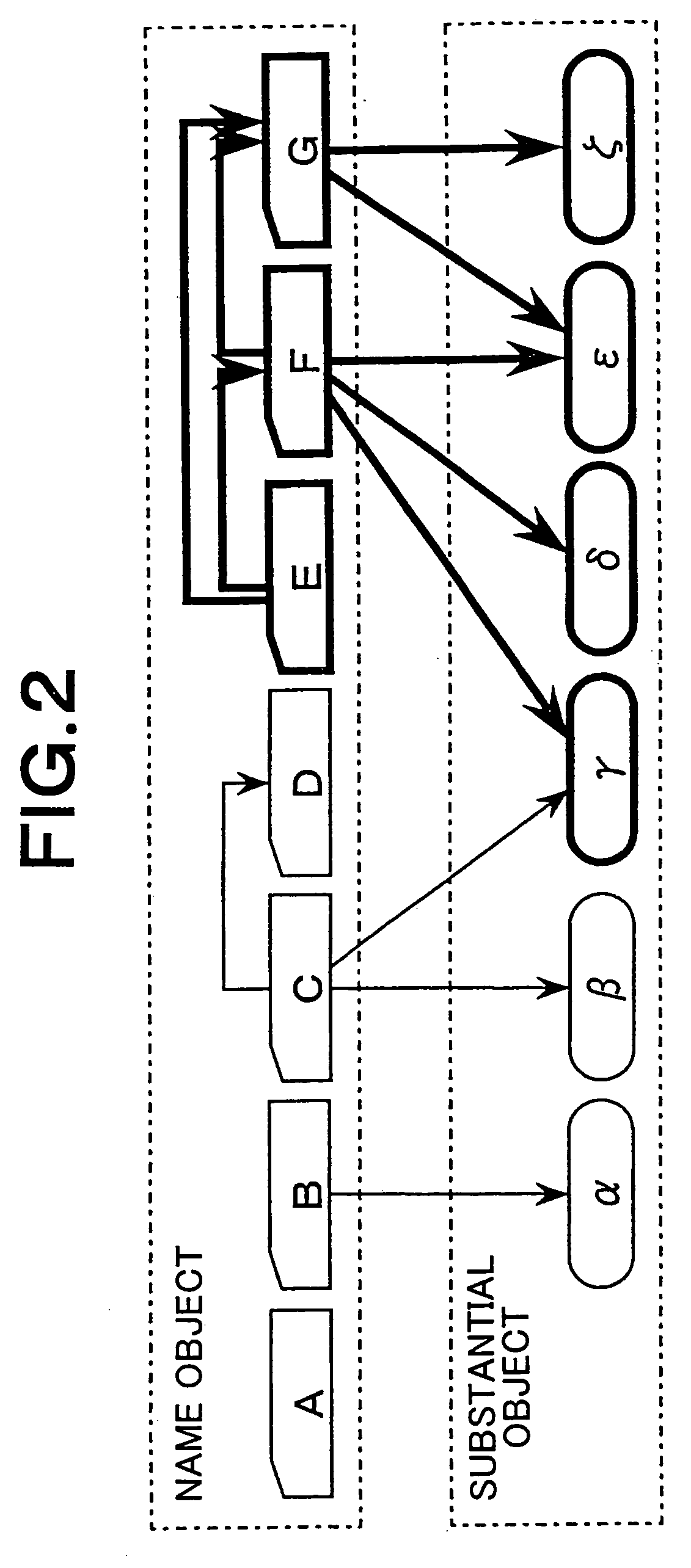
An access-control list (ACL), with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject and an operation. For instance, if a file object has an ACL that contains (Alice: read,write; Bob: read), this would give Alice permission to read and write the file and Bob to only read it.
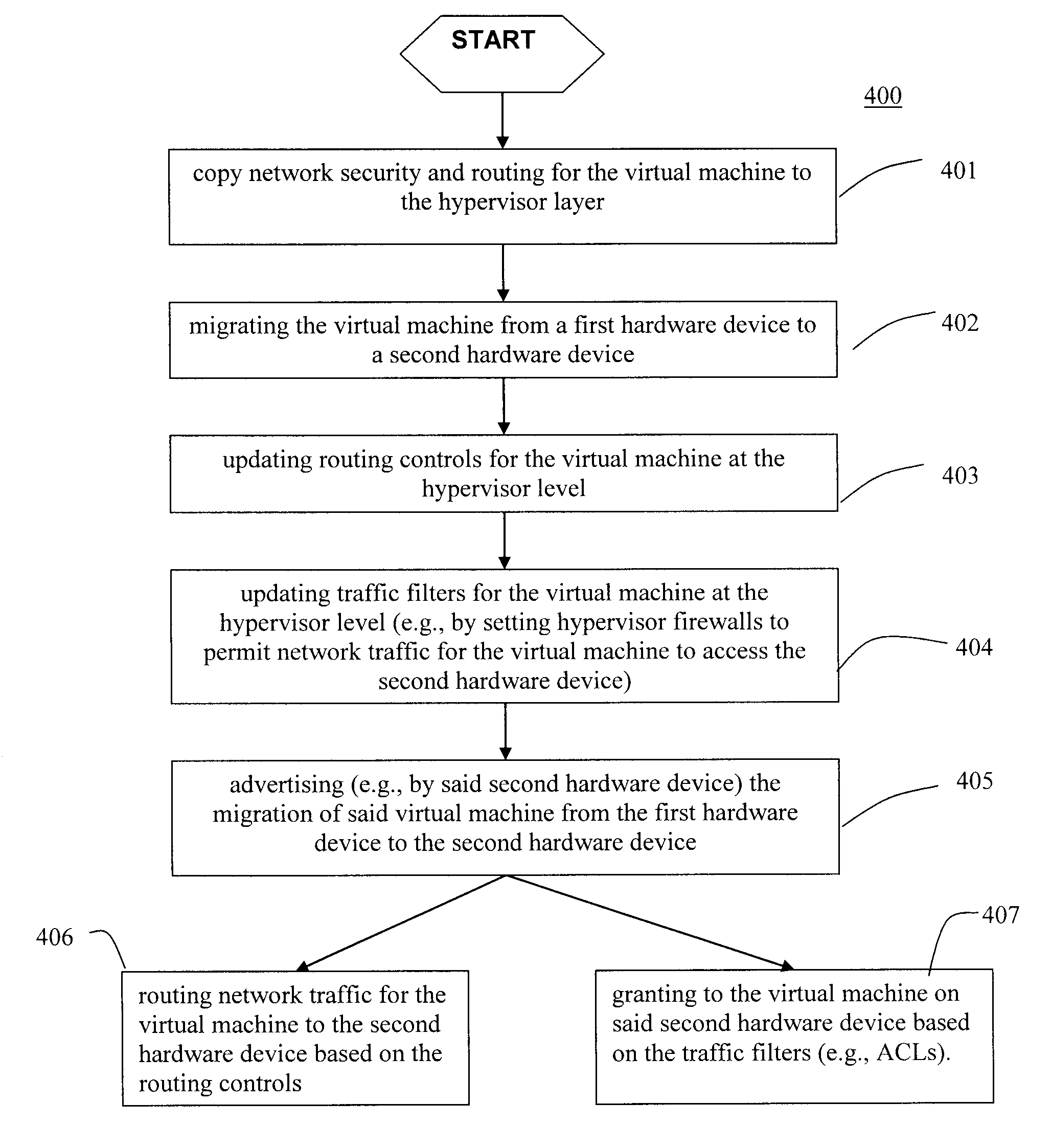
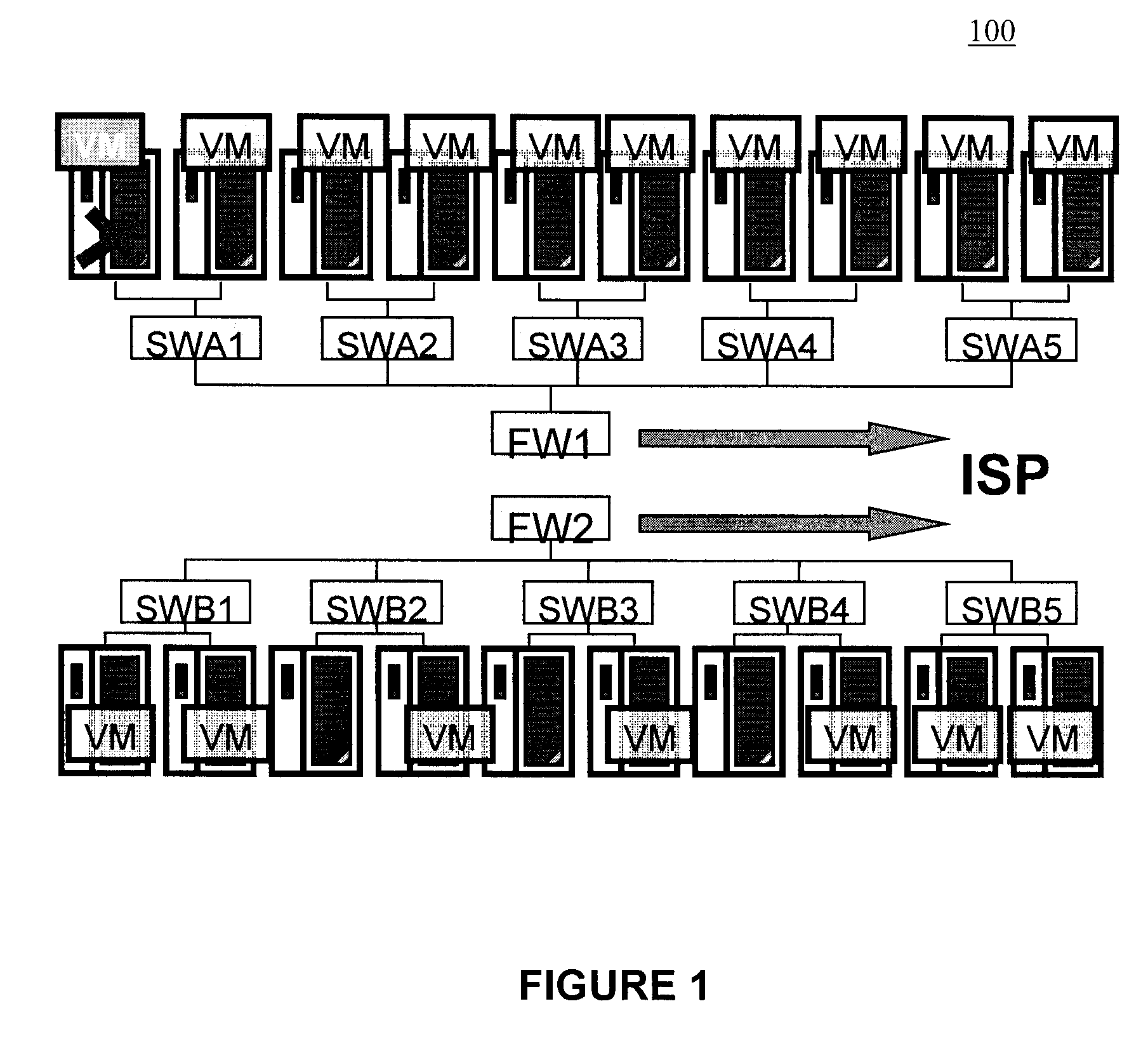
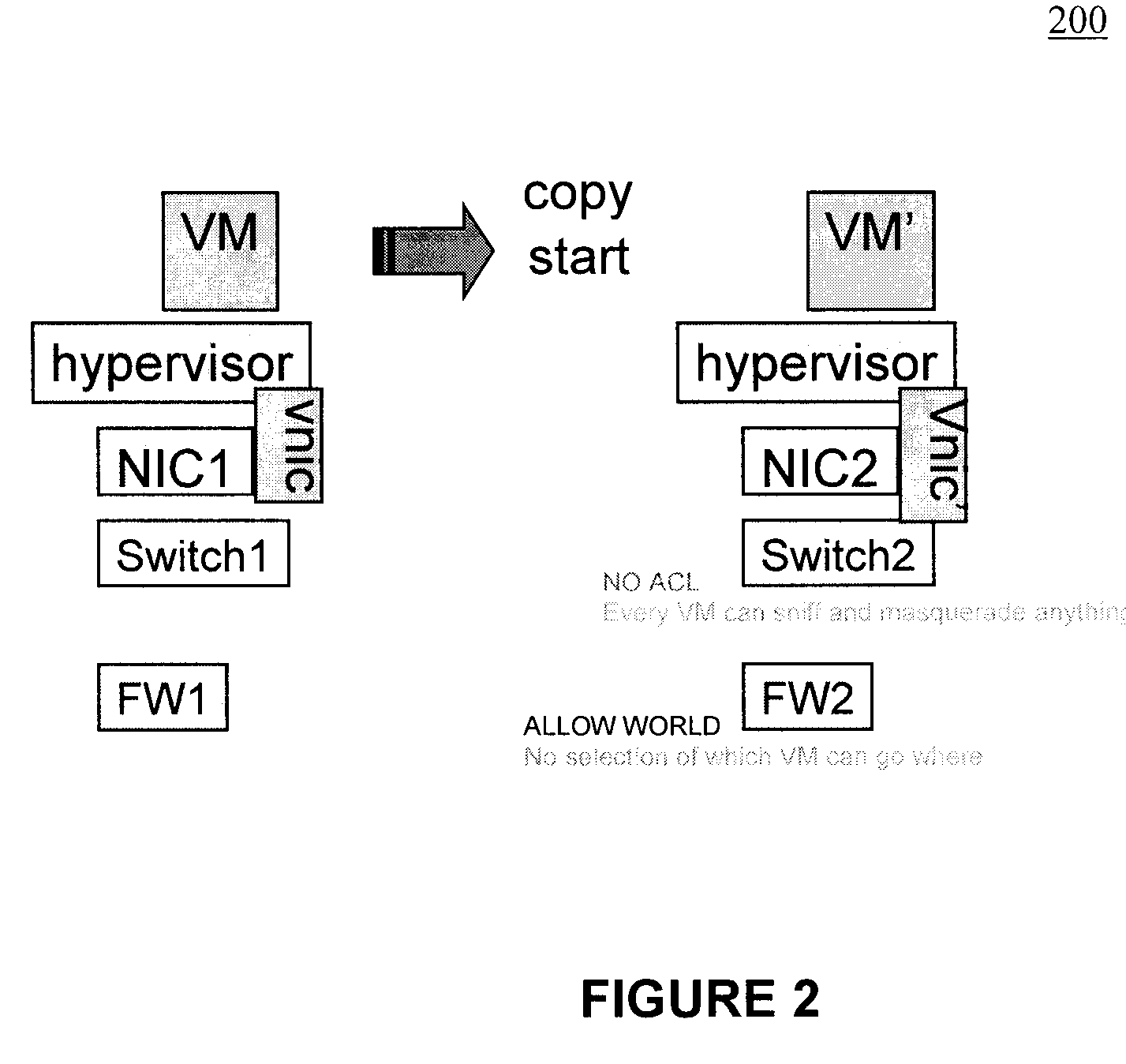
Moveable access control list (ACL) mechanisms for hypervisors and virtual machines and virtual port firewalls
ActiveUS20080163207A1Efficient responseRapid deploymentSemiconductor electrostatic transducersMicrophone structural associationVLAN access control listAccess control list
A method (and system) which provides virtual machine migration with filtered network connectivity and control of network security of a virtual machine by enforcing network security and routing at a hypervisor layer at which the virtual machine partition is executed, and which is independent of guest operating systems.
Owner:DAEDALUS BLUE LLC
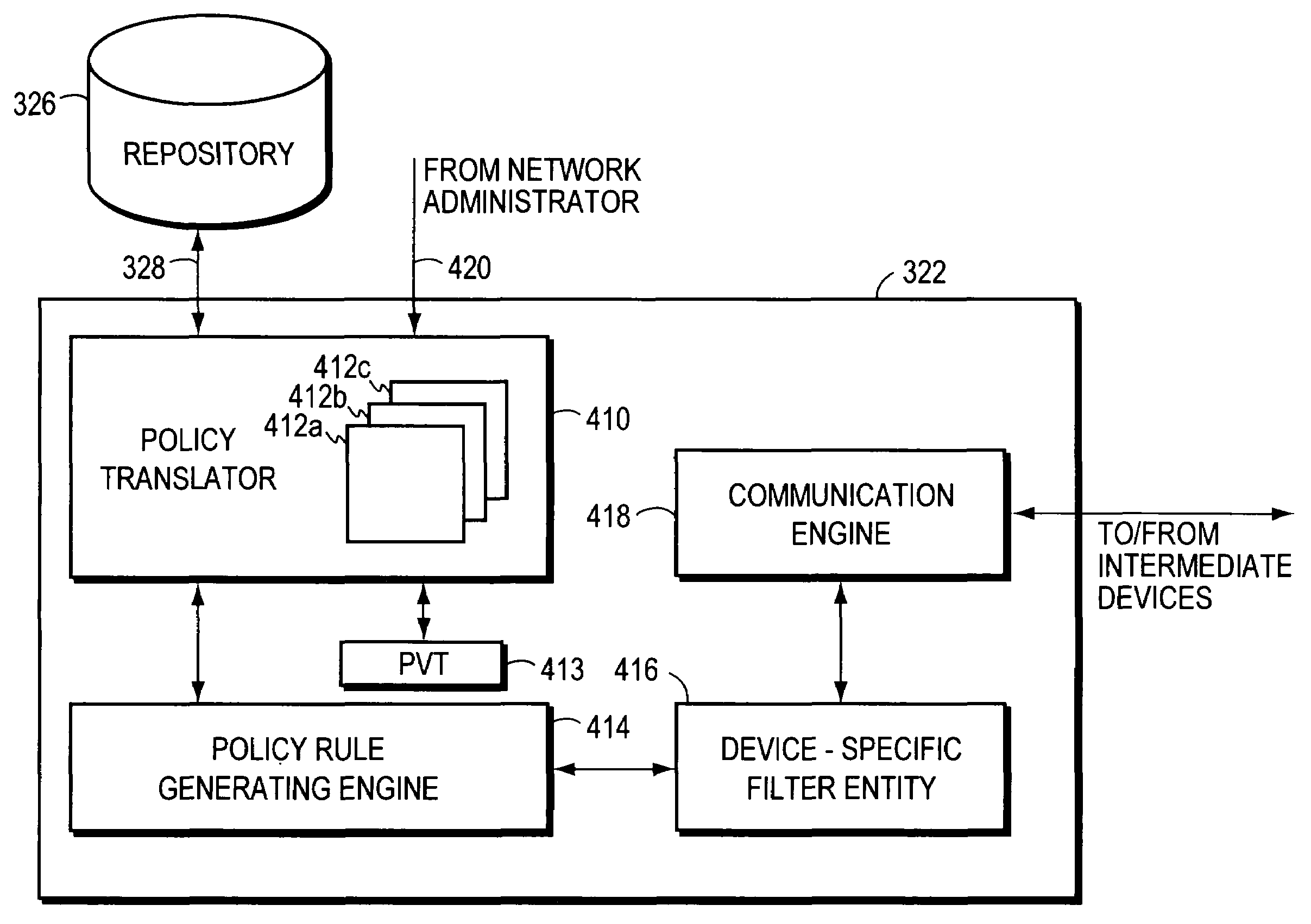
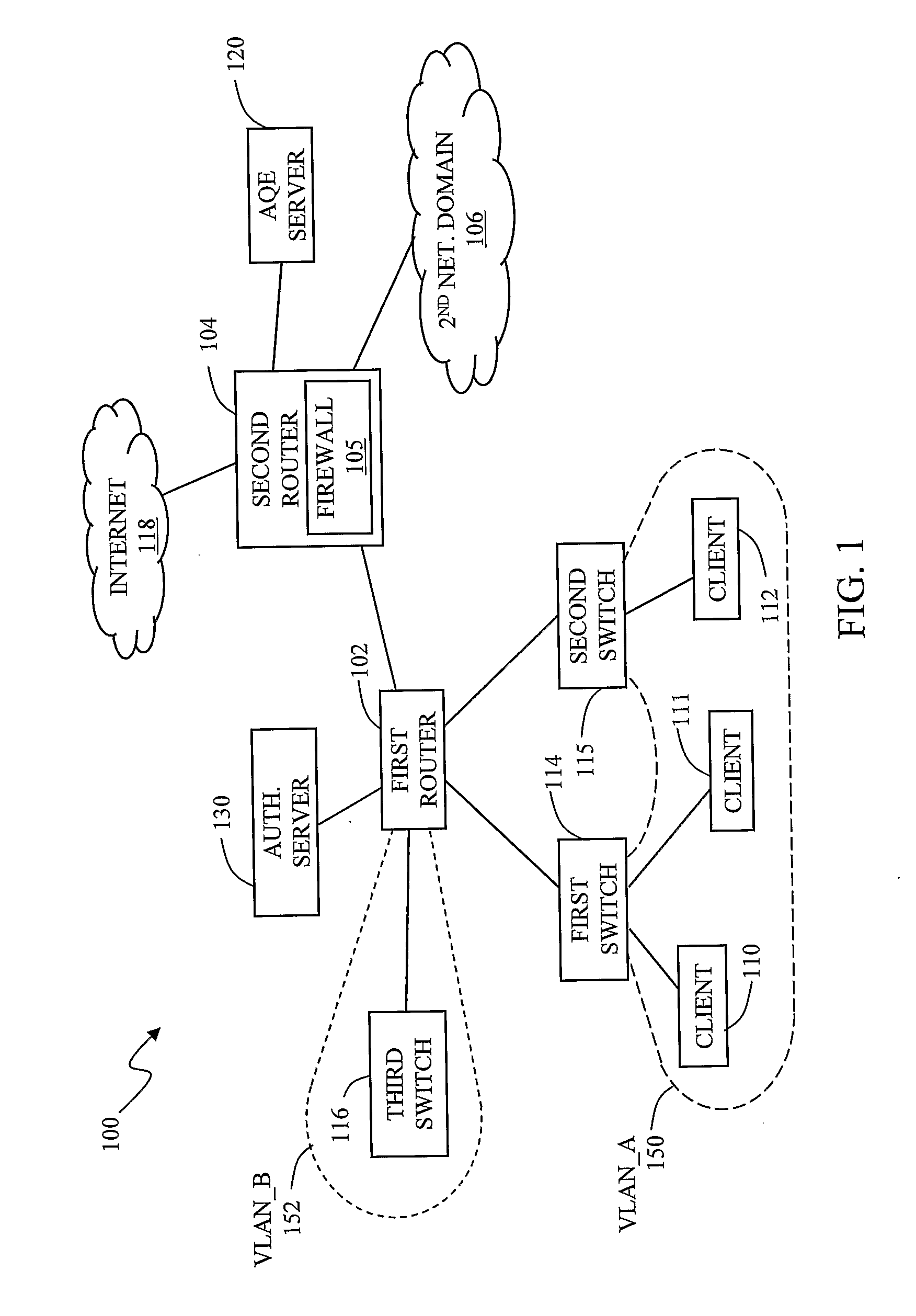
Method and apparatus for defining and implementing high-level quality of service policies in computer networks
InactiveUS7185073B1Multiple digital computer combinationsData switching networksNetwork strategyNetwork administrator
A computer network having multiple, dissimilar network devices includes a system for implementing high-level, network policies. The high-level policies, which are generally device-independent, are translated by one or more policy servers into a set of rules that can be put into effect by specific network devices. Preferably, a network administrator selects an overall traffic template for a given domain and may assign various applications and / or users to the corresponding traffic types of the template. Location-specific policies may also be established by the network administrator. The policy server translates the high-level policies inherent in the selected traffic template and location-specific policies into a set of rules, which may include one or more access control lists, and may combine several related rules into a single transaction. Intermediate network devices, which may have one or more roles assigned to their interfaces, are configured to request traffic management information from the policy server which replies with a particular set of transactions and rules. The rules, which may correspond to the particular roles assigned to the interfaces, are then utilized by the intermediate devices to configure their particular services and traffic management mechanisms. Other rules are utilized by the intermediate devices to classify packets with a particular priority and / or service value and to treat classified packets in a particular manner so as to realize the selected high-level policies within the domain.
Owner:CISCO TECH INC
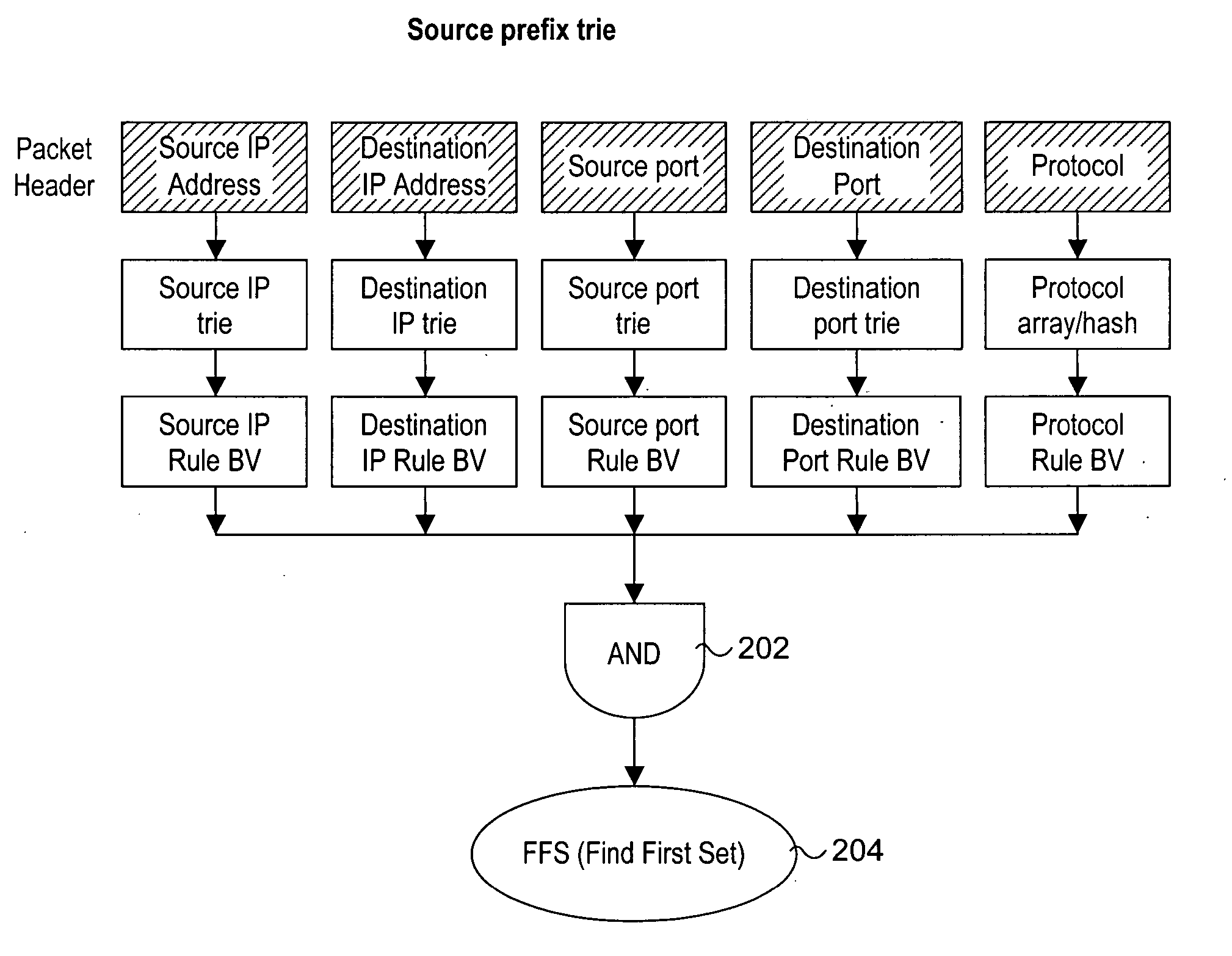
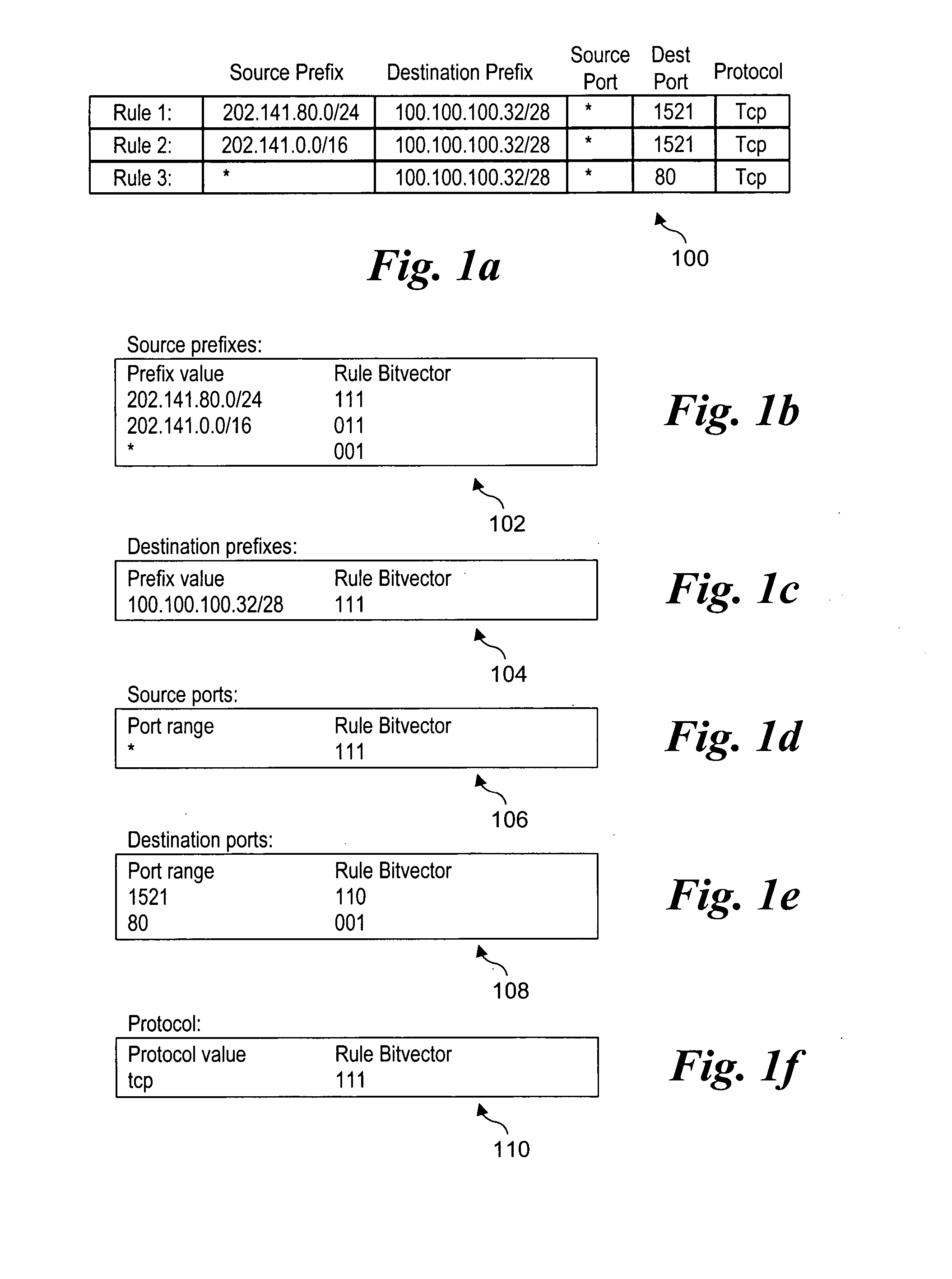
Methods for performing packet classification via prefix pair bit vectors
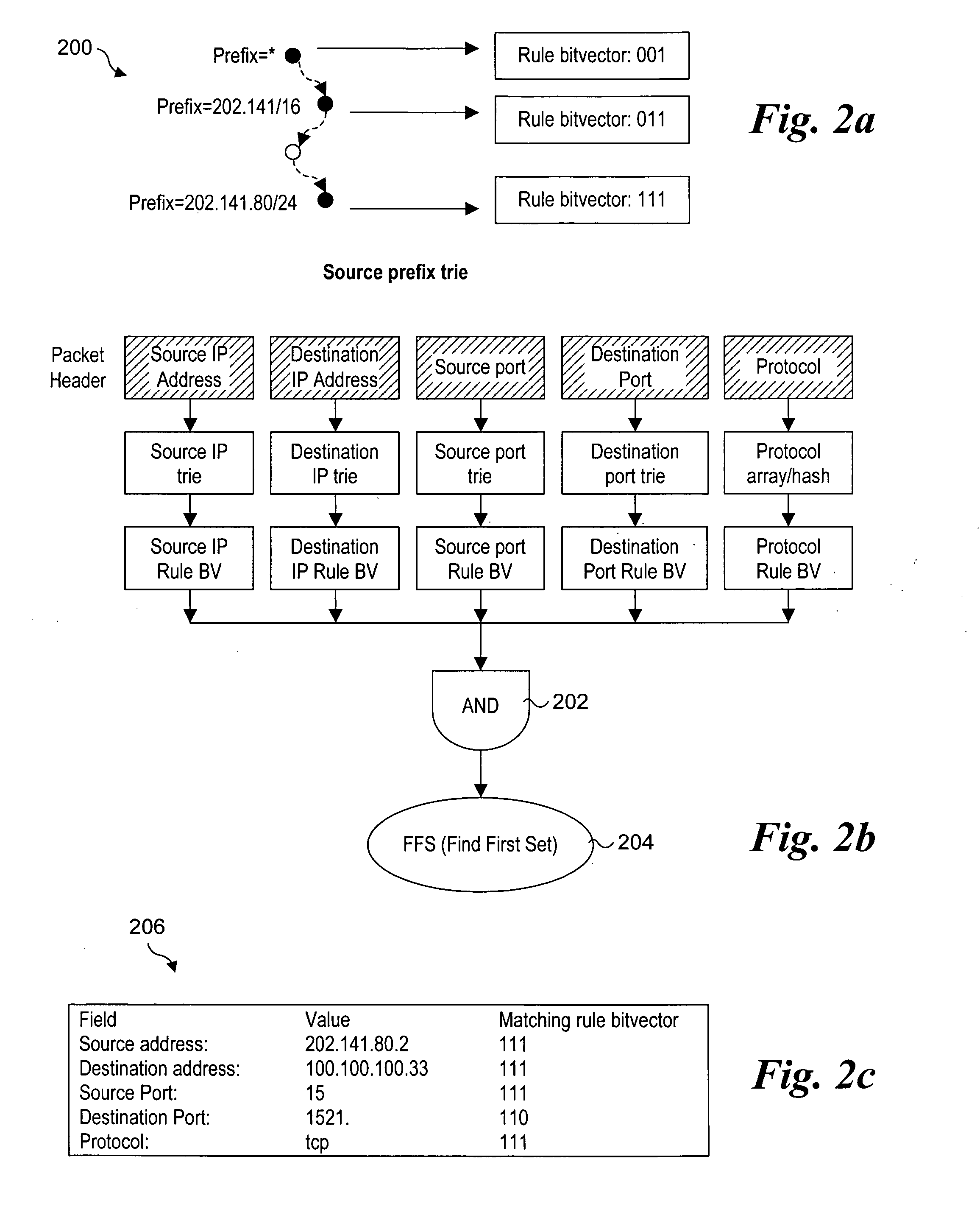
InactiveUS20060221956A1Data switching by path configurationPrefix headerTheoretical computer science
Methods for performing packet classification via prefix pair bit vectors. Unique prefix pairs in an access control list (ACL) are identified, with each prefix pair comprising a unique combination of a source prefix and a destination prefix. Corresponding prefix pair bit vectors (PPBVs) are defined for each unique source prefix and unique destination prefix in the ACL, with each PPBV including a string of bits and each bit position in the string associated with a corresponding prefix pair. A list of transport field value combinations are associated with each prefix pair based on corresponding entries in the ACL. During packet-processing operations, PPBV lookups are made using the source and destination prefix header values, and the PPBVs are logically ANDed to identify applicable prefix pairs. A search is then performed on transport field value combinations corresponding to the prefix pairs and the packet header to identify a highest priority rule.
Owner:INTEL CORP
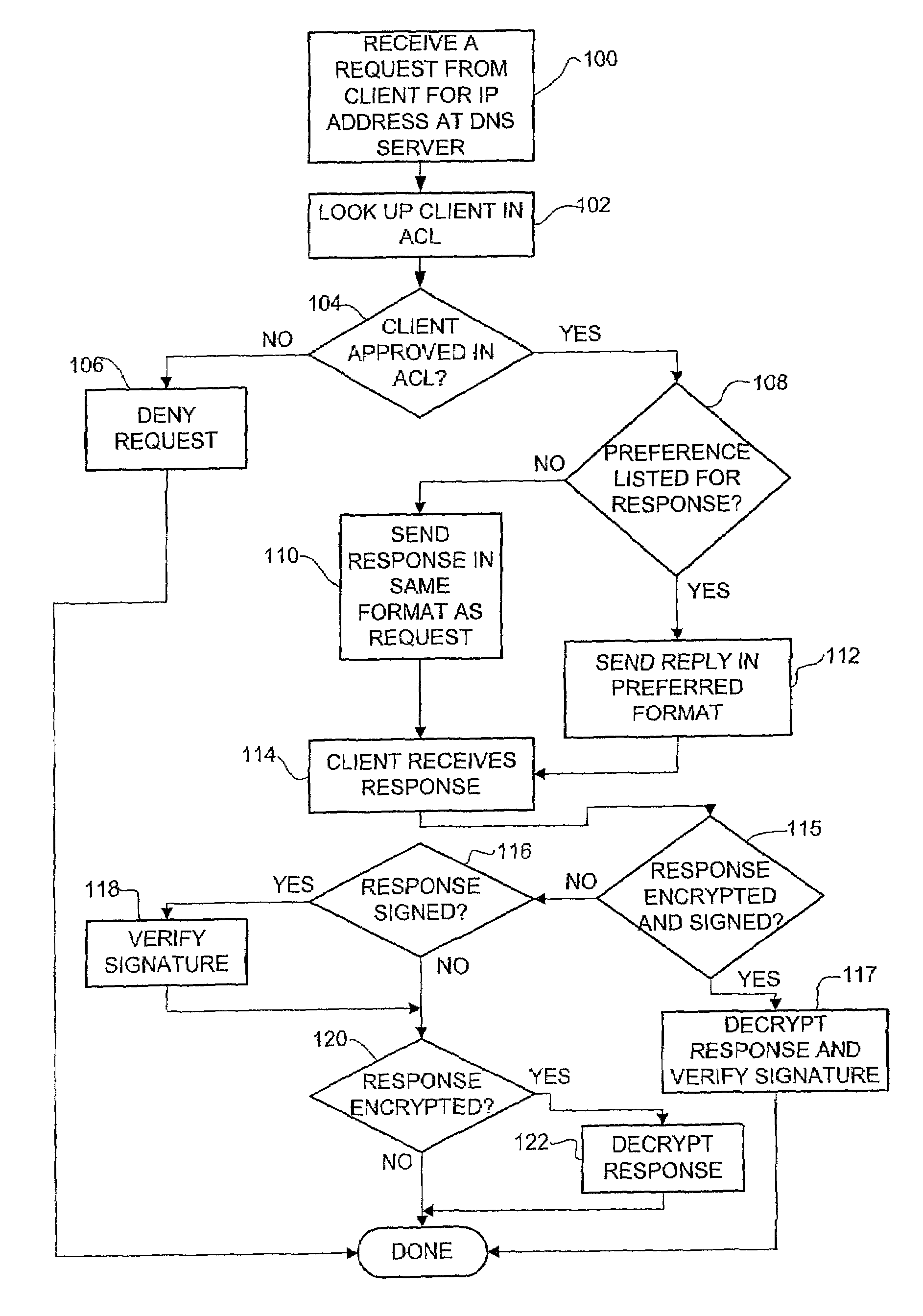
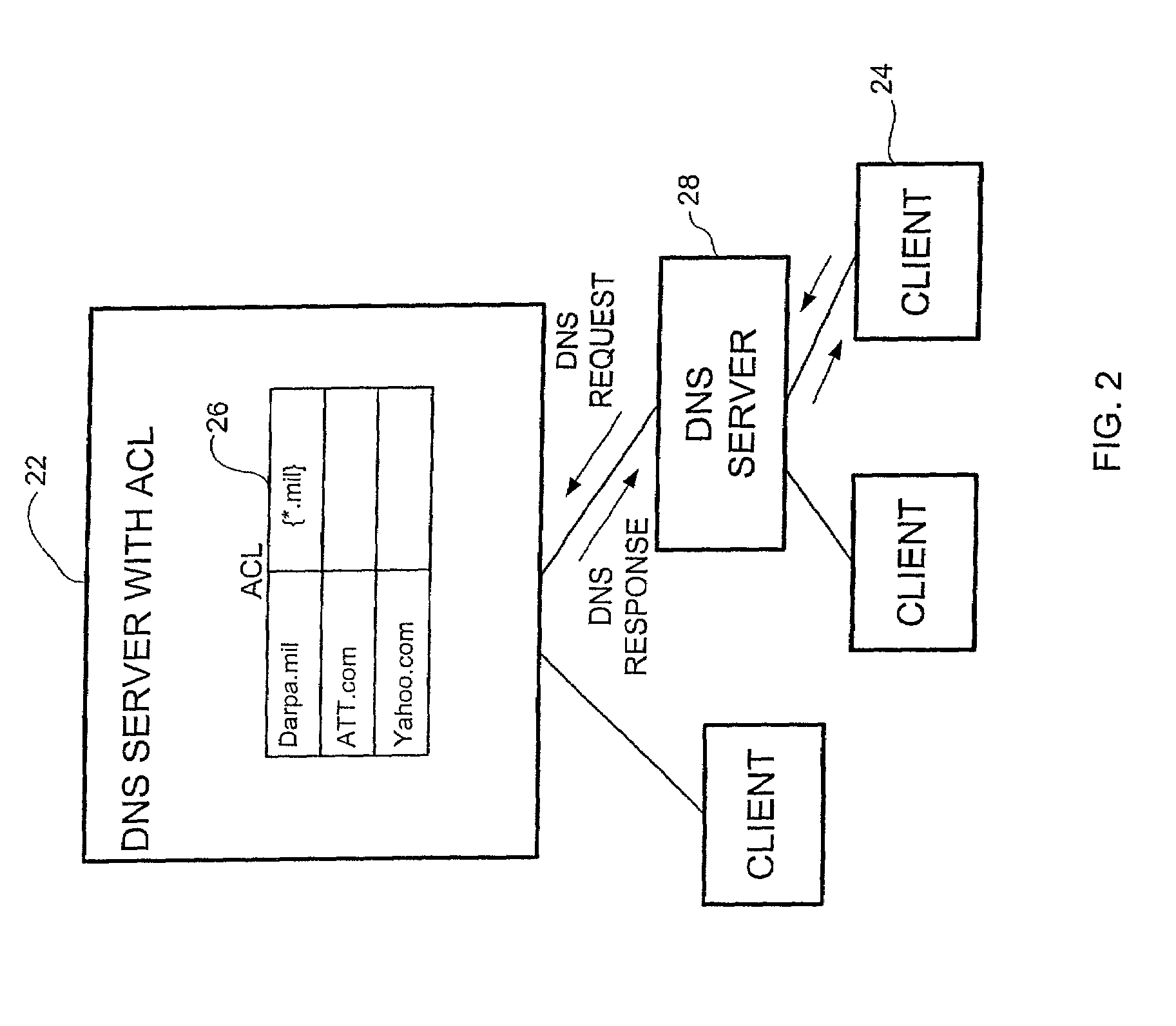
DNS server access control system and method
A method for controlling access to information from a DNS server having an access control list specifying clients approved to receive an IP address corresponding to a domain name of a target host is disclosed. The method includes receiving a request from a client for an IP address of a domain name at the DNS server and looking up the domain name in an access control list. The client is sent a reply containing the IP address of the domain name if the client is authorized in the access control list to receive the IP address. If the client is not authorized to receive the IP address, the request is denied.
Owner:MCAFEE LLC
Virtual machine based network carriers
InactiveUS20070079307A1Environment safetyTransmissionSoftware simulation/interpretation/emulationData packData set
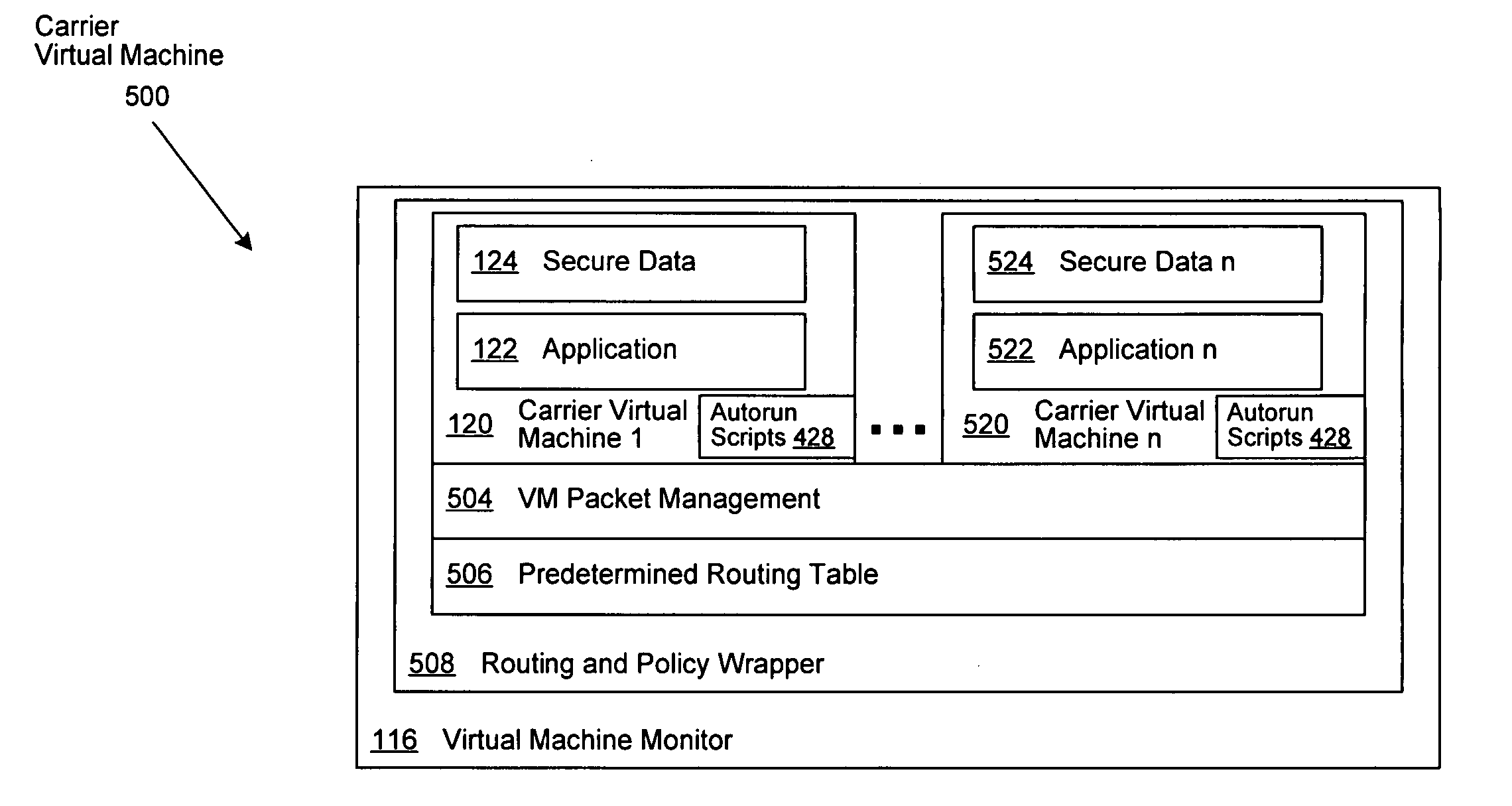
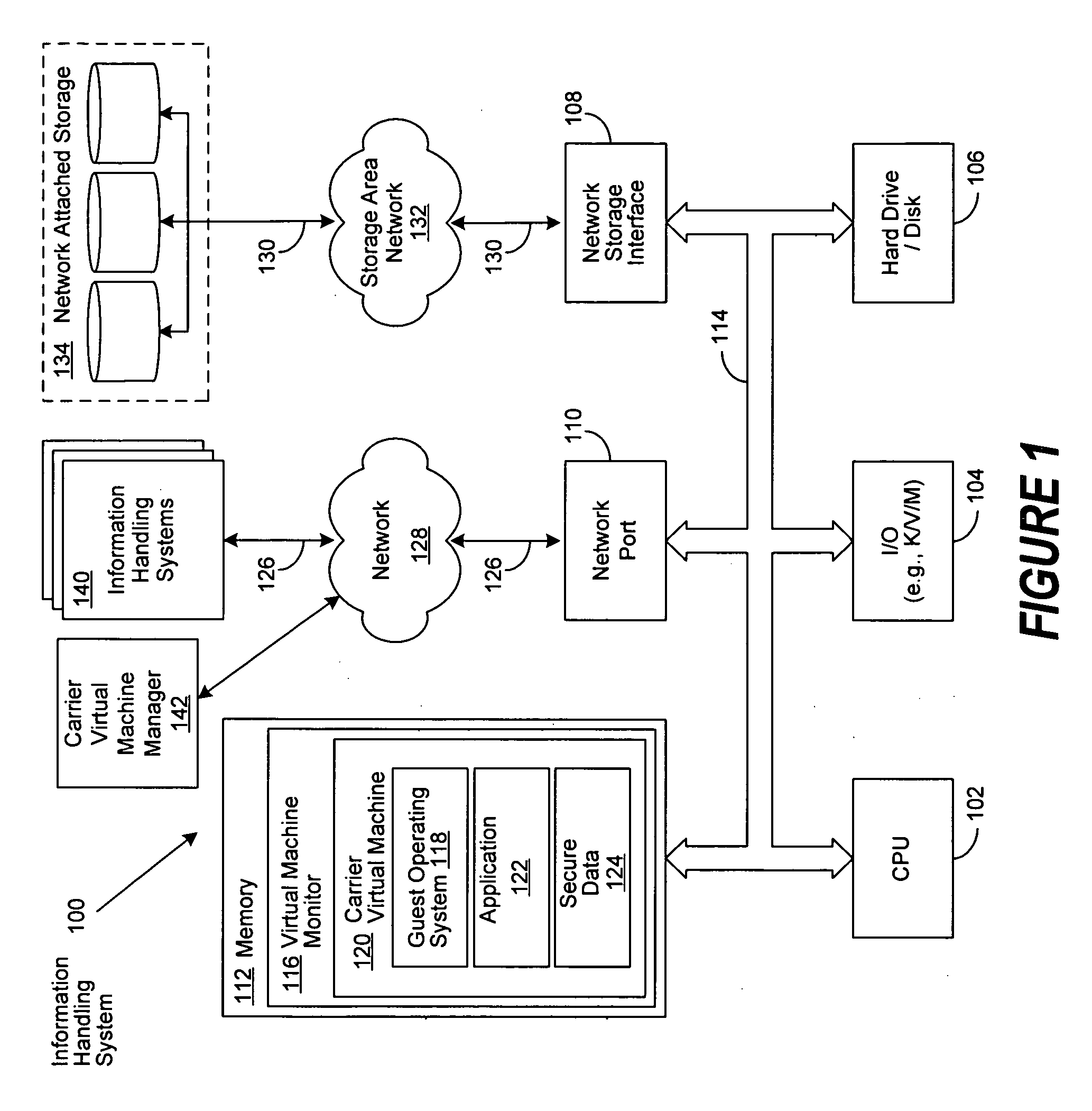
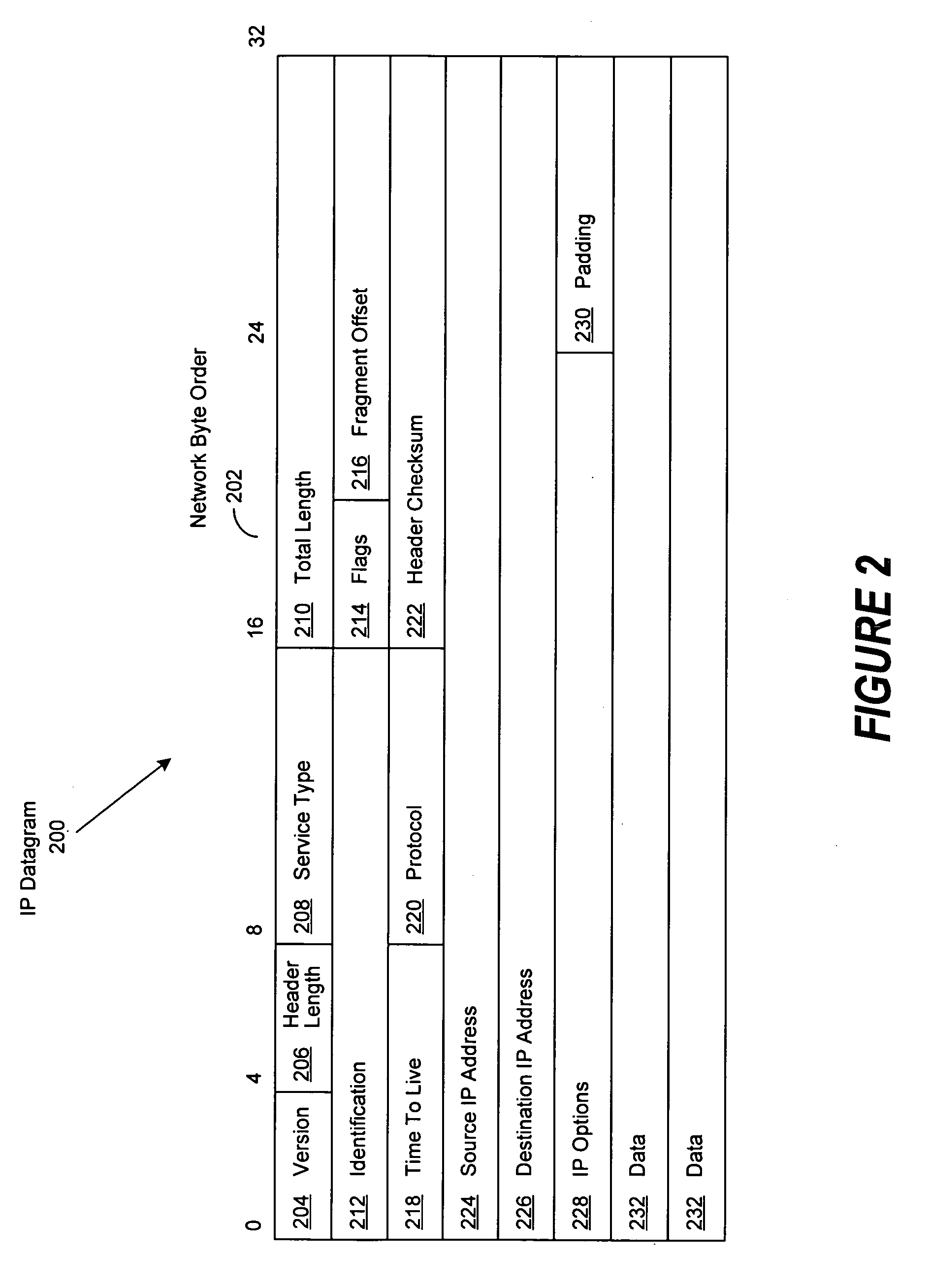
A system and method is disclosed for the secure transfer of data by carrier virtual machines between participating physical hosts through a virtual network (VNET) implemented on one or more internal and / or external networks. The method of the invention can provide additional security controls, comprising parameters that may include, but are not limited to, time-to-live (TTL), access control lists (ACLs), usage policies, directory roles, etc. Additionally, access to one or more of a plurality of carrier virtual machine payloads by security groups, individual access, subdivided individual access, and MIME-like subdivision of a VM-encapsulated payload may be controlled, thereby providing the carrier VM the ability to carry many secured payloads. In addition, VM packets, a group of packets, a single VM, or subpackets within a VM between network endpoints, or at a predetermined intermediary network point, may be quarantined to realize further security. Individual or combinations of these functionalities on carrier virtual machines, and by extension, application and / or one or more sets of secure data may be implemented.
Owner:DELL PROD LP
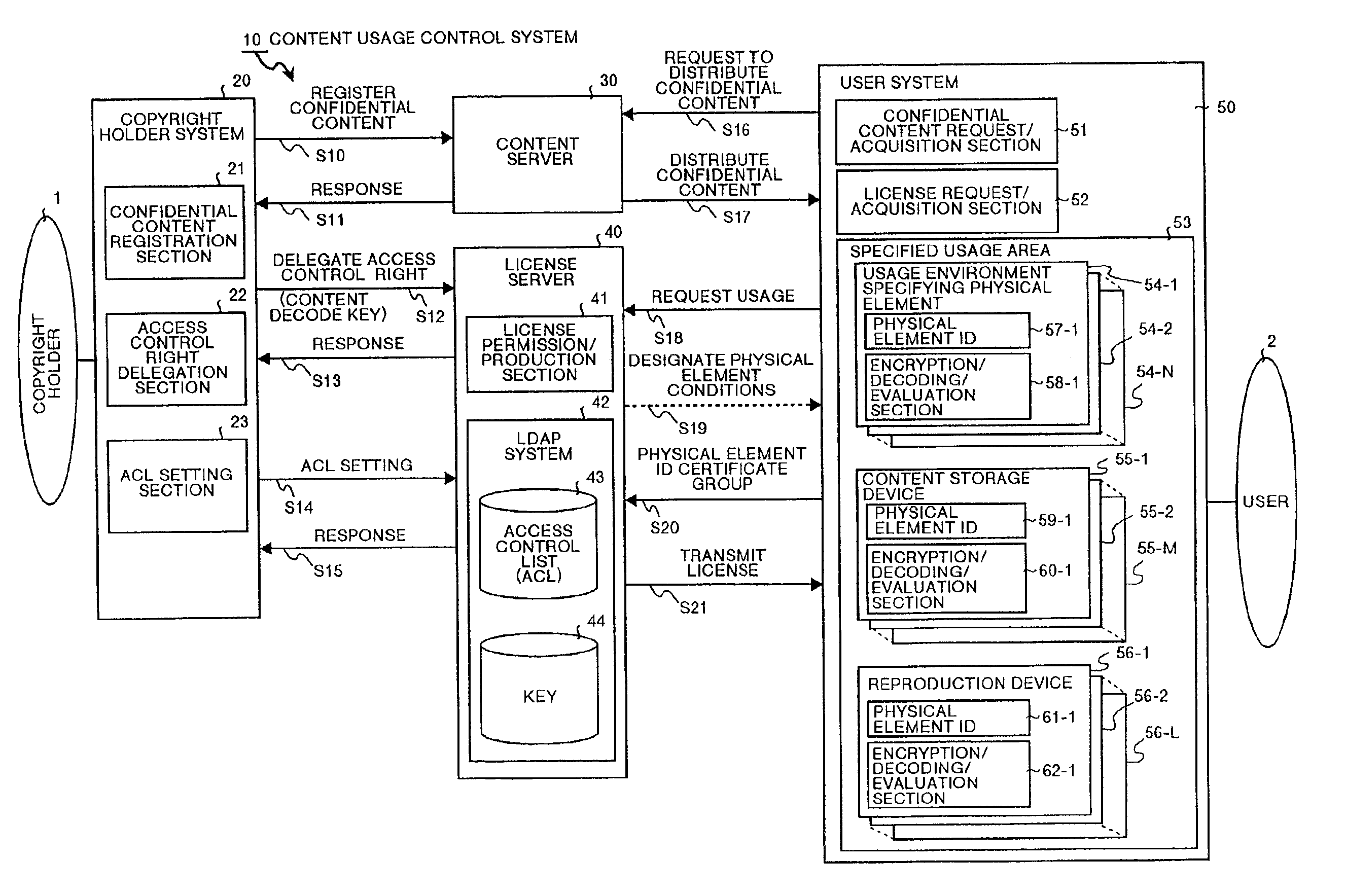
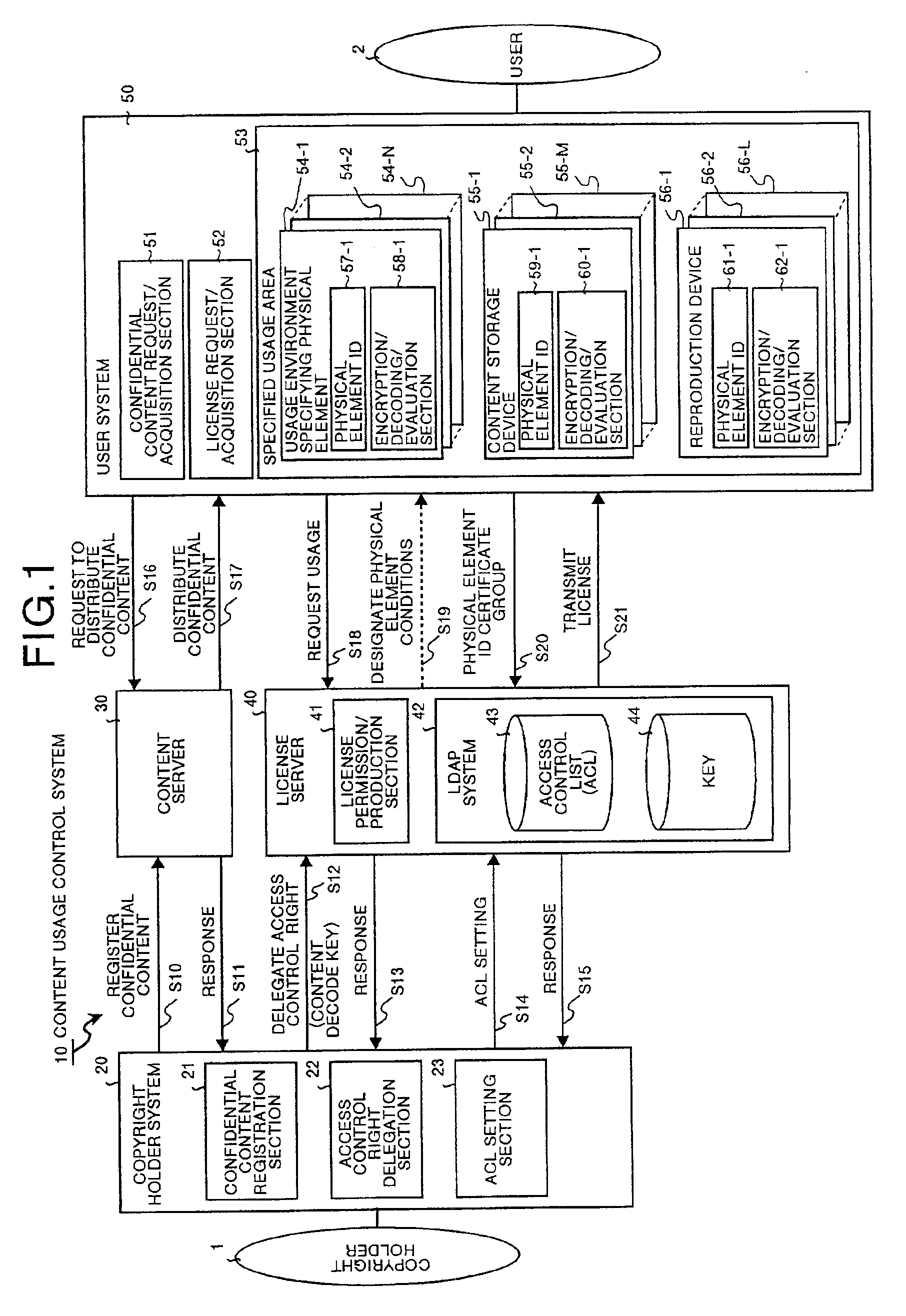
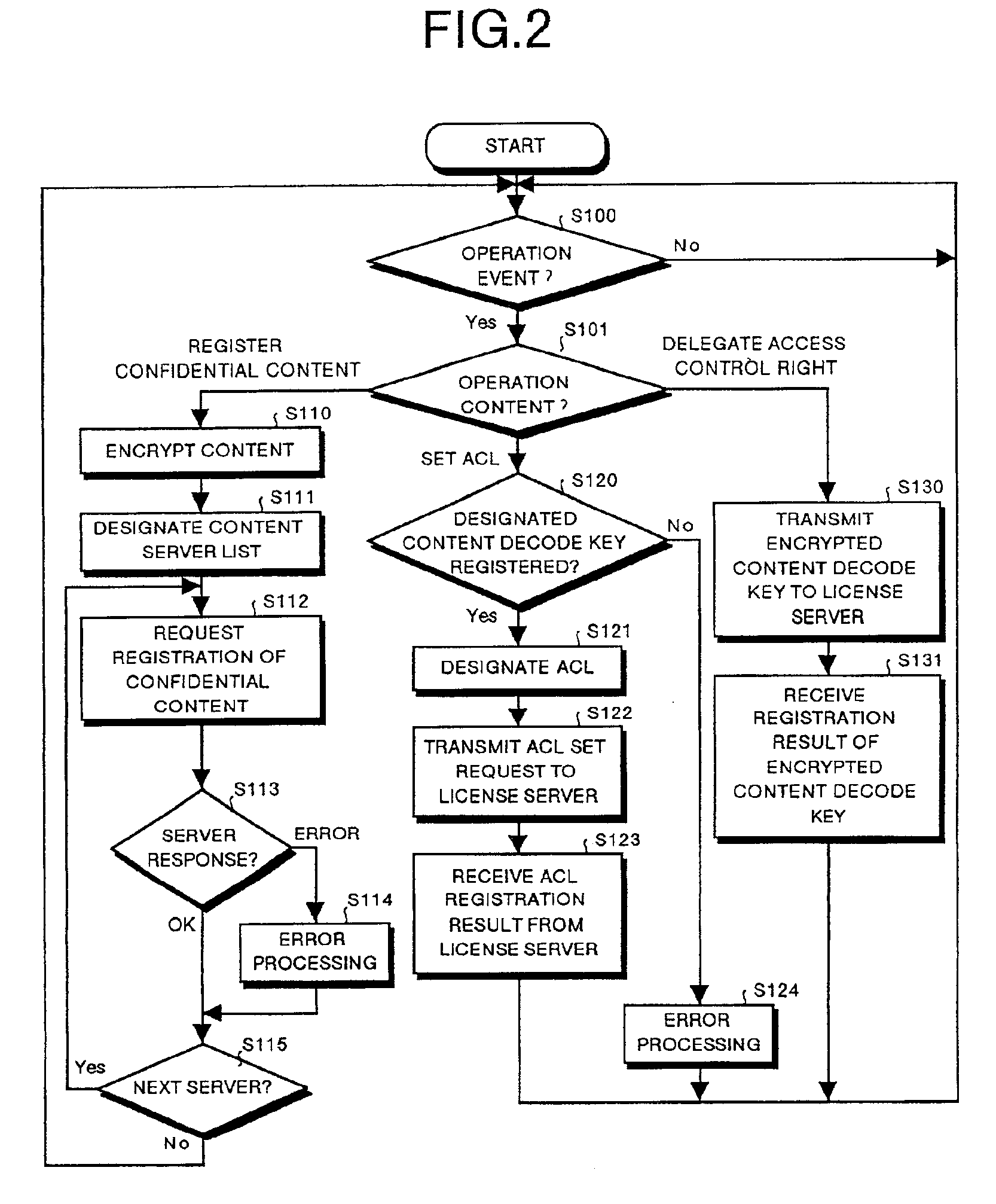
Content usage control system, content usage apparatus, computer readable recording medium with program recorded for computer to execute usage method
InactiveUS6873975B1Prevent illegal useImprove accuracyDigital data processing detailsAnalogue secracy/subscription systemsControl systemStructure of Management Information
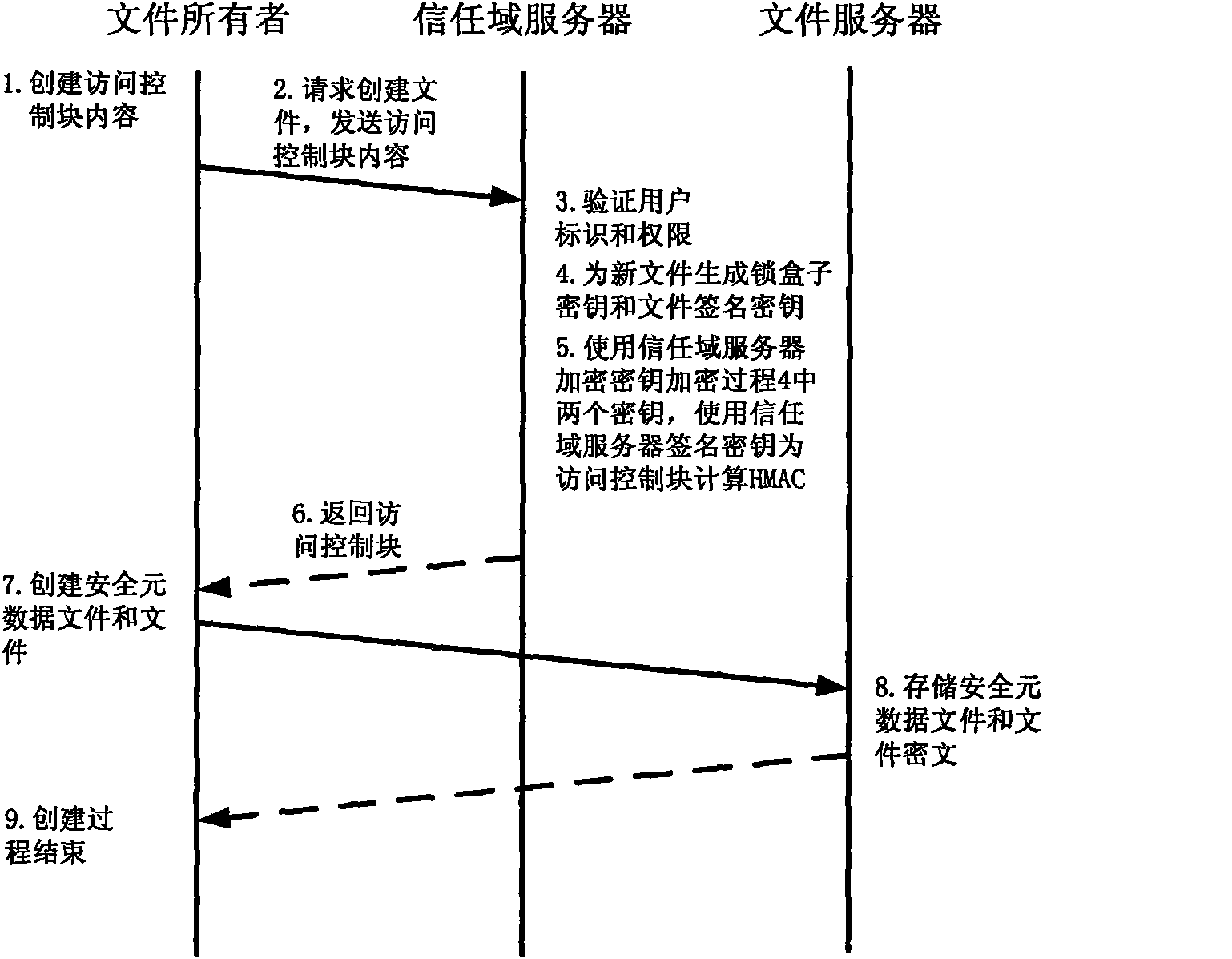
A content usage control system comprises a copyright holder system, content server, license server and user system. The ACL setting section of the copyright holder system sets a license ACL expressed as a structure by a combination of logic sums and logic products of a plurality of partial licenses for the content, based on the user ID and a plurality of physical element IDs including media used in the user system, and stores the license ACL in an access control list. The license server controls the usage of the content by the user utilizing the access control list.
Owner:FUJITSU LTD
Data storage incorporating cryptographically enhanced data protection
ActiveUS8856530B2Key distribution for secure communicationUser identity/authority verificationVLAN access control listUser identifier
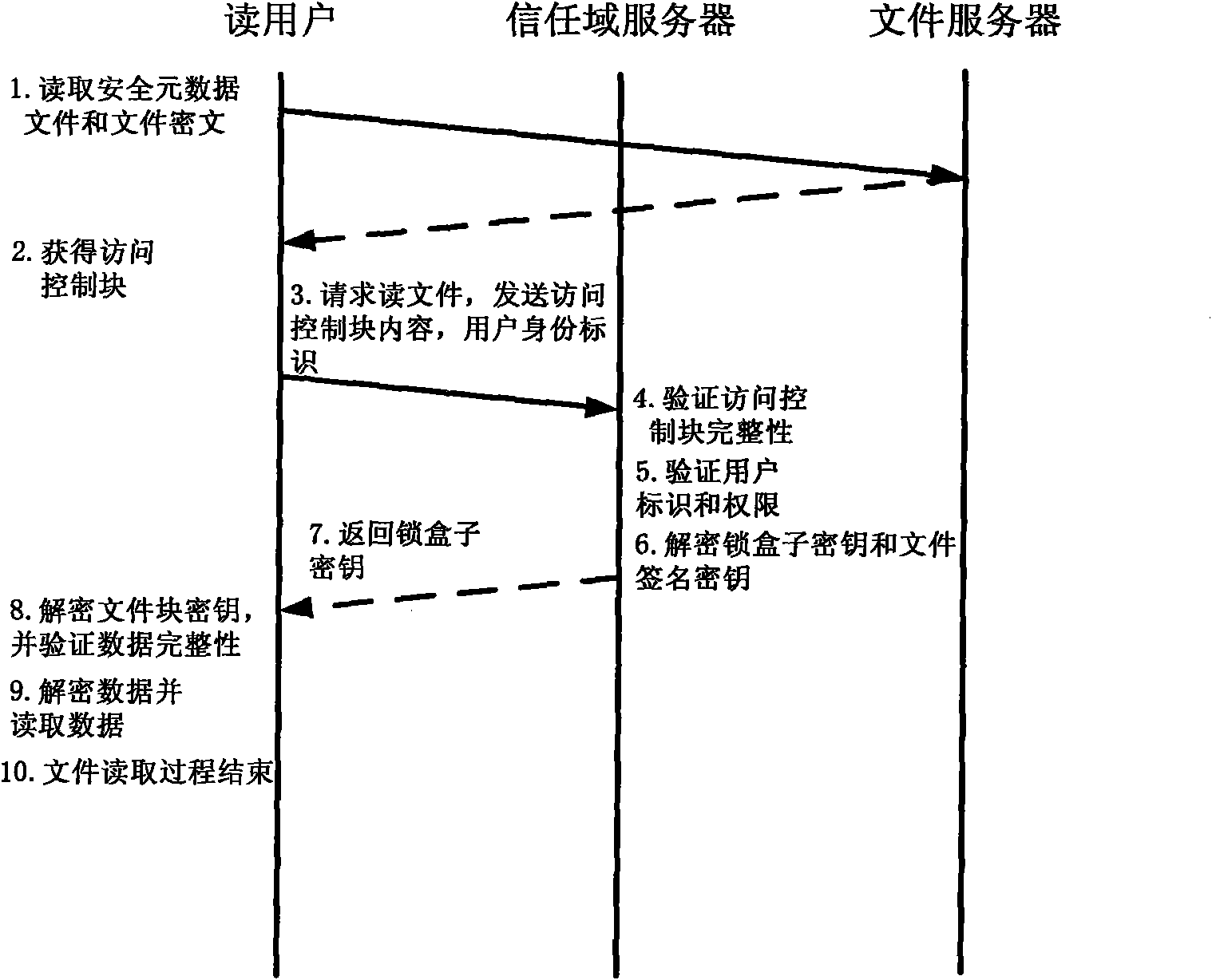
Various exemplary embodiments relate to a system for storing encrypted data and providing access to a group of users. The system may include: a record of user accounts including: a user identifier and a public encryption key; an access control list (ACL) defining an access control policy including: permissions defining access to data objects associated with the ACL and an ACL key list including copies of a an ACL key encrypted with the public keys of the users; a user-data storage medium including: encrypted user data, stored as a plurality of data objects, each object associated with an ACL and encrypted with the ACL key, and meta-data; and an access controller configured to: receive a request for a data object, and send a copy of the data object and the ACL key encrypted with the public key of the user if the user has permission to access the data object.
Owner:ONYX PRIVACY
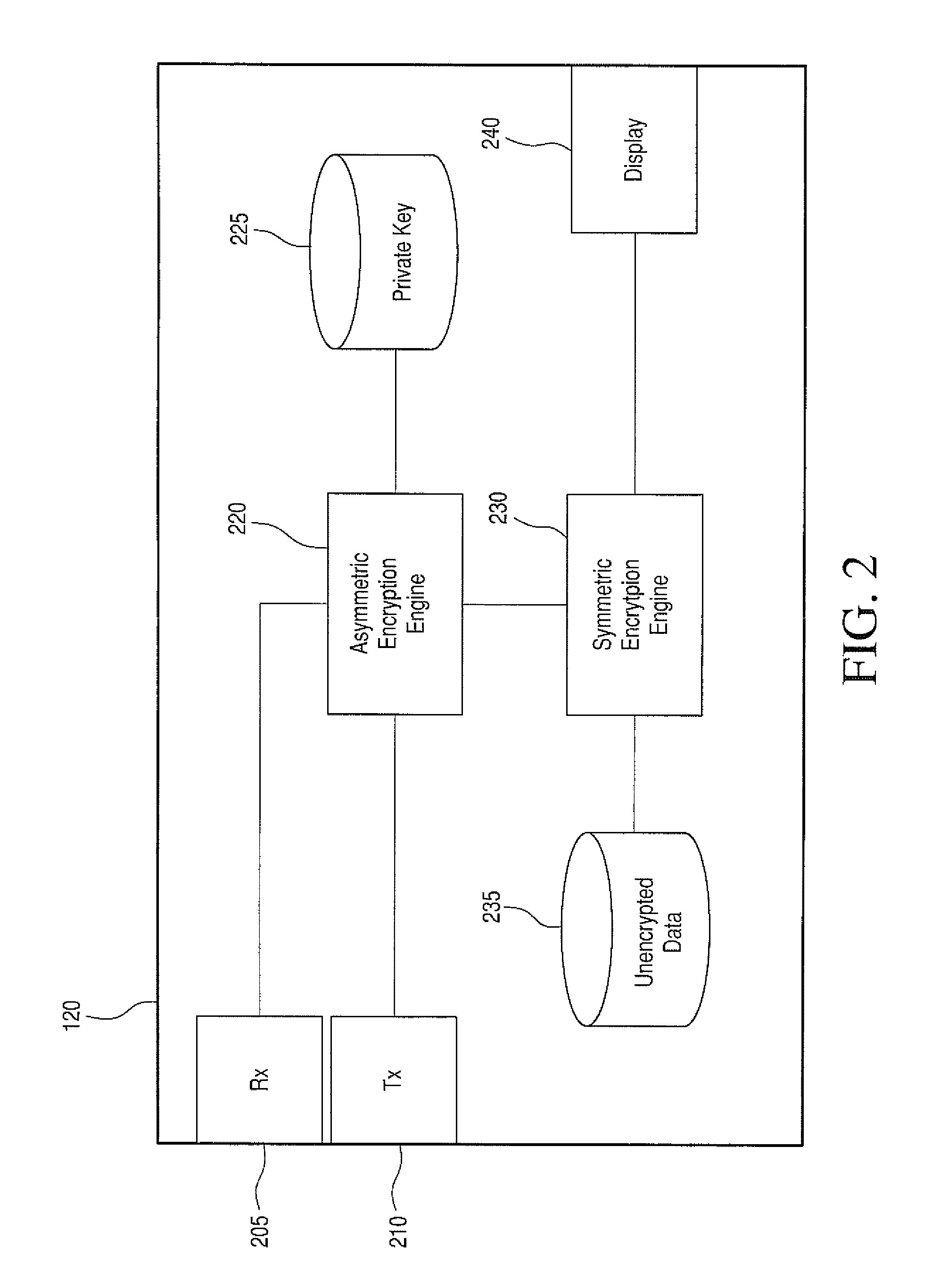
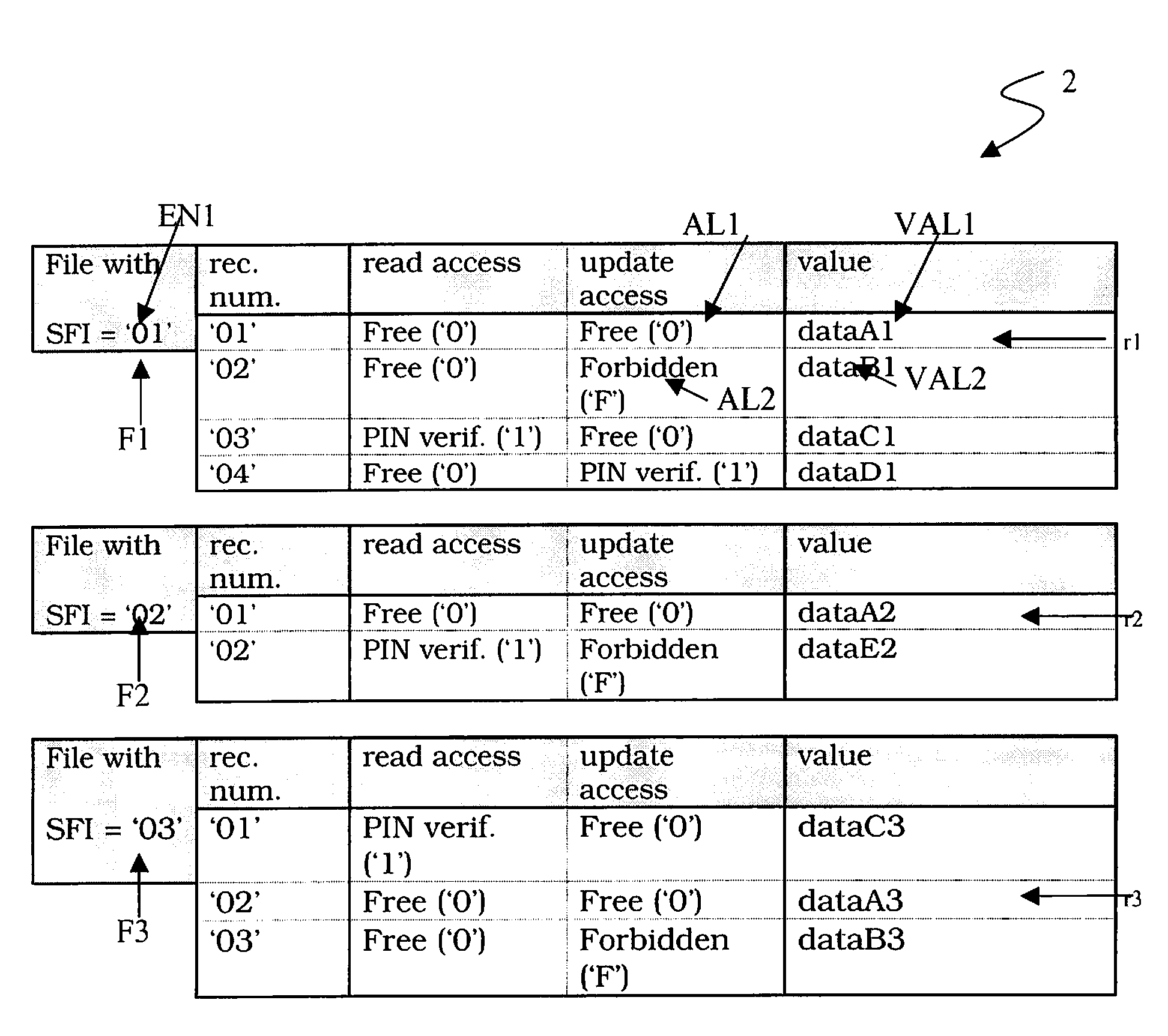
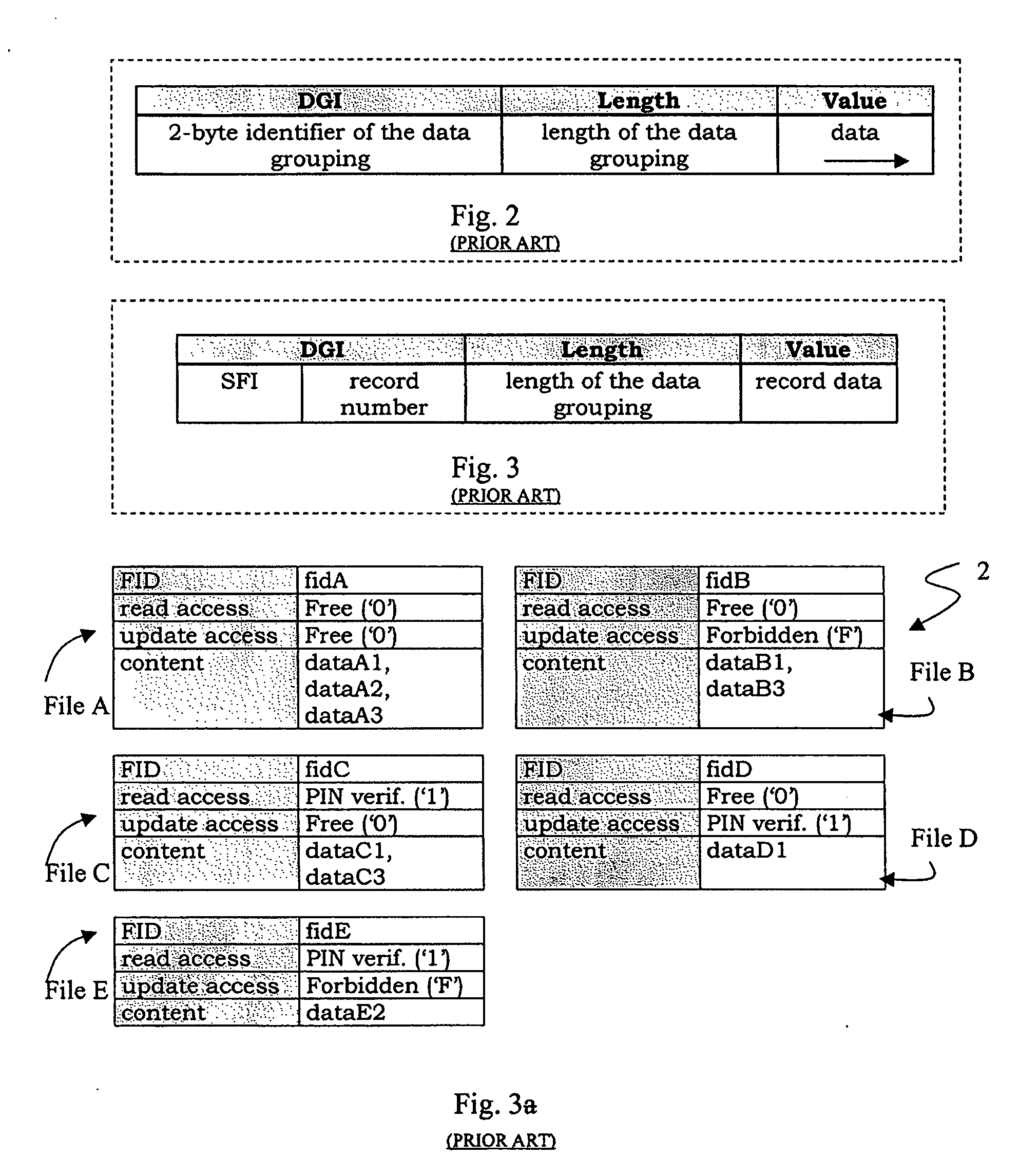
Method for Configuring an IC Card in Order to Receive Personalization Commands
ActiveUS20080126398A1Cheap and time consumeAcutation objectsDigital data processing detailsPersonalizationOperating system
An IC card is configured to receive personalization commands which are used to transmit data to the IC card. An access control list is associated with the data. The data is stored in the IC card in a record structure that includes a plurality of entries. The access control list is stored in the IC card in the record structure. The personalization commands include a card personalization specification (CPS).
Owner:STMICROELECTRONICS INT NV
Multiple tiered network security system, method and apparatus using dynamic user policy assignment
InactiveUS20050055570A1Improve network securityEfficiently provideUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThree levelPhysical address
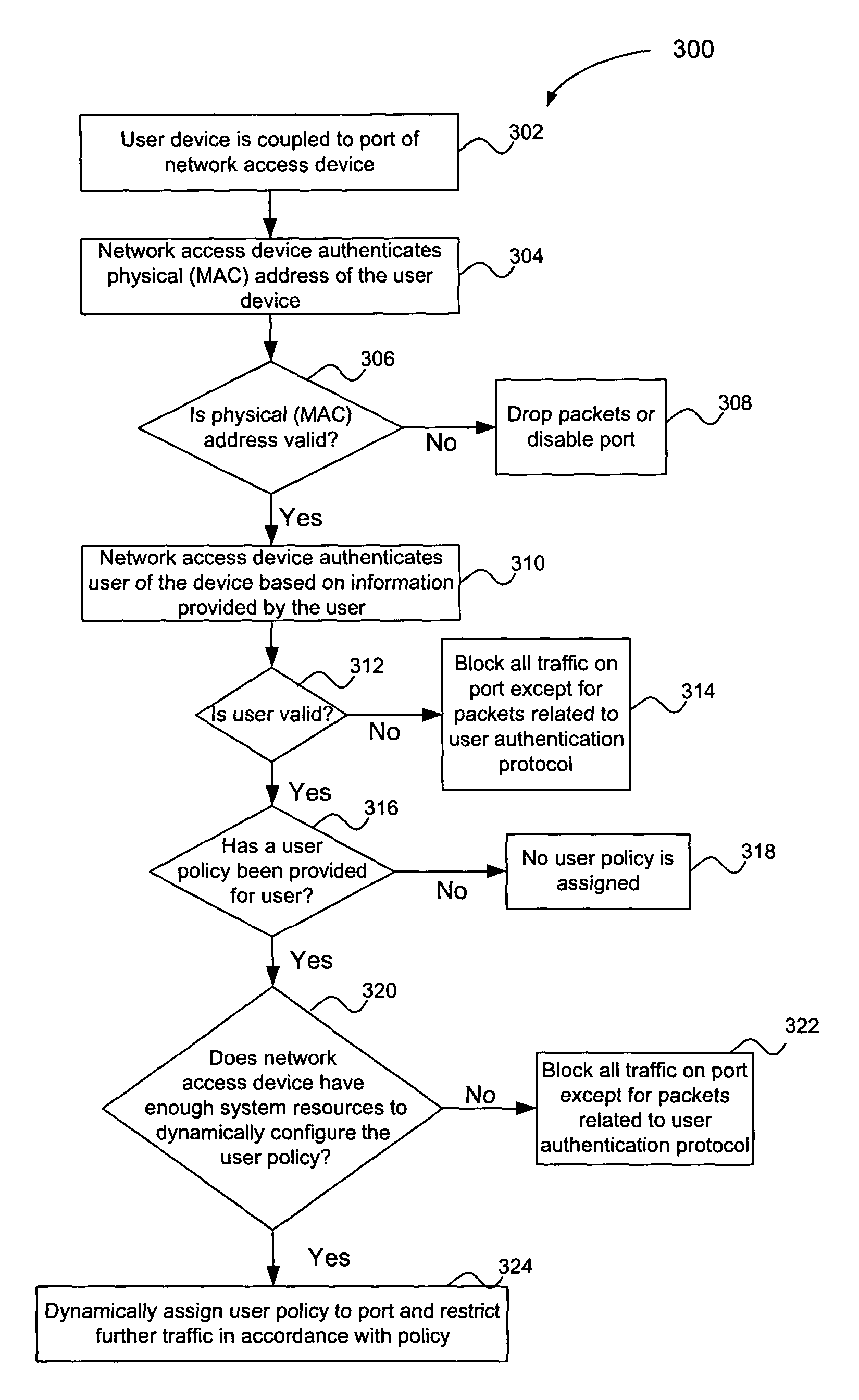
A multiple key, multiple tiered network security system, method and apparatus provides at least three levels of security. The first level of security includes physical (MAC) address authentication of a user device being attached to the network, such as a user device being attached to a port of a network access device. The second level includes authentication of the user of the user device, such as user authentication in accordance with the IEEE 802.1x standard. The third level includes dynamic assignment of a user policy to the port based on the identity of the user, wherein the user policy is used to selectively control access to the port. The user policy may identify or include an access control list (ACL) or MAC address filter. Also, the user policy is not dynamically assigned if insufficient system resources are available to do so. Failure to pass a lower security level results in a denial of access to subsequent levels of authentication.
Owner:AVAGO TECH INT SALES PTE LTD
System and method for providing a hierarchical role-based access control
InactiveUS20070214497A1Improve the level ofImprove efficiencyDigital data processing detailsUser identity/authority verificationControl systemWorld Wide Web
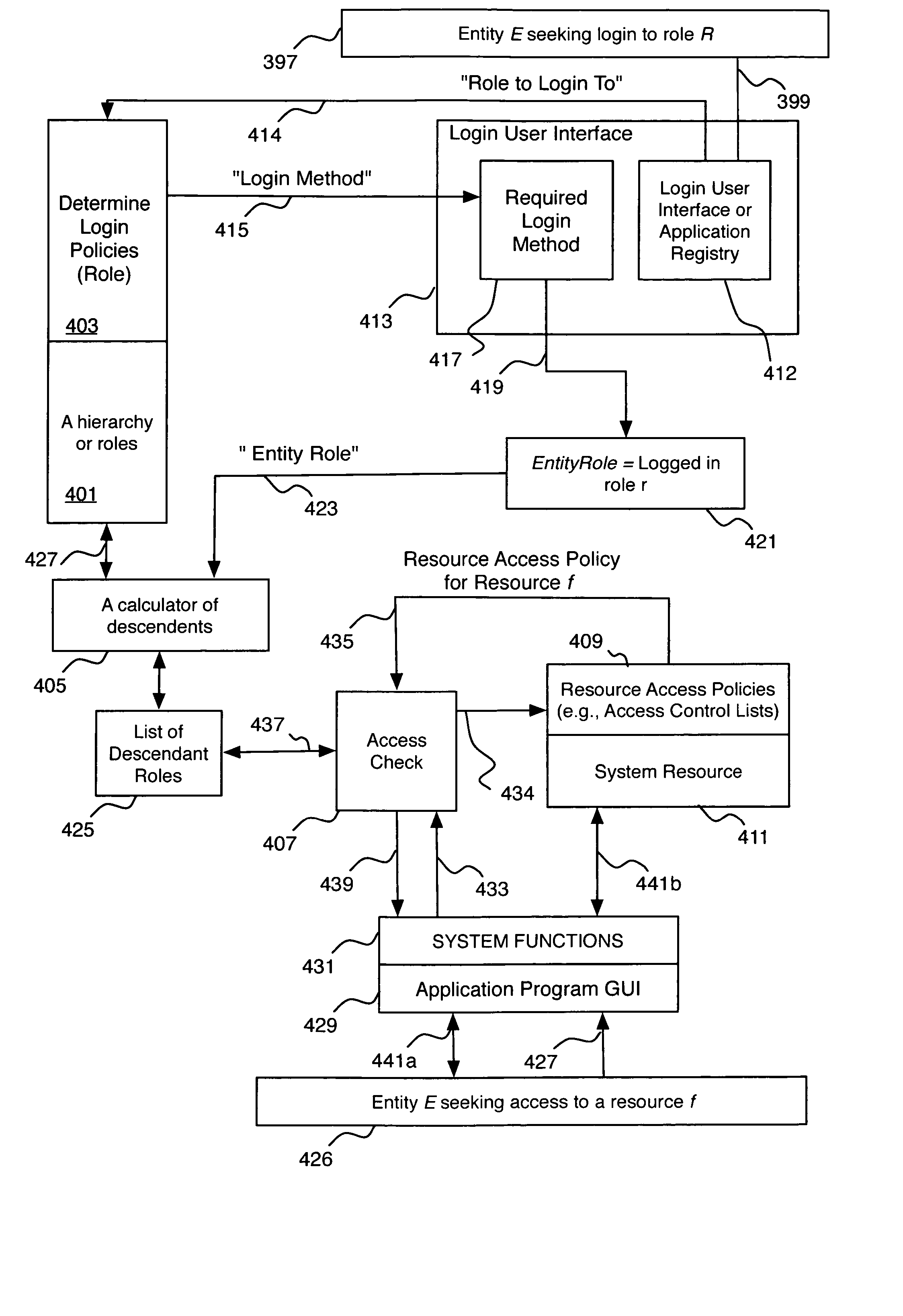
Role-based hierarchical access control system and method. A computer system having a data storage capacity and a central processing unit and at least one resource has an access control data structure defining role-based access control lists for the resource, wherein the access control list defines based on the role of a user the types of access that the user may have to the at least one resource. A hierarchy of roles having at least a first role and a second role wherein the second role inherits the permissions granted to the first role for the at least one resource. Access to the resource is determined by comparing roles defined to have access privileges to the resource and the permissions granted to such roles to the role of an entity seeking access to the resource.
Owner:AXALTO INC
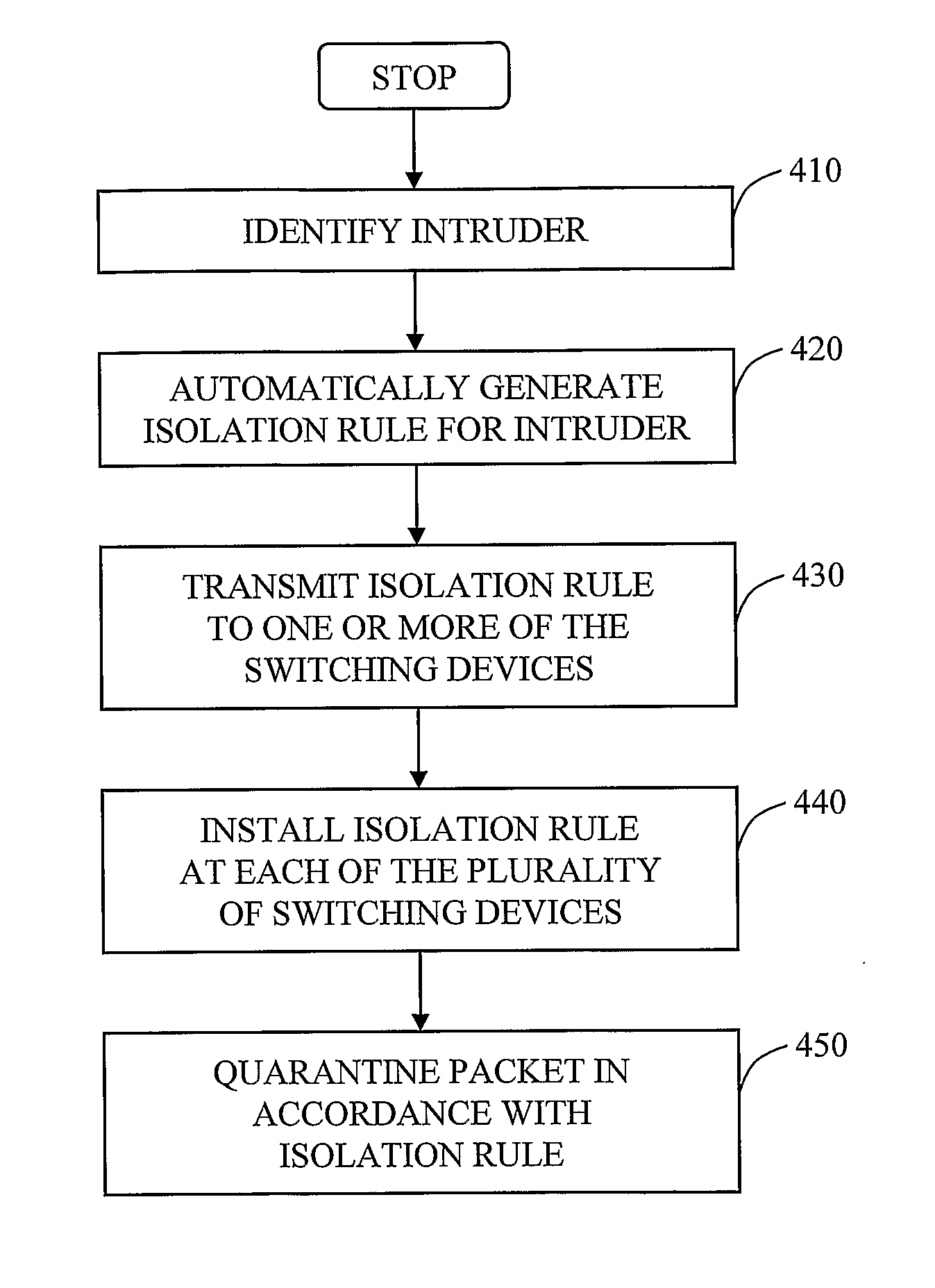
Automated containment of network intruder
InactiveUS20070192862A1Network degradationLow costMemory loss protectionError detection/correctionAutomatic controlVirtual LAN
The invention in the preferred embodiment features a system (200) and method for automatically segregating harmful traffic from other traffic at a plurality of network nodes including switches and routers. In the preferred embodiment, the system (200) comprises an intrusion detection system (105) to determine the identity of an intruder and a server (130) adapted to automatically install an isolation rule on the one or more network nodes (114, 115, 116) to quarantine packets from the intruder. The isolation rule in the preferred embodiment is a virtual local area network (VLAN) rule or access control list (ACL) rule that causes the network node to route any packets from the intruder into a quarantine VLAN or otherwise isolate the traffic from other network traffic. In large networks, the isolation rule may be installed on a select plurality of network nodes under the gateway router (104) associated with the node at which the intruder first entered the network (100).
Owner:VERMEULEN VINCENT +1
Access control system, access control method, and access control program
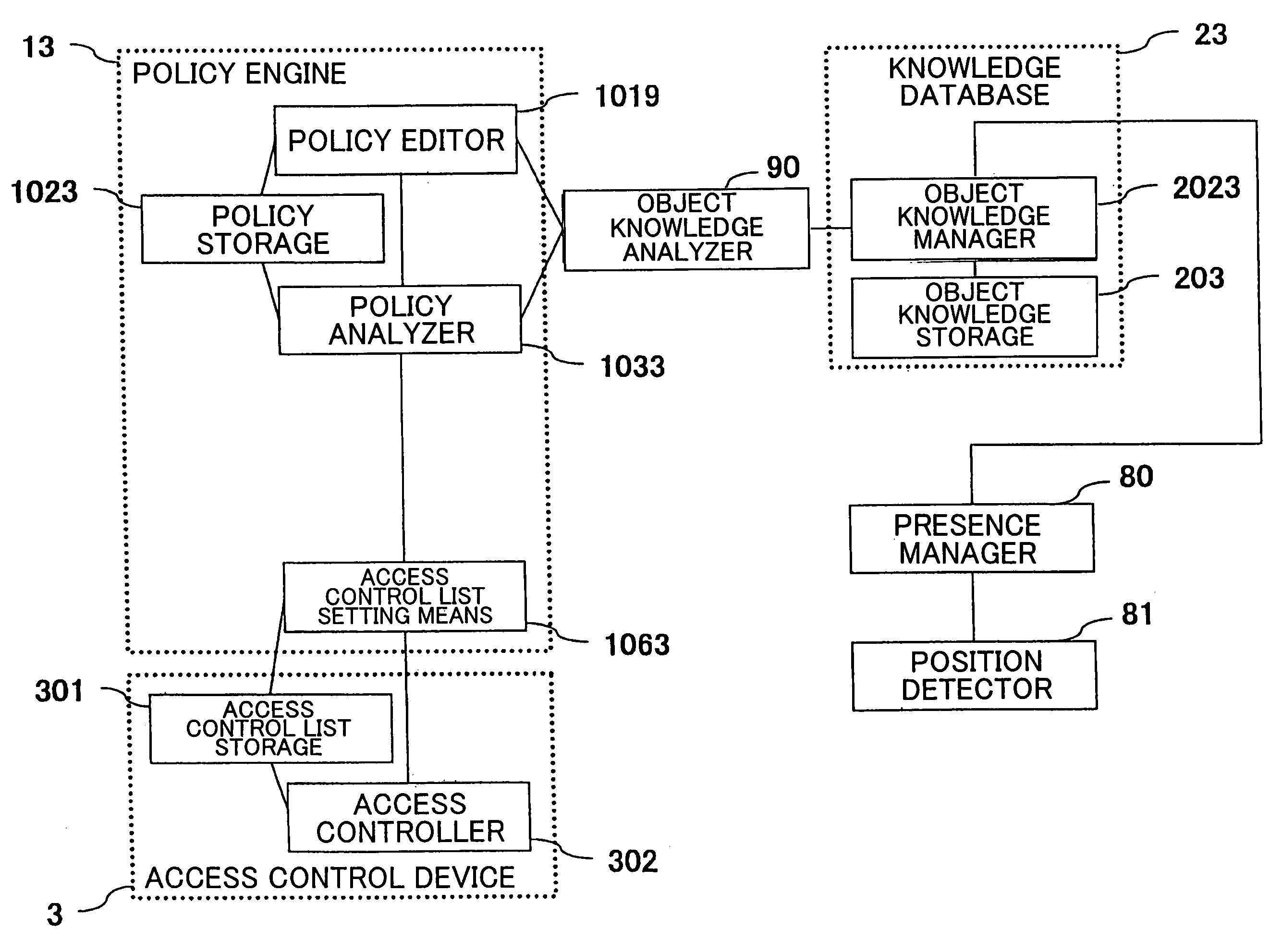
ActiveUS20050262132A1Efficient updateEffective controlDigital data processing detailsDigital data protectionControl systemAccess control list
A policy storage stores an access control policy as a set of setting information items to make resources (access destinations) shared by an adhoc group. When a part of the access control policy is edited, a policy analyzer updates a rule generated from the edited access control policy. At this time, the rule is updated with use of object knowledge having a data configuration capable of expressing a user as belonging to plural user groups. An access control list setting means updates a part of an access control list, based on the updated rule. Accordingly, an access control list can be generated with respect to a user group including a user who belongs to plural organizations, and the access control list can be updated efficiently.
Owner:NEC CORP
Method and apparatus for using non-secure file servers for secure information storage
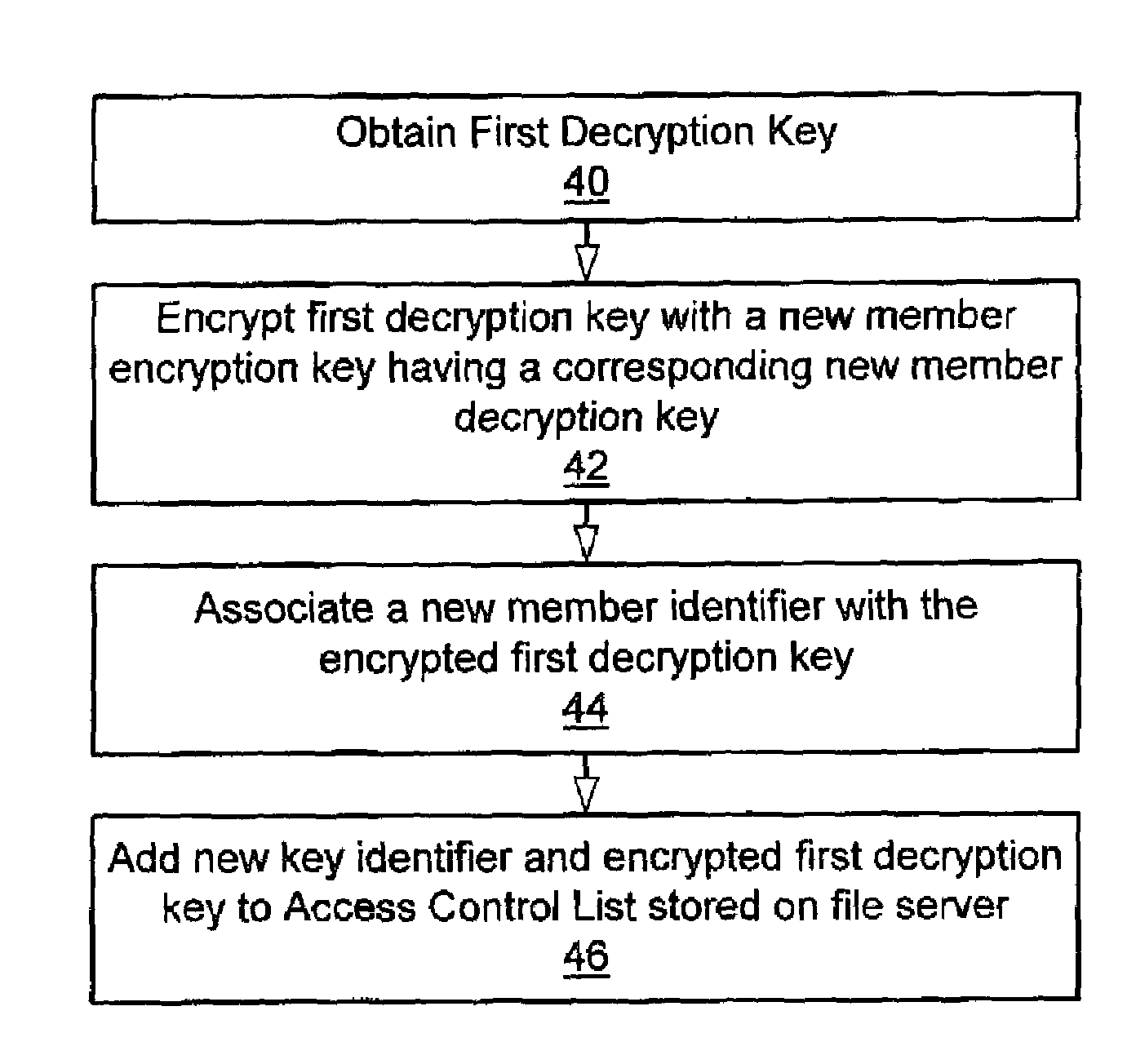
InactiveUS7178021B1Safe storageEasy accessKey distribution for secure communicationPublic key for secure communicationClient-sideData storing
A method and apparatus for utilizing a non-secure file server for storing and sharing data securely only among clients and groups authorized to read and modify the data. A first client that desires to store data on the file server encrypts the data with a first encryption key having an associated first decryption key. The client encrypts the first decryption key with a second encryption key having an associated second decryption key known to the first client. Additionally, the first decryption key is encrypted with respective encryption keys of other clients or groups intended to have access to the data stored on the file server and the clients and groups retain their respective decryption keys. All of the encrypted first decryption keys are stored within an access control list in association with the encrypted data on the non-secure file server. In response to an indication that the data should be transmitted to one of the clients, the file server returns to the client the encrypted data along with at least the applicable encrypted first decryption key for the respective client. The client is able to decrypt the first decryption key and decrypt the data using the unencrypted first decryption key. The data may then be modified and securely stored on the file server as described above. The first decryption key may also be encrypted with a second encryption key having a second decryption key known to members of a group or a group server. The first encryption key encrypted with the group second encryption key is stored in the access control list so that group members can obtain access to the encrypted data stored on the file server.
Owner:ORACLE INT CORP
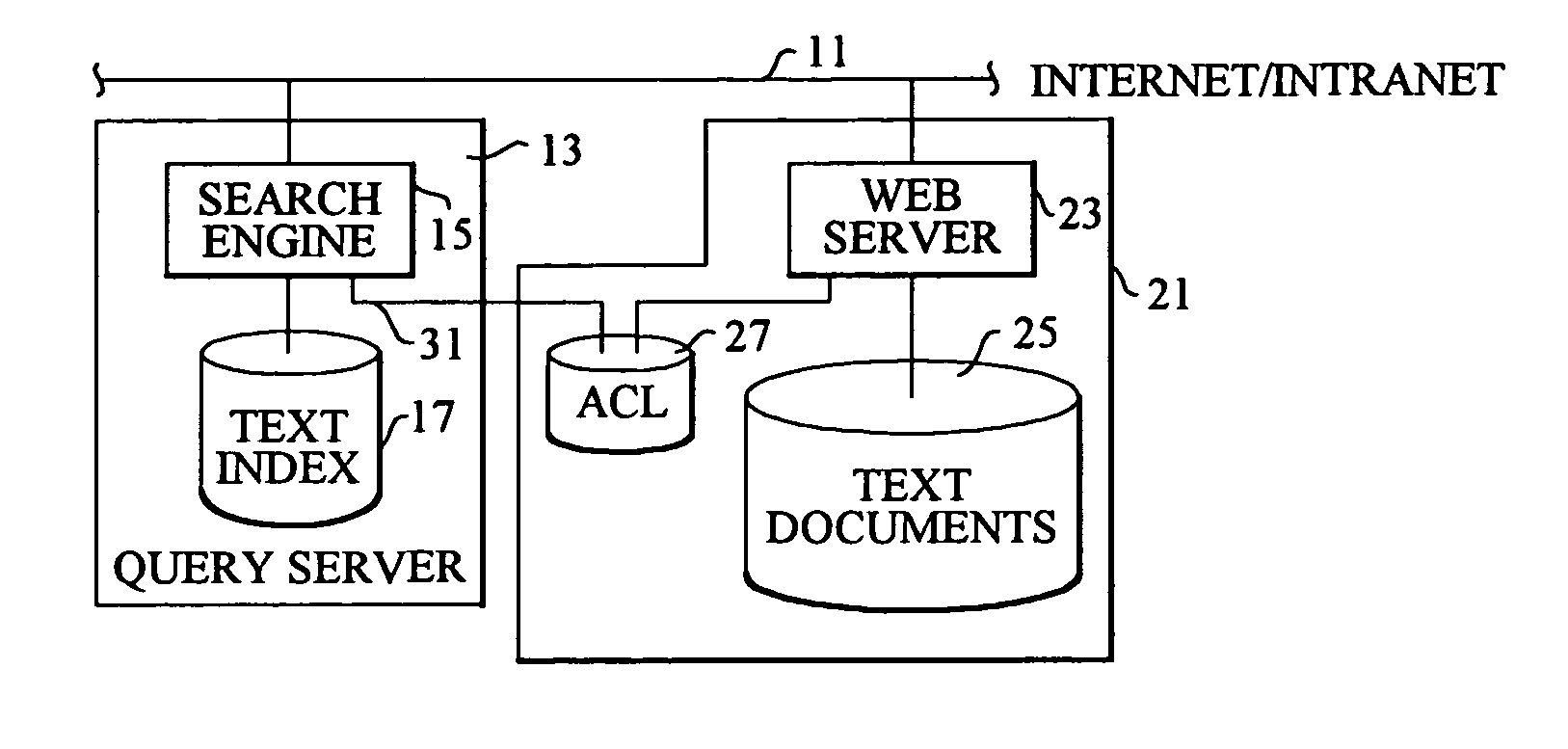
Document retrieval system with access control
InactiveUS7031954B1Data processing applicationsDigital data information retrievalElectronic documentUniform resource locator
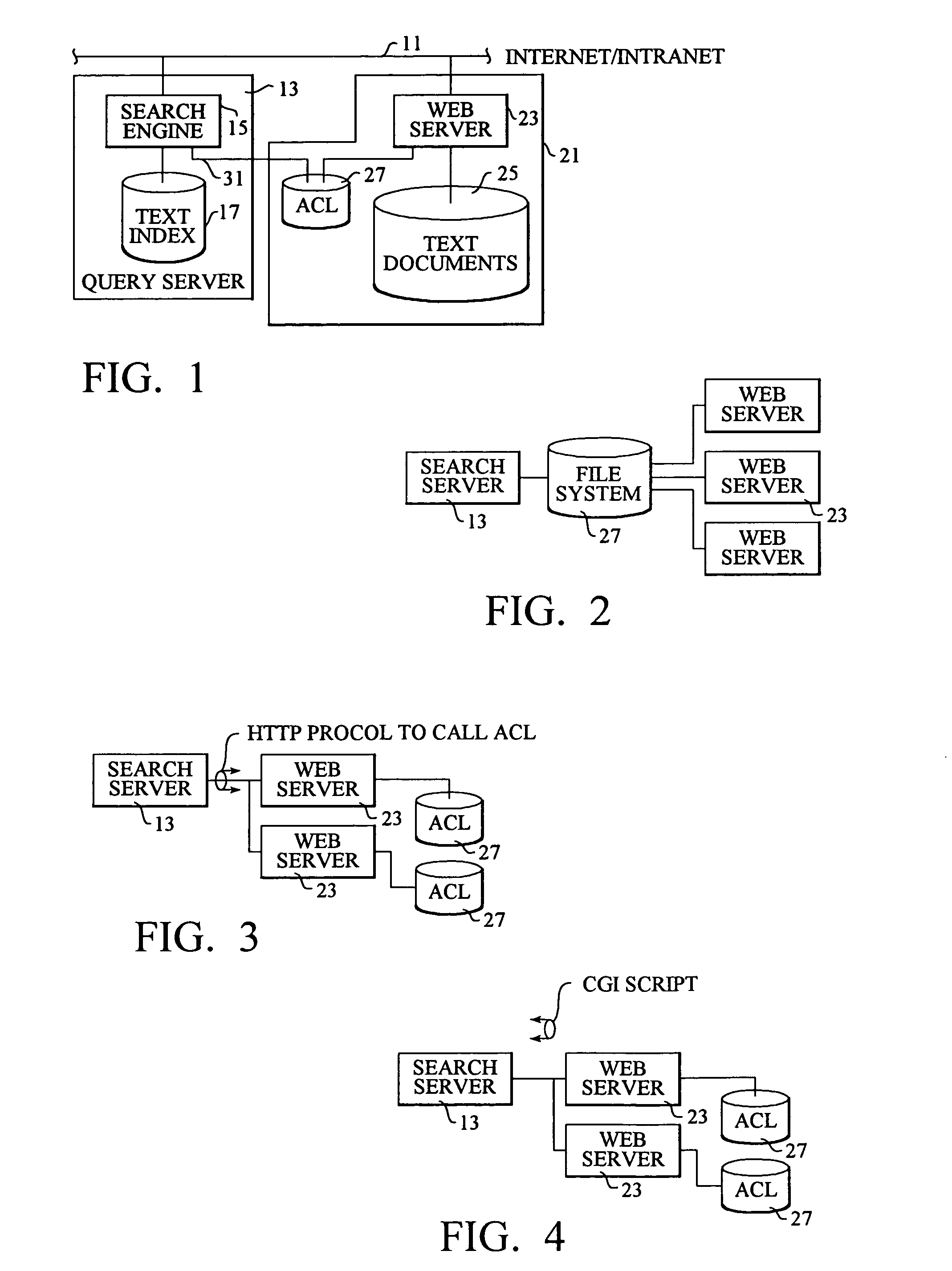
An electonic document retrieval system and method for a collection of information distributed over a network having documents stored in web or document servers in which an access control list relates user identification to documents to which a user has access. No access control lists are contained in the documents themselves nor are comparisons made between lists of users, with their access levels, and the classifications of documents. Rather, by the use of URLs or pointers, it is possible to associate every document to which a user has access with the user identification number or code. URLs have a hierchical format which allows partial URLs to indicate levels of access. HTTP protocol, FTP and CGI protocol employ URL calls for documents and can use the access control method and system of the present invention. When a search query is applied to a query server, a list of hits is returned, together with pertinent URLs. The query server consults each access control list associated with each document server, to present to the user only those URLs for which he has a proper access level. Other URLs for which the user does not have proper access are kept hidden from the user.
Owner:GOOGLE LLC
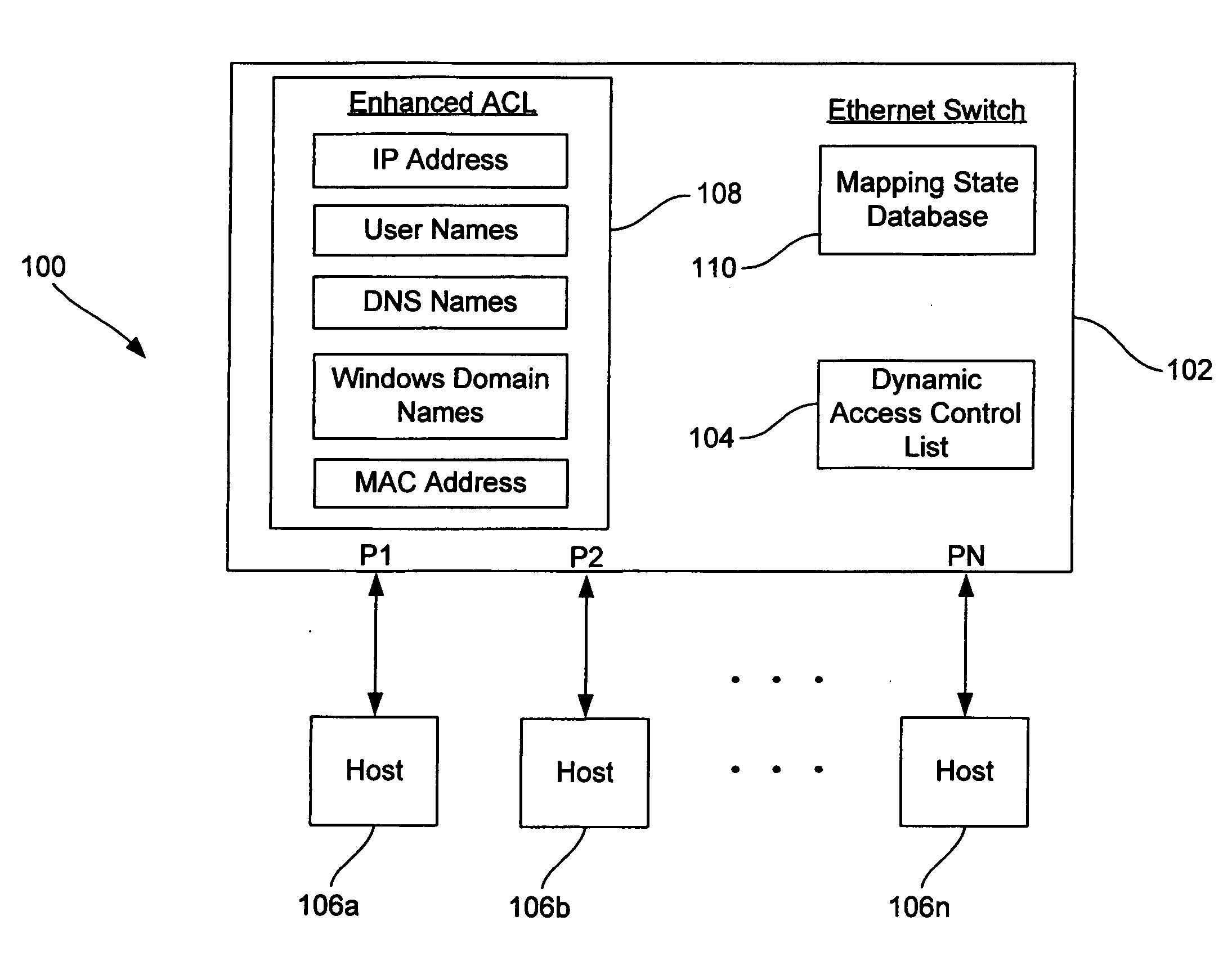
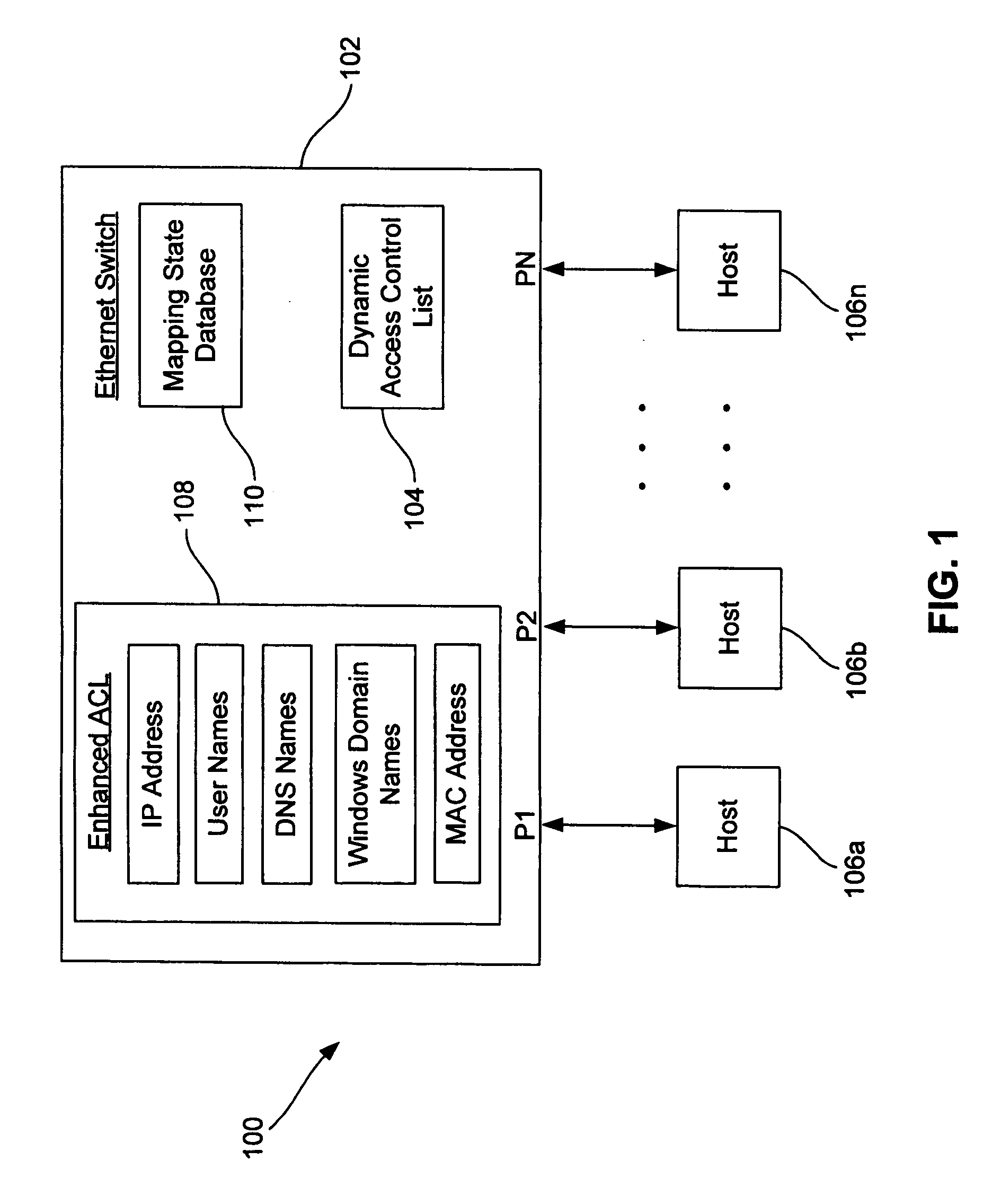
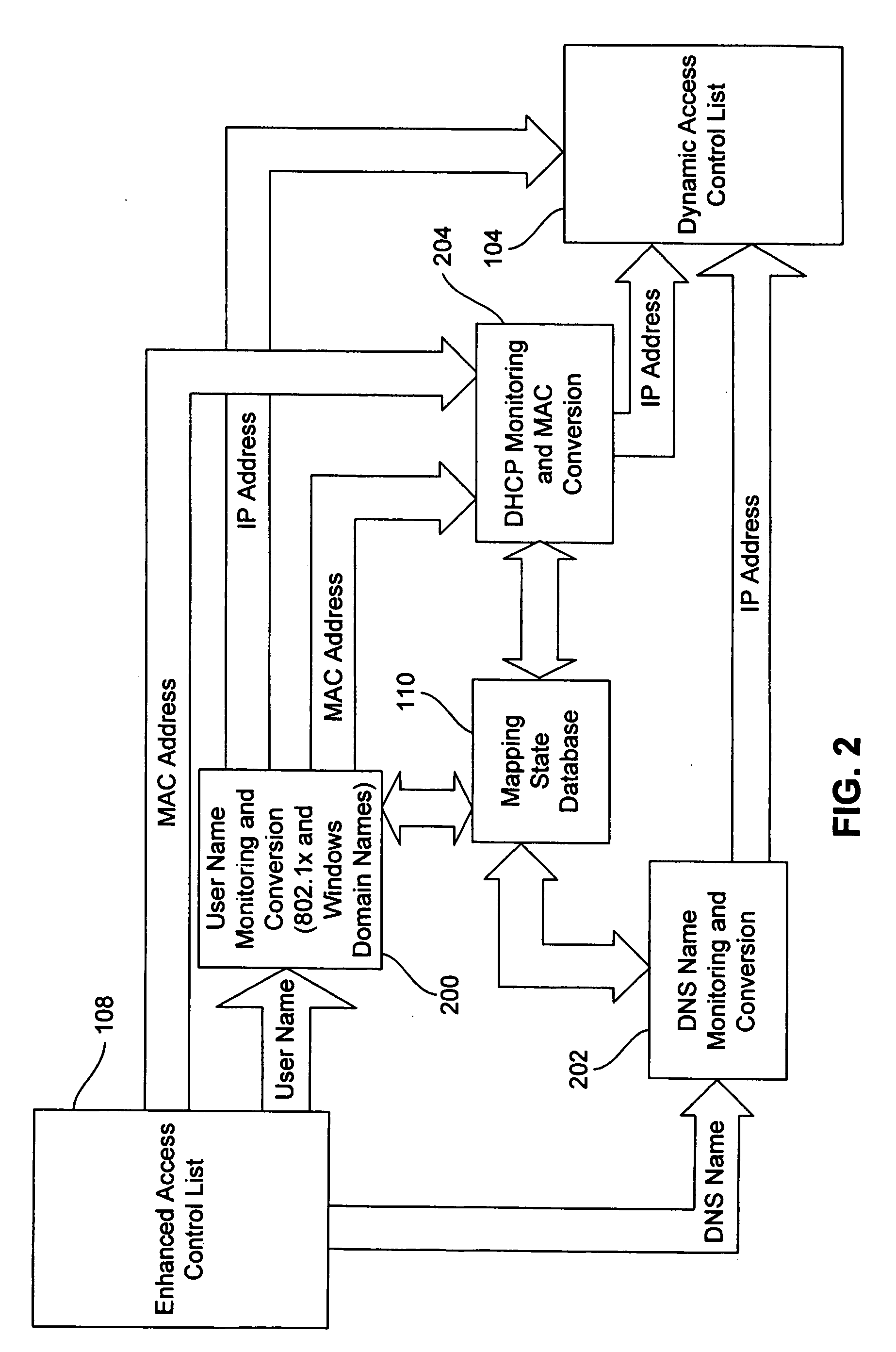
Dynamic access control lists
ActiveUS20050259654A1Data switching by path configurationMultiple digital computer combinationsDomain nameIp address
A method controls access of a user to a network including a plurality of hosts coupled together through a network switch. The method includes storing in the network switch an enhanced access control list containing data related to at least one of user names, DNS names, domain names, and physical addresses. A dynamic access control list is generated from the enhanced access control list, with the dynamic access control list containing a plurality of IP addresses that restrict access of the user to the network.
Owner:LIONRA TECH LTD
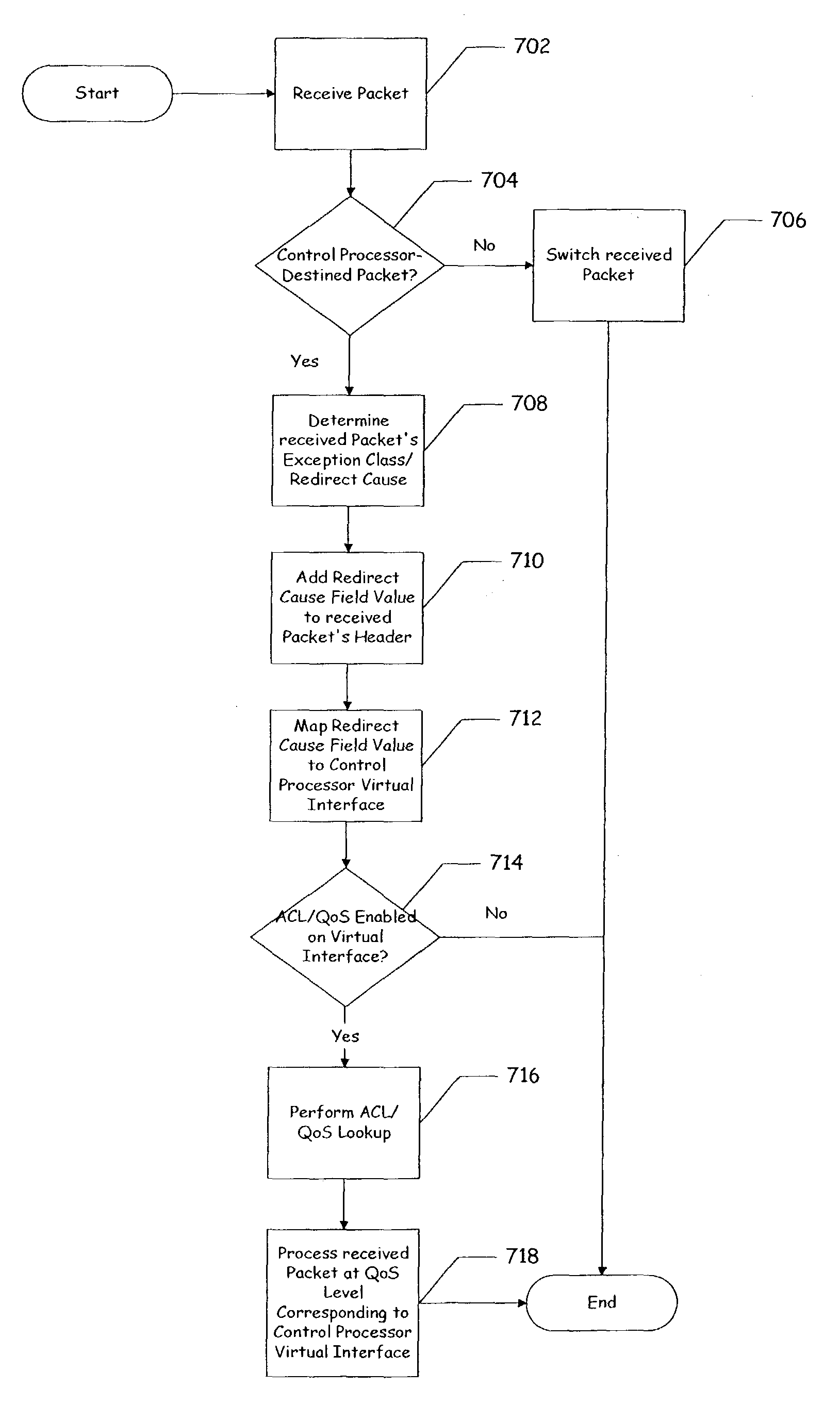
Method and apparatus to apply aggregate access control list/quality of service features using a redirect cause
ActiveUS7953885B1Fine granularityDigital computer detailsData switching by path configurationQuality of serviceDistributed computing
A method and apparatus to apply aggregate ACL / QoS features using a redirect cause is disclosed. According to one embodiment of the present invention, a control processor configured to support a plurality of virtual interfaces is provided, wherein each of the plurality of virtual interfaces is associated with a quality of service level. According to another embodiment, each quality of service level is associated with a processing bandwidth of the control processor. According to yet another embodiment, a control processor interface is provided coupled to the control processor which is configured to select a virtual interface of the plurality of virtual interfaces using data of a received data unit, and to transfer the received data unit to the selected virtual interface.
Owner:CISCO TECH INC
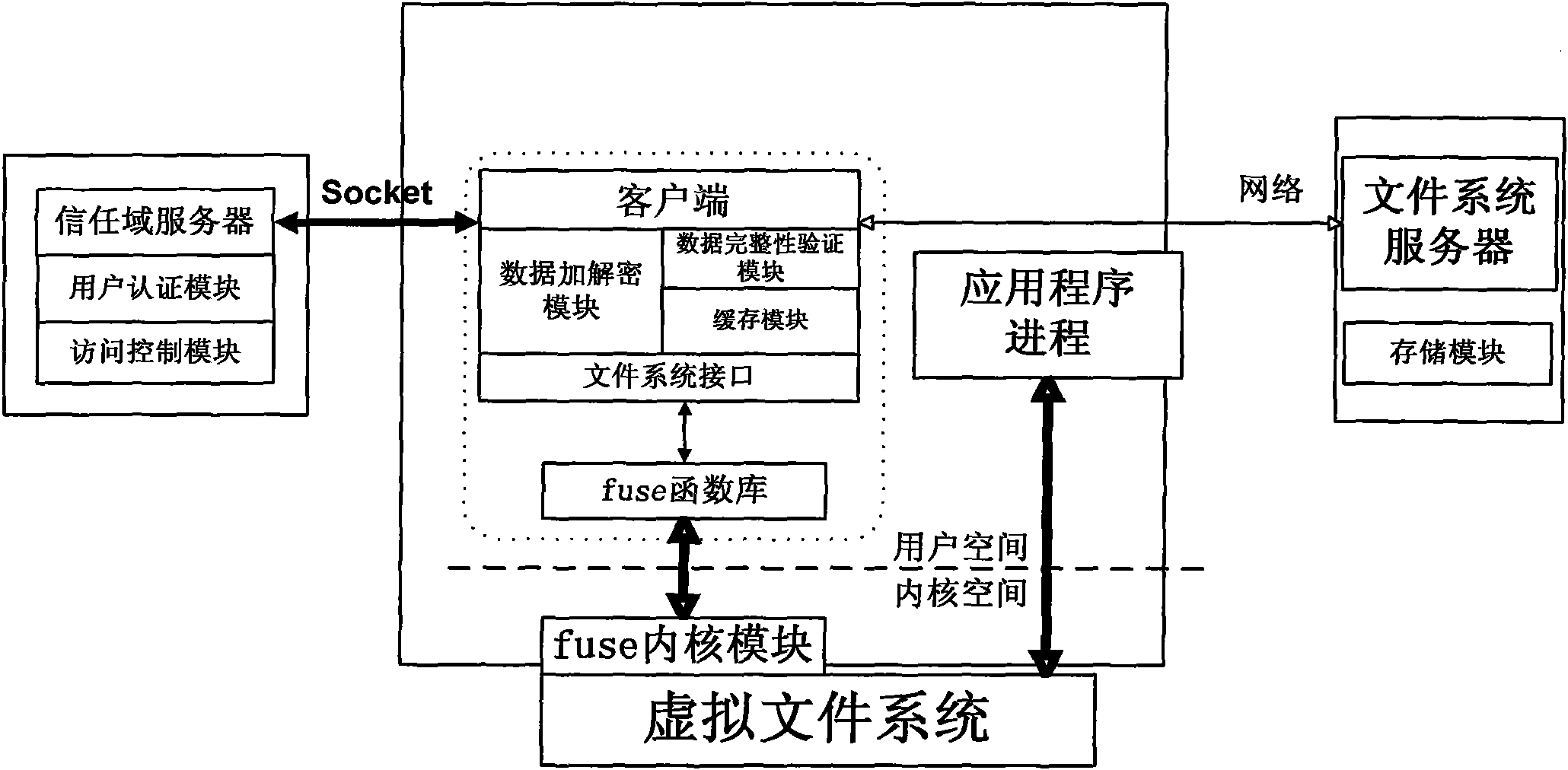
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
Remote access vpn mediation method and mediation device
InactiveUS20060143702A1Secure distributionKey distribution for secure communicationDigital data processing detailsPrivate IPCommunication unit
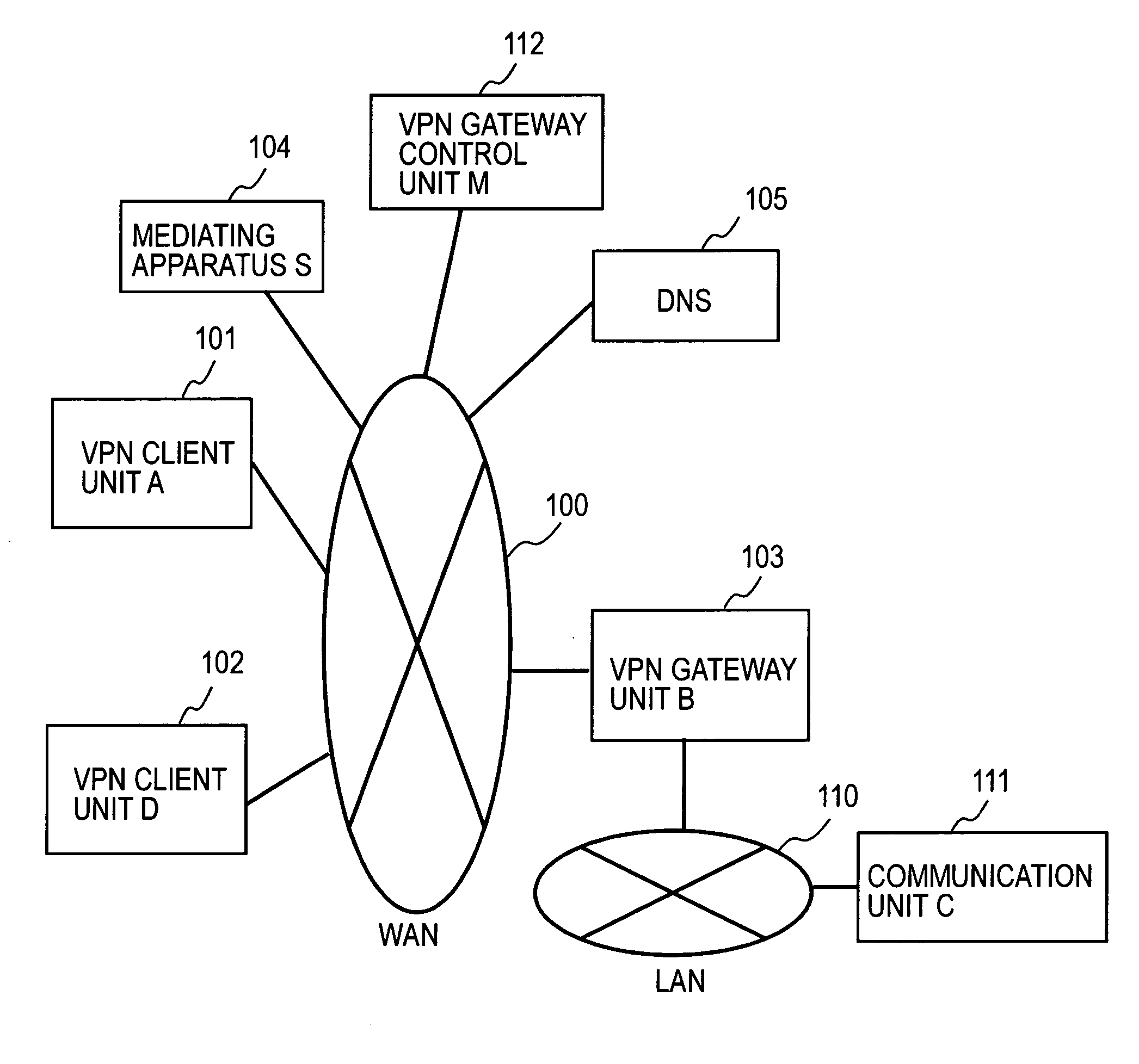
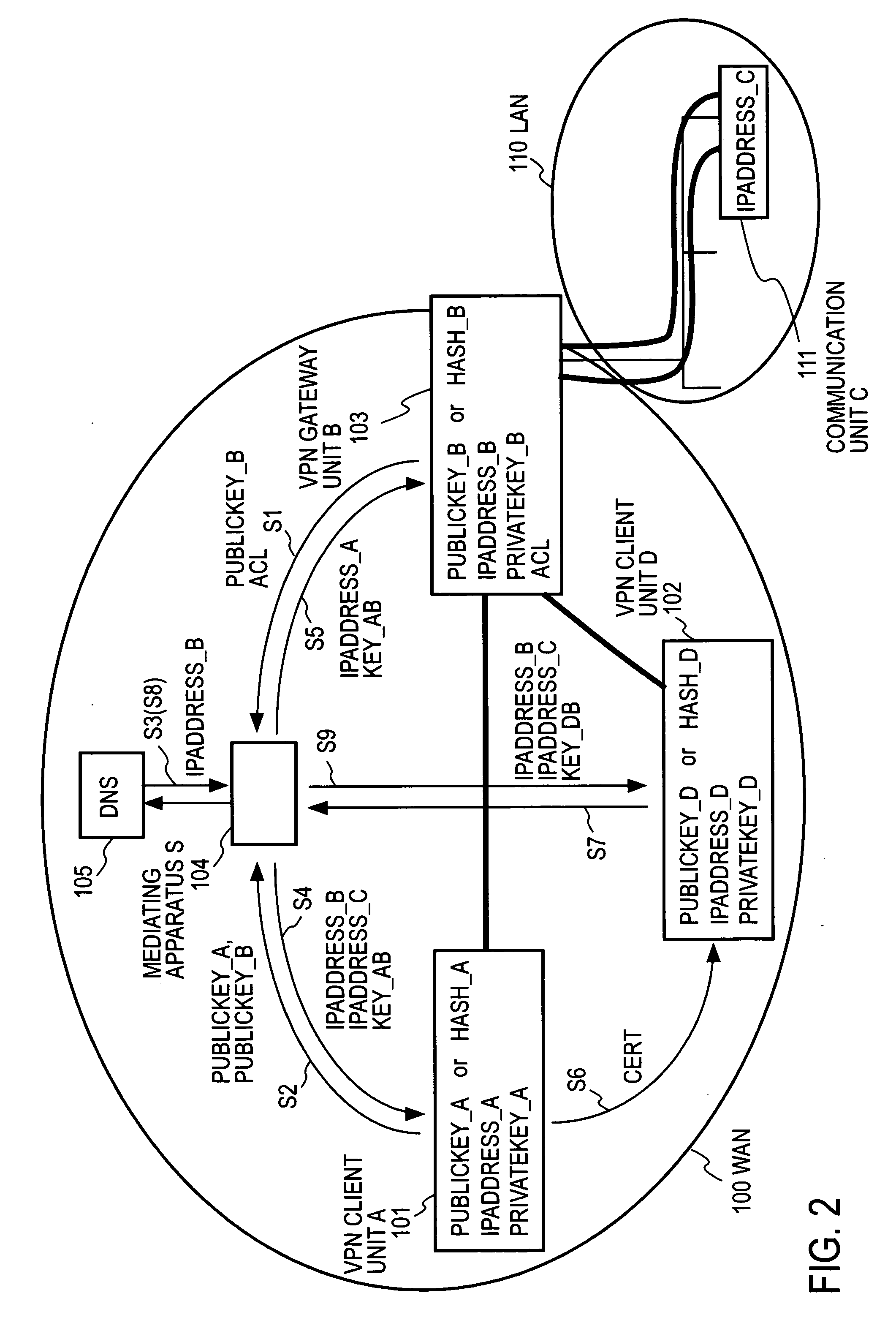
A mediating apparatus is provided on an IP network, and stores an access control list (ACL) retained in a VPN gateway unit. The mediating apparatus: receives a retrieval request from a VPN client unit; acquires a private IP address of a communication unit by reference to ACL; searches DNS to acquire therefrom an IP address of the VPN gateway unit; generates a common key that is used for authentication between the VPN client unit and the VPN gateway unit and for encrypted communication therebetween; sends the IP address of the VPN gateway unit, the private IP address of the communication unit, and the common key to the VPN client unit; and sends the IP address of the VPN client unit and the common key to the VPN gateway unit.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
System for electronic repository of data enforcing access control on data retrieval
InactiveUS6839843B1Improve system efficiencyAvoid repetitionDigital data processing detailsUser identity/authority verificationThird partyElectronic document
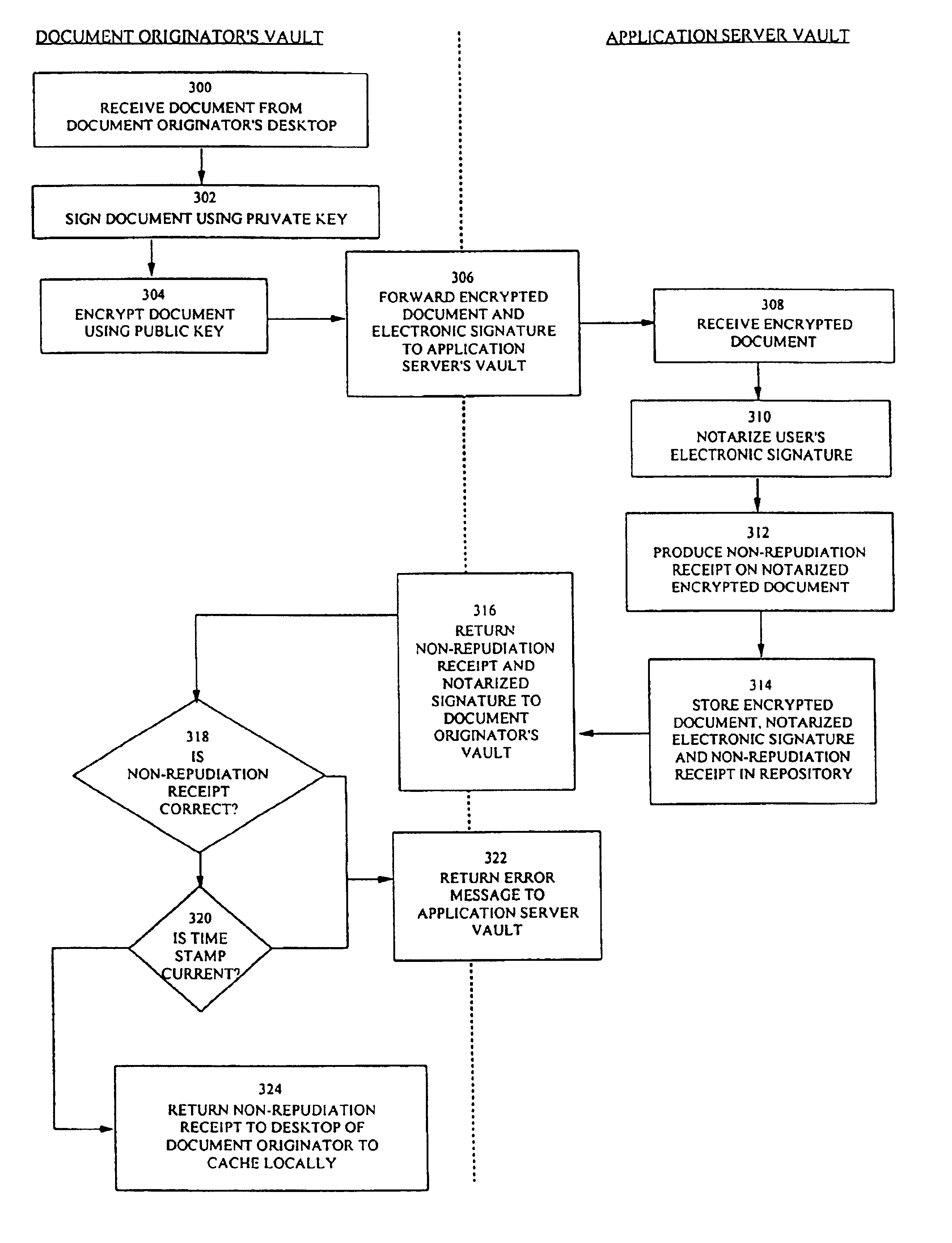
When an electronic document is made available for review by other entities, it is often convenient to store the document in a repository or database managed by a third party. A system is provided in which the originator of the document is able to ensure the integrity and security of its document filed with a third party repository without having to trust the administrator of the repository. Both the document originator and the repository administrator have vault environments which are secure extensions of their respective work spaces. The vault of the document originator encrypts a document that it receives from the originator, prior to forwarding it on to the vault of the repository. On receipt of the encrypted document, the repository's vault signs the encrypted document itself before storing the document in the electronic repository and returns to the originator's vault proof of deposit of the encrypted document in the form of a copy of the signed encrypted document. An access control list identifying access ownership privileges for the document are also stored in the repository. Updates to the access control list are under the control of document originator, or another computer designated by the document originator. When a request is made to view the document, it is made from the vault of the requesting party (a secure extension of the requesting party's work space) to the repository's vault. The repository's vault retrieves a copy of the encrypted document which it forwards, along with the requestor's identity to the originator's vault. The originator's vault verifies that the access control is valid, then verifies that the requestor is authorized to view the document from the access control list, then decrypts the document and forwards the decrypted document directly to the requestor's vault. The requestor provides proof of receipt of the decrypted document.
Owner:IBM CORP
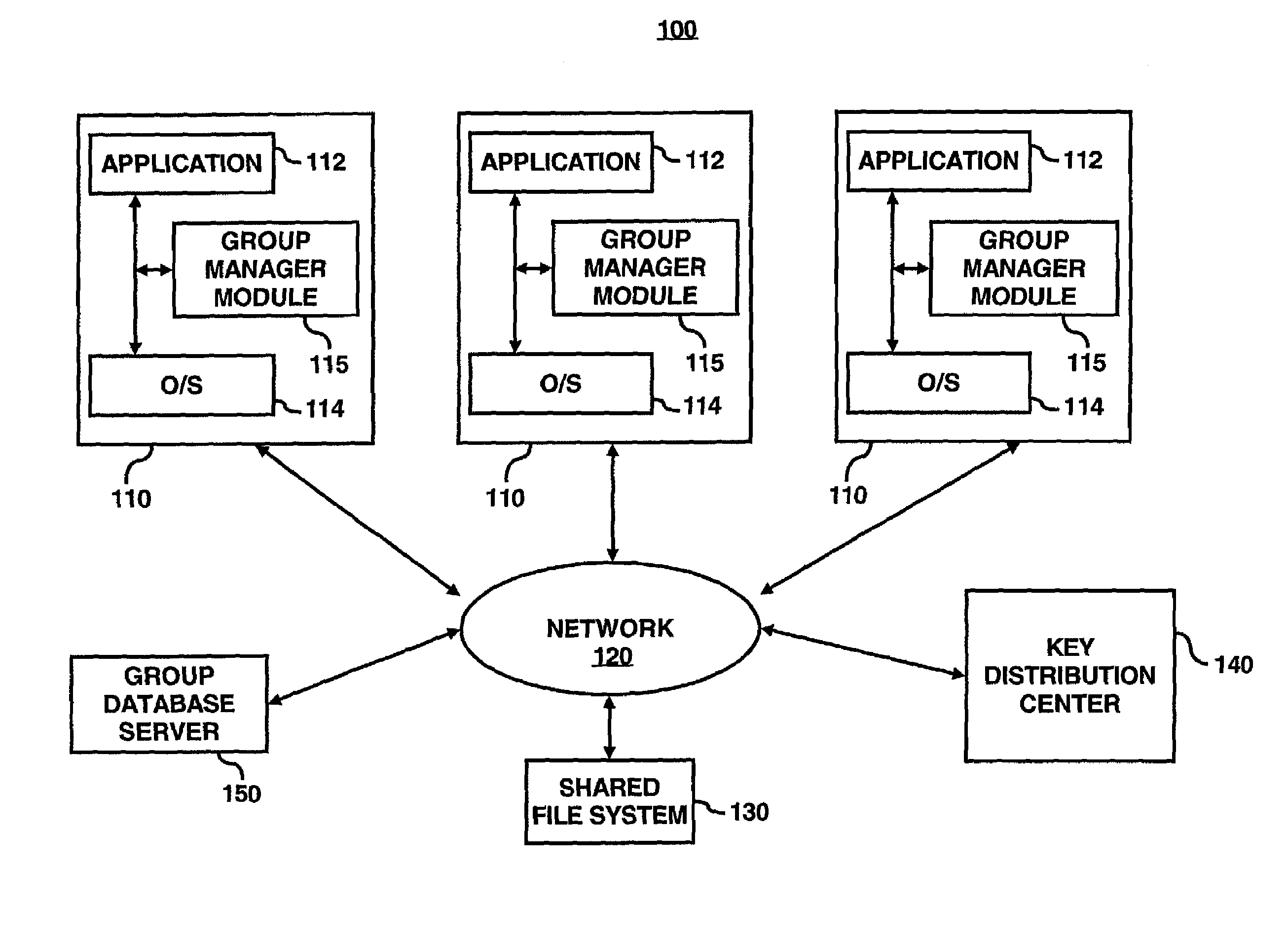
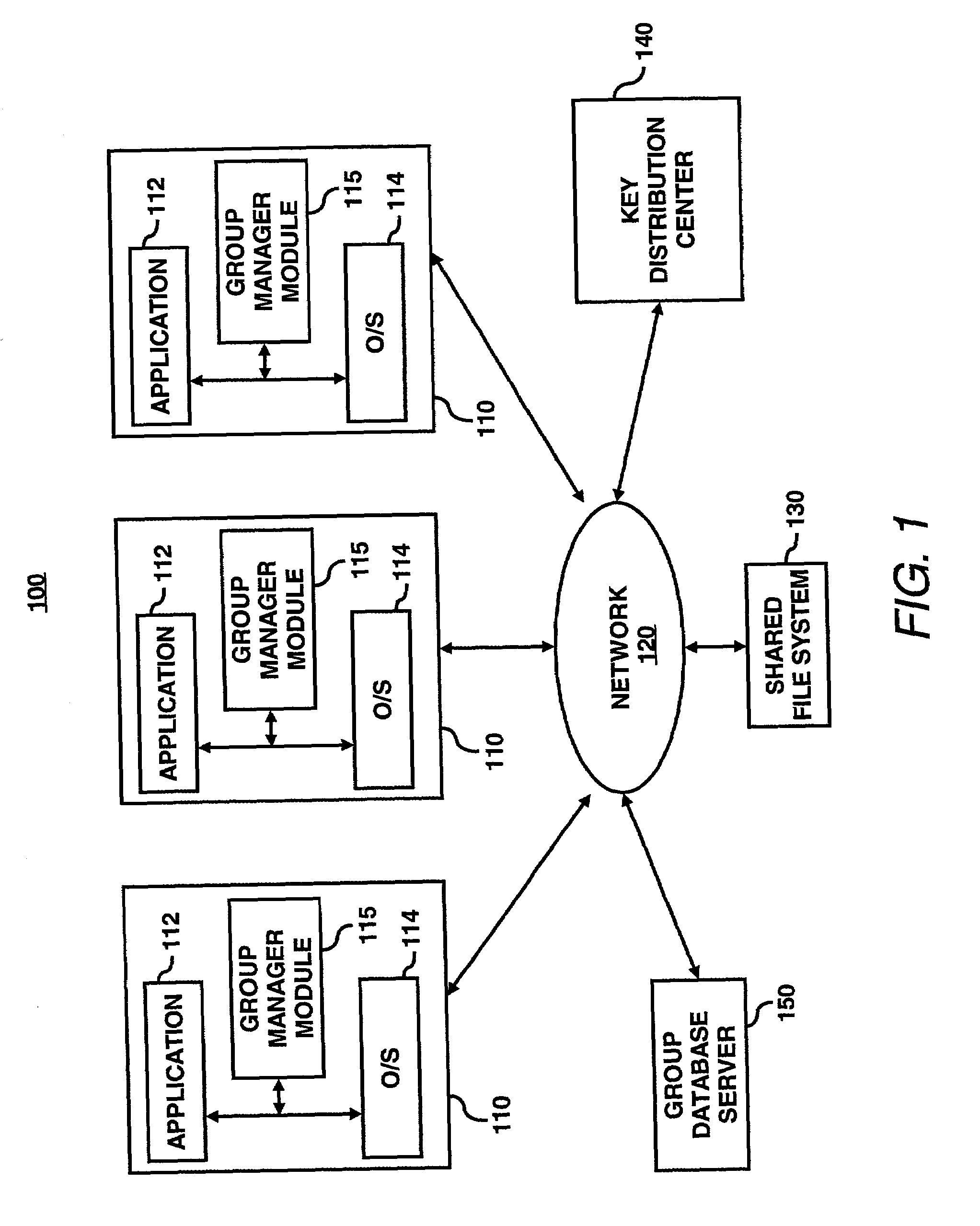
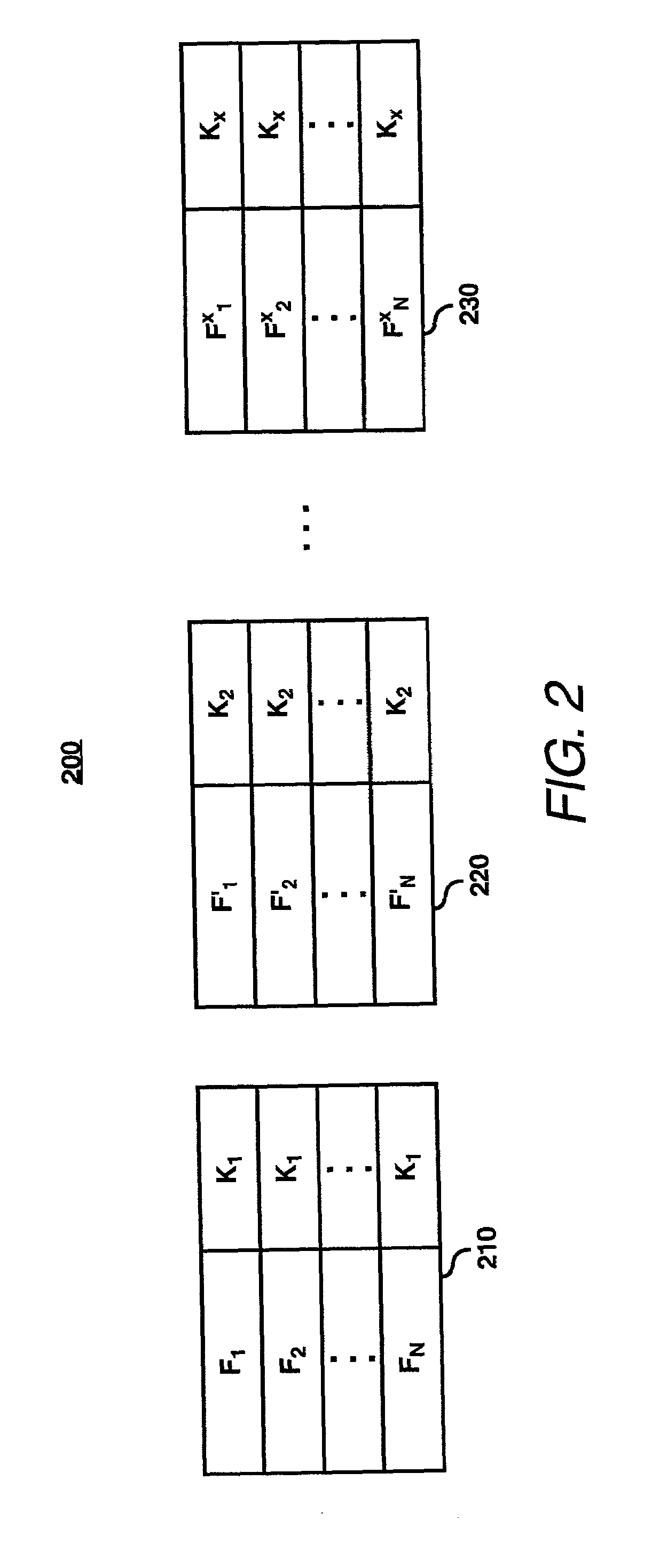
System for optimized key management with file groups
A group manager module may provide the capability to segregate or associate files into file encryption groups. A file may be placed into a file encryption group based on the attributes of the file. The attributes may be characteristics / parameters that describe who has access to a file such as UNIX permission / mode bits (group-read / write / executable bit, owner-read / write / executable bits, users-read / write / executable bits) or other system for access control lists (ACLs). Once associated with a file encryption group, the file may be encrypted with the encryption (or write) key of the selected file encryption group, and thus, decrypted with the decryption (or read) key of the file encryption group. A user may have membership into multiple file encryption groups as long as the user possesses the appropriate read / write key pairs. Membership of a file in a file encryption group is determined automatically by the system based on the permission attributes assigned by the system—groups are not explicitly created by administrators or other centralized authority. It is not users that belong to groups based on their access rights, but files which belong to groups based on their permission attributes.
Owner:HEWLETT PACKARD DEV CO LP
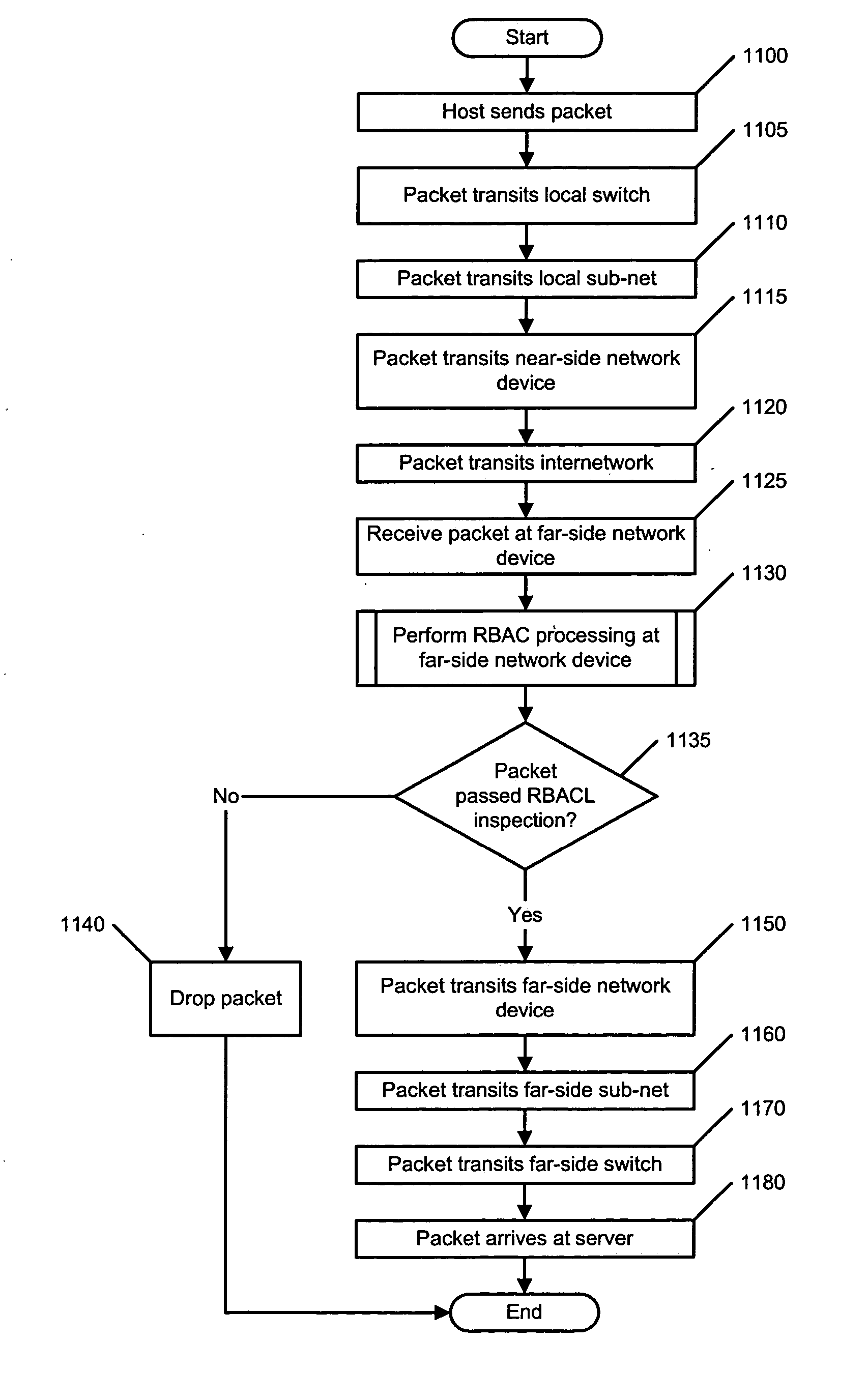
Method and apparatus for providing network security using role-based access control
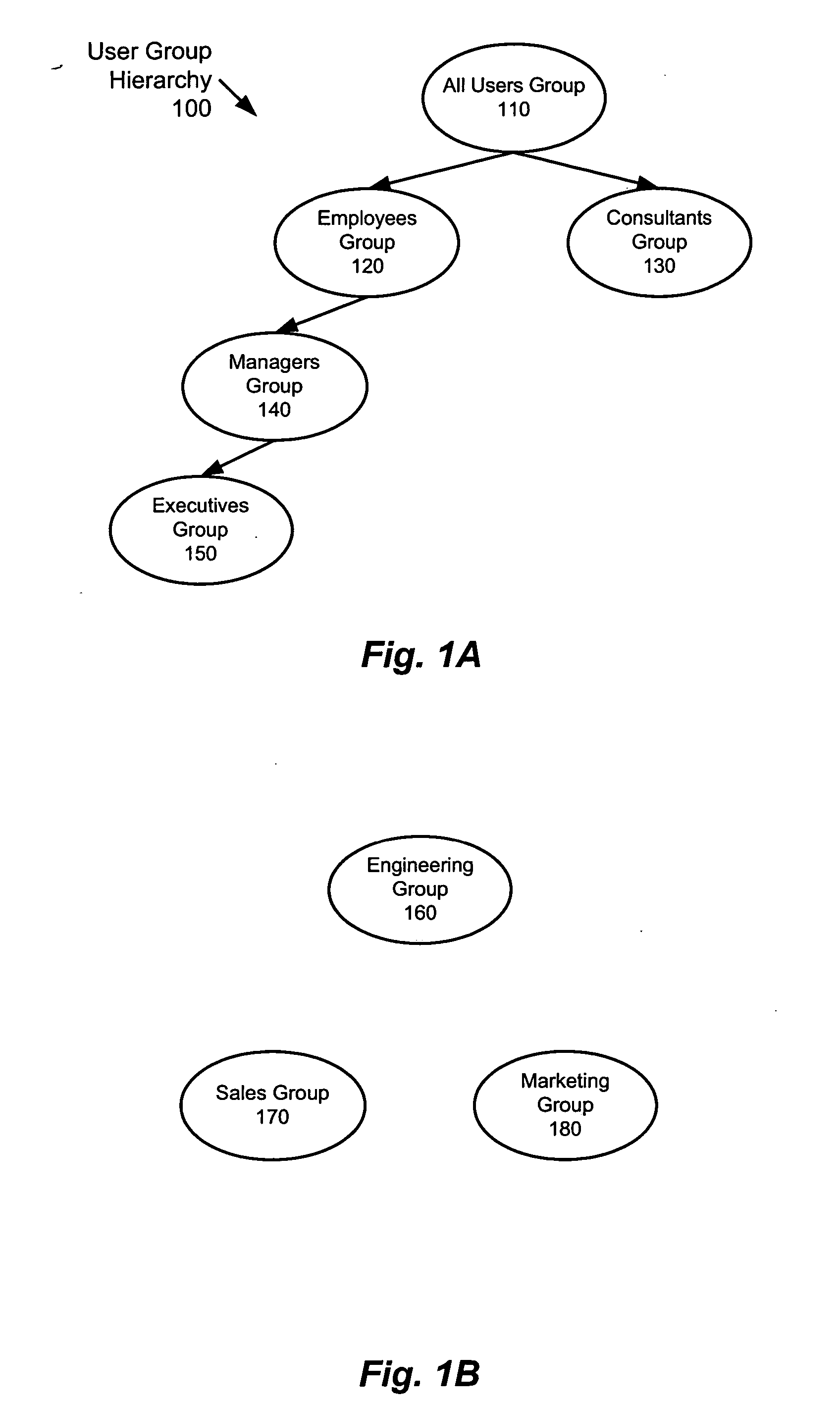
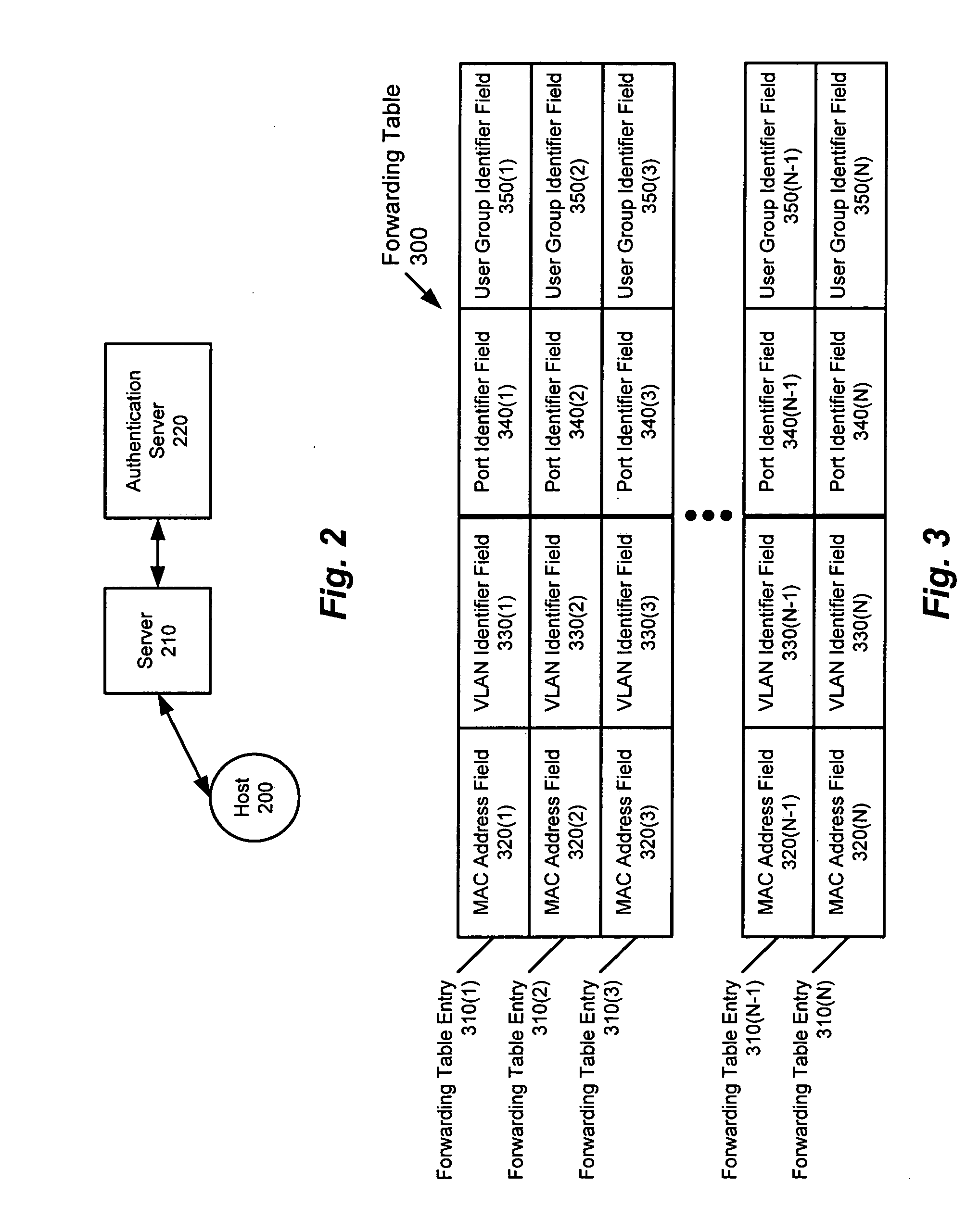
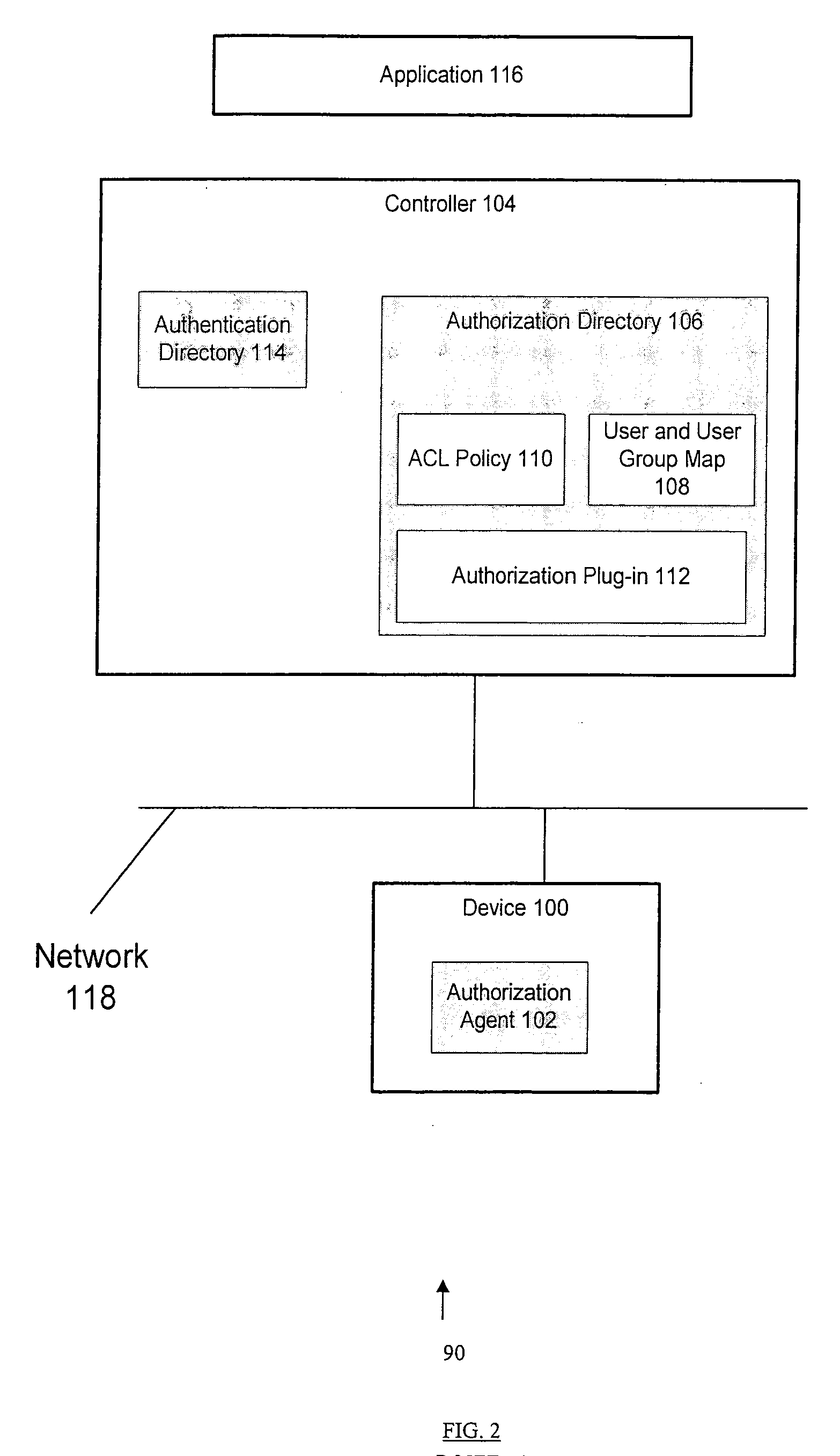
ActiveUS20050055573A1Small sizeImprove performanceDigital data processing detailsAnalogue secracy/subscription systemsAccess control listUser group
A method and apparatus for providing network security using role-based access control is disclosed. A network device implementing such a method can include, for example, an access control list. Such an access control list includes an access control list entry, which, in turn, includes a user group field. Alternatively, a network device implementing such a method can include, for example, a forwarding table that includes a plurality of forwarding table entries. In such a case, at least one of the forwarding table entries includes a user group field.
Owner:CISCO TECH INC
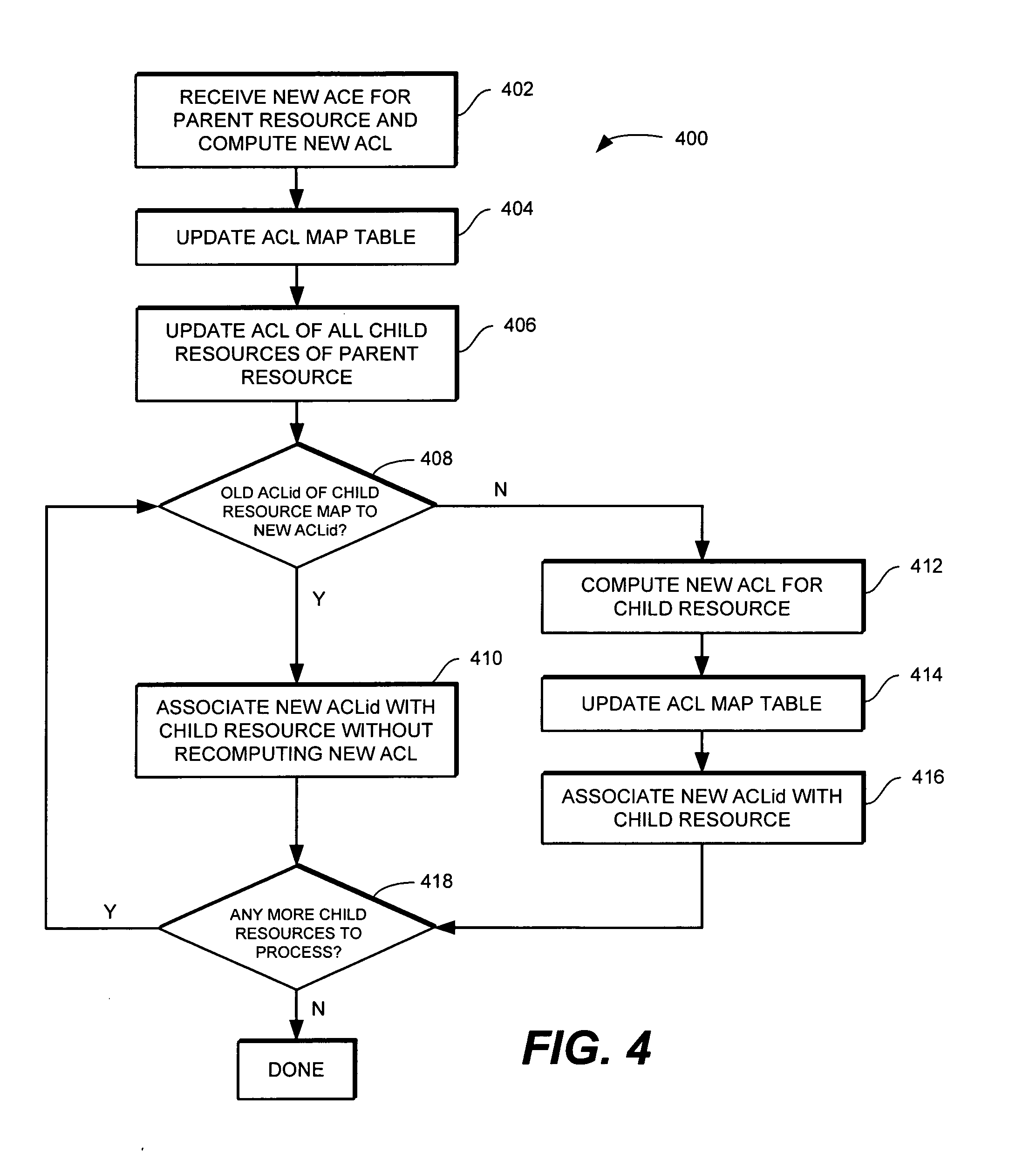
Method and apparatus for access control list (ACL) binding in a data processing system
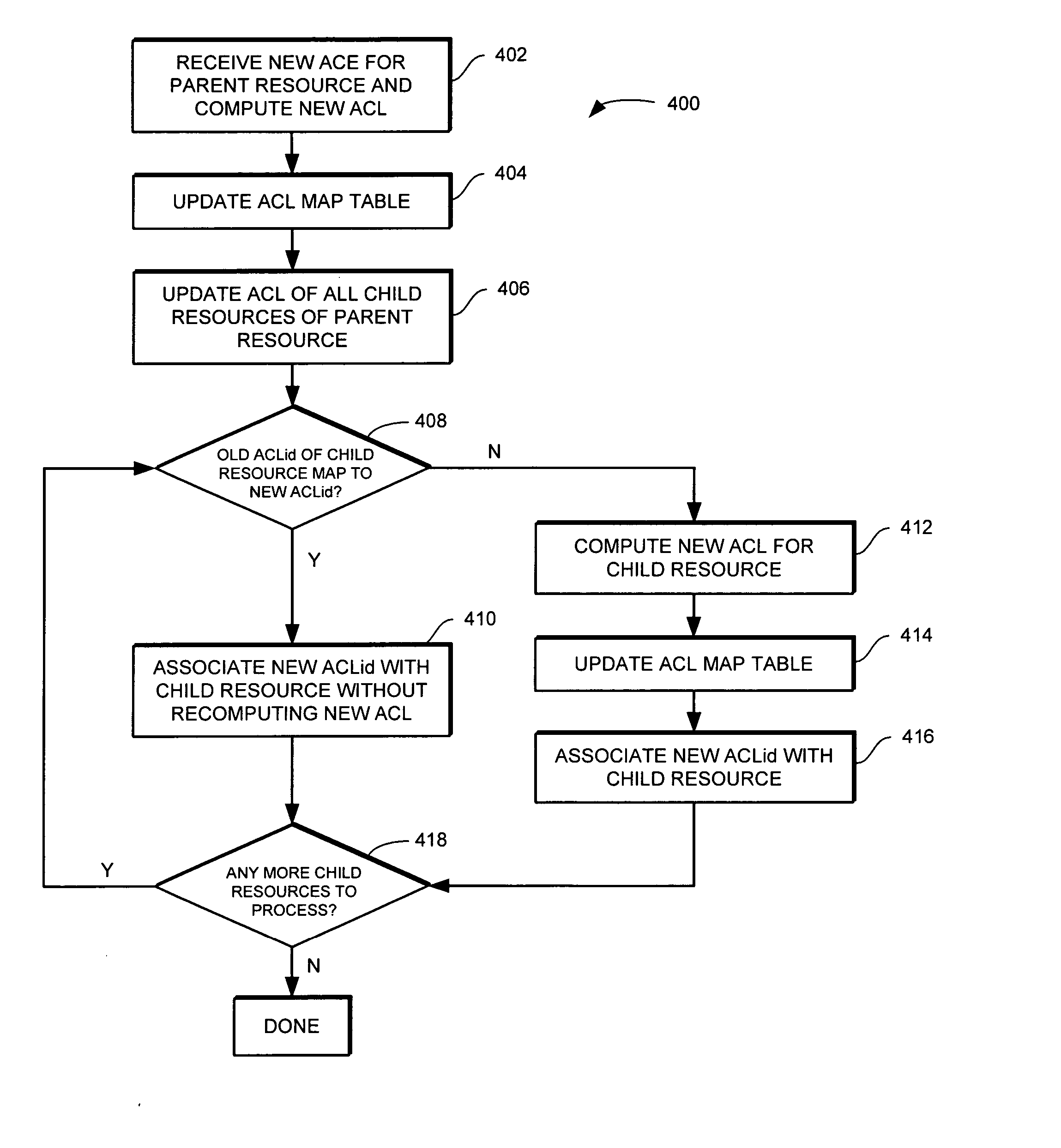
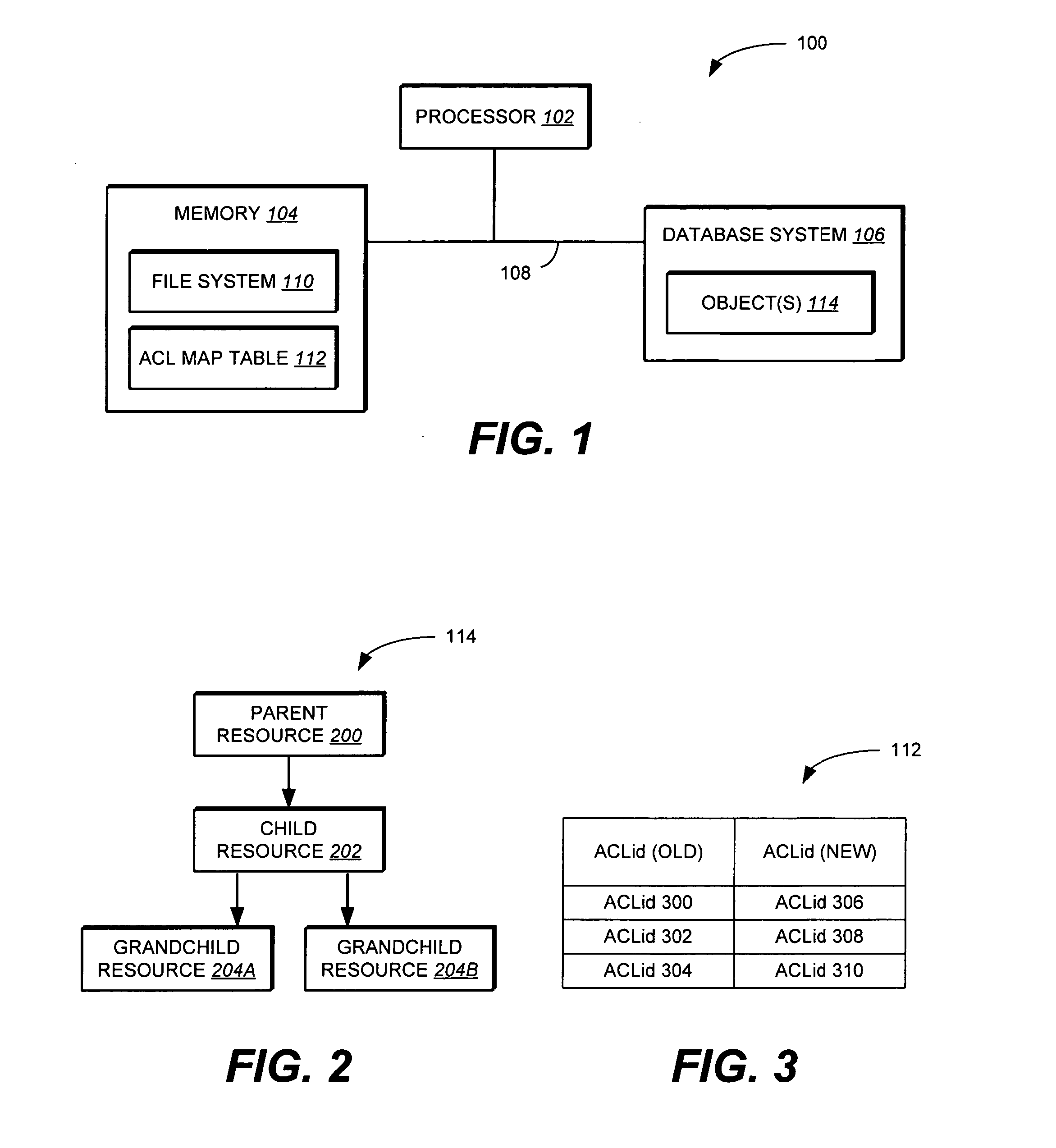
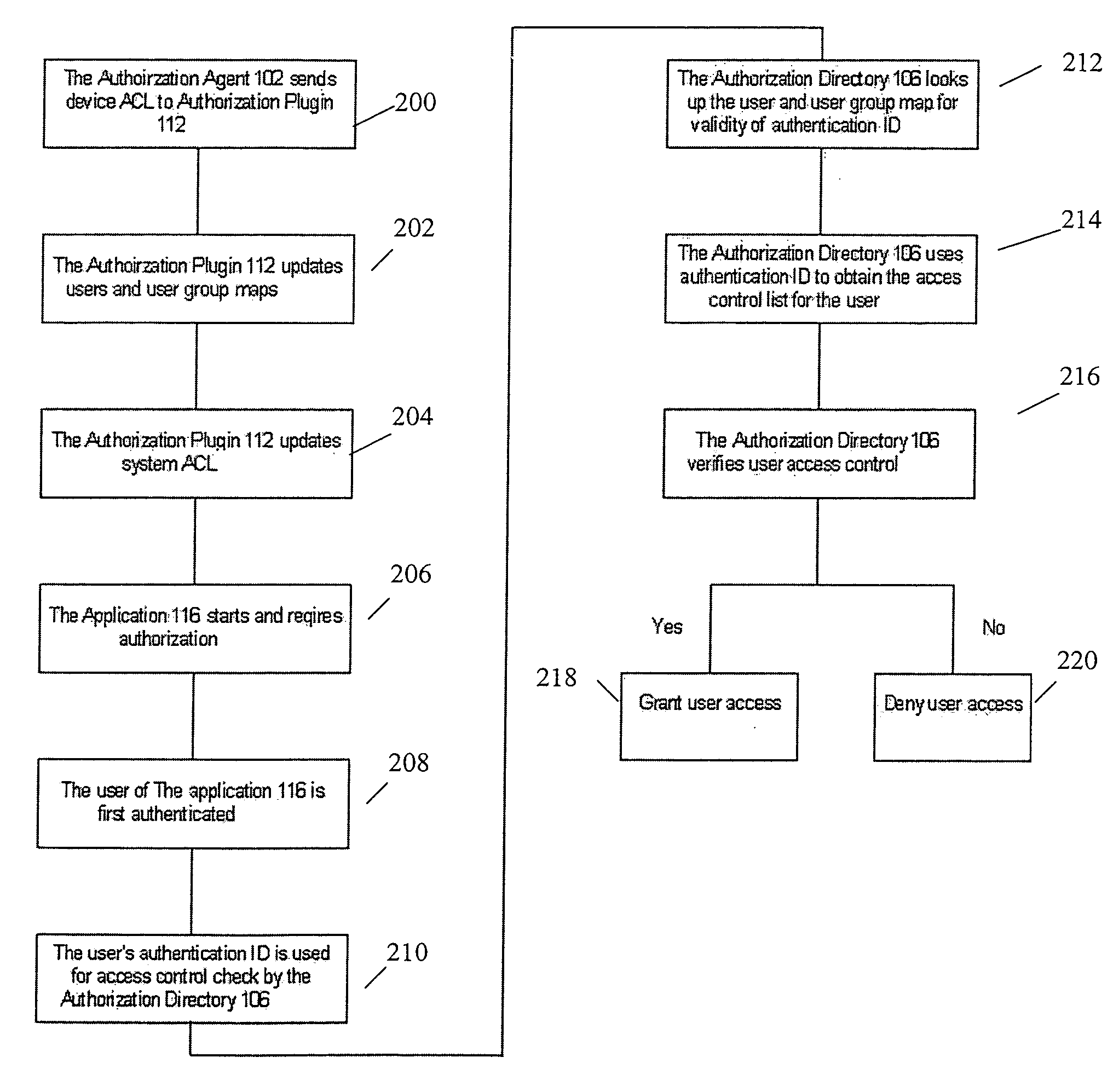
InactiveUS20070100830A1Effective processing timeEfficient executionDatabase updatingComputer security arrangementsData processing systemAccess control list
Methods, computer programs, and systems for updating an access control list (ACL) associated with one or more resources in a data processing system are provided. The method includes providing a table including a list of one or more first ACLs that map to a corresponding one or more previously computed second ACLs; and updating a current ACL associated with a first resource of the one or more resources in the data processing system including determining whether one of the one or more first ACLs in the table matches the current ACL associated with the first resource. If one of the one or more first ACLs in the table matches the current ACL associated with the first resource then updating the current ACL associated with the first resource by associating the corresponding second ACL with the first resource.
Owner:IBM CORP
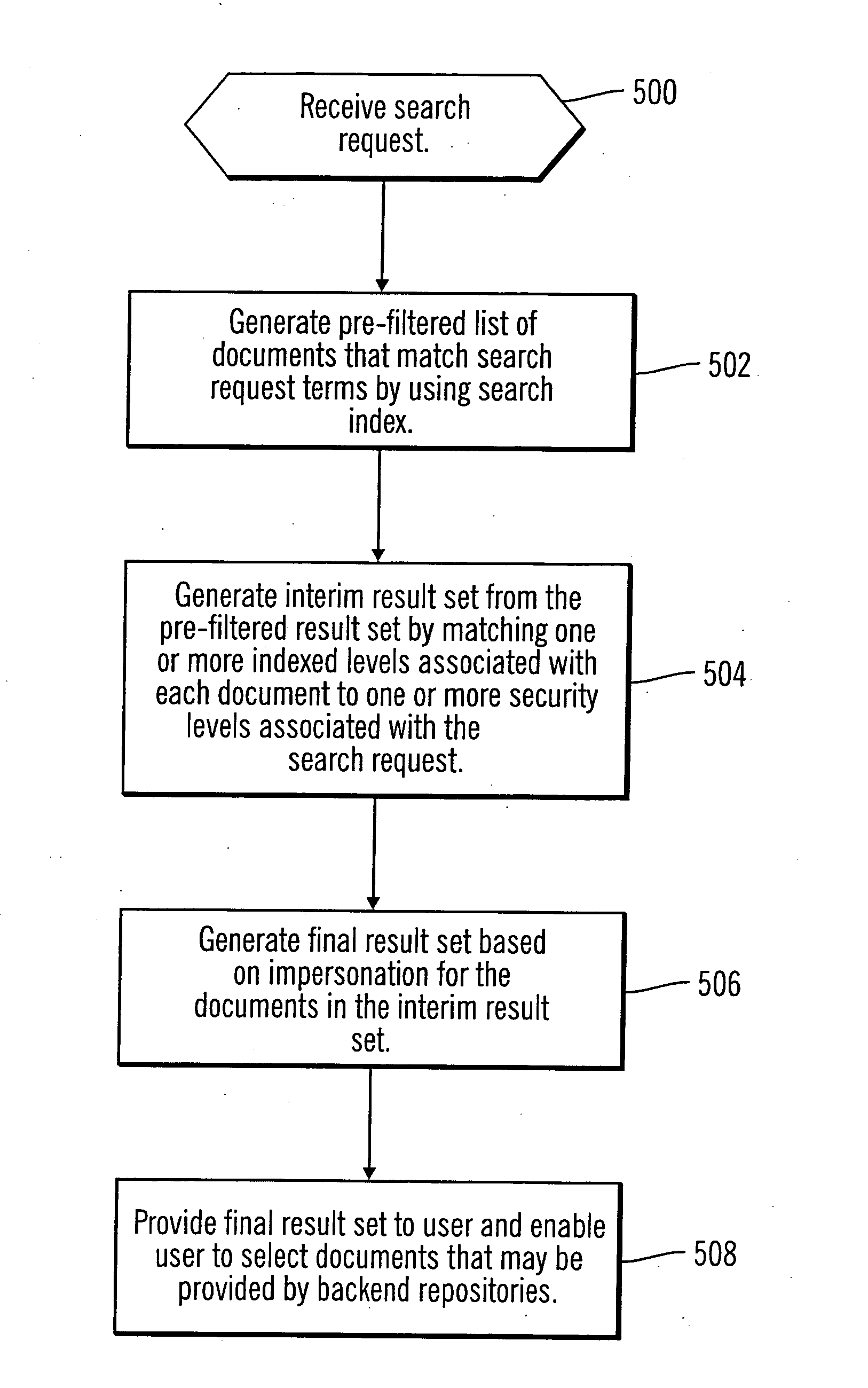
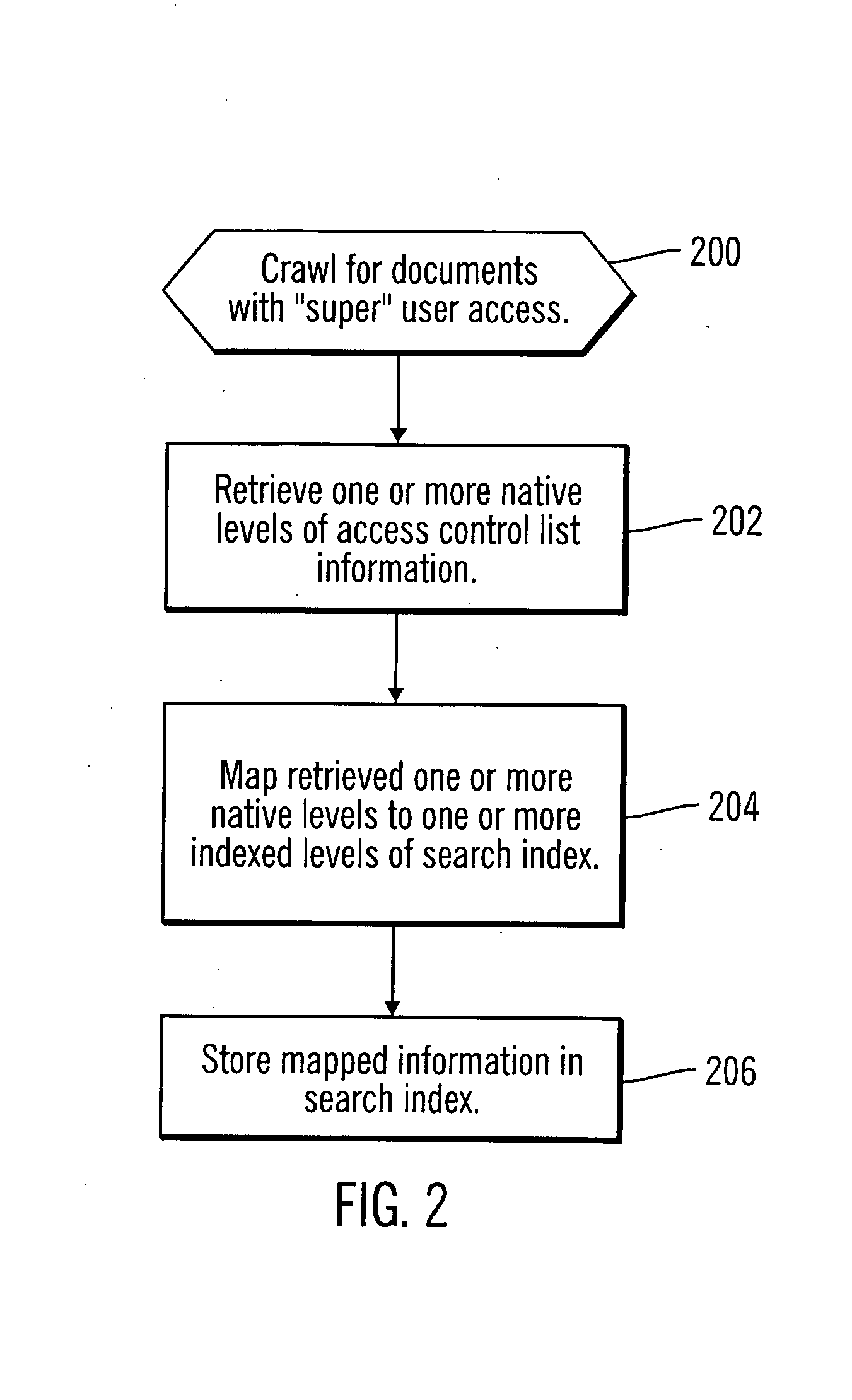
Enforcing native access control to indexed documents
InactiveUS20070016583A1Computer security arrangementsSpecial data processing applicationsPaper documentDocument preparation
Techniques are provided for processing a search request. One or more indexed levels of access control list information are stored in a search index for each document identified in the search index. An interim result set is generated by matching the one or more indexed levels of access control list information associated with each said document to one or more security groups associated with the search request. A final result set is generated from the interim result set by performing impersonation.
Owner:IBM CORP
System and method for configuring security in a plug-and-play architecture
InactiveUS20070208948A1Security configurationConfiguring security in a PnP architectureDigital data processing detailsUnauthorized memory use protectionDocumentationProtocol Application
A plug-and-play (PnP) for configuring security in a PnP architecture includes a security manager and a PnP device. The PnP device is adapted to send a device description document to a user entity. The device description document includes an address pointing to the security manager, and as such, the user entity is capable of accessing the security manager based upon the address. The security manager is adapted to authenticate the user entity, and it authenticated, to communicate with the user entity to configure application-layer security of the PnP device, whereby configuring the application-layer security includes creating an access control list (ACL) document for restricting access to a service of the PnP device. In a further aspect, the PnP device may bootstrap establishing its link-layer security with configuring its application-layer security.
Owner:CORE WIRELESS LICENSING R L
Access control system, access control method, and access control program
ActiveUS7624424B2Efficient updateEffective controlDigital data processing detailsUser identity/authority verificationAccess control matrixData access control
Owner:NEC CORP
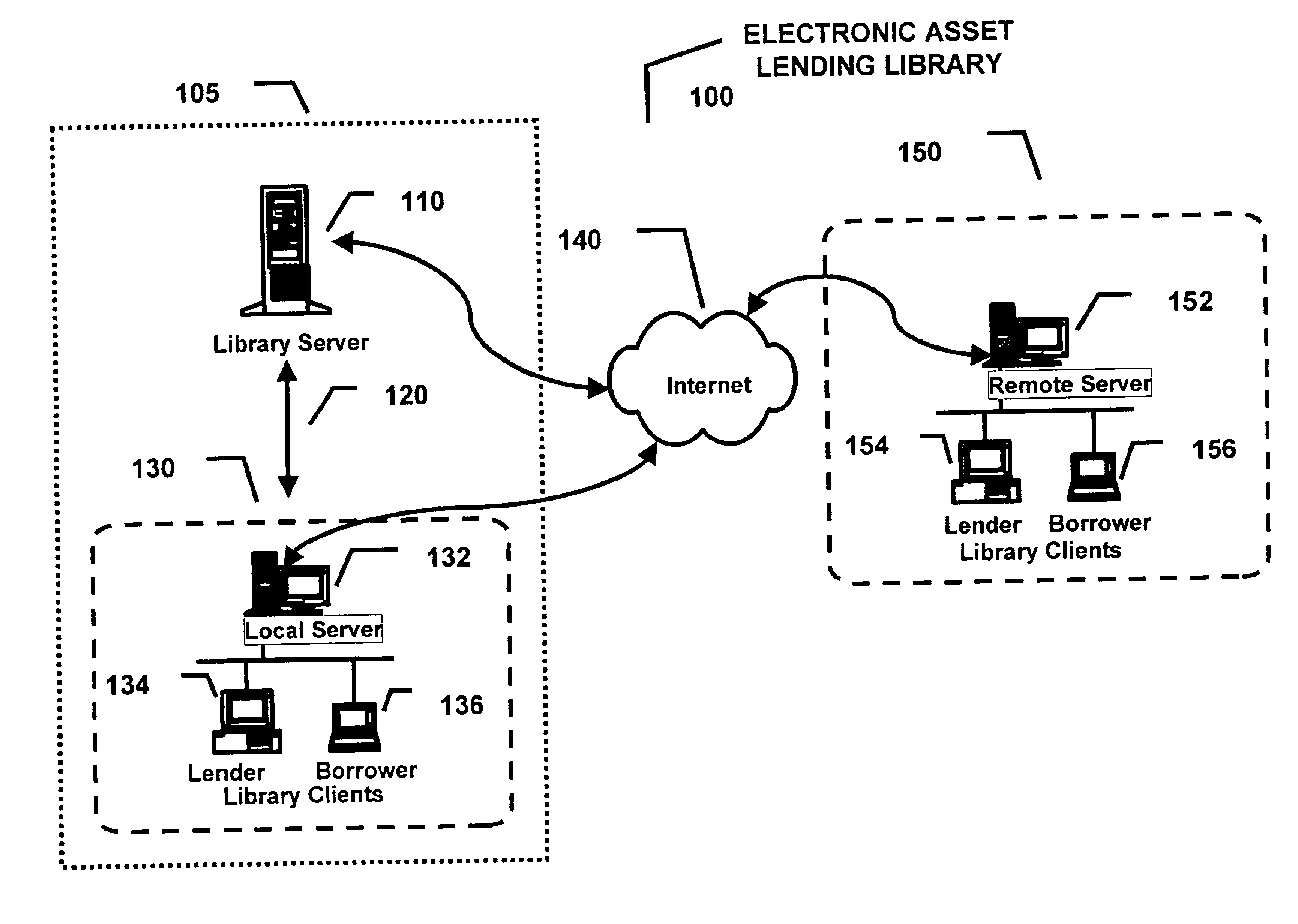
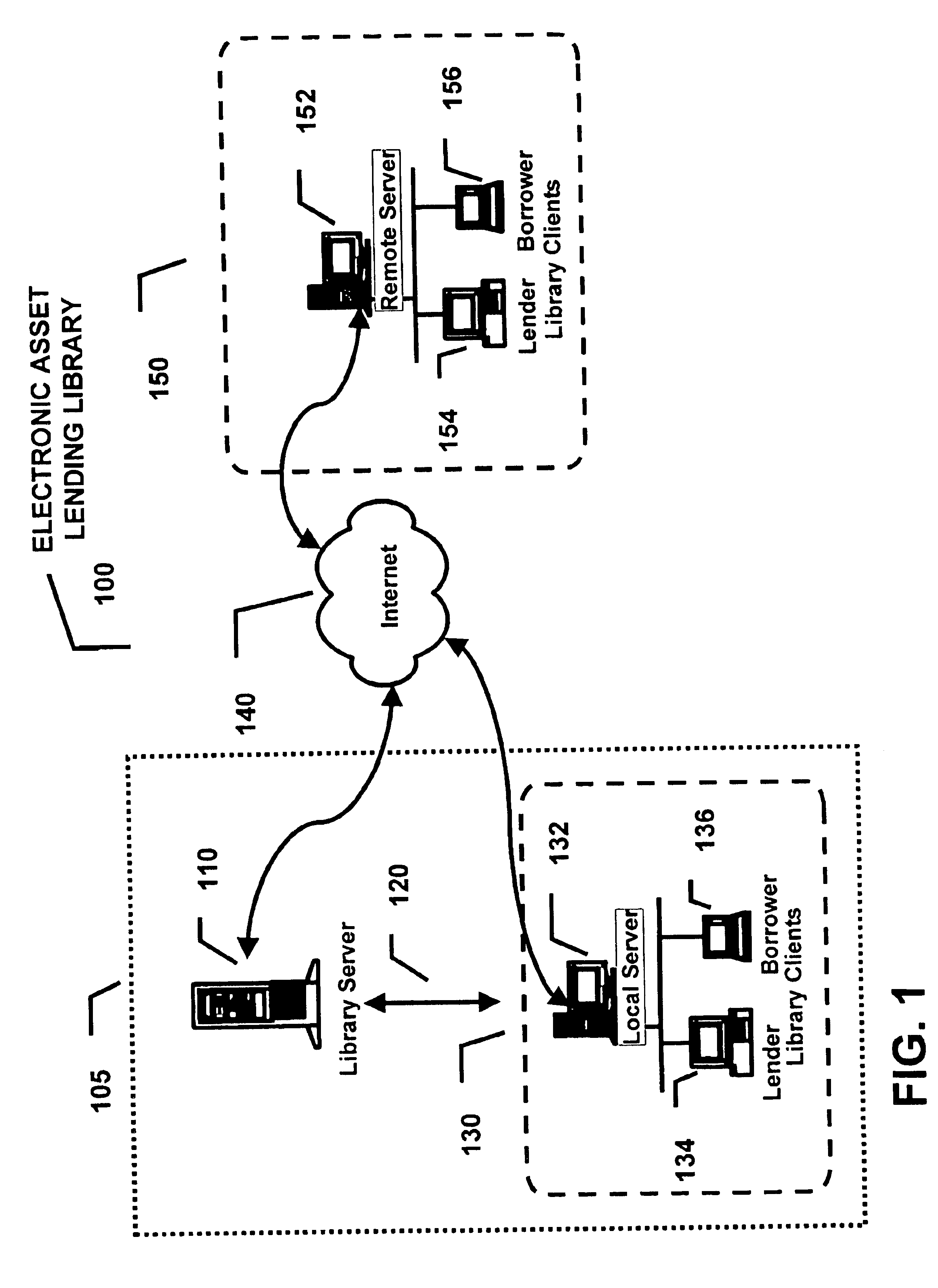
Electronic asset lending library method and apparatus
InactiveUS6901386B1Digital data processing detailsUser identity/authority verificationLibrary scienceLicense
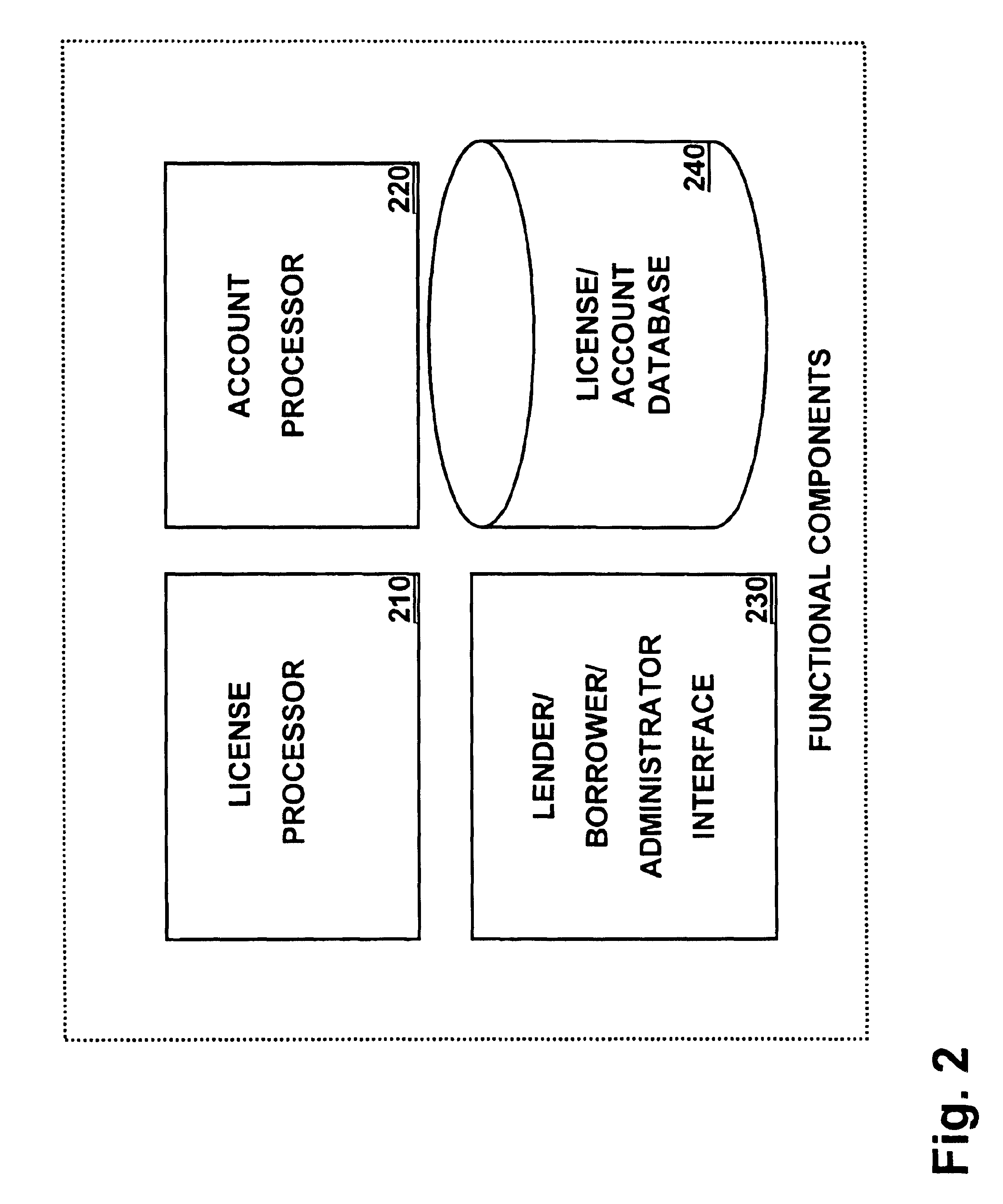
A electronic asset lending library method and apparatus enables the electronic management and reassignment of licenses for unused electronic assets installed on computers connected through a communications network. Licensing data for the unused electronic assets is released by the currently assigned owner and made available to one or more communities of users for display by product category, name, or keyword search. Once released, the lending library notifies the currently assigned owner to remove the unused electronic asset from their computer and transfers the licensing data to a library account. Eligible borrowers are permitted to request a re-assignment of an available released license for an unused electronic asset from a lending library account to their own account. Upon re-assignment the electronic asset lending library automatically notifies the borrower with instructions for the download and installation of the unused electronic asset to their computer. A borrower is determined to be eligible if she belongs to the same community as the currently assigned owner of the unused electronic asset and if she is on an access control list previously created for the unused electronic asset. Ineligible borrowers can request exception overrides to enable them to borrow a selected electronic asset. Licenses can be re-assigned at no cost or for a fee negotiated by the currently assigned owner.
Owner:INTEL CORP
System and method for controlling the downstream preservation and destruction of electronic mail
InactiveUS20050204008A1Simple interfaceMultiple digital computer combinationsData switching networksEmail addressPassword
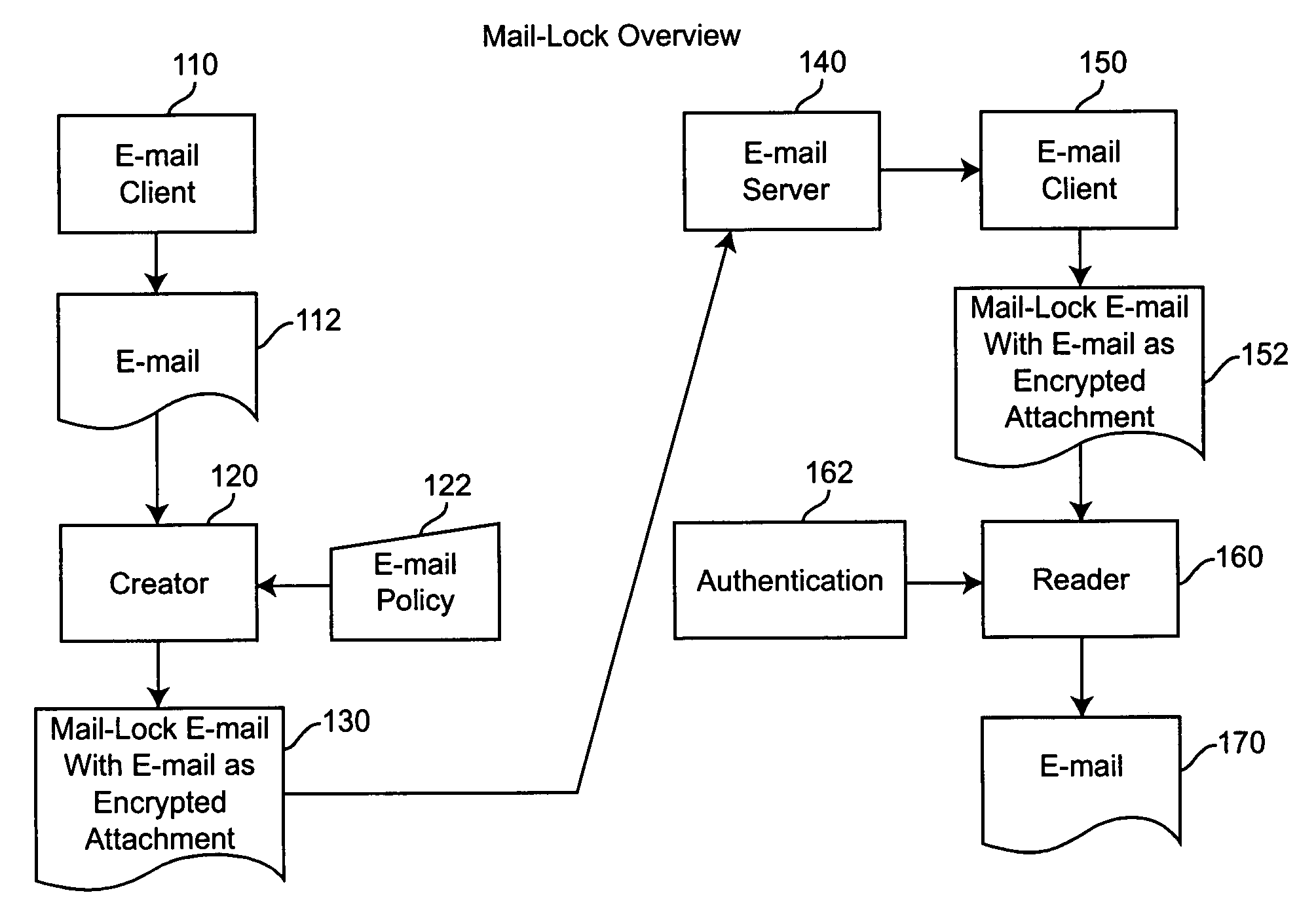
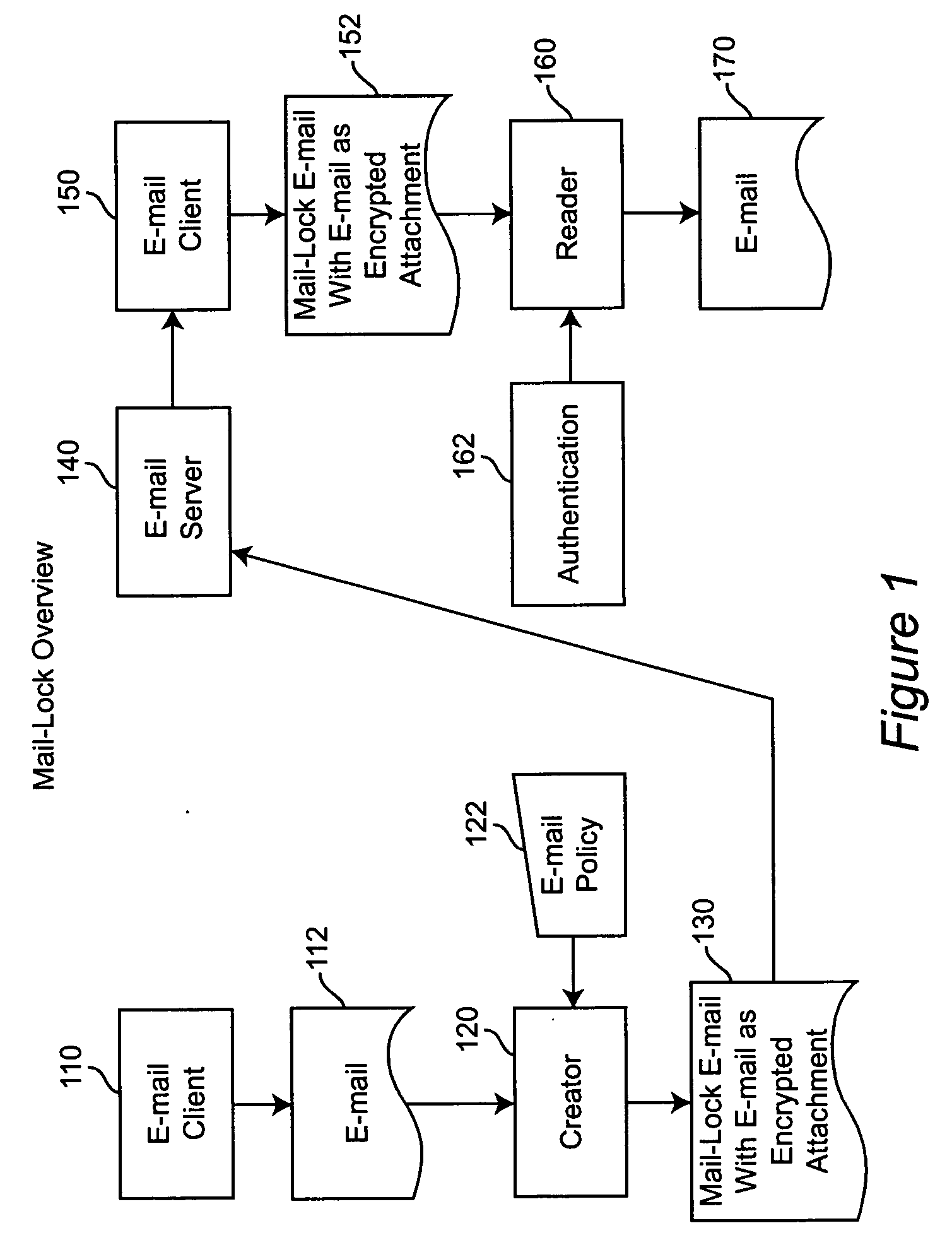
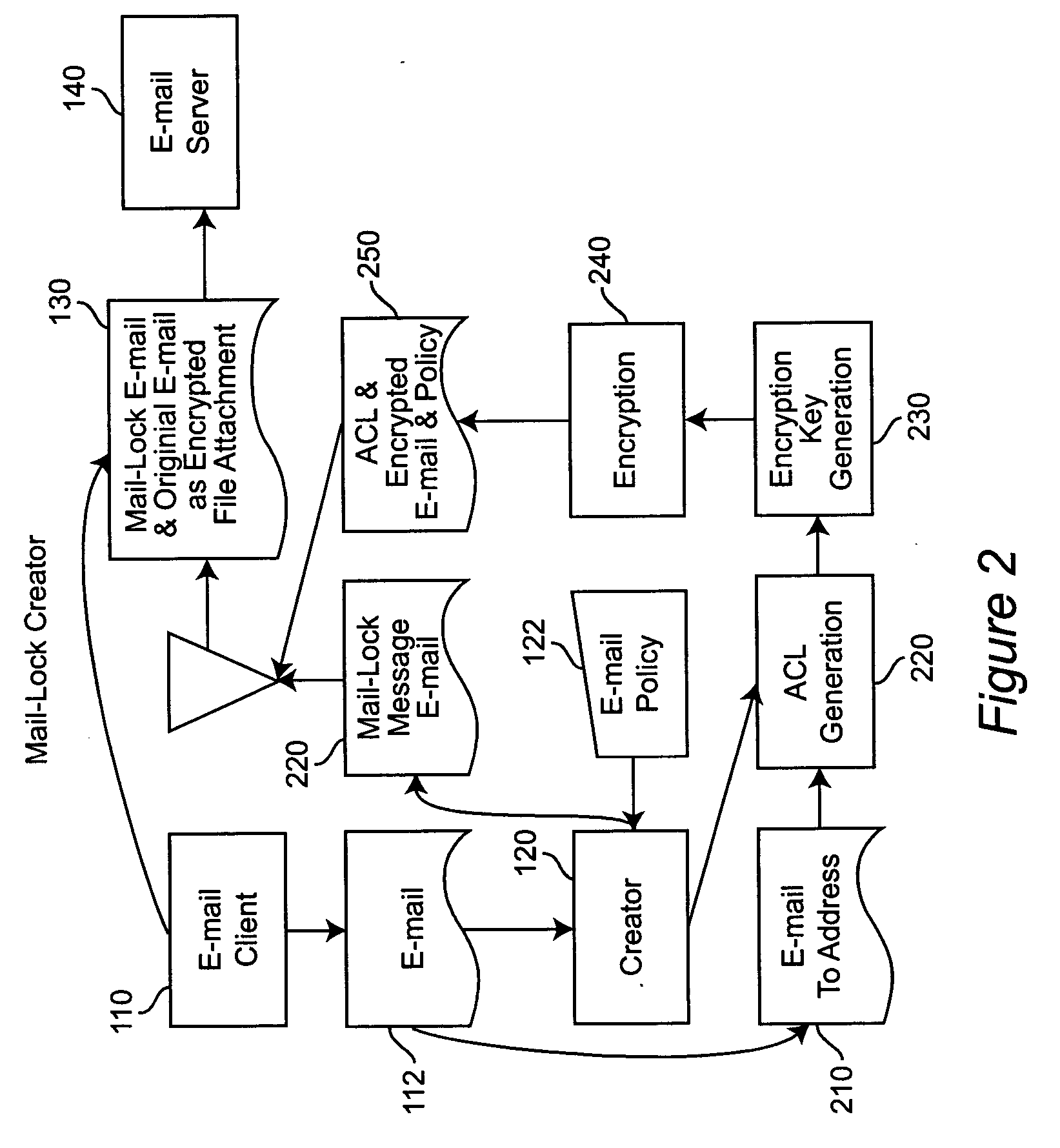
A system and method for controlling the downstream preservation and destruction of electronic mail by encrypting the electronic mail and limiting access to the encrypted file based on registration of recipient e-mail addresses, and detection and restriction of output functionality available to the recipient. The registration procedure limits access to recipients included on an access control list, who receive a pre-configured reader and then authenticate their e-mail address to the reader via a known SMTP Server. The sender of an e-mail is provided with a dialog for determining the limitations on access to the e-mail by the recipient: whether the e-mail is to be inaccessible after a certain period of time, whether a recipient may copy or print the e-mail and / or its attachments, or whether a password is required to read the e-mail. These limitations comprise an access control policy applicable to the e-mail, the pre-configured reader being adapted to decrypt the e-mail and apply the policy.
Owner:GRPWARE SOFTWARE SOLUTIONS
System and method for user access control to content in a network
InactiveUS20060184530A1Simple methodData taking preventionUser identity/authority verificationHome rangeWorld Wide Web
A method of unifying the different, device-specific and platform-specific access control lists (ACL) for different users and user groups in a home network. The home network has networked heterogeneous devices and hosting where a user is presented with a consistent, single view of ACL on home-wide users and user groups. Users in the home network, therefore, do not need to control ACL for device-specific users and user groups on each individual device. Instead, a user controls the home-wide ACL for home-wide users and user groups. The changes to home-wide ACL for home-wide users and user groups are propagated to individual devices. Further, changes on individual devices can be made to device-specific ACL for device-specific users and user groups. Such changes are subsequently propagated to the home-wide ACL for home-wide users and user groups.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for using ternary and binary content-addressable memory stages to classify packets
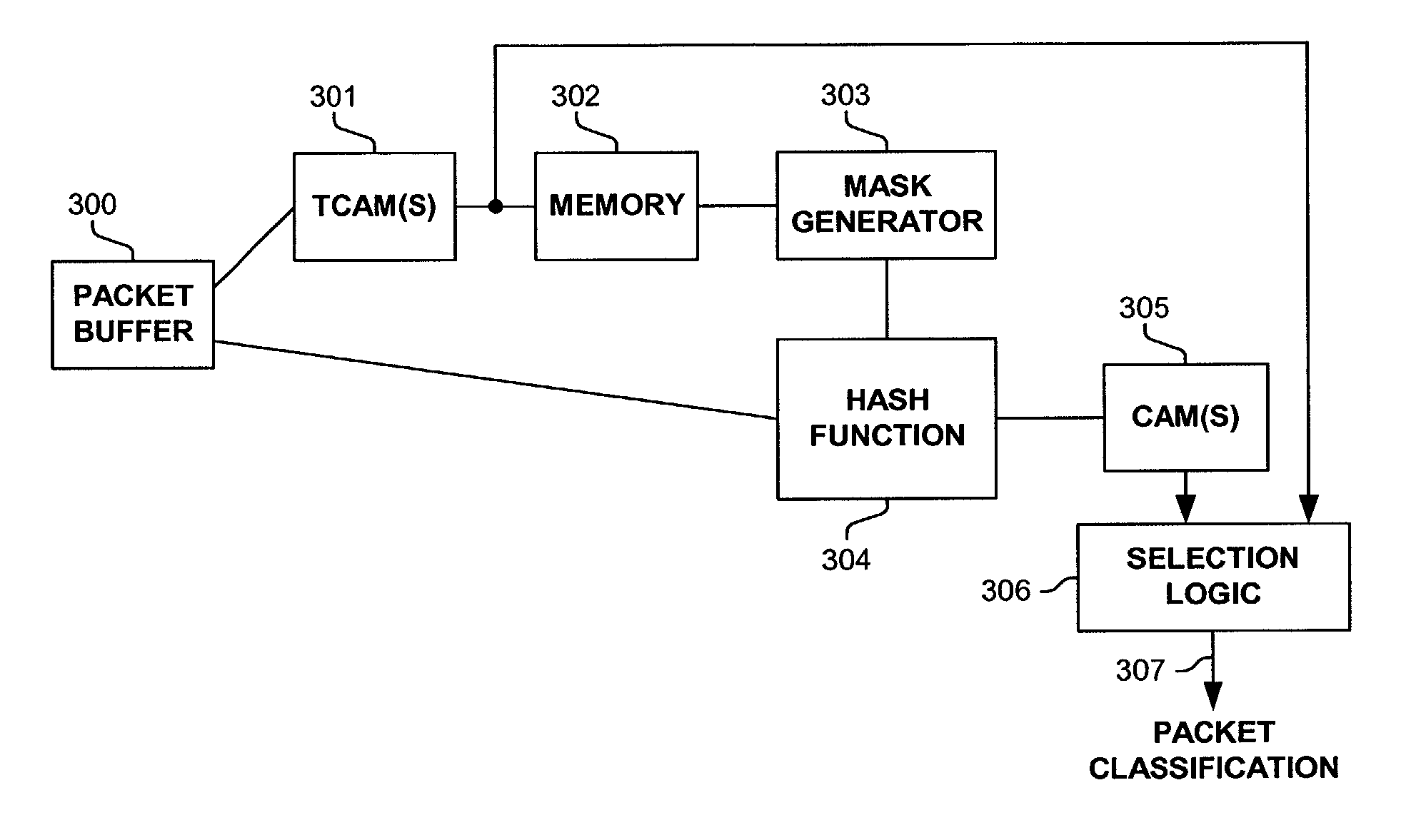
InactiveUS7002965B1Data processing applicationsDigital computer detailsQuality of serviceVirtual LAN
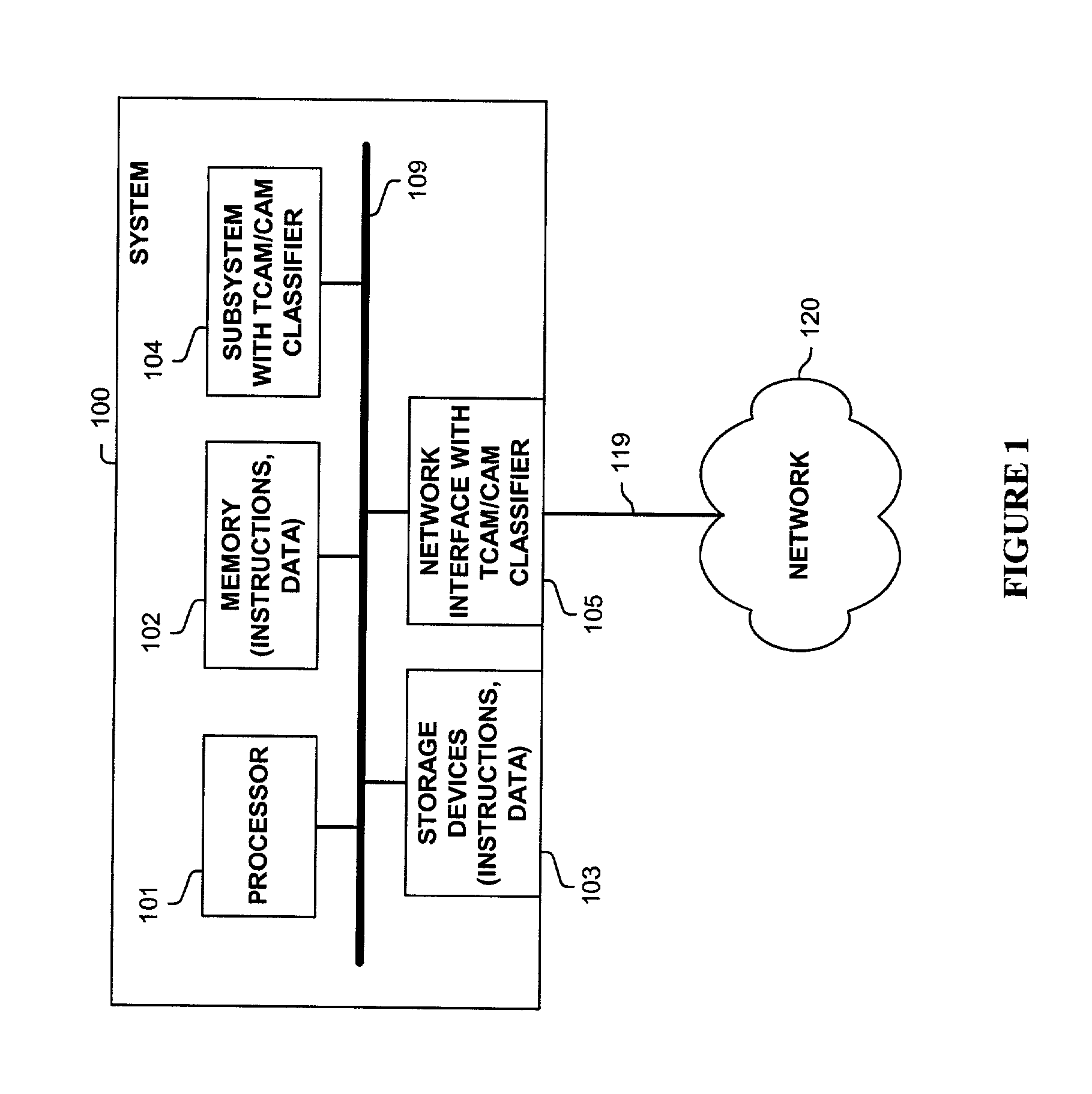
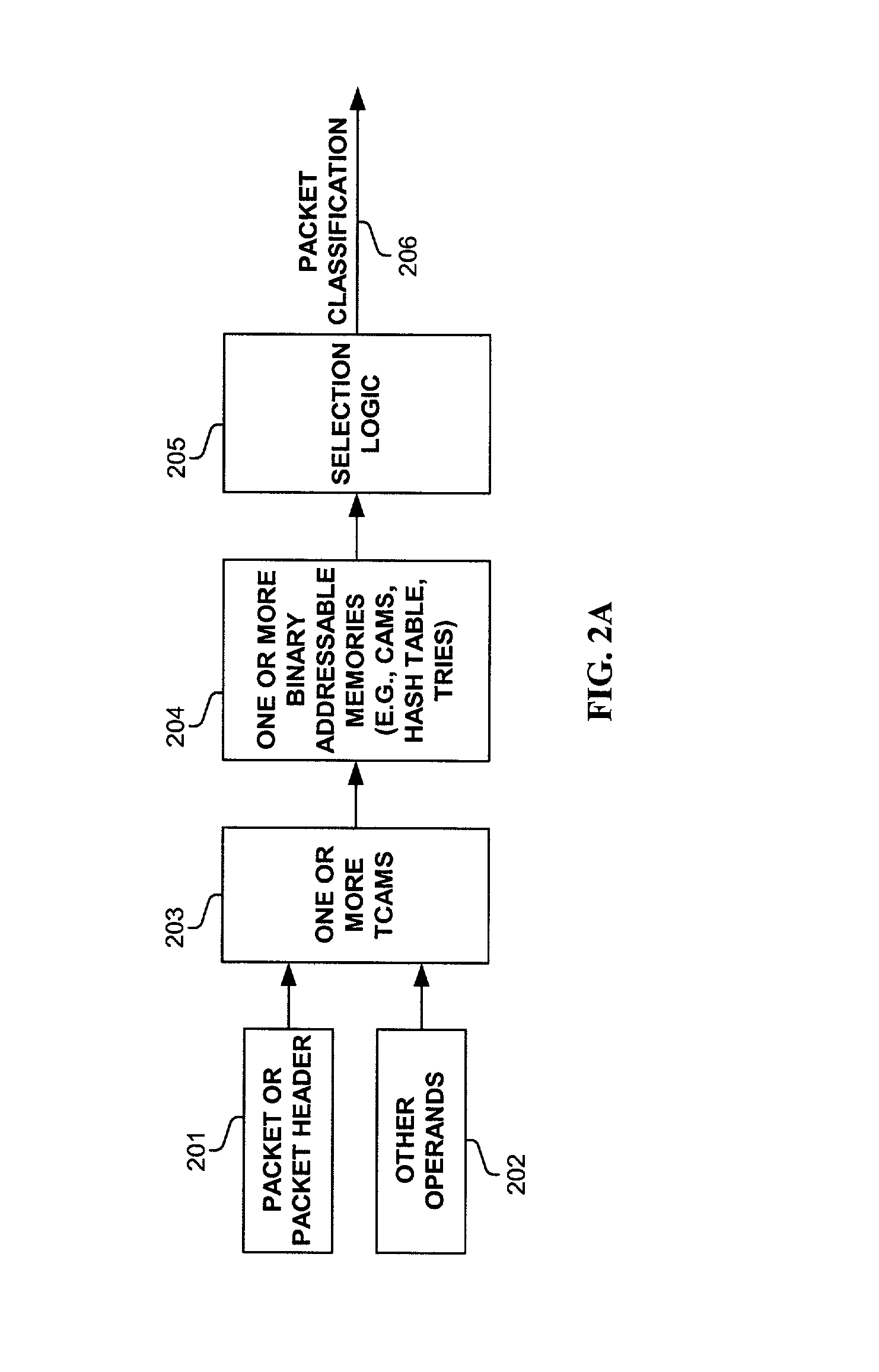
Methods and apparatus are disclosed herein for classifying packets using ternary and binary content-addressable memory stages to classify packets. One such system uses a stage of one or more TCAMS followed by a second stage one or more CAMS (or alternatively some other binary associative memories such as hash tables or TRIEs) to classify a packet. One exemplary system includes TCAMs for handling input and output classification and a forwarding CAM to classify packets for Internet Protocol (IP) forwarding decisions on a flow label. This input and output classification may include, but is not limited to routing, access control lists (ACLs), quality of service (QoS), network address translation (NAT), encryption, etc. These IP forwarding decisions may include, but are not limited to IP source and destination addresses, protocol type, flags and layer 4 source and destination ports, a virtual local area network (VLAN) id and / or other fields.
Owner:CISCO TECH INC
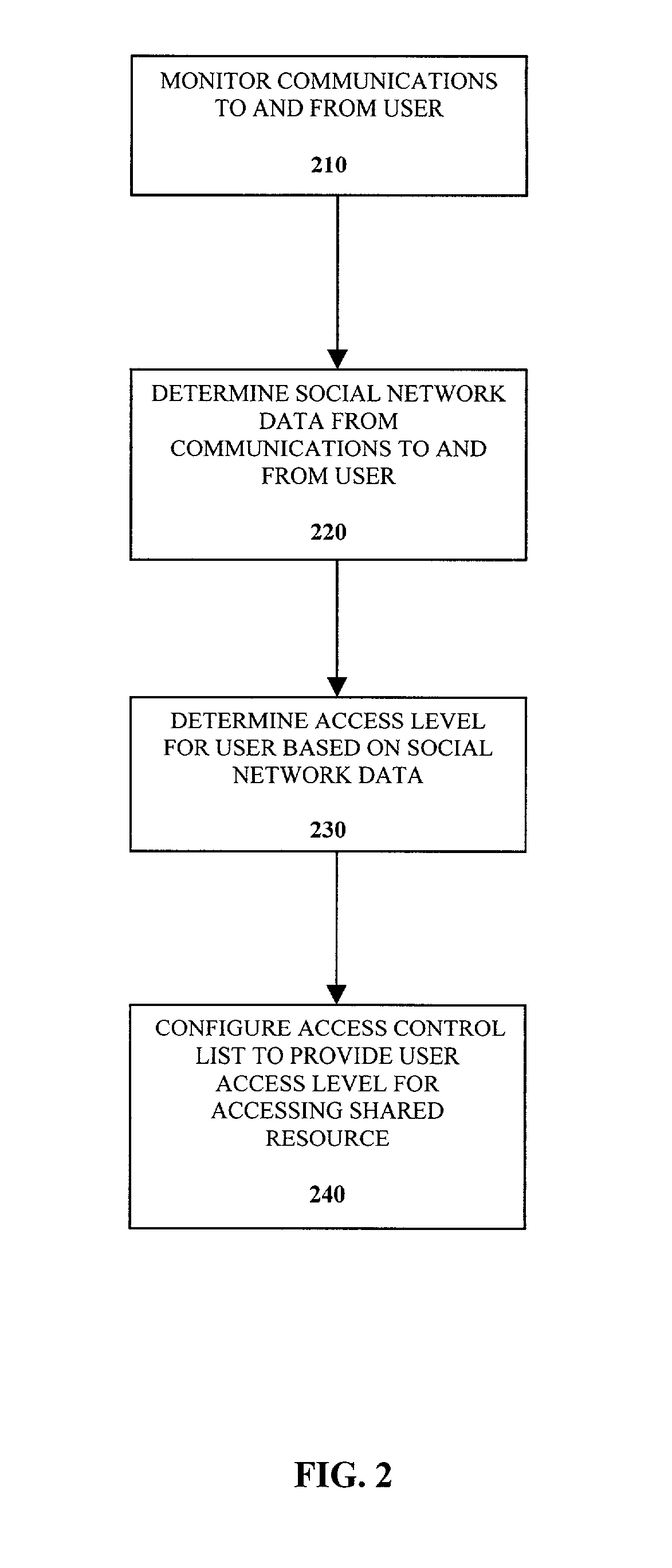
Control of access control lists based on social networks
InactiveUS7467212B2Specific access rightsDigital data processing detailsVLAN access control listSocial web
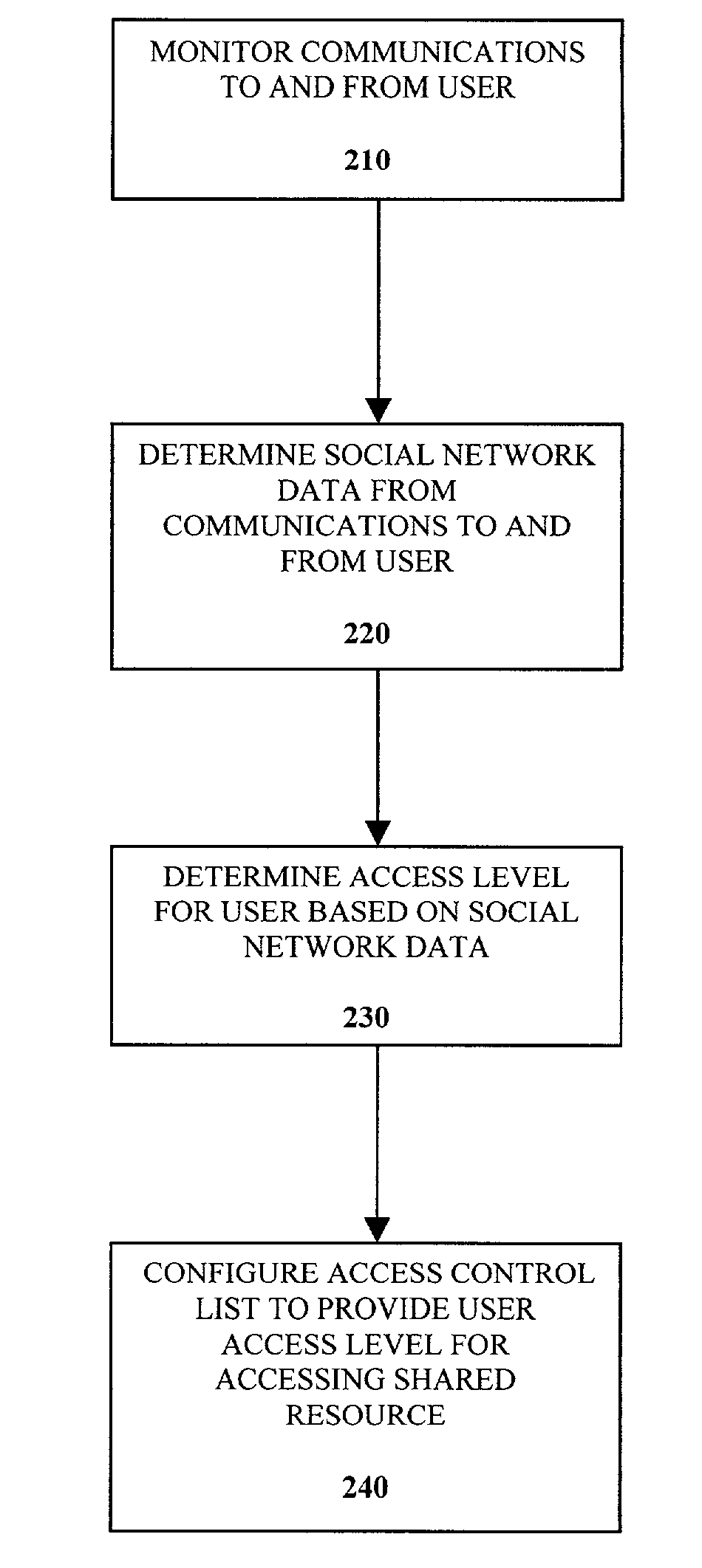
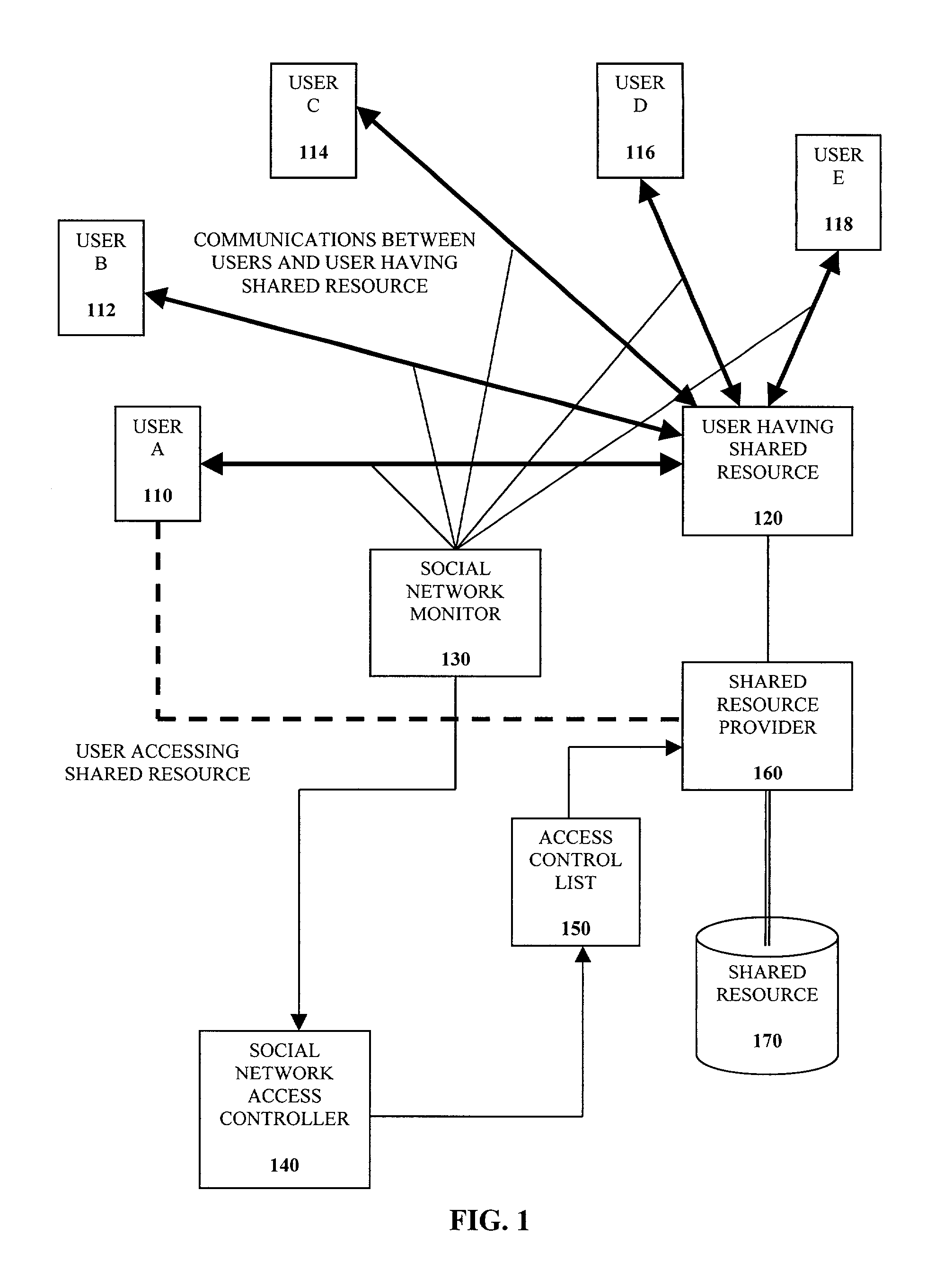
A method of controlling a social network access control list (ACL) for a shared resource includes monitoring communications to and from a user. Social network data from the communications to and from the user is determined. An access level for the user is determined based on the social network data. The access control list is configured to provide the user the access level determined for accessing the shared resource.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com