A self-study-based configuration method of linux security policy
A technology of security policy and configuration method, applied in program control devices, digital transmission systems, electrical components, etc., can solve problems such as increasing the difficulty of configuring administrator security configuration, complex SELinux configuration process, and main body not working normally, etc. Simplifies configuration, reduces human error, and improves security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
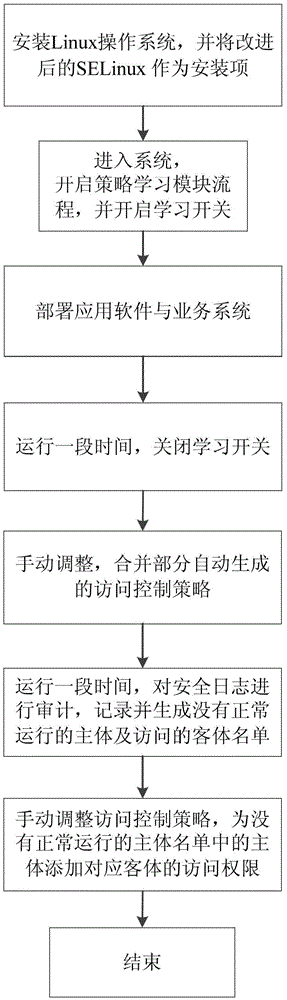
[0040] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
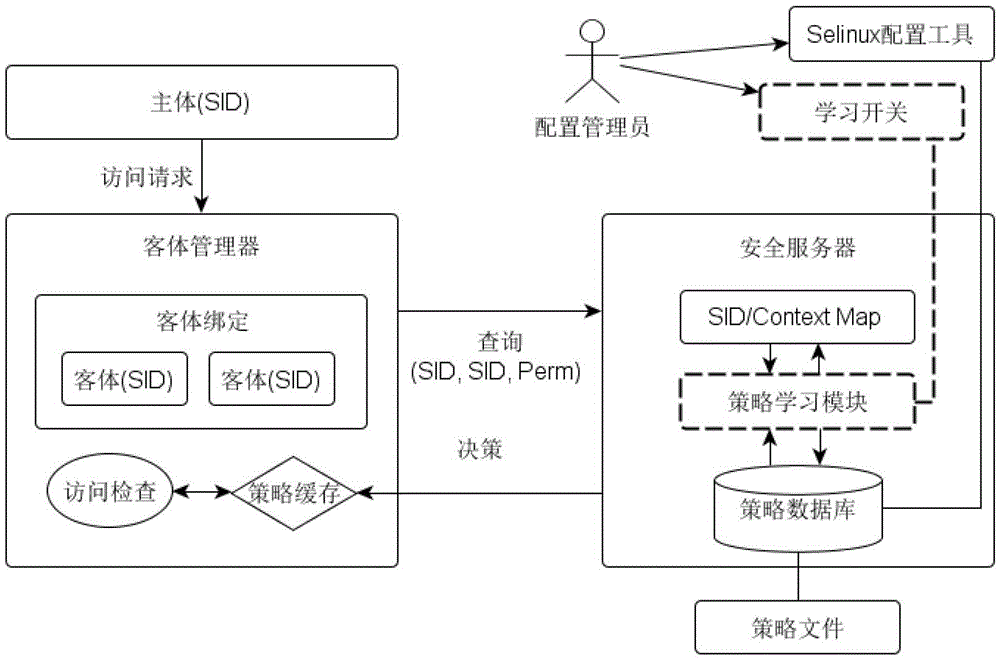
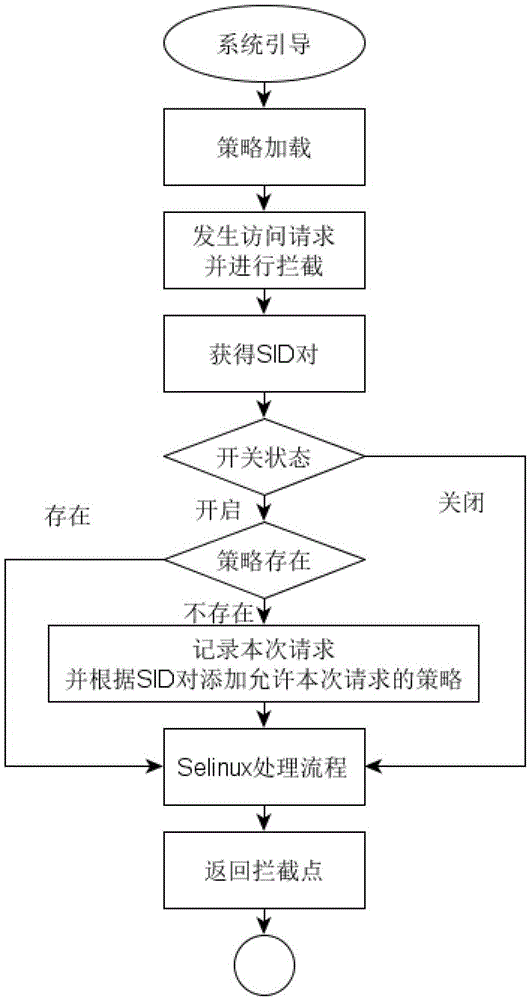
[0041] SELinux access control rules are stored in security policy files. Policy files are divided into binary and source code files. The source code is described in the form of policy configuration language, created and maintained by the configuration administrator. The source code is compiled by the policy configuration tool to generate a binary file. The binary policy is loaded into the kernel space during system startup, forms a policy library and cache in memory, and is managed by the SELinux security server.
[0042] For a secure operating system that uses SELinux, after booting, any access request made by the subject to the object will be intercepted by the Hook function of the LSM (Linux Security Module), and at the same time, the corresponding access policy will be obtained through the security server, and decisi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com