Novel virtual machine software protection method based on stack hiding
A software protection and virtual machine technology, applied in program/content distribution protection, software simulation/interpretation/simulation, instruments, etc., can solve problems such as plaintext instruction sequences in memory, and achieve the effect of improving operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be further described in detail and in-depth below in conjunction with the accompanying drawings.
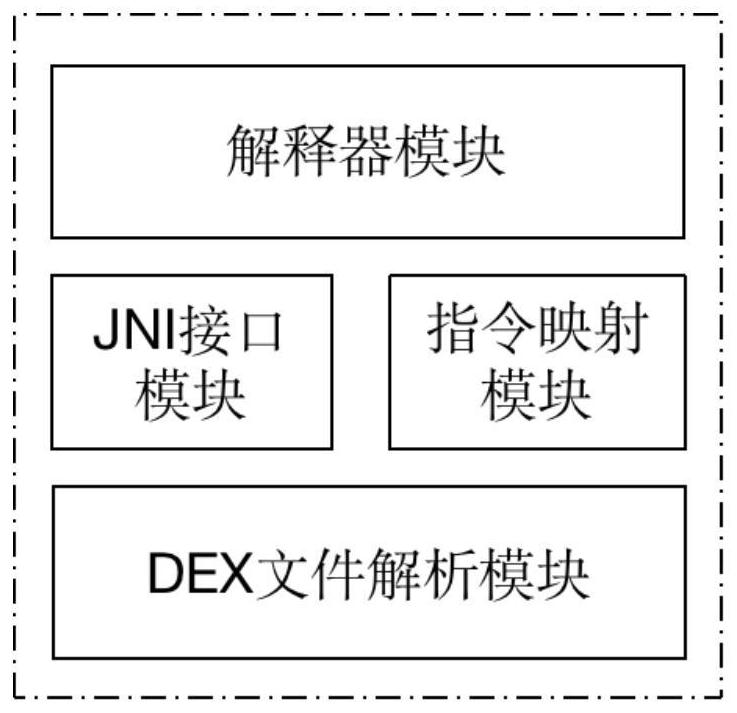
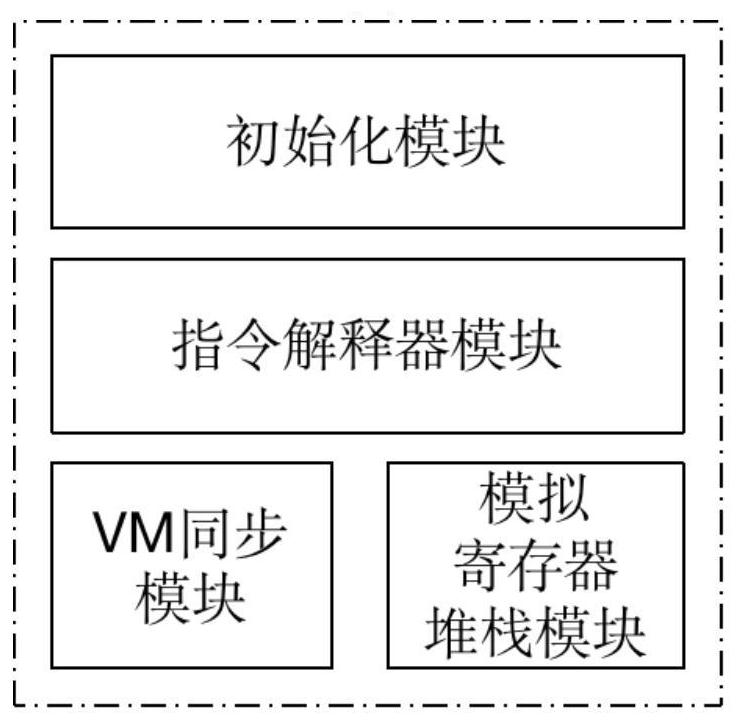
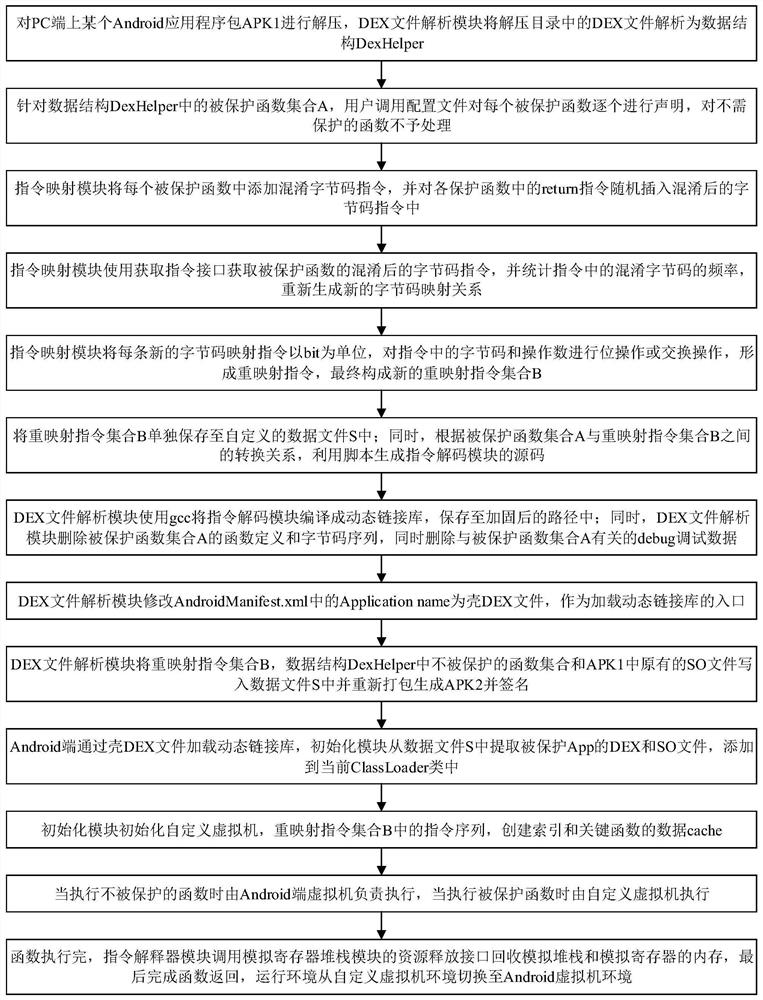
[0045]The present invention is a software protection method based on a virtual machine, which is realized in two parts: one part is the PC end, which is mainly responsible for software reinforcement processing, that is, the original App is reinforced and processed into a safe App; the second part is the Android end, which is mainly responsible for The processing of the runtime environment is to ensure that the safe App runs normally on the Android platform.
[0046] After processing the original App, the PC end generates a data file in a custom format and packs it into the APK installation package. This file contains the instruction sequence of the protected method, and the Android end needs to obtain the protected method from this file whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com