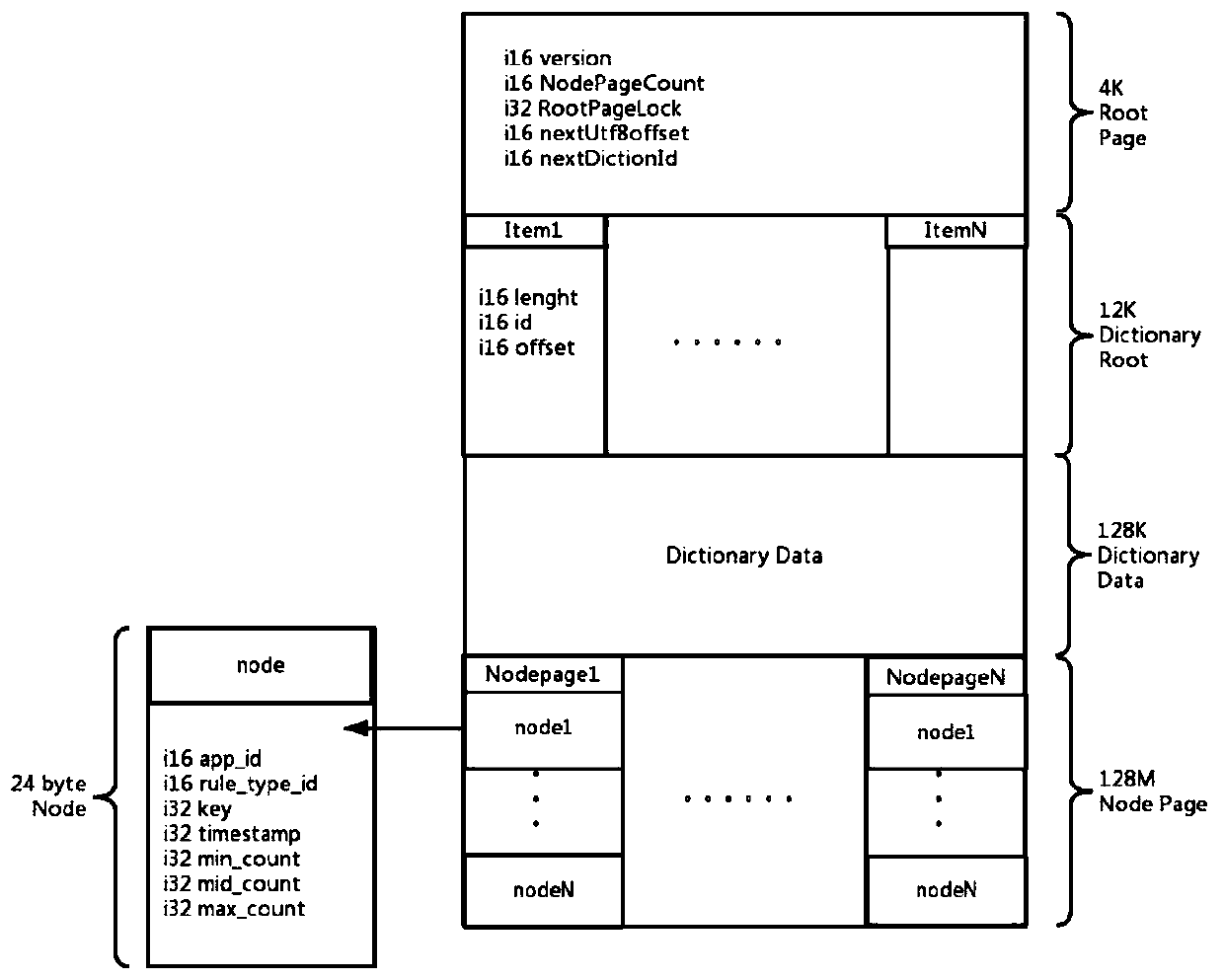
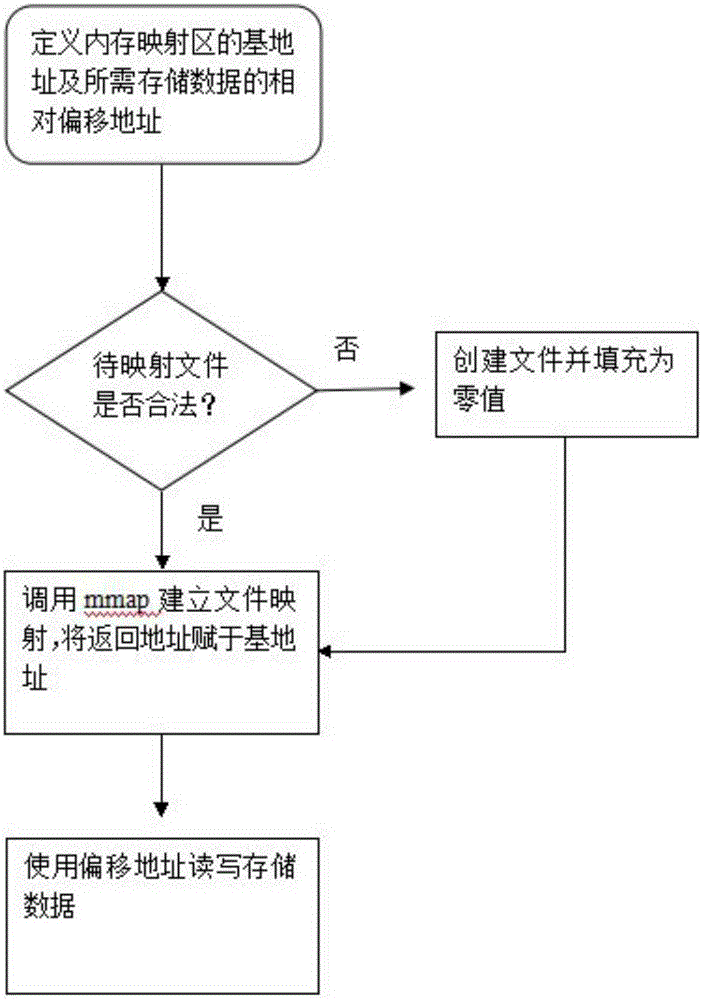
Patents
Literature
42 results about "Mmap" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
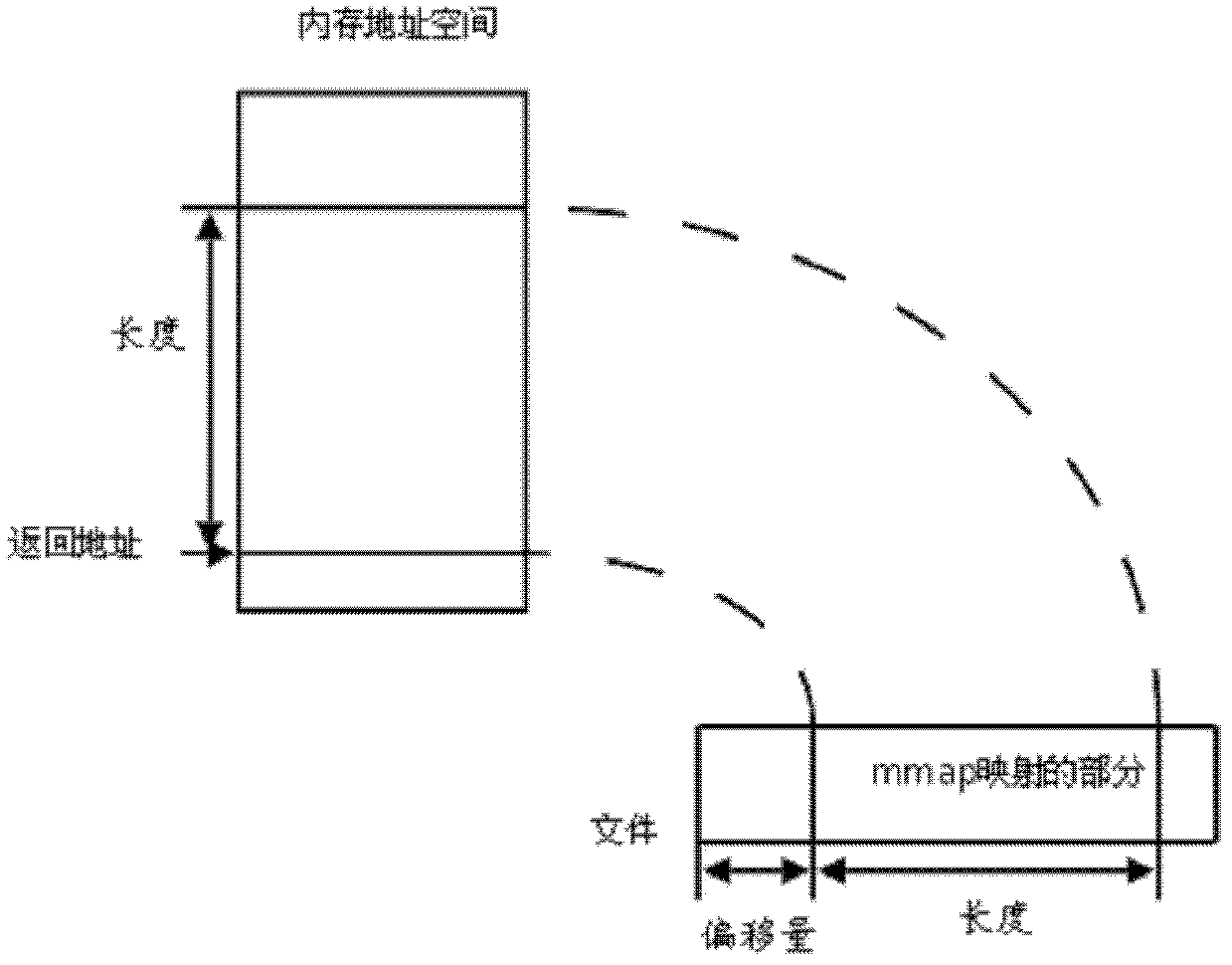
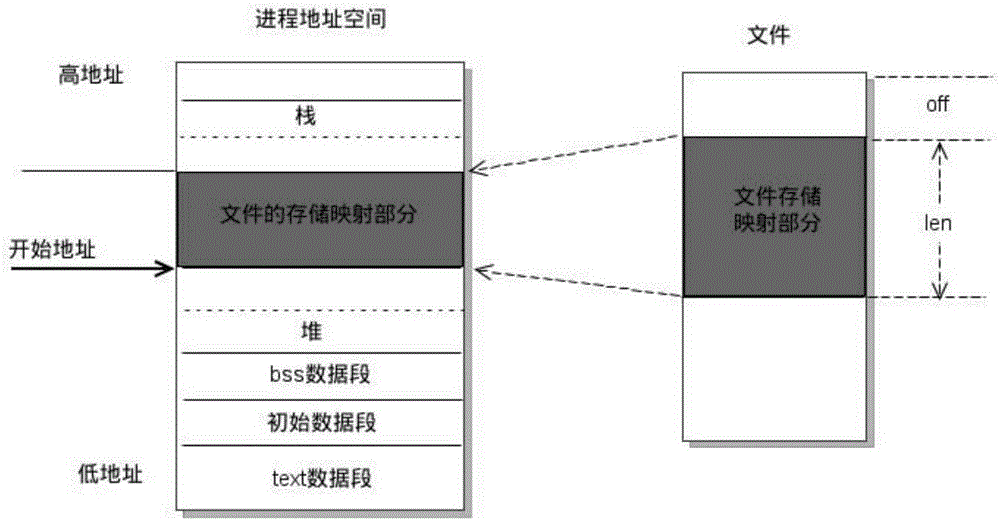
In computing, mmap(2) is a POSIX-compliant Unix system call that maps files or devices into memory. It is a method of memory-mapped file I/O. It implements demand paging, because file contents are not read from disk directly and initially do not use physical RAM at all. The actual reads from disk are performed in a "lazy" manner, after a specific location is accessed. After the memory is no longer needed, it is important to munmap(2) the pointers to it. Protection information can be managed using mprotect(2), and special treatment can be enforced using madvise(2).
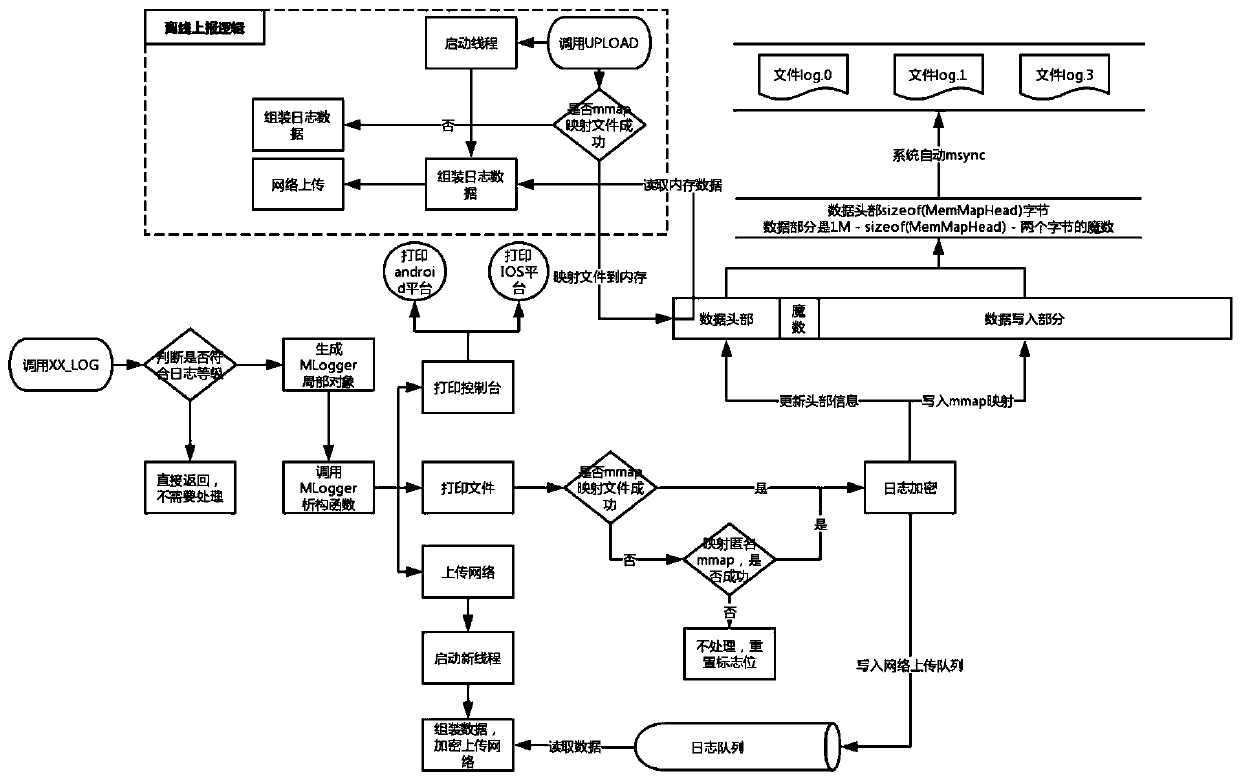
Method and device for processing client log
ActiveCN103309767AEnsure safetyData lostMemory loss protectionRedundant operation error correctionMmapInternal memory
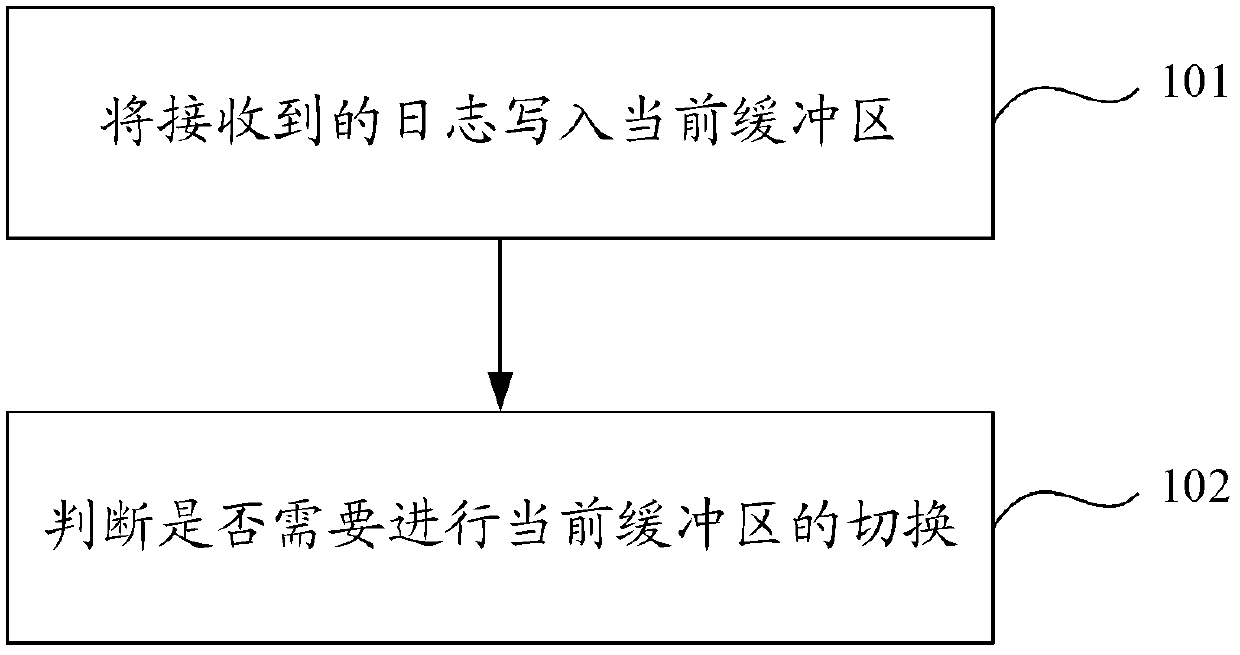
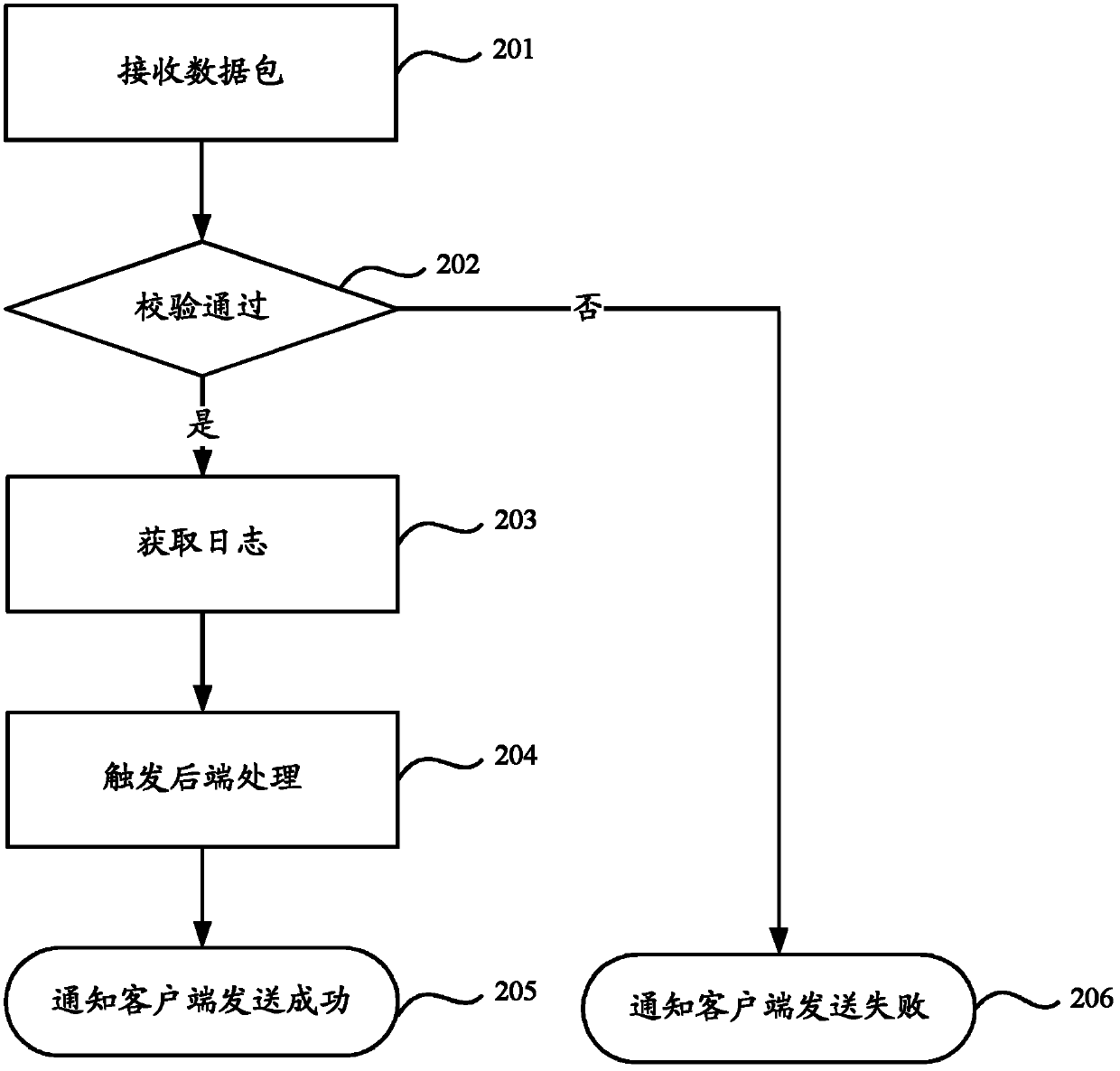
The embodiment of the invention provides a method and a device for processing a client log. The method comprises the following steps of adopting a double buffering mechanism, previously setting two MMAP (map files or devices into memory) internal memories to be respectively used as a current buffering area and a standby buffering area, switching the standby buffering area to be the current buffering area when the current buffering area is filled, and transmitting a log stored in the filled buffering area to a distributed file system to be stored, so that the problem that the log processing capacity is limited because the quantity of the processed logs is limited by the limit space of the existing disk can be solved. Due to the characteristics of the MMAP technology, in the operation process, the data in the buffering area can be forcedly outputted to the disk by the system, so that even if a server is restarted or collapsed, the data stored in the buffering area can be restored through the disk without being lost, and the safety of the log stored in the buffering area can be guaranteed.
Owner:TAOBAO CHINA SOFTWARE
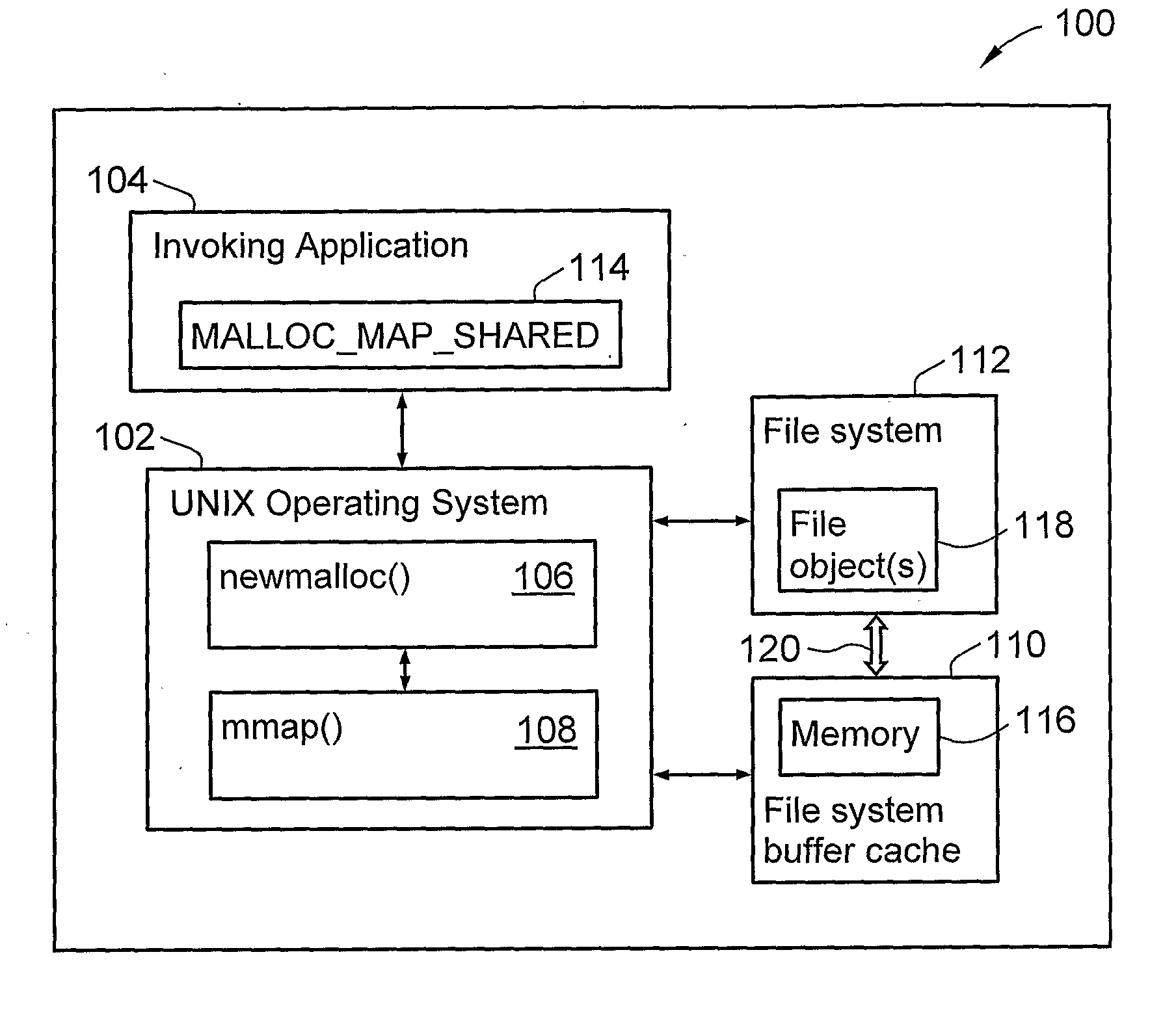
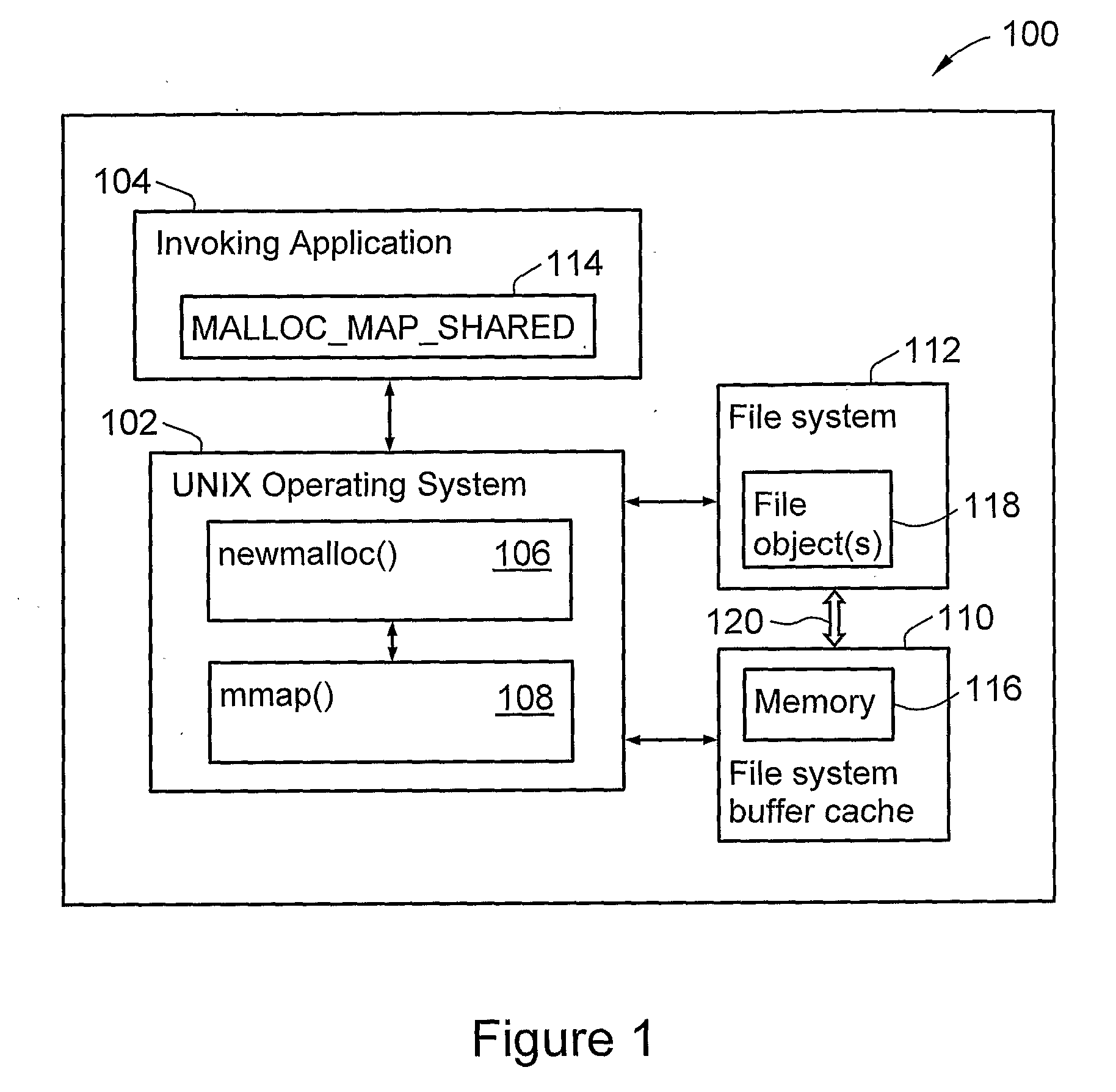
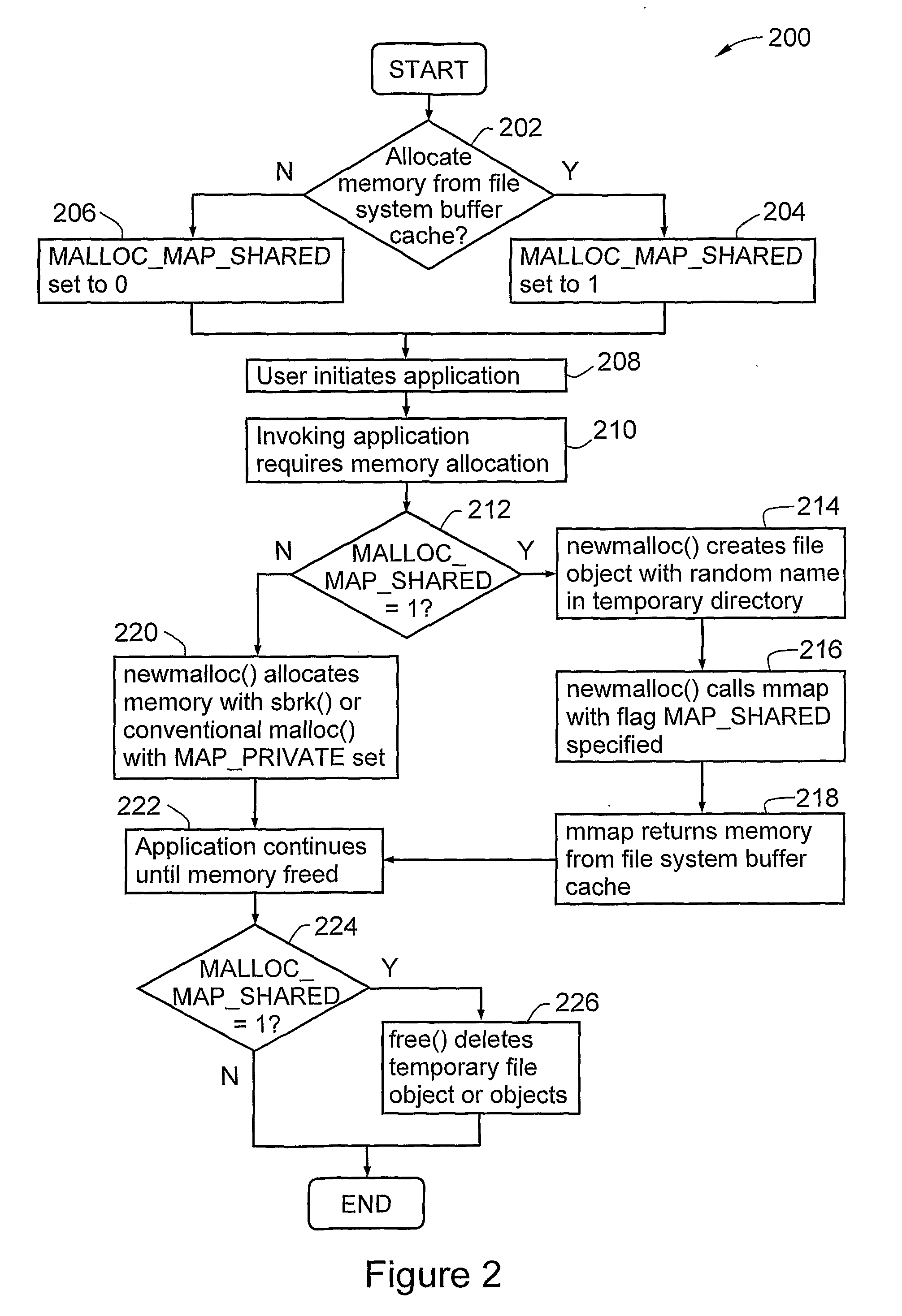
Method and System for Allocating Memory in a Computing Environment
A method and product for allocating memory in a computing environment, the method comprising providing a memory allocation routine adapted to use mmap( ) with a MAP SHARED or equivalent flag specified so that the memory is allocated from a file system buffer cache. In one embodiment, the method comprises allocating the memory by using mmap( ) with a MAP_SHARED or equivalent flag specified so that the memory is allocated from a file system buffer cache.
Owner:HEWLETT PACKARD DEV CO LP
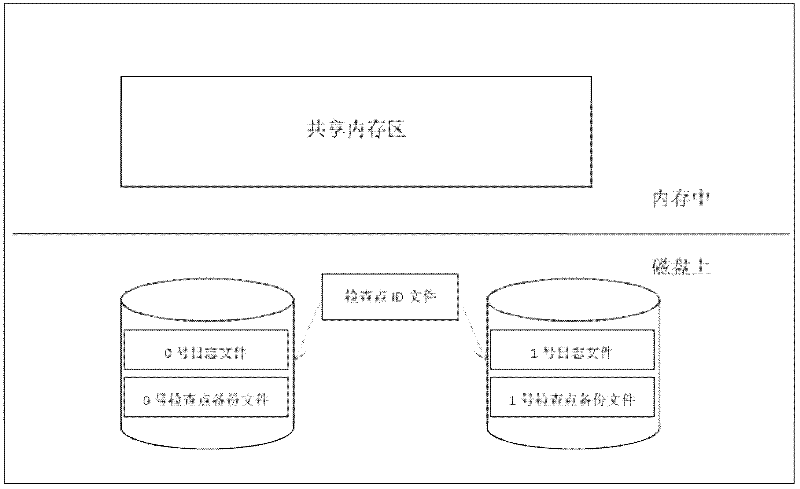
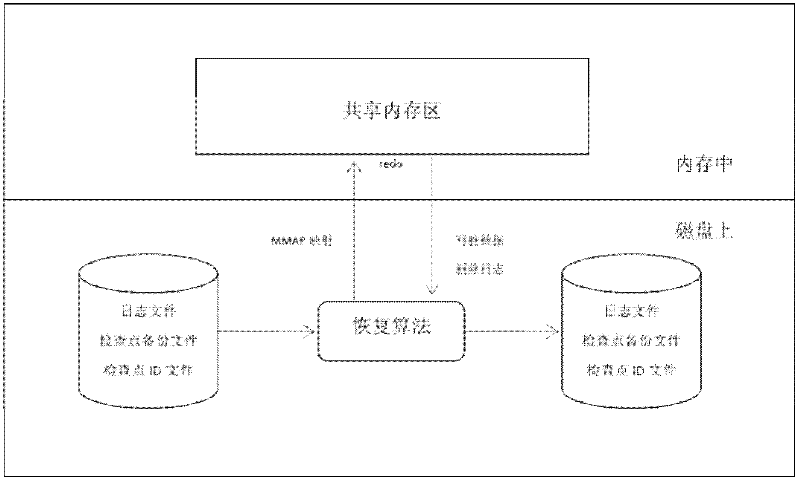
Log check point recovery method applied to memory data base OLTP (online transaction processing)
ActiveCN102541691AHigh speedReduce the burden onRedundant operation error correctionSpecial data processing applicationsRecovery methodMmap
The invention discloses a log check point recovery method applied to memory data base OLTP (online transaction processing), which uses the log check point technique based on double-log double-check-point backup. Two backup files can be used in turn, and a data base can recover to a latest uniform state no matter in a transaction process, a check point executive process or breakdown in a recovery process. Meanwhile, an MMAP (memory-mapped analog page) sharing mechanism is used for quickly setting up the mapping from a check point standby file to a memory, and rapid recovery of massive data bases is realized.
Owner:北京人大金仓信息技术股份有限公司
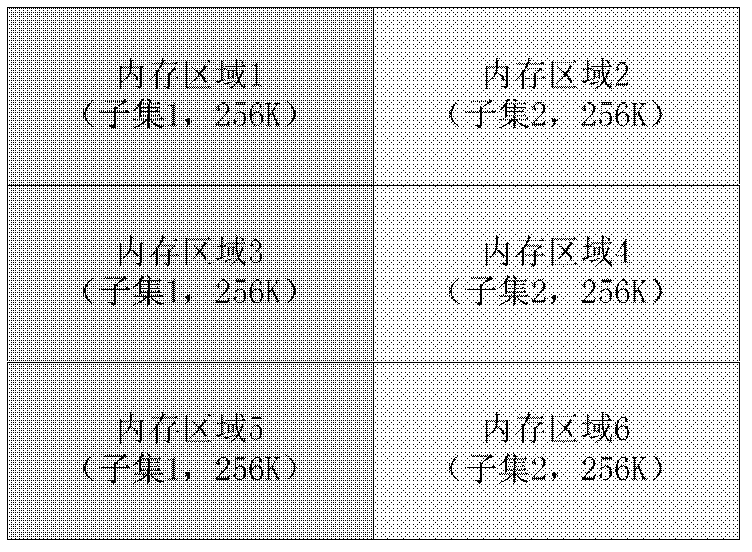
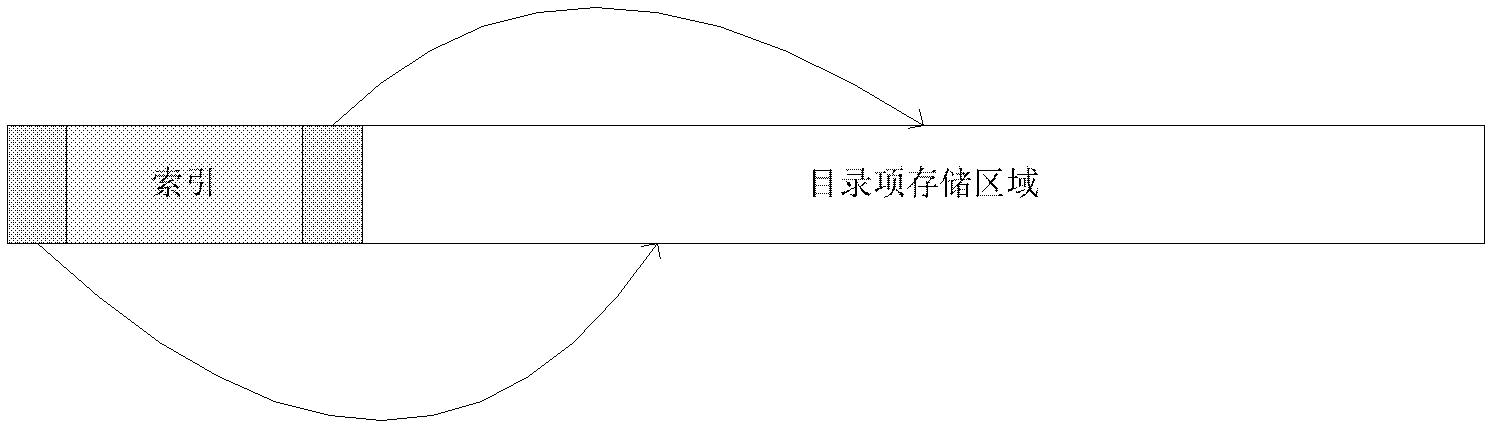
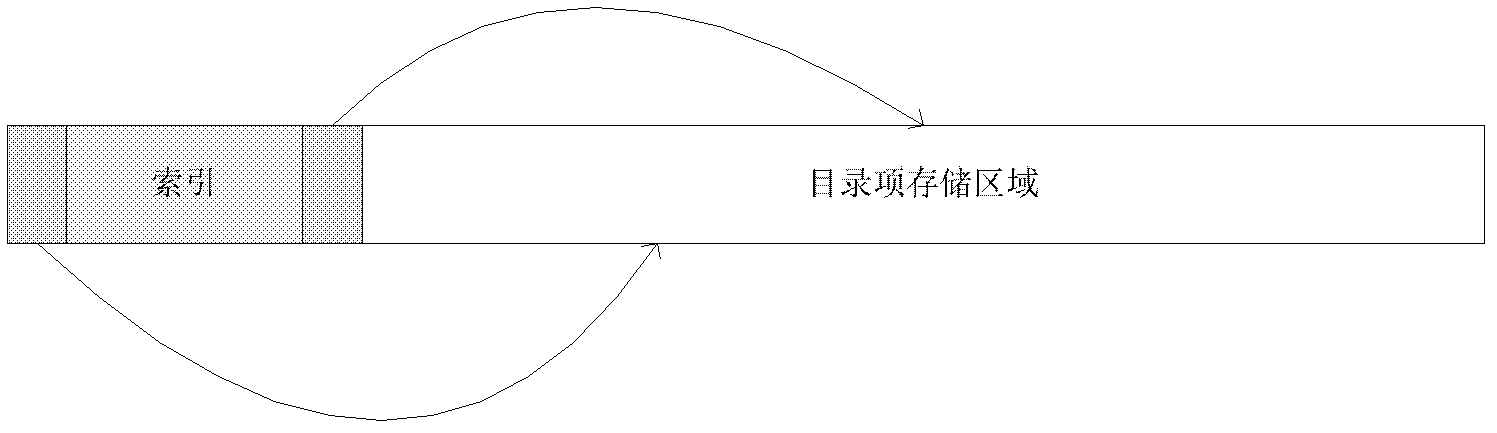
Catalogue access method in DFS (distributed file system)
ActiveCN102385623ATake advantage of read-ahead featuresAvoid the build processSpecial data processing applicationsMmapAccess method
In the invention, the content of catalogues is stored by documents, and as for the catalogue items in the catalogues, the catalogue items are divided into a plurality of subsets by hashing the titles of the catalogue items. Different subsets are stored in the catalogue documents in a striped manner, and the strip is relatively larger, so that the pre-reading function of a bottom file system can be fully utilized when a disc is read. The catalogue items in the strips of each subset are stored in a binary tree manner, so that the binary tree can be prevented from being set when initial reading is conducted. All the strips are accessed in a memory map (mmap) mode, so that expenditure caused by memory allocation and invocation of a read-write system of a system document when the disc data is accessed each time can be avoided.
Owner:DAWNING INFORMATION IND BEIJING +1
Method for capturing real-time network data
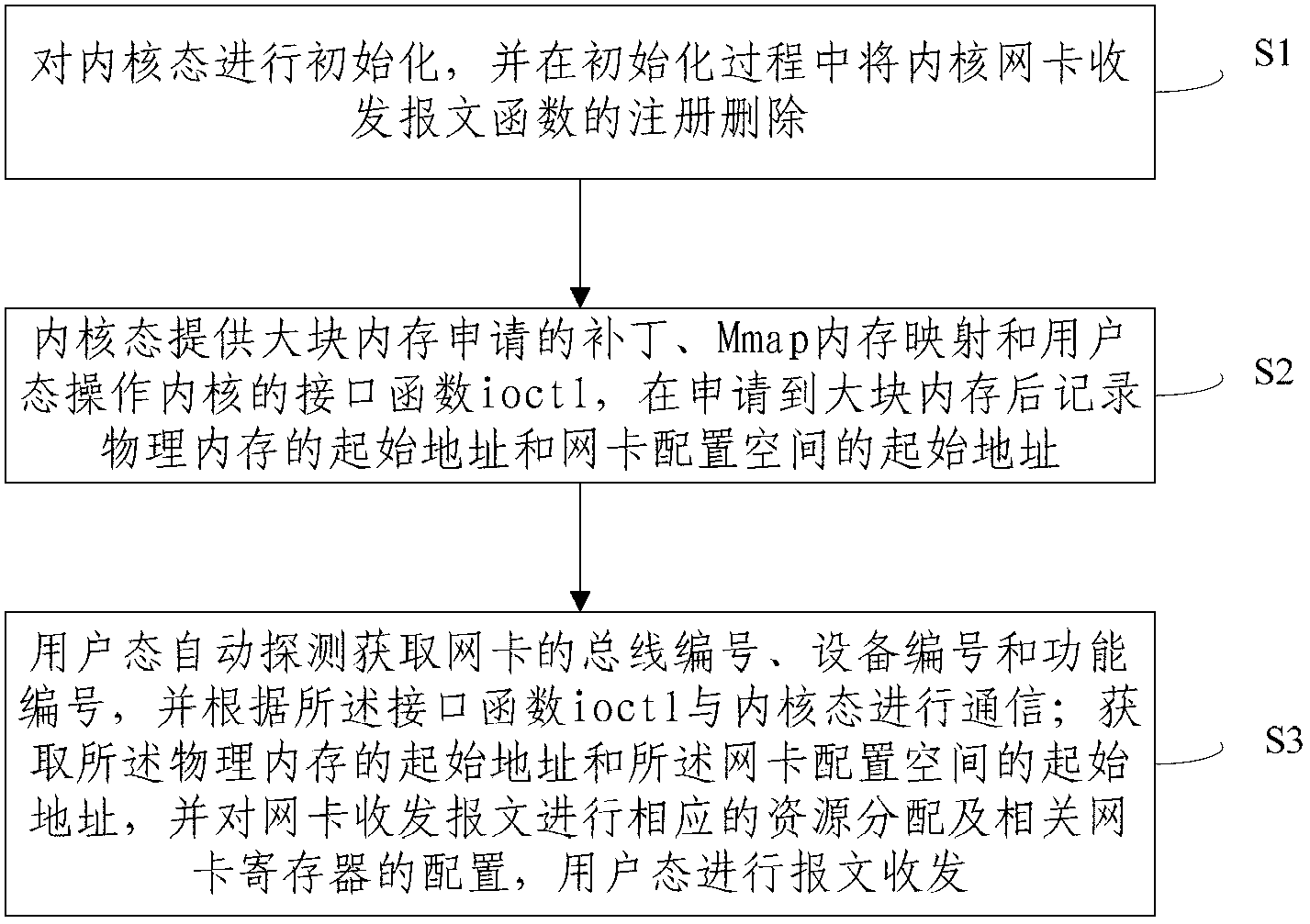
InactiveCN103269284AReduce performance lossSatisfy perceived needsData switching networksMmapProcessor register
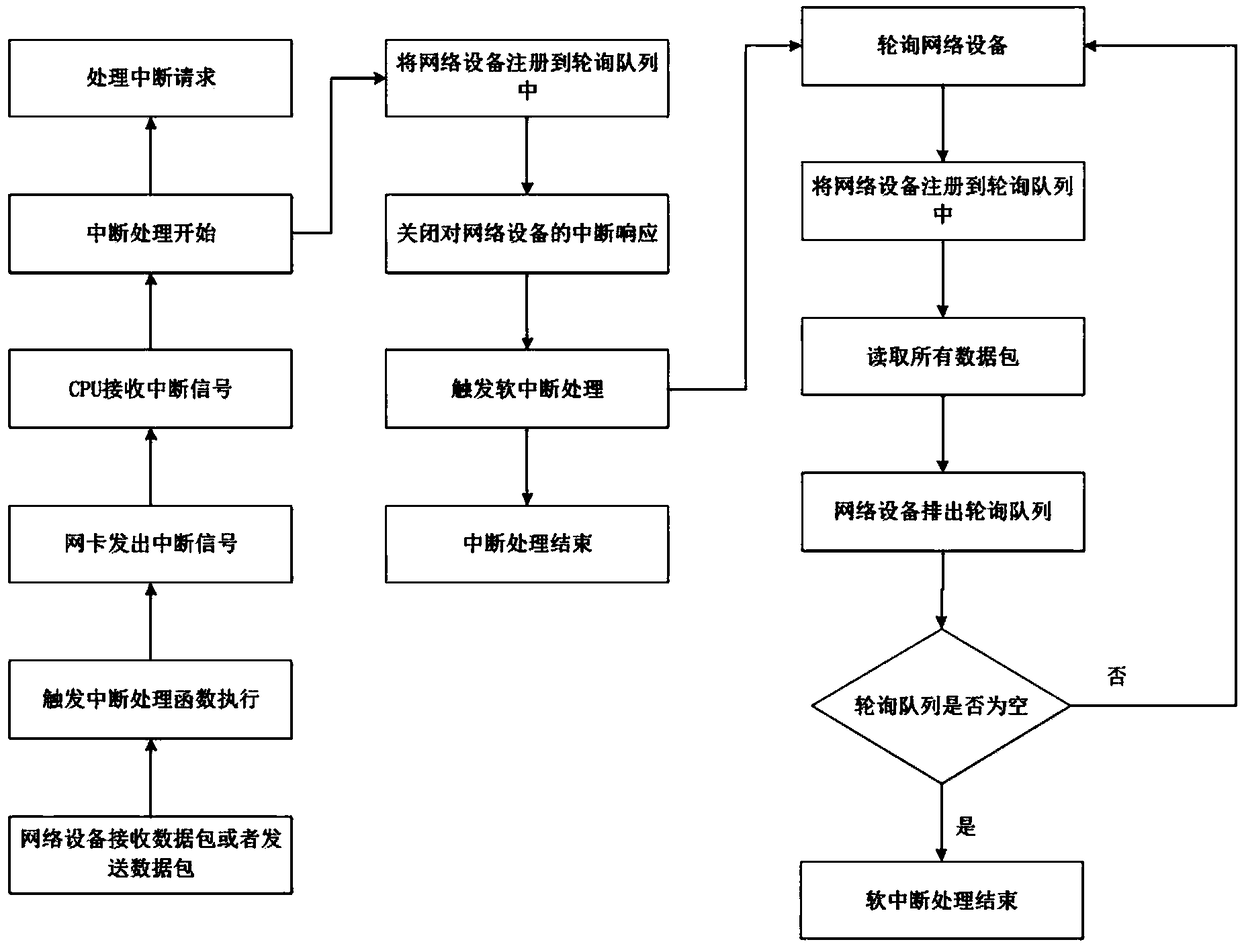
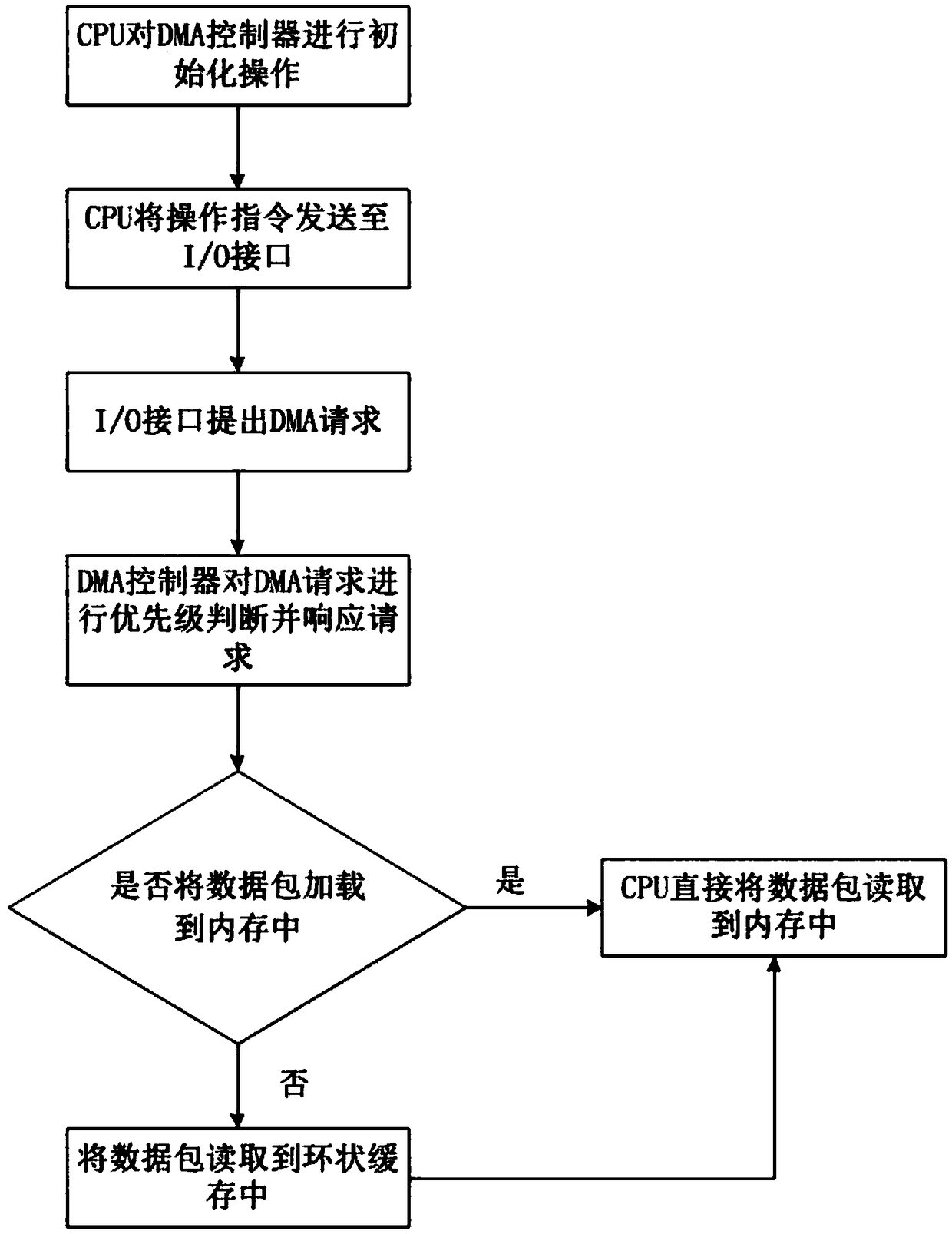
The invention provides a method for capturing real-time network data. The method comprises the following steps: S1, a kernel mode is initialized, and register information for receiving and sending message functions by a kernel network card is deleted in the process of initializing; S2, the kernel mode provides a large patch applied by internal storage, an Mmap memory map and an interface function ioctl of a user mode operation kernel, and the starting address of physical memory and the starting address of a network card configuration space are recorded; S3, a user mode automatically detects and acquires the bus number of the network card, the number of equipment and a function number, and is in communication with the kernel mode according to the interference function ioctl; corresponding resource allocation and corresponding network card register configuration are conducted on network card receiving and sending messages, and the user mode receives and sends the messages. According to the method for capturing the real-time network data, loading and driving in the kernel mode and message receiving and sending in the user mode of the network card are achieved, and network card driving interrupt in the kernel mode and performance damage caused by data copy are removed.
Owner:OPZOON TECH
High performance data message capture method and device based on Linux
InactiveCN103441941AReduce the number of copiesReduce occupancyData switching networksMmapTraffic capacity
The invention relates to the technical field of networks, in particular to a high performance data message capture method and device based on Linux. The method comprises the steps that a data message capture program is notified to process a trigger signal in an interruption mode according to the trigger signal; the trigger signal is shielded if network flow is large, and a network card is initiatively polled on whether a data message is received; if the data message is received, the data message of the network card is synchronized to kernel memory; if the network flow is small, correspondence to the trigger signal is performed, and the data message of the network card is synchronized to the kernel memory; a data message storage address in the kernel memory is obtained, and the storage starting address of the data message is mapped to user virtual address space through the memory mapping function mmap. Kernel interrupt processing is reduced through a semi-polling method, a path for transmitting the data message of the network card is changed, copy frequency of the data message is reduced through the memory mapping function mmap, high performance network sniffing is conducted under the gigabit and 10 gigabit environment, packet loss rate is reduced, and CPU occupation rate is reduced.
Owner:GUANGDONG EFLYCLOUD COMPUTING CO LTD
High-speed message processing method, apparatus and system
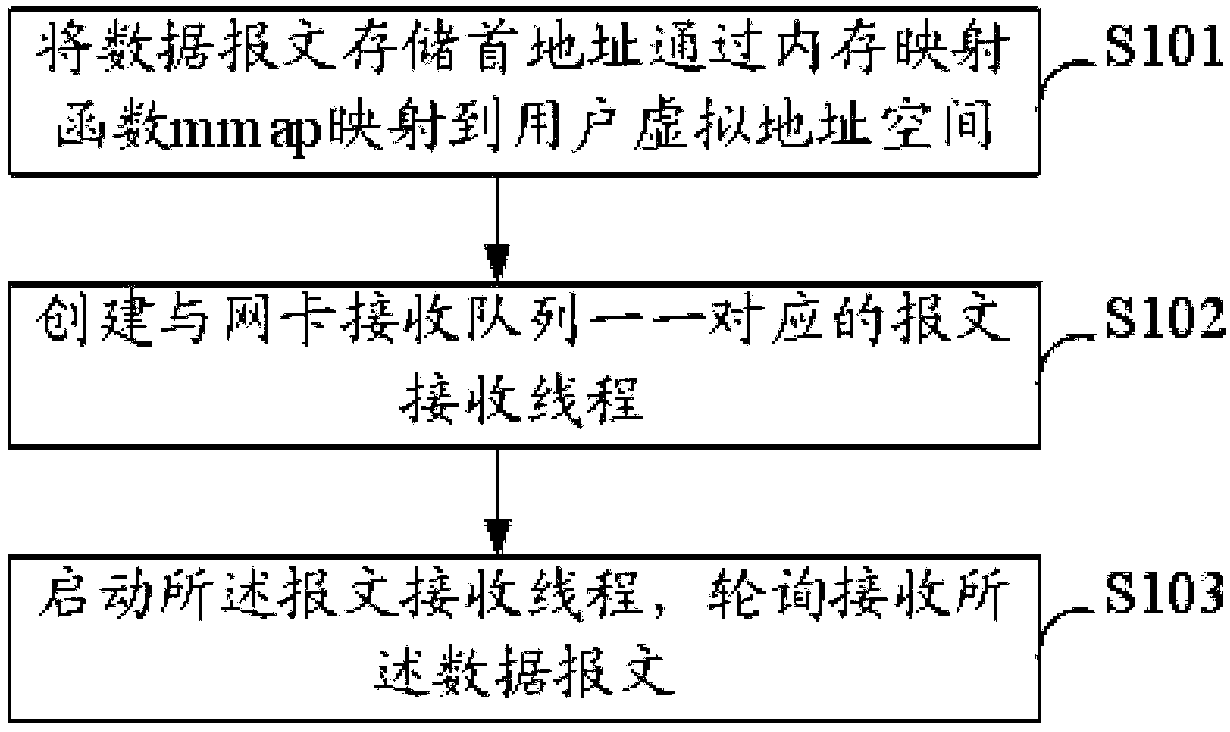
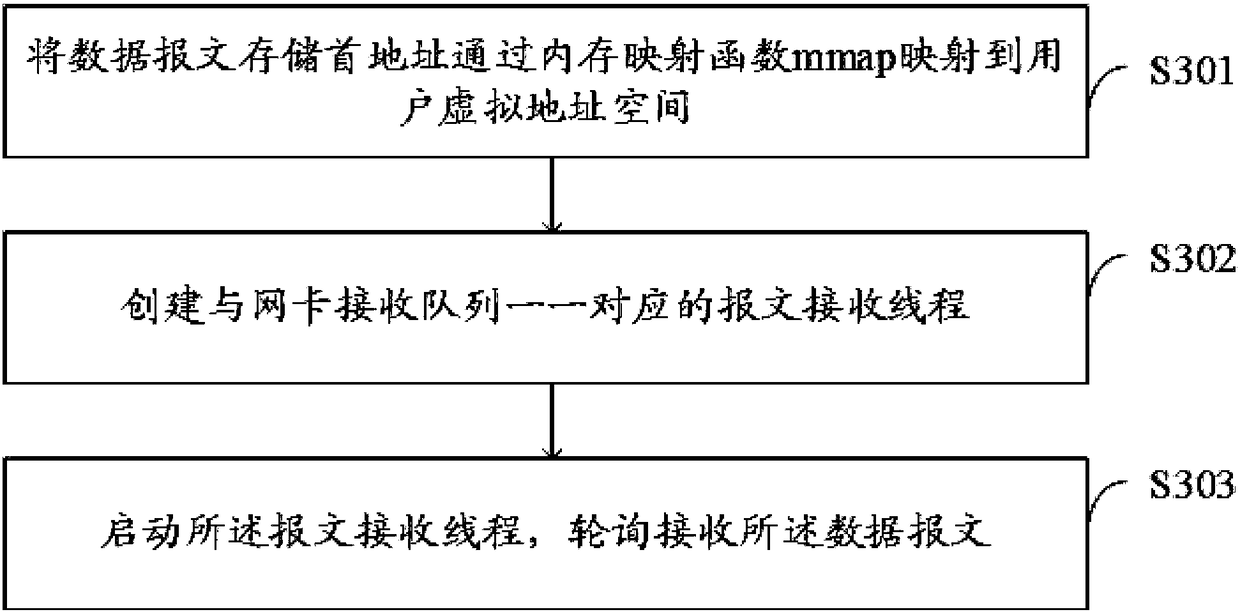
InactiveCN108111558AEasy to handleReduce CPU performance consumptionTransmissionMmapOperational system
The invention provides a high-speed message processing method, apparatus and system, and belongs to the technical field of network cache. The method comprises the following steps: mapping a first datamessage storage address into a user virtual address space through a memory mapping function mmap; creating message receiving threads in one-to-one correspondence with network card receiving queues; and starting the message receiving threads, and receiving data messages in a polling manner. According to the high-speed message processing method, apparatus and system provided by the invention, as apreset receiving mode is established between an operating system kernel module and the user virtual space, when the user virtual space receives and sends a data file, the user virtual space directly communicates with a network card, and the data file does not need to be processed by an operating system kernel, so that the processing capability of the data file is improved.
Owner:ZTE CORP
Method and system for enhancing performance of WEB servers on basis of zero copy
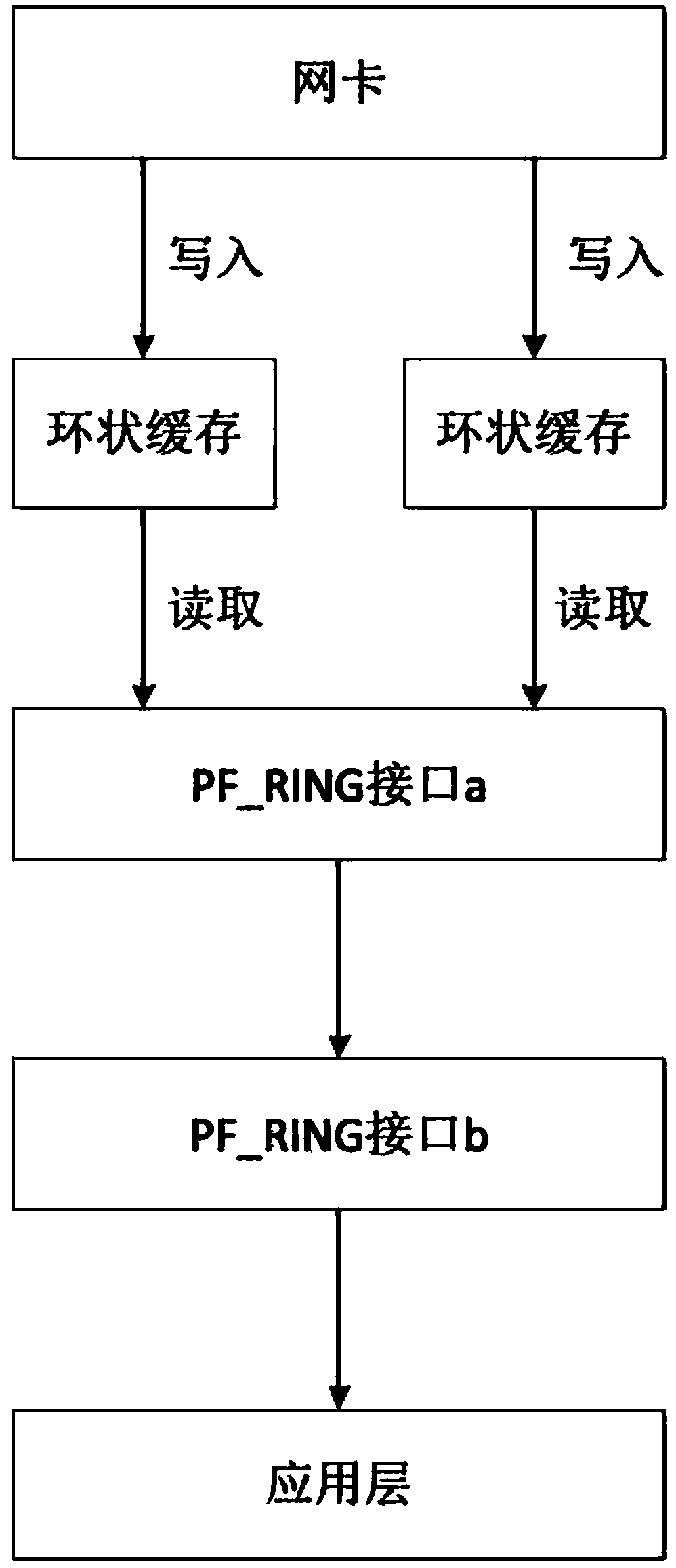
InactiveCN108090003AReduce processing overheadReduce participationData switching networksElectric digital data processingMmapZero-copy
The invention discloses a method for enhancing performance of WEB servers on the basis of zero copy. The method is characterized by comprising the following steps of: loading a PF-RING module in a linux kernel; capturing a data package by a network card which is loaded with the PF-RING module by adoption of an equipment polling-based NAPI manner; storing the data package in a ring-shaped cache byadoption of a DMA manner; and directly transmitting the data package to an application layer by the PF-RING module through an MMAP mechanism. According to the method, intermediate copy processes, in internal storage of hosts, of communication data, so that the data package reception and transmission speeds are improved, the data communication efficiency is improved, corresponding speeds are improved and then the performance of web servers are improved.
Owner:GUANGDONG EFLYCLOUD COMPUTING CO LTD
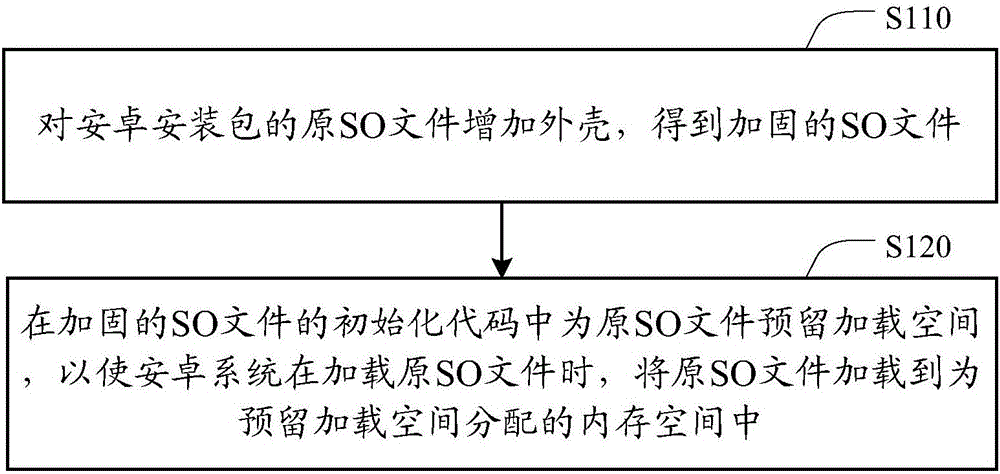
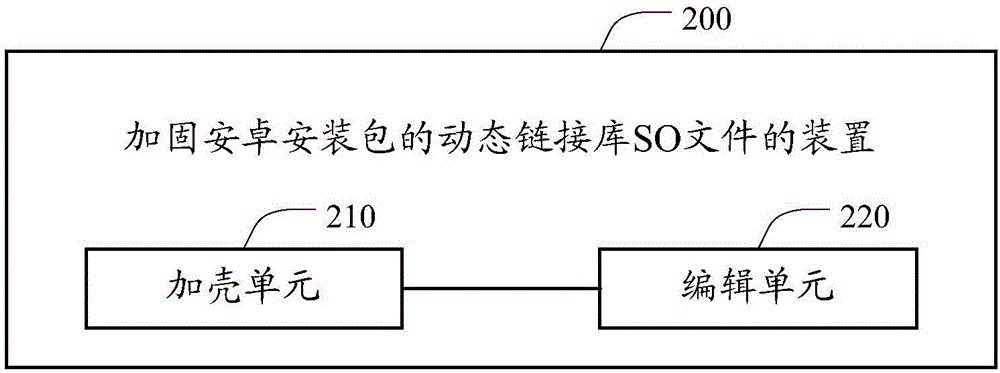
Method and device for reinforcing dynamic link library SO file of Android installation package
The invention discloses a method and device for reinforcing a dynamic link library SO file of an Android installation package. The method includes the following steps: adding a shell to an original SO file of the Android installation package to obtain a reinforced SO file; preserving a loading space for the original SO file in initialization codes of the reinforced SO file, so that when the Android system loads the original SO file, the original SO file is loaded in a memory space distributed for the preserved loading space. According to the technical scheme, the method no longer calls a mmap function alone to distribute a memory space for the original SO file, but uses a part of memory space distributed to the reinforced SO file for loading of the original SO file when the reinforced SO file is loaded, therefore, when the system releases the memory space occupied by the reinforced SO file, the memory space occupied by the original SO file can be released together, normal use of the original SO file is not affected, and memory leaking is not caused.
Owner:BEIJING QIHOO TECH CO LTD
Device having a security module
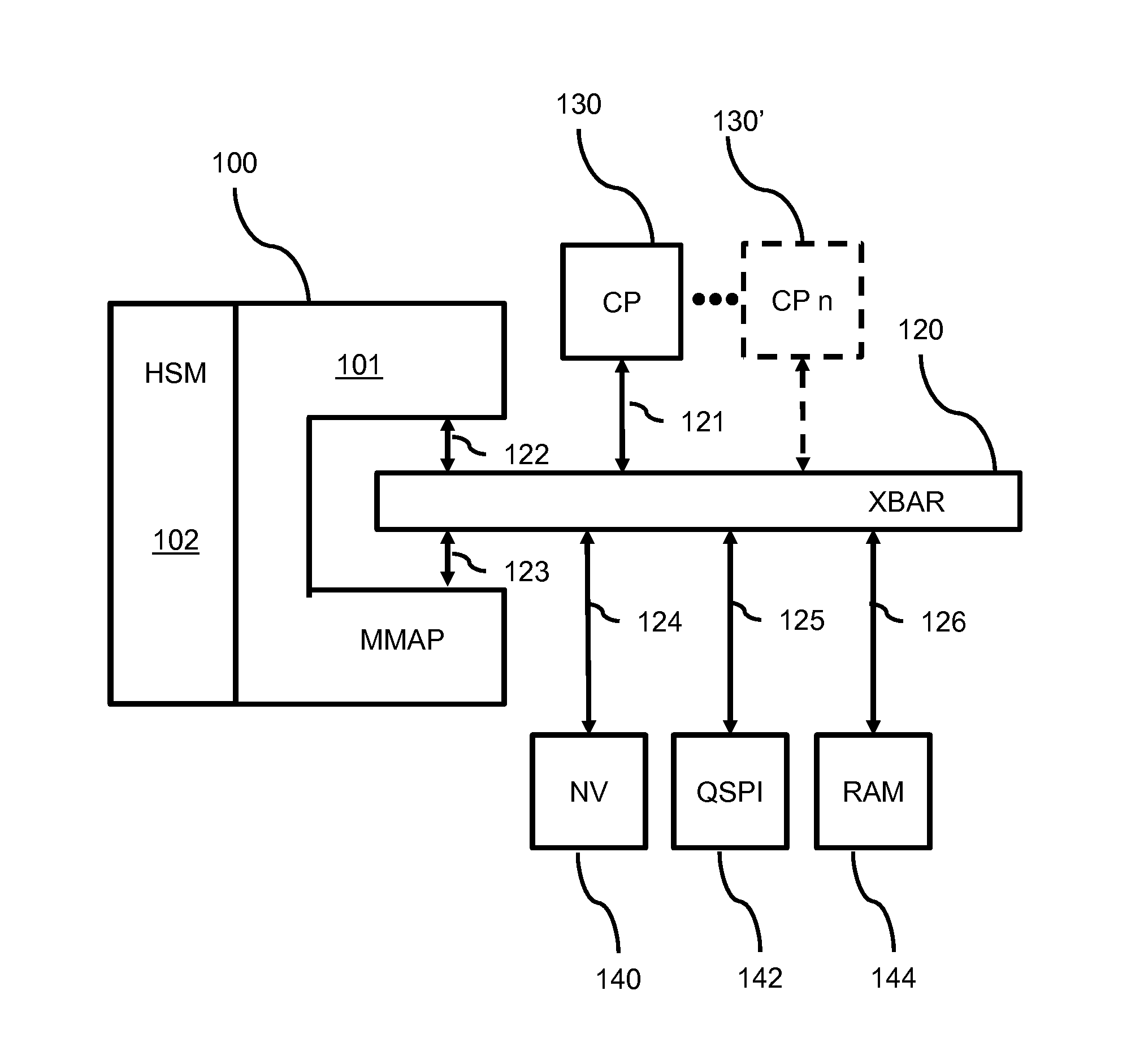
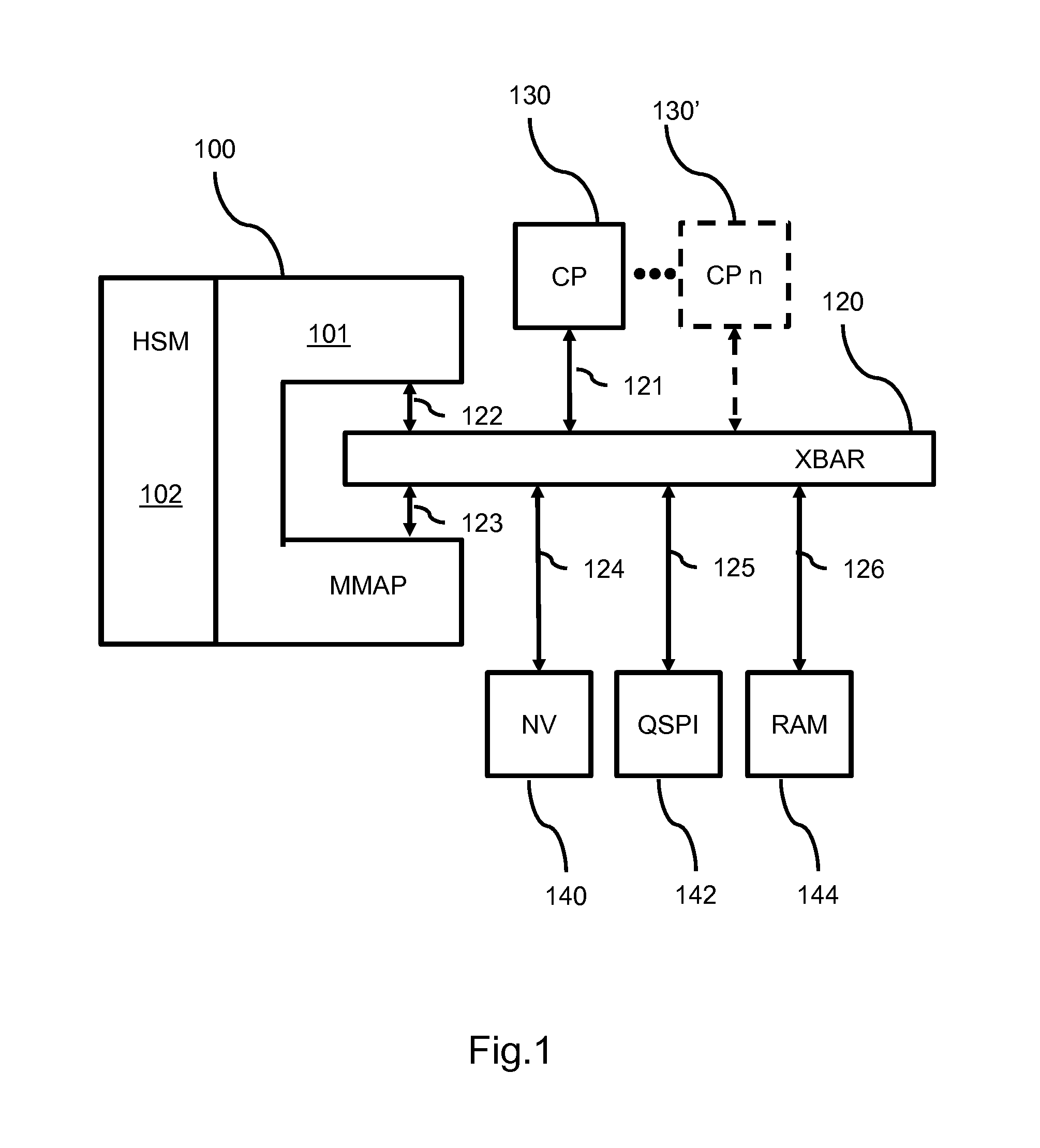
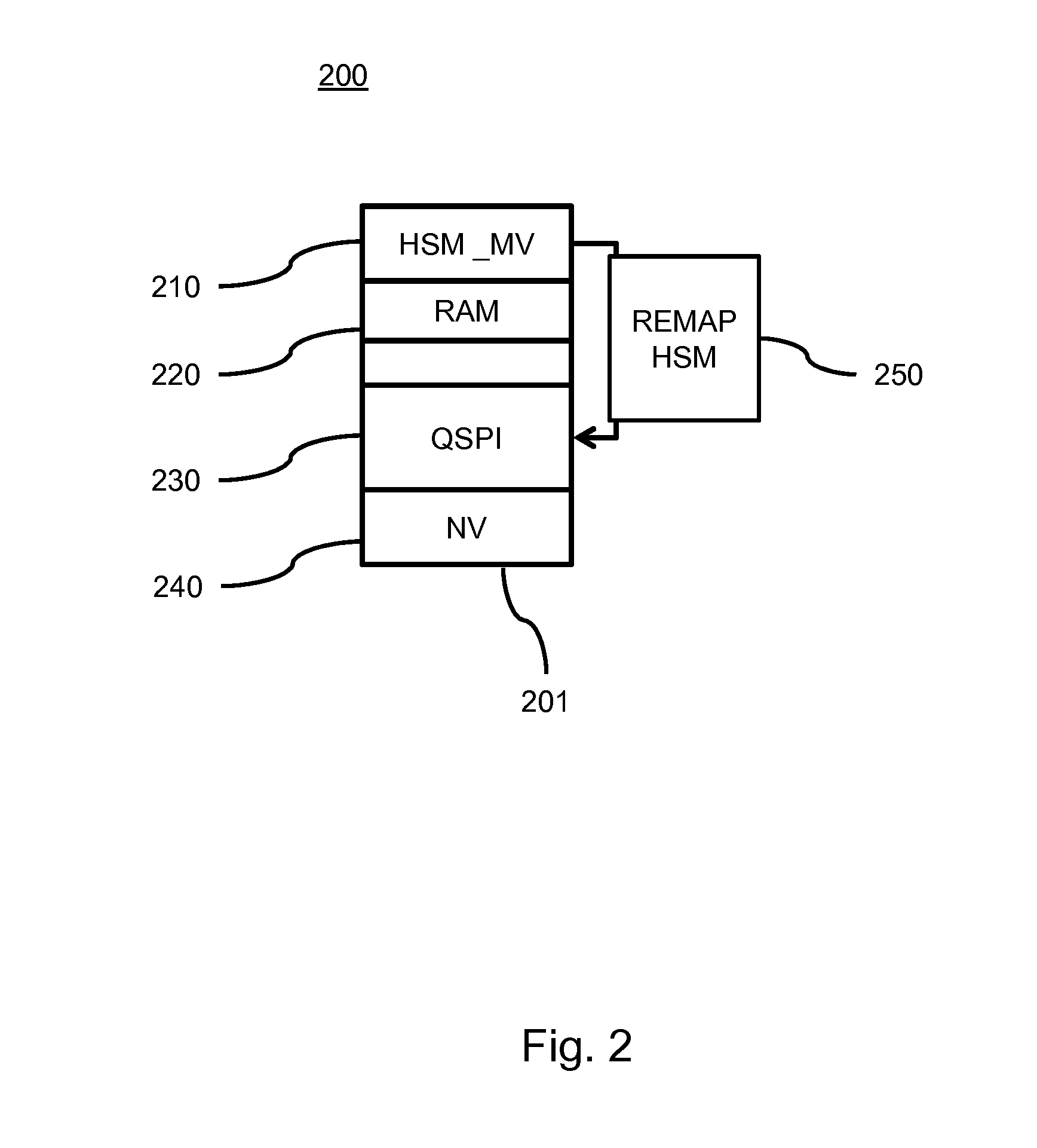
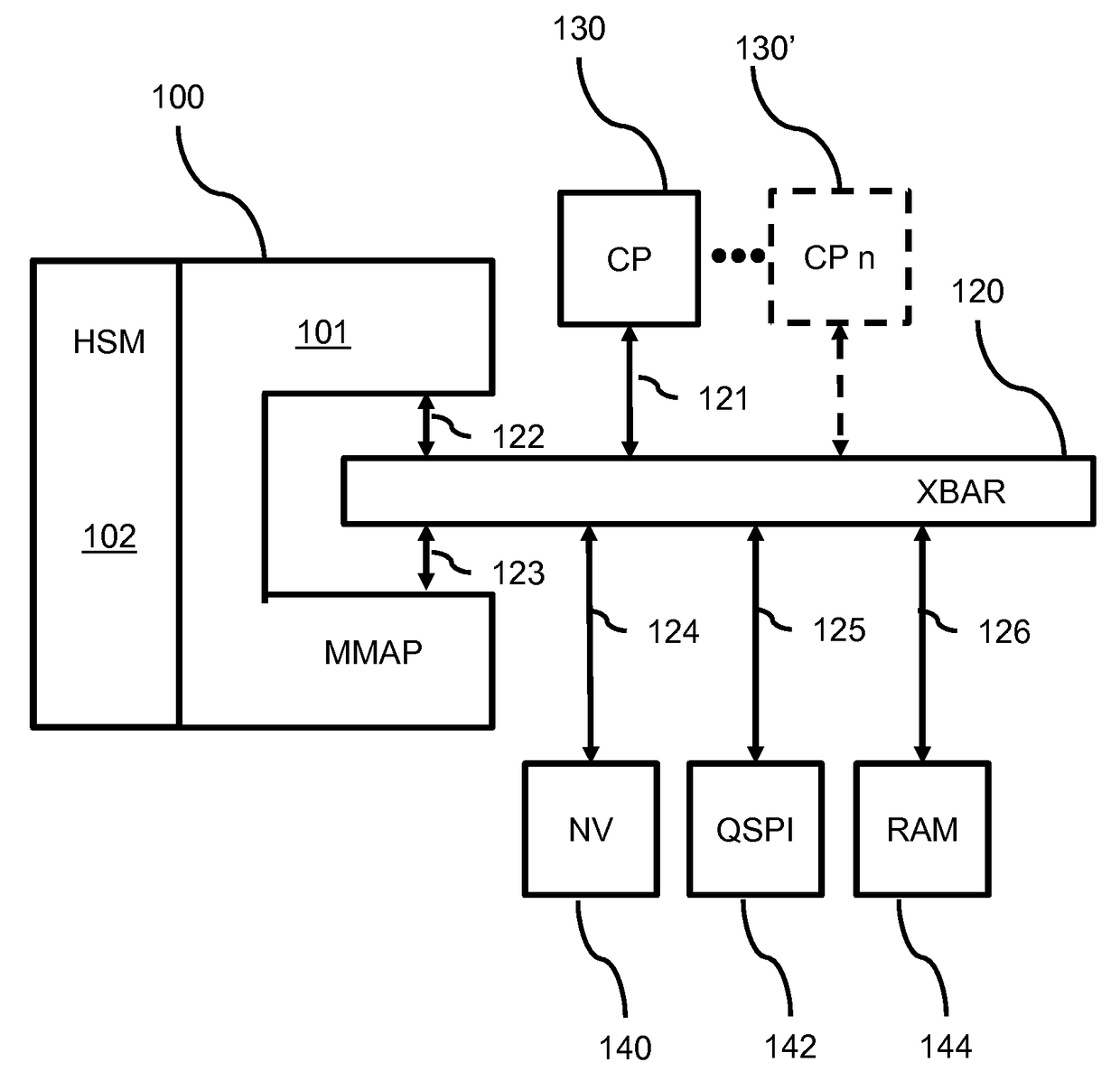
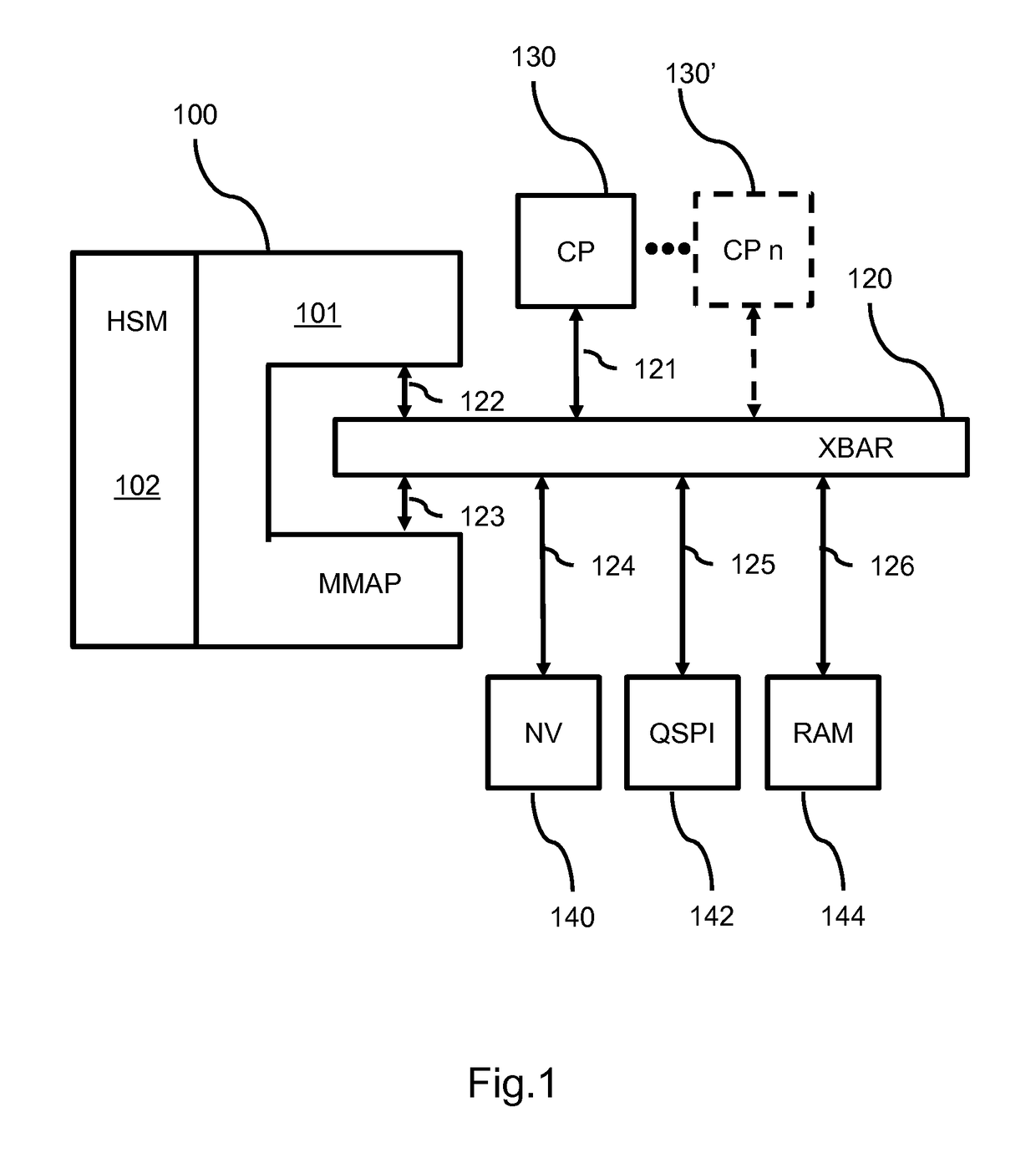
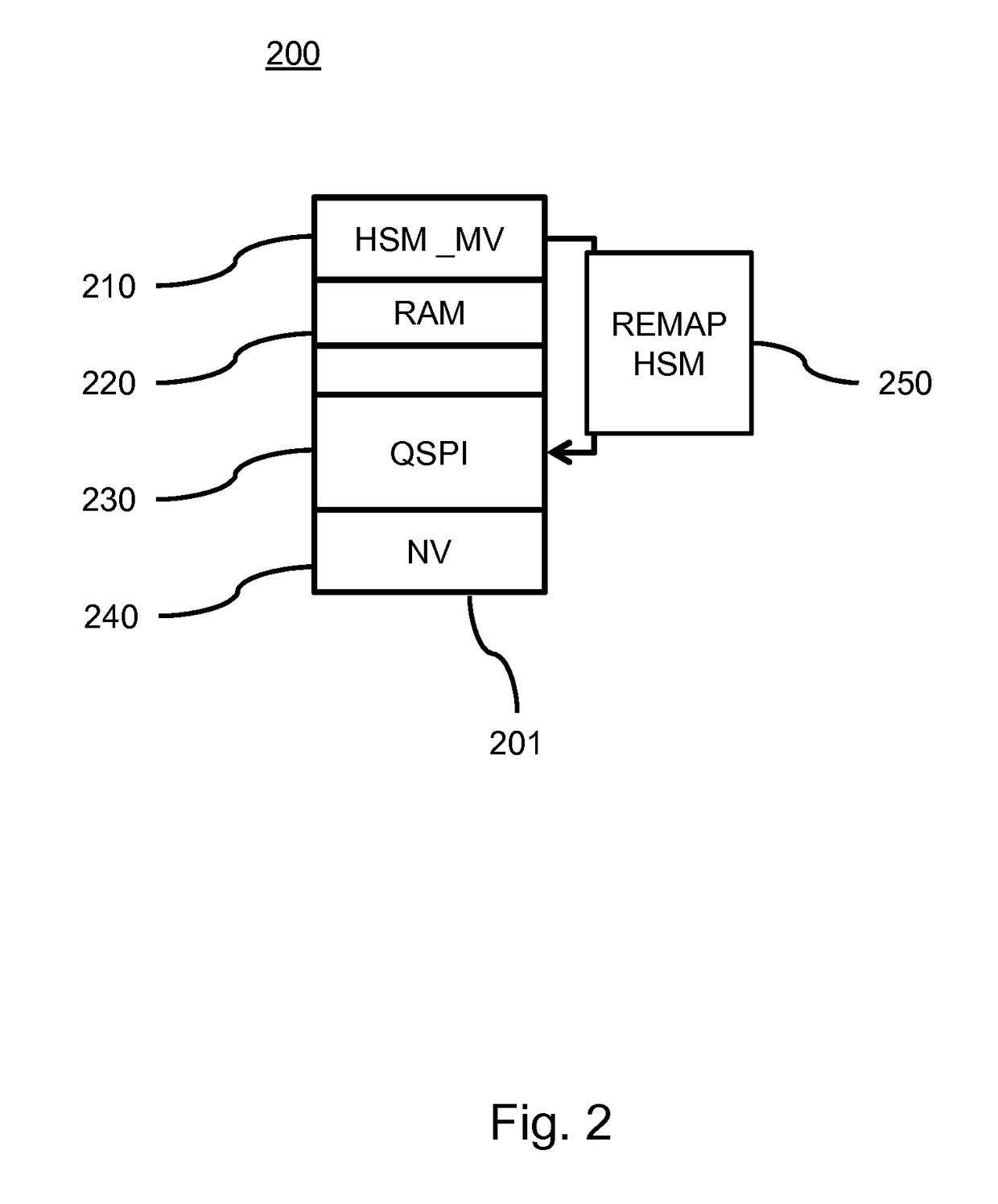
ActiveUS20160078253A1Not flexibleMemory architecture accessing/allocationDigital data processing detailsMmapMemory interface
A device securely accesses data in a memory via an addressing unit which provides a memory interface for interfacing to a memory, a core interface for interfacing to a core processor and a first and second security interface. The device includes a security processor HSM for performing at least one security operation on the data and a remapping unit MMAP. The remapping unit enables the security processor to be accessed by the core processor via the first security interface and to access the memory device via the second security interface according to a remapping structure for making accessible processed data based on memory data. The device provides a clear view on encrypted memory data without requiring system memory for storing the clear data.
Owner:NXP USA INC
System and method for handling kernel mmap call failure
InactiveCN102567068AGet unlimited usageImprove compatibilityProgram controlMemory systemsMmapThird party
The invention provides a system and a method for handling kernel mmap call failure. The method is used for creating a private memory device in a kernel mode by the aid of a driver, and all memory mappings and data sharing are operated on the private memory device, so that sharing of data in a user mode and in the kernel mode of each kernel version is realized. The system and the method for handling kernel mmap call failure have the advantages that firstly, compatibility is greatly improved as mmap can be independent from a kernel only by writing a small-scale driver, and compatibility of the kernel versions of various systems is realized; and secondly, controllability is greatly enhanced as user mode application programs and bottom equipment can be arbitrarily accessed and controlled only by writing one driver. If the scheme is not adopted, the kernel is recompiled or third-party software is adopted, both compatibility and controllability are greatly reduced.
Owner:DAWNING INFORMATION IND BEIJING
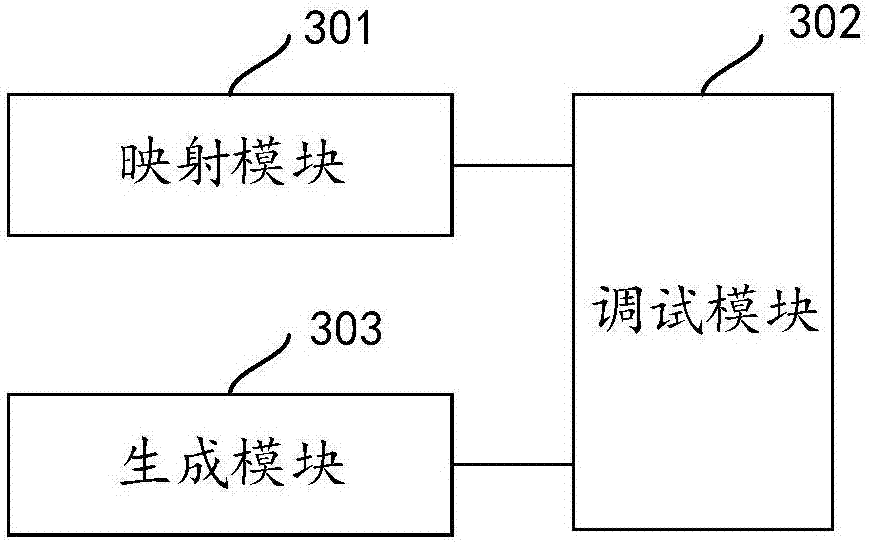
Program debugging method and apparatus
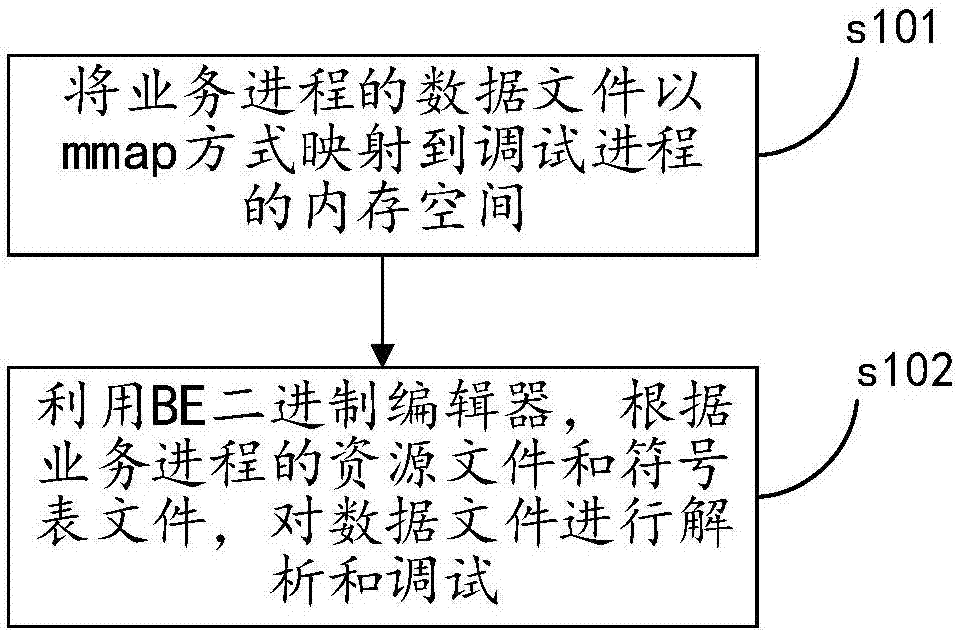
InactiveCN107402885AWill not affect executionGuaranteed execution efficiencySoftware testing/debuggingMmapData file
The invention discloses a program debugging method. The program debugging method comprises the steps of mapping data files of a business process to a memory space of a debugging process in an mmap manner; and parsing and debugging the data files according to resource files and symbol table files of the business process by utilization of a BE binary editor, wherein the resource files and the symbol table files are generated during a compilation process of the business process in advance. By mapping the data files of the business process to the debugging process, the data files can be parsed to complete debug according to the resource files and the symbol table files without influencing execution efficiency of the business process. The invention also discloses a program debugging apparatus having the above beneficial effect.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
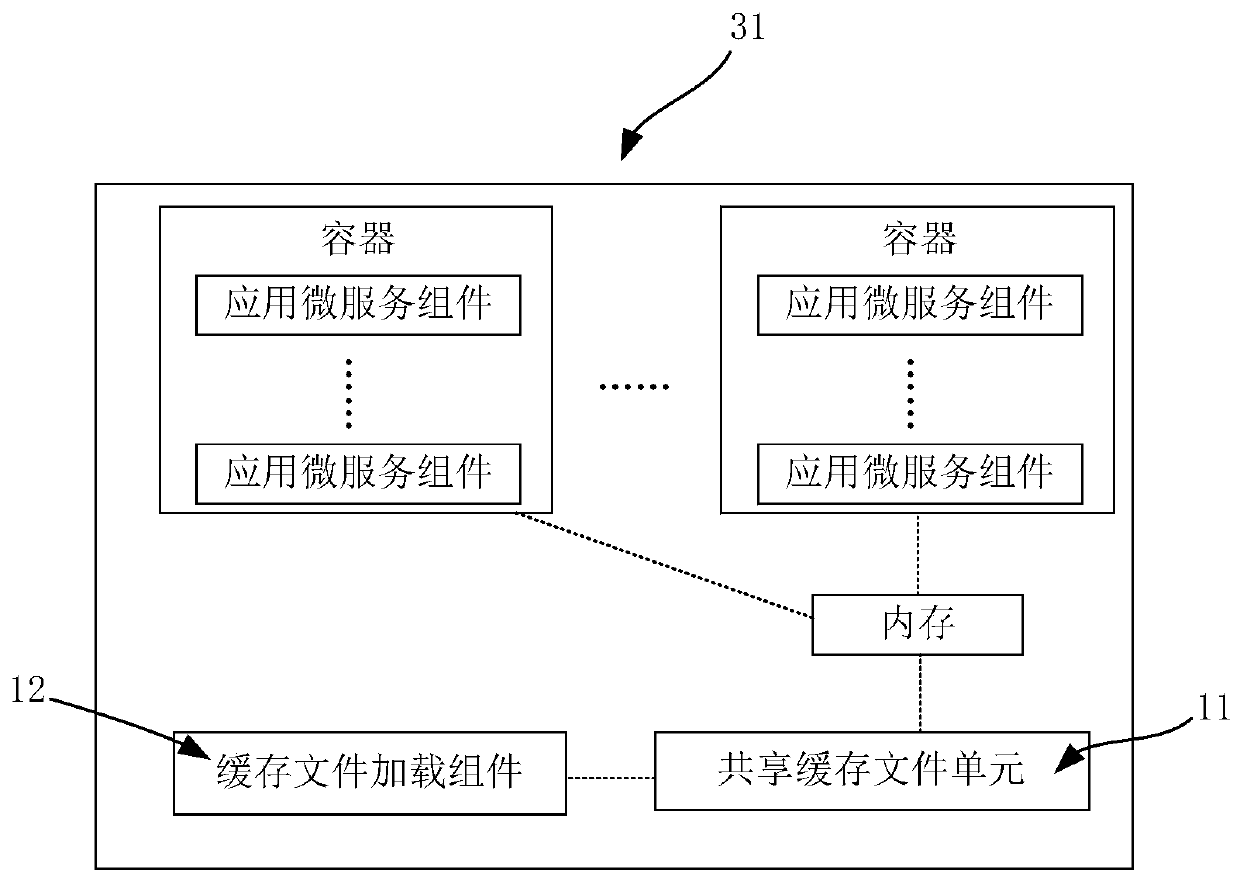
Multi-process data sharing method and related device
ActiveCN110334069AImprove data exchange efficiencyReduce overheadDigital data information retrievalInterprogram communicationMmapParallel computing
The invention provides a multi-process data sharing method and a related device, wherein the method comprises the steps: enabling an application carried by each application container on the same hostmachine to map a cache file in an MMAP sharing mode, and achieving the sharing caching based on a memory. And each application on the same host machine performs data access by utilizing the shared cache based on the memory. On one hand, the process accesses the shared cache data conveniently and quickly like accessing a stack memory or a heap memory, so that the data exchange efficiency among theprocesses is improved; on the other hand, only one copy of the shared cache data exists in the physical memory of the host machine, so that the overhead of a system protocol stack is effectively reduced, and the overall performance of the system is improved; furthermore, by means of the cache loading master control assembly, after the shared cache data of all the host machines in the distributed computing system are successfully loaded, the shared cache data in all the host machines take effect in a unified mode, and the consistency of the cache data of all the computing nodes is guaranteed.
Owner:TRAVELSKY
Method, device and terminal for dynamically detecting simulator
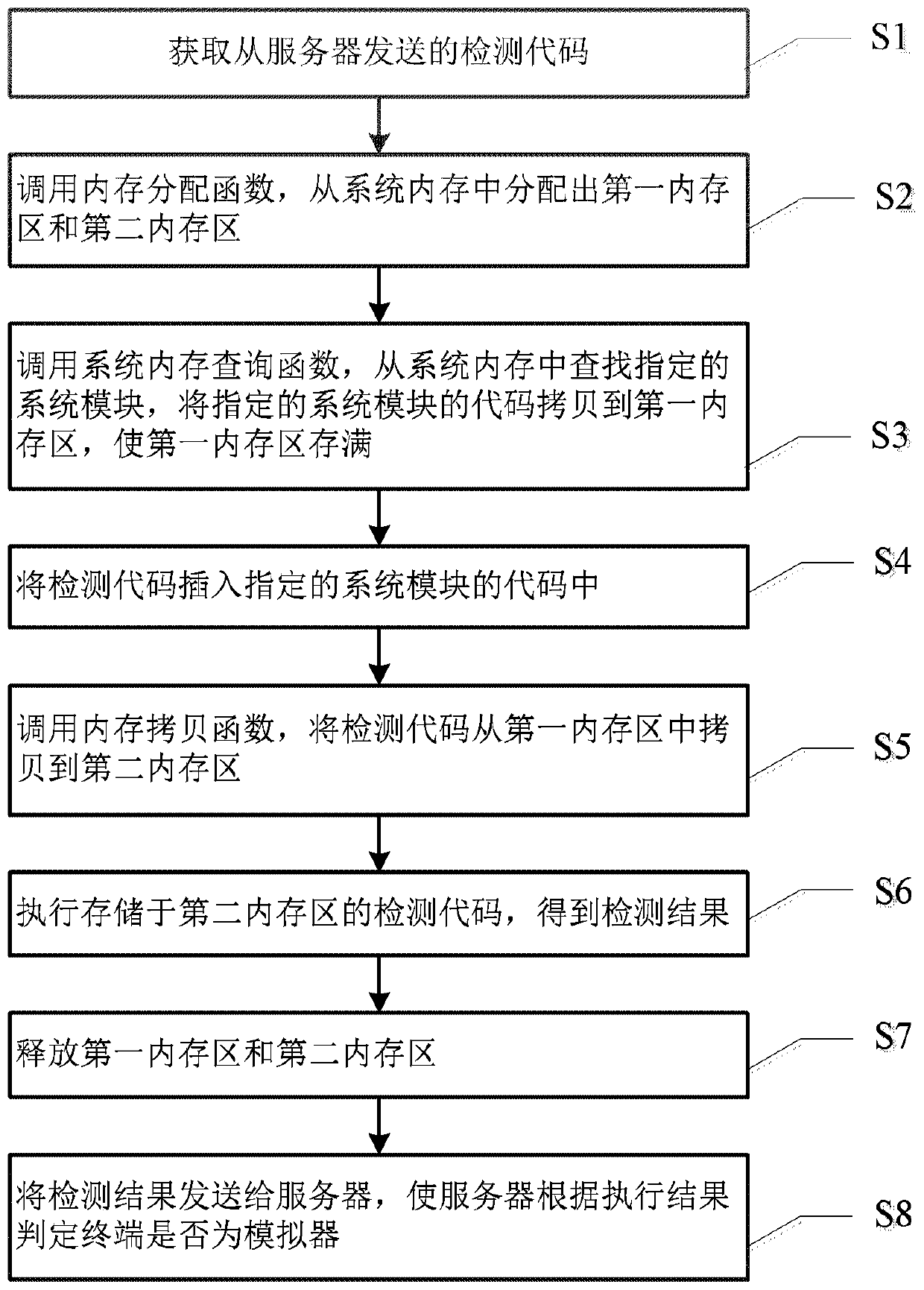
ActiveCN110147329AEffectively hideAvoid searchingDigital data protectionSoftware testing/debuggingMmapComputer module
The invention discloses a method for dynamically detecting a simulator, which is used for a terminal and relates to the technical field of information security. The method comprises steps of obtainingdetection codes, calling a memory allocation function mmap (), and allocating a first memory area and a second memory area from the system memory; calling a system file reading function, searching aspecified system module from the system memory, and copying codes of the specified system module to the first memory area; inserting the detection codes into the codes of the specified system module;calling a memory copy function Memcpy (), and copying the detection code from the first memory area to the second memory area; executing the detection code stored in the second memory area to obtain adetection result; releasing the first memory area and the second memory area; and sending the detection result to the server, so that the server judges whether the terminal is a simulator according to the execution result. The invention further provides a device and a terminal for dynamically detecting the simulator. The above process can effectively hide the detection code and prevent the detection code from being discovered and cracked by hackers.
Owner:武汉瓯越网视有限公司
Access method and device for input/output port
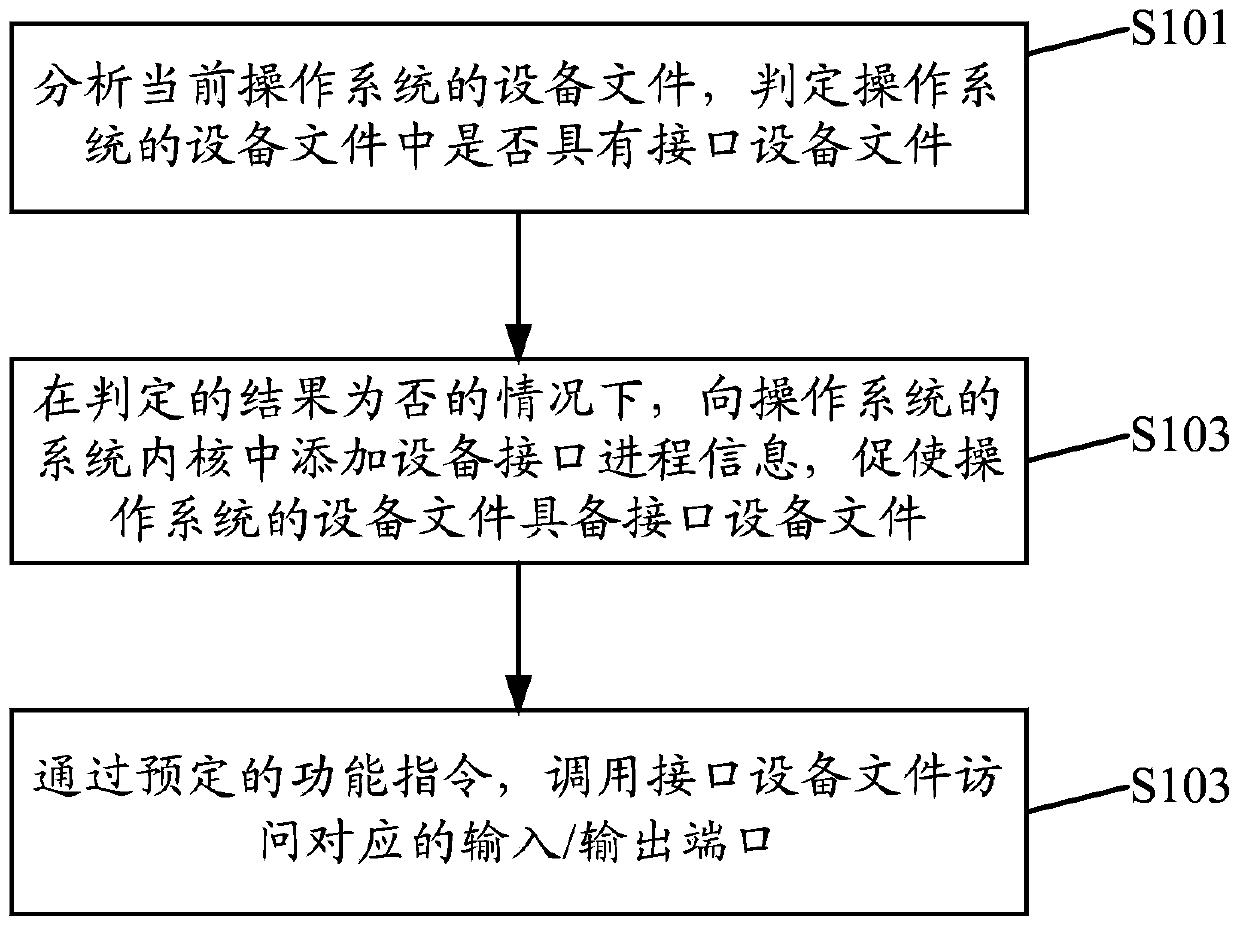
ActiveCN103744687ALow technical requirementsEasy accessProgram loading/initiatingMmapOperational system
The invention discloses an access method and device for an input / output port. The access method includes the steps that a device file of a current operation system is analyzed, and whether an interface device file exists in the device file of the operation system or not is judged; if not, device interface process information is added in a system kernel of the operation system, so that the device file of the operation system is prompted to have the interface device file; through a preset functional instruction, the interface device file is called to have access to the input / output port. When the operation system lacks the interface device file, the device interface progress information is added, so that the operation system is prompted to have the interface device file, a user can call the interface device file to have the access to the port through the preset functional instruction, the trouble that a mmap function, mapping and other operation need to be called to have the access to the input / output port by user space is avoided, and technical requirements are reduced for the user.
Owner:DAWNING INFORMATION IND BEIJING +1
Techniques for millimeter wave mobile communication
A Base Station (BS), a Mobile Station (MS), and a millimeter Wave (mmWave) Access Point (mmAP), for use in a mobile communication system that includes a plurality of Base Stations BSs capable of communicating with a plurality of Mobile Stations (MSs), are provided. The BS includes a cellular band transceiver for communicating in a cellular band, an mmWave band transceiver for communicating in the mmWave band, and a controller for controlling both the cellular band transceiver and the mmWave band transceiver for communication with an MS.
Owner:SAMSUNG ELECTRONICS CO LTD
Multi-dimensional service flow limiting method and system based on shared memories among containers
ActiveCN109871260ASolve the problem of not being able to cross service containersFix performance issuesInterprogram communicationSoftware simulation/interpretation/emulationMmapThree party
The embodiment of the invention provides a multi-dimensional service flow limiting method and system based on an inter-container shared memory. The method comprises the steps that for a plurality of application processes on the same server, a flow limiting counting file is mapped into a virtual address space of the application processes through the MMAP technology, and for any application process,three dimensions of the application process are selected for flow limiting according to the type of the application process. According to the multi-dimensional service flow limiting method and systembased on the shared memory between the containers, the problem that a traditional flow limiting method cannot cross service containers is solved, the performance problem caused by the fact that a common distributed flow limiting algorithm accesses three-party middleware is solved, and good balance is achieved between the traditional flow limiting method and the three-party middleware.
Owner:今天东翼科技有限公司
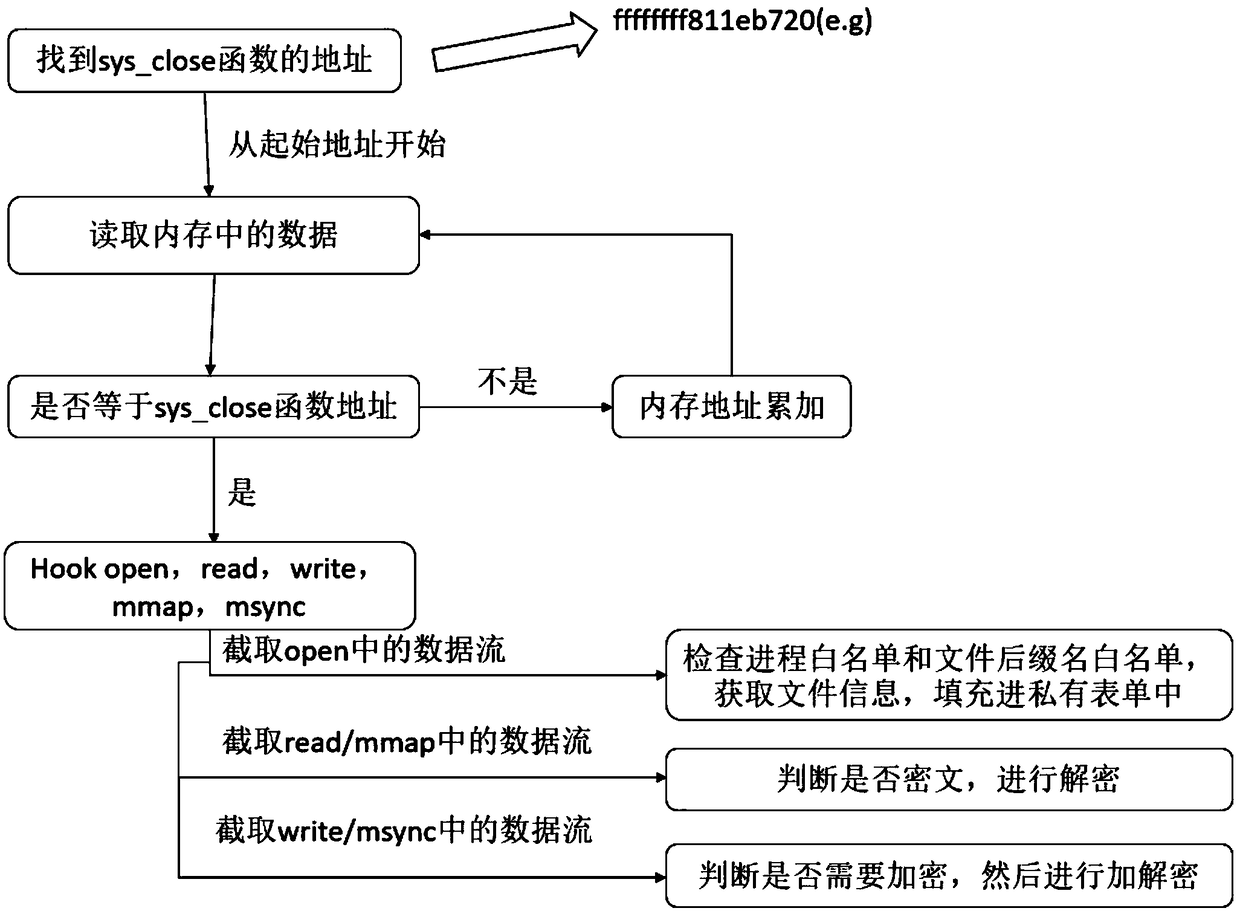
Linux operating system file read-write transparent encryption and decryption method
The invention discloses a Linux operating system file read-write transparent encryption and decryption method, comprising the following steps: 1, finding the address of a sys_close function; 2, starting from the starting address of the memory, reading the data in the memory and matching; and if the content is the address of the system call sys_close, determining that the matching is successful, and carrying out the next step; If not, determining that the matching fails, and reading the data in the next memory and performing matching; 3, after the matching is successful, calling the open, read,write, mmap and msync functions on the hook system to encrypt and decrypt the data; 4, achieving the function of file encryption protection. The method has the advantages of simple process and wide platform compatibility, and is not only suitable for Mips processors, but also suitable for Arm processors. The search method is simple; the code is simple and understandable.
Owner:浙江华途信息安全技术股份有限公司
Embedded type Linux based data storage method for electric energy data acquire terminal
ActiveCN105224471AEasy to read and writeImprove performanceMemory adressing/allocation/relocationMmapElectricity
The invention discloses an embedded type Linux based data storage method for an electric energy data acquire terminal by using a memory mapping file to store data. The data needed to be read-written is mapped to a user process space through an memory mapping function mmap (Linux system call), and the stored data is accessed in the manner of reading and writing the memory, so that the data storage method has the advantages of data solidification and data storage, without losing data in power failure, convenience in reading and writing, excellent property, cost reduction and the like.
Owner:INTEGRATED ELECTRONICS SYST LAB
Secure file transfer to process
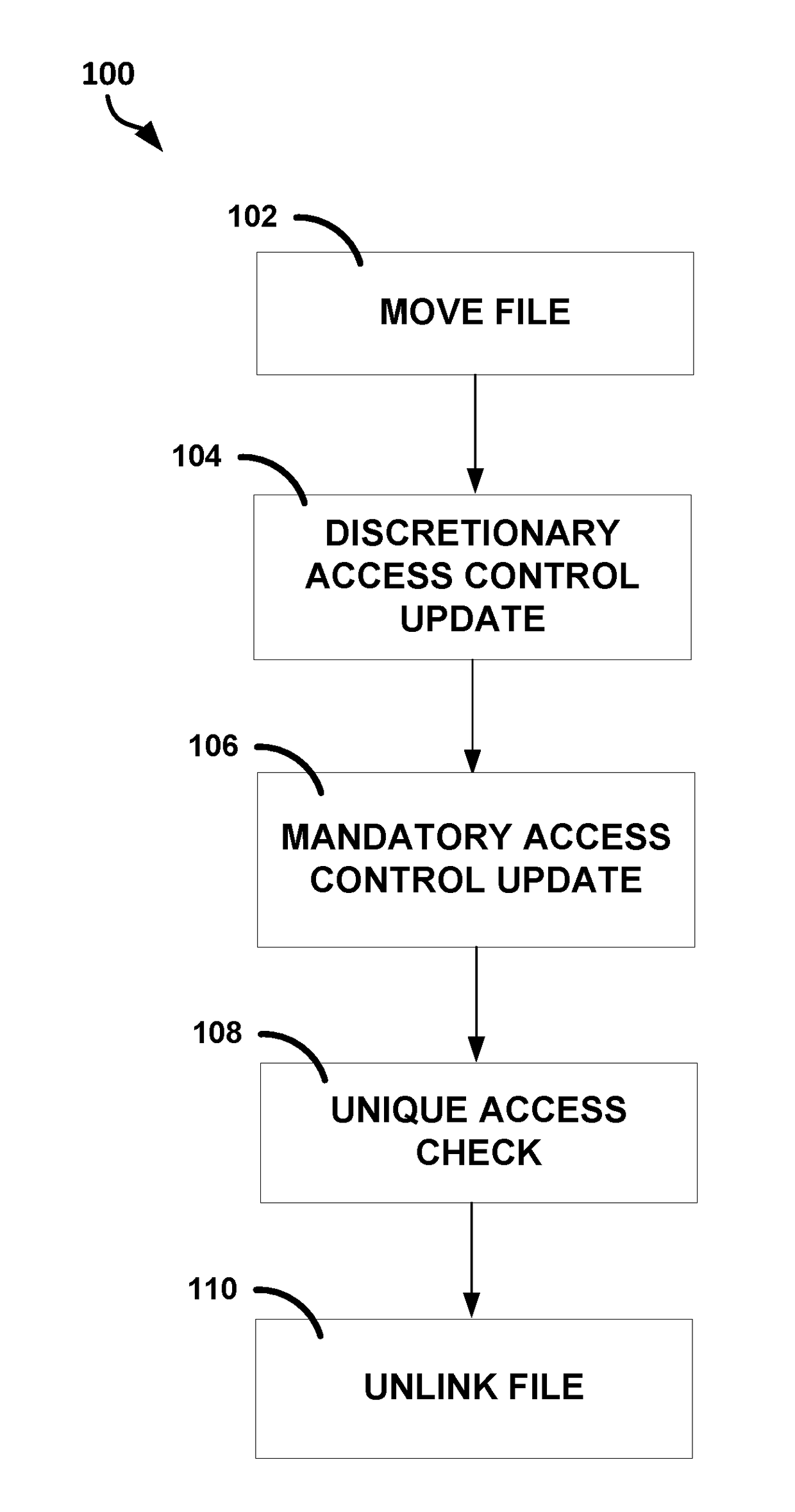
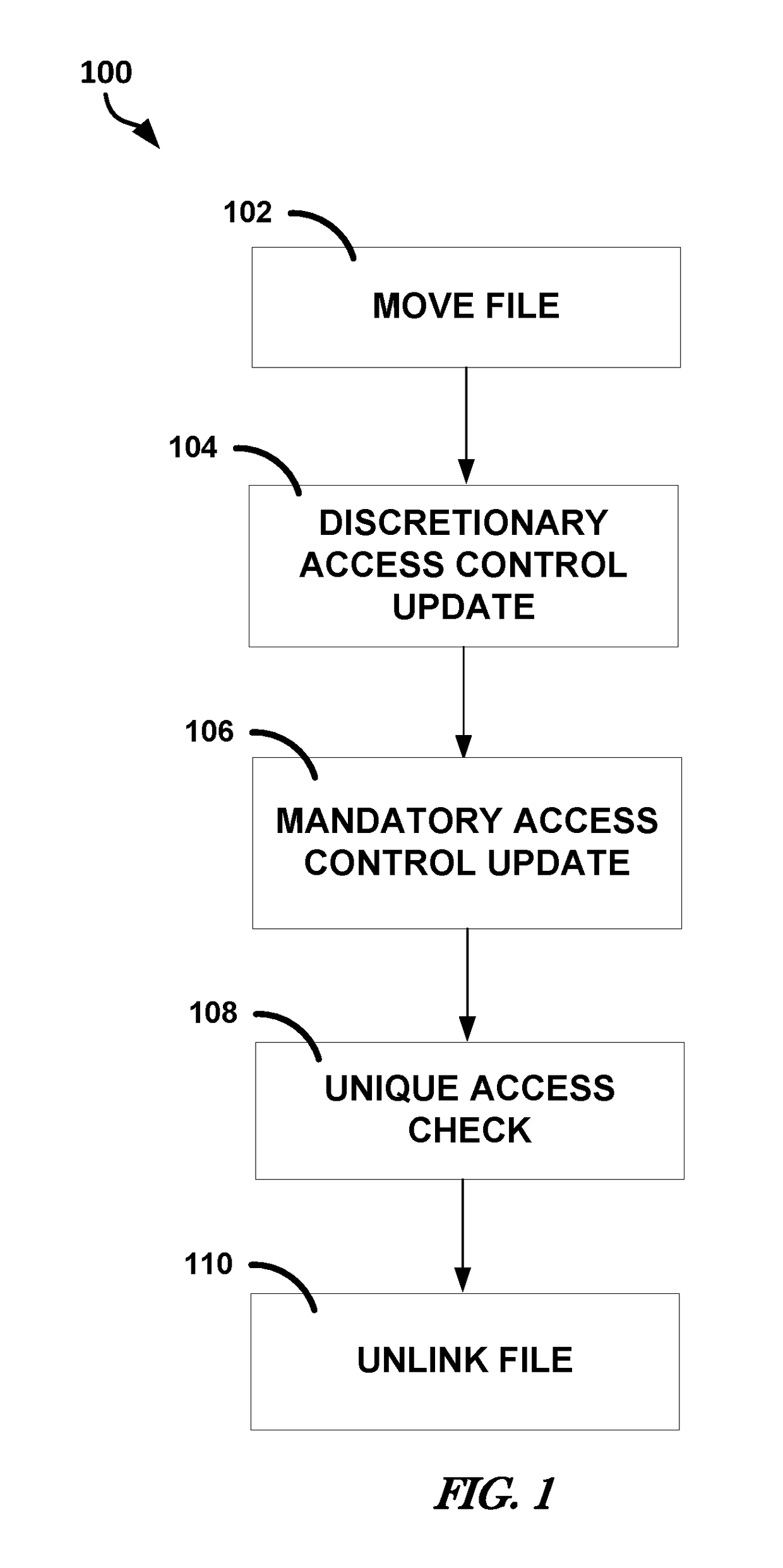
Discussed herein are methods, devices, and systems for moving a file to a process. A device can include a kernel, a memory, and processing circuitry to: issue one or more move and rename instructions to the memory to change a location and name of a file requested by the second process, issue one or more update access control instructions to update permissions, perform a UAC to determine whether any processes other than the second process currently have the file open and whether any MMaps have the file open, and allow the second process to access the renamed and moved file only if it is determined that no other processes other than the second process have the file open and no MMaps have the file open.
Owner:FORCEPOINT FEDERAL
Storage method for preventing client logs from losing easily
ActiveCN110046135ASolve the lossImprove experienceInput/output to record carriersEnergy efficient computingMmapLogfile
The invention discloses a storage method for preventing a client log from losing easily, which comprises the following steps of step A, finding a log file with a transition effect under a log directory, and mapping the log file with the transition effect into an MMAP memory according to an MMAP rule; b, when log data is received, writing the log data into an MMAP memory; c, using the MMAP memory to print the received log data into the log file with the transition effect; and step D, scanning the log files in the log directory, and renaming the scanned log files. According to the method, the problem that the log information is lost due to client crash is solved, and meanwhile, a plurality of log files can be written without increasing the memory, so that the IO consumption caused by log writing of the client can be reduced, the jamming problem caused by log writing is reduced, and the user experience is improved.
Owner:HUNAN HAPPLY SUNSHINE INTERACTIVE ENTERTAINMENT MEDIA CO LTD
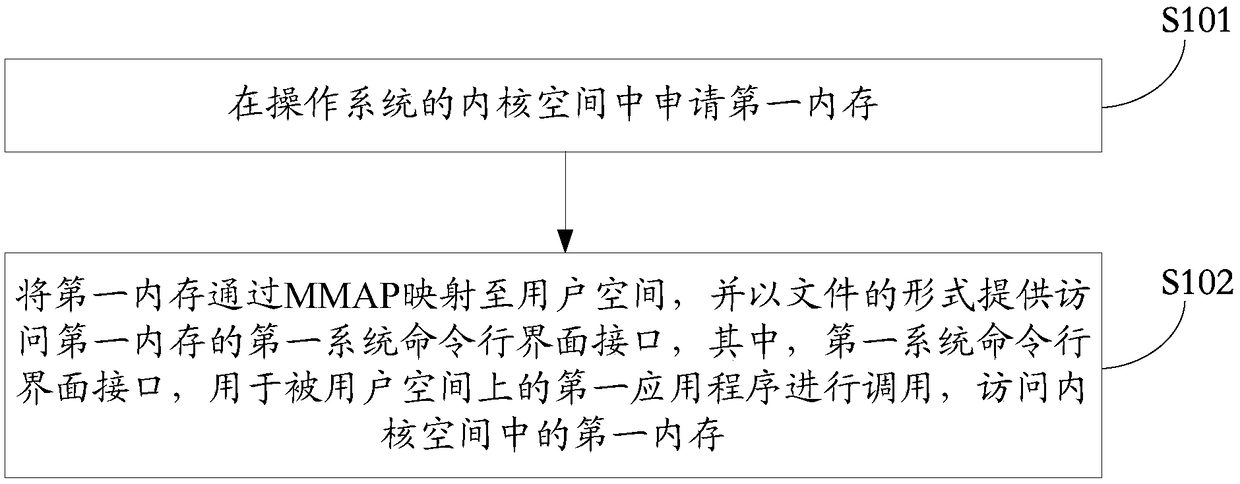
Method and device for improving the calling efficiency of system command line interface
InactiveCN109062713AImprove calling efficiencyImprove data transfer performanceInterprogram communicationMmapCommand-line interface
The invention discloses a method and a device for improving the calling efficiency of a system command line interface, includes requesting a first memory in a kernel space of an operating system, thefirst memory is then mapped to a user space via MMAP, A first system command line interface for accessing the first memory is provided in the form of a file, so that a first application program on user space accesses the first memory on the kernel space by using the first system command line interface to realize interaction with the kernel space. As seen, that application program directly access the first memory in the kernel space using the first system command line interface, The first memory is used for data exchange between the application program and the kernel space, so that the data transmission performance between the application program and the kernel space is improved, and the invocation efficiency of the system command line interface is further improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Device having a security module
ActiveUS9798901B2Memory architecture accessing/allocationMemory adressing/allocation/relocationMmapMemory interface
A device securely accesses data in a memory via an addressing unit which provides a memory interface for interfacing to a memory, a core interface for interfacing to a core processor and a first and second security interface. The device includes a security processor HSM for performing at least one security operation on the data and a remapping unit MMAP. The remapping unit enables the security processor to be accessed by the core processor via the first security interface and to access the memory device via the second security interface according to a remapping structure for making accessible processed data based on memory data. The device provides a clear view on encrypted memory data without requiring system memory for storing the clear data.
Owner:NXP USA INC
User-defined packet capture system
InactiveCN106953774AReduce sizeOptimize packet capture performanceData switching networksMmapZero-copy
The invention relates to a user-defined packet capture system. The system comprises a network card system optimization system, a lock-free queuing system, and user-defined capture conditions, wherein the network card system optimization system ignores a protocol stack of the Linux system, directly transmits packets from a kernel to user space through mmap ring, and adopts an NAPI-based zero-copy design; the lock-free queuing system judges whether a head pointer and a tail pointer are identical or not; and the user-defined capture conditions are combinations of various complex conditions such as a source destination IP, a source destination port, a protocol type and a port number, and an internal program inspects the filtering conditions in a real-time manner during storage of captured packets. The system provided by the invention has the advantages that the problem of the traditional capture method that the captured packet loss rate for 10Gbps traffics is high is solved; and through a user-defined capture filtering algorithm, the capture performance can be effectively optimized, the sizes of the captured files can be reduced, and the analysis efficiency can be improved.
Owner:WUXI JUYUN TECH
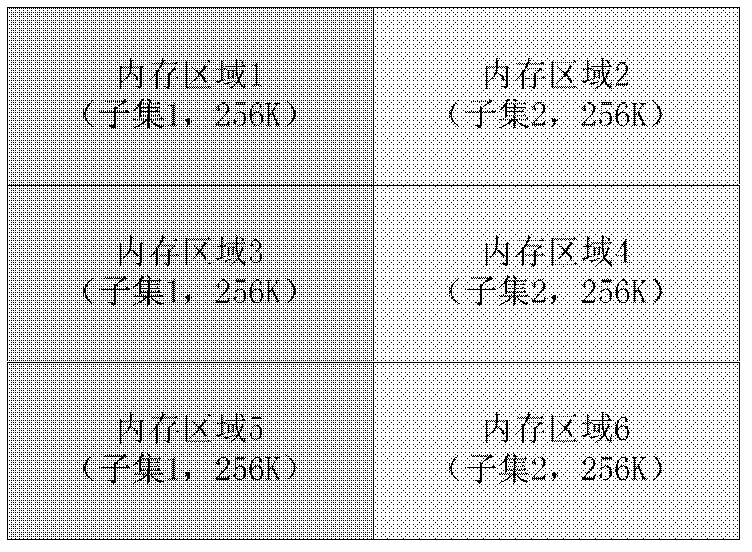
Catalogue access method in DFS (distributed file system)
ActiveCN102385623BTake advantage of read-ahead featuresAvoid the build processSpecial data processing applicationsMmapAccess method
In the invention, the content of catalogues is stored by documents, and as for the catalogue items in the catalogues, the catalogue items are divided into a plurality of subsets by hashing the titles of the catalogue items. Different subsets are stored in the catalogue documents in a striped manner, and the strip is relatively larger, so that the pre-reading function of a bottom file system can be fully utilized when a disc is read. The catalogue items in the strips of each subset are stored in a binary tree manner, so that the binary tree can be prevented from being set when initial reading is conducted. All the strips are accessed in a memory map (mmap) mode, so that expenditure caused by memory allocation and invocation of a read-write system of a system document when the disc data is accessed each time can be avoided.
Owner:DAWNING INFORMATION IND BEIJING +1
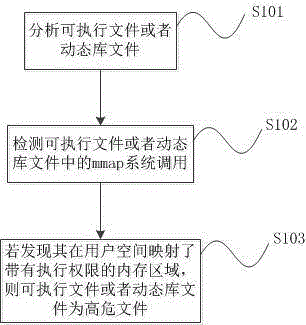
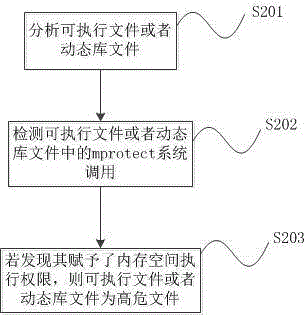
Method and system for analyzing executable file to judge high-risk file
InactiveCN105989286AImprove the ability to find high-risk filesOvercoming the problem of malicious operationsPlatform integrity maintainanceNarrow rangeMmap
The invention discloses a method and a system for analyzing an executable file to judge a high-risk file. According to the method, the executable file or a dynamic library file is analyzed in a Linux system; whether the executable file or the dynamic library file applies for a memory in a user space and modifies a default permission or not is judged by detecting mmap system call and mprotect system call in the executable file or the dynamic library file, namely, a PROT_EXEC permission is defined in Linux; and if yes, it is regarded that the executable file or the dynamic library file is the high-risk file. Through the method, the technical problems of low file detection efficiency and narrow range in a conventional bug environment are solved.
Owner:WUHAN ANTIY MOBILE SECURITY
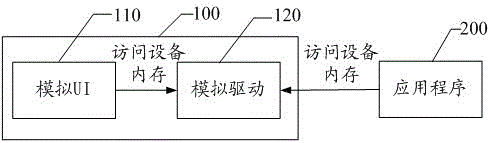
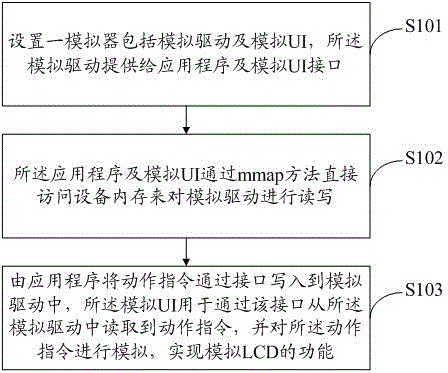
Simulator for simulating LCD (liquid crystal display) in mobile terminal and implementing method thereof
InactiveCN104156310AImprove development efficiencySoftware testing/debuggingMmapLiquid-crystal display
The invention discloses a simulator for simulating an LCD (liquid crystal display) in a mobile terminal and an implementing method thereof. The simulator comprises a simulation drive and a simulation UI (user interface) for LCD simulation; the simulation drive is to be provided for an application program and the simulation UI; the application program and the simulation UI gain direct access to a device memory by an mmap method to read or write the simulation drive; the application program writes an action command into the simulation drive through an interface; the simulation UI reads the action command from the simulation drive through the interface and simulates the action command, and the function of LCD simulation is achieved. The simulator and the implementing method have the advantages that the application program can be developed independently of hardware, regardless of a difference of running on the simulator and the true hardware, late modification is not required, and development efficiency of software is greatly improved.
Owner:TCL COMM NINGBO
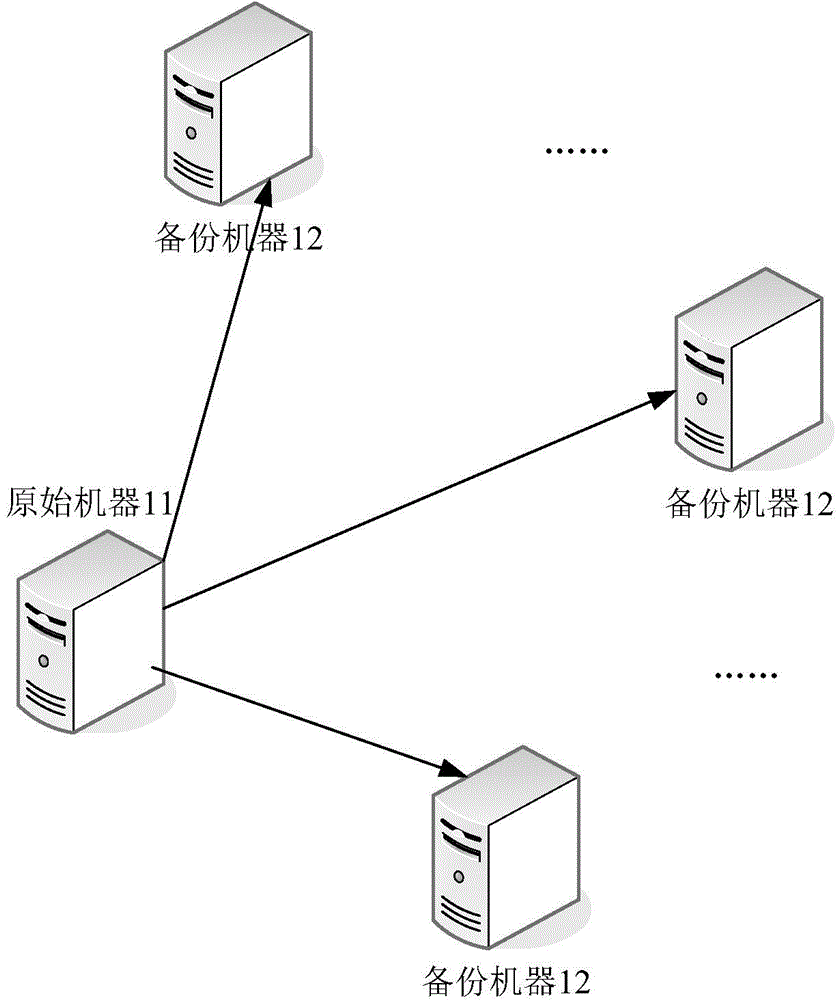
Multi-machine backup method and system
ActiveCN105302662AGuaranteed synchronizationAvoid the problem of inconsistent business process stateRedundant operation error correctionMmapMulti machine
Embodiments of the invention provide a multi-machine backup method and system, so that the problem that a business process of a backup machine is not consistent with a business process of an original machine after being recovered can be avoided. The method comprises the steps that: the original machine calls a memory map creation function mmap() of the business process to map data of the business process into a memory, and marks that a mapping region of mapping data in the memory is shared; the original machine calls a refresh change function msync() to write the data of the business process in the mapping region into a backup file, wherein the backup file is positioned in a disk; and the original machine sends the data in the backup file to the backup machine. The multi-machine backup method and system are suitable for multi-machine backup of a business system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
H3-based method for driving OV5640 camera under Linux
The invention discloses an H3-based method for driving an OV5640 camera under a Linux. The method comprises the following steps of opening an equipment file / dev / videoX corresponding to the OV5640 camera; adding a read-write register sys file system interface for driving the OV5640 camera; initializing the OV5640 camera and adding an automatic focusing function; reading an ability value of the OV5640 camera; arranging a video input source; setting an initial value of a VFE-driven default input source to be 0; setting the type and the format of a data stream; setting a VFE-supported video format to be the format of the OV5640 camera; initializing a memory-mapped allocation buffer zone; querying the size of the buffer zone; mapping the equipment buffer zone into an application space mmap; adding the buffer zone to an input queue; starting the video stream, beginning to collect data until data collection is stopped, stopping the video stream and stopping data collection; releasing memory map; and closing the equipment file / dev / videoX. The gap of a Linux operation system operated by an H3 chip in the aspect of a software drive module of supporting the OV5640 camera is filled.
Owner:广州趣通信息科技有限公司
Method and system for zero-copy receiving message
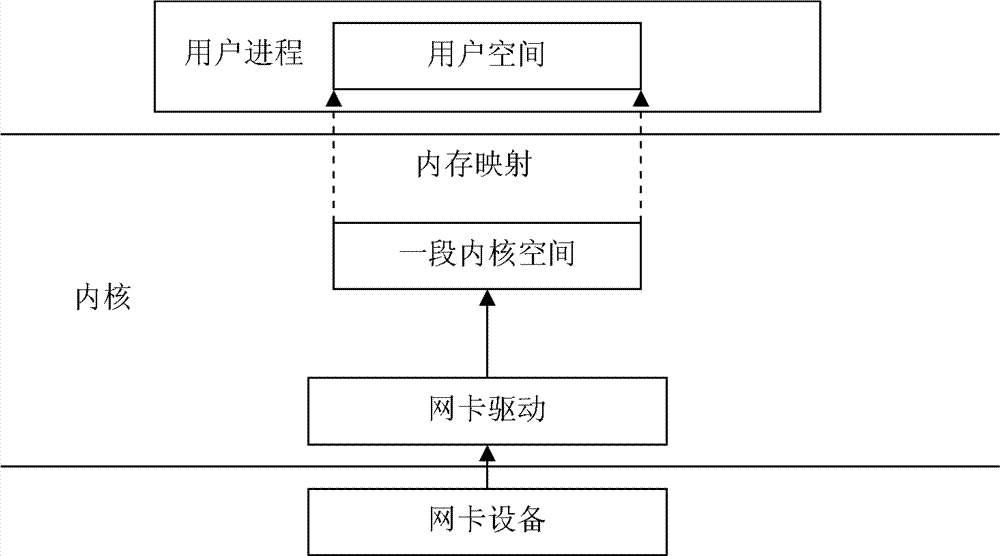
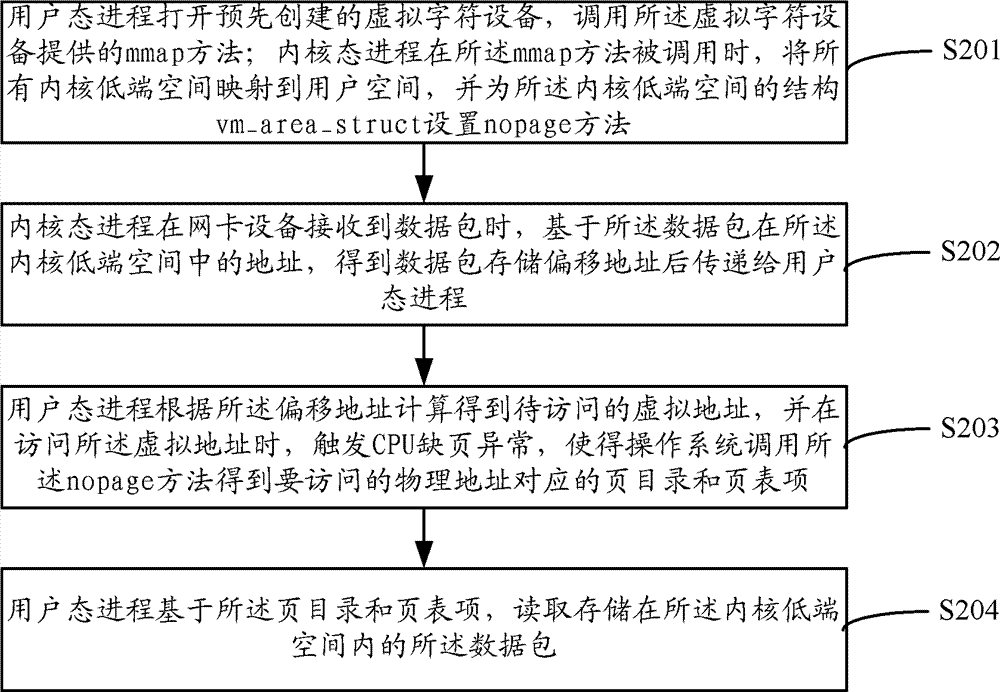
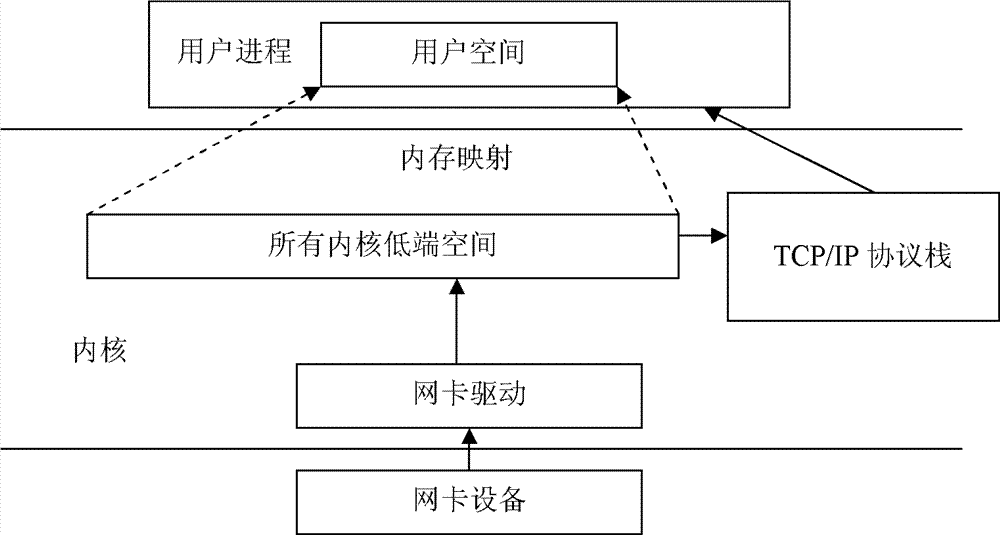
ActiveCN102402487BOvercome deficienciesEasy to handleMemory adressing/allocation/relocationData switching networksMmapOperational system
The invention discloses a zero-copy message reception method and system, the method comprises: opening a previously created virtual character device under user mode process, calling the MMAP method; when the kernel process in the MMAP method is called, mapping all kernel low-end space to the user space, setting NOPAGE method for the structure of VM--struct; when the network equipment receives data packets under kernel process, delivering the offset address of data packets at the lower end of the memory space to the user mode process; the user mode process visiting the calculated virtual address, triggering CPU page exception, so that the operating system calls the nopage method to get access to the page directory and the page table of the physical address; the user mode process reading the data packet stored in the lower end of the kernel address space. The invention solves the problems of insufficient buffer of prior zero copy technology and unable to arbitrarily amend or move the message in the process of zero copy.
Owner:BEIJING TOPSEC TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com