A Cryptographic Calculation Method Based on Nonlinear Theory
A calculation method and nonlinear technology, applied in the field of cryptography, can solve the problems of chaotic orbit collapse and low efficiency, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be described in further detail below by means of specific embodiments:
[0046] 2.2 Main technical solutions
[0047] In our inventive design, there are two chaotic systems in the form:
[0048]
[0049]
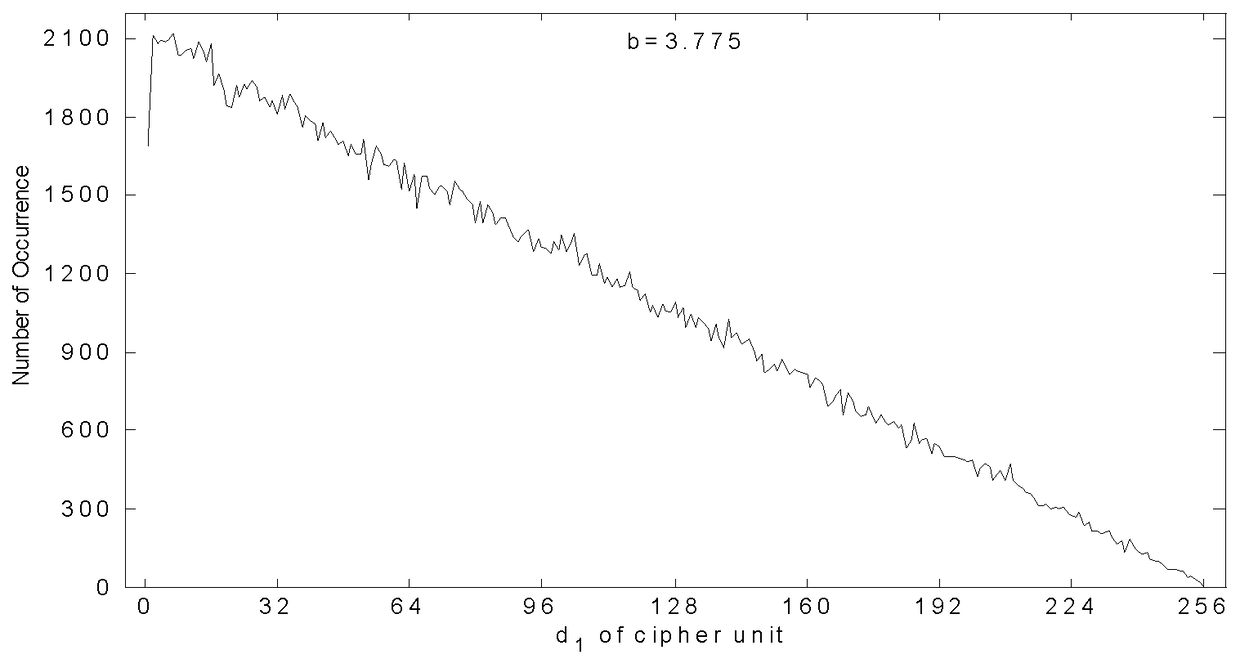
[0050] Both chaotic systems are piecewise linear maps (PLCMs). This choice is due to the fact that PLCMs have better chaotic dynamics behavior than other chaotic systems such as Logistic maps. The difference between them is that they have different control parameters b 1 and b 2 , these two parameters are also added with F 1 the initial state x 0 , that is, the triplet (b 1 ,b 2 ,x 0 ) constitutes the key Key of the cryptosystem, when (b 1 ,b 2 ,x 0 When the three values of ) all belong to the interval (0,1), the iteration of the equation (1, 2) has the characteristics of chaotic dynamics.
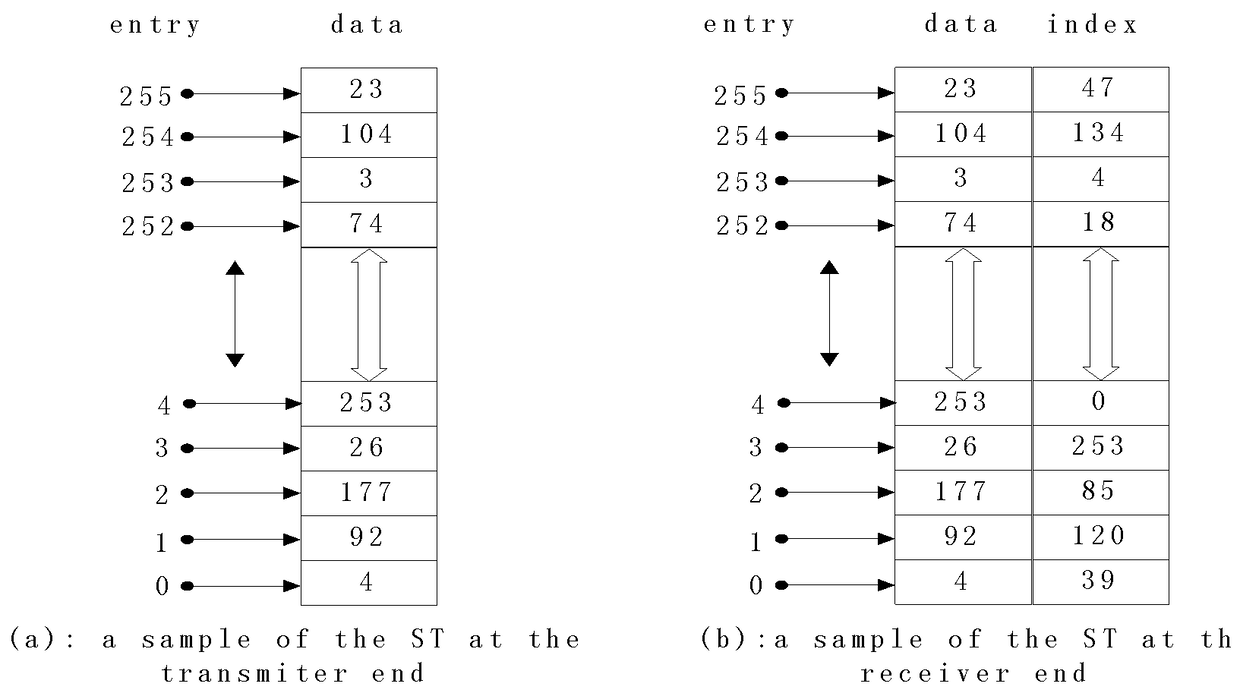
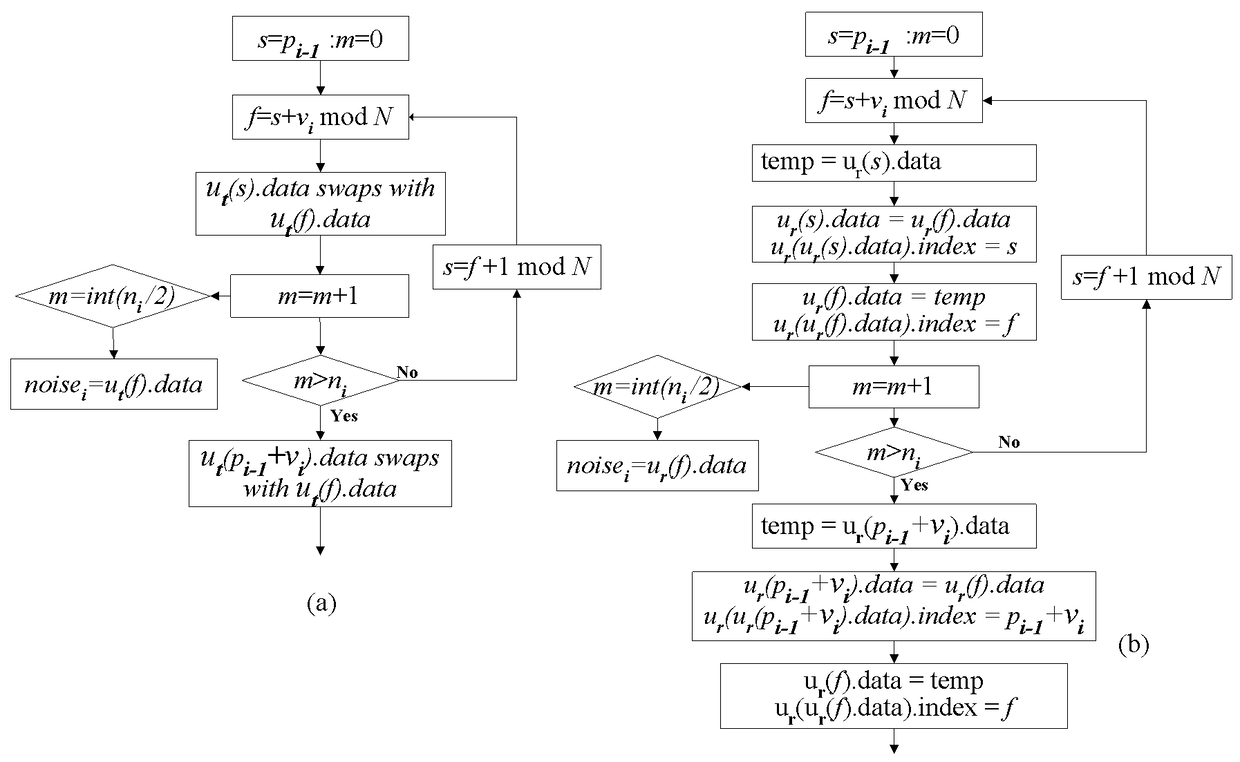
[0051] The plaintext information P consists of a series of m-bit plaintext blocks, so there are N=2 m different plaintext block value...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com