Network device and its access control method
A network equipment and access control technology, applied in the field of communications, can solve the problems of reduced processing capacity, malicious attacks on network equipment, reduced processing capacity of network equipment, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Specific examples according to the present invention will be described below.
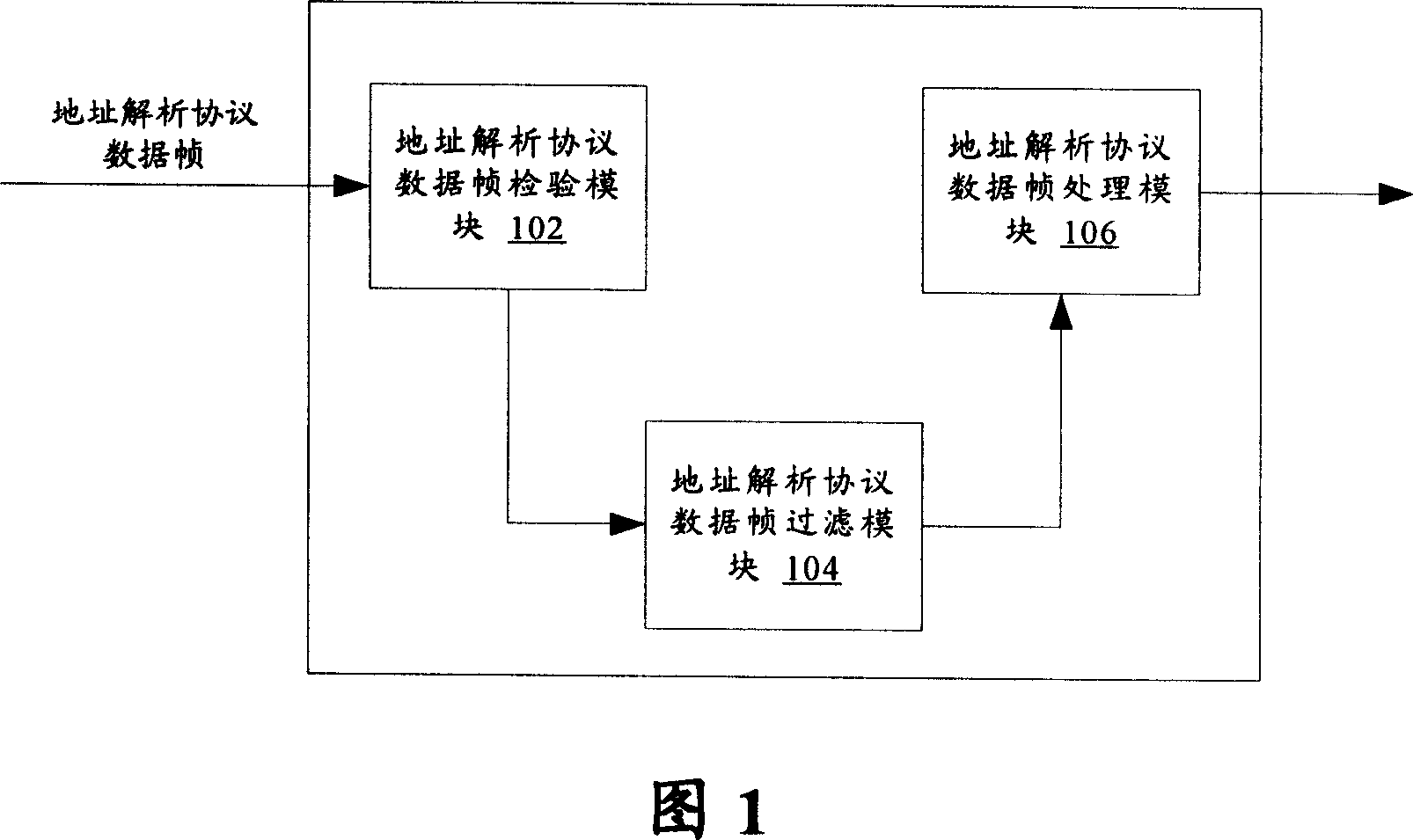
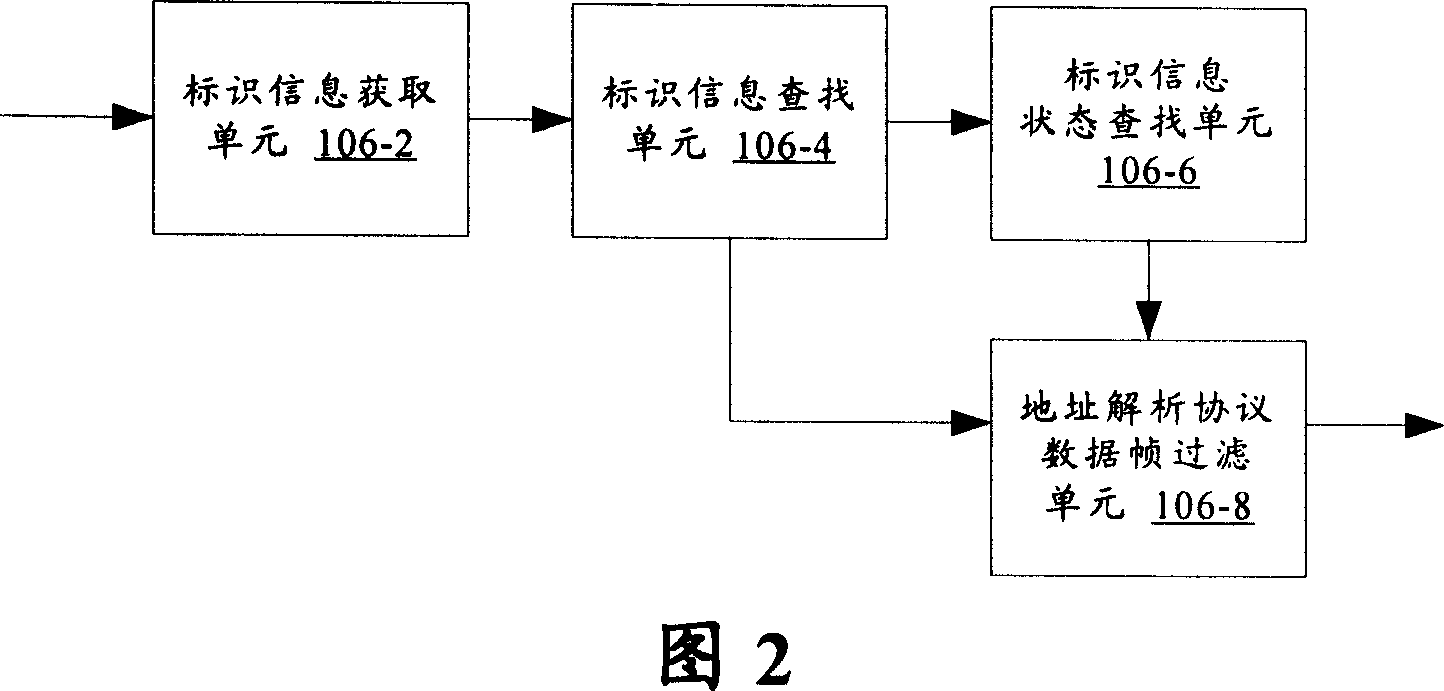
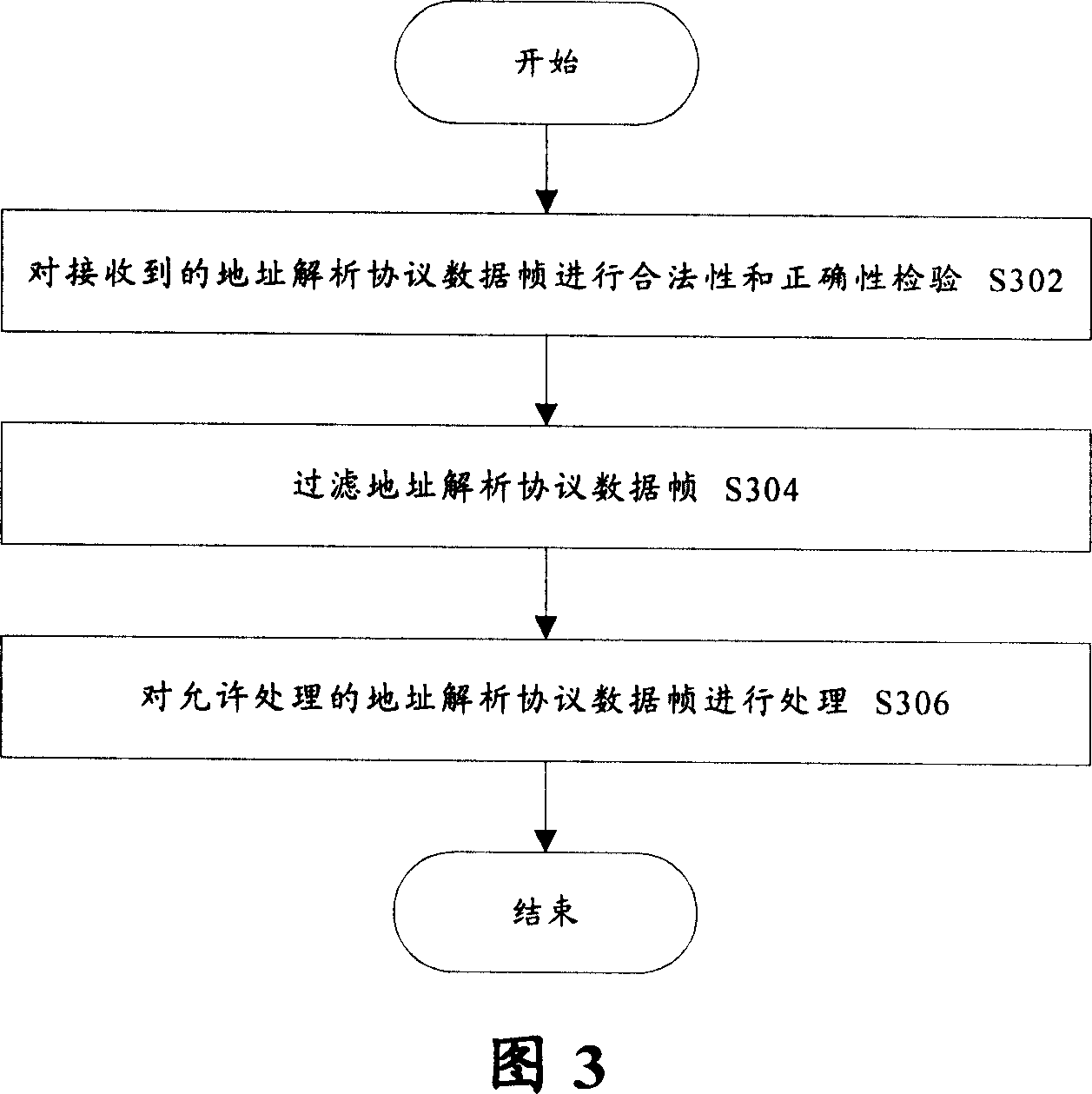
[0031] Fig. 1 is a schematic structural diagram of a network device according to the present invention. As shown in Figure 1, the network equipment according to the present invention has the access control list function based on IP, and this network equipment comprises: ARP data frame filtering module 104, is used for according to the ARP data frame that network equipment receives The identification information searches the access control list, and filters the address resolution protocol data frame according to the status corresponding to the identification information in the access control list. The network device also includes: an address resolution protocol data frame checking module 102, which is used to check the legality and correctness of the address resolution protocol data frame before the address resolution protocol data frame filtering module filters the address resolution protoco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com