Patents
Literature
51 results about "Ioctl" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
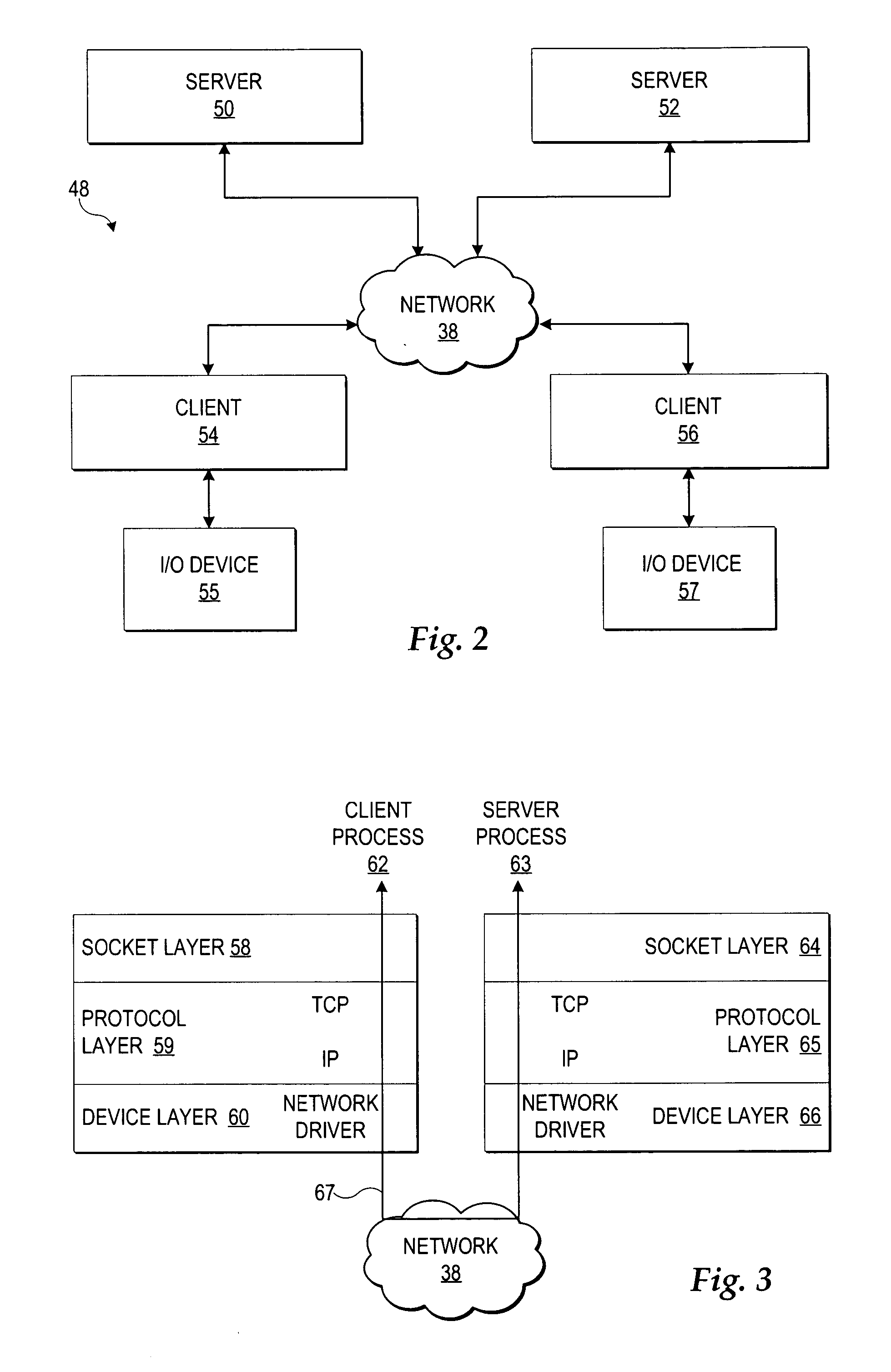
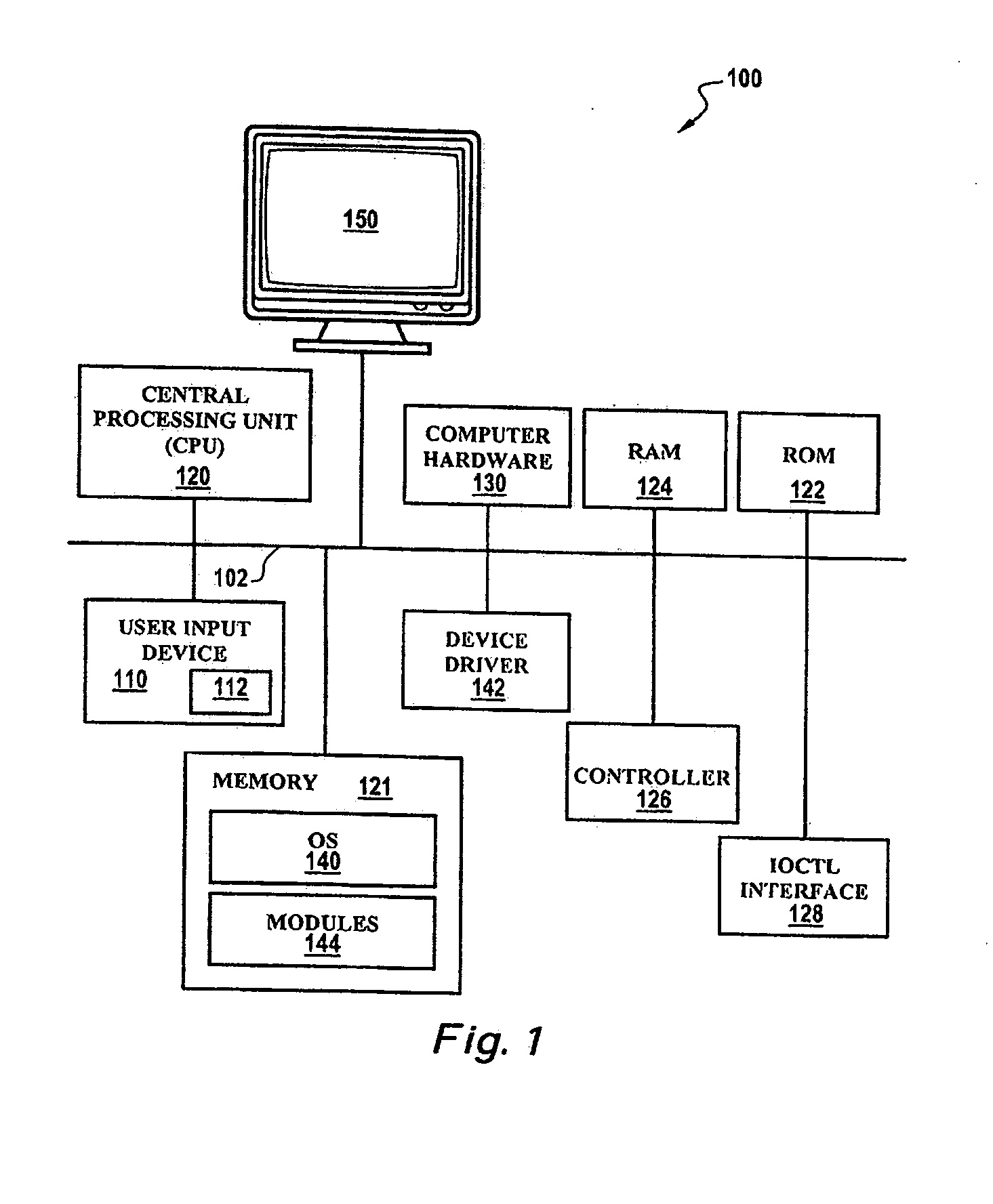
In computing, ioctl (an abbreviation of input/output control) is a system call for device-specific input/output operations and other operations which cannot be expressed by regular system calls. It takes a parameter specifying a request code; the effect of a call depends completely on the request code. Request codes are often device-specific. For instance, a CD-ROM device driver which can instruct a physical device to eject a disc would provide an ioctl request code to do that. Device-independent request codes are sometimes used to give userspace access to kernel functions which are only used by core system software or still under development.
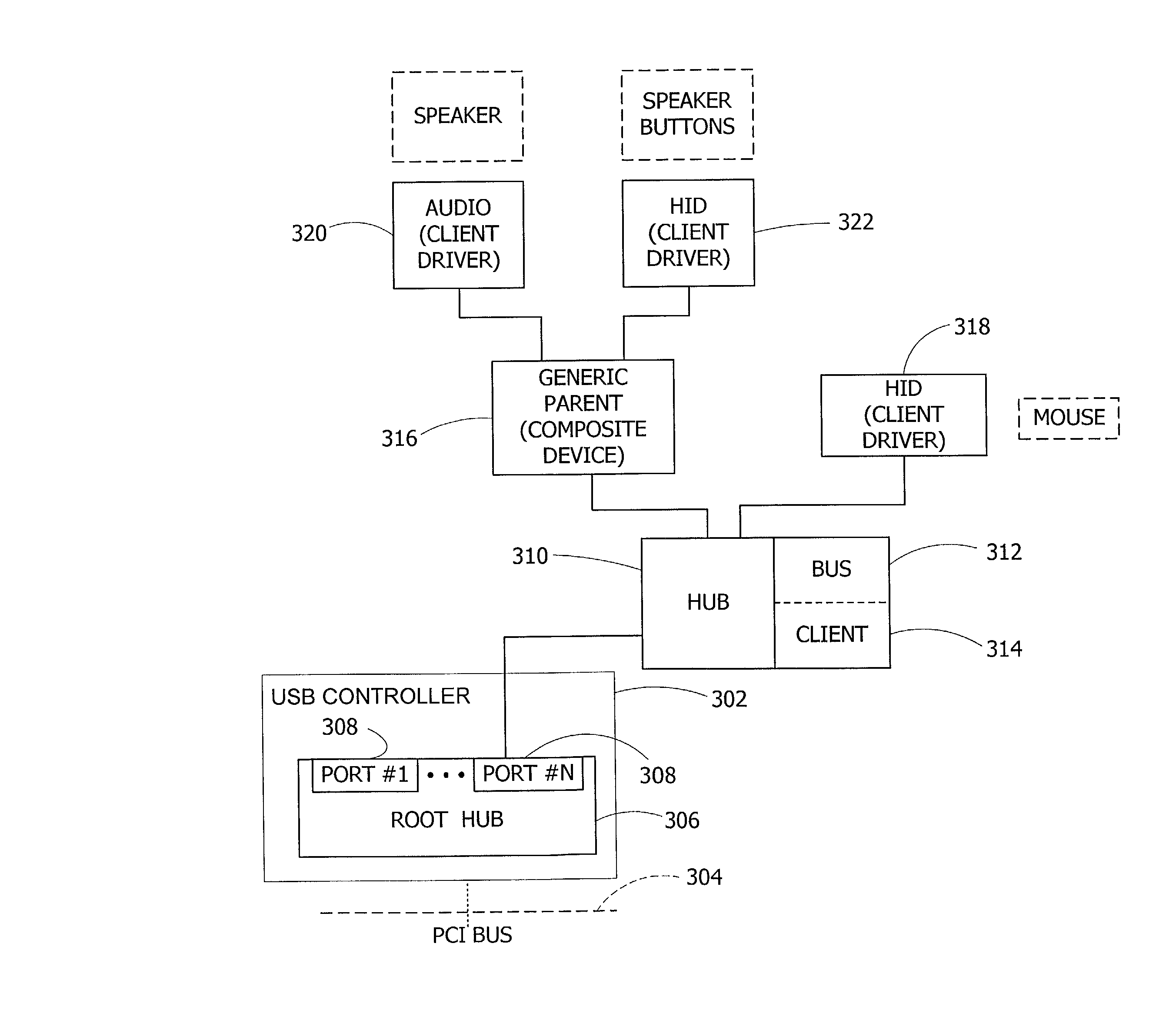
Selective suspension of bus devices
InactiveUS7103788B1Save powerEnergy efficient ICTPower supply for data processingEmbedded systemPower control
A method and system for asserting power control over one or more hardware devices connected via a bus. The invention includes a method and system for signaling and waiting to suspend a first device connected to a second device. The invention also includes a method and system for suspending a tree of devices with one or more of the devices hierarchically organized as parent devices and child devices in the tree. A controller at a root of the tree receives an idle request from one or more of the child devices and suspends all devices in the tree after receiving an idle request from each of the child devices. The invention also includes an input / output control (IOCTL) data structure for communicating the idle request.
Owner:MICROSOFT TECH LICENSING LLC
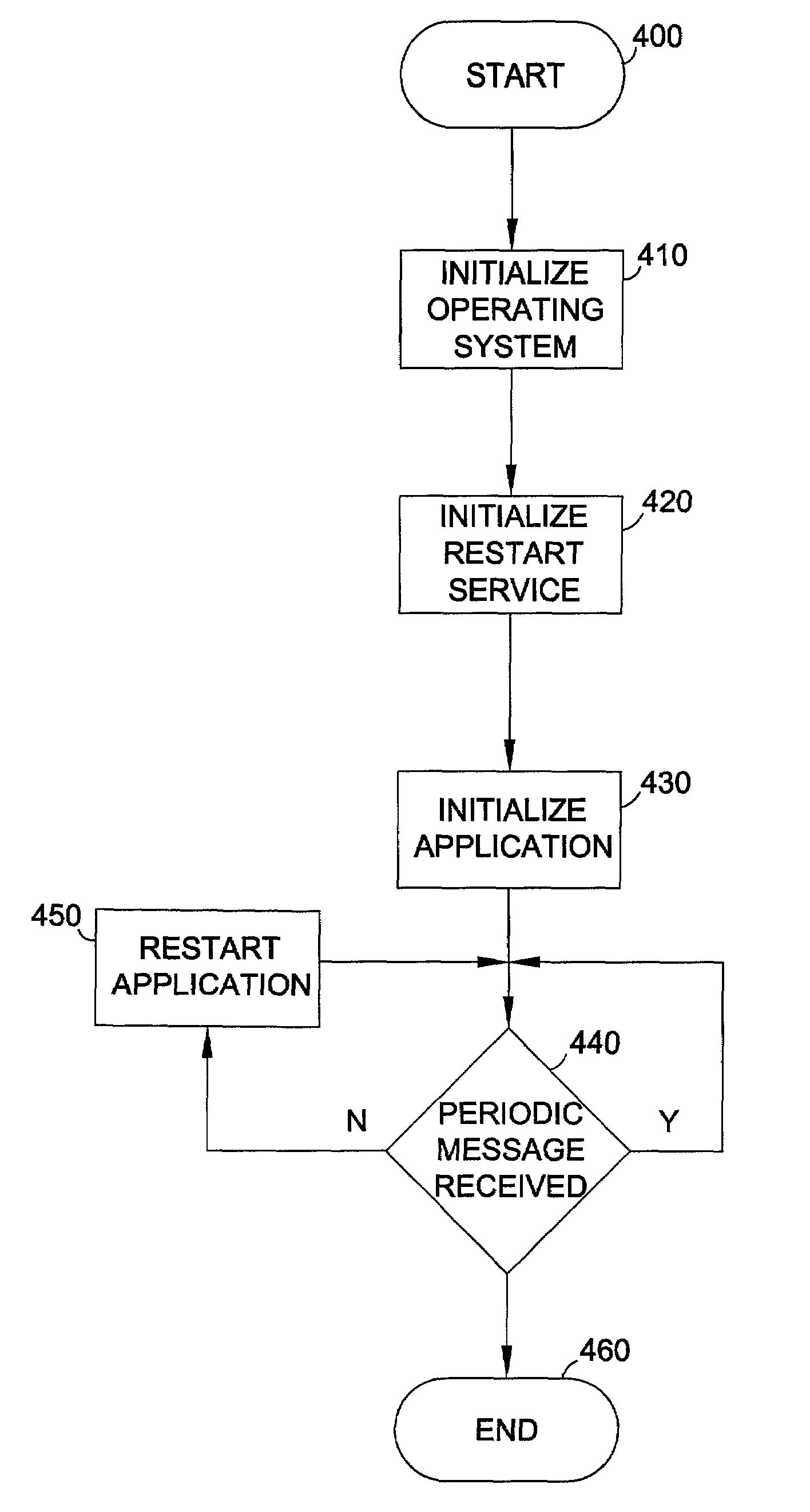
Application-level software watchdog timer
InactiveUS7000100B2Error detection/correctionData resettingCommunication interfaceOperational system
A software implementation of an application watchdog, comprising a restart service operating in the user mode and a watchdog driver operating in the kernel mode of a computer operating system. The driver incorporates a system thread configured to monitor a plurality of user applications operating in the user mode. The driver provides a first IOCTL signal interface for communicating control signals between the watchdog driver and one of the user applications and a second IOCTL signal interface for communicating control signals between the watchdog driver and the restart service. A communication interface exists for coordinating timer events with the operating system scheduler. If the system thread does not receive a message from one of said applications within an allotted period of time, the timer event alerts the watchdog driver that the allotted time has elapsed and the watchdog driver signals the restart service to restart that application.
Owner:HEWLETT PACKARD DEV CO LP
Monitoring thread usage to dynamically control a thread pool
InactiveUS20050086359A1Efficient loadingResource allocationMultiple digital computer combinationsClient-sideThread pool
A method, system, and program for monitoring thread usage to dynamically control a thread pool are provided. An application running on the server system invokes a listener thread on a listener socket for receiving client requests at the server system and passing the client requests to one of multiple threads waiting in a thread pool. Additionally, the application sends an ioctl call in blocking mode on the listener thread. A TCP layer within the server system detects the listener thread in blocking mode and monitors a thread count of at least one of a number of incoming requests waiting to be processed and a number of said plurality of threads remaining idle in the thread pool over a sample period. Once the TCP layer detects a thread usage event, the ioctl call is returned indicating the thread usage event with the thread count, such that a number of threads in the thread pool may be dynamically adjusted to handle the thread count.
Owner:IBM CORP
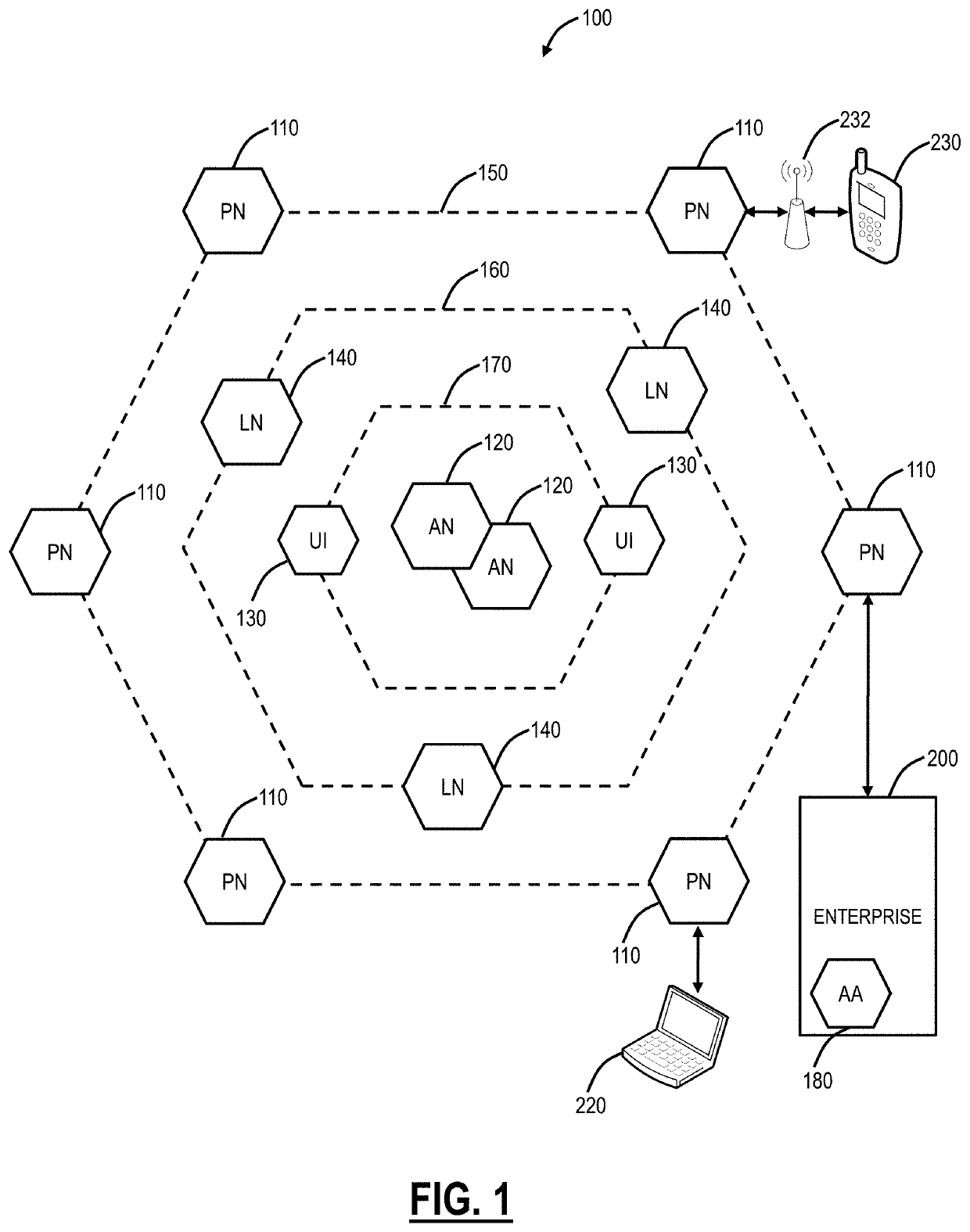
Device identification for management and policy in the cloud
ActiveUS20200077265A1Digital data authenticationPlatform integrity maintainanceUser deviceSoftware engineering
Systems and methods for device identification for management and policy in the cloud, using a combination of several hardware parameters and user's identification to generate a unique identifier for a user device and associated user. IOCTL and Assembly can be used to get the different hardware parameters. All the hardware parameters can then run through a process to generate a fixed size hardware fingerprint. A base64 encoding can be performed to convert it into a string, for consumption of database. The resultant identifier is unique and it is never stored on machine. The application can simply generate it whenever needed. The resultant identifier can used by a service provider to uniquely identify the device even when the device is moving hands or locations. The resultant identifier is never stored, so moving data from one device to another will not result in the same identifier for two devices.
Owner:ZSCALER INC
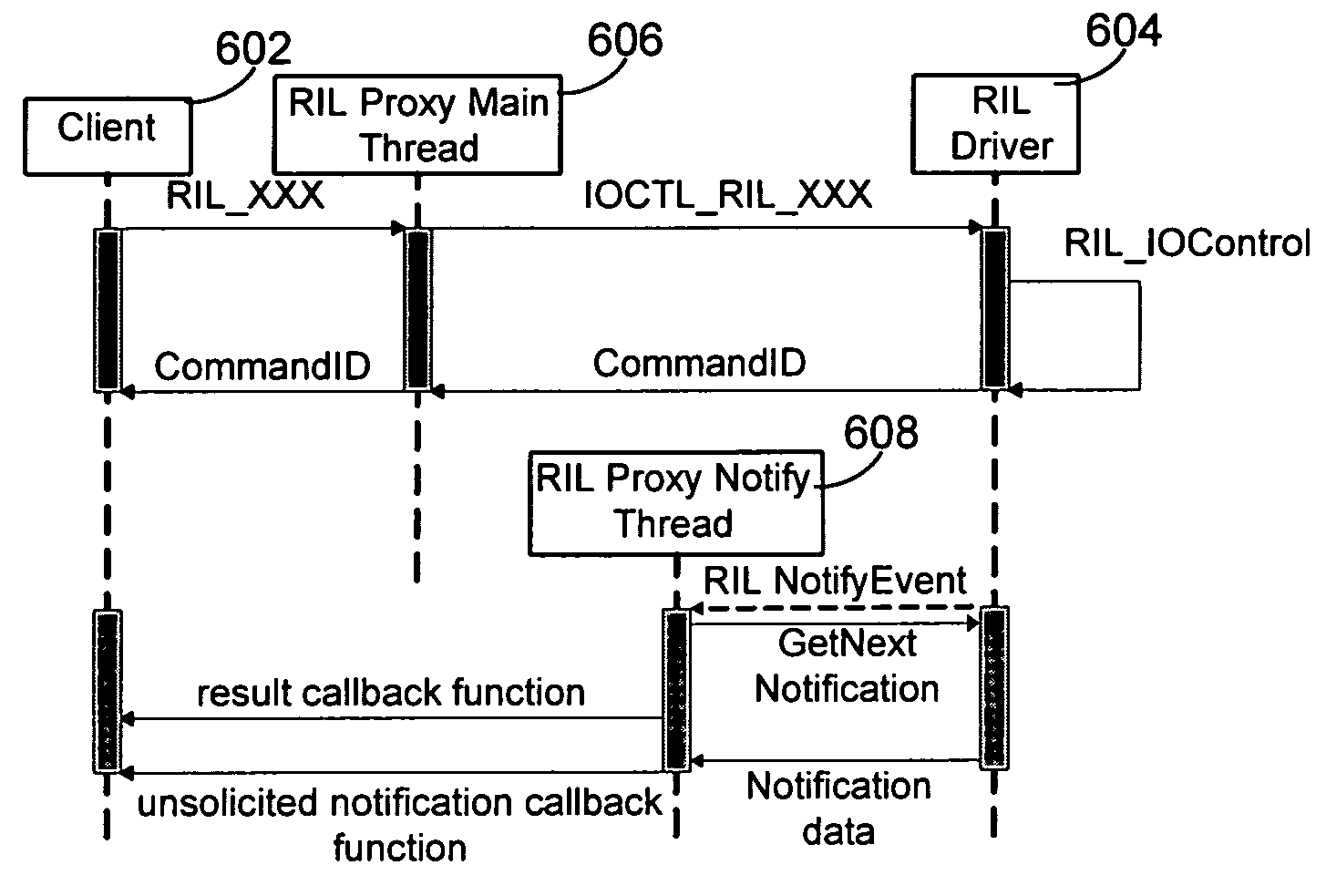
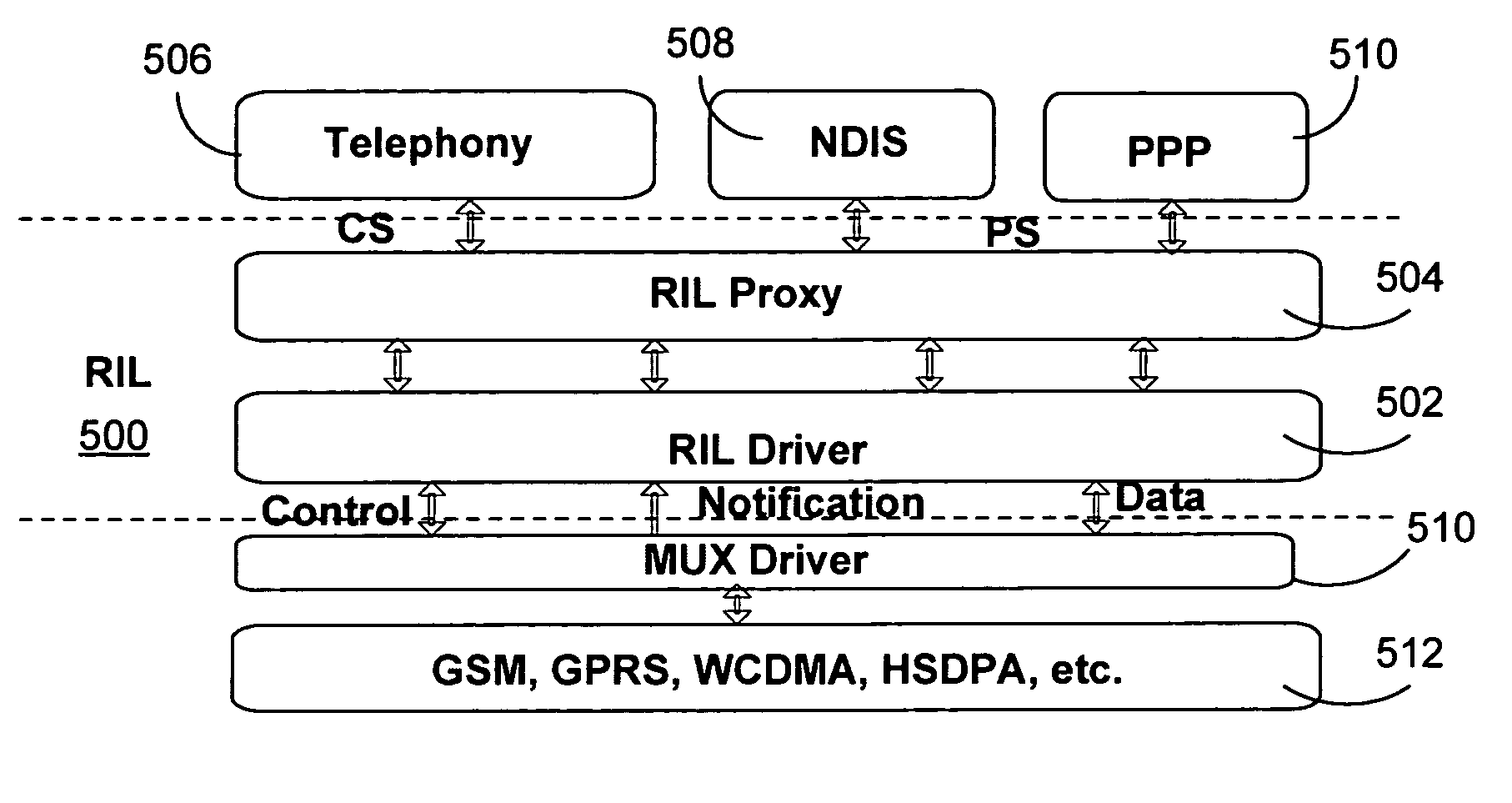
Synchronous RIL proxy
InactiveUS20060225082A1Efficient communicationEasy to useMultiprogramming arrangementsSubstation equipmentMobile phoneReal-time computing
A hardware-independent proxy layer for synchronous processing of commands in a mobile telephone is disclosed. Such synchronous processing may include receiving a function call of an application program interface (API) that is associated with a function to be performed by a mobile telephone, waiting to receive from a driver layer a result notify event indicating that the function has been performed, and, after receiving the result notify event from the driver layer, passing to the client first result data associated with the first result notify event. The API may be translated into an input / output control (IOCTL) code, which may be sent to the driver layer.
Owner:MICROSOFT TECH LICENSING LLC
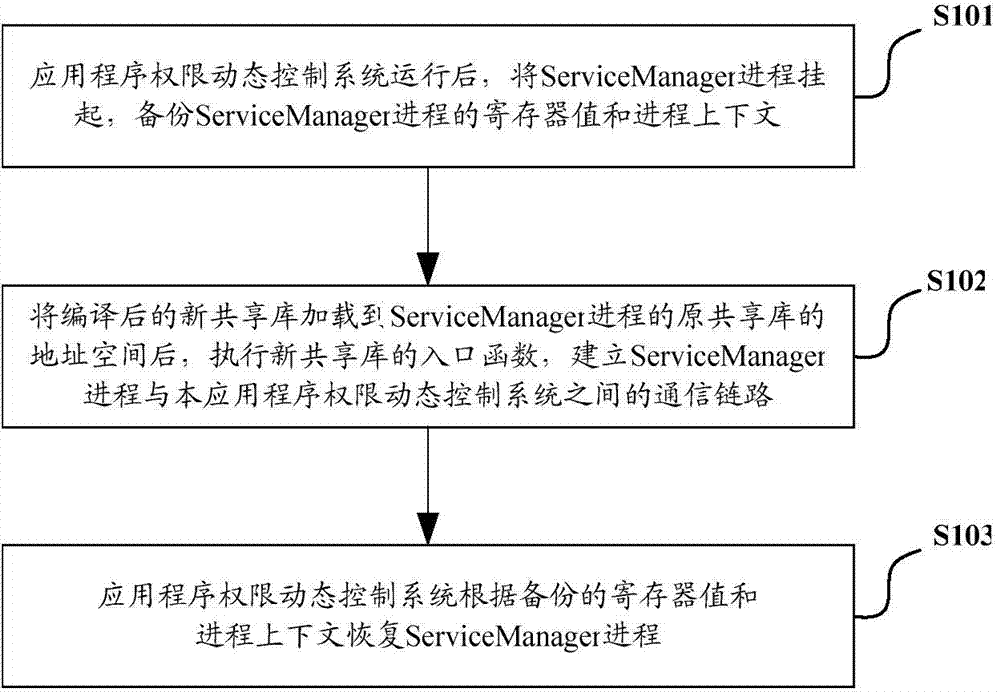
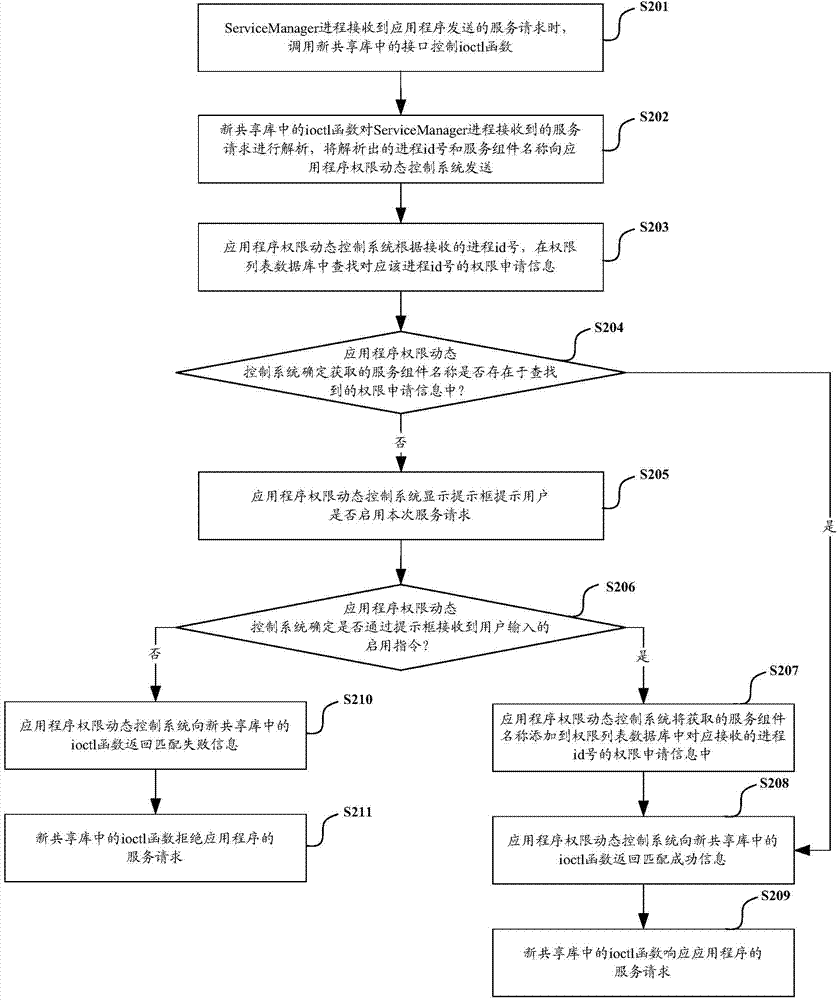
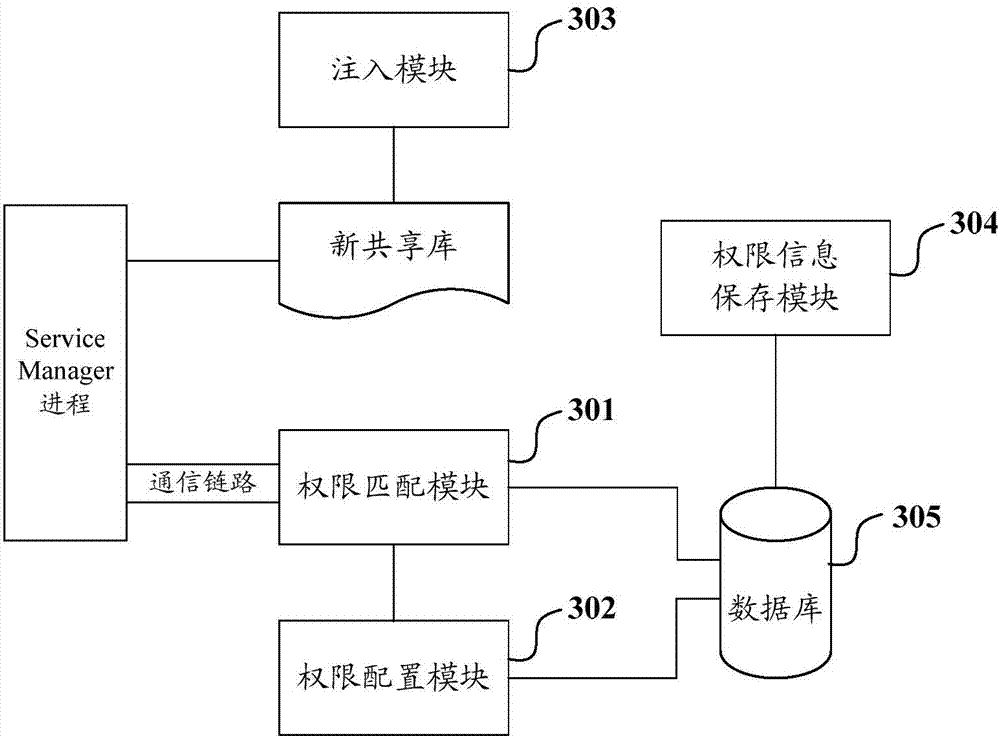
Application program authority dynamic control method and system
ActiveCN103617380AImprove versatilityIncrease flexibilityProgram/content distribution protectionControl systemApplication software
The invention discloses an application program authority dynamic control method and system. The method includes the steps that a new ioctl function injected in a shared library is called when an SM progress receives a service request of an application program; the new ioctl function obtains a progress id number and a service component name for requesting a service, and the progress id number and the service component name are sent to an application program authority dynamic control system; if the system determines that the received service component name exists in an authority application information list corresponding to the progress id number, information of successful matching is sent back to the new ioctl function; if not, a user is prompted to perform configuration; if the system receives a start order of the user, the received service component name is added to the authority application information list corresponding to the progress id number, the information of the successful matching is sent back to the new ioctl function, and the SM progress responds to a service request; if not, the information of failed matching is sent back, and the SM progress refuses the service request. Thus, the application program authority dynamic control method and system are higher in flexibility and universality.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Monitoring thread usage to dynamically control a thread pool
InactiveUS7363369B2Efficient loadingResource allocationMultiple digital computer combinationsClient-sideApplication software
A method, system, and program for monitoring thread usage to dynamically control a thread pool are provided. An application running on the server system invokes a listener thread on a listener socket for receiving client requests at the server system and passing the client requests to one of multiple threads waiting in a thread pool. Additionally, the application sends an ioctl call in blocking mode on the listener thread. A TCP layer within the server system detects the listener thread in blocking mode and monitors a thread count of at least one of a number of incoming requests waiting to be processed and a number of said plurality of threads remaining idle in the thread pool over a sample period. Once the TCP layer detects a thread usage event, the ioctl call is returned indicating the thread usage event with the thread count, such that a number of threads in the thread pool may be dynamically adjusted to handle the thread count.
Owner:INT BUSINESS MASCH CORP
Method for capturing real-time network data
InactiveCN103269284AReduce performance lossSatisfy perceived needsData switching networksMmapProcessor register
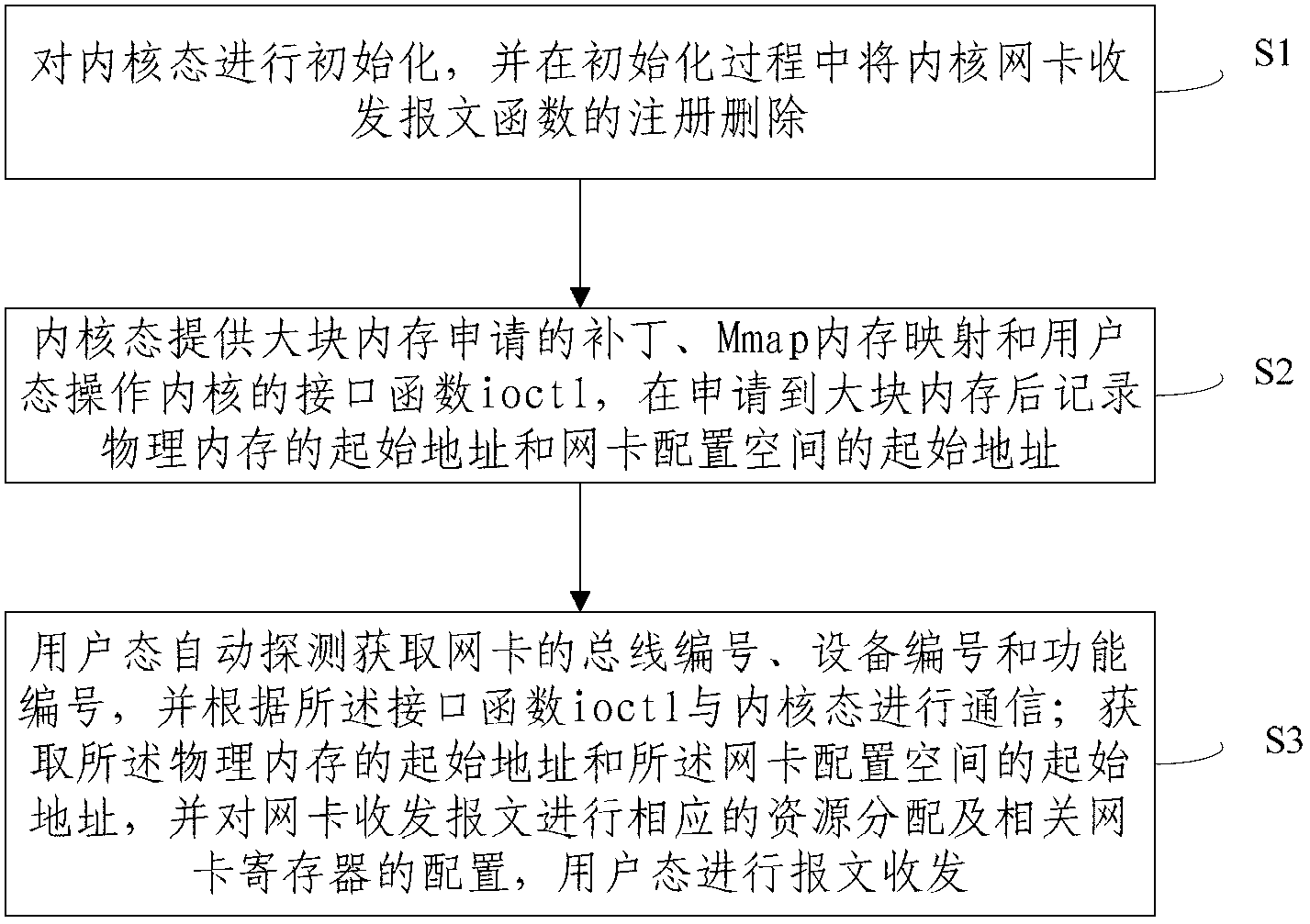
The invention provides a method for capturing real-time network data. The method comprises the following steps: S1, a kernel mode is initialized, and register information for receiving and sending message functions by a kernel network card is deleted in the process of initializing; S2, the kernel mode provides a large patch applied by internal storage, an Mmap memory map and an interface function ioctl of a user mode operation kernel, and the starting address of physical memory and the starting address of a network card configuration space are recorded; S3, a user mode automatically detects and acquires the bus number of the network card, the number of equipment and a function number, and is in communication with the kernel mode according to the interference function ioctl; corresponding resource allocation and corresponding network card register configuration are conducted on network card receiving and sending messages, and the user mode receives and sends the messages. According to the method for capturing the real-time network data, loading and driving in the kernel mode and message receiving and sending in the user mode of the network card are achieved, and network card driving interrupt in the kernel mode and performance damage caused by data copy are removed.
Owner:OPZOON TECH
Serial port time-sharing multiplexing method in embedded system
The invention discloses a serial port time-sharing multiplexing method in an embedded system, comprising the following steps of: 1) screening target data on a drive layer according to the frame head and the frame tail of the received data; 2) feeding the screened target data in a data buffer; 3) invoking ioctl () function to copy the target data of the data buffer to an application layer; and 4) obtaining the target data from the application layer. Via the serial port time-sharing multiplexing method disclosed by the invention, the purpose of directly obtaining serial port data is realized in case of no influence on the original circuit procedure, thus realizing serial port multiplexing.
Owner:北京神戎科技有限公司
Method and system for acquiring process information of KVM (Kernel-based Virtual Machine)
InactiveCN103077071AAchieve introspectionProgram loading/initiatingSoftware simulation/interpretation/emulationRelevant informationProcessor register
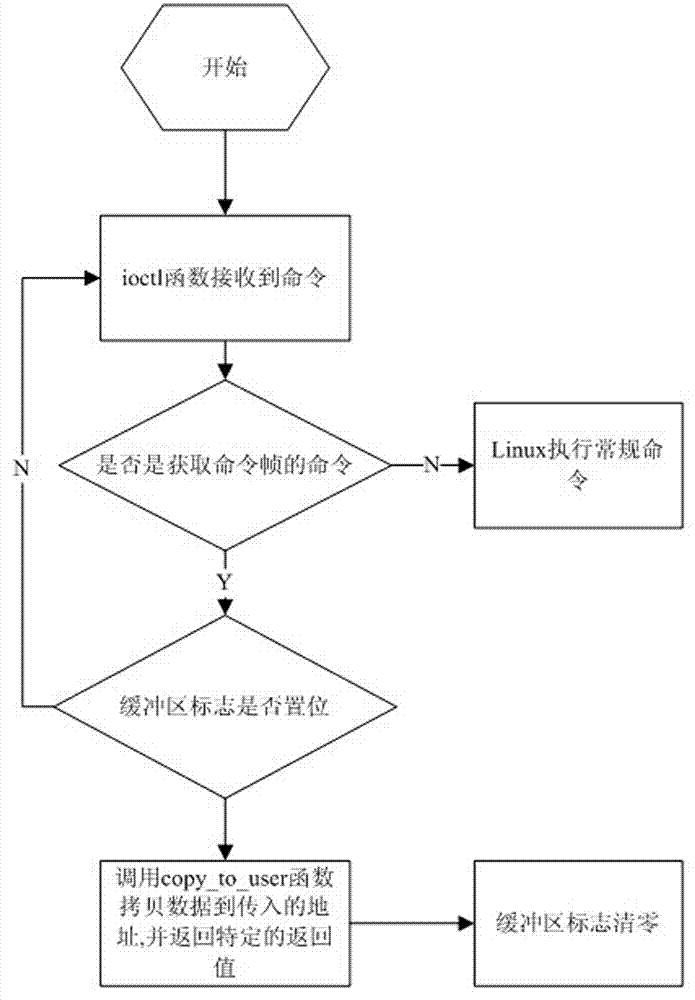
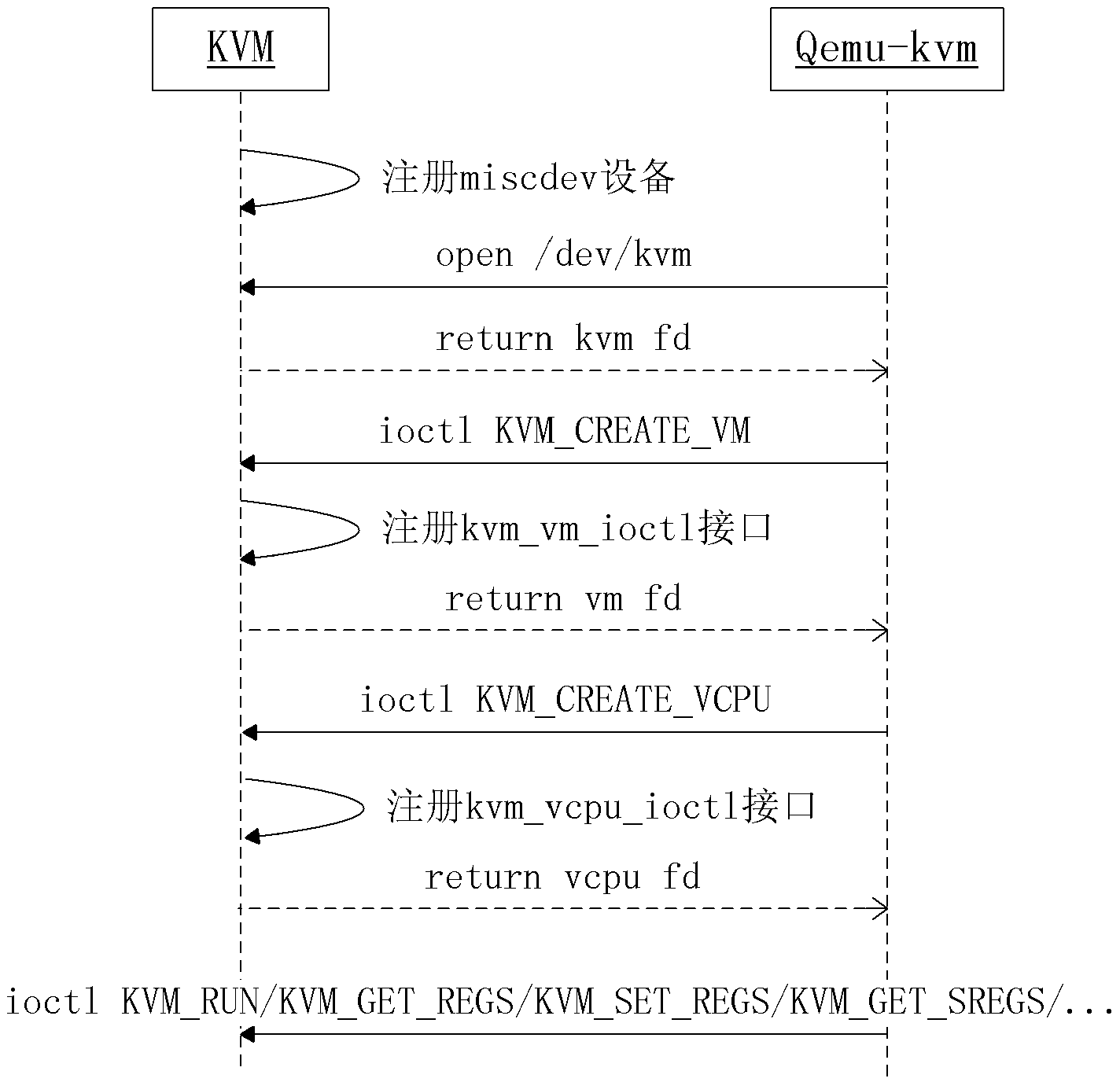
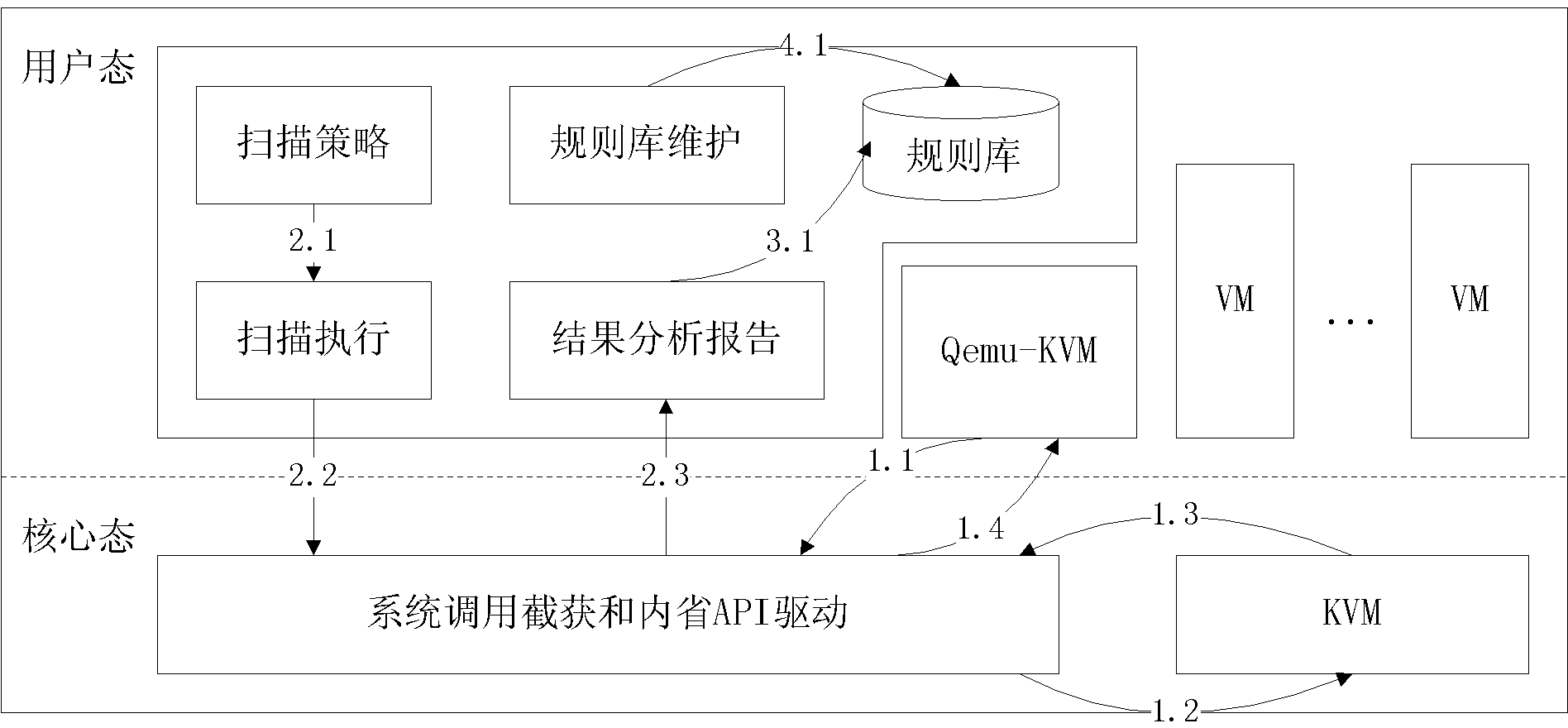
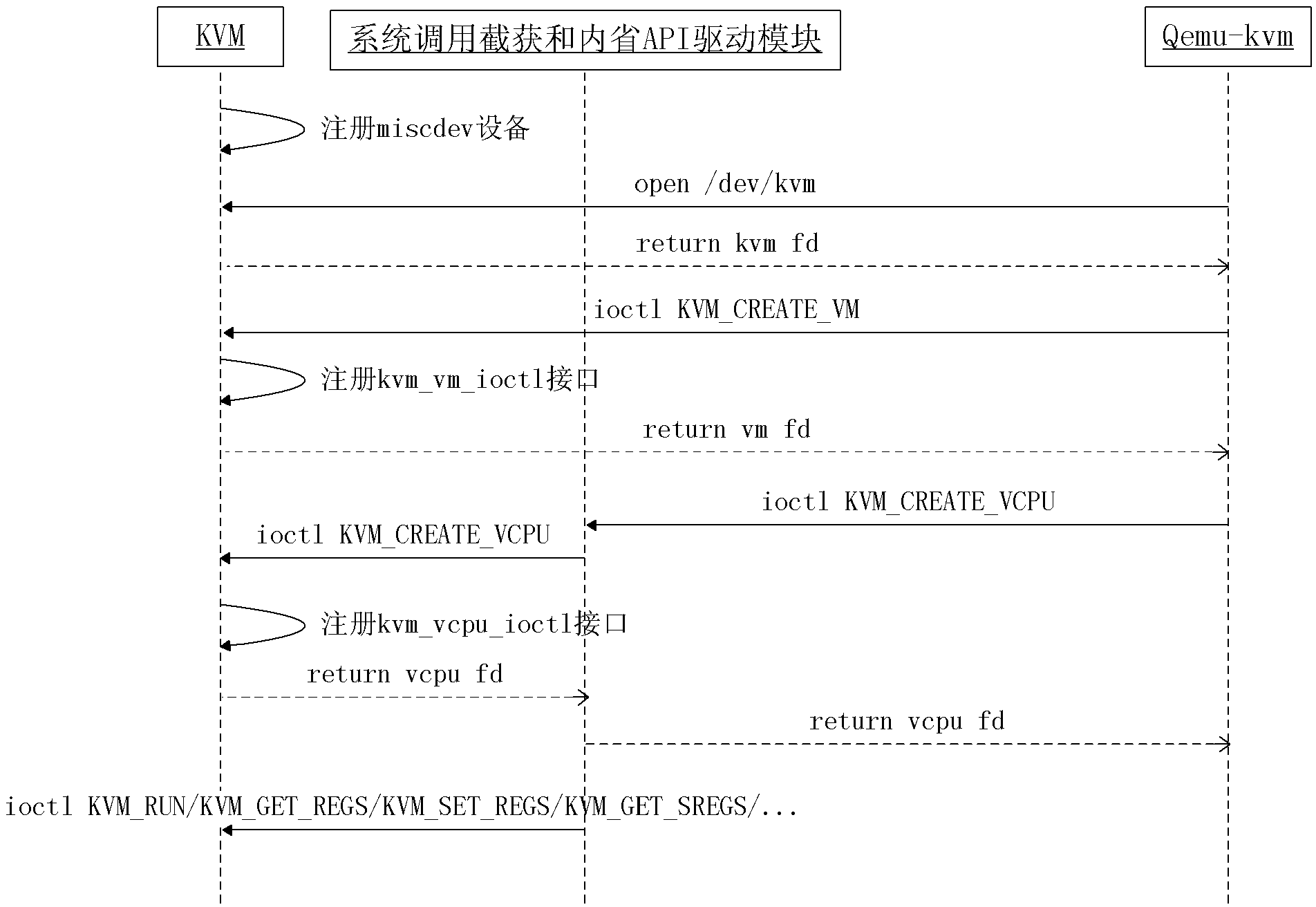
The invention discloses a method and a system for acquiring the process information of a KVM (Kernel-based Virtual Machine), relating to the technical field of information security. The system disclosed by the invention comprises a system call intercepting and capturing module and an introspection API (Application Program Interface) drive module, wherein the system call intercepting and capturing module is used for intercepting and capturing an IOCTL (Input Output Control) system call initiated by Qemu-kvm and sending called parameters to the introspection API drive module; and the introspection API drive module is used to substitute the Qemu-kvm to initiate the IOCTL system call to the KVM, record a vcpu (virtual central processing unit) which is called by the KVM after response, return the record to the Qemu-kvm, acquire process running in the virtual machine and relevant information of a register, carry out structured processing on the acquired relevant information, expose the relevant information subjected to structured processing to an external program through a process scanning interface, receive a scanning command initiated by the external program and initiate the request to KVM through the vcpu. The invention further discloses the method for acquiring the process information of the KVM. According to the technical scheme disclosed by the invention, the introspection of the information of a process running in the virtual machine can be realized transparently on the premise of not modifying Qemu-kvm and KVM codes.
Owner:BEIJING VENUS INFORMATION TECH +1
Rapid response video monitoring method and system based on Linux system
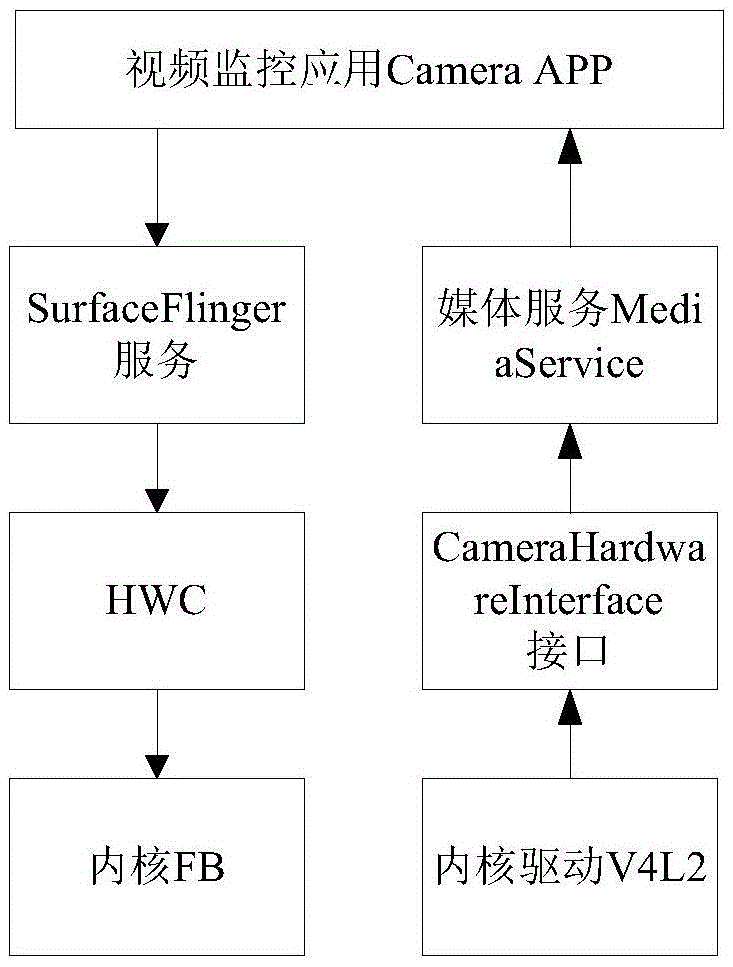
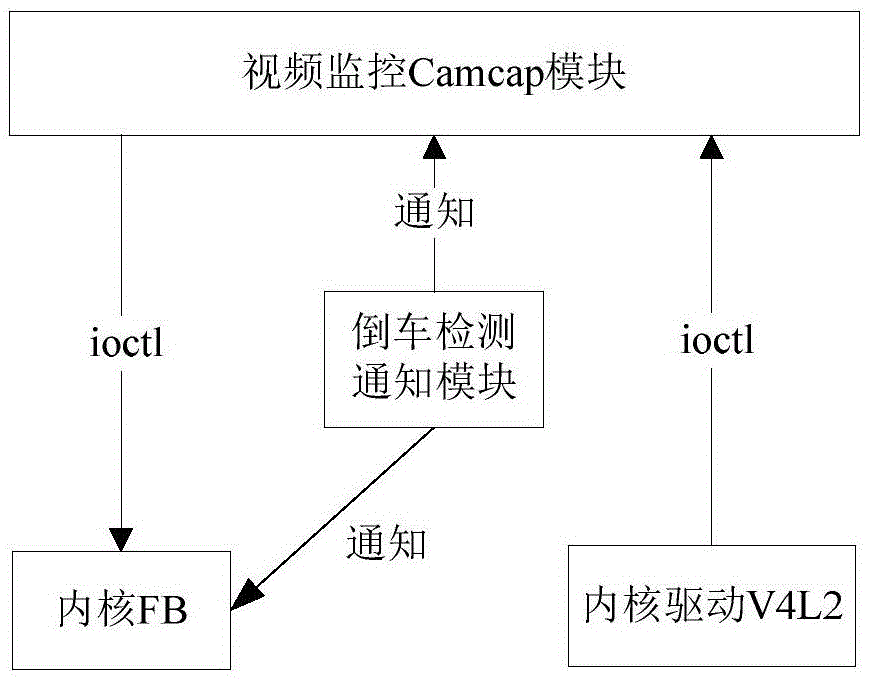
ActiveCN105657369AQuick responseShorten the timeClosed circuit television systemsVideo monitoringGNU/Linux
The invention provides a rapid response video monitoring method based on a Linux system. The method comprises that a video monitoring Camcap module is set in the Linux system; the video monitoring Camcap module reads video monitoring data from an kernel driver V4L2 through ioctl system invoking and transmits the data to a kernel FB (frame buffer) for operation through ioctl system invoking; the video monitoring Camcap module obtains video data through Linux system invoking of the kernel driver V4L2 and transits the video data to a screen for display through Linux system invoking of the kernel FB, thus finishing the rapid response of the Linux system. The invention also provides a video monitoring method based on the rapid response of the Linux system. According to the method and the system provided by the invention, the original boot sequence of the system is not influenced; special modifications aiming at different sensors are unnecessary; and the rapid response is carried out to the video monitoring.
Owner:FUZHOU ROCKCHIP SEMICON
Wireless mesh network access security authentication method based on WLAN
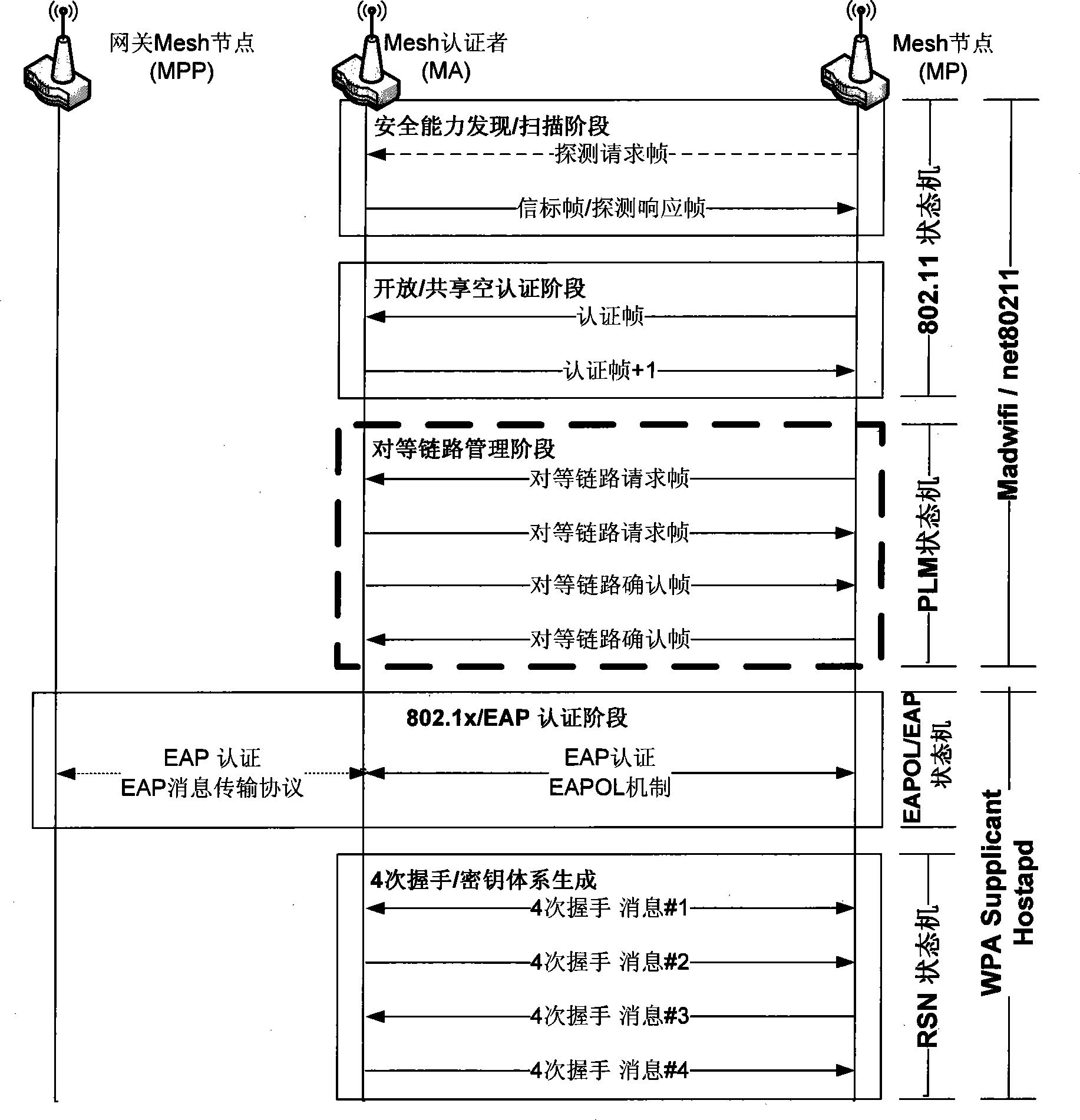
InactiveCN101394281AMeet the needs of new features such as dynamic self-organizationImprove compatibilityUser identity/authority verificationMachine controlWireless mesh network
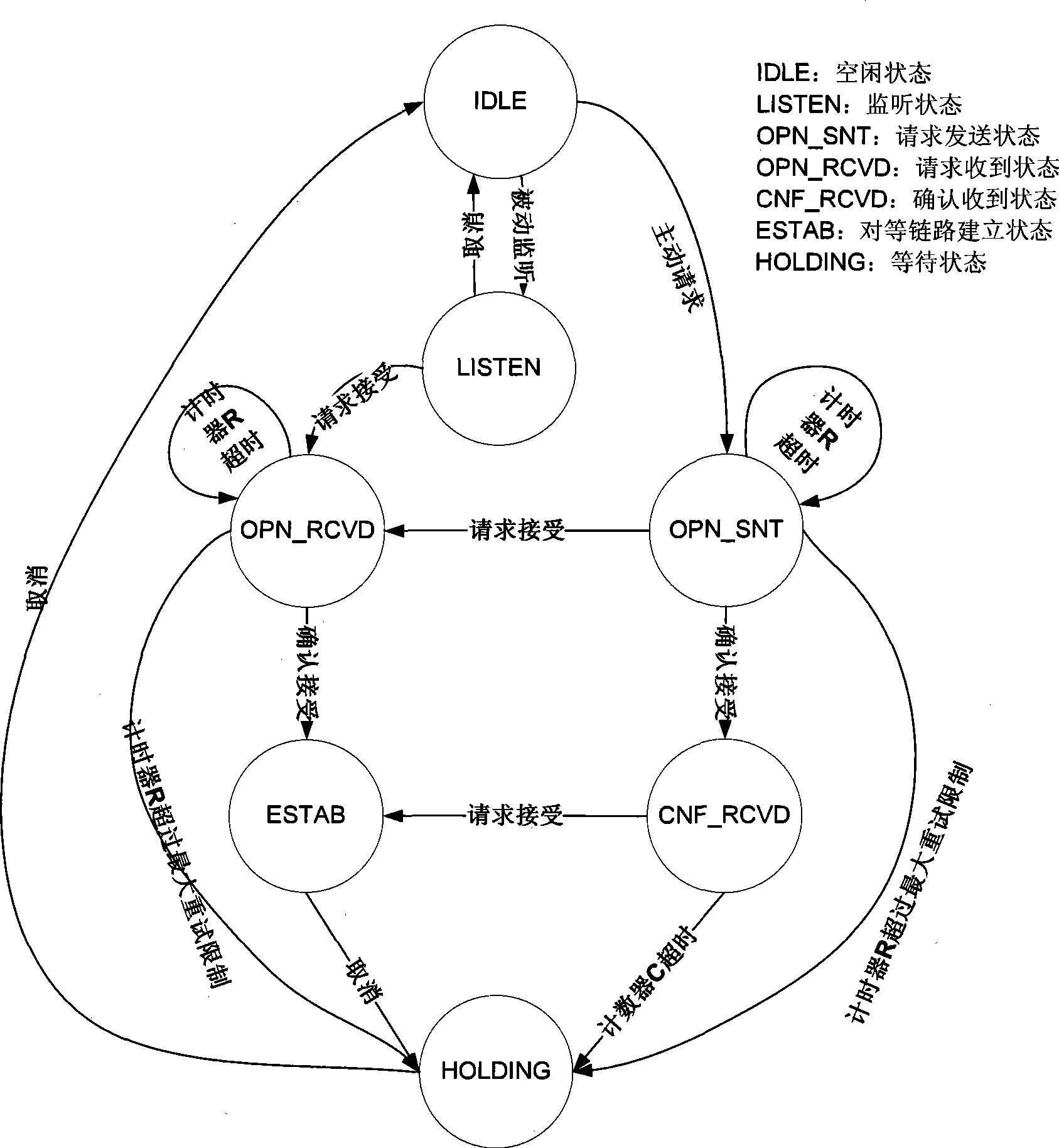
The invention disclose a security certificating method for the access of the wireless mesh network based on a wireless local area network in the technical field of wireless networks. When both certificating sides enter a PLM process used for exchanging security parameters after completing 802.11 open certification; a PLM state machine takes over the operation of a 802.11 state machine; the PLM process is composed of a pair of equivalent link requesting / equivalent link confirming messages respectively sent by both certification sides; a 802.11i / RSN security parameter and a 802.11s / MSA security parameter are mutually consulted, and a storage key used for pre-certification is selected, and the role of each during the following EAP certification stage is determined; the PLM state machine controls a mechanism for transceiving and retransmitting the message; and when the PLM process is over, the mechanism is recontrolled by the 802.11 state machine, and an internal event calling IOCTL is produced to notify an EAP user end to prepare to begin an EAP certification process and four times of handshake interaction. The method satisfies the new features such as the dynamical self-organization of a WLAN Mesh network, and has reliable safety performance.
Owner:SHANGHAI JIAO TONG UNIV
System and method for passing information from one device driver to another
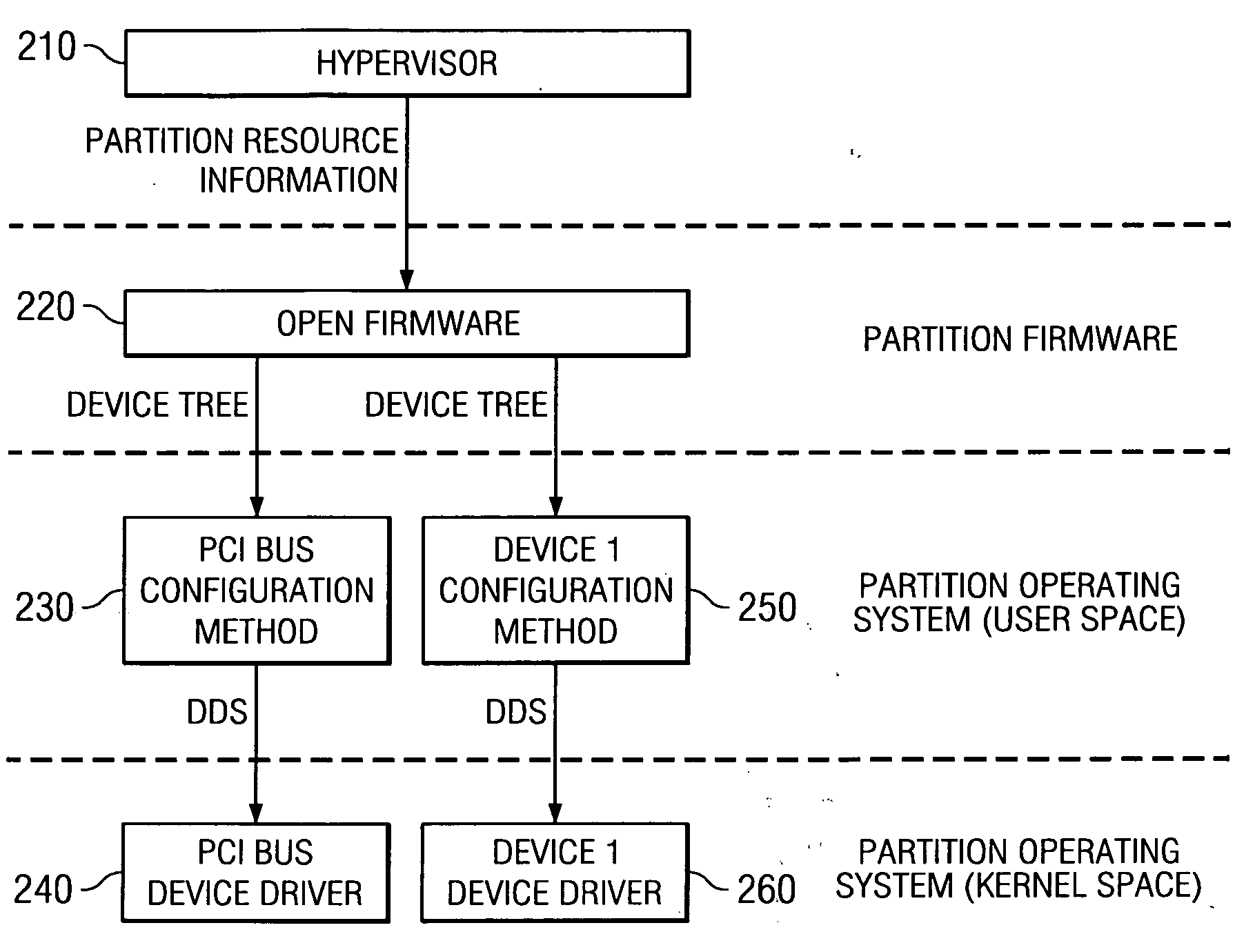
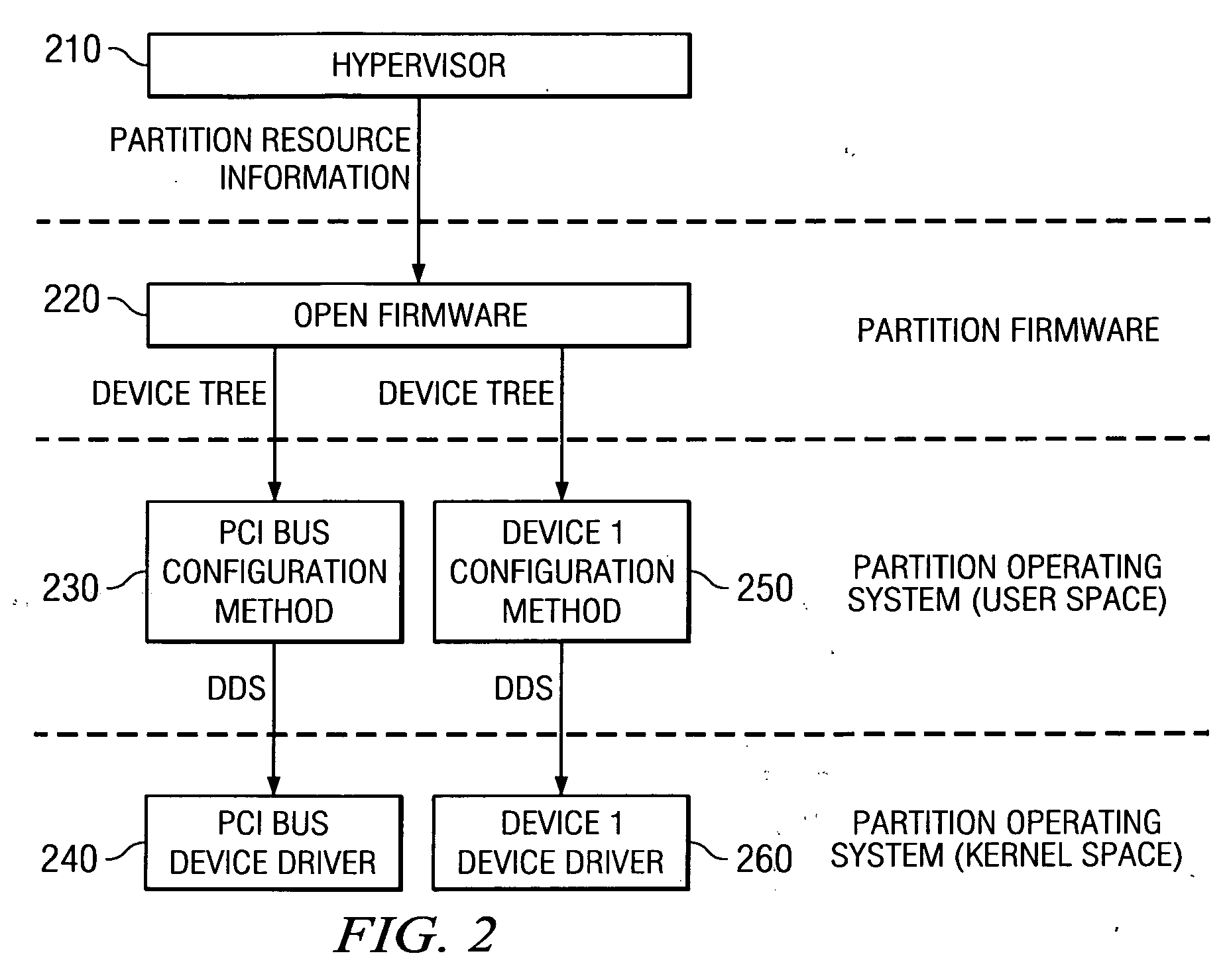
A system and method for passing Direct Memory Access (DMA) configuration information from one device driver to another in order to initialize devices for DMA operations are provided. More specifically, a mechanism for passing information, identifying a DMA address space allocated to a child virtual device, from the child virtual device to the virtual I / O (VIO) bus is provided so that DMA operations may be initialized for the child virtual device via the VIO bus. With the system and method, the device driver of the child virtual device passes information regarding the DMAble address space of the child virtual device directly to the device driver of the VIO bus using one of a I / O control (IOCTL) interface and an operating system kernel service. This information is then used by the VIO bus device driver to setup the VIO bus for DMA operations from the child virtual device.
Owner:IBM CORP
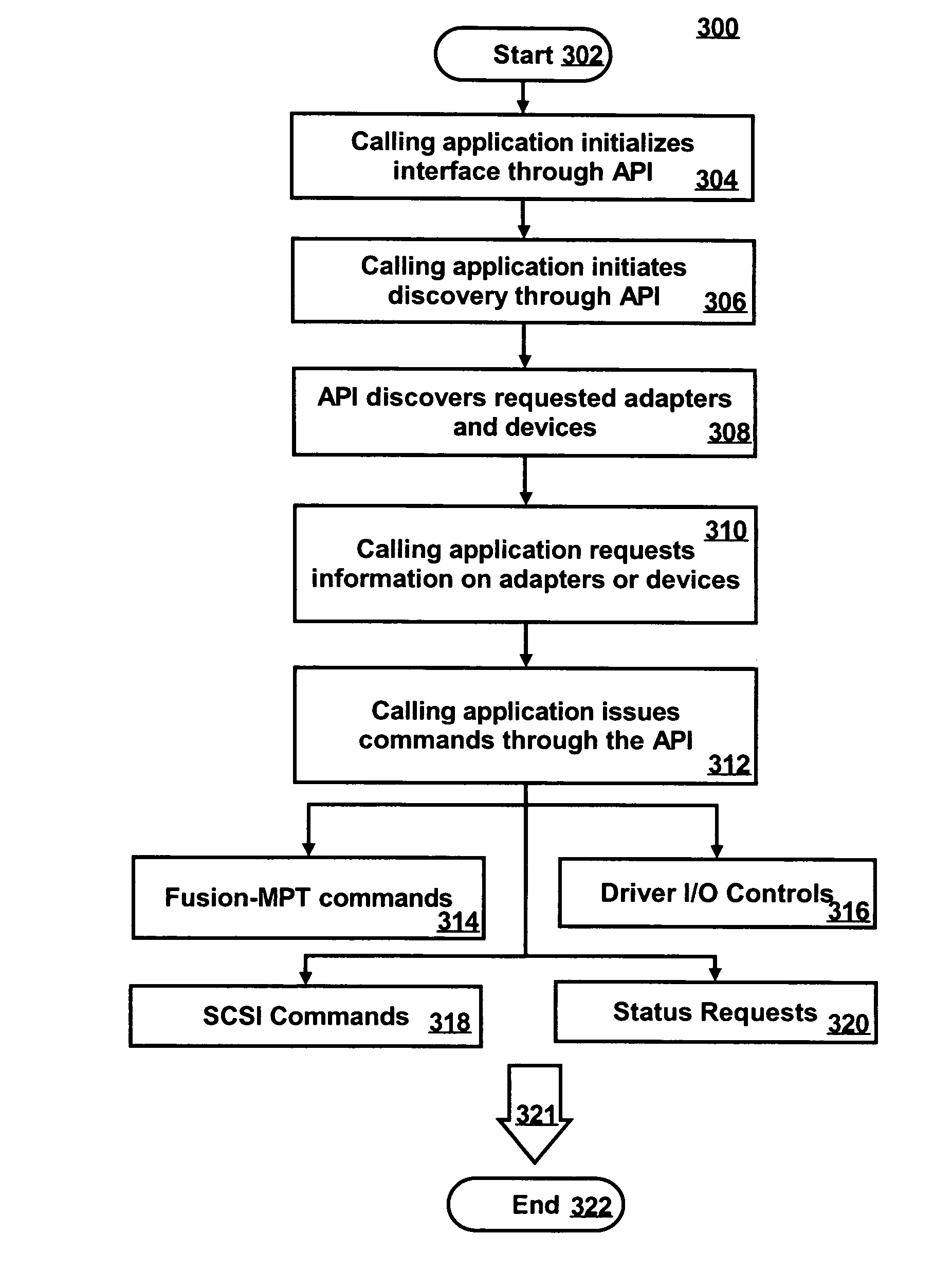
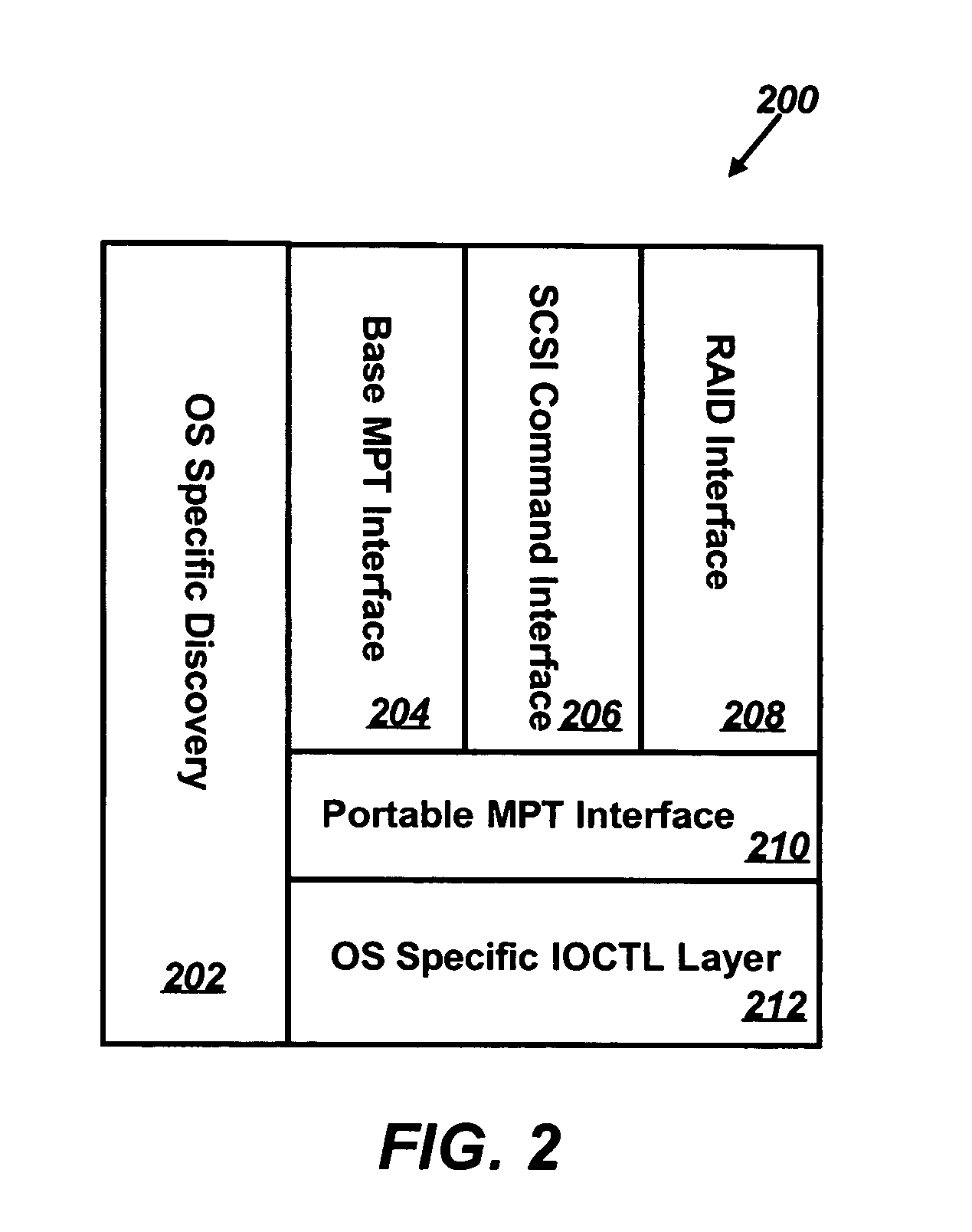
Application programming interface for fusion message passaging technology
ActiveUS20060277553A1Easy to callImprove application development efficiencyMultiprogramming arrangementsMultiple digital computer combinationsData processing systemApplication programming interface
A data-processing system and method are disclosed, which generally includes a plurality of components connected to a bus within a data-processing apparatus utilizing one or more input / output interfaces (e.g., IOCTL) in communication with the bus. A dynamic interface is implemented, which includes a plurality of interface modules that permits varying data-processing applications to scan, identify and interface with the plurality of components utilizing the input / output interface, thereby increasing data-processing application development efficiency relative to one or more components within the data-processing system.
Owner:NETWORK APPLIANCE INC +1
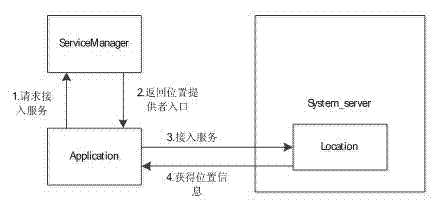
Android platform based GPS (global positioning system) data intercepting control method
InactiveCN103049707AImplement interceptionInterception control implementationDigital data protectionPrivacy protectionTwo step
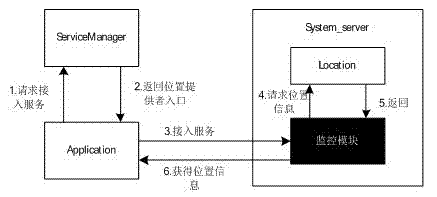
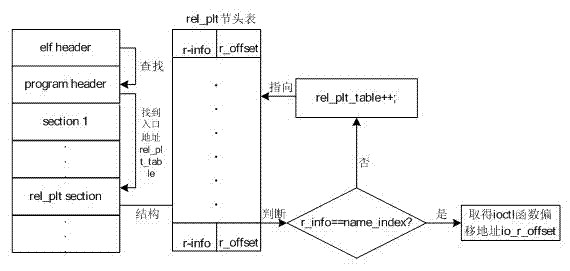
The invention belongs to the technical field of location privacy protection and provides an Android platform based GPS (global positioning system) data intercepting control method. Without impacting Android system performances, an own location service monitoring module is inserted into a system_server process to achieve intercepting control of GPS data. For achieving GPS data intercepting control of an Android platform, the method includes the two steps of firstly, finding an entry address of an ioctl function during operation of the system_server process, and secondly, loading the own monitoring module at the entry address of the ioctl function in the system_server process so that GPS datagram is intercepted on the bottom layer.
Owner:WUHAN UNIV +1
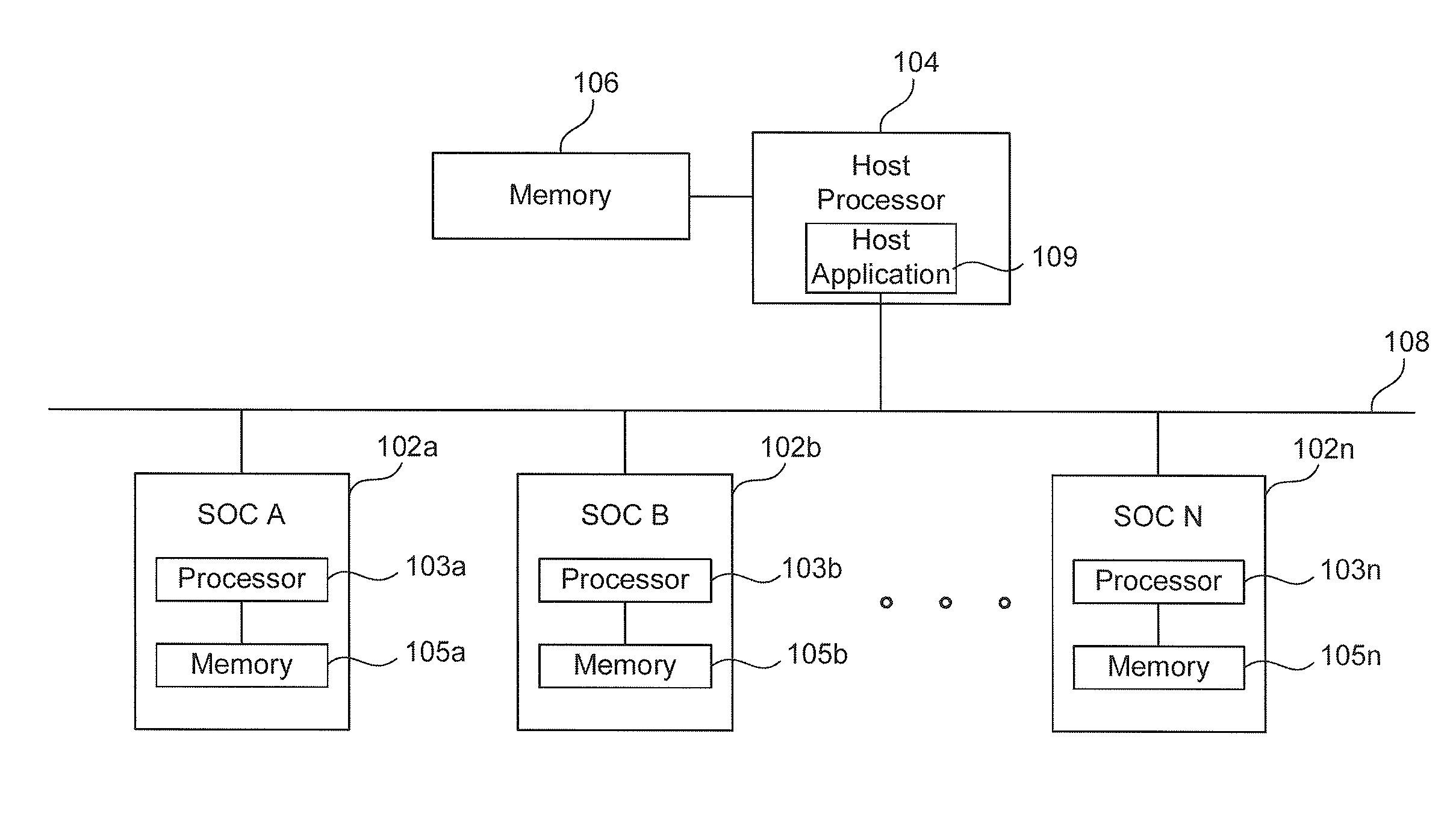
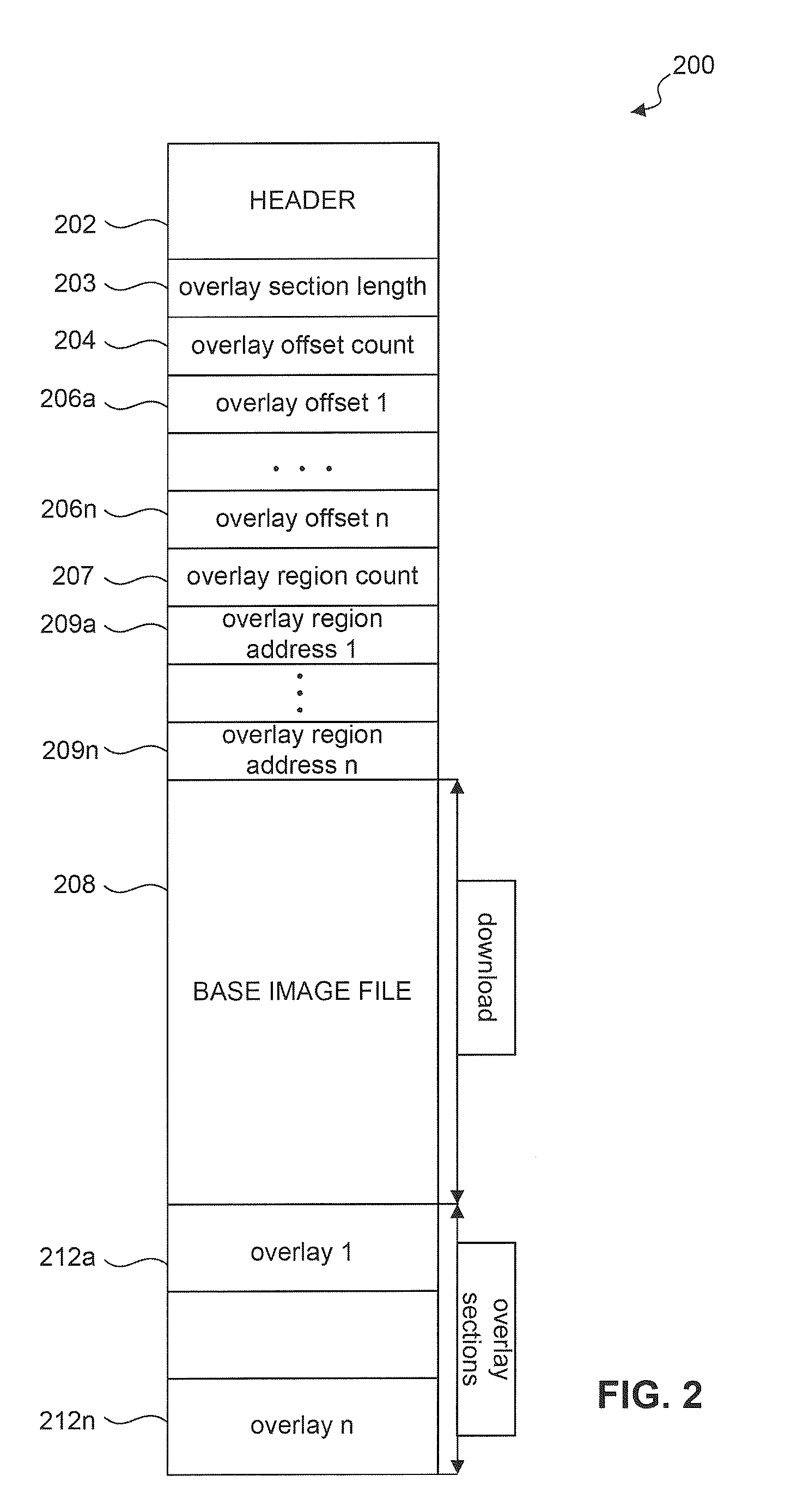
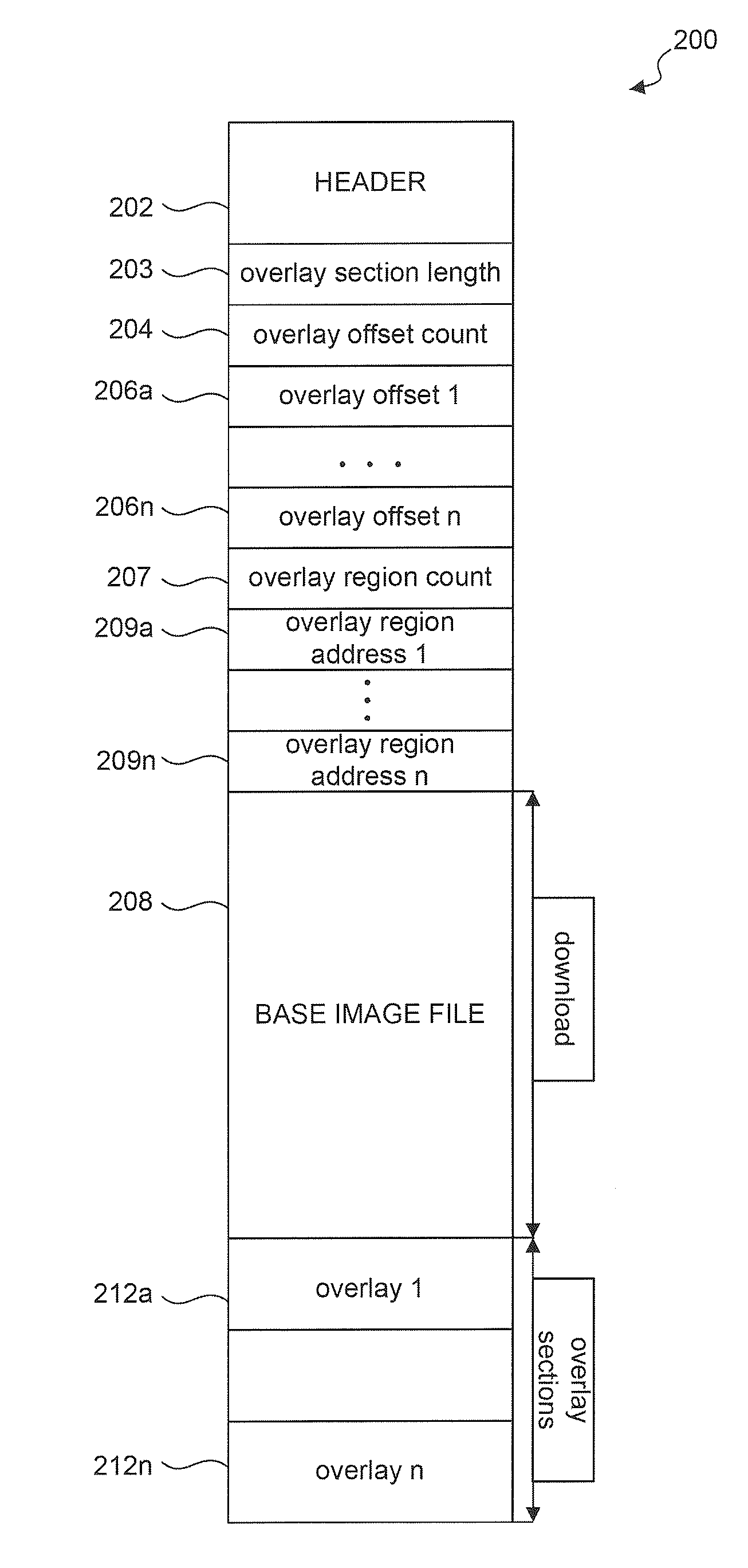
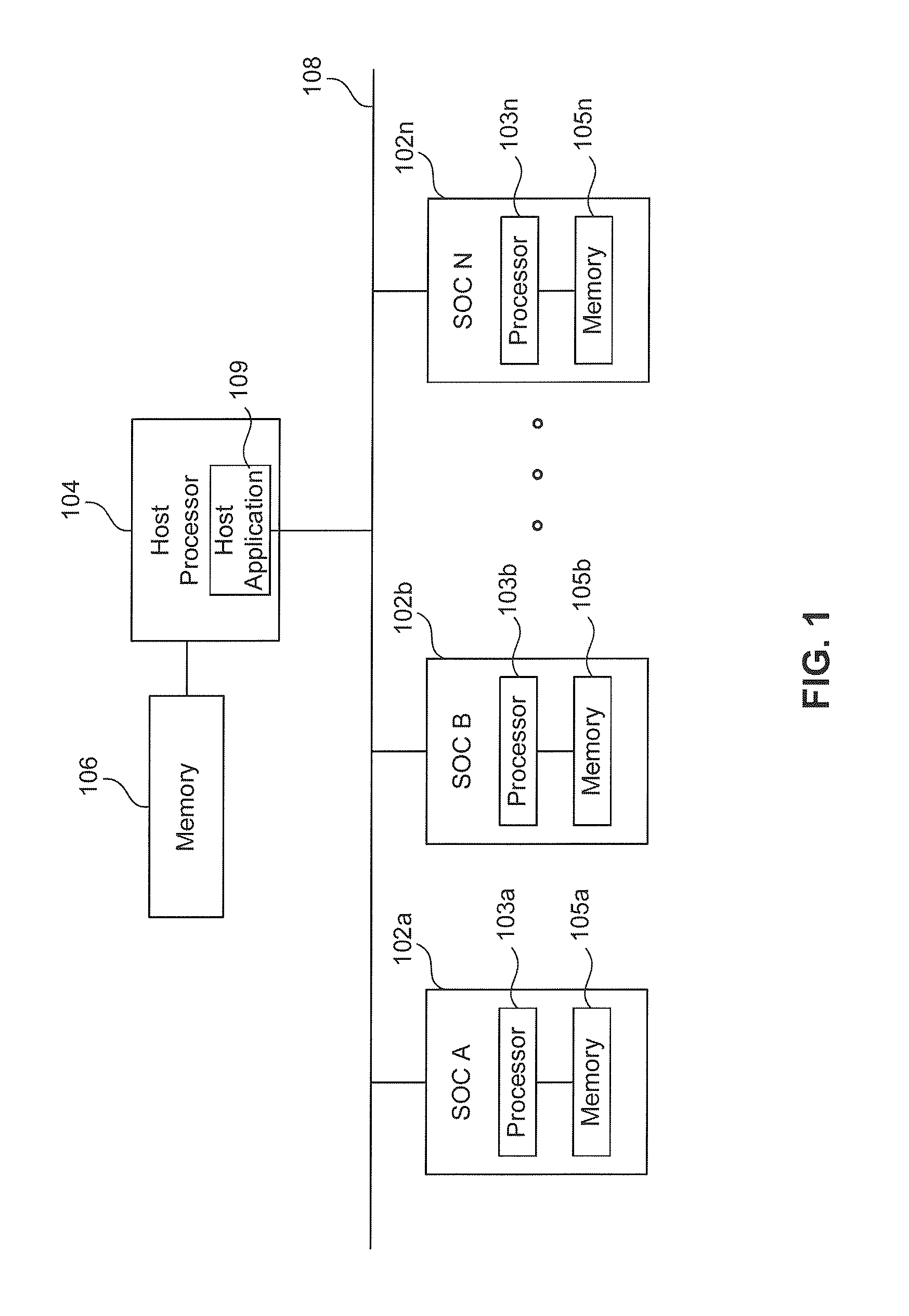
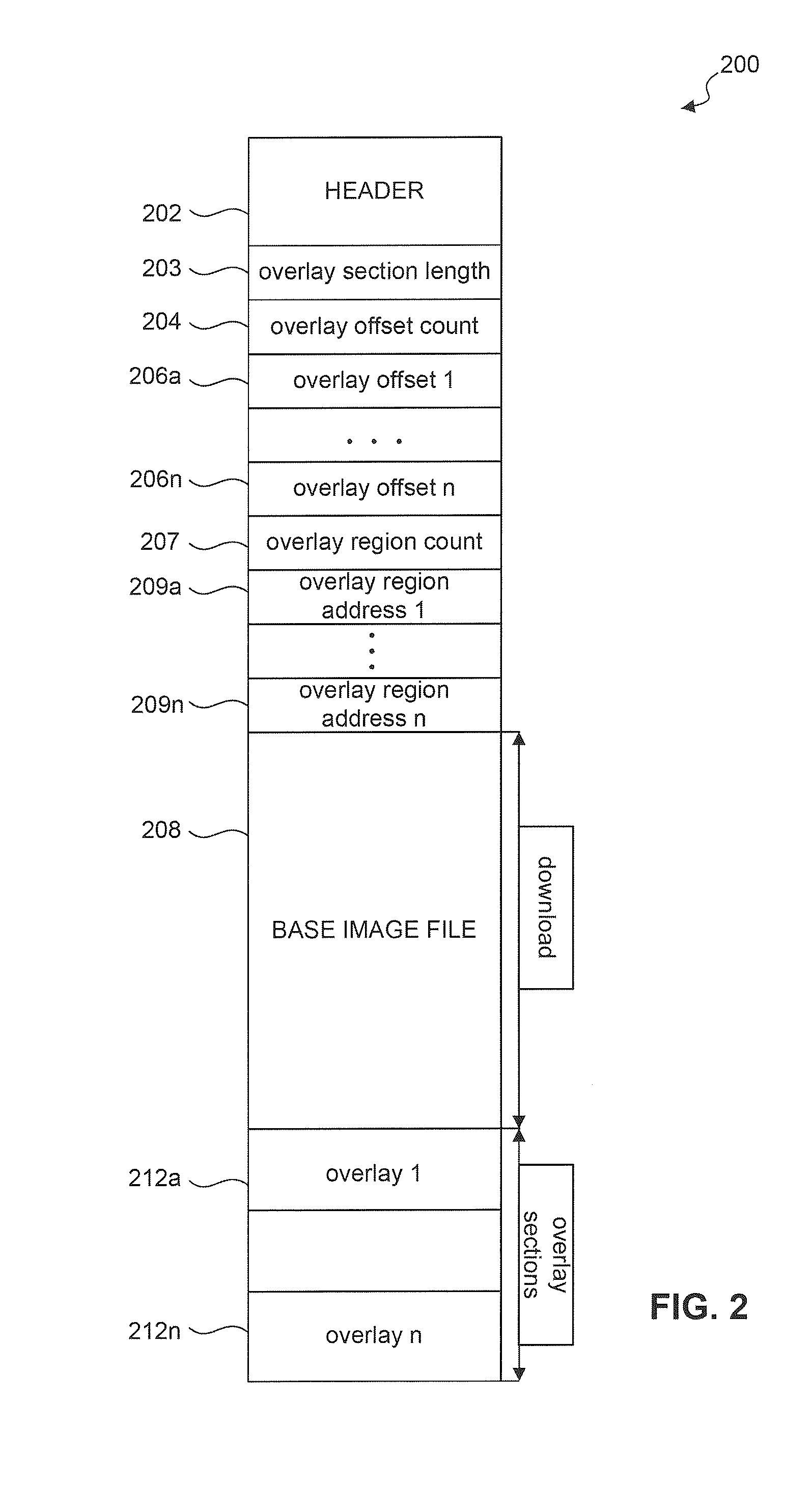
Method and system to transmit code to a system on a chip (SOC)
ActiveUS20110185162A1Energy efficient ICTDigital computer detailsApplication softwareMaster processor
A method and system to transmit code to a System on Chip (SOC) from a host processor using a host-side driver is provided herein. The SOC and host processor are coupled by a bus. The host driver receives an overlay from an application layer and stores the overlay. The host driver receives an IOCTL to be transmitted to the SOC. The host driver determines whether an input / output control (IOCTL) value of the IOCTL to be transmitted to the SOC corresponds to an IOCTL value in one of the stored overlays. The host driver transmits an overlay to the SOC if the IOCTL value of the IOCTL to be transmitted is equal to at least one IOCTL value in the overlay. The host driver then transmits the IOCTL to the SOC.
Owner:AVAGO TECH INT SALES PTE LTD
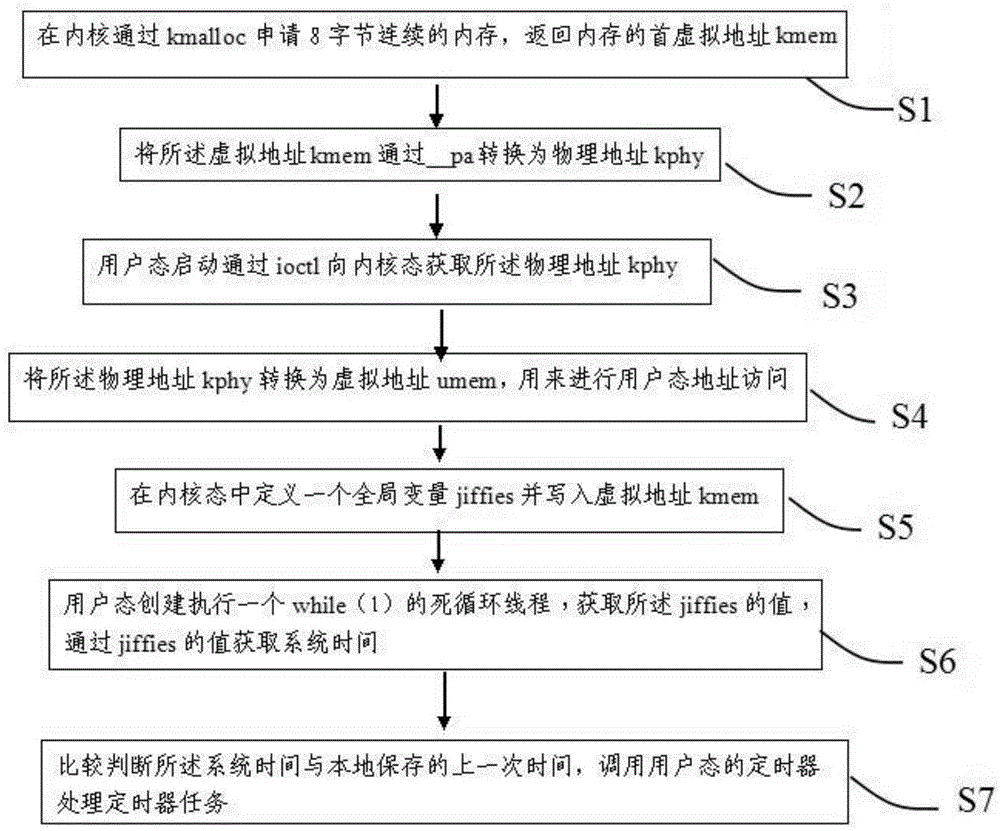
Linux user mode based method and system for calling timer
The present invention discloses a linux user mode based method and system for calling a timer. The method comprises: applying for an 8-byte consecutive memory by means of kmalloc in a kernel, and returning a head virtual address kmem of the memory; converting the virtual address kmem to a physical address kphy by means of _pa; enabling a user mode to acquire the physical address kphy from a kernel mode by means of ioctl; converting the physical address kphy to a virtual address umem, used for accessing a user mode address; defining a global variable jiffies in the kernel mode and writing the global variable into the virtual address kmem; enabling the user mode to create an infinite loop thread for performing a while (1), acquiring a value of the jiffies, and acquiring a system time by means of the value of the jiffies; and comparing and determining the system time and a locally stored last time, and calling a user mode timer to process a timer task. Thus, system calling is reduced, and system performance and efficiency are improved.
Owner:OPZOON TECH
Method for calling user mode function by kernel mode
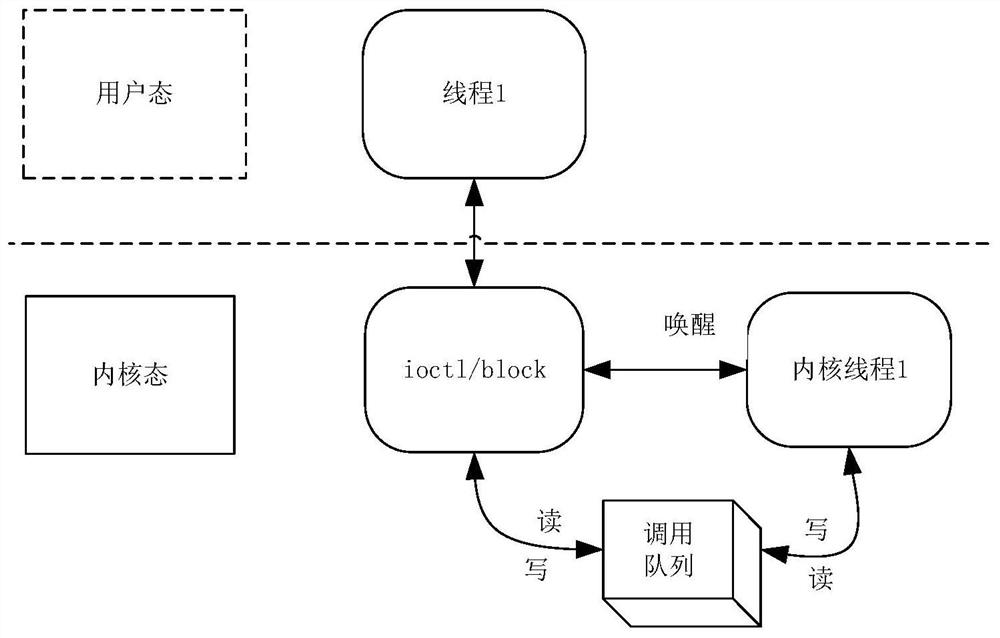
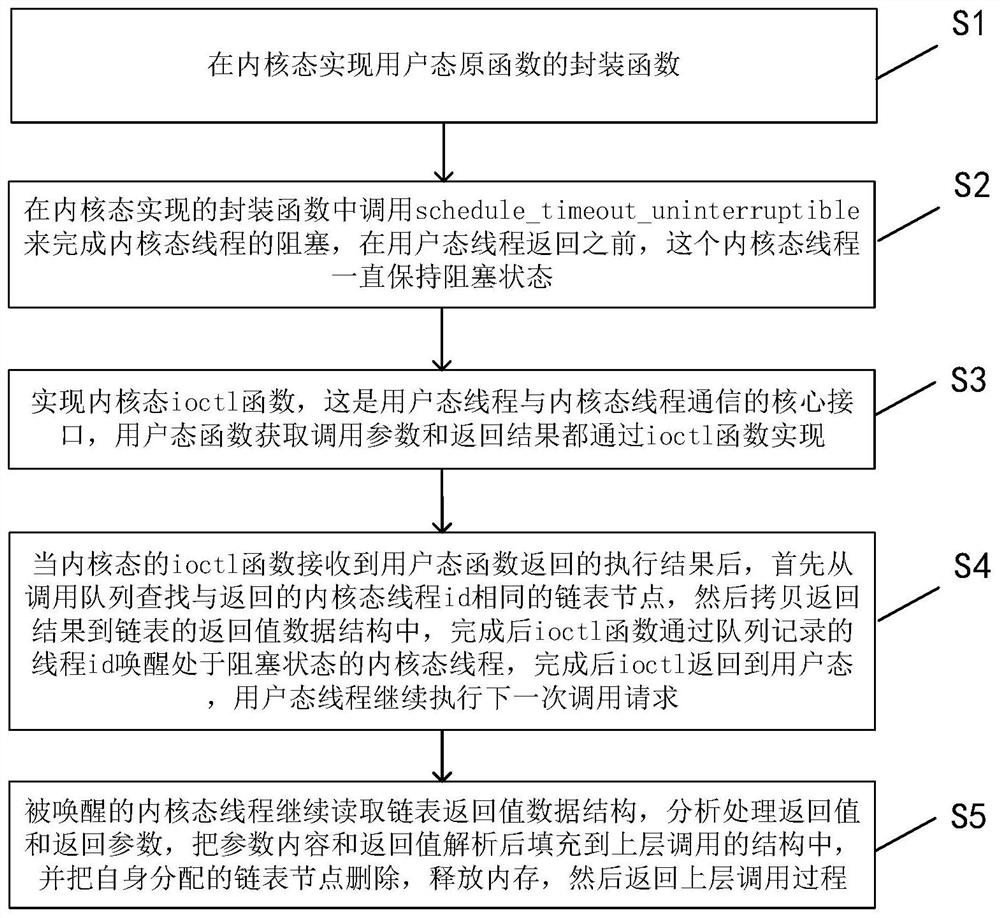
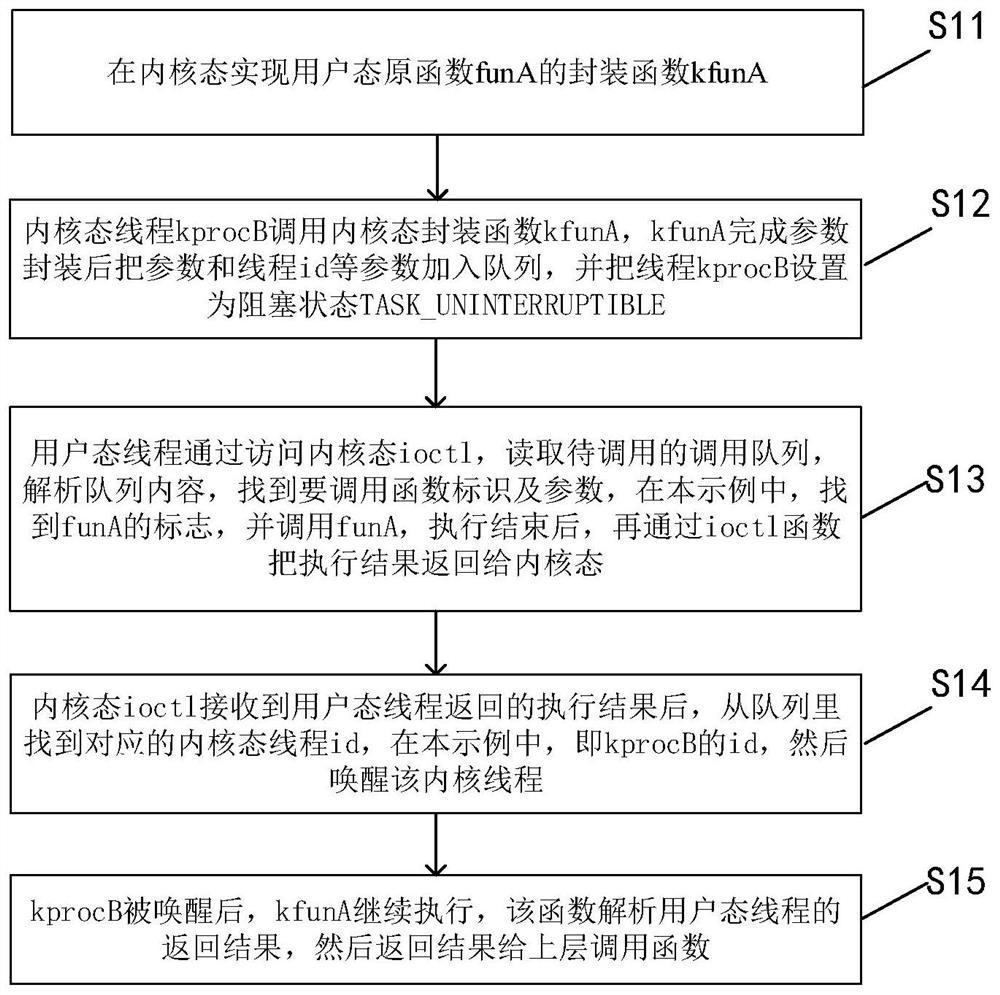
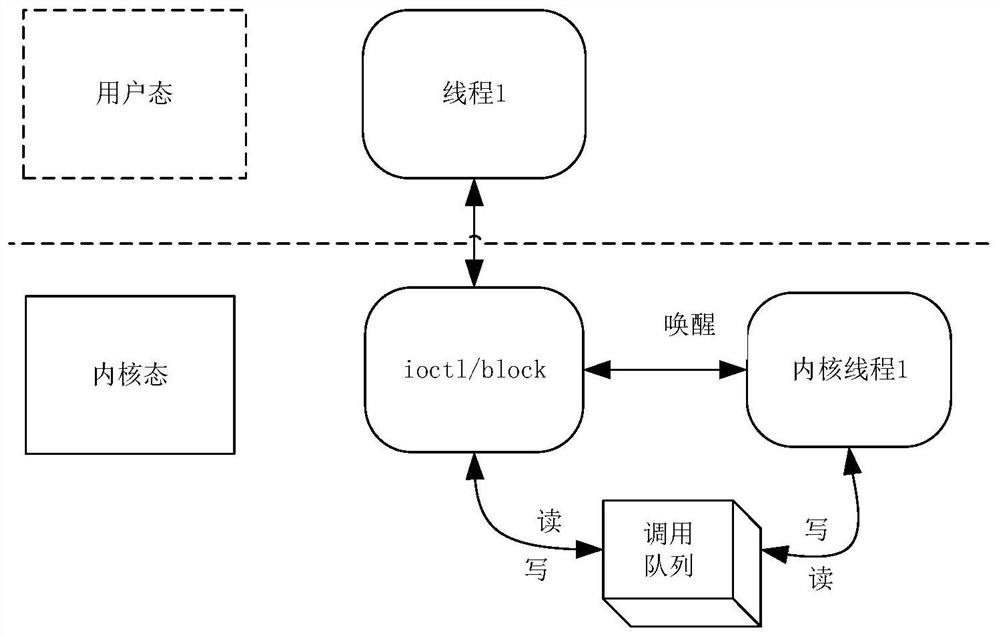
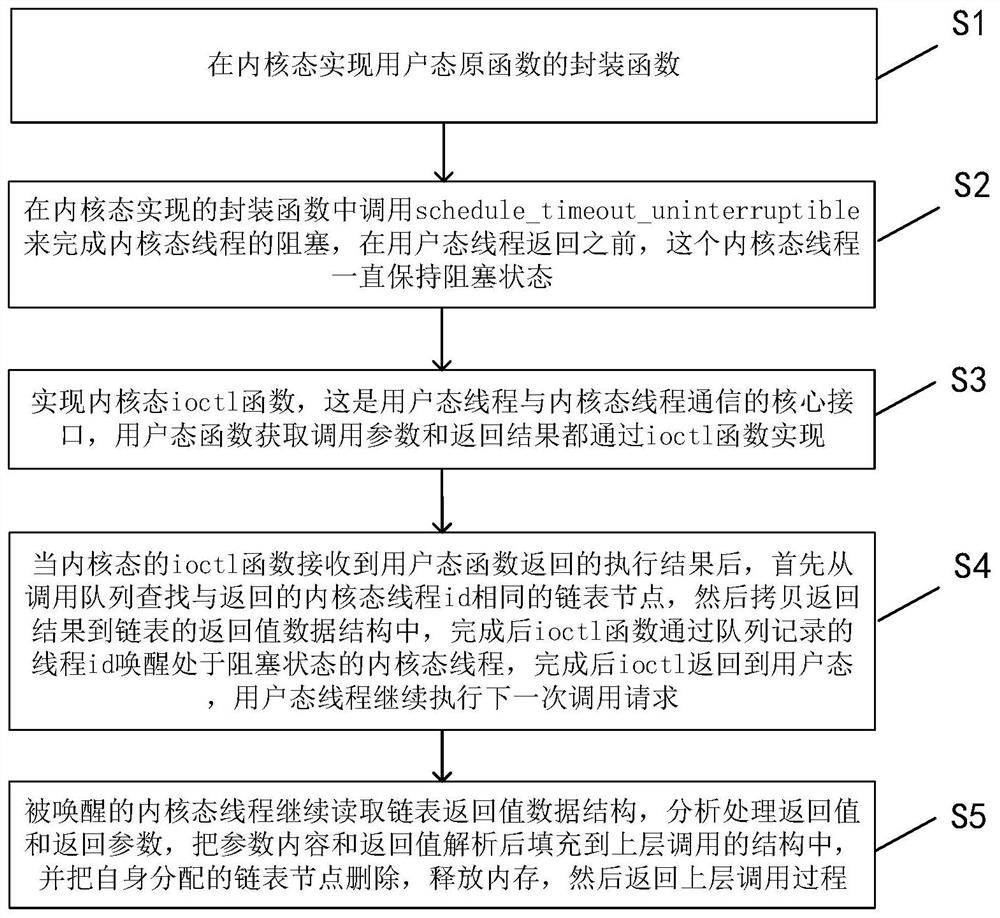
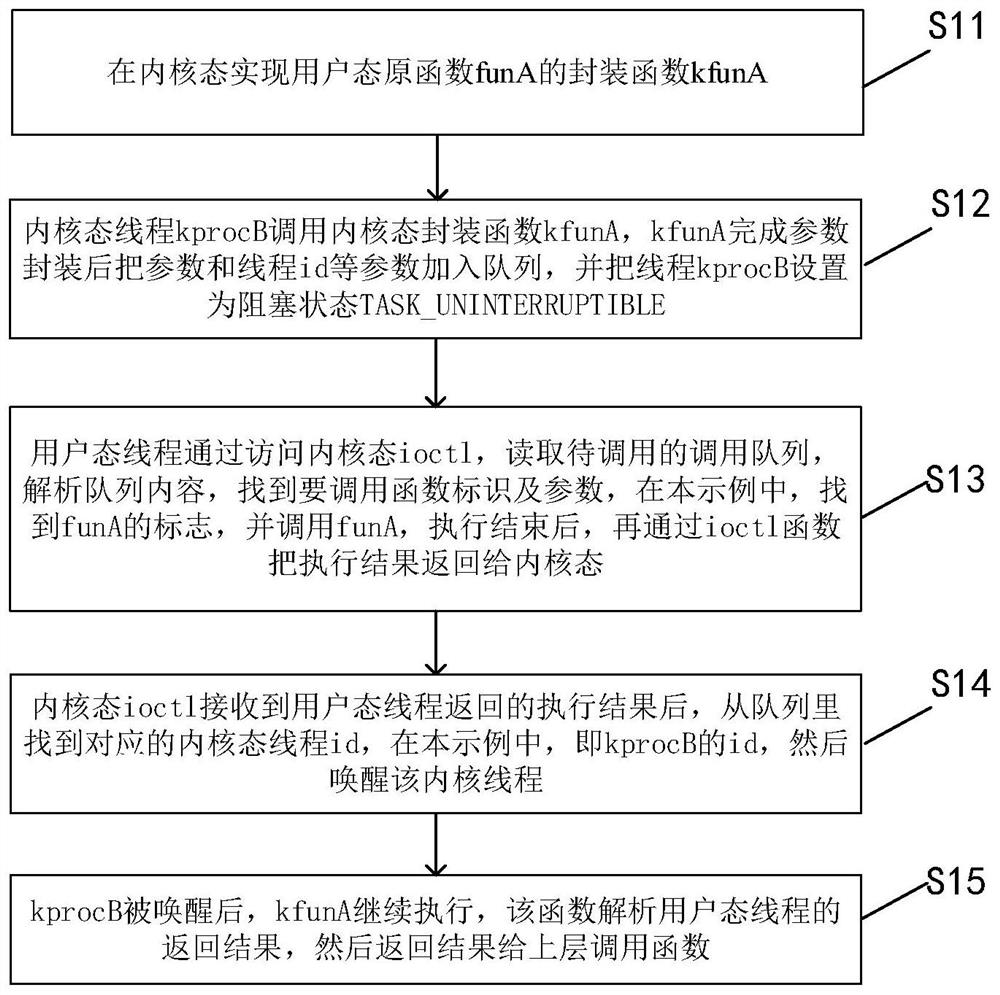
ActiveCN111857993AImplement the callDo not modify logicProgram initiation/switchingInterprogram communicationProgramming languageOperating system
The invention discloses a method for calling a user mode function by a kernel mode. The method comprises the steps that calling of a kernel mode to a user mode function is converted into blocking andawakening of a kernel mode thread; in the kernel mode, parameter encapsulation, kernel mode thread blockage and ioctl message communication of the called user mode function are realized to complete calling of the user mode function; and after the called user mode function returns a calling result, the user mode function return result is sent to the kernel mode through ioctl message communication,and the blocked kernel mode thread is awakened to finish the whole process of function calling. According to the invention, calling of the kernel mode to the user mode function is achieved; under thecondition that kernel logic is not modified, transparent calling from the kernel mode to the user mode is completed in a blocking awakening mode, and logic of an original function is not modified.
Owner:FENGHUO COMM SCI & TECH CO LTD +1
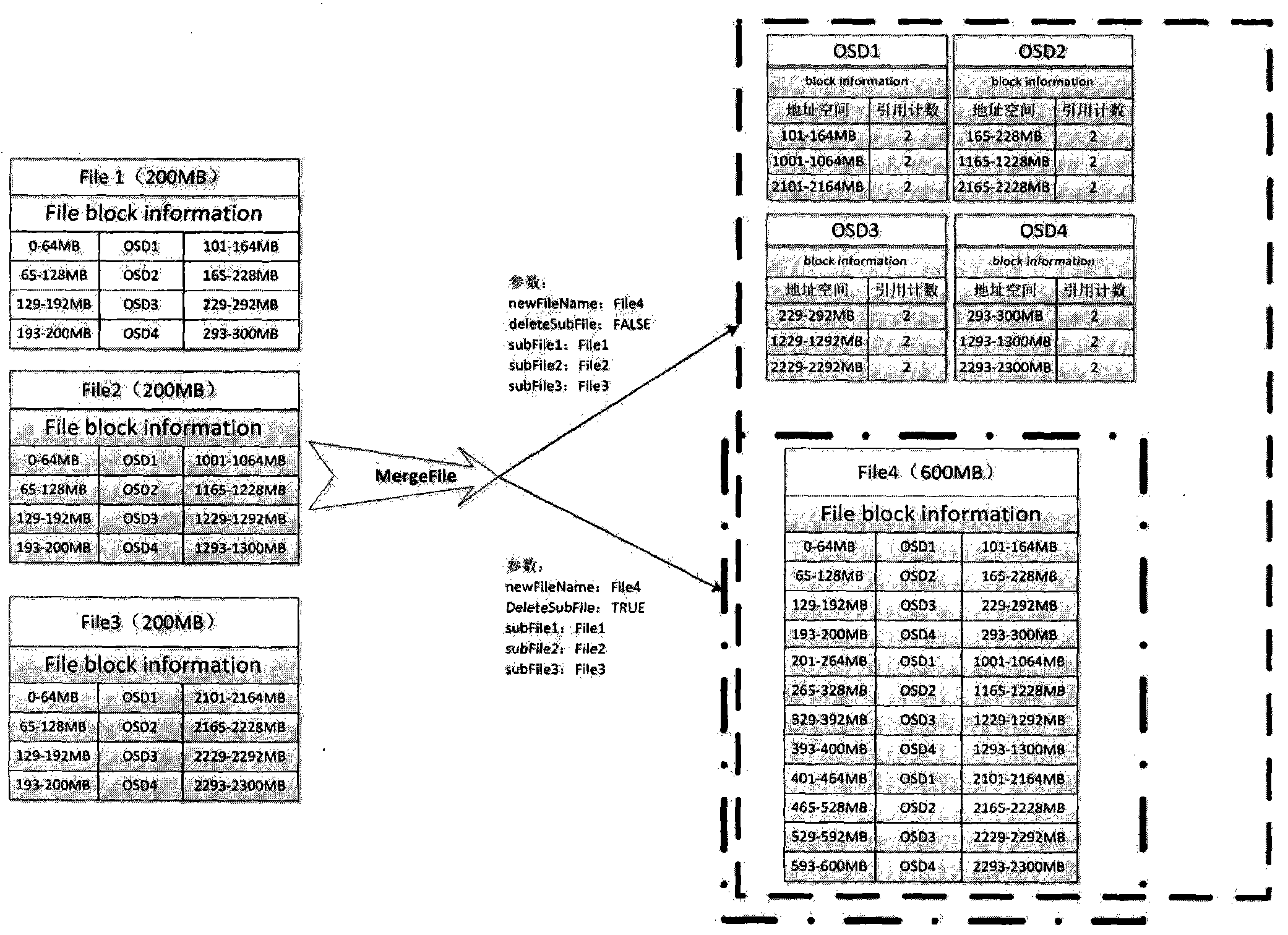
Method for quickly splitting and merging file on basis of restructured file metadata
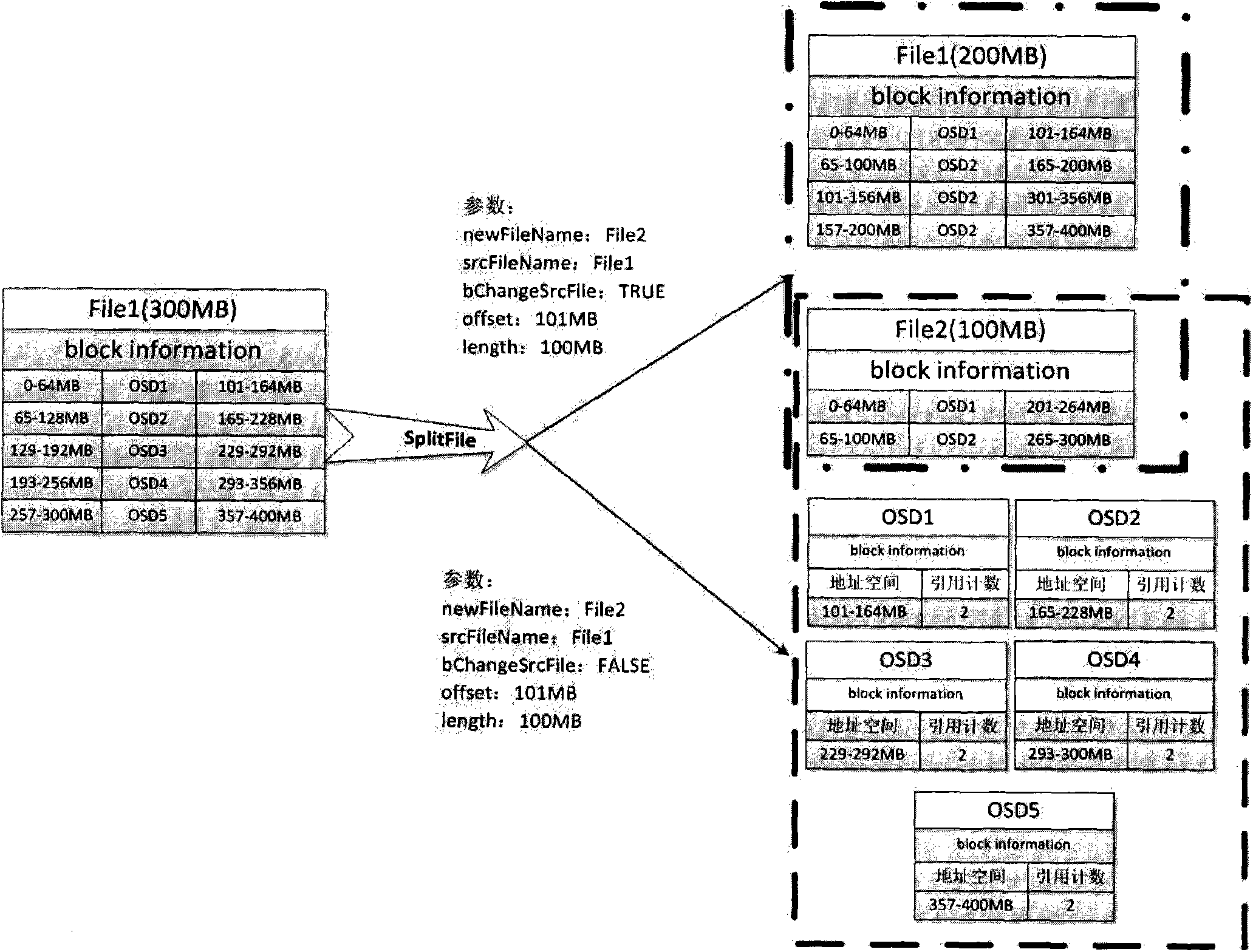
ActiveCN104077409AEasy to cutCombined application convenienceSpecial data processing applicationsFile systemsOperational systemFile system
The invention discloses a method for quickly splitting and merging a file on the basis of restructured file metadata. The method includes the steps that original POSIX file operation interfaces namely newly added file splitting and merging interfaces are extended, the two extension interfaces interact with an inner core of an operation system in an IOCTL mode, and work procedures of the Split File interface and work procedures of the Merge File interface are carried out. Convenience is brought to applications needing file splitting and merging, coping cost in the file splitting and merging processes is eliminated, the method is very effective to a distributive file system, a large quantity of I / O operations are eliminated and performance of the applications such as file splitting and merging is substantially improved.
Owner:BEIJING LOONGSTORE TECH
Synchronous RIL proxy
InactiveUS7886311B2Efficient communicationEasy to useMultiprogramming arrangementsSubstation equipmentApplication programming interfaceApplication software
Owner:MICROSOFT TECH LICENSING LLC
Providing a secure communication channel between kernel and user mode components
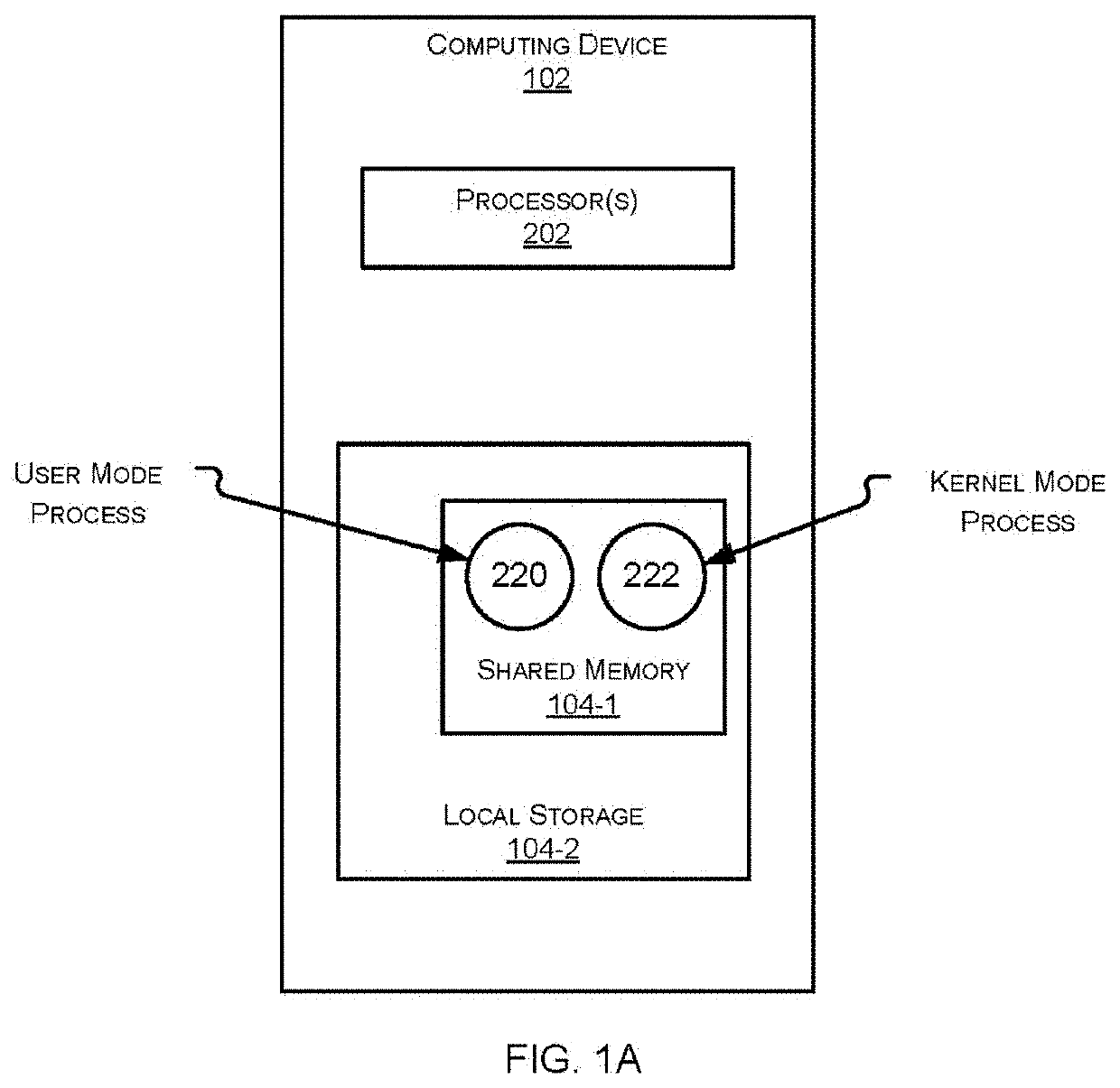
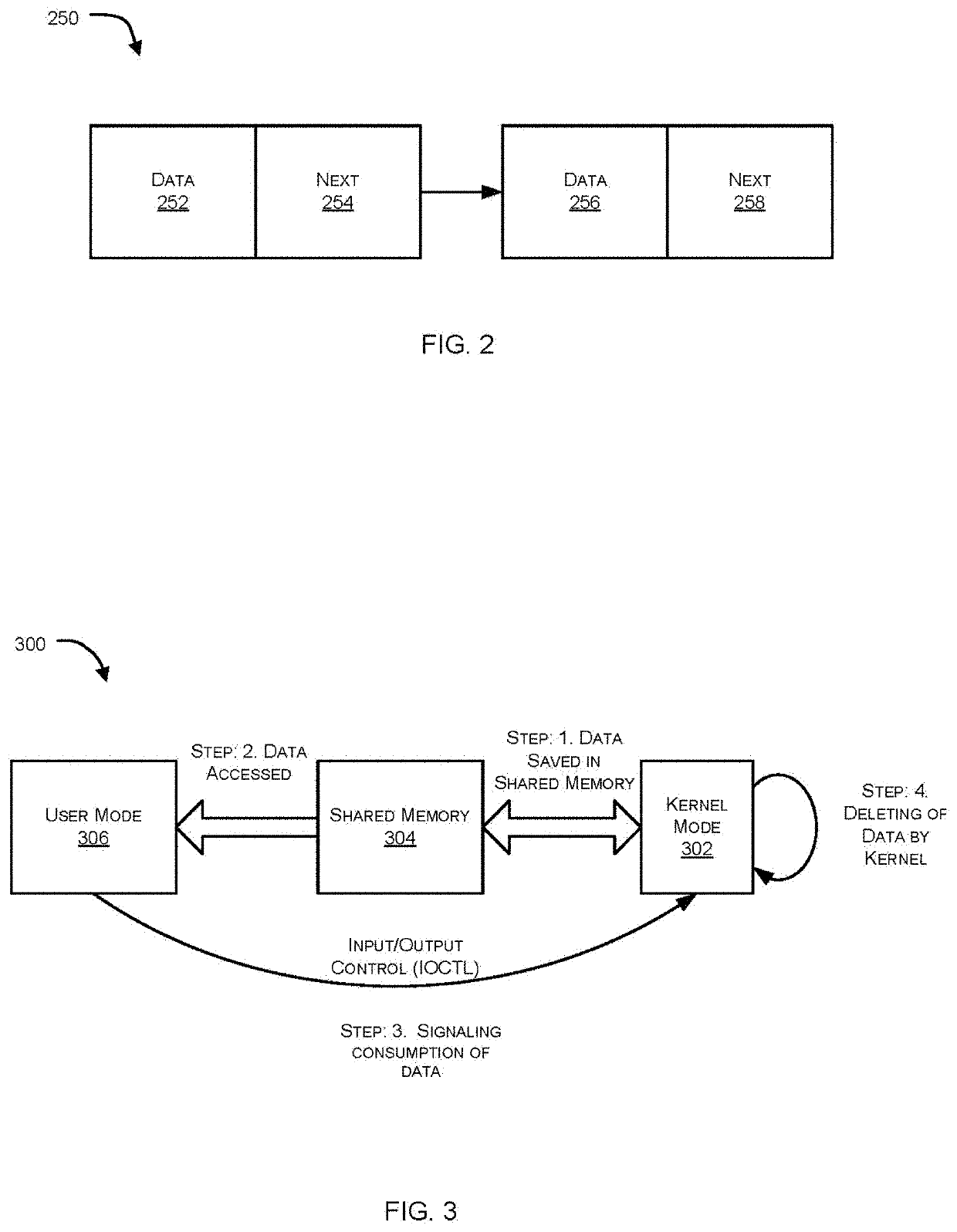
ActiveUS20210279184A1Memory architecture accessing/allocationMemory adressing/allocation/relocationSecure communicationComputer network
Systems and methods for implementing a secure communication channel between kernel and user mode components are provided. According to an embodiment, a shared memory is provided through which a kernel mode process and a user mode process communicate. The kernel mode process is assigned read-write access to the shared memory. The user mode process is assigned read-only access to the shared memory. An offset-based linked list is implemented within the shared memory. Kernel-to-user messages are communicated from the kernel mode process to the user mode process by adding corresponding nodes to the offset-based linked list. One or more kernel-to-user messages are read by the user mode process following the offset-based linked list in order. The kernel mode process is signaled by the user mode process that a kernel-to-user message has been consumed by the user mode process through an input output control (ioctl) system call or an event object.
Owner:FORTINET
Application programming interface for fusion message passing technology
ActiveUS7761630B2Improve application development efficiencyMultiple digital computer combinationsSpecific program execution arrangementsData processing systemApplication programming interface
Owner:NETWORK APPLIANCE INC +1
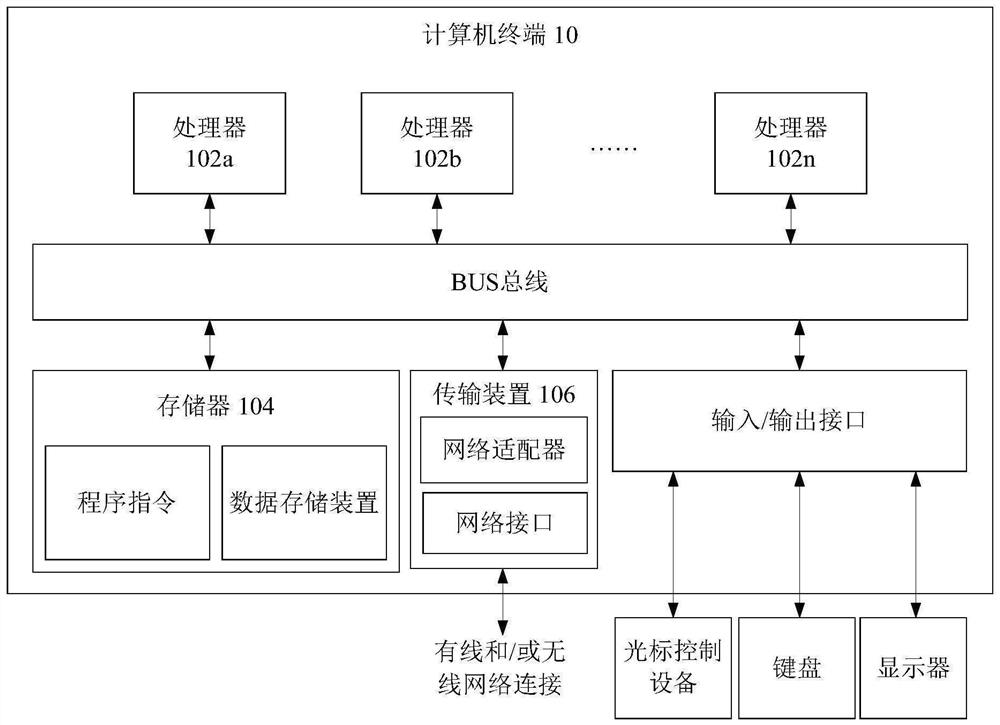
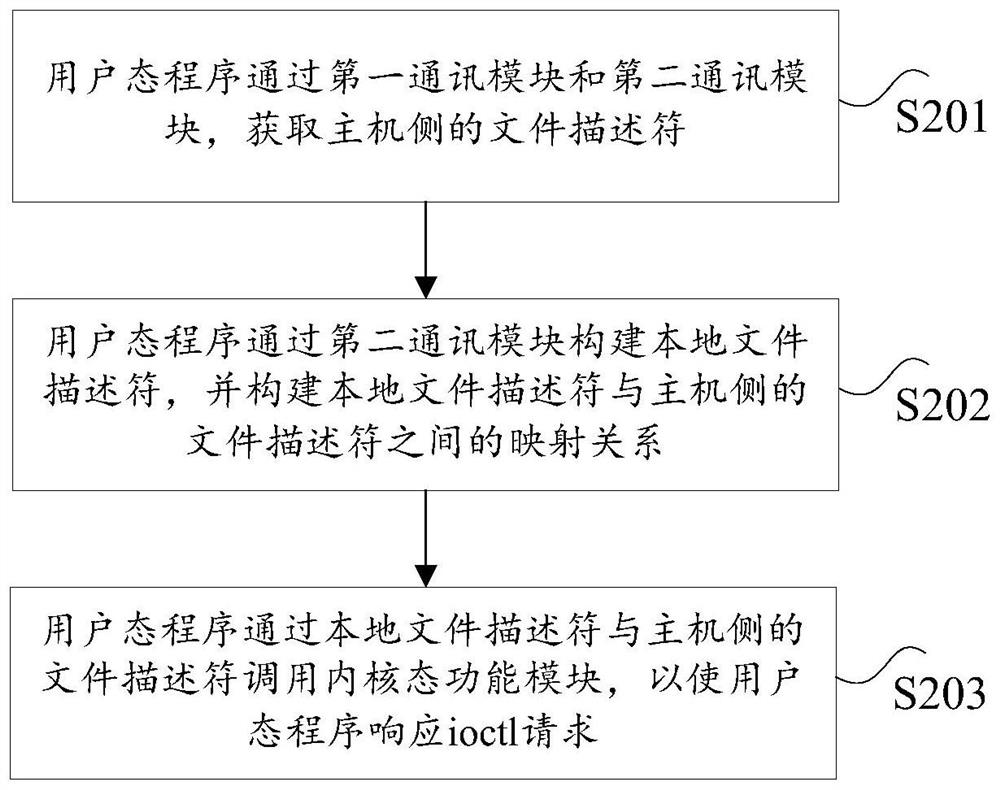
User mode program processing method and device, storage medium and processor
PendingCN114691390AImprove efficiencySolve technical problems with low efficiencyInterprogram communicationProgram loading/initiatingFile descriptorProcessing
The invention discloses a user mode program processing method and device, a storage medium and a processor. The method comprises the steps that the user mode program obtains a file descriptor on the host side through a first communication module and a second communication module, and the file descriptor on the host side is an identifier corresponding to a kernel mode function module needing to be called by the user mode program; the user mode program constructs a local file descriptor through the second communication module, and constructs a mapping relation between the local file descriptor and the file descriptor on the host side; and the user mode program calls the kernel mode function module through the local file descriptor and the file descriptor on the host side, so that the user mode program responds to the ioctl request. According to the method and the device, the technical problem that the efficiency is relatively low due to the fact that the normal operation of the business of the user mode program is realized by adopting a syscale remote agent mode is solved.
Owner:ALIBABA (CHINA) CO LTD
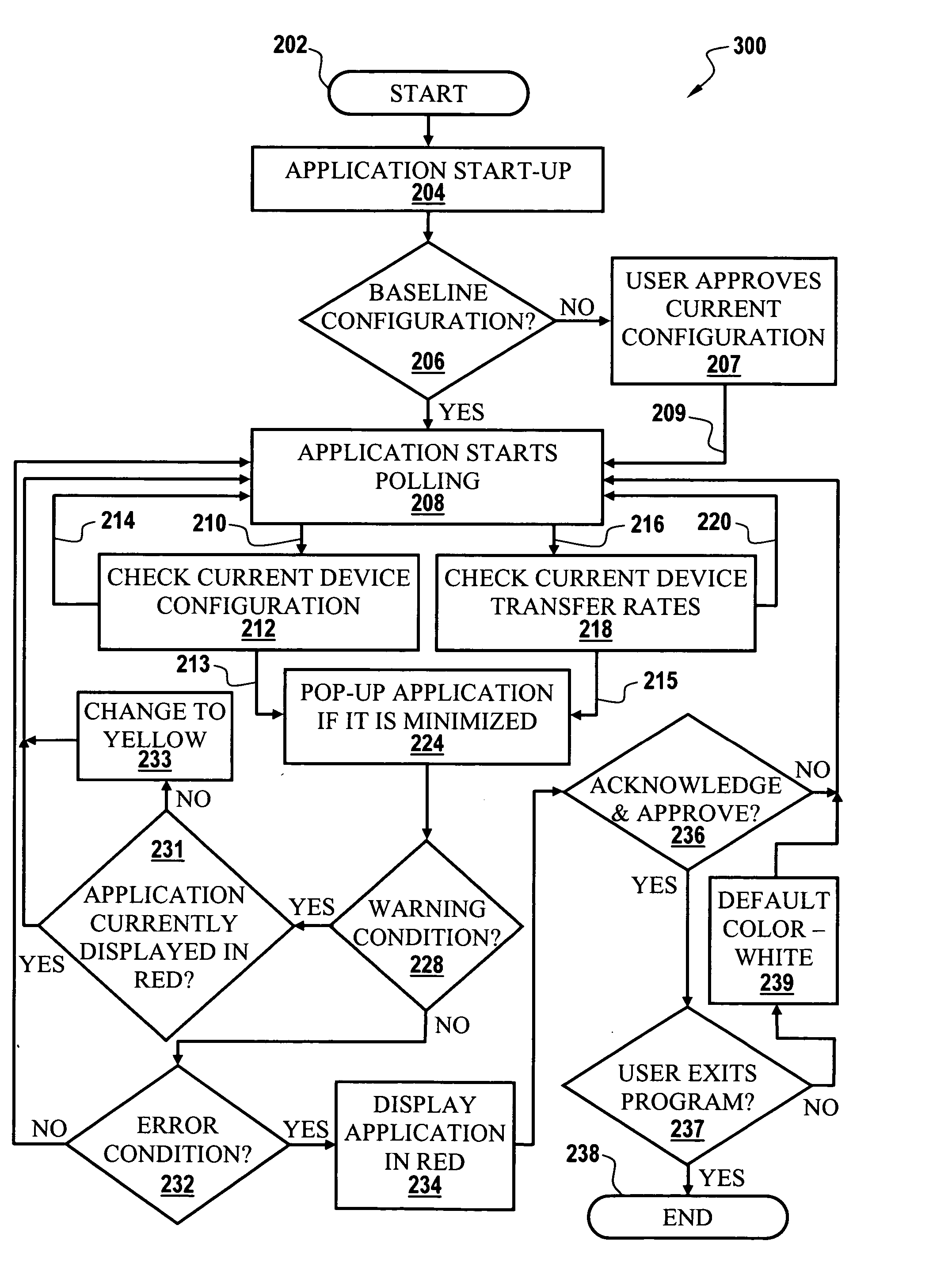
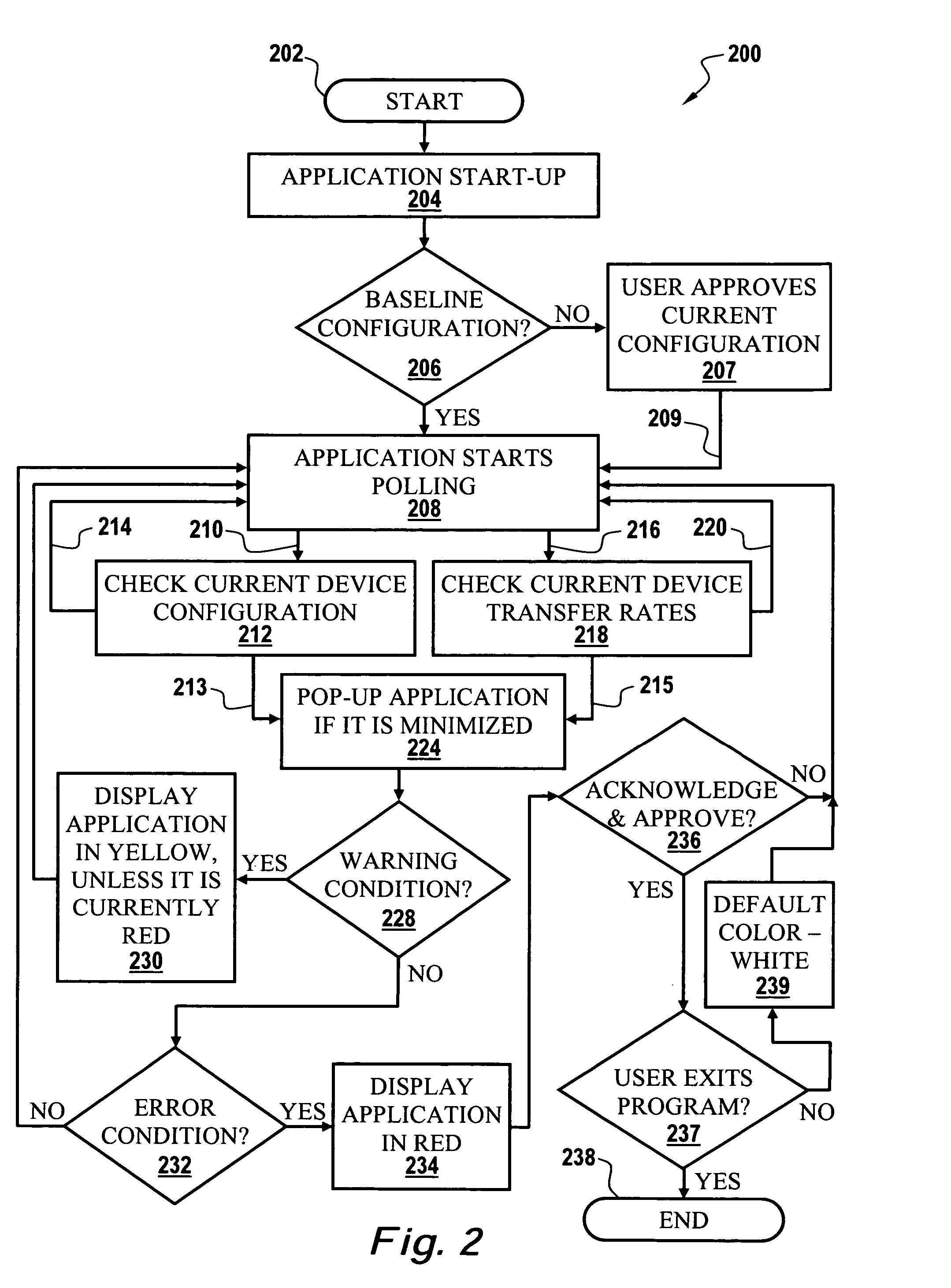
Methods and systems for unattended tracking of device transfer rates and reporting of performance degradation
InactiveUS20060074583A1Easy to understandSimple methodResistance/reactance/impedenceError detection/correctionOperational systemMessage Passing Interface
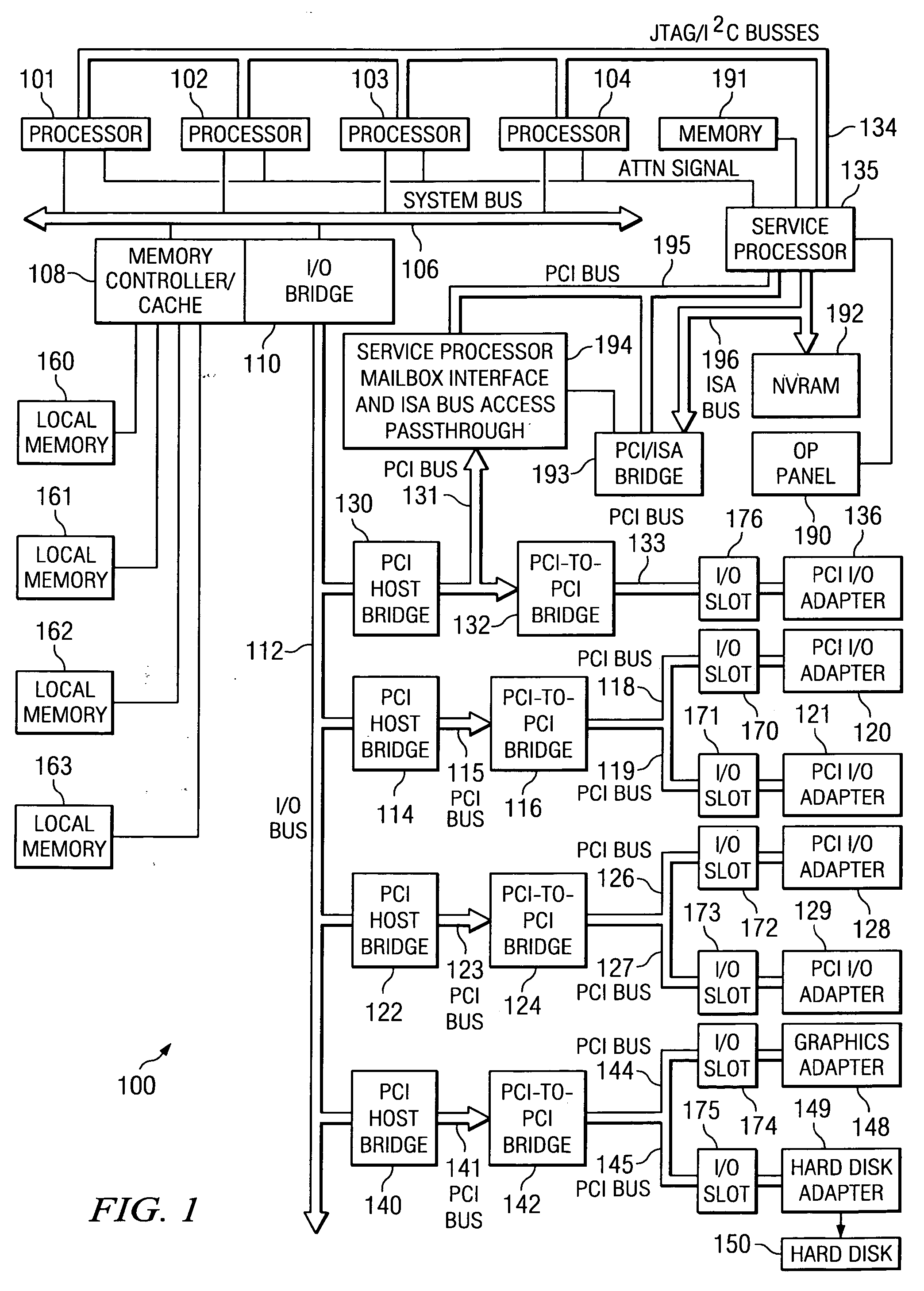
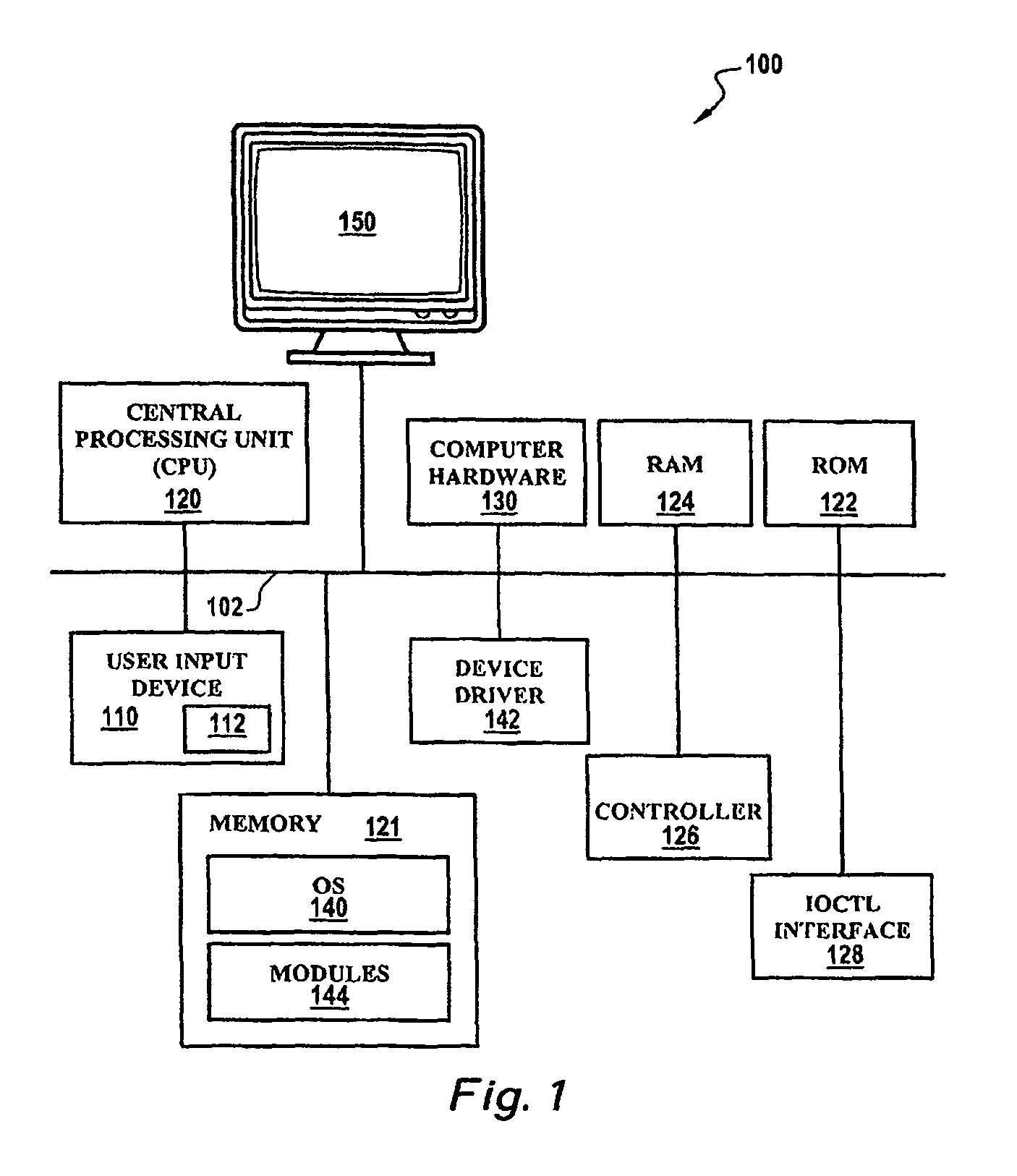
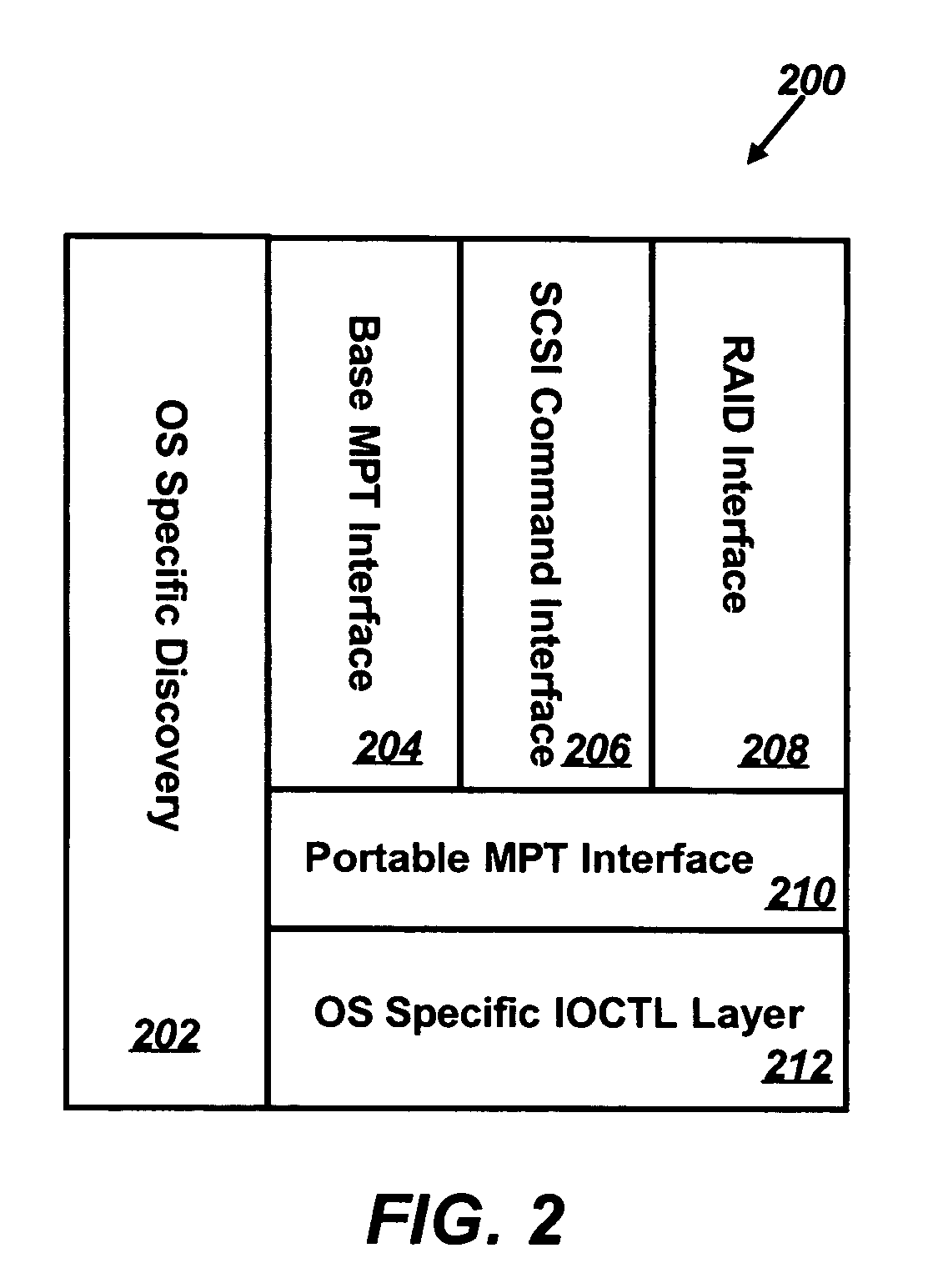
An operating system's input / output control (IOCTL) interface can communicate with one or more device drivers, which may be implemented as Message Passing Technology (MPT) based drivers. At start-up and at user-defined intervals, Message Passing Interface (MPI) pass-through messages can be sent utilizing the IOCTL interface. Such messages can be formatted as Configuration Page Request messages, and can then return data that includes the current negotiated rates and widths for all devices connected via the bus. Whenever a drop in rate occurs for any device connected to the bus, the event will be logged, and the user informed. Utilizing such technology, device transfer rates can be automatically tracked performance degradation thereof reported.
Owner:LSI CORPORATION
Method and system to transmit code to a system on a chip (SOC)
A method and system to transmit code to a System on Chip (SOC) from a host processor using a host-side driver is provided herein. The SOC and host processor are coupled by a bus. The host driver receives an overlay from an application layer and stores the overlay. The host driver receives an IOCTL to be transmitted to the SOC. The host driver determines whether an input / output control (IOCTL) value of the IOCTL to be transmitted to the SOC corresponds to an IOCTL value in one of the stored overlays. The host driver transmits an overlay to the SOC if the IOCTL value of the IOCTL to be transmitted is equal to at least one IOCTL value in the overlay. The host driver then transmits the IOCTL to the SOC.
Owner:AVAGO TECH INT SALES PTE LTD
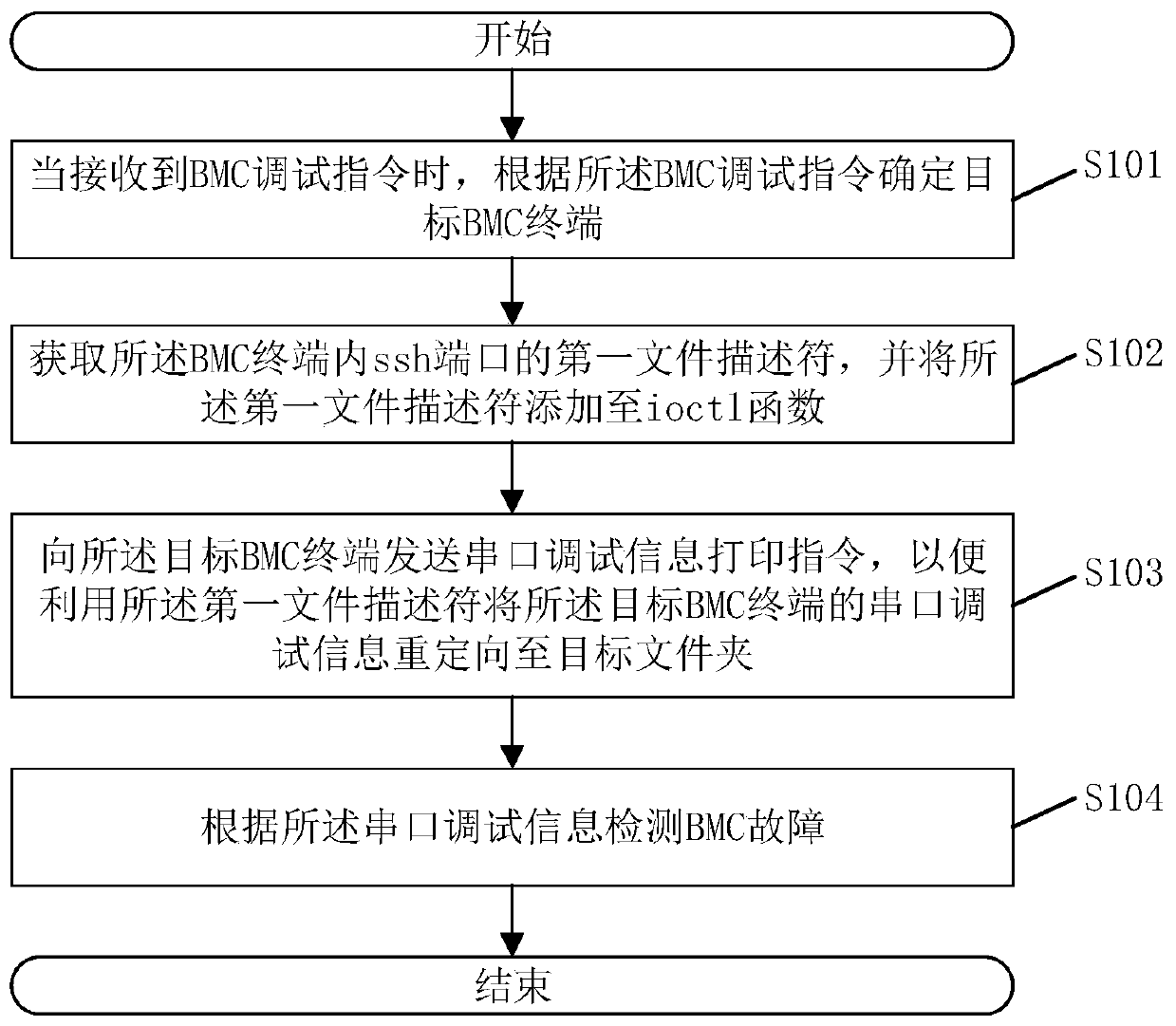
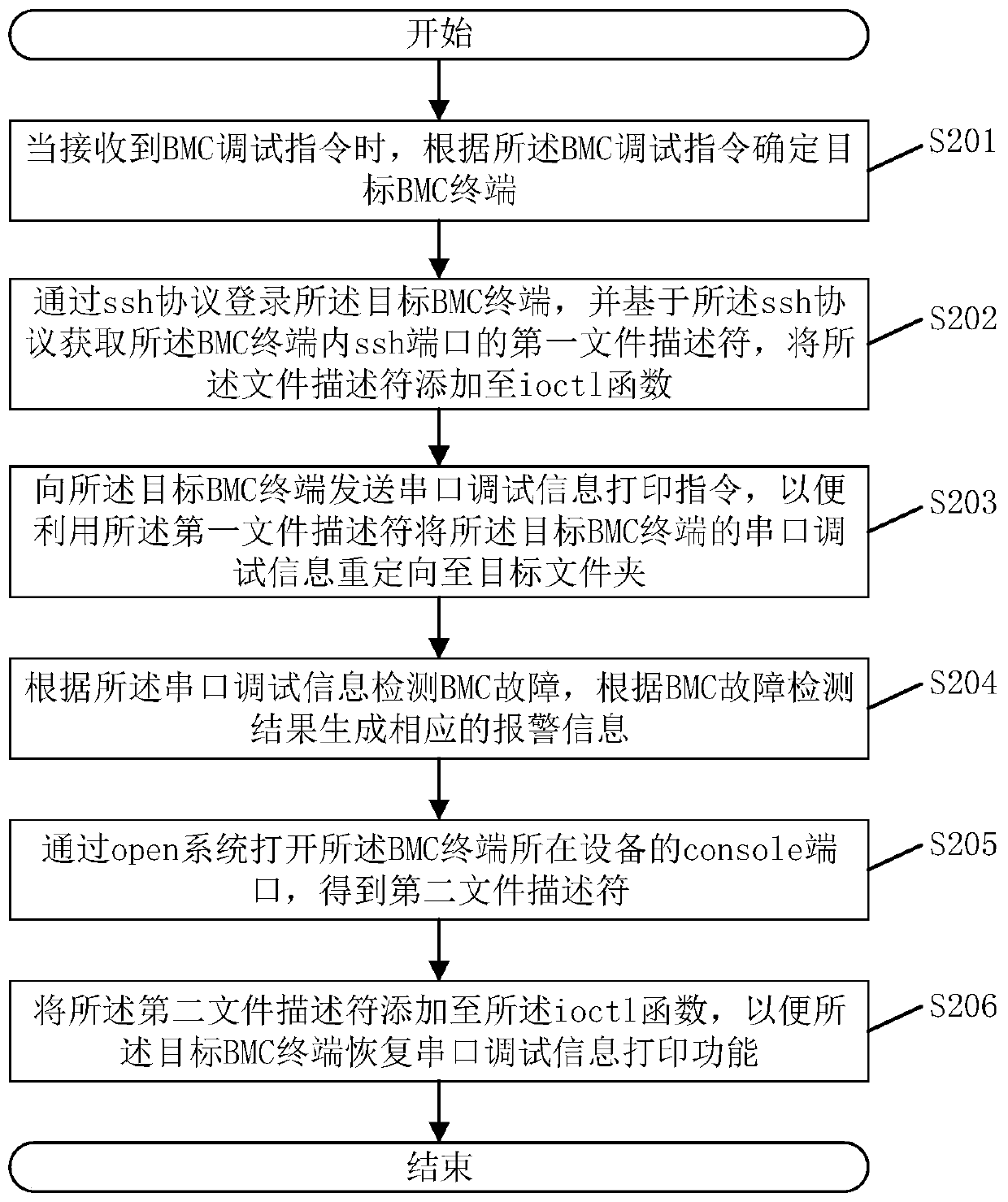
BMC fault detection method and system and related components
ActiveCN110134559ASolve the inconvenience of accessImprove convenienceDetecting faulty computer hardwareFile descriptorObject file
The invention discloses a BMC fault detection method, and the method comprises the steps: determining a target BMC terminal according to a BMC debugging instruction when the BMC debugging instructionis received; obtaining a first file descriptor of an ssh port in the BMC terminal, and adding the first file descriptor to an ioctl function; sending a serial port debugging information printing instruction to the target BMC terminal so as to redirect the serial port debugging information of the target BMC terminal to a target folder by using the first file descriptor; and detecting a BMC fault according to the serial port debugging information. According to the method, the convenience of obtaining the serial port debugging information of the BMC can be improved, and BMC faults can be rapidlydetected. The invention also discloses a BMC fault detection system, a computer readable storage medium and electronic equipment, which have the above beneficial effects.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
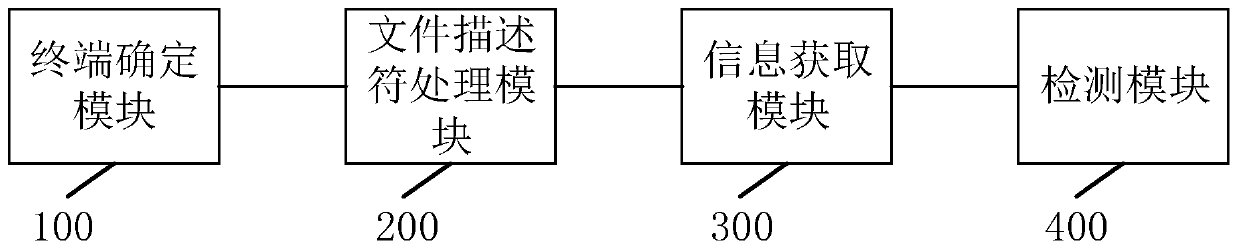
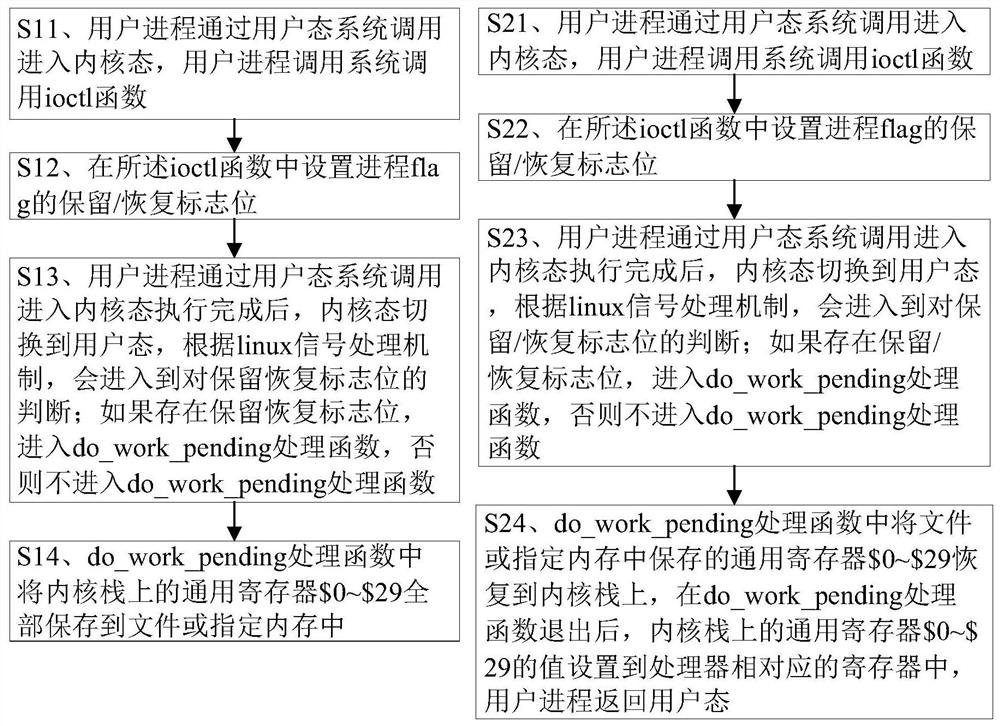
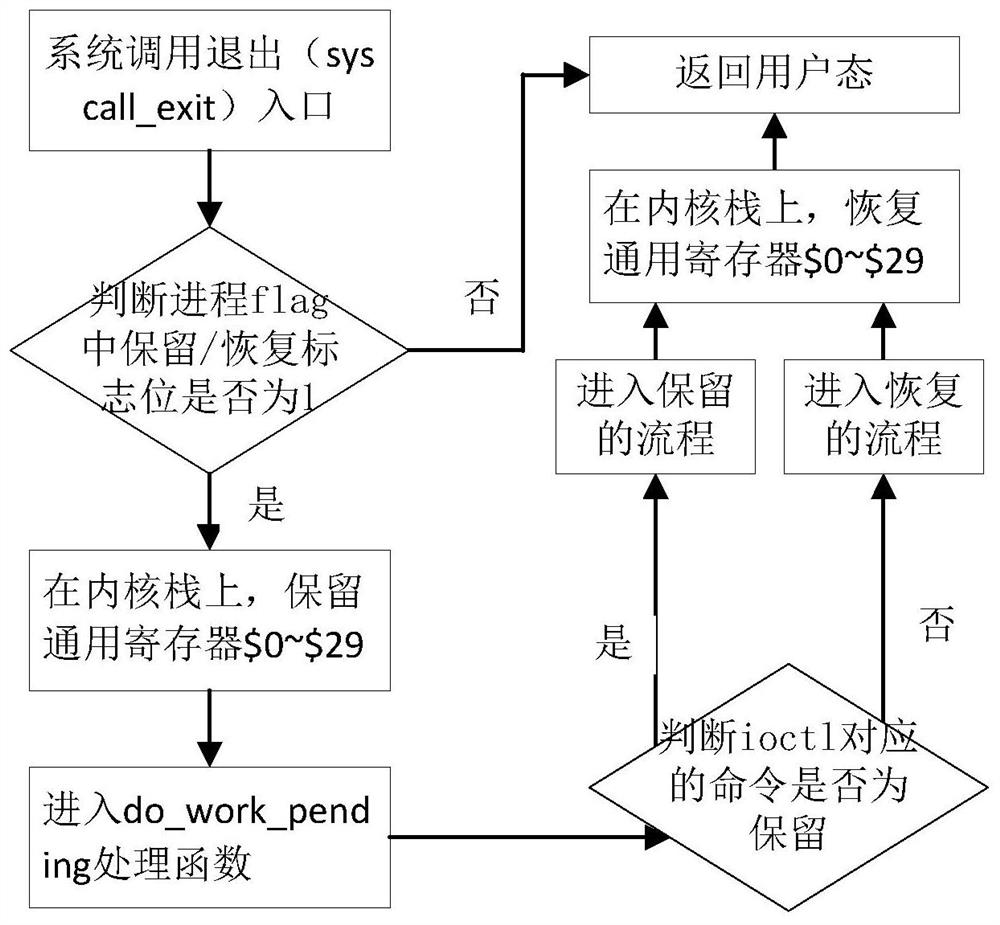
Implementation method for general register reservation recovery
ActiveCN112540871ARegister arrangementsInterprogram communicationParallel computingSoftware engineering
The invention discloses a method for realizing retention and recovery of a universal register. The process retention method comprises the following steps: enabling a user process to call a system callioctl function; setting a process flag retention / recovery flag bit in the ioctl function; switching a kernel mode to a user mode, and entering judgment on a reservation / recovery flag bit according toa linux signal processing mechanism; if the reservation / recovery flag bit exists, entering a do_work_pending processing function; and storing all the general registers $0-$29 on the kernel stack intoa file or a specified memory by the do_work_pending processing function; according to the process recovery method, the first three steps are the same as the steps of the process retention method, andthe process recovery method also comprises the steps: switching a kernel mode to a user mode, and entering the judgment on a retention / recovery flag bit according to a linux signal processing mechanism; if the reservation / recovery flag bit exists, entering the do_work_pending processing function; and recovering a file or a universal register $0-$29 stored in a specified memory to the kernel stackin the do_work_pending processing function, and returning a user state by the user process after the do_work_pending processing function exits. The problem that a general register is not completely reserved is solved.
Owner:JIANGNAN INST OF COMPUTING TECH
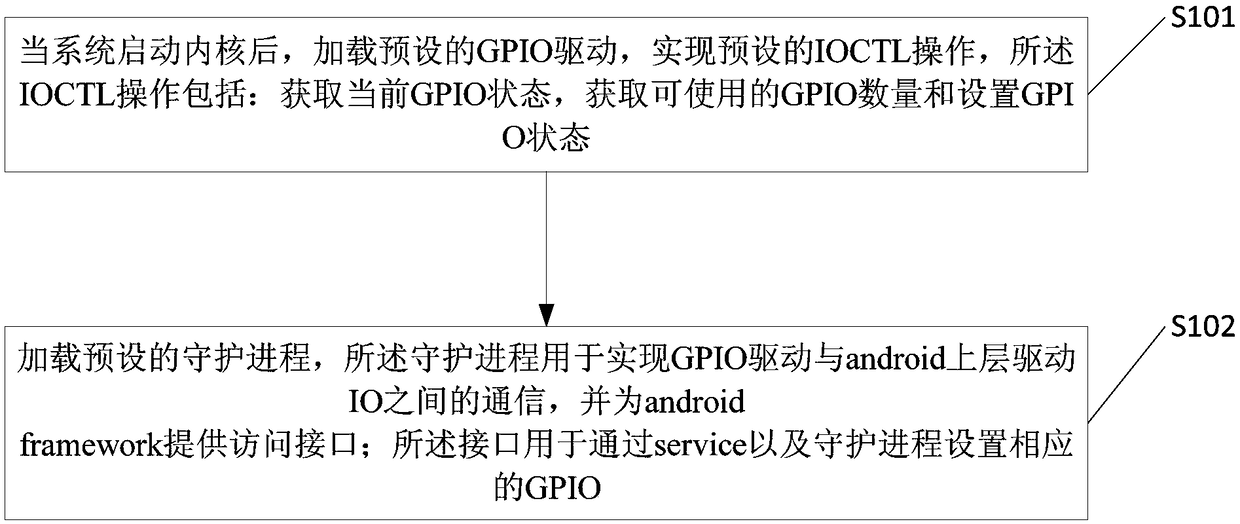
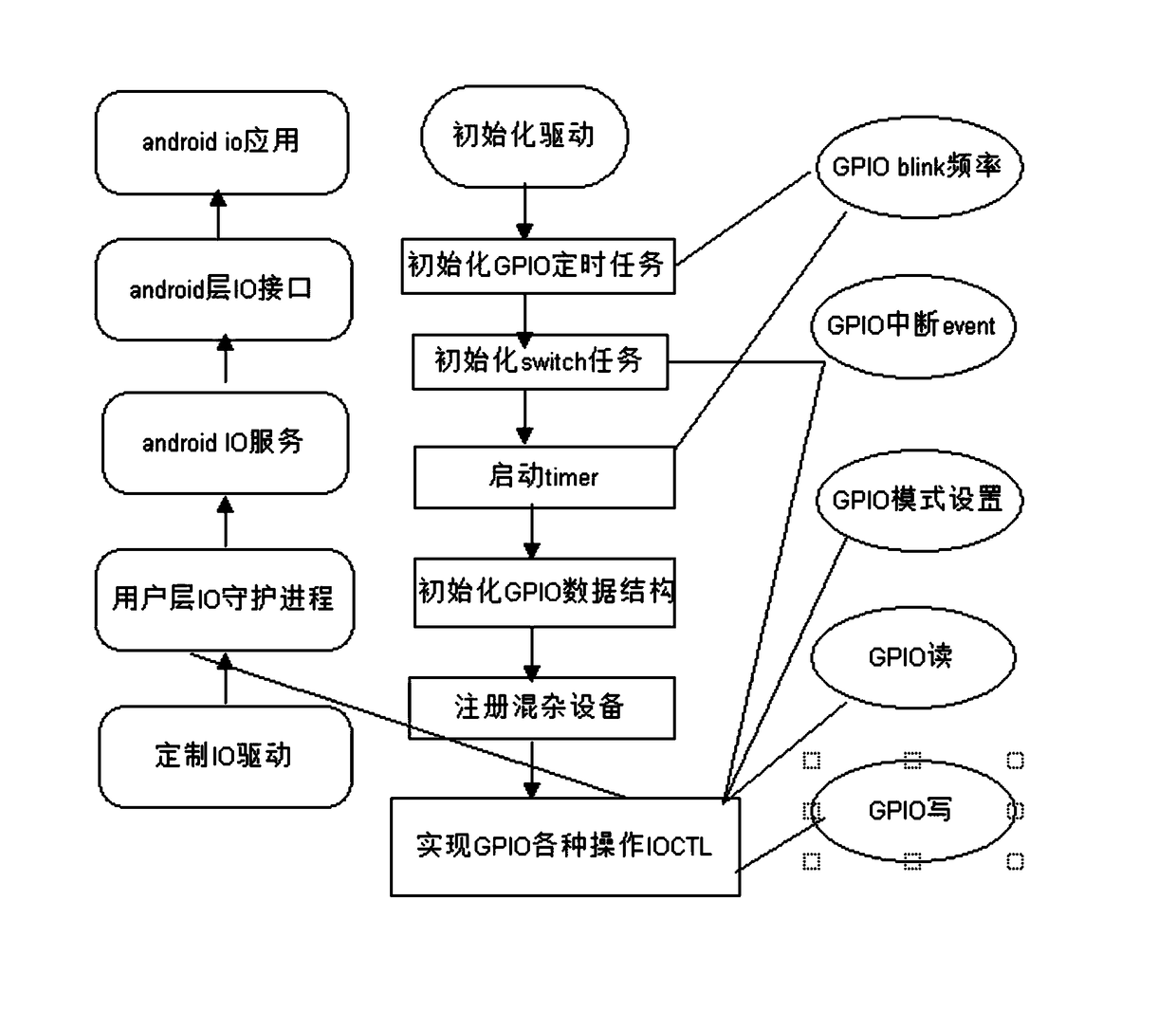
Method for realizing android upper layer driving IO and related products
Owner:深圳市智微智能科技股份有限公司
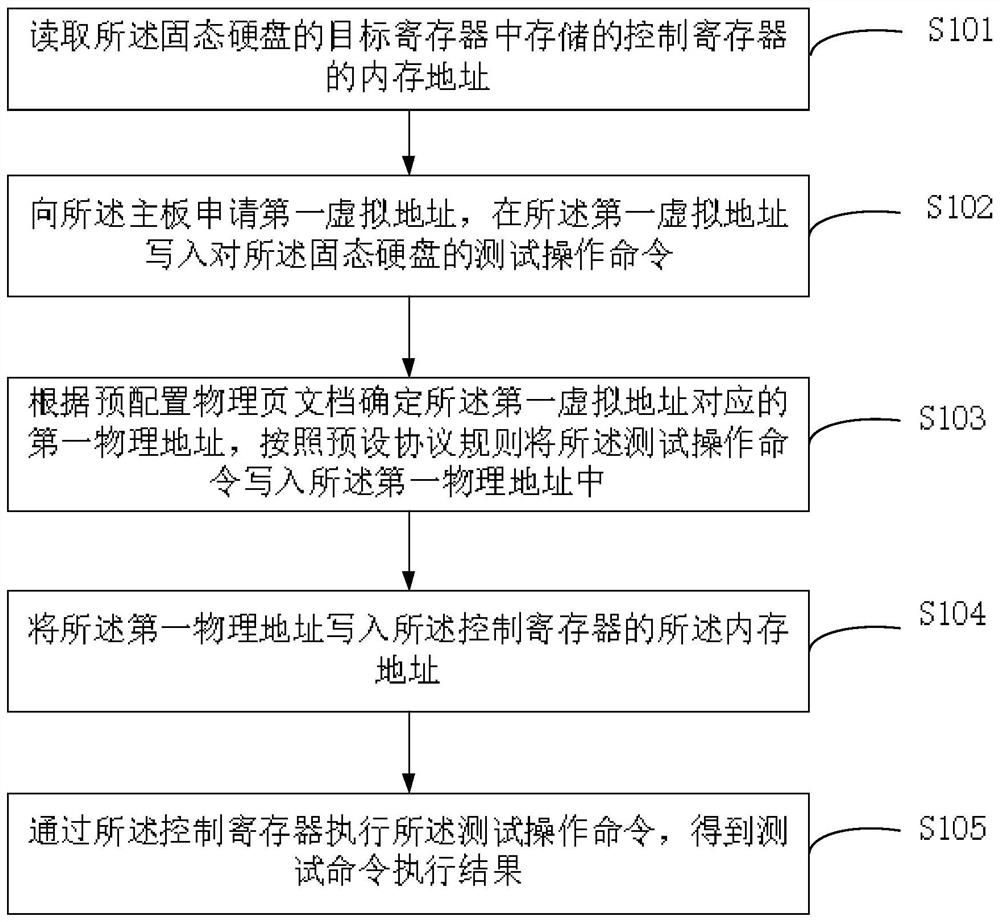
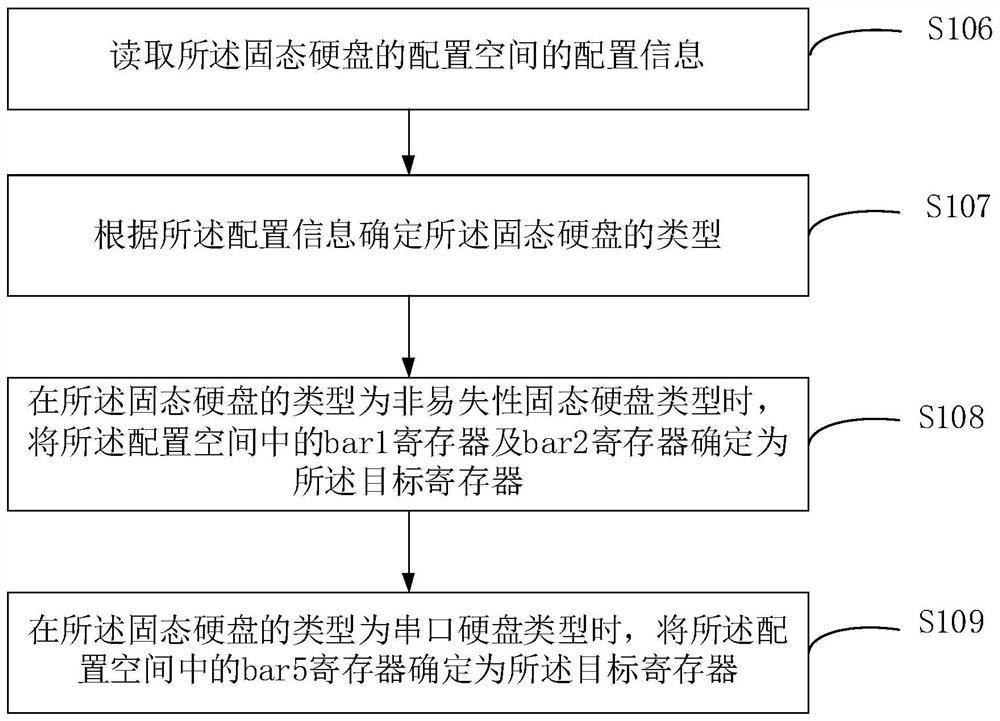
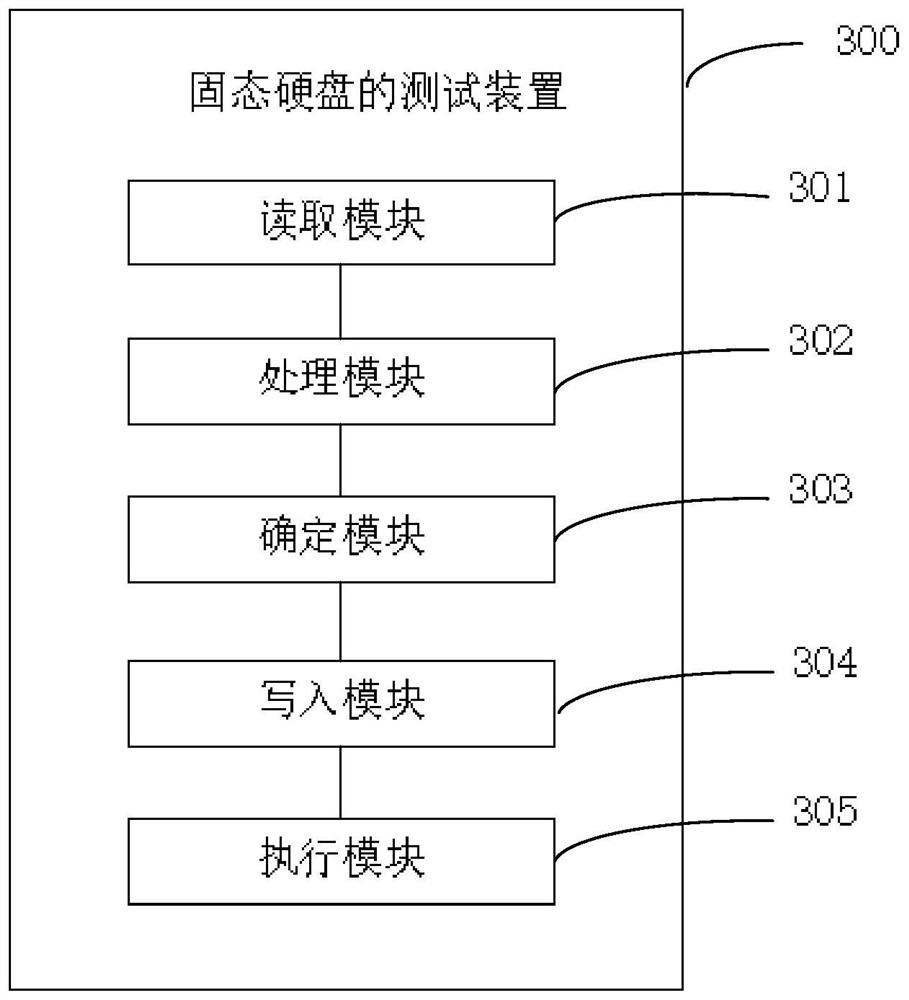
Solid state disk testing method and device and electronic equipment
PendingCN113948146AImprove test resultsReduce testing costsStatic storageMemory addressControl register
The embodiment of the invention provides a solid state disk testing method and device and electronic equipment. The method comprises the following steps: reading a memory address of a control register stored in a target register of a solid state disk ; applying a first virtual address to the mainboard, andwriting a test operation command for the solid state disk in the first virtual address; determining a first physical address corresponding to the first virtual address according to the pre-configured physical page document, and writing the test operation command into the first physical address according to a preset protocol rule; writing the first physical address into a memory address of a control register; and executing the test operation command through the control register to obtain a test command execution result. Therefore, the use of a packaged ioctl function is avoided, the linux application layer can send the test operation command to the solid state disk, the test effect of the solid state disk is improved, and the test cost of the solid state disk is reduced.
Owner:JIANGSU XINSHENG INTELLIGENT TECH CO LTD
A method for calling user mode functions from kernel mode
ActiveCN111857993BImplement the callDo not modify logicProgram initiation/switchingInterprogram communicationTheoretical computer scienceOperating system
The invention discloses a method for invoking a user mode function in a kernel mode, comprising: converting the invocation of the user mode function in the kernel mode into blocking and waking up the kernel mode thread; realizing the parameters of the invoked user mode function in the kernel mode Encapsulation, kernel mode thread blocking, ioctl message communication to complete the user mode function call, when the called user mode function returns the call result, the user mode function return result is sent to the kernel mode through ioctl message communication, and then the blocked kernel mode is woken up The thread, completes the entire process of the function call. The invention realizes the calling of the user state function from the kernel state, and uses the blocking wake-up mode to complete the transparent call from the kernel state to the user state without modifying the logic of the original function without modifying the logic of the original function.
Owner:FENGHUO COMM SCI & TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com