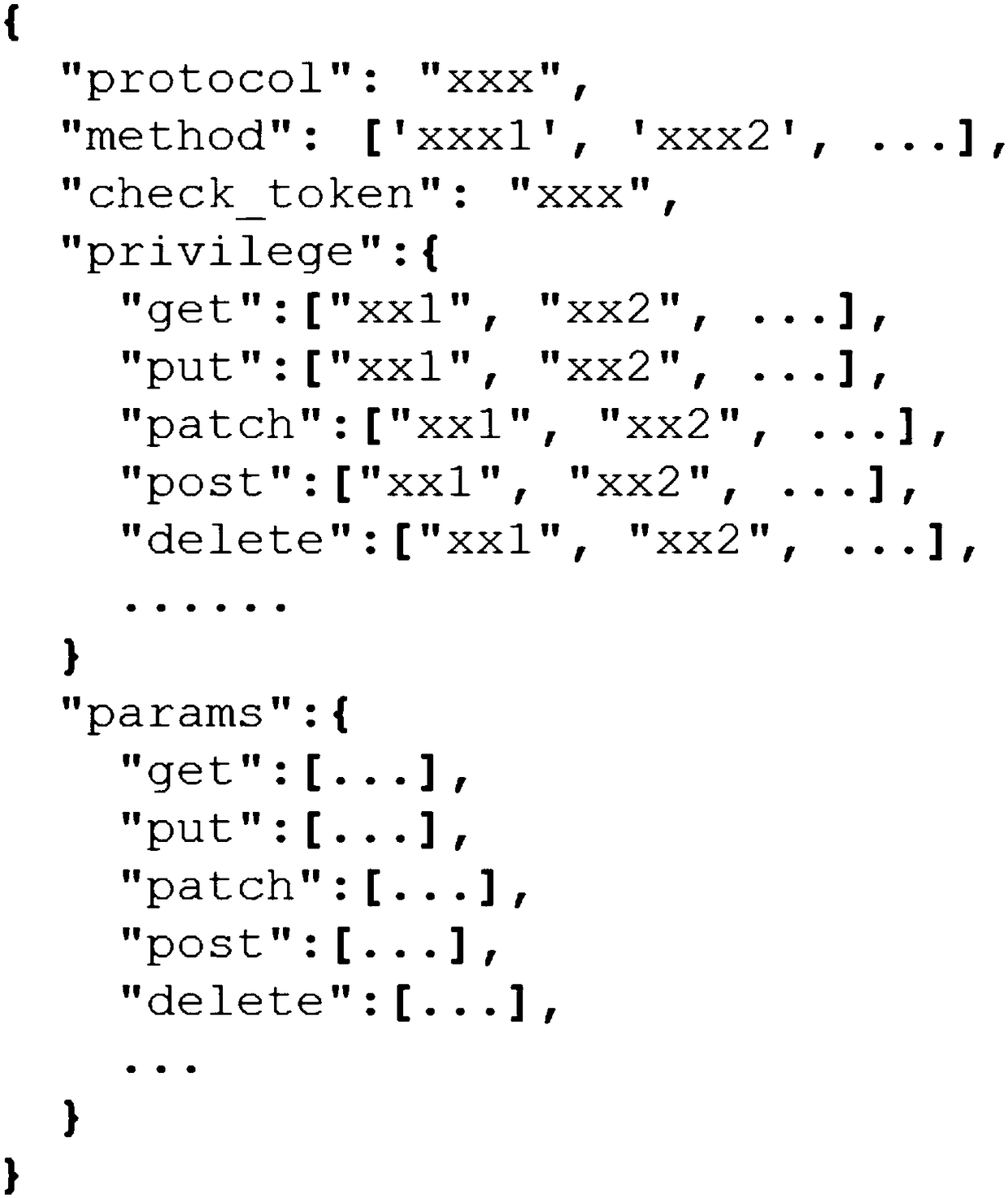
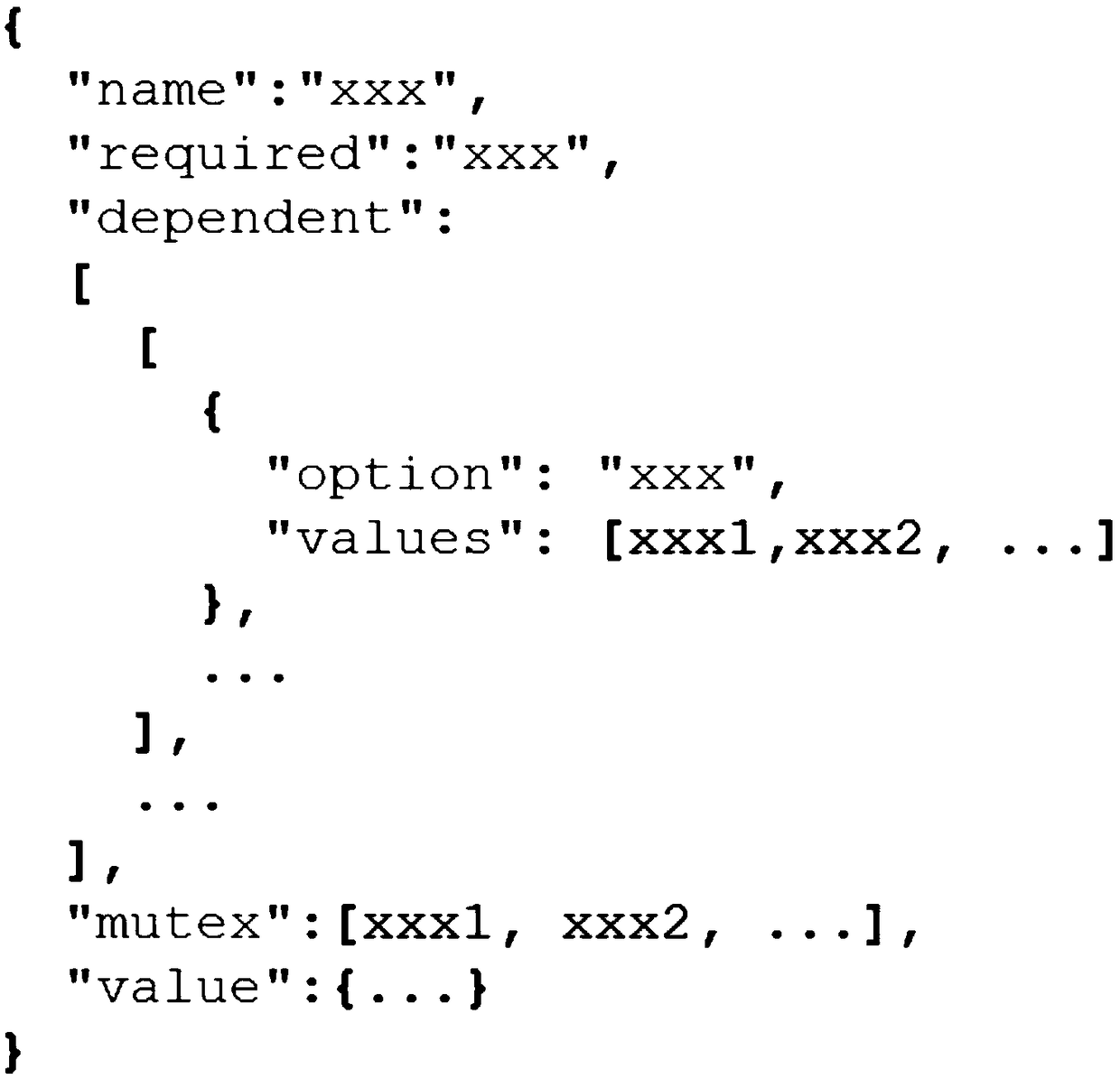
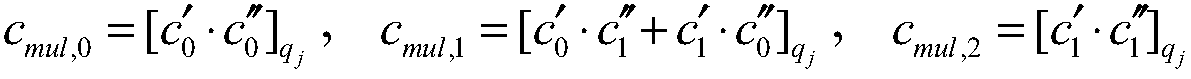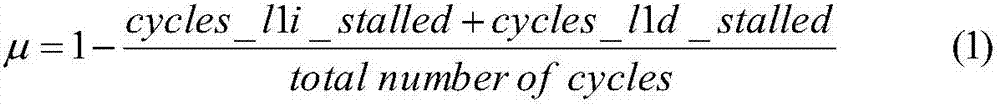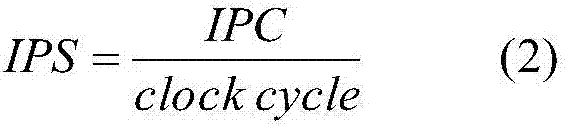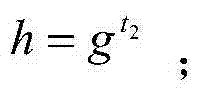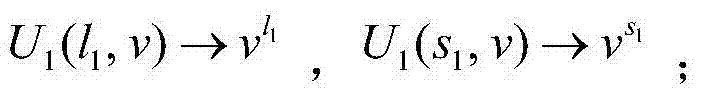Patents
Literature
134results about How to "Reduce calls" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
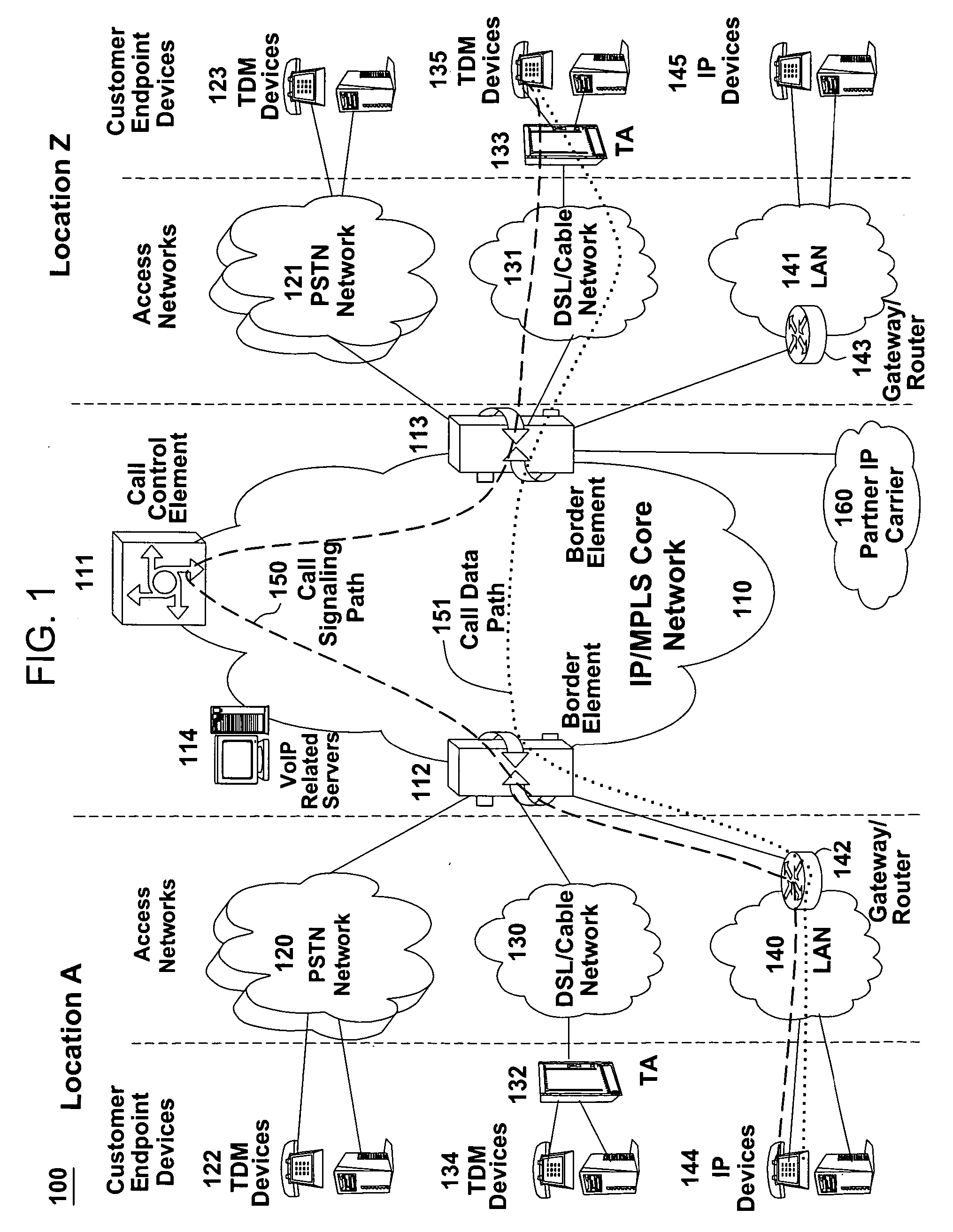
Method and network element for controlling handover
InactiveCN1505907AImprove resource utilizationEasy to useRadio/inductive link selection arrangementsWireless communicationQuality of serviceRadio access technology
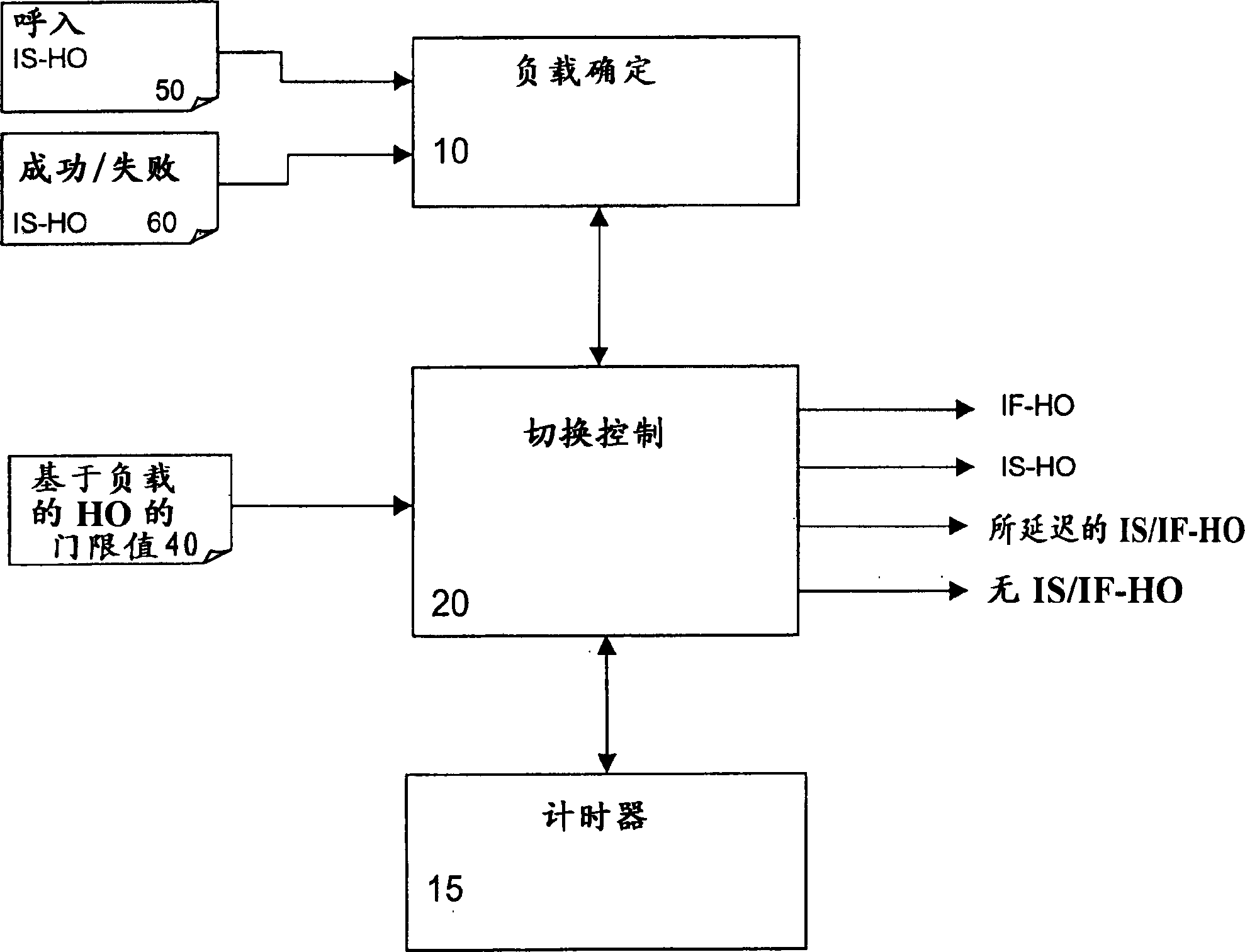
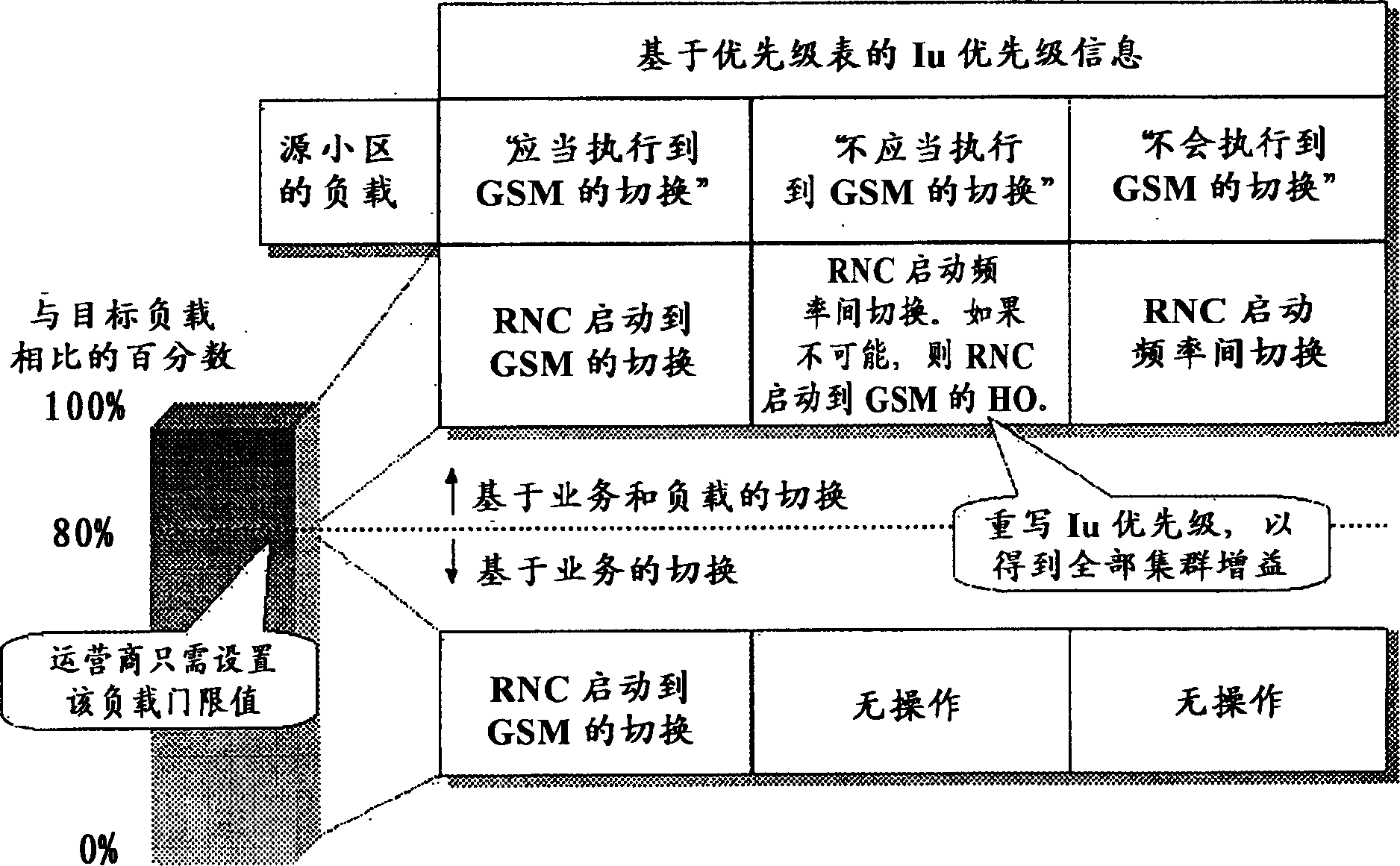
The present invention relates to a method and apparatus for controlling a connection transfer in a cellular network having at least two systems, such as a GSM system and a WCDMA system. Based on a load determination, a service-based inter-system or inter-frequency handover of the connection to another system or to another carrier of the same system is initiated if the determined is below a threshold and service priorities are indicating it. If it exceeds the threshold, an additional load-based inter-system or inter-frequency handover can be initiated. If the load of the target cell is not known, a load estimation based on a learning process can be used to derive a probability of success of an interfrequency or inter-system hand-over, which may be used for deciding on the initiation of the inter-system hand-over. The learning process may be performed by evaluating preceding interfrequency or inter-system handovers to the target cell or preceding interfrequency or inter-system handovers from the target cell. Thereby, users can be shared between different radio access technologies or systems or between different carriers of one system to thereby improve network capacity and quality of service for both systems and carriers. Furthermore, unnecessary inter-system handovers can be prevented in case the load of the target cell of the other system is not known.
Owner:NOKIA TECH OY
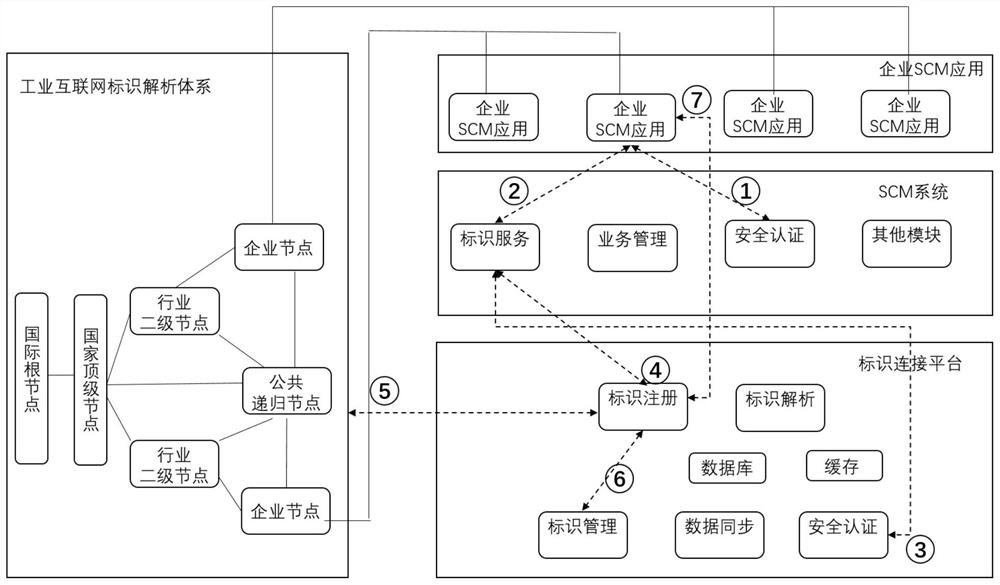
SCM-oriented industrial Internet identifier registration and analysis method and identifier connection platform and system
ActiveCN112491960ABreak the status quo of strong association constructionSimple dockingTransmissionManufacturing computing systemsThe InternetEngineering
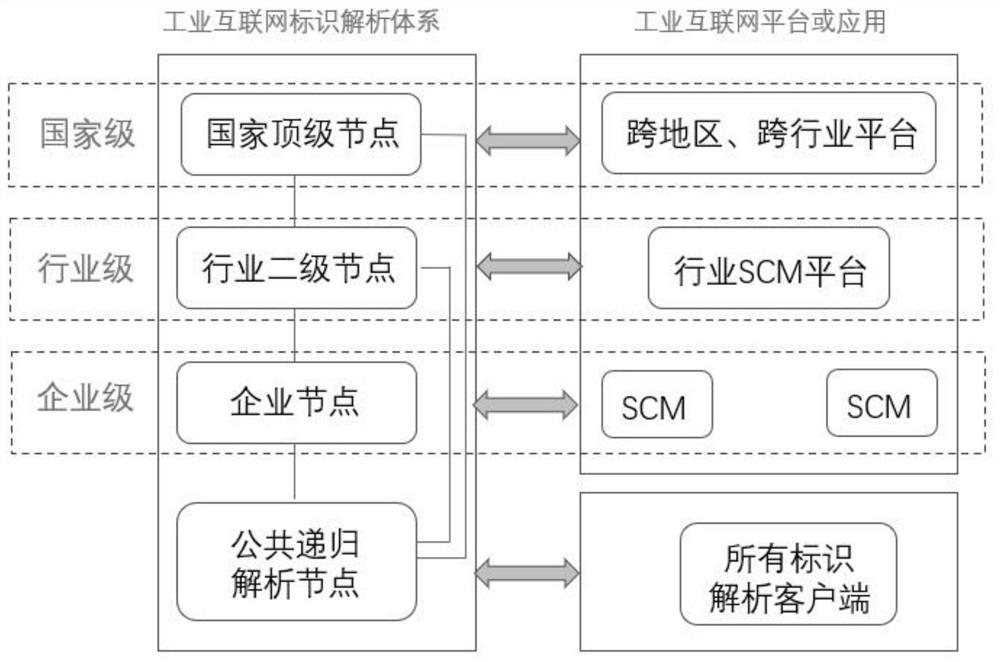
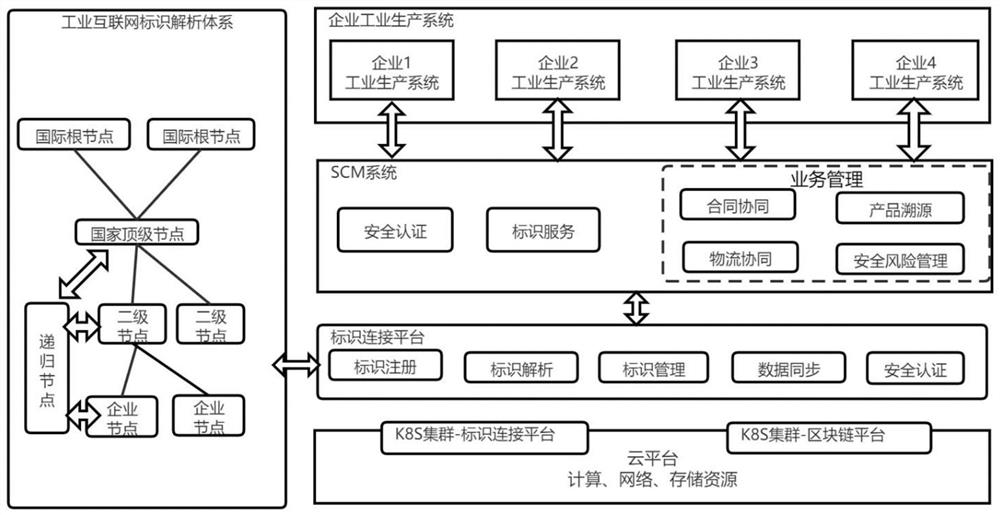
The invention discloses an SCM-oriented industrial Internet identifier registration and analysis method and an identifier connection platform and system, and the method comprises the steps: calling aninterface of an industrial Internet identifier analysis system for identifier registration according to a client identifier registration request; storing the identifier mapping relationship of the identifier registration information into an identifier connection platform database, and returning the identifier registration information to the client; according to the client identifier analysis request, performing identifier analysis query in an identifier connection platform cache, an identifier connection platform database or an industrial Internet identifier analysis system, and returning theobtained corresponding identifier mapping relationship to the client. According to the invention, the SCM system is associated with the industrial Internet identifier analysis system through the identifier connection platform, so that the docking mode of the enterprise SCM application and a plurality of secondary nodes is simplified, the current situation that most of SCM applications are strongly associated and constructed with the industrial secondary nodes at present is broken through, and the identifier service docking efficiency is improved.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
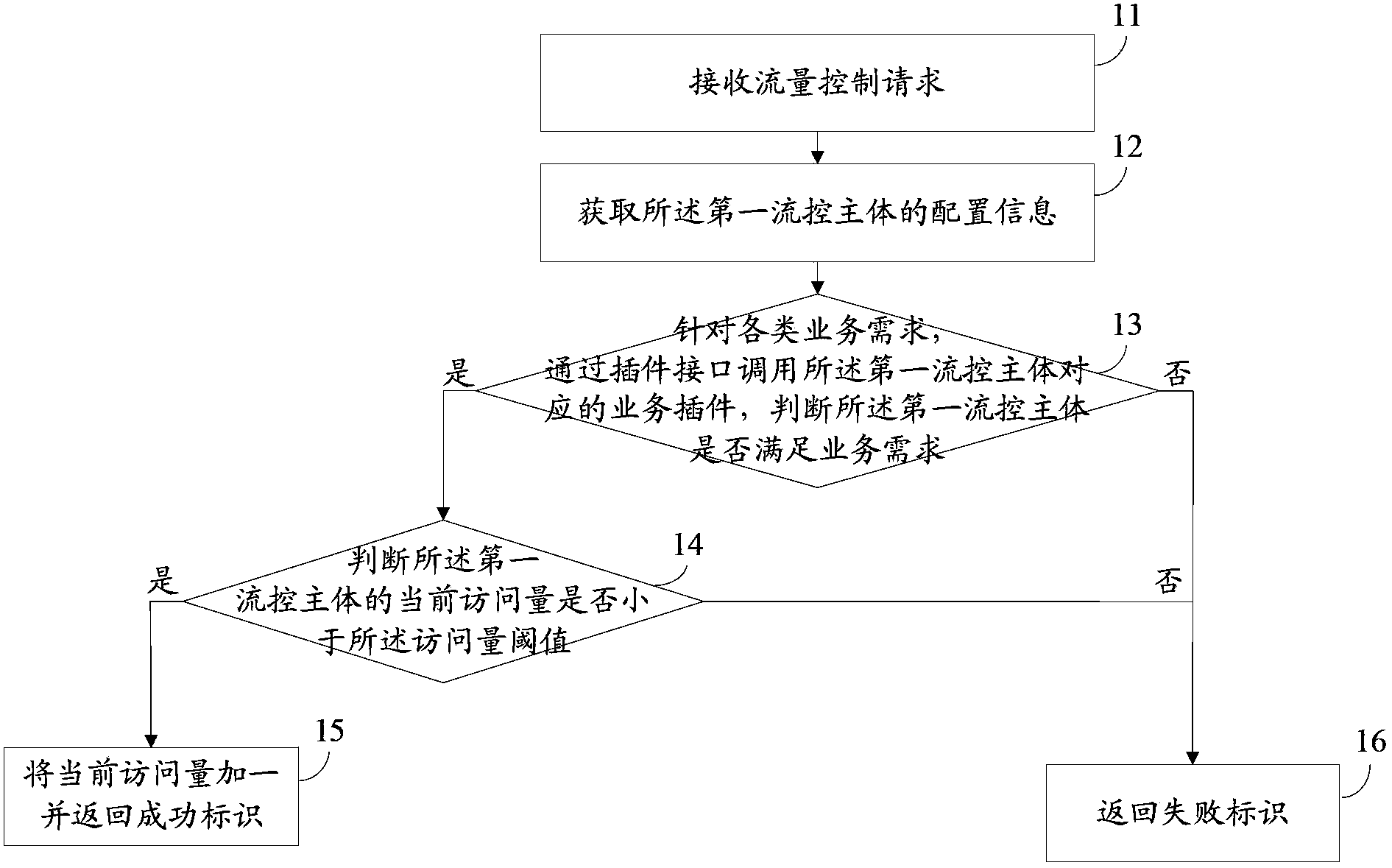
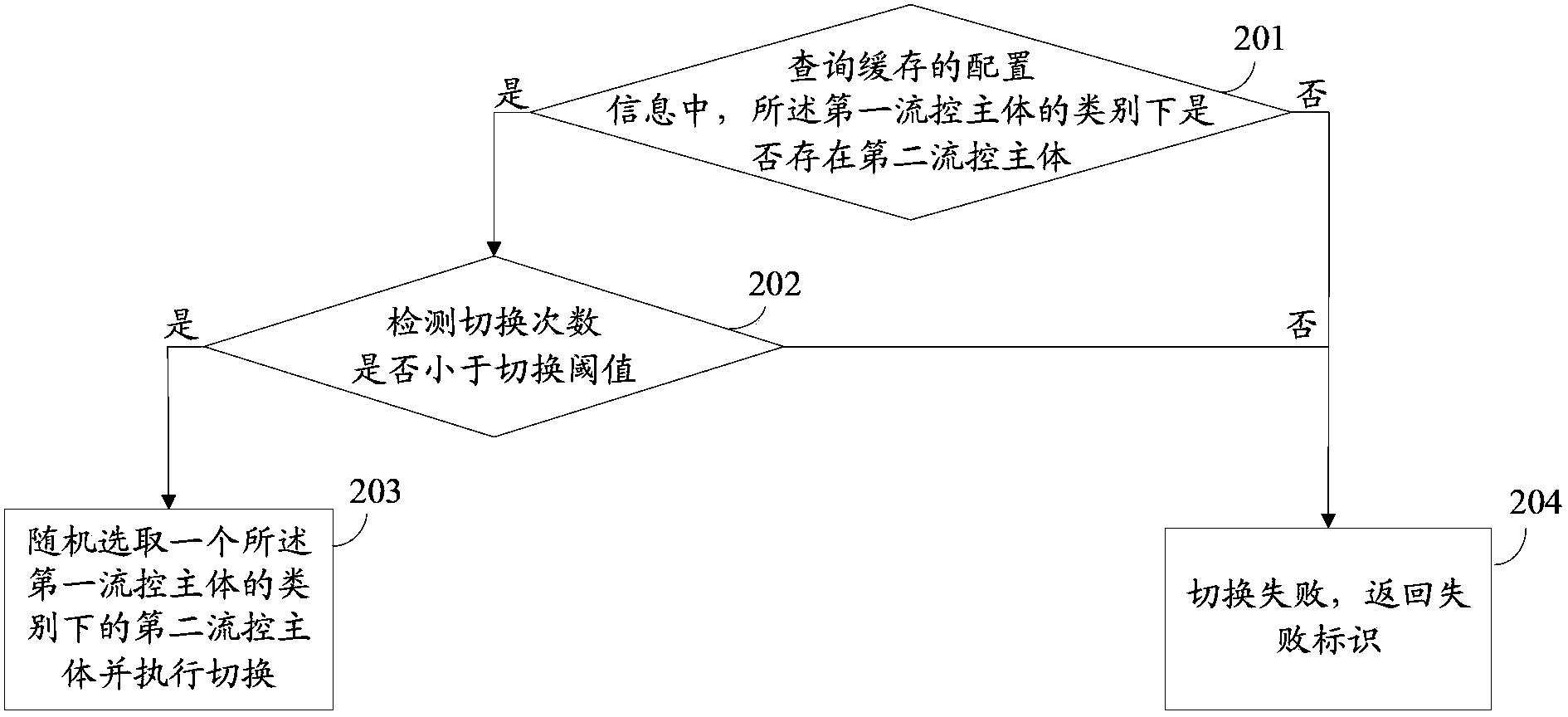
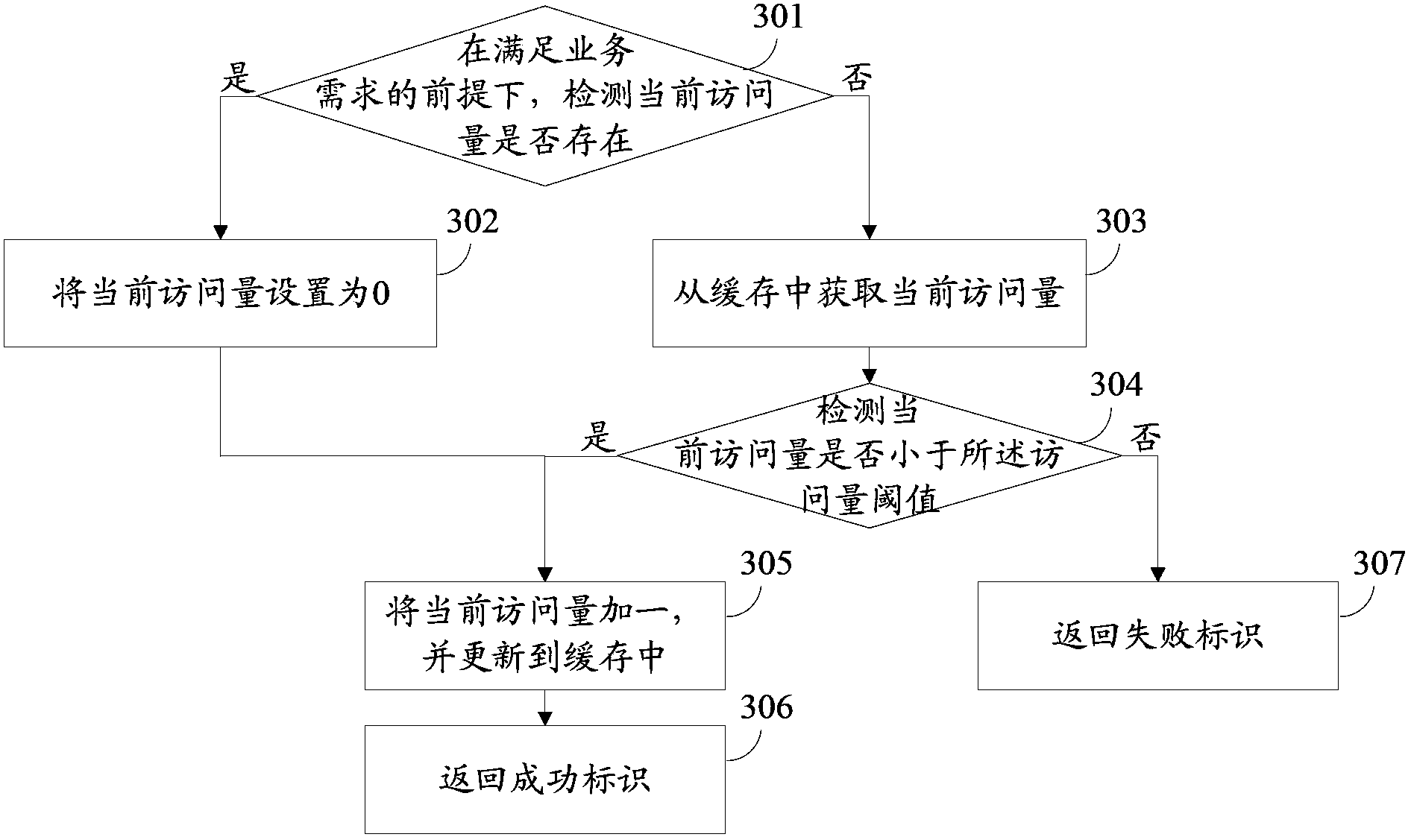
Flow control method and flow control device
ActiveCN103546388AImprove reusabilityFlexible flow control methodData switching networksReusabilityBusiness requirements
The invention provides a flow control method and a flow control device. The flow control method and the flow control device are used for solving problems of high pertinence and low reusability of an existing flow control method. The flow control method includes receiving a flow control request containing a first flow control main body; acquiring configuration information of the first flow control main body; calling a business plug-in unit via a plug-in unit interface, and detecting whether the first flow control main body meets business requirements or not; adding one to a current access quantity on the premise that the first flow control main body meets the business requirements when the current access quantity of the first flow control main body is smaller than an access quantity threshold value, and returning a success mark; returning a failure mark if the first flow control main body does not meet the business requirements or when the current access quantity of the first flow control main body is higher than or equal to the access quantity threshold value. The configuration information contains the access quantity threshold value of the first flow control main body, and the business plug-in unit corresponds to the first flow control main body and is used for storing business requirement strategies. The flow control method and the flow control device have the advantages of applicability to various types of business and extremely high reusability.
Owner:ADVANCED NEW TECH CO LTD
Fully-homomorphic encryption method and device and computer readable storage medium
ActiveCN108718231AReduce callsImprove the efficiency of homomorphic operationsPublic key for secure communicationCommunication with homomorphic encryptionPlaintextComputer hardware
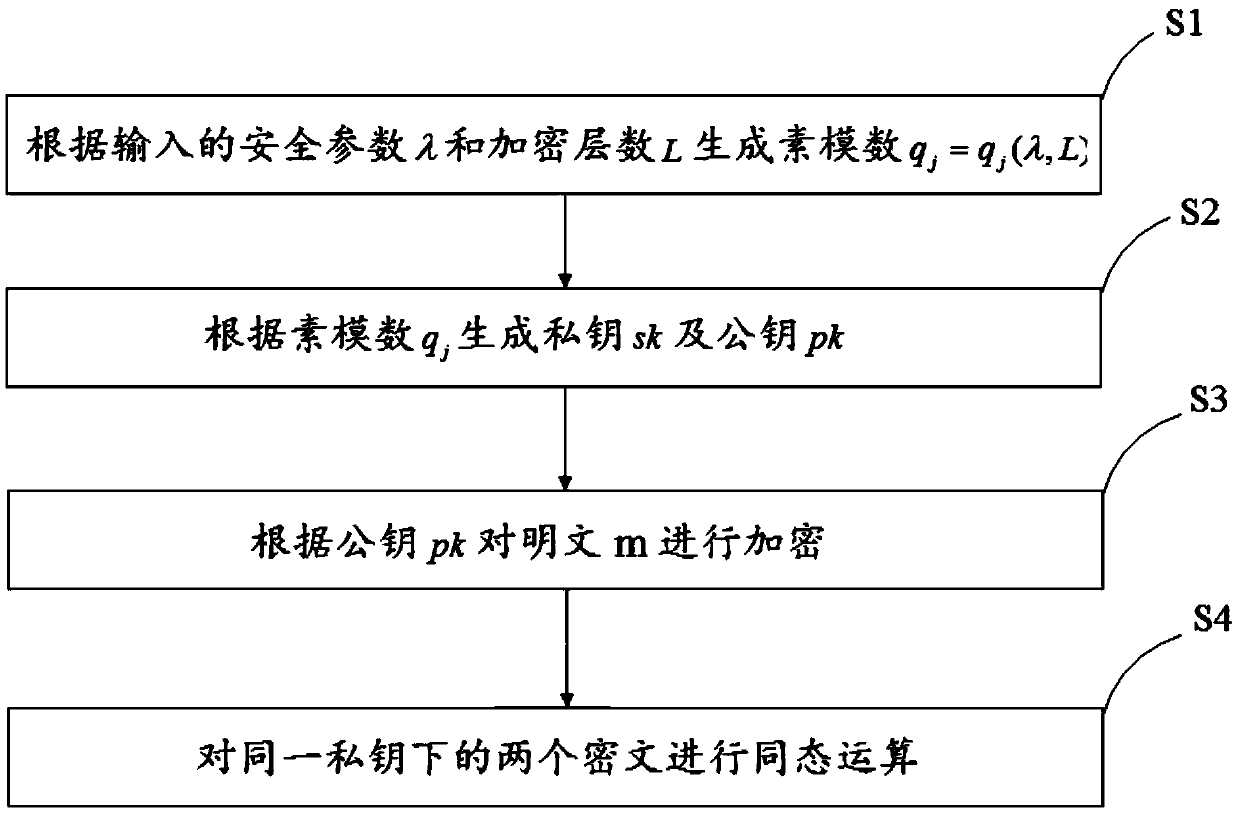
The embodiment of the invention discloses a fully-homomorphic encryption method and device and a computer readable storage medium, and aims at improving the efficiency of multiplication homomorphic calculation in the fully-homomorphic encryption method. The method comprises the steps of S1, generating a prime modulus qj=qj(lambda, L), q jmod n=1 according to an input safety parameter lambda and anencryption layer number L, wherein n is an integer power of 2, j=0,1...L-1, and q 0<q 1<...<q L-1; S2, generating a private key sk and a public key pk according to the prime modulus qj; S3, encrypting a plaintext m according to the public key pk; S4, conducting homomorphic operations on two ciphertexts under the same private key, wherein the homomorphic operations comprise the homomorphic additive operation FHE.Add(c', c'') and the homomorphic multiplication operation FHE.Mul(c', c'').
Owner:SHENZHEN UNIV
SM2 dot multiplication configuration preventing side-channel attack
ActiveCN108964914ANo increase in resource usageEasy to callPublic key for secure communicationCryptographic attack countermeasuresComputer moduleFault analysis
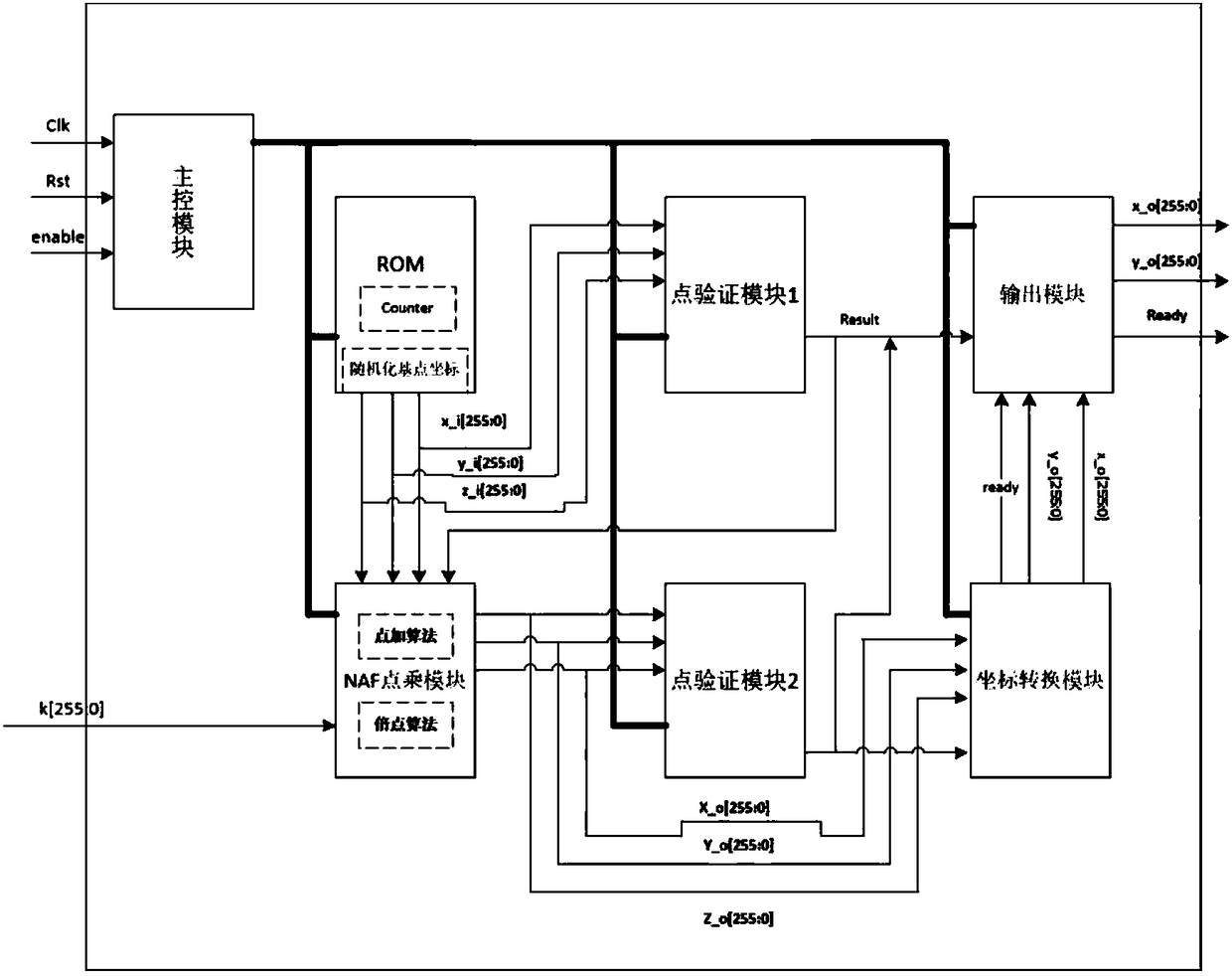
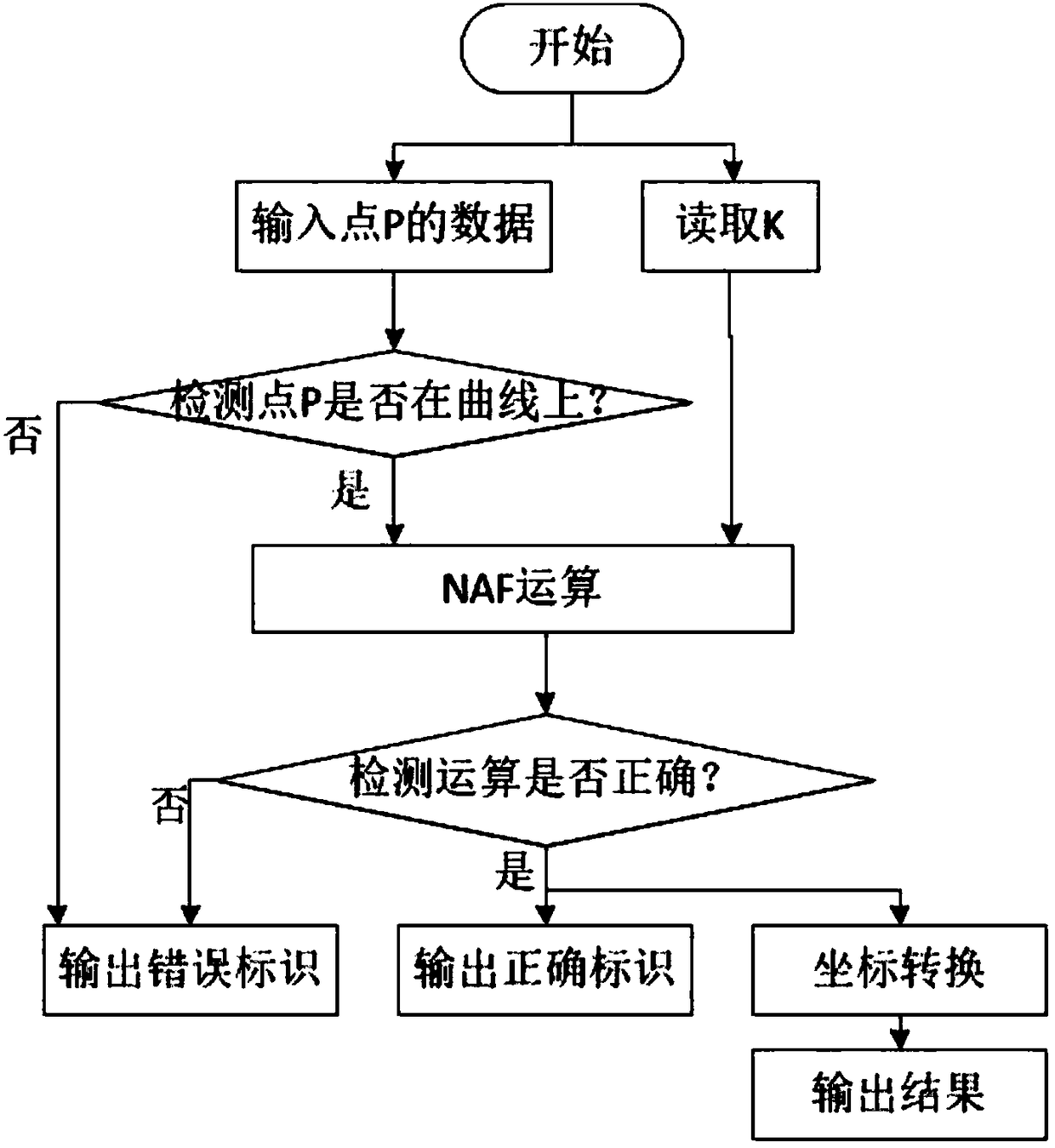
The invention discloses an SM2 dot multiplication configuration preventing a side-channel attack. An NAF(k) calculation point multiplication algorithm is modified by adding redundant operation to thealgorithm, so that the algorithm can resist attack of simple power consumption analysis; the coordinate of a basic point is made random, so that different basic-point coordinates are used in calculation to resist attack of differential power consumption analysis; and a point verification module is added to defend a fault analysis attack.
Owner:UNIV OF SCI & TECH OF CHINA
High-aspect-ratio wing optimization design method based on model merging method
ActiveCN107391891AImprove design efficiencyReduce callsGeometric CADSustainable transportationAlgorithmInto-structure
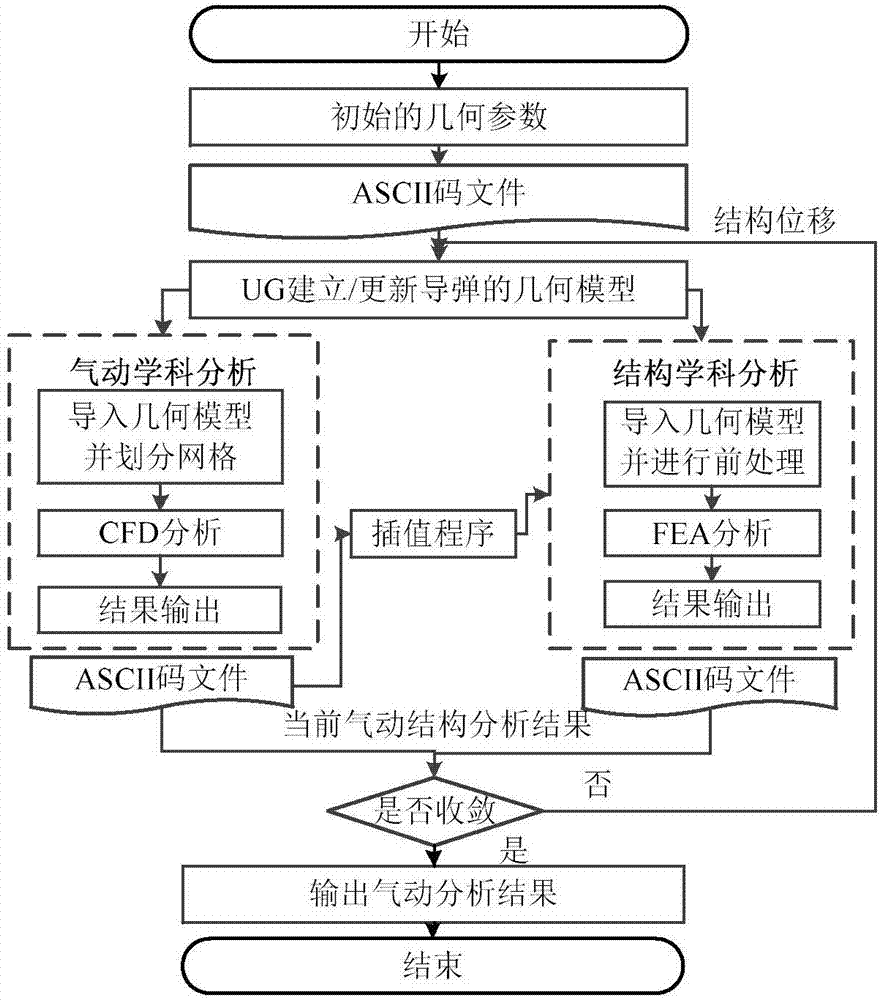
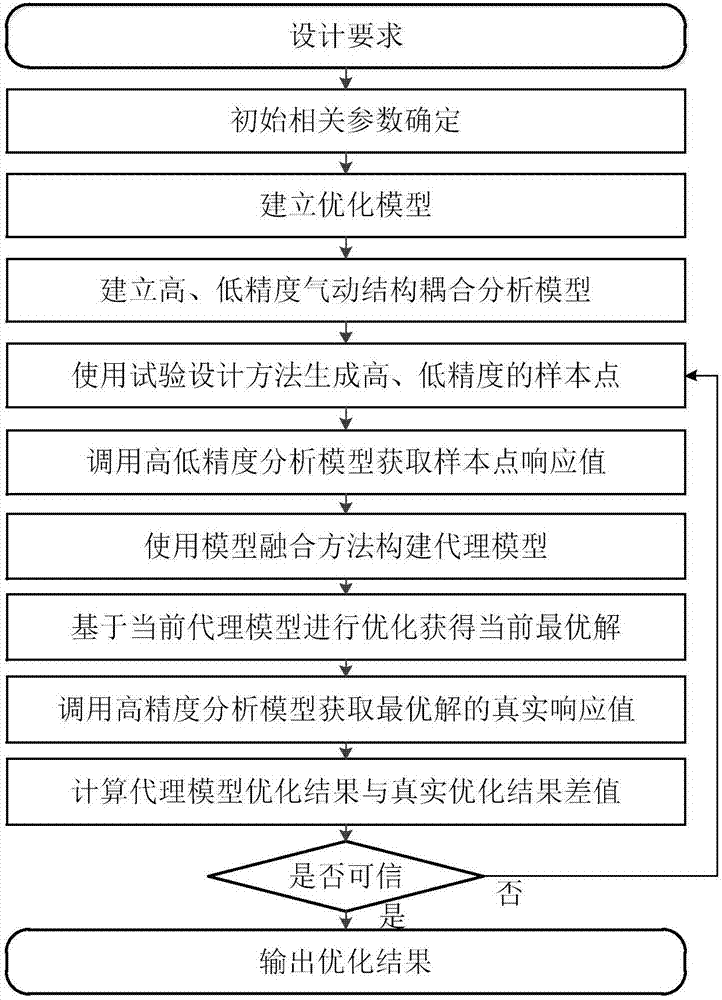
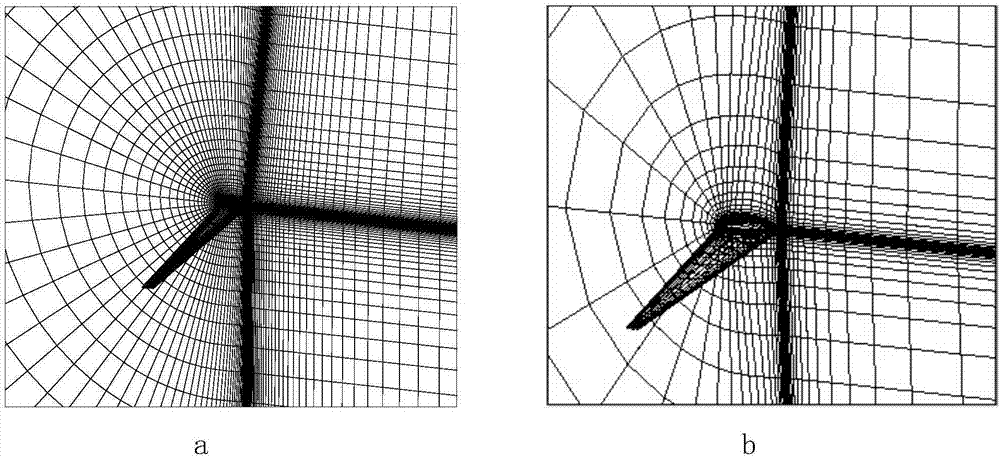
The invention discloses a high-aspect-ratio wing optimization design method based on a model merging method, and belongs to the technical field of overall optimization design of aircraft. The method comprises the steps that a penalty function method is used for processing complex constraints for an optimization model and a system-level optimization model which are optimally divided into structure subjects as needed; a high precision pneumatic structure coupling analysis model and a low precision pneumatic structure coupling analysis model are built through a pneumatic structure coupling modeling technology; high precision sample points and low precision sample points are generated through an experiment design method; high precision sample information and low precision sample information are obtained by calling the high precision pneumatic structure coupling analysis model and the low precision pneumatic structure coupling analysis model respectively and stored; by using the model merging method, the high precision sample information and the low precision sample information are merged to build a surrogate model; optimization solution is conducted based on an optimization method for a current surrogate model, whether the optimization result is credible or not is judged according to a difference value of a true response value of the optimal solution and a surrogate model value based on the model merging method, if not, the step is executed again to rebuild a merging model for optimization solution, if yes, the optimal design result is output, and optimization design is completed.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Peer to peer remote control method between one or more mobile devices
ActiveUS20160029216A1Reduce callsReduce in quantityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsRemote controlTrust relationship
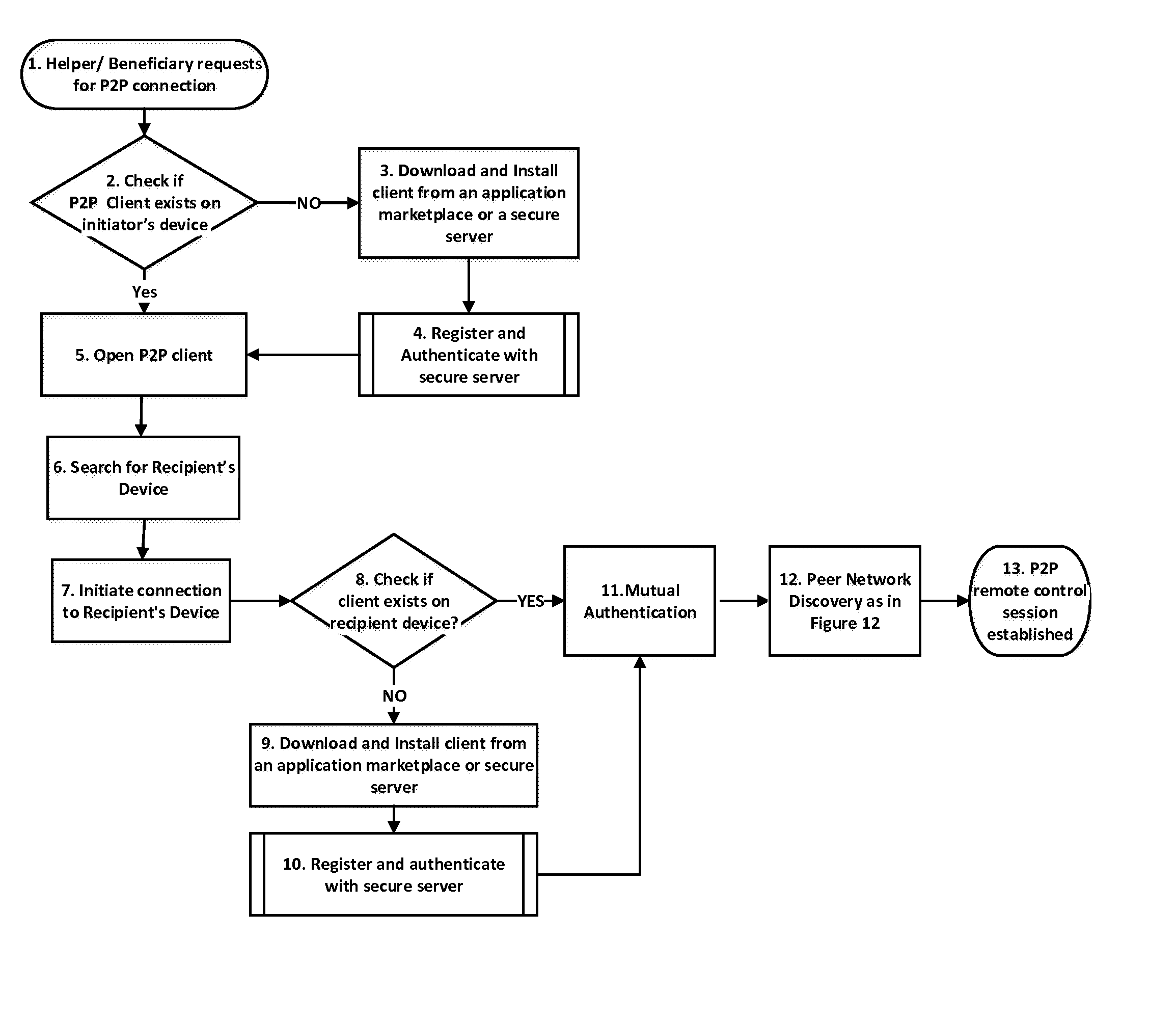
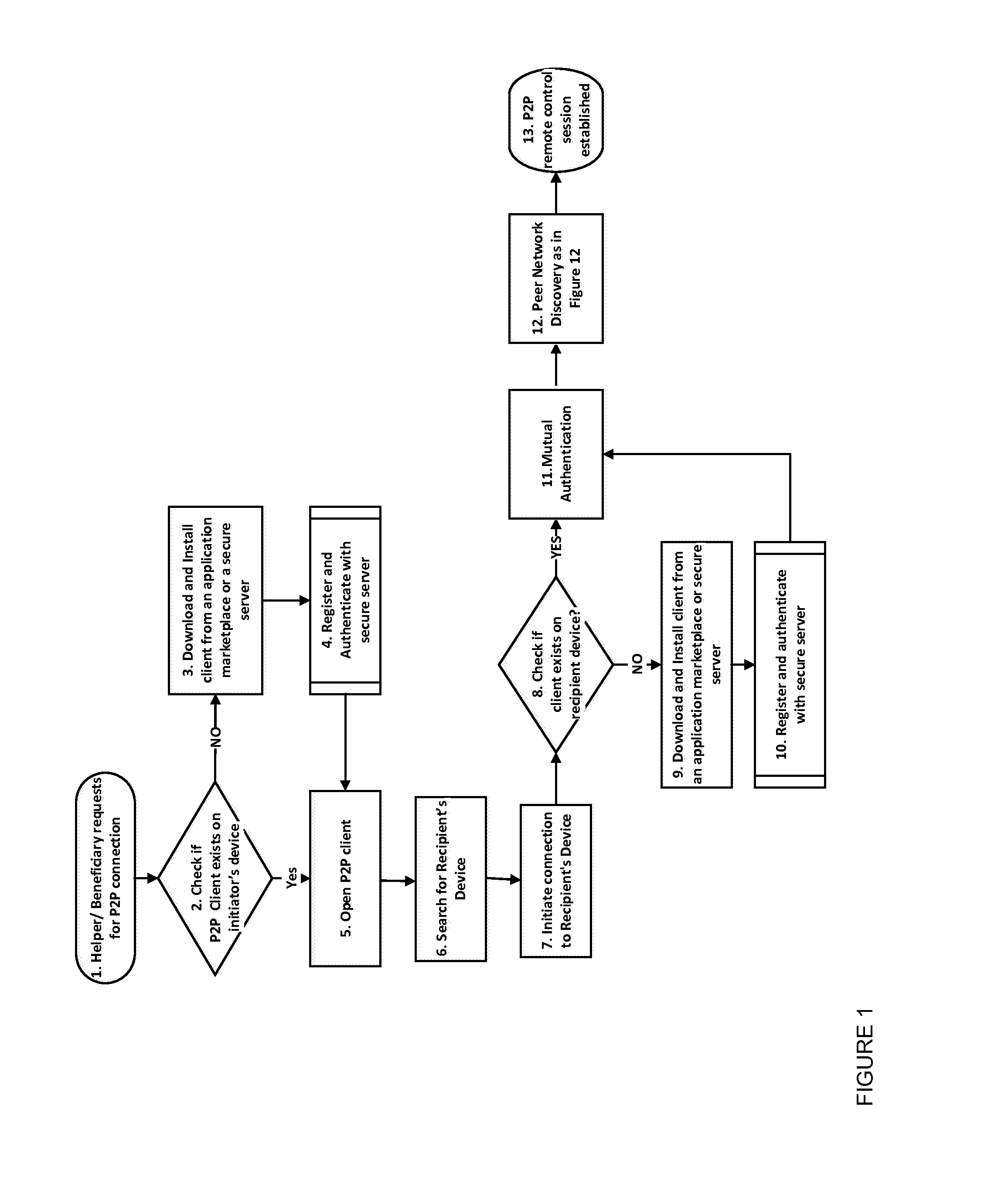
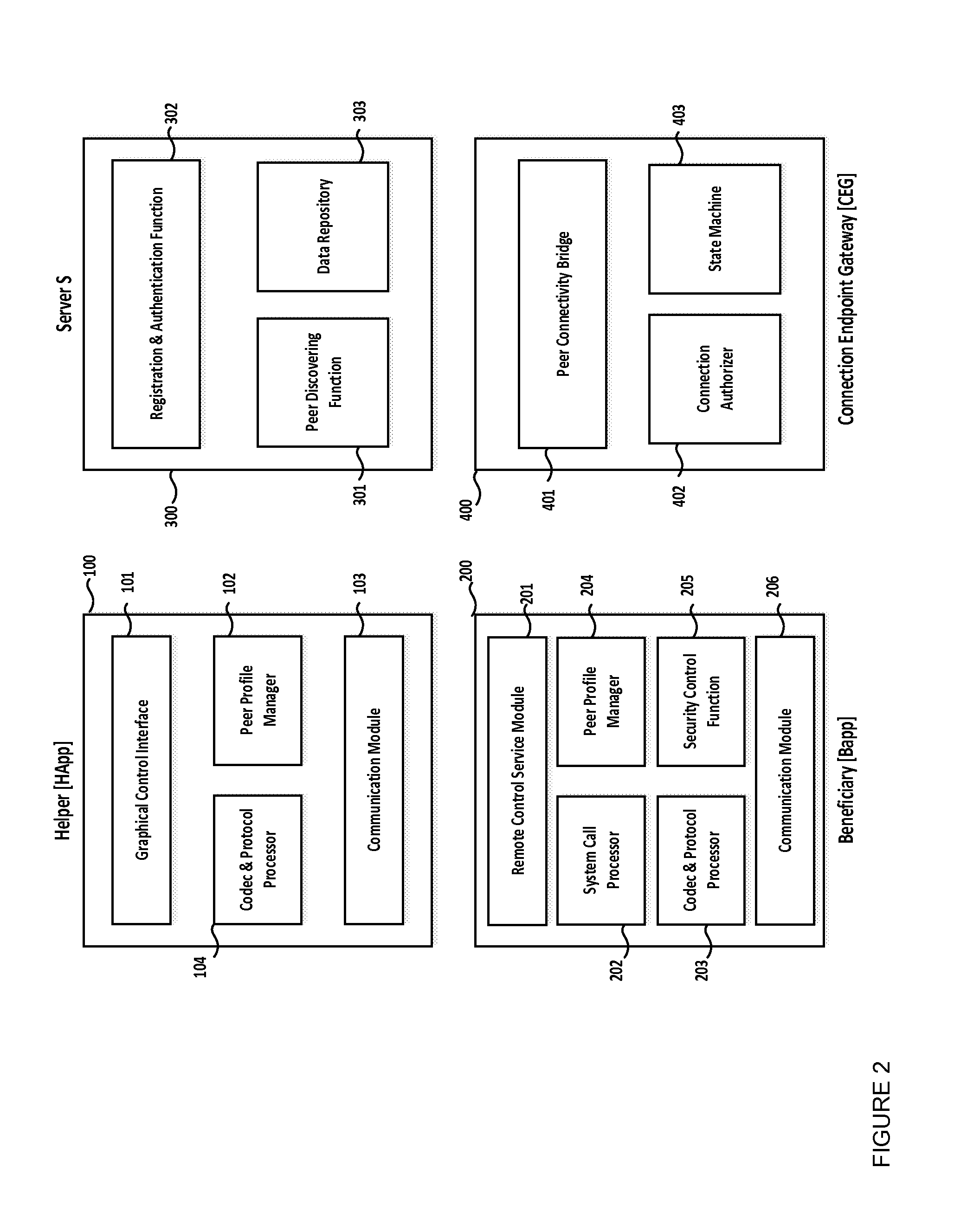
Described herein is a method for providing peer to peer remote control management between a helper and a beneficiary mobile device. The method includes registering, by the helper and beneficiary mobile devices, with a secure server. The helper mobile device authenticates with the secure server. The helper or the beneficiary mobile device perform discovery with respect to the other device. A trust relationship is established between the helper and beneficiary mobile devices by performing mutual authentication. An auto connection discovery process is performed to determine if the helper and the beneficiary mobile devices are on a same sub network. A peer to peer connection is established between the helper and the beneficiary mobile devices if the helper and the beneficiary mobile devices are on the same sub network and a secure server mediates between the helper and the beneficiary mobile devices if they are on different sub networks.
Owner:VMWARE INC
A lightweight class method for system power consumption optimization based on online learning
ActiveCN106991030AReduce the number of iterationsReduce loadHardware monitoringDesign optimisation/simulationWork periodOnline learning
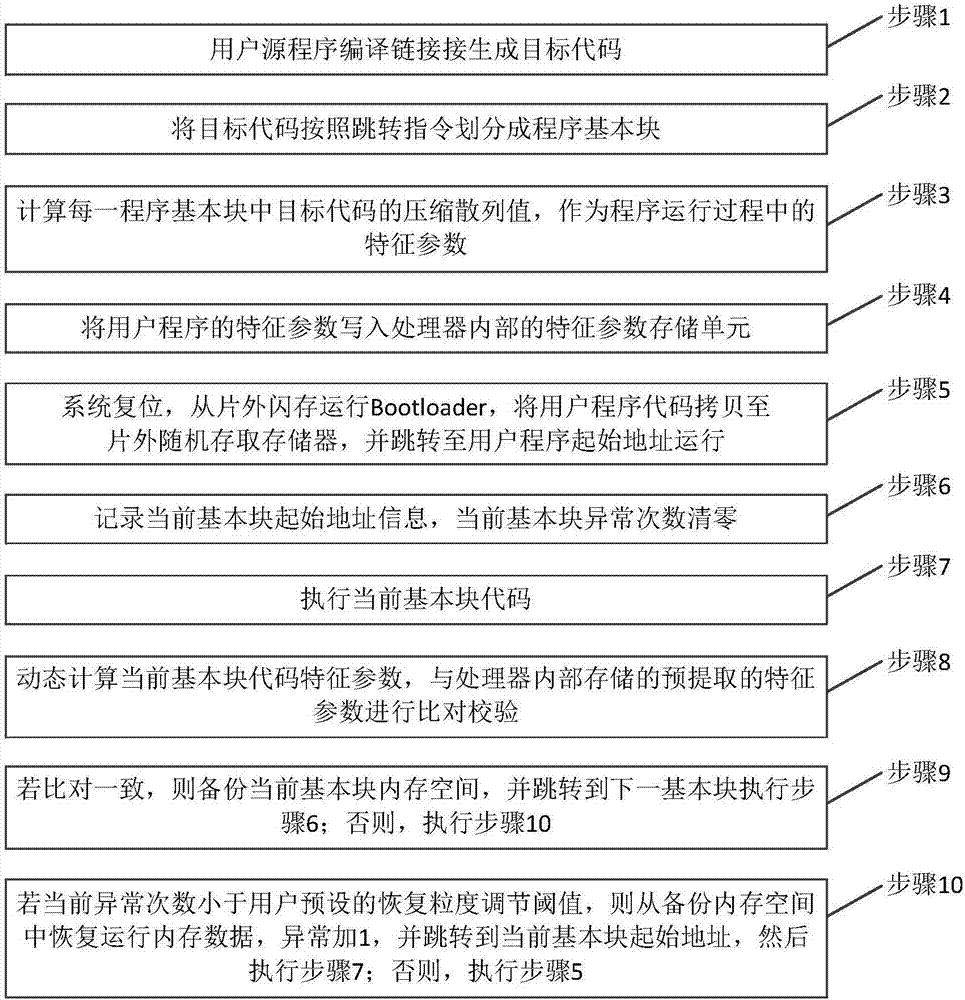
The invention provides a lightweight class method for system power consumption optimization based on online learning. The method comprises the steps of: 1, performing program compiling to generate target codes; 2, starting a monitoring module to monitor hardware events; 3, performing normalization processing of events; 4, building a system power consumption module; 5, designing different optimization modes; 6, designing a value function module; 7, writing the power consumption module, a penalty factor and the value function module into an agent module Agent; 8, designing a software timer and starting the third step and the seventh step regularly; 9, executing a program, the seventh step and the third step and updating the Agent; 10; setting convergence; 11, according to results of the Agent module, going to the second step and starting from the third step until operation is over. Through the steps, temperature, performance and power consumption are comprehensively and synergistically considered and a lightweight class machine learning algorithm is used to search for existing optimization space, so that the effects of low power consumption and reasonable performance are achieved and the problem is solved that working time is influenced because embedded devices are limited by batteries.
Owner:BEIHANG UNIV
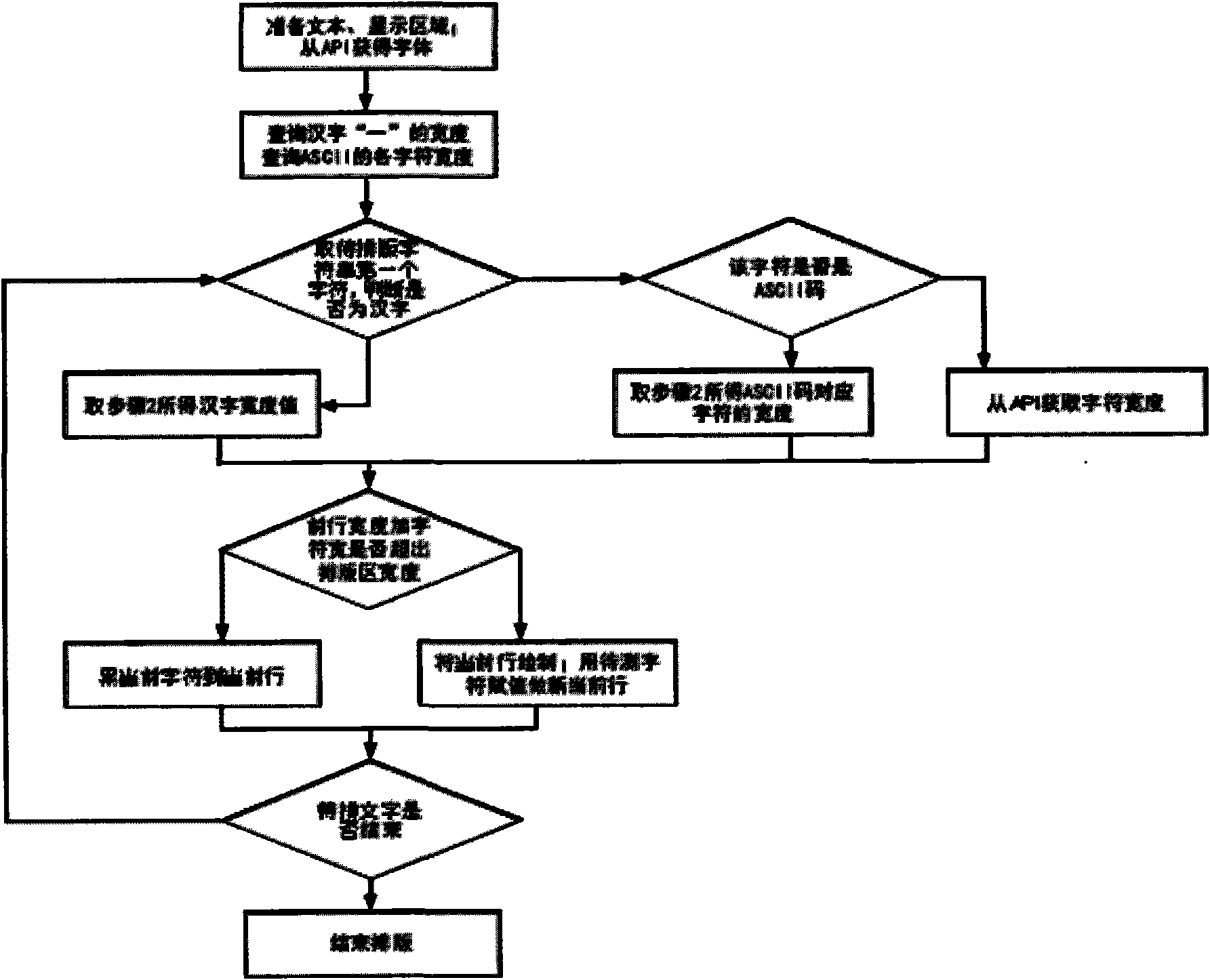
Fast text composition method of mobile terminal
InactiveCN102063413AReduce callsSave the number of callsSpecial data processing applicationsEngineeringComputer science
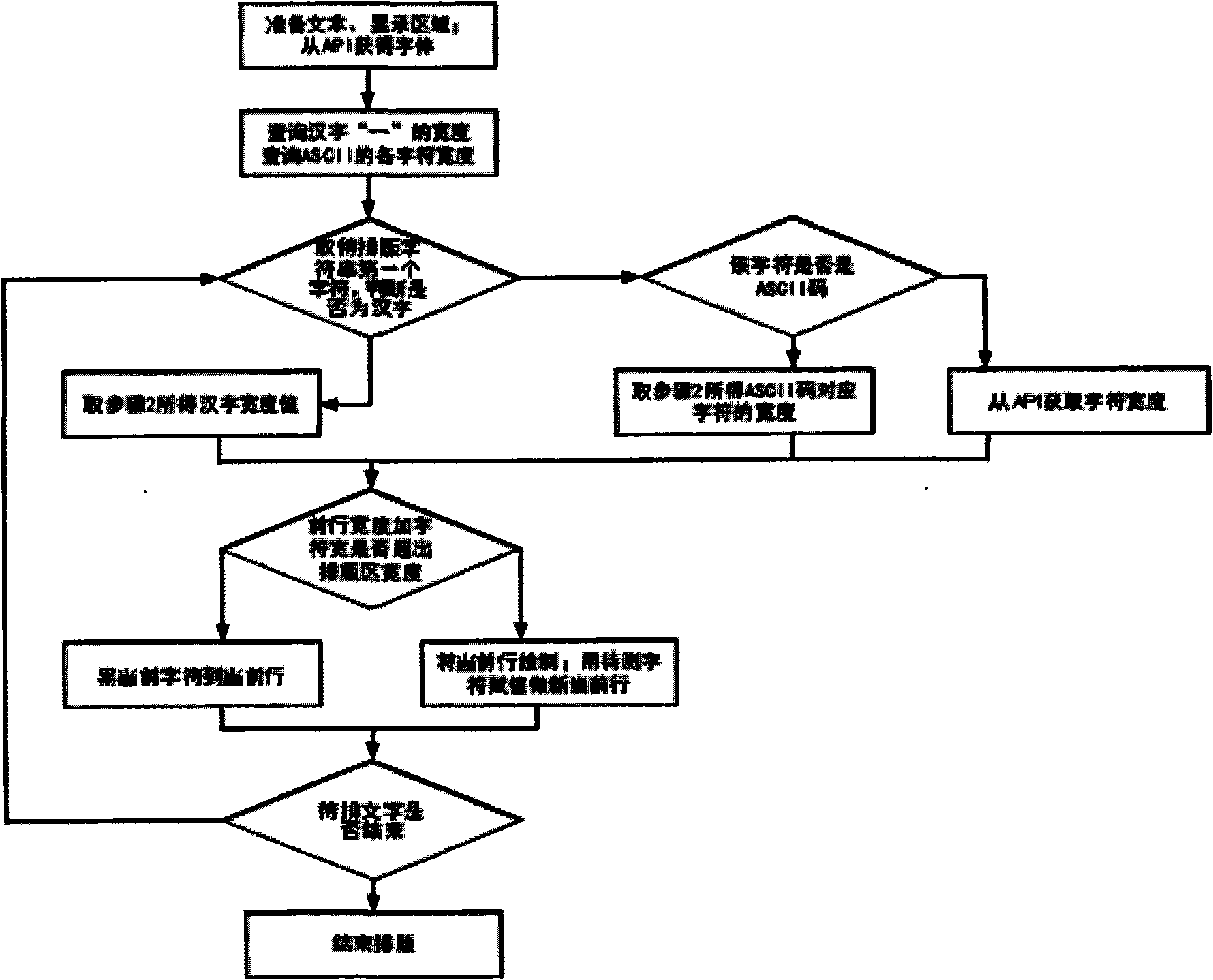
The invention relates to a fast text composition method of a mobile terminal, belonging to the technical field of communication. The fast text composition method comprises the following steps of: selecting a font, a character height value, the height value and the width value of a display area; calculating the width of a single character and the width of an ASCII (American Standard Code for Information Interchange) code symbol; judging the attribute of a first character of a character string, and then determining the display width of the first character; adding the judged first character to the tail part of a current display character string, and deleting the first character contained in a character string to be composed; summarizing the display widths of characteristics of the current display character string to obtain a current display line width; comparing whether the current display line width is larger than the width value of the display area or not, determining whether adding a new display line or not, and judging whether the product of a display line number and the character height value is larger than the height value of the display area or not to determine whether the composition of the character string to be composed on the display area needs to be completed or not. The invention can outstandingly increase the text composition speed and enable the battery with same electric quantity to work for a longer time.
Owner:ZHANGFU TECH NANJING
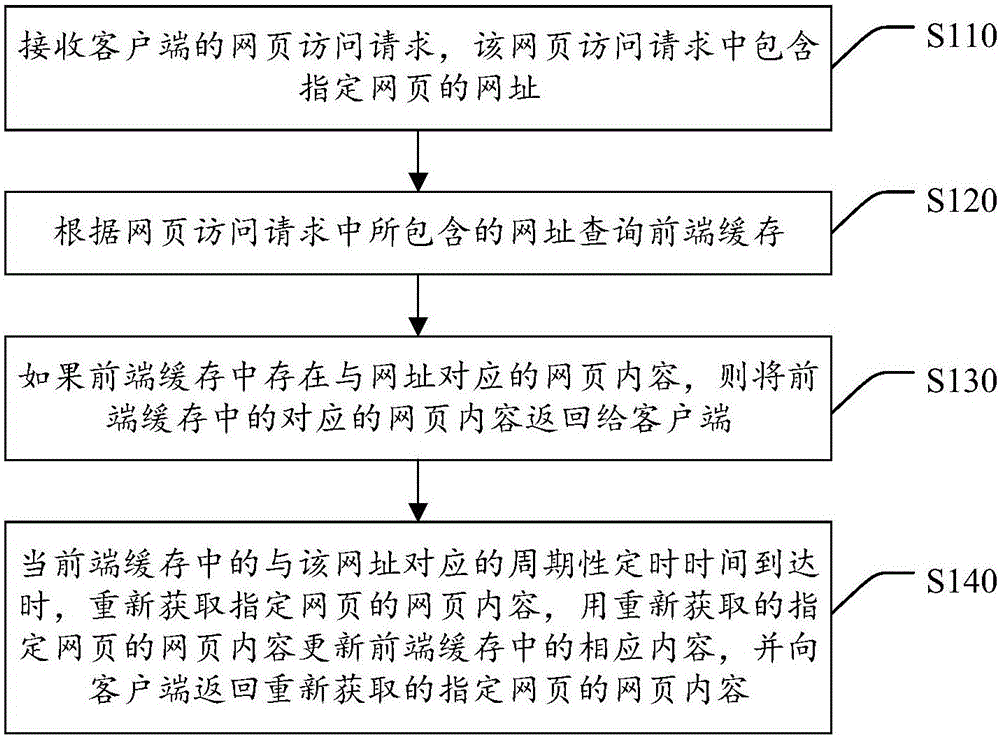
Webpage accessing request processing method and server
InactiveCN105930538ARelieve stressReduce callsSpecial data processing applicationsClient-sideWeb page
The invention discloses a webpage accessing request processing method and a server. The method comprises the following steps: receiving a webpage accessing request from a client terminal, wherein the webpage accessing request comprises a web address of a specific webpage; querying front-end cache according to the web address included in the webpage accessing request; returning the corresponding webpage content in the front-end cache to the client terminal if the webpage content corresponding to the web address exists in the front-end cache; re-acquiring the webpage content of the specific webpage when periodic timing time corresponding to the web address in the front-end cache arrives, updating the corresponding content in the front-end cache by using the re-acquired webpage content of the specific webpage and returning the re-acquired webpage content of the specific webpage to the client terminal. According to the scheme of the invention, a repeated calling of a back-end service can be reduced; a user can acquire a requested webpage in a short time, so that the surfing experience of the user can be improved.
Owner:BEIJING QIHOO TECH CO LTD +1
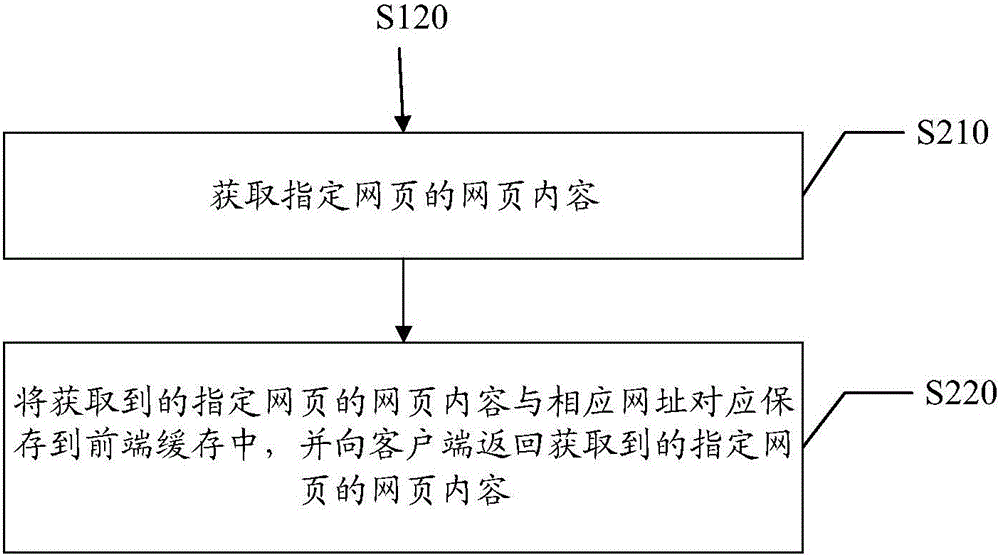
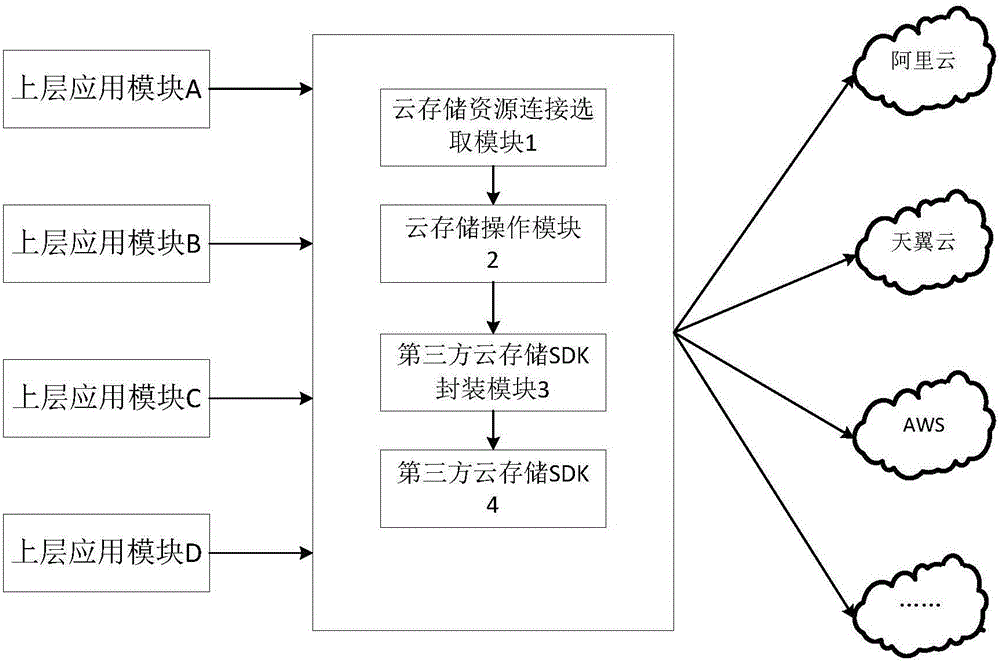
Method and system for adapting various kinds of cloud storage interfaces
The invention relates to a method and system for adapting various kinds of cloud storage interfaces. The method includes the following steps of: 1) selecting a processing process of third-party cloud storage connection information, and steps 2), 3) and 4) are executed; 2) uploading a file to the processing process of cloud storage; 3) downloading a file to a local processing process; and 4) deleting the processing process of the file in the cloud storage. The system includes a cloud storage resource connection selection module, a cloud storage operation module, a third-party cloud storage SDK packaging module and a third-party cloud storage SDK. Compared with the prior art, the method and system of the invention can reduce the development cost of adaption of upper-layer application to the cloud storage.
Owner:EISOO SOFTWARE
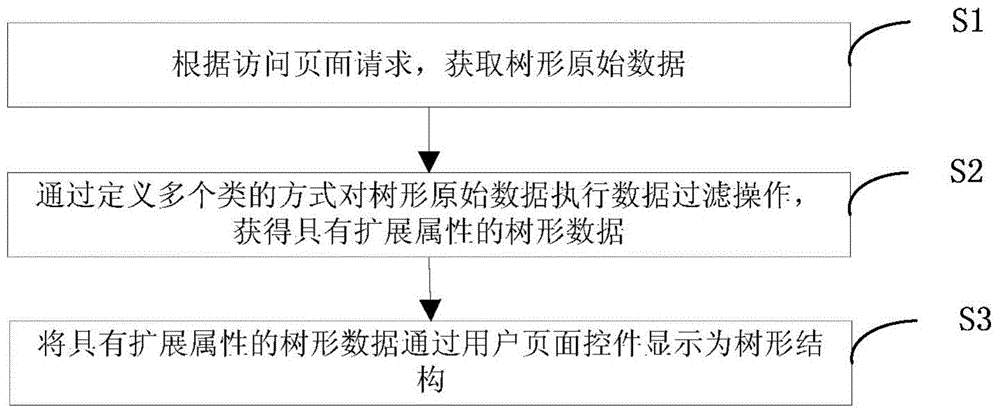
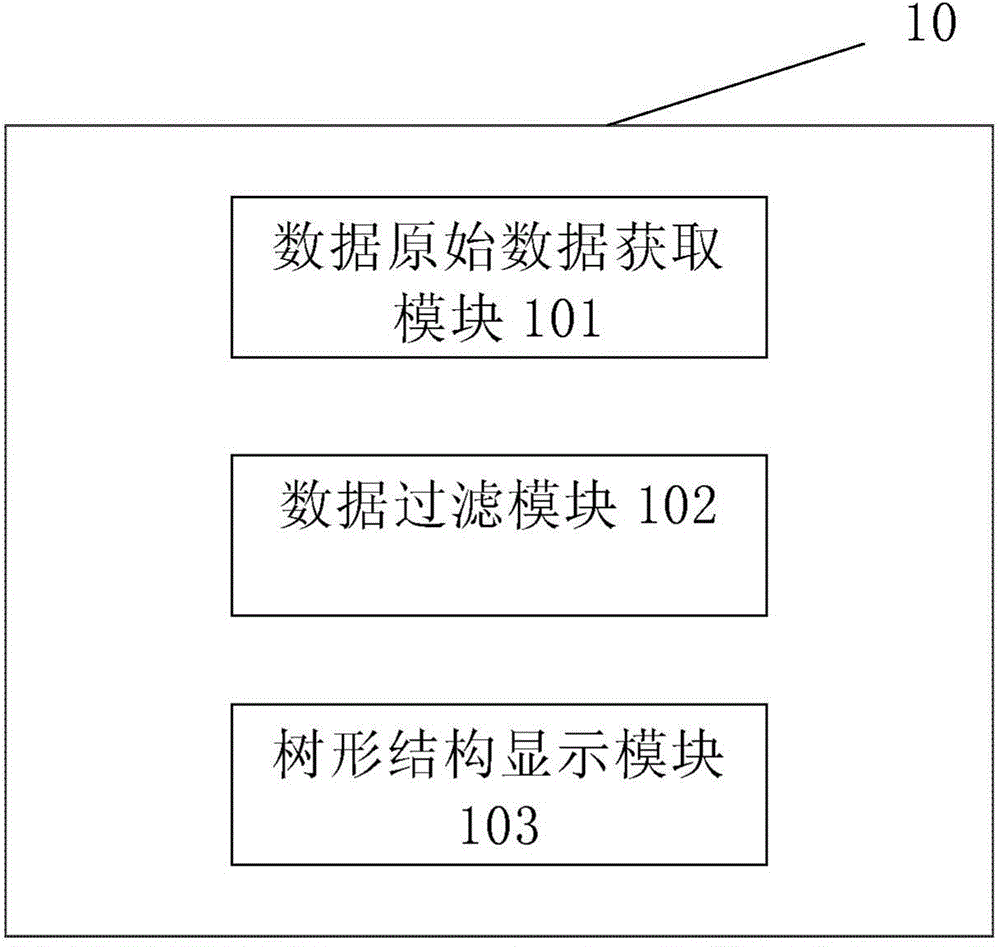
Filtering method and apparatus based on tree structure
ActiveCN104991778AReduce callsImprove data processing capabilitiesSpecific program execution arrangementsOriginal dataData mining
The present invention discloses a filtering method based on a tree structure, which comprises: according to a page access request, acquiring tree original data; executing an data filtering operation on the tree original data in a manner of defining a plurality of categories to obtain tree data with an extended attribute; and displaying the tree data with the extended attribute into the tree structure by a user page control. The present invention also discloses a filtering apparatus based on the tree structure.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
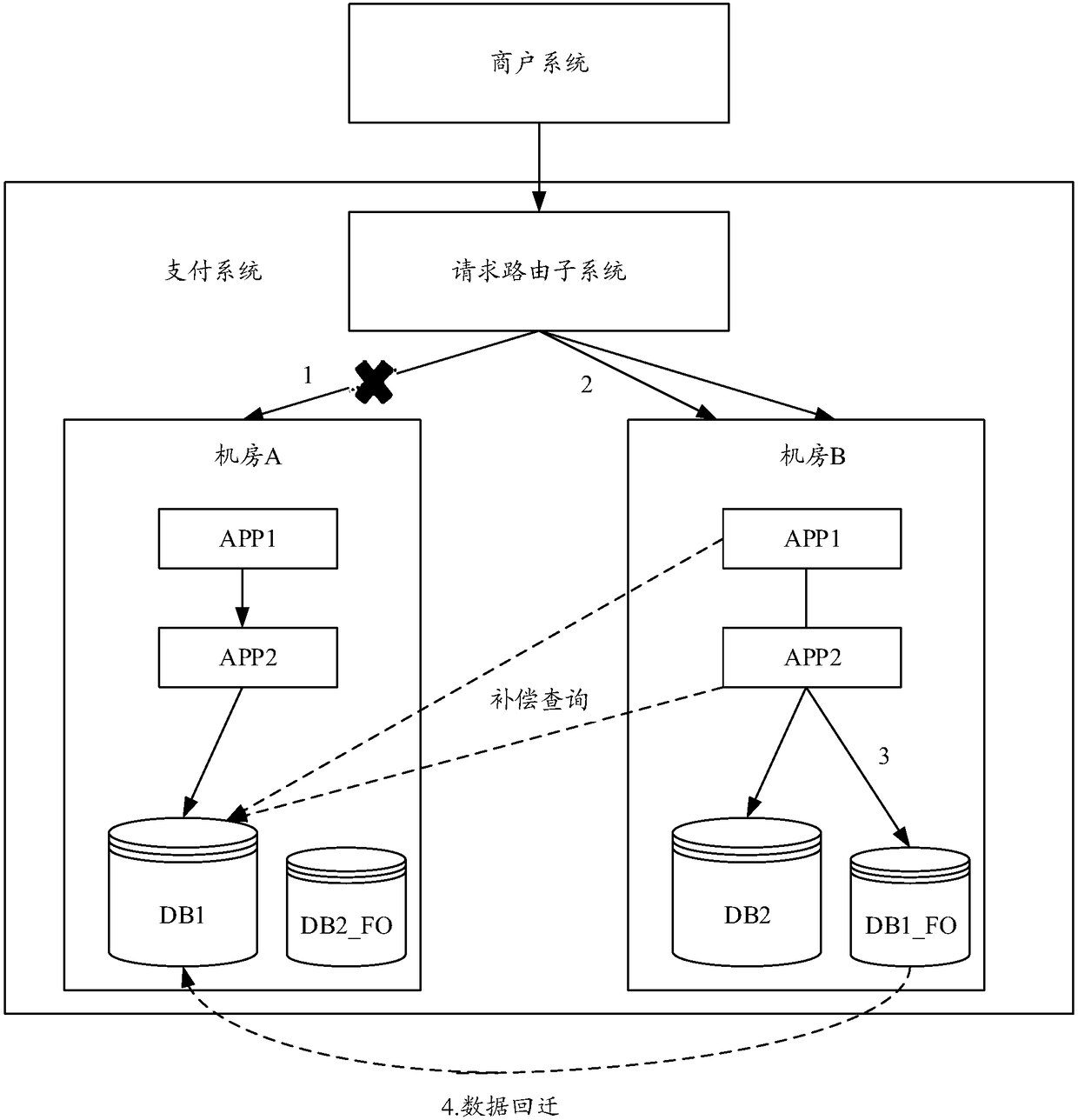
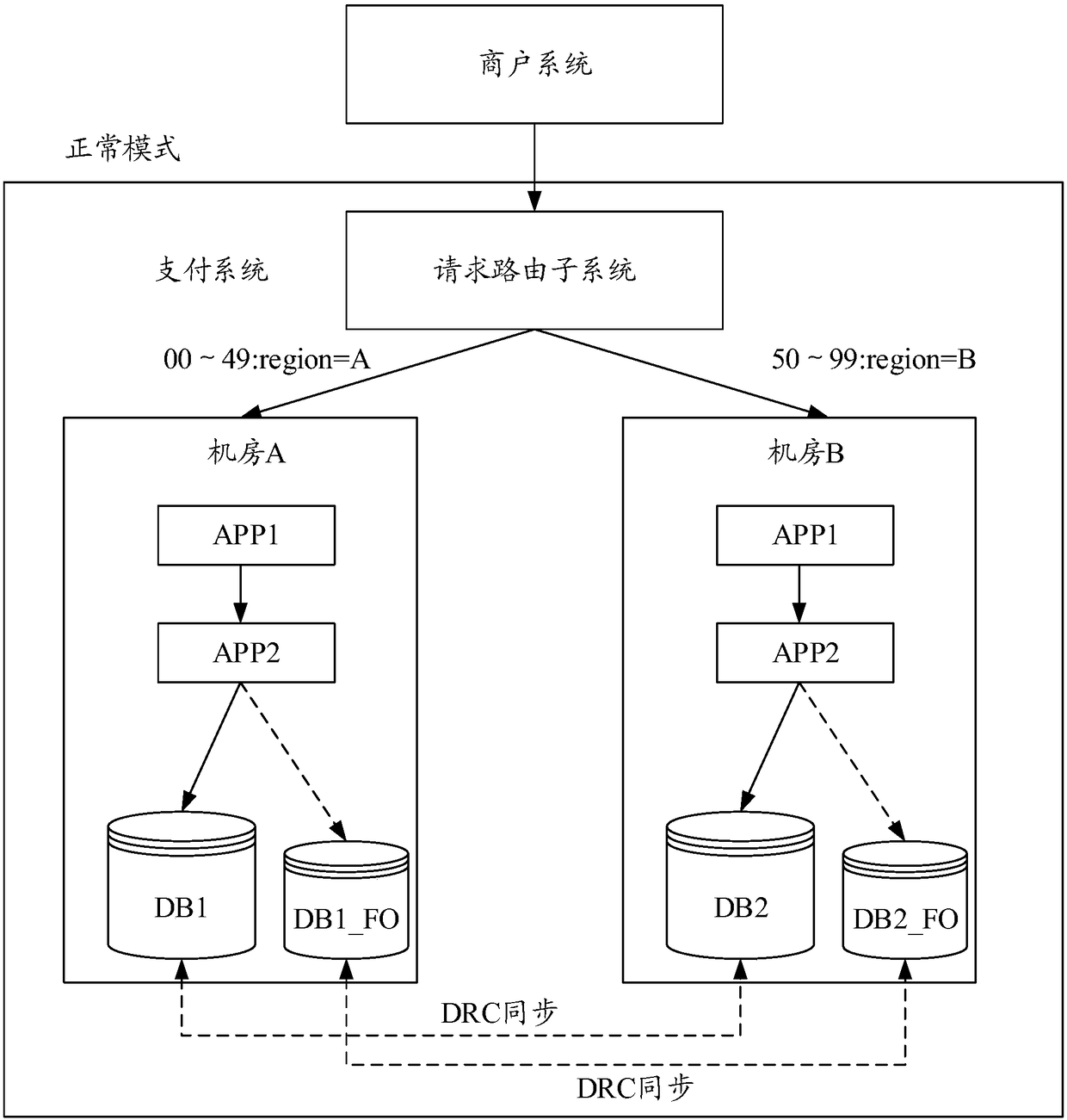
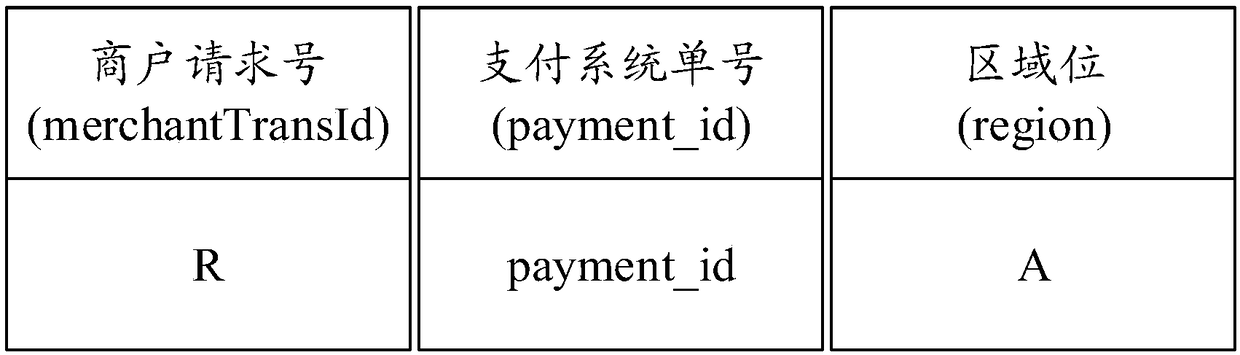
Disaster tolerance system, method, apparatus and device
ActiveCN108415792AReduce callsGuaranteed idempotent controlDatabase distribution/replicationRedundant operation error correctionData synchronizationComputer module
Embodiments of the present specification disclose a disaster tolerance system, method, apparatus and device. According to the technical scheme disclosed by the embodiments of the present specification, when a service request is received and allocated to the machine room, a corresponding relationship between the machine room for processing the request and the service request is established and stored; and the service processing result is synchronized between the machine room and the mirror machine room through a data synchronization module, so that there is a full amount of data in the two machine rooms, when one machine room is in disaster, the other machine room has the data of the disaster room, and at the moment, the idempotence control of the data part in the disaster room can be guaranteed.
Owner:ADVANCED NEW TECH CO LTD
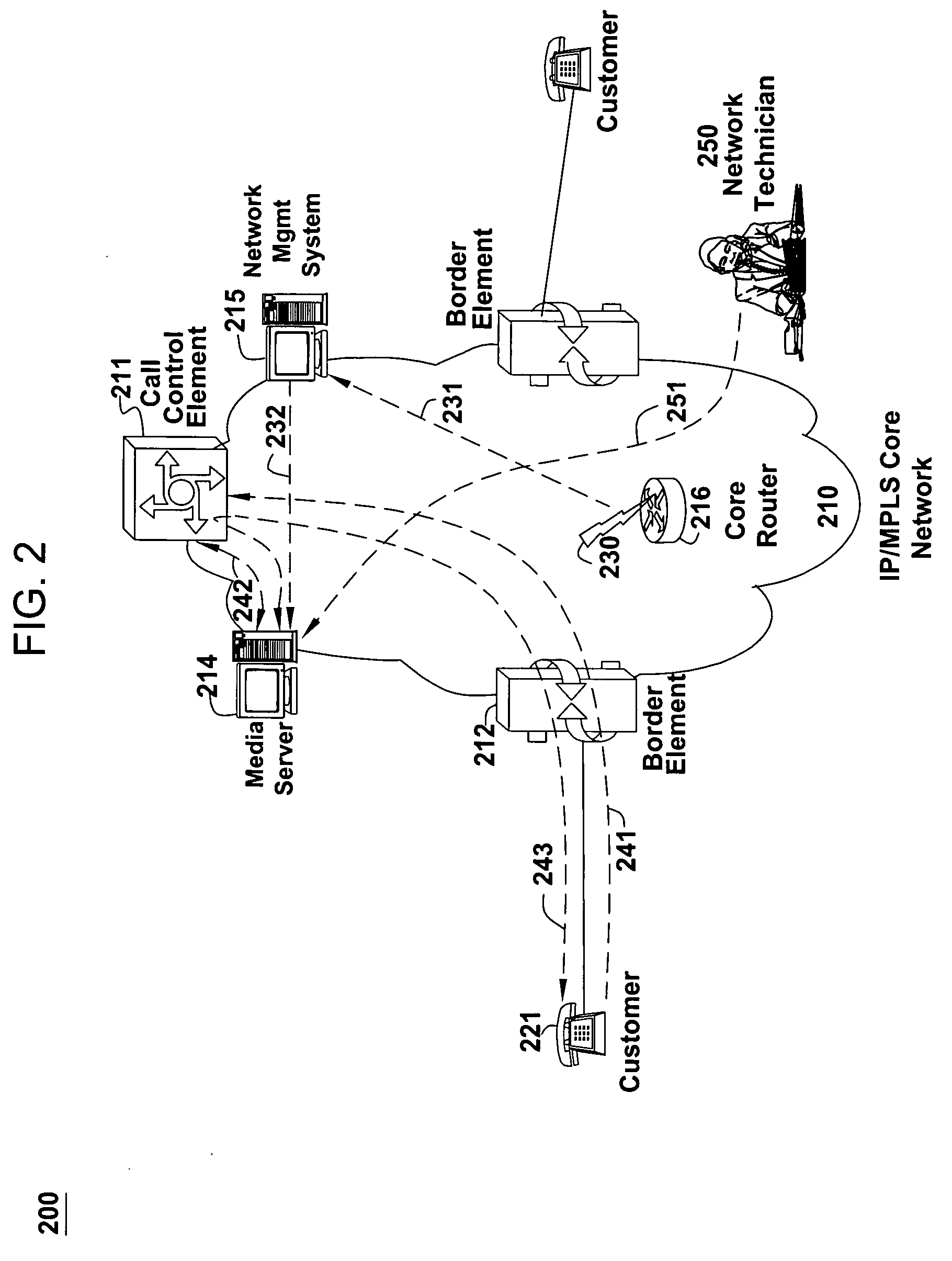
Method and apparatus for providing network announcements about service impairments
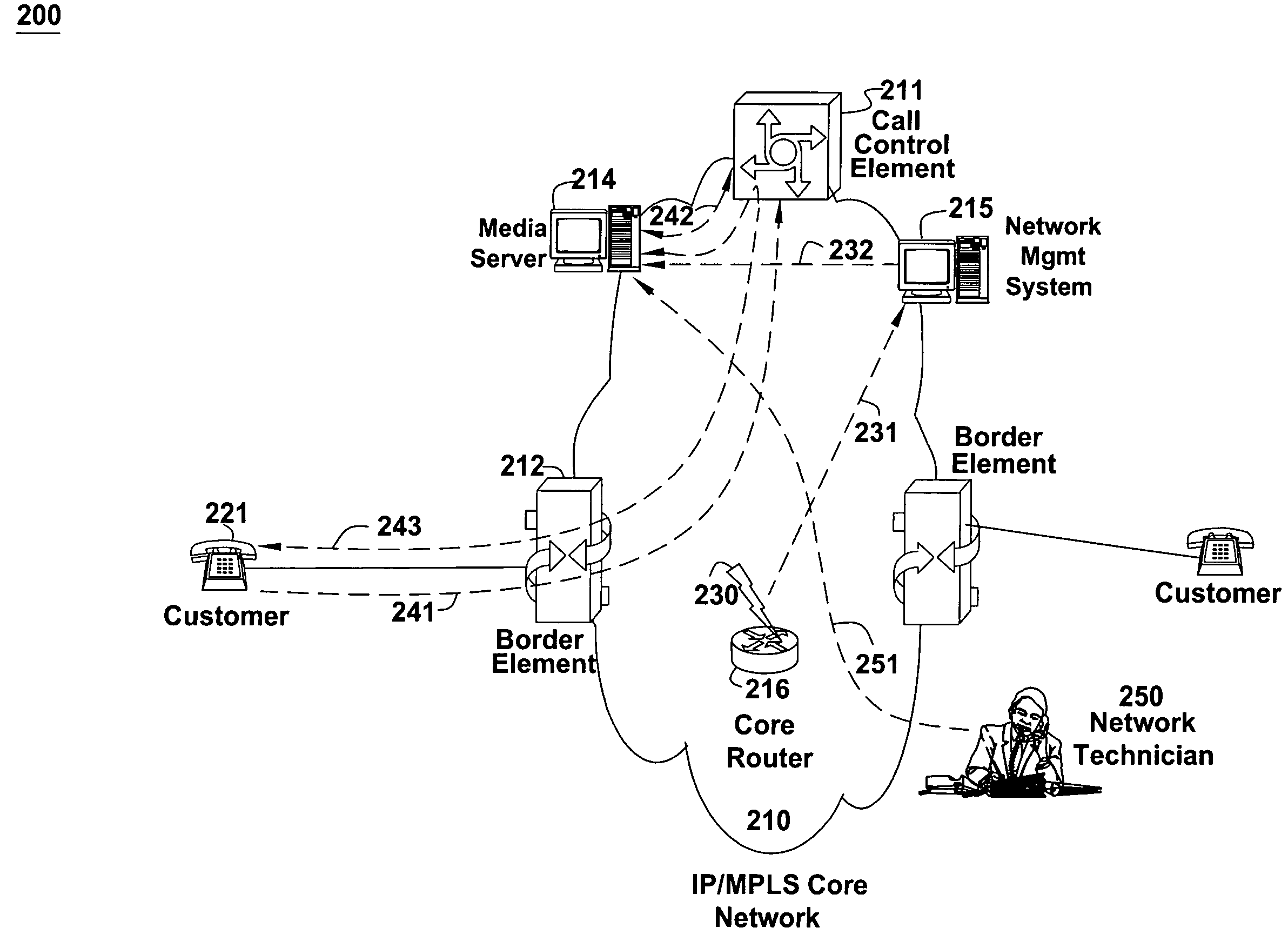
InactiveUS20060147023A1Reduce callsImprove customer satisfactionAutomatic call-answering/message-recording/conversation-recordingTwo-way working systemsMedia serverSpeech sound
The present invention enables information about a service impacting network event to be collected from network operations and automatically conveyed to a Media Server that plays a network announcement to callers into network customer service center. The announcement can be played as an option on an Interactive Voice Response (IVR) menu and informs the caller of known service issues that are being addressed and estimates of when service should return to normal.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
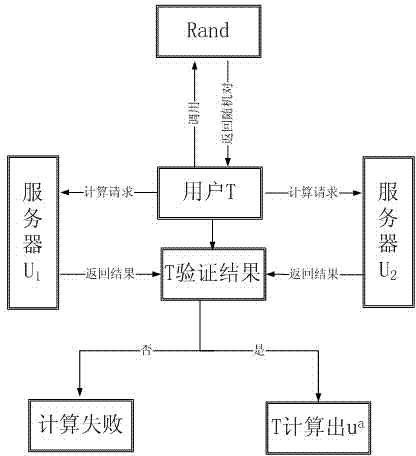
Method and system for outsourcing security mode indexes in cloud environment
The invention relates to the technical field of cloud computing, and discloses a method for outsourcing security mode indexes in a cloud environment. The method specially includes the steps that u is split into a formula shown in the specification by a user T according to pairs returned by Rand, the formula is sent to an idle server U1 and an idle server U2 which are not collaborated to be computed, the two servers return the computing results to the user T, and the user T verifies the returned results. By the adoption of the method, calling of Rand is small, logic splitting of u is simple, the computing amount is small, and the detection rate can reach 100%. The invention further discloses a system for outsourcing the security mode indexes in the cloud environment.
Owner:SICHUAN UNIVERSITY OF SCIENCE AND ENGINEERING
Building multi-performance oriented design optimization method
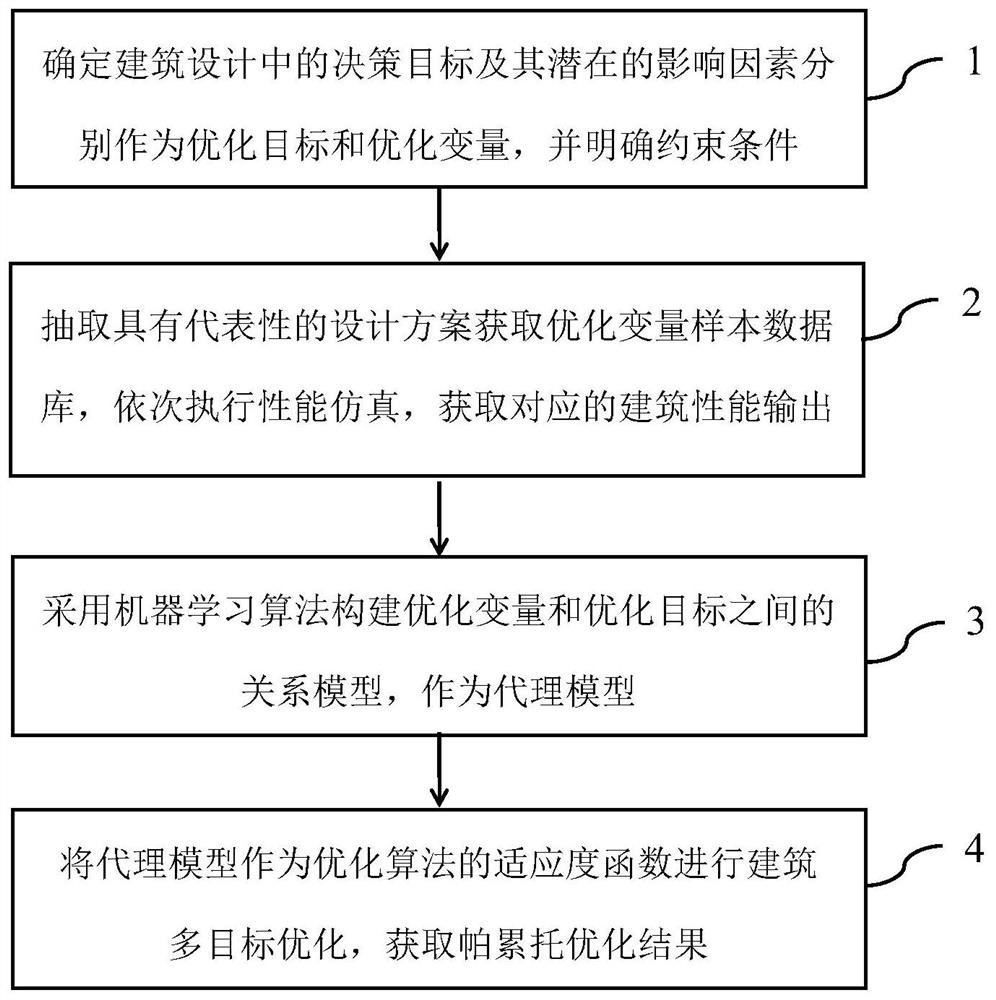
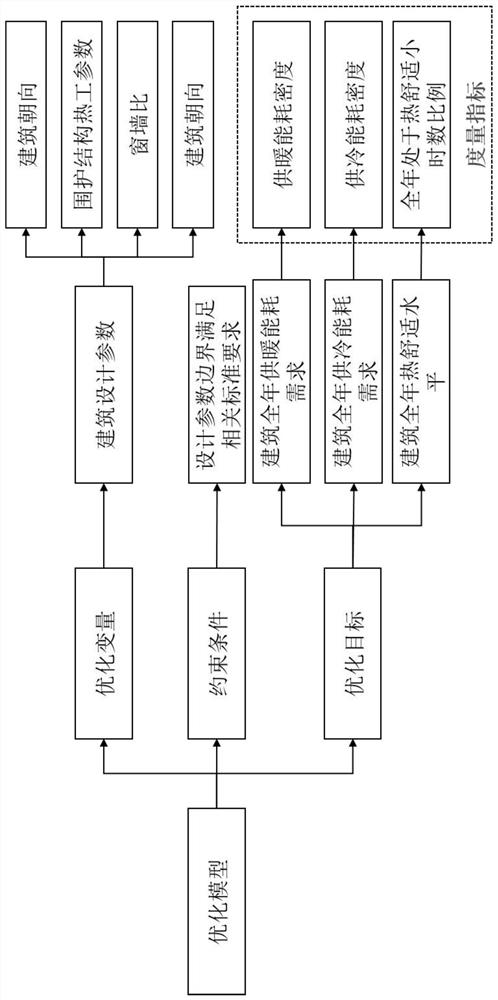
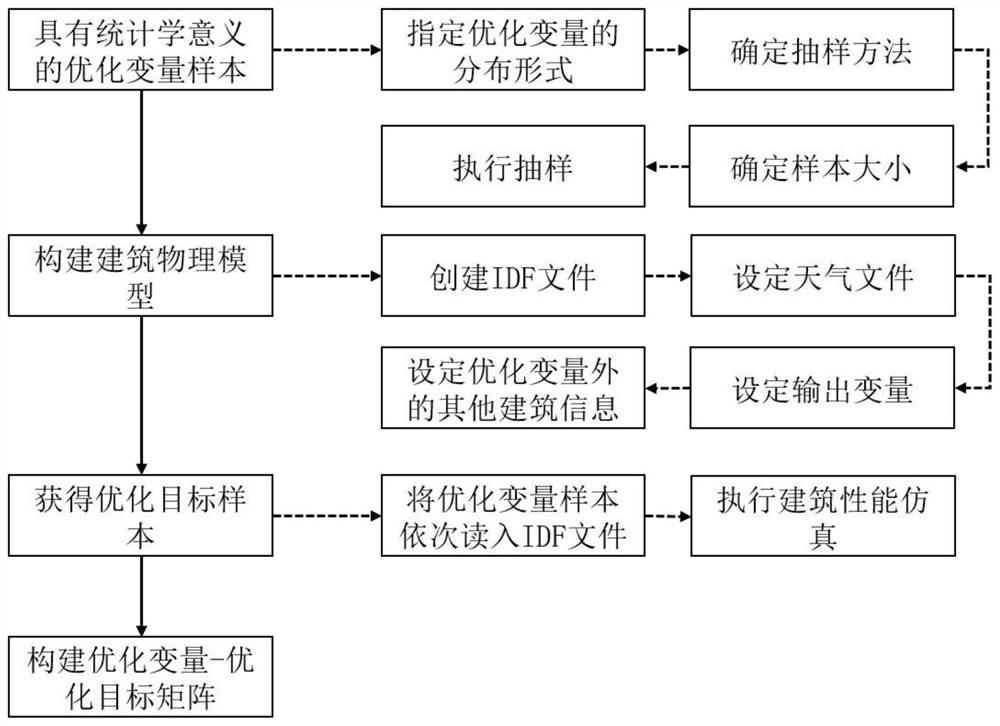
ActiveCN112149209AReduce callsReduce optimization timeGeometric CADDesign optimisation/simulationGenetics algorithmsPhysical model
The invention discloses a building multi-performance oriented design optimization method, which comprises the steps of 1, determining a building design decision target and potential influence factorsthereof as an optimization target and an optimization variable respectively, and defining constraint conditions so as to construct an optimization model; 2, obtaining a building performance sample library with statistical representativeness, wherein the step comprises construction of an optimization variable sample matrix, setting of a building physical model, construction of a building performance output matrix and construction of a building multi-dimensional input and multi-dimensional output sample matrix; 3, constructing a simplified relation model between the optimization variable and theoptimization target by adopting a machine learning algorithm, and taking the simplified relation model as an agent model; and 4, taking the agent model as a fitness function of an optimization algorithm, executing building multi-objective optimization, and obtaining a Pareto optimization result. According to the method, the multi-objective optimization process of the building performance can be more scientific and standard, calling of EnergyPlus software in the optimization process is reduced through the coupling agent model and the multi-objective genetic algorithm, and the optimization timeis shortened.
Owner:TIANJIN UNIV
Receiving apparatus using non-volatile memory and method of operating the same
InactiveUS20070157270A1Reduce startup timeEasy to startTelevision system detailsPosition fixationBroadcast dataOperating system
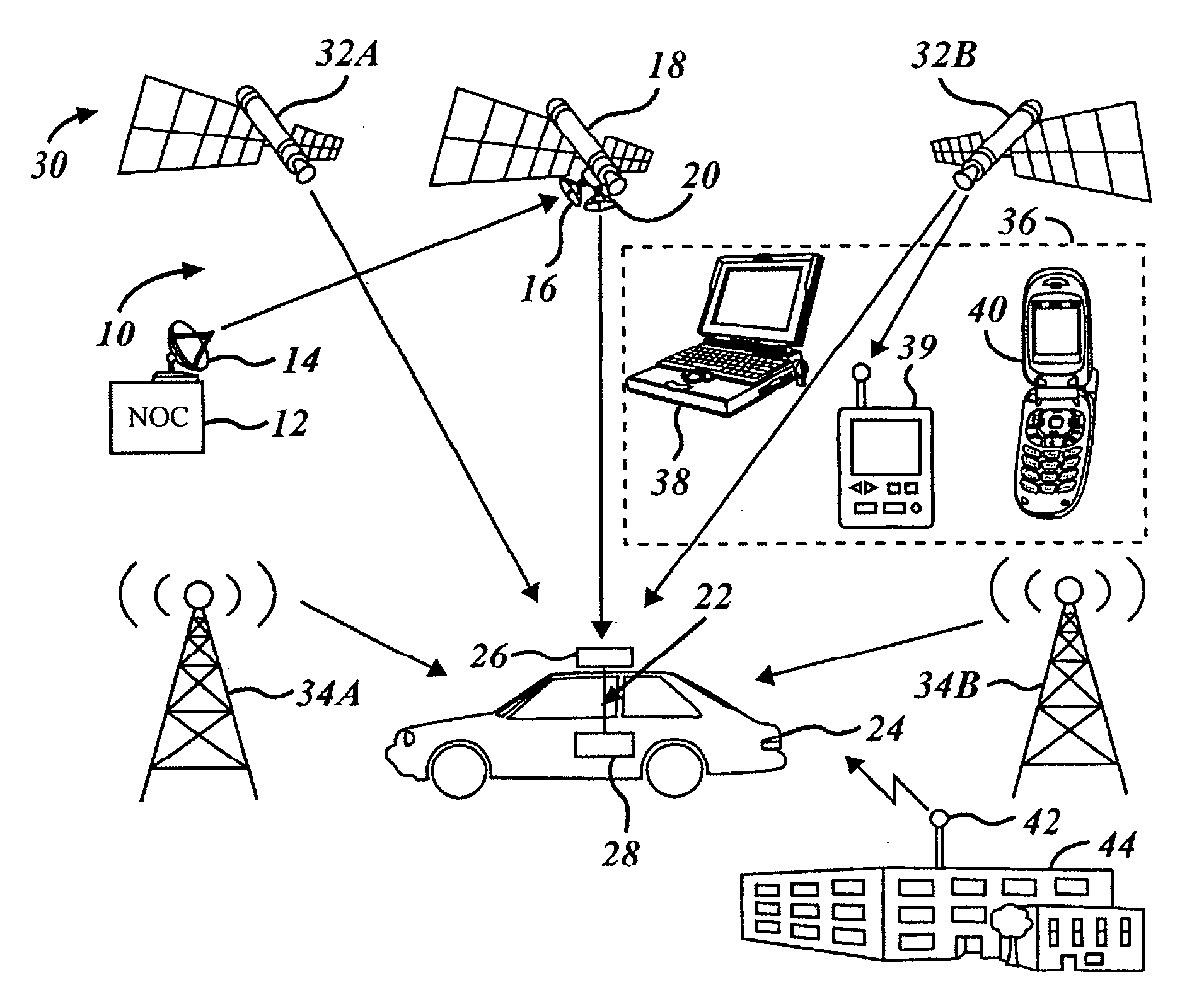
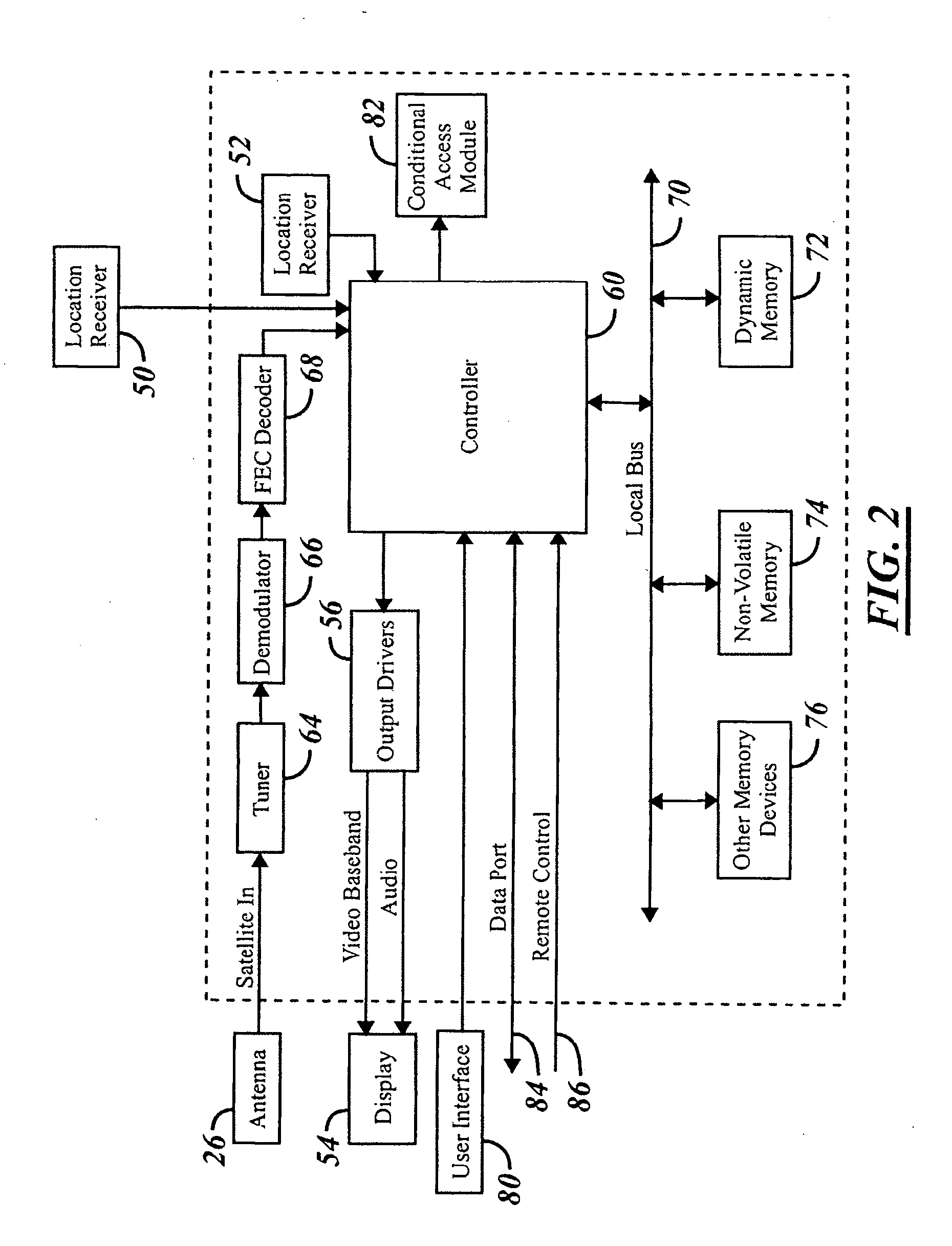
A mobile receiving unit (28) may be coupled to an antenna (26) for receiving various information. A tuner (64) receives the information such as program guide data from the antenna and provides it to controller (60). Controller (60) may be coupled to a non-volatile memory (74). The non-volatile memory (74) may be used to store information such as a program guide. The program guide may operate from a dynamic memory (72). The non-volatile memory (74) thus saves the information so that the program guide does not need to be reloaded from broadcast data upon a reboot of the system. The program guide data may be loaded from non-volatile memory (74) upon a reboot.
Owner:THE DIRECTV GROUP
Method for obtaining system call white list required by container
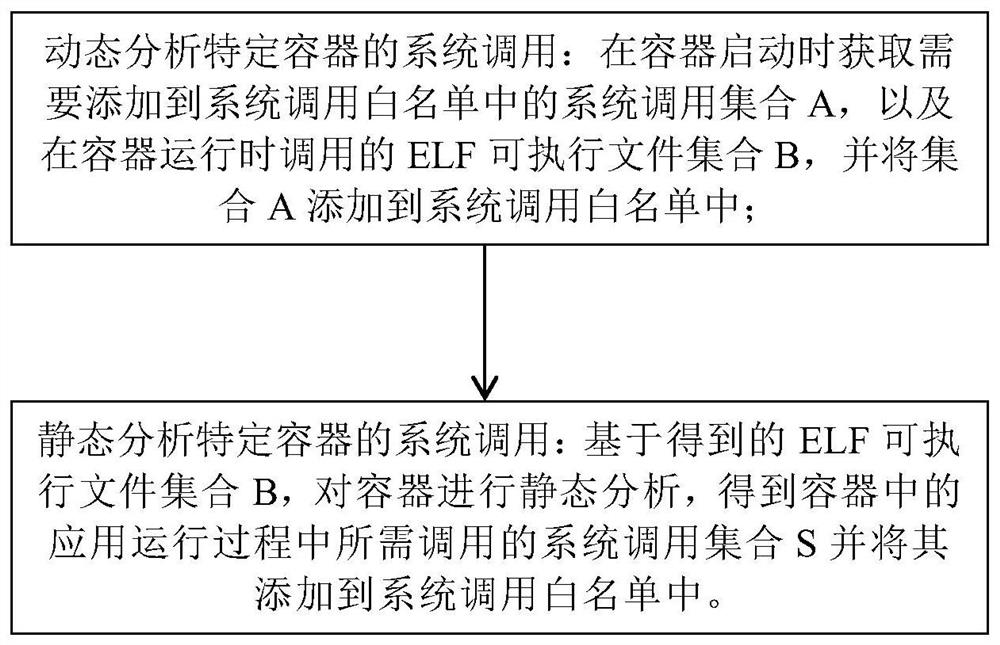
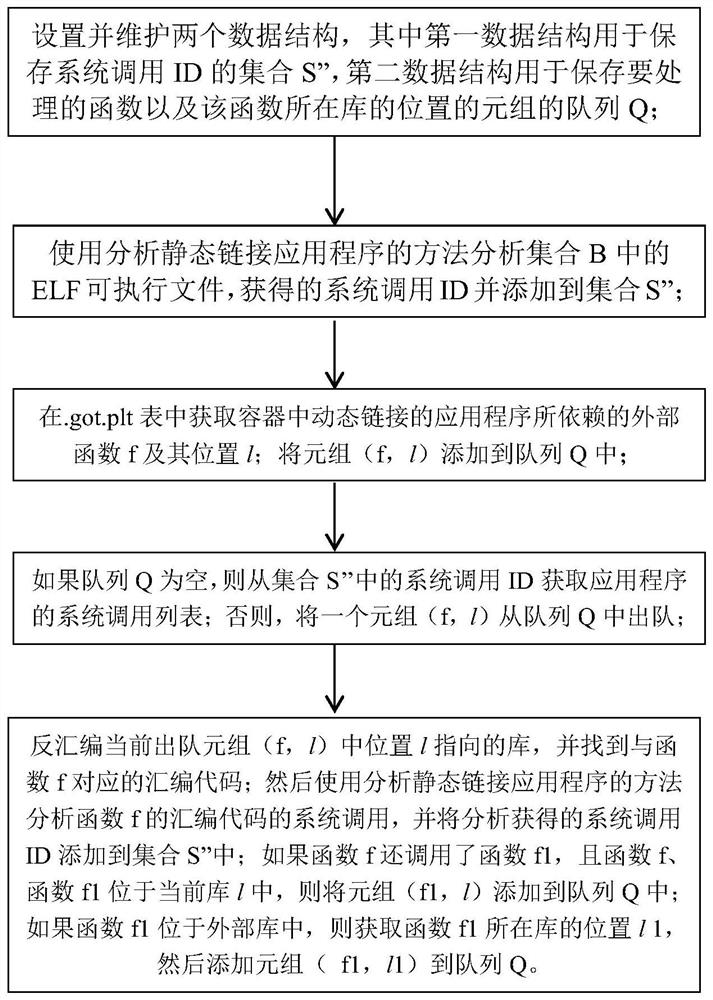
ActiveCN111651752AReduce callsReduce percentageProgram initiation/switchingPlatform integrity maintainanceSoftware engineeringSystem call
The invention discloses a method for obtaining a system call white list required by a container, which comprises the following steps of: 1) when the container is started, obtaining a system call set Arequired to be added into the system call white list and an ELF executable file set B called when the container runs, and adding the set A into the system call white list; and 2) based on the ELF executable file set B obtained in the step 1), carrying out static analysis on the container to obtain a system call set S required to be called in an application running process in the container, and adding the system call set S into a system call white list. According to the method, the system call white list is obtained through dynamic analysis and static analysis, compared with default configuration of Docker, system call is reduced by 69.27%-85.89%, and safety and operation efficiency are improved.
Owner:PEKING UNIV
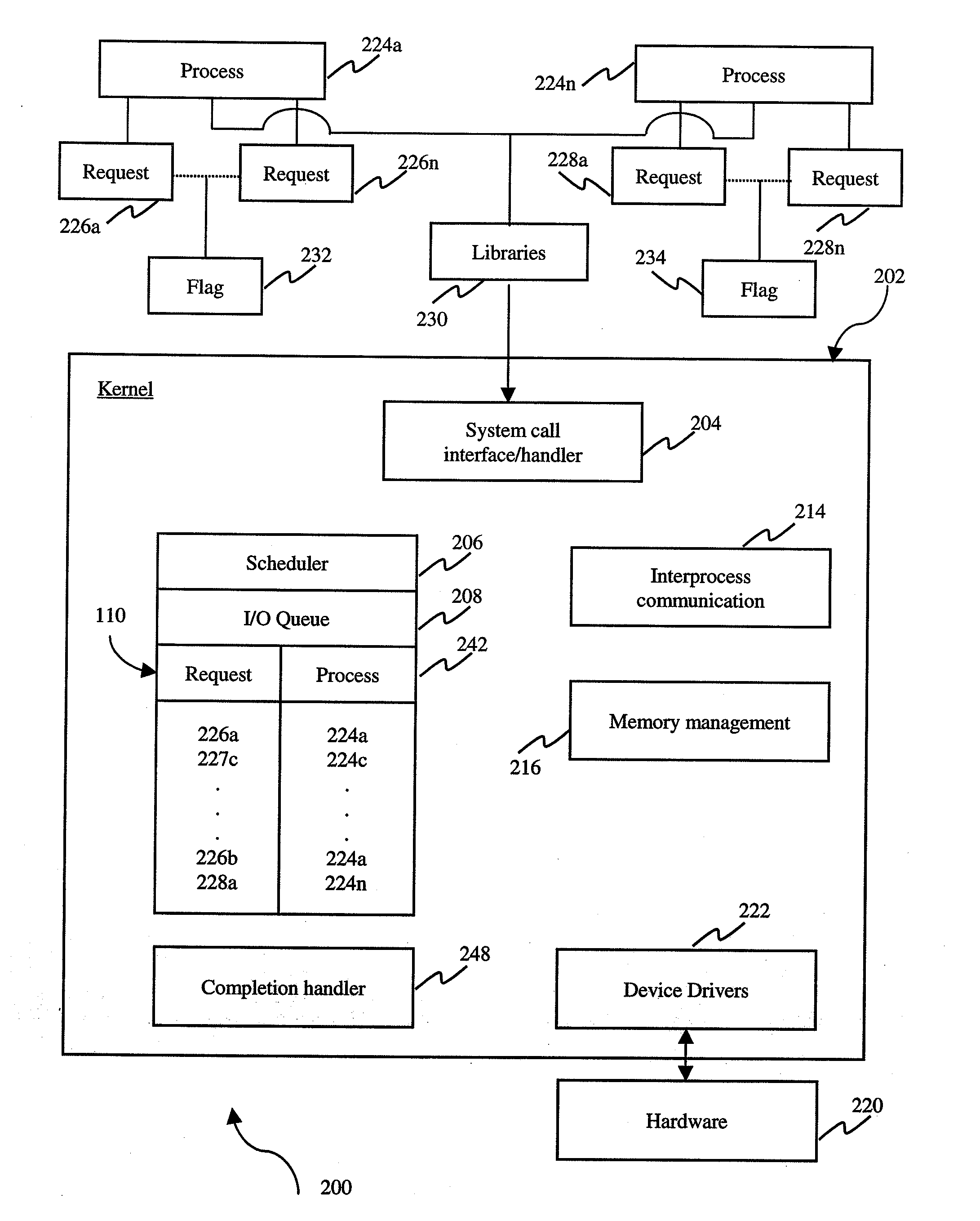
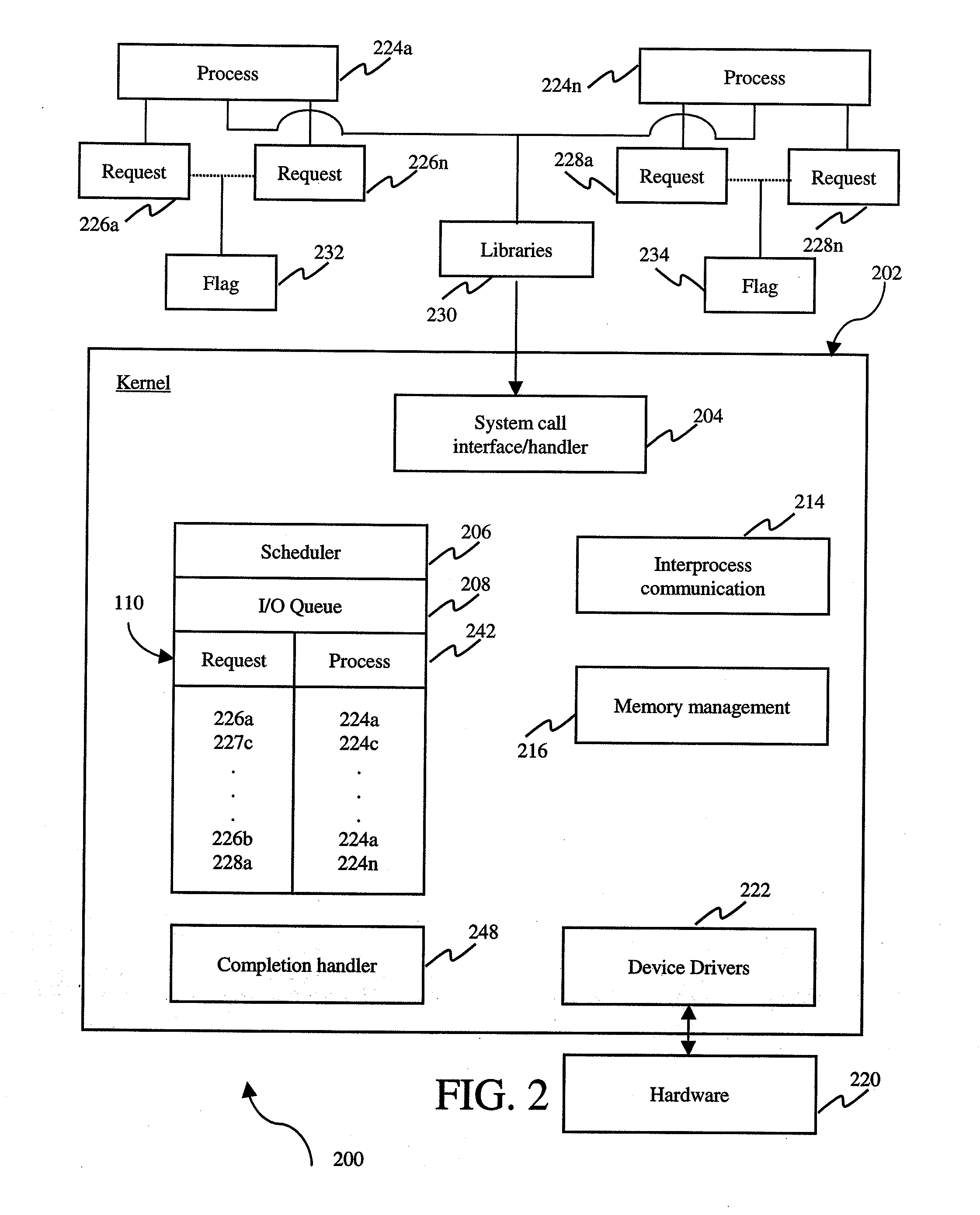
System, method and medium for providing asynchronous input and output with less system calls to and from an operating system
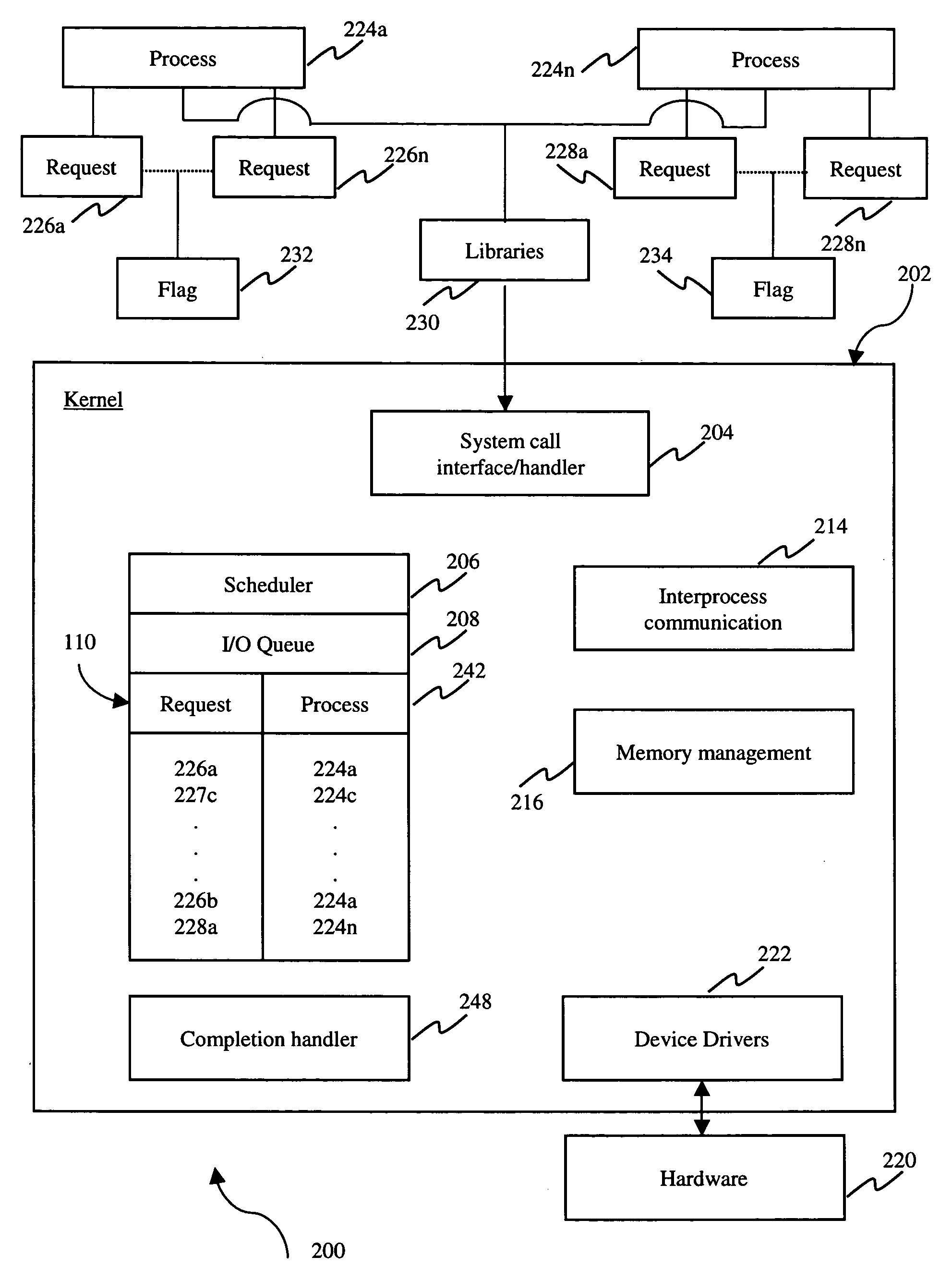
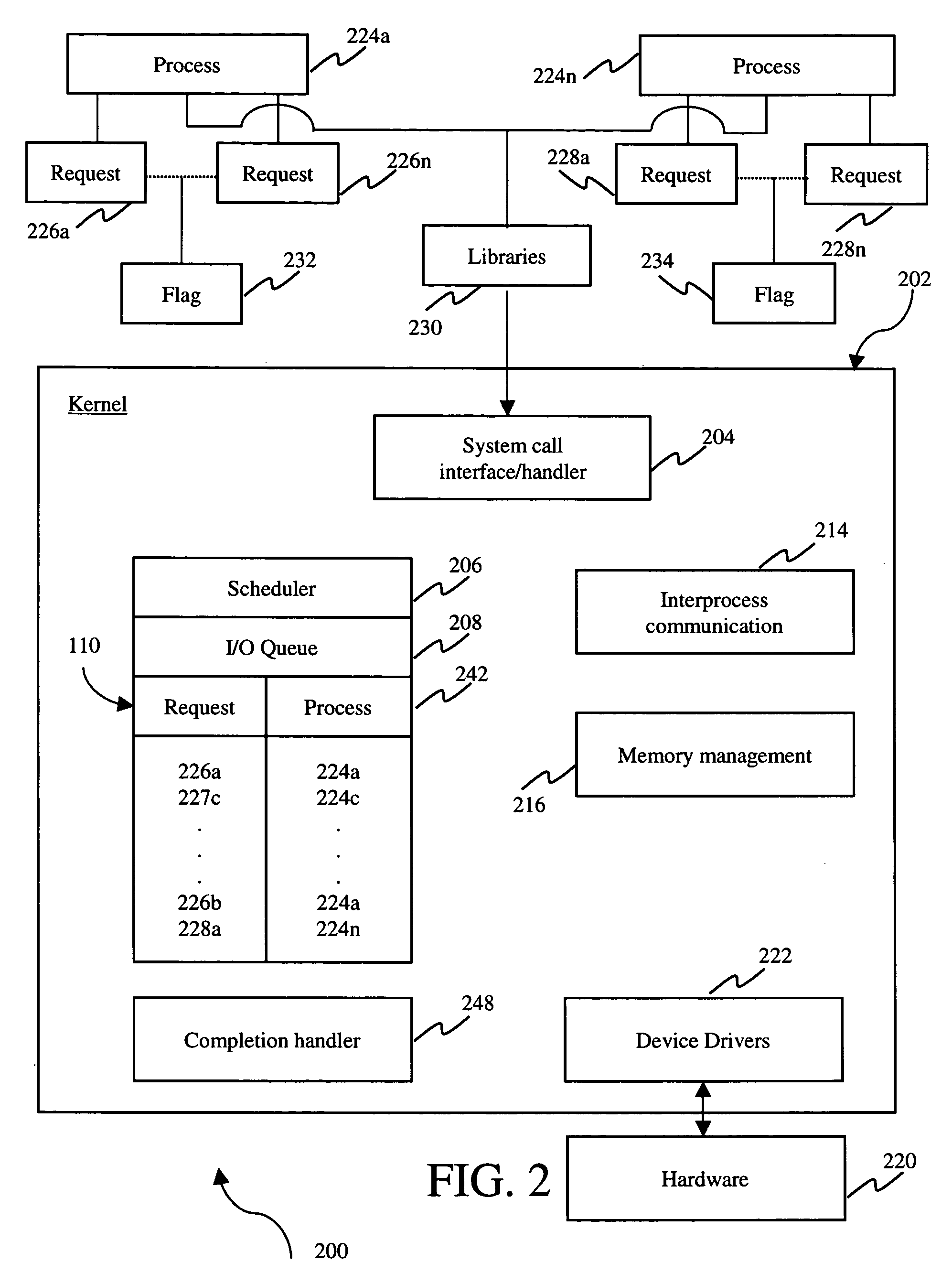
ActiveUS20060184948A1Less system callsMany timesMultiprogramming arrangementsSoftware simulation/interpretation/emulationOperational systemSystem call
A system, method and medium for reducing the number of system calls from an application program to an operating system kernel. In an embodiment, a method includes the steps of creating a list of requests issued by an application program, associating an indicia with the list indicating whether the list contains a request, querying the indicia to determine if the list contains a request, and adding a new application program request to the list when the indicia indicates that the list includes a request.
Owner:RED HAT
System, Method and Medium for Providing Asynchronous Input and Output with Less System Calls to and From an Operating System
ActiveUS20100169897A1Less system callsMany timesMultiprogramming arrangementsMultiple digital computer combinationsOperational systemApplication procedure
A system, method and medium for reducing the number of system calls from an application program to an operating system kernel. In an embodiment, a method includes the steps of creating a list of requests issued by an application program, associating an indicia with the list indicating whether the list contains a request, querying the indicia to determine if the list contains a request, and adding a new application program request to the list when the indicia indicates that the list includes a request.
Owner:RED HAT
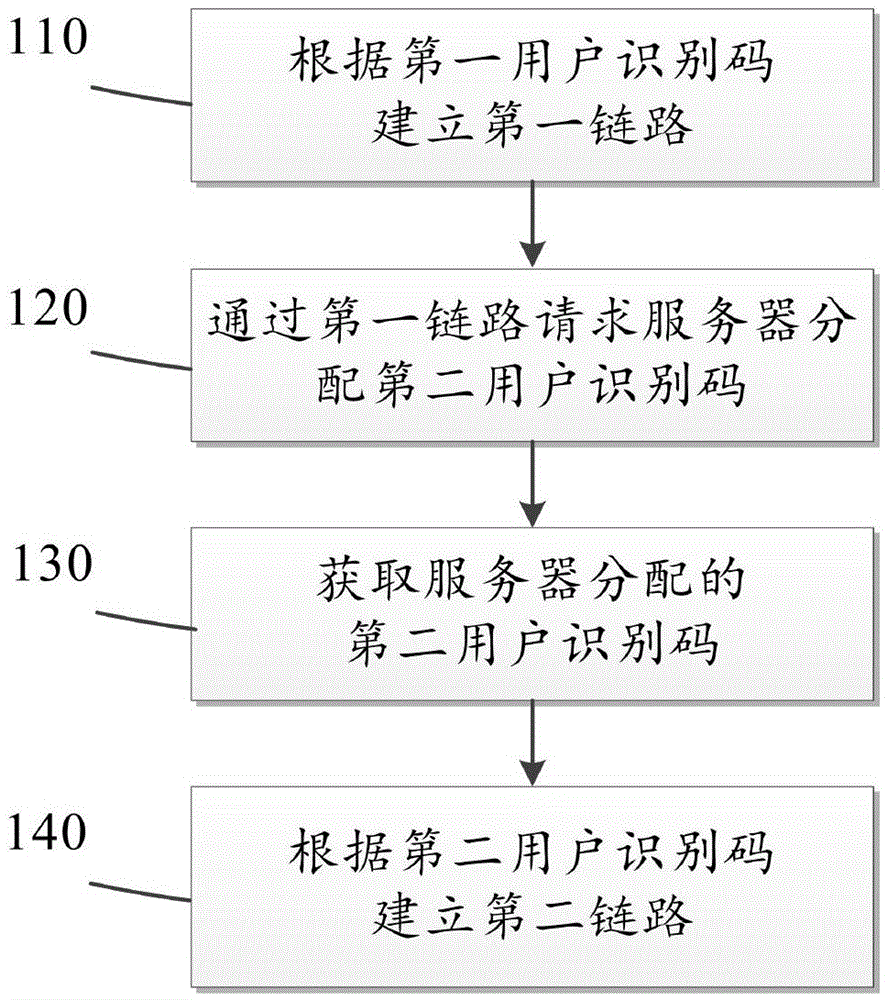
Access method, user equipment and server
InactiveCN105682086AConvenient calls and trafficReduce calls and trafficNetwork topologiesConnection managementServer allocationCommunication quality
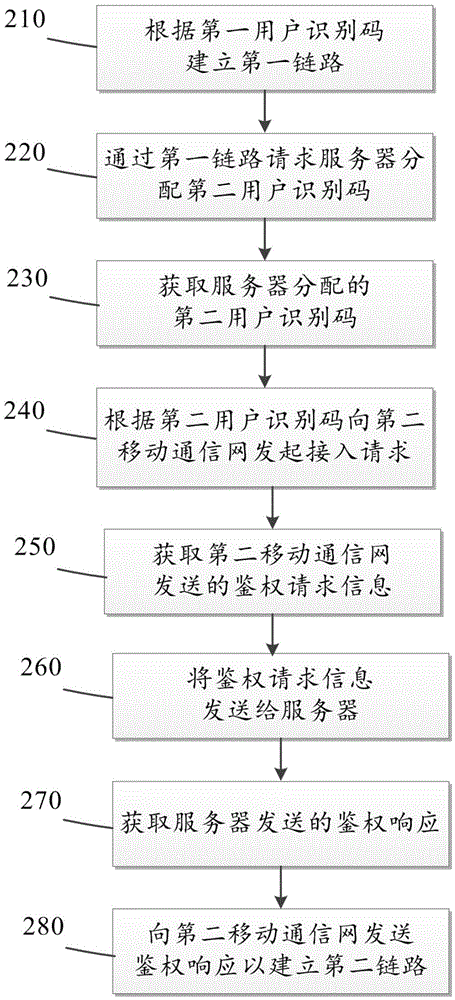
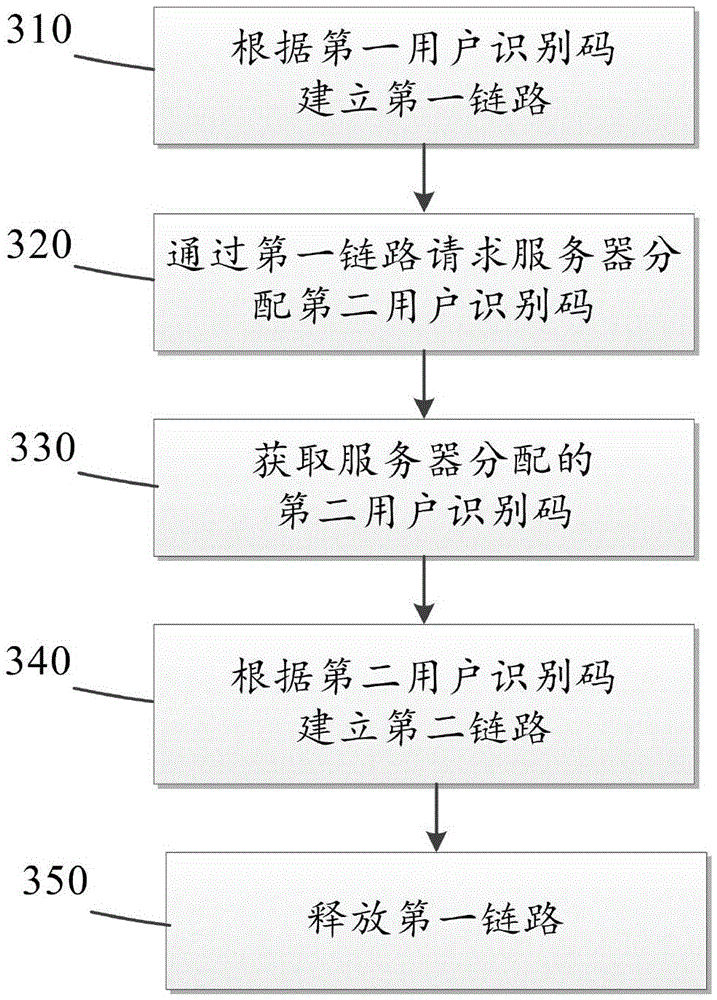
The embodiment of the invention provides an access method. The access method comprises the following steps of: establishing a first link between user equipment and a first mobile communication network according to a first user identification code; requesting a server for distributing a second user identification code to the user equipment through the first link, wherein the second user identification code is a user identification code corresponding to one SIM card in the server; and furthermore, the second user identification code is a local user identification code at the position, where the user equipment is currently; obtaining the second user identification code distributed by the server through the first link; and establishing a second link between the user equipment and a second mobile communication network in the current position according to the second user identification code. By means of the embodiment of the invention, the roaming charge can be reduced; and the communication quality can be improved.
Owner:SHENZHEN TUGE INFORMATION CO LTD
Method for improving IPS detection performance by adopting AMP architecture
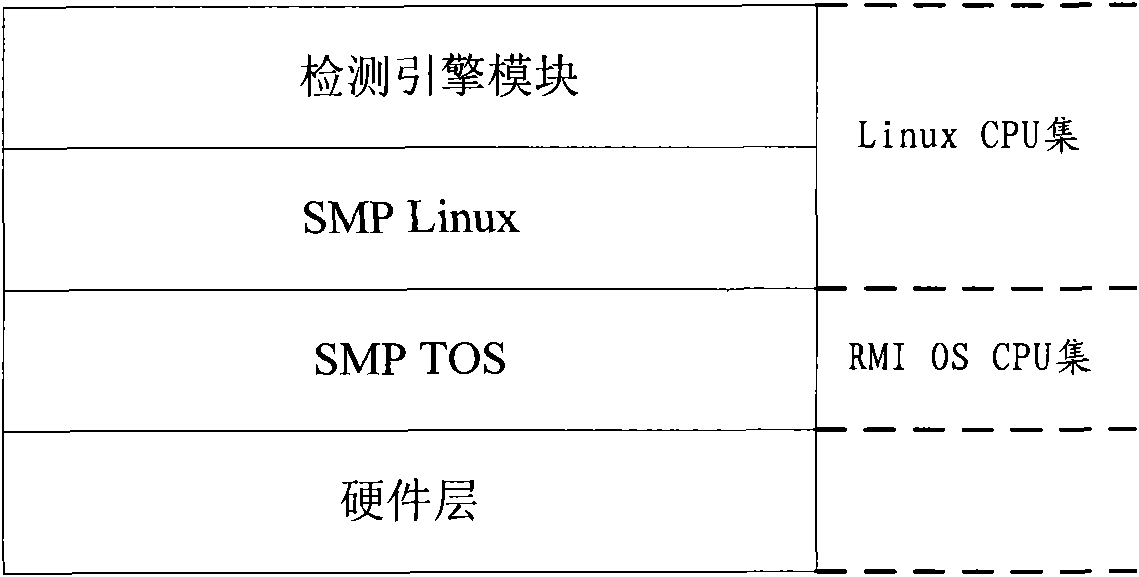
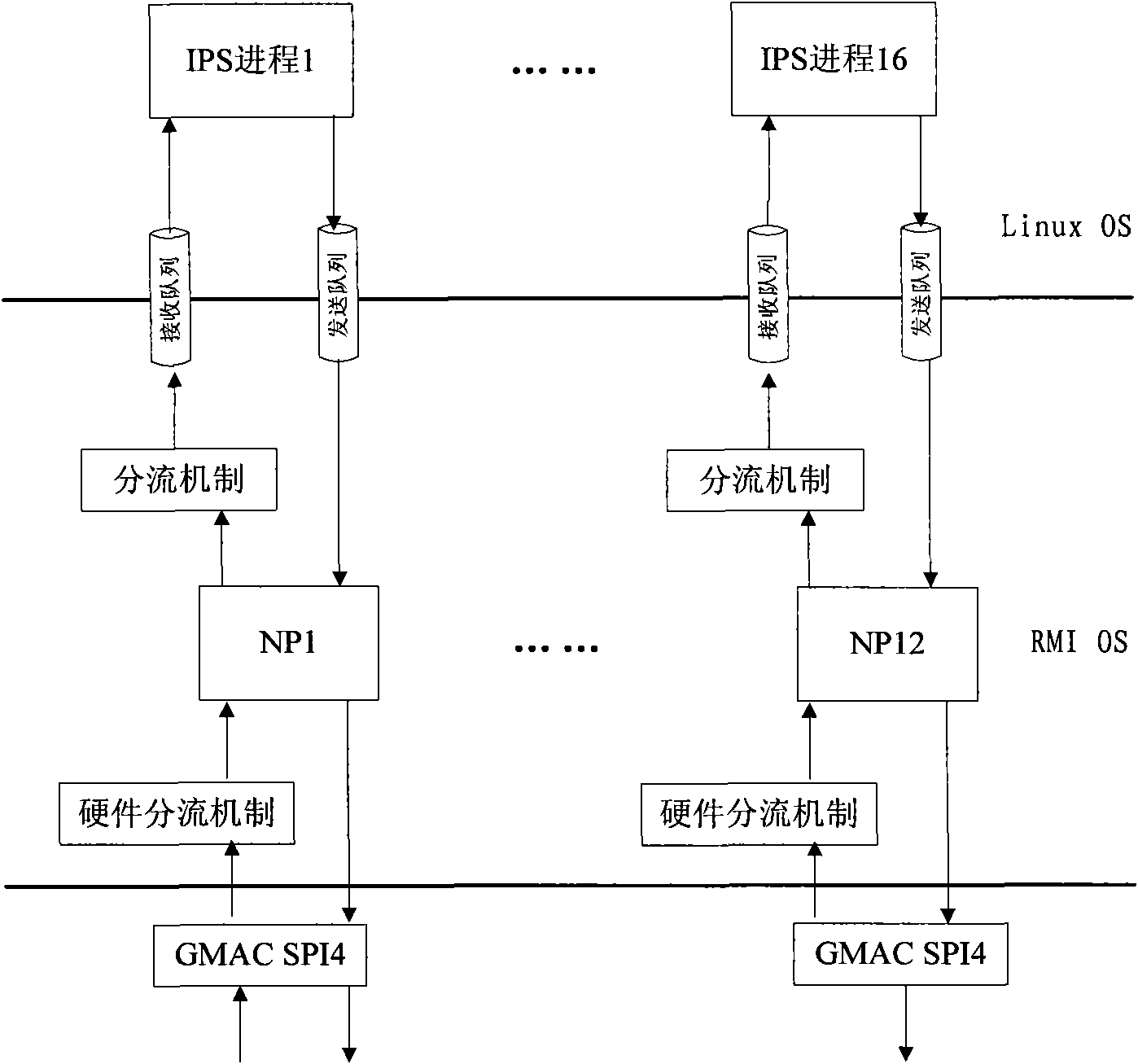
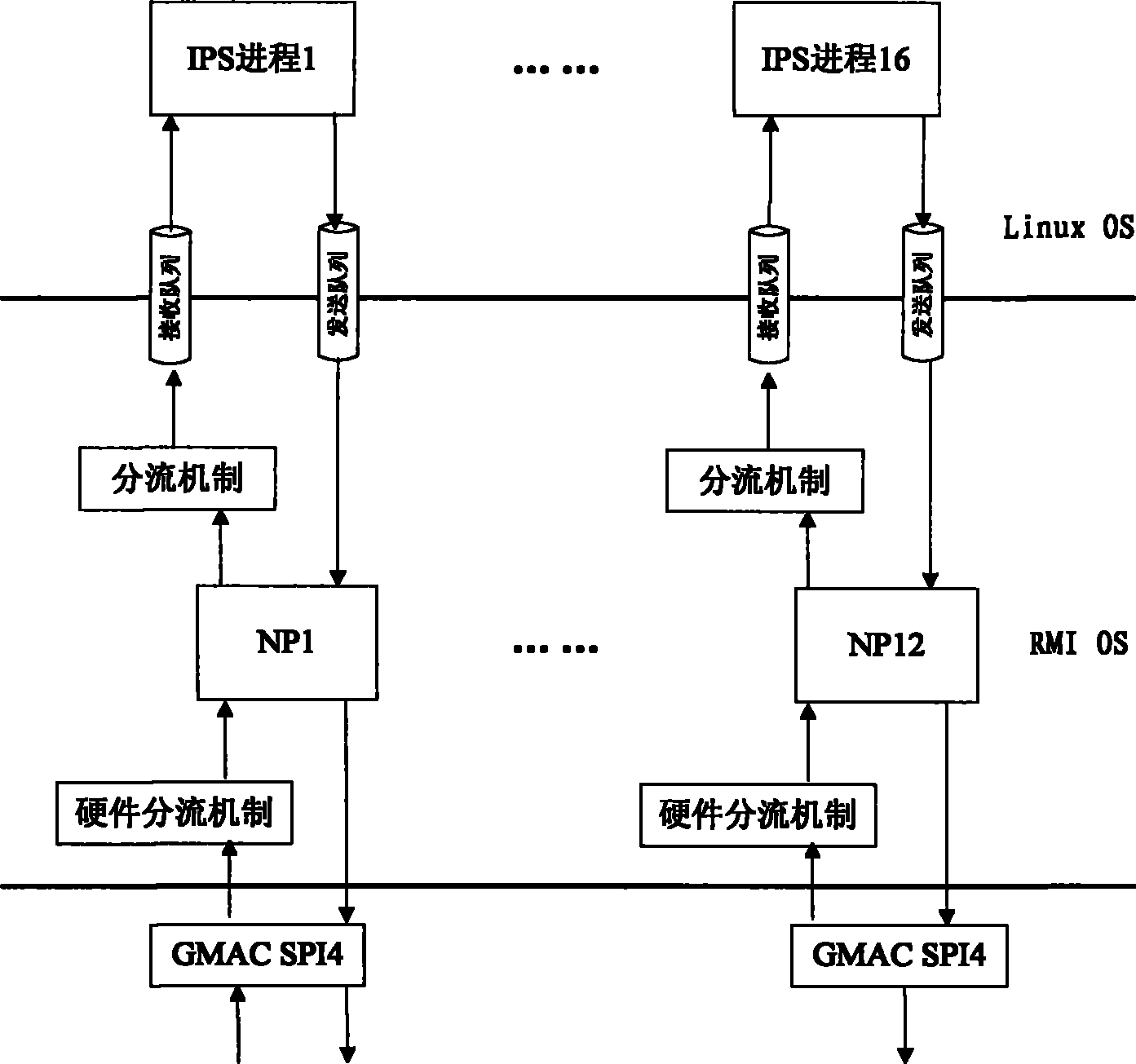
InactiveCN101778012AImprove processing efficiencyImprove performanceData switching networksTraffic volumeMulti-core processor
The invention provides a method for improving IPS detection performance by adopting AMP architecture, which comprises the following steps: step A, a hardware layer receives network data packets, and the data packets are transferred to a network processor (NP) through a hardware shunting mechanism; step B, after the NP receives the data packets, network flow processing (comprising recombination of IP fragments, decoding and exchanging of the data packets and establishment and maintenance of connection) is carried out on the data packets, and the processed data packets are packed into IPS queues, wherein each IPS detection process corresponds to an IPS queue; step C, each IPS process waits for data on the IPS queue thereof, when the data exists on the IPS queue, feature detection is carried out on the data packets, and the detected data packets are injected into a network processing layer; and step D, the NP acquires the data packets which are transferred from each IPS process and are processed by IPS detection, and the subsequent processing is carried out according to detection results. The invention can improve IPS performance on a multi-core processor platform by utilizing the parallel processing technique.
Owner:BEIJING TOPSEC TECH
Novel virtual machine software protection method based on stack hiding
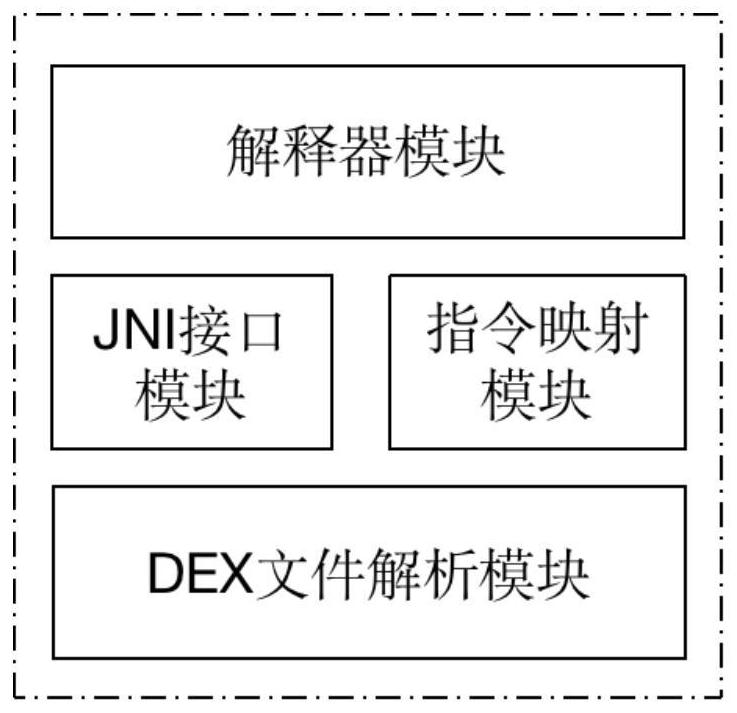
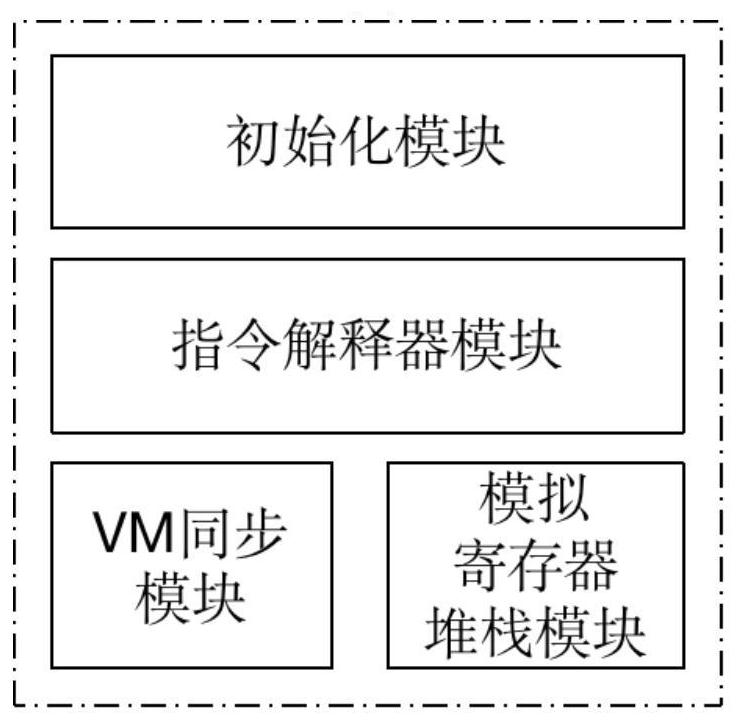
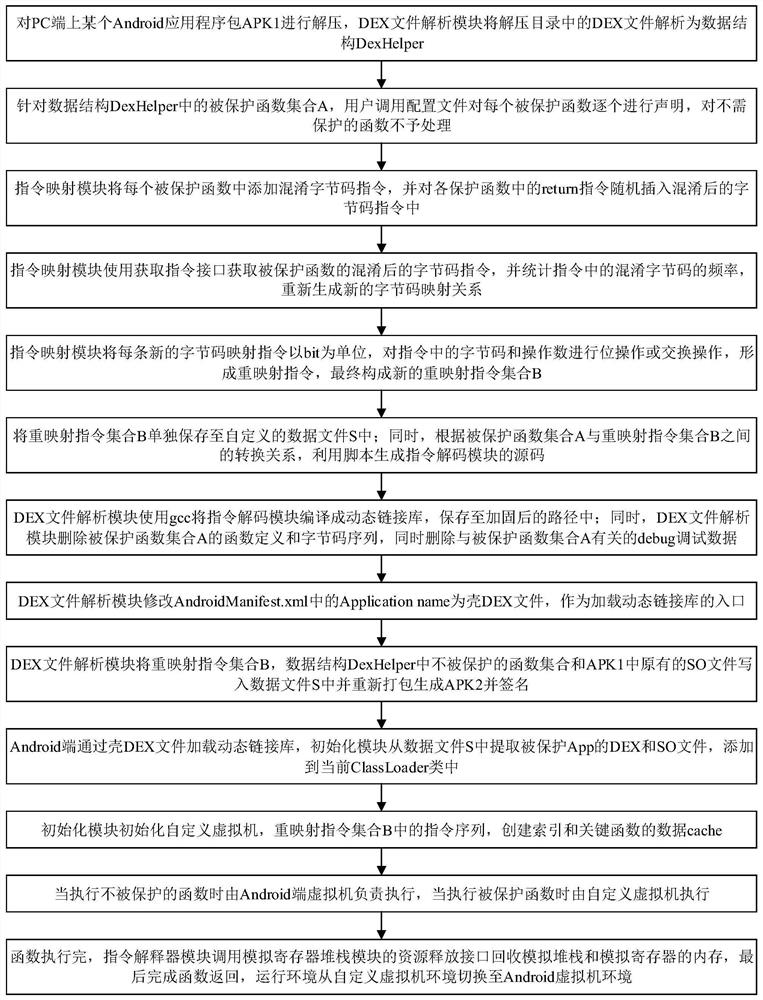
ActiveCN112163195AGuess the detailed functionPrevent guessworkProgram/content distribution protectionSoftware simulation/interpretation/emulationSoftware engineeringData file
The invention discloses a novel virtual machine software protection method based on stack hiding, and belongs to the field of mobile application reinforcement. The method comprises the steps: analyzing a DEX file into a data structure DeHelper, enabling an instruction mapping module to add an obfuscated byte code instruction to each protected function, randomly inserting a return instruction intothe obfuscated byte code instruction, and counting the frequency of the obfuscated byte codes; enabling the instruction mapping module to perform bit operation or exchange operation on byte codes andoperands in each new byte code mapping instruction to form a new remapping instruction set B; writing an unprotected function set in the data structure DeHelper and an original SO file in the APK1 into a data file S, performing repackaging to generate the APK2 and performing signing; enabling an Android end initialization module to extract DEX and SO files of a protected App from the data file S,and creating an index and a data cache of a key function; enabling an Android end virtual machine to be responsible for executing an unprotected function, and enabling a user-defined virtual machine to execute a protected function. The method has the advantages of universality, portability and safety.
Owner:BEIJING UNIV OF POSTS & TELECOMM
A method for self-adaptive display of address book and terminal thereof
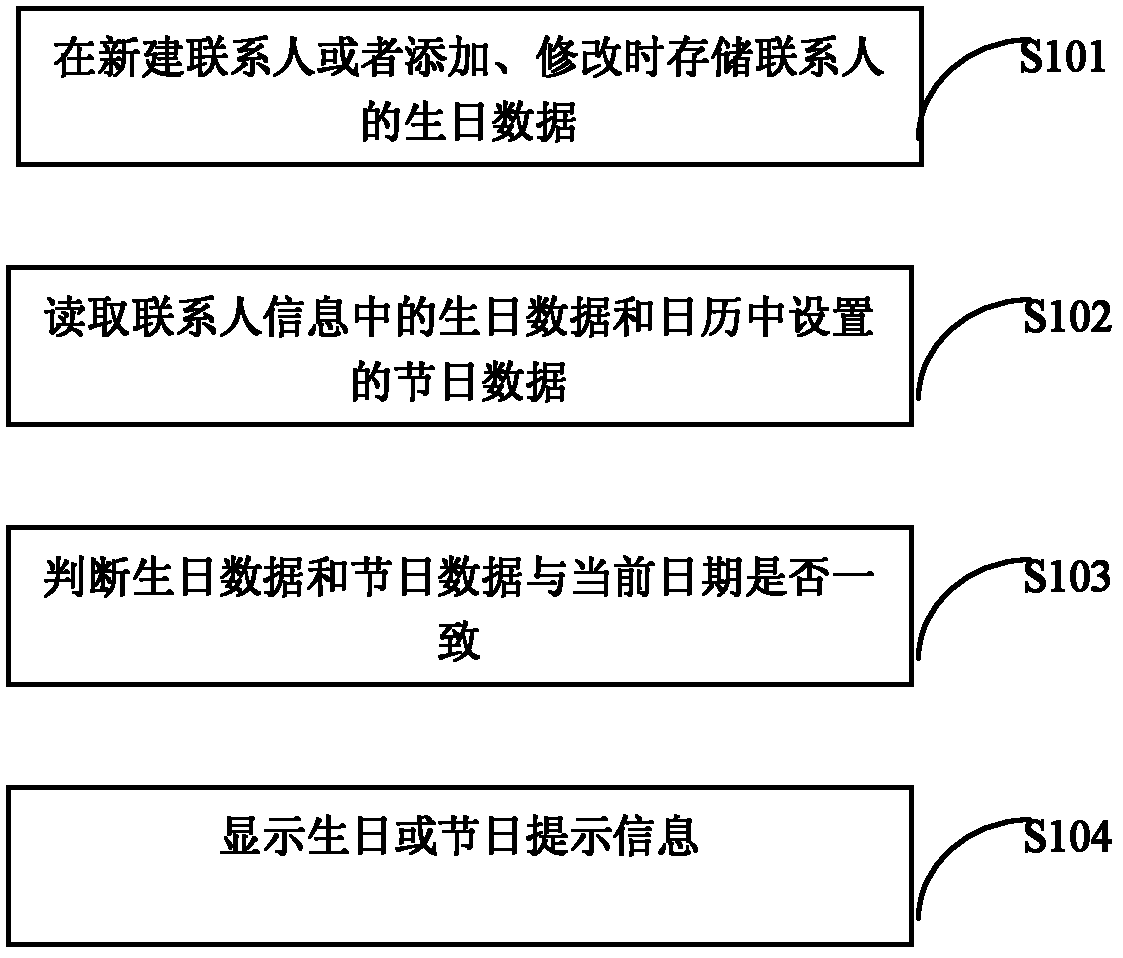
The invention discloses an adaptive display method for a contact list. The method comprises an adaptive display method for contact birthday and festival prompting information, and the adaptive display method for the contact birthday and festival prompting information comprises the following steps of: 101, storing the birthday data of a contact in the creation, addition or modification of the contact; 102, reading the birthday data from contact information and festival data set in a calendar; 103, judging whether the birthday data and the festival data are consistent with a current date or not; and 104, if the birthday data and the festival data are consistent with the current date, displaying the birthday or festival prompting information. The method further comprises a list sequencing adaptive display method and an adaptive display method for call suitability prompting information. The invention also provides a terminal for realizing the adaptive displaying of the contact list. By the method and the terminal, the adaptive sequencing, rich functions and convenience of searching of the contact list can be realized.
Owner:菏泽建数智能科技有限公司
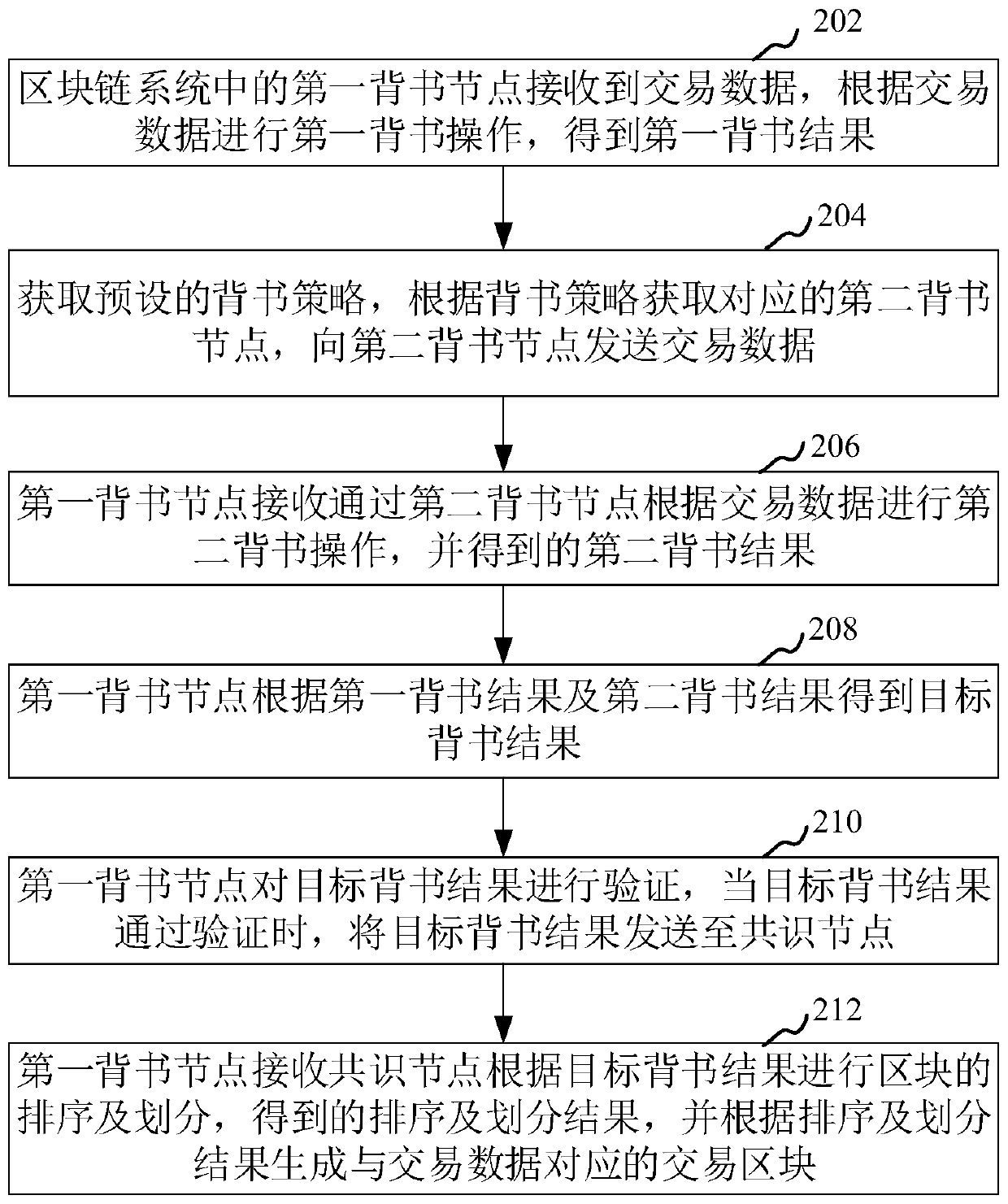
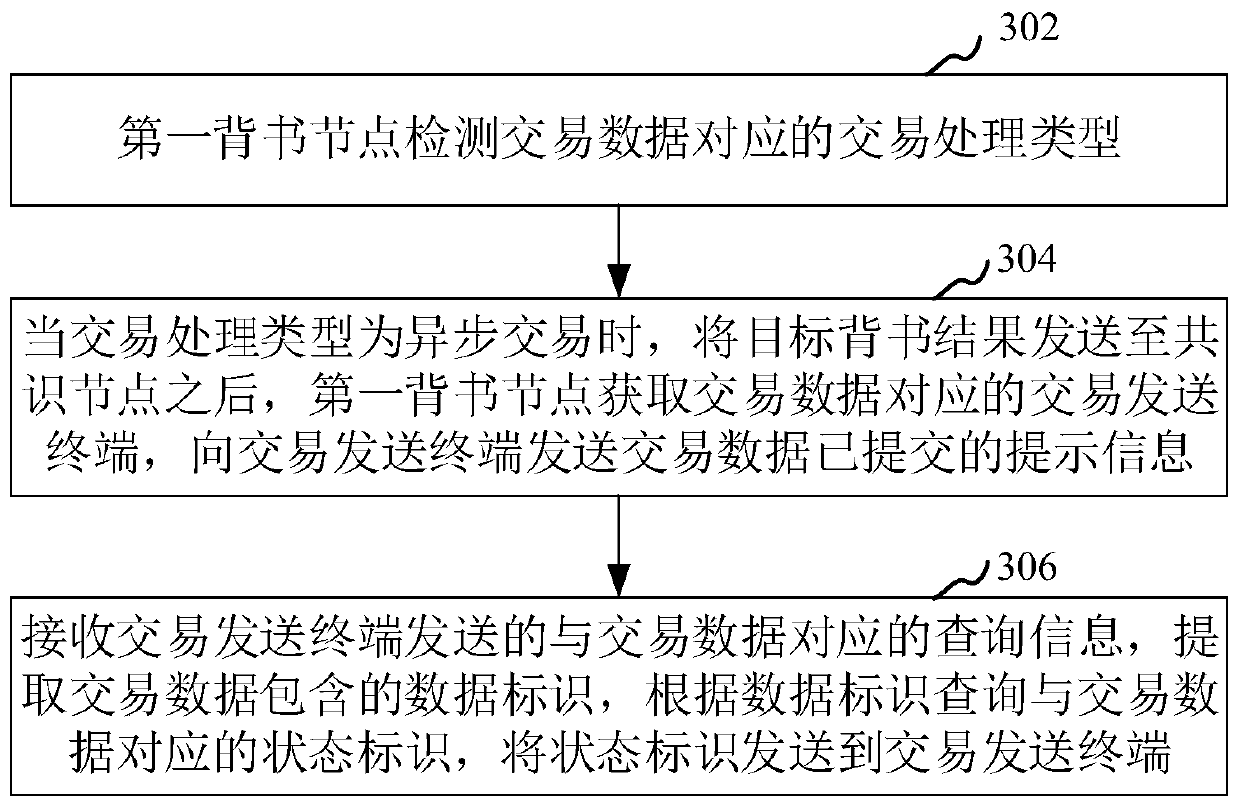
Block chain transaction data processing method and device, computer equipment and storage medium
PendingCN110555769AReduce callsSave resourcesFinanceDatabase distribution/replicationTransaction dataChain system
The invention relates to the technical field of block chains, in particular to a block chain transaction data processing method and device, computer equipment and a storage medium. The method comprises: enabling a first endorsement node in a block chain system to receive transaction data and perform a first endorsement operation to obtain a first endorsement result; obtaining a preset endorsementstrategy, obtaining a second endorsement node according to the endorsement strategy, and sending transaction data; enabling the first endorsement node to receive a second endorsement result obtained through the second endorsement node; obtaining a target endorsement result according to the first endorsement result and the second endorsement result; verifying the target endorsement result, and sending the target endorsement result to the consensus node when the verification is passed; and enabling the first endorsement node to receive a sorting and division result obtained by the consensus nodefor sorting and dividing the blocks according to the target endorsement result, and generating transaction blocks corresponding to the transaction data according to the result. By adopting the method, network calls can be reduced in the block chain transaction process, and resources are saved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
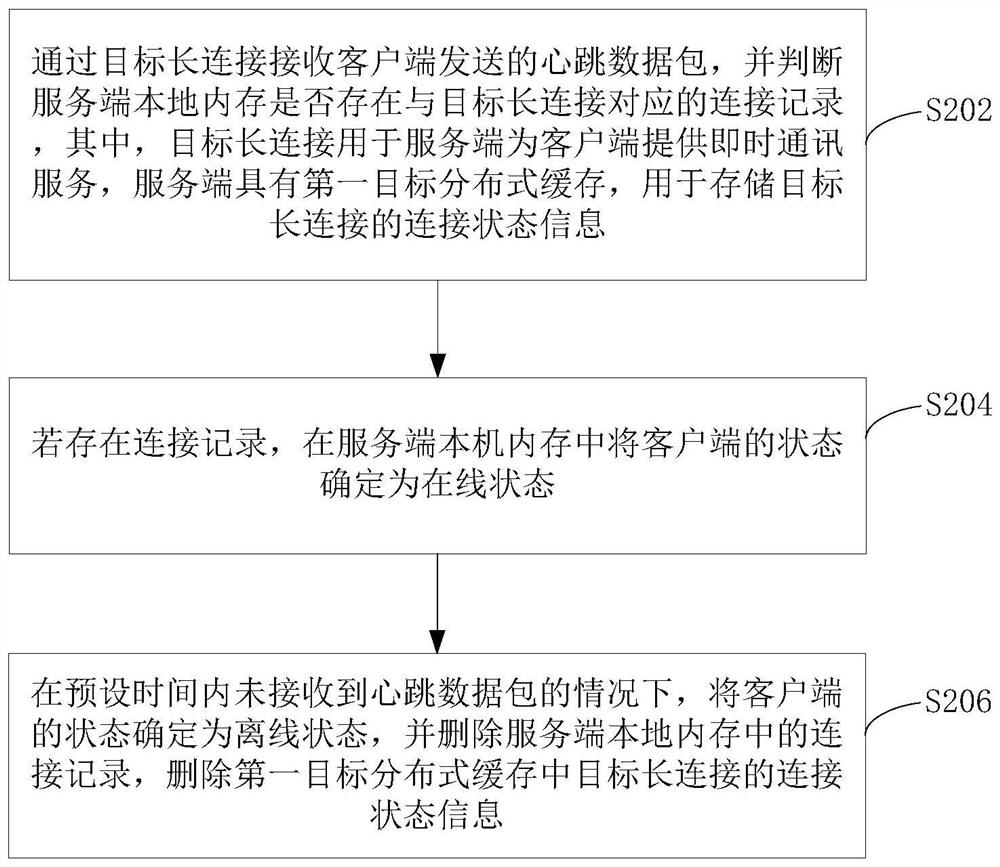
Instant messaging client state updating method and device
The invention relates to a client state updating method and device for instant messaging. The method comprises the steps: receiving a heartbeat data packet sent by a client through a target long connection, and judging whether a connection record corresponding to the target long connection exists in a local memory of a server or not, wherein the target long connection is used for providing instant messaging service for the client by the server, and the server is provided with a first target distributed cache, and is used for storing connection state information of target long connection; if the connection record exists, determining the state of the client as an online state in the local memory of the server; and under the condition that the heartbeat data packet is not received within the preset time, determining the state of the client as an offline state, deleting the connection record in the local memory of the server, and deleting the connection state information of the target long connection in the first target distributed cache. According to the invention, the technical problem of serious waste of server resources under high concurrency is solved.
Owner:BEIJING PERFECT WORLD SOFTWARE TECH DEV CO LTD
Server cluster and server cluster configuration information management method
ActiveCN109039730AEasy to manageReduce maintenance difficultyData switching networksOperating systemService process
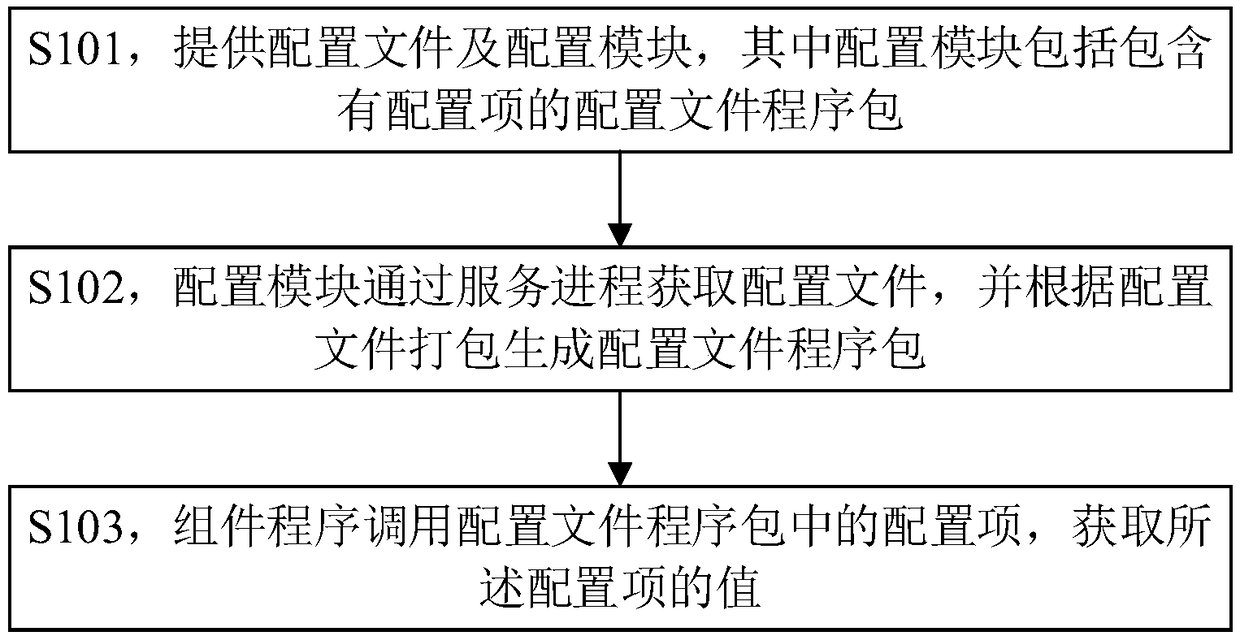
The embodiment of the invention provides a method for obtaining configuration information of a server cluster, comprising the following steps: a configuration file and a configuration module are provided, wherein the configuration module comprises a configuration file program package containing a configuration item; the configuration module obtains the configuration file through the service process; the configuration module generates a configuration file package according to the configuration file; the component program calls a configuration item in a configuration file package to obtain the value of the configuration item. The embodiment of the invention also provides a server cluster and a server. The invention can reduce the maintenance difficulty of the configuration file and improve the development efficiency.
Owner:CHINANETCENT TECH
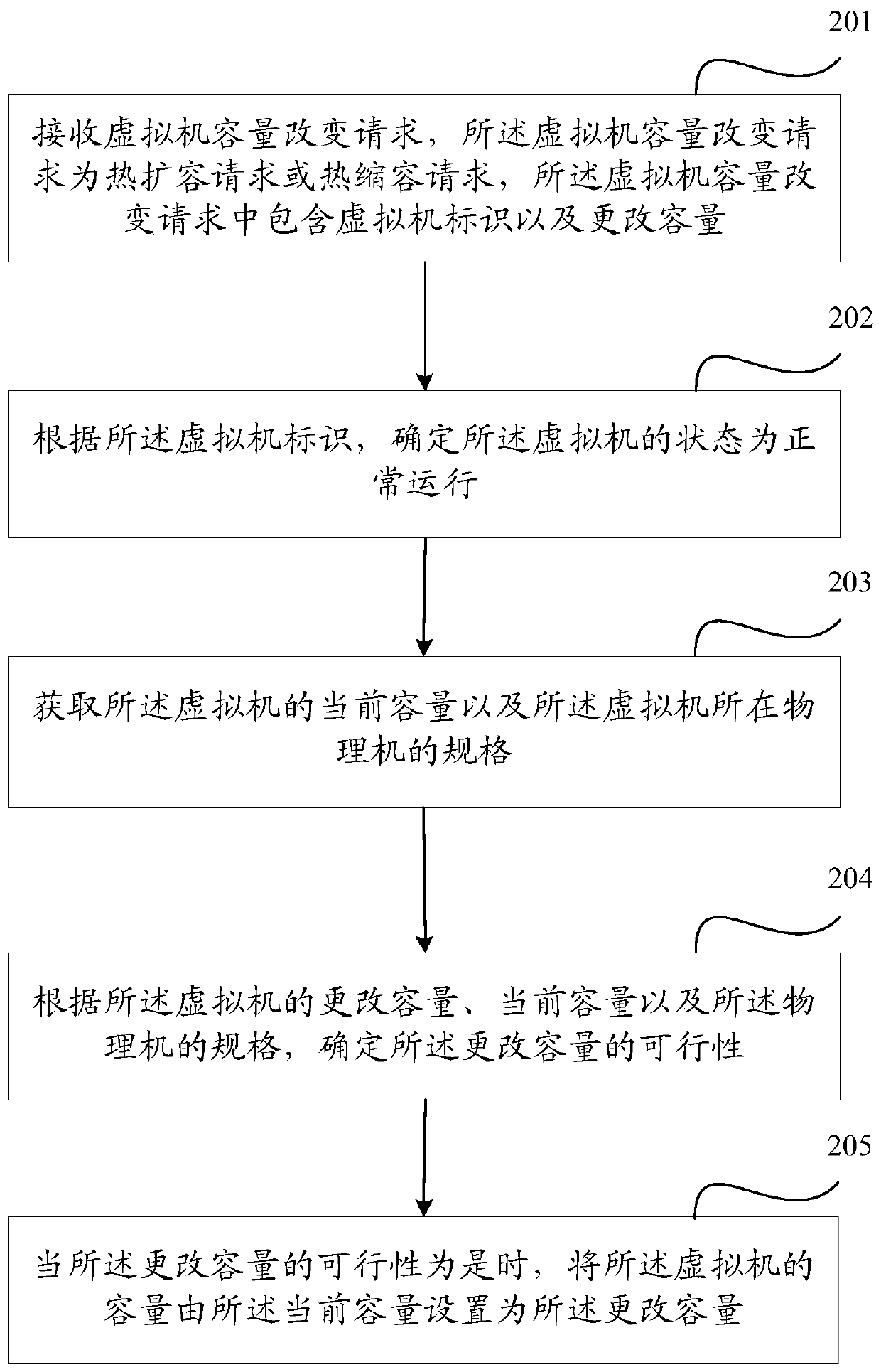
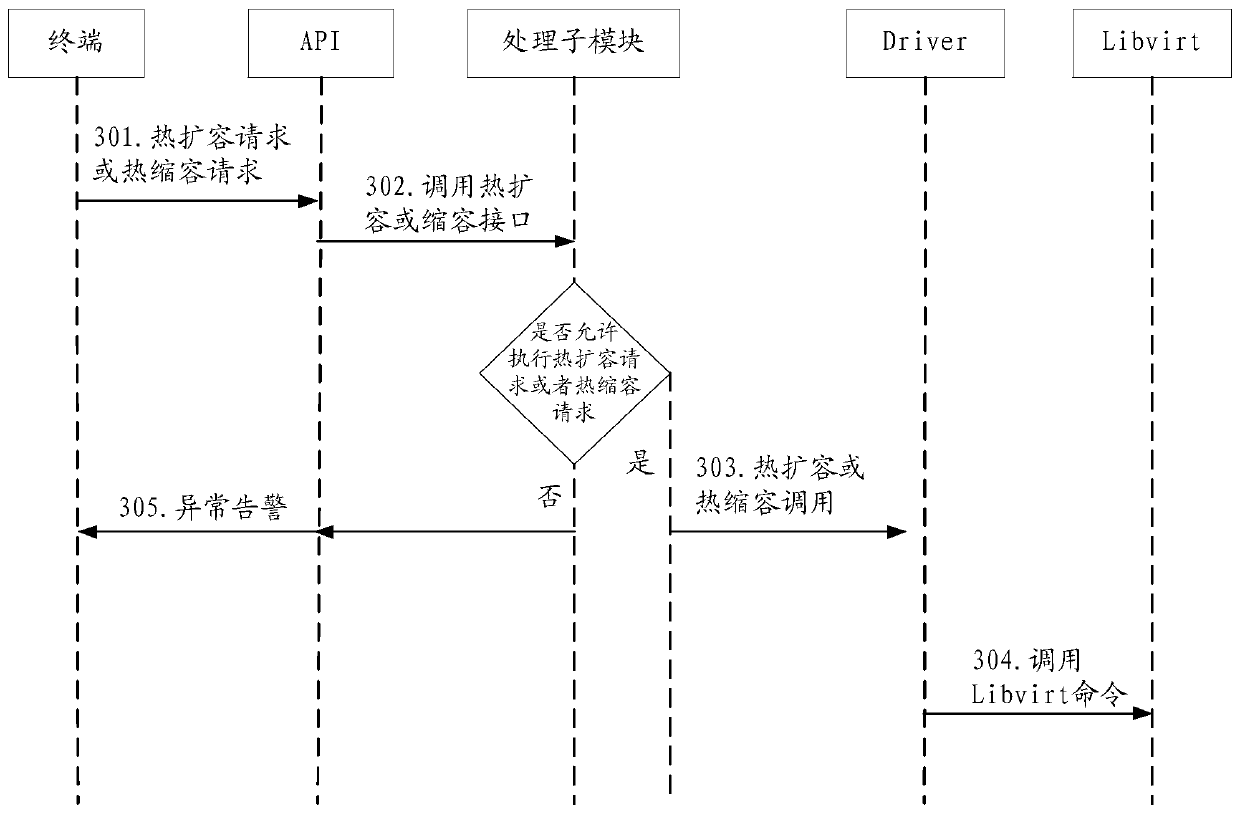
Capacity changing method and device for virtual machine
PendingCN111143031AIt will not affectGuaranteed continuitySoftware simulation/interpretation/emulationControl engineeringComputer science
The embodiment of the invention relates to the technical field of computers, in particular to a capacity changing method and device for a virtual machine, which are used for solving the problem that the service continuity cannot be ensured when the capacity of the virtual machine is changed. The method comprises the steps: receiving a virtual machine capacity change reques, whereinthe virtual machine capacity change request is a thermal expansion request or a thermal shrinkage request, and the virtual machine capacity change request comprises a virtual machine identifier and a change capacity;determining that the state of the virtual machine is normal operation according to the virtual machine identifier; obtaining the current capacity of the virtual machine and the specification of a physical machine where the virtual machine is located; according to the change capacity and the current capacity of the virtual machine and the specification of the physical machine, determining the feasibility of the change capacity; and when the feasibility of changing the capacity is yes, setting the capacity of the virtual machine from the current capacity to the changed capacity.
Owner:CHINA UNIONPAY
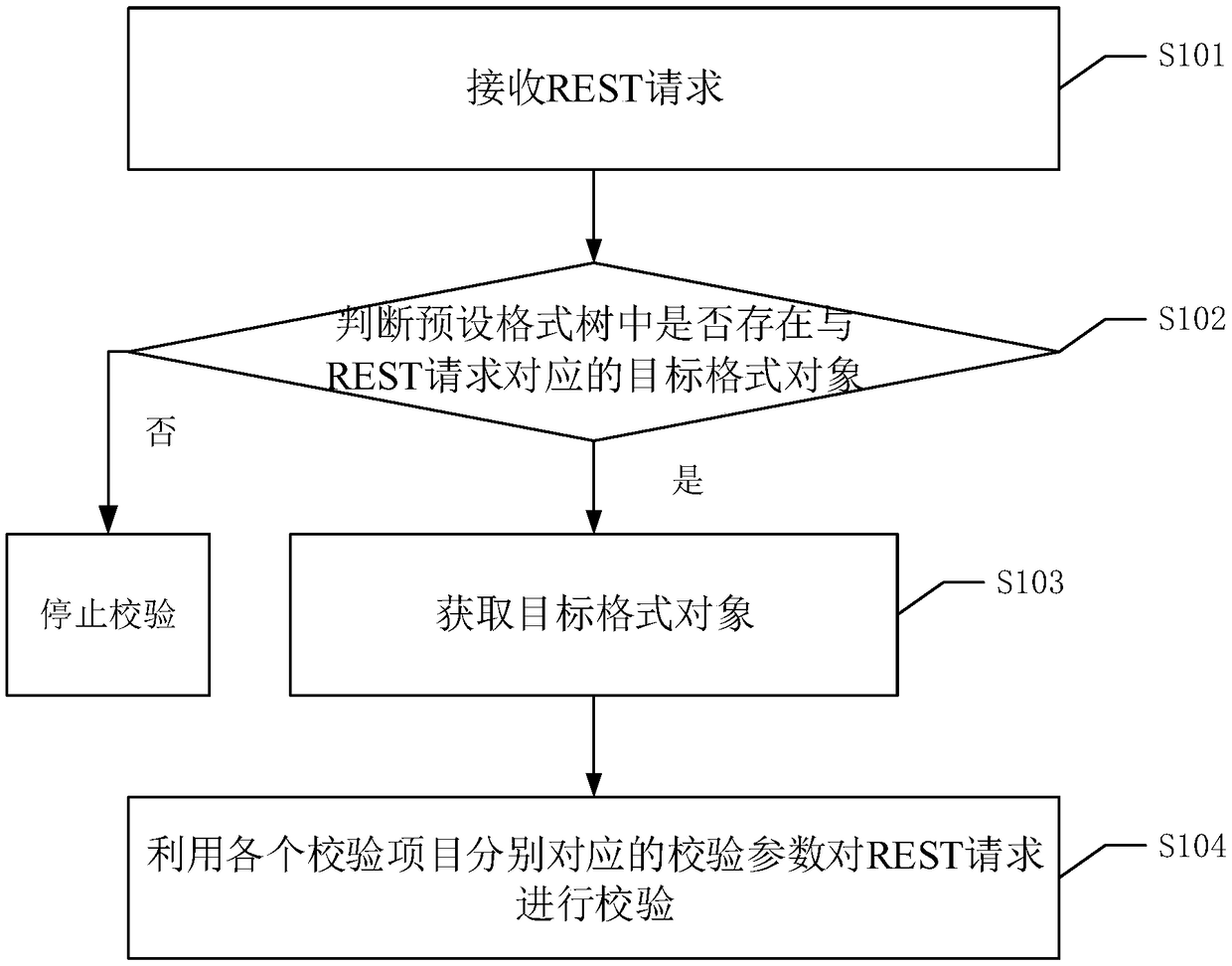
REST unified verification method, device, device and readable storage medium
ActiveCN109324958AReduce unified verificationRealize unified verificationSoftware testing/debuggingComputer engineeringComputer science
The invention discloses a REST unified verification method, which comprises the following steps: receiving a REST request; Judging whether there is a target format object corresponding to the REST request in the preset format tree; In the preset format tree, the nodes corresponding to each REST interface correspond to a format object, and the format object includes verification parameters corresponding to each verification item. If so, the target format object is obtained; The REST request is checked by using the checkout parameters corresponding to each checkout item of the target format object. When receiving a REST request, the parameter verification of various REST requests can be smoothly completed, that is, the RSET unified verification is realized, the development process is simplified, the calling of functions or methods is reduced, and the accuracy of REST verification results can be effectively improved. The invention also discloses a REST unified verification device, a device and a readable storage medium, which have corresponding technical effects.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
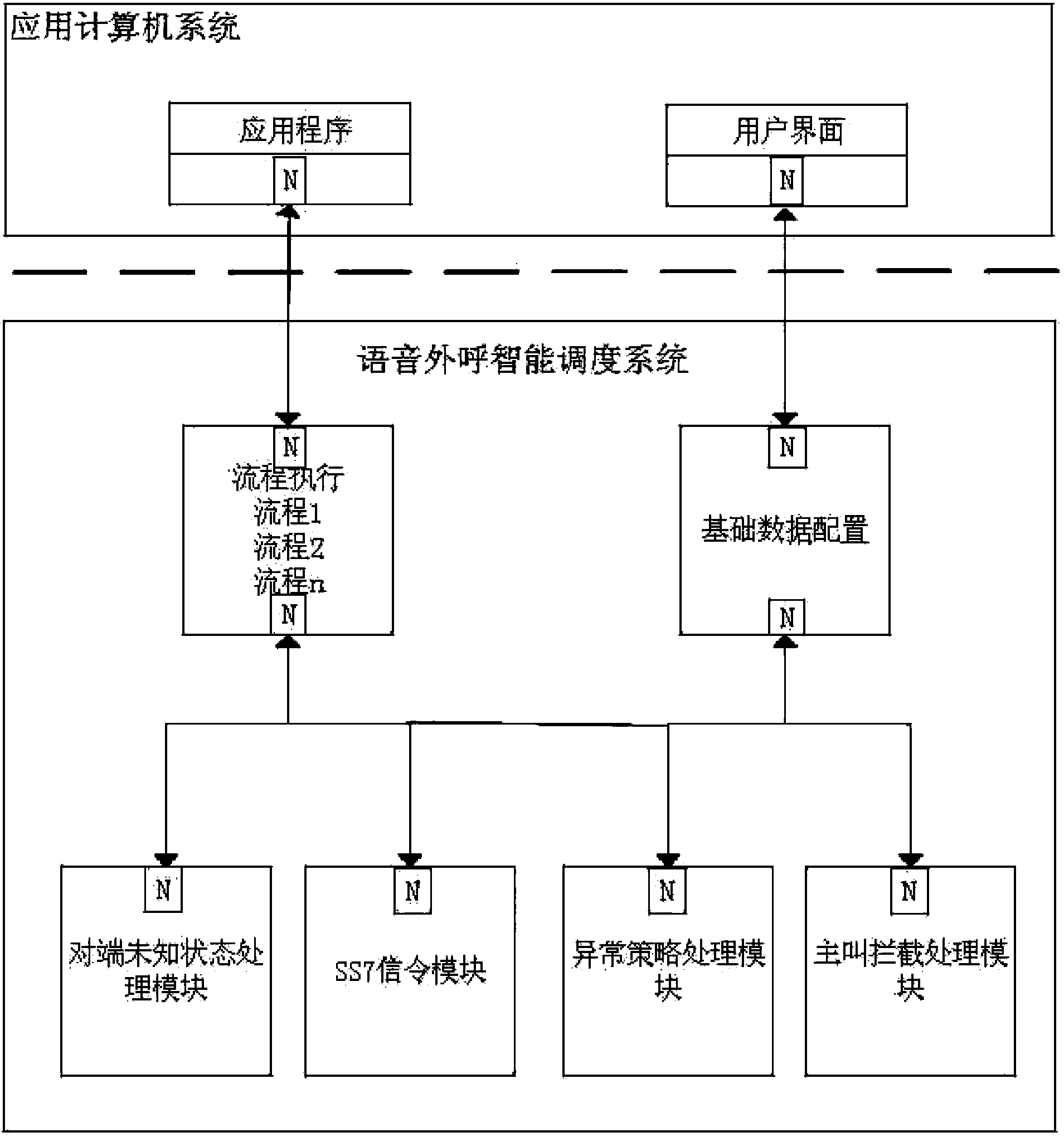
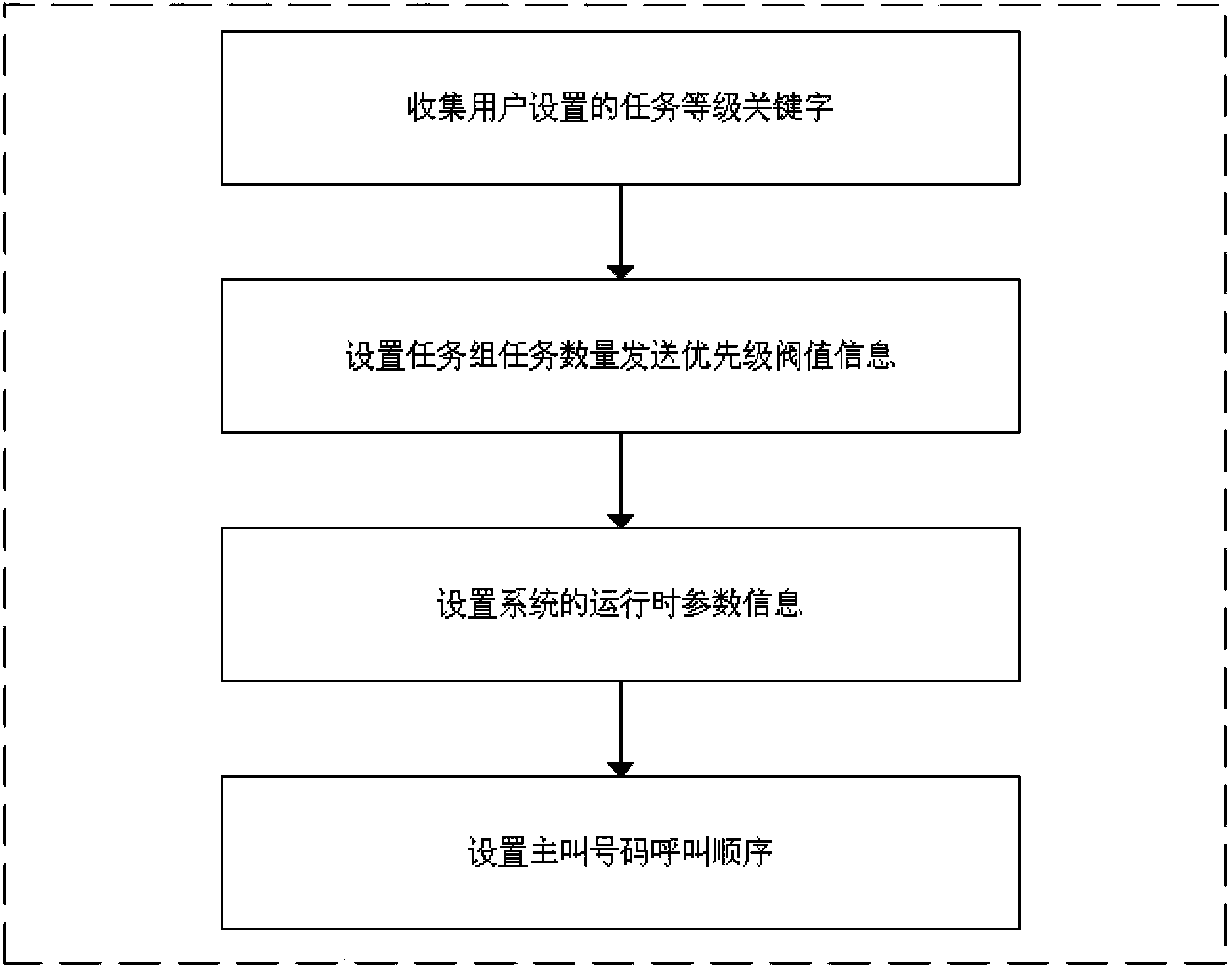
Intelligent dispatching system and dispatching method for mass individual voice calls
ActiveCN103546651ARealize intelligent scheduling and sendingReduce execution prioritySpecial service for subscribersInteraction layerUser input
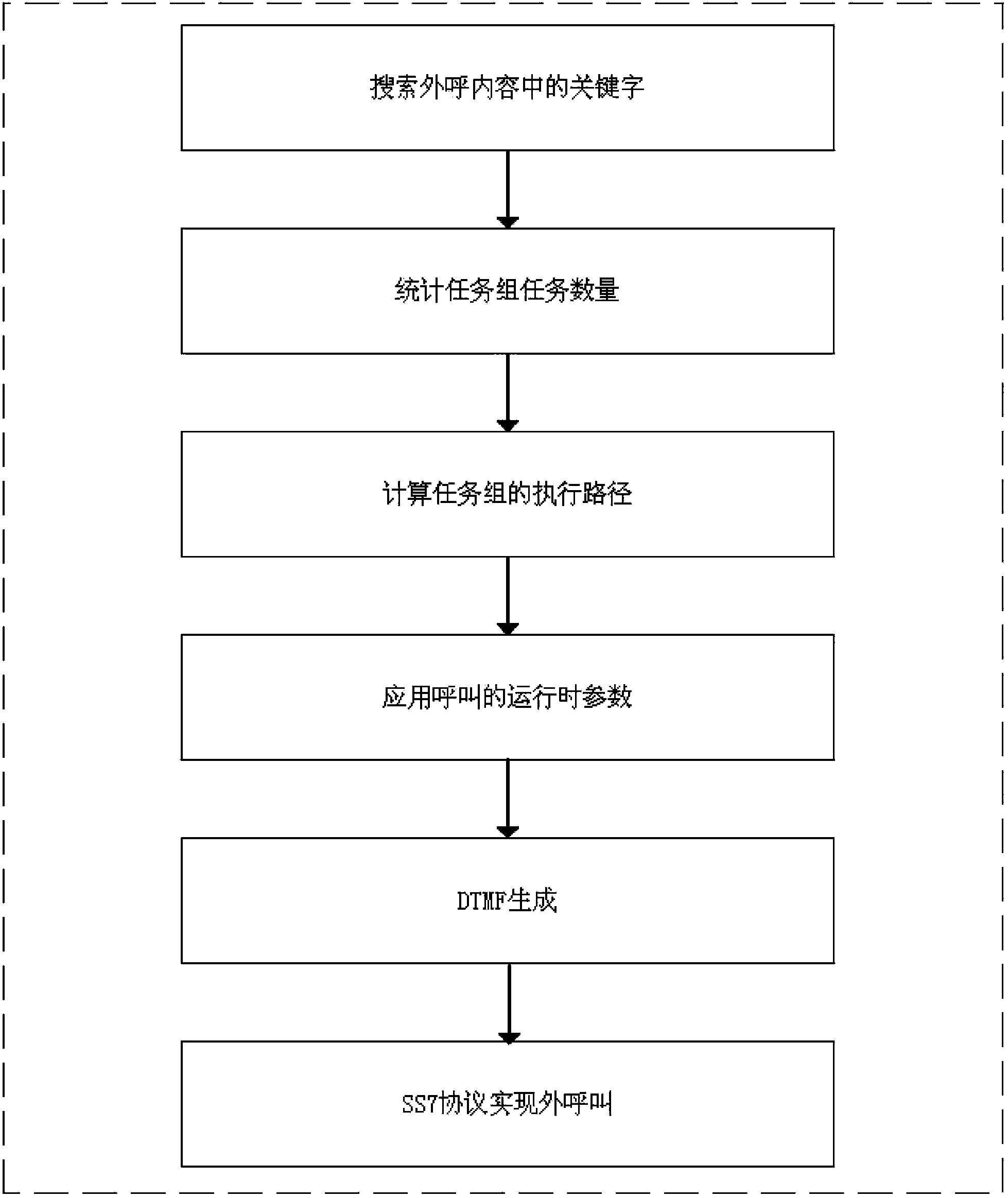
The invention relates to an intelligent dispatching system and a dispatching method for mass individual voice calls. The system comprises a user interaction layer, a service fulfillment layer and a base protocol layer, wherein the user interaction layer is used for collecting user data and configuring base data, the service fulfillment layer is used for selecting execution paths and applying an exception handling strategy and a failure retry mechanism, and the base protocol layer is used for implementing SS7 signaling, generating and analyzing DTMF (dual-tone multi-frequency) signaling, analyzing and operating terminal state return codes, adjusting parameter paths in running and making and adjusting the exception handling strategy. State values collected in the production process can be combined with characteristic threshold values inputted by a user, so that numbers with excellent states can be found and executed in priority in a large data volume task environment, execution priority and the number of calls of the numbers with low states can be decreased, and large data volume tasks are intelligently dispatched.
Owner:V COM FUJIAN INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com