Patents
Literature
71results about How to "Simplify configuration work" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Character constant weight method
InactiveCN1773413AVersatileGood security propertiesDigital data processing detailsManagement toolOperational system
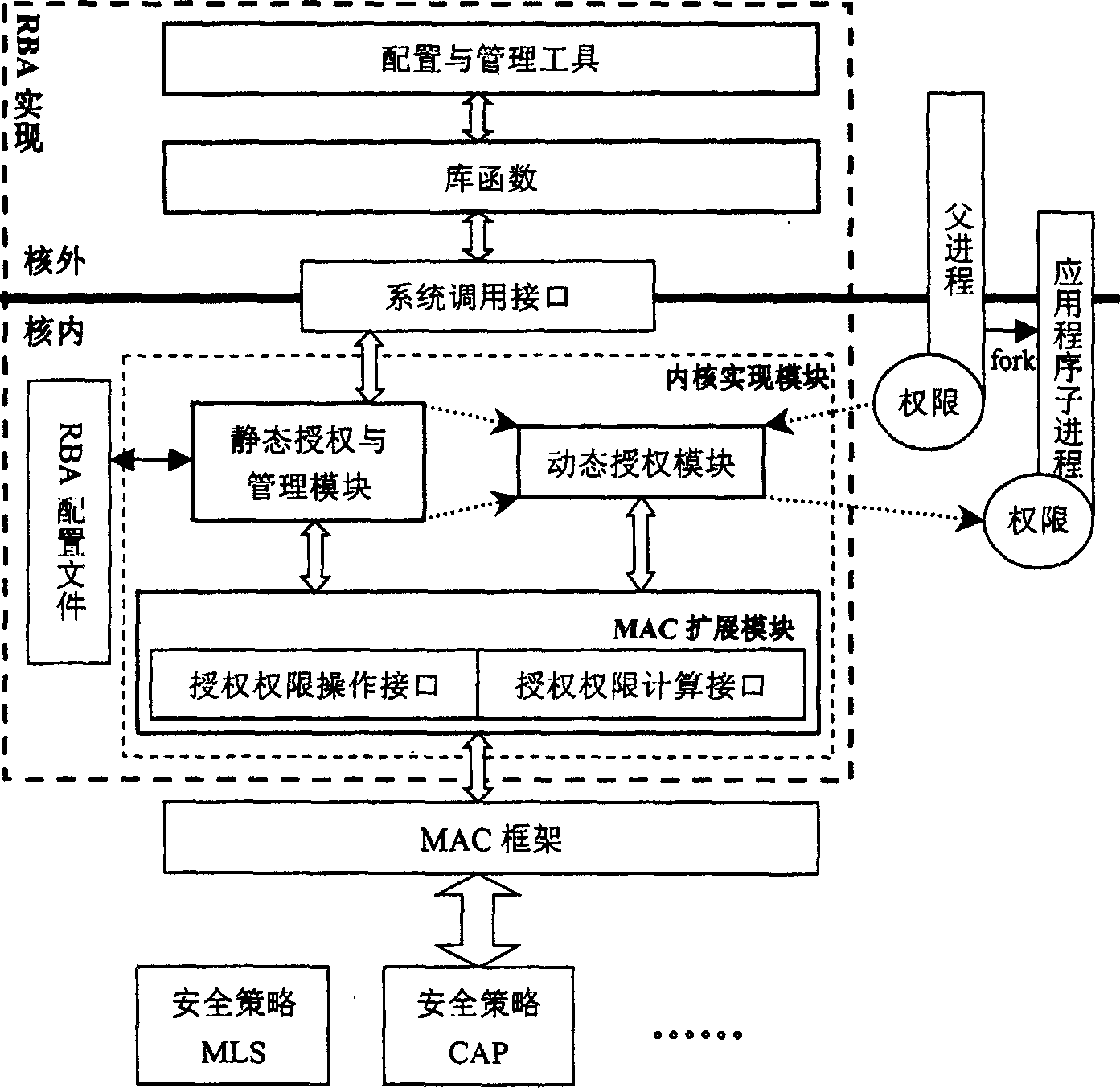
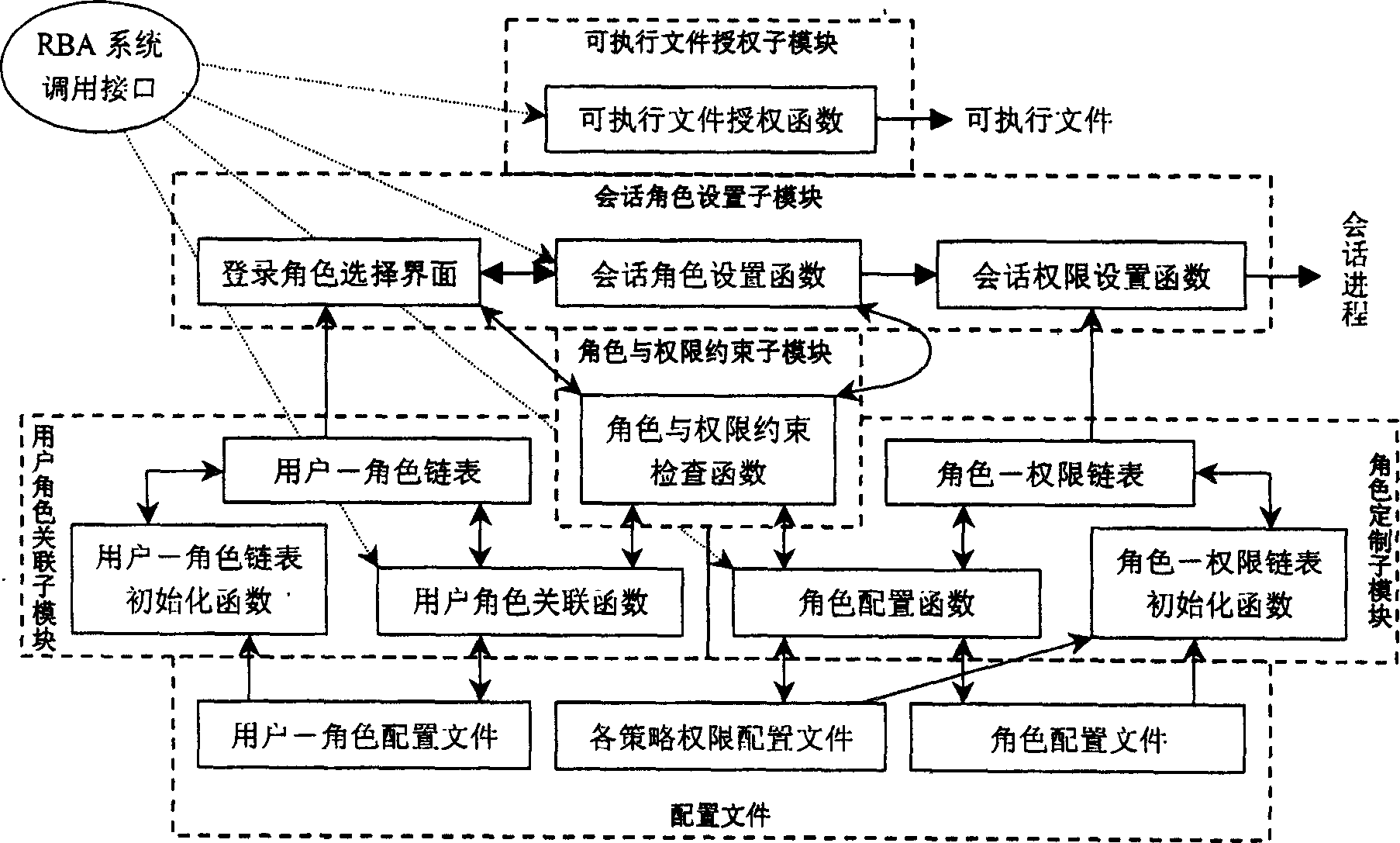
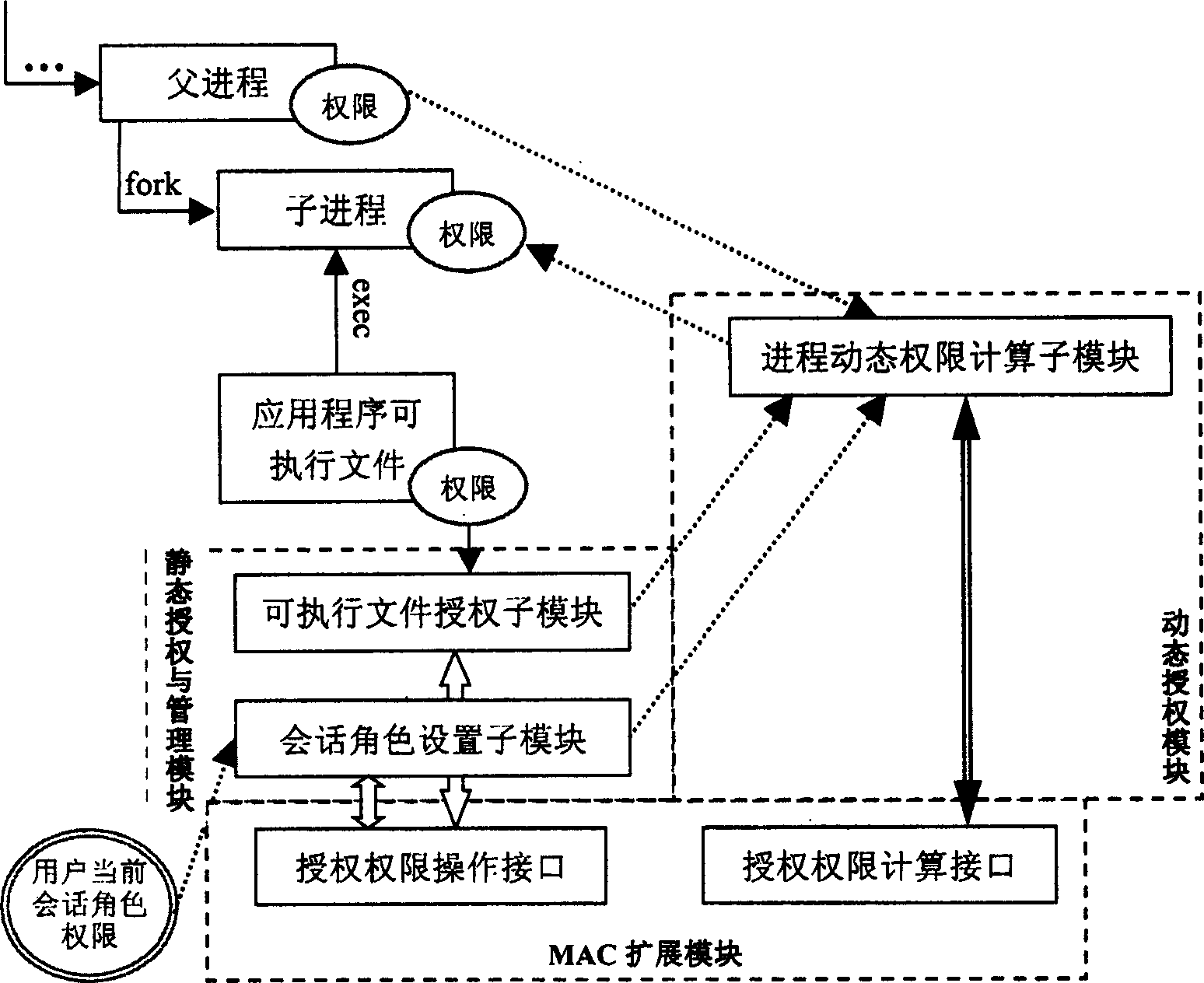
The present invention discloses an actor authority defining method. Its technical scheme includes the following contents: on the forced access frame MAC of operation system constructing a RBA implement system to make authorization for main body in safety operation system adopting forced access control MAC mechanism and configure management. The RBA implement system is formed from internal kernel implement module, RBA configuration file, system calling interface, library function and configuration and management tool. Besides, said invention also provides the concrete implement steps of said method by adopting said RBA implement system.
Owner:NAT UNIV OF DEFENSE TECH
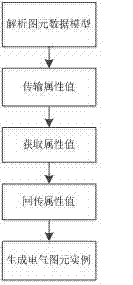
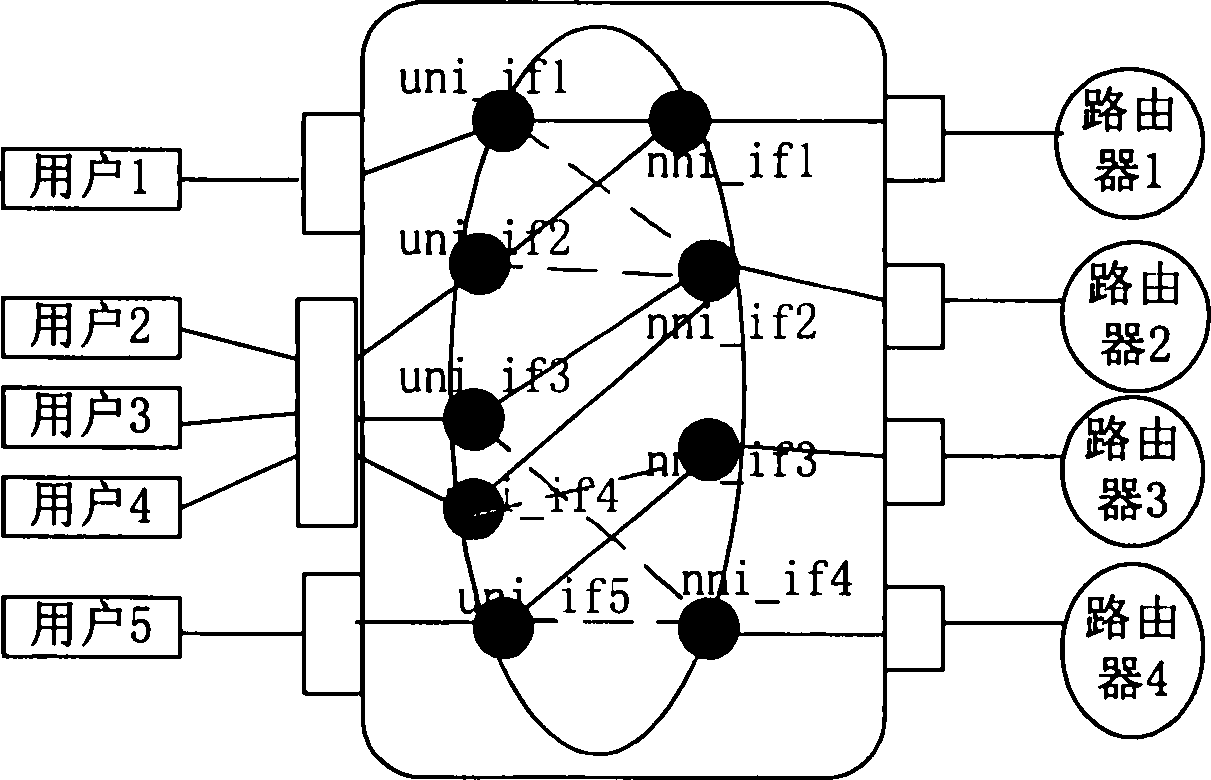
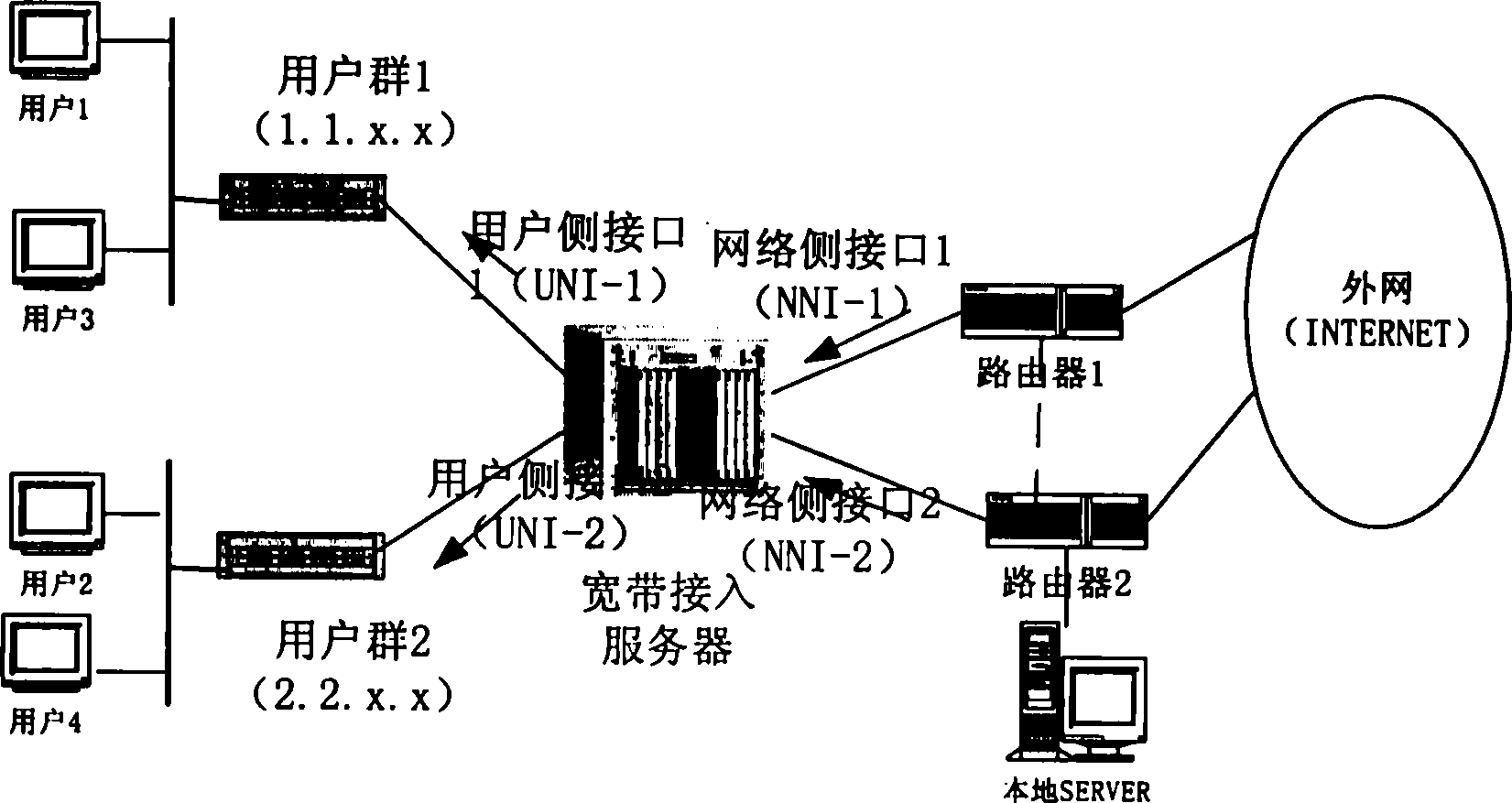
IEC (international electrotechnical commission) 61850-based visual graphics configuration method and IEC61850-based visual graphics configuration system
InactiveCN103927332ASimplify configuration workRealize synchronous generationData processing applicationsSemi-structured data retrievalGraphicsConfiguration language
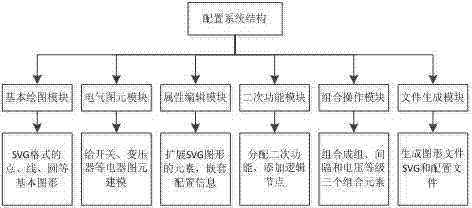
The invention discloses an IEC (international electrotechnical commission) 61850-based visual graphics configuration method and an IEC61850-based visual graphics configuration system. The IEC61850-based visual graphics configuration system comprises a basic drawing module, an electric graphics primitive module, an attribute editing module, a secondary function module, a combination operation module and a file generation module. Visual graphics replace complicated text information, levels of the configuration information are represented by topological structures of the graphics, and users and the graphics interact with one another, so that SCL (substation configuration language) configuration files which meet requirements can be generated. The IEC61850-based visual graphics configuration method and the IEC61850-based visual graphics configuration system have the advantages that the traditional text configuration mode is converted into a visual graphics configuration mode, and accordingly configuration work can be simplified; the configuration information is associated with the visual graphics, so that SVG (scalable vector graphics) with the configuration information can be automatically generated.
Owner:HOHAI UNIV
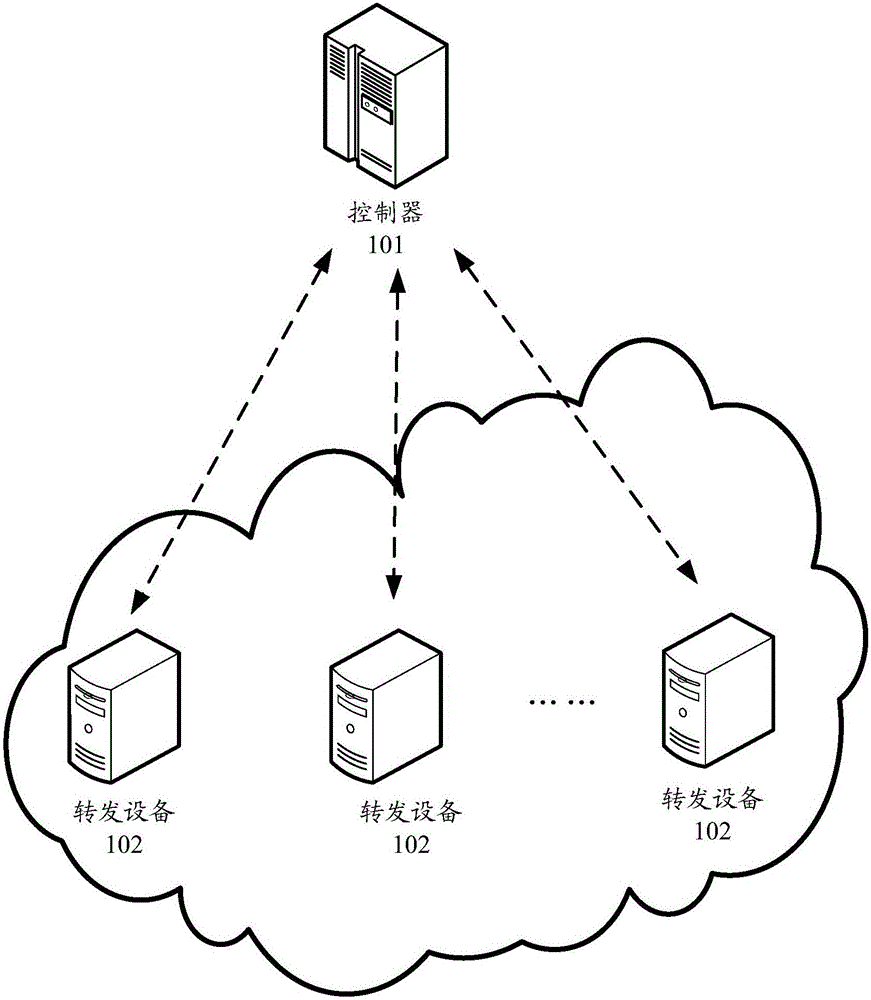
Control method, device and system for counting traffic
ActiveCN105871602ASimplify configuration workReduce in quantityData switching networksFlow controlTraffic countTraffic capacity
The embodiment of this invention discloses a control method for counting traffic. The method comprises the following steps: a control node acquires a counting instruction; the counting instruction is used for counting the traffic of a target data flow; the control node generates a traffic counting strategy according to the counting instruction; the traffic counting strategy comprises a matching identifier of the target data flow, a first command and a second command; and the control node sends the traffic counting strategy to a forwarding node. The first command is used for setting a traffic identifier for the target data flow according to the matching identifier; the second command is used for indicating the forwarding node to count the traffic generated by a target message into the traffic counting result corresponding to the traffic identifier; the target message belongs to the target data flow; the traffic counting result corresponding to the traffic identifier is used for describing the traffic of the target data flow. Moreover, the embodiment of this invention further discloses a control device and a control system for counting the traffic.
Owner:HUAWEI TECH CO LTD
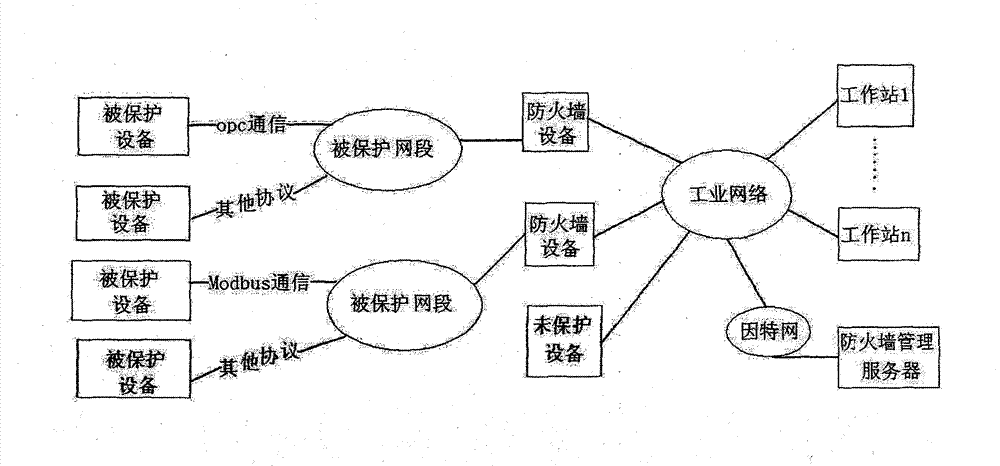
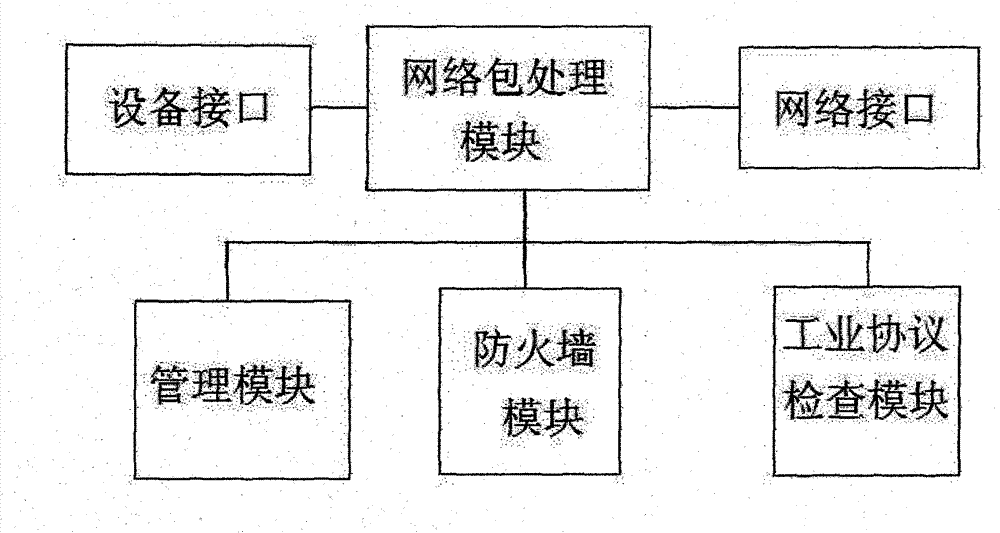
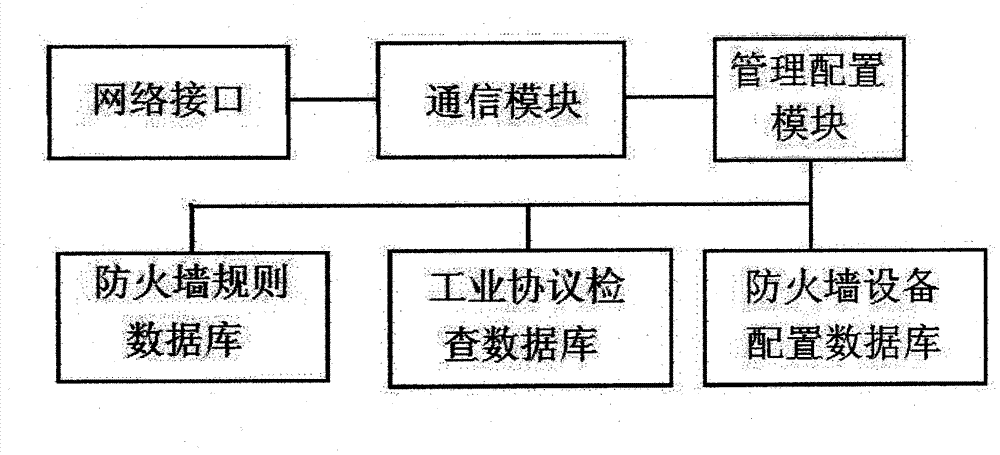
Industrial firewall without industrial protocol (IP) distributed type depth check arithmetic based on industrial protocol object linking and embedding for process control (OPC) classic
InactiveCN103036870AEasy to installImprove real-time performanceTransmissionComputer networkEngineering
The invention relates to an industrial firewall without industrial protocol (IP) distributed type depth check arithmetic based on industrial protocol object linking and embedding for process control (OPC) classic. An industrial firewall is arranged on an advanced position of a protected device, and network information is not needed to be configurated in advance. Installation, management and configuration of the firewall are simplified. At the same time, the industrial firewall without IP is designed to be arranged on an edge of industry network, handled flow is less, network delay is short, and instantaneity is good.
Owner:青岛海天炜业过程控制技术股份有限公司
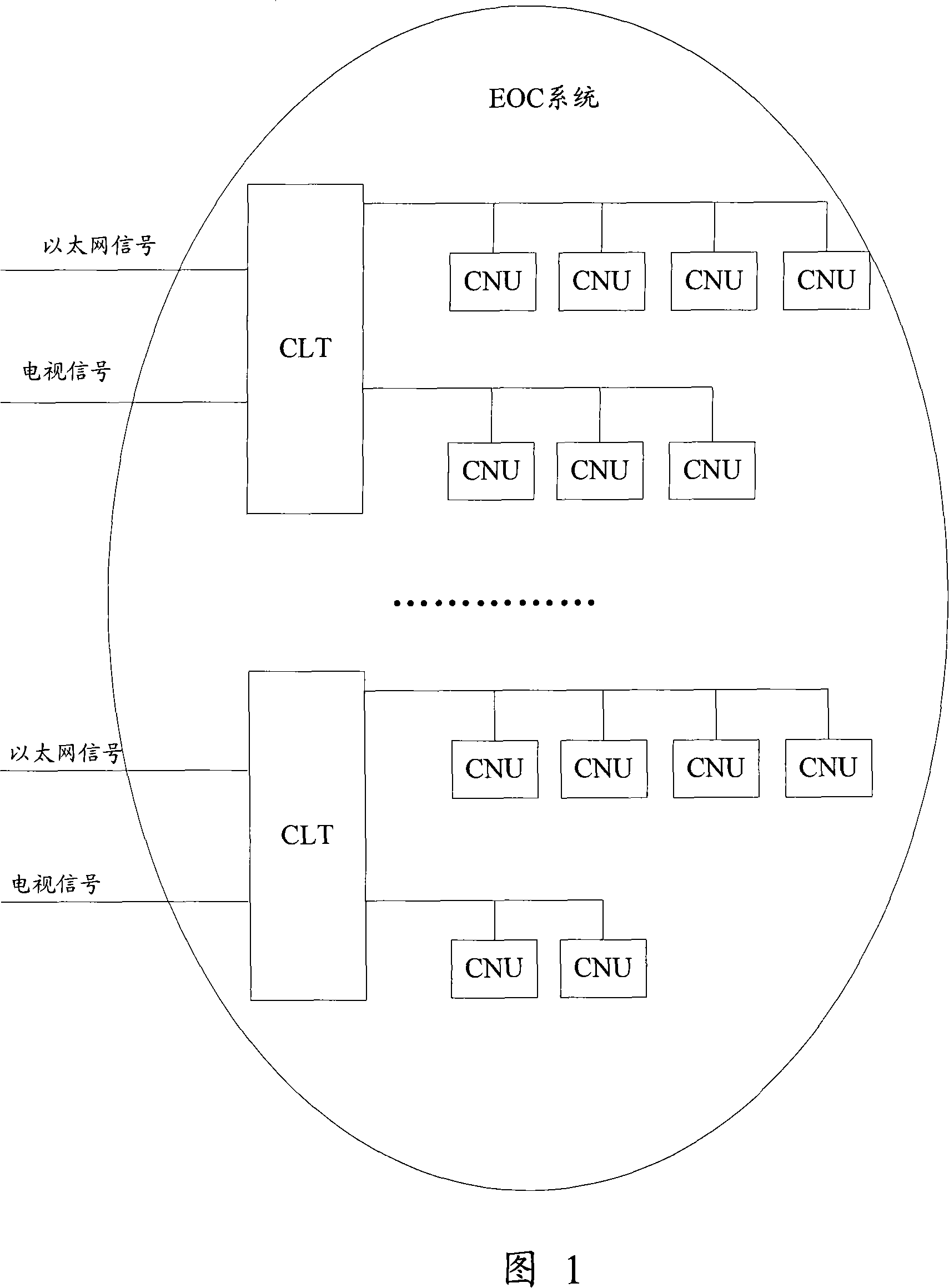
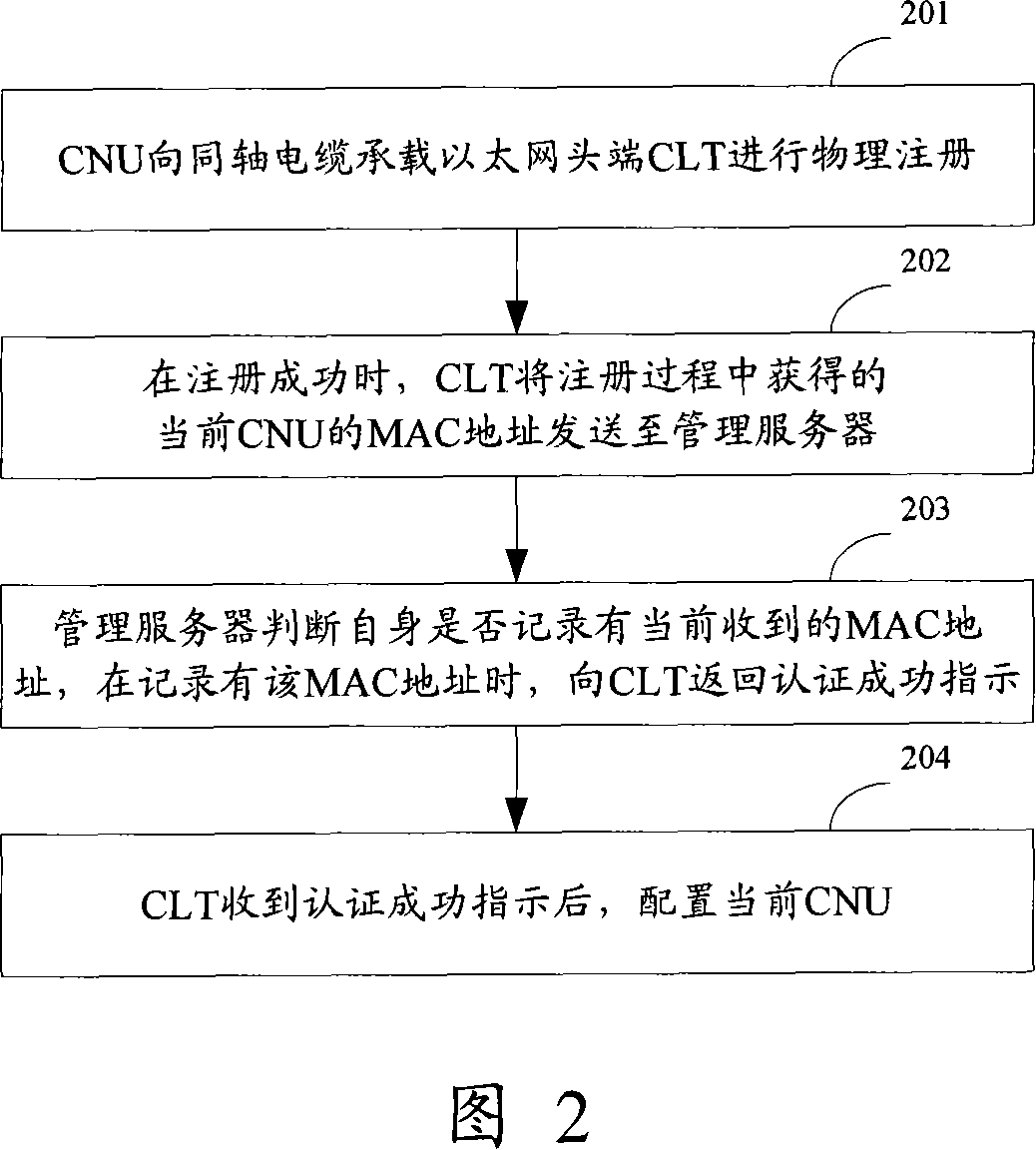
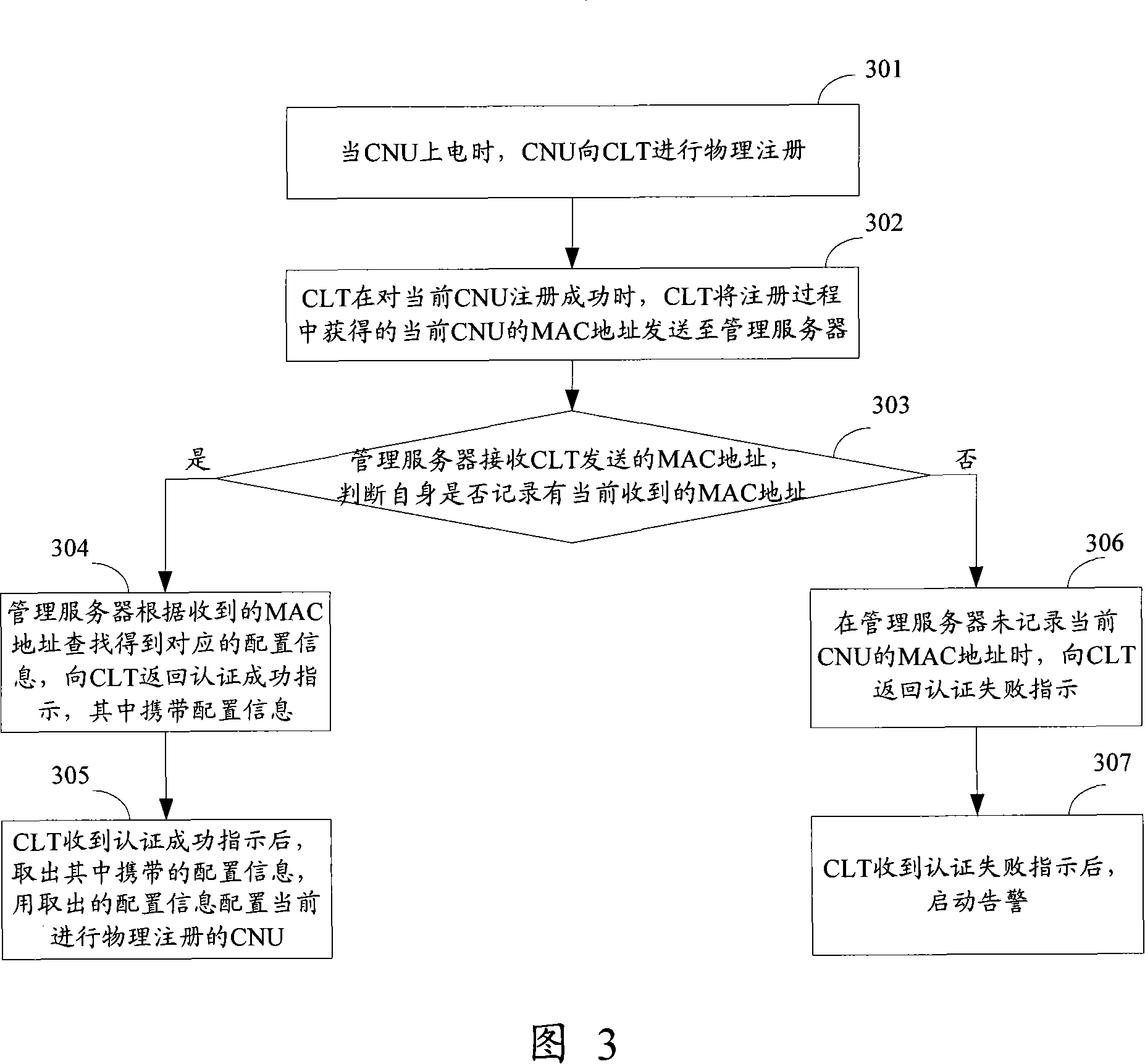
Method, system and management server for configuring coaxial cable carrier Ethernet terminal
InactiveCN101123537AEasy to manageRealize dynamic distributionLine-transmission monitoring/testingData switching networksTTEthernetCoaxial cable
The present invention discloses a technical scheme of configuring coaxicial cable-carried Ethernet terminals (CNU), which includes three steps. Firstly, a configured management server records the media access control (MAC) address of an authorized CNU; secondly, when the CNU needs to access the Internet via a coaxicial cable-carried Ethernet head end (CLT), then the CLT sends the MAC address of the CNU to the management server; finally, according to whether the management server records the received MAC address, the management server determines whether the CNU is an authorized CNU, and if theCNU is determined as an authorized CNU, the management server instructs the CLT to configure the CNU. The technical scheme of the present invention realizes the effective management of each CNU in anEOC system by centrally recording the MAC address of each authorized CNU in the management server, which controls the access of CNUs.
Owner:NEW H3C TECH CO LTD
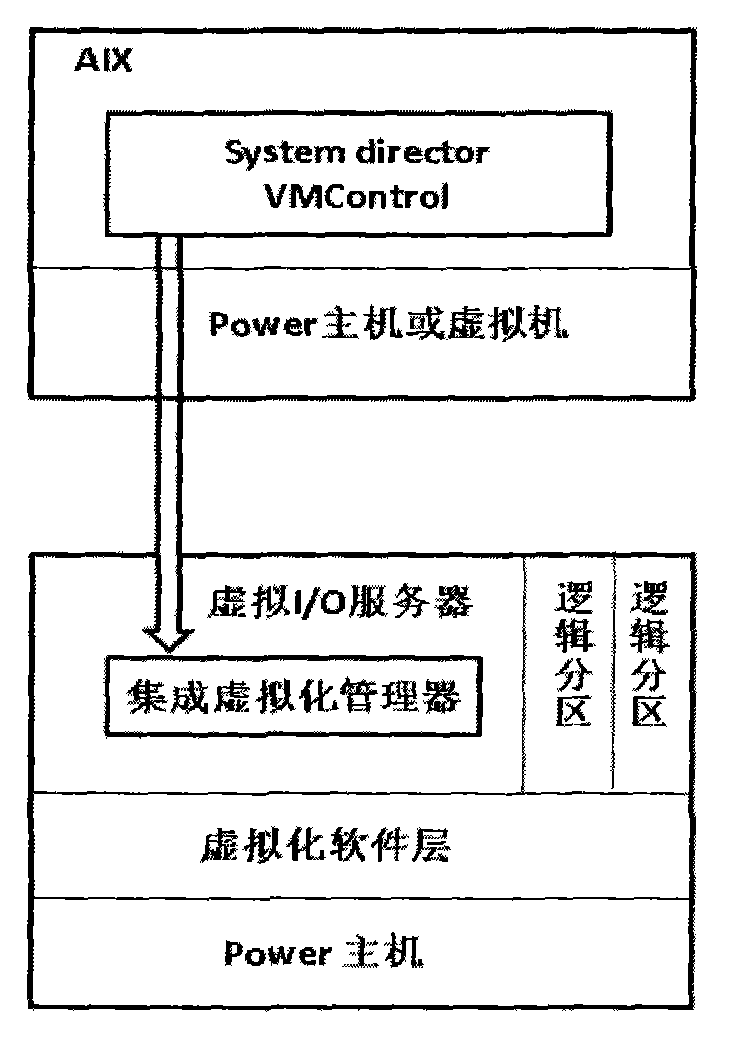
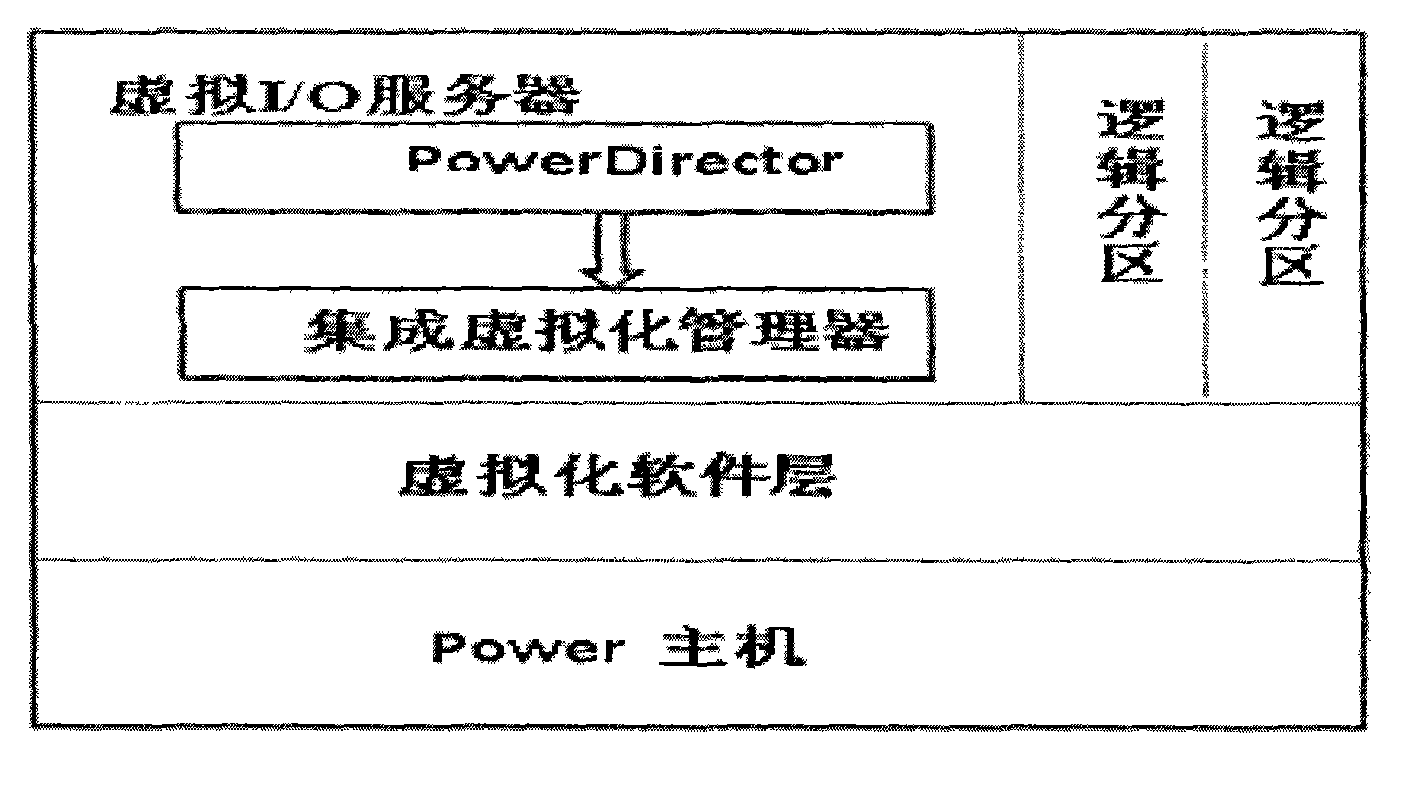
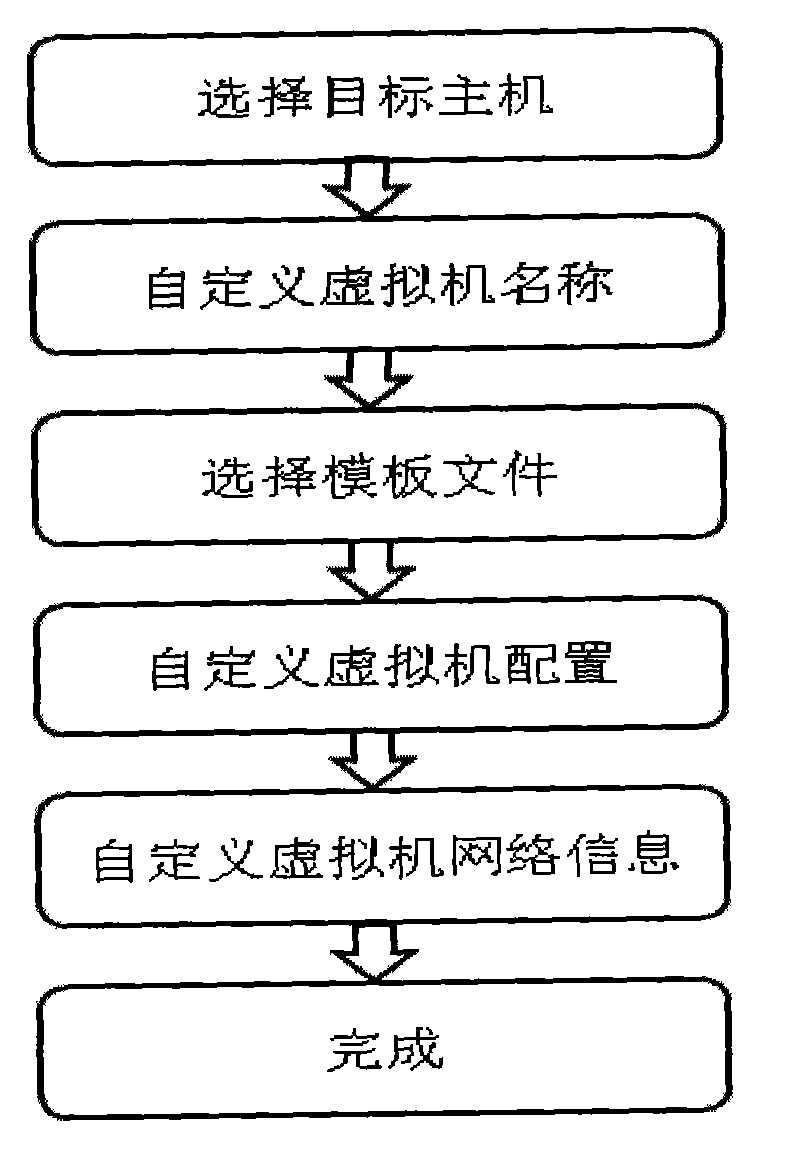
Virtualization implementing method for Power server
ActiveCN102981888ASimplify the deployment processSimplify configuration workSoftware simulation/interpretation/emulationVirtualizationOperational system
A virtualization implementing method for a Power server includes the steps of enabling virtualization management software to be directly installed in a virtual machine input / output (I / O) server; enabling at least one integrated virtualization manager (IVM) to be used as a platform and then to be registered to virtualization management software (Power Director); using commands supplied by the virtual machine I / O server and each IVM to create a virtual machine; enabling a preset installing module to automatically install in the created virtual machine through an image management function according to demands of a user and enabling a configuration file, an operating system, a network information configuration of the virtual machine to be completed. The virtualization implementing method for the Power server does not need to singly be supplied with another host machine or the virtualization management software so as to save host machine source and largely simplify deployment and configuration of the virtualization management software, and improve working efficiency of managers.
Owner:BEIJING TEAMSUN TECH
Message transmission method and device in VXLAN network
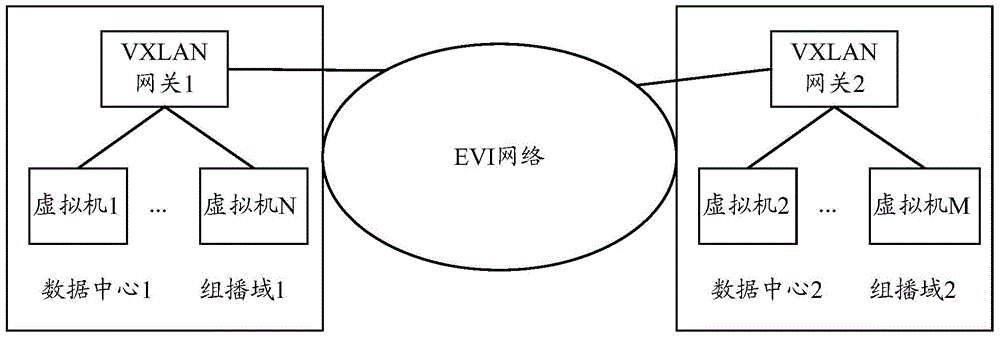
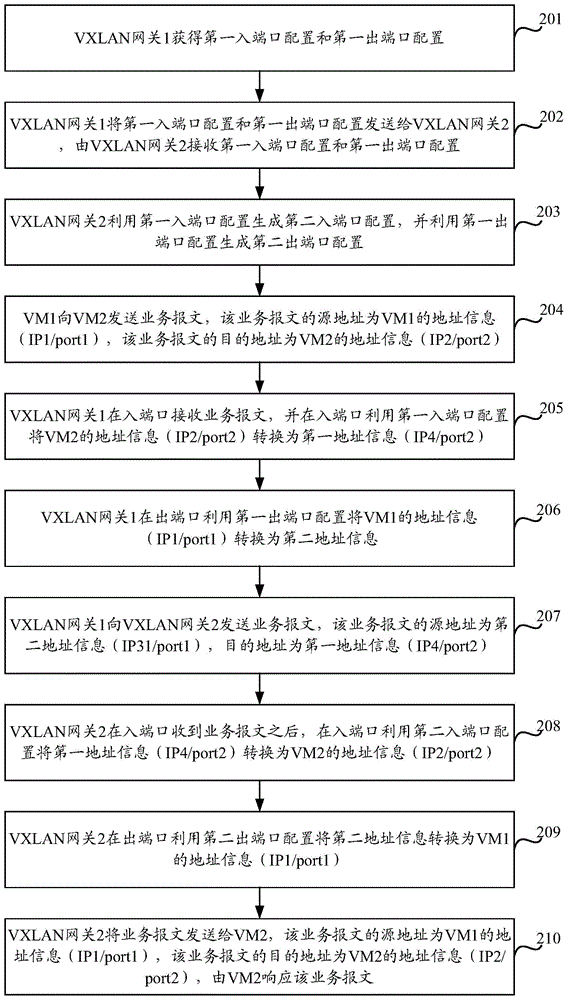
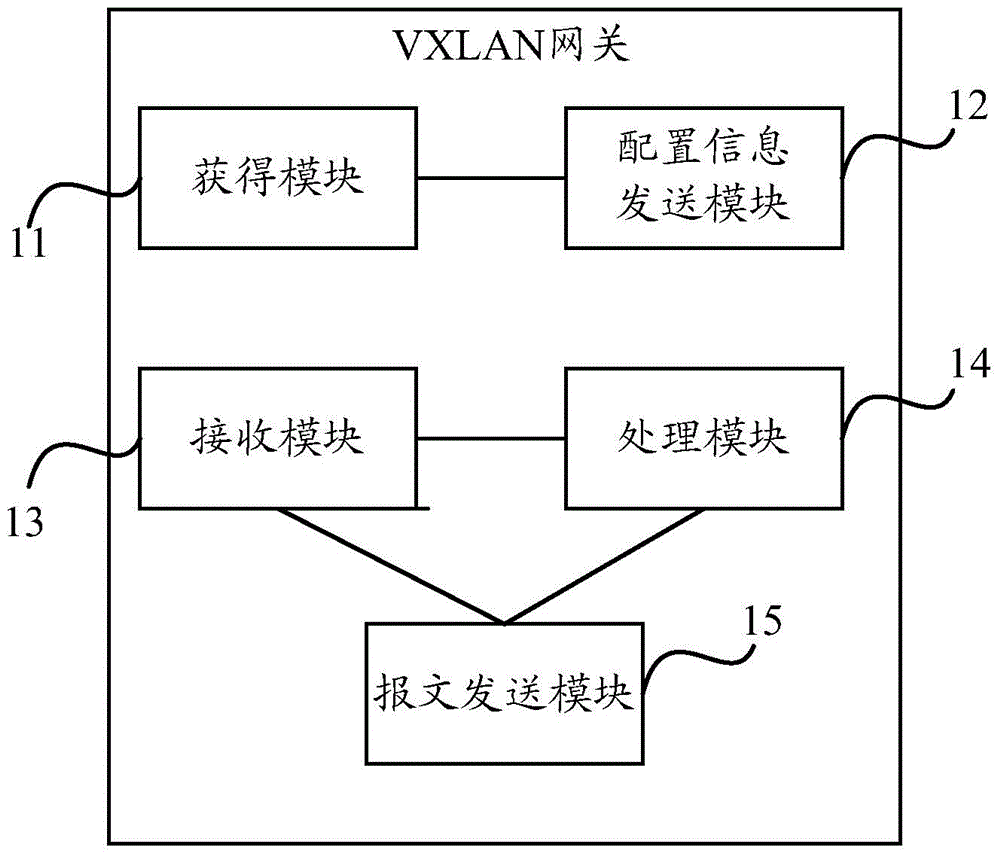
ActiveCN104468306AAvoid interruptionRealize Layer 2 interconnectionNetworks interconnectionData centerDistributed computing
The invention discloses a message transmission method and device in the VXLAN network. The method includes the steps that a first VXLAN gateway obtains first input port allocation and first output port allocation; the first VXLAN gateway transmits the first input port allocation and the first output port allocation to a second VXLAN gateway; the second VXLAN gateway generates second input port allocation through the first input port allocation and generates second output port allocation through the second input port allocation; when the first VXLAN gateway receives a service message, a destination address of the service message is converted through the first input port allocation, a source address of the service message is converted through the first output port allocation, and the converted service message is transmitted to the second VXLAN gateway. In the embodiment, interruption of interaction of the service message between virtual machines of different data centers is avoided.
Owner:NEW H3C TECH CO LTD
Network device management method
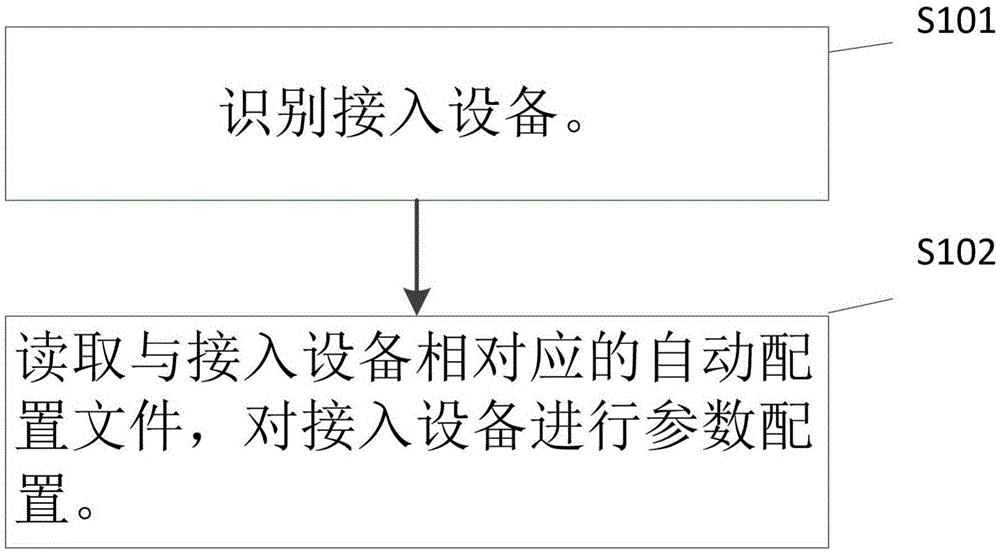
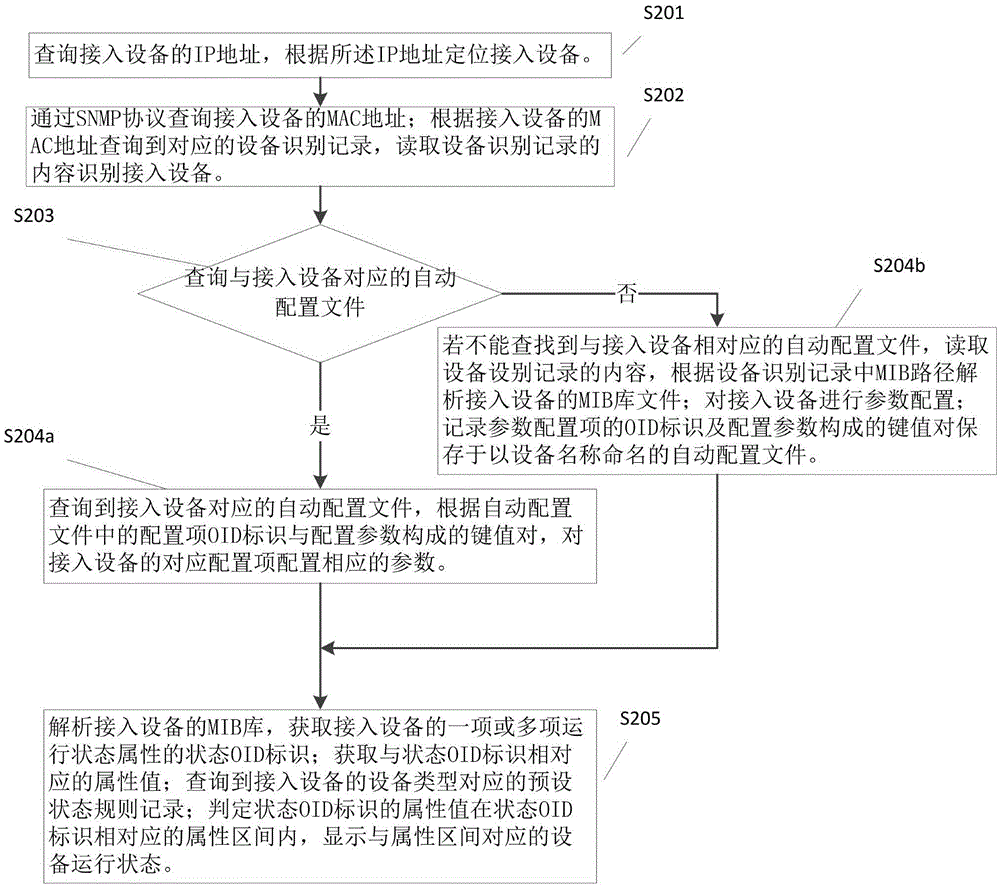
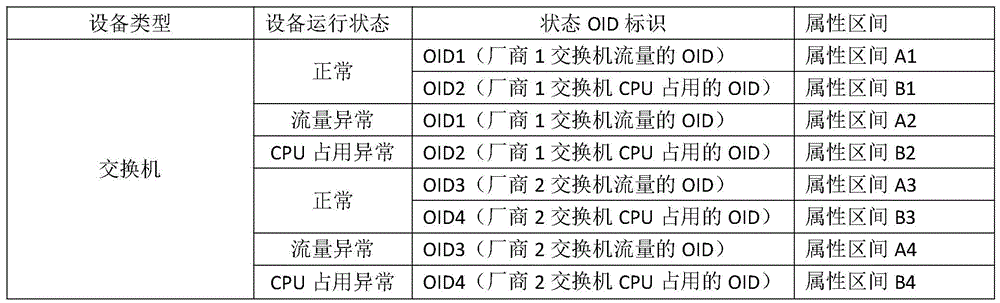
ActiveCN105634829ASimplify configuration workProvide work efficiencyData switching networksTroubleshootingAuto-configuration
The present invention provides a network device management method. The network device management method comprises: identifying a connected device; and reading an automatic configuration file corresponding to the connected device, to perform parameter configuration on the connected device. The connected device is identified, and the automatic configuration file corresponding to the connected device is read, so that the connected device is automatically configured. Therefore, work of configuring the network device is greatly simplified, and in addition to the working efficiency is improved, the risk of errors caused by manual network device configuration is avoided, and maintenance and troubleshooting are facilitated.
Owner:ZHEJIANG ANGEL SCI & TECH CO LTD
Method for realizing configuration of network devices
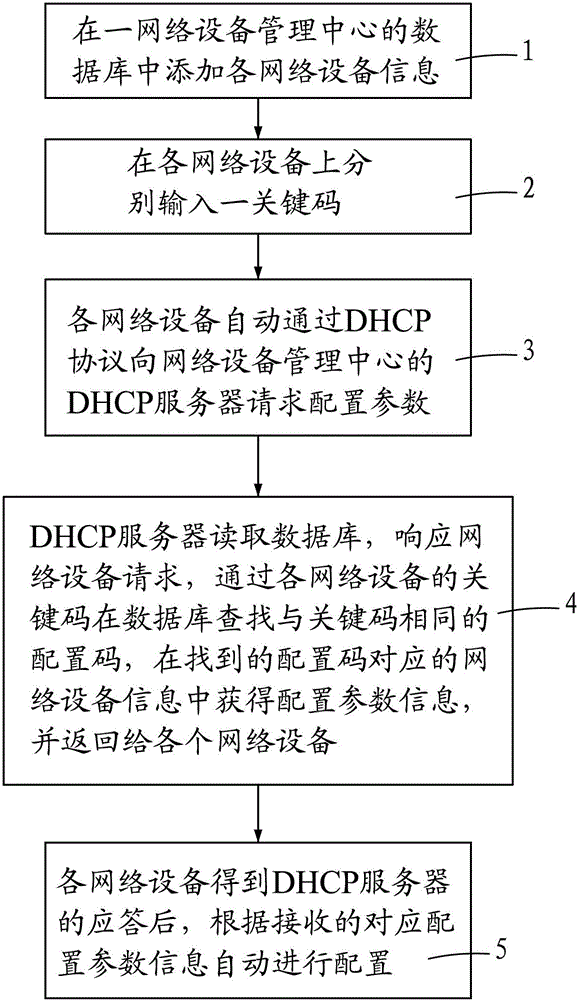
ActiveCN102752135ASimplify configuration workLower education requirementsData switching networksComputer networkNetwork block device
The invention provides a method for realizing the configuration of network devices, which specifically comprises the following steps that: 1, the information of each network device is added into a database of a network device management center; 2, a key code is respectively inputted into each network device; 3, each network device asks a DHCP (dynamic host configuration protocol) server of the network device management center to configure parameters automatically through a DHCP protocol; 4, the DHCP server reads the database, responds to the request of each network device, searches a configuration code same as the key code in the database through the key code of each network device, acquires configuration parameter information in network device information corresponding to the searched configuration code, and returns the configuration parameter information to each network device; and 5, each network device automatically carries out configuration according to the received corresponding configuration parameter information. By using the method disclosed by the invention, the problem that a plurality of contents are required to be configured on the traditional network device is solved; and because only a key code is required to be configured, the operation of the construction and installation personnel is greatly simplified, and the installation operation is easy, therefore, the method is easily completed by persons with low cultural level.
Owner:FUJIAN STAR NET COMM
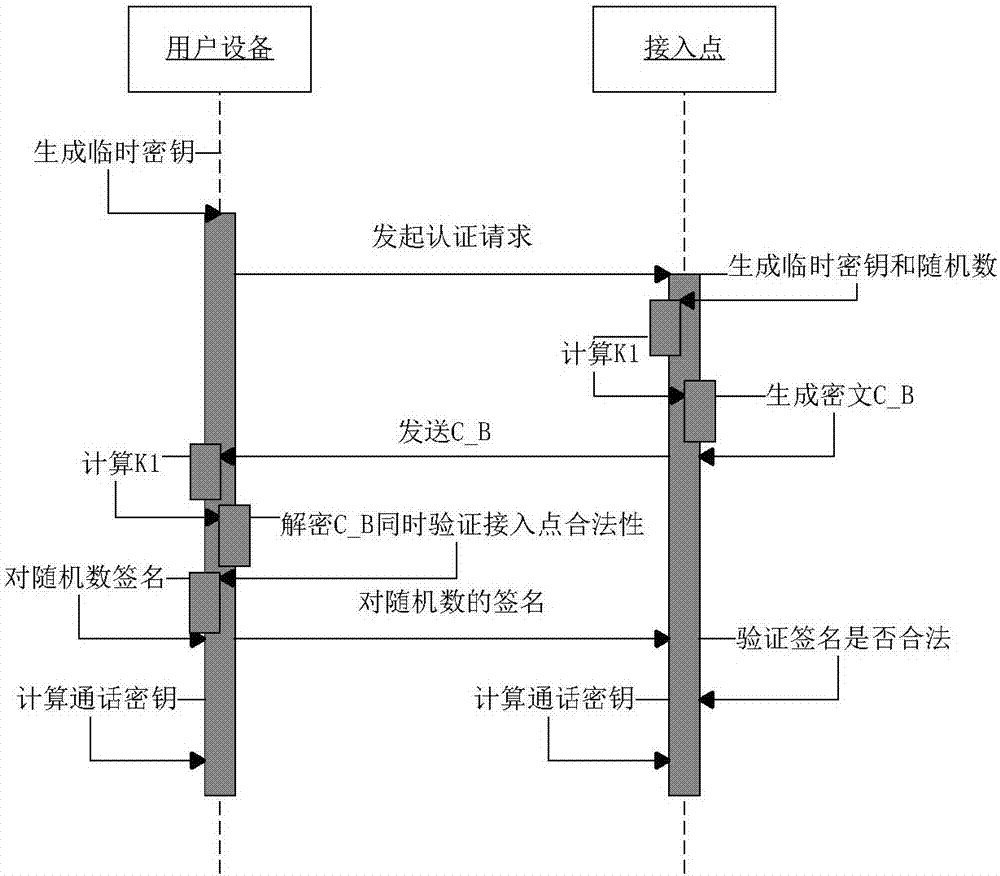
Wireless network access method based on NFC certificateless authentication
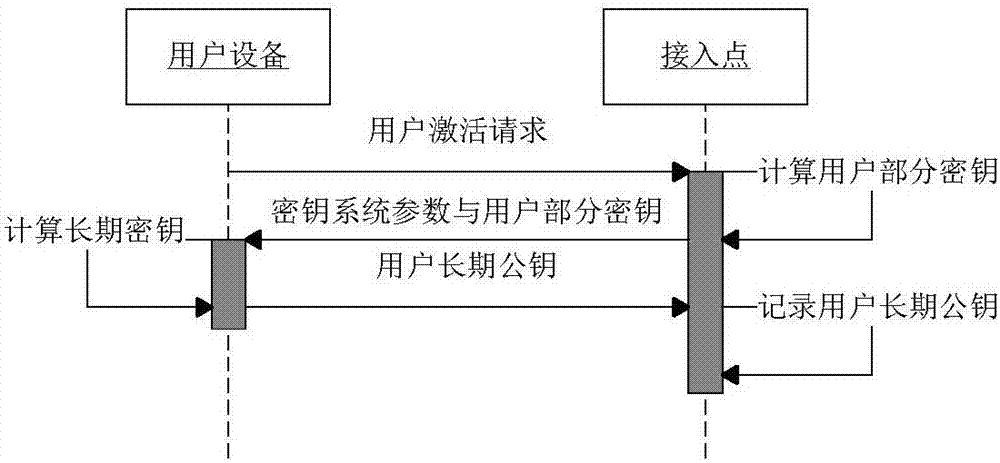
ActiveCN106992866ASimplify the steps to access the networkSimplify configuration workKey distribution for secure communicationPublic key for secure communicationAccess methodPhishing
Wireless network access authentication is a guarantee for wireless local area network security. At present, security problems such as wireless network monitoring, a phishing AP (Access Point) and illegal access are exposed in a wireless network access mode. In order to improve the wireless local area network access security and convenience, the invention provides a wireless network access method based on NFC certificateless authentication. The method comprises the steps that user equipment establishes a communication channel of a point-to-point working mode with a near field communication module of an access point AP through the near field communication module, wherein the channel is taken as a security channel for transmitting parameters when certificateless authentication is carried out; and a user, as an initiator in near field communication, initiates an activation and authentication request to a target AP, and after the user passes identity authentication, the user and a WLAN carry out encrypted transmission on information through a symmetrical key negotiated by two parties. The method has the perfect forward security; the eavesdropping, phishing and illegal access security problems can be effectively prevented; the security of the wireless local area network is improved; and steps of accessing the network by the user are simplified.
Owner:GUANGDONG UNIV OF TECH
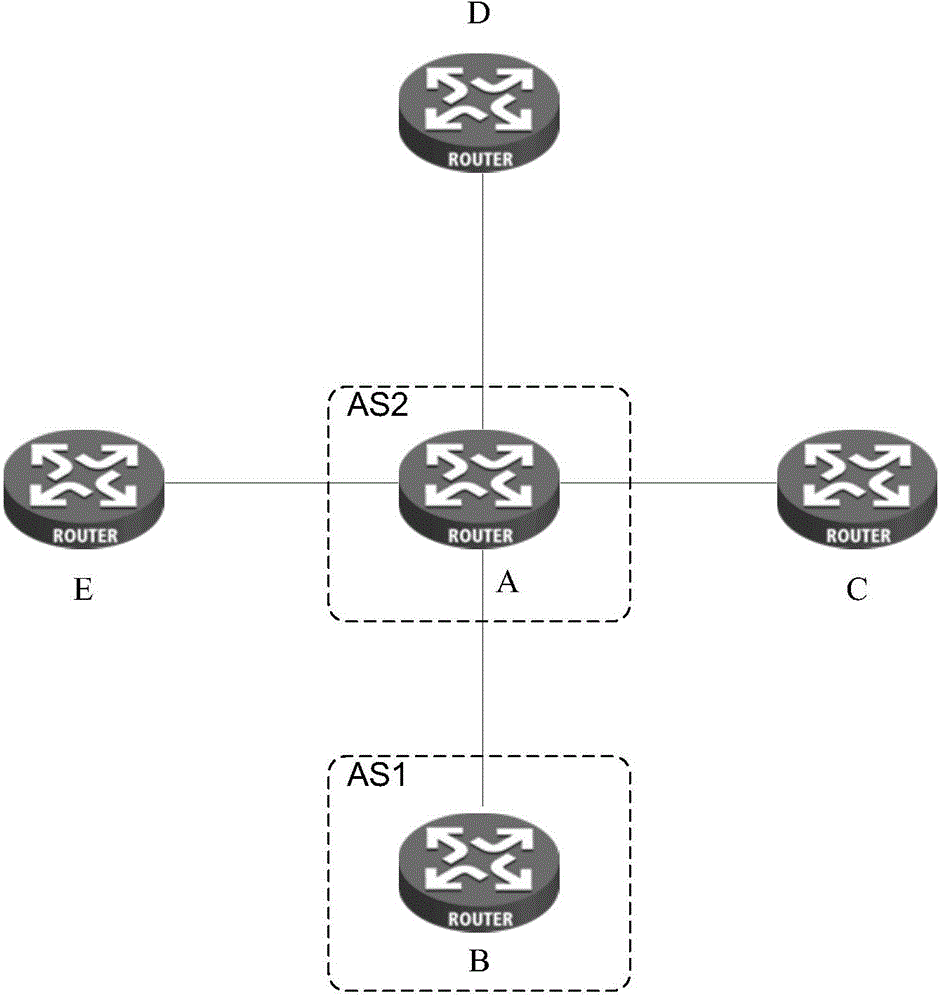
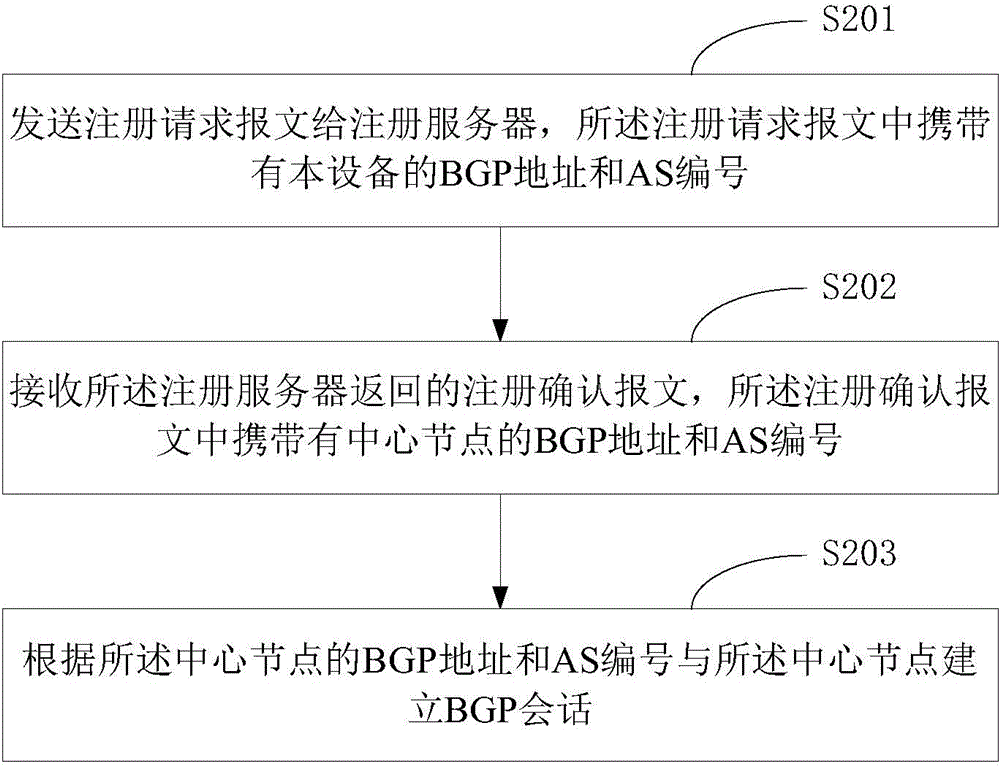
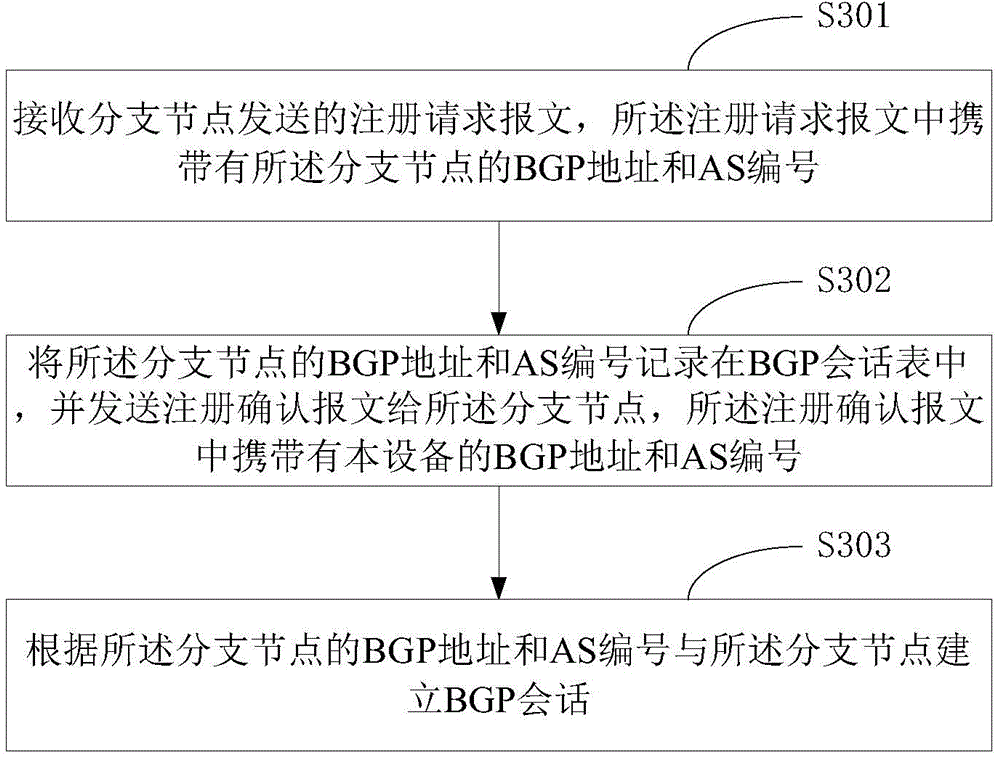
BGP conversation establishing method and device
ActiveCN104092687ASimplify configuration workFlexible function expansionTransmissionNetwork managementComputer science
The invention provides a BGP conversation establishing method and device. The method comprises the steps that a registration request message is sent to a registration server, wherein the registration request message carries a BGP address and an AS serial number of the device; a registration confirmation message returned by the registration server is received, wherein the registration confirmation message carries a BGP address and an AS serial number of a central node; a BGP conversation with the central node is established according to the BGP address and the AS serial number of the central node. According to the technical scheme, the configuration work of network management personnel is simplified.
Owner:NEW H3C TECH CO LTD
Data collecting method and system based on HTML stream processing
InactiveCN101859321ASolve the accuracy problemSolve associativityTransmissionSpecial data processing applicationsUser needsData stream
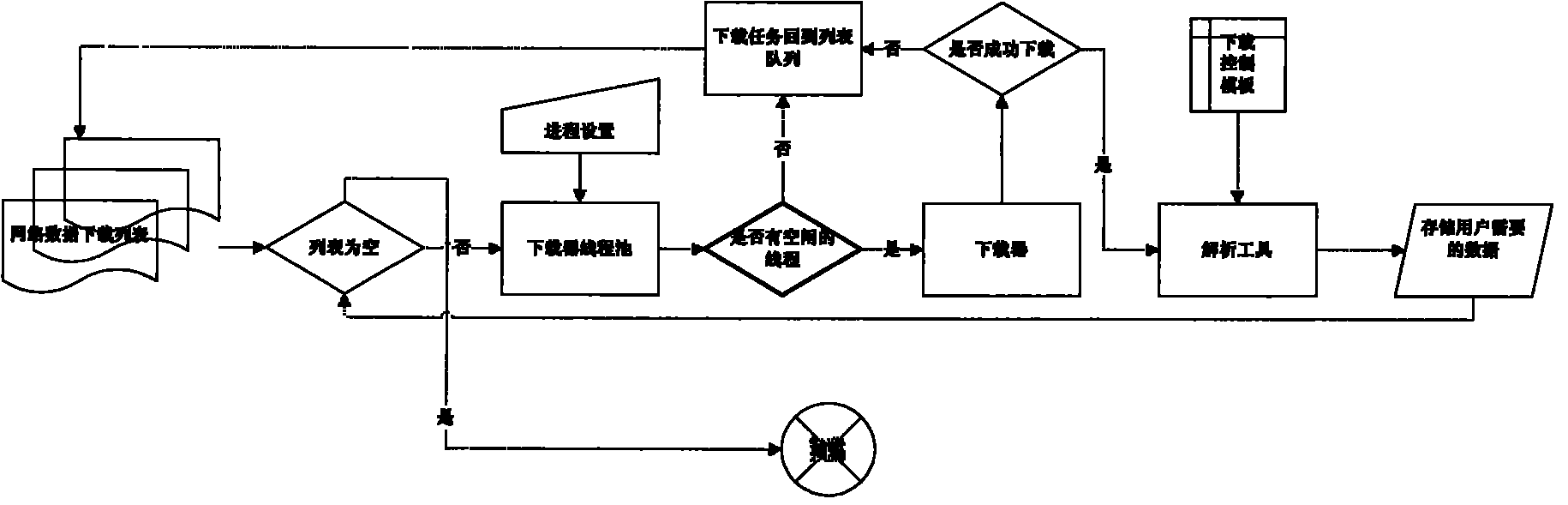
The invention belongs to the technical field of webpage information extraction, and particularly discloses a data collecting method and a data collecting system based on HTML stream processing, wherein the data collecting system consists of the multi-thread collector which guarantees working speed, a download control template which guarantees working accuracy and a data storage system. The system can collect the user-needed network data via a simple template configuration. Practical application proves that the invention has excellent stabilization, high practicability and high efficiency.
Owner:FUDAN UNIV
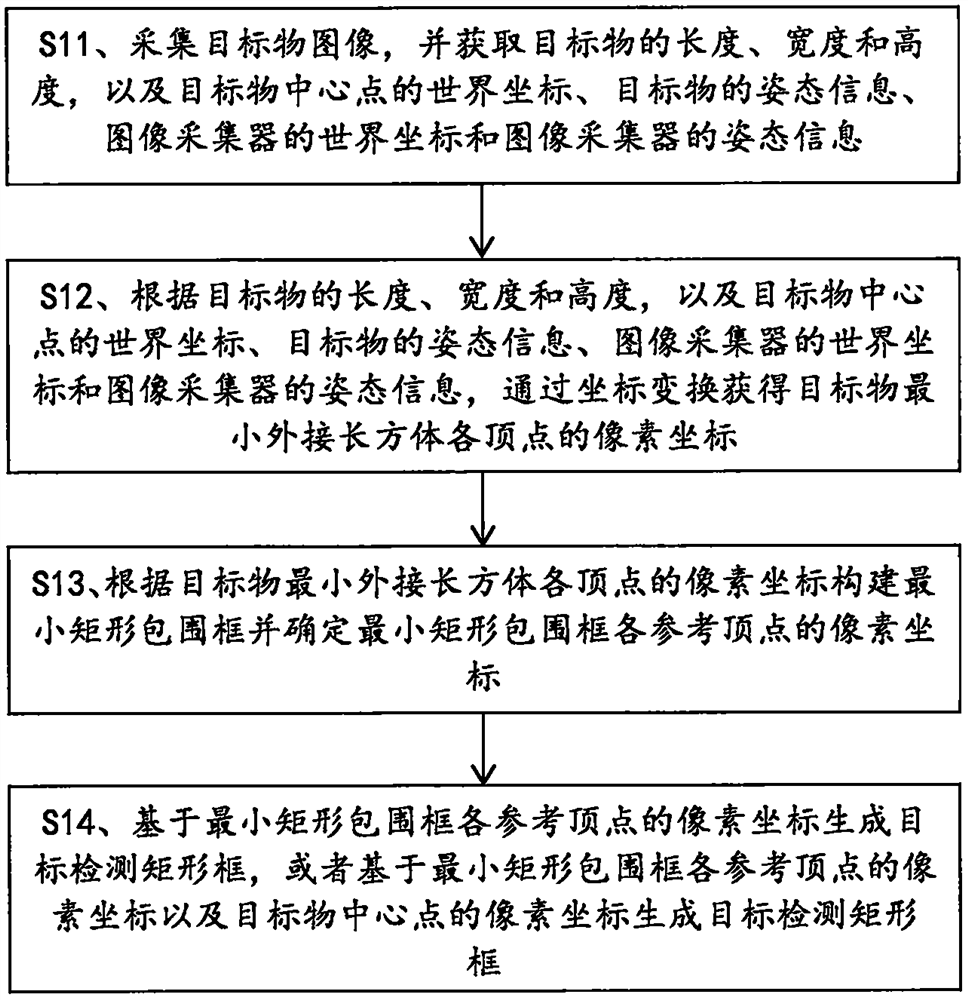
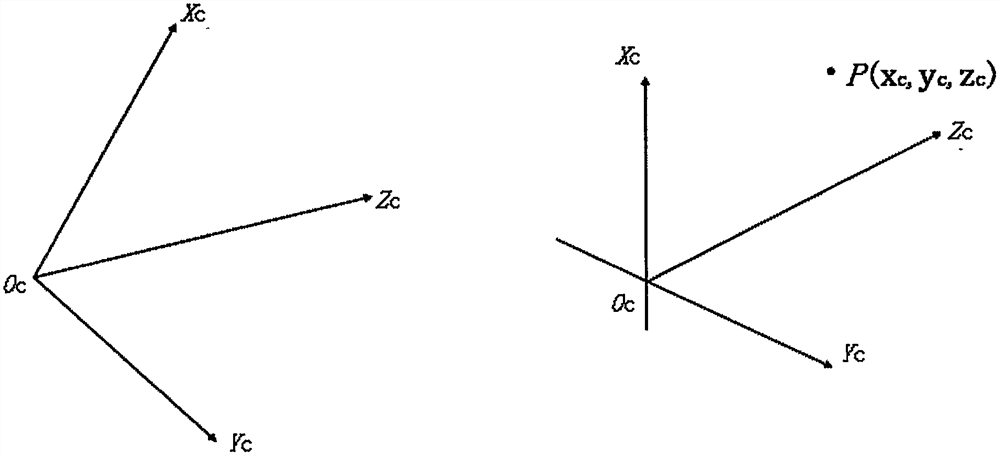
Target detection box generation method and image data automatic labeling method and system
PendingCN112818990ARealize automatic generationEasy to operateCharacter and pattern recognitionPattern recognitionComputer graphics (images)
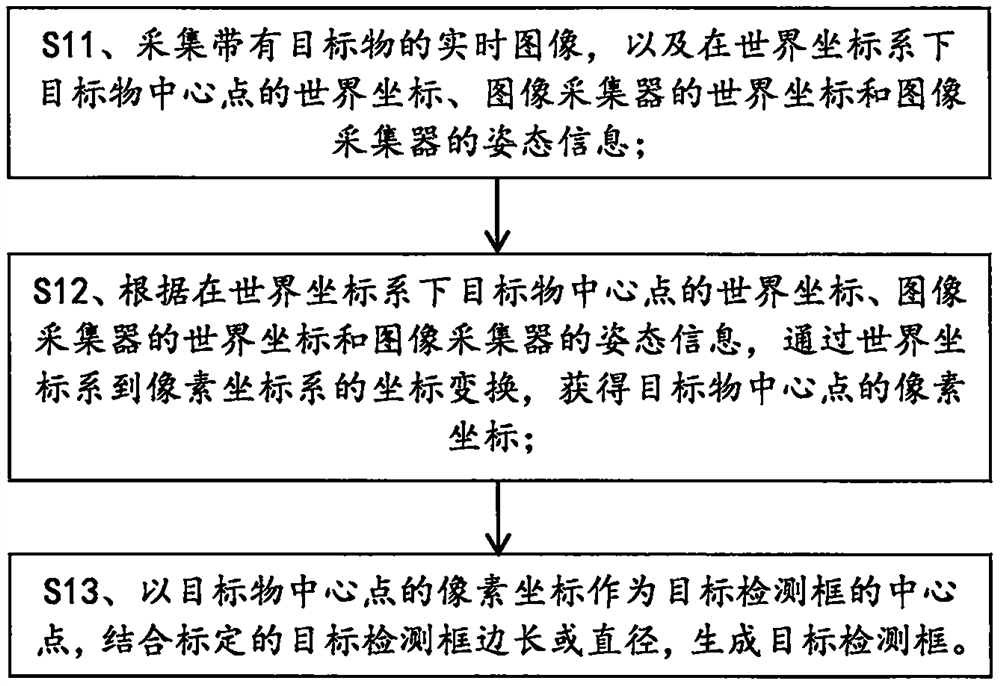
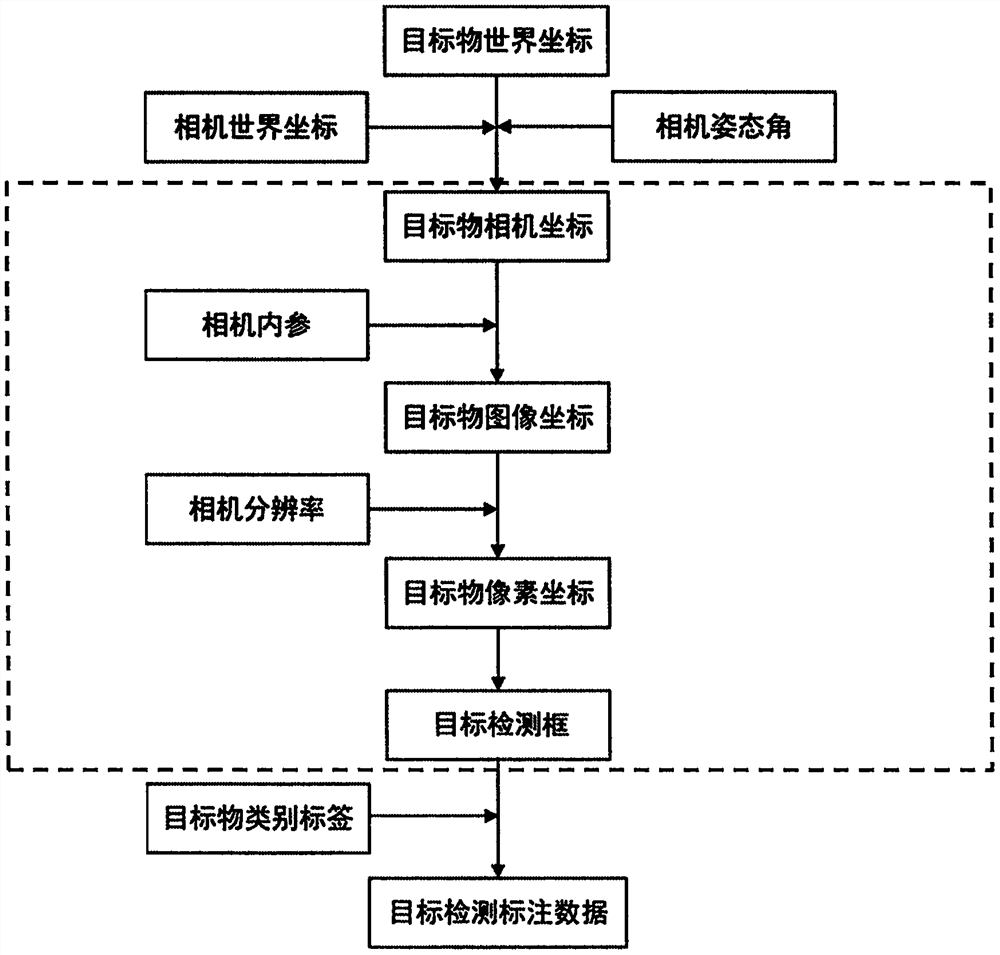
The invention provides a target detection box generation method and an image data automatic labeling method and system. The generation method comprises the following steps: acquiring a real-time image with a target object, a world coordinate of a center point of the target object under a world coordinate system, a world coordinate of an image collector and attitude information of the image collector; according to the world coordinate of the central point of the target object in the world coordinate system, the world coordinate of the image collector and the attitude information of the image collector, obtaining the pixel coordinate of the central point of the target object through coordinate transformation from the world coordinate system to a pixel coordinate system; and taking the pixel coordinate of the central point of the target object as the central point of a target detection box, and in combination with the calibrated side length or diameter of the target detection frame, generating the target detection box. According to the method, on the premise that human intervention is not needed, automatic generation of the target detection data is truly realized, and the operation process is simplified.
Owner:NAT INNOVATION INST OF DEFENSE TECH PLA ACAD OF MILITARY SCI
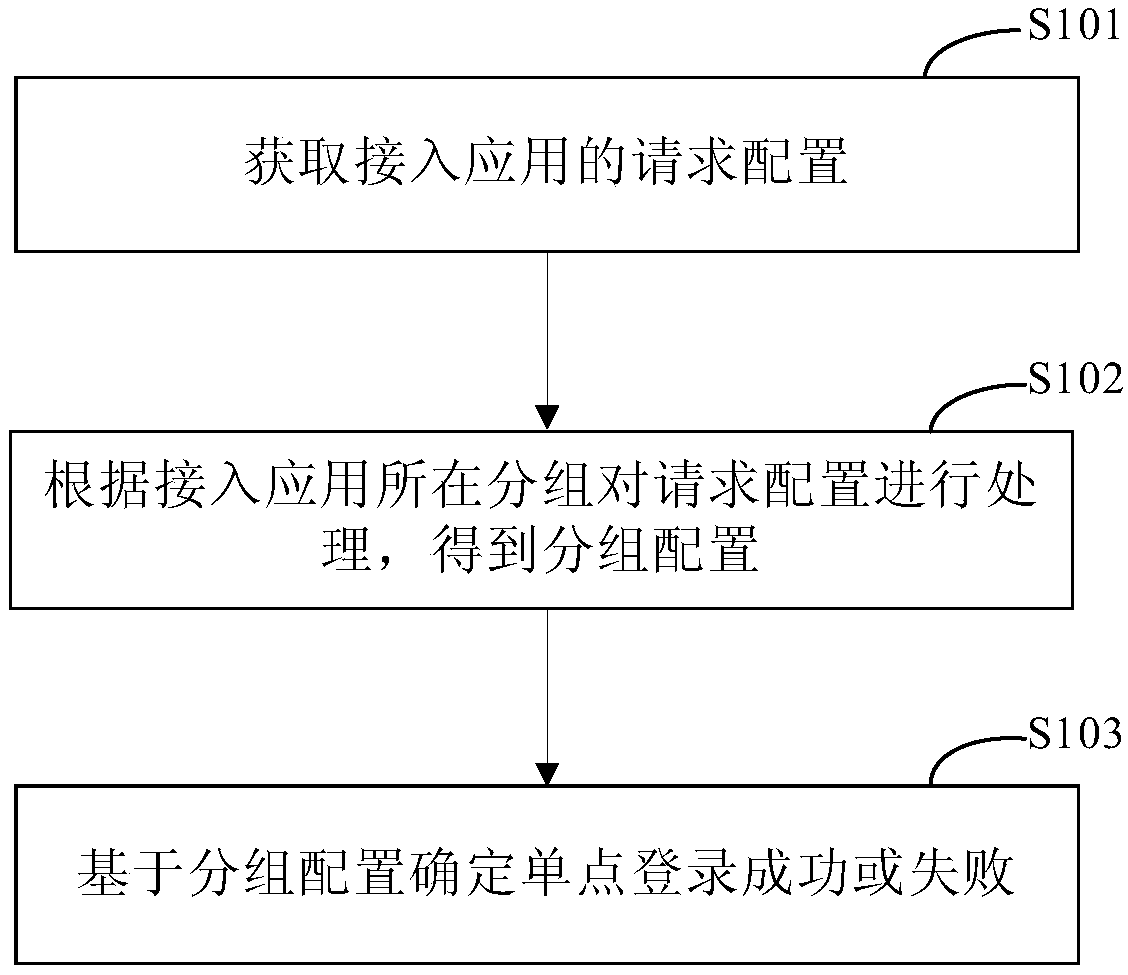
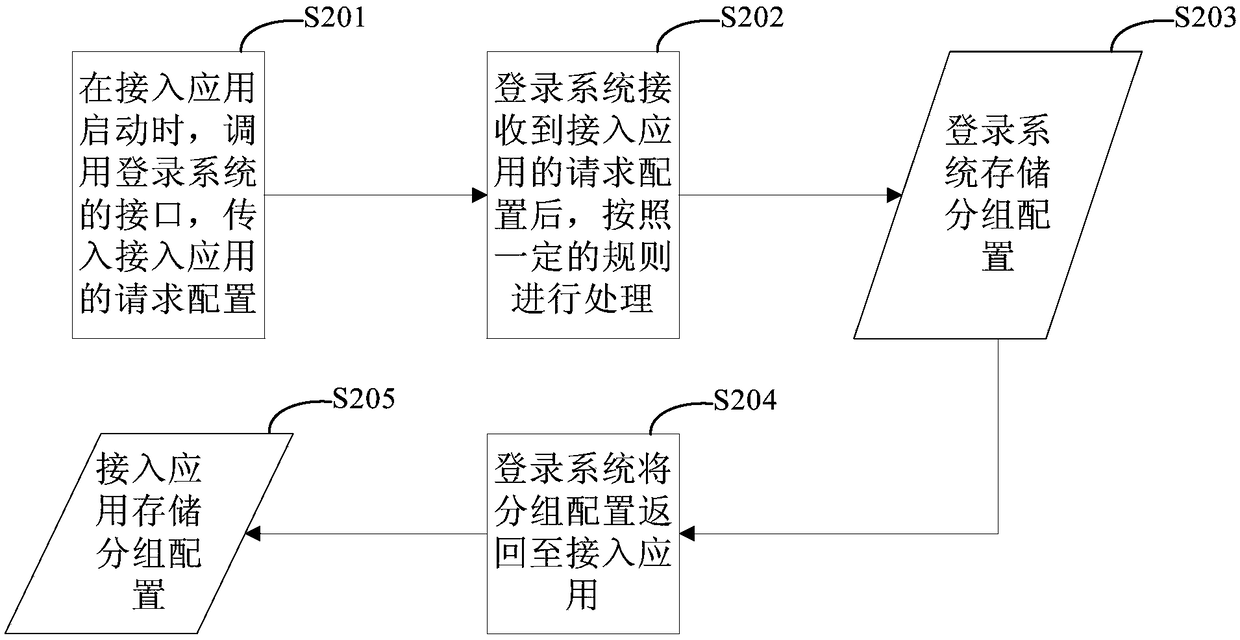
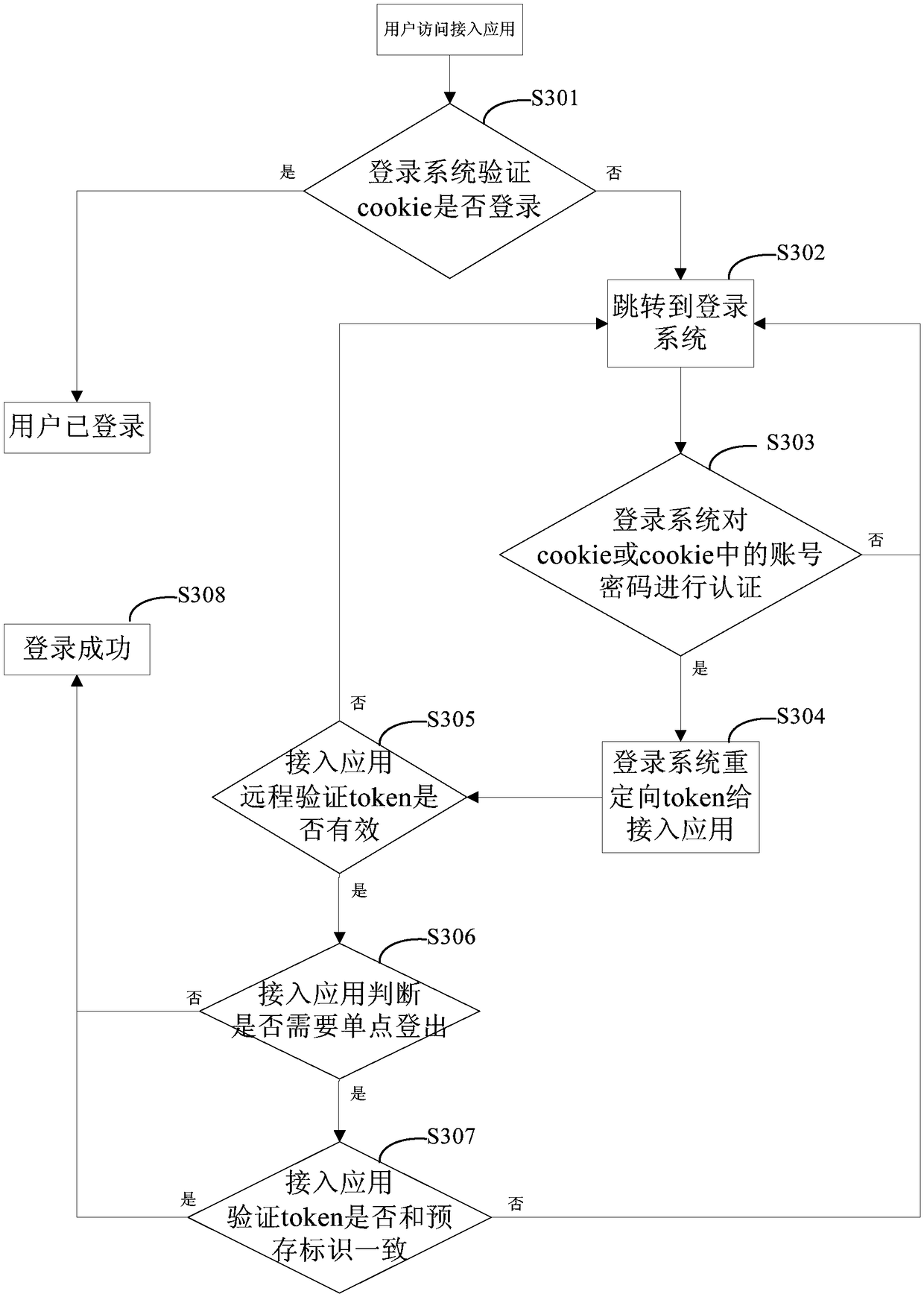
Single sign on method and apparatus
The invention discloses a single sign on method and apparatus, and relates to the technical field of computers. A specific embodiment of the method comprises the following steps: obtaining a request configuration of an access application; processing the request configuration according to a packet where the access application is located to obtain a packet configuration; and determining whether thesingle sign on succeeds or fails based on the packet configuration. By adoption of the specific embodiment, the login states of access applications in different packets can be isolated, multiple datasources are supported, and single sign on and single-person online are achieved; and the configuration work of the access application is simplified.
Owner:JINGDONG TECH HLDG CO LTD
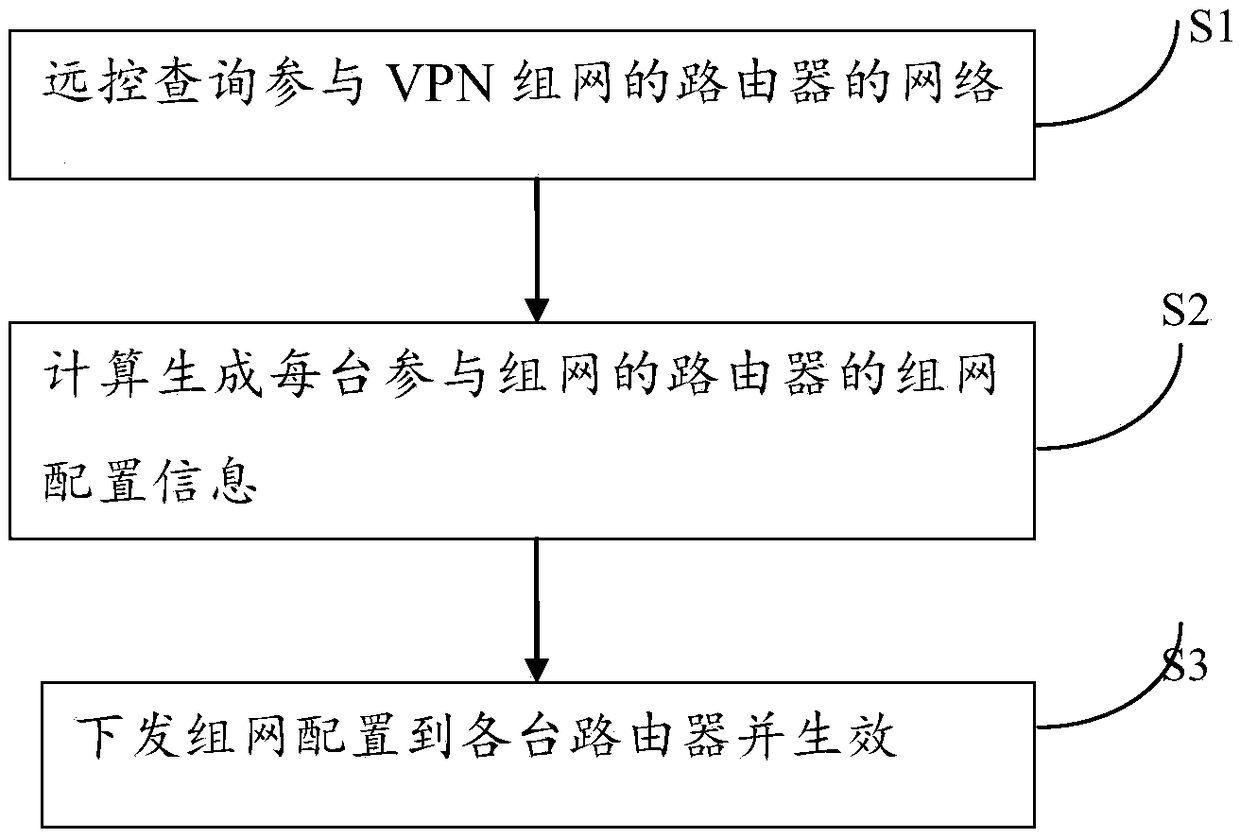
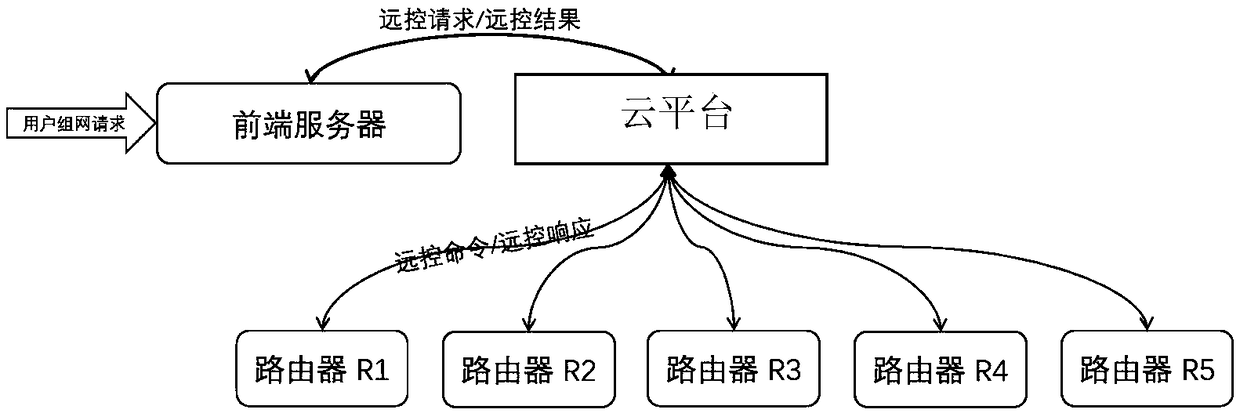
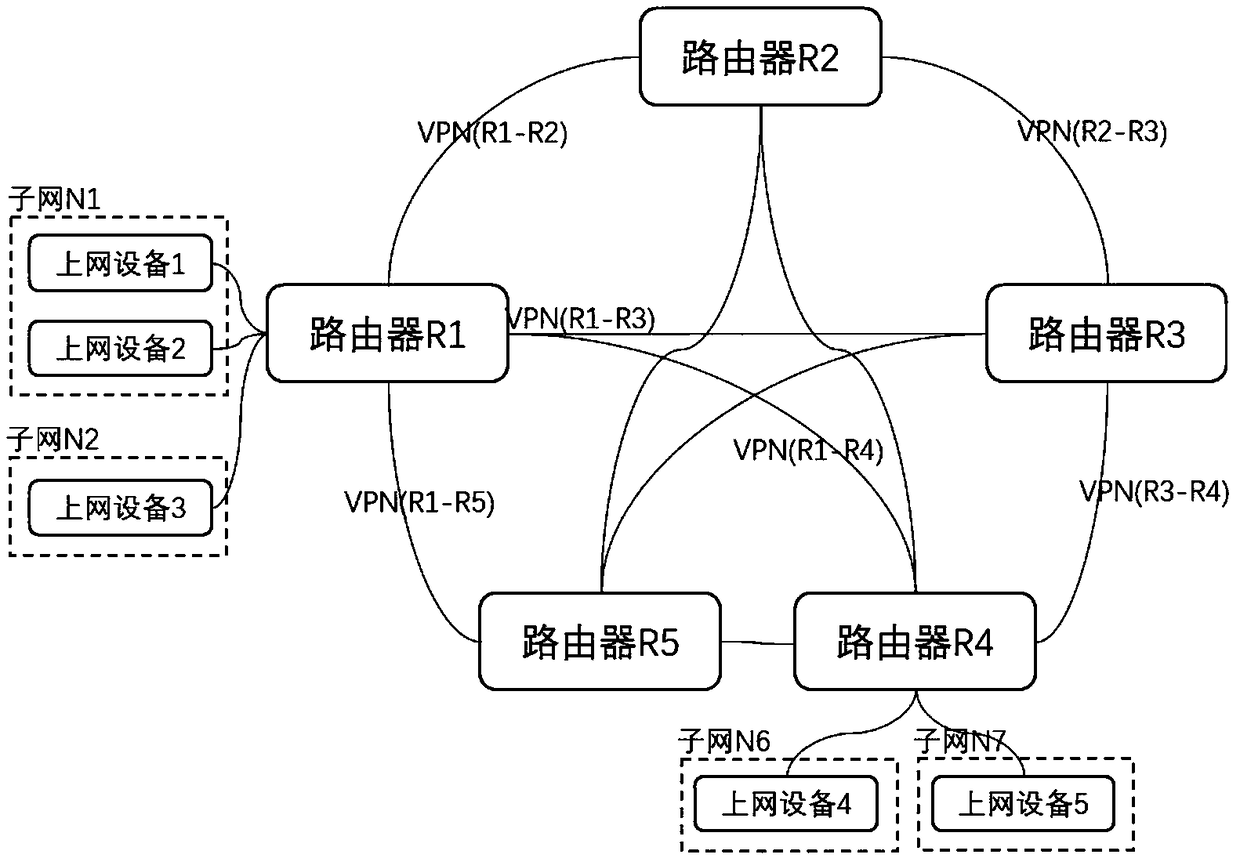
Multi-router VPN automatic networking method and system based on centralized remote control
InactiveCN109120726ASimplify configuration workAvoid configuration errorsNetworks interconnectionRemote controlDistributed computing
The invention discloses a multi-router VPN automatic networking method and system based on centralized remote control. The method includes the steps: remotely querying network parameters of routers participating in the VPN networking; calculating network configuration information of each router participating in the networking, wherein the networking configuration information includes a VPN connection relationship between all routers, and the static route relationship between the VPN of each router and the subnets owned by other routers; transmitting the networking configuration to each routerand taking effect. The method remotely controls multiple routers distributed in different locations in a centralized manner through a cloud platform, and automatically establishes a VPN network between the routers to solve the problems of complex configuration, difficult expansion, poor availability, and difficult monitoring and maintenance of the operation status in the multi-router VPN networking scenario.
Owner:QUANXUN HUIJU NETWORK TECH BEIJING CO LTD
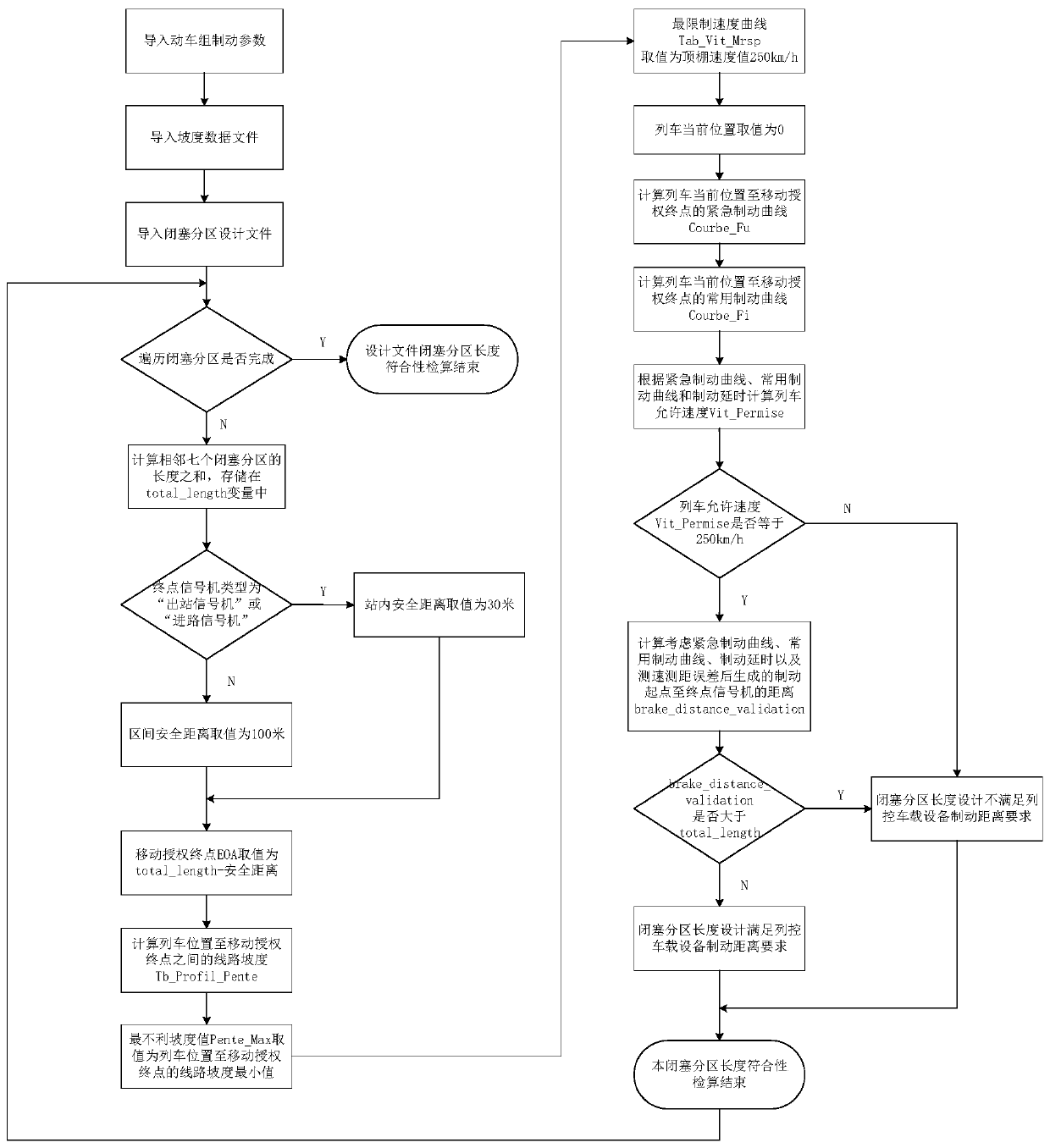
Conformance checking and calculation method and platform of block section length
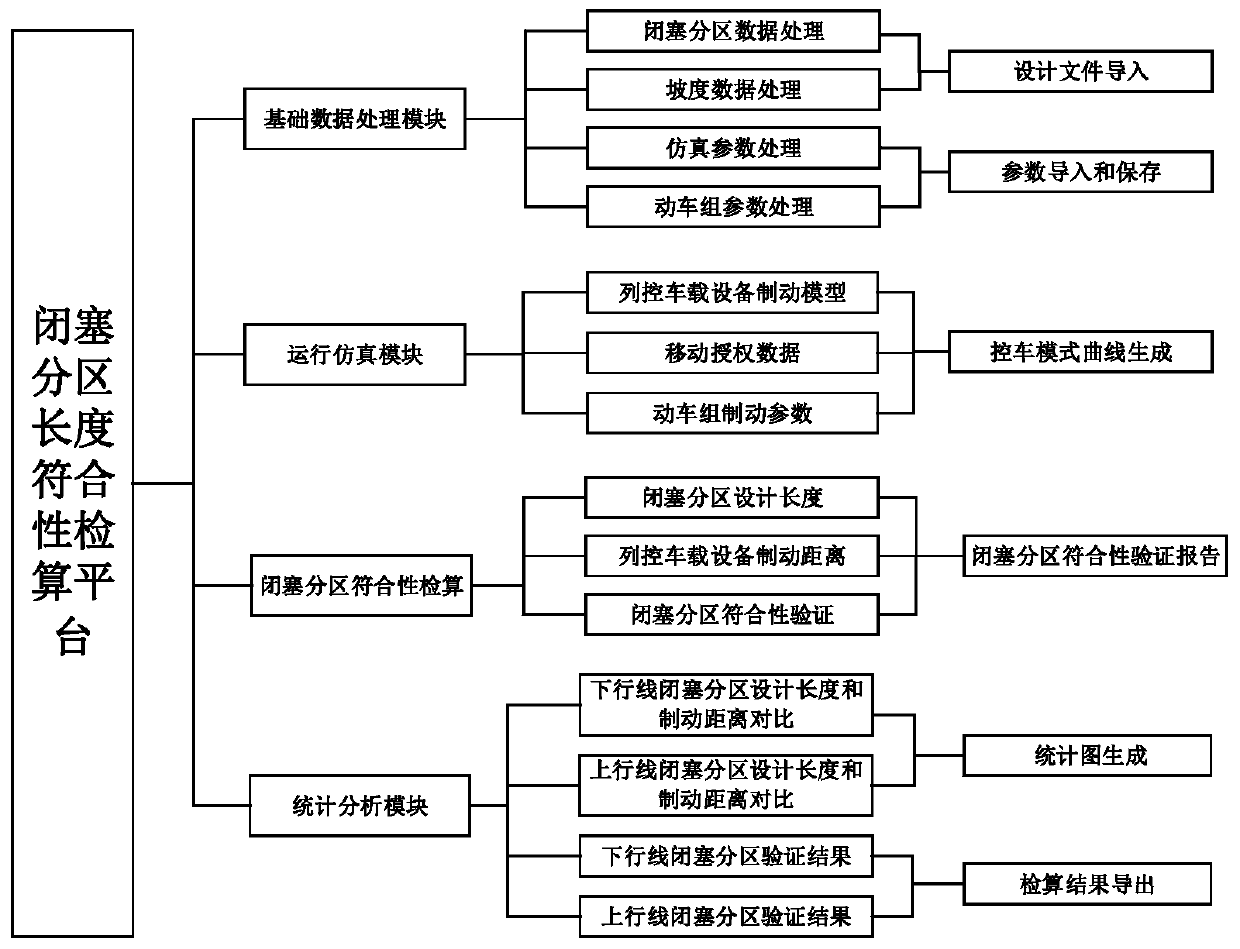
ActiveCN110239590ASimplify configuration workThe testing process is simpleRailway traffic control systemsSignalling indicators on vehicleTest flowBraking distance
The invention discloses a conformance checking and calculation method and platform of the block section length. According to the conformance checking and calculation method and platform, a brake model of column control vehicle-mounted equipment is adopted, length design and gradient data of a newly-built railway block section are automatically imported, and configuration working of simulation data is simplified; the conformance checking and calculation method and platform do not need simulate a running scene of a train-set in a newly-built railway, the test process is simplified, the checking and calculation period is shortened, and a conformance checking and calculation result of the block section length is fed back in time; the conformance checking and calculation method and platform automatically generate the conformance checking and calculation result of the newly-built railway block section length, and artificial misjudgment is avoided; and the conformance checking and calculation method and platform can visually display block section length design and the braking distance required by the train-controlled vehicle equipment, and a checking and calculation result file is exported.
Owner:SIGNAL & COMM RES INST OF CHINA ACAD OF RAILWAY SCI +3
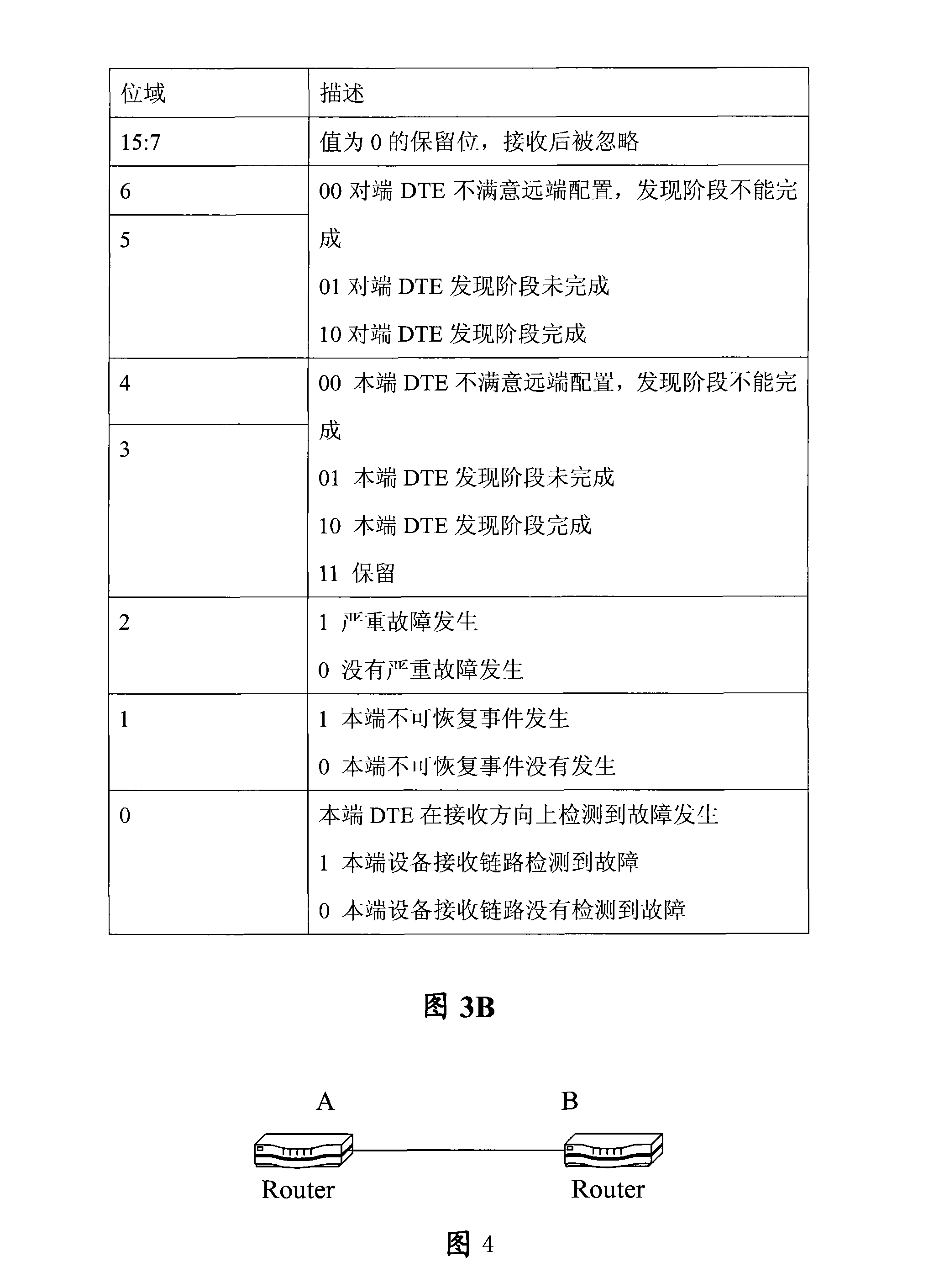
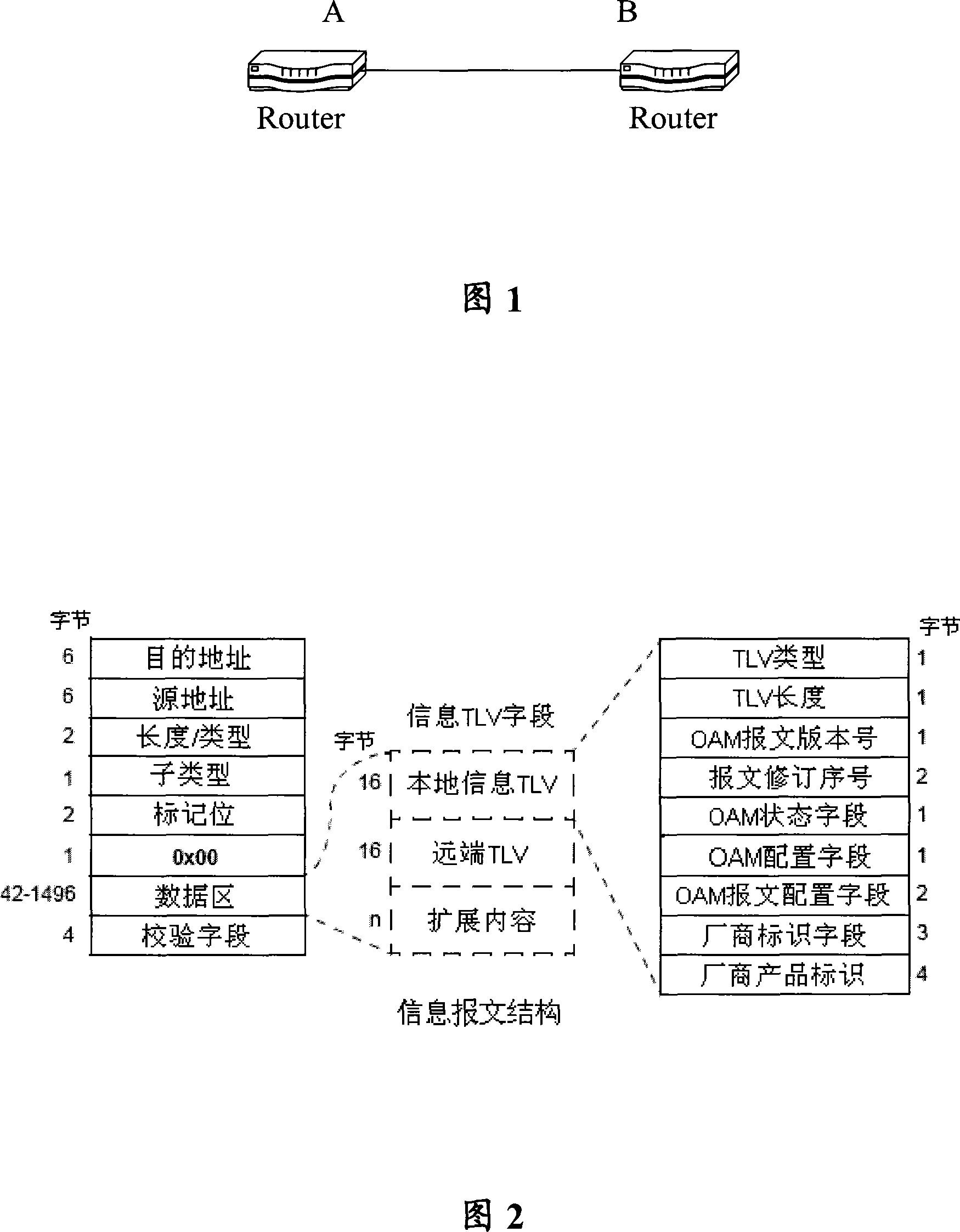
Report negotiation method, device and system
The embodiment of the invention discloses a method, a device and a system used in message negotiation, wherein after a port in passive OAM mode receives an 802.3ah Hello message sent by an active port, bit-by-bit analysis of the OAM configuration field in the message is completed; if the passive port supports the corresponding function of a bit but the active port does not support, the function is shielded. The embodiment of the invention ensures that the passive mode port can furthest ensure that the OAM configuration mode of the passive mode port keeps synchronization with an active mode port; moreover, both ports do not need to be set at the same configuration, thereby simplifying port configuration.
Owner:HUAWEI TECH CO LTD
Smart home control method and system
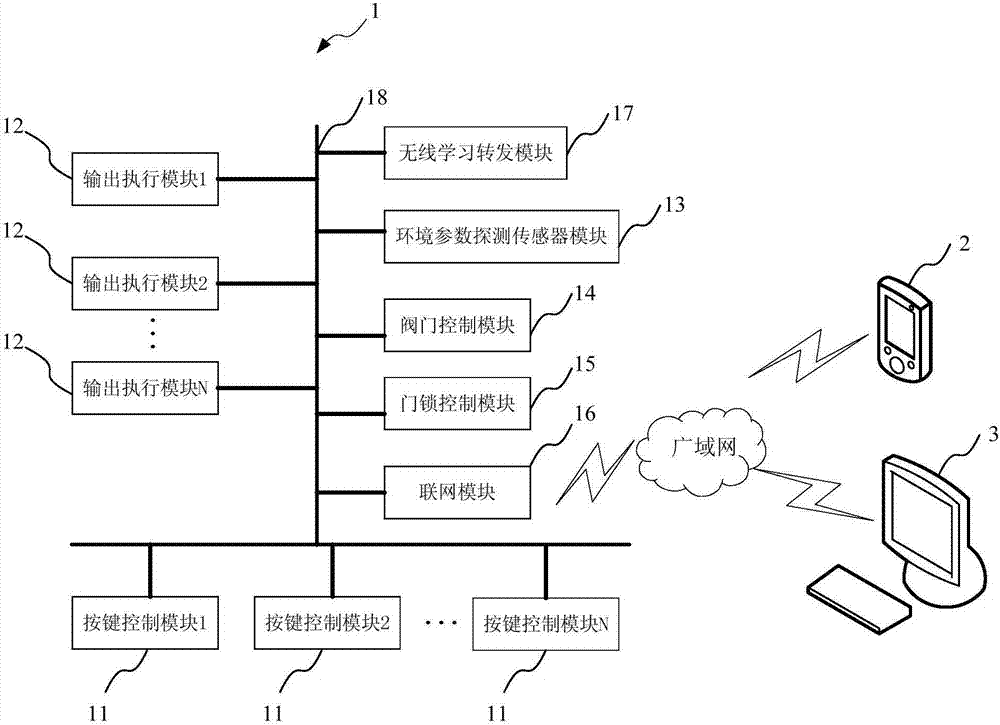
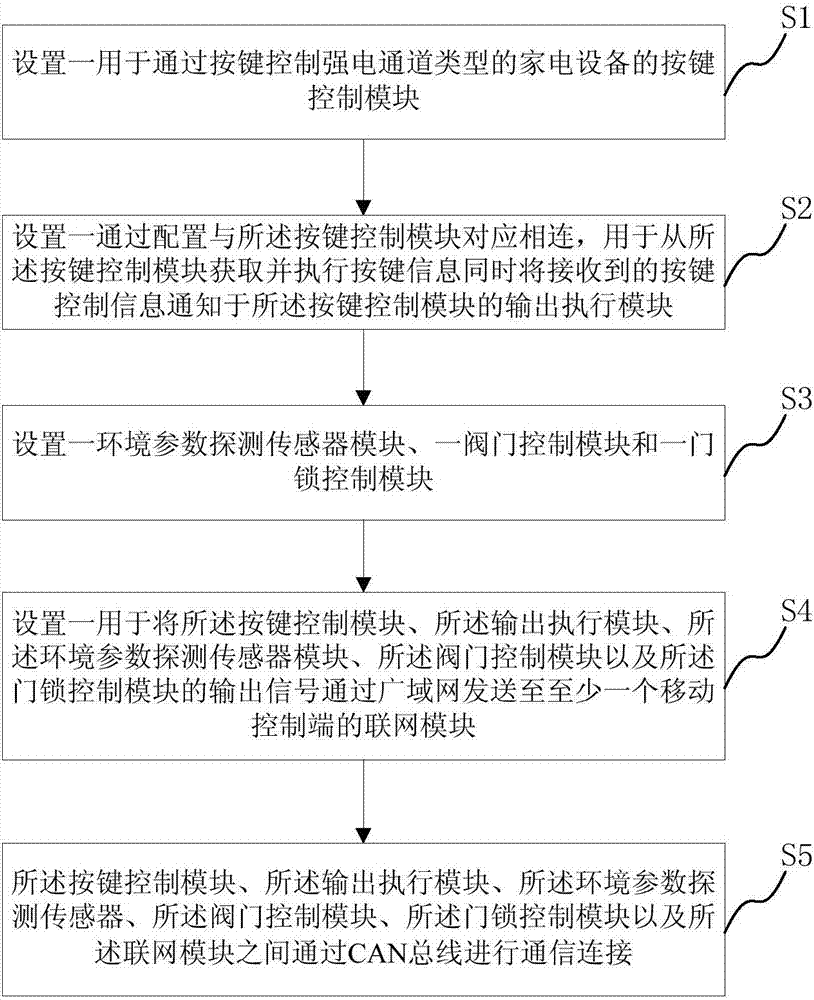
InactiveCN107168074ASimplify configuration workReduce configuration and maintenance costsComputer controlProgramme total factory controlEmbedded systemChannel types
The present invention provides a smart home control method and system. The system comprises key control modules, output execution modules, an environmental parameter detection sensor module, a valve control module, a door lock control module and a networking module; the key control modules are used for controlling home appliances of a strong electric channel type through keys; the output execution modules are correspondingly connected with the key control modules through configuration and are used for obtaining key information from the key control modules, executing the key information and informing the key control modules of received key control information; the networking module is used for sending the output signals of the other modules to at least one control end through a wide area network; and the key control modules, the output execution modules, the environmental parameter detection sensor module, the valve control module, the door lock control module and the networking module are in communication with one another through a CAN bus. According to the smart home control method and system of the invention, a CAN bus data broadcast communication mode is adopted, and therefore, the smart home control method and system have the advantages of simple configuration, flexible networking, low maintenance cost and high economic practicability.
Owner:SHANGHAI ETABOFT INFORMATION TECH
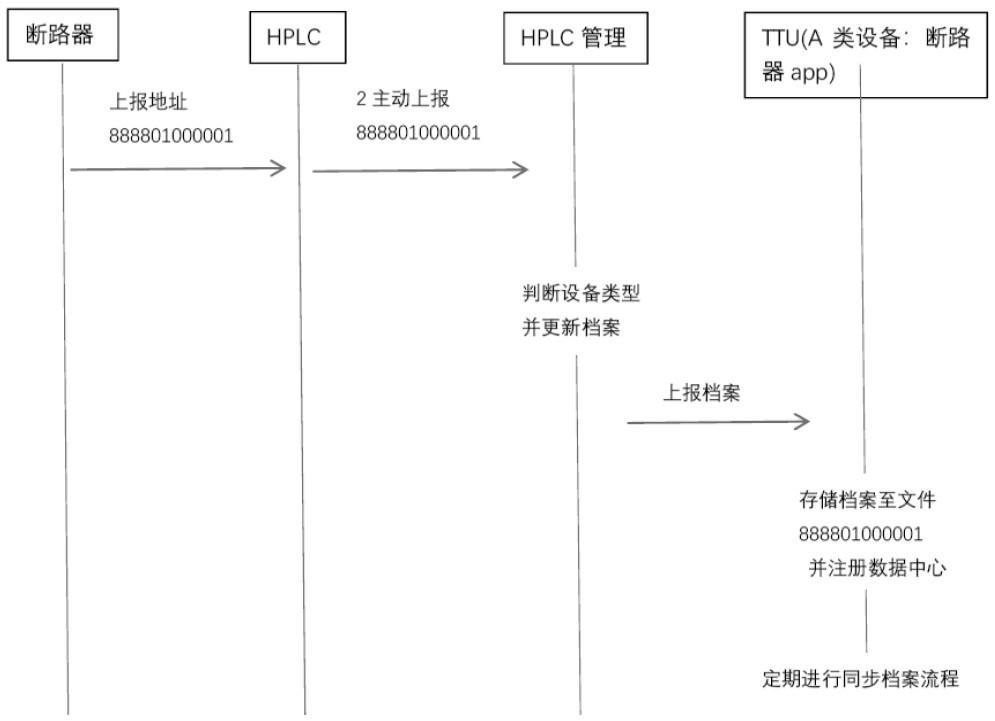
Plug-and-play method for power distribution Internet of Things end-side equipment based on HPLC communication
PendingCN113659713ASimplify device configuration workUneven levels of resolutionCircuit arrangementsSustainable buildingsData transmissionPlug and play
The invention discloses a plug-and-play method for power distribution Internet of Things end-side equipment based on HPLC communication and belongs to the technical field of power distribution. The method comprises the following steps: step A, plug-and-play end-side equipment is installed on site; B after the end-side equipment is powered on and is scanned and found by a transformer area intelligent fusion terminal, the transformer area intelligent fusion terminal collects information of the end-side equipment; and C, the transformer area intelligent fusion terminal generates a model file of the end-side equipment according to the information of the end-side equipment, and uploads the model file to the master station system through an MQTT protocol or an IEC104 mode. The method has the advantages that plug and play of the end side equipment can be achieved, data transmission between the end side equipment and the transformer area intelligent fusion terminal is achieved through HPLC communication, and the problems that at present, breakers and branch monitoring terminals of the end side equipment of a power distribution transformer area are various, and models are not uniform are solved.
Owner:SHIJIAZHUANG KE ELECTRIC +1
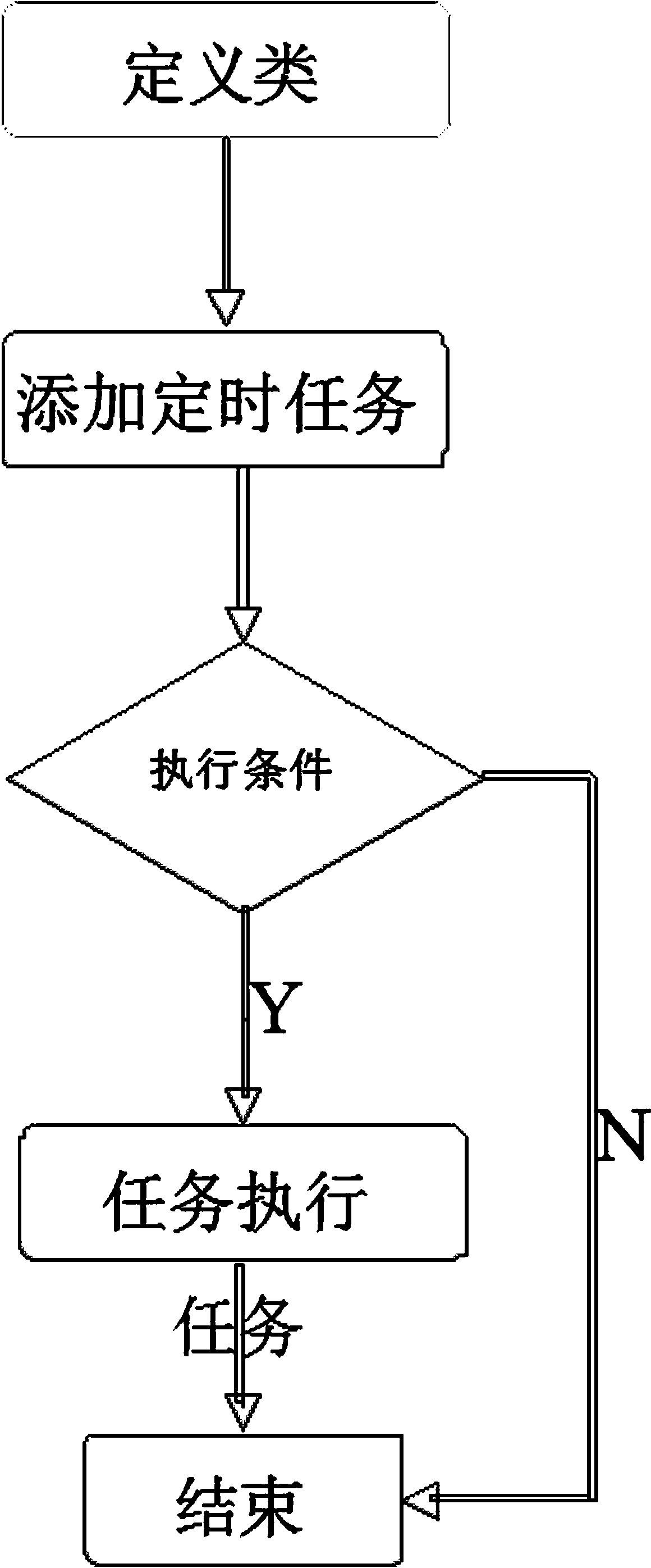
Method for achieving data synchronization through timing task based on cloud computing
InactiveCN103810281AEfficient sharingSimplify configuration workDatabase distribution/replicationSpecial data processing applicationsData synchronizationConcurrency control
The invention provides a method for achieving data synchronization through a timing task based on cloud computing. The method includes the specific implementation steps that firstly, a class is defined, the function of extracting required data is achieved, a sql statement is achieved, and a system automatically generates an xml message; the class is added to the timing task, the timing task is added, the name of the task, the name of the class, execution time, execution strategies and validity duration are added, and the timing task automatically synchronizes data according to system settings and time stamps or synchronization marks; eventually, the timing task executes data synchronization operation according to the execution strategies and the execution time, and the timing task is synchronized through a mechanism of a database lock; the timing task is destroyed after being executed. Compared with the prior art, the method for achieving data synchronization through the timing task based on cloud computing has the advantages that calling of concurrency control tasks under the cloud computing environment is achieved in a database lock mode, and the method is high in practicality, wide in application range and easy to popularize.
Owner:INSPUR GROUP CO LTD
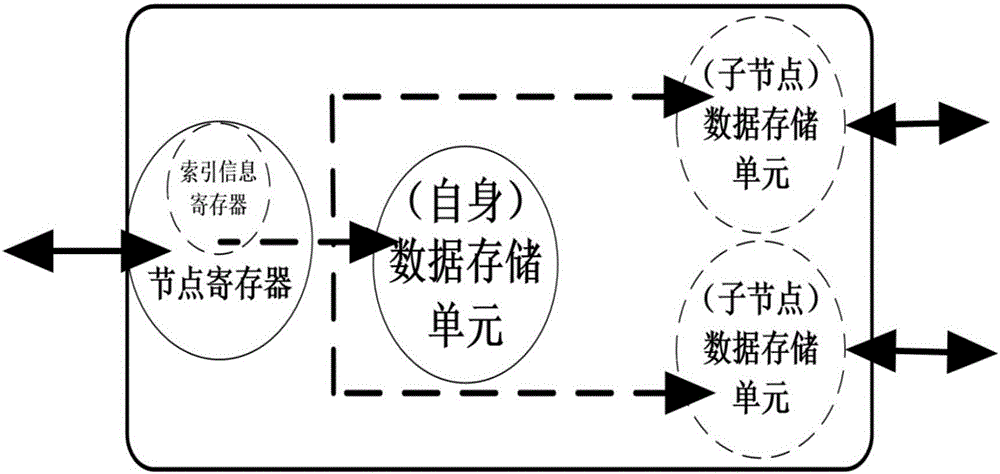
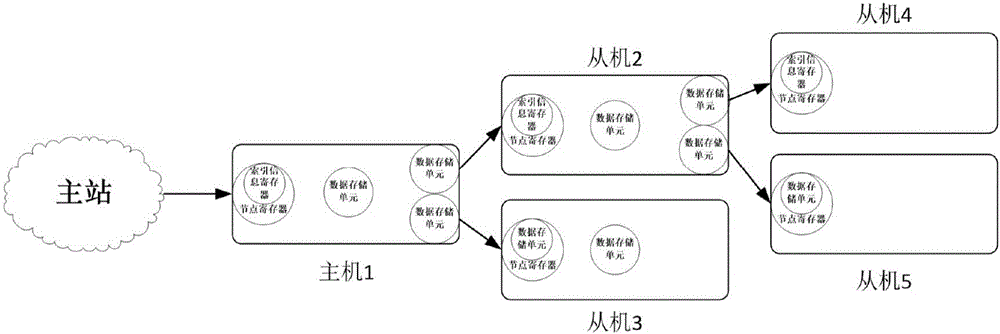
Communication device applied to intelligent network charge interactive terminal
InactiveCN106789203ASimple configurationIncrease flexibilityPower network operation systems integrationCircuit arrangementsIntelligent NetworkProcessor register
The invention discloses a communication device applied to an intelligent network charge interactive terminal. The communication device comprises an upper interface, a lower interface, an own data storage unit, a sub-node data storage unit and a node register, and further comprises an index information register, wherein the node register is used for collecting the data in the data storage units corresponding to this communication device and all lower communication devices therebelow; or the node register can collect the index information of the data through the internal index information register; the internal structures of the communication devices are consistent when the communication devices communicate with the upper or the lower, the data content corresponding to the node register is uploaded through the upper interface, and the transmission can be performed according to the required order of the upper communication device in the uploading. Therefore, an operation of independently performing master-slave configuration on each node according to a hierarchical relation between the nodes is unnecessary, the workload of the networking configuration is greatly reduced, and the communication device can be high-flexibly applied to various distribution automation fields.
Owner:ELEFIRST SCI & TECH
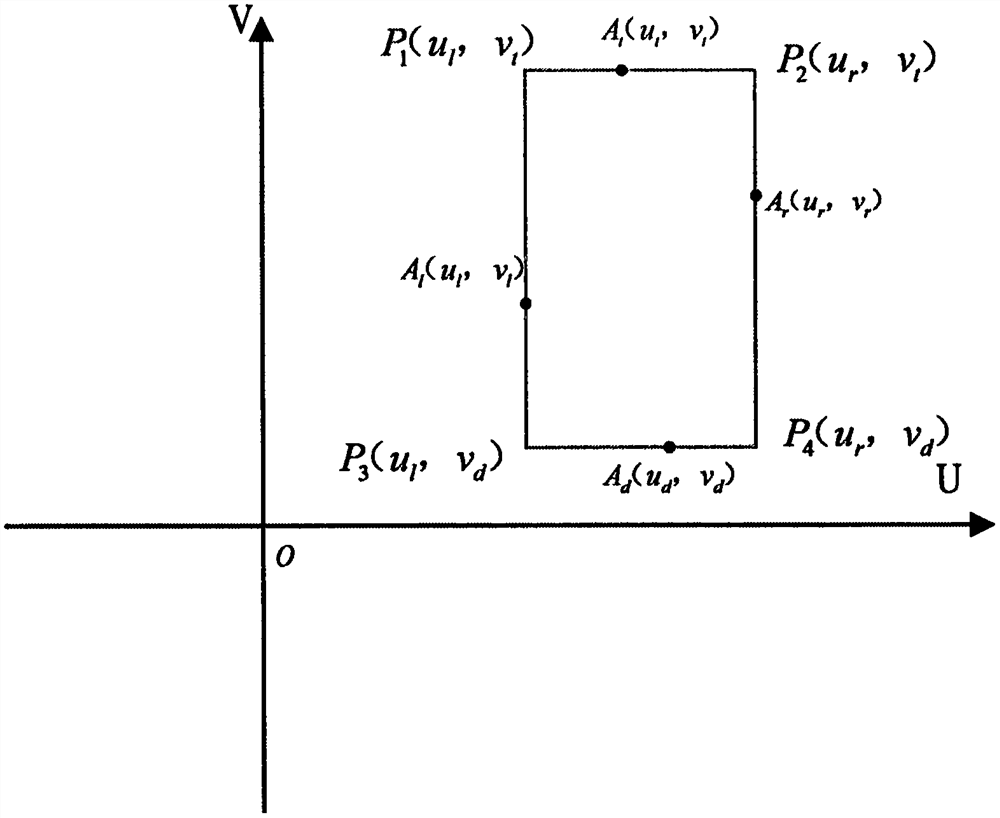
Image data target detection rectangular frame automatic labeling method and system
PendingCN113327283ARealize automatic generationEasy to operateImage enhancementImage analysisPattern recognitionComputer graphics (images)
The invention provides an image data target detection rectangular frame automatic labeling method and system. The labeling method comprises the steps of collecting a target object image and related information of a target object and an image collector; calculating pixel coordinates of each vertex of the minimum circumscribed cuboid of the target object; constructing a minimum rectangular bounding box according to the pixel coordinates of the vertexes of the minimum bounding cuboid of the target object, and determining the pixel coordinates of the reference vertexes of the minimum rectangular bounding box; and generating a target detection rectangular frame based on the pixel coordinates of the reference vertexes of the minimum rectangular bounding box, or generating the target detection rectangular frame based on the pixel coordinates of the reference vertexes of the minimum rectangular bounding box and the pixel coordinates of the central point of the target object. According to the method and the system, the automatic generation of the target detection rectangular frame can be really realized on the premise of not needing human intervention; besides, the operation process can be simplified, and the accuracy of labeling is ensured.
Owner:NAT INNOVATION INST OF DEFENSE TECH PLA ACAD OF MILITARY SCI
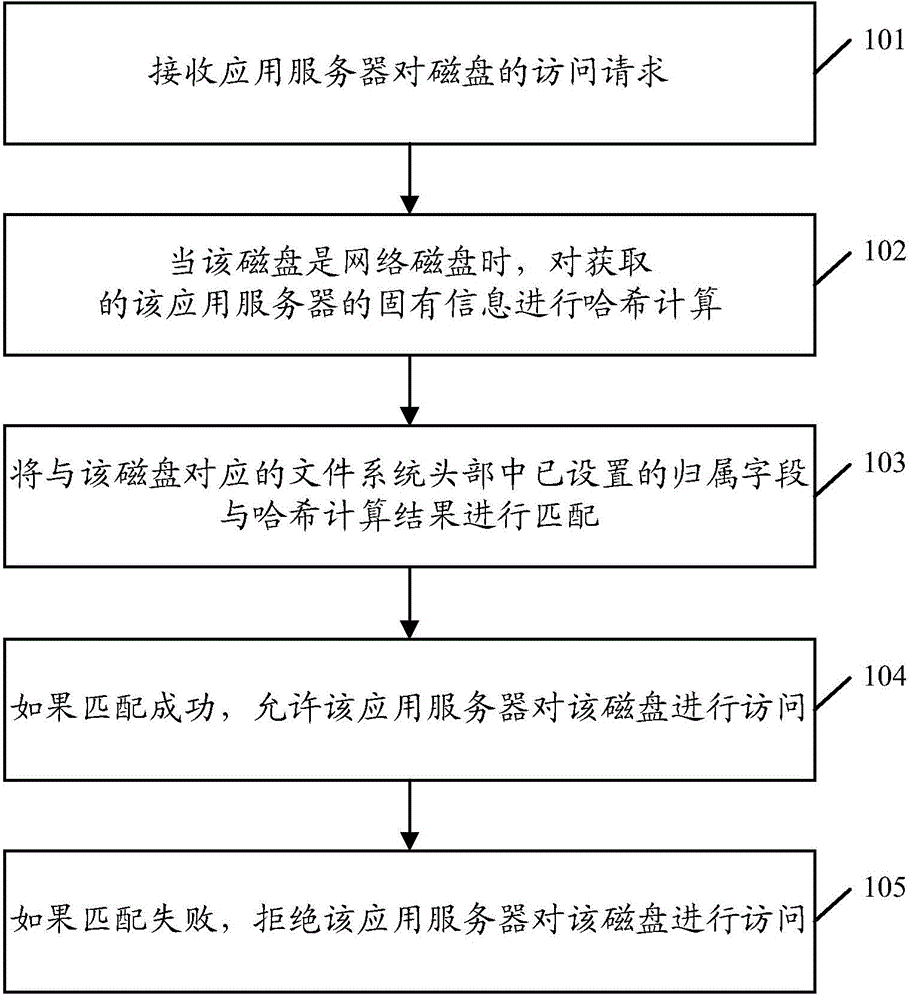
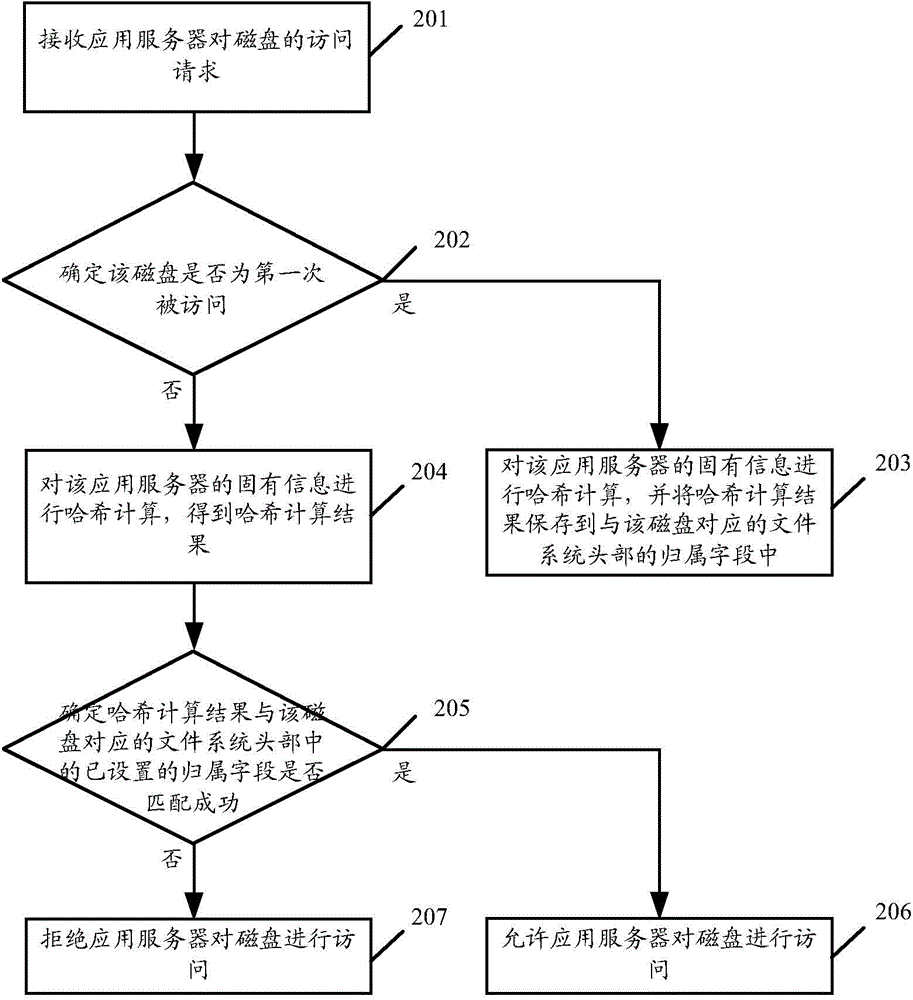
Disk access control method and device
ActiveCN106155563AAvoid data confusion and lossSimplify configuration workInput/output to record carriersApplication serverFile system
The invention discloses a disk access control method and device. The disk control method and device comprises the steps that an access request of an application server for a disk is received; when the disk is a network disk, hash calculation is carried out on the acquired inherent information of the application server; an affiliation field set in the head part of a file system corresponding to the disk is matched with a hash calculation result; if matching is successful, the application server is allowed to have access to the disk; if matching fails, the application server is refused to have access to the disk. By means of the scheme, the access of the application server to the disk is automatically and effectively controlled.
Owner:ZHEJIANG DAHUA TECH
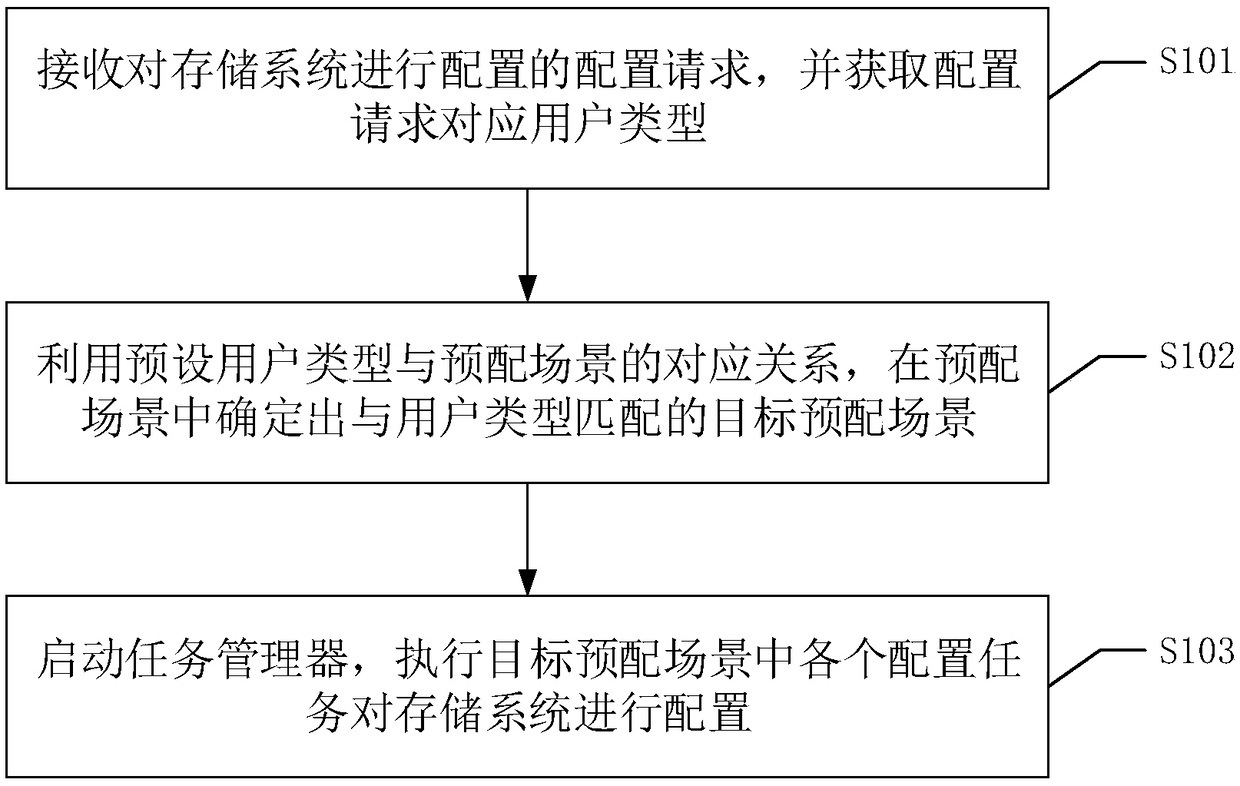
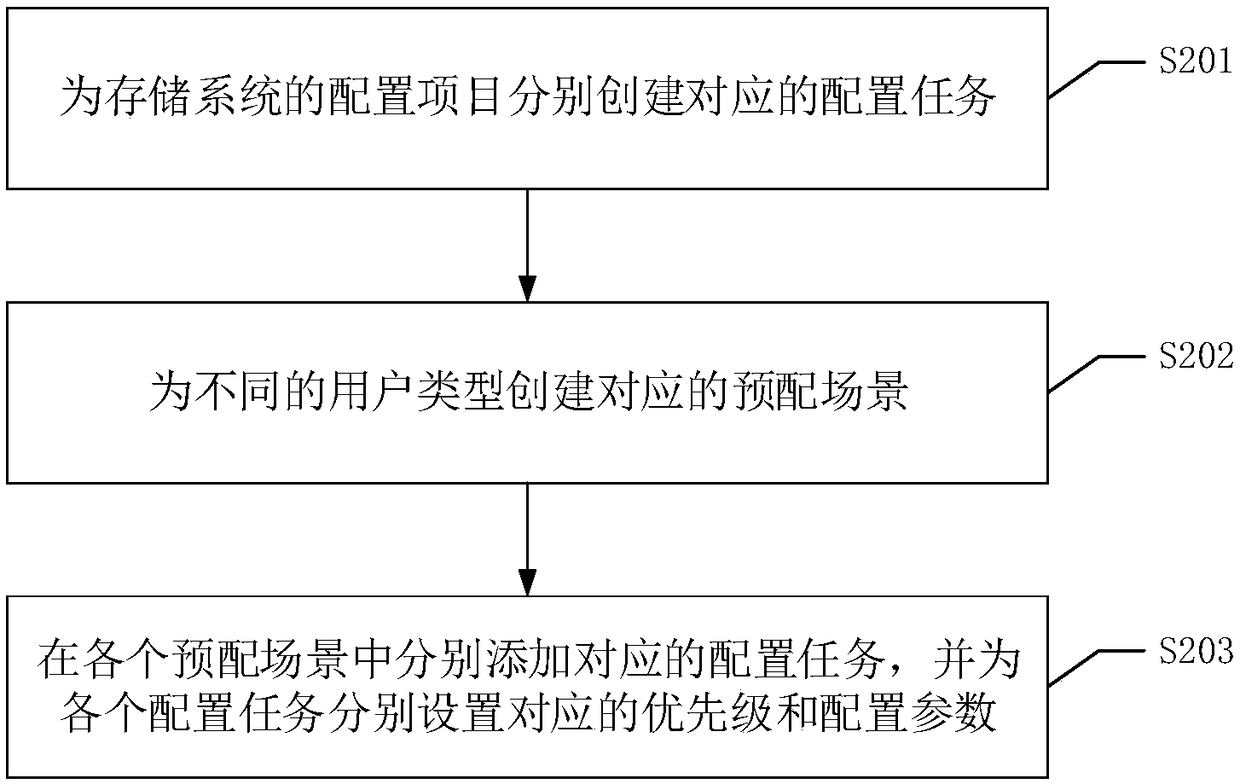
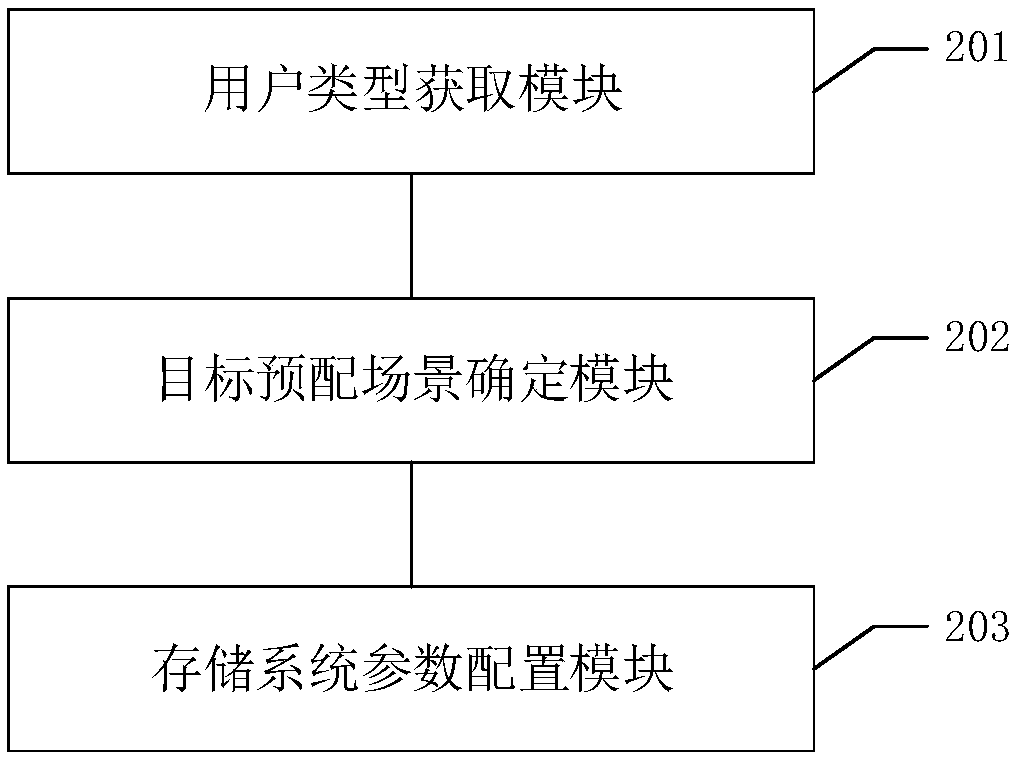
Storage system configuration method, device and equipment, and readable storage medium
ActiveCN108845825ASimplify configuration workImprove configuration efficiencyResource allocationVersion controlConfiguration itemSystem configuration
The invention discloses a storage system configuration method, which comprises the following steps that: receiving a configuration request for configuring a storage system, and obtaining a user type corresponding to the configuration request; utilizing a corresponding relationship between a preset user type and a pre-configured scene to determine a target pre-configured scene matched with the usertype in the pre-configured scene; and starting a task manager, and executing each configuration task in the target pre-configured scene to configure the storage system. Users or professional after-sales staffs (technicists) do not need to configure each configuration item one by one, so that the configuration work of the storage system can be simplified, and configuration efficiency is improved.In addition, in field configuration engineering, manual intervention (manual operation) is reduced, and configuration accuracy can be improved. The invention also discloses a storage system configuration device and equipment and a readable storage medium, and has corresponding technical effects.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
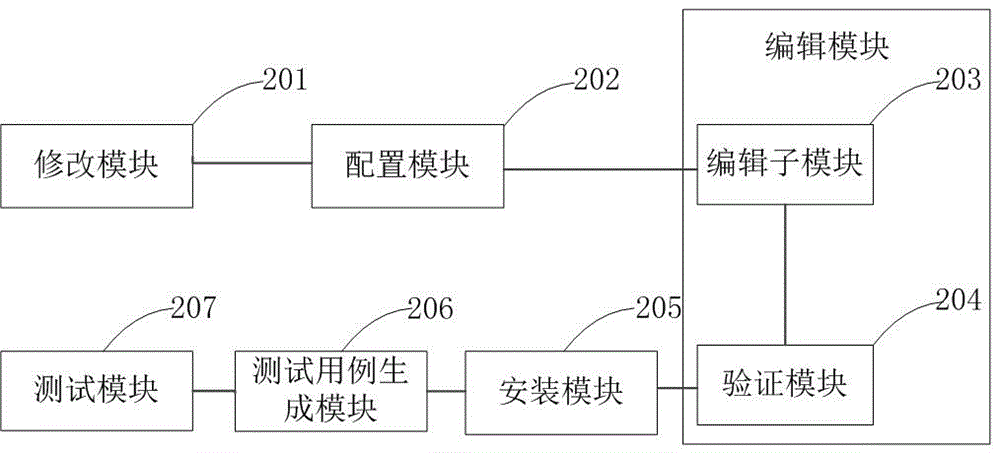
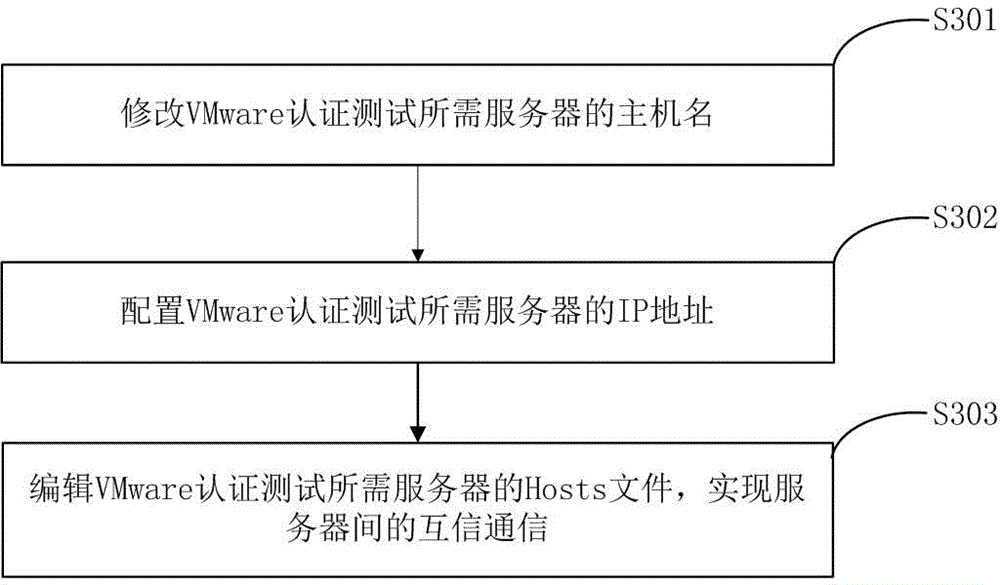
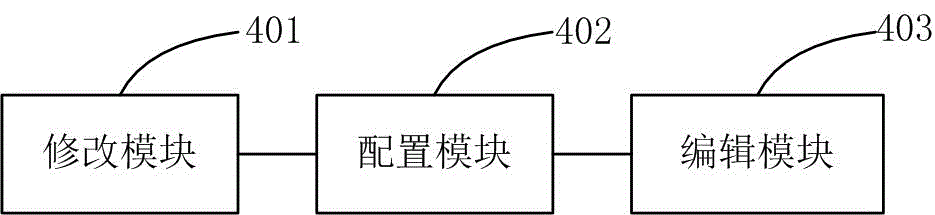
Method and device of mutual trust communication among severs
InactiveCN106686158ASimplify configuration workShorten the timeData switching networksIp addressConfiguration system
The invention relates to the computer filed. The invention discloses a method of mutual trust communication among severs which comprises the following steps: modifying the host name of the server required for the VMware authentication test; configuring the VMware authentication test to test the IP address of the server; editing the Hosts file for the server that the VMware authentication requires to realize the mutual trust communication of the sever. The invention also discloses a device of mutual trust communication among severs which comprises: editing the module which is used to modify the host name required by authentication test; configuring the module which is used to configure the IP address of the sever required by authentication test; editing the module which is used to edit Hosts file of the sever required by authentication test, the trust and communication among the severs are realized. The scheme realizes the trust and communication so that the severs and authenticates and tests the VMware through configured system file Hosts.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
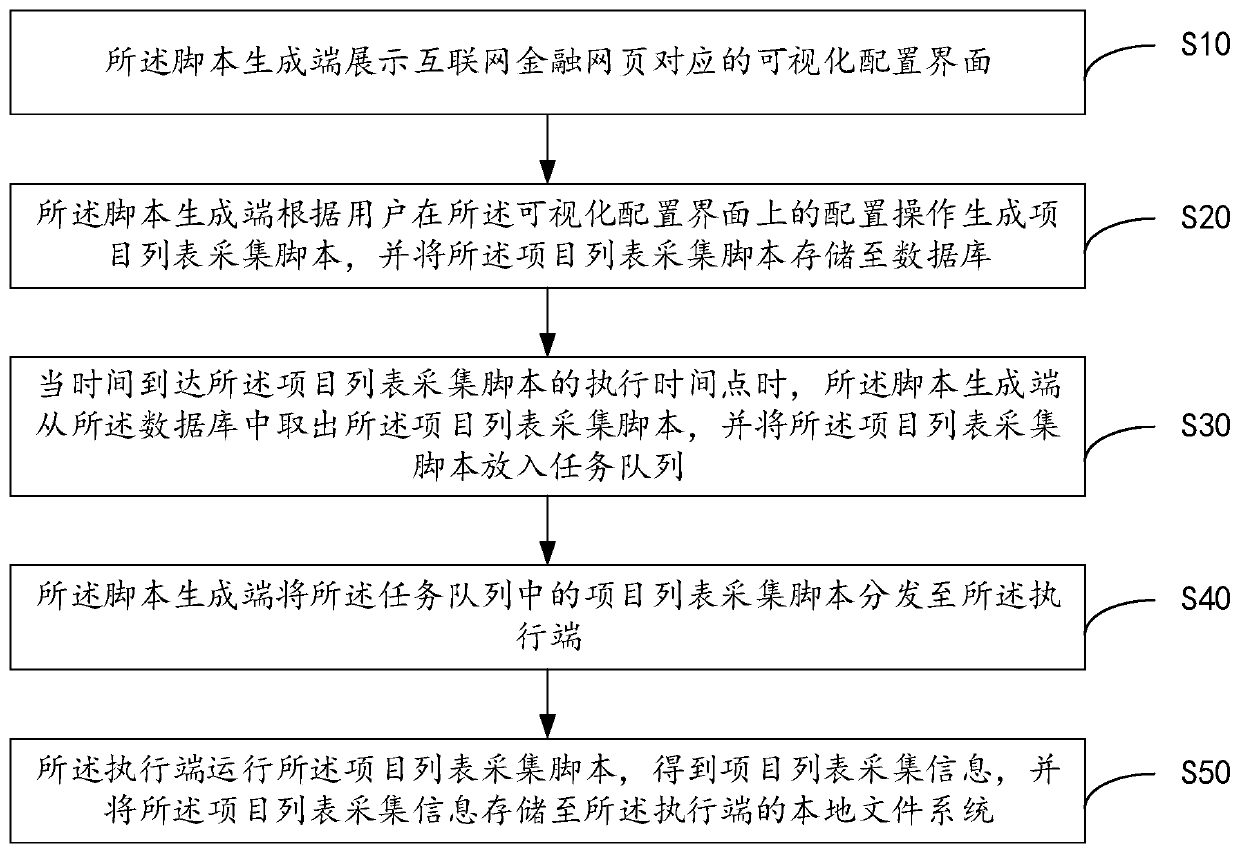
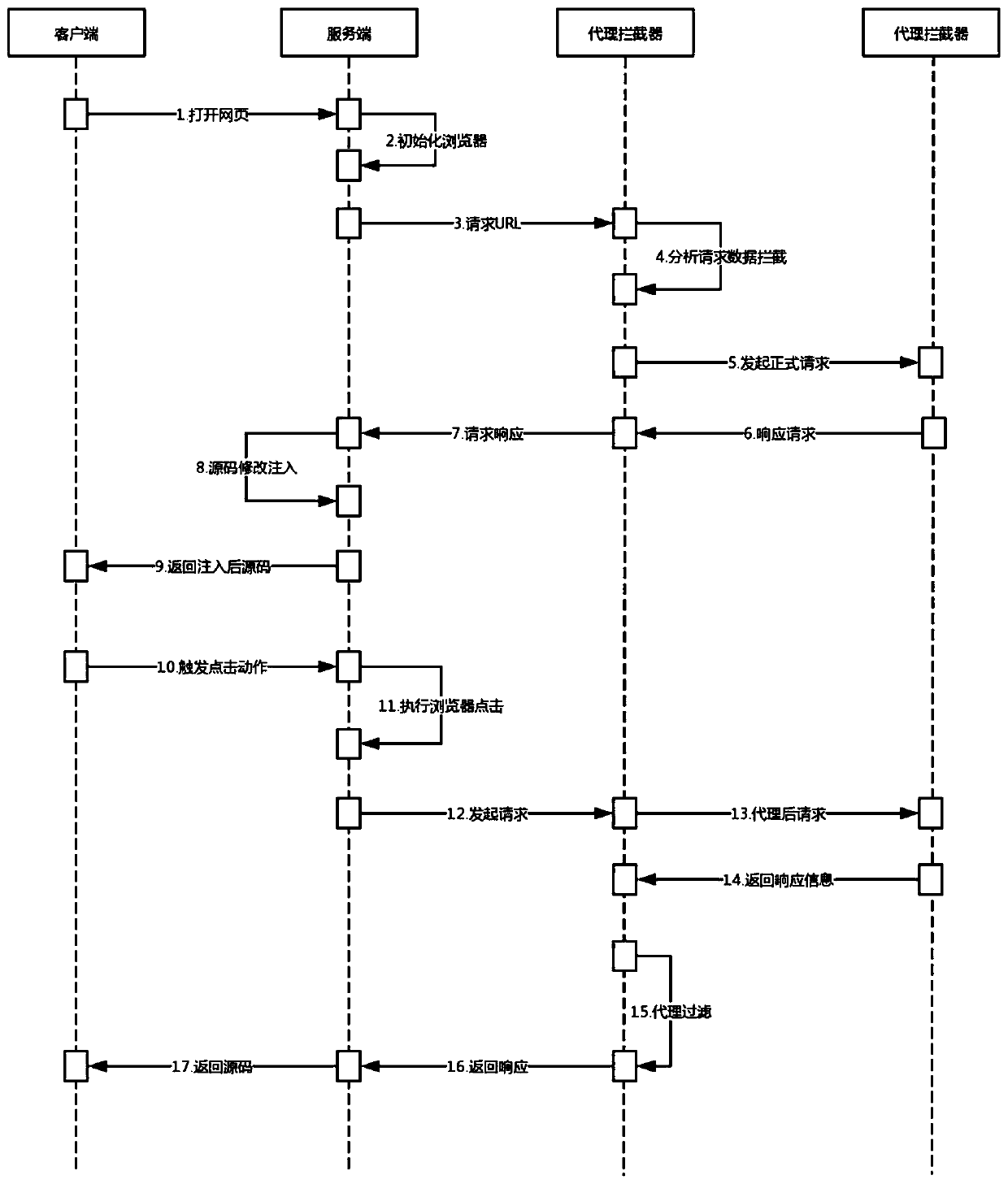
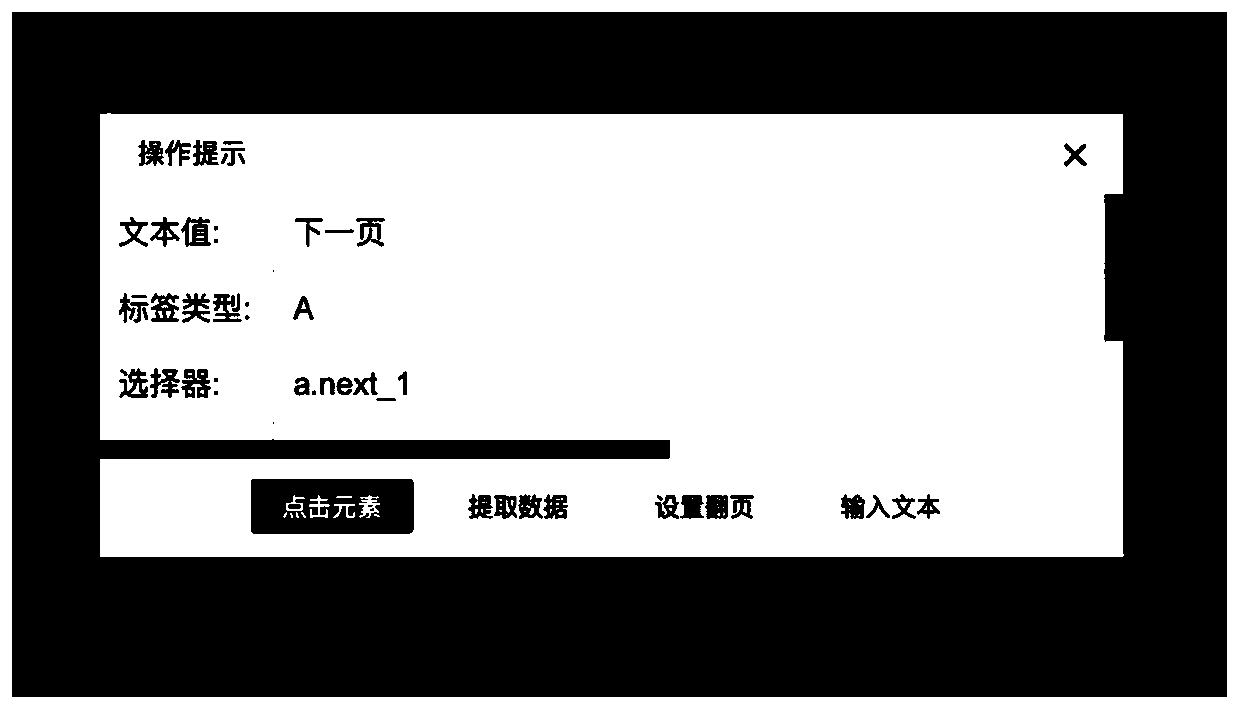
Method and system for collecting project list of internet financial webpage
PendingCN111045659ASimplify configuration workImprove collection efficiencyCreation/generation of source codeFile systemSoftware engineering
The invention discloses a method and system for collecting a project list of an internet financial webpage. The method comprises that a script generation end displays a visual configuration interfacecorresponding to the internet financial webpage; the script generation end generates a project list collection script according to the configuration operation of the user on the visual configuration interface, and stores the project list collection script in a database; when the time reaches the execution time point of the project list acquisition script, the script generation end takes out the project list acquisition script from the database and puts the project list acquisition script into a task queue; the script generation end distributes the project list acquisition scripts in the task queue to the execution end; and the execution end runs the project list acquisition script to obtain project list acquisition information, and stores the project list acquisition information in a localfile system of the execution end. According to the method and the device, the script configuration work is greatly simplified through a visual configuration mode, so that the data acquisition efficiency is improved.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
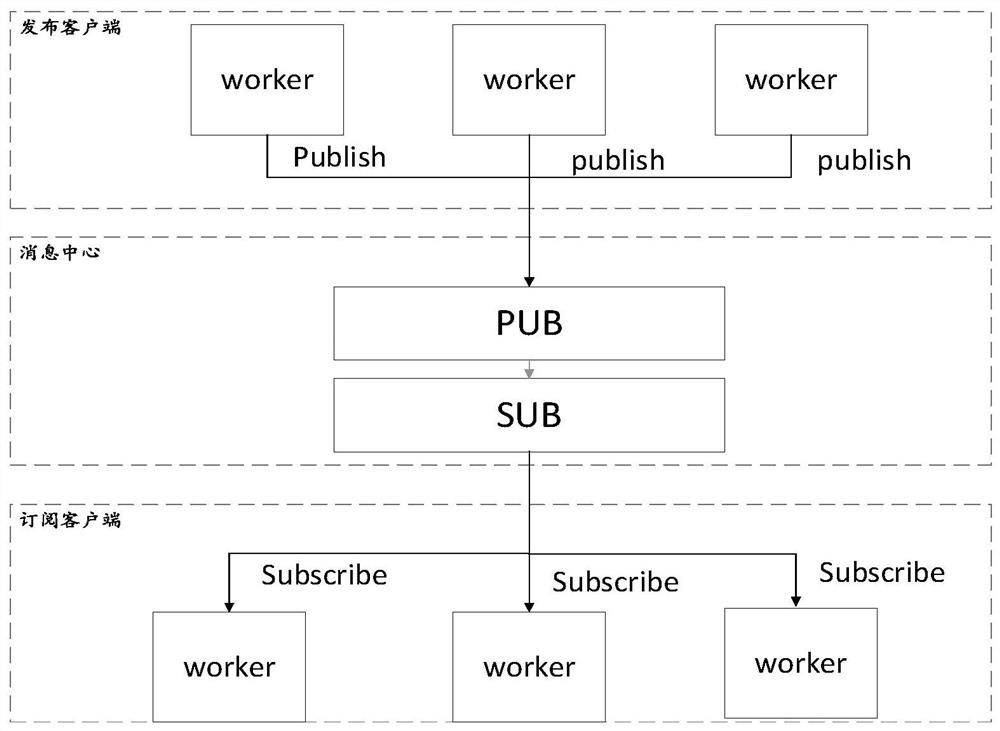
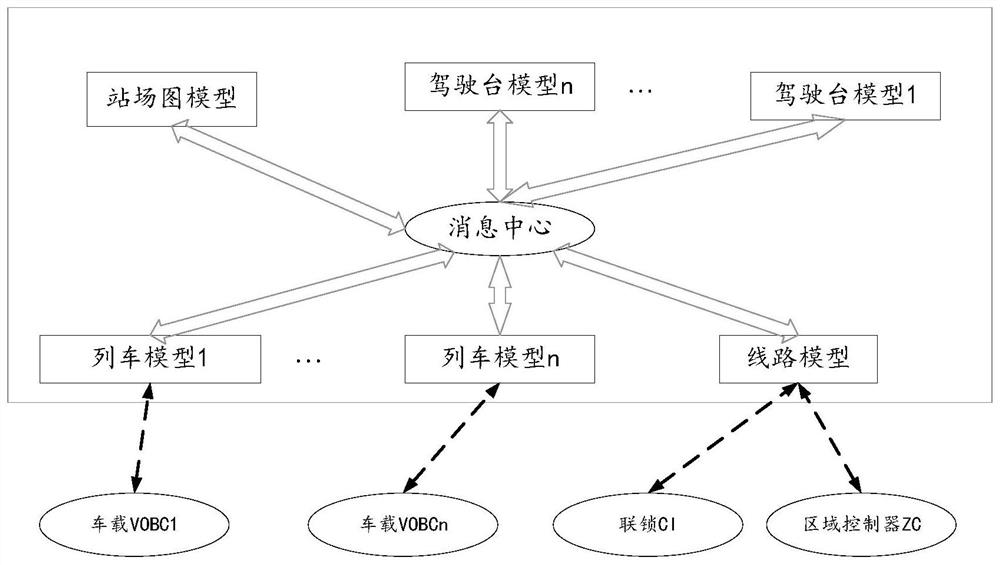
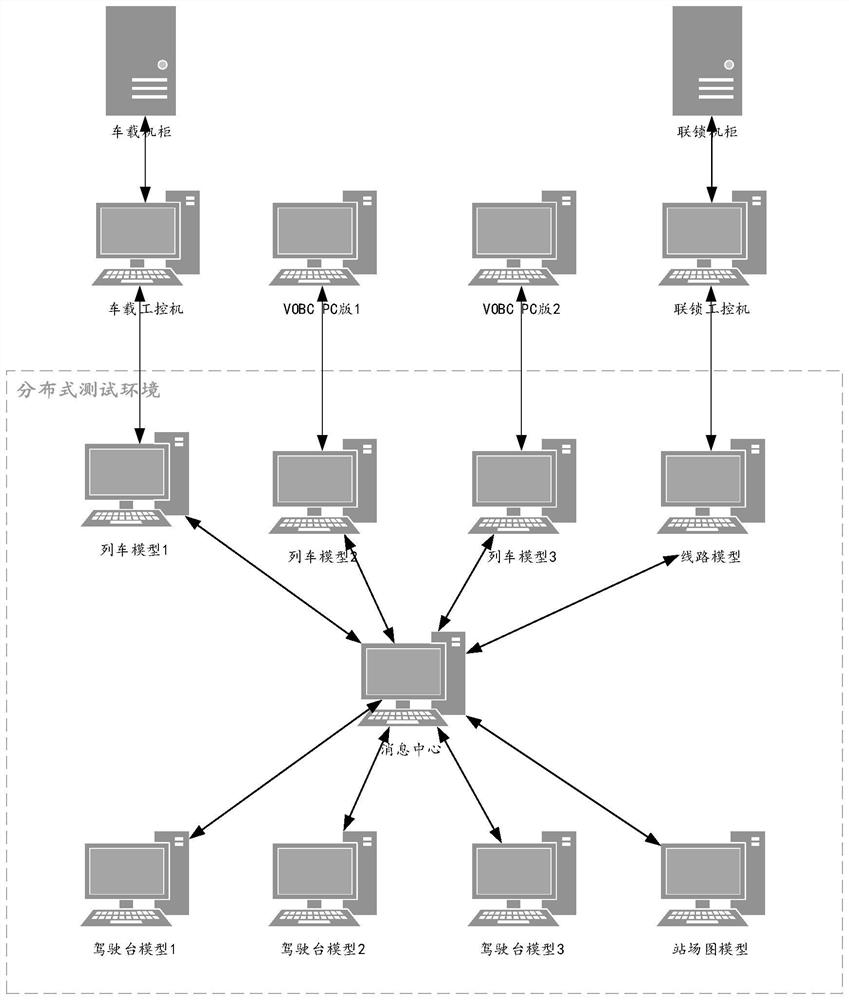
Distributed automatic test system based on OPC UA architecture Pub-Sub mode
InactiveCN112799379ALow costSimplify configuration workProgramme controlElectric testing/monitoringMessage queueStation
The invention relates to a distributed automatic test system based on an OPC UA architecture Pub-Sub mode. The system architecture comprises a message center, a line model, a train model, a bridge model and a station yard graph model, wherein the line model, the train model, the bridge model and the station yard graph model form a dynamic star topology structure through the message center, the message center is set to be a message framework configured based on an OPC UA architecture Pub-Sub mode, supports a dynamic topology mode from n to m, and carries out IP address and port binding at a PUB end and a SUB end, and the line model, the train model, the bridge model and the station yard graph model communicate with one another by configuring the IP address of the message center. According to the test system, distributed communication and a star topology structure are realized by adopting a message queue based on an OPC UA publishing / subscribing mechanism, and compared with traditional mesh communication, the test system is simple in configuration and higher in efficiency, and a test environment is more convenient to expand.
Owner:CRRC QINGDAO SIFANG ROLLING STOCK RES INST
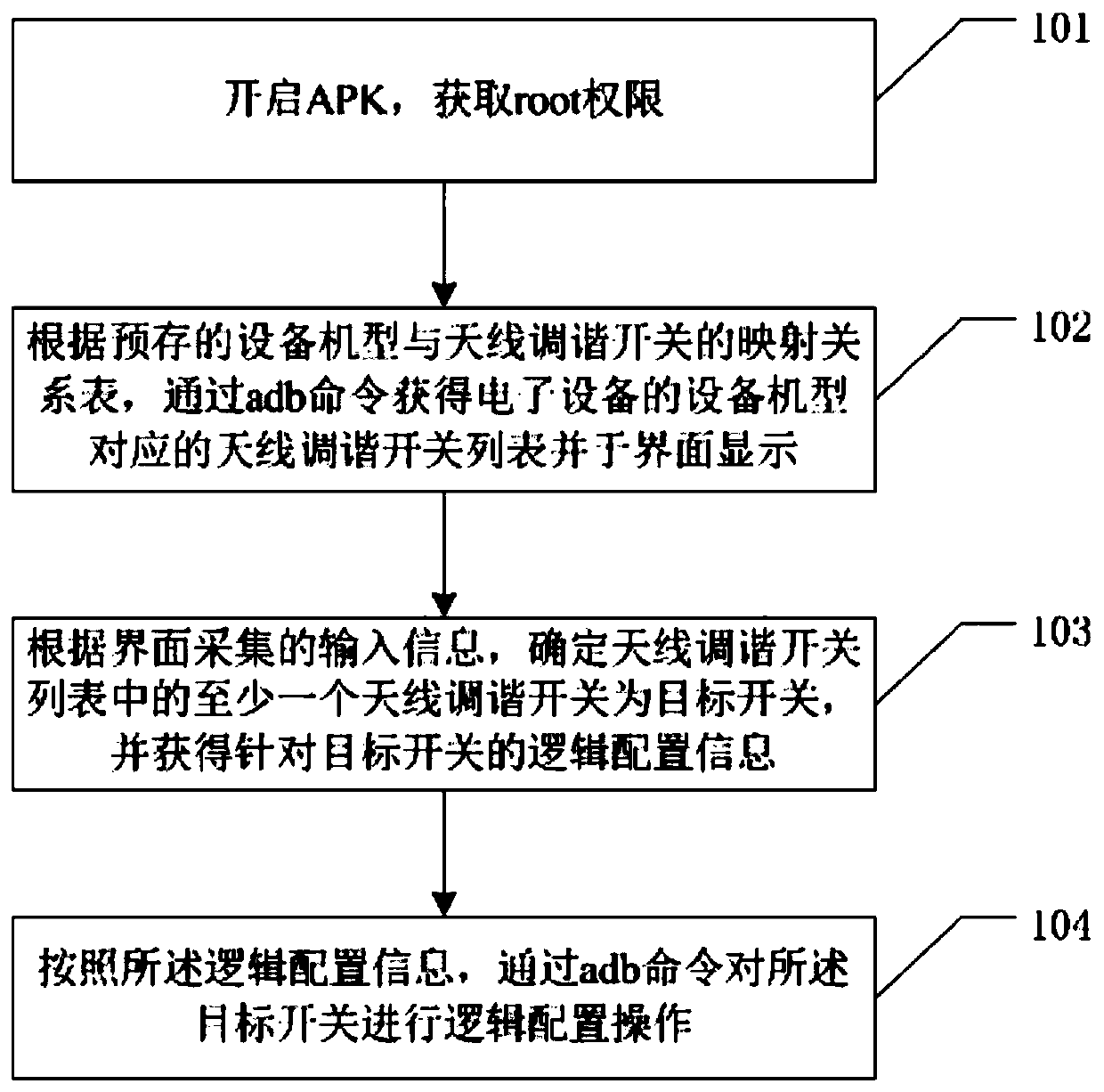
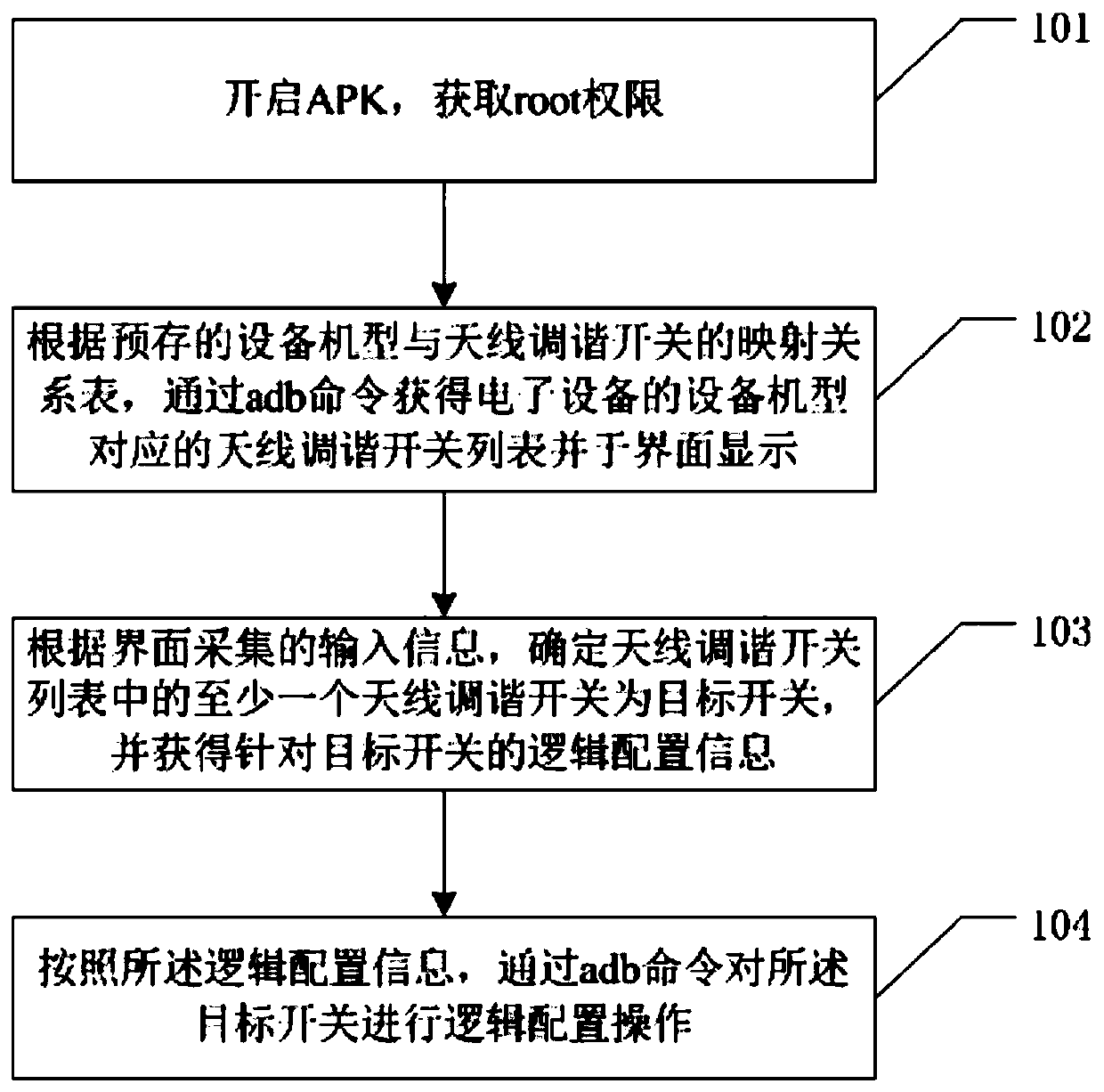
Antenna tuning switch logic control method, system and terminal
ActiveCN111147091ASimplify configuration workImprove work efficiencyTransmissionComputer hardwareEmbedded system
The invention relates to the technical field of communication, and discloses an antenna tuning switch logic control method, system and terminal. The method comprises the steps of obtaining an antennatuning switch list corresponding to an equipment type of a terminal through an adb command according to a mapping relation table of the equipment type and an antenna tuning switch, and displaying theantenna tuning switch list on an interface; determining at least one antenna tuning switch in the list as a target switch according to the input information collected by the interface, and obtaining logic configuration information for the target switch; and performing logic configuration operation on the target switch through the adb command according to the logic configuration information. The method is different from a conventional permanent writing mode; according to the invention, a temporary write-in mode is adopted; the method is realized based on the Android APK, and a worker can directly and flexibly control the state of the antenna tuning switch on an equipment interface without professional software programming personnel and a computer, so that the configuration work of the antenna tuning switch logic is simplified, and the working efficiency is improved.
Owner:上海摩勤智能技术有限公司
Method for realizing chain circuit polymer function based on strategy route
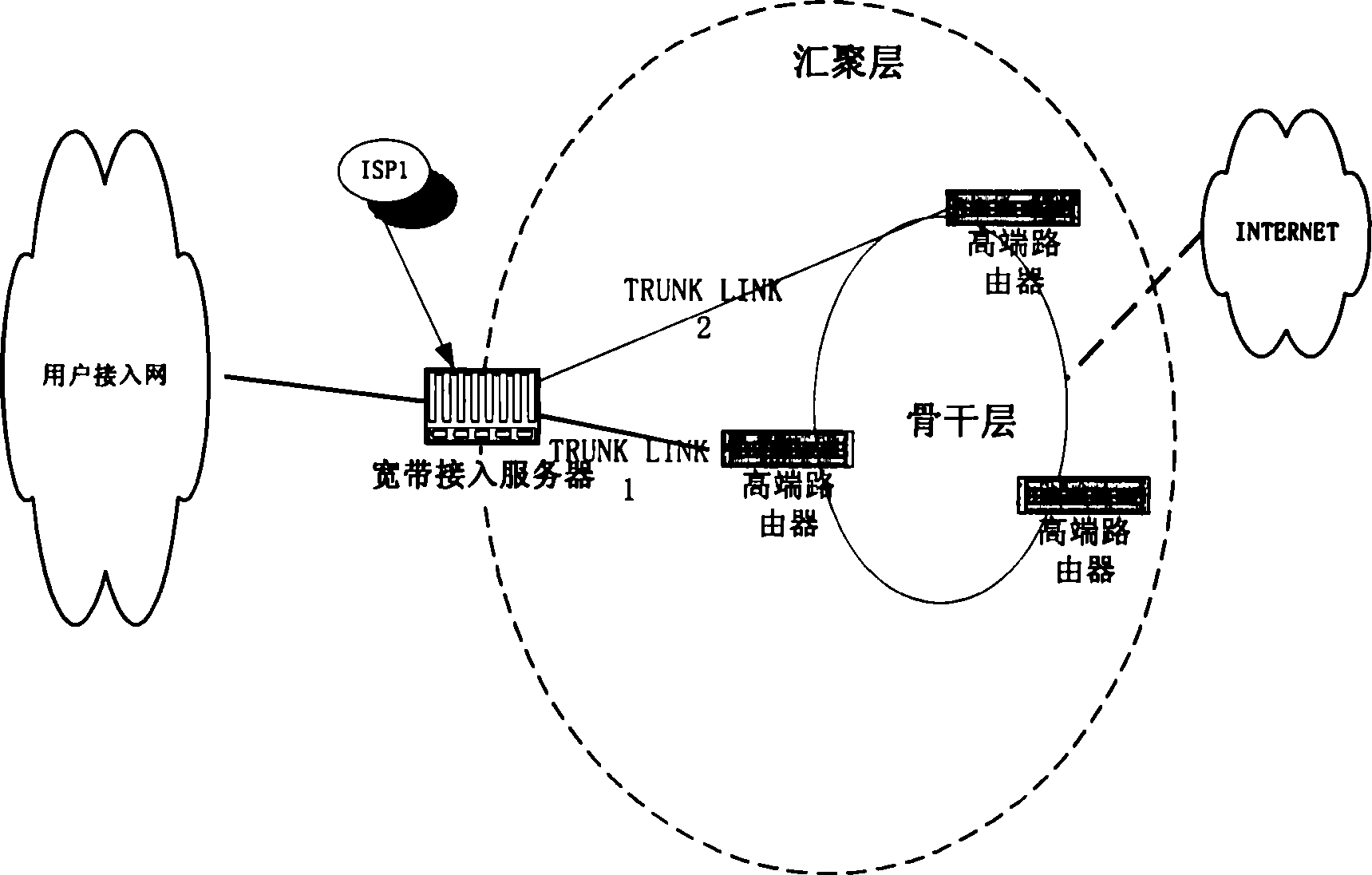
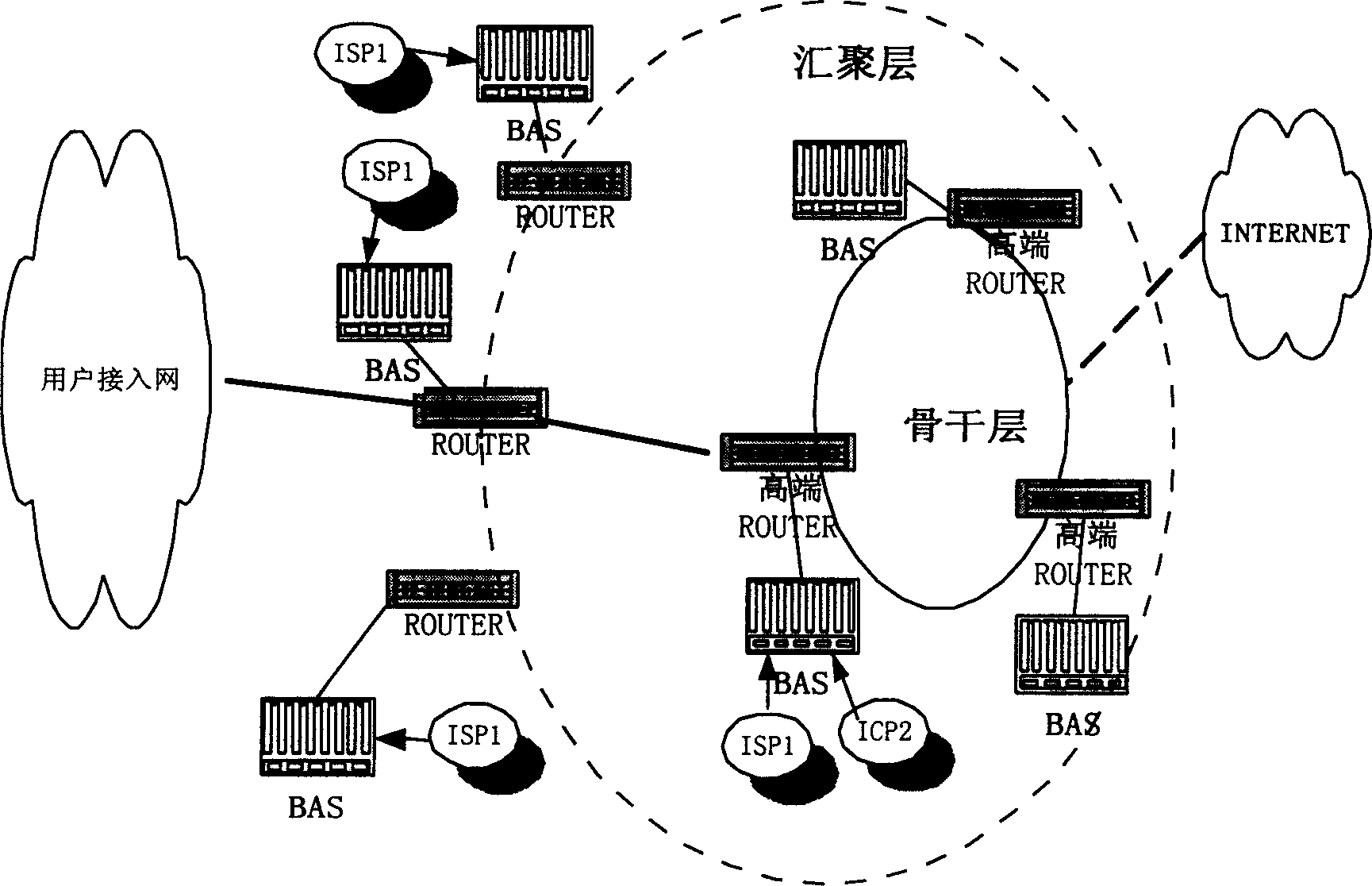
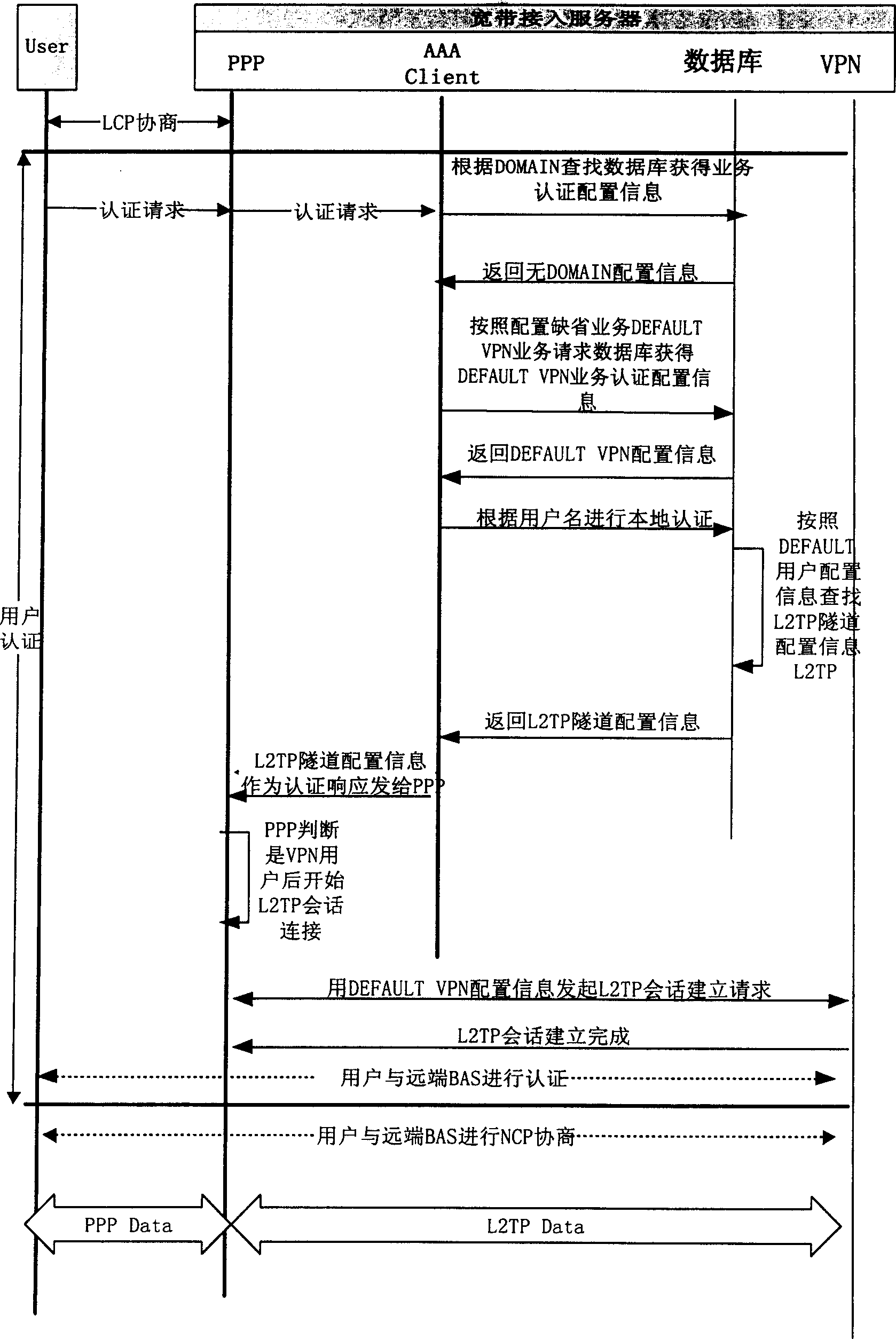
InactiveCN1298138CImprove primary and backup functionsSimplify configuration workTransmitter/receiver shaping networksNetwork connectionsStreaming dataLink aggregation
This invention discloses a method for implementing link aggregation based on policy-based routing. It includes following steps: the user sends the PPP calling to the wideband access server, the above sever completes the service access, transmits process and service reversing of PPF / IP, when the state of gate exit link turns on, sends the user data to the router, the down stream data is sent to the wideband access server through the router. When the gateway exit link turns off , the user data is sent to backup router, the down stream user data is sent the wide band server through the backup router. The invention can implement the configuration management for the exit of main rout reliably and high efficiently.
Owner:ZTE CORP
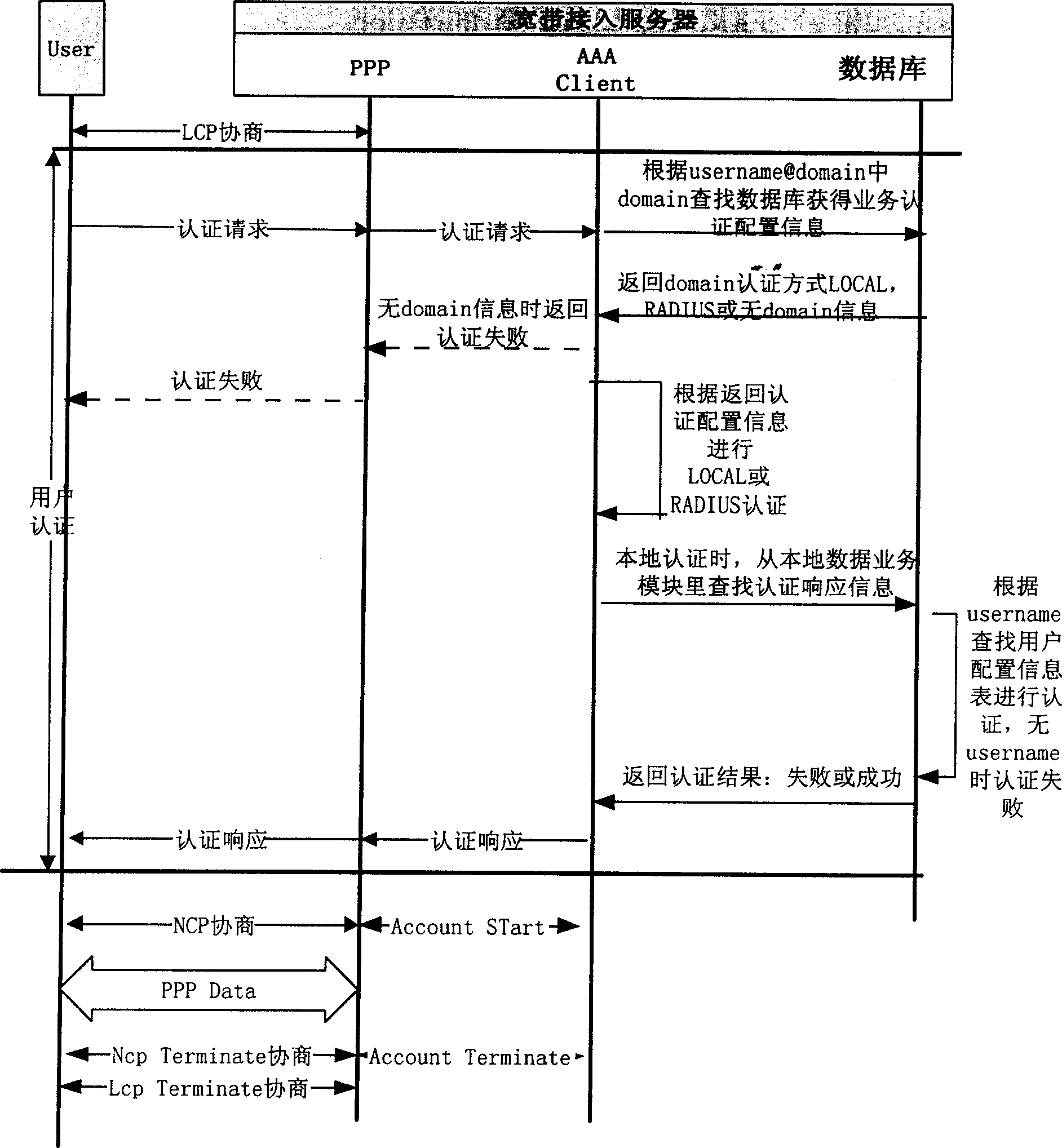
Allocation method of wide band access user
InactiveCN1241366CSimplify configuration workSimplify administrationUser identity/authority verificationSpecial service for subscribersService product managementService configuration
This invention discloses a configuration management method to wideband cut-in customers, and uses the L2TP and VPDN technology based on the tunnel mode. Cut-in request service of small service customers is transferred to the core wideband cut-in server via L2TP tunnel to finish the required cut-in service management. The service of ISP and ICP of unstable service is managed on central confugration only by a few number of core cut-in servers, and therefore the daily service performing managements of network operators are greatly reduced and the flexibility of service configuration management is increased so as to realize distributed network plan and centralized service management.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com