Method for obtaining system call white list required by container
A whitelist and container technology, applied in the direction of instruments, multi-program devices, program control design, etc., can solve problems such as multiple disks and memory space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
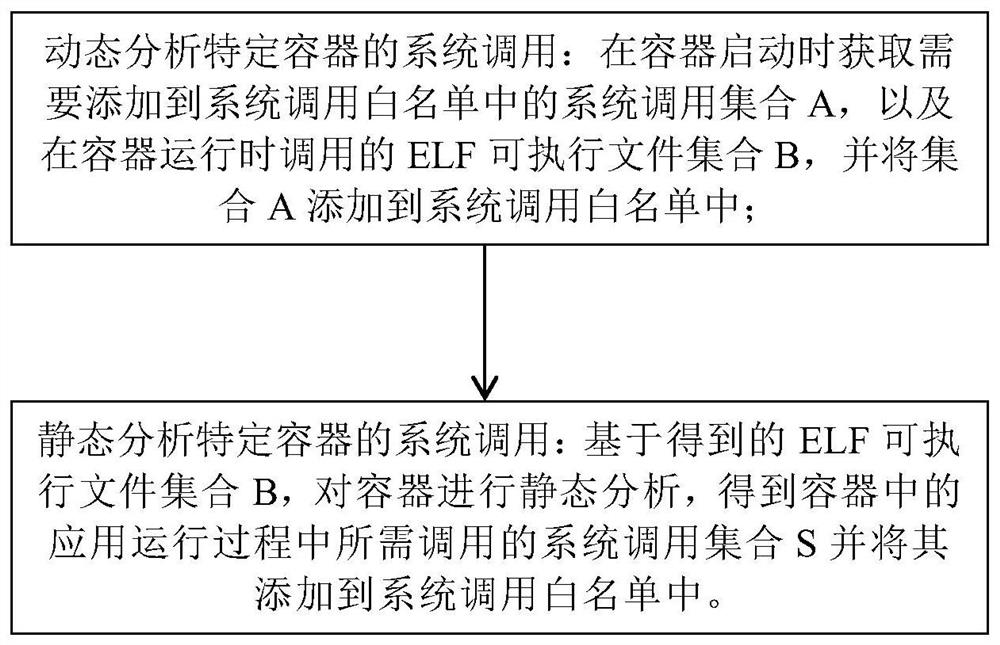
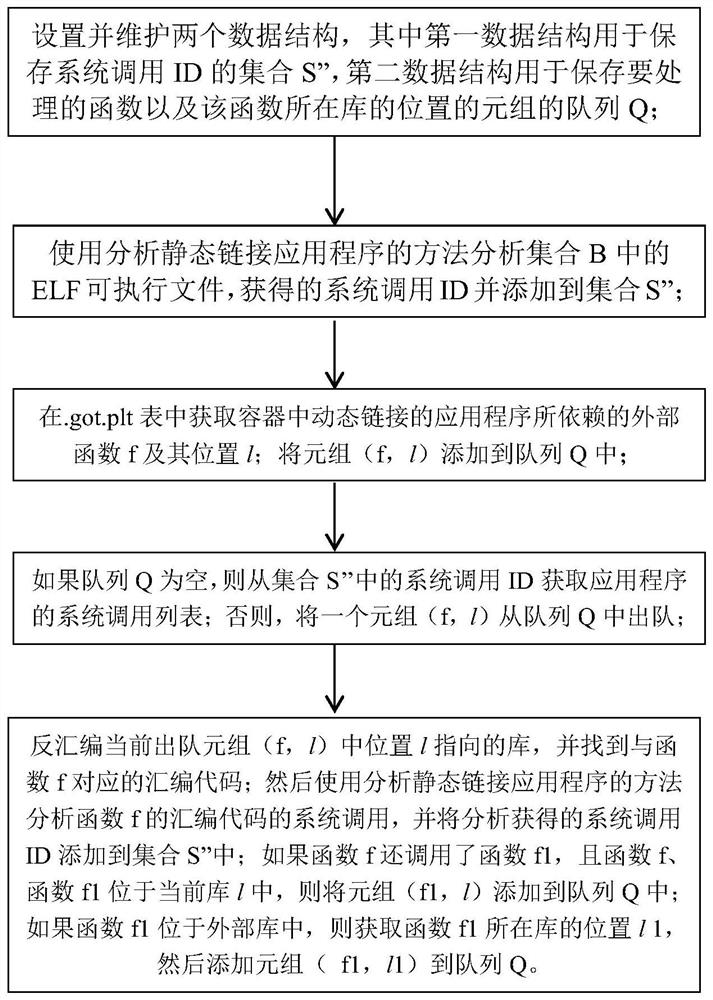
[0078] A user downloaded a container from Docker Hub, but it is not clear whether the application running in the container is credible and safe, so the user wants to limit the system calls that can be called by the container as much as possible without affecting the normal function of the container. Then the user can use the present invention to obtain the system calls needed by the container, and then add these system calls to the container's seccomp configuration file whitelist, and use the configuration file as the container's system call whitelist when the container is actually started.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com