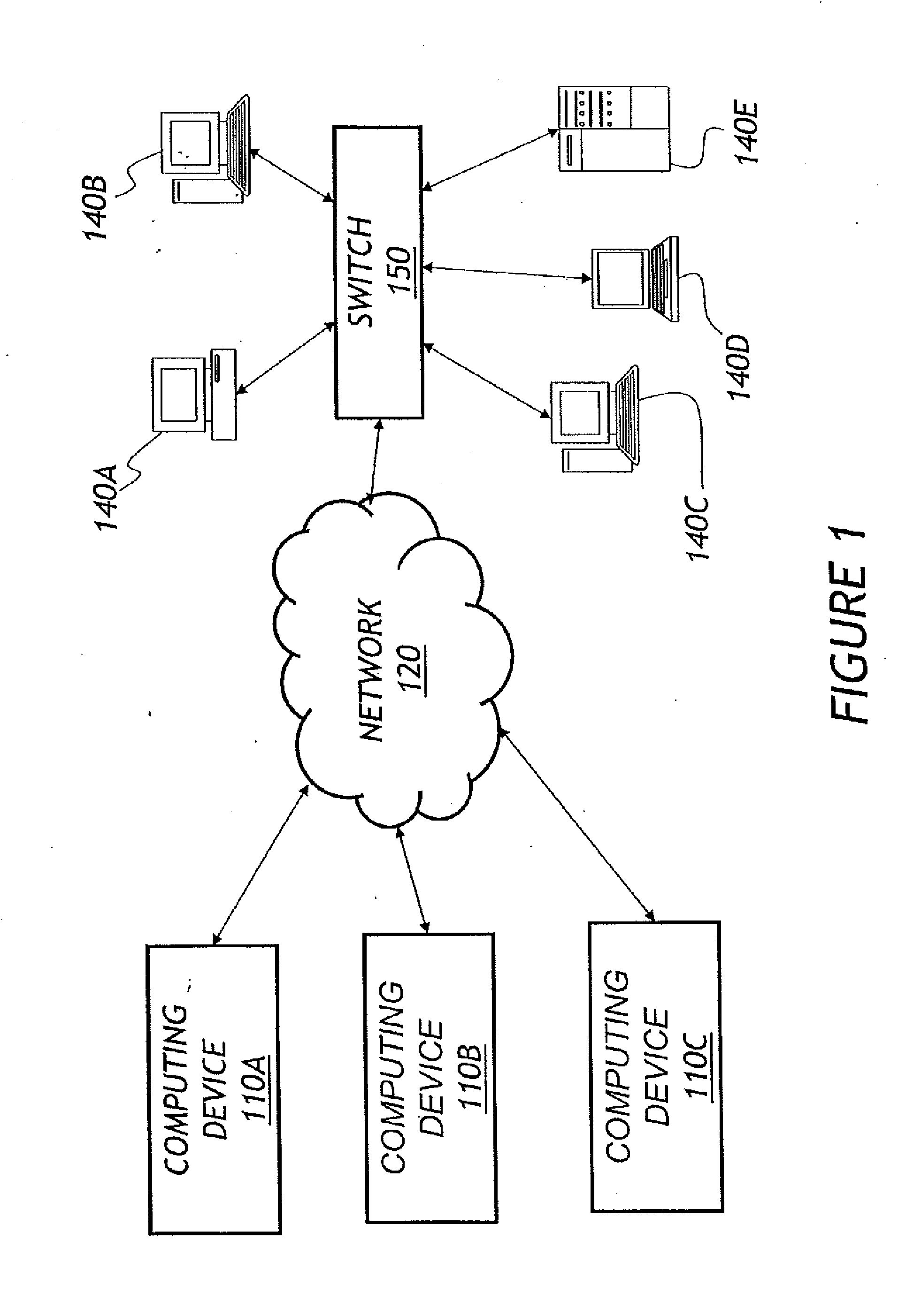
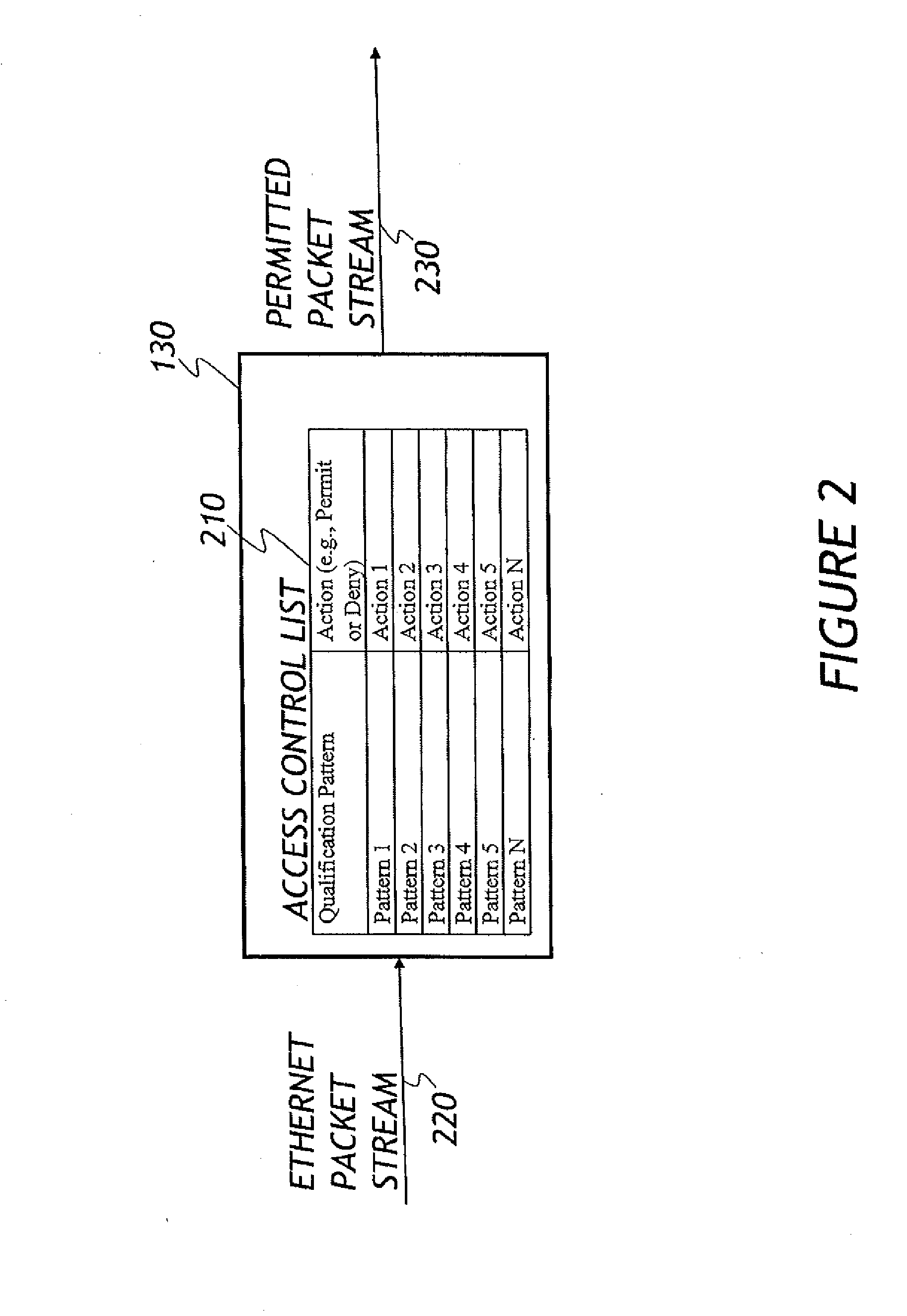
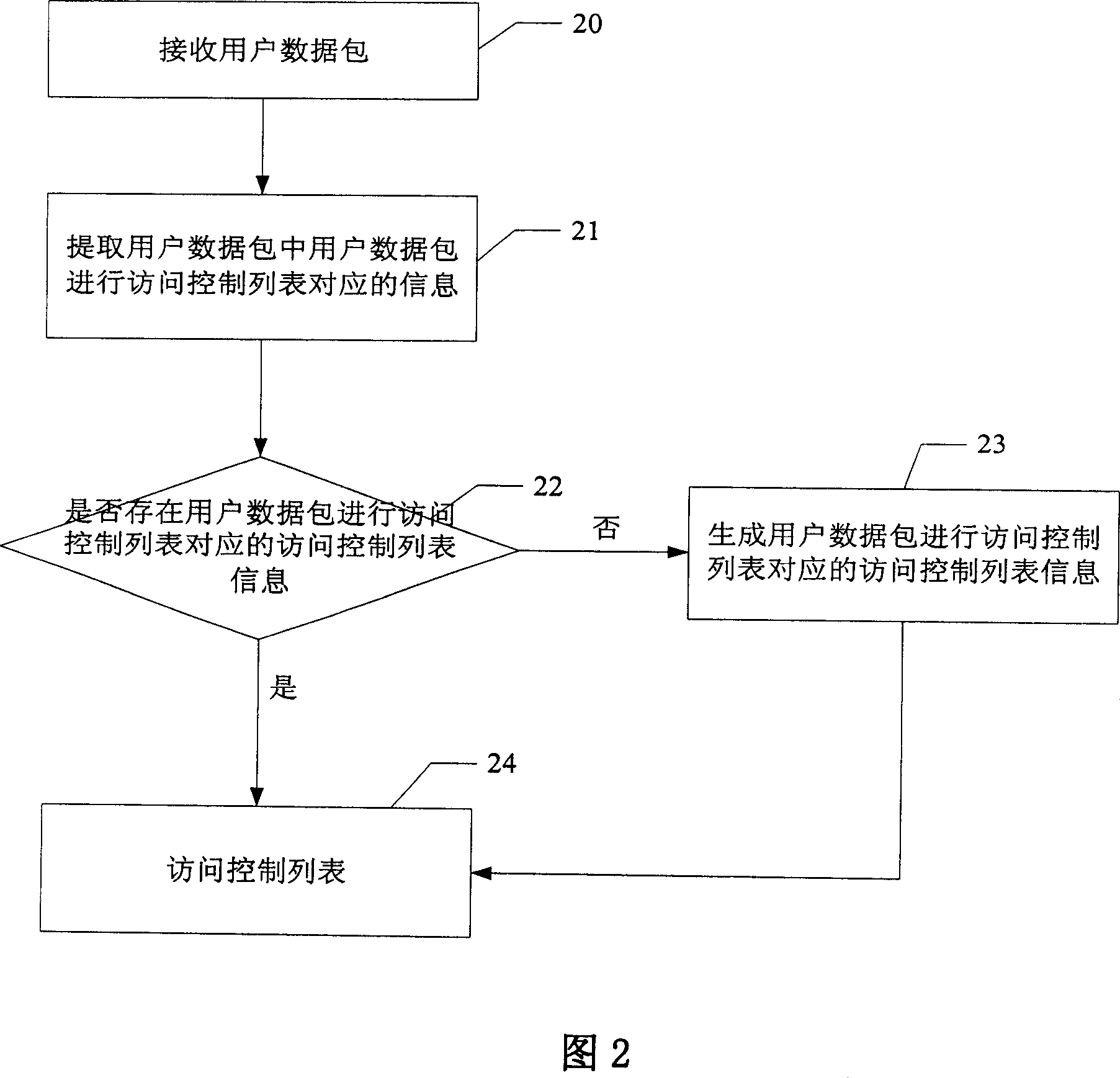
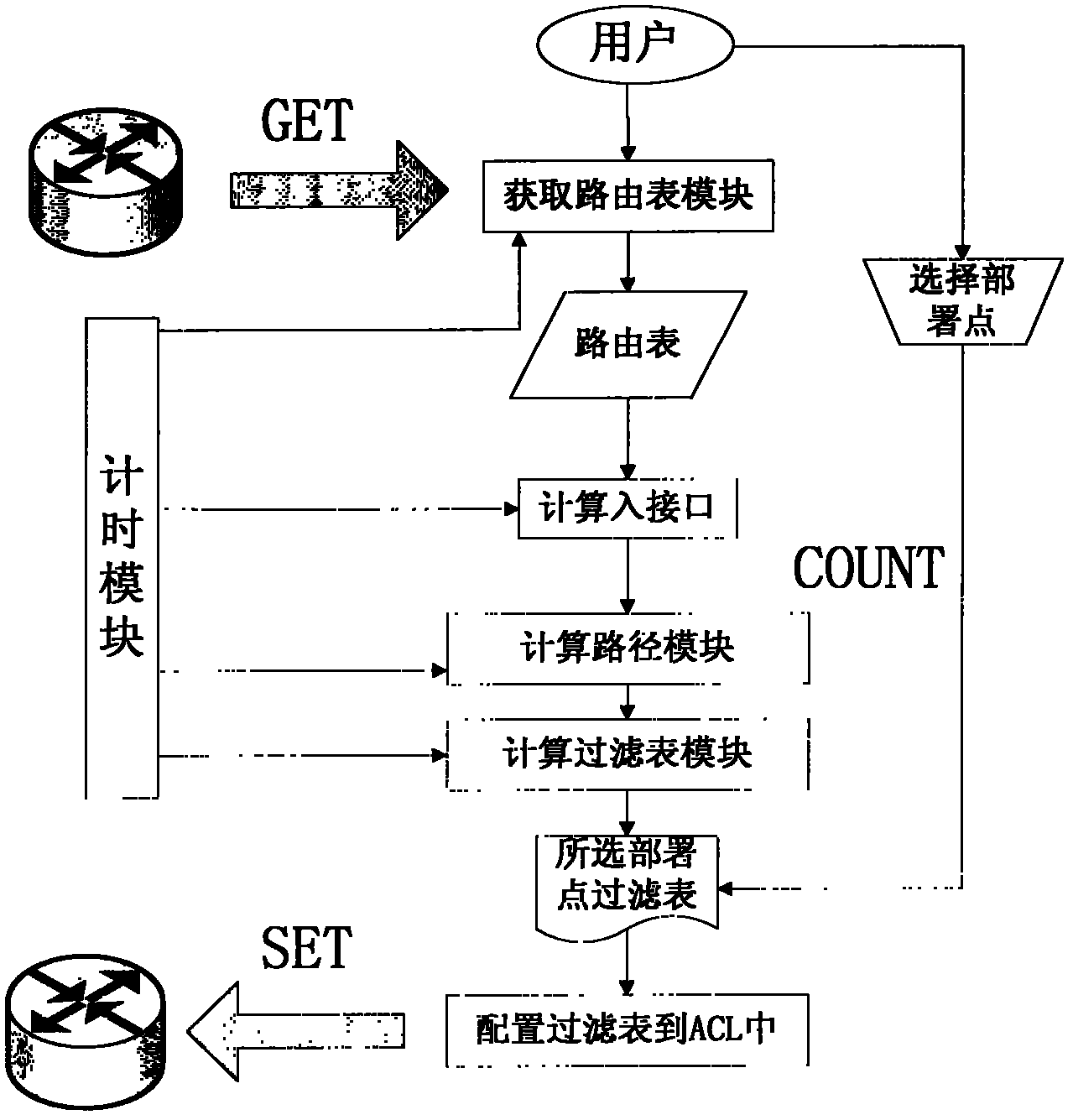
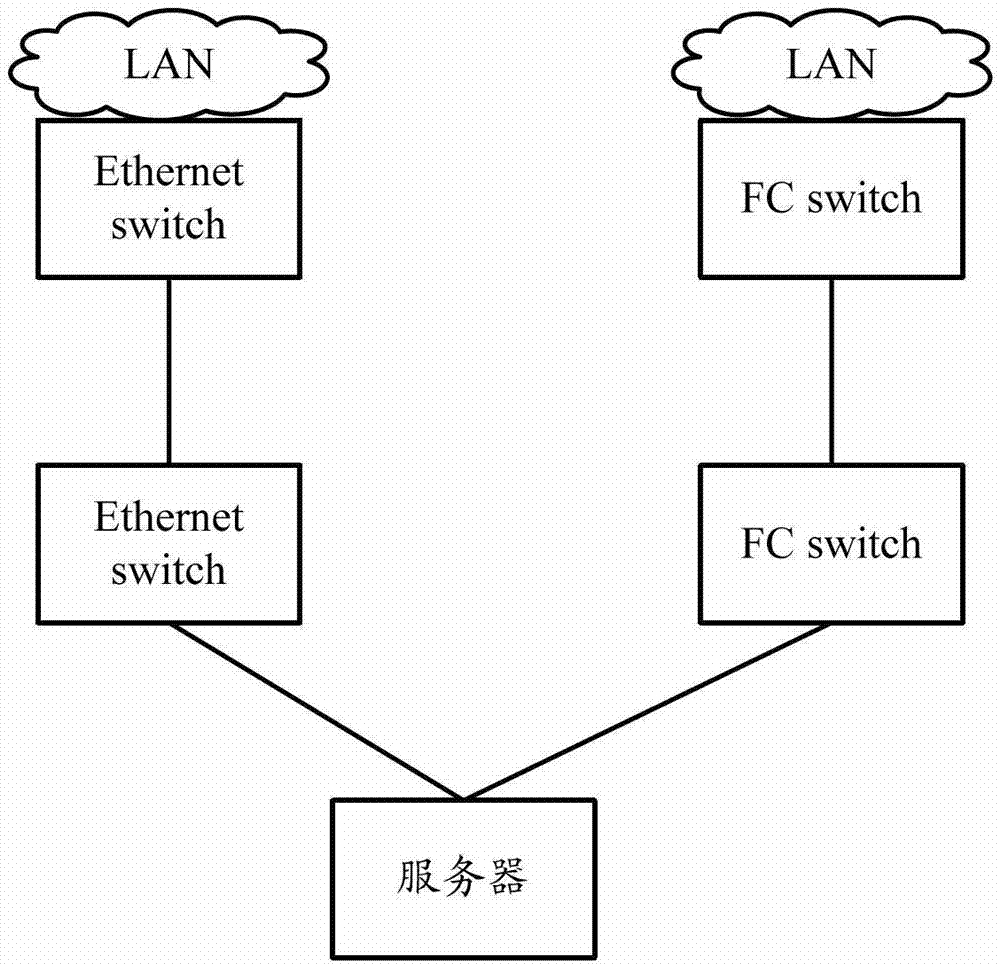
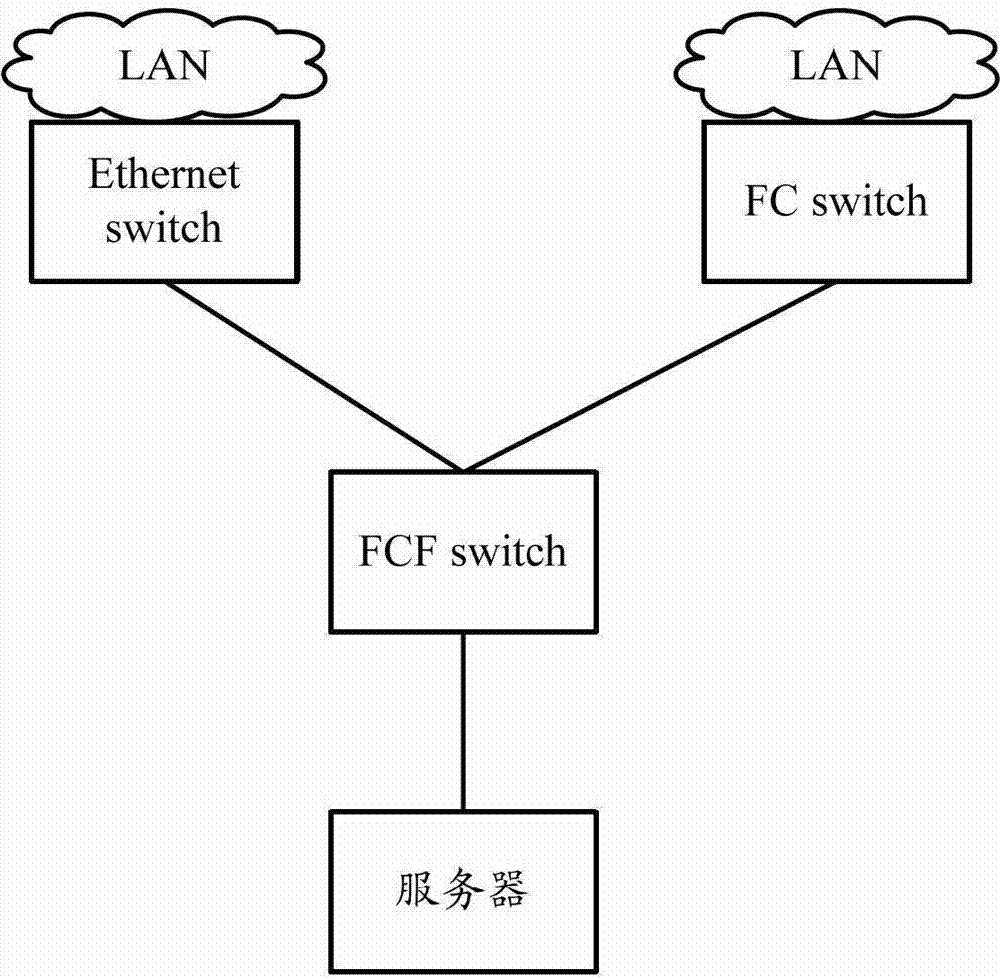
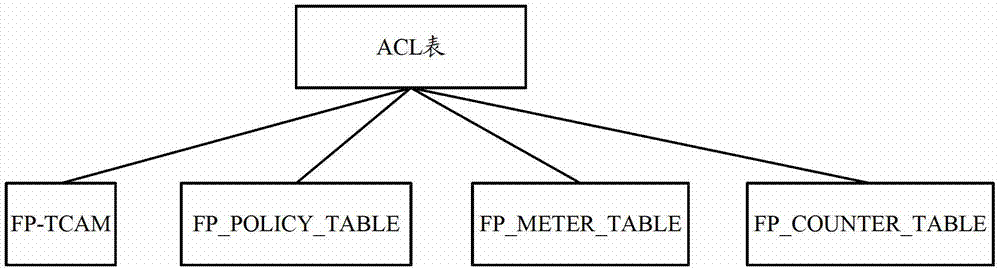
Patents
Literature
116 results about "VLAN access control list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
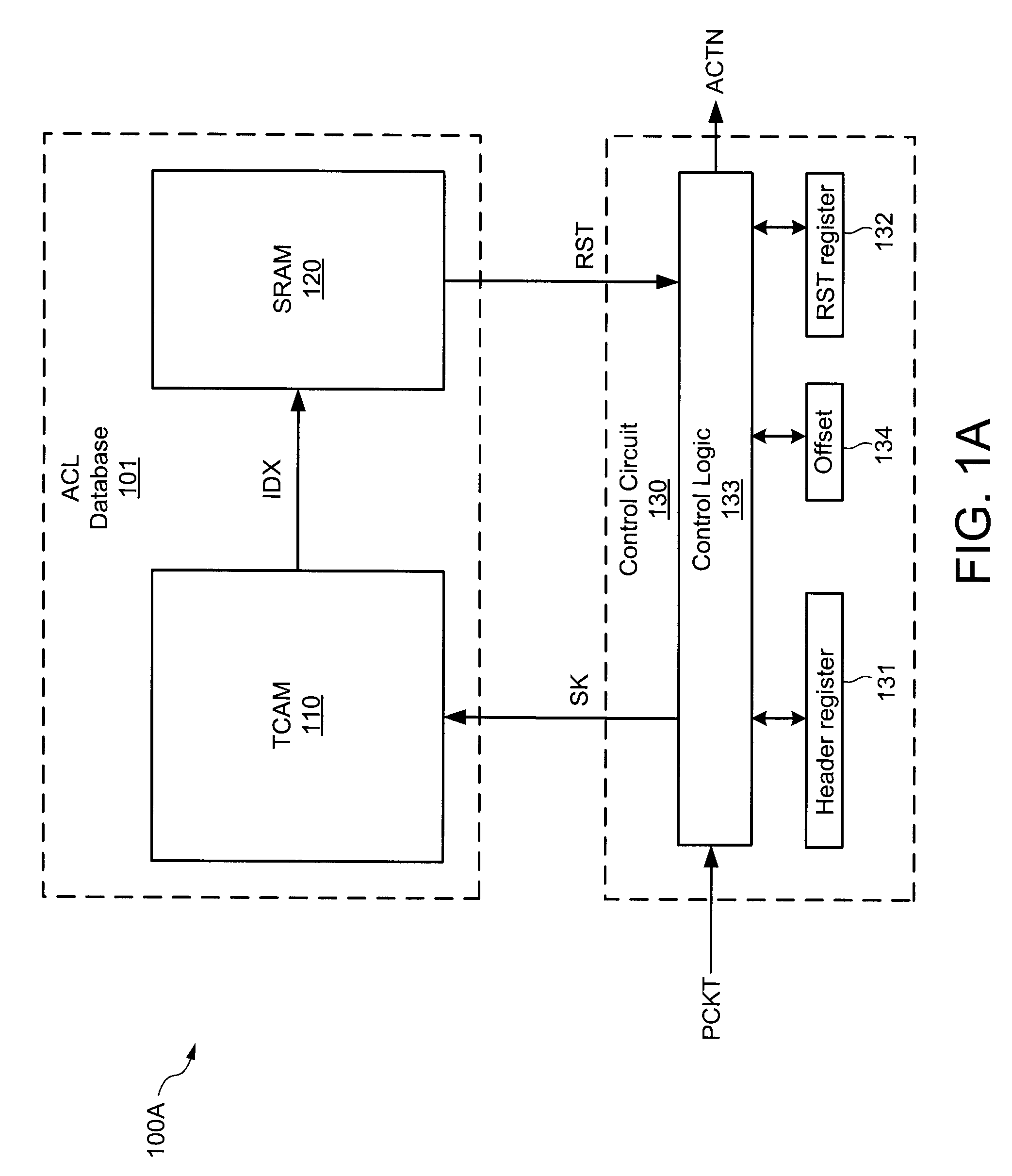
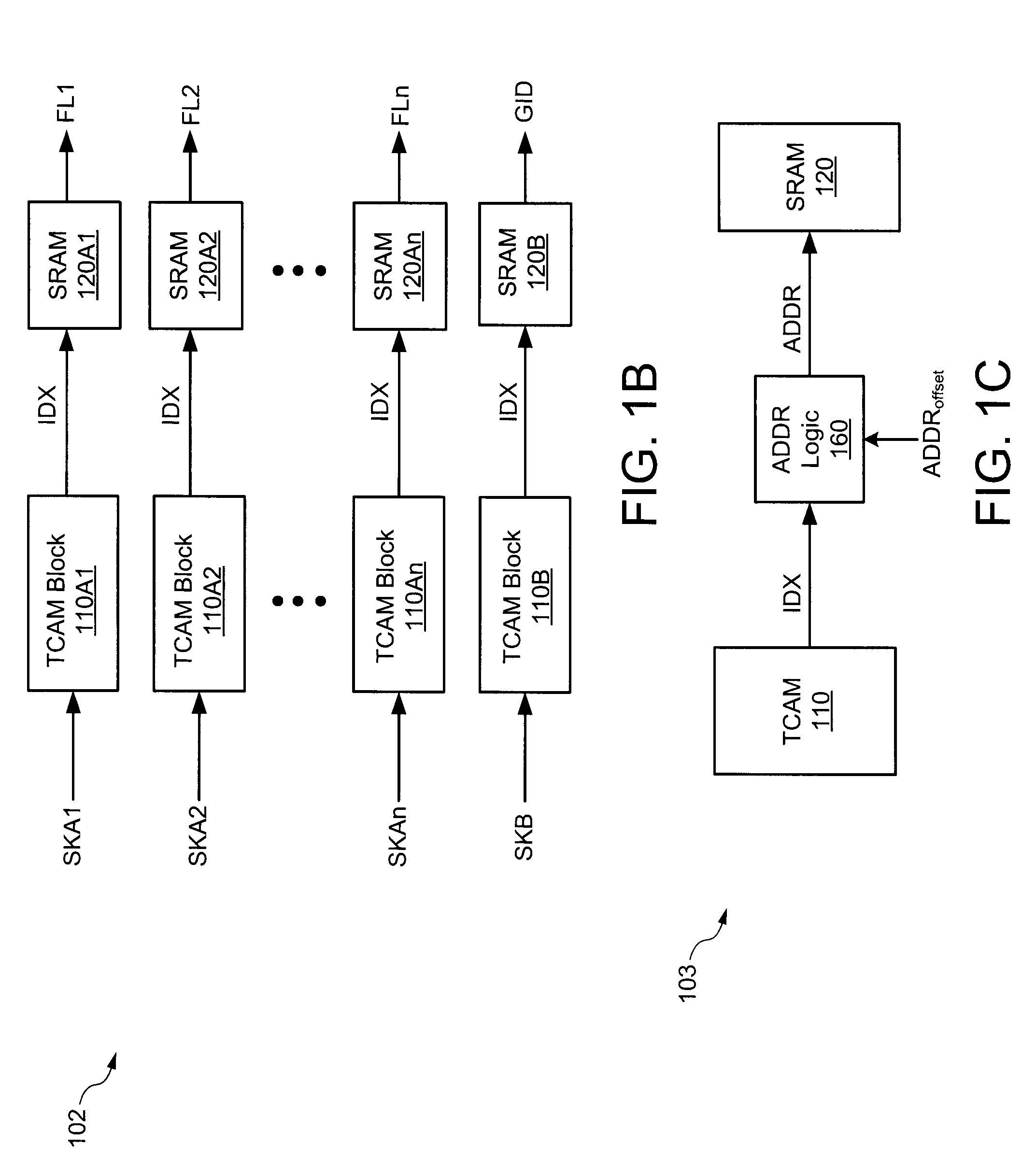
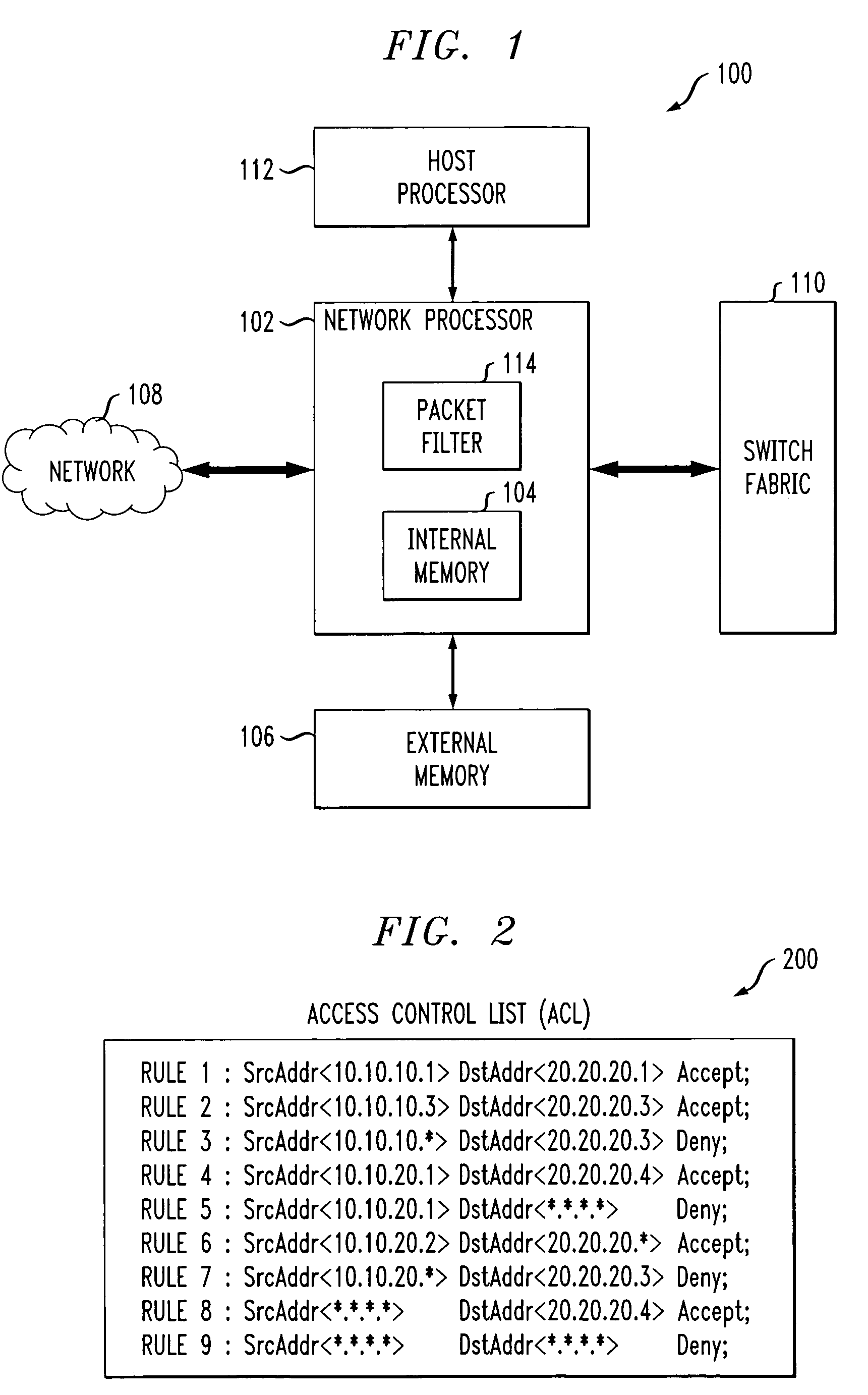
A VLAN access control list (VACL) provides access control for all packets that are bridged within a VLAN or that are routed into or out of a VLAN. Unlike regular Cisco IOS access control lists that are configured on router interfaces and applied on routed packets only, VACLs apply to all packets. The technology was developed by Cisco on the Catalyst 6500 Series switch platform.
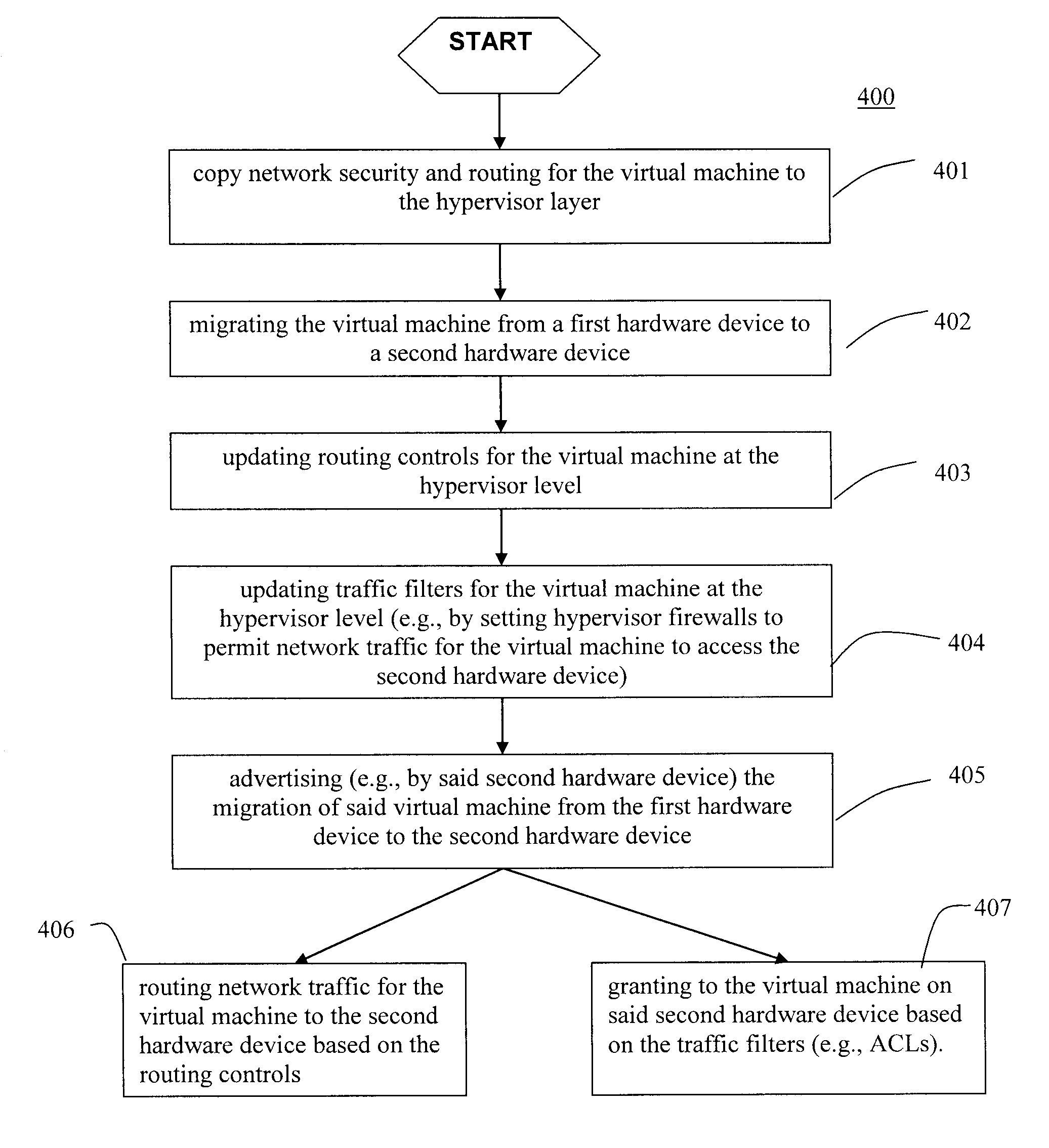
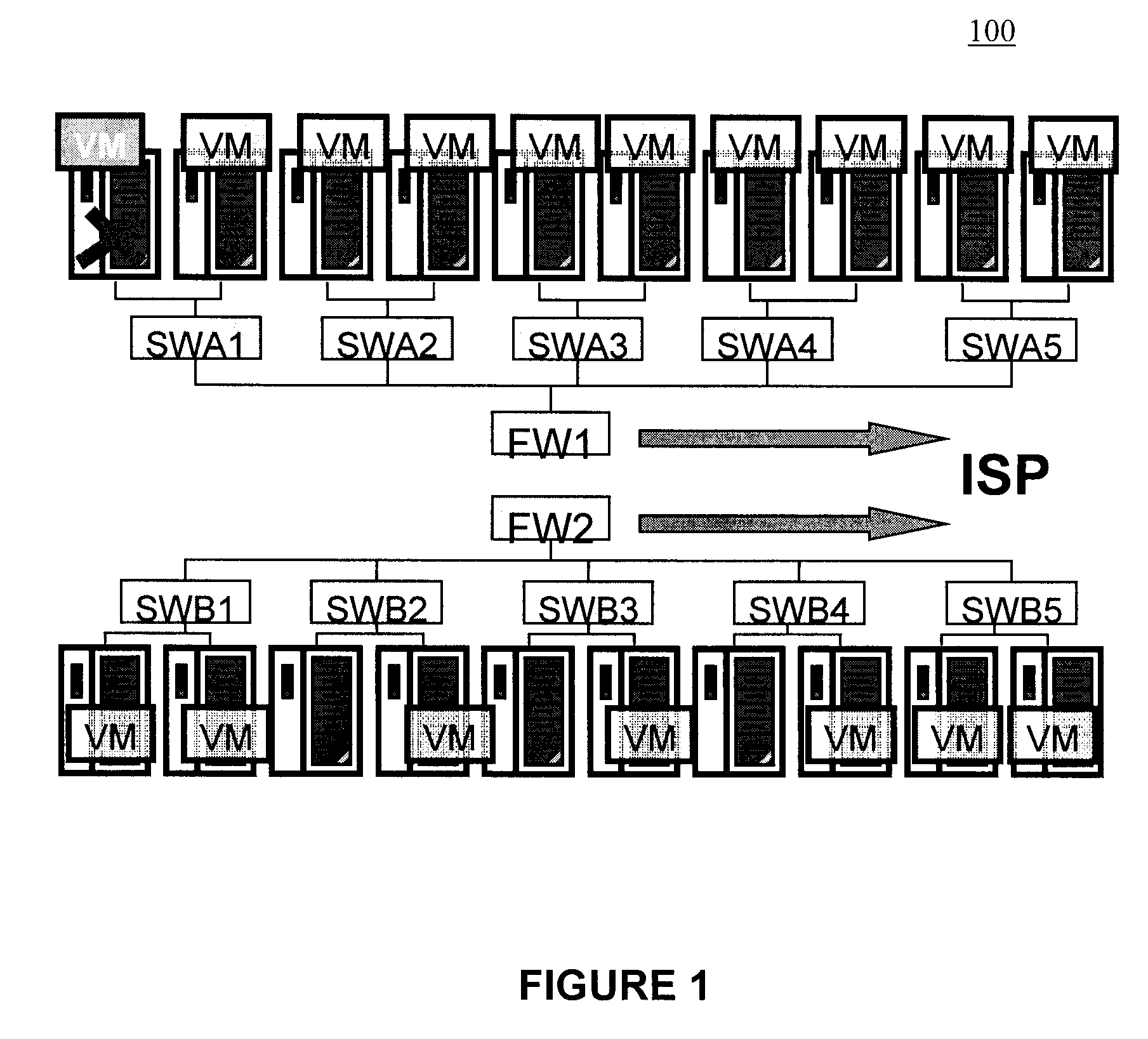
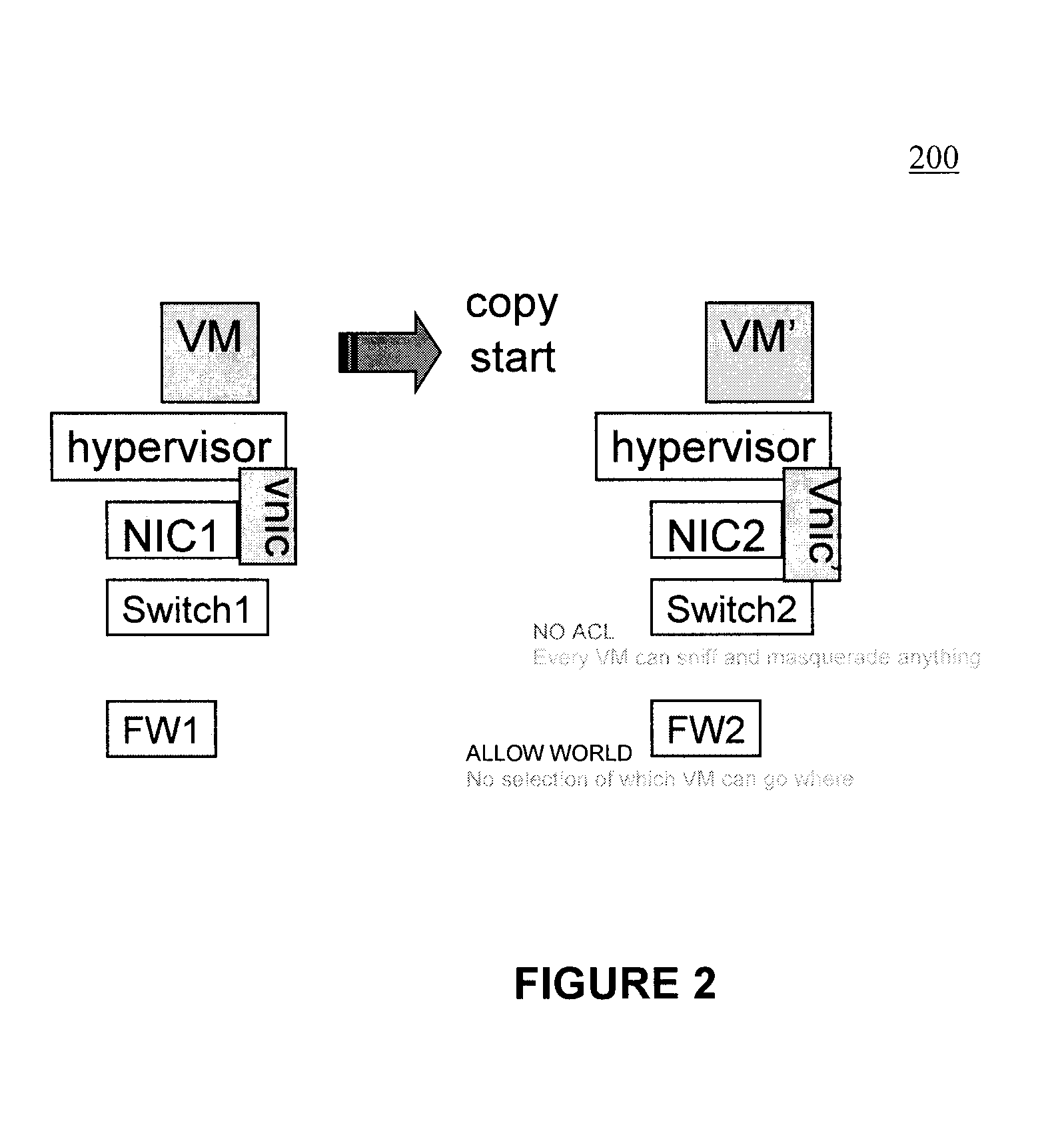
Moveable access control list (ACL) mechanisms for hypervisors and virtual machines and virtual port firewalls
ActiveUS20080163207A1Efficient responseRapid deploymentSemiconductor electrostatic transducersMicrophone structural associationVLAN access control listAccess control list
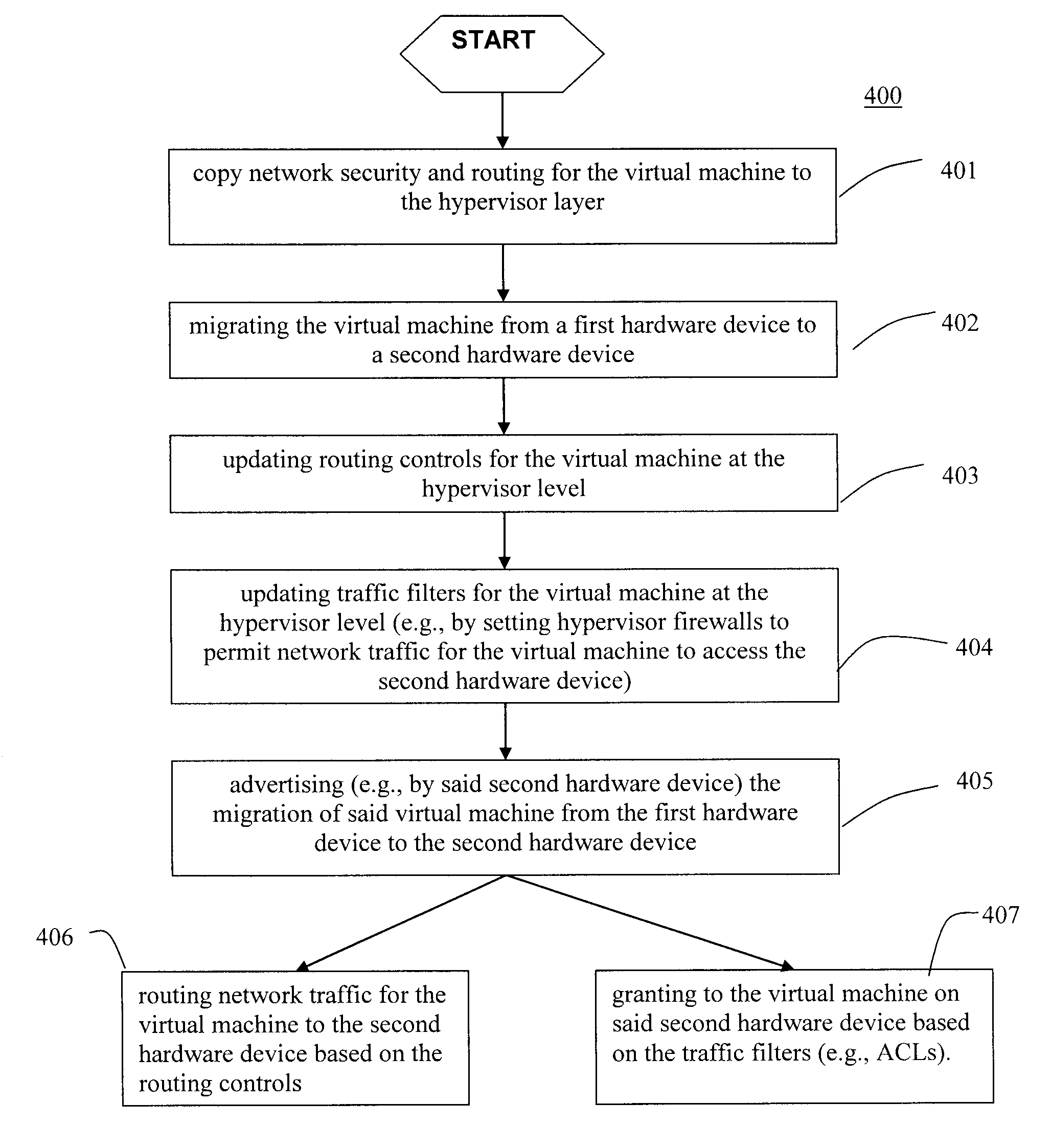
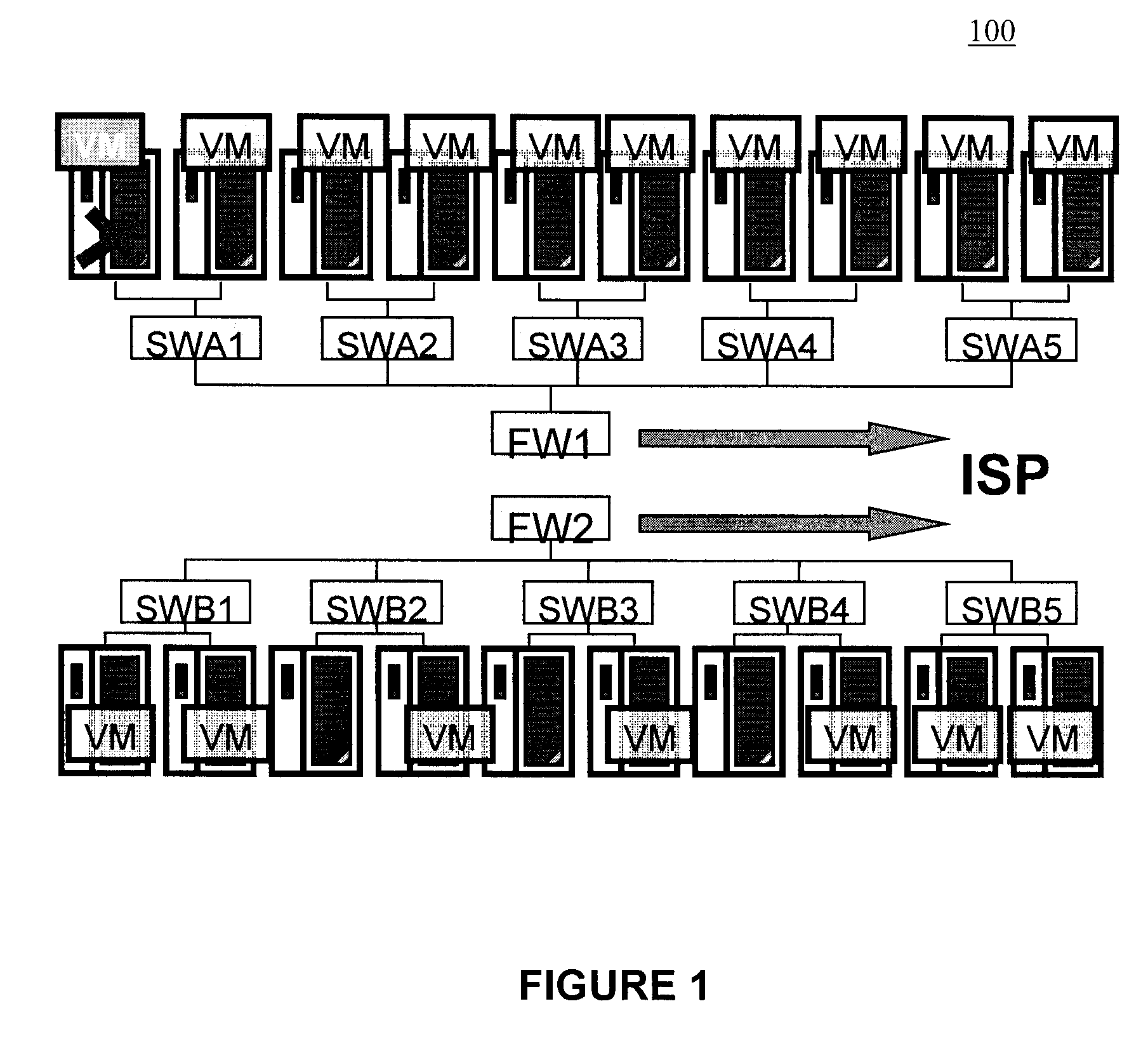
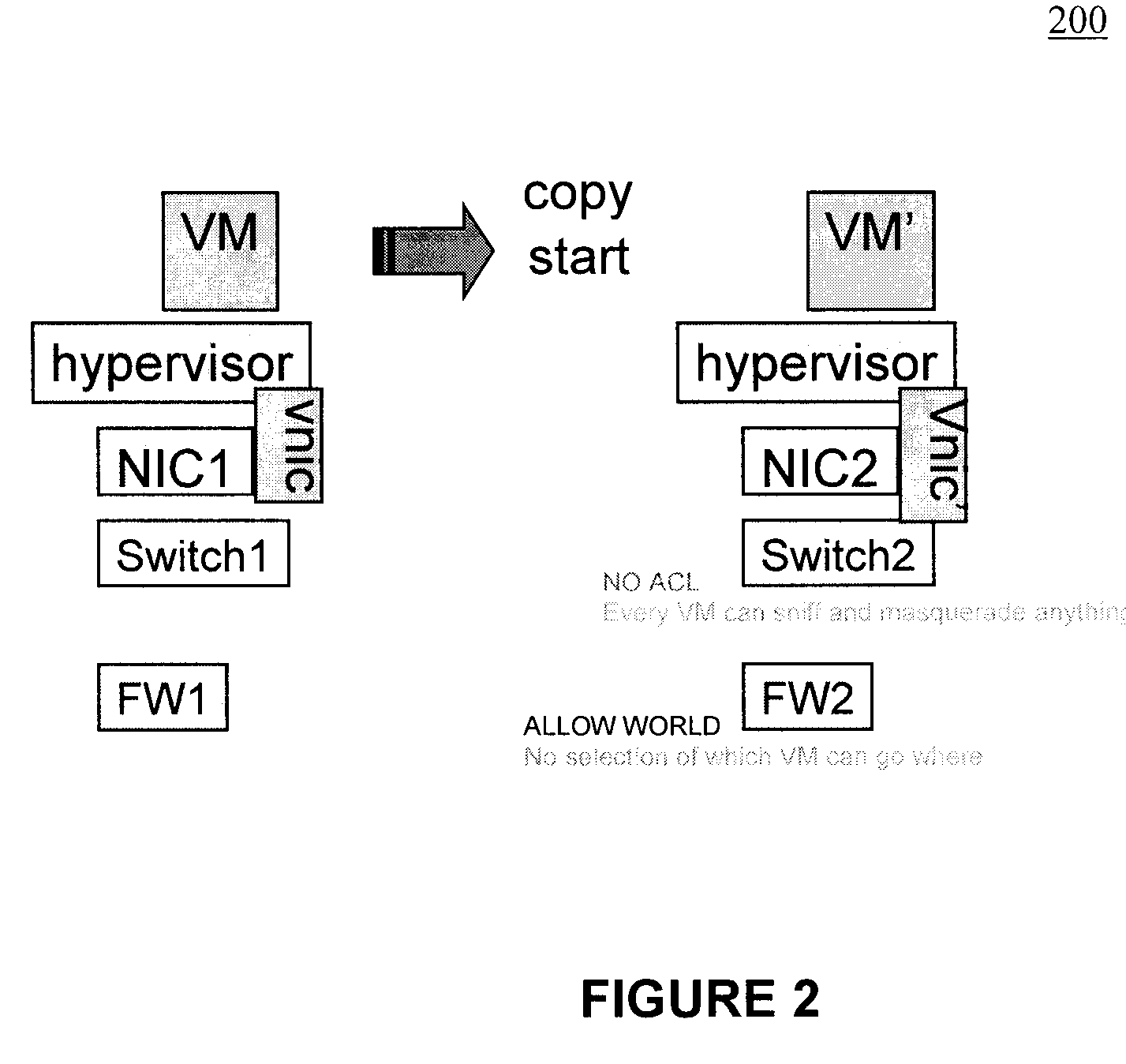
A method (and system) which provides virtual machine migration with filtered network connectivity and control of network security of a virtual machine by enforcing network security and routing at a hypervisor layer at which the virtual machine partition is executed, and which is independent of guest operating systems.
Owner:DAEDALUS BLUE LLC
Data storage incorporating cryptographically enhanced data protection
ActiveUS8856530B2Key distribution for secure communicationUser identity/authority verificationVLAN access control listUser identifier
Various exemplary embodiments relate to a system for storing encrypted data and providing access to a group of users. The system may include: a record of user accounts including: a user identifier and a public encryption key; an access control list (ACL) defining an access control policy including: permissions defining access to data objects associated with the ACL and an ACL key list including copies of a an ACL key encrypted with the public keys of the users; a user-data storage medium including: encrypted user data, stored as a plurality of data objects, each object associated with an ACL and encrypted with the ACL key, and meta-data; and an access controller configured to: receive a request for a data object, and send a copy of the data object and the ACL key encrypted with the public key of the user if the user has permission to access the data object.
Owner:ONYX PRIVACY
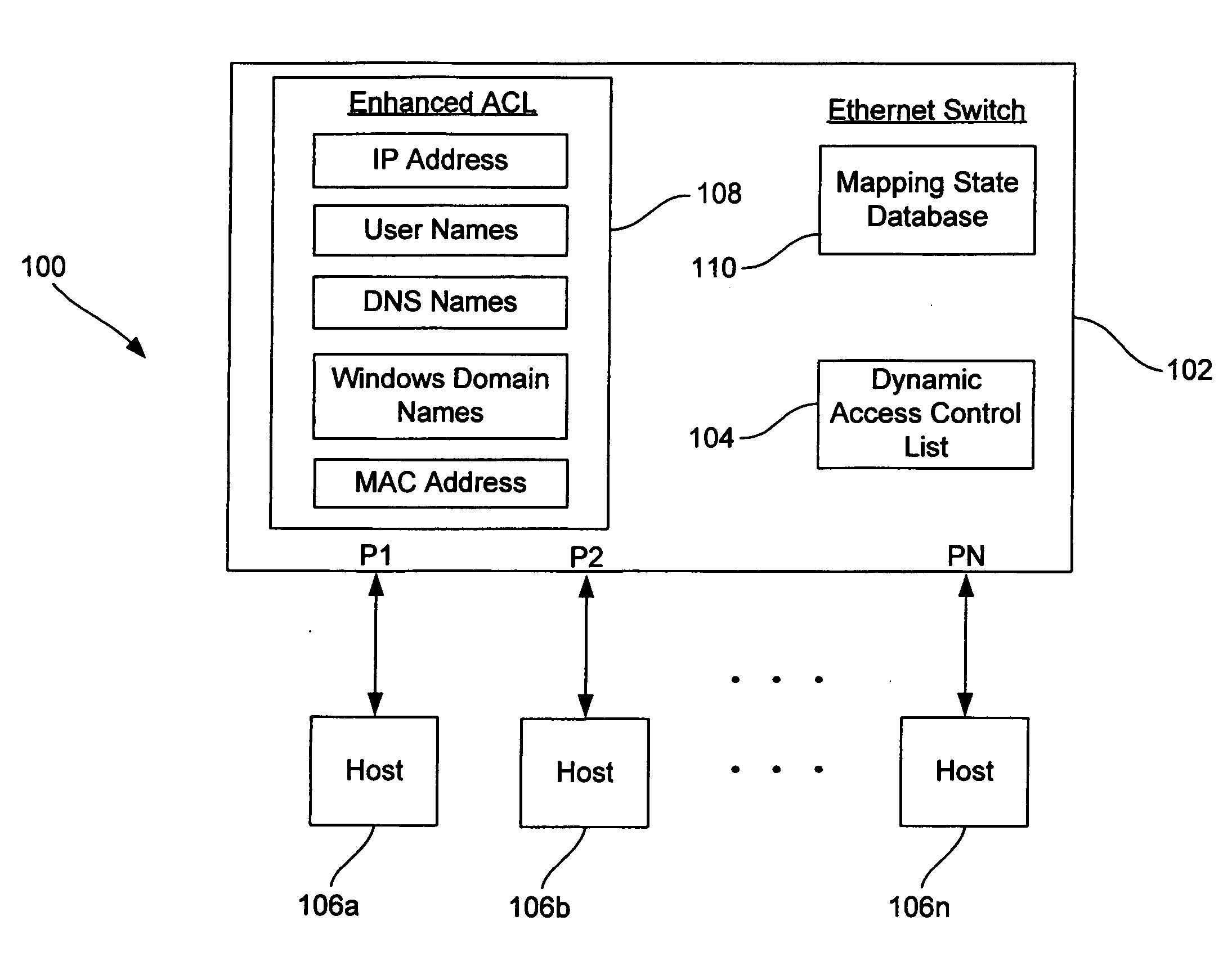
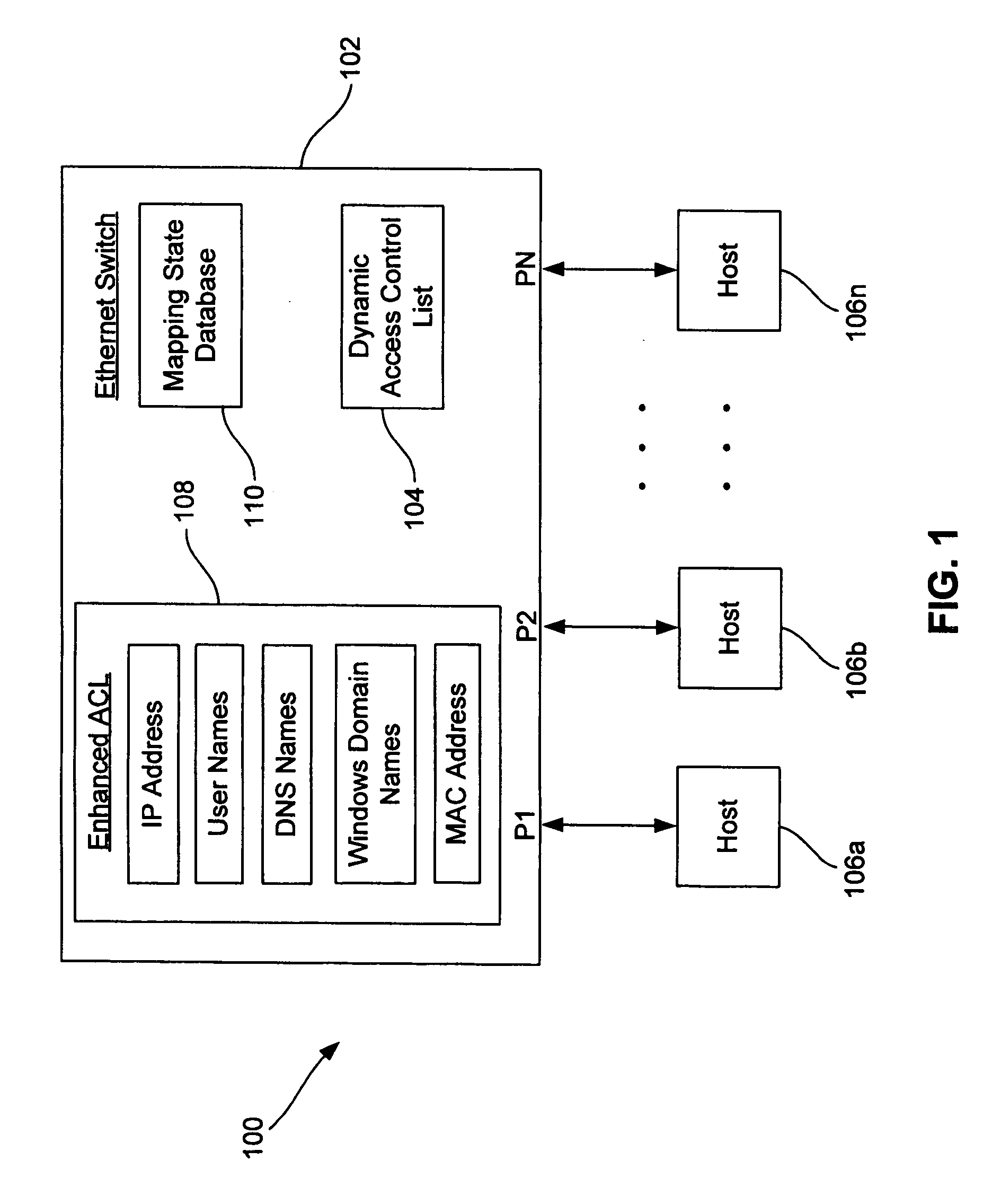
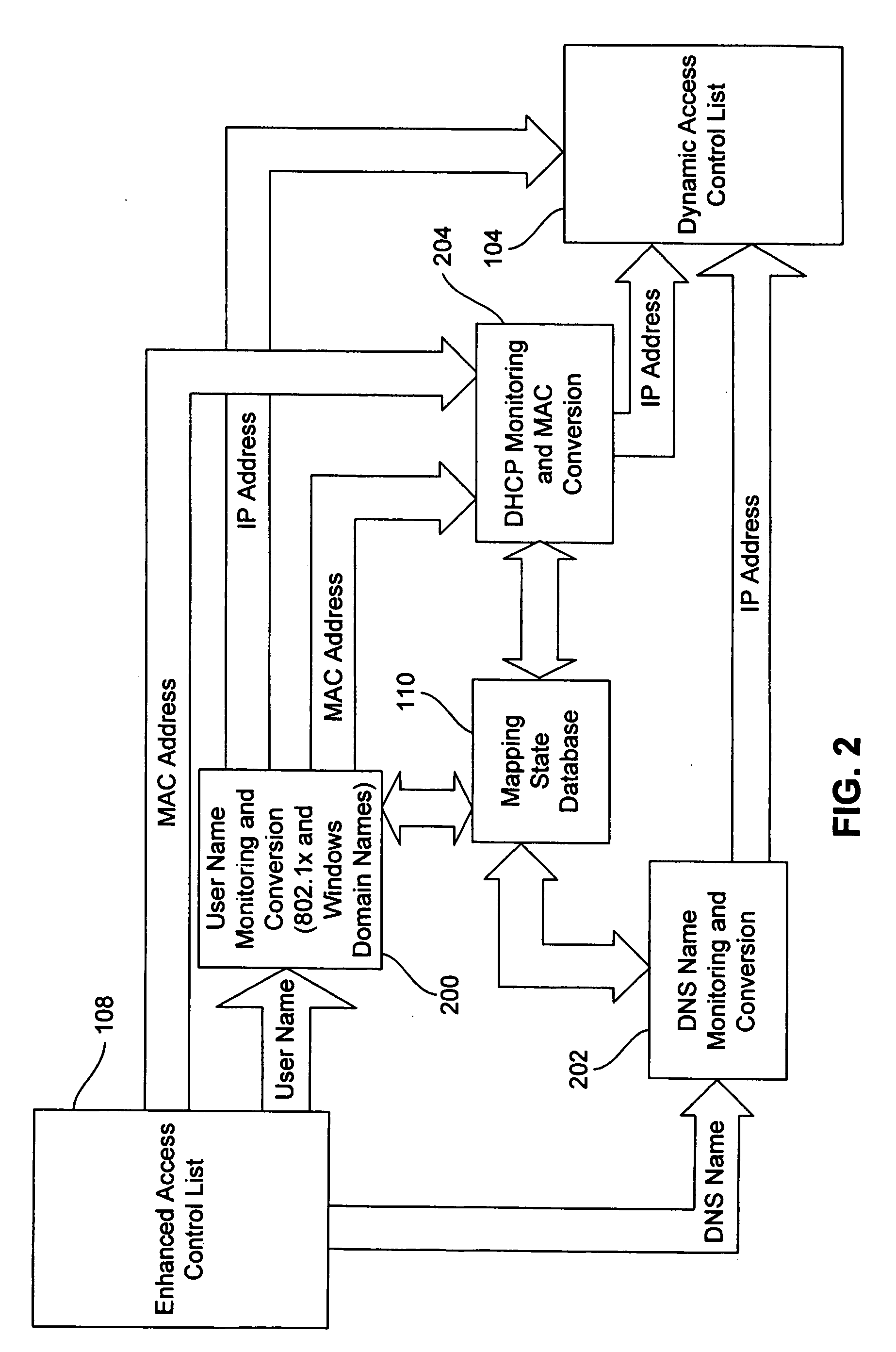
Dynamic access control lists
ActiveUS20050259654A1Data switching by path configurationMultiple digital computer combinationsDomain nameIp address
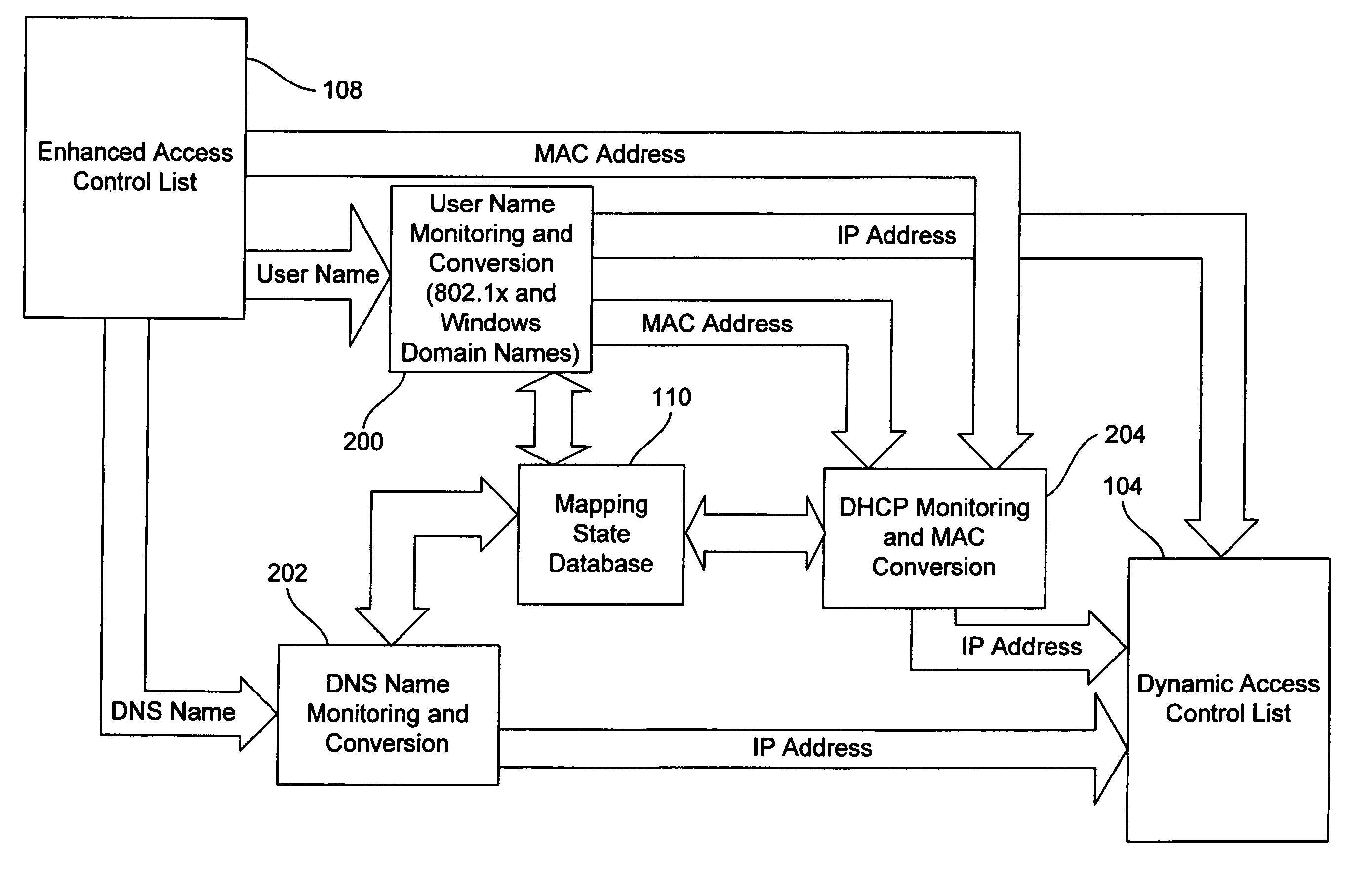
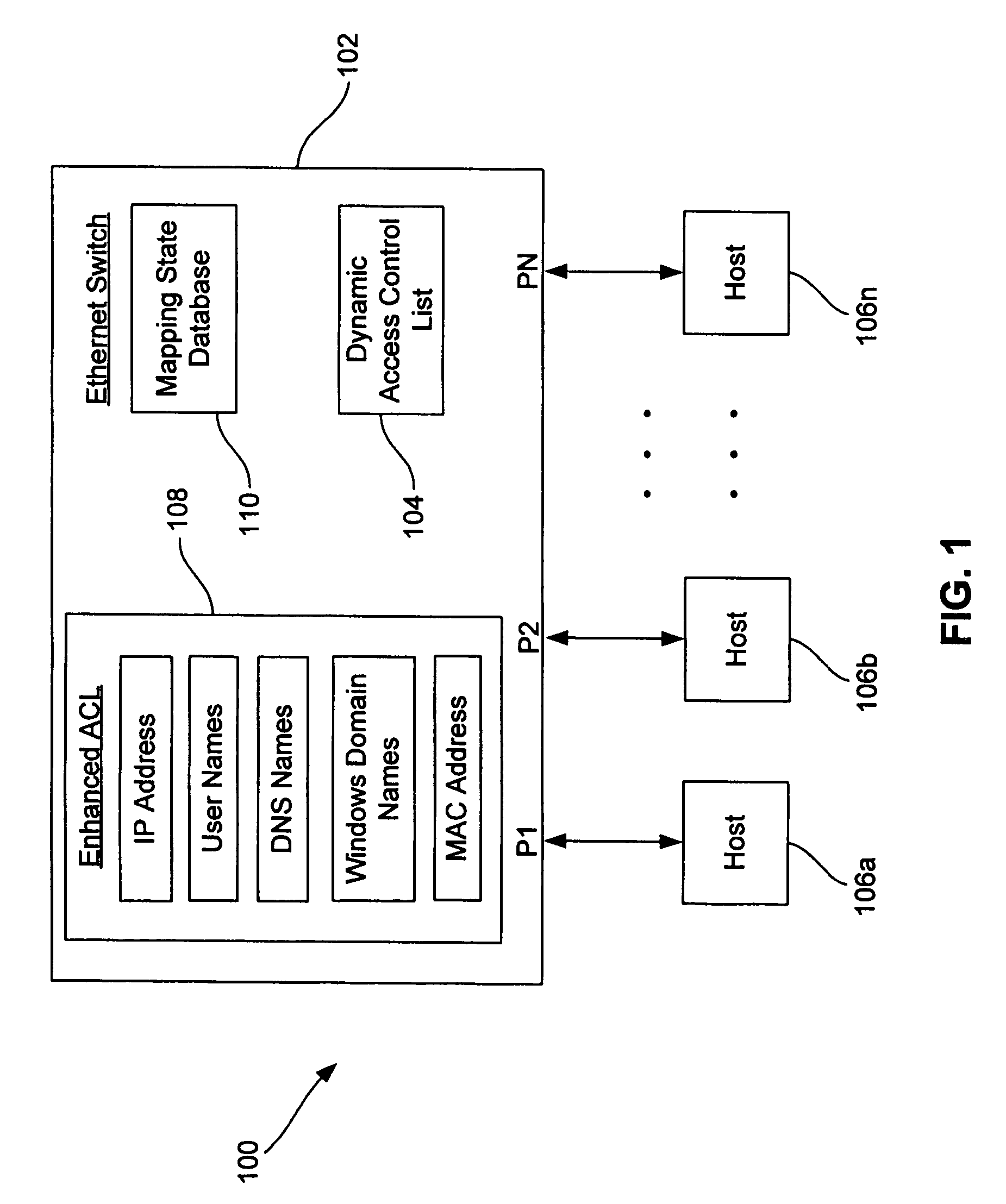
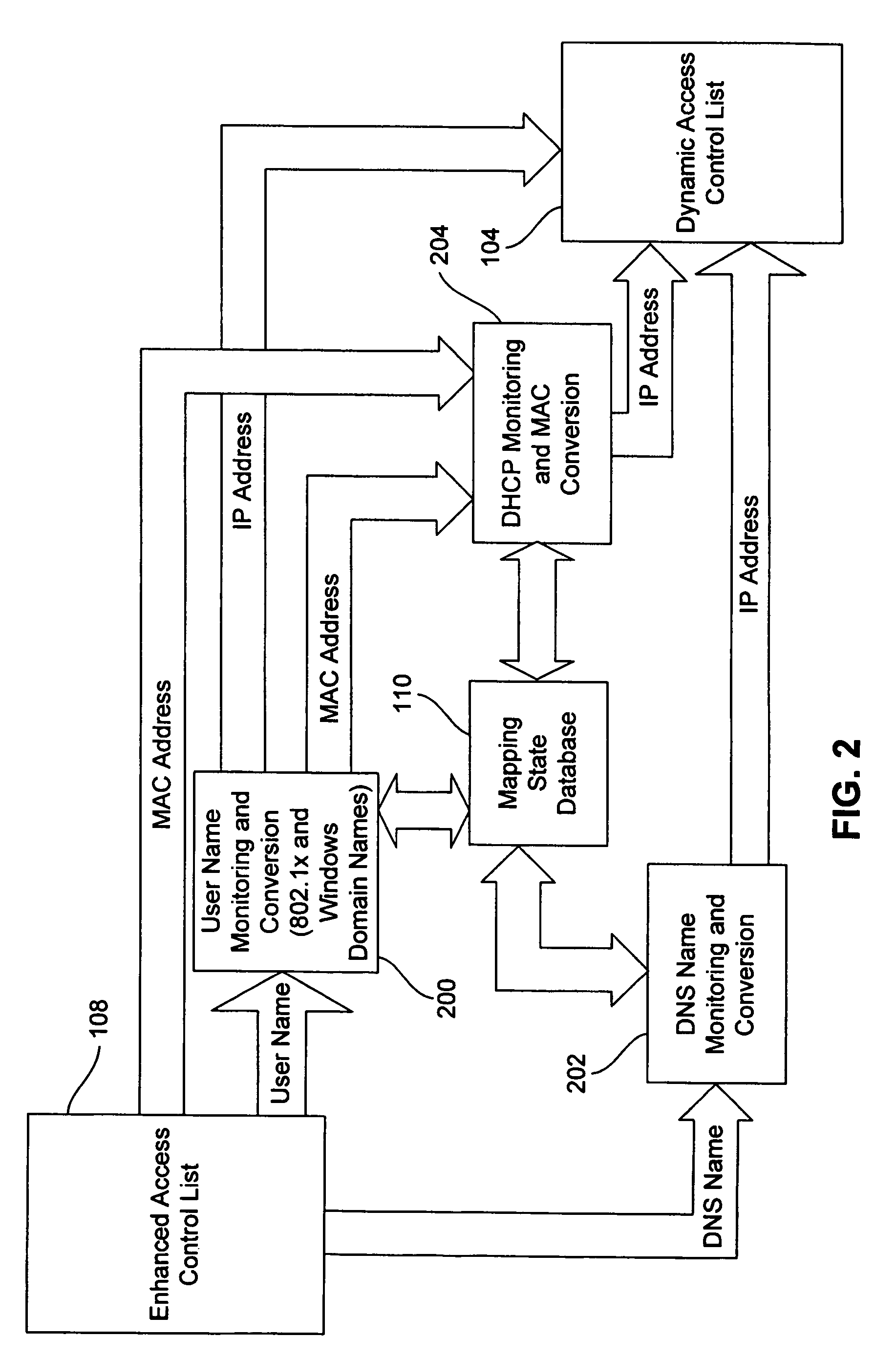
A method controls access of a user to a network including a plurality of hosts coupled together through a network switch. The method includes storing in the network switch an enhanced access control list containing data related to at least one of user names, DNS names, domain names, and physical addresses. A dynamic access control list is generated from the enhanced access control list, with the dynamic access control list containing a plurality of IP addresses that restrict access of the user to the network.
Owner:LIONRA TECH LTD
Access control system, access control method, and access control program
ActiveUS7624424B2Efficient updateEffective controlDigital data processing detailsUser identity/authority verificationAccess control matrixData access control
Owner:NEC CORP
Control of access control lists based on social networks
InactiveUS7467212B2Specific access rightsDigital data processing detailsVLAN access control listSocial web
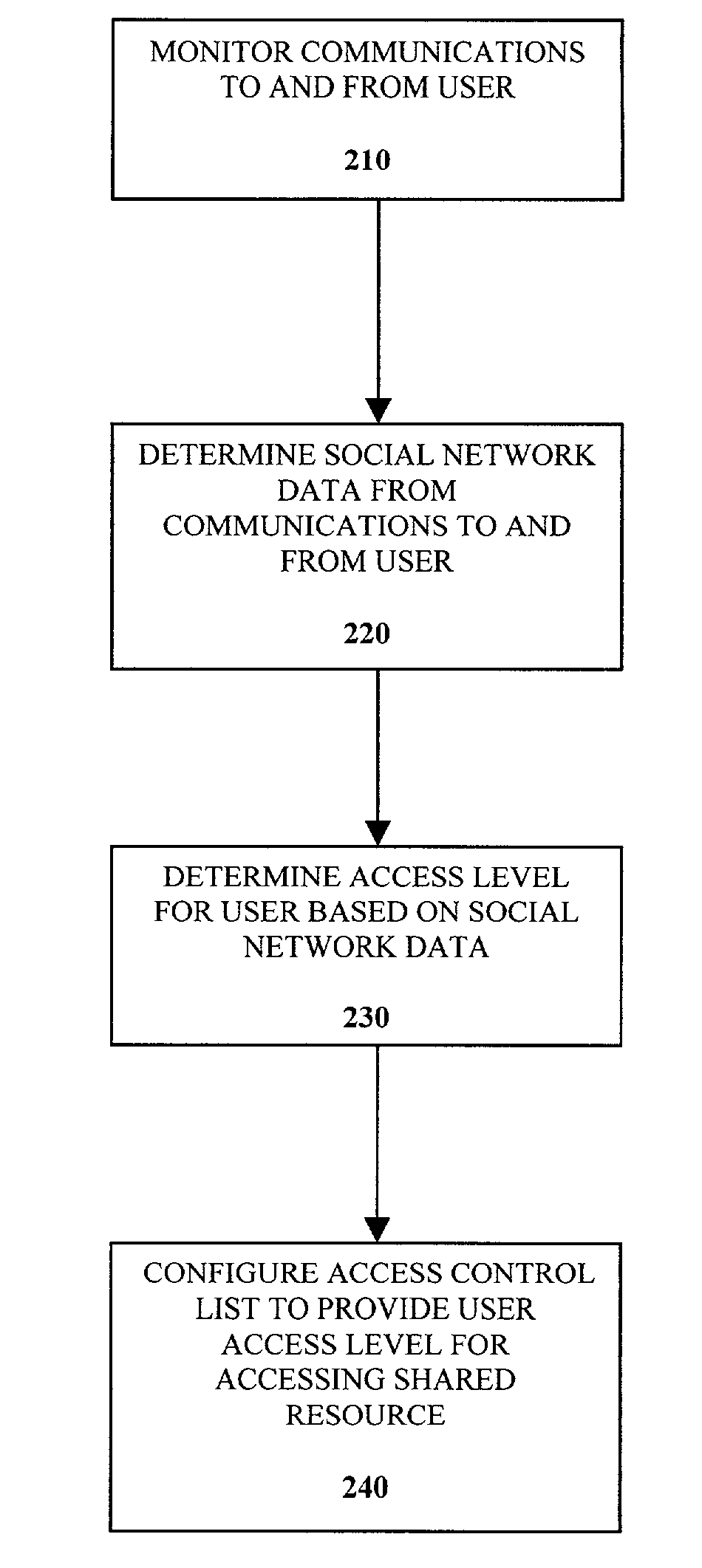
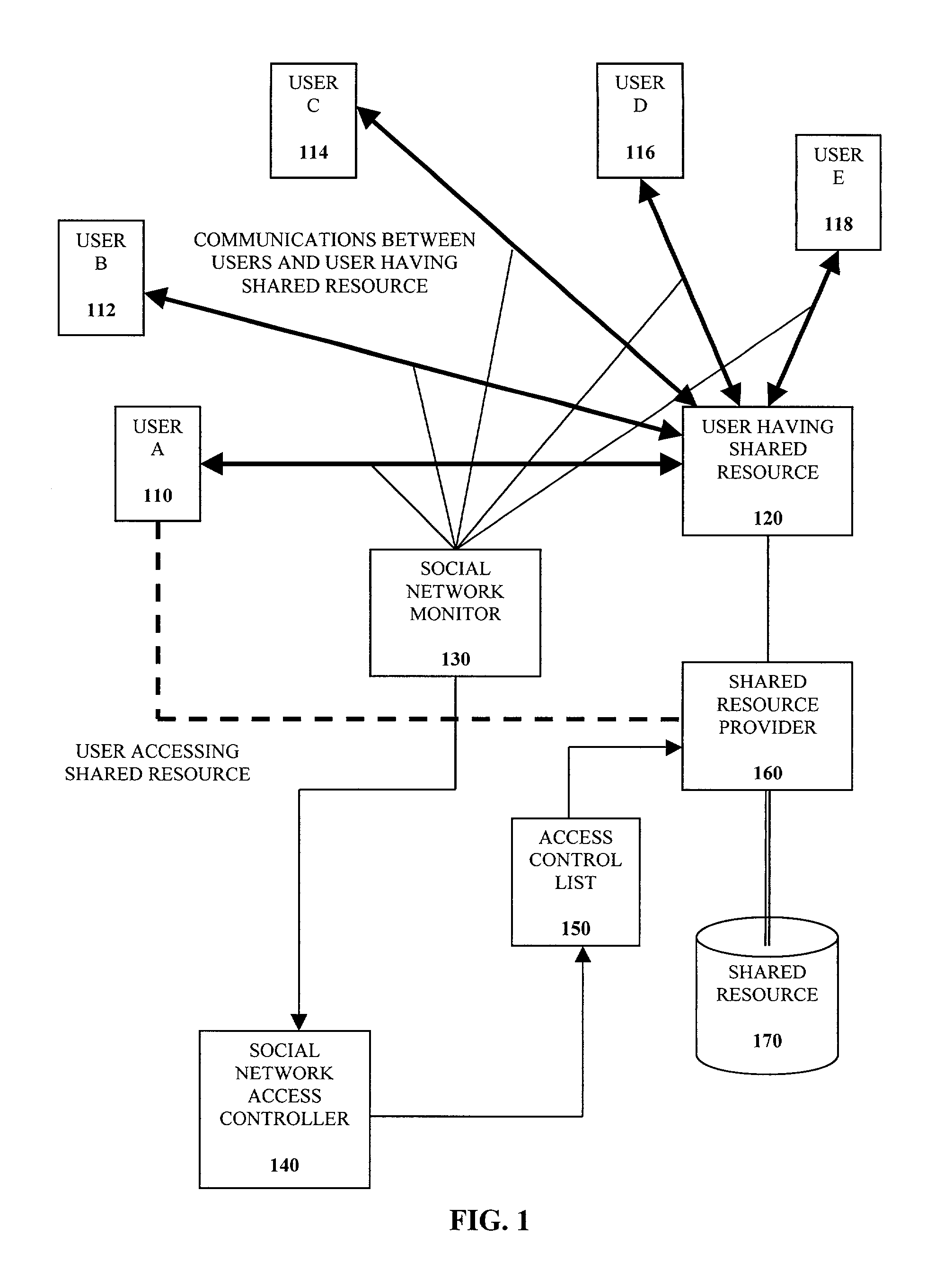
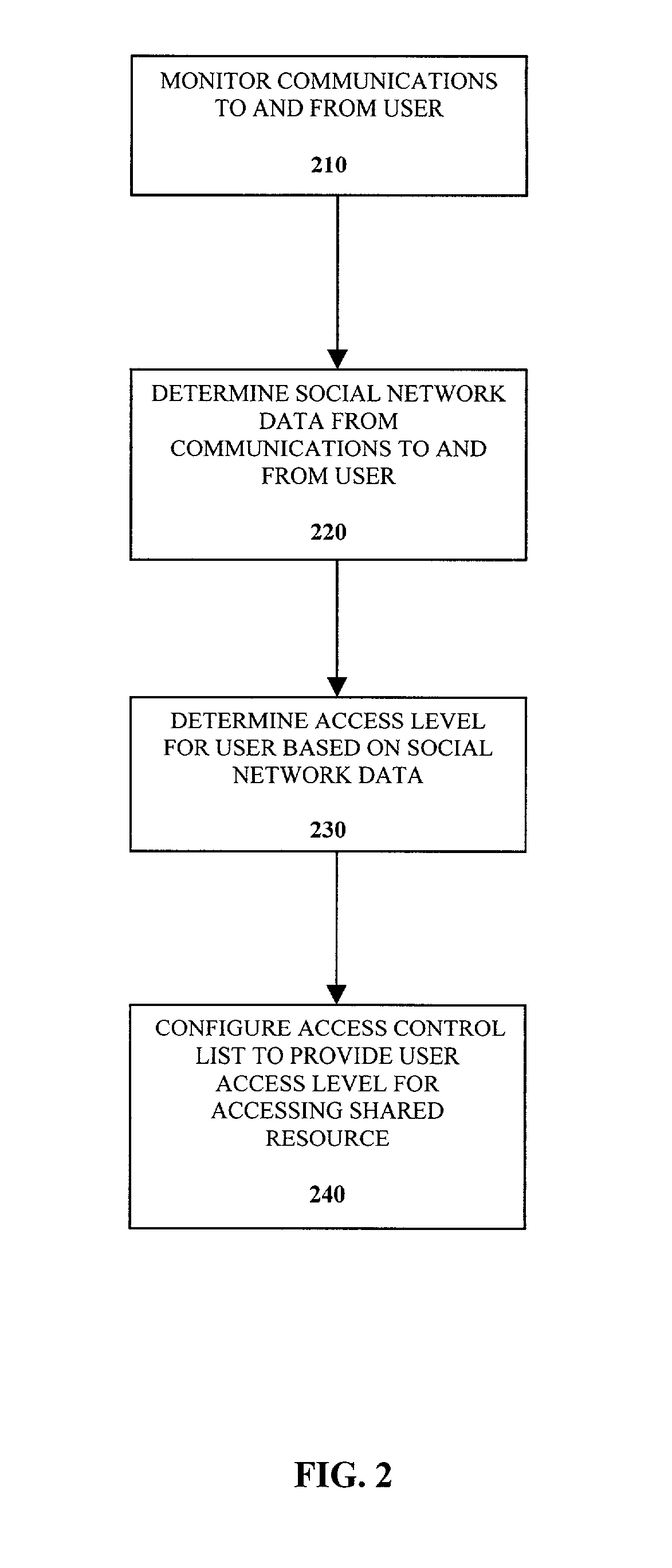
A method of controlling a social network access control list (ACL) for a shared resource includes monitoring communications to and from a user. Social network data from the communications to and from the user is determined. An access level for the user is determined based on the social network data. The access control list is configured to provide the user the access level determined for accessing the shared resource.
Owner:INTEL CORP
Method for combining and storing access control lists
A method of minimizing an amount of memory area required to store a plurality of rules associated with one or more access control lists (ACLs) includes selectively combining the plurality of rules into one or more groups depending upon similarities between the entries within each field and storing the groups in a database including a content addressable memory (CAM) device and a random access memory (RAM) device.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Emergency access interception according to black list
InactiveUS20050108257A1Increase the amount of dataKeep for a long timeDigital data processing detailsUnauthorized memory use protectionVLAN access control listBlack list
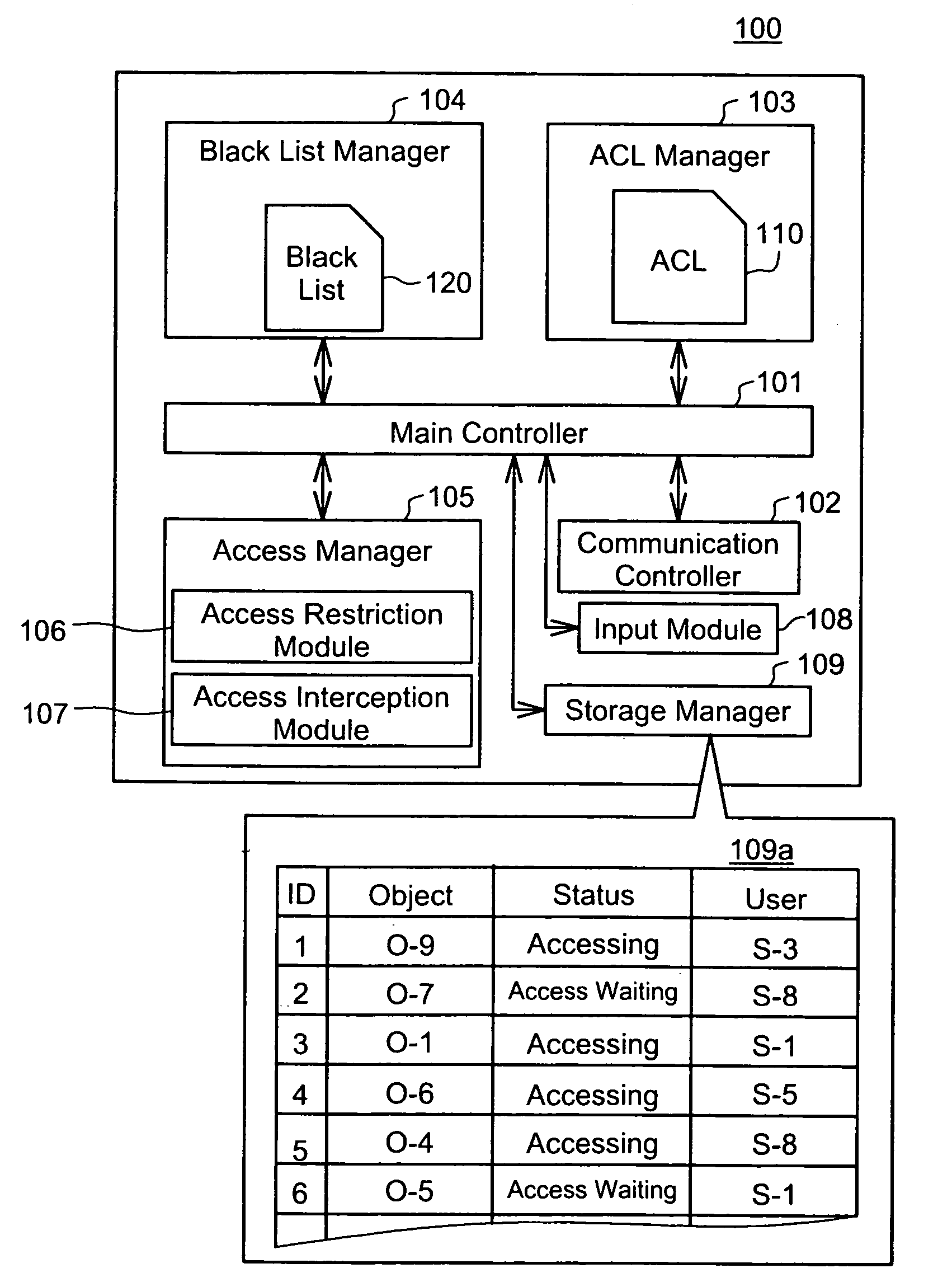
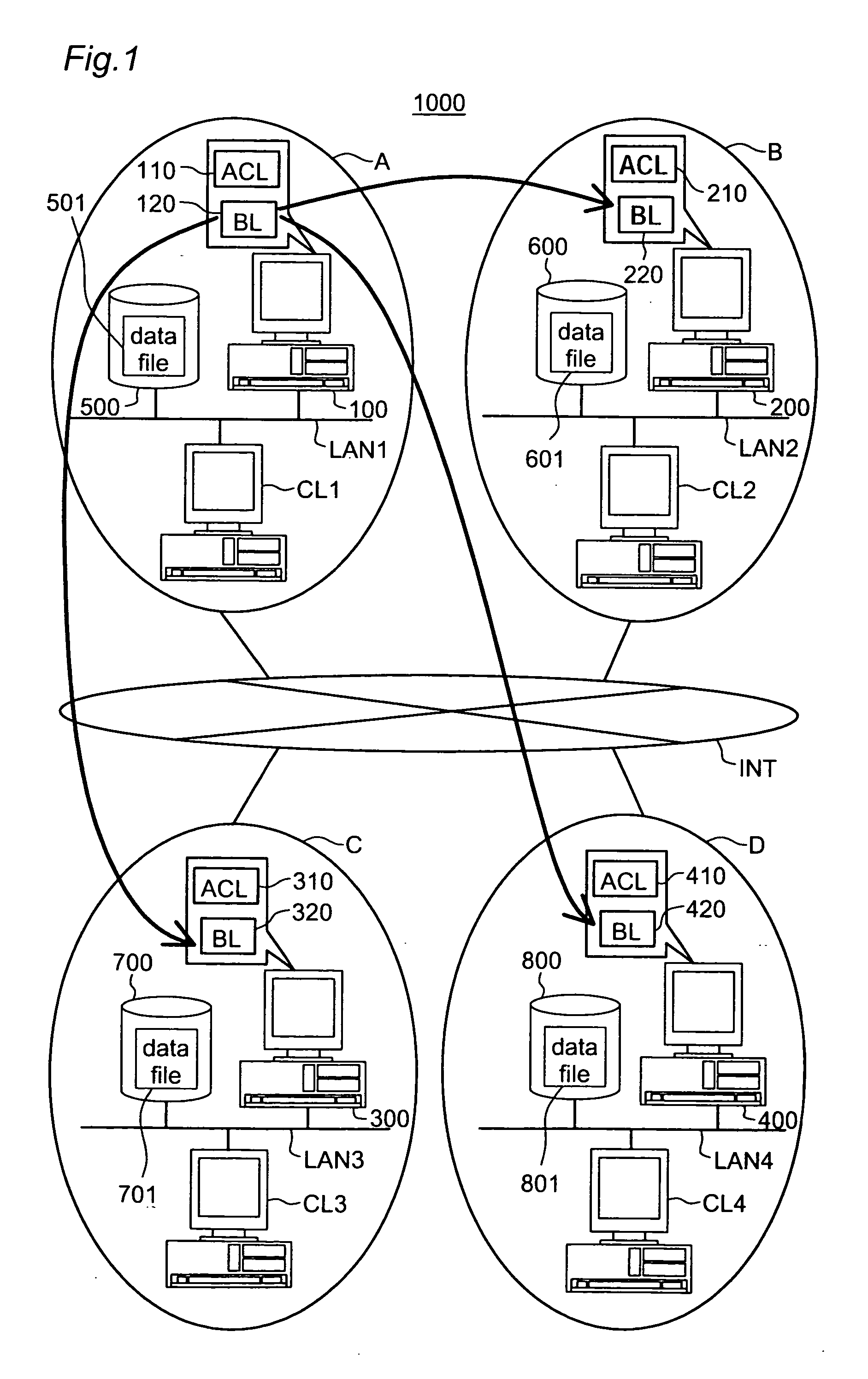
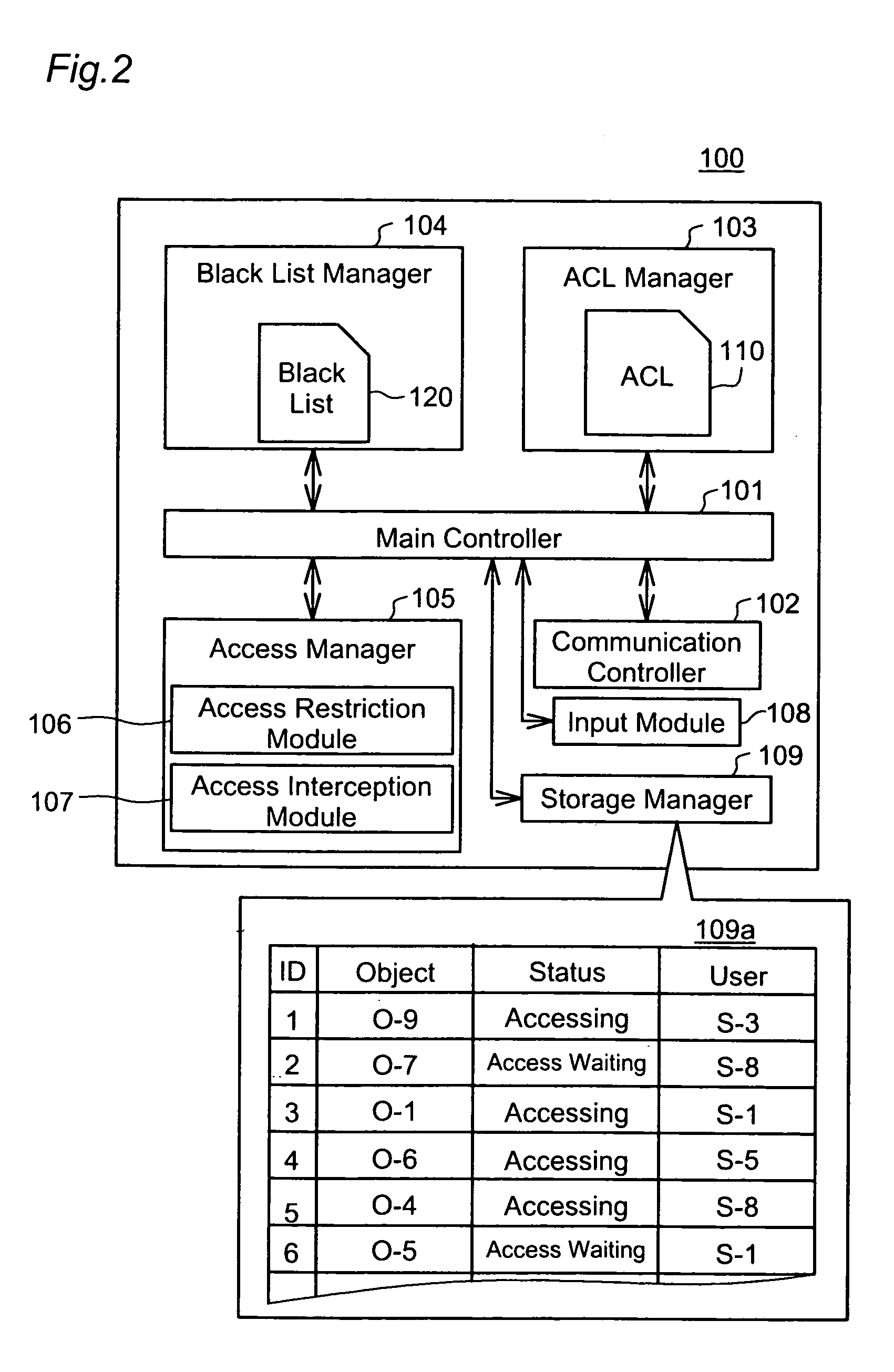
This invention addresses to execute an emergency access interception in a widely distributed environment. An access controller 100 manages an access control list (ACL) 110 recording access right to each object, and a black list (BL) 120 recording user information corresponding to the emergency access interception. The access controller 100 receives a request for authentication to access right and judges whether or not the access right is proper, first according to the BL 120 then ACL110. In case where the user information corresponding to the request is recorded in the BL 120, the access controller 100 sends out the user information to other access controllers and instructs them to register it in the black list. This invention effectively actualizes the emergency access interception under the widely distributed environment in case where the interception is required for any user.
Owner:GOOGLE LLC
Data storage incorporating crytpographically enhanced data protection
Various exemplary embodiments relate to a system for storing encrypted data and providing access to a group of users. The system may include: a record of user accounts including: a user identifier and a public encryption key; an access control list (ACL) defining an access control policy including: permissions defining access to data objects associated with the ACL and an ACL key list including copies of a an ACL key encrypted with the public keys of the users; a user-data storage medium including: encrypted user data, stored as a plurality of data objects, each object associated with an ACL and encrypted with the ACL key, and meta-data; and an access controller configured to: receive a request for a data object, and send a copy of the data object and the ACL key encrypted with the public key of the user if the user has permission to access the data object.
Owner:ONYX PRIVACY
Moveable access control list (ACL) mechanisms for hypervisors and virtual machines and virtual port firewalls
ActiveUS8381209B2Efficient responseRapid deploymentSemiconductor electrostatic transducersMicrophone structural associationVLAN access control listAccess control list
A method (and system) which provides virtual machine migration with filtered network connectivity and control of network security of a virtual machine by enforcing network security and routing at a hypervisor layer at which the virtual machine partition is executed, and which is independent of guest operating systems.
Owner:DAEDALUS BLUE LLC
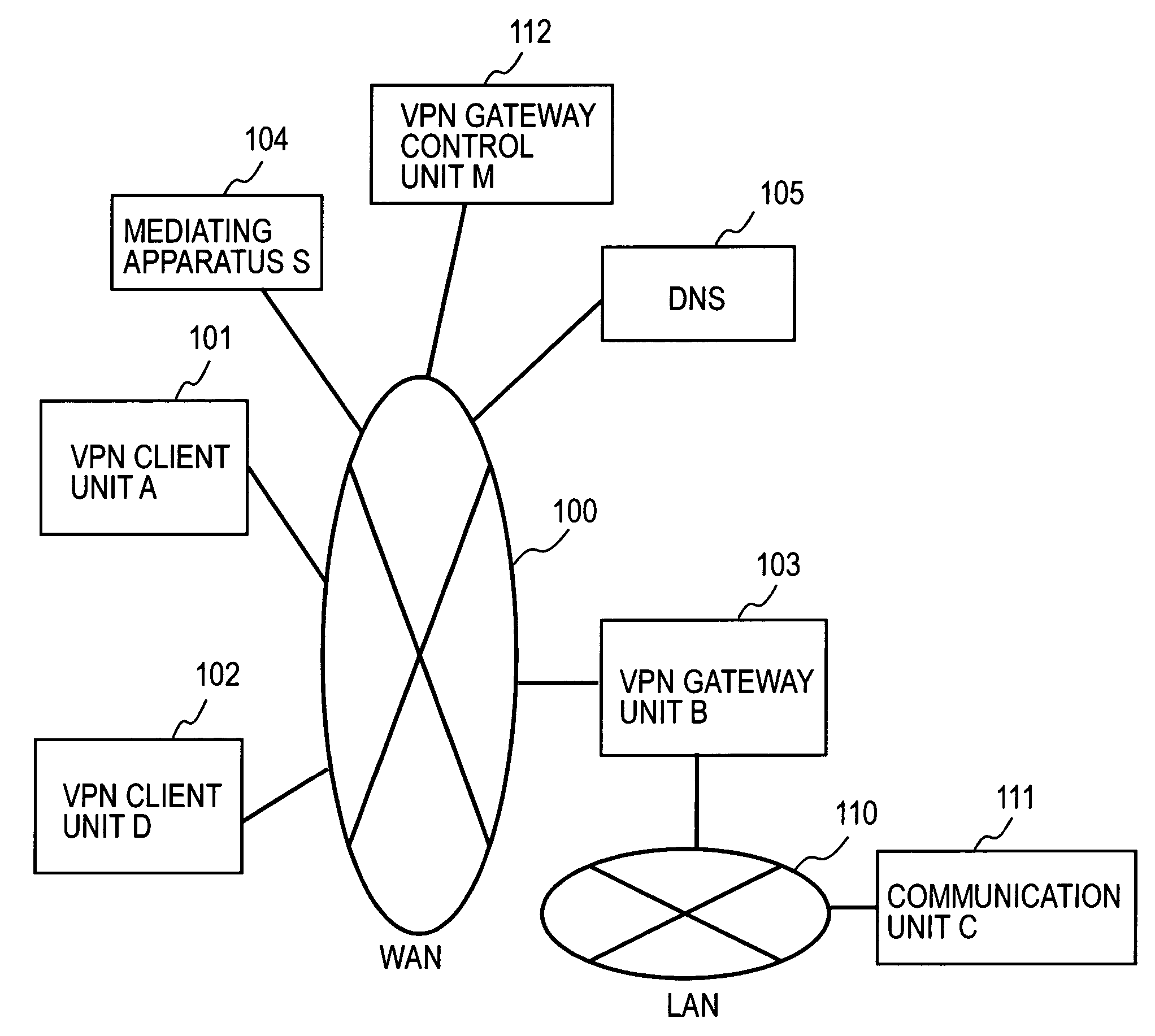
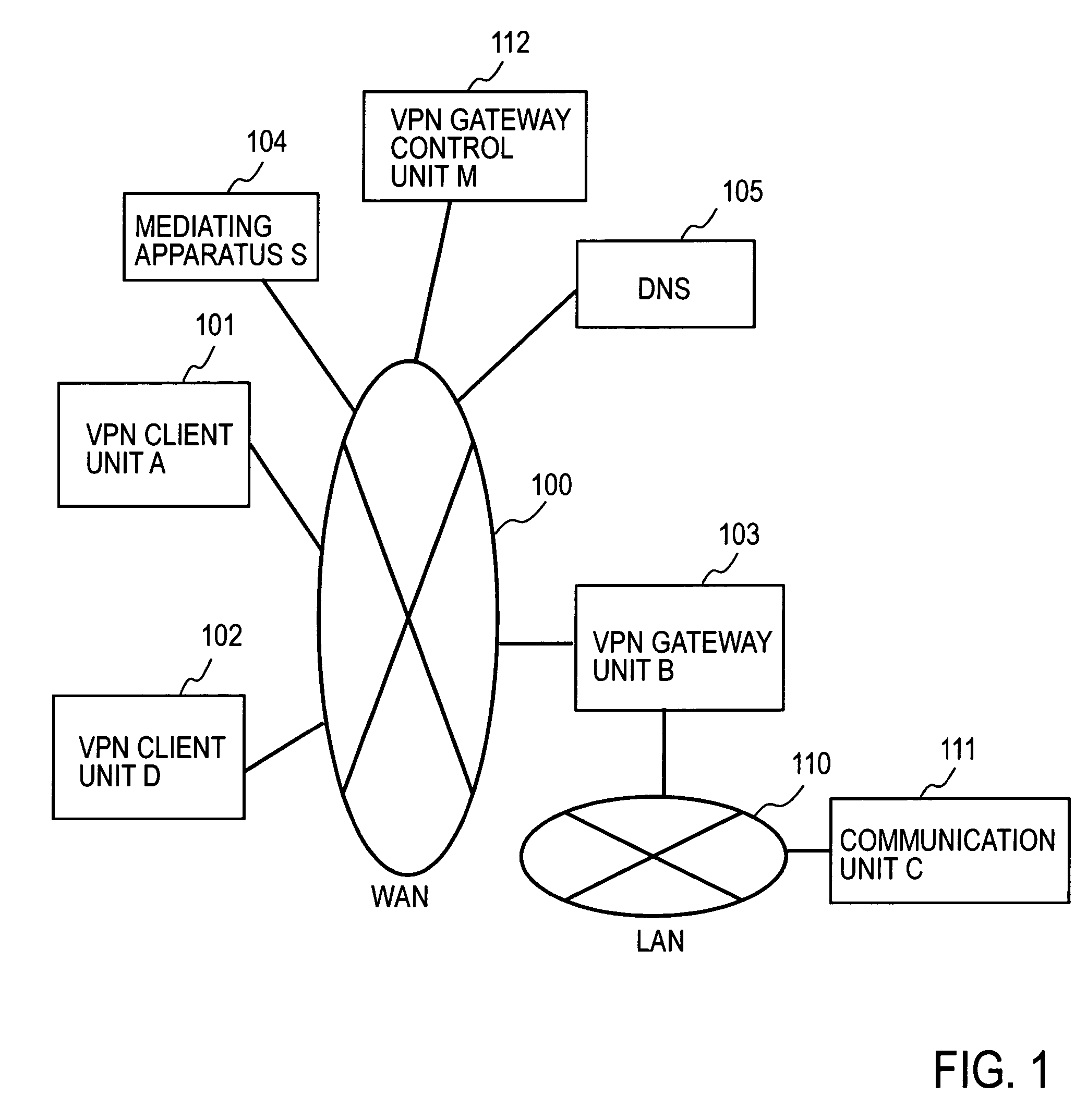
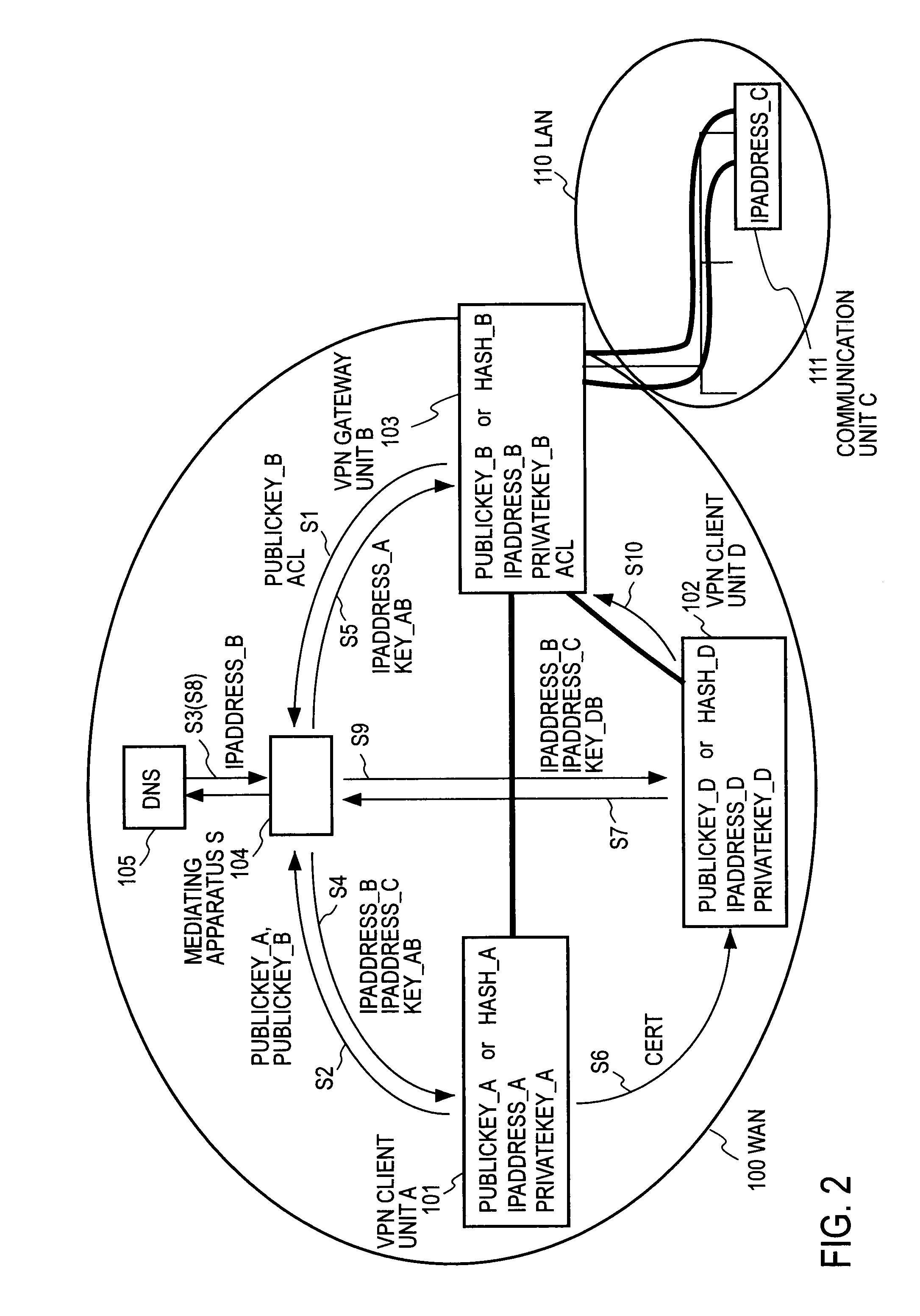
Remote access VPN mediation method and mediation device
InactiveUS7665132B2Secure distributionKey distribution for secure communicationDigital data processing detailsPrivate IPCommunication unit
A mediating apparatus is provided on an IP network, and stores an access control list (ACL) retained in a VPN gateway unit. The mediating apparatus: receives a retrieval request from a VPN client unit; acquires a private IP address of a communication unit by reference to ACL; searches DNS to acquire therefrom an IP address of the VPN gateway unit; generates a common key that is used for authentication between the VPN client unit and the VPN gateway unit and for encrypted communication therebetween; sends the IP address of the VPN gateway unit, the private IP address of the communication unit, and the common key to the VPN client unit; and sends the IP address of the VPN client unit and the common key to the VPN gateway unit.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
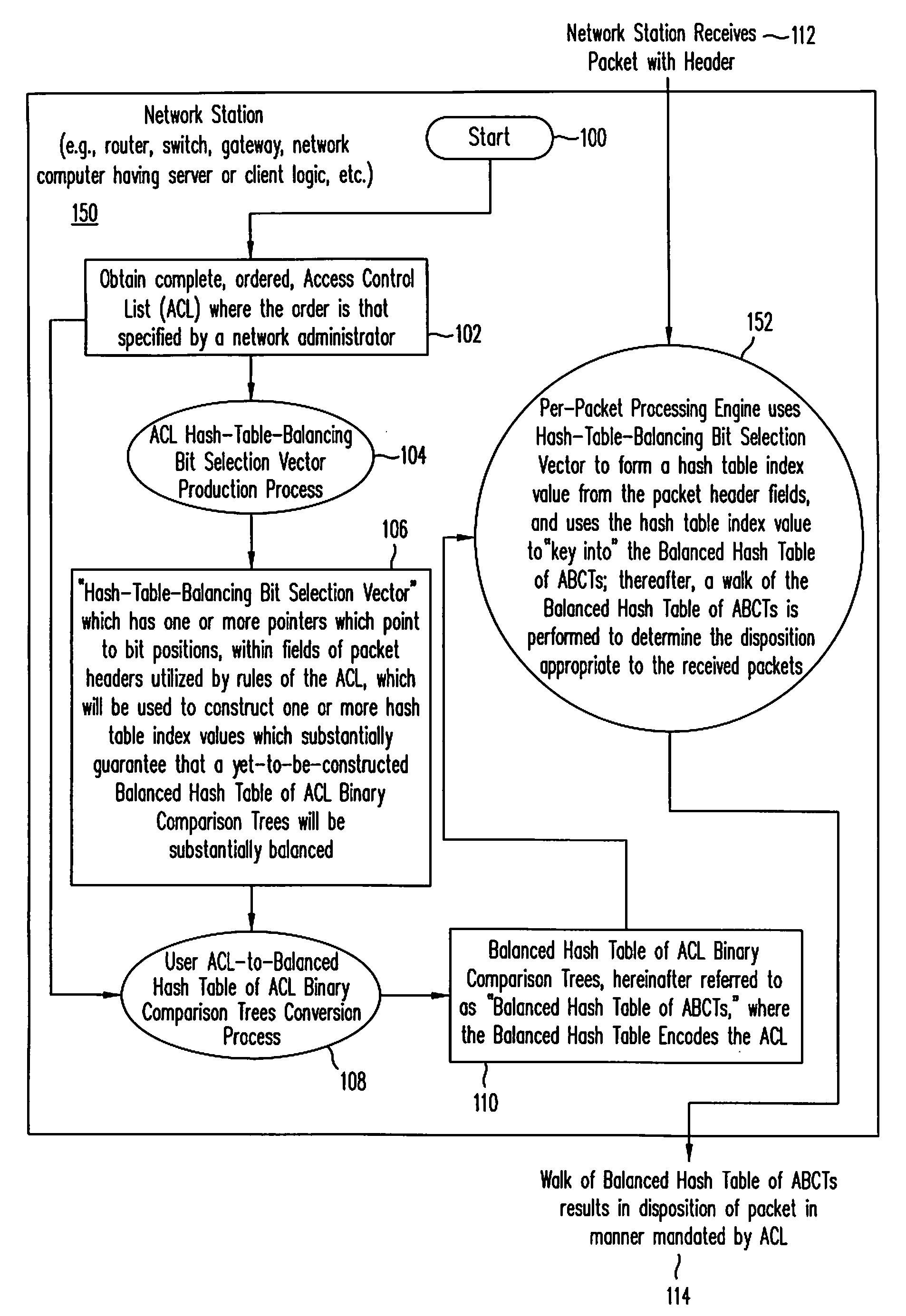
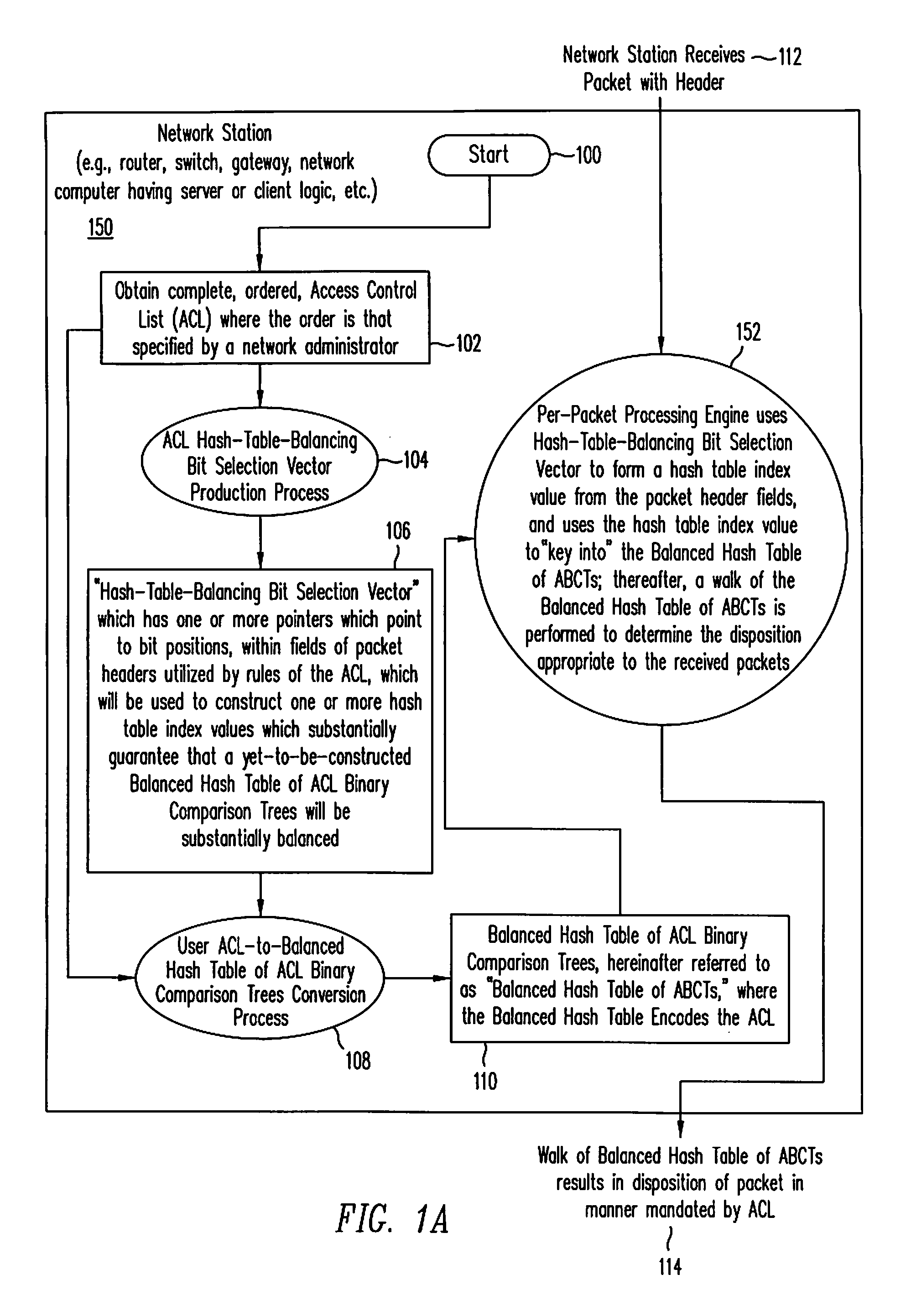
Implementing access control lists using a balanced hash table of access control list binary comparison trees
InactiveUS7324514B1Improved ACL performanceProlong lifeData switching by path configurationNetwork connectionsTheoretical computer scienceVLAN access control list
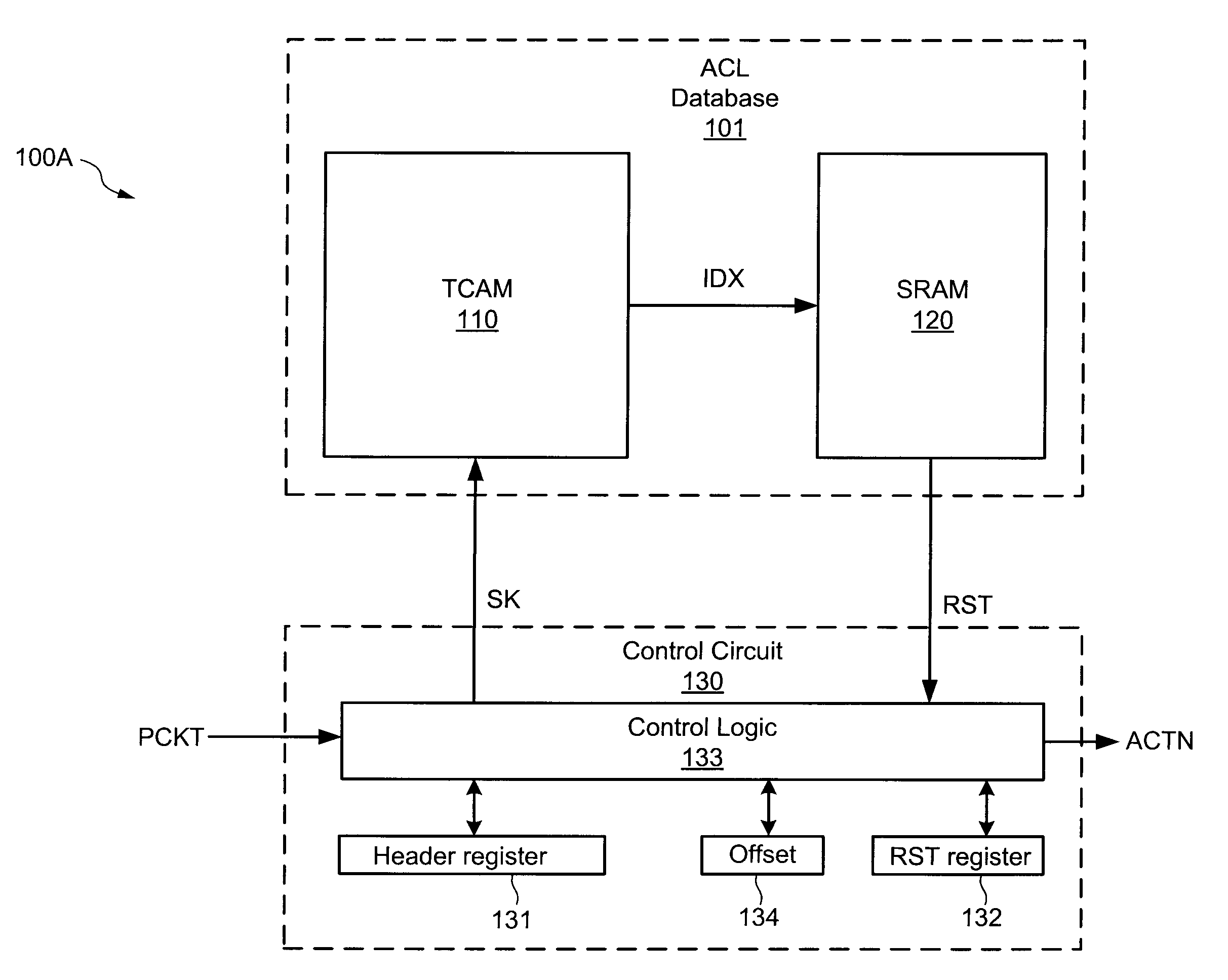
A method and system for implementing Access Control Lists (ACLs) using a Balanced Hash Table of ACL Binary Comparison Trees (ABCTs), where the Balanced Hash Table of ABCTs encodes the replaced ACL. In one embodiment, the method includes but is not limited to receiving at least one packet, and disposing of the received at least one packet in response to a walk of a Balanced Hash Table of ABCTs, where the Balanced Hash Table of ABCTs encodes an Access Control List. In another embodiment, the method further includes converting the Access Control List to the Balanced Hash Table of ABCTs, the Balanced Hash Table of ABCTs encoding the Access Control List. In one embodiment, the system receives at least one packet, and disposing disposes of the received at least one packet in response to a walk of a Balanced Hash Table of ABCTs, where the Balanced Hash Table of ABCTs encodes an Access Control List. In another embodiment, the system further includes converts the Access Control List to the Balanced Hash Table of ABCTs, where the Balanced Hash Table of ABCTs encodes the Access Control List.
Owner:CISCO TECH INC
Compilation of access control lists
InactiveUS7646771B2Improve compilation speedReduce in quantityDigital computer detailsData switching by path configurationParallel computingVLAN access control list
An improvement in the compilation of classification tables from across control lists increases the efficiency of memory utilization by fragments in the lower level tables and using the classification ID's from a pair of higher-level tables as pointers to the fragments and as indicators of the depth of the entries in the fragments. A further improvement makes use of aggregate bit vectors, thereby simplifying construction of the lower-level tables. The bit-vector sections preferably coincide with the cache lines of the processing, thereby maximizing the speed with which the relevant bits in the bit vector can be identified from the aggregate bit vectors.
Owner:CISCO TECH INC
Method and apparatus for taking effect rules of access control list
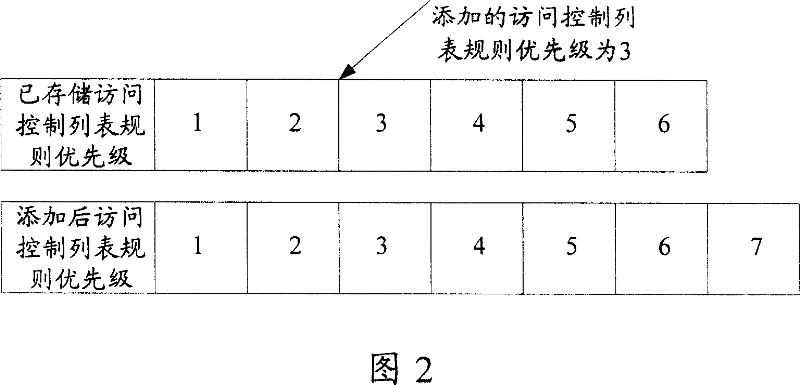
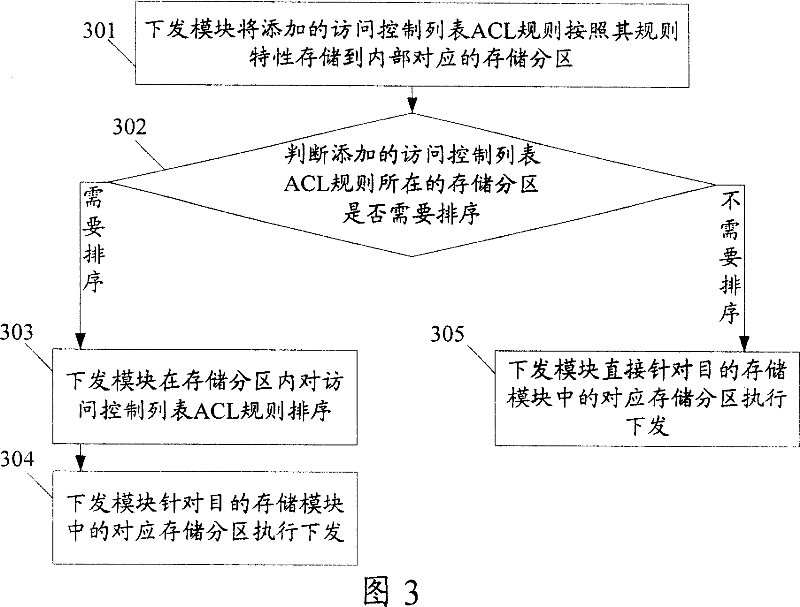
InactiveCN101039271AAchieve millisecond-level effectivenessProlong the effective timeData switching networksVLAN access control listAccess control list
The present invention discloses a becoming effective method for the access control list (ACL) rule. A special storage partition for the corresponding access control list (ACL) rule is arranged in the down sending module and the objective storage module. The method comprises the following part: The additional ACL rule is store in the storage partition of the down sending module according to the corresponding ACL rule. When a sorting is needed the down sending module will sort the additional ACL rule in the storage partition and execute the down sent according to the corresponding storage partition in the objective storage module. Otherwise the down sending module executes the down sent according to the corresponding storage partition in the objective storage module. The present invention also discloses a becoming effective device of the ACL rule which comprises the down sending module and the objective storage module.The present invention can reduce the time of moving and deleting the ACL rule when the ACL rule is sent, which can realize the ACL rule becoming effective in a millisecond.
Owner:HUAWEI TECH CO LTD
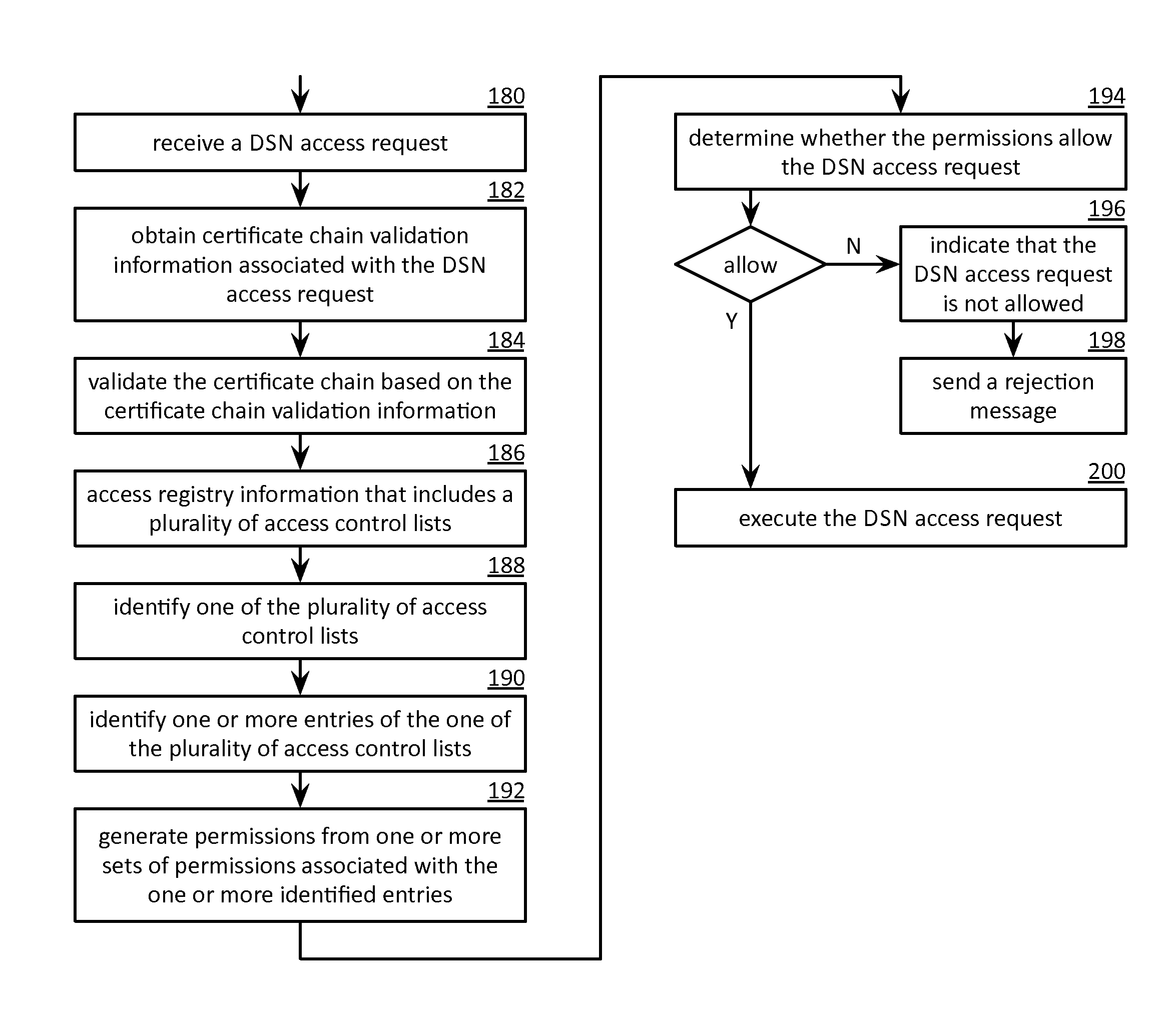
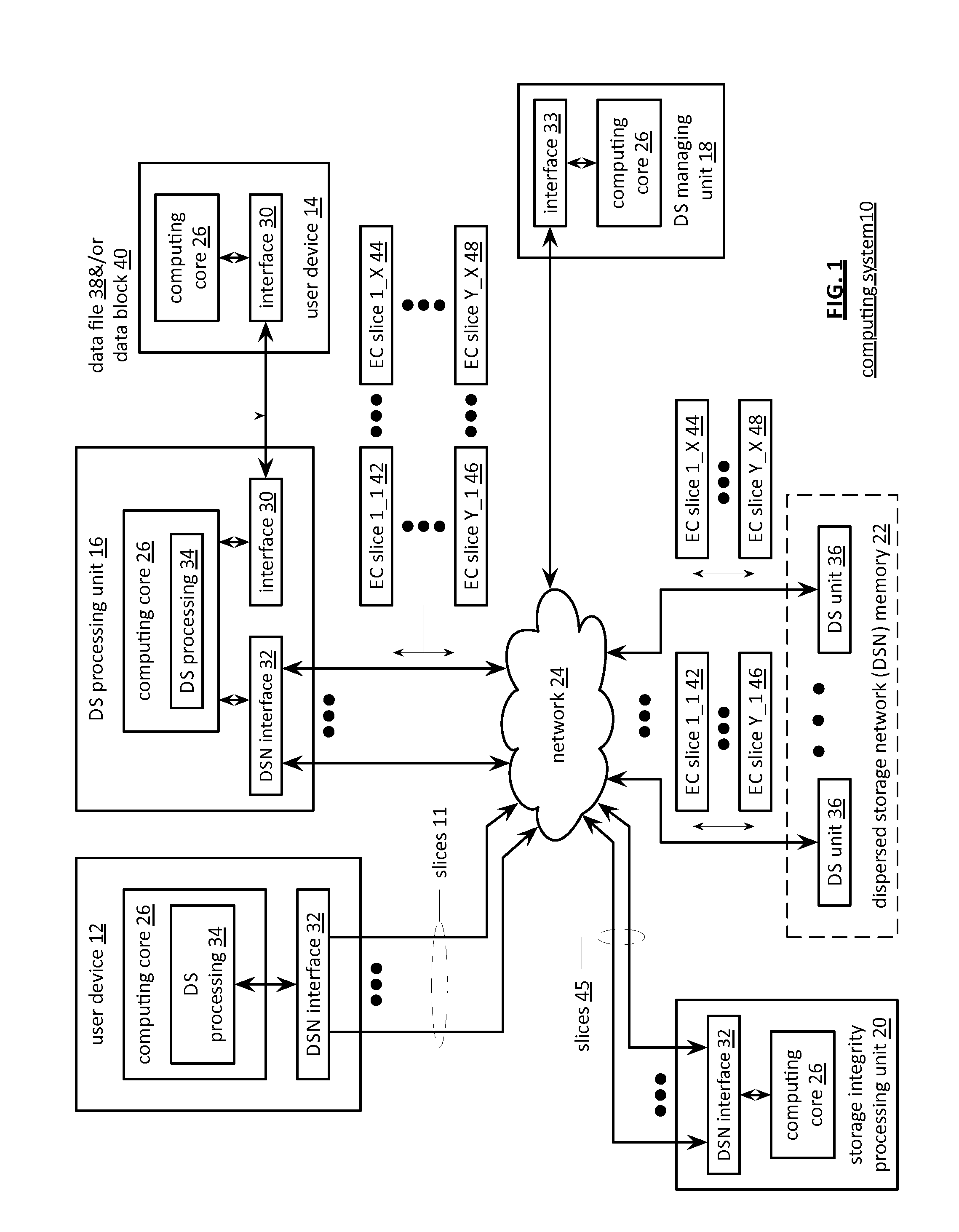
Processing a dispersed storage network access request utilizing certificate chain validation information
A method begins by a processing module receiving a dispersed storage network (DSN) access request that includes a requester identifier (ID), wherein the requester ID is associated with a certificate chain. When the certificate chain is valid, the method continues with the processing module accessing registry information for the DSN. The method continues with the processing module identifying one of a plurality of access control lists based on at least one of information associated with the requester ID and information associated with the certificate chain, identifying one or more entries of the one of the plurality of access control lists based on the information associated with the certificate chain to produce one or more identified entries, and generating, for the DSN access request, permissions from one or more sets of permissions associated with the one or more identified entries.
Owner:IBM CORP
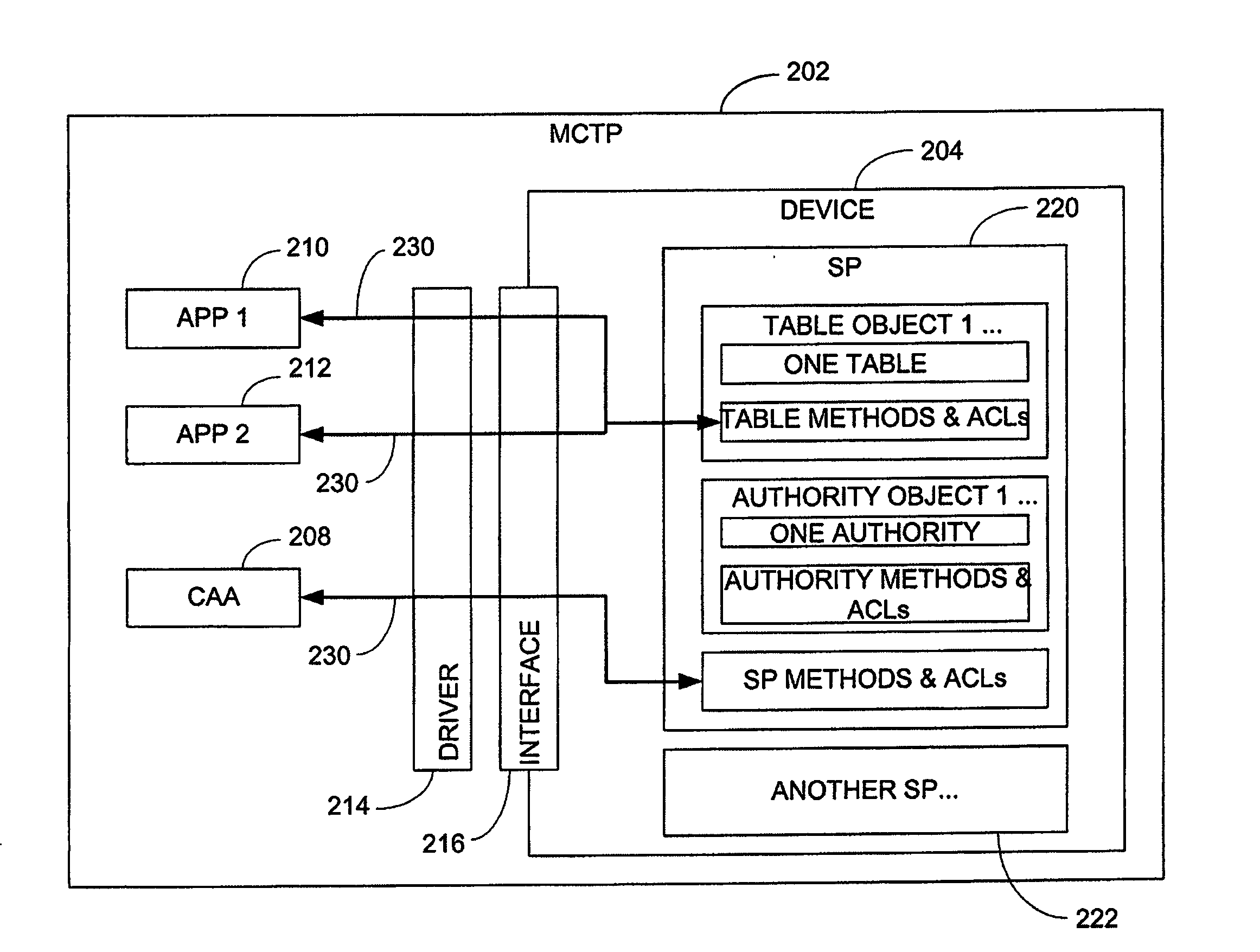
Versatile access control system
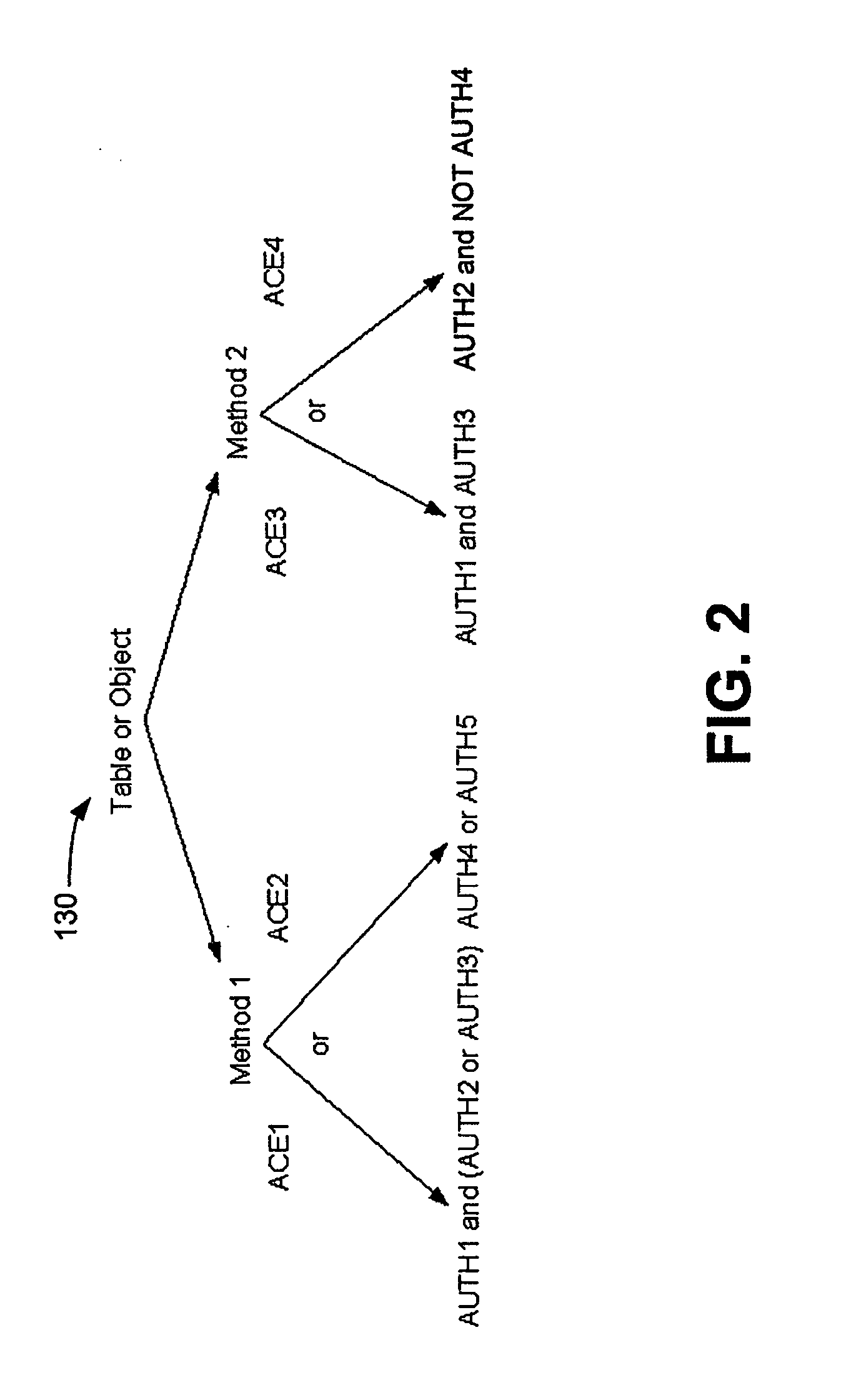
ActiveUS20070250915A1Digital data processing detailsUser identity/authority verificationControl systemVLAN access control list
An access control system and method are provided, which include a plurality of authorities, a plurality of access control elements and an access control list. Each authority associates at least one of a plurality of proof of knowledge operations with at least one of a plurality of proof of knowledge credentials. Each access control element identifies a Boolean combination of at least one of the authorities. The access control list identifies one or more of the access control elements by which a method to be executed can be authenticated.
Owner:SEAGATE TECH LLC
Oblivious transfer with hidden access control lists
InactiveUS20120063593A1Computer security arrangementsSecuring communicationOblivious transferVLAN access control list
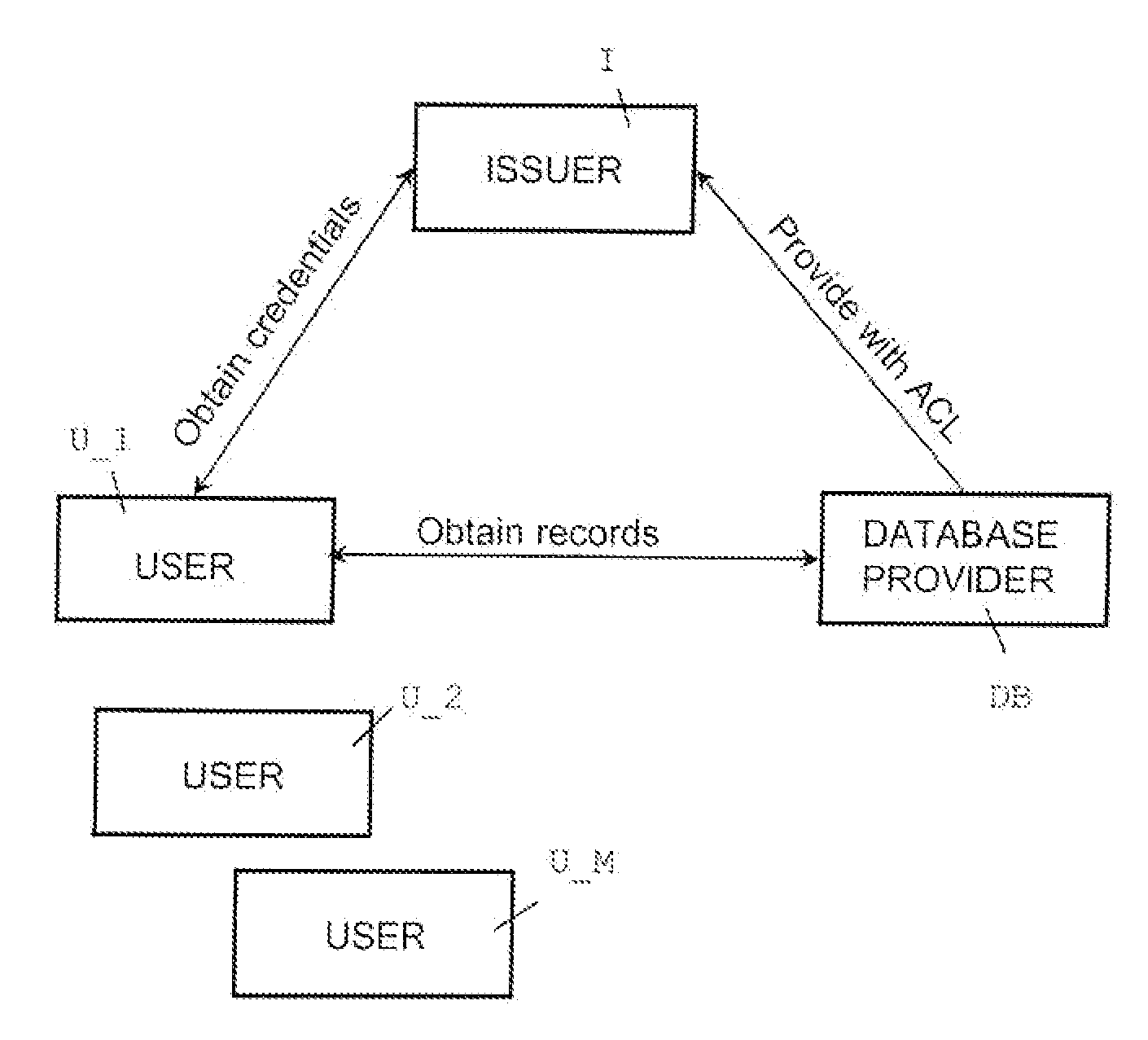
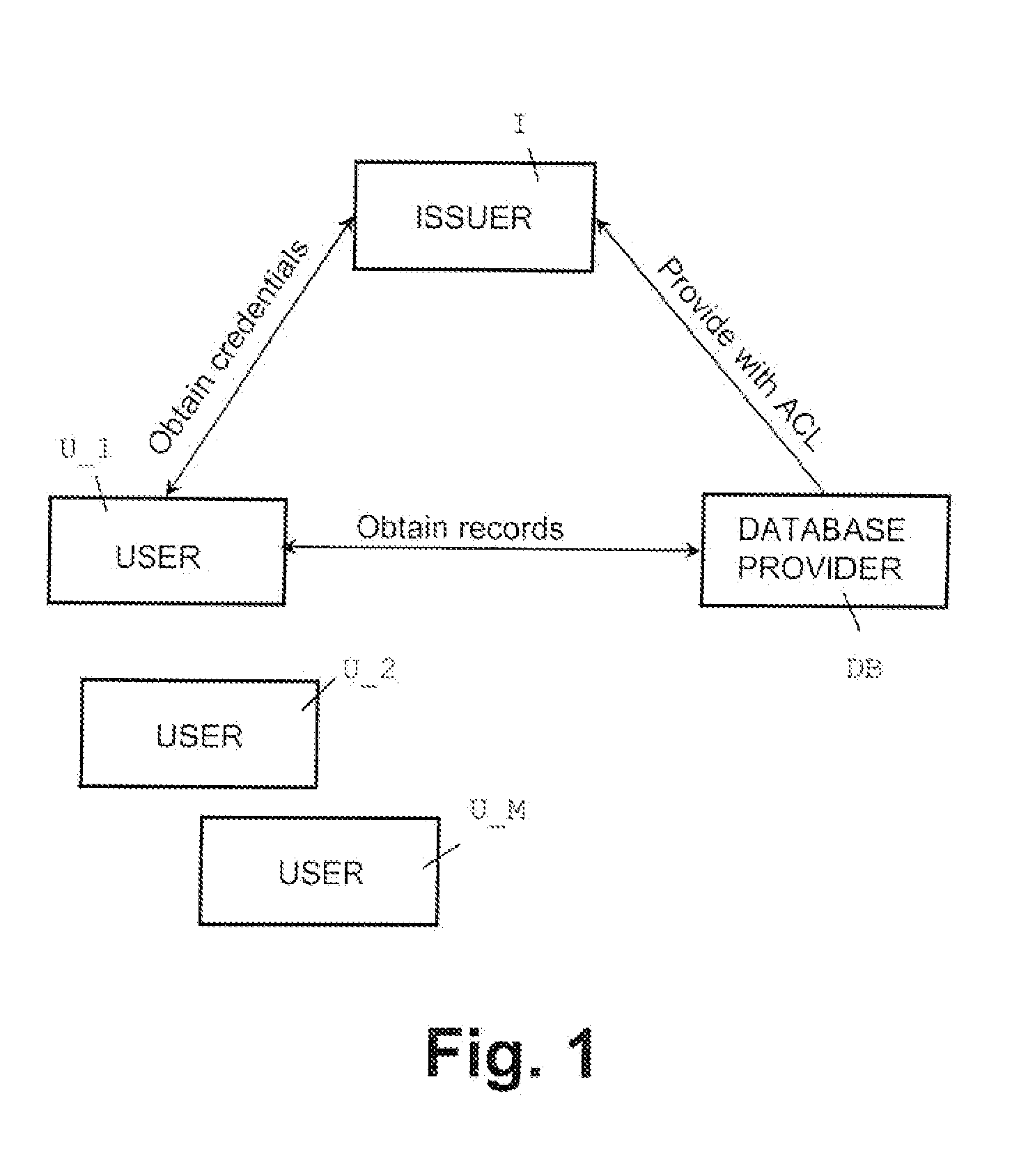
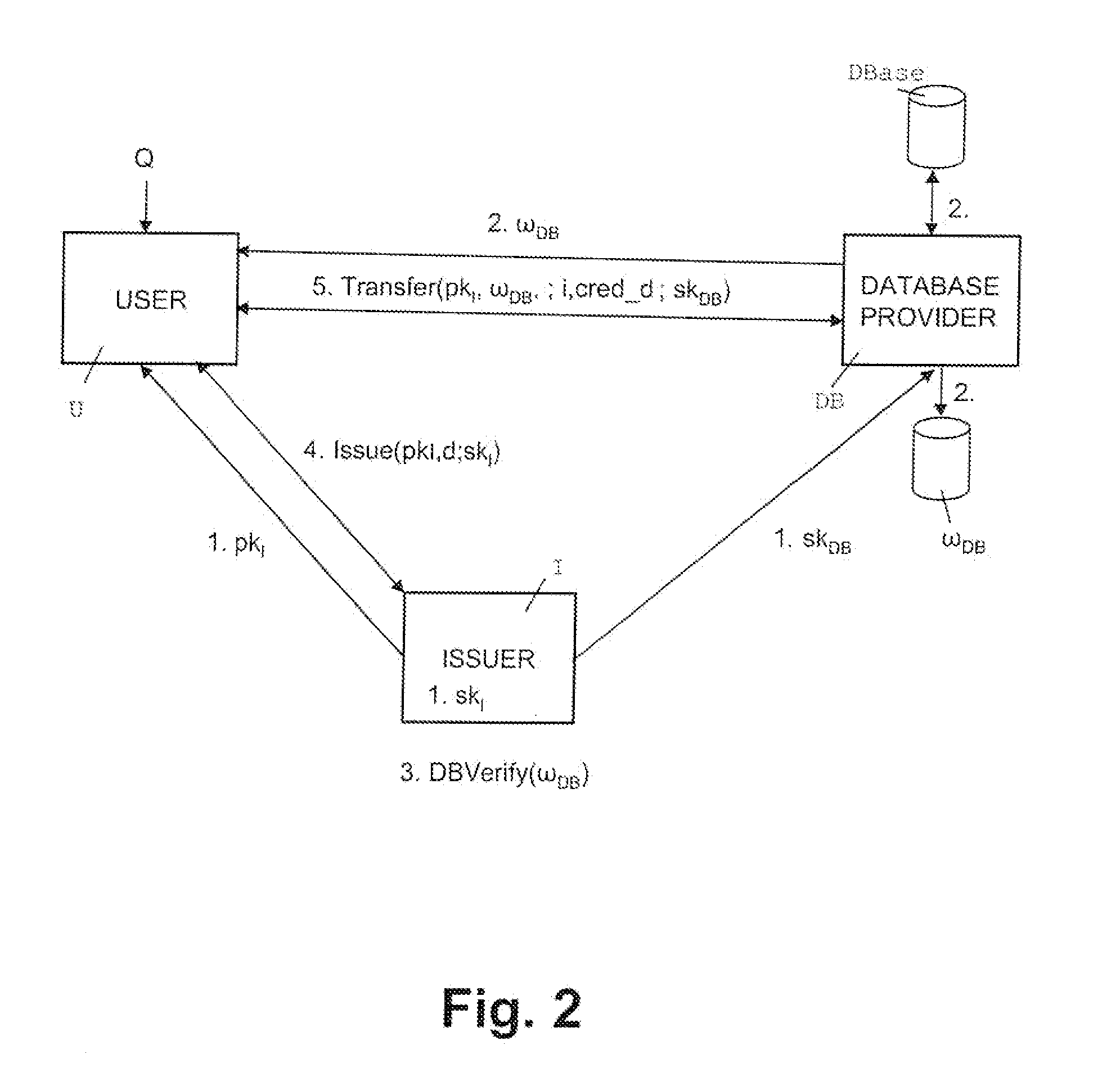
A method, apparatus, and a computer readable storage medium having computer readable instructions to carry out the steps of the method for anonymous access to a database. Each record of the database has different access control permissions (e.g. attributes, roles, or rights). The method allows users to access the database record while the database does not learn who queries a record. The database does not know which record is being queried: (i) the access control list of that record or (ii) whether a user's attempt to access a record had been successful. The user can only obtain a single record per query and only those records for which he has the correct permissions. The user does not learn any other information about the database structure and the access control lists other than whether he was granted access to the queried record, and if so, the content of the record.
Owner:IBM CORP
Resource access control
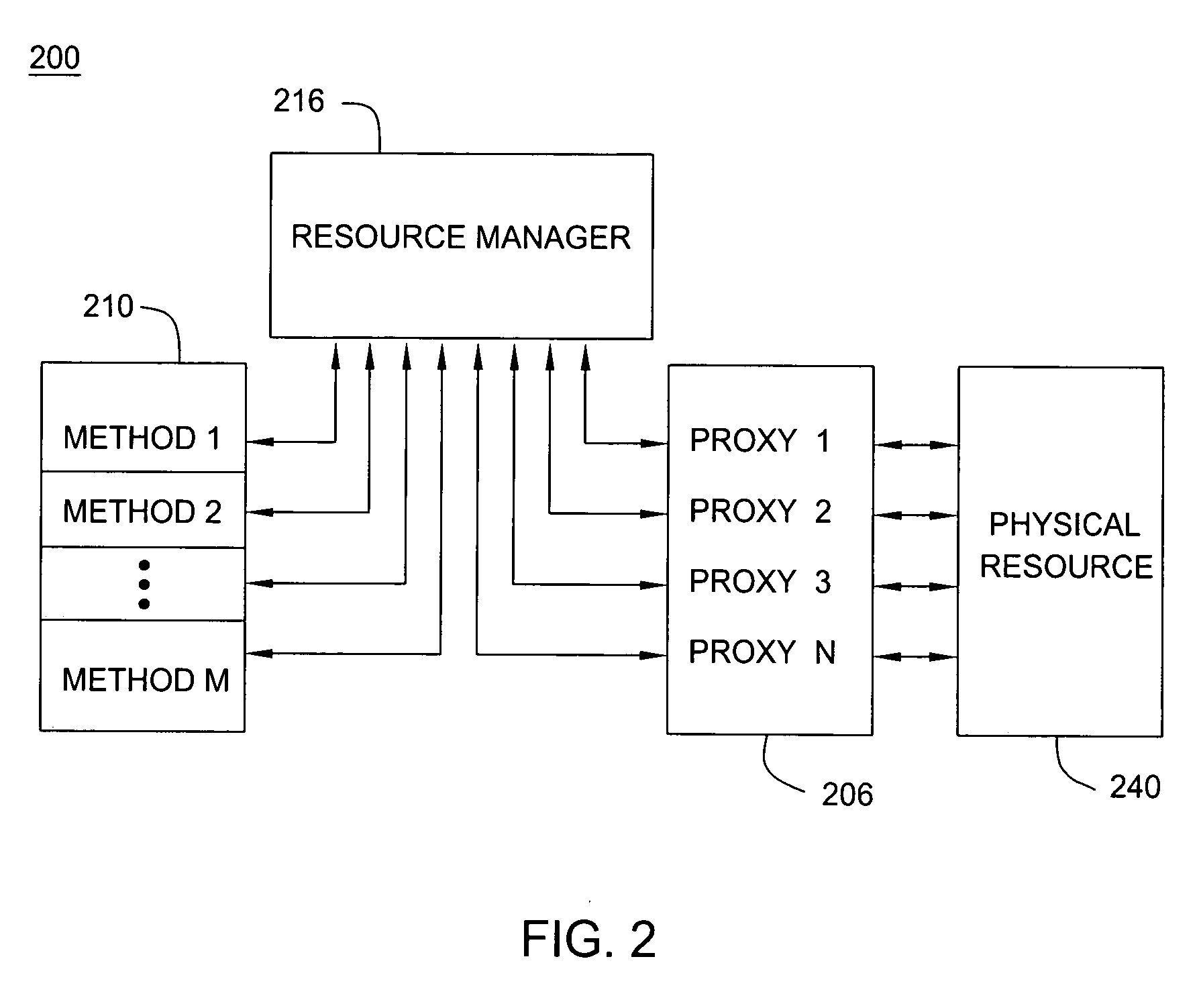
ActiveUS20060174333A1Digital data processing detailsUser identity/authority verificationControl systemResource management
A method and apparatus for enabling multiple application programs to control a system's physical resources by way of multiple resource proxies, while still enabling exclusive control of the physical resource by one application program. Control tokens are used to limit control to one proxy. The proxy having the control token is tracked in an access control list. Java API methods that can alter the state of a physical resource are marked with an access control attribute during grinding. A resource management module intercepts API methods attempting to obtain control of the physical resource. If a proxy controlled by the application program invoking the intercepted method has control the method is allowed to use the proxy to control the physical resource.
Owner:COMCAST CABLE COMM MANAGEMENT LLC
Variable domain resource data security for data processing systems
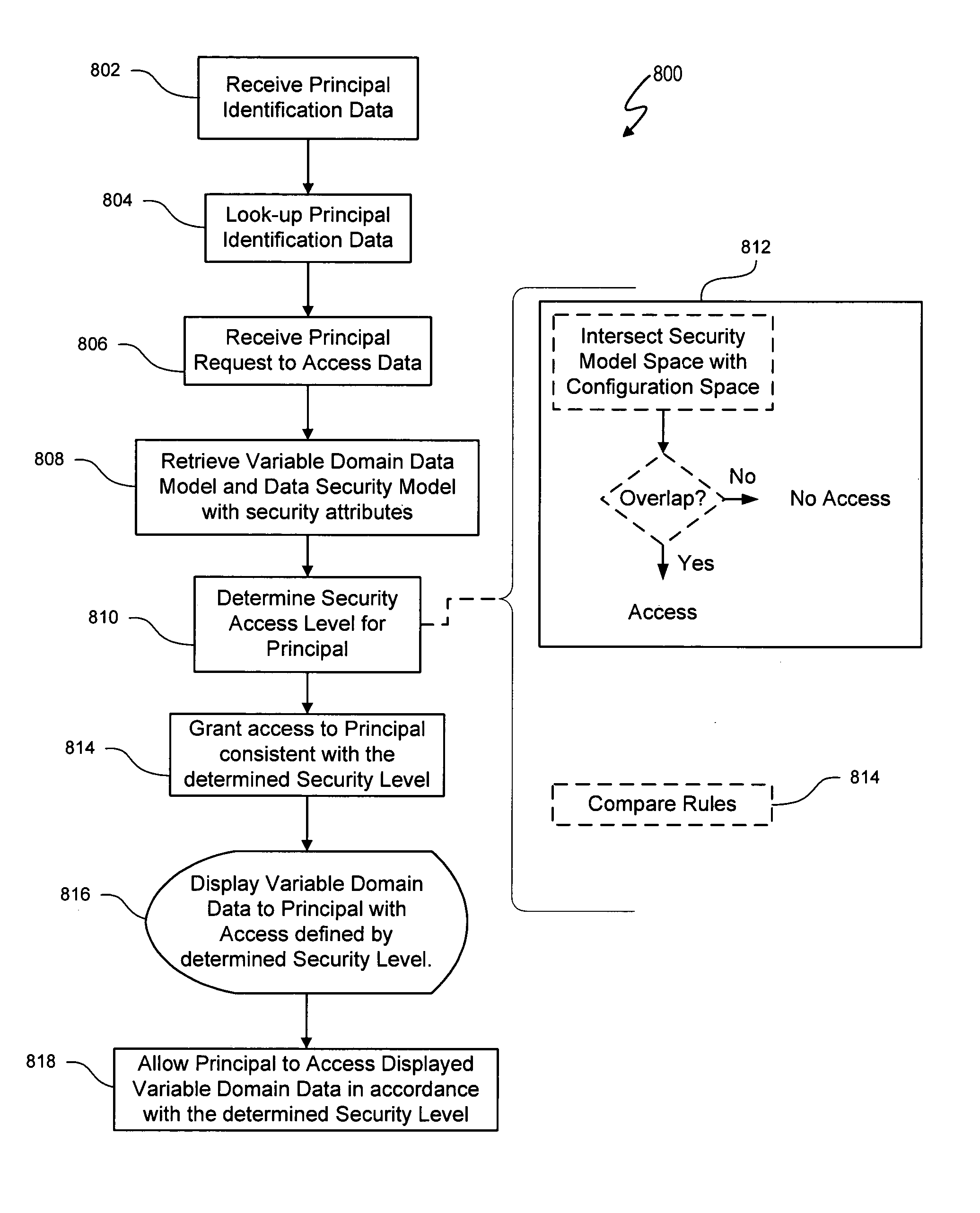
ActiveUS8590011B1Digital data processing detailsMultiple digital computer combinationsData processing systemData access control
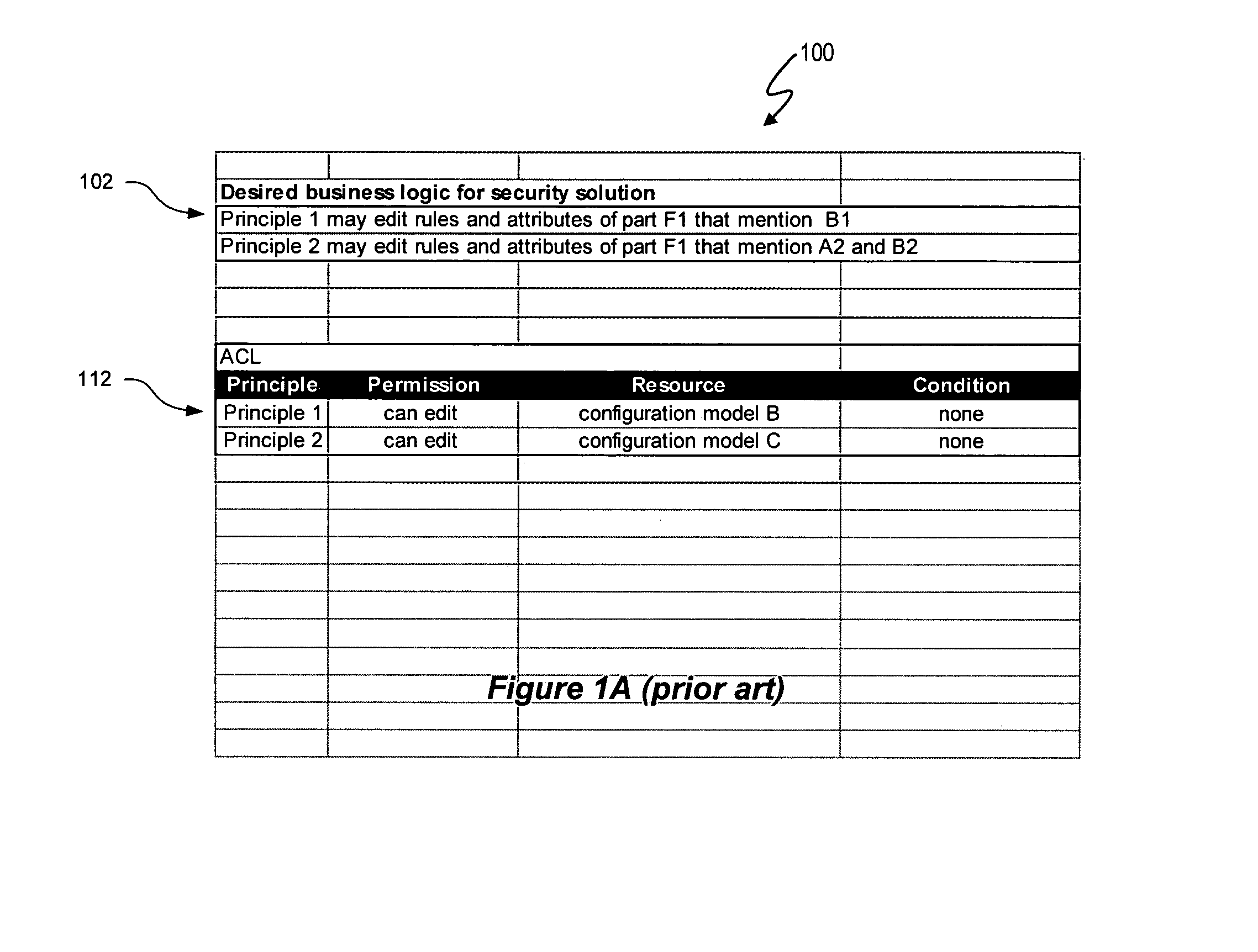
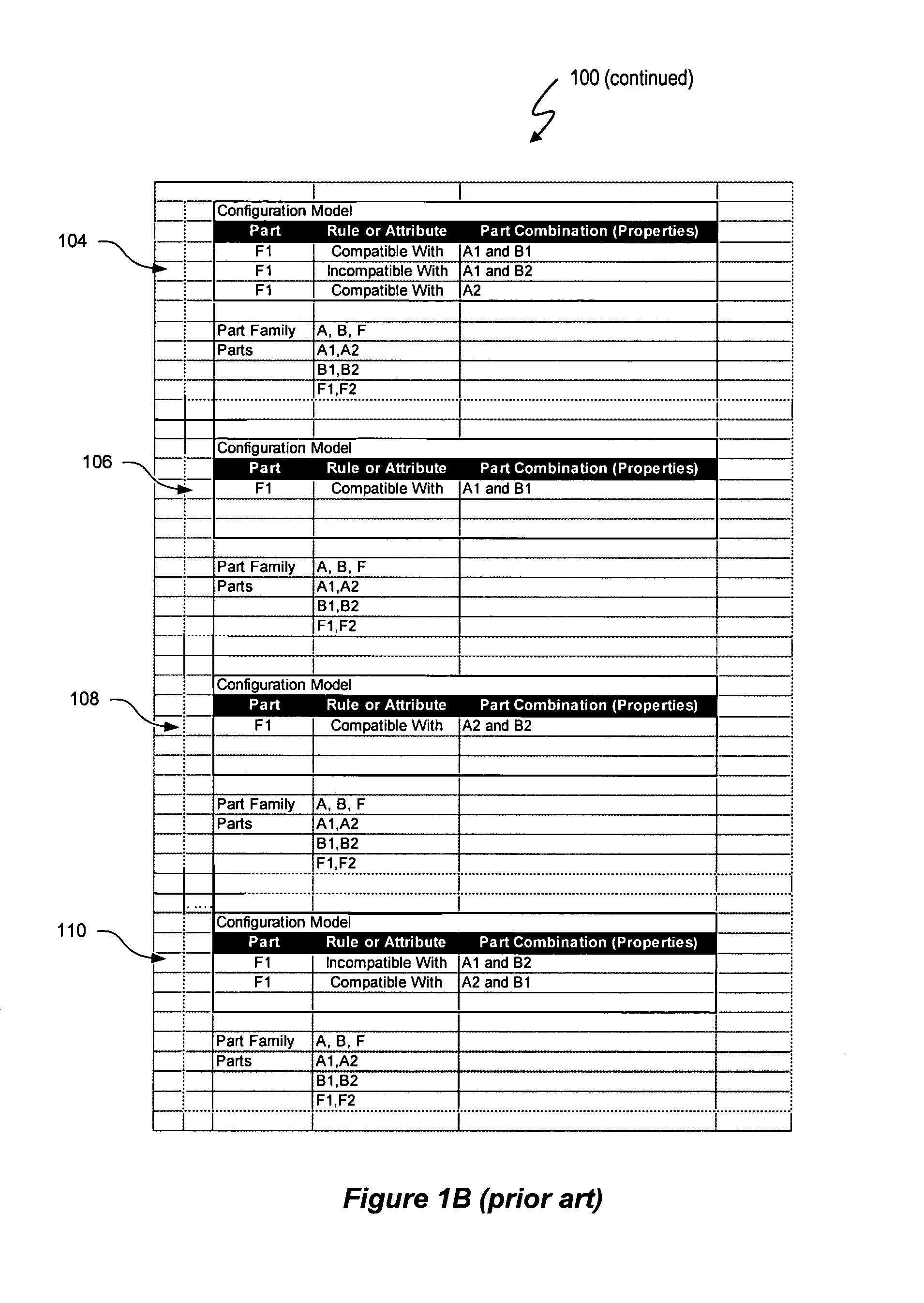
The variable domain data access control system and method described herein use the same variable domain to describe a data security model and a variable domain data model, such as a product configuration model. A variable domain is a set of resource data that can be described using a logical relationship data structure. The variable domain utilizes logical relationship expressions, such as a Boolean logic language, to define resource data in terms of parts, rules and / or attributes, and any other property that can be accessed for viewing, manipulation, or other purposes. The data security model represents an access control list (ACL) that includes security attributes as resource data and uses the same data structure and logical relationship expressions as an associated variable domain data model. An application, such as a configuration engine, can be used to create controlled access to the variable domain data model using the data security model.
Owner:VERSATA DEV GROUP
Failure positioning method and associated equipment
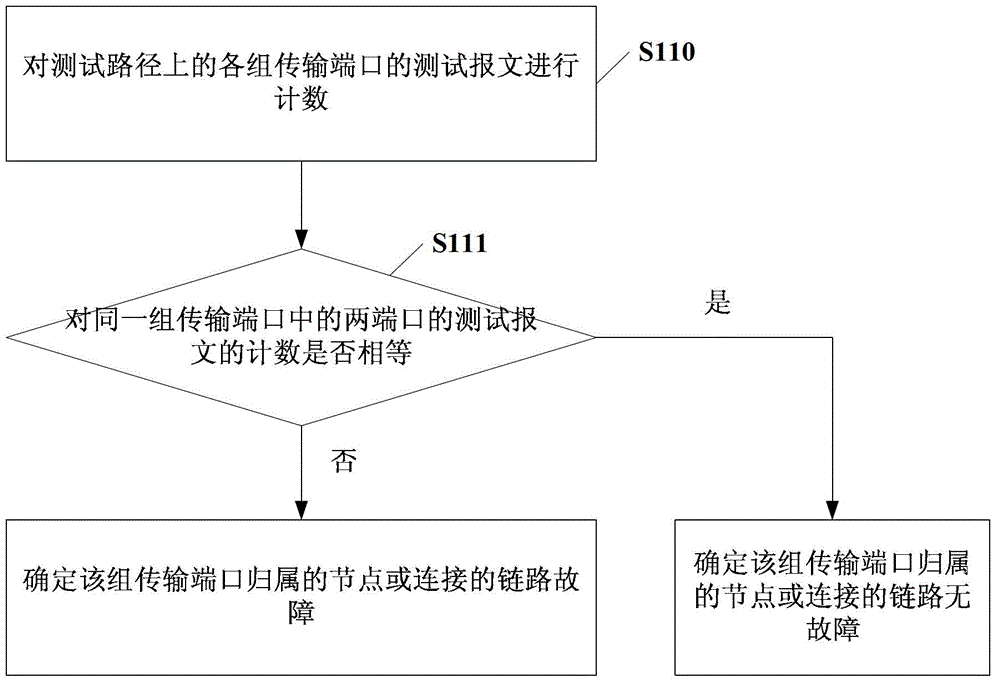
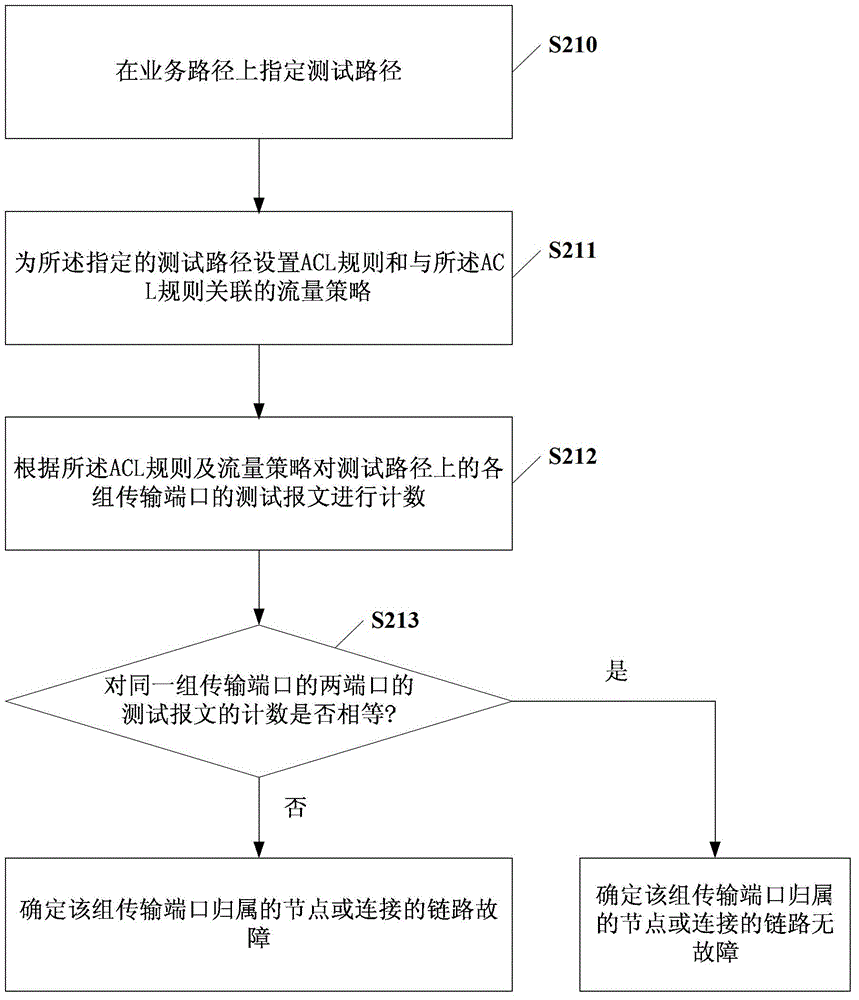
The embodiment of the invention discloses a failure positioning method and associated equipment. The failure positioning method comprises the following steps of: counting test messages of each group of transmission ports in a test path according to a preset access control list (ACL) rule and a flow policy, wherein the flow policy comprises classification identifiers of the test messages; judging whether the quantity of the test messages of two ports in each group of transmission ports is equal according to a counting result; and if the quantity of the test messages of the two ports in each group of transmission ports is unequal, determining the failures of attribution nodes or connecting links of the group of transmission ports. By the embodiment of the invention, the failures can be quickly, effectively and accurately positioned.
Owner:HUAWEI TECH CO LTD
Network device and its access control method
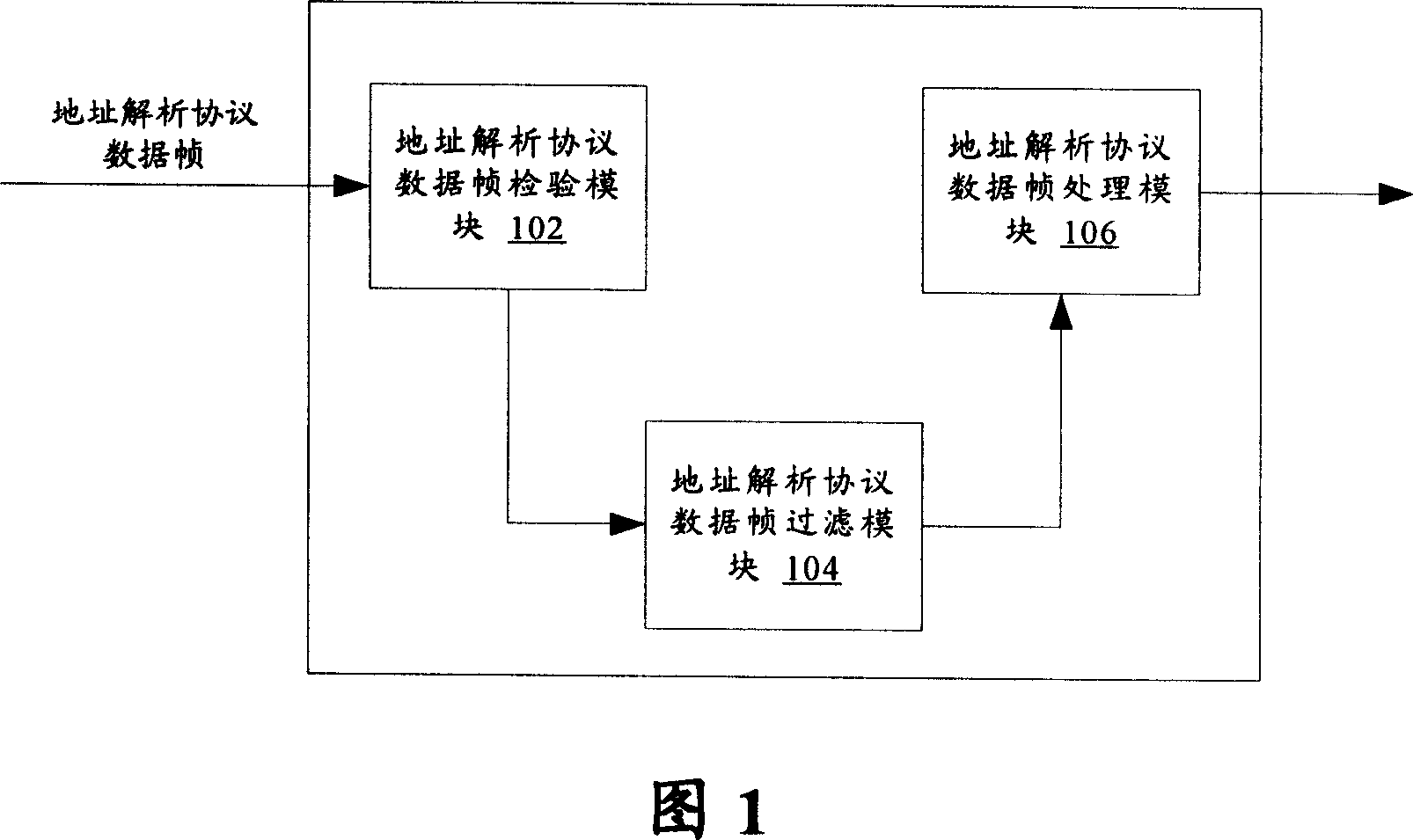
InactiveCN101056306AImprove securityAvoid the problem of occupying too many resources of network equipmentTransmissionAddress Resolution ProtocolVLAN access control list
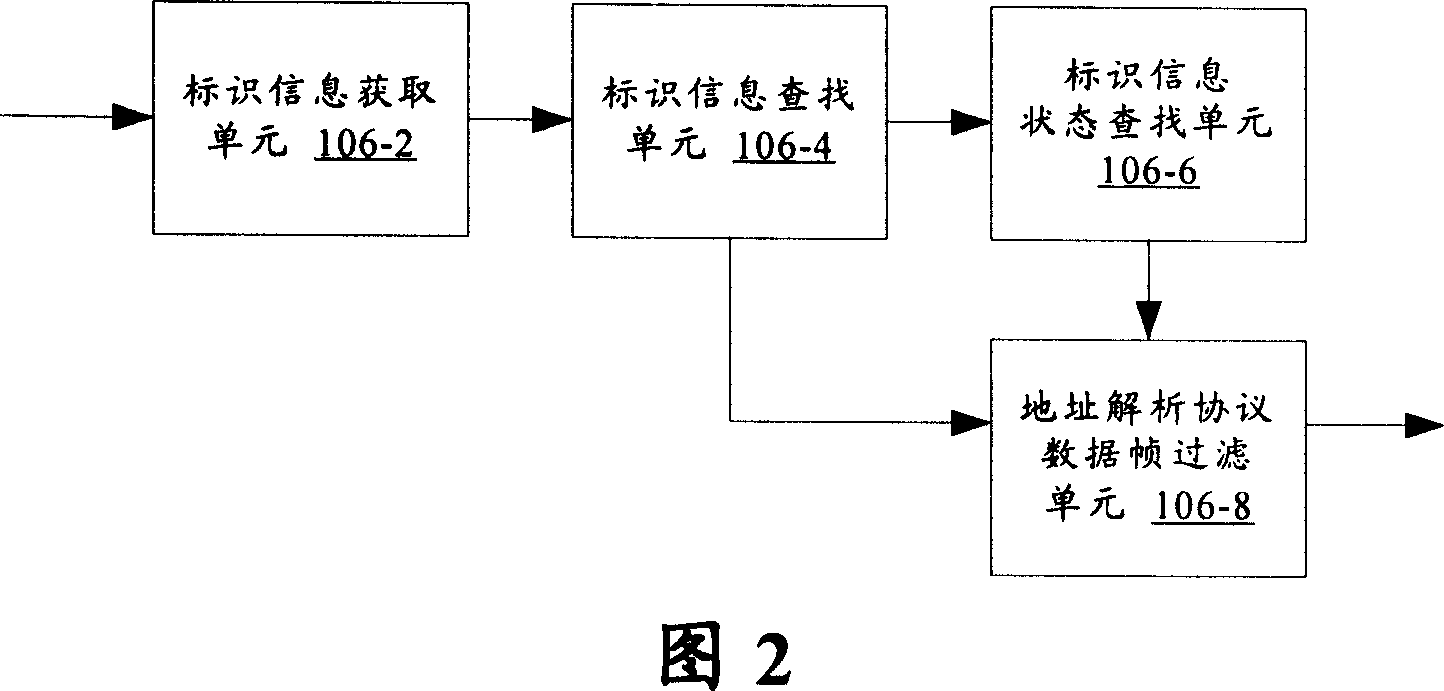
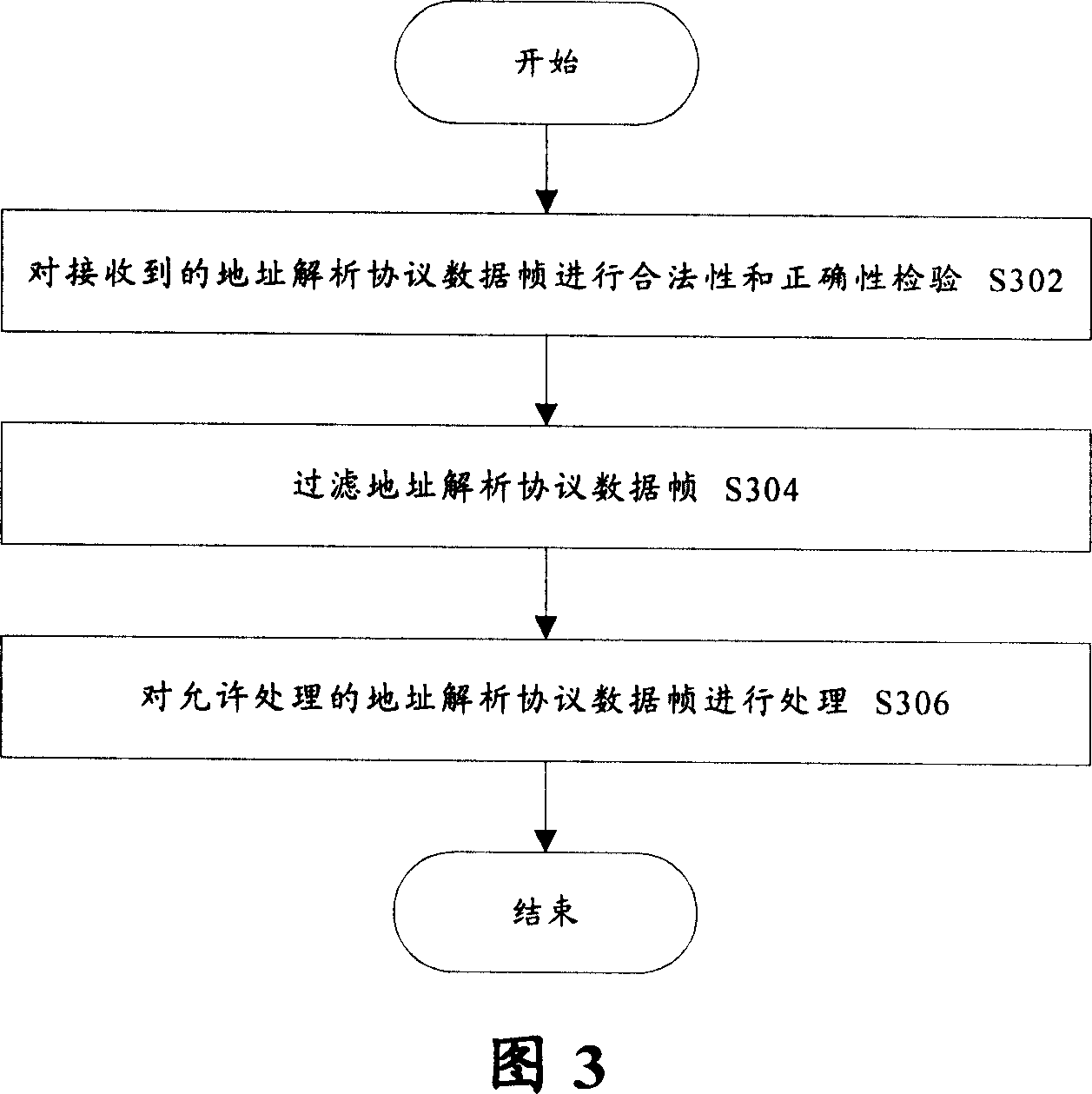
The present invention provides a network equipment and its access control methods. Said network equipment comprises an address resolution protocol (ARP) data frame filter module which is used for searching for access control list on the basis of identification information in the address resolution protocol data frames received by the network equipment, and filtrating the address resolution protocol data frames according to the corresponding states of the identification information in the access control list. Said network equipment comprises further an address resolution protocol (ARP) data frame inspection module which is used for inspecting the validity and correctness of the address resolution protocol data frames before the address resolution protocol data frame filter module filtrates the address resolution protocol data frames; and an address resolution protocol (ARP) data frame treatment module which is used for dealing with the address resolution protocol data frames permited by the address resolution protocol (ARP) data frame filter module. The present invention is capable of preventing an illegal equipment attacking viciously network equipments through address resolution protocol data frames, with improved security and reliability.
Owner:ZTE CORP
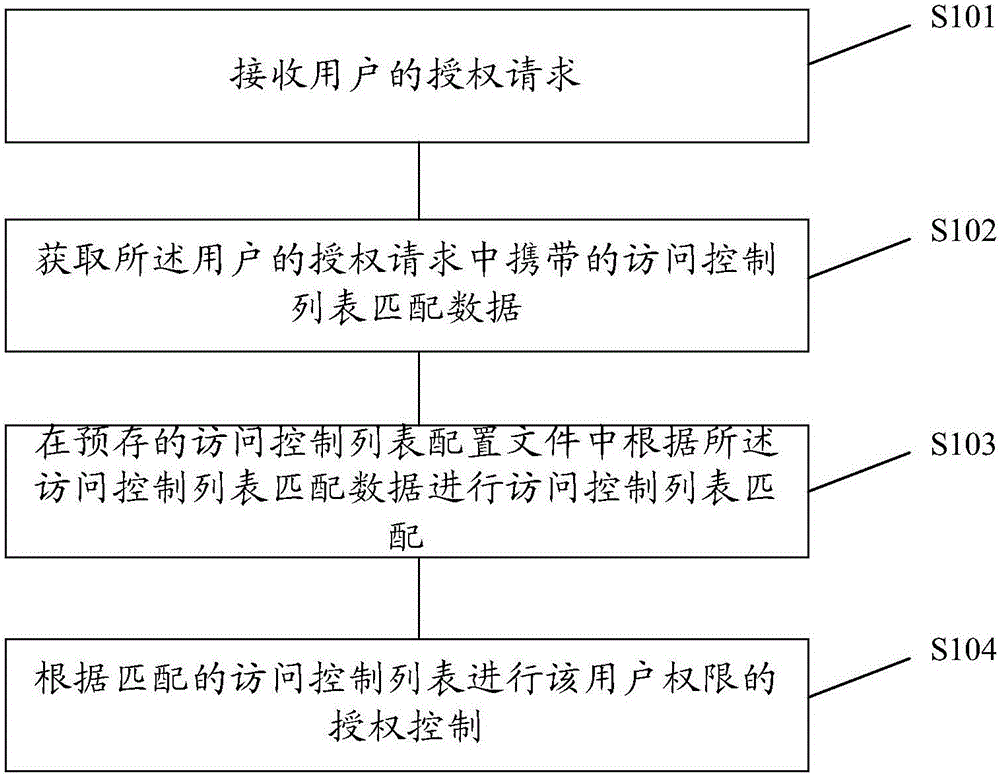
Service management system, user authority control method and system
The present invention provides a business management system, a user authority control method and system, which receive the user's authorization request; obtain the access control list matching data carried in the user's authorization request; The access control list matching data is used for access control list matching; the authorization control of the user authority is performed according to the matched access control list, and when the granularity of the user authority control needs to be changed, the definition of the corresponding access control list type element can be extended Achievable, you can conveniently implement finer-grained user authority control, and when you need to expand user authority control data, you only need to modify the access control list configuration file, which is more convenient for expansion.
Owner:1VERGE INTERNET TECH BEIJING
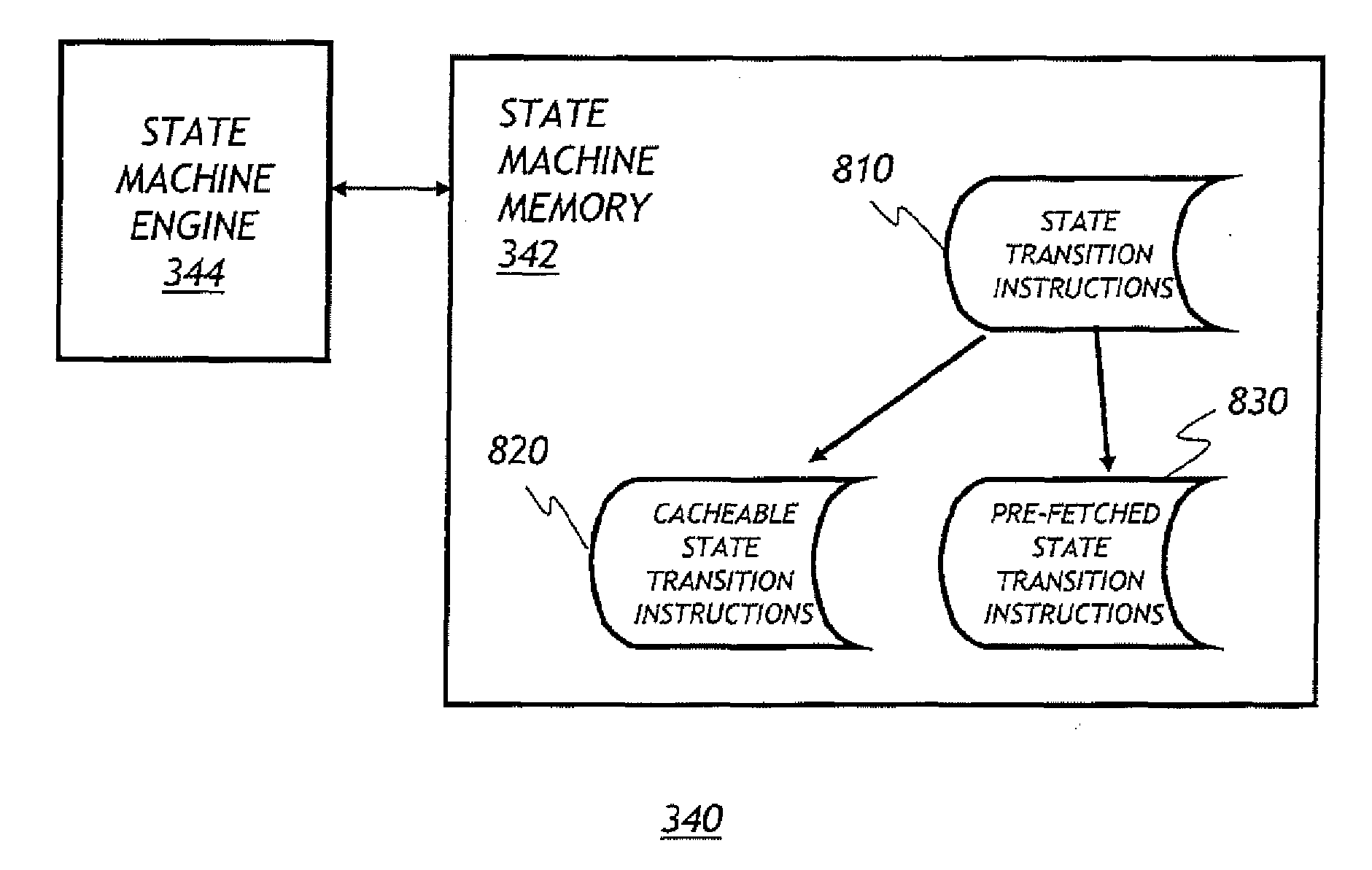
Systems and methods for processing access control lists (ACLS) in network switches using regular expression matching logic
InactiveUS20100217936A1Fast access timeFast read timeOrganic chemistryError preventionTraffic capacityVLAN access control list
A network node, such as an Ethernet switch, is configured to monitor packet traffic using regular expressions corresponding to Access Control List (ACL) rules. In one embodiment, the regular expressions are expressed in the form of a state machine. In one embodiment, as packets are passed through the network node, an access control module accesses the packets and traverses the state machine according to certain qualification content of the packets in order to determine if respective packets should be permitted to pass through the network switch.
Owner:AVAGO TECH INT SALES PTE LTD
NAT method and method for realizing access control list
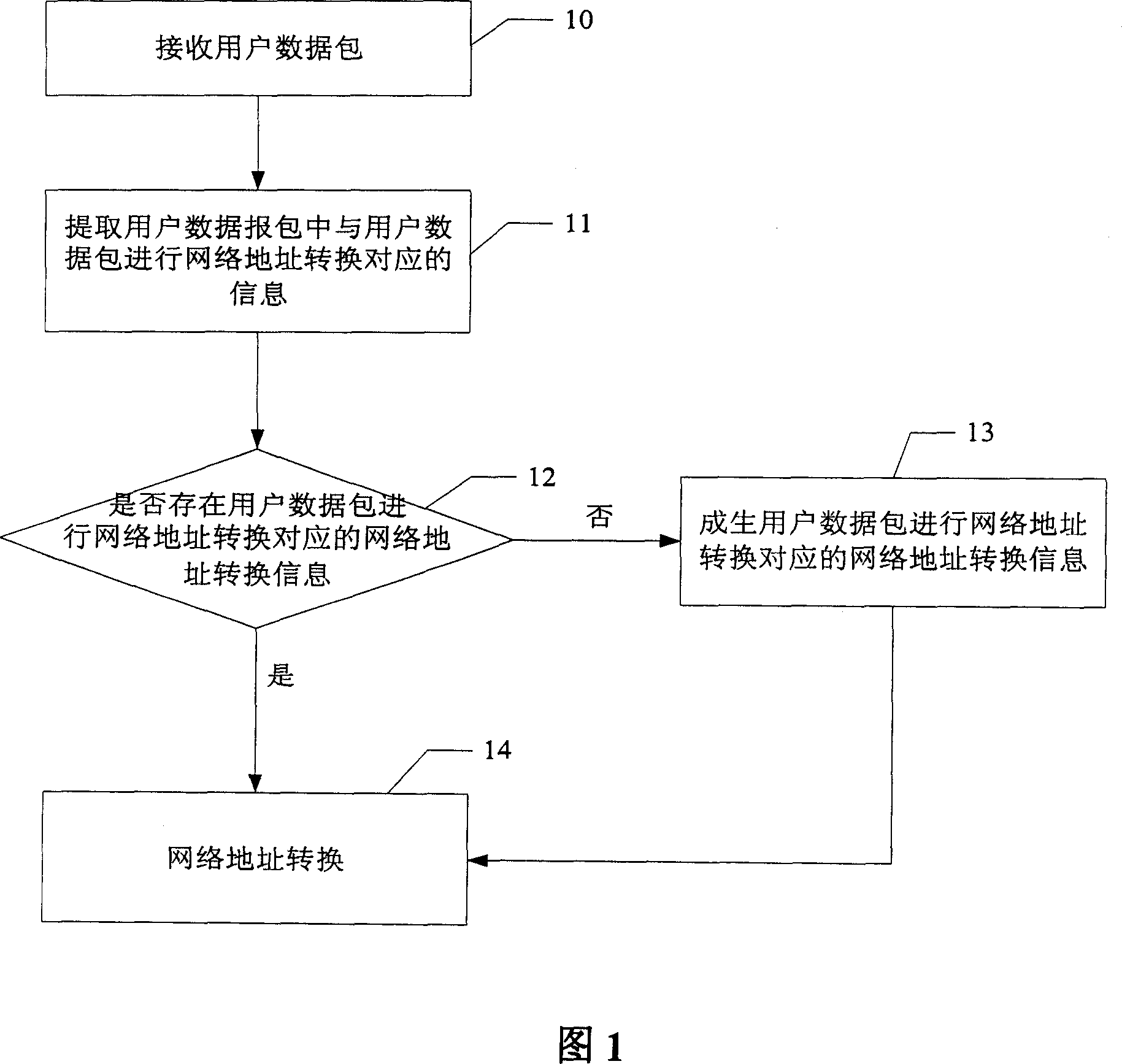
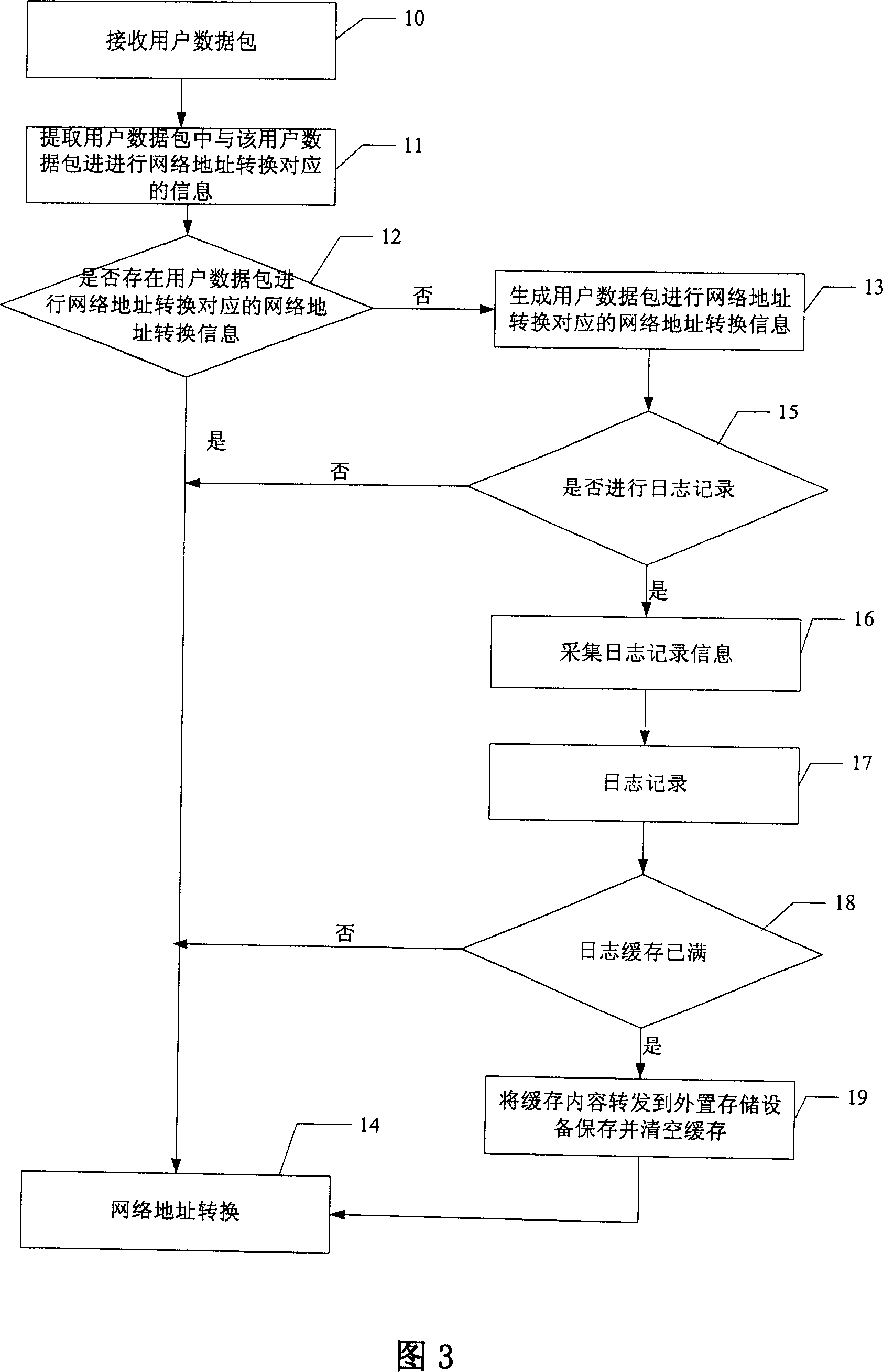
InactiveCN101079798ALow costReduce workloadMultiplex system selection arrangementsData switching networksAccess methodNetwork addressing
The invention discloses a control list conversing and accessing method of network address, which comprises the following steps: A. judging whether network address is conversed into network address conversion information through the user data pack; executing the step C if the judging result is to converse; executing the step B if the result is not to converse; B. generating the user data pack to converse the network address into the network address conversion information; recording the journal; C. conversing the network address of the user data pack according to the network address conversion information corresponding to the user data pack. The invention is convenient for user to access the historical information, on-line and off-line time, which is accurate to judge the attack source and attack time when the network is attached and off-line.
Owner:HUAWEI TECH CO LTD
Method for service matching of messages by means of access control list (ACL)
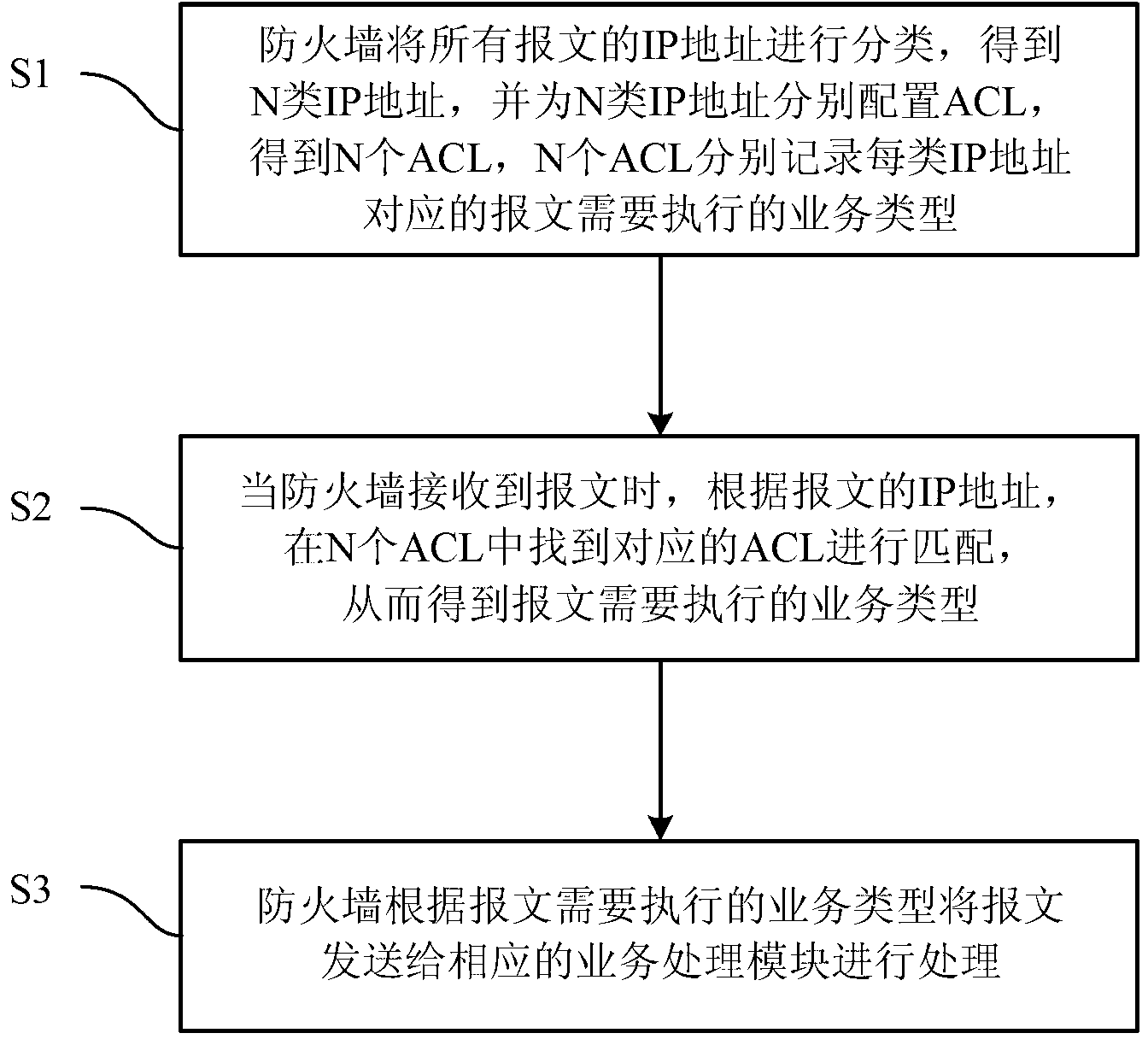
InactiveCN103220287AProcessing speedReduce the number of timesTransmissionIp addressSpeed of processing
The invention relates to a firewall technique, and particularly discloses a method for service matching of messages by means of an access control list (ACL). The method includes that a firewall classifies all IP addresses of the messages, the IP addresses of N types are obtained, the ACL is respectively distributed for the IP addresses of N types, N ACLs are obtained, and the N ACLs respectively record service types which need to be executed by the messages corresponding to the IP address of each type. When receiving the messages, the firewall finds the corresponding ACL in the N ACLs for matching according to the IP addresses of the messages, and therefore the service types which need to be executed by the messages are obtained. The firewall sends the messages to a corresponding service processing module for processing according to the service types which need to be executed by the messages. By means of the technical scheme, when the firewall processes the messages, the ACL needs to be matched only once, and therefore people can know what services the messages need to carry out. By means of the method, the speed of processing the messages is greatly increased.
Owner:OPZOON TECH
Rules engine for access control lists in network units
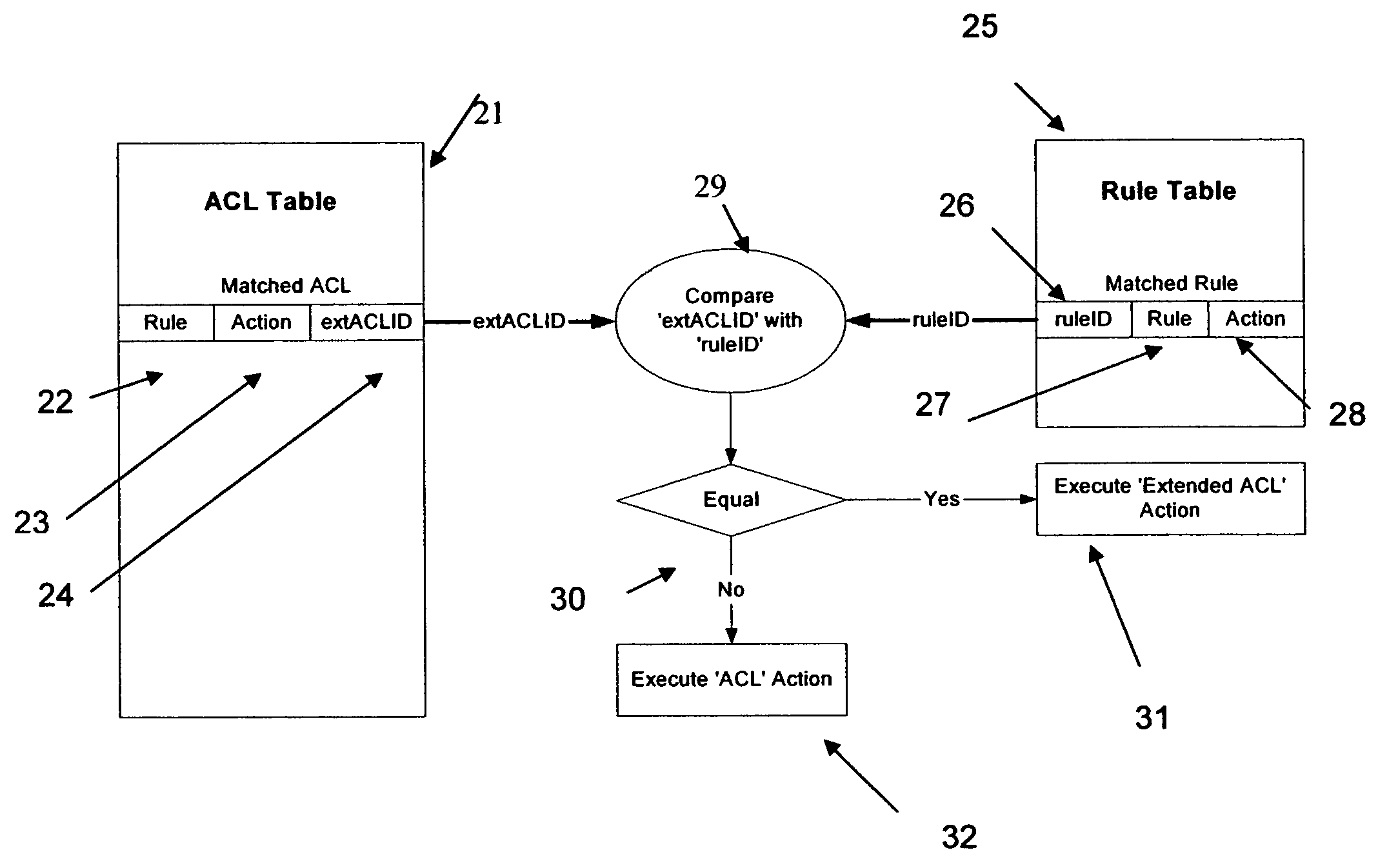
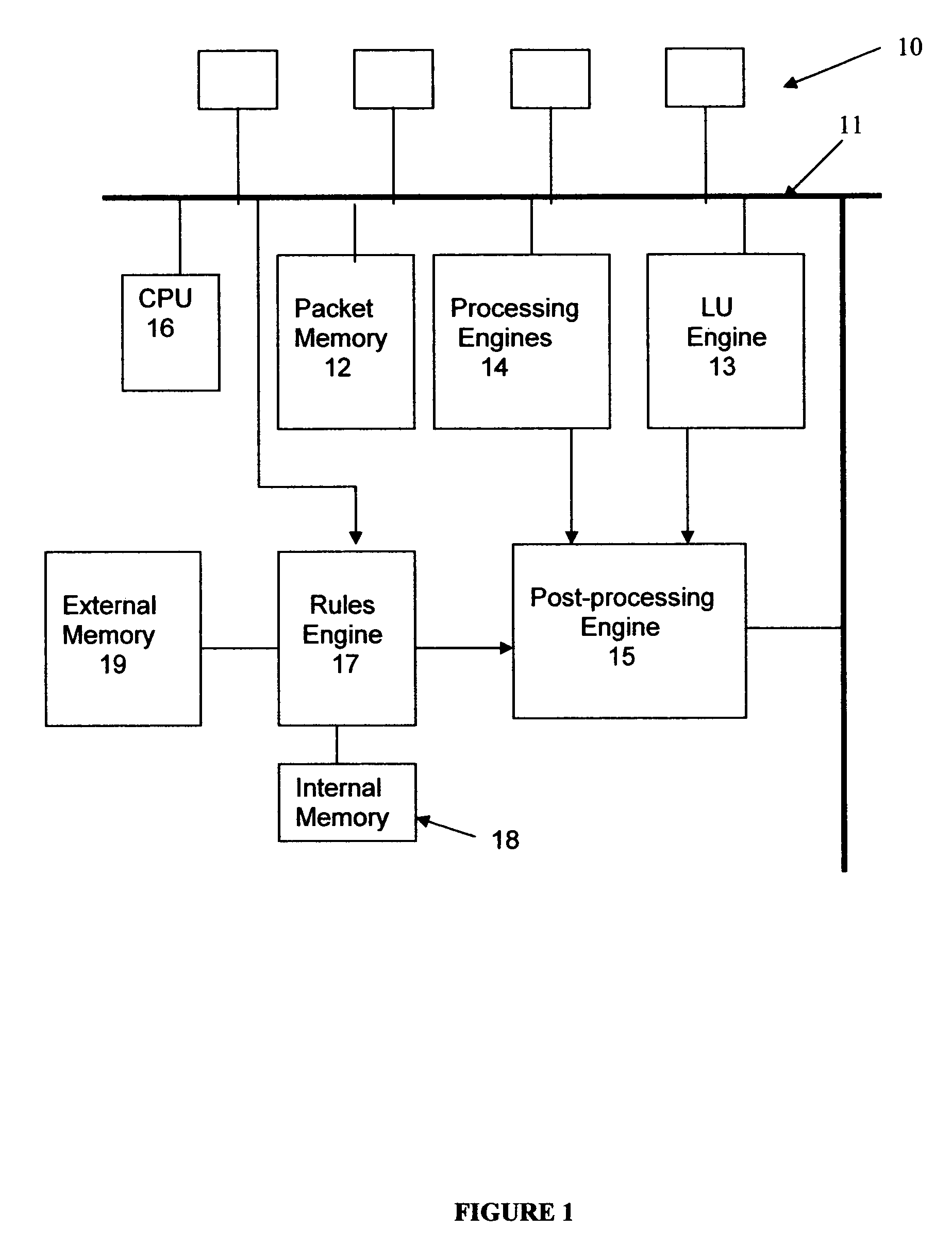
ActiveUS7480299B2Limited spaceUse of access control lists more versatile and efficientDigital data processing detailsData switching by path configurationTransport layerNetwork addressing
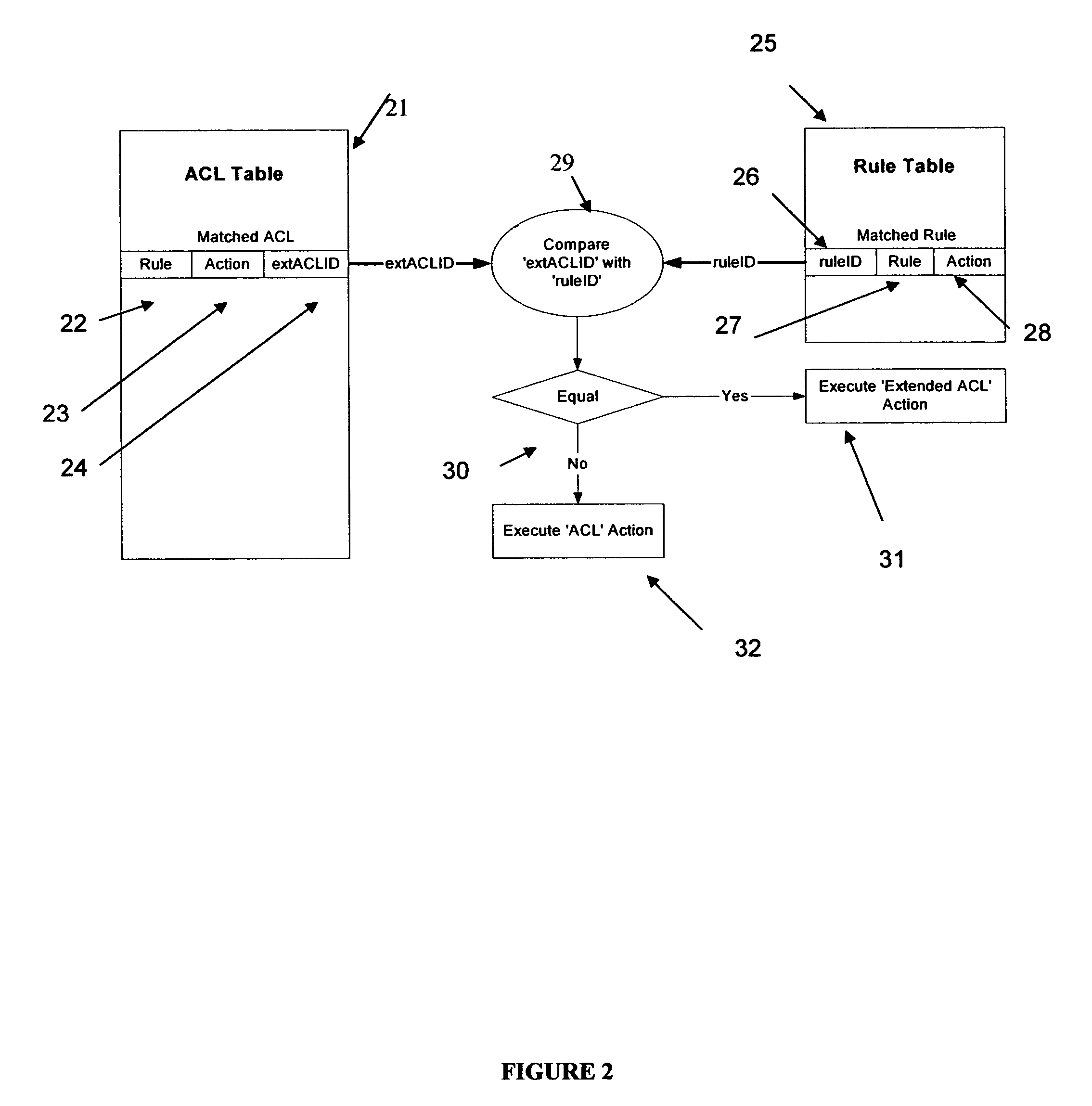
A rules engine for the examination of selected fields in an addressed data packet has an access control list table of which the entries each define an access control list rule, an action and a chain identifier. The access control list rule may be a basic rule which refers to network addresses and transport layer port numbers. The rules engine also has an extension rule table of which the entries each define an extension rule, a respective action and a respective rule identifier. The extension rule may refer to a particular TCP flag. When a packet arrives, the engine searches both tables. This search is made independently of the ordinary network layer or link layer address lookup. If there is a match in both tables, and the chain identifier matches the extension rule identifier, the rules engine prescribes the action associated with the extension rule. If the chain identifier of a matched access control list rule does not match a rule identifier of a matched extension rule the rules engine prescribes the action associated with the basic rule. In the absence of a match with any access control list rule the action on a packet is based on the result from the ordinary address lookup.
Owner:VALTRUS INNOVATIONS LTD +1
Directed graph approach for constructing a tree representation of an access control list
InactiveUS7644085B2Reduce the amount of memoryReduce the amount requiredDigital data processing detailsMultiple digital computer combinationsDirected graphBase function
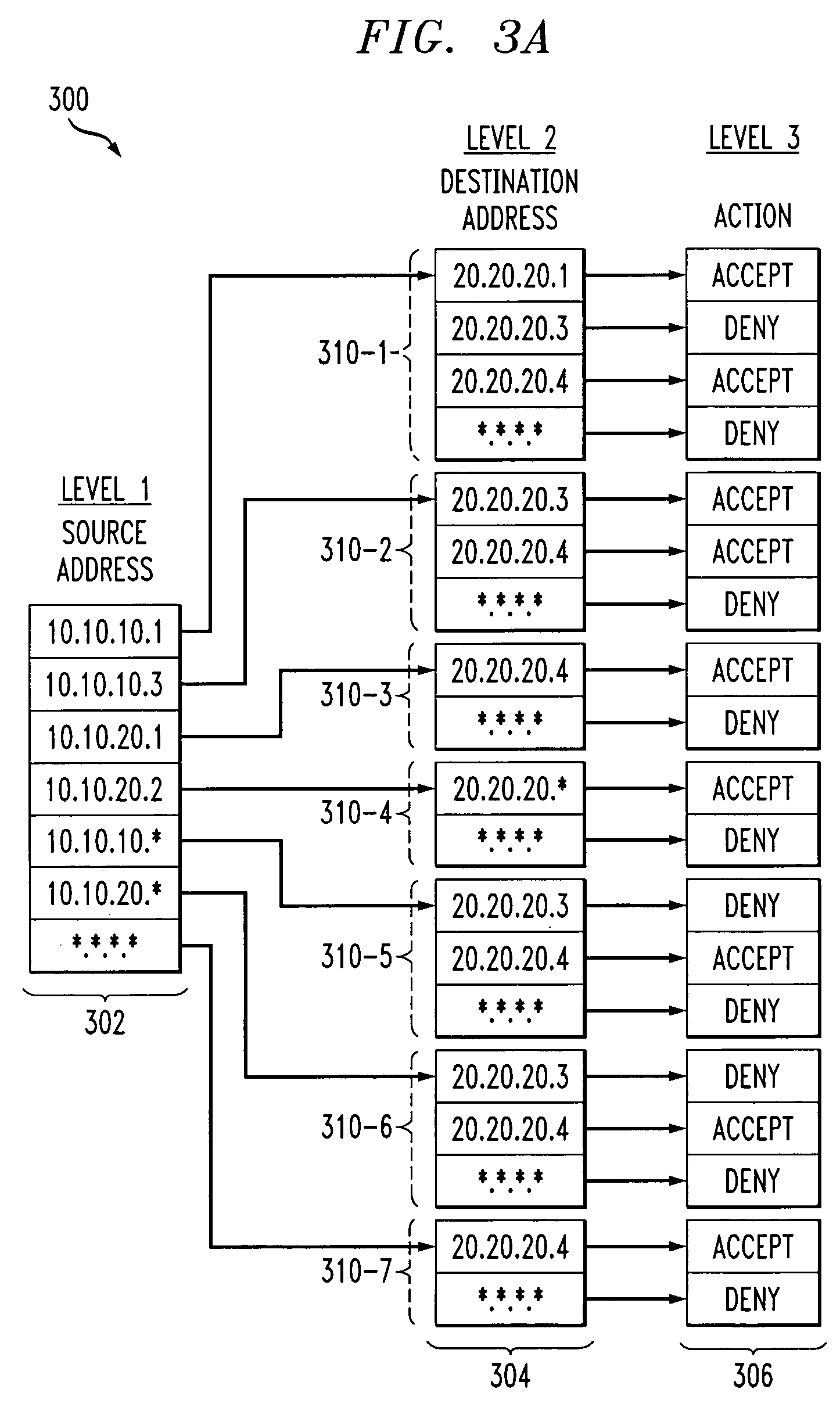
Techniques are disclosed for generating a representation of an access control list, the representation being utilizable in a network processor or other type of processor to perform packet filtering or other type of access control list based function. A plurality of rules of the access control list are determined, each of at least a subset of the rules having a plurality of fields and a corresponding action. The rules are processed to generate a multi-level tree representation of the access control list, in which each of one or more of the levels of the tree representation is associated with a corresponding one of the fields. At least one level of the tree representation comprises a plurality of nodes, with two or more of the nodes of that level having a common subtree, and the tree representation including only a single copy of that subtree. The tree representation is characterizable as a directed graph in which each of the two nodes having the common subtree points to the single copy of the common subtree.
Owner:INTEL CORP
Dynamic access control lists
ActiveUS7623518B2Data switching by path configurationMultiple digital computer combinationsDomain nameIp address
A method controls access of a user to a network including a plurality of hosts coupled together through a network switch. The method includes storing in the network switch an enhanced access control list containing data related to at least one of user names, DNS names, domain names, and physical addresses. A dynamic access control list is generated from the enhanced access control list, with the dynamic access control list containing a plurality of IP addresses that restrict access of the user to the network.
Owner:LIONRA TECH LTD
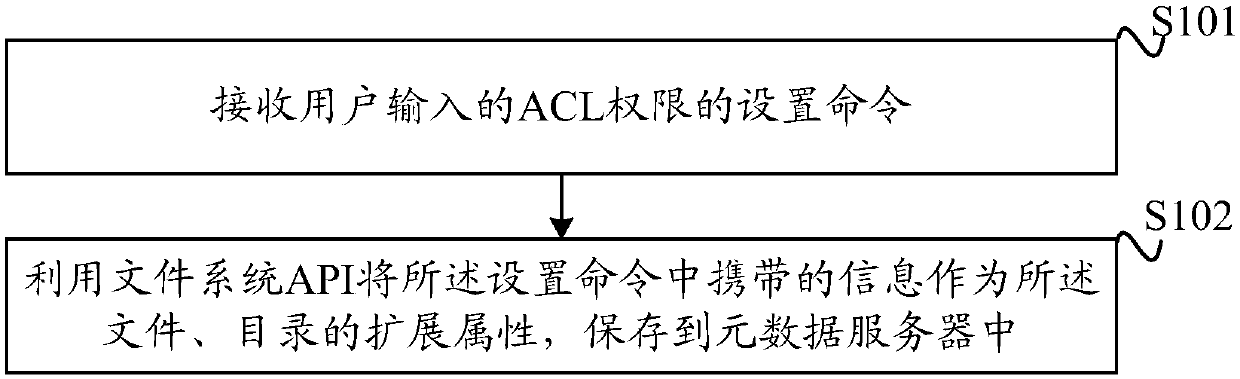
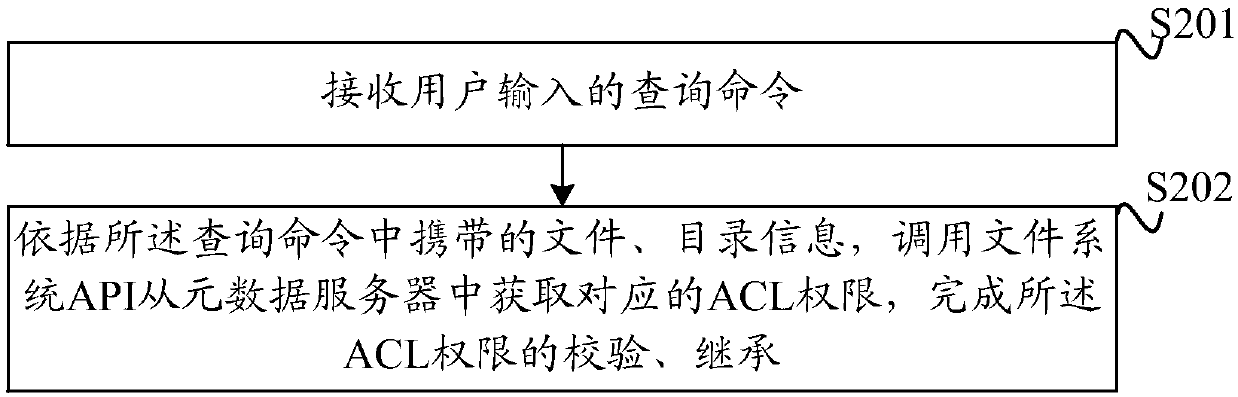
ACL (access control list) authority control method and device
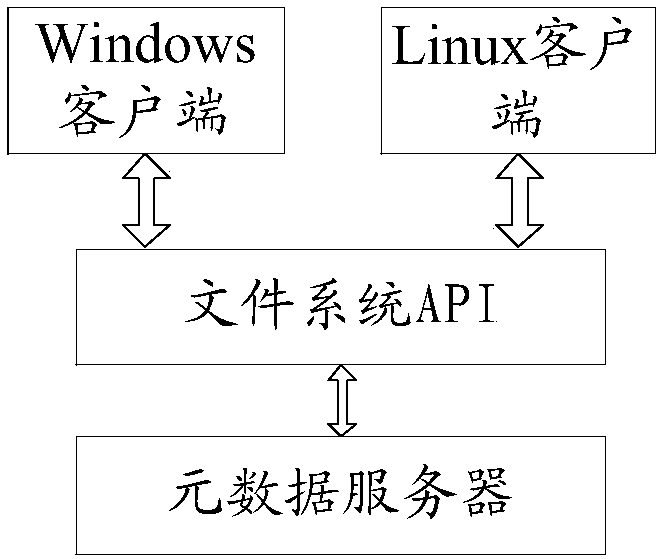
An embodiment of the invention discloses an ACL (access control list) authority control method and device. A user can set ACL authorities of a file and a directory by a Linux client, the set ACL authorities serve as extended attributes of the file and the directory and are stored in a metadata server, and the ACL authorities can include a read authority, a write authority, an execution authority,a deletion authority and a visual authority. A Windows client acquires the corresponding ACL authorities from the metadata server by calling a file system API (application program interface), and theACL authorities are verified and inherited. Based on the read authority, the write authority and the execution authority, the deletion authority and the visual authority are added. Compared with traditional ACL authority control, more advanced user access authority types are provided, diversified demands of enterprise users for data access authorities can be met, and users can control file readingand writing and authority granting capacity.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
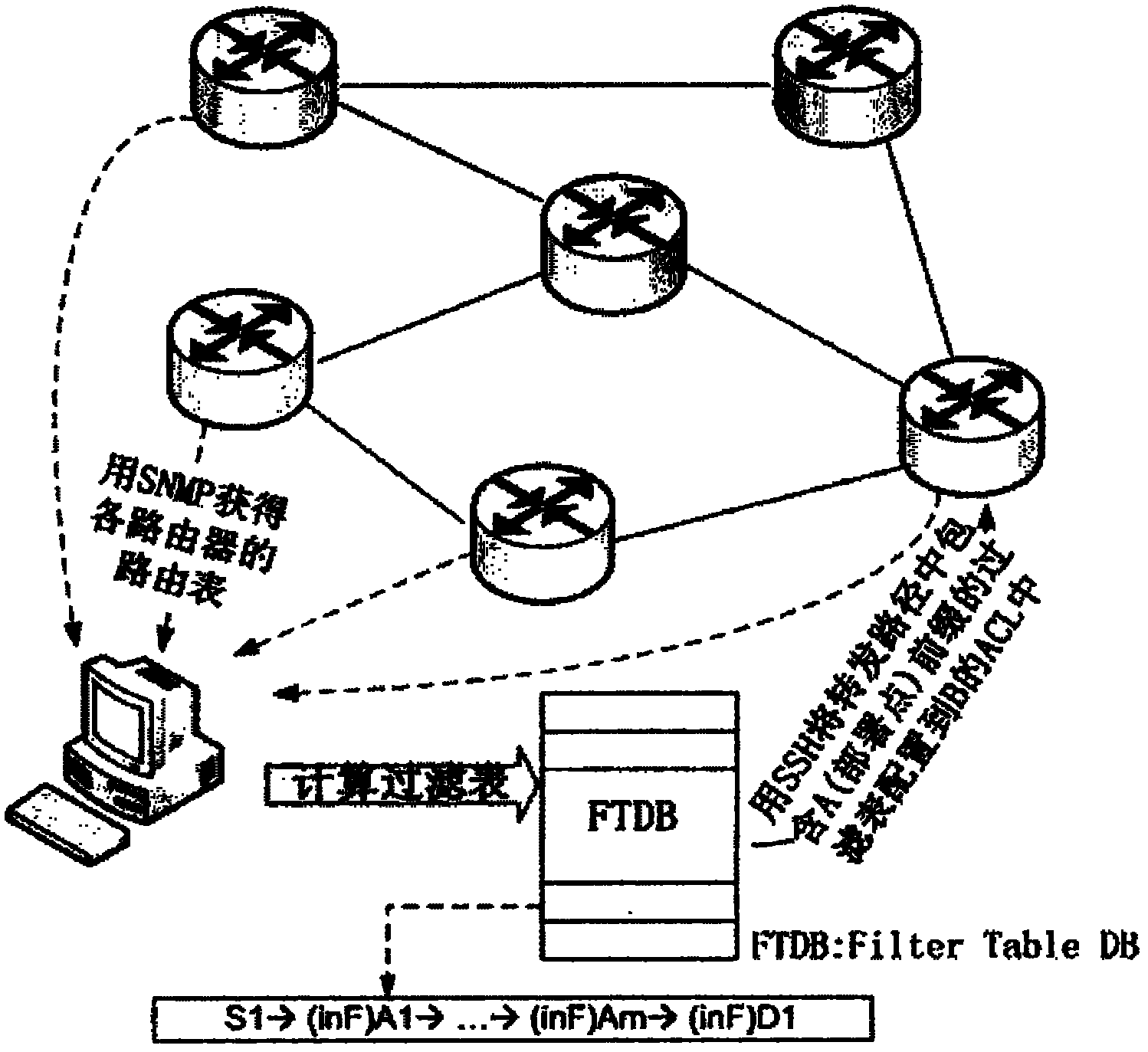
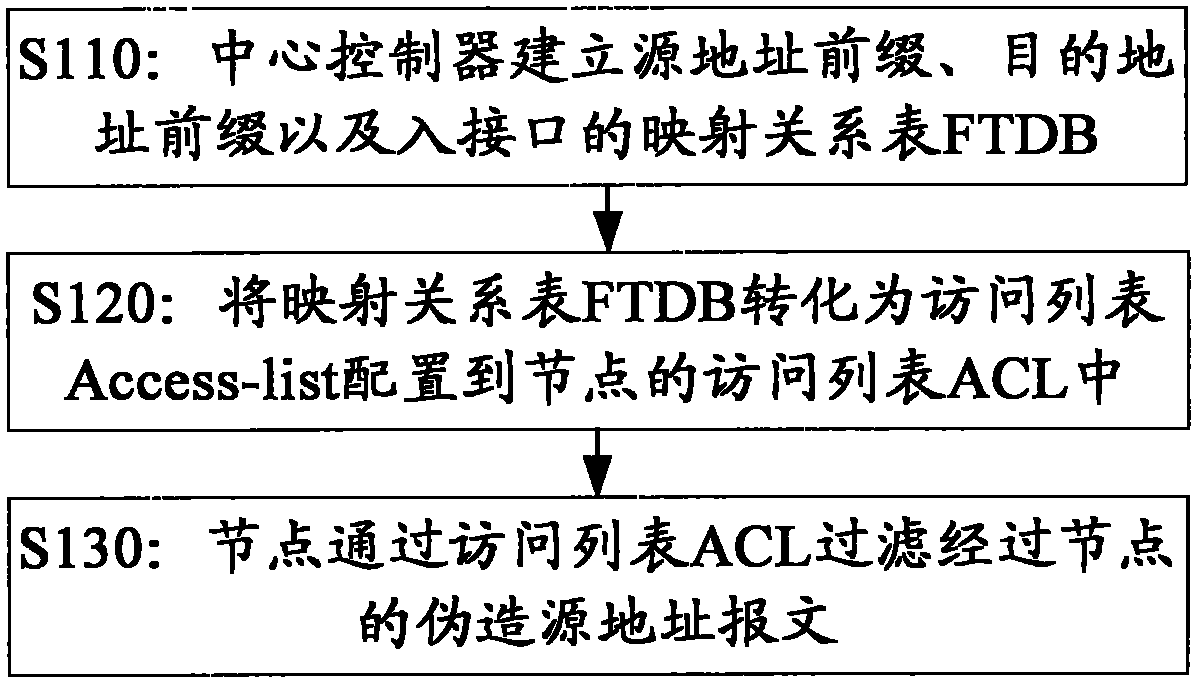
Method for verifying intra-domain Internet protocol (IP) source address
ActiveCN101917434ASolve the verification problemMinor changesData switching networksVLAN access control listRelational table
The embodiment of the invention discloses a method for verifying an intra-domain Internet protocol (IP) source address. The method comprises the following steps of: establishing a prefix of the source address, a prefix of a destination address and a mapping relation table which is called filter database (FTDB) in the invention of an inbound interface by a central controller; converting the mapping relational table which is called filter database (FTDB) in the invention into an access list and configuring the access list in an access control list (ACL) of a node; and filtering a false source address message passing through the node through the ACL by the node. In the scheme provided by the invention, the message is checked and verified by recording the source address, the destination address and an inlet port, so that the problem of the verification of the intra-domain IP source address under the conventional Ipv6 or Ipv4 protocol is solved.
Owner:TSINGHUA UNIV
Method and device for issuing ACL (access control list) items
ActiveCN102857510AAvoid momentary mismatchesAvoid lossData switching networksVLAN access control listWorld Wide Web
The invention provides a method and a device for issuing ACL (access control list) items. The method includes determining target positions of slice where ACL items to be issued; identifying the target positions which are not idled, and looking for idle item positions nearest the target positions in the slice; transferring in a manner of copying action policy items corresponding to the ACL items from an action policy list, then copying the ACL items and deleting original policy items and original ACL items; sequentially transferring the ACL items and the correspondingly policy items one by one from the ACL item nearest the idle item position to the nearest positions of the idle item positions in the above transferring manner until the target positions are idled; and issuing the ACL items to be issued to the target positions.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com