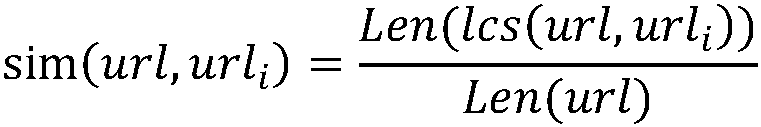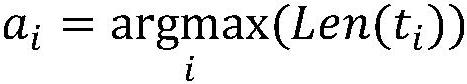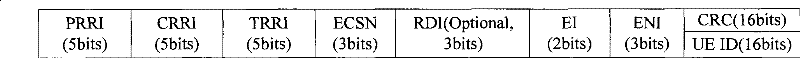Patents
Literature
35results about How to "Will not affect execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
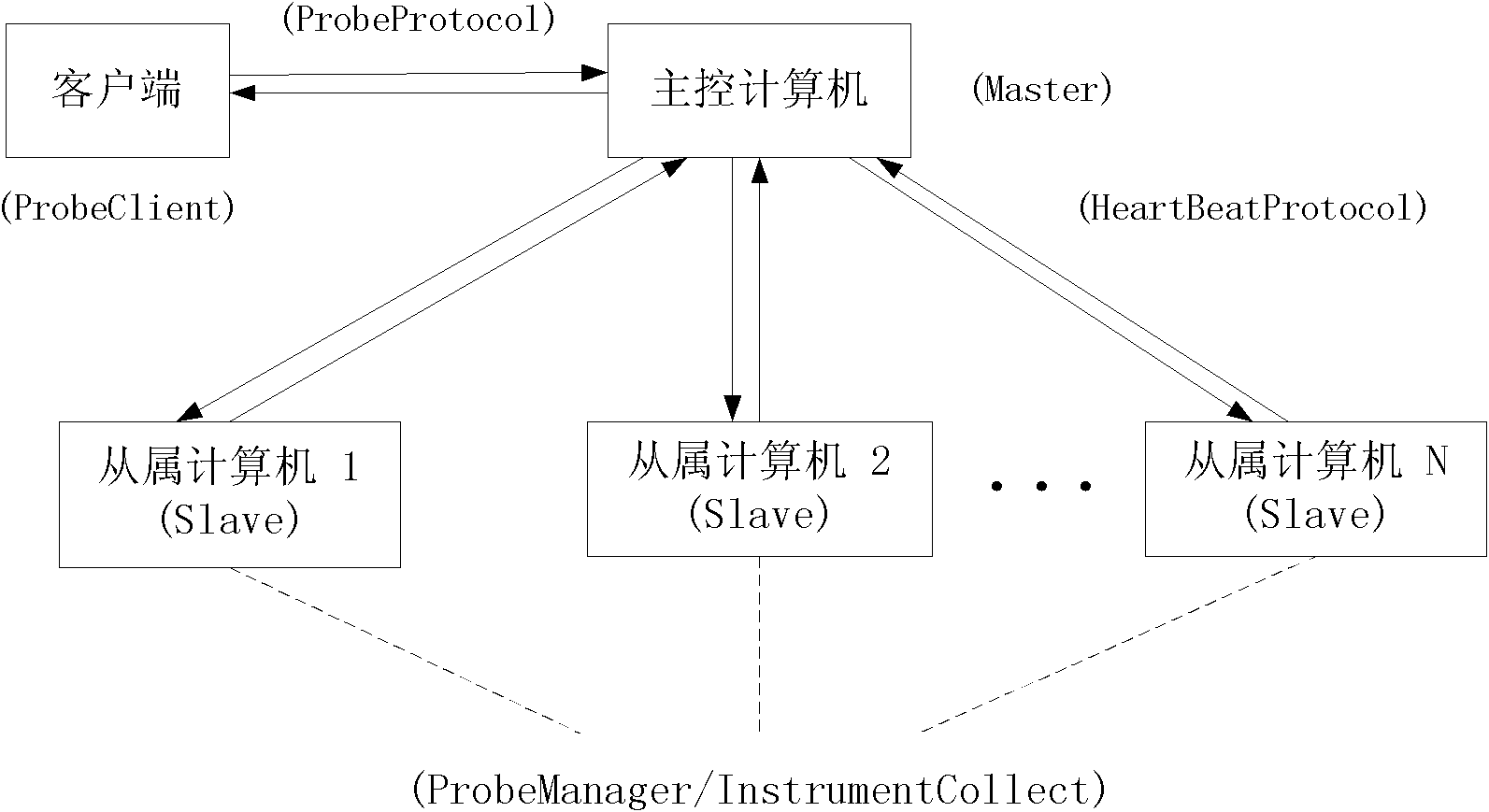
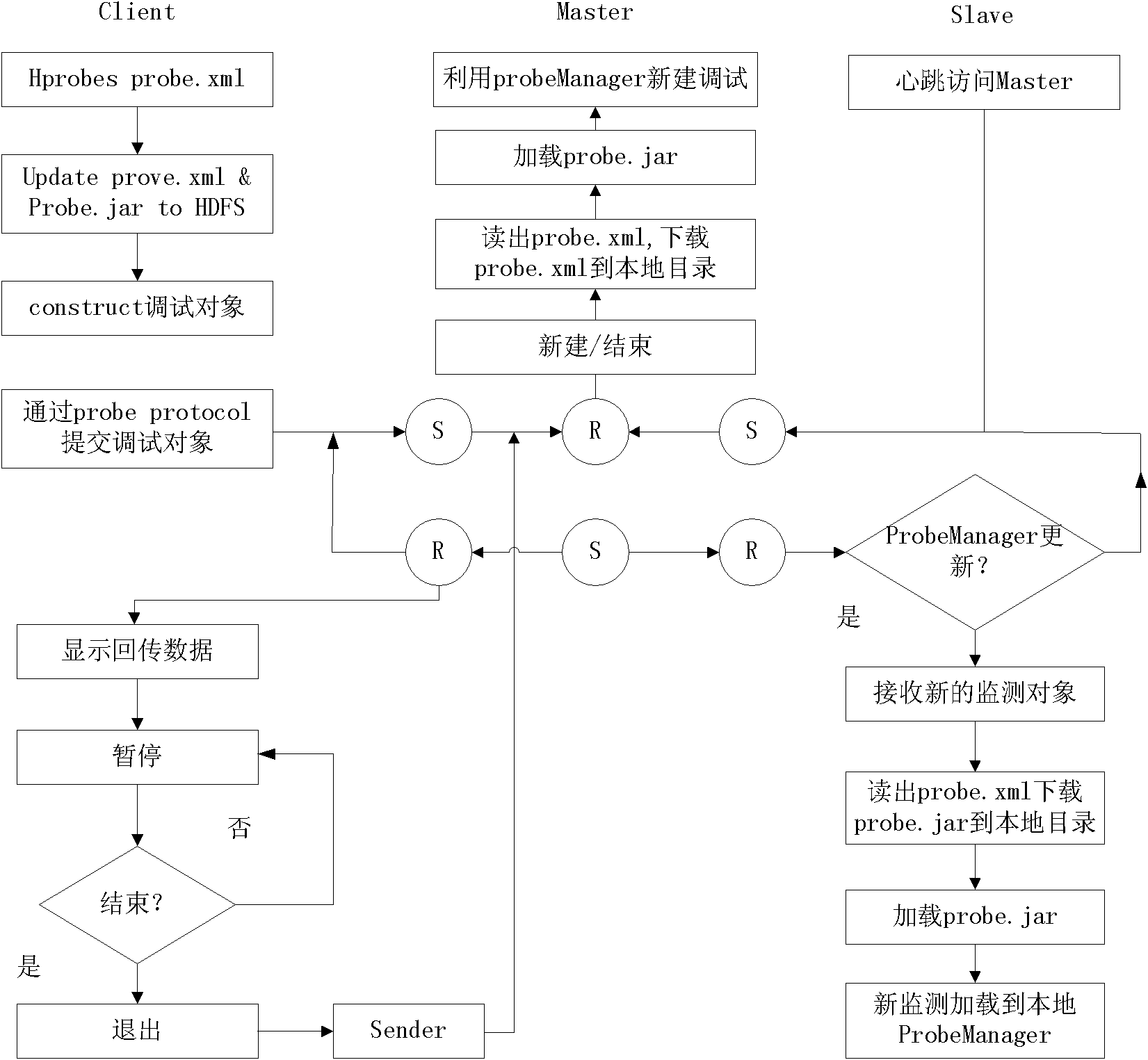
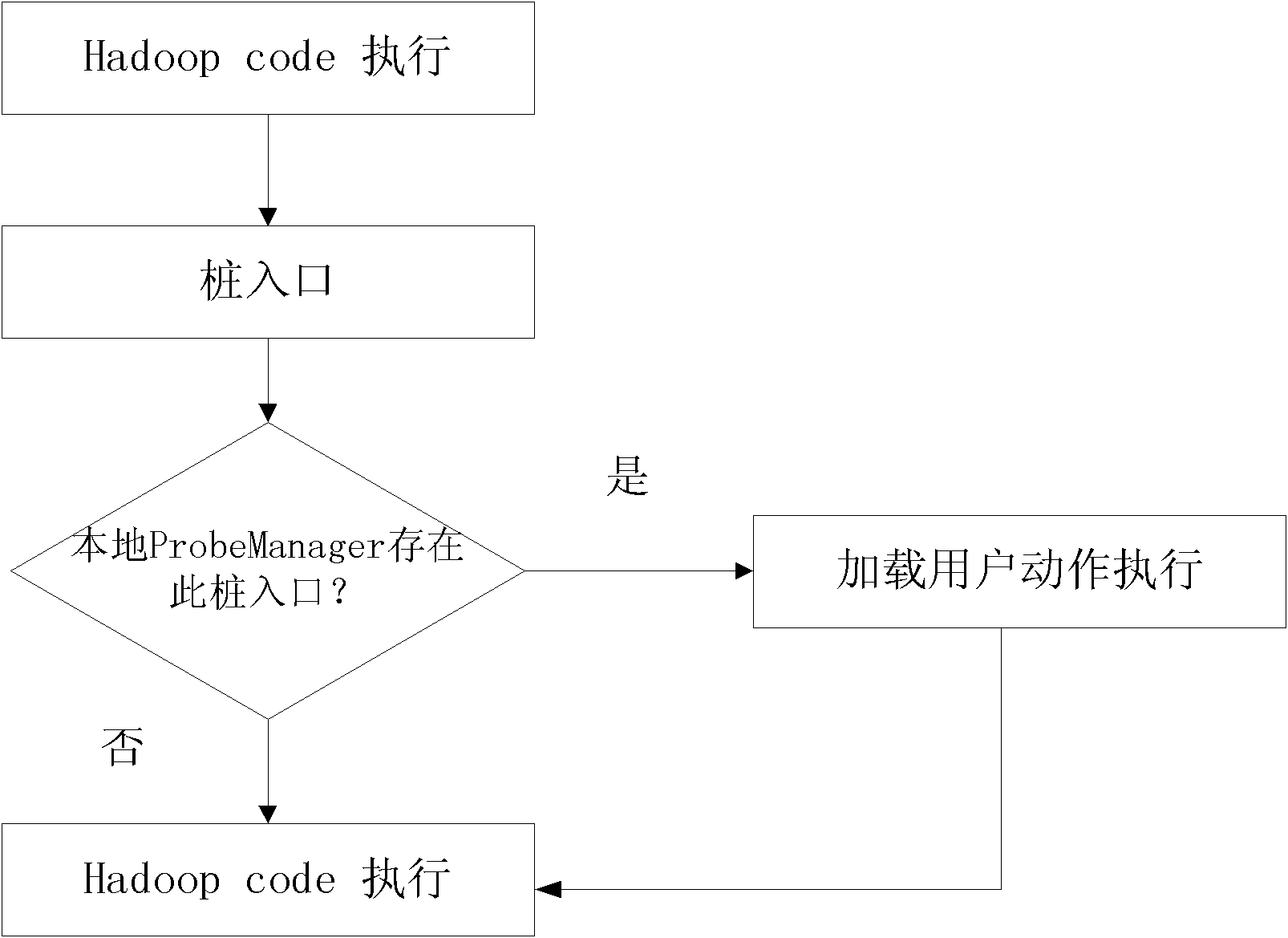
Distributed monitoring system based on Hadoop cluster and monitoring method thereof
ActiveCN102130950AEffective monitoringThe monitoring results are accurateTransmissionWork taskMonitoring system
The invention discloses a distributed monitoring system based on a Hadoop cluster and a distributed monitoring method thereof. The system comprises a client, a master computer and a slave computer. The system is characterized in that: the master computer and the slave computer in the system are constructed based on a MapReduce framework of the Hadoop cluster; the client is used for submitting a monitoring work request to the master computer; after responding to the monitoring work request, the master computer divides monitoring work and distributes the divided monitoring work to the salve computer for independent completion; and the slave computer is used for completing an independent monitoring work task, integrating a result through the master computer and returning data to the client. By the invention, data such as the task schedule and the like of a distributed computing network MapReduce can be effectively monitored, the monitoring result can be precisely obtained in real time, and independent dynamic switching is realized under the condition of not influencing work execution.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
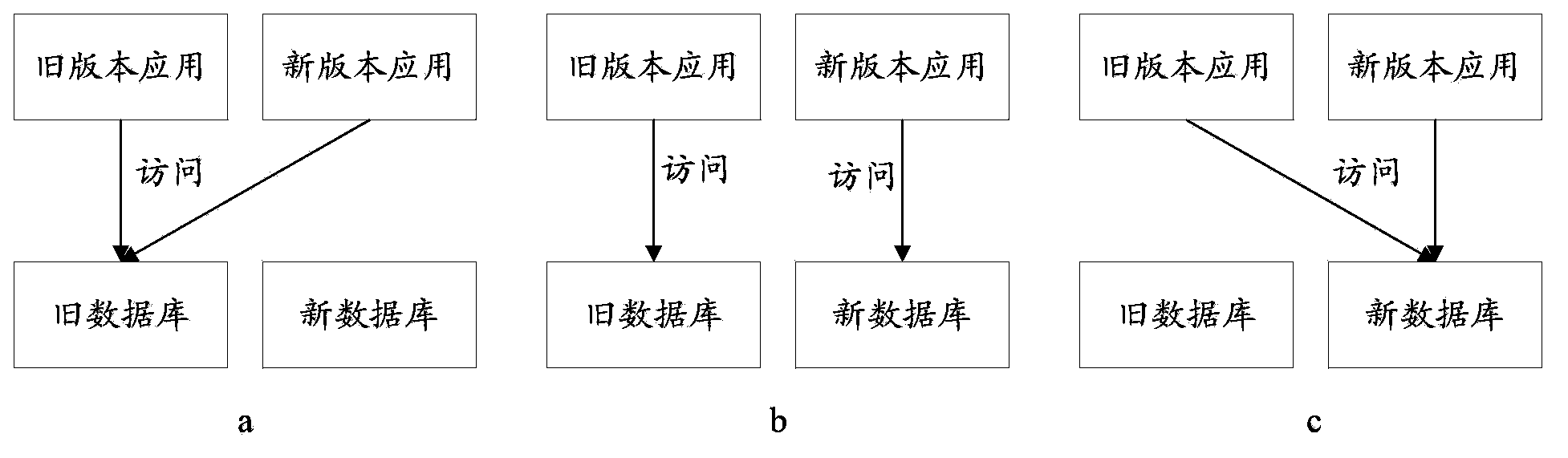
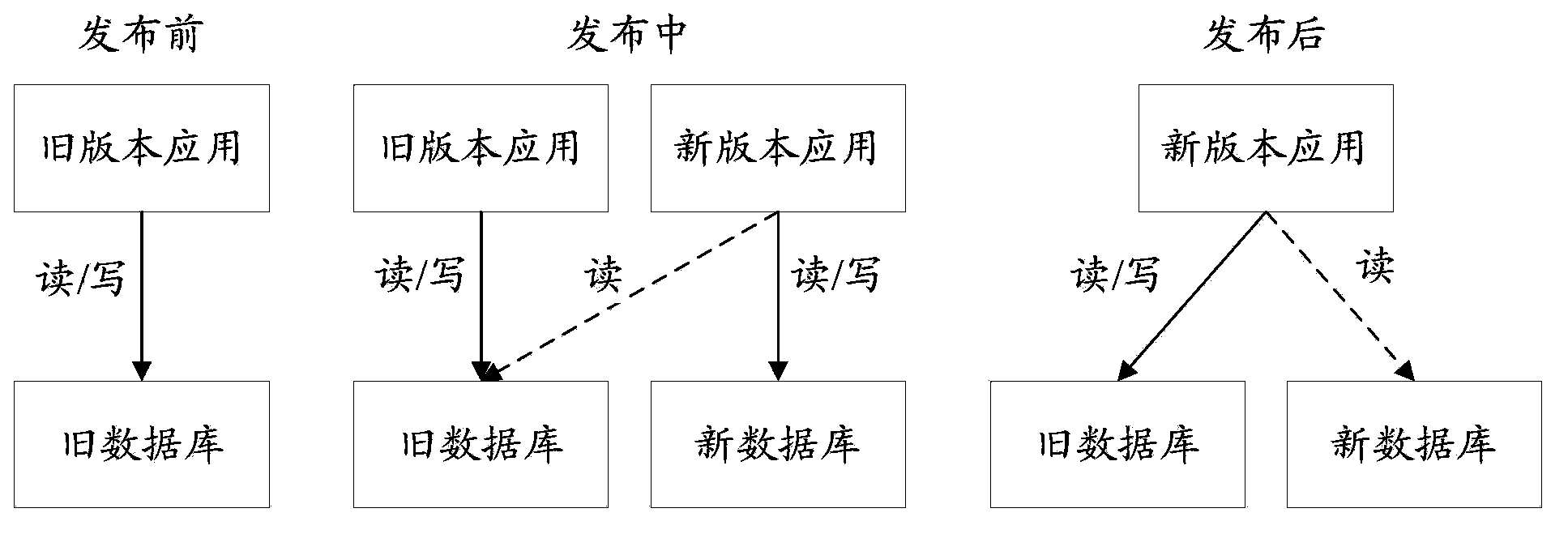
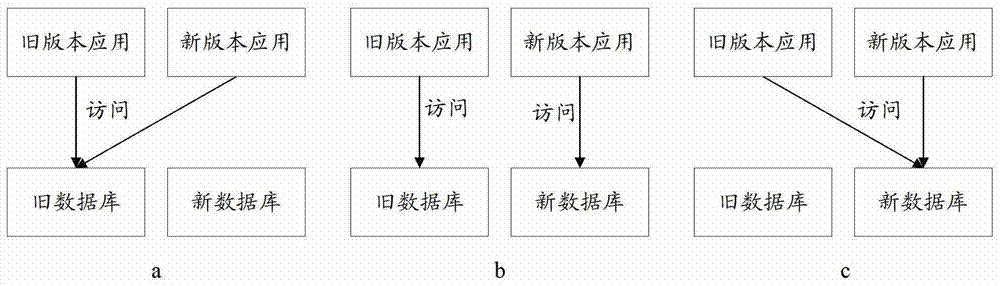
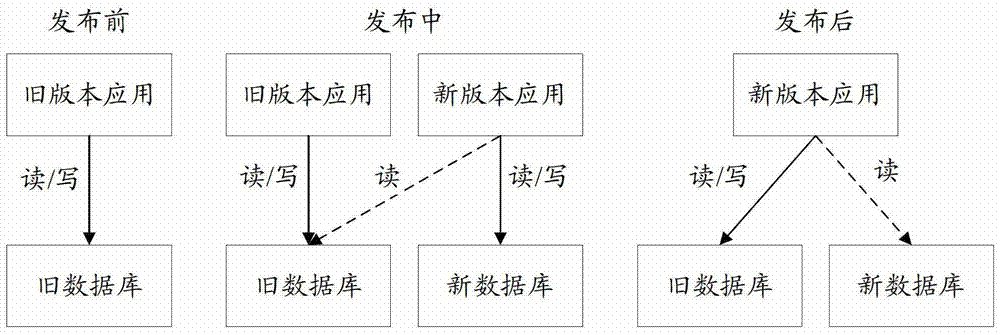
Data on-line migration method and device for updating applications in network platform
The invention provides a data on-line migration method and device for updating applications in a network platform in order to solve the problem that services fail to be executed in the prior art. The method includes the steps that at the first stage of updating, a new version application and an old version application are run simultaneously, and the new version application and the old version application have access to an old database in the running process; the first stage of updating is finished, data in the old database are all synchronized to a new database, the second stage of updating is carried out, the new version application and the old version application are run simultaneously, the new version application has access to the new database in the running process, and the old version application has access to the old database; the second stage of updating is finished, the third step stage of updating is carried out, the new version application and the old version application are run simultaneously, and the new version application and the old version application have access to the new database in the running process; when the third stage of updating is finished, the new version application is run, and the new version application has access to the new database in the running process.
Owner:ADVANCED NEW TECH CO LTD
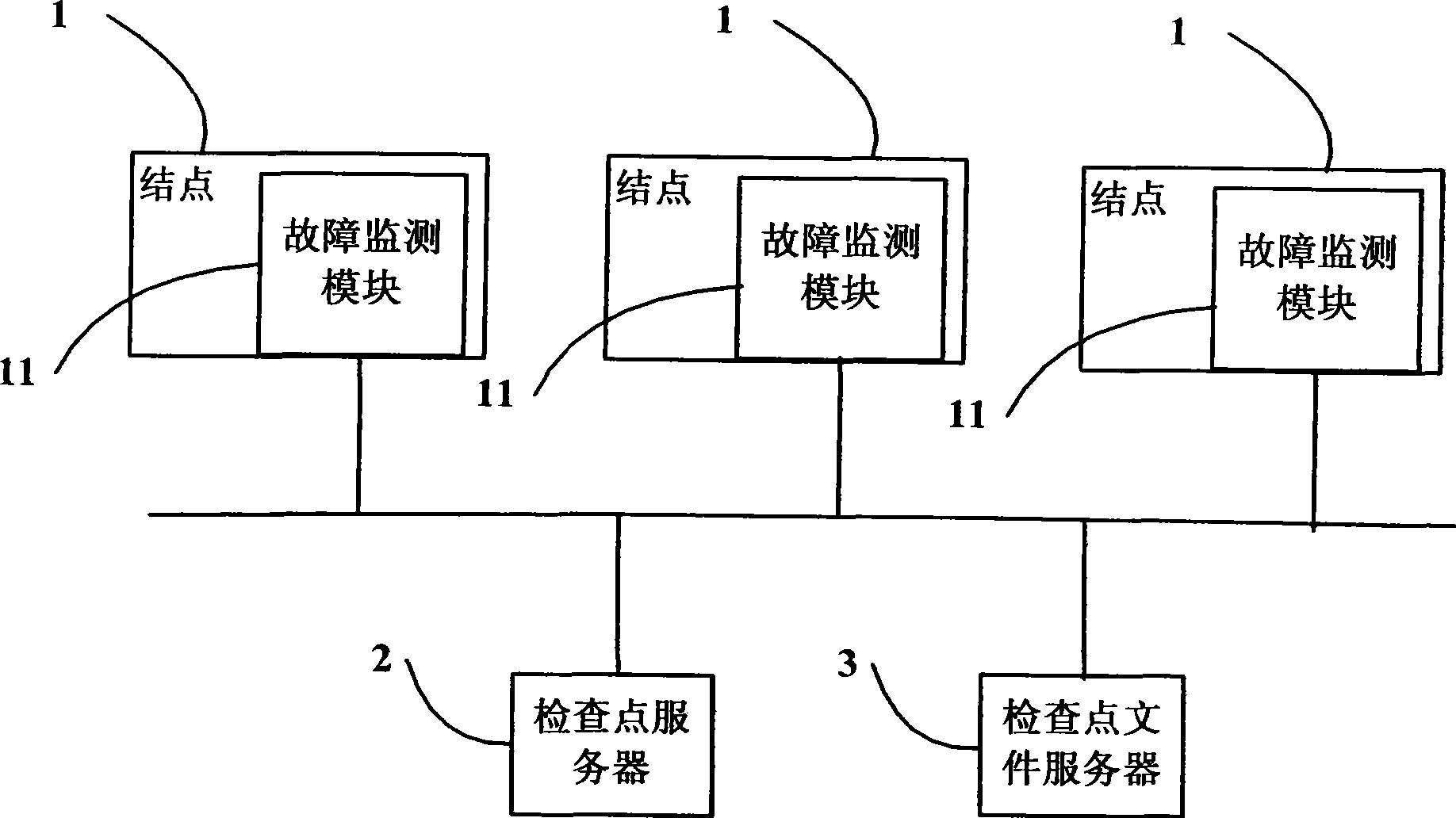
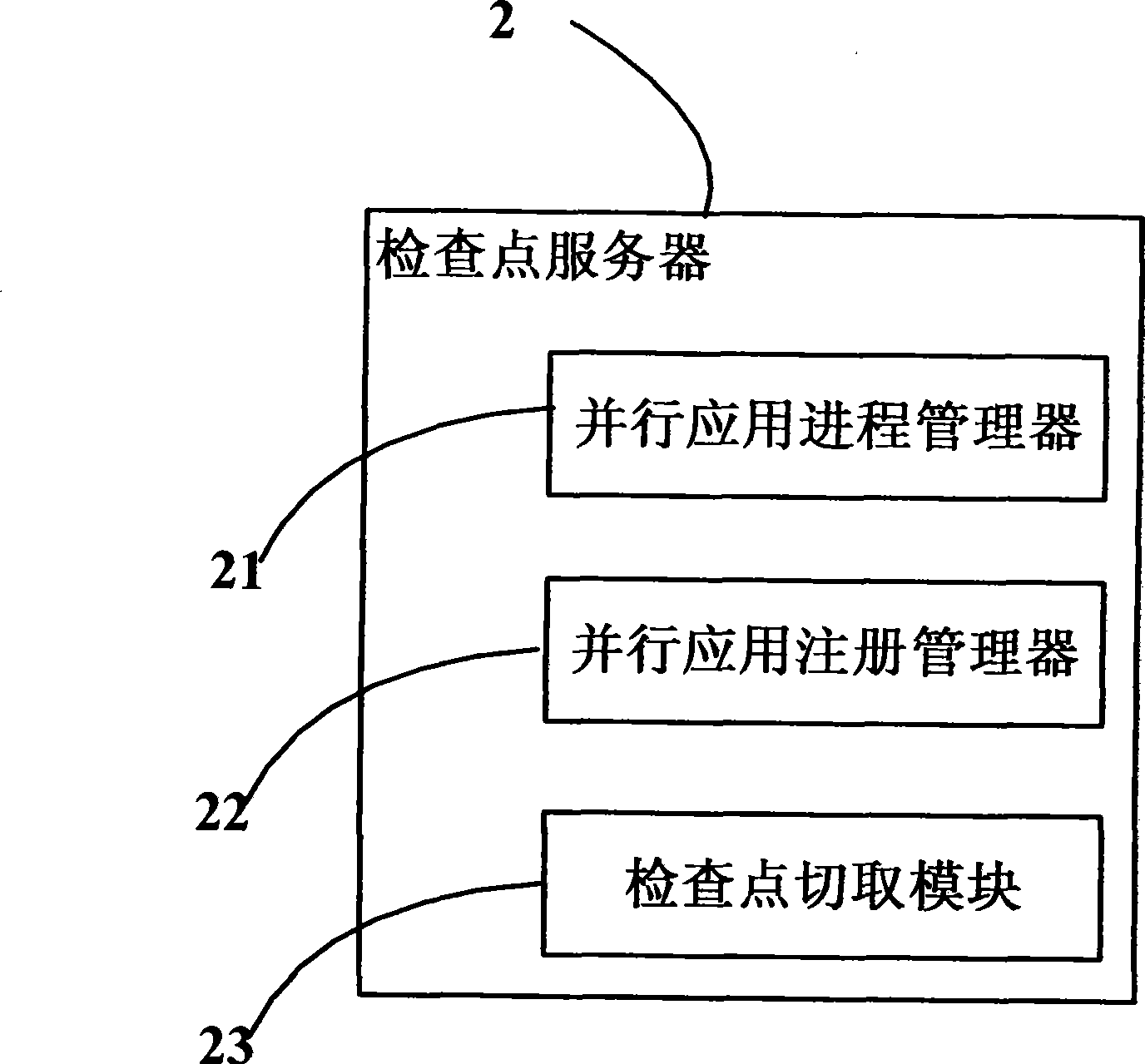
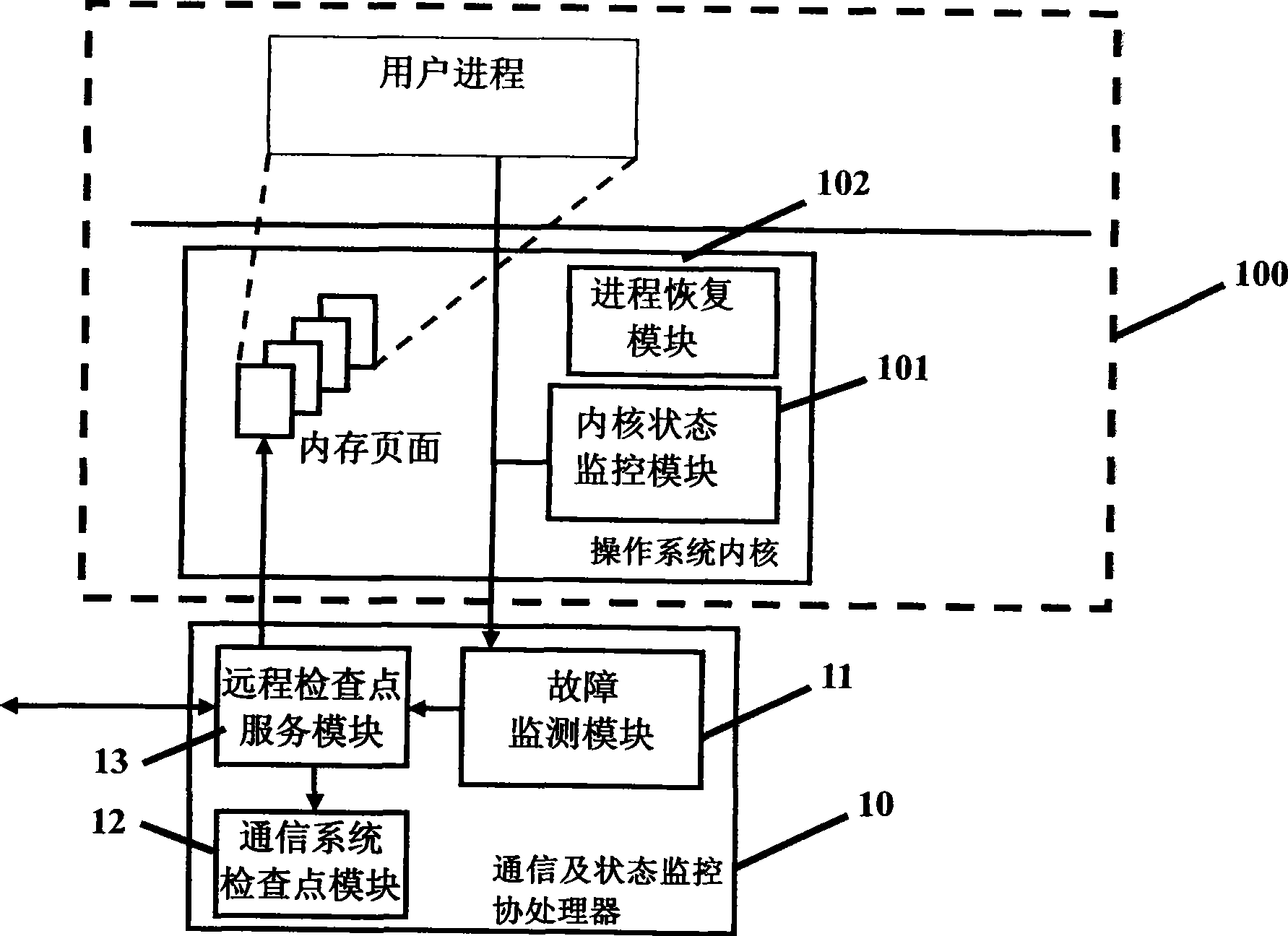
System and method for cluster fault toleration
ActiveCN101377750AAvoid performanceAvoid storage overheadRedundant operation error correctionFault toleranceOperational system
The invention discloses a system for cluster fault tolerance and a method thereof. The system comprises a checkpoint server which is connected with a plurality of nodes through networks and used for collecting information, which is applied in parallel, of all of processes, sending monitoring request to the nodes and responding to the checkpoint operation request from the nodes as well as saving checkpoint files on a checkpoint file server; on the completion of cutting operation of the checkpoints, the checkpoints are recovered; the checkpoint file server is connected with a plurality of nodes through networks, used for storing checkpoint files, and provides support for accessing checkpoint files during process recovery; a fault monitoring module is arranged on the nodes, and used for monitoring the running status of the operation systems of the local nodes and the specified running status of the specified process in the monitor request, and the specified status of the specified hardware components in the monitoring request according to the monitoring request, as well as sending checkpoint operation request to the checkpoint server when faults are monitored.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
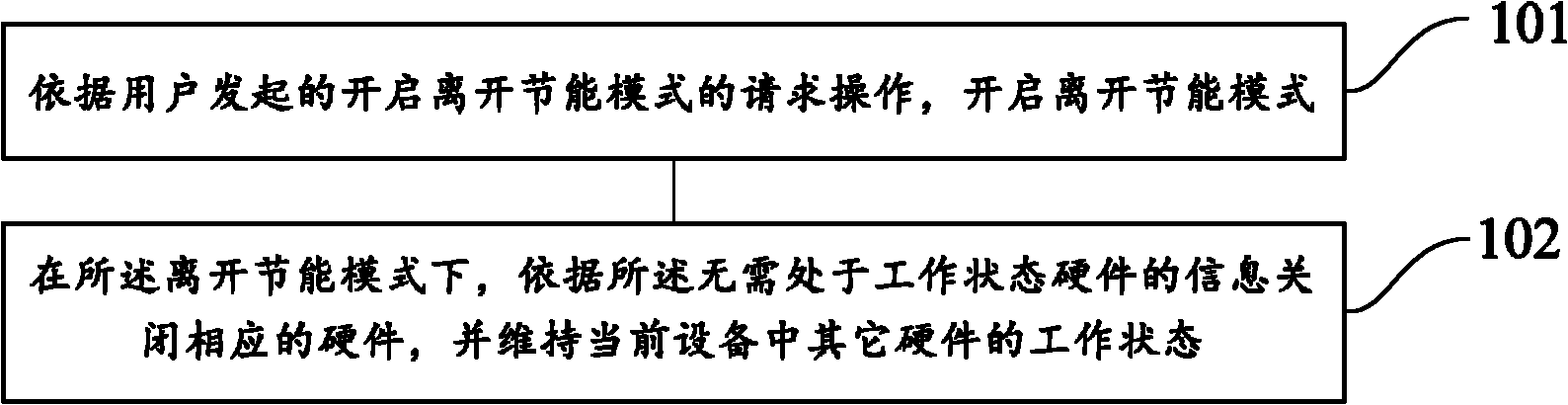
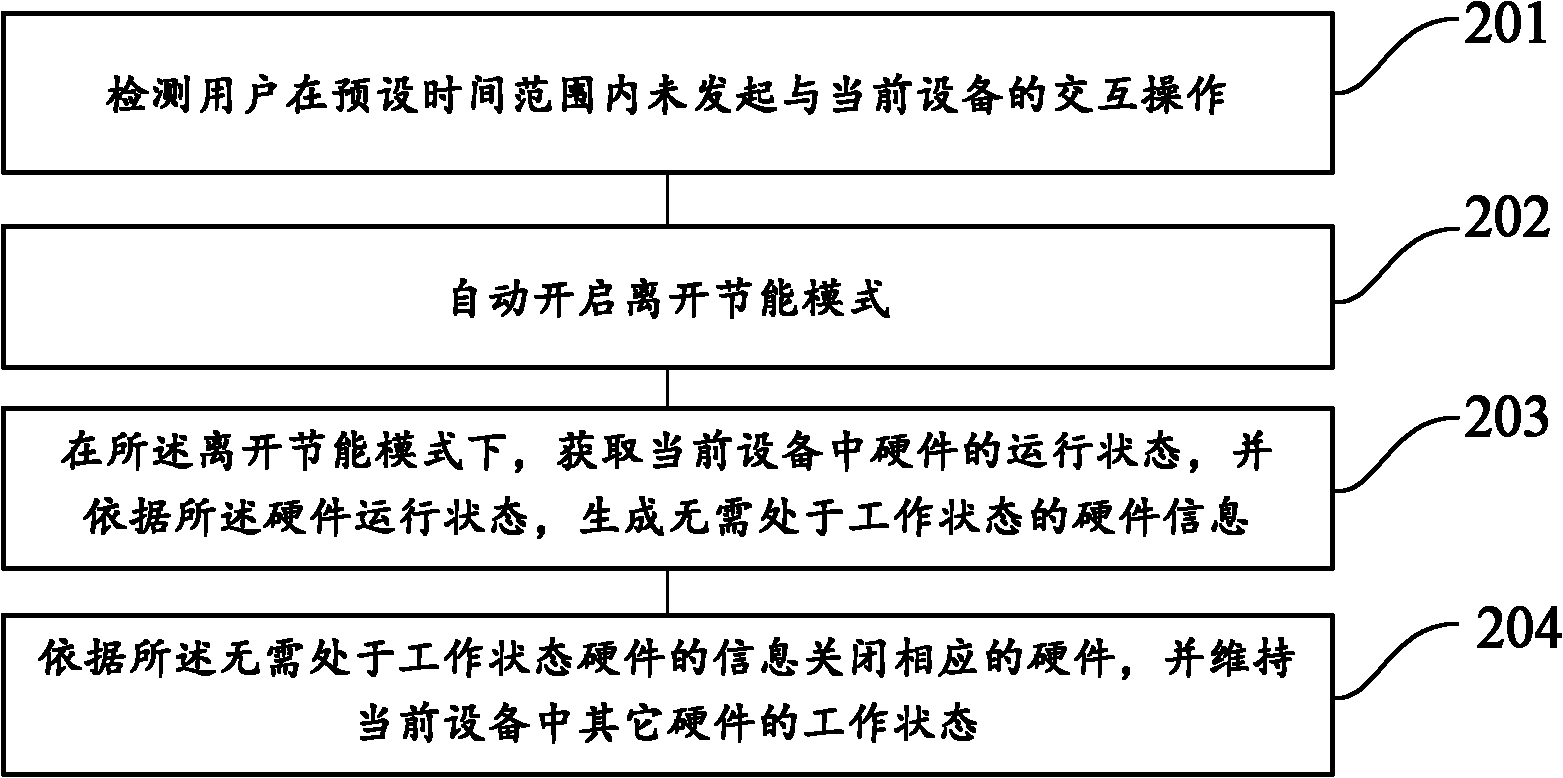
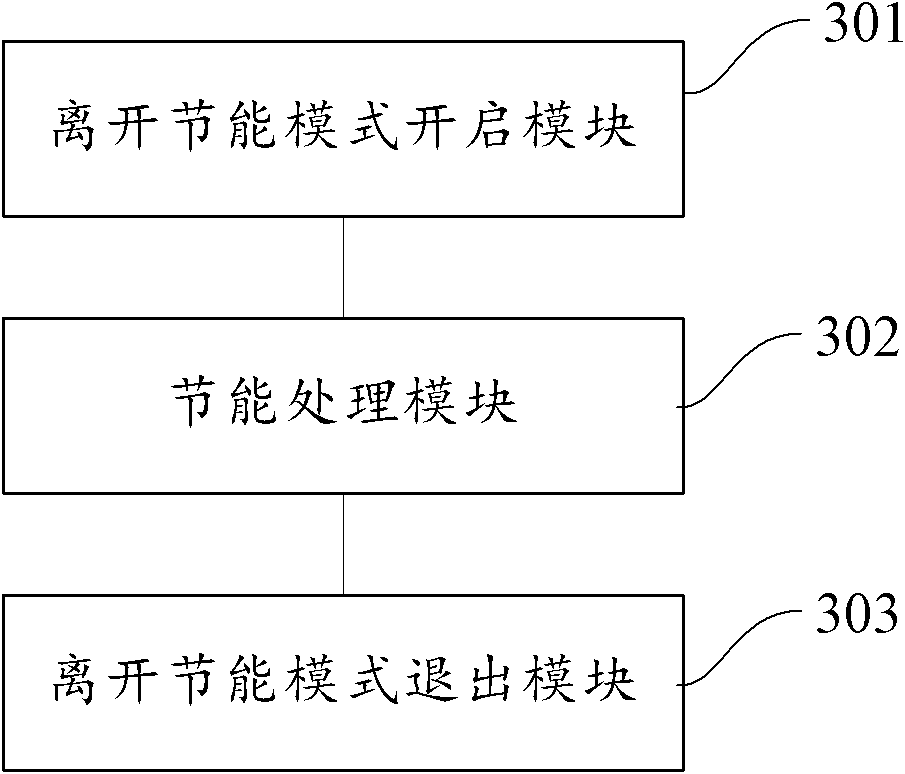
Hardware energy-saving processing method and device
InactiveCN102156534AExtended service lifeGuaranteed normal executionPower supply for data processingWork statusEmbedded system
The invention provides a hardware energy-saving processing method. The method comprises the following steps: starting an off energy-saving mode; in the off energy-saving mode, closing hardware which is unnecessary in a working state in the current equipment, and maintaining the working state of other hardware in the current equipment. By the method and the device, electric energy can be saved as much as possible on the basis of ensuring user task execution.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
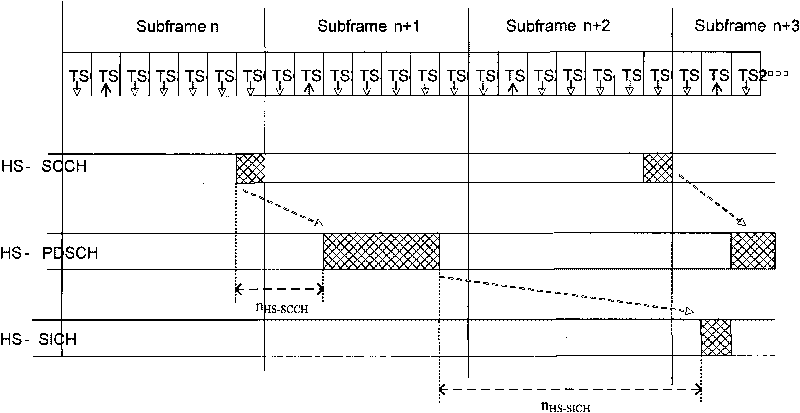
Resource allocation method and resource using method, device and system
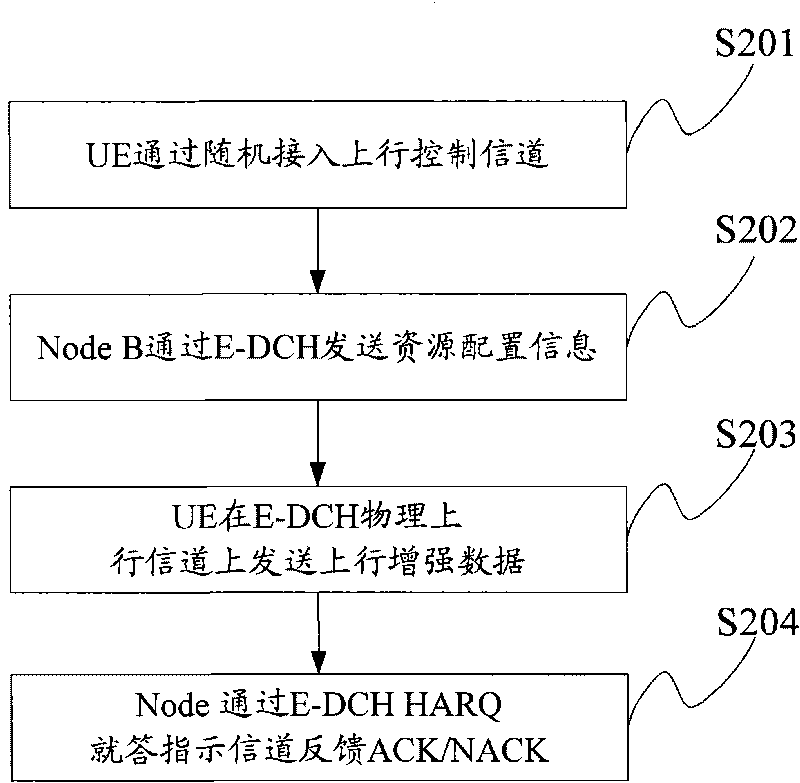
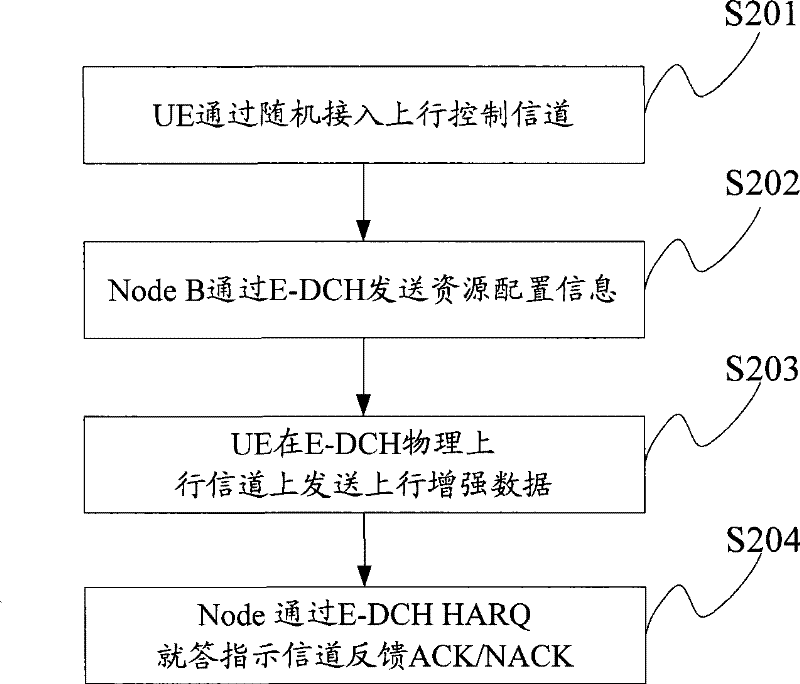
ActiveCN101742656AWill not affect executionFlexible resource allocationForward error control useData switching networksControl channelUser equipment
The embodiment of the invention discloses a resource allocation method, which comprises the following steps of: setting a corresponding relation between a predefined control channel format and a preset resource type; and when allocating the resource of the preset resource type to target user equipment (UE), transmitting resource allocation information according to a corresponding newly defined control channel format, and indicating the predefined control channel format to the target UE so that the target UE correctly acquires the resource allocation information and uses the resource designated by the resource allocation information according to a using method corresponding to the preset resource type. The embodiment of the invention also provides a resource using method and a device and a system for implementing the method. In the resource allocation method, the resource configuration information is flexibly set as required and the control channel format is indicated to the UE by establishing the corresponding relation between the control channel format and the resource type, thus semi-persistent resources can be allocated to the UE, the time of transmitting the resource allocation information is reduced, and the system overhead is saved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Multi-domain RBAC (Role-Based Access Control) model-based access control policy composition method
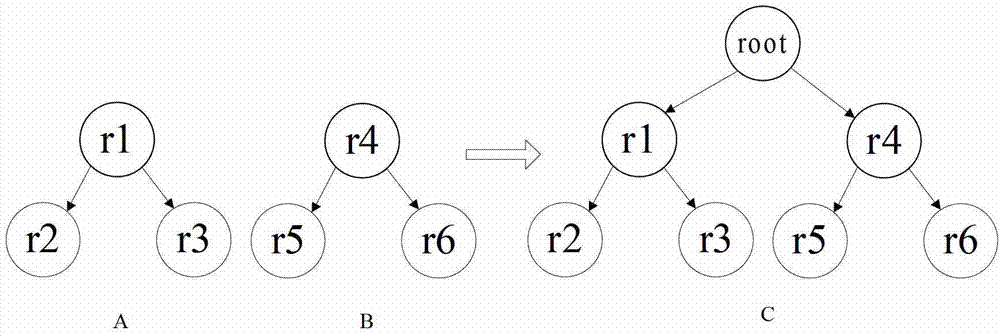
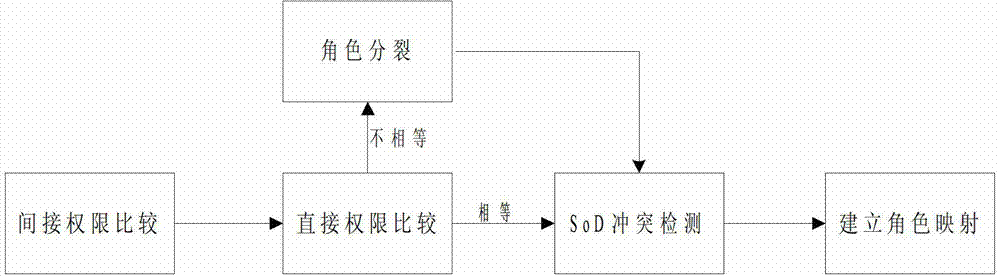
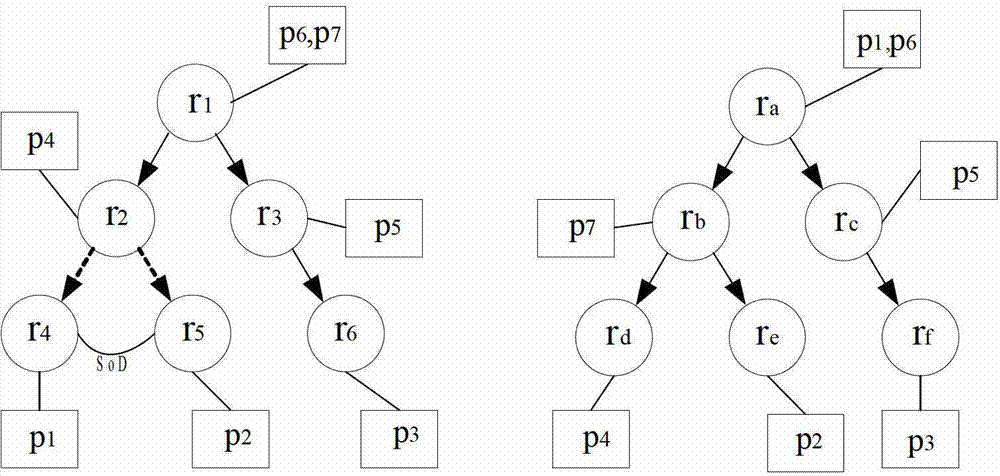
A multi-domain RBAC model-based access control policy composition method includes the following steps: tree merge is carried out in a single domain, indirect permission sets of roles, i.e. A inherited permission set and I inherited permission set, are then calculated, finally, the permission sets of the inter-domain rolles are recursively compared, the roles to be divided are determined, inter-domain role mapping is established, and a global access policy is generated. The multi-domain RBAC model-based access control policy composition method inputs the RBAC policies of multiple domains to be composed as a method, establishes inter-domain role mapping sets according to the role permission assignment relations, the role hierarchies and the inter-role SOD (Separation of Duties) constraints in the original domains, and generates and outputs a global access control policy.
Owner:SHANGHAI JIAO TONG UNIV
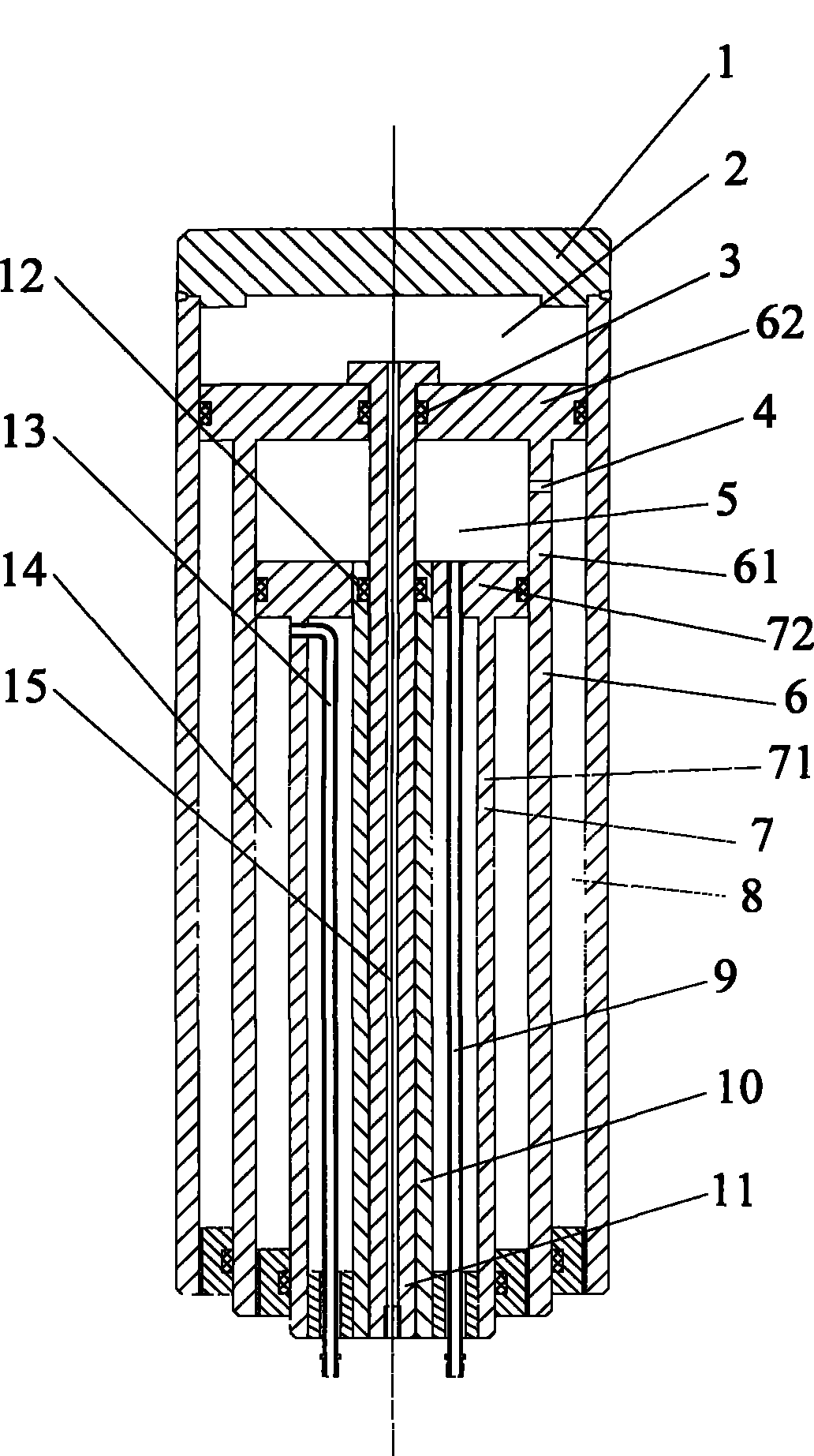
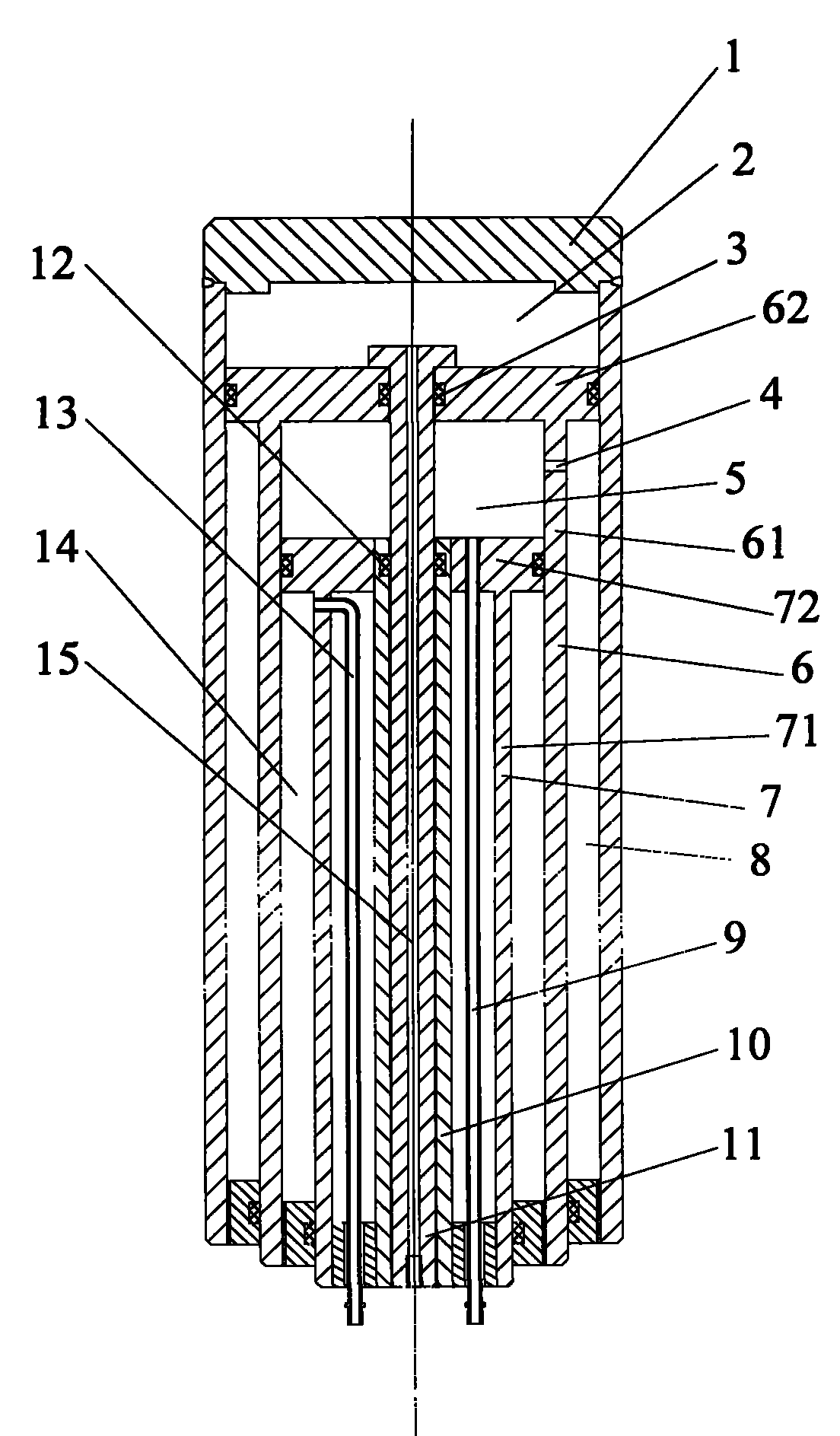
Multi-stage oil cylinder and hydraulic device with same
ActiveCN101900150AReduce in quantityOptimize layoutFluid-pressure actuatorsSingle stagePulp and paper industry
The invention provides a multi-stage oil cylinder and a hydraulic device with the same. The multi-stage oil cylinder comprises a primary cylinder barrel (1), a final-grade cylinder barrel (7) sleeved in the primary cylinder barrel (1) and single-stage or multi-stage middle cylinder barrels (6) sleeved between the primary cylinder barrel (1) and the final-stage cylinder barrel (7) in turn, wherein the cylinder barrels (7) of all stages except the primary cylinder barrel (1) all comprise cylinder barrel parts (61, 71) and piston parts (62, 72) arranged at inner side ends of the cylinder barrel parts (61, 71); a rodless cavity of the primary cylinder barrel (1) is communicated with a rodless cavity oil duct (15) communicated with the outside; a rod cavity of the middle cylinder barrel (6) of a previous stage of the final-stage cylinder (7) is communicated with a rod cavity oil duct (13) communicated with the outside; and a side oil duct (4) is formed on a barrel wall of the middle cylinder barrel (6) and communicated with the rodless cavity of the middle cylinder barrel (6) and the rod cavity of the previous-stage cylinder barrel (1). The multi-stage oil cylinder and the hydraulic device with the same have the advantages of simple structure, convenient processing and capability of bearing heavier work load.
Owner:SANY AUTOMOBILE HOISTING MACHINERY
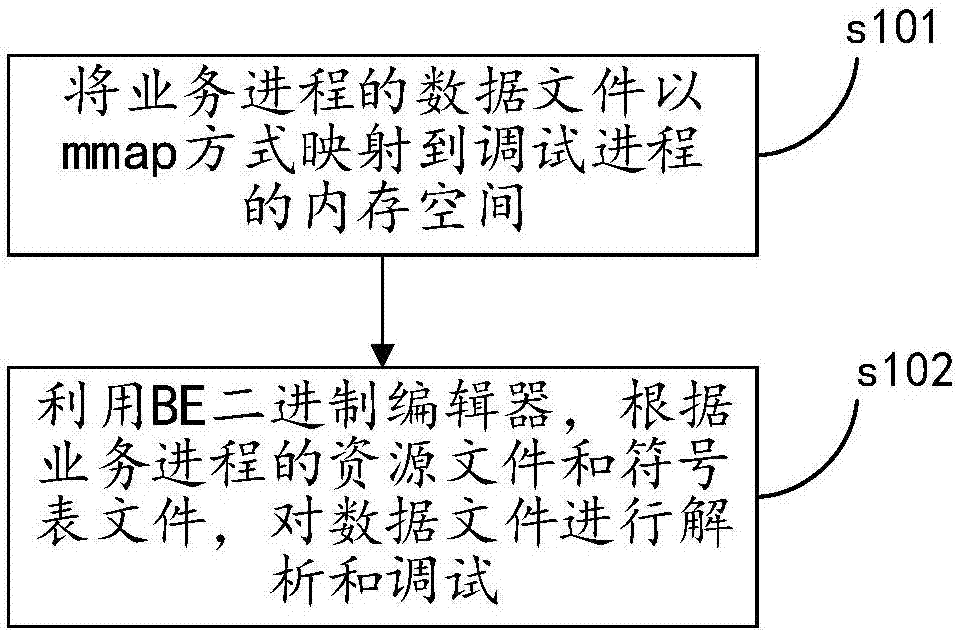
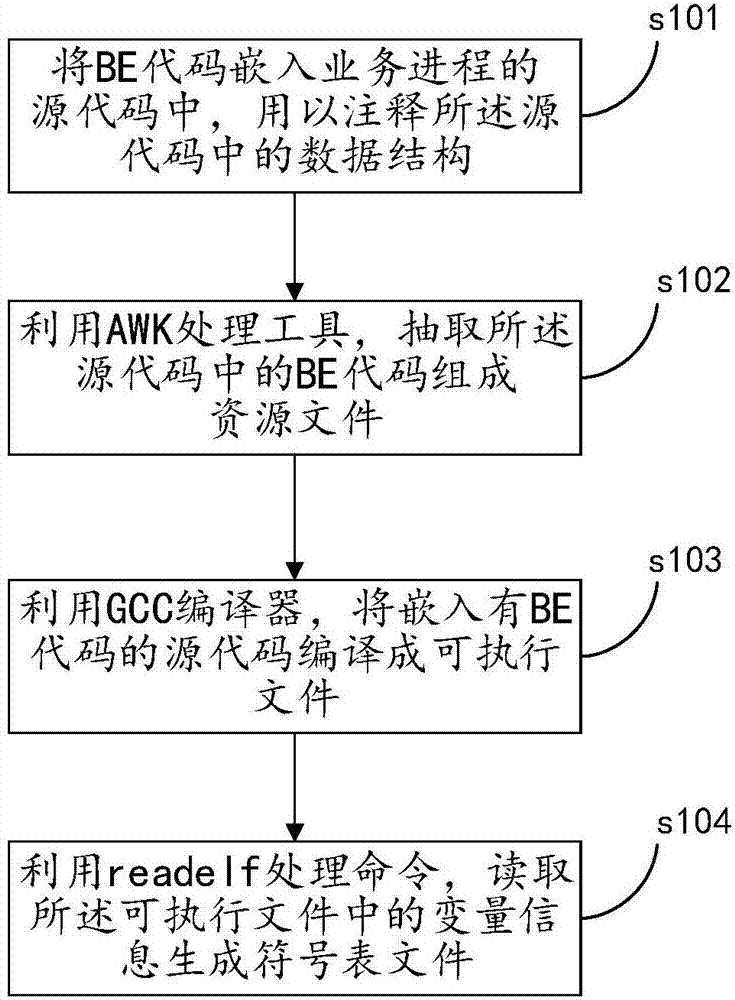
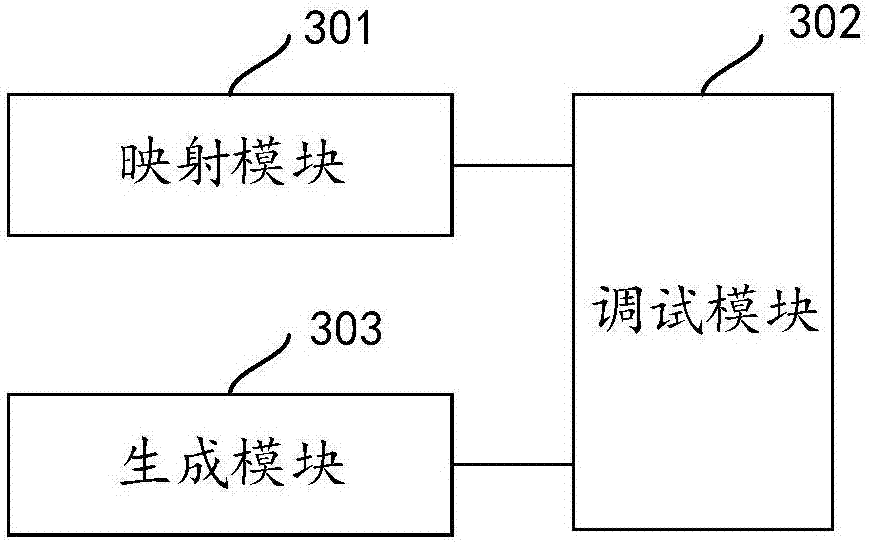
Program debugging method and apparatus
InactiveCN107402885AWill not affect executionGuaranteed execution efficiencySoftware testing/debuggingMmapData file
The invention discloses a program debugging method. The program debugging method comprises the steps of mapping data files of a business process to a memory space of a debugging process in an mmap manner; and parsing and debugging the data files according to resource files and symbol table files of the business process by utilization of a BE binary editor, wherein the resource files and the symbol table files are generated during a compilation process of the business process in advance. By mapping the data files of the business process to the debugging process, the data files can be parsed to complete debug according to the resource files and the symbol table files without influencing execution efficiency of the business process. The invention also discloses a program debugging apparatus having the above beneficial effect.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
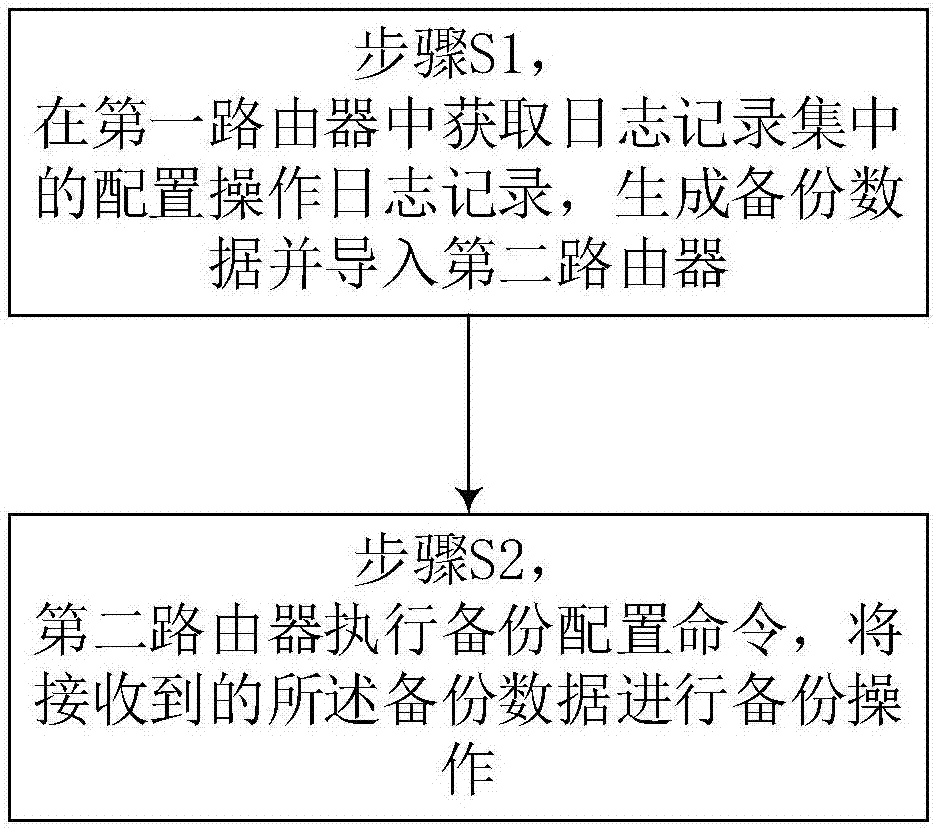
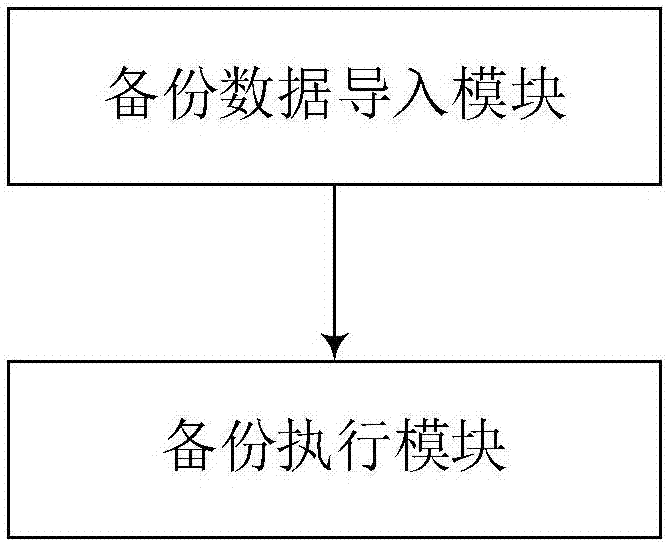
Data backup method among routers and system thereof
InactiveCN107453920AReduce the differenceWill not affect executionData switching networksConfiguration itemSoftware
A data backup method among routers and a system thereof belong to the communication field. The method comprises the following steps that stepS1, a configuration operation log record in a log record set is acquired in a first router, and backup data is generated and imported into a second router; and step S2, the second router executes a backup configuration command and carries out backup operation on the received backup data. A purpose of the invention is to change backup contents and a final configuration item is changed to the backup configuration command. A process of backup recovery is actually a process of issuing a configuration command to the router again. Differences between different models and different software versions are reduced. When the router does not support the command, implementation of other normal commands is not influenced, so that data backup can be performed among the routers with the different models and the different software versions.
Owner:台州市吉吉知识产权运营有限公司
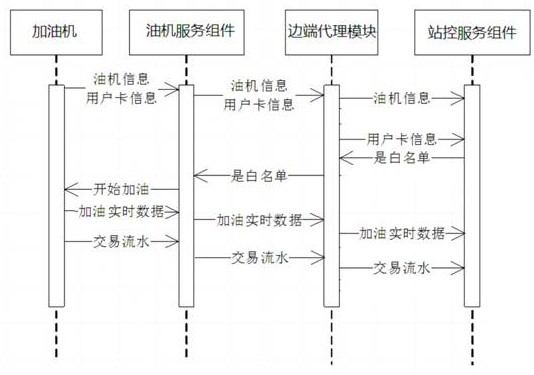
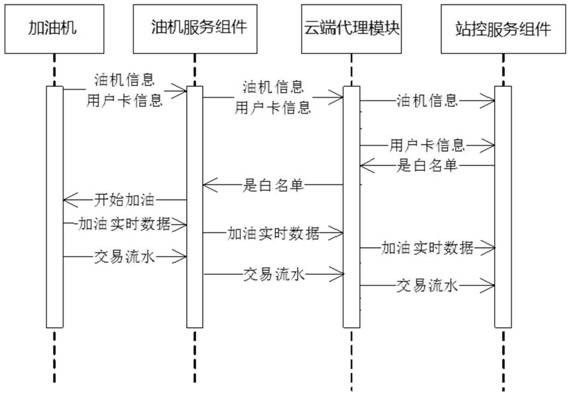
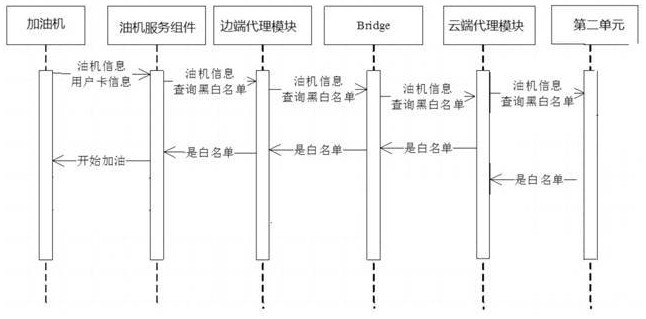
Edge cloud collaborative management and control system and method
ActiveCN113114716AWill not affect executionIncrease elasticityData switching networksTotal factory controlData synchronizationControl system
The invention discloses an edge cloud collaborative management and control system and method. The system comprises a cloud subsystem and an edge subsystem. The side end subsystem comprises a side end agent module and a plurality of side end service components; the side end agent module is respectively in signal connection with the cloud subsystem and each side end service component, and each side end service component is also in signal connection with the cloud subsystem; when the side end agent module works normally, the side end service components communicate with one another through the side end agent module, and the side end agent module also collects communication data of the side end service components and synchronizes the communication data to the cloud subsystem; when the side end agent module works abnormally, the side end service components communicate with one another through the cloud subsystem, and the cloud subsystem stores corresponding communication data. According to the invention, when the side end agent module fails, the side end service components interact through the cloud subsystem, so that the normal operation of the business is ensured, and the business flexibility is improved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
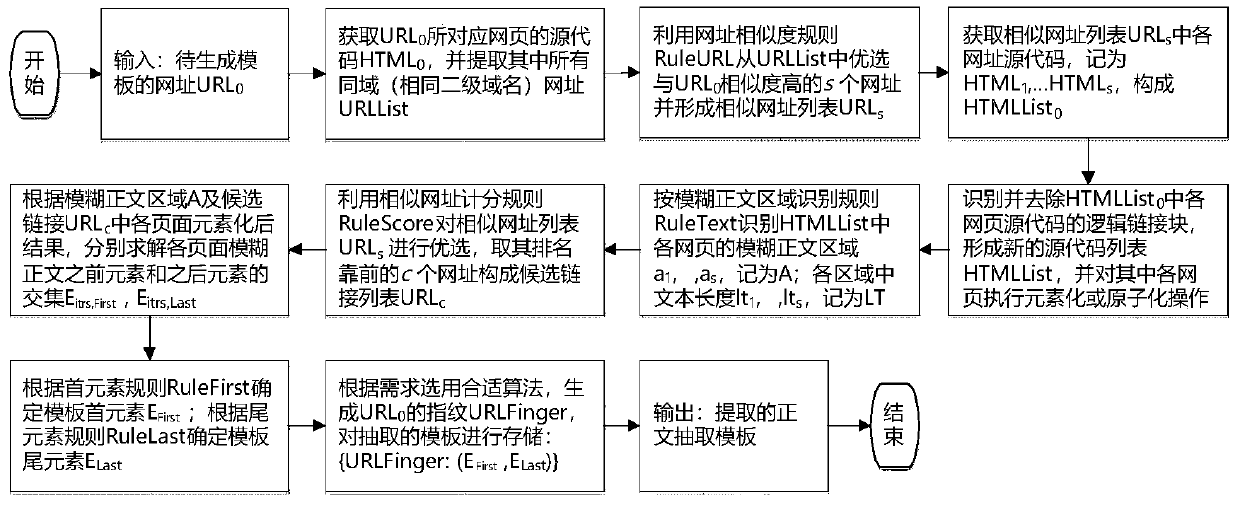
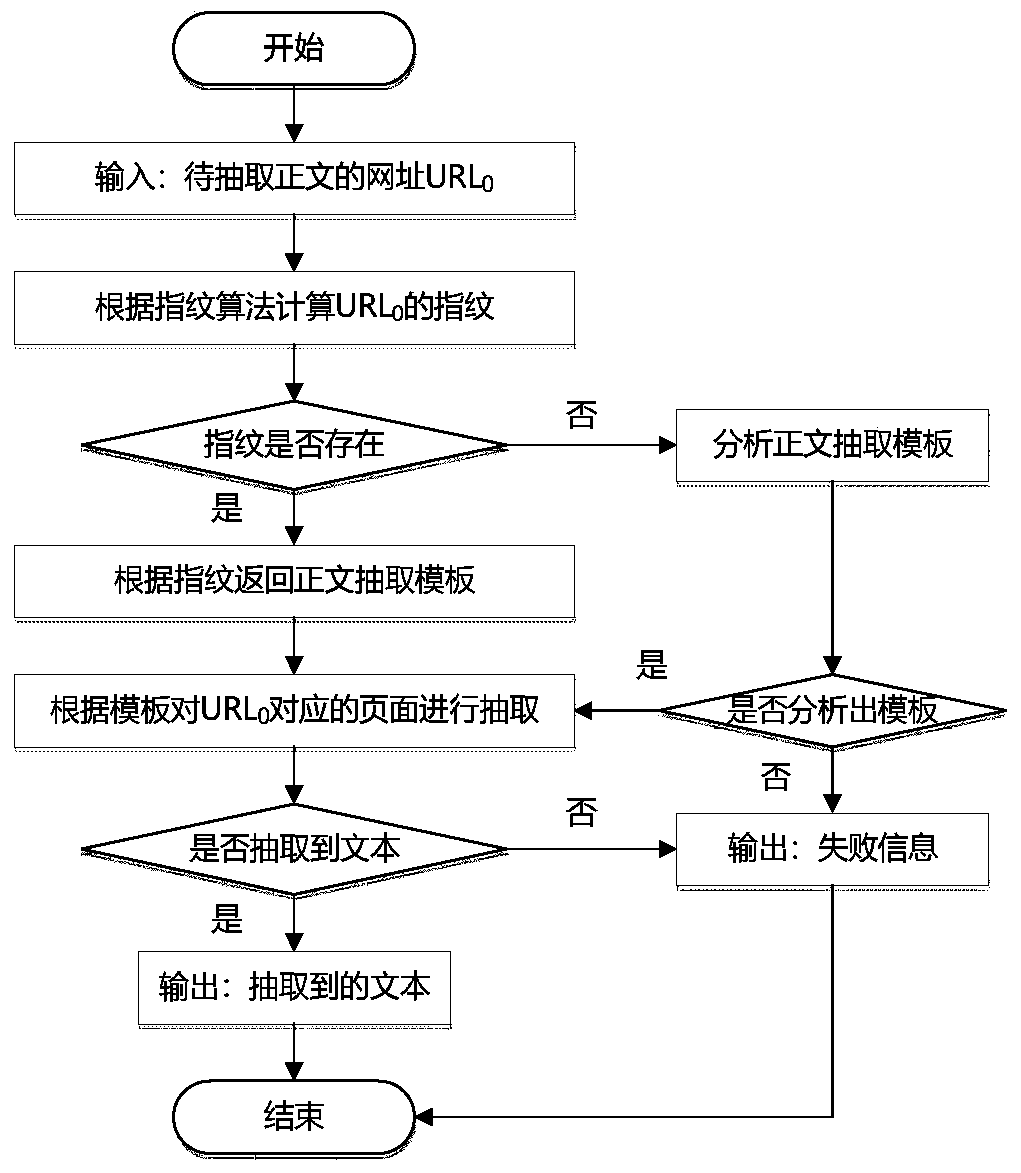
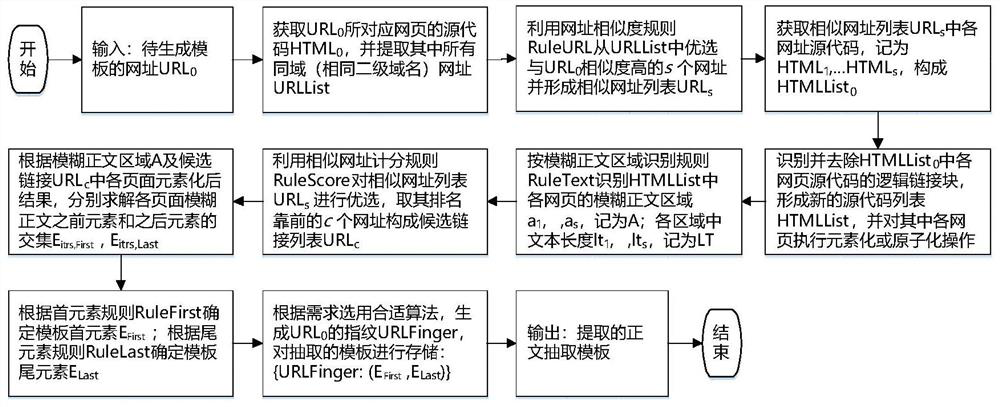
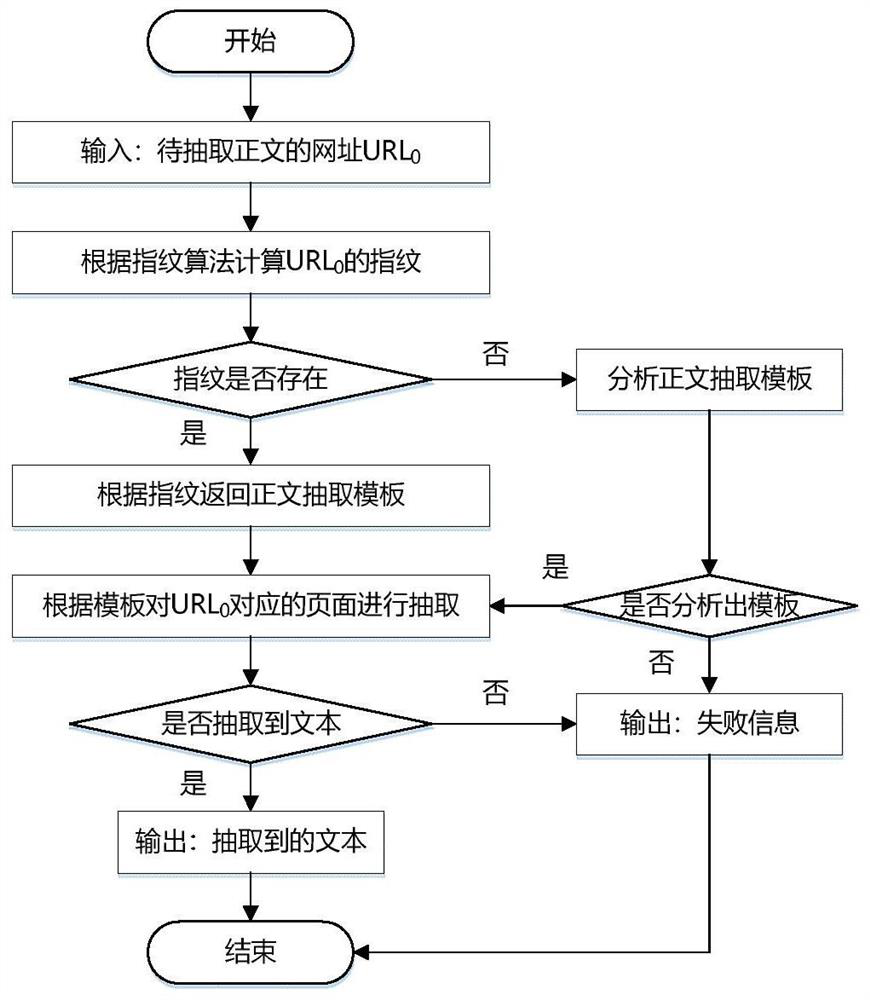
A webpage text extraction method based on a logic link block
ActiveCN109740097AImprove recallImprove accuracyWebsite content managementInformation processingEngineering
The invention discloses a webpage text extraction method based on a logic link block, and the method only depends on the current webpage in the process of extracting a webpage template and a text, anddoes not need heuristic rule support, so that the method has good universality; the extraction process of the webpage template does not need manual intervention, and the automation degree is high; the analysis process is simple, and label analysis does not need to be carried out on the webpage, so that the analysis speed is high, the anti-interference performance is high, and the method can better adapt to a Web page with nonstandard design; the method also has a better extraction effect on pages with very short text contents; and finally, the template extracted by the method is simple in form and easy to use. Therefore, it is determined that the method has potential application value in the aspect of Web page text extraction, can be used for text extraction of various news, blogs or webpages with similar structures, and also has wide application prospects in other Web information processing and mining fields with low requirements for link block fine granularity.
Owner:WENZHOU UNIV OUJIANG COLLEGE
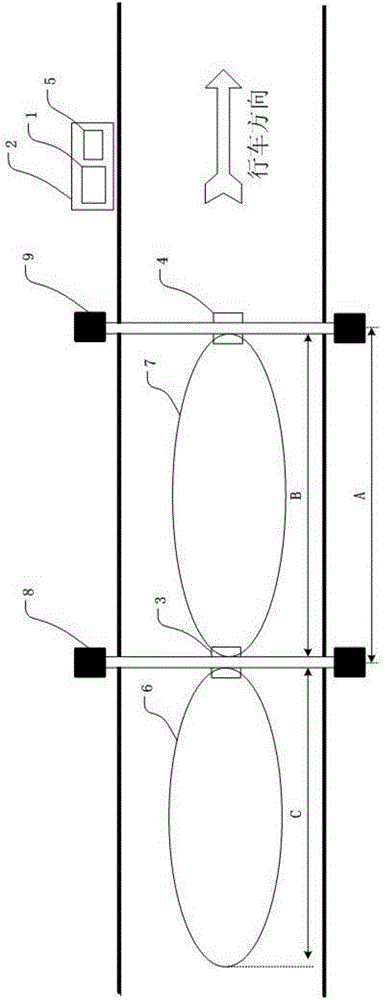
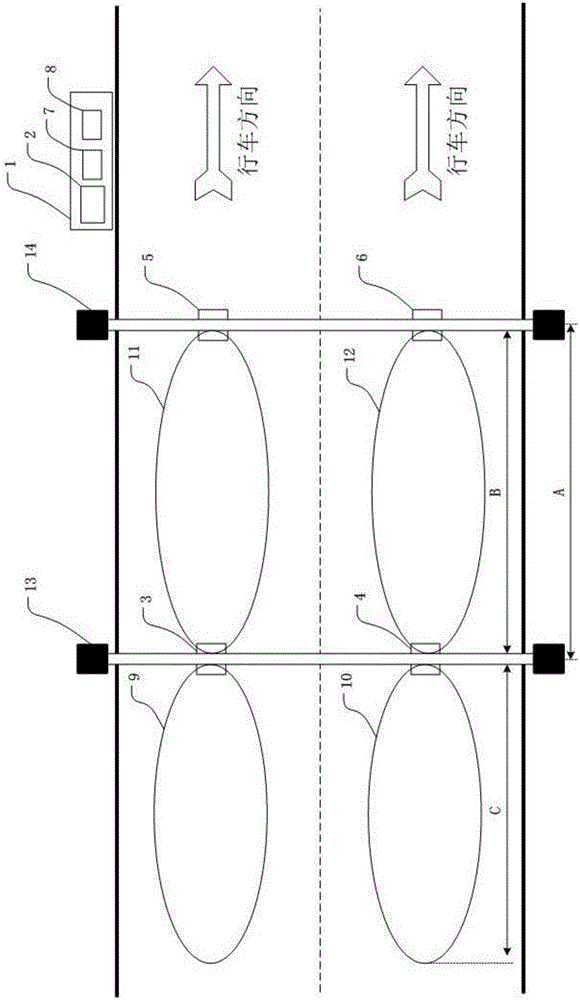
Free-flow electronic non-stop toll lane system and method based on continuous processing
ActiveCN103473820BIncrease time slackGuaranteed transaction success rateTicket-issuing apparatusMicrowaveIn vehicle
The invention discloses a free-flow electronic non-stop toll lane system and method based on continuous processing. The system includes a main control computer and a roadside read-write device, and the main control computer is connected with the roadside read-write device. The roadside reading and writing equipment includes one or more microwave antennas and an antenna controller connected with one or more microwave antennas, and the microwave antennas can project two or more communication areas on the lane. The method is that when the vehicle-mounted electronic tag only completes part of the transaction processing operation in one of the communication areas, the unfinished transaction processing operation of the vehicle-mounted electronic tag in the previous communication area can be continued in the next communication area, and the above-mentioned processing process vehicle Free-flow is possible, and even cross-lane traffic has no impact on handling. The electronic non-stop toll lane system of the present invention not only helps to improve the transaction success rate of the electronic tag, but also can be used in a high-speed free-flow environment.
Owner:GUANGZHOU HUAGONG INFORMATION SOFTWARE
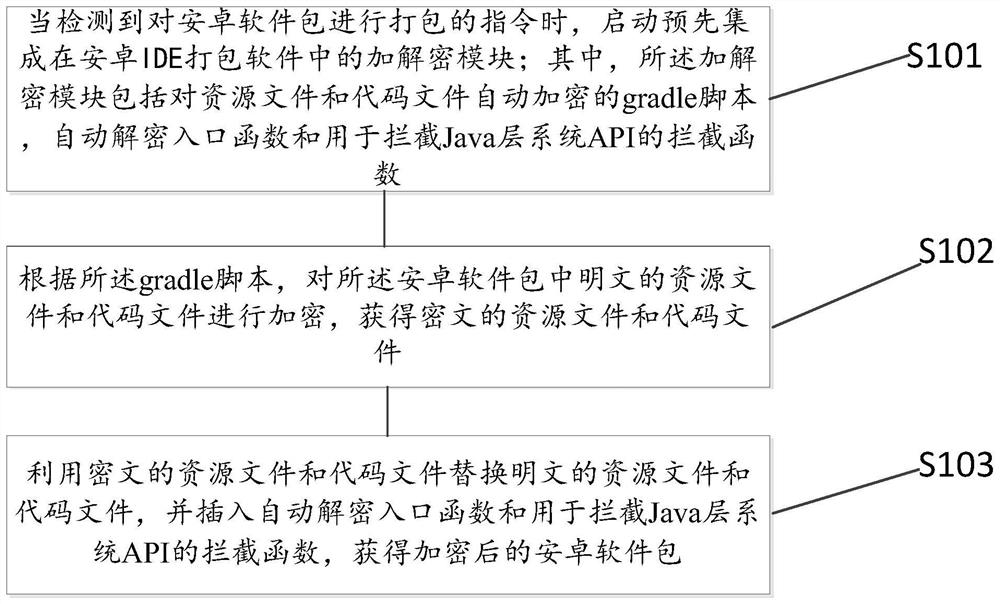
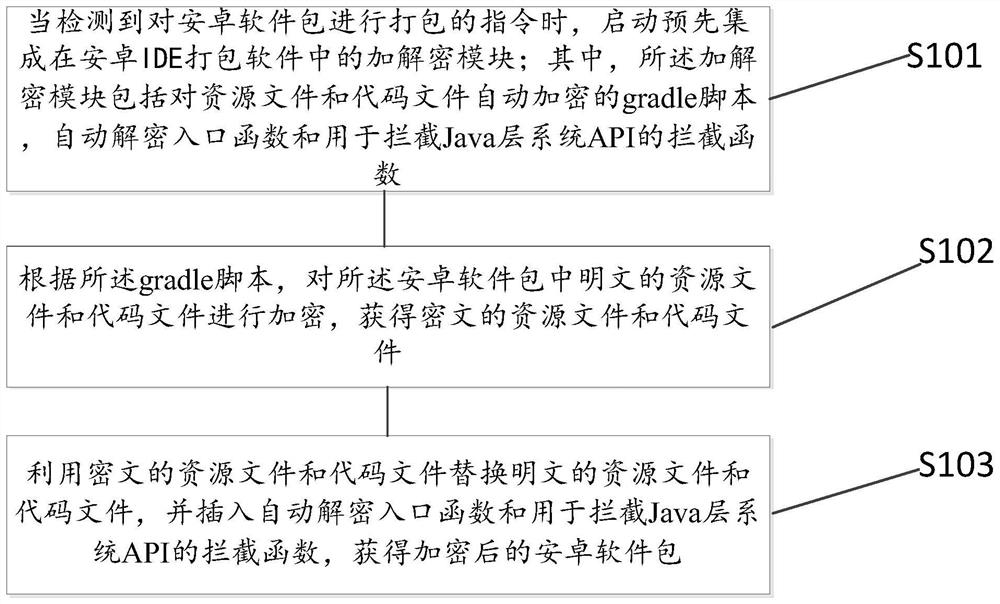
Android software package automatic encryption and decryption method, device and equipment and storage medium
PendingCN113961912ASupport encryptionImprove securityDigital data information retrievalDigital data protectionPlaintextCiphertext
The embodiment of the invention provides an Android software package automatic encryption and decryption method, device and equipment and a storage medium, and the method comprises the steps: starting an encryption and decryption module which is pre-integrated in Android IDE packaging software when an instruction for packaging the Android software package is detected, wherein the encryption and decryption module comprises a gradle script for automatically encrypting a resource file and a code file, an automatic decryption entry function and an interception function for intercepting a Java layer system API (Application Program Interface); encrypting a plaintext resource file and a plaintext code file in the Android software package according to the gradle script, and inserting an automatic decryption entry function and an interception function for intercepting a Java layer system API (Application Program Interface) to obtain a plaintext resource file and a plaintext code file; and replacing the plaintext resource file and the plaintext code file with the ciphertext resource file and the plaintext code file to obtain an encrypted Android software package. According to the invention, the security and convenience of encryption and decryption of the installation software package can be improved.
Owner:厦门市易联众易惠科技有限公司
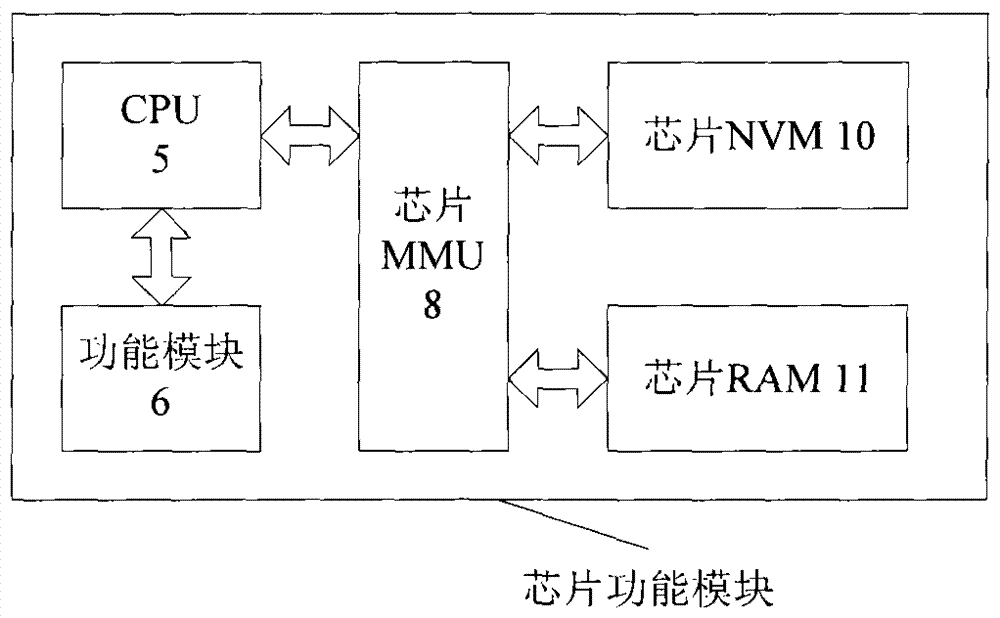
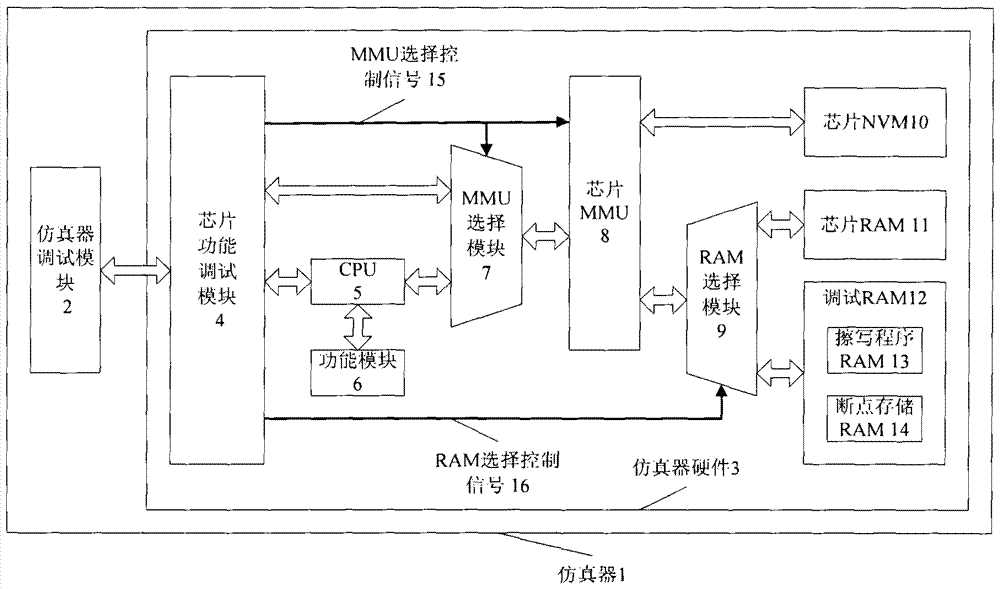
An emulator and method supporting nvm soft breakpoint debugging
ActiveCN104461859BFast operationWill not affect executionSoftware testing/debuggingParallel computingBackup
The invention introduces an emulator and method supporting NVM soft breakpoint debugging, and relates to the technical field of chip emulation. The emulator includes an emulator debugging module and emulator hardware. The emulator hardware mainly includes modules such as a chip function debugging module, a CPU, a chip MMU, a chip NVM, a chip RAM, and a debugging RAM. The emulator debugging module writes the erasing program and breakpoint data into the erasing program RAM and breakpoint storage RAM of the debugging RAM respectively, and backs up the code of the chip NVM breakpoint address to the breakpoint storage RAM according to the breakpoint data, and controls The CPU executes the erasing program to write the code of the NVM breakpoint address as a breakpoint instruction to realize the breakpoint setting function; change the chip NVM breakpoint instruction back to the breakpoint storage RAM backup code to realize the breakpoint clearing function.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
APP integrity checking method based on UDS-FBL
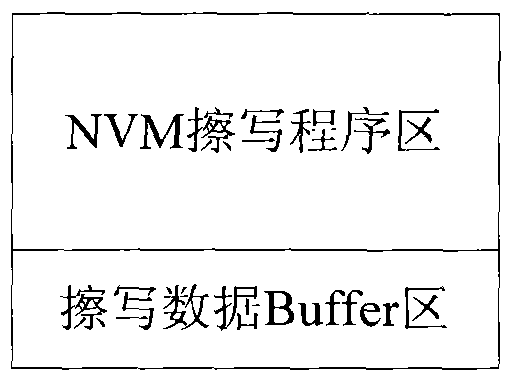
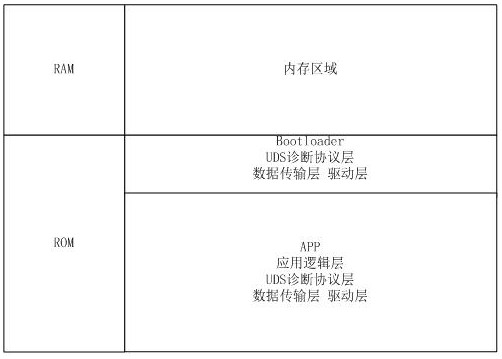
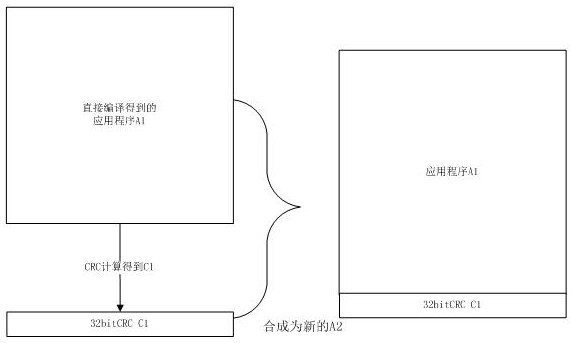
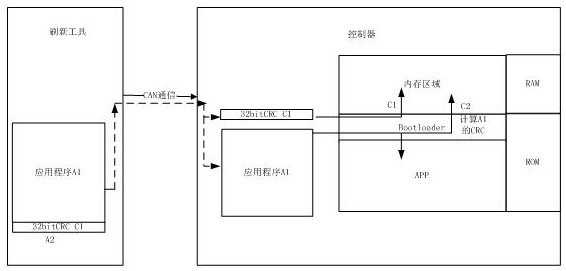
PendingCN114741737AWill not affect executionDigital data protectionPlatform integrity maintainanceSoftware engineeringApplication procedure
The invention discloses an APP integrity checking method based on UDS-FBL. The method comprises the following steps: sending a request message related to flashing through a UDS unified diagnosis service; the method comprises the following steps of: generating and downloading a bootloader program and binary data corresponding to an application program, storing the bootloader program and the binary data in an ROM (Read Only Memory) space of a controller, entering a Bootloader programming mode, receiving FALSHDRIVER downloaded through diagnosis service, then erasing the application program through the FALSHDRIVER, writing an effective flag bit of the application program as invalid by the Bootloader program, and erasing a region corresponding to the application program in the ROM space; writing the new binary data of the application program into the ROM space corresponding to the application program; and the Bootloader program performs integrity verification on the new application program, if the verification is successful, the validity of the new application program is set to be valid, and the controller restarts and enters the new application program.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
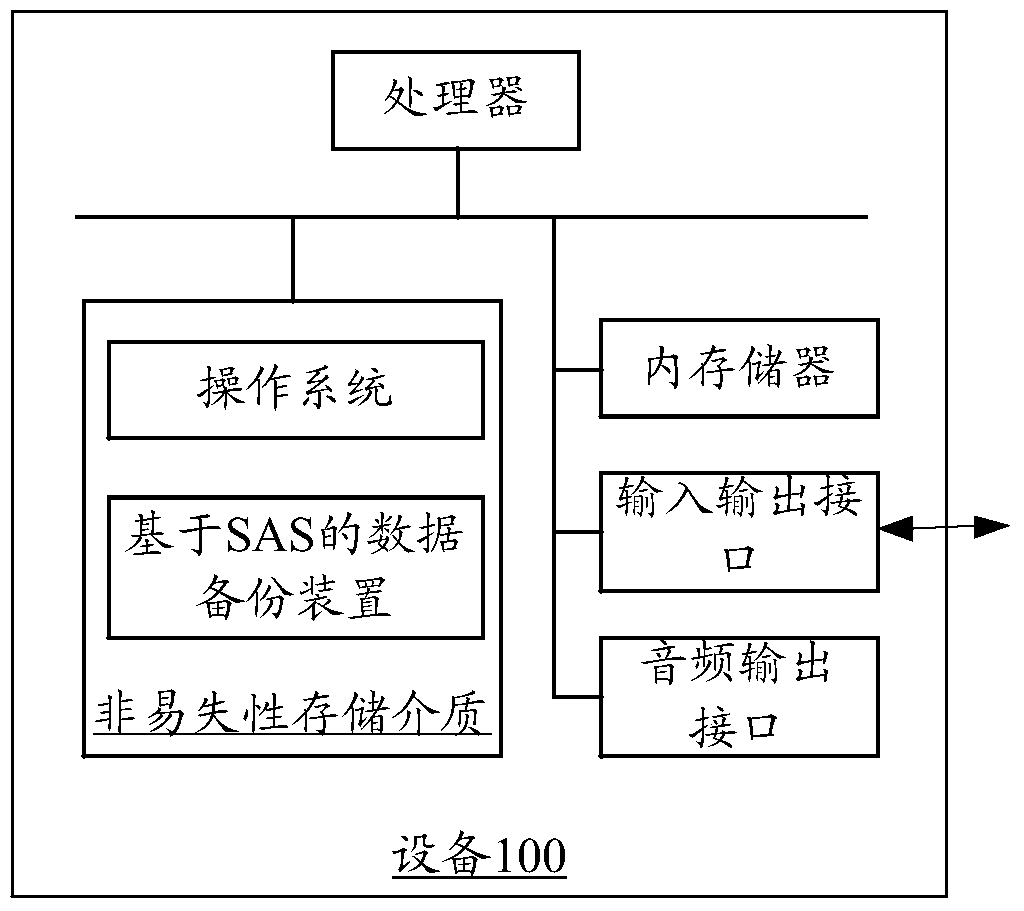
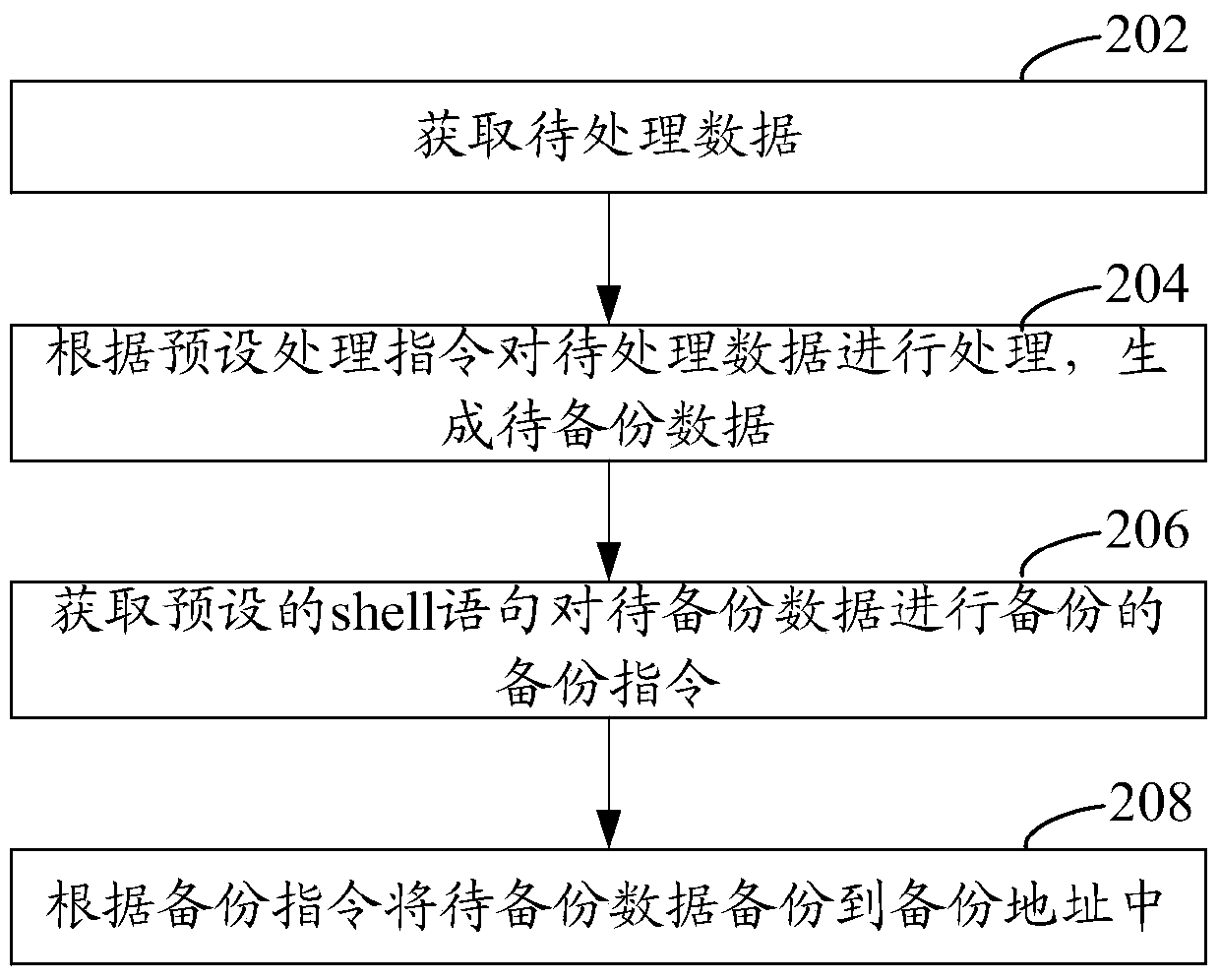
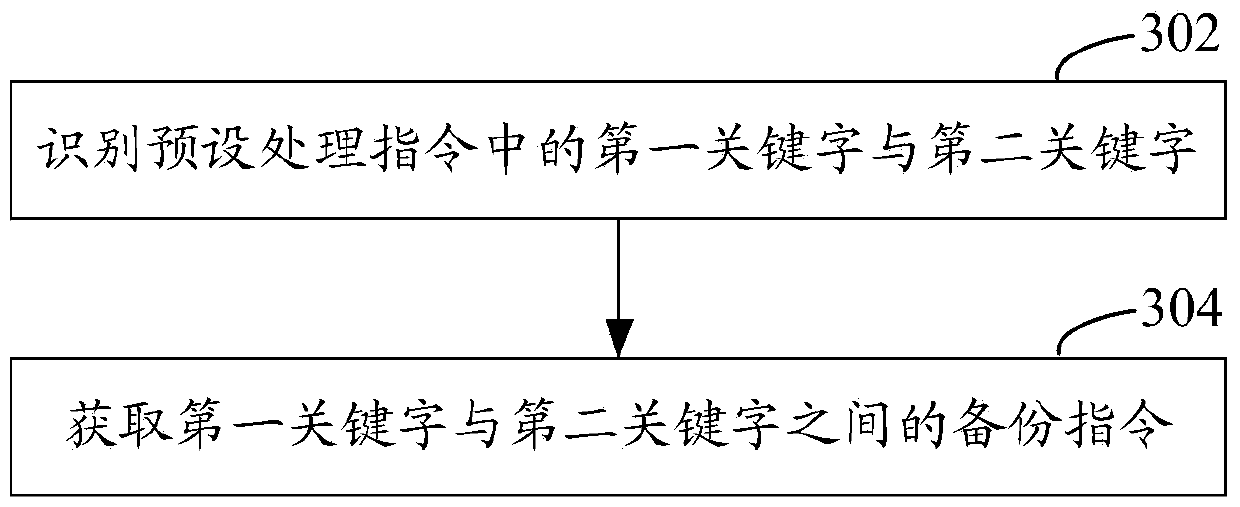
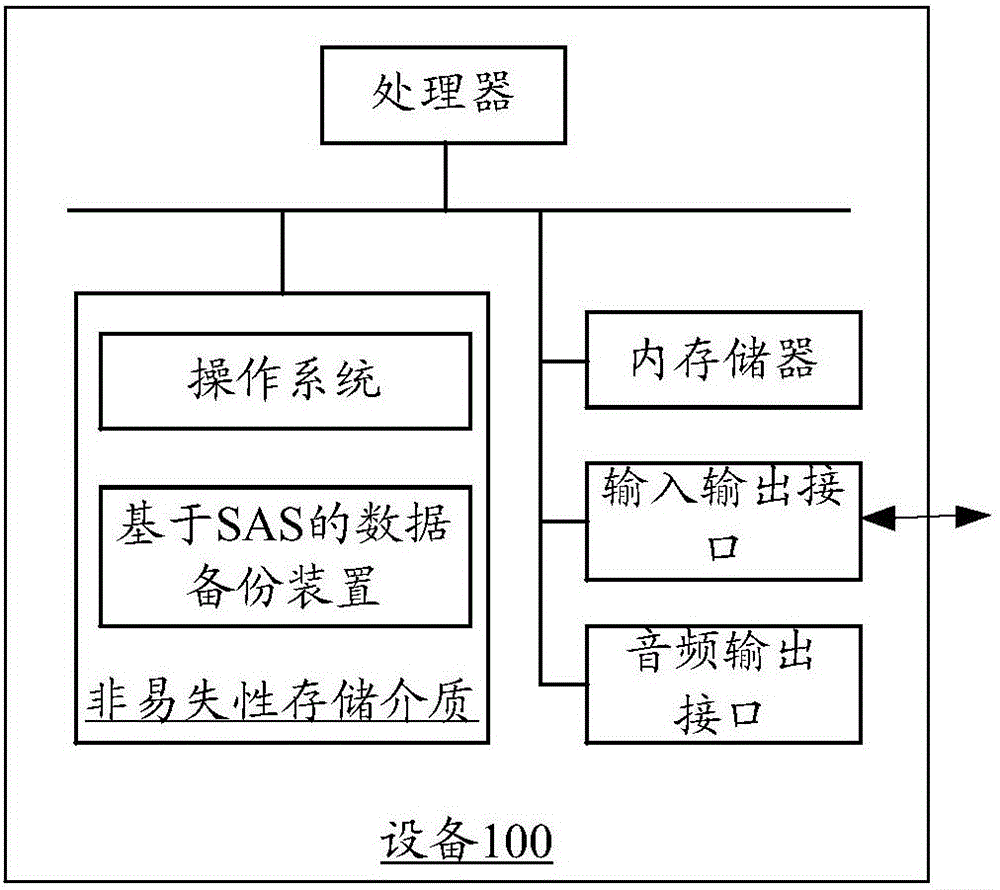
SAS-based data backup method and device
ActiveCN106055427BWill not affect executionImprove backup efficiencyRedundant operation error correctionProcessing InstructionStatistical analysis
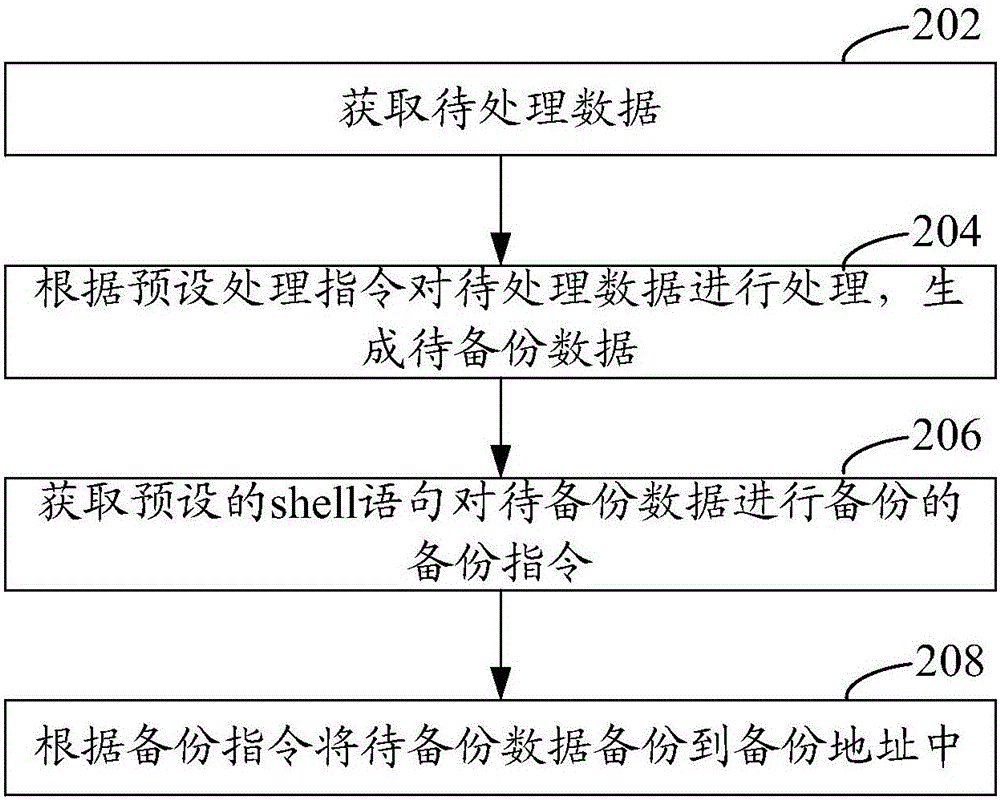
The present invention relates to an SAS (Statistical Analysis System)-based data backup method, and is characterized in that the method comprises obtaining to-be-processed data; processing the to-be-processed data according to a preset processing instruction, generating to-be-backup data, and storing the to-be-backup data to a preset storage address; obtaining a preset backup instruction for backing up the to-be-backup data by a shell sentence, the backup instruction including the preset storage address and a backup address; and backing up the to-be-backup data to the backup address according to the backup instruction. According to the backup method, execution of other instructions by an SAS system cannot be influenced, backup can be carried out without listing the to-be-backup data, and compared with a traditional data backup method, backup efficiency of SAS data can be improved. In addition, an SAS-based data backup apparatus is also correspondingly provided.
Owner:PING AN TECH (SHENZHEN) CO LTD
SAS-based data backup method and apparatus
ActiveCN106055427AWill not affect executionImprove backup efficiencyRedundant operation error correctionProcessing InstructionStatistical analyses
The present invention relates to an SAS (Statistical Analysis System)-based data backup method, and is characterized in that the method comprises obtaining to-be-processed data; processing the to-be-processed data according to a preset processing instruction, generating to-be-backup data, and storing the to-be-backup data to a preset storage address; obtaining a preset backup instruction for backing up the to-be-backup data by a shell sentence, the backup instruction including the preset storage address and a backup address; and backing up the to-be-backup data to the backup address according to the backup instruction. According to the backup method, execution of other instructions by an SAS system cannot be influenced, backup can be carried out without listing the to-be-backup data, and compared with a traditional data backup method, backup efficiency of SAS data can be improved. In addition, an SAS-based data backup apparatus is also correspondingly provided.
Owner:PING AN TECH (SHENZHEN) CO LTD
Progress invoking method of shared windows
ActiveCN100514300CWill not affect executionReduce couplingMultiprogramming arrangementsIndependent functionCoupling
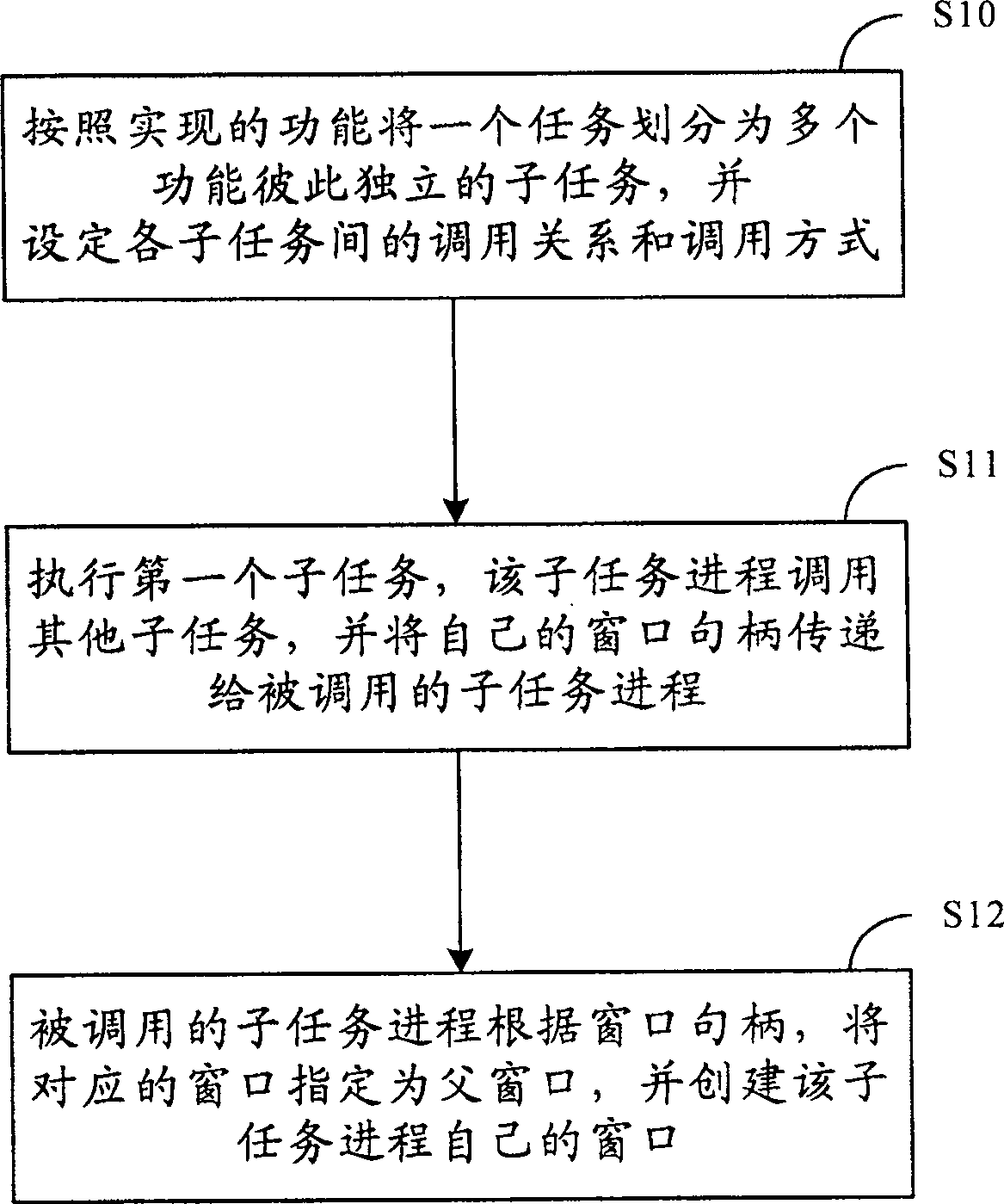
The invention discloses a method for calling a shared window process, which includes: dividing the task into a plurality of subtasks with independent functions according to each subfunction of the task; when one of the subtasks is running, the subtask process calls other subtasks, and pass their own window handle to the called subtask; when the called subtask is running, its process will create the window of the process calling the subtask as its parent window according to the received window handle own window. By adopting the method of the invention, the coupling degree of the system can be reduced, and when the process of a subtask crashes, it will not affect the execution of the whole task, thereby improving the operating efficiency of the system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data processing method and device and computer readable storage medium
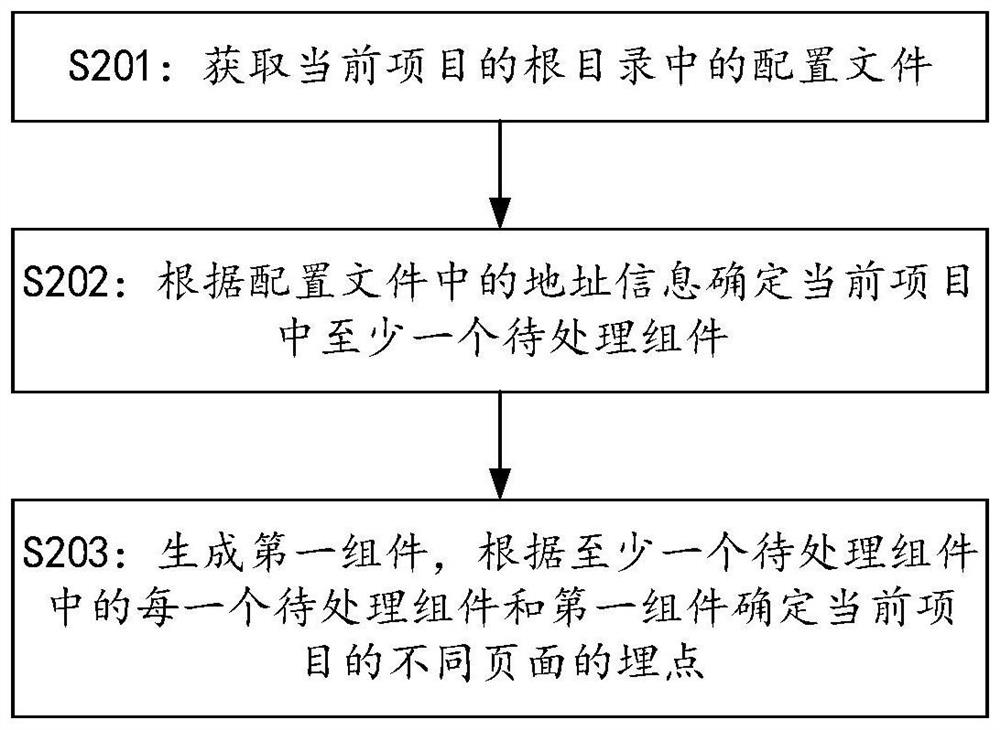
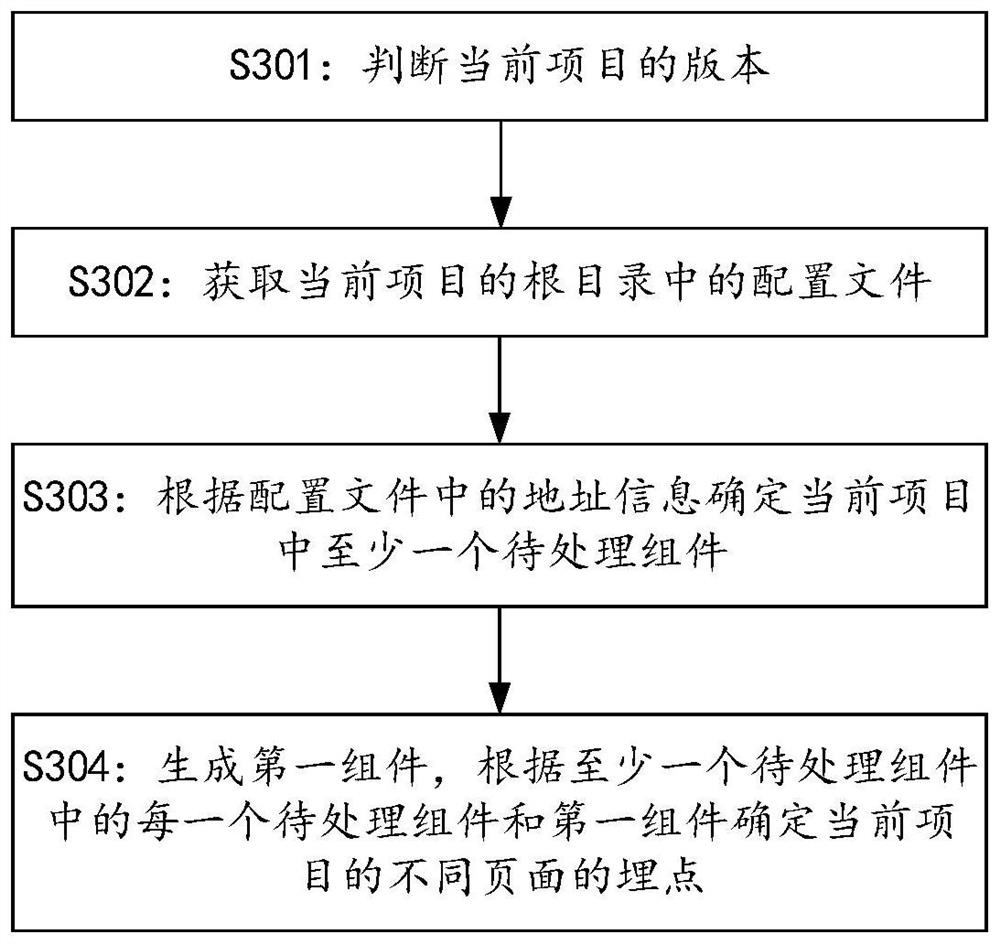
PendingCN114356290AWill not affect executionDoes not affect readabilityVersion controlIntelligent editorsData processingSoftware engineering
The embodiment of the invention relates to the technical field of data analysis, and provides a data processing method and device and a computer readable storage medium, and the method comprises the steps that configuration information in a root directory of a current project is acquired, and a configuration file comprises address information; determining at least one to-be-processed component in the current item according to address information in the configuration file; and generating a first component, and determining burying points of different pages of the current item according to the first component and the at least one to-be-processed component. According to the embodiment of the invention, the readability of project codes can be improved, and the development efficiency is improved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
A Webpage Text Extraction Method Based on Logical Link Blocks
ActiveCN109740097BImprove recallImprove accuracyWebsite content managementInformation processingEngineering
Owner:WENZHOU UNIV OUJIANG COLLEGE
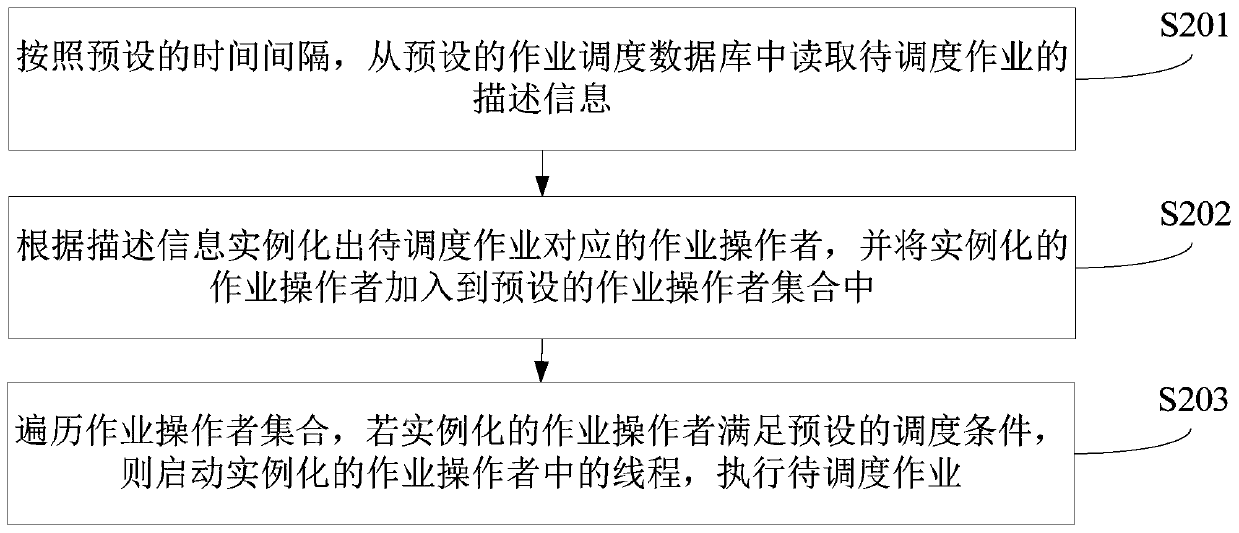
Job scheduling method and device, computer equipment and readable storage medium
PendingCN110597605AWill not affect operationEasy to manageProgram initiation/switchingComputer equipmentExecution time
The invention relates to a job scheduling method and device, computer equipment and a readable storage medium. The job scheduling method comprises the steps: reading the description information of a to-be-scheduled job from a preset job scheduling database according to a preset time interval, wherein the preset time interval is smaller than the execution time interval of the to-be-scheduled job; instantiating a job operator corresponding to the job to be scheduled according to the description information, and adding the instantiated job operator into a preset job operator set; and traversing the job operator set, and if the instantiated job operator meets a preset scheduling condition, starting a thread in the instantiated job operator to execute the job to be scheduled. In the job scheduling method, each to-be-scheduled job is an independent executable program, so that the operation of other jobs is not influenced, and each to-be-scheduled job is convenient to manage.
Owner:WUHAN UNITED IMAGING HEALTHCARE CO LTD
Resource allocation method and resource using method, device and system
ActiveCN101742656BWill not affect executionFlexible resource allocationForward error control useData switching networksControl channelUser equipment
The embodiment of the invention discloses a resource allocation method, which comprises the following steps of: setting a corresponding relation between a predefined control channel format and a preset resource type; and when allocating the resource of the preset resource type to target user equipment (UE), transmitting resource allocation information according to a corresponding newly defined control channel format, and indicating the predefined control channel format to the target UE so that the target UE correctly acquires the resource allocation information and uses the resource designated by the resource allocation information according to a using method corresponding to the preset resource type. The embodiment of the invention also provides a resource using method and a device and asystem for implementing the method. In the resource allocation method, the resource configuration information is flexibly set as required and the control channel format is indicated to the UE by establishing the corresponding relation between the control channel format and the resource type, thus semi-persistent resources can be allocated to the UE, the time of transmitting the resource allocation information is reduced, and the system overhead is saved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
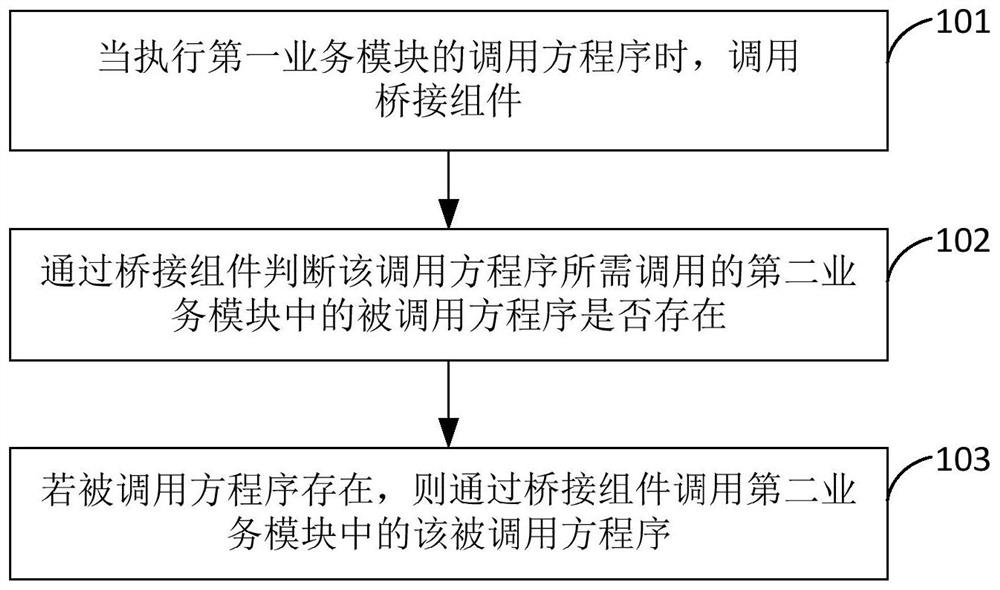
Implementation method and device for mutual calling of business modules, equipment and storage medium
PendingCN113448698AAbility to communicate across modulesRealize hierarchical managementProgram initiation/switchingInterprogram communicationSoftware engineeringApplication procedure
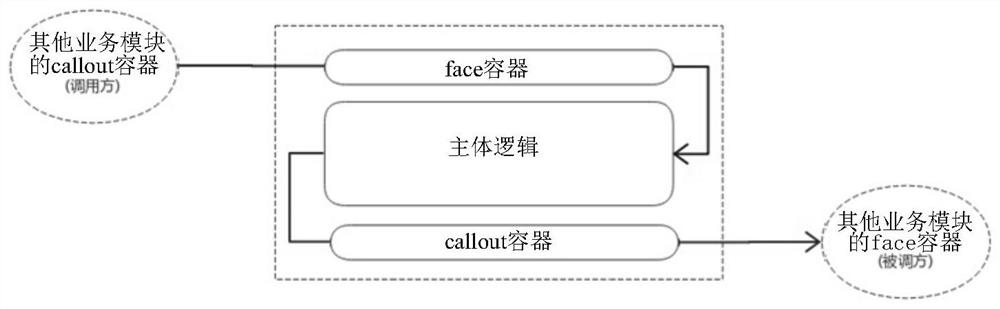
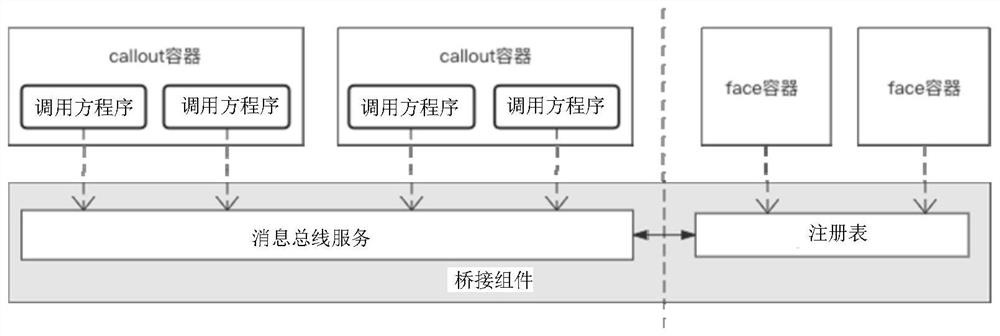
The invention provides an implementation method and device for mutual calling of business modules, equipment and a storage medium, and the method comprises the steps: calling a bridging component when a calling party program of a first business module is executed; judging whether a called party program of a second business module needing to be called by the calling party program exists or not through the bridging component; and if the called party program exists, calling the called party program of the second business module through the bridging component. According to the method, the program pointers of the calling party programs of the modules point to the message bus service of the bridging component, and the called party programs of the modules are written into the registry of the bridging component. And the bridging component enables the association relationship among the modules to be organized and ordered, so that the application program has the cross-module communication capability. The modules are mutually independent, and execution of other modules is not affected when any module is pulled out of a main project of the application program. And multi-module independent parallel development and level-to-level management of code permissions are realized.
Owner:北京新氧科技有限公司
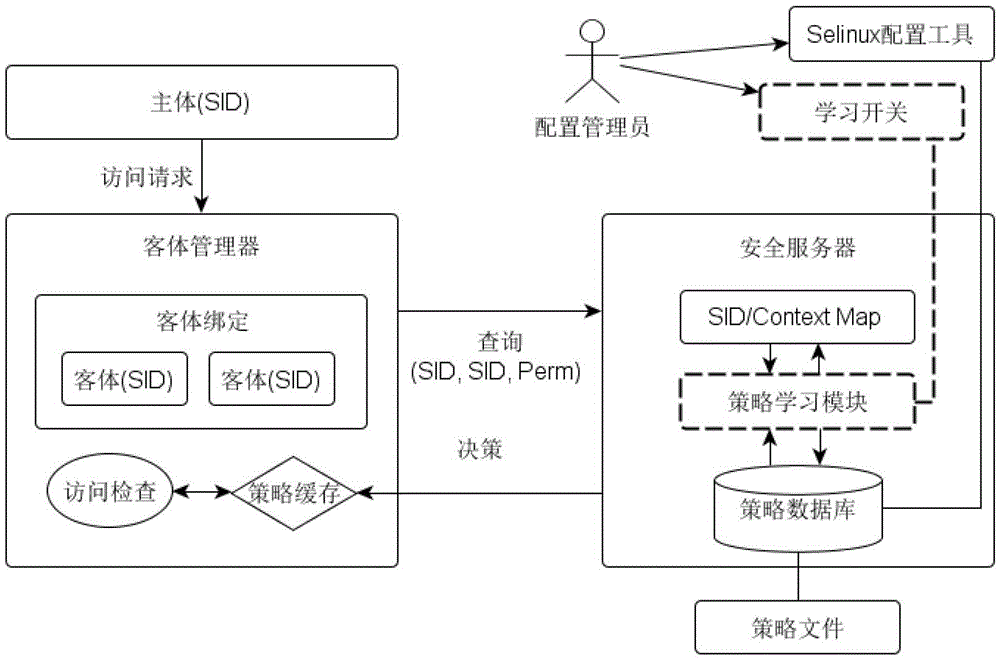
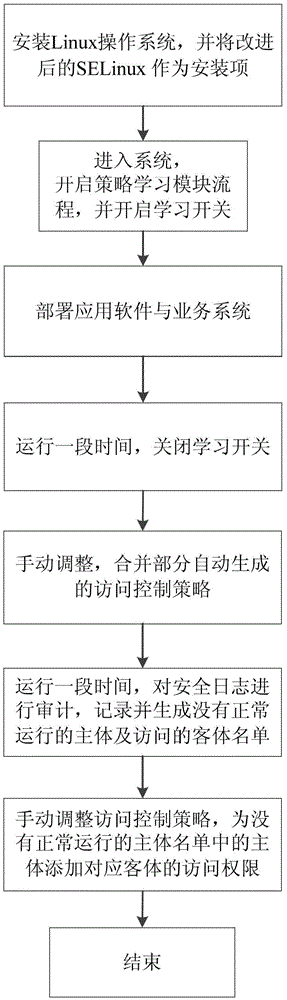
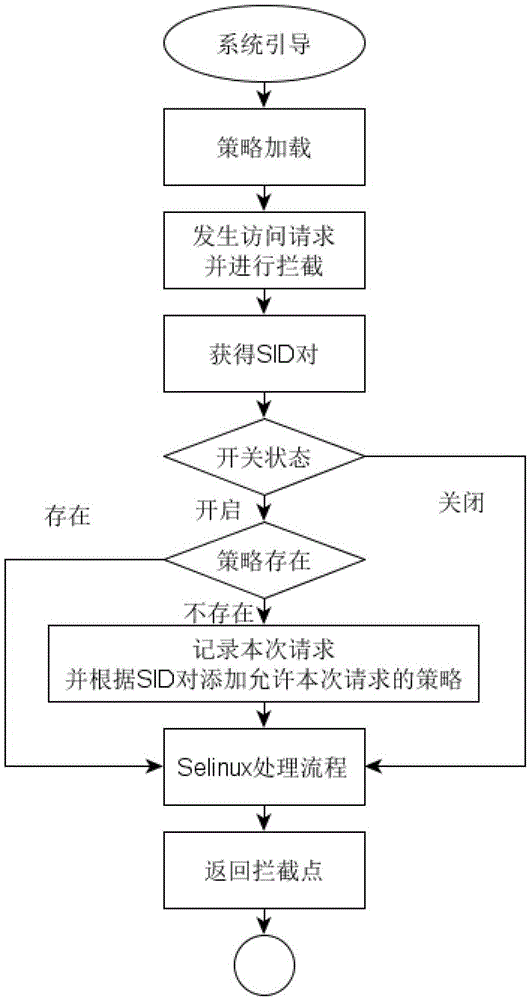
A self-study-based configuration method of linux security policy
ActiveCN103176817BSimplify configuration workAvoid security issuesProgram loading/initiatingData switching networksGNU/LinuxSystem configuration
The invention provides a Linux security policy configuration method based on self-learning aiming at the problem that Linux security policy configuration is difficult so as to simplify the working process of system configuration. According to the Linux security policy configuration method, a policy study module is embedded in a security server area of Security-Enhanced Linux (SE Linux). The module provides an automatic learning switch for a configuration administrator user so that a security server can automatically generate an access control policy by judging the on-off state. When the switch is in the on-state, all access requests between subjects and objects intercepted by an LSM are recorded, corresponding access control policies are automatically generated, and simultaneously the requests are released. When the switch is in the off-state, the policy study module no longer plays the role, and the security server returns the existing access control policies. The policies generated with the Linux security policy configuration method in the self-learning mode all meet the requirements of minimum privilege of the subjects, hidden safety dangers or stability dangers caused by errors in manual configuration can be avoided to the maximum extent, and system safety can be further improved.
Owner:CHINA ELECTRIC POWER RES INST +2
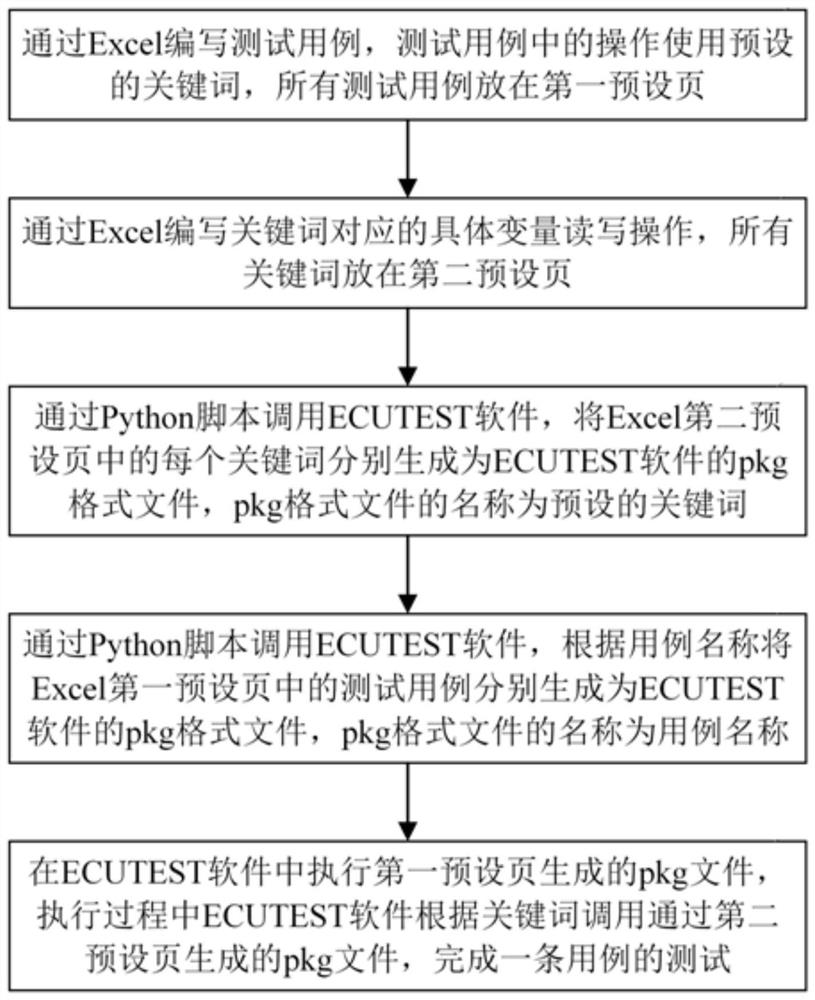
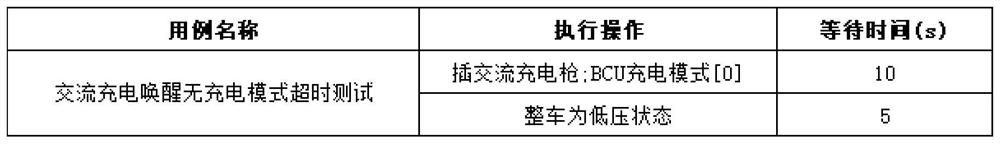
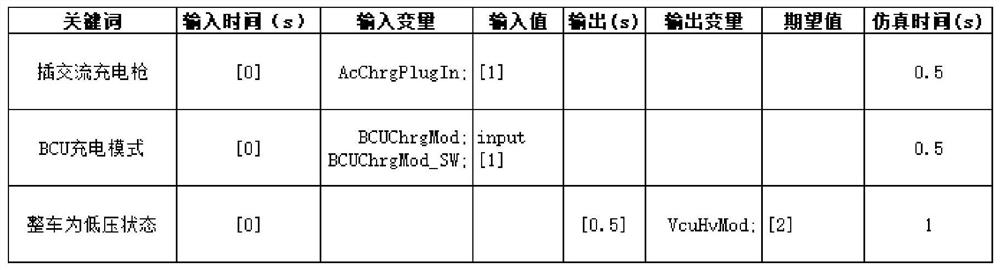
Vehicle control unit hardware-in-loop automatic test case design method
PendingCN114780425AWill not affect executionEasy to changeSoftware testing/debuggingTestwareElectric cars
The invention relates to a vehicle control unit hardware-in-the-loop automatic test case design method, which comprises the steps that test cases are written through Excel, preset keywords are used for operation in the test cases, and all the test cases are placed on a first preset page; specific variable read-write operation corresponding to the keywords is written through Excel, and all the keywords are placed on a second preset page; the automatic test software is called through the script, a pkg format file of the automatic test software is generated for each keyword in the second preset page of the Excel, and the name of the pkg format file is the preset keyword; the automated testing software is called through the script, the testing cases in the first preset page of the Excel are generated into pkg format files of the automated testing software according to the names of the testing cases, and the names of the pkg format files are the names of the testing cases. The case designed by the invention can be compatible with different electric vehicle projects, is easy to change, can be directly written through Chinese, and does not affect the execution of the whole test case by changing the intermediate operation.
Owner:深蓝汽车科技有限公司
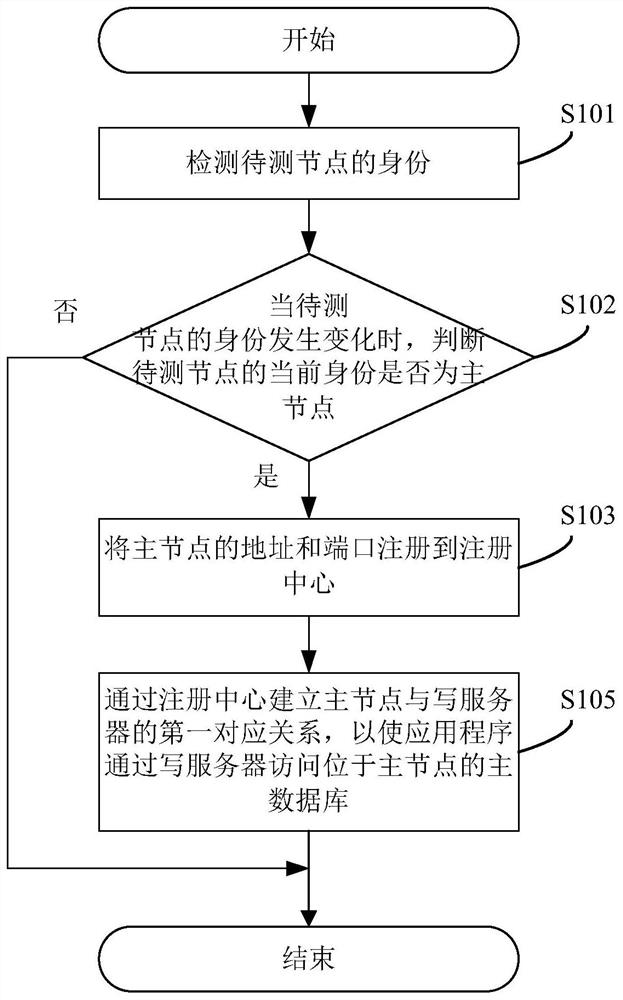
Database access method, system and device and readable storage medium
PendingCN112286738AWill not affect executionHigh availability accessRedundant hardware error correctionEnergy efficient computingDomain nameApplication procedure
The invention discloses a database access method. The method comprises the steps of detecting an identity of a to-be-detected node; when the identity of the to-be-tested node changes, judging whetherthe current identity of the to-be-tested node is a main node or not; if so, registering the address and the port of the main node to a registration center; establishing a first corresponding relationship between the main node and the write server through the registration center, wherein the application program accesses a main database located at the main node through the write server. By utilizingthe service discovery characteristic of the registration center, the application program can access the main database located at the main node through the write server without worrying about whetherthe IPs of the write node database and the read-only node database are changed or not, the application is not perceived during database fault switching, the execution of the service is not influenced,and high-availability access of the domain name after database fault switching is realized. The invention furthermore provides a database access system and device, and a readable storage medium, which have the above beneficial effects.
Owner:政采云有限公司
Method for implementing multi-opening of android application, mobile terminal and storage medium
ActiveCN107665302BMore to achieve securityRealize safe and reliableComputer security arrangementsSoftware deploymentServerOpen implementation
The invention discloses a method for realizing multi-opening of Android applications, a mobile terminal and a storage medium, wherein the method includes: starting the cloned application after starting the original application of the mobile terminal; providing a registration and storage path for the cloned application at the frame layer; The cloned application communicates with the remote server in the original application as the host. The method for realizing multi-opening of Android applications, the mobile terminal and the storage medium of the present invention realize the multi-opening of the same application program through the operation in the host set on the mobile terminal, and realize it from the framework layer, which will not cause any harm to the application and the system. Confusion or misleading crashes can safely implement multiple applications without affecting the execution of the original application, and its implementation is simpler and feasible.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
A data online migration method and device for application update in a network platform
ActiveCN103729204BGuaranteed normal executionNo failureProgram loading/initiatingDatabase accessThird phase
The present application provides an online data migration method and system for application update in a network platform, so as to solve the problem of service execution failure in the prior art. The method includes: running the new version application and the old version application at the same time in the first stage of the update, and the new version application and the old version application access the old database during the running; ending the first stage of the update, storing the data in the old database in full. Synchronize to the new database and enter the second stage of the update, run the new version of the application and the old version of the application at the same time, the new version of the application is running to access the new database, and the old version of the application accesses the old database; end the second stage of the update , and enter the third stage of the update, run the new version of the application and the old version of the application at the same time, the new version of the application and the old version of the application are running to access the new database; at the end of the third stage of the update, the new version of the application is run, and the new version of the application is running. The version application has access to the new database.
Owner:ADVANCED NEW TECH CO LTD
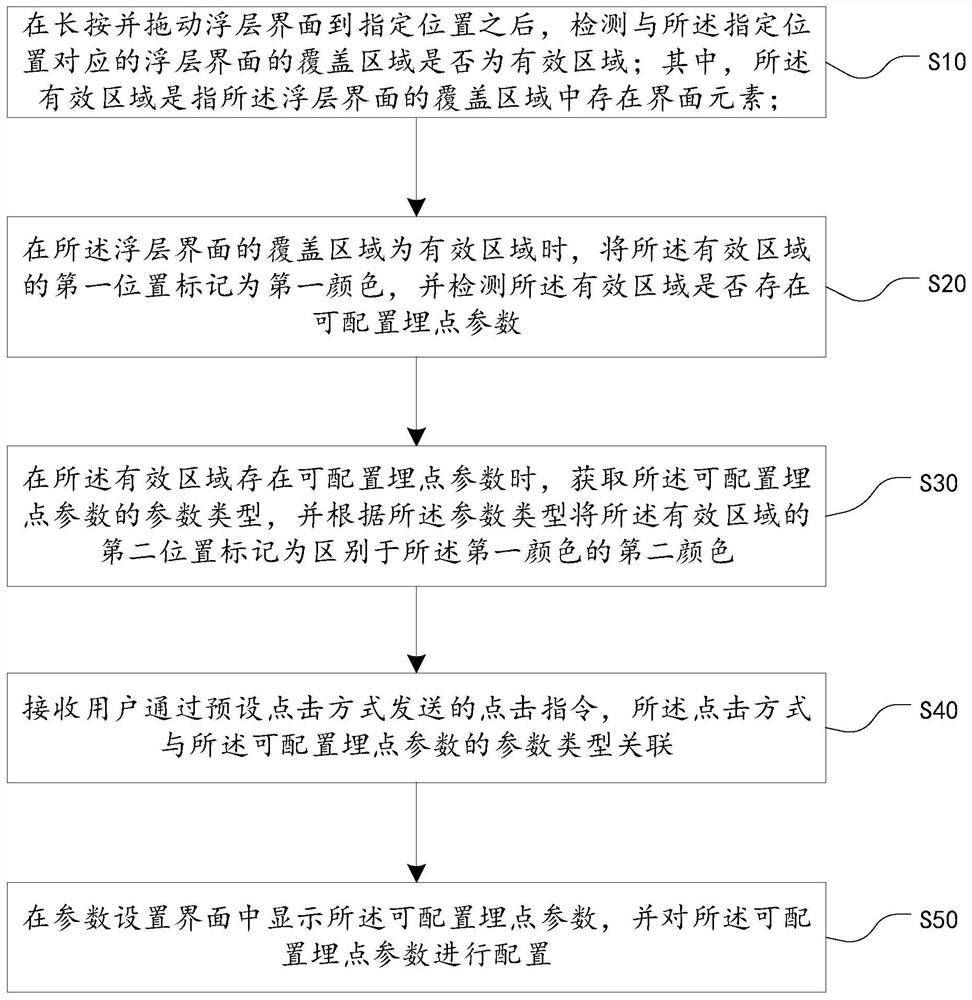
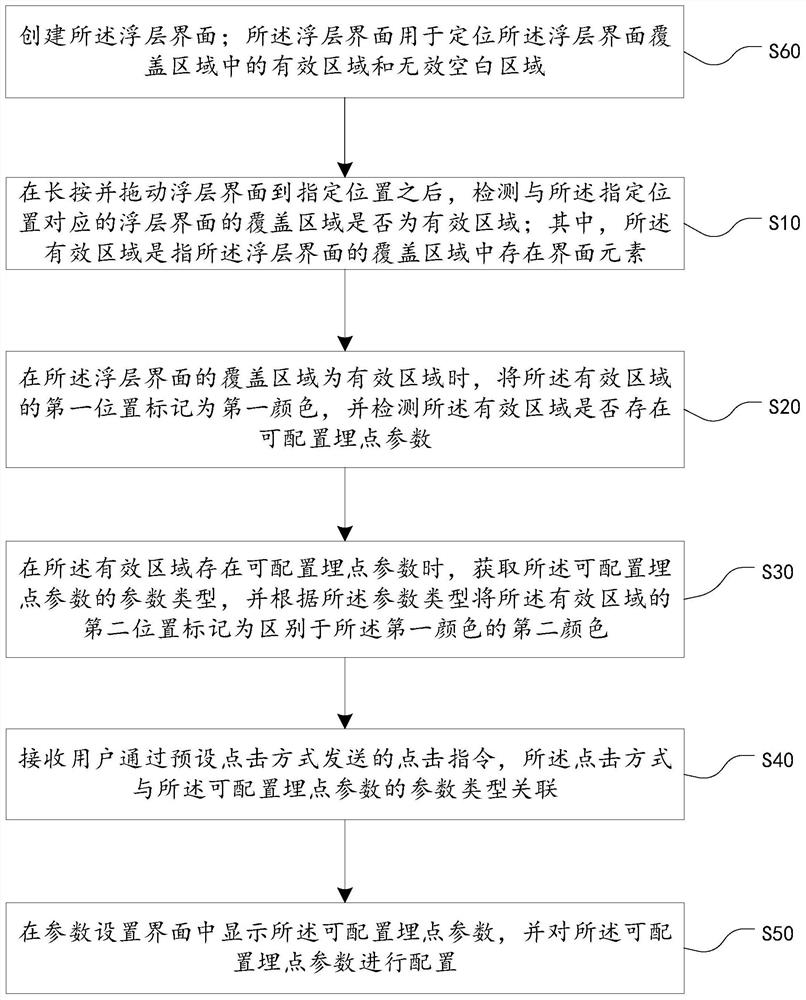
Buried point method, device, equipment and storage medium based on floating layer interface
ActiveCN109521919BIntuitive configurationWill not affect executionInput/output processes for data processingComputer hardwareLayer interface
The invention discloses a point-burying method, device, equipment and storage medium based on a floating layer interface. The method includes: detecting whether the coverage area of the floating layer interface is an effective area; when the coverage area of the floating layer interface is an effective area , when the first position of the valid area is marked with the first color and there are configurable buried point parameters in the valid area, the parameter type of the configurable buried point parameter is obtained, and the second position of the valid area is marked as different from the configurable buried point parameter according to the parameter type. The second color of the first color; receive the click instruction sent by the user through the preset click method, and the click method is associated with the parameter type of the configurable buried point parameter; display the configurable buried point parameter in the parameter setting interface, and configure the configurable Buried point parameters are configured. The present invention is more intuitive for the configuration of buried point parameters, and can simultaneously support the configuration of buried point parameters for two types of buried point events, click event and exposure event, and will not affect the execution of normal business events.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Intelligent commanding and dispatching method for converged media based on mobile internet
PendingCN114518784AAvoid hysteresisSlow responseDigital data processing detailsResourcesProduction scheduleProduction line
The invention relates to the technical field of production scheduling, in particular to a convergence media intelligent commanding and scheduling method based on the mobile internet. According to the technical scheme, the system comprises a main tablet personal computer, sub tablet personal computers, a wall-mounted display and a computer, and a total production dispatcher sends a production plan of the day to the sub tablet personal computer of a responsible person of each production line through the main tablet personal computer; the responsible personnel of each production line distributes the production plan of the production line to each worker for production; the production line capacity is counted in real time on the computer, data is sent to the sub-tablet personal computer of the responsible person of each production line, then the responsible person of each production line sends the capacity data to the main tablet personal computer of the production general dispatching personnel through the sub-tablet personal computer, and the production general dispatching personnel distributes and dispatches the capacity data. The method has the advantages that the dispatching instruction is transmitted in real time, the hysteresis of personnel transmission is avoided, the response is slow, and the execution of the production plan is not influenced.
Owner:武汉冠华天视数码科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com