Method for intercepting operating of suspicious programs
A program running, suspicious technology, applied in the field of information security, can solve the problem of new Trojan horses not having the ability to detect and kill, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
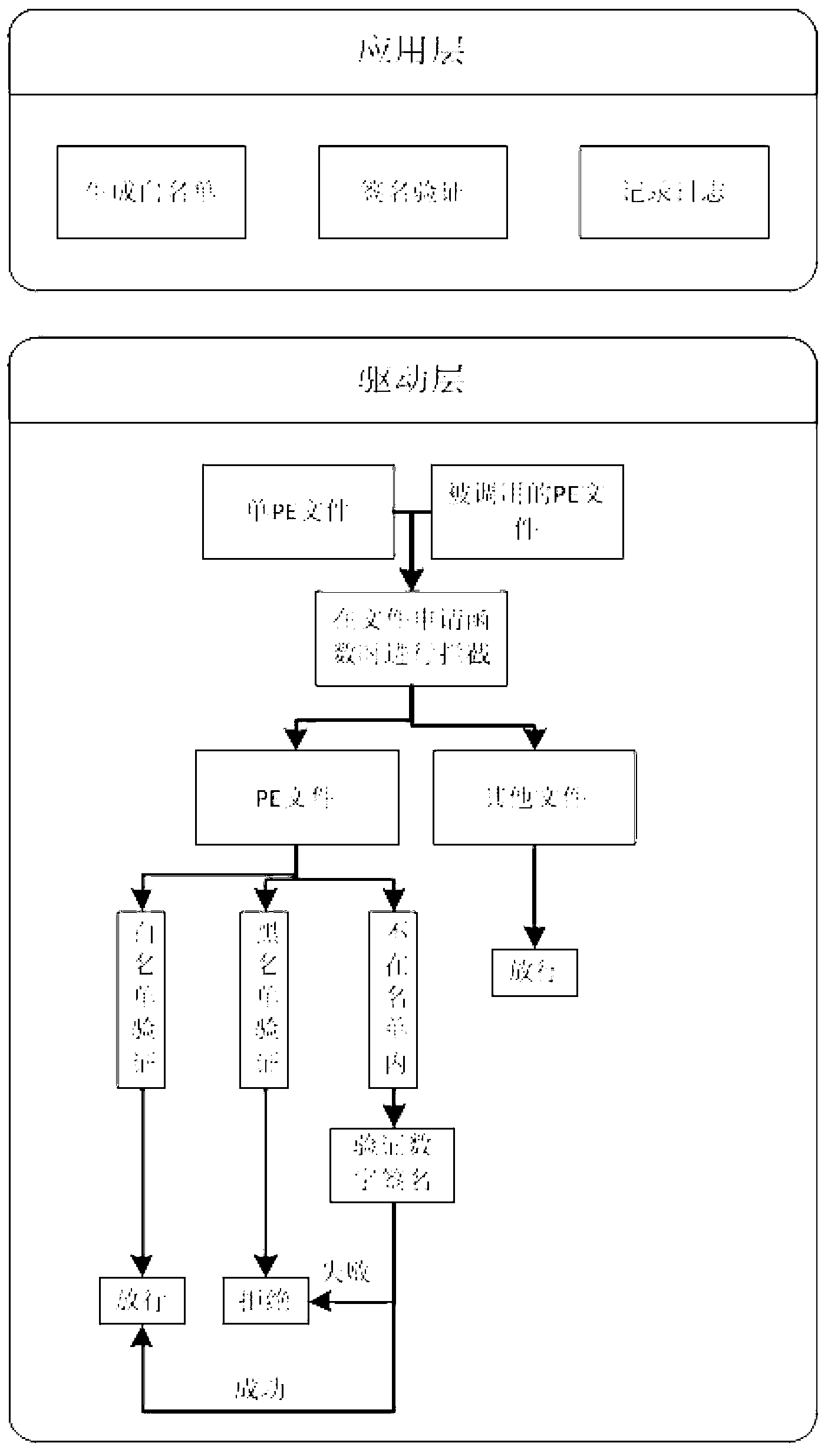
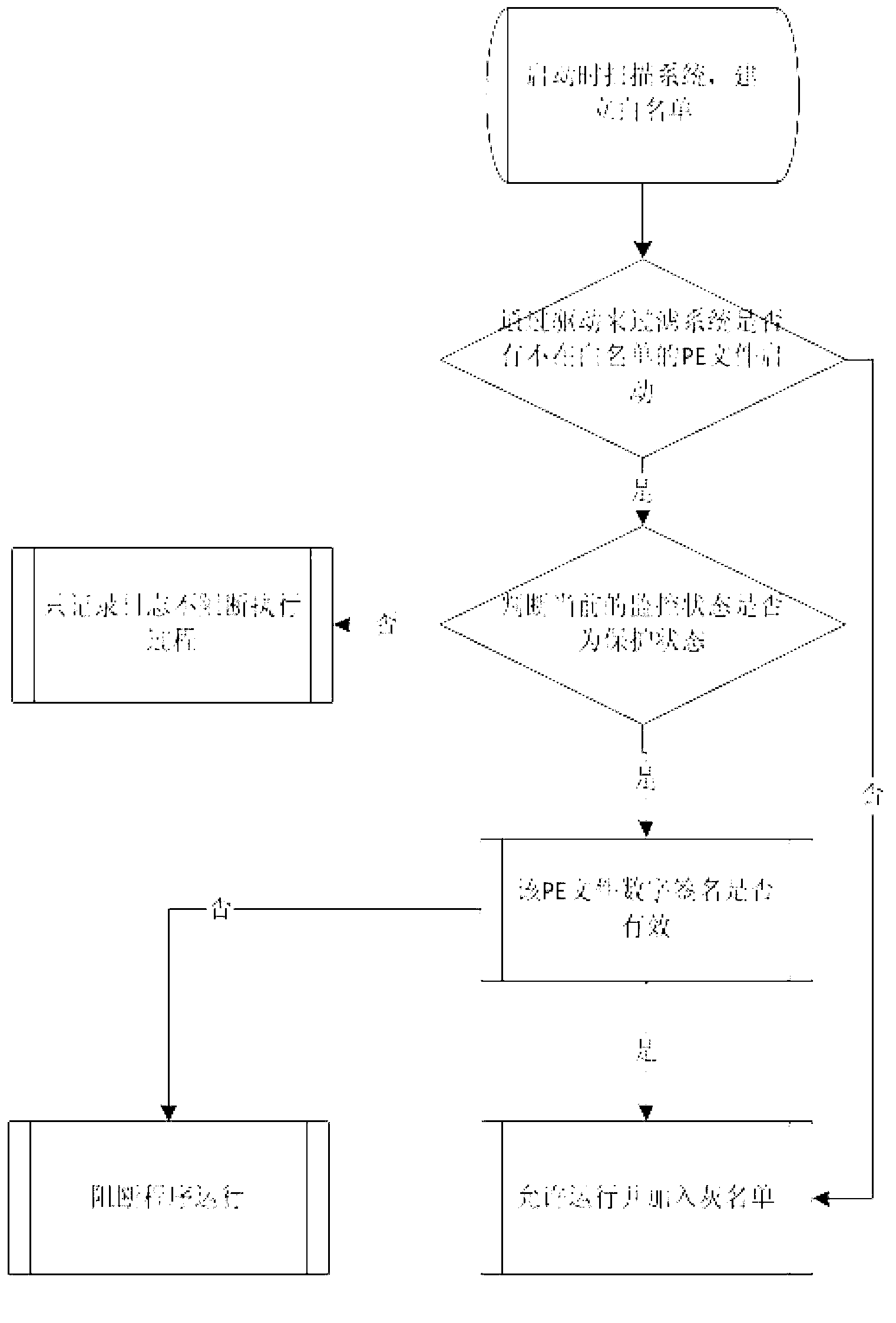
[0026] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments. Such as figure 1 As shown, the embodiment of the present invention is to run directly on the computer to be protected in the form of software, and the specific interception steps are as follows:
[0027] 1. Generate a white list of this computer: on the premise that there is no Trojan horse virus on the protected computer (such as a newly installed operating system, etc.), when the system runs for the first time, it uses multi-threading to scan the entire computer, and calculates and generates all corresponding files on the computer. Whitelist of PE files.
[0028] 2. Intercept process start: realize the function NtCreateSection that the operating system calls for loading files when the HOOK process starts by loading the driver, from which it is judged whether the file to be loaded by the operating system is a PE file, and the file path of the file i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com