Patents
Literature
175results about How to "Simplify the deployment process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
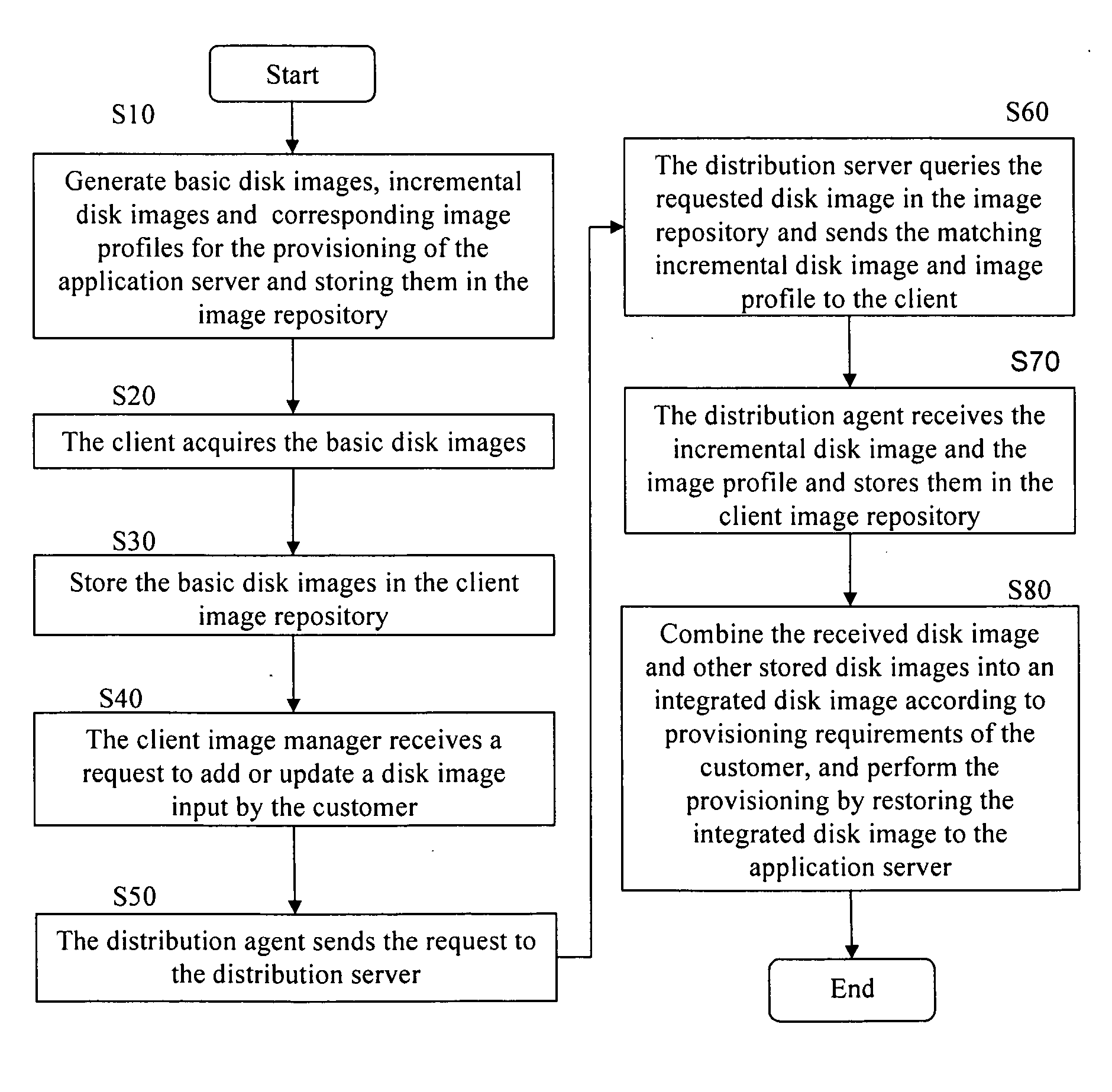
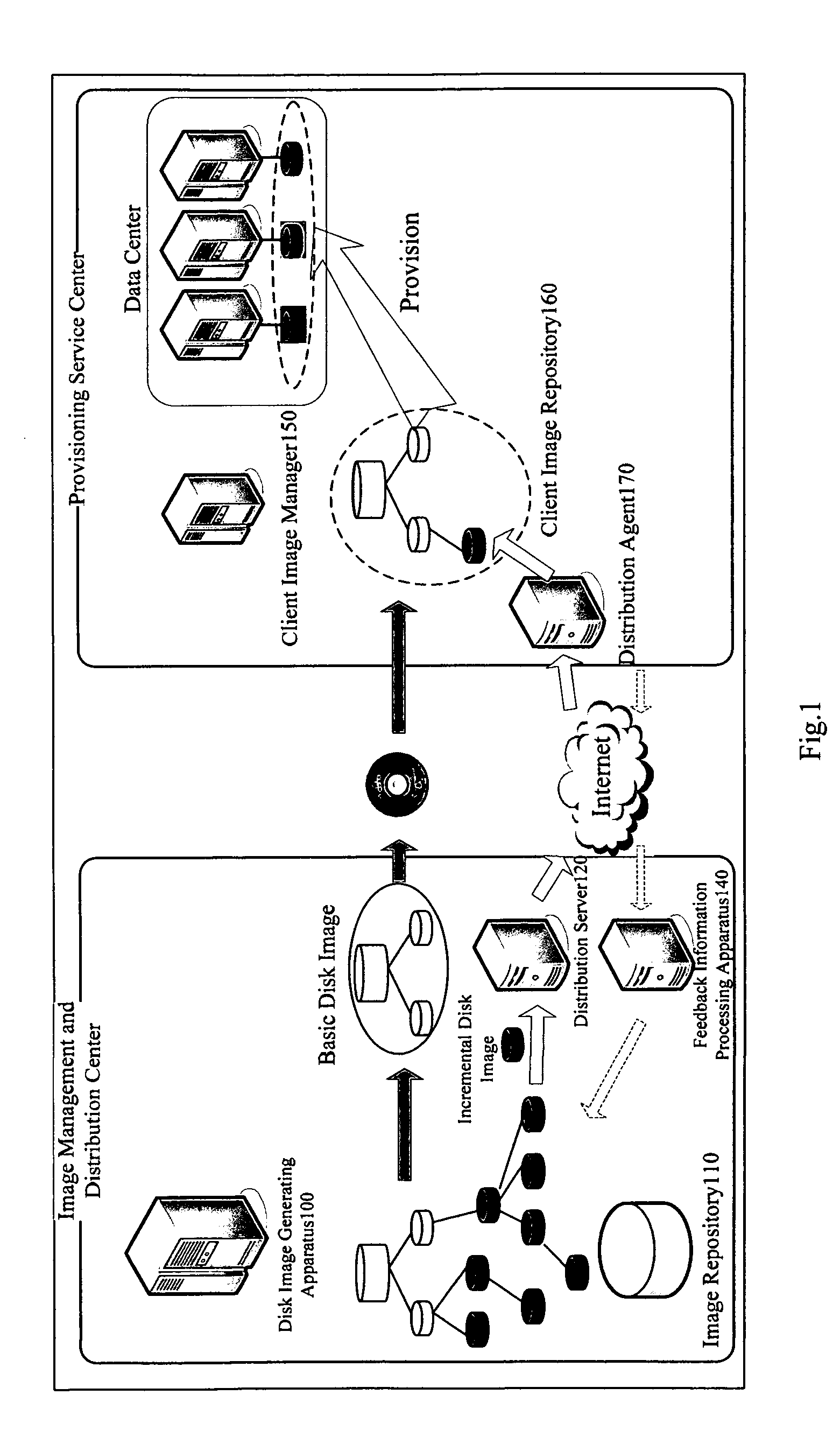
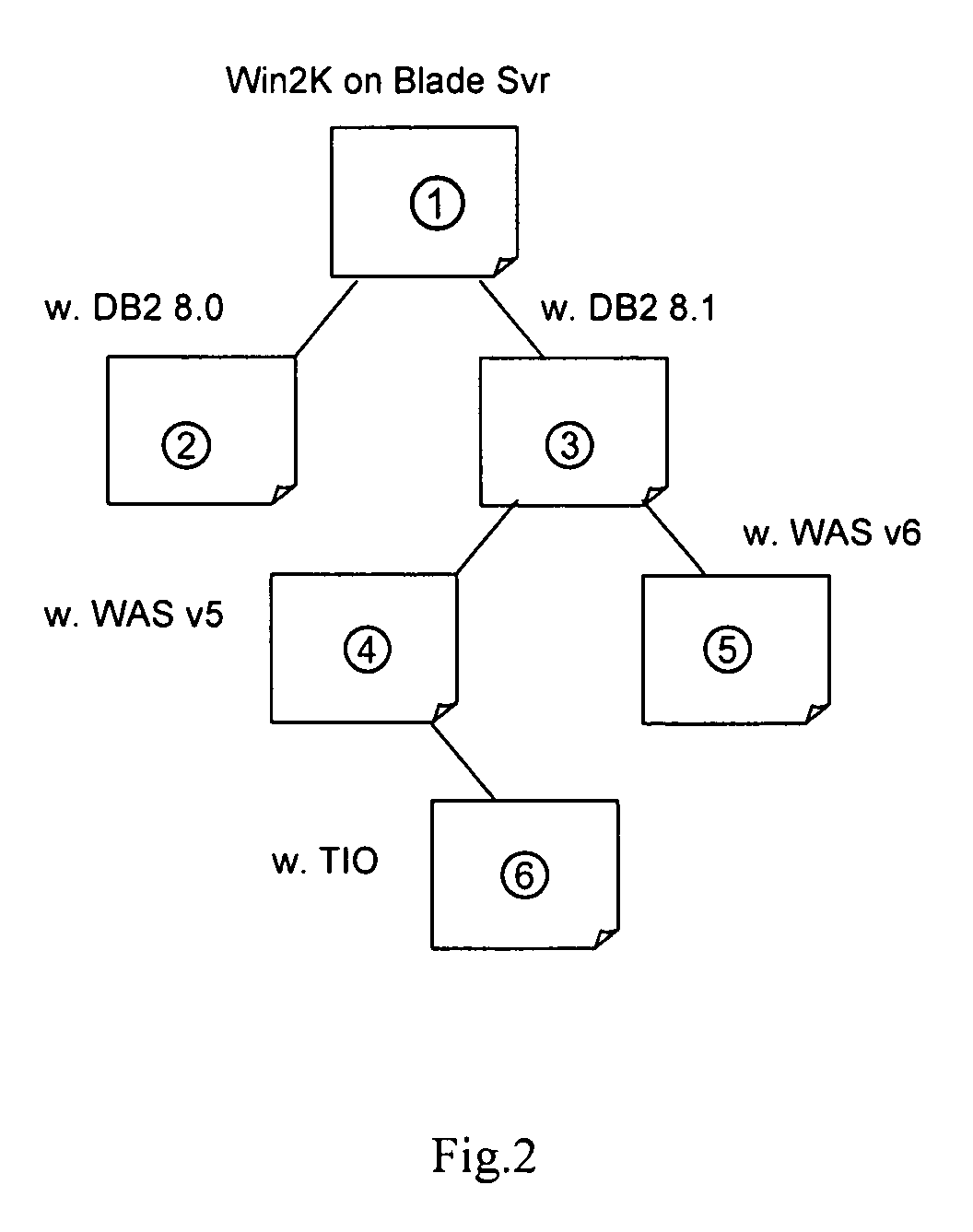
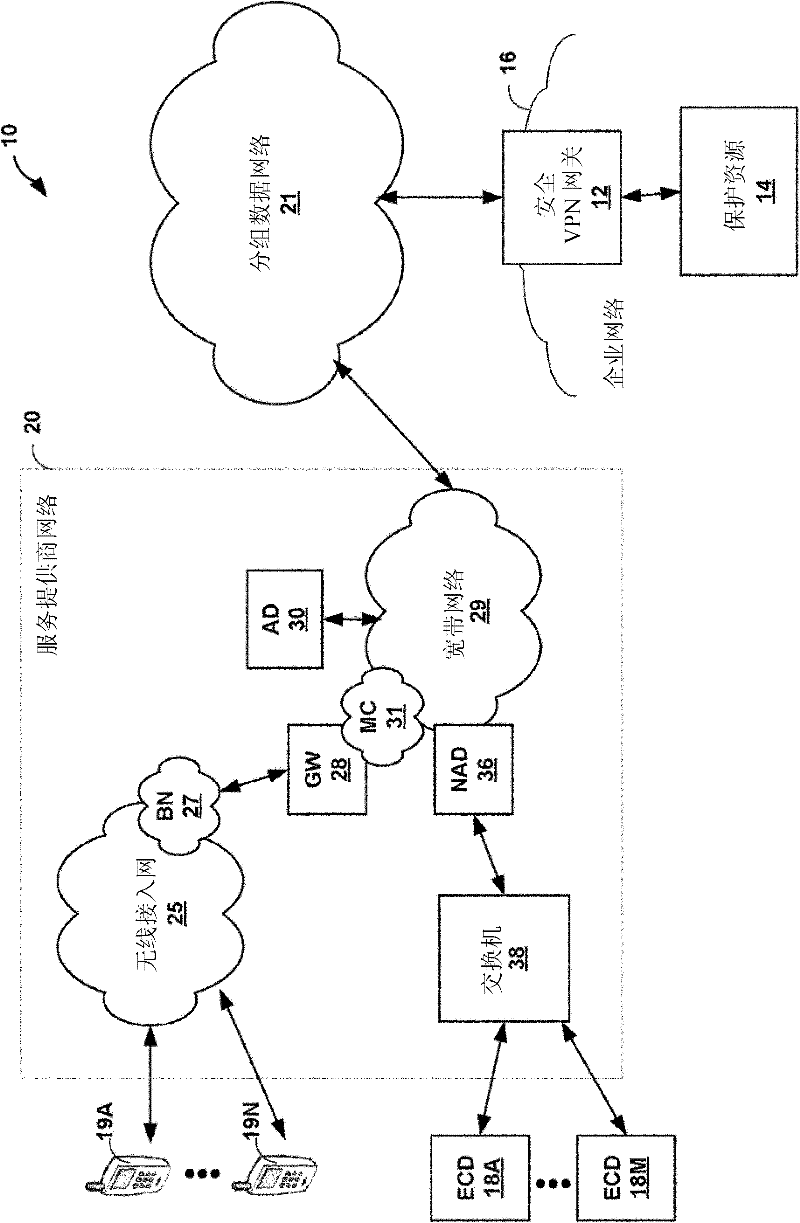
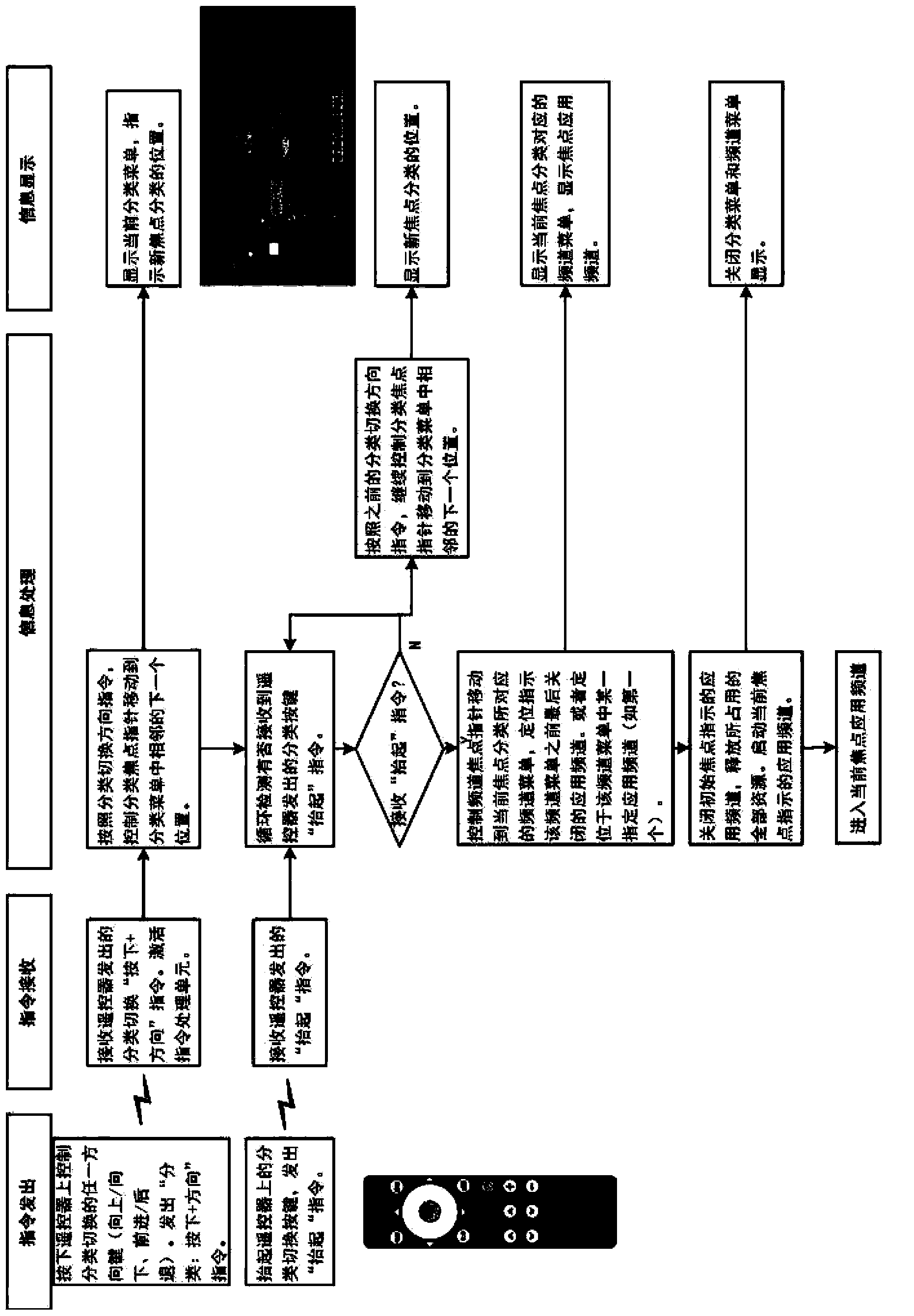
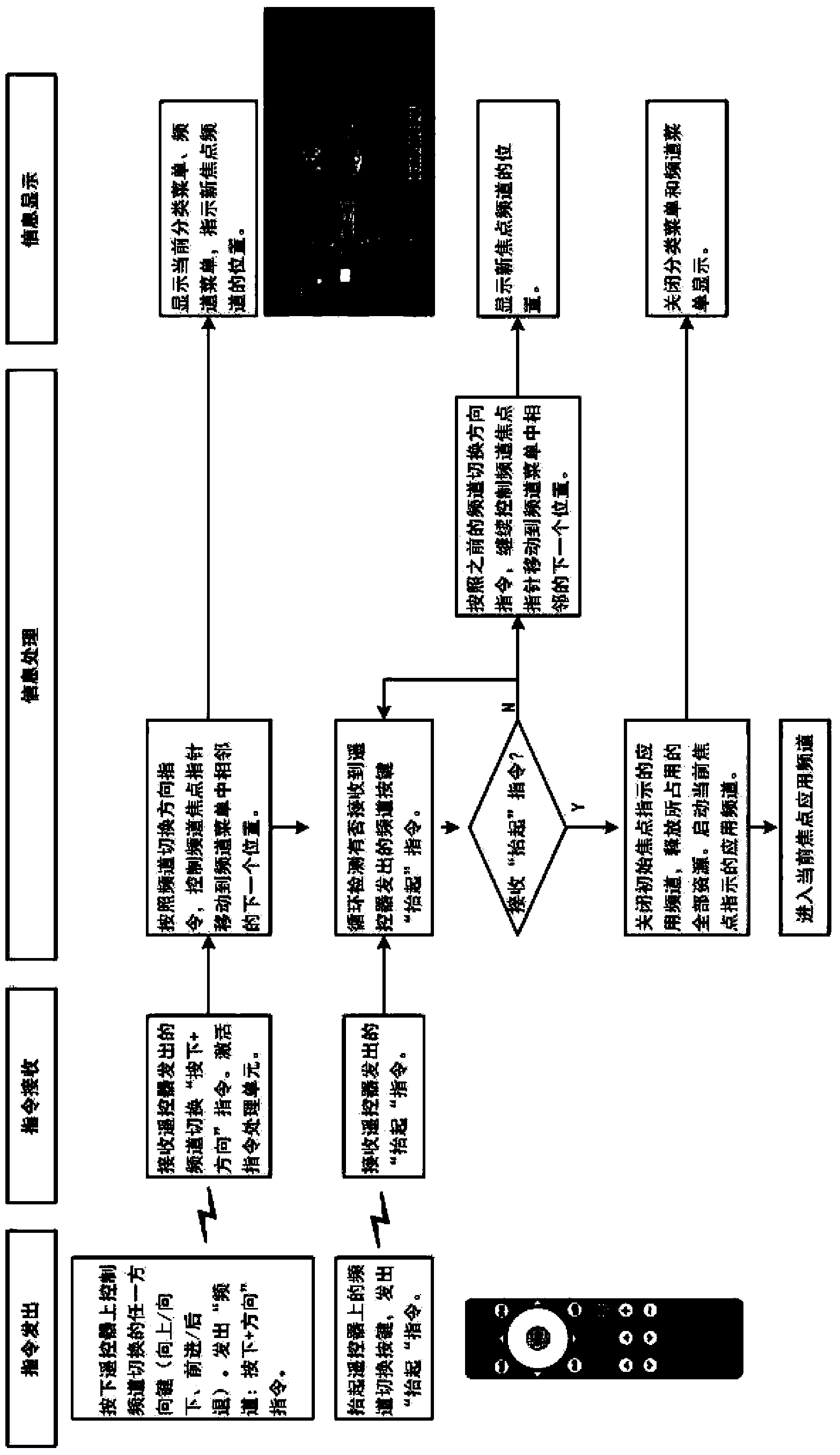
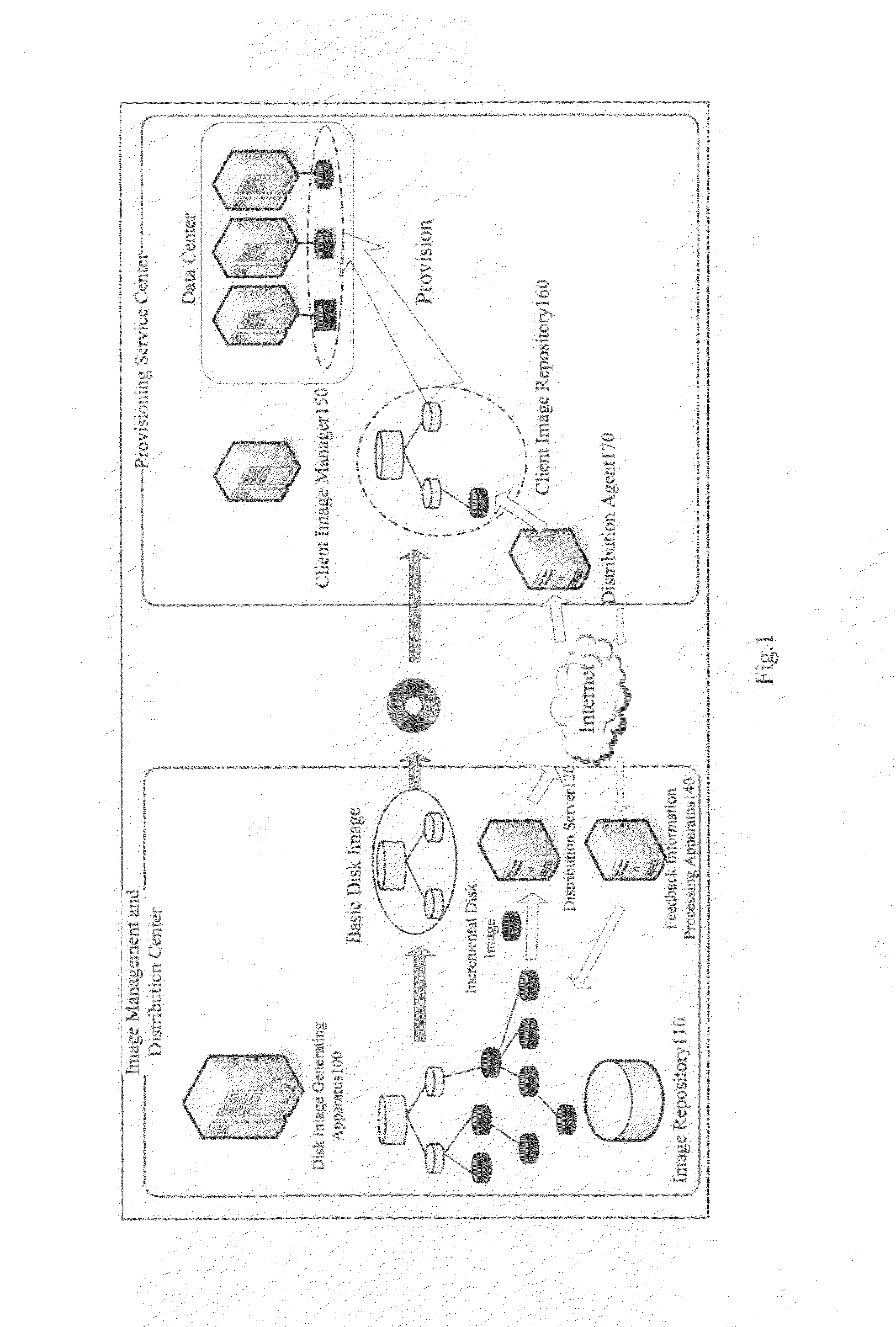
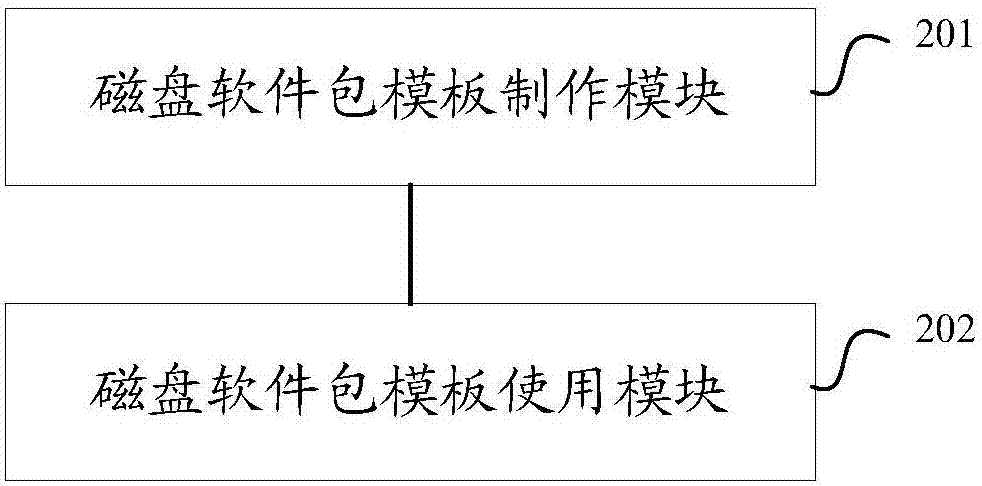
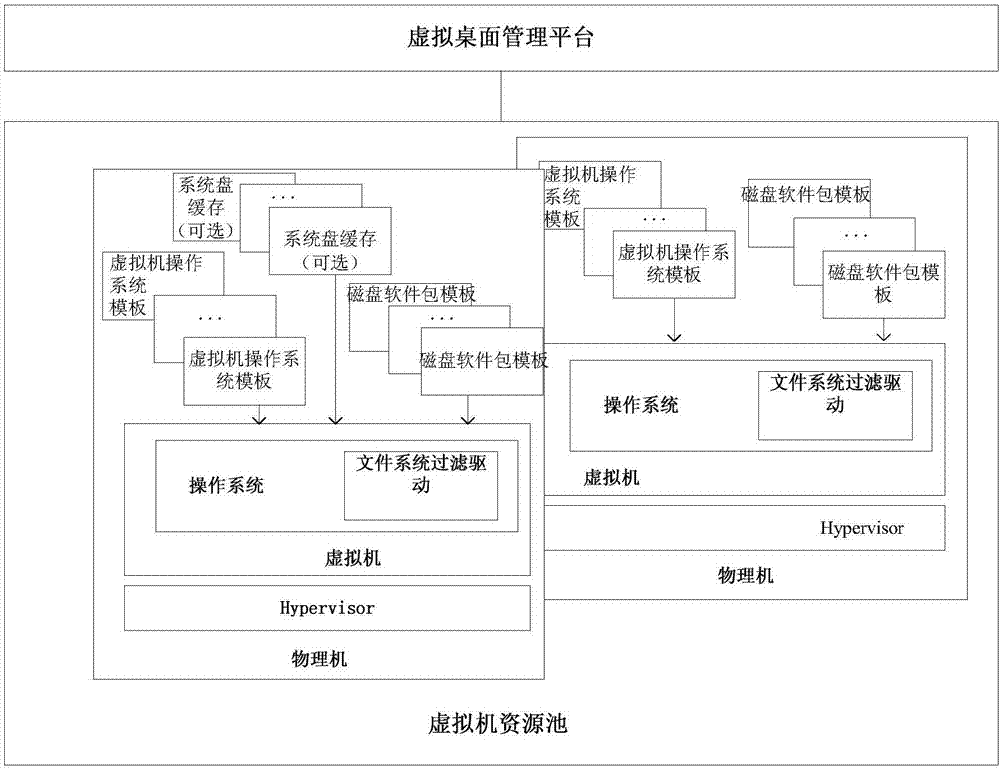
Application server provisioning system and method based on disk image profile
InactiveUS20080235266A1Fast and easy provisioning processReduce consumptionDigital data processing detailsSpecial data processing applicationsApplication serverDistribution system
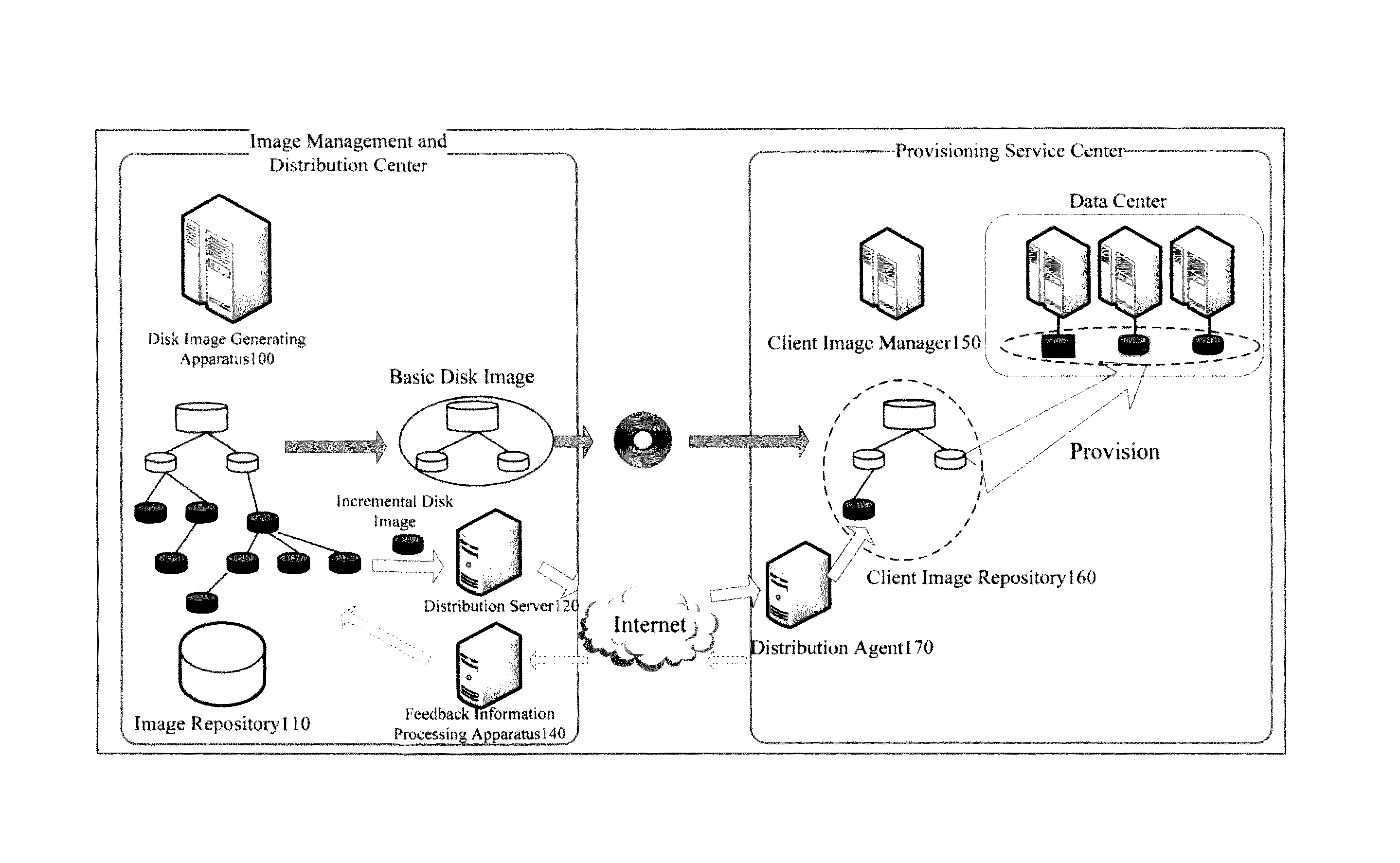
An application server disk image generating apparatus and method comprising a basic disk image generating component for generating basic disk images for basic programs used by the server; an incremental disk image generating component for generating incremental disk images including heritage relationship for other respective applications based on the basic programs used by the server; and an image profile generating means for generating an image profile for each of the basic disk images and the incremental disk images. By using the apparatus, the storage consumption can be decreased greatly and the storage efficiency can be improved. The invention also discloses an application server disk image management and distribution system to which the application server disk image generating apparatus is applied, and a system for provisioning the application server using disk images.
Owner:DOORDASH INC
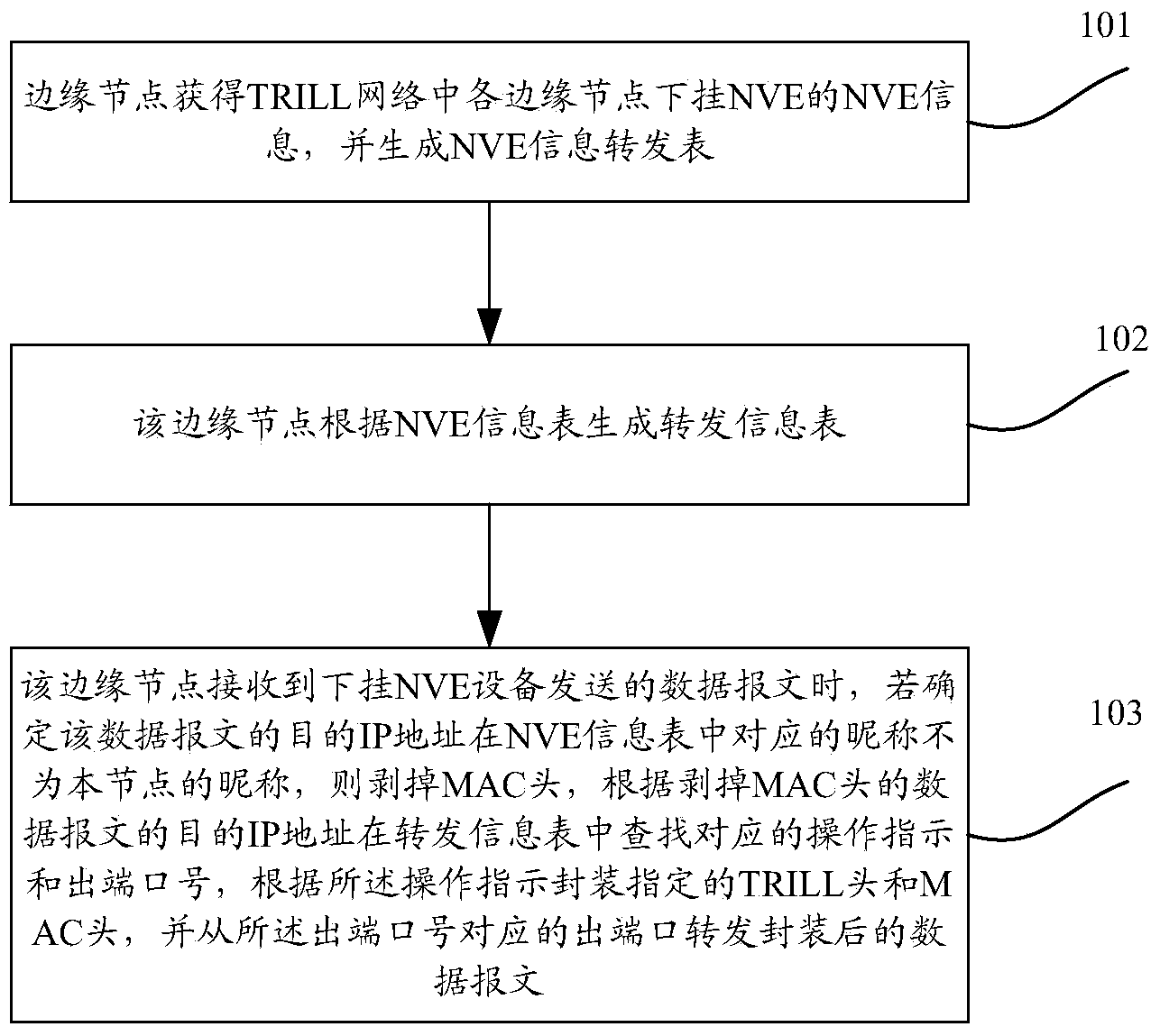
Method and device for forwarding messages in multilink transparent Internet
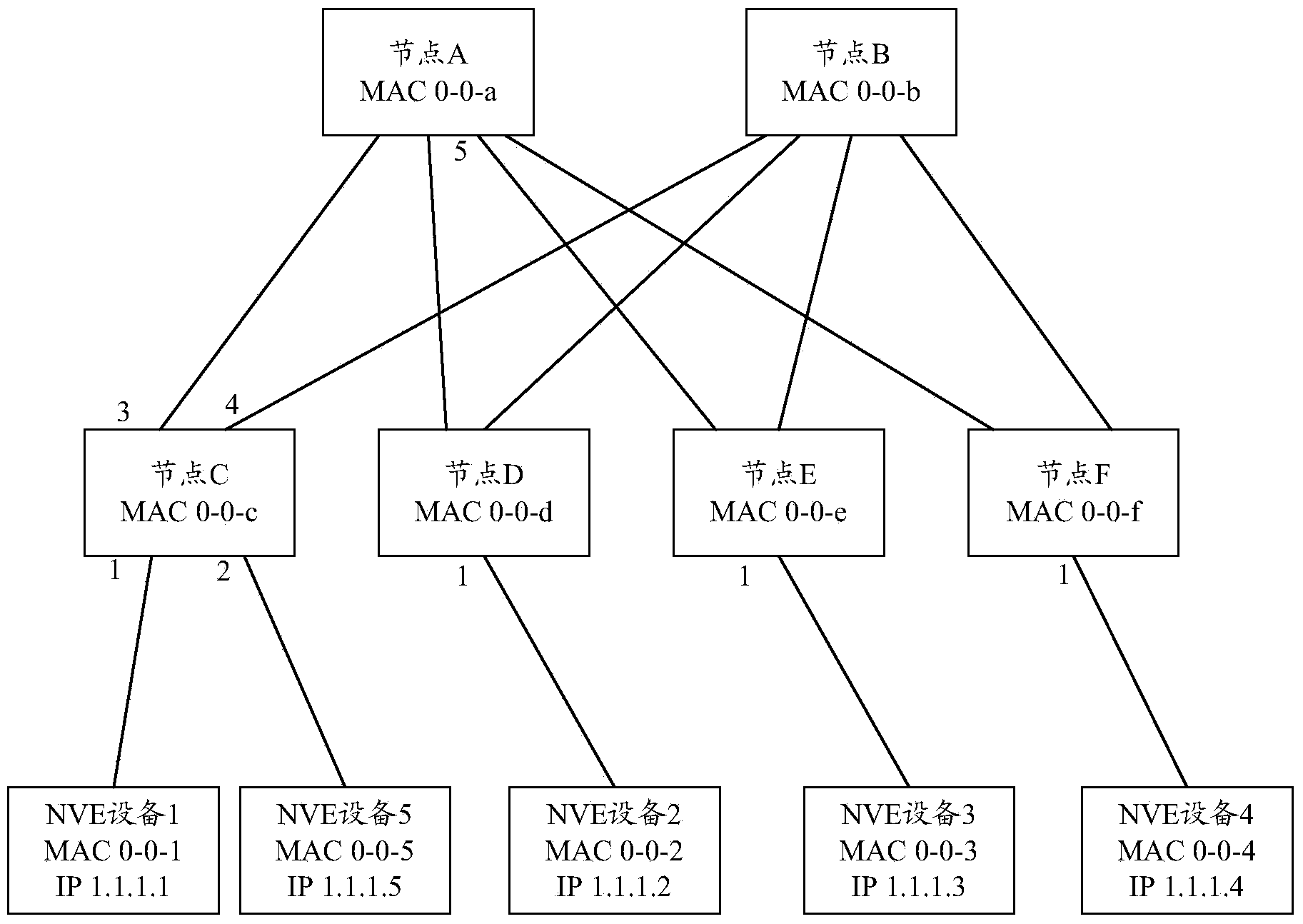
The invention provides a method for forwarding messages in the multilink transparent Internet. The method includes the steps that fringe nodes obtain NVE information of low-hung NVE devices of the fringe nodes in a TRILL network and generates a forward information list according to the obtained NVE information; the fringe nodes forward the data messages according to the forward information list when receiving the data messages sent by the low-hung NVE devices. On the basis of the same invention concept, the invention further provides a device for forwarding the messages in the multilink transparent Internet. When an overlay network is deployed, the TRILL network is used as an underlay network carrier, and the deploying process is simplified.
Owner:NEW H3C TECH CO LTD
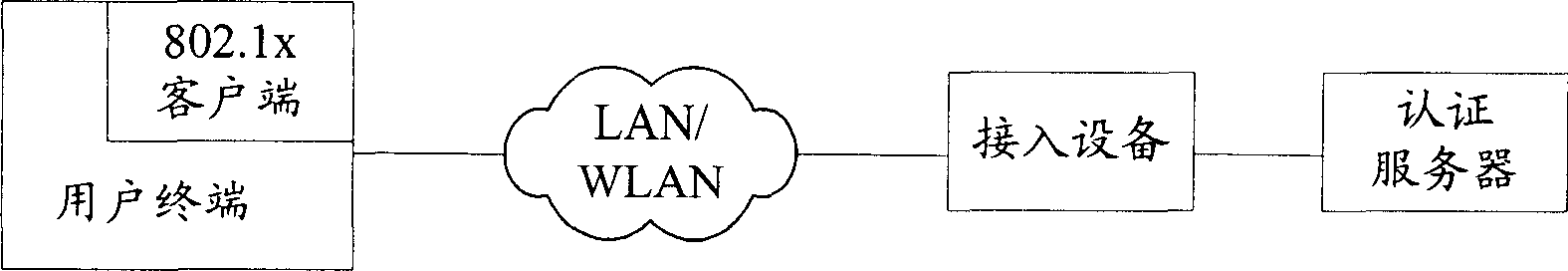
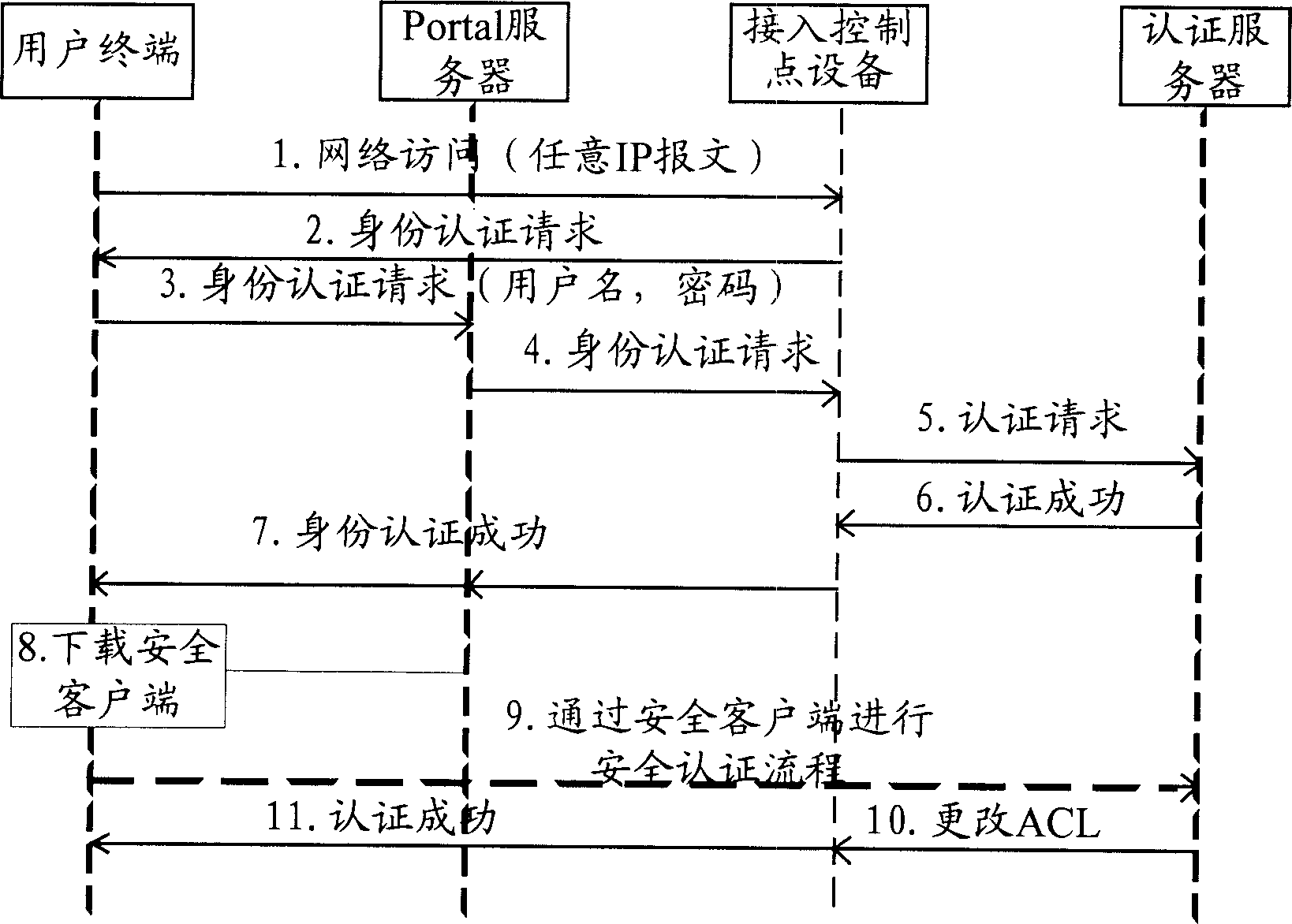
Method of controlling network access and its system
ActiveCN1753364AEasy to useNot threatenedData taking preventionUser identity/authority verificationSystem maintenanceClient-side
This invention discloses a network access control method and a system including: limiting the access extent of authority to users on-line by the web certification of a portal server to limit it to access the limited network resources only, a user downloads the safety UE by the Web, when the user accesses the protected network resources, the safety UE is used to certificate the safety of the UE and users passing through the safety certification access the protected network resources freely. The system includes: network access devices connected by network, a portal server and an AAA server.
Owner:NEW H3C TECH CO LTD
Development, testing, operation and maintenance integration system, deployment and full-quantity and incremental updating method
ActiveCN106293820ARealize integrationImplement automatic deploymentSoftware testing/debuggingProgram loading/initiatingApplication softwareMirror image
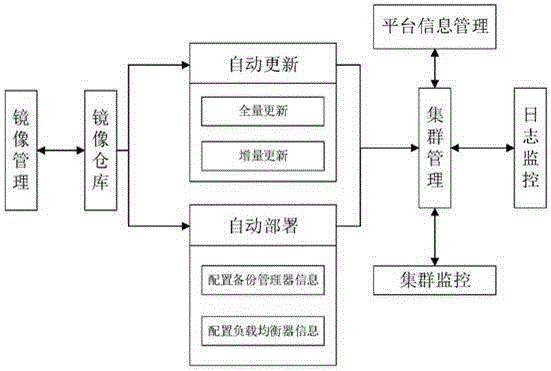
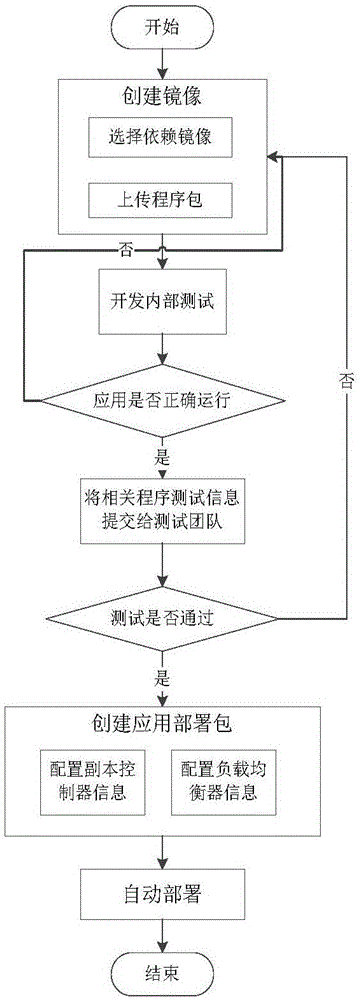
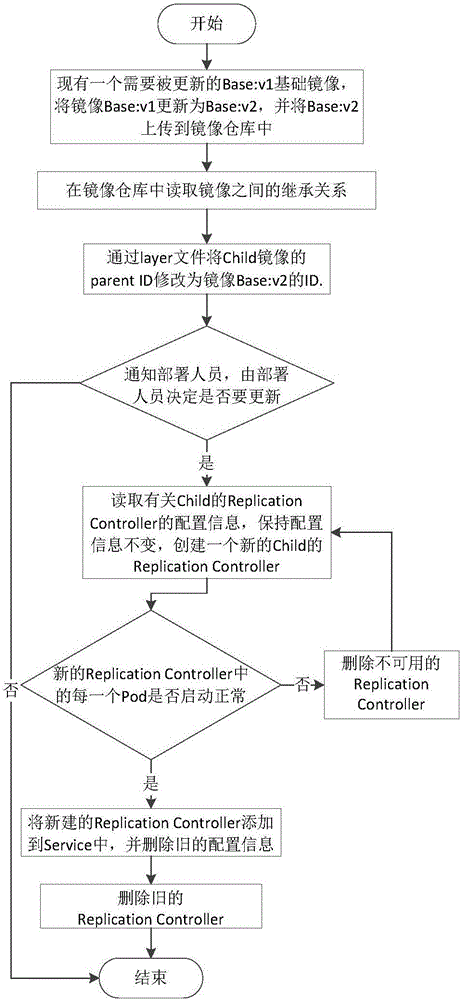
The invention discloses a development, testing, operation and maintenance integration system, deployment and a full-quantity and incremental updating method. The system comprises an automatic deployment module and an automatic updating module, wherein the automatic deployment module configures corresponding backup controller information and load balancer information according to mirror images in a mirror image warehouse at a developer end, automatically generates an application deployment script, and automatically / manually spreads the application deployment script to a testing deployment end; the testing deployment end automatically deploys an application to the testing, operation and maintenance environment by executing an application deployment script file, the automatic updating module updates an application program according to the mirror images in the mirror image warehouse at the developer end, generates an update pack file in a full-quantity or incremental updating mode and automatically / manually spreads the update pack file to the testing deployment end; the testing deployment end automatically deploys the updated application to the testing, operation and maintenance environment by executing the update pack file. Cooperation obstacles among development, testing, operation and maintenance are reduced, the cooperation efficiency is improved, application deployment processes are simplified, a developer pays close attention to business flows, and the requirement for technological levels of operation and maintenance staffs is lowered.
Owner:SHANDONG UNIV
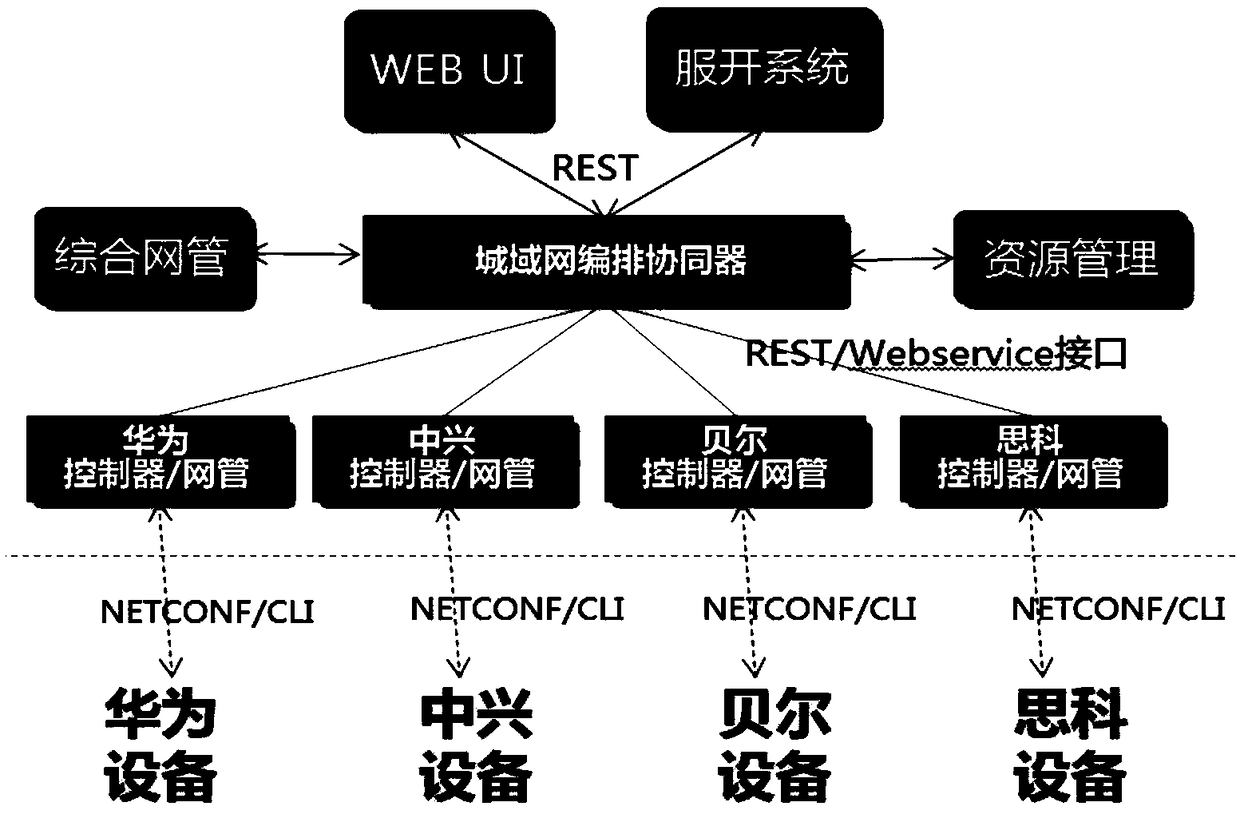
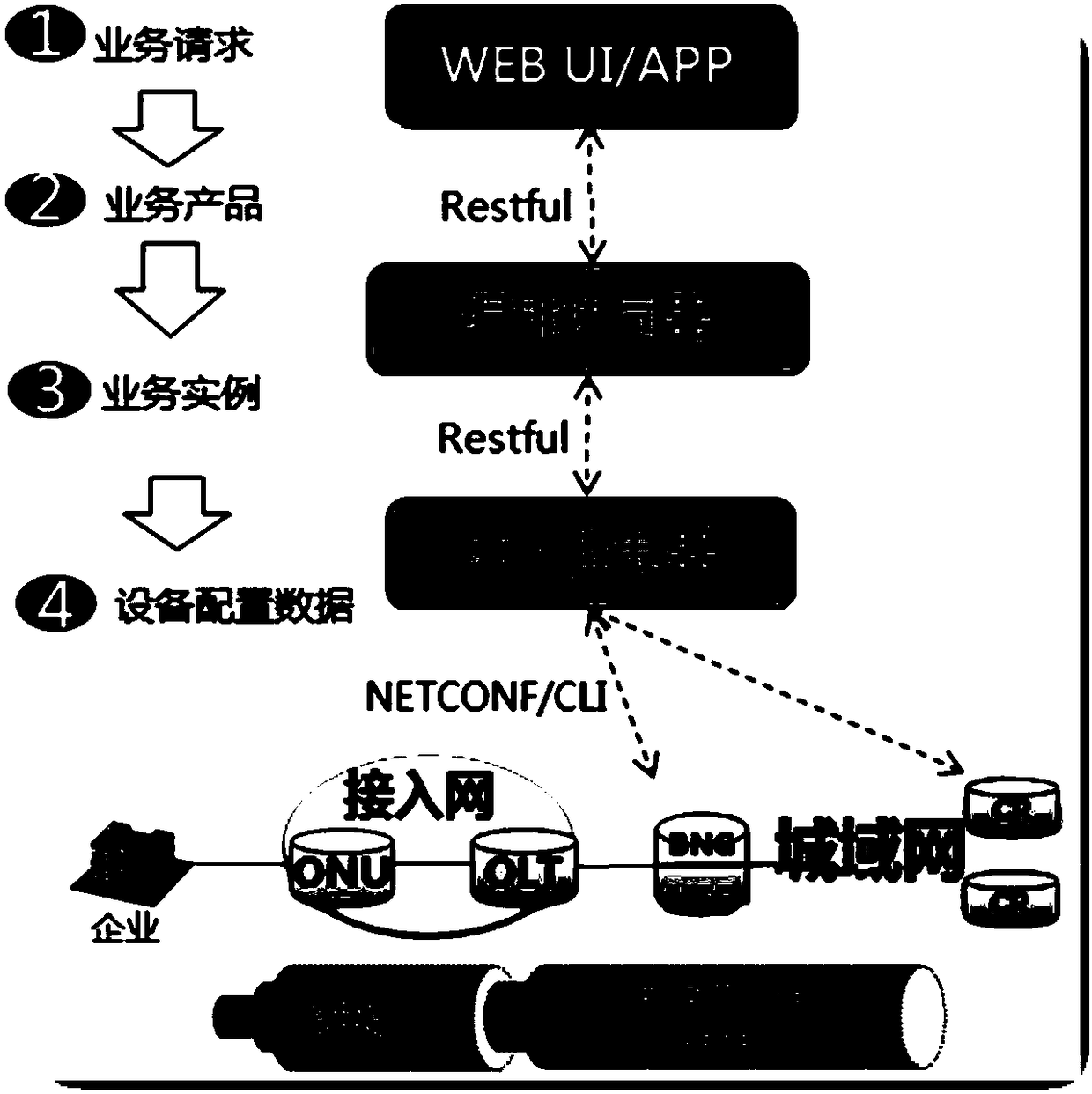
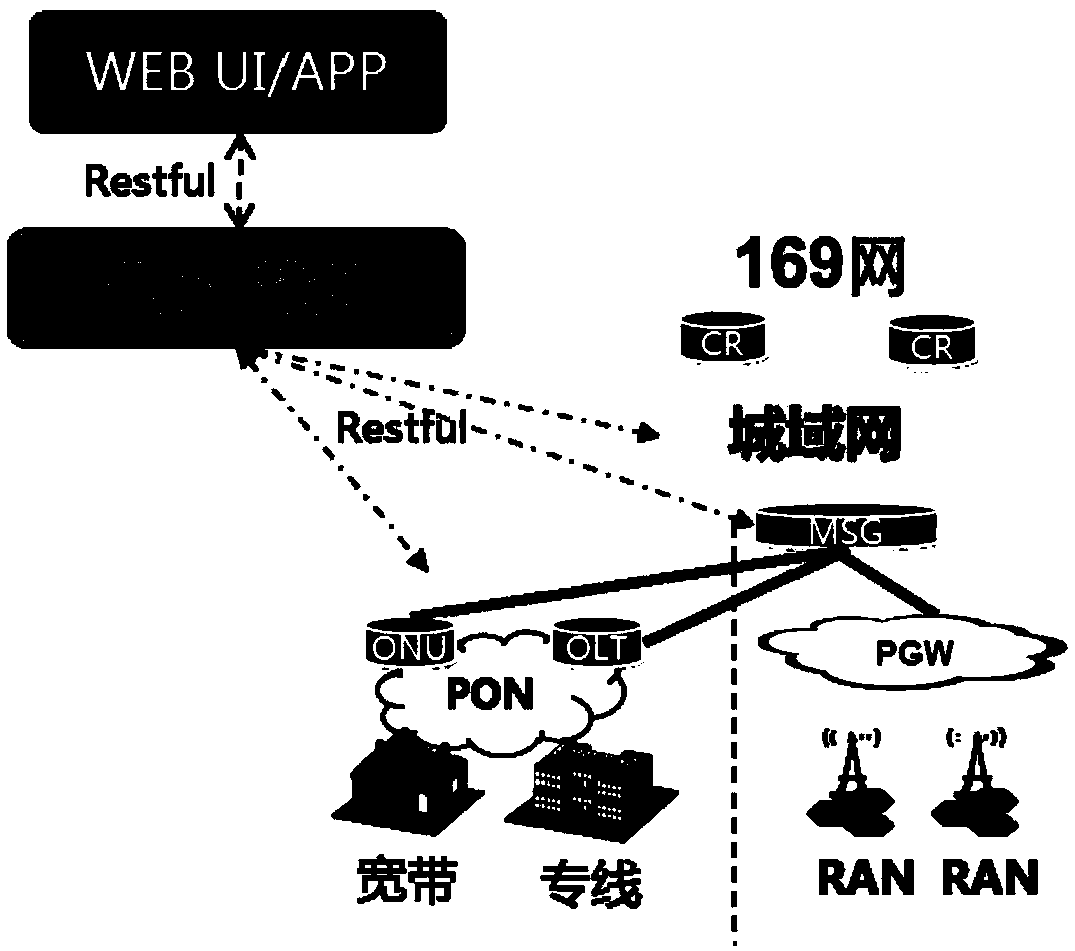
Service orchestrator-based metropolitan area network service processing method
ActiveCN109120459ARapid Deploy BuildSimplify the operation and maintenance processData switching by path configurationUser needsTraffic capacity
The invention discloses a service orchestrator-based metropolitan area network service processing method. According to the method, a service orchestrator is in butt joint with an application end and an SDN controller. The method includes the following steps that: S1, the application end submits a service request and invokes a service product in the service orchestrator; S2, the service orchestrator configures the service product with related parameters, creates a service instance, and issues an instruction to the SDN controller; S3, the SDN controller generates device configuration data according to the instruction of the orchestrator; and S4, the SDN controller sends the device configuration data to a metropolitan area network device through a NetConf protocol. With the method of the invention adopted, customized programming is performed based on user requirements; scheduling and adjustment are performed based on the traffic of an entire network; the closed management and control modeof a traditional network device is discarded; and the entire network can be rapidly deployed and constructed.
Owner:中国联合网络通信有限公司广东省分公司
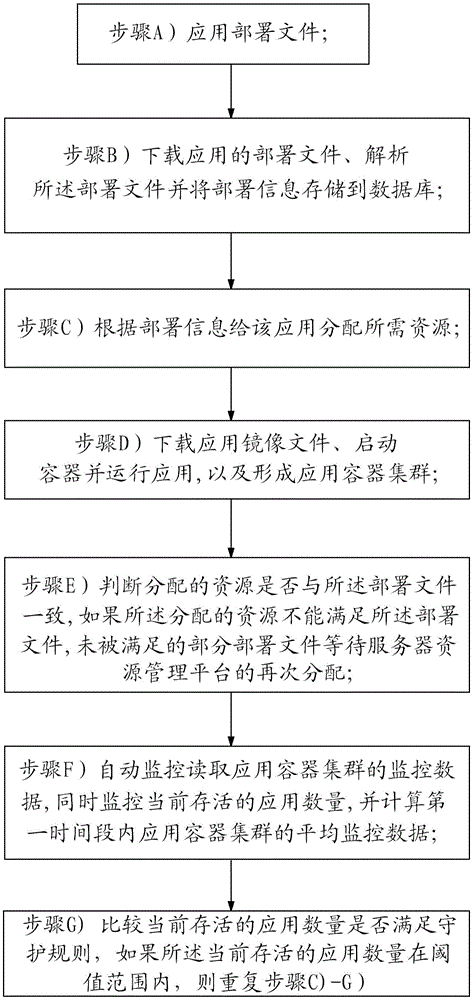
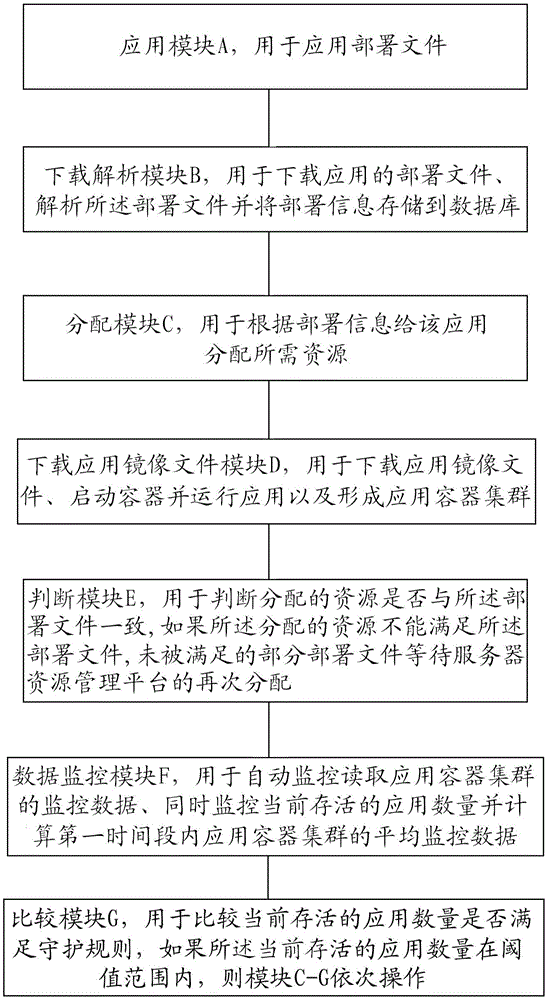
Method and system for automatically and flexibly assigning resource under cloud platform
ActiveCN105119952ANon-stop serviceSimplify the deployment processTransmissionClosed platformResource management
The invention provides a method and system for automatically and flexibly assigning resource under a cloud platform. The method includes steps of A, application disposition files, B, downloading the application disposition files, parsing the disposition files and storing the disposition information to a database, C, assigning required resources to the application according to the disposition information, D, downloading application mirror image documents, starting containers, running the application and forming an application container cluster, E, determining whether the assigned resource is consistent with the disposition files, and if the assigned resource can not satisfy the disposition files, the unsatisfied portion of the disposition files waiting the re-assigning of a server resource management platform, F, automatically monitoring and reading monitoring data of the application container cluster, monitoring the quantity of the current live applications and calculating the average monitoring data of the application container cluster in a first time period, G, comparing whether the quantity of the current live applications satisfies the protection rules, and repeating the step C-G if the quantity of the current live applications is within the threshold scope.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Container-based block chain deployment method
InactiveCN109800056ASimplify the deployment processTroubleshoot deployment issuesSoftware simulation/interpretation/emulationOperational systemLow speed
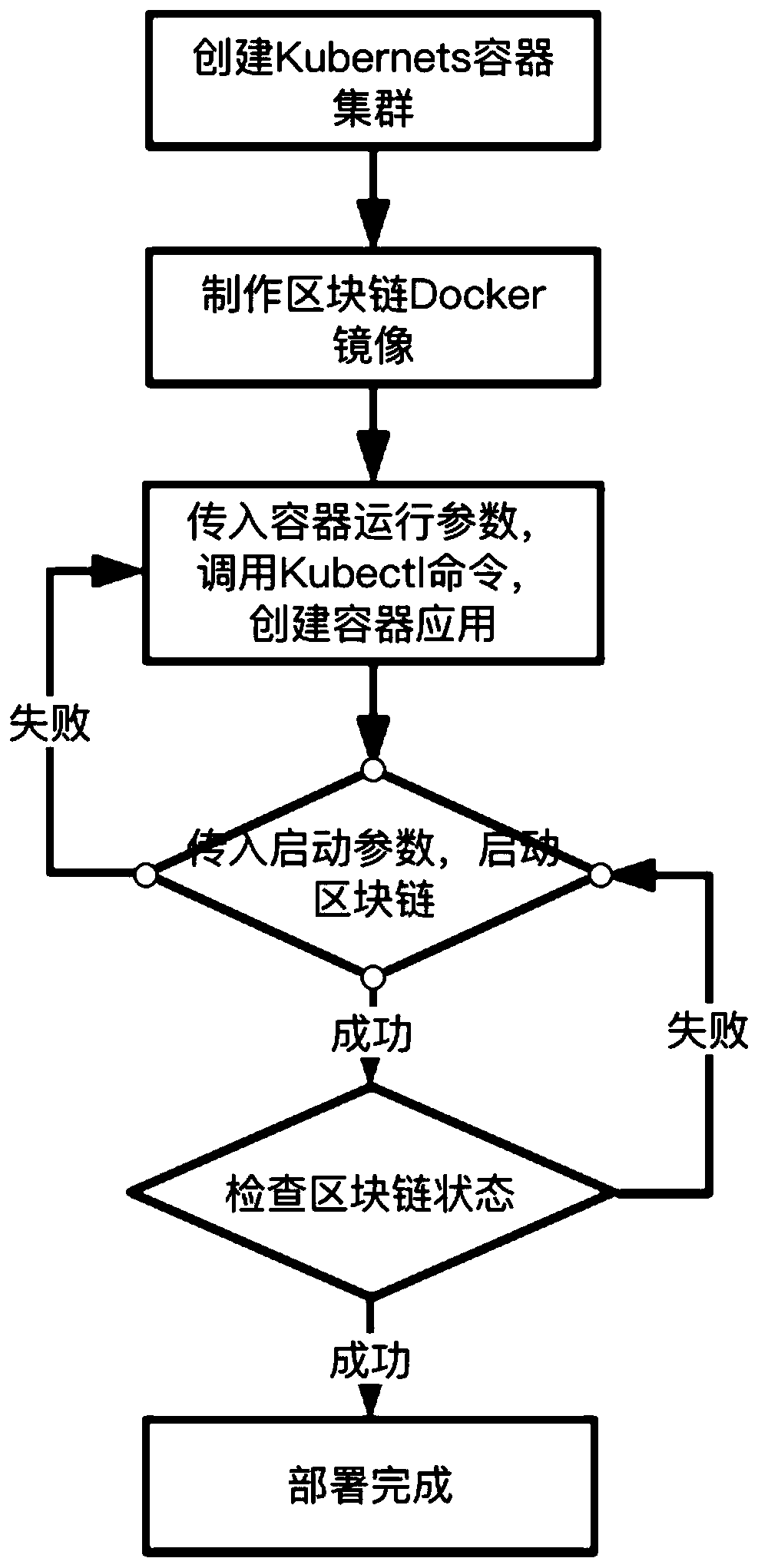
The invention discloses a container-based block chain deployment method. The method comprises the following steps: 1) establishing a kubernetes container cluster; 2) manufacturing a Docker mirror image comprising an operating system, a block chain installation package, a daemon process and a startup script; 3) creating a container arrangement file, and defining the number of container instances, aused mirror image ID, a running port, an NAT gateway ID and an elastic IP; 4) calling a Kubectl command line tool, connecting the container cluster created in the step 1), loading the docker image produced in the step 2) by using the container arrangement file created in the step 3), and creating a blockchain container application; 5) communicating with a daemon process in the container through the GRPC, calling a command for starting the block chain, transmitting a starting parameter, and starting the block chain; And calling a command for checking the block chain state, checking whether theblock chain is successfully started or not, and completing the deployment of the block chain. According to the invention, the container-based block chain deployment method is realized, and the problems of complex operation and low speed of block chain deployment are solved.
Owner:HANGZHOU QULIAN TECH CO LTD
Virtual machine performance testing system based on cloud service
InactiveCN105847088AImprove performance testing efficiencyImprove readabilityData switching networksSystems managementStructure of Management Information
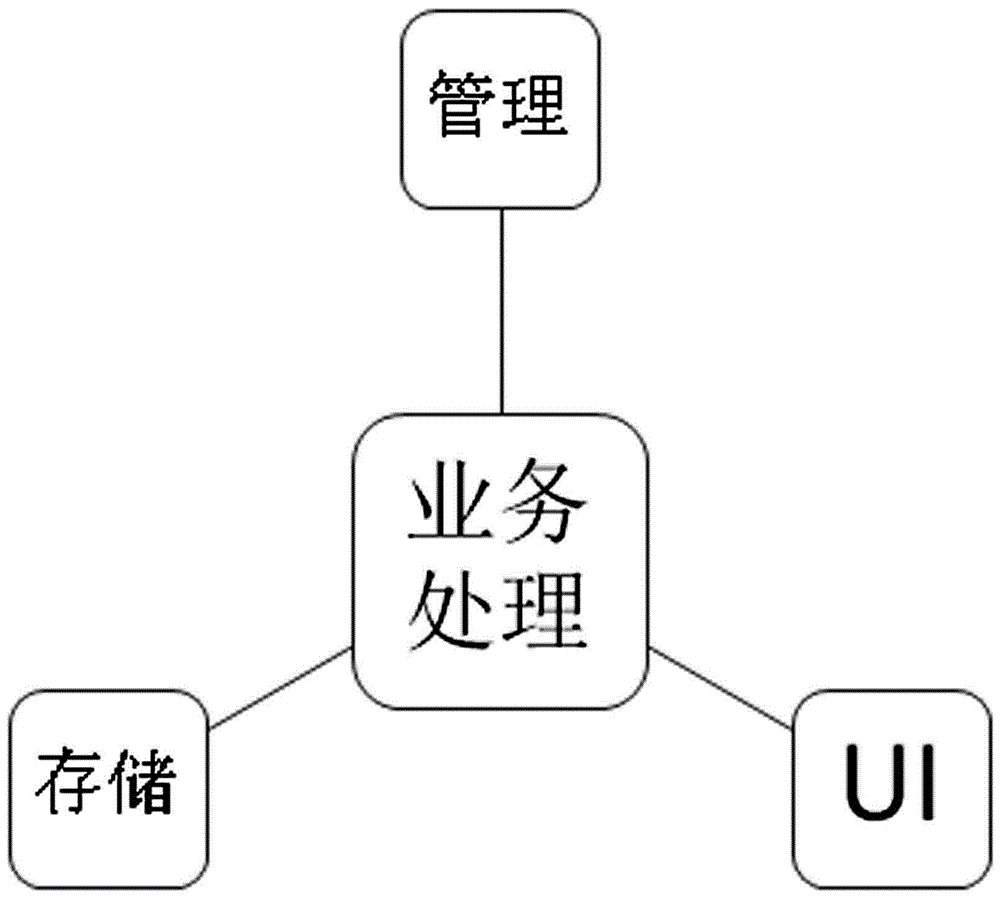
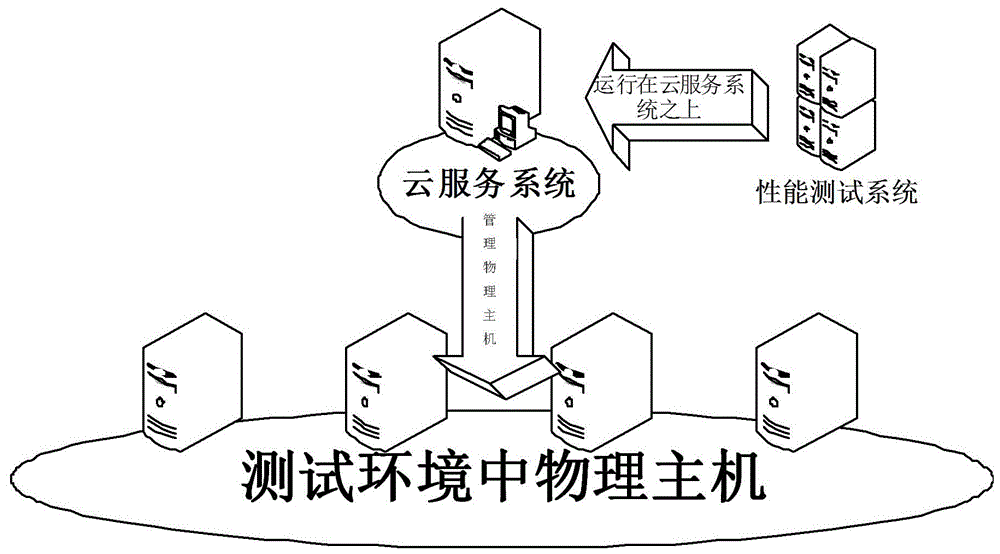
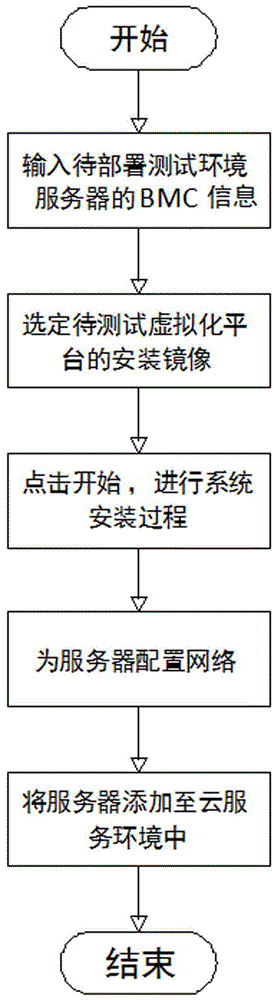
The invention discloses a virtual machine performance test system based on cloud service, which includes a performance test system, and its structure is composed of a business processing module, a storage module, a UI module and a management module, wherein the business processing module is responsible for the processing and processing of various business flows Scheduling, the storage module stores relevant information, the UI module provides an interactive interface, and the management module is responsible for the daily operation and management of the system; the cloud service system, the above-mentioned performance test system runs on the cloud service system, and the cloud service system performs unified management, including the initial network The configuration and testing of storage and storage require the construction of a virtual machine; the physical host is managed by the above-mentioned cloud service system and used to deploy the virtual platform to be tested. Compared with the existing technology, this virtual machine performance test system based on cloud service greatly simplifies the process of building the test environment, provides a variety of test solutions in package and has good scalability, strong practicability, and easy promote.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Safety service platform and safety service deployment method
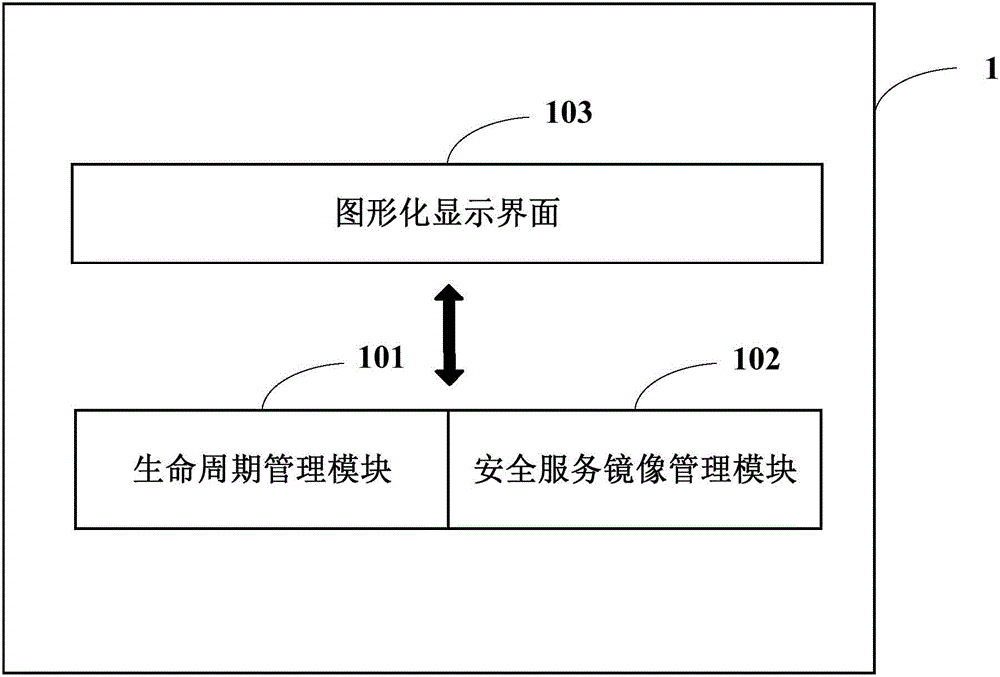
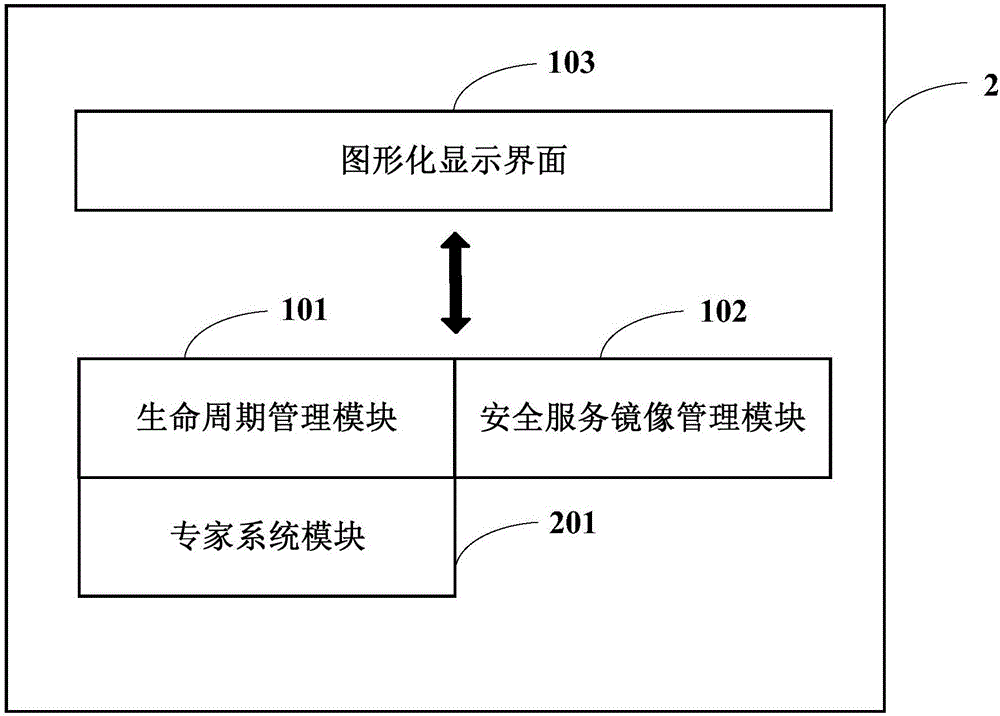
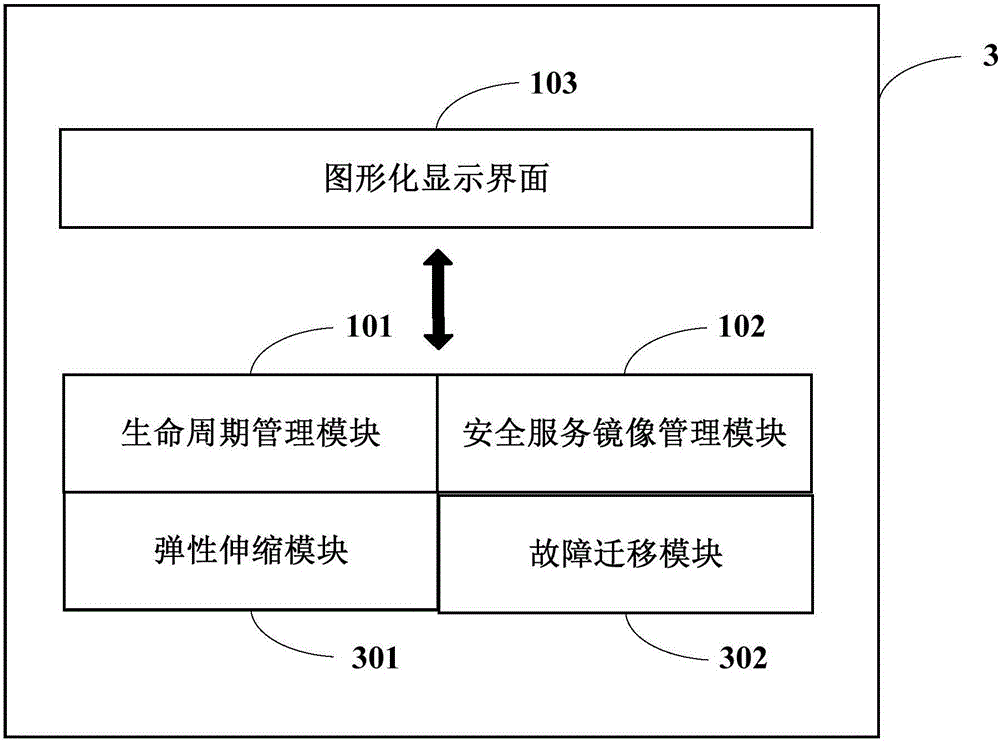
InactiveCN106330575AEasy to deployEasy maintenanceData switching networksGraphical user interfaceComputer science
The invention embodiment discloses a safety platform and a safety service deployment method. The safety service platform comprises a lifecycle management module, a safety service image management module and a graphical display interface, wherein the lifecycle management module is used for providing configuration interface for the users, which acquires deployed configuration information of safety service required by the users through configuration interface, and deploys safety service in the targeted cloud platform based on the configuration information; communication of safety service image management module and lifecycle management module is under connection, which is used for providing ate least one image information of safety service for lifecycle management module; graphical display interface is used for graphical display of lifecycle management module and safety service image management module. The safety platform and safety service deployment method implementation provides unified operation platform for safety service deployment by adopting the above technical scheme, easy for operation, low-priced, and is convenient for the related technicians to implement unified deployment and maintenance for different safety services through the platform, to improve maintenance efficiency.
Owner:上海有云信息技术有限公司
Distributed storage system deployed on the basis of container technology and storage method thereof
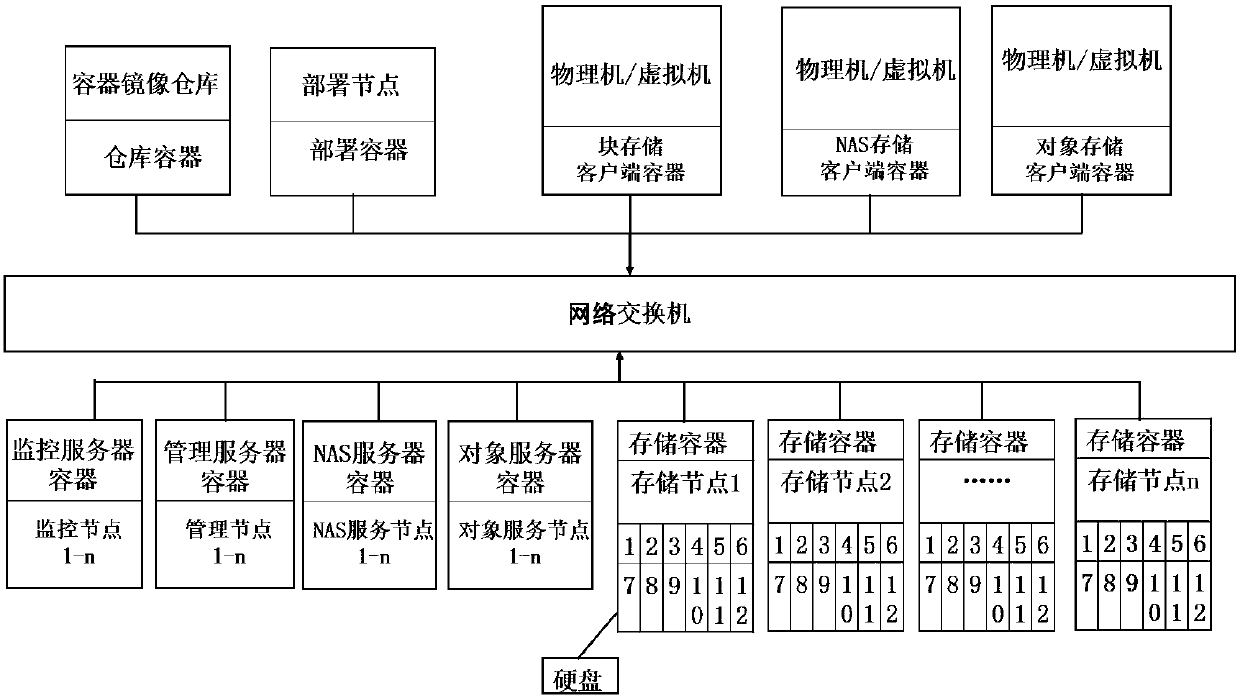
ActiveCN107797767ASimplify the deployment processImplement deploymentInput/output to record carriersLogfileDistributed memory systems
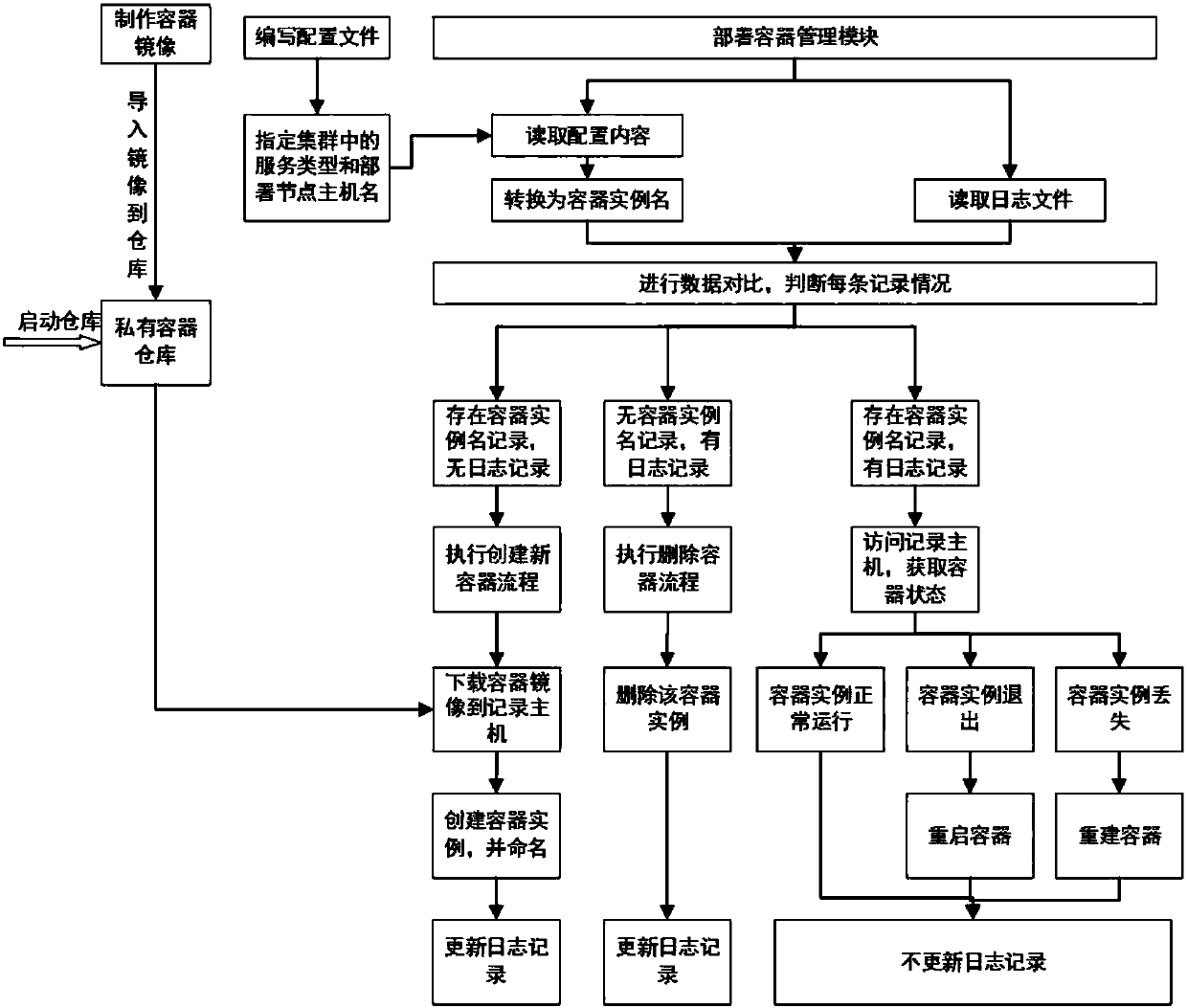
The invention discloses a distributed storage system deployed on the basis of container technology. The system includes a plurality of nodes connected with a network switch. The nodes are divided intoa deployment node, a container mirror image warehouse node and a plurality of service end nodes and client nodes used for deploying distributed storage. A storage method of the above storage system includes the steps of: (1) making a container mirror images of various services to establish a private container warehouse; (2) specifying all service types in a cluster and node host names, which needto be used for deployment, to save the same to a configuration file; (3) reading configuration file contents and log file contents through a deployment container management module; (4) obtaining instance names of all containers by conversion according to the read configuration file contents; (5) carrying out data comparison according to the container instance names, which are obtained by conversion, and a read log file to judge status of all records; and (6) carrying out distinguishing according to comparison results of all the records, and carrying out different operations. The system and the method realize simple and highly efficient automated management.
Owner:南京卓盛云信息科技有限公司
Virtualization implementing method for Power server
ActiveCN102981888ASimplify the deployment processSimplify configuration workSoftware simulation/interpretation/emulationVirtualizationOperational system
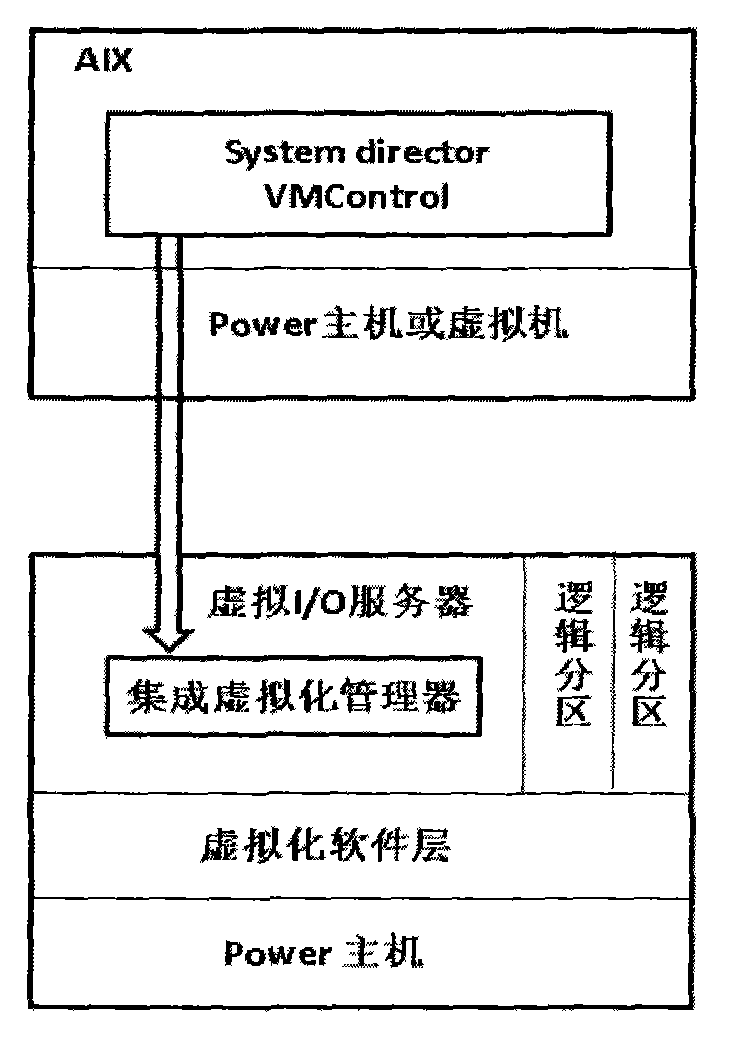
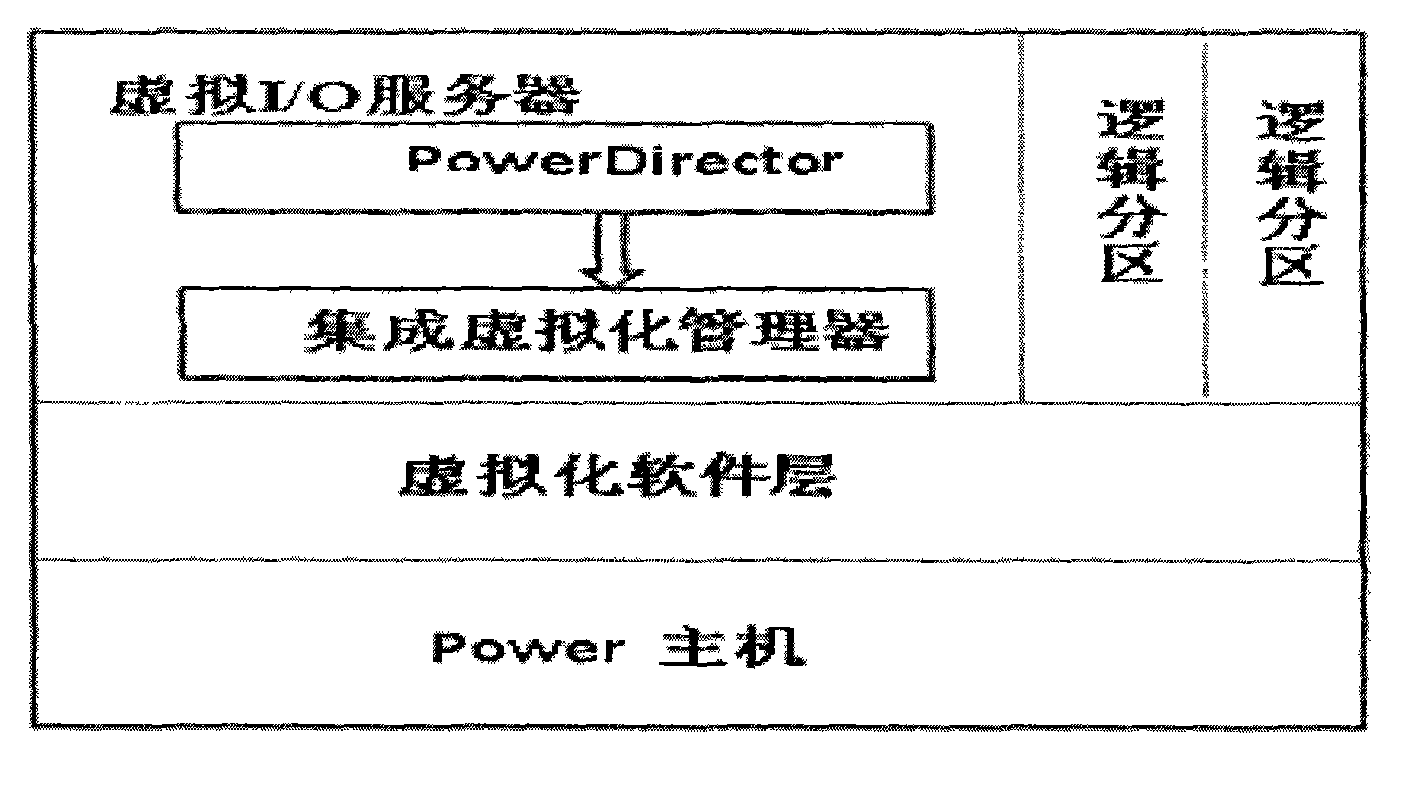
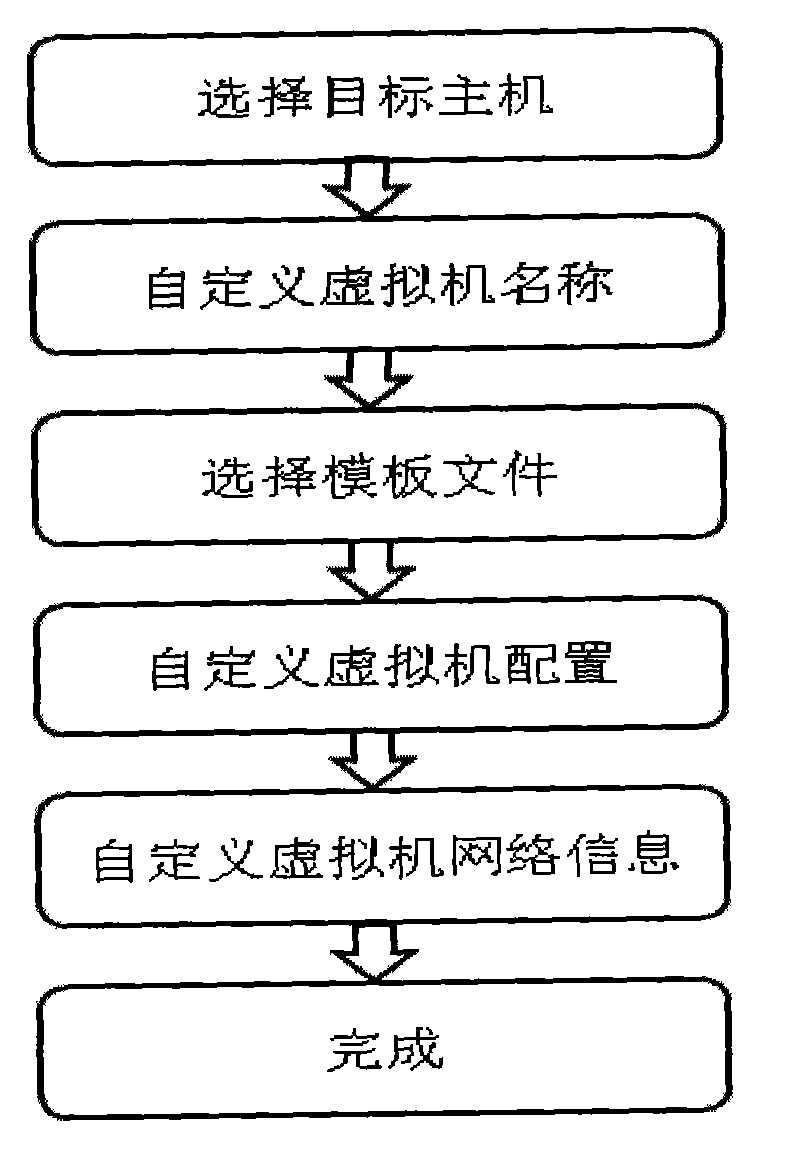
A virtualization implementing method for a Power server includes the steps of enabling virtualization management software to be directly installed in a virtual machine input / output (I / O) server; enabling at least one integrated virtualization manager (IVM) to be used as a platform and then to be registered to virtualization management software (Power Director); using commands supplied by the virtual machine I / O server and each IVM to create a virtual machine; enabling a preset installing module to automatically install in the created virtual machine through an image management function according to demands of a user and enabling a configuration file, an operating system, a network information configuration of the virtual machine to be completed. The virtualization implementing method for the Power server does not need to singly be supplied with another host machine or the virtualization management software so as to save host machine source and largely simplify deployment and configuration of the virtualization management software, and improve working efficiency of managers.
Owner:BEIJING TEAMSUN TECH
Method and device for deploying virtualized management node
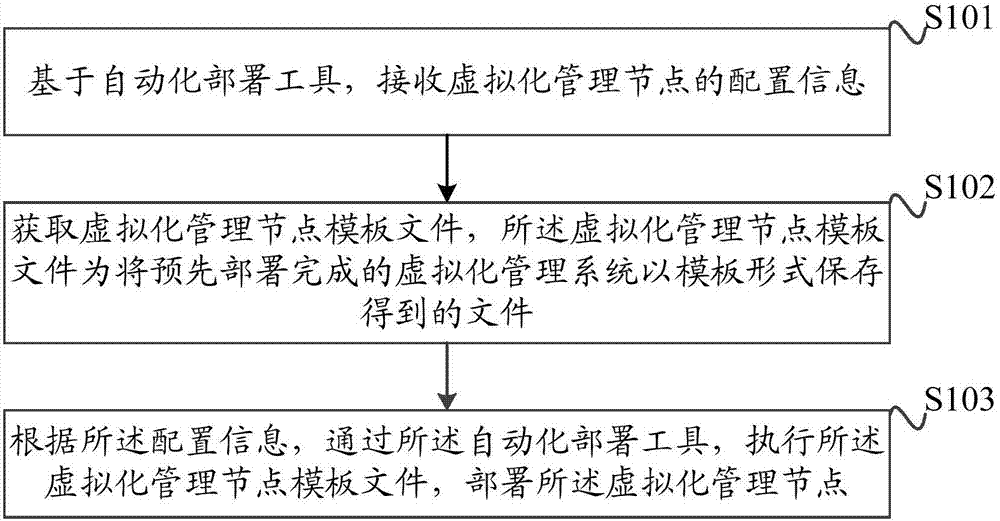
InactiveCN107153571AEfficient and easy to deployLower deployment costsSoftware simulation/interpretation/emulationRedundant hardware error correctionVirtualizationOperating system
The invention discloses a method for deploying a virtualized management node. The method is based on an automatic deployment tool and comprises the steps of receiving deployment information of the virtualized management node, acquiring a virtualized management node template file, executing the virtualized management node template file through the automatic deployment tool according to the deployment information, and deploying the virtualized management node, wherein the virtualized management node template file is a file obtained by storing a virtualized management system deployed in advance in a form of template. The virtualized management node template file stored and deployed in advance is executed through the automatic deployment tool, the virtualized management node is automatically installed and deployed without spending a large quantity of manpower and time, and the deployment cost is lowered; the traditional deployment flow is simplified, the deployment of the virtualized management node is efficient and convenient, and the deployment efficiency is improved. In addition, the invention further discloses a device for deploying the virtualized management node, and the device has advantages corresponding to the method one by one.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Visual data processing flow setting method and device, equipment and storage medium
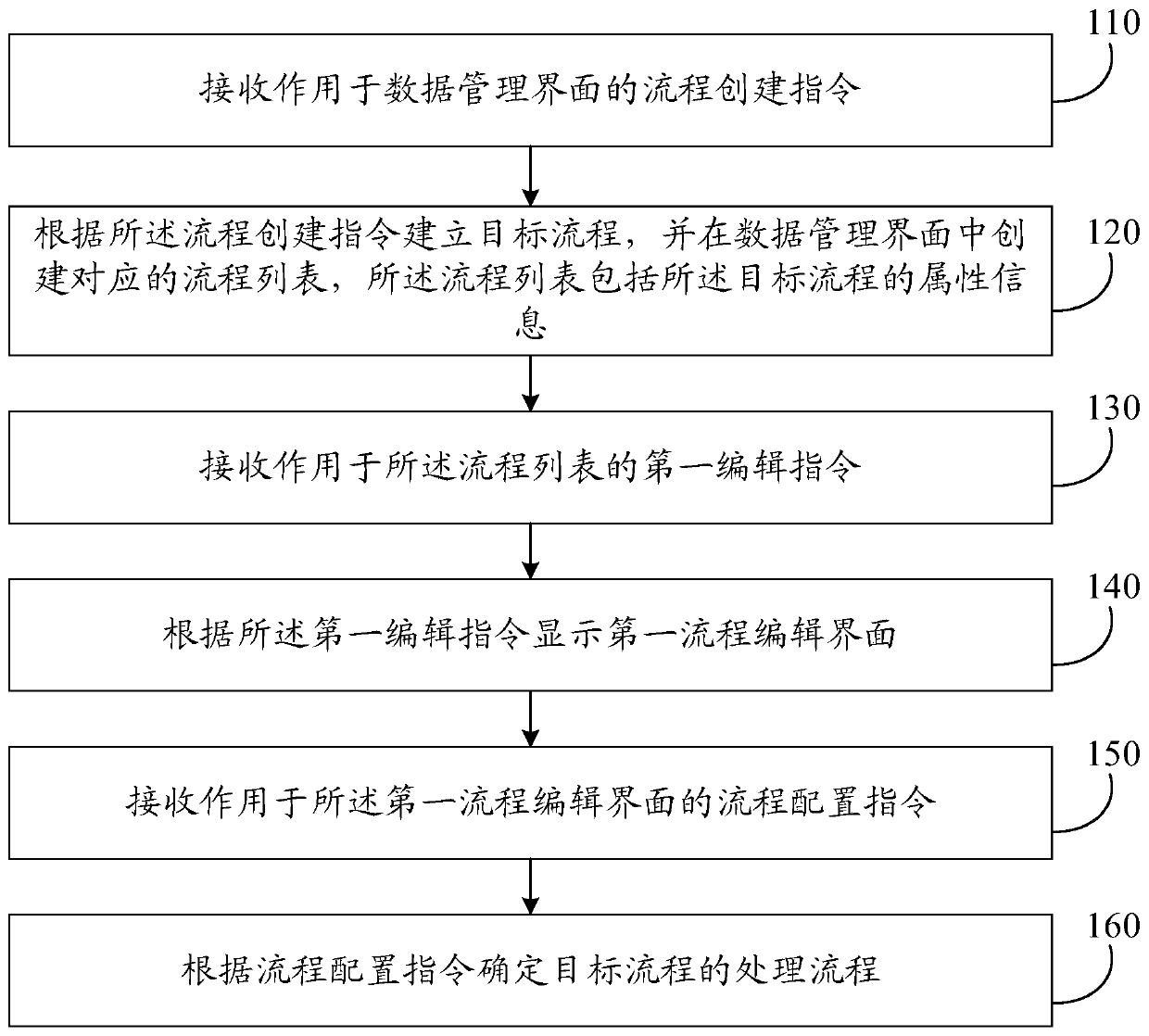
InactiveCN110007913ASimplify the deployment processReduce difficultyVisual/graphical programmingProcess configurationData processing
The embodiment of the invention discloses a visual data processing flow setting method and device, equipment and a storage medium. The method comprises: receiving a flow creation instruction acting ona data management interface; establishing a target flow according to the flow establishment instruction, and establishing a corresponding flow list in the data management interface, the flow list comprising attribute information of the target flow; receiving a first editing instruction acting on the flow list; displaying a first process editing interface according to the first editing instruction, the first process editing interface comprising a plurality of target components, one target component corresponding to one processing mode; receiving a process configuration instruction acting on the first process editing interface, wherein the process configuration instruction is used for selecting a target component required by a target process; and determining a processing flow of the targetflow according to the flow configuration instruction. The setting process of the data processing flow is optimized.
Owner:PCI TECH GRP CO LTD
Wireless network deployment method, apparatus and system
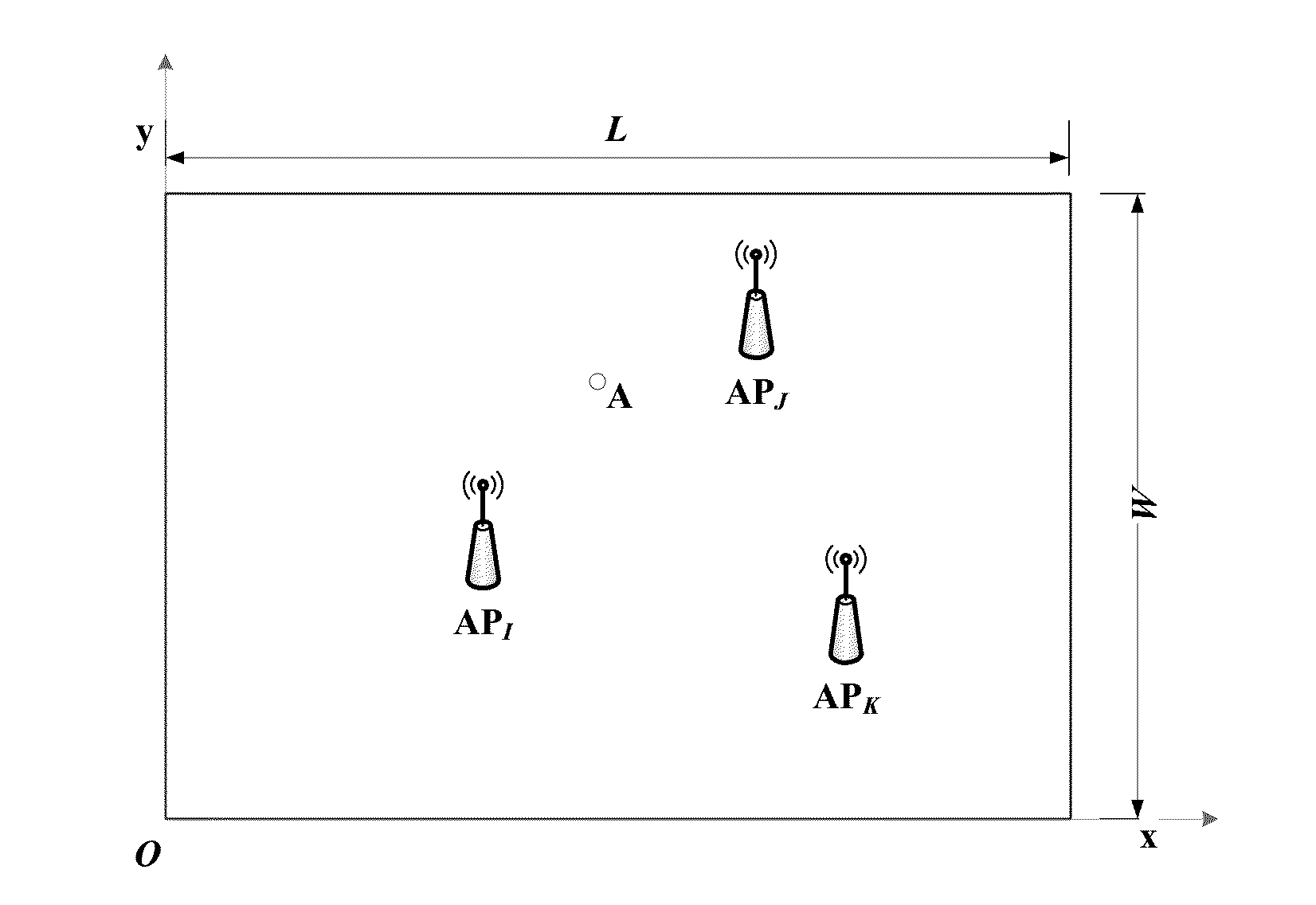
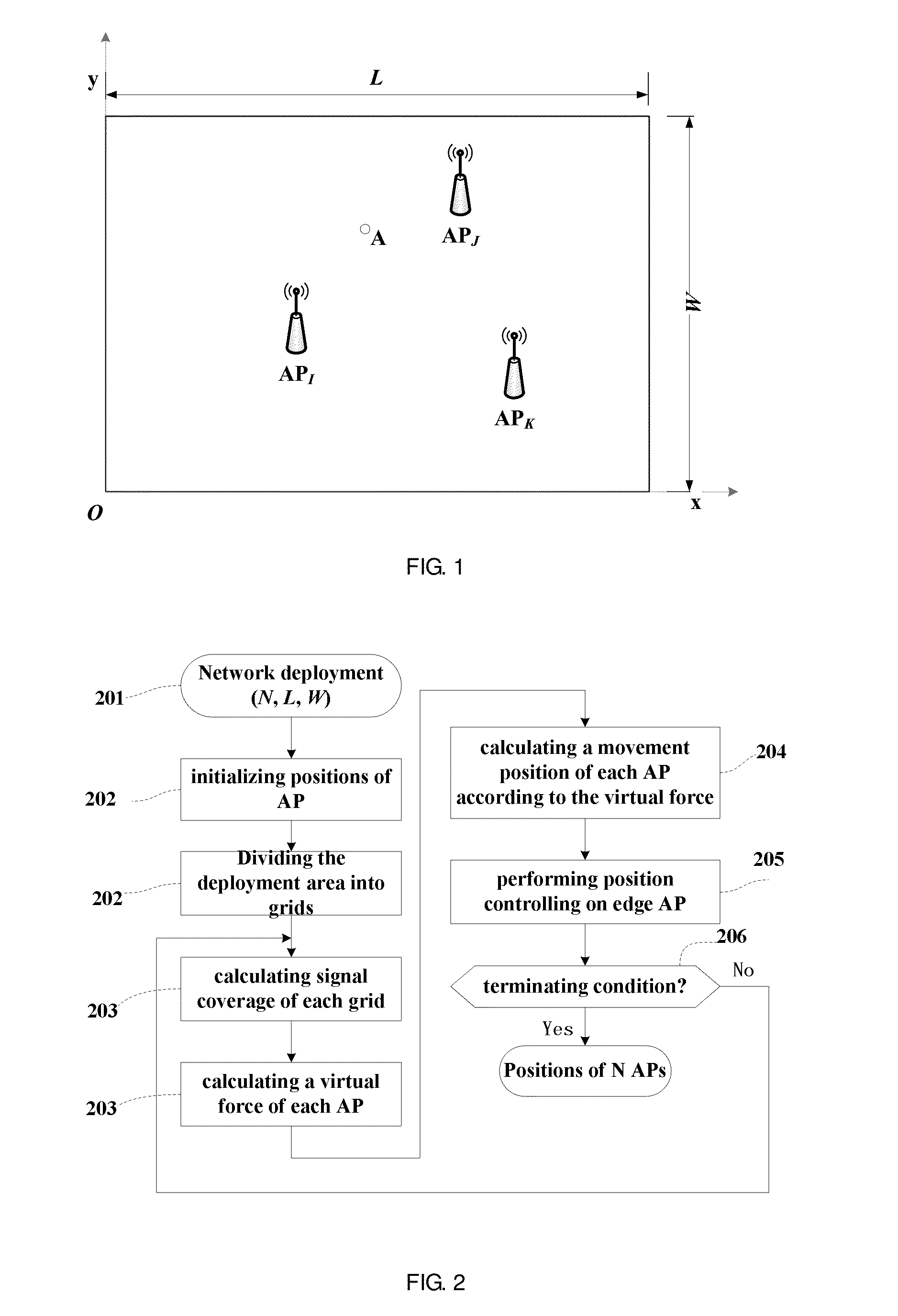
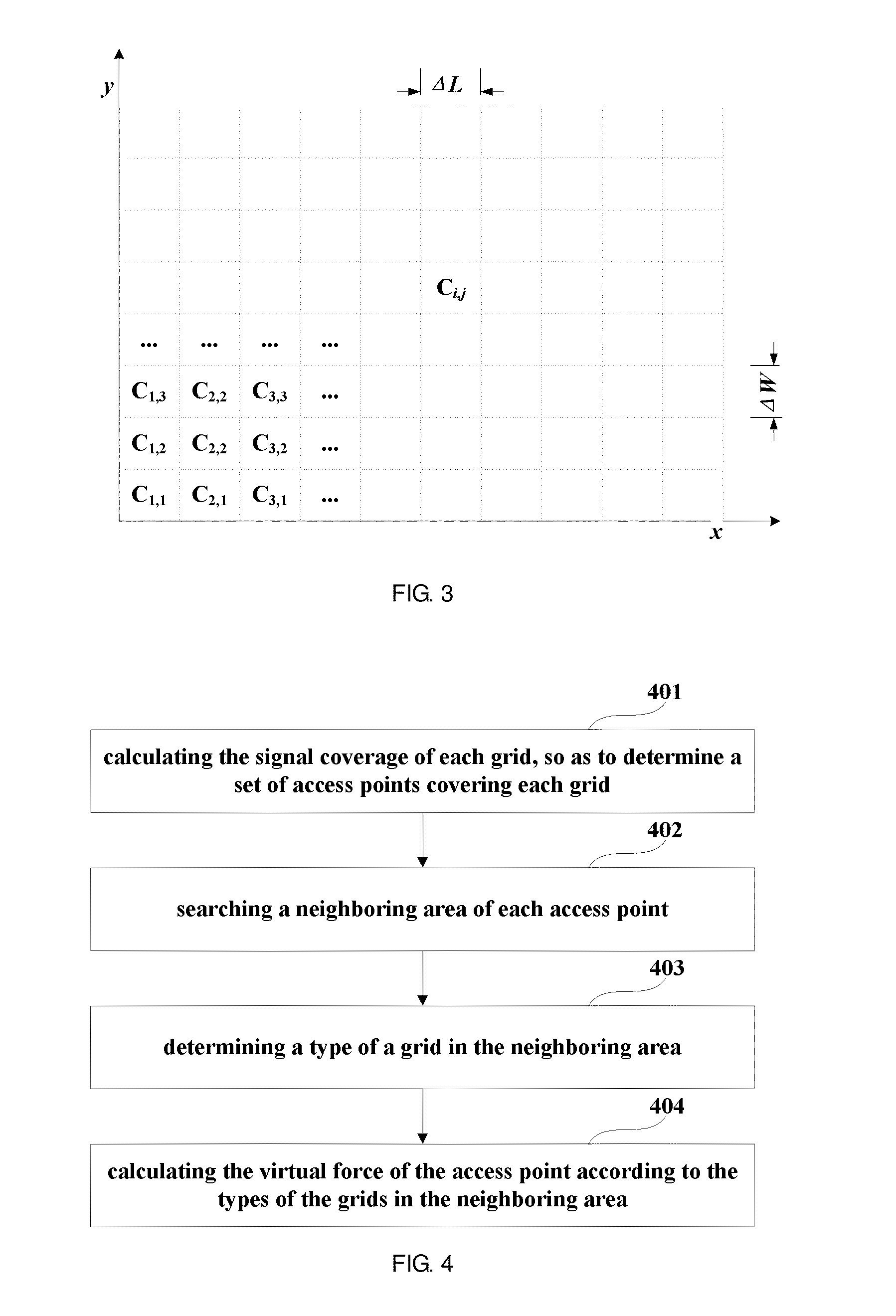
InactiveUS20160127916A1Simplify the deployment processFast convergenceNetwork planningMobile locationRepulsion force
A wireless network deployment method, apparatus and system where the includes: initializing the wireless network to determine a deployment area and the number of access points needing to be deployed; initializing positions of the access points, and dividing the deployment area into grids; calculating a virtual force of each access point based on signal coverage of each grid; calculating a movement position of each point according to the virtual force; performing edge controlling on each point; and terminating processing when a terminating condition is satisfied. A deployment process is simulated as a dynamic physical process, movement of the access points along a direction of a resultant force of all repulsion forces and attractive forces is controlled following the principle that an overlapping covered area produces a repulsion force and an uncovered area produces an attractive force.
Owner:FUJITSU LTD
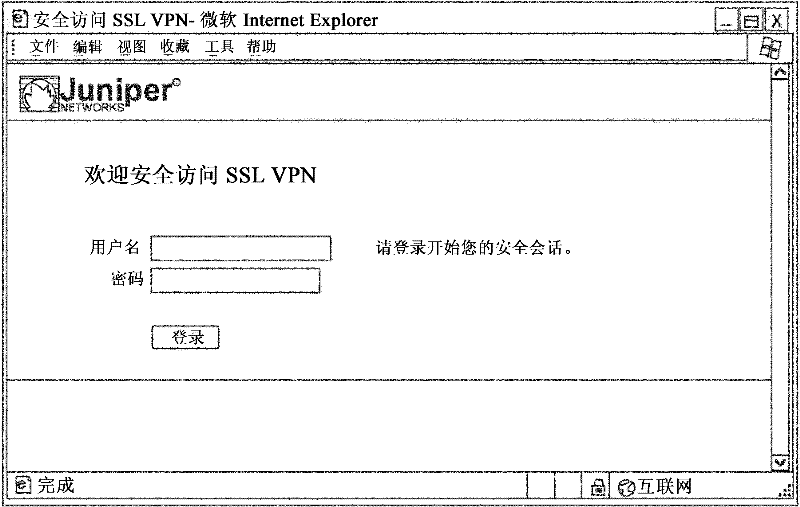
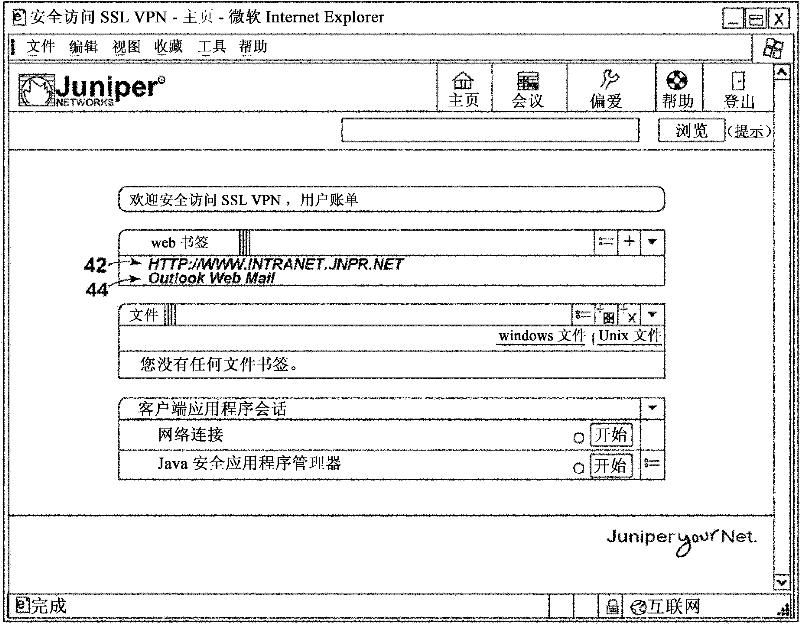
Vpn network client for mobile device having fast reconnect
ActiveCN102333110AConflict minimizationReduce in quantityTransmissionSecurity arrangementWeb browserNetwork packet
A virtual private network (VPN) client for cellular mobile devices is described. The VPN network client processes network packets for securely tunneling the network packets between the cellular mobile device and the remote VPN security device. Upon establishing the VPN connection, the VPN network client receives a web-based home page from the secure VPN device via a secure response, dynamically parses bookmark links from the secure response and renders a bookmark window using input controls native to the cellular mobile device without invoking a web browser on the cellular mobile device. Each of the input controls corresponds to a different one of the bookmarks parsed from the secure response. Upon selection of one of the input controls, the VPN network client formulates and outputs an appropriate request to the secure VPN device as if a corresponding one of the bookmark links were selected by the user.
Owner:PULSE SECURE
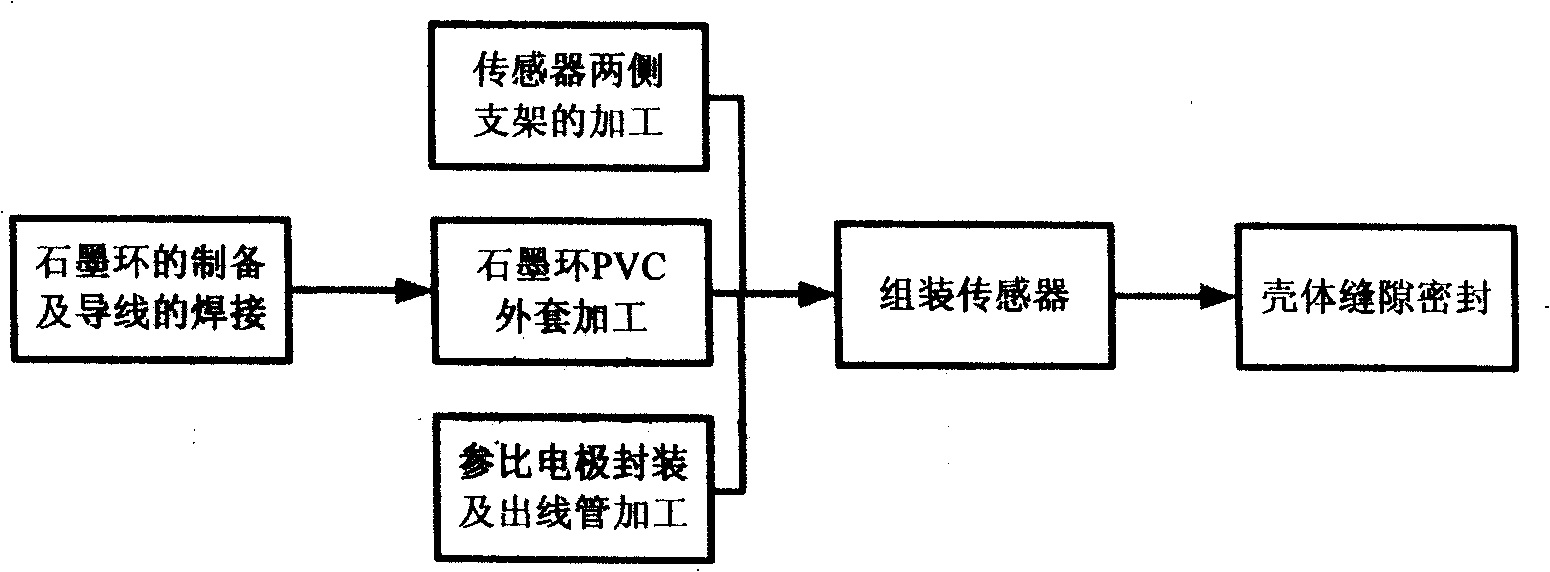
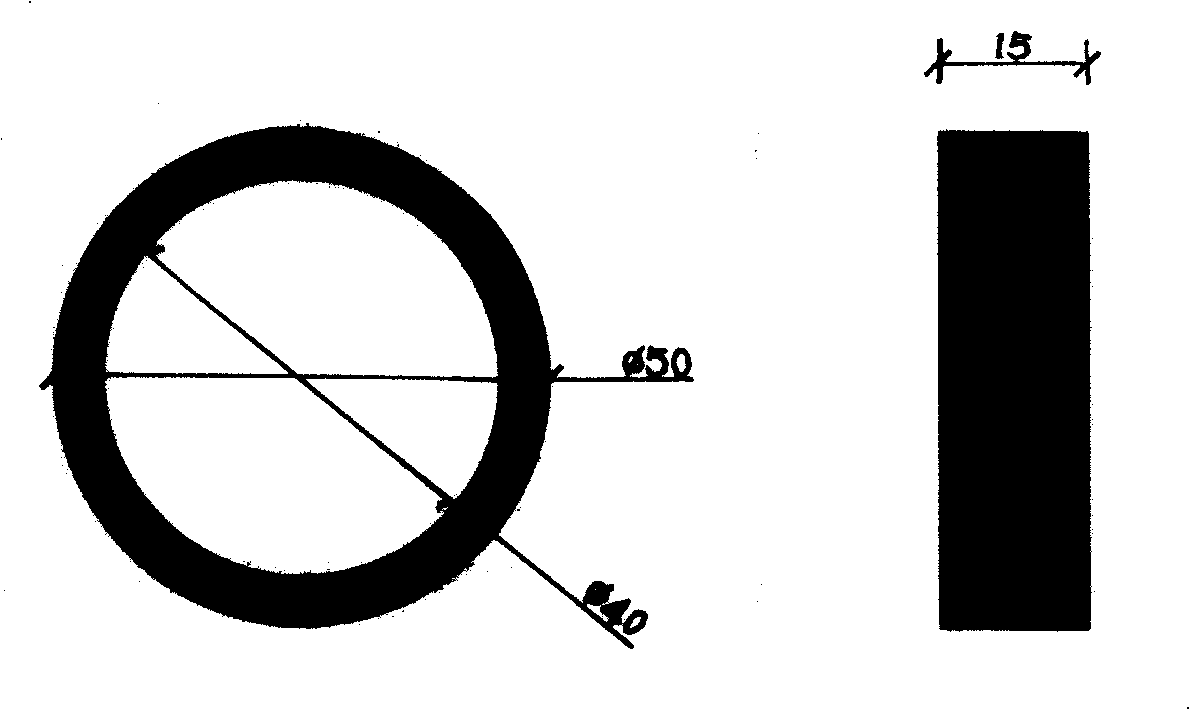
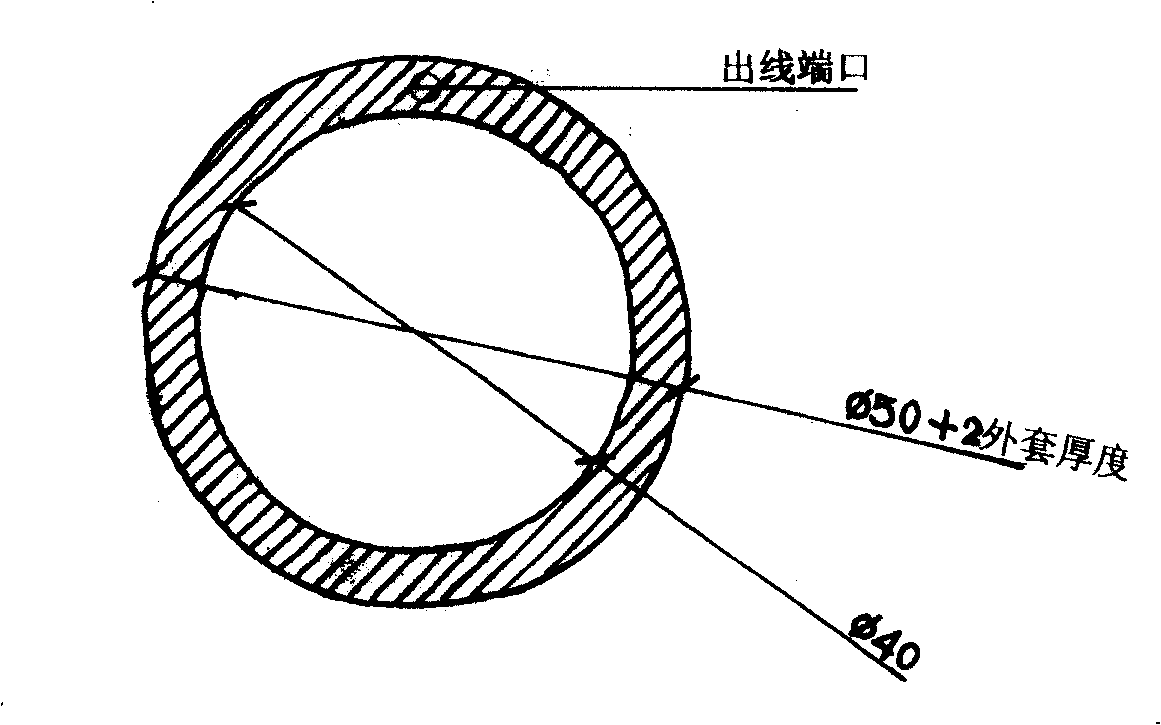
Complete solid-state beam current type reinforcing steel corrosion monitoring sensor and method for producing the same
InactiveCN101299018ARealize online monitoringSolution to short lifeWeather/light/corrosion resistanceMaterial analysis by electric/magnetic meansDielectricElectricity
The present invention provides a total solid beam contraction type steel corrosion monitoring sensor and a preparation method thereof. The total solid beam contraction type steel corrosion monitoring sensor comprises three graphite beam contraction rings, three total solid reference electrode, two sensor fixing racks, three sets of beam contraction protecting casing and three sets of PVC tubes used for packing the total solid reference electrodes and leading out the conducting wire. The invention uses finite elements for analyzing the arrangement characteristic of potential wire in solid dielectric of concrete, and at the same time adopts a long-lifetime and total solid reference electrodes which are developed independently for realizing the control to the area of working electrode in the corrosion monitoring process with the electrochemistry method. Finally the total solid beam contraction type corrosion sensor which has reasonable structure and is suitable for the application of actual project is designed out. A designing concept of ''plug and play'' is adopted in the designing process of sensor. The fast construction requirement can be satisfied, and the laying process of the sensor is greatly simplified.
Owner:HARBIN INST OF TECH
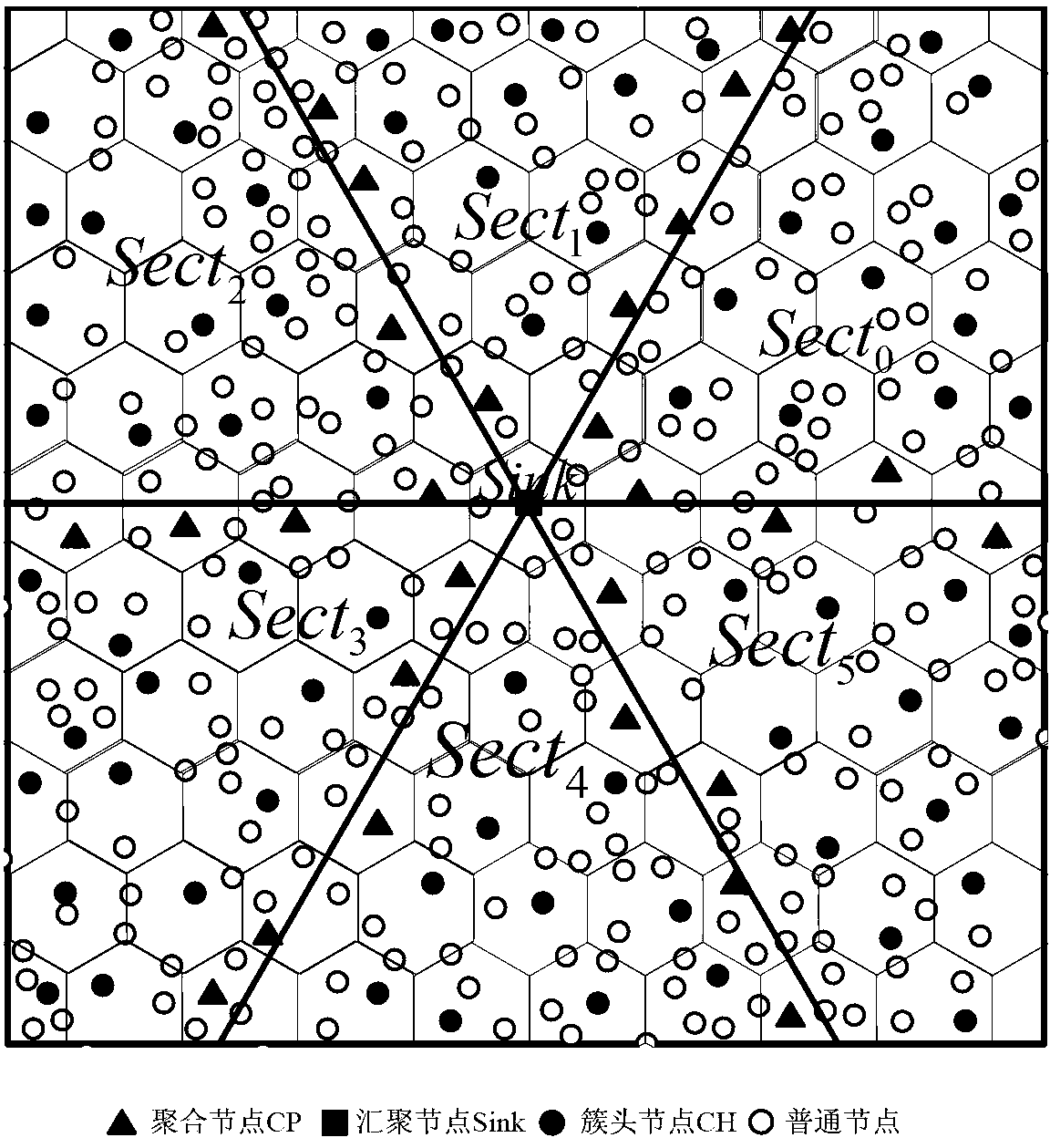
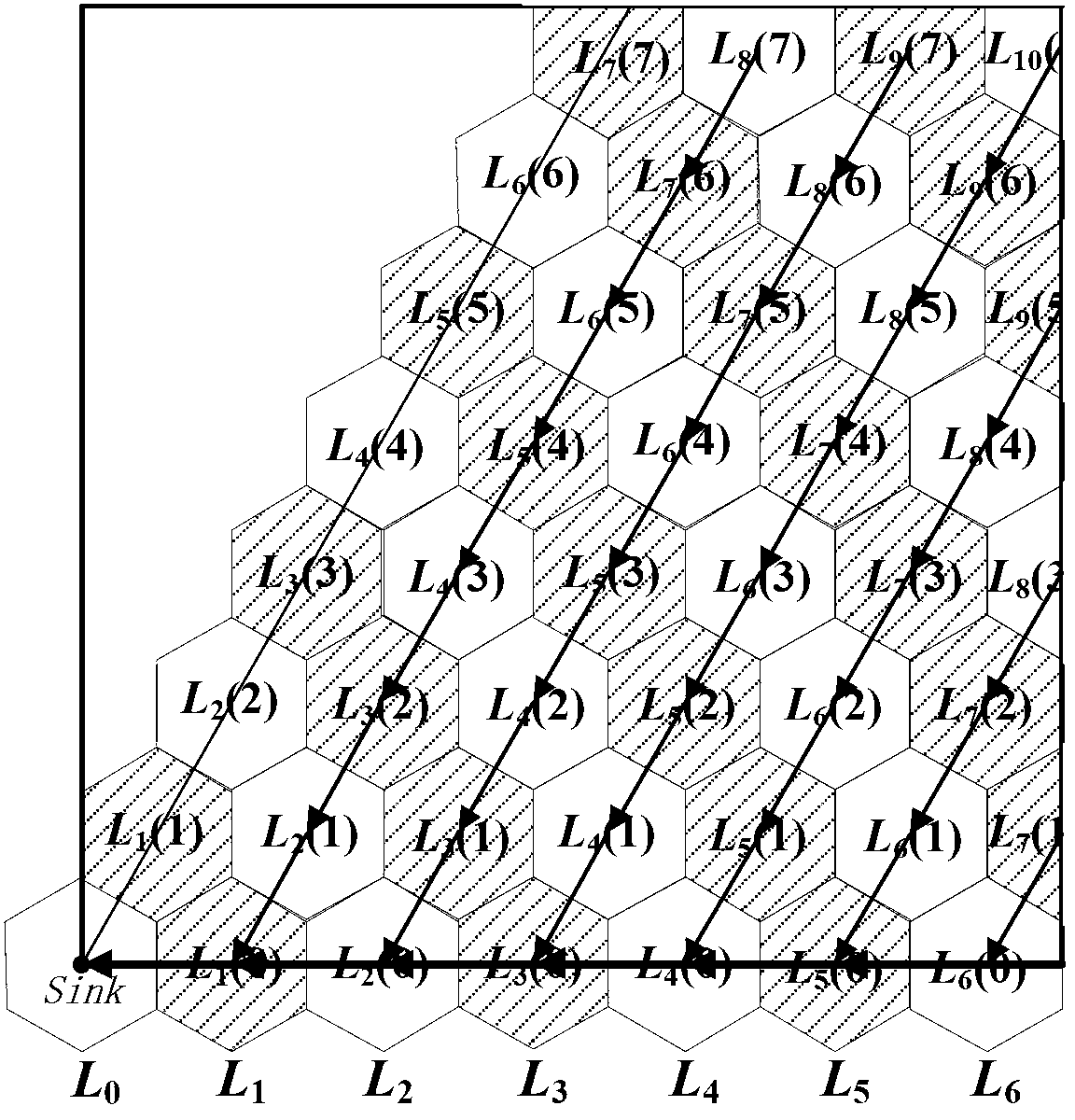
Wireless sensor network clustering routing method based on hexagonal regional division
InactiveCN103281741AShorten initialization timeExtend the life cycleHigh level techniquesWireless communicationMulti hop relayHigh energy
The invention discloses a wireless sensor network clustering routing method based on hexagonal regional division. The method comprises the following steps that six line segments (base lines) from a Sink node of a sensing area center divide a sensing area into six sector areas, wherein the included angle between every two adjacent base lines is 60 degrees; the sensing area is densely paved by hexagonal grids, a sensing node acquires longitude and latitude information by sensing self position information and calculates the distance between the position thereof and the closest base line, so that whether the hexagonal area where the sensing node is located is on the base line or not is judged, and if the hexagonal area is on the base line, after a clustering head is selected, the node that is selected to be the clustering head is changed into a gathering point; clustering head selection and data are transmitted by a multi-hop relay between the clustering head and the gathering point; the flow of the wireless sensing network from start to data acquisition is divided into a clustering head selecting and intra-cluster single-hop transmission process, and inter-cluster routing between the clustering head and the gathering point. The problem of too high energy consumption caused by too long transmission distance between clustering heads is solved, and the energy consumption during data acquisition of the network is greatly reduced.
Owner:SOUTHEAST UNIV
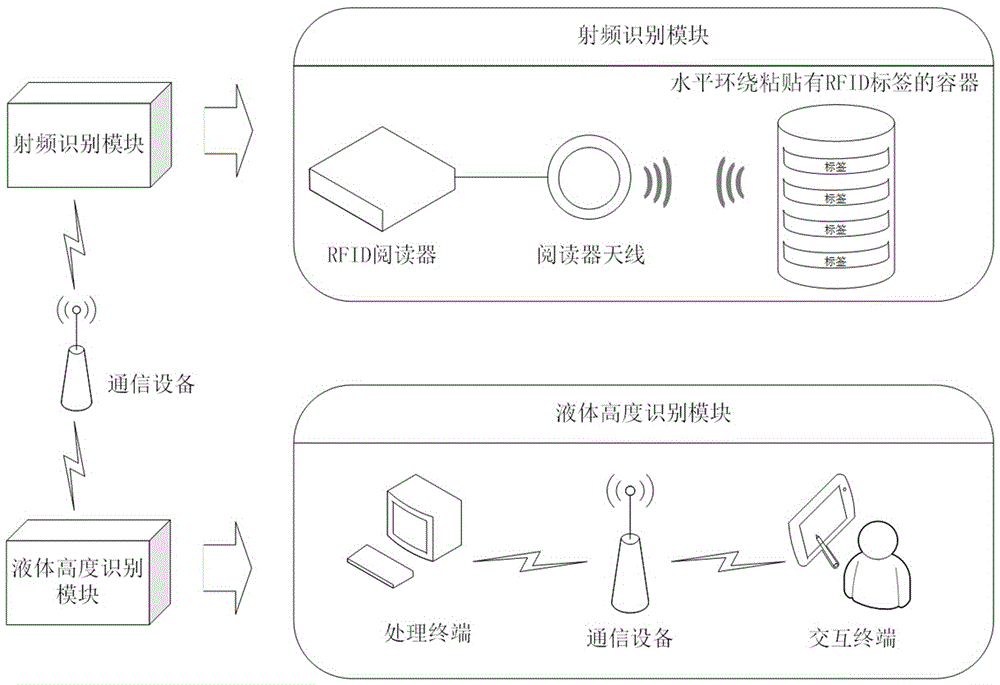
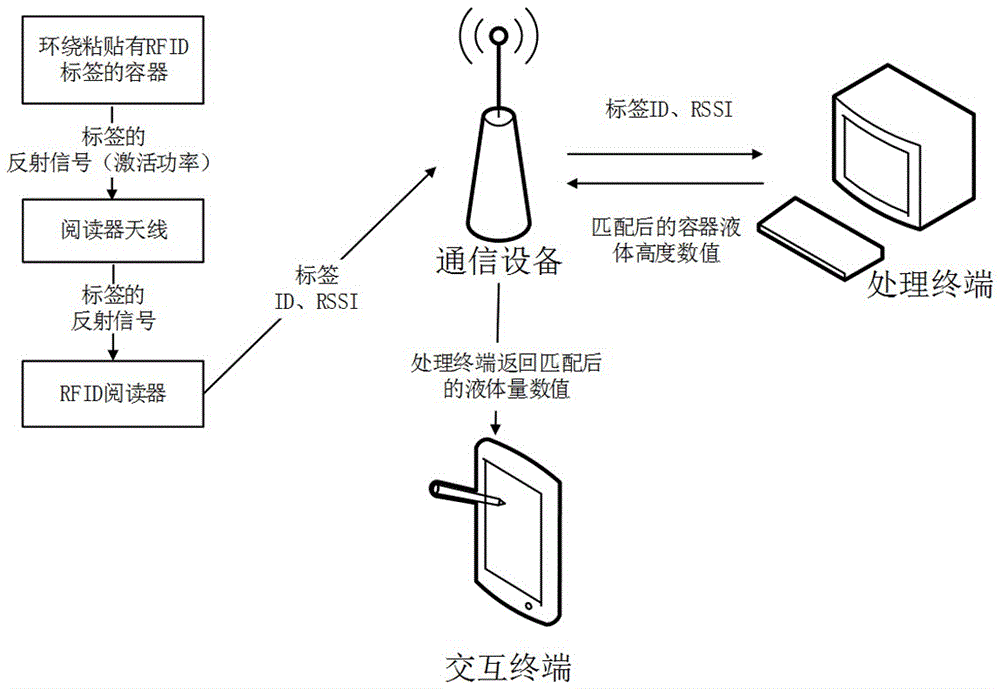
Container liquid height detection system based on radio frequency identification (RFID) technique and working method thereof
InactiveCN106382969ALow costEasy to deployCo-operative working arrangementsLevel indicators by physical variable measurementRadio frequencyLiquid height
The invention discloses a container liquid height detection system based on a radio frequency identification (RFID) technique and a working method thereof. The system mainly comprises a nonmetal container adhered with RFID tags in a surrounding manner, an RFID reader, a reader antenna, a processing terminal, an interaction terminal and communication equipment. According to the working method, the RFID reader and the reader antenna are connected, a common container is placed in a space and is adhered with a plurality of the RFID tags in a surrounding manner, the reader reads tag information on the container and simultaneously transmits the tag information to the processing terminal through the communication equipment, the processing terminal processes data acquired by a radio frequency identification module to obtain liquid height of the container and interacts with the interaction terminal through the communication equipment, and a user can detect the liquid height of the container in real time by virtue of the interaction terminal. The system and the method can adapt to complex environments and have the advantages that the operation is simple, the sensing precision is high, the identification speed is high, and the cost is low.
Owner:NANJING UNIV
Application navigation control method of intelligent television
InactiveCN103402132AComply with the operation modeIn line with the habitSelective content distributionHome pageControl selection
The invention discloses an application navigation control method of an intelligent television. A home page type application navigation interface commonly used at present is cancelled, and a menu type navigation interface consisting of two rows of vertical menus is adopted, wherein a category icon menu and an application icon menu corresponding to the present category are respectively placed in the menu type navigation interface, and a user can conveniently select required application service without multi-page operation or page turning operation by using a category button and an application button specific on a remote controller to respectively control and select category menu focus and application menu focus in the navigation interface, so that the navigation of the intelligent television has obvious advantages of intuitive arrangement, no invalid operation, quick application switching and the like, and the number of times of operation is reduced.
Owner:FOSHAN YUNLIAN TECH
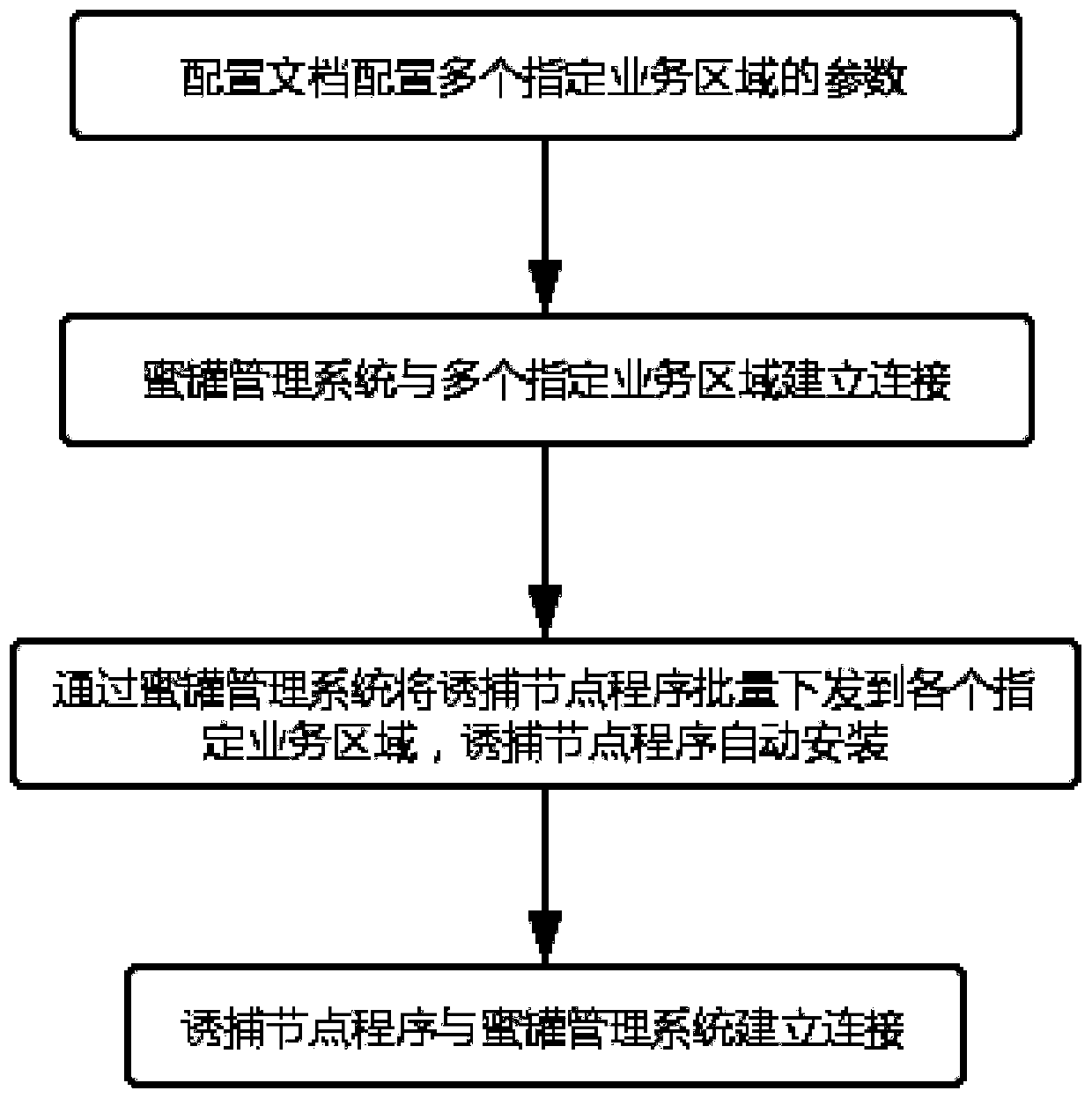
Honey pot deployment method
InactiveCN111431891ARapid deploymentAchieve connectionTransmissionInformation transmissionNode deployment
The invention discloses a honeypot deployment method, and relates to the technical field of digital information transmission. The method comprises the following steps: S1, configuring parameters of aplurality of specified service areas for a configuration document; S2, establishing connection between a honeypot management system and the plurality of specified service areas; S3, issuing the trapping node programs to all the designated service areas in batches through the honeypot management system, and automatically installing the trapping node programs; and S4, establishing connection betweenthe trapping node program and the honeypot management system. According to the method, the trapping node program is deployed in the designated service area, the trapping node program can be rapidly connected with the honeypot system, the honeypot is rapidly and automatically deployed, and the manual node deployment link and the honeypot deployment link are reduced.
Owner:广州锦行网络科技有限公司
Application server provisioning system and method based on disk image profile
InactiveUS8612393B2Fast and easy provisioning processReduce consumptionDigital data processing detailsSpecial data processing applicationsApplication serverDistribution system
Owner:DOORDASH INC
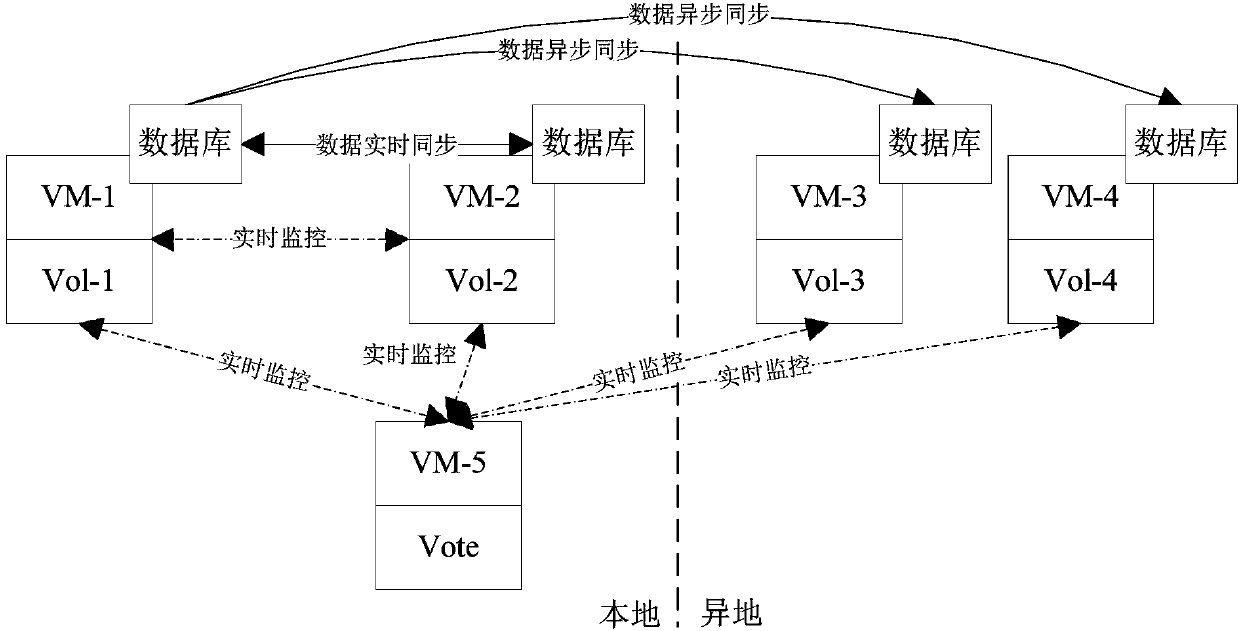
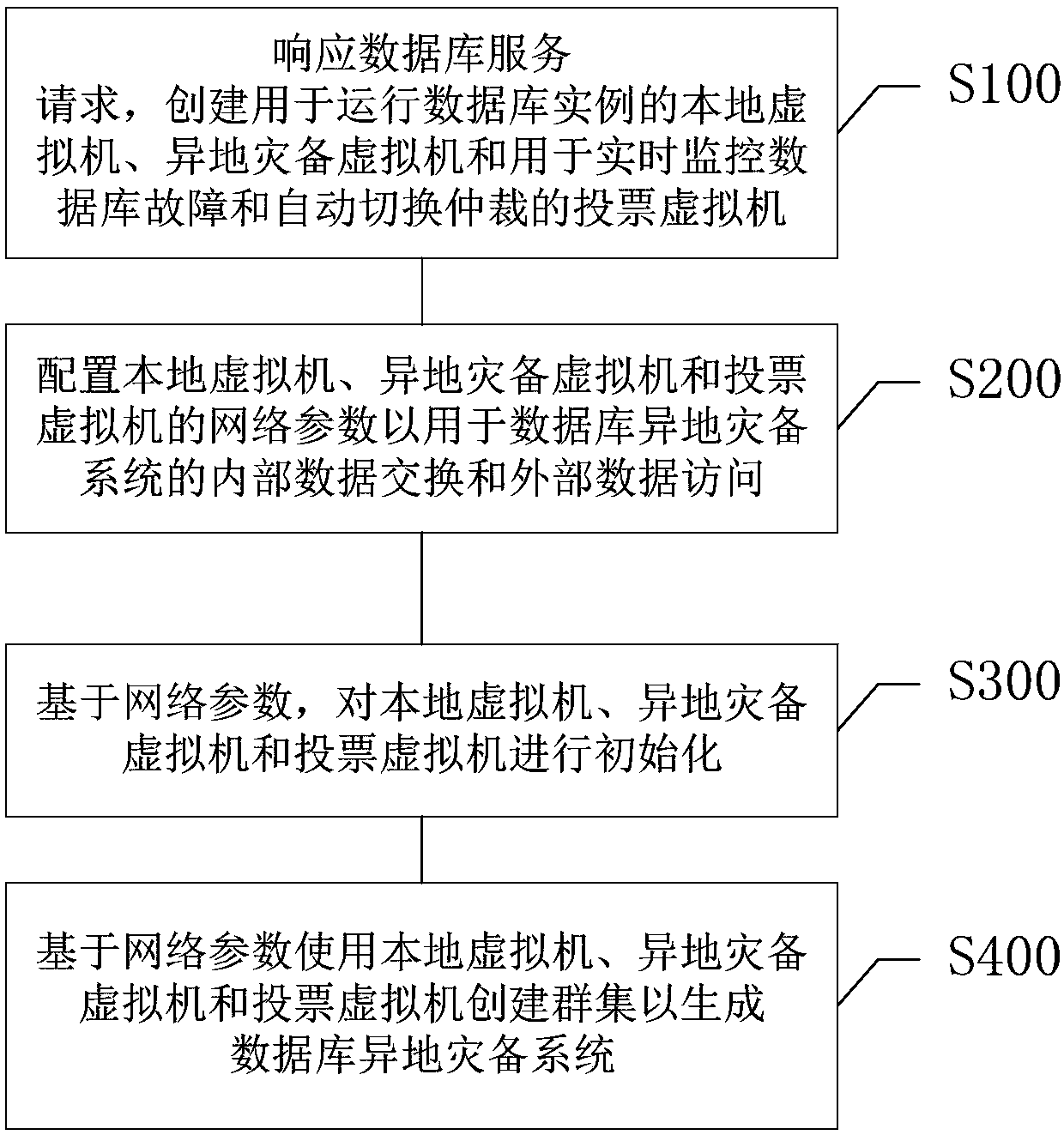
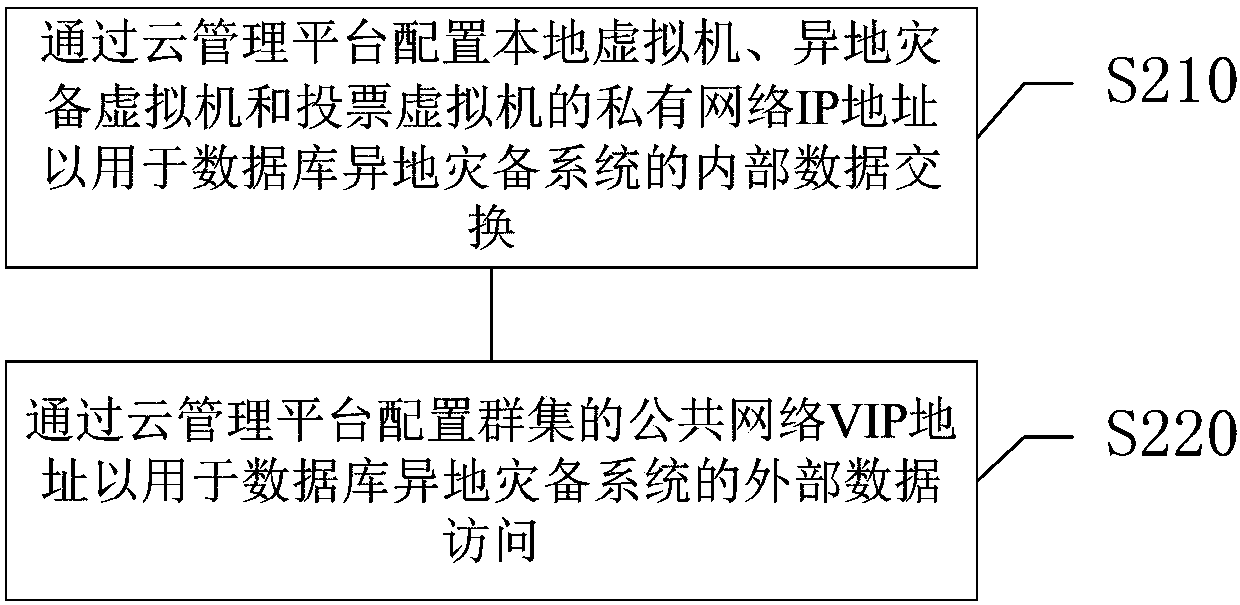
Database remote disaster recovery system and deployment method and deployment device thereof
ActiveCN109947591AImprove resource delivery efficiencySimplify the deployment processSoftware simulation/interpretation/emulationRedundant operation error correctionResource utilizationHigh availability
The invention relates to a database remote disaster recovery system and a deployment method and device thereof, a medium and electronic equipment. The deployment method of the database remote disasterrecovery system comprises the following steps: responding to a database service request, and creating a local virtual machine, a remote disaster recovery virtual machine and a voting virtual machine;Configuring network parameters of the local virtual machine, the remote disaster backup virtual machine and the voting virtual machine; Based on the network parameters, initializing a local virtual machine, a remote disaster backup virtual machine and a voting virtual machine; And creating a cluster by using the local virtual machine, the remote disaster recovery virtual machine and the voting virtual machine based on the network parameters to generate a database remote disaster recovery system. According to the method, a background program generates a whole set of database remote disaster recovery high-availability architecture through the cloud management platform, manual intervention is not needed, the database resource delivery efficiency is remarkably improved, the labor cost is saved, meanwhile, more businesses can be supported by the physical machine, and the resource utilization rate of storage and the like is higher.
Owner:TENCENT CLOUD COMPUTING BEIJING CO LTD
VPN network client for mobile device having fast reconnect
ActiveCN102316092AEasy maintenanceSimplify the management processConnection managementData switching networksUnique identifierControl channel
The invention relates to a VPN network client for mobile device having fast reconnect. The VPN network client establishes a secure VPN connection with a remote VPN security device. The VPN network client establishes a secure control channel with the secure VPN gateway and, upon a successful authentication, receives a session cookie with a unique identifier. In the event communication with the secure VPN gateway is subsequently temporarily lost, the VPN network client performs a fast reconnect without requiring re-authentication of the cellular mobile device by communicating the session cookie to the secure VPN gateway. Prior to performing the fast reconnect, the VPN network client identifies a set of transport mechanisms currently available to the cellular mobile device and, when only a cellular network is available and not a wireless packet-based connection, the VPN network client defers the fast reconnect until application-layer data is received from a user application and is ready to be sent to the remote VPN security device via the VPN connection.
Owner:PULSE SECURE
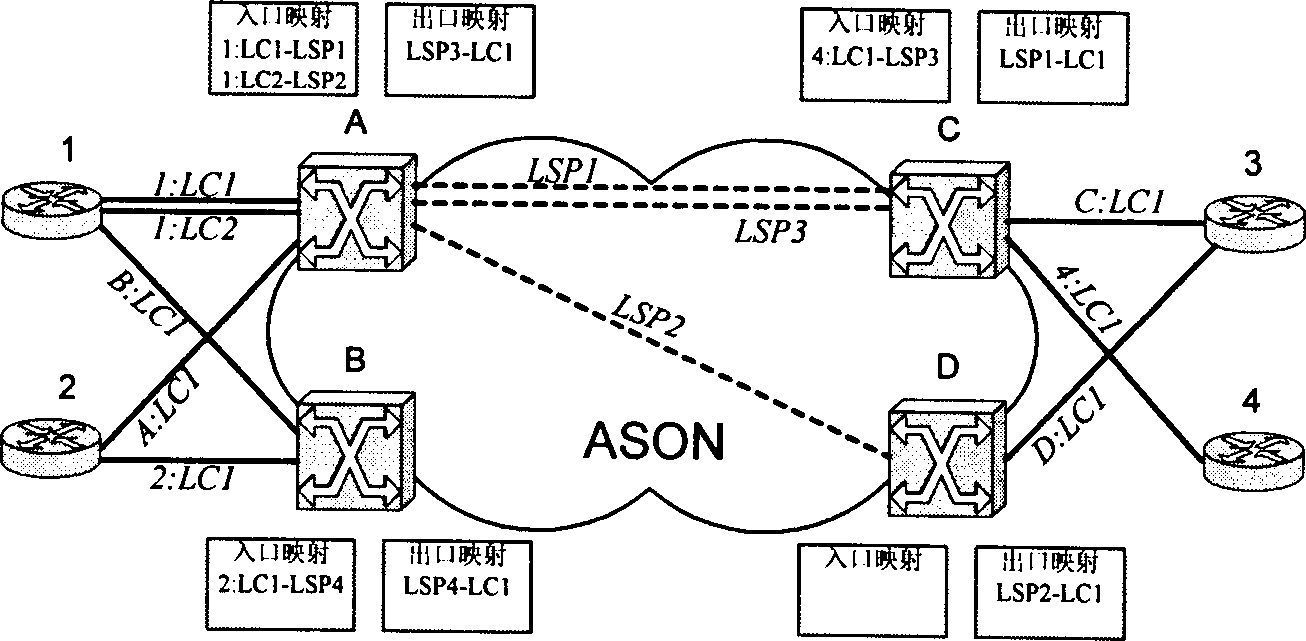
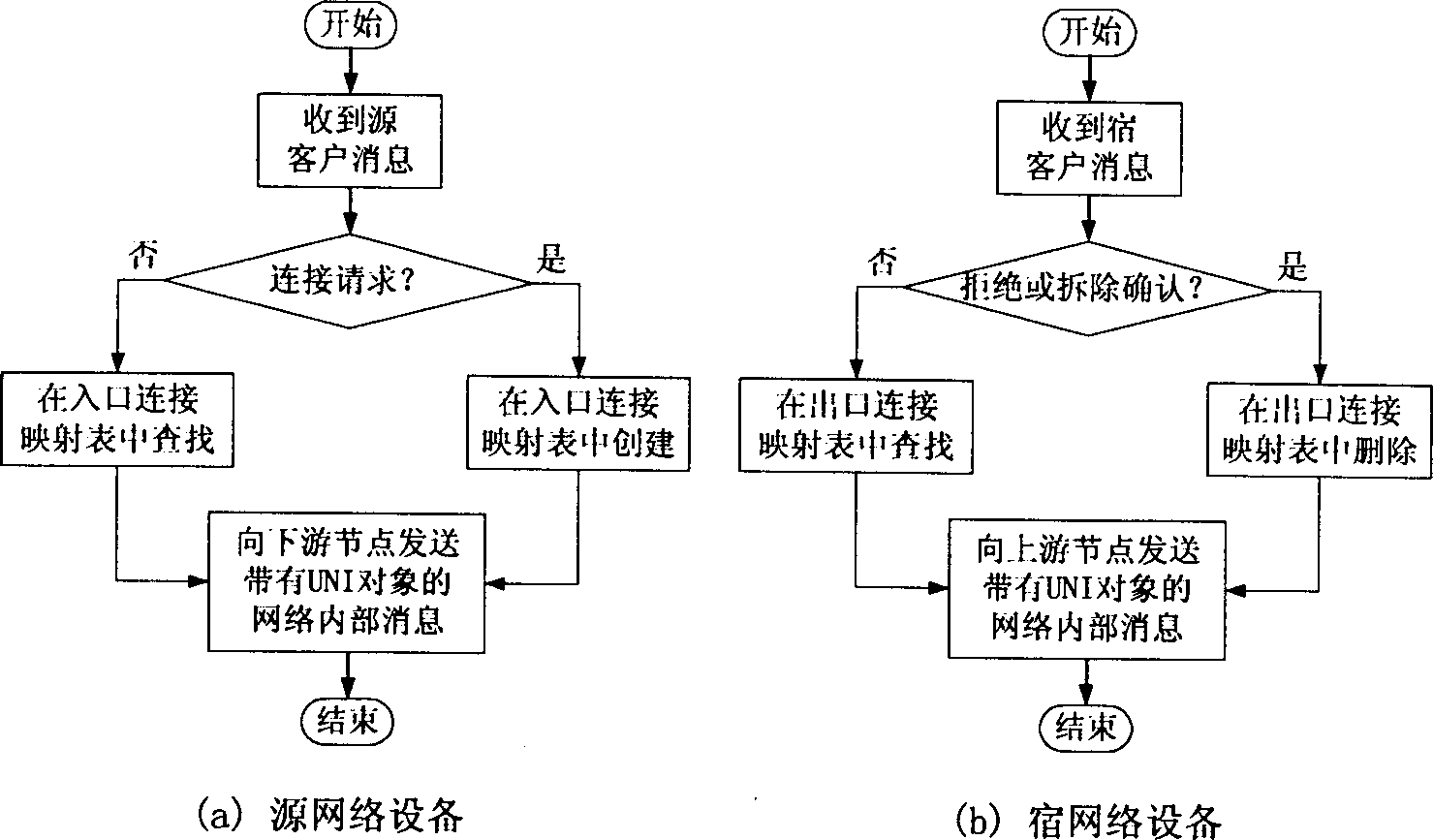
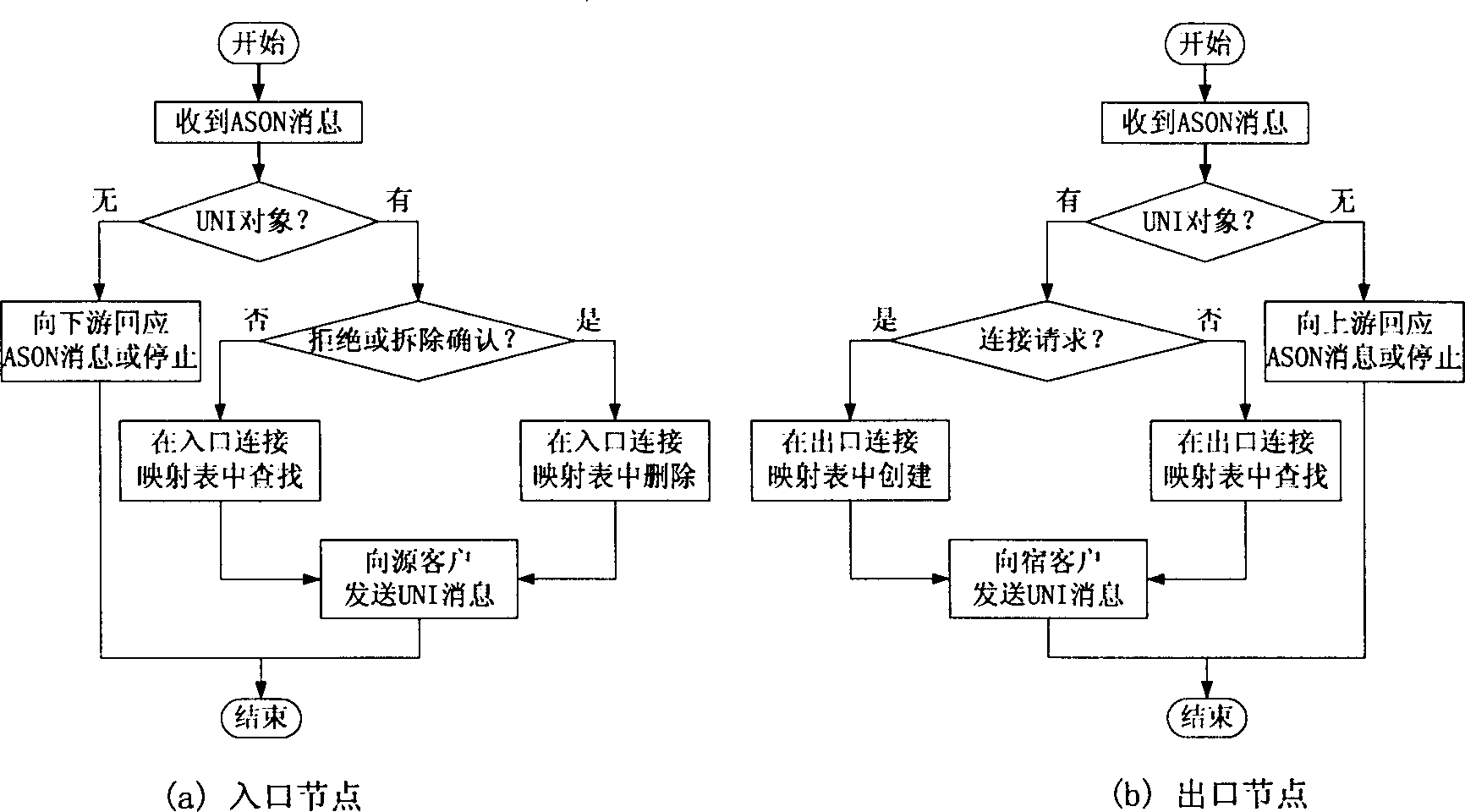
Signaling cascading method of exchange connection in automatic exchange optic/transport network
InactiveCN1431833AImprove interoperabilitySimplified implementationMultiplex system selection arrangementsElectromagnetic transmissionInteroperabilityEdge node
Each network edge node maintains the two tablets of the connection map: the entrance and exit. With being received the interface message of the user network sent by the client device, the relation between the corresponding network internal connection and the local connection of the user network interface are created, deleted and looked up on the connection map. The interface message of the user network is turned to 'private object', which is sent out together with the network internal signaling. With the signaling message with the interface object of the corresponding user network being received, the remote edge nodes create, delete or look up corresponding local connection of the user network interface, which is sent to client devices.
Owner:SHANGHAI JIAO TONG UNIV
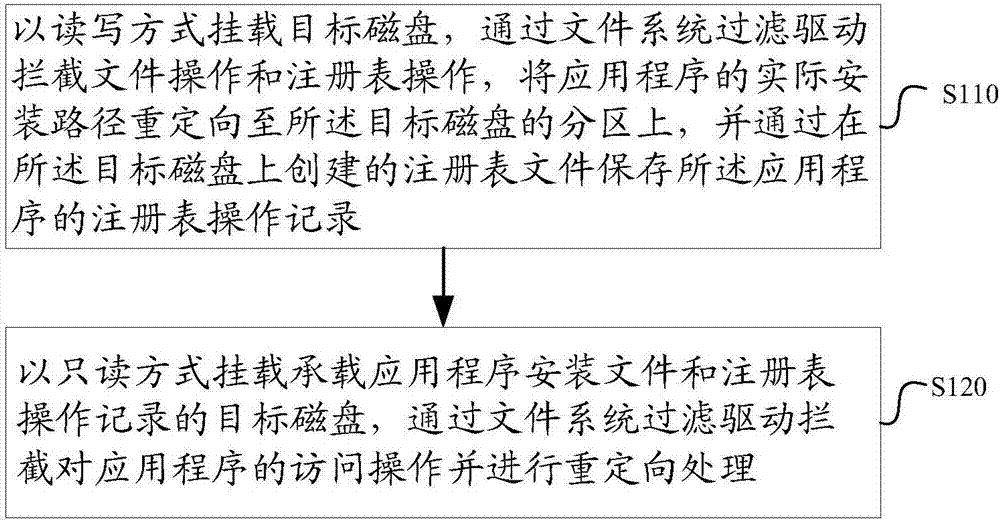
Method and device to deploy application software and virtual machine
ActiveCN107992355ASimplify the deployment processImprove deployment efficiencySoftware simulation/interpretation/emulationRedundant operation error correctionApplication softwareVirtual machine
The patent discloses a method and device to deploy application software and a virtual machine. The method comprises: mounting a target disk in reading-writing manner, intercepting file operation and registry operation by a file system filter driver, re-directing an actual installation path of an application to a partition of the target disk, and saving registry operation record of the applicationthrough a registry file created on the target disk; mounting the target disk that bears an application installation file and the registry operation record in read-only manner, intercepting access operation for the application through the file system filter driver, and performing re-directing. The method and device and the virtual machine according to the technical scheme can provide simplified application deployment process and improved deployment efficiency.
Owner:ZTE CORP
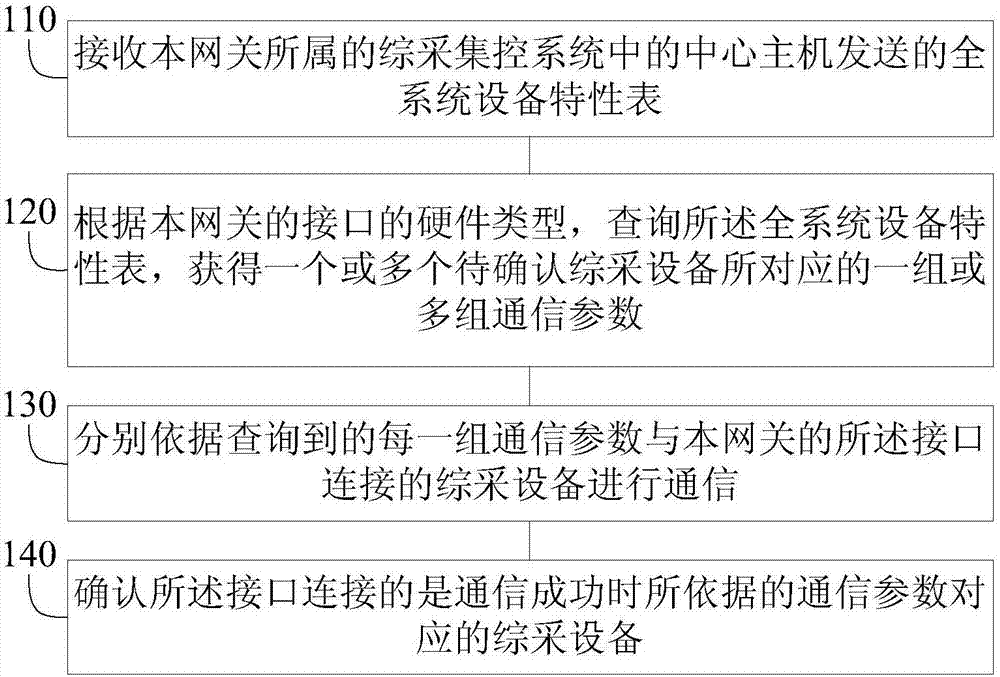
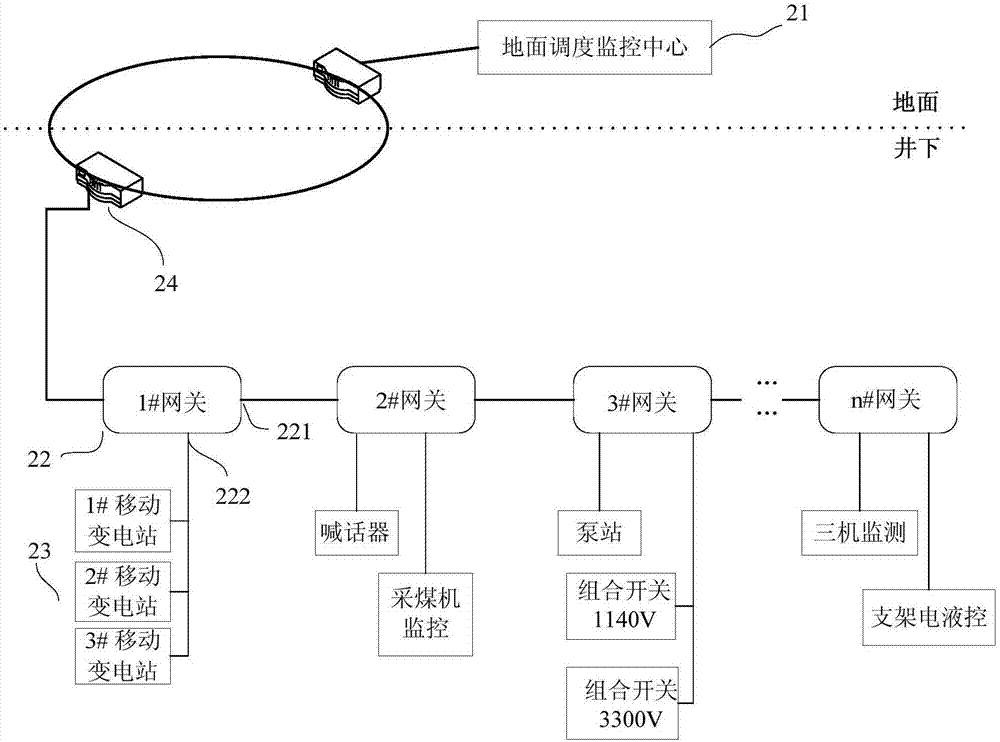
Recognition method, device and system for fully-mechanized coal mining equipment, gateway, and storage medium
ActiveCN107959620ASimplify deployment and maintenanceSimplify the deployment processData switching detailsNetwork connectionsCoal miningIdentification device
The invention discloses a recognition method for fully-mechanized coal mining equipment, and the method comprises the steps: receiving a complete system equipment property list sent by a central hostin a fully-mechanized coal mining centralized control system where a gateway belongs; querying the complete system equipment property list according to the hardware type of an interface of the gateway, and obtaining one or more groups of communication parameters corresponding to one or more pieces of to-be-confirmed fully-mechanized coal mining equipment; carrying out the communication with the fully-mechanized coal mining equipment connected with the interface of the gateway according to each group of queried communication parameters; and confirming that the fully-mechanized coal mining equipment connected with the interface is corresponding to the communication parameters during the successful communication. Correspondingly, the invention also discloses a recognition device for the fully-mechanized coal mining equipment, the gateway, and a storage medium. According to the embodiment of the invention, the method achieves a purpose that the gateway achieves the automatic recognition ofthe connected fully-mechanized coal mining equipment, and simplifies the deployment and maintenance operation of the onsite fully-mechanized coal mining equipment.
Owner:HITACHI BUILDING TECH GUANGZHOU CO LTD
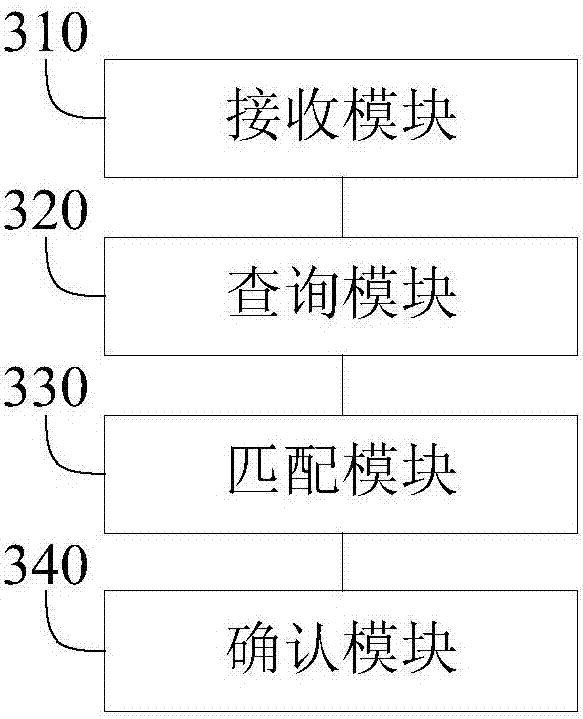
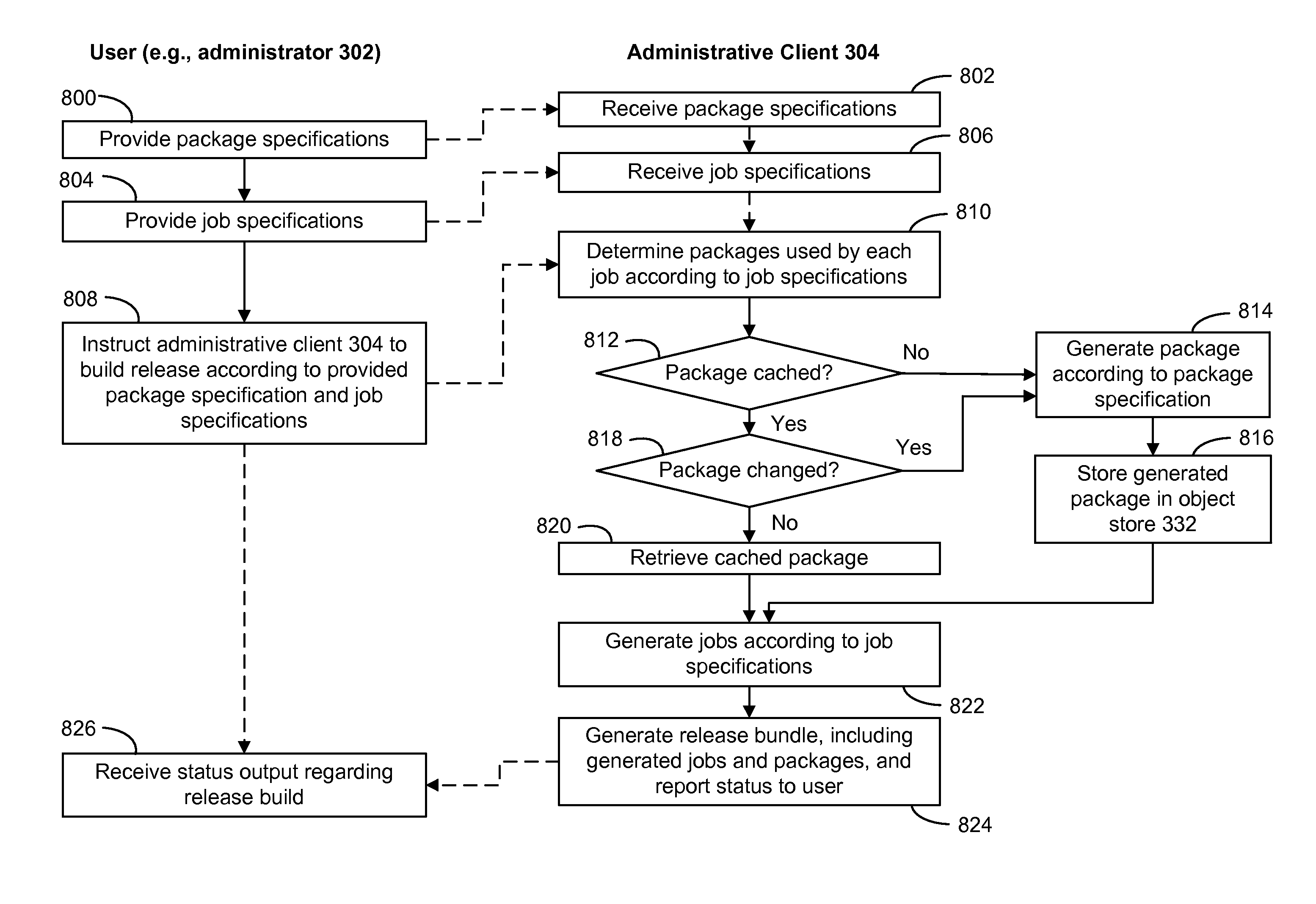
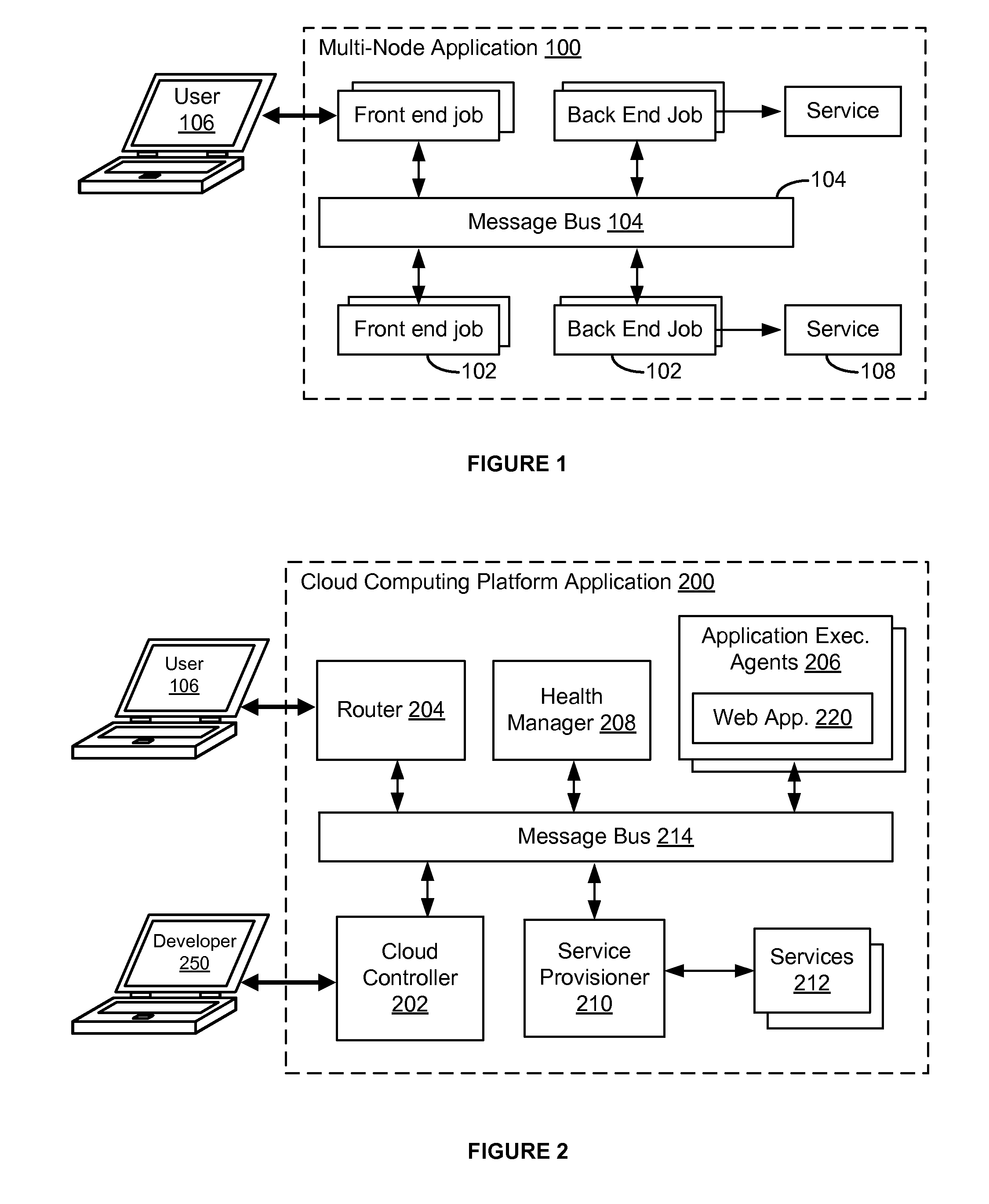
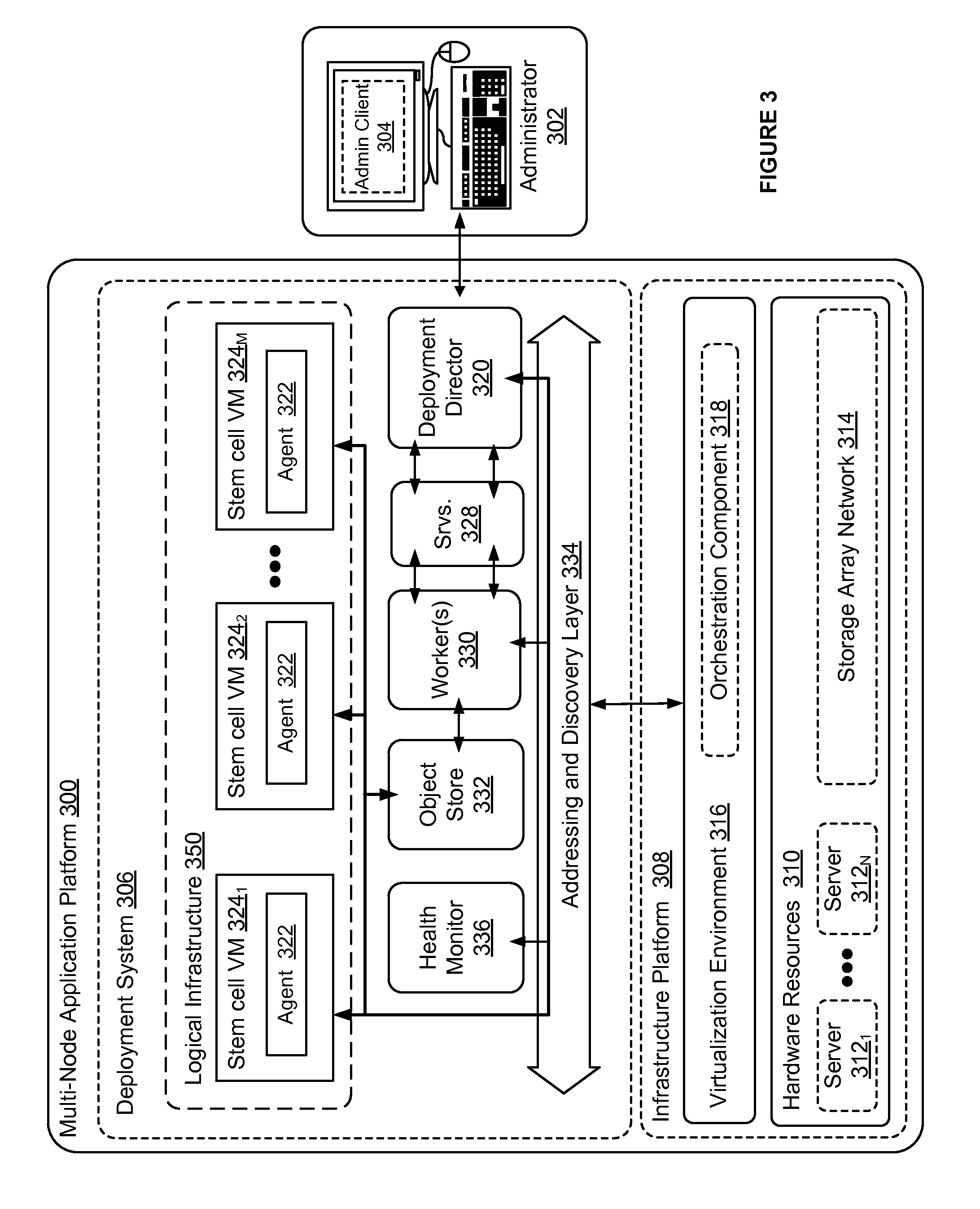
Release management system for a multi-node application
ActiveUS9043767B2Simplify the deployment processResource allocationVersion controlRelease managementApplication software
A deployment system provides the ability to deploy a multi-node distributed application, such as a cloud computing platform application that has a plurality of interconnected nodes performing specialized jobs. The deployment system includes a release management system that builds and manages versioned releases of application services and / or software modules that are executed by the plurality of nodes of the cloud computing platform application. The release management system utilizes specification files to define a jobs and application packages and configurations needed to perform the jobs. The jobs and application packages are assembled into a self-contained release bundle that may be provided to the deployment system. The deployment system unwraps the release bundle and provides each job to deployment agents executing on VMs. The deployment agents apply the jobs to their respective VM (e.g., launching applications), thereby deploying the cloud computing platform application.
Owner:GOPIVOTAL
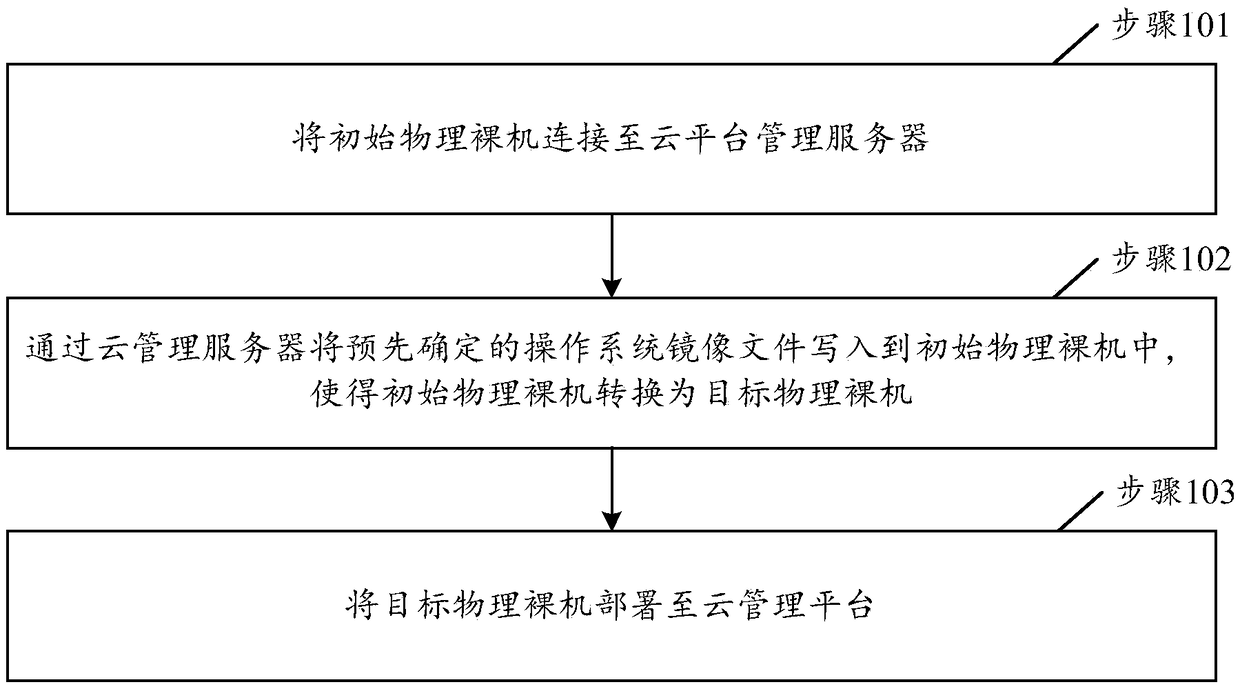
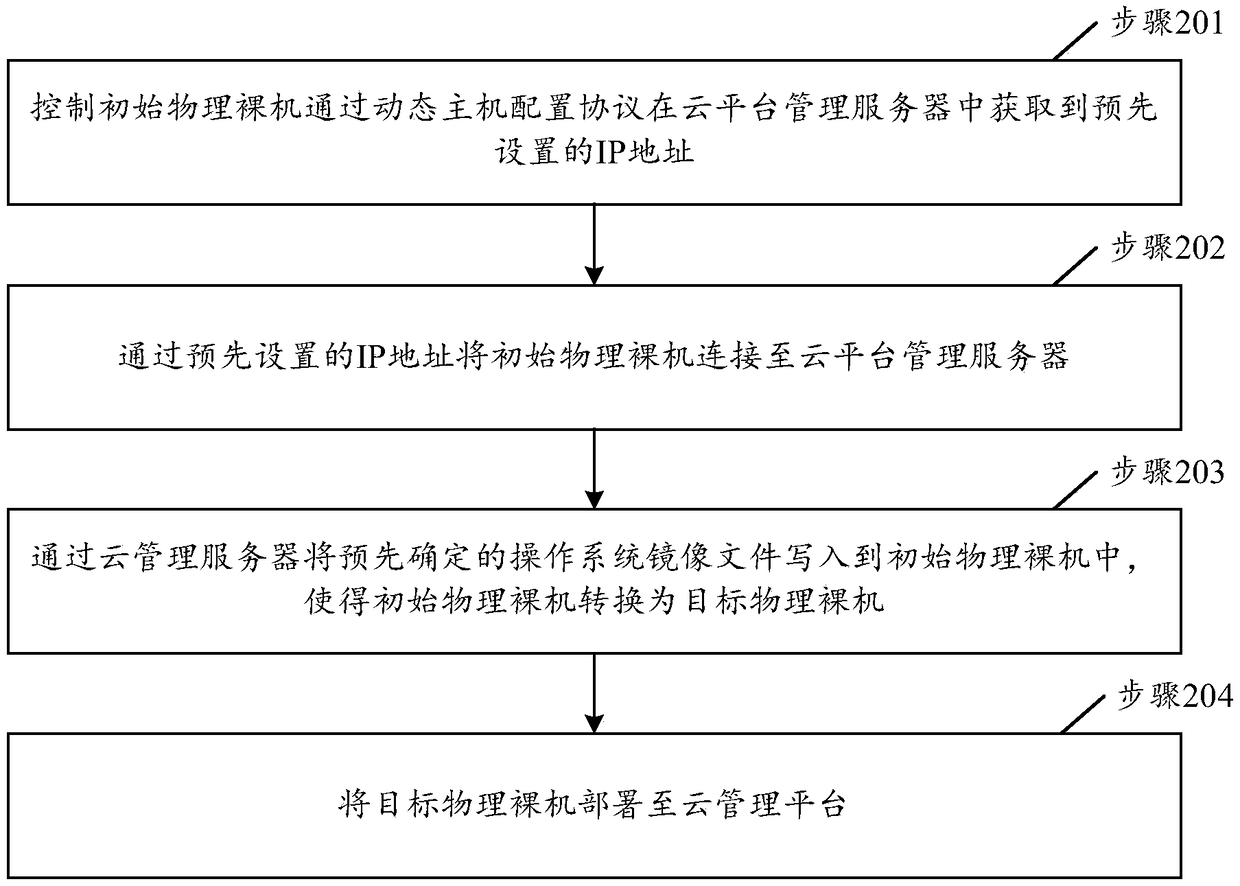
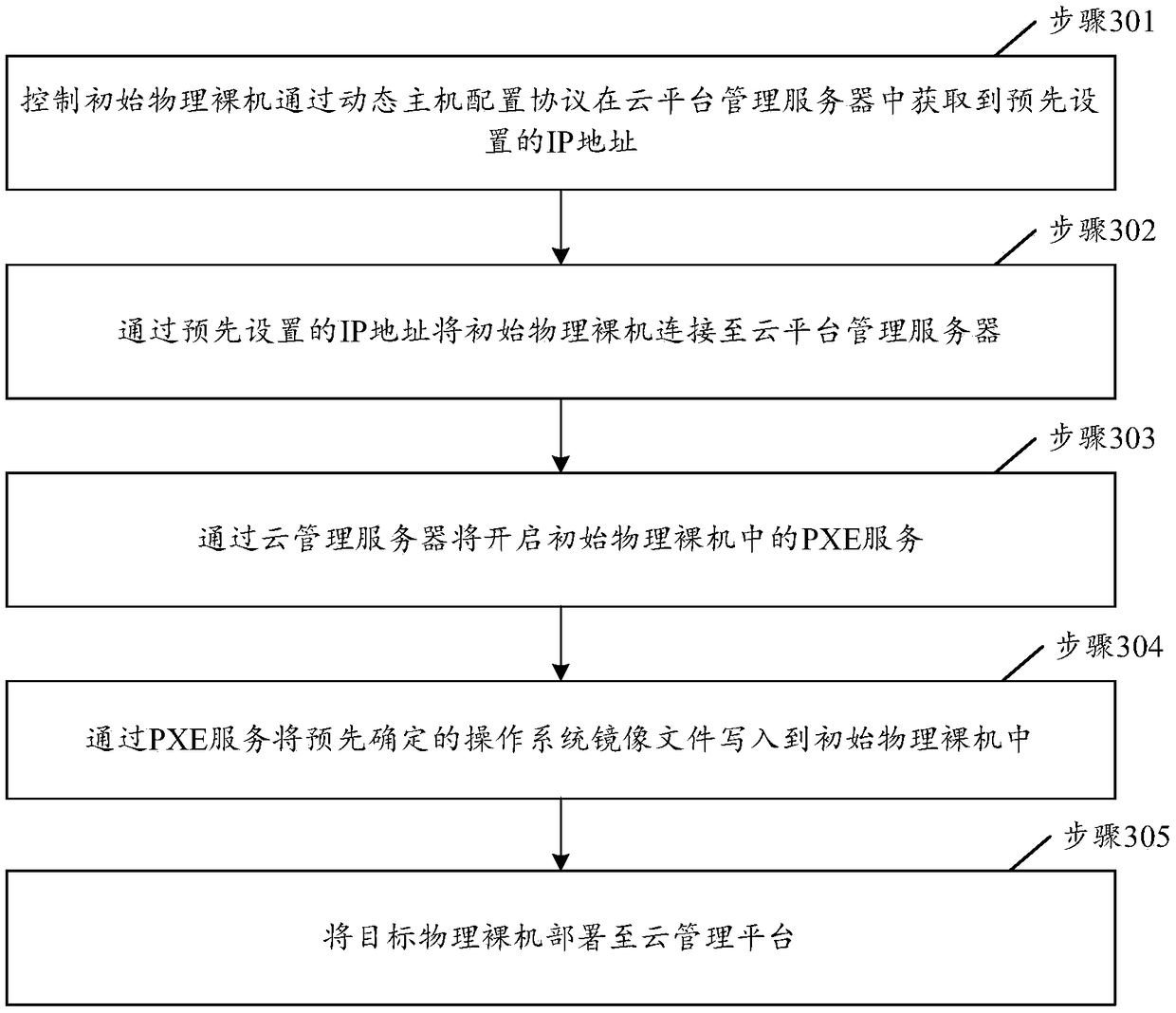
Deployment method and device of physical bare machine, electronic device and storage medium of physical bare machine
InactiveCN109388475ASimplify the deployment processImprove deployment efficiencySoftware simulation/interpretation/emulationComputer hardwareOperational system
The invention discloses a deployment method and device of a physical bare machine, an electronic device and a storage medium. The method comprises the following steps: connecting an initial physical bare machine to a cloud platform management server; writing a predetermined operating system image file into the initial physical bare metal through the cloud management server, so that the initial physical bare metal is converted into a target physical bare metal, wherein the initial physical bare machine is a physical bare machine that is not written into the operating system image file; the target physical bare machine is a physical bare machine which has been written into the operating system image file; the target physical bare metal is deployed to a cloud management platform. The deployment process of the physical bare metal can be simplified, and the deployment efficiency of the physical bare metal can be improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
5G wireless access type indoor distribution system
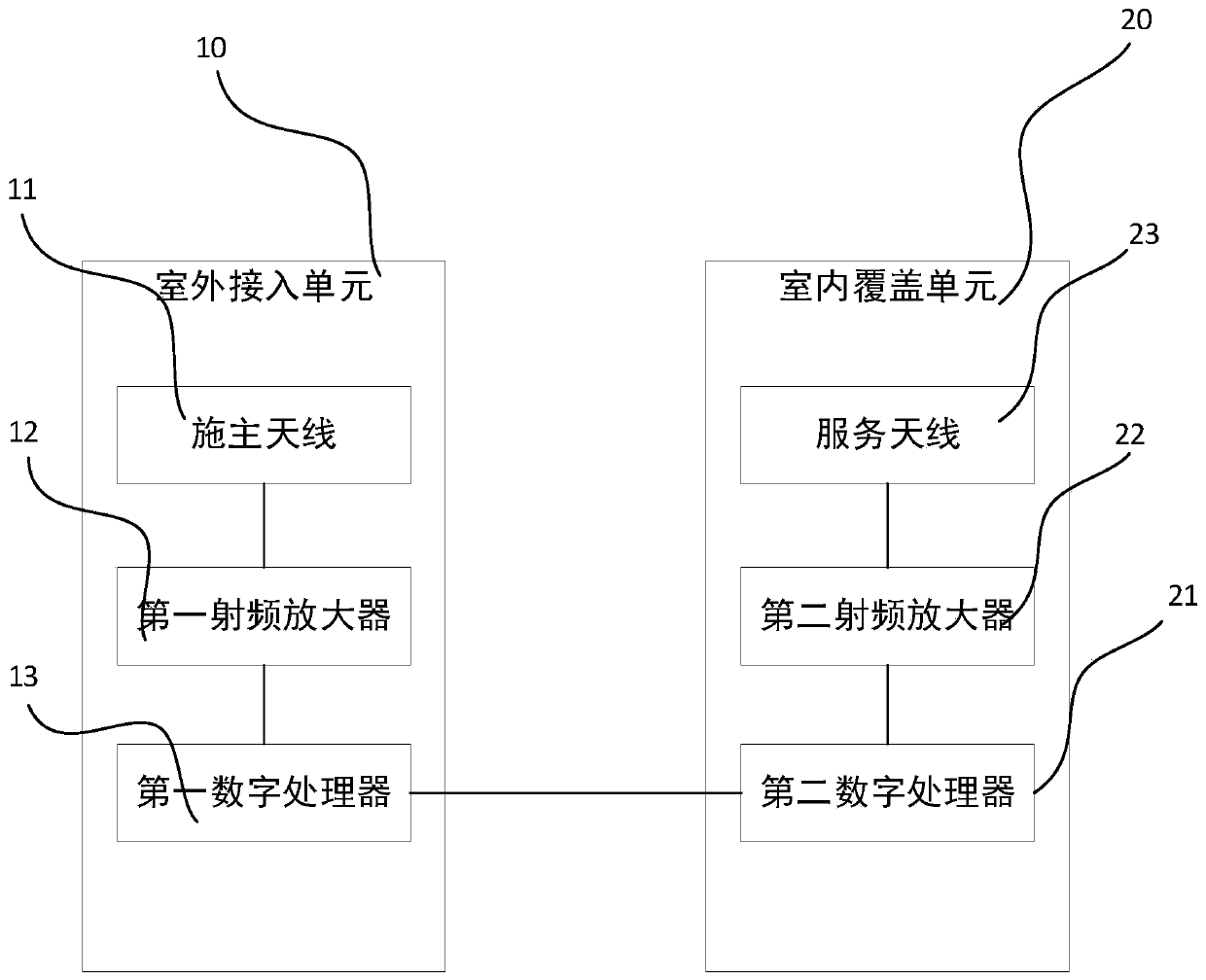
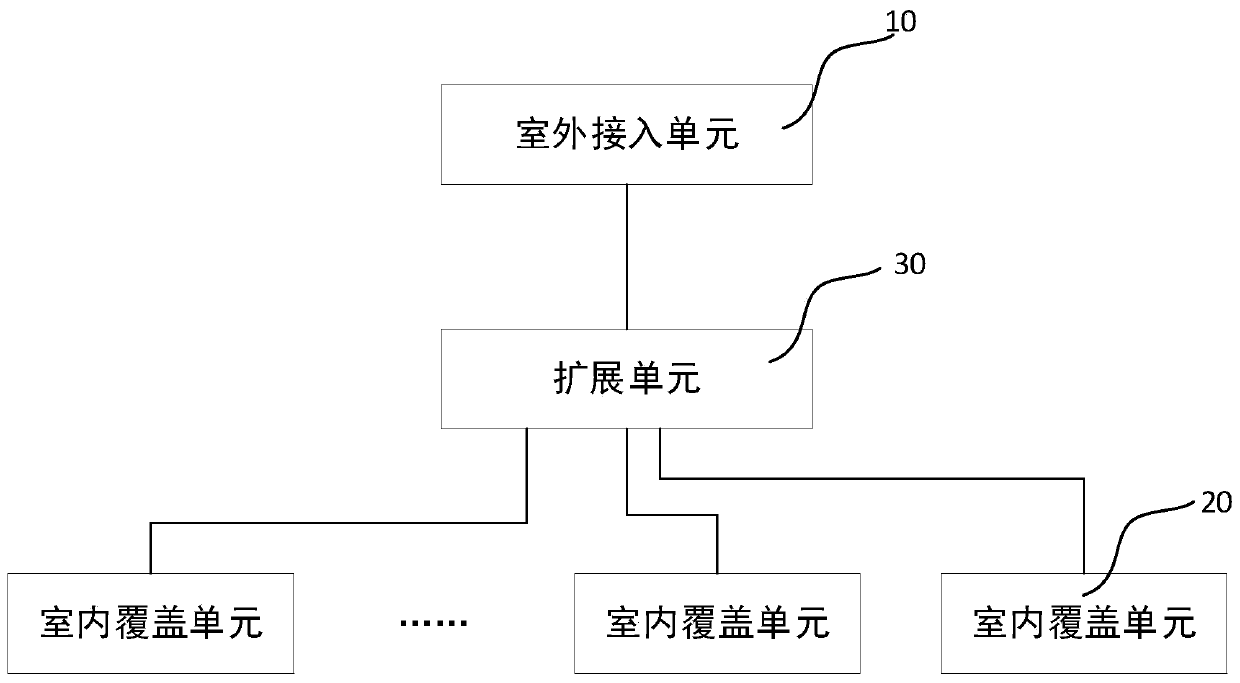
PendingCN110475254ALow costImprove deployment efficiencyNetwork planningAudio power amplifierDistribution system
The invention discloses a 5G wireless access type indoor distribution system. An outdoor access unit comprises a donor antenna, a first radio frequency amplifier and a first digital processor which are connected in sequence; wherein the donor antenna is used for establishing wireless connection between the outdoor access unit and a 5G base station, the first radio frequency amplifier is used for amplifying a radio frequency signal sent by the donor antenna or the first digital processor, and the first digital processor is connected with the indoor coverage unit; the indoor coverage unit comprises a second digital processor, a second radio frequency amplifier and a service antenna which are connected in sequence; the second digital processor is connected with the outdoor access unit, the second digital processor is used for converting signals, the second radio frequency amplifier is used for amplifying radio frequency signals, and the service antenna is used for establishing wireless connection between the indoor coverage unit and the indoor mobile terminal; thus, indoor signal coverage can be completed without deploying a 5G base station indoors, and the cost required by 5G indoorsignal deployment is greatly saved.
Owner:福建京奥通信技术有限公司
Positioning, deviation correcting and theft judging method of intelligent iron shoe
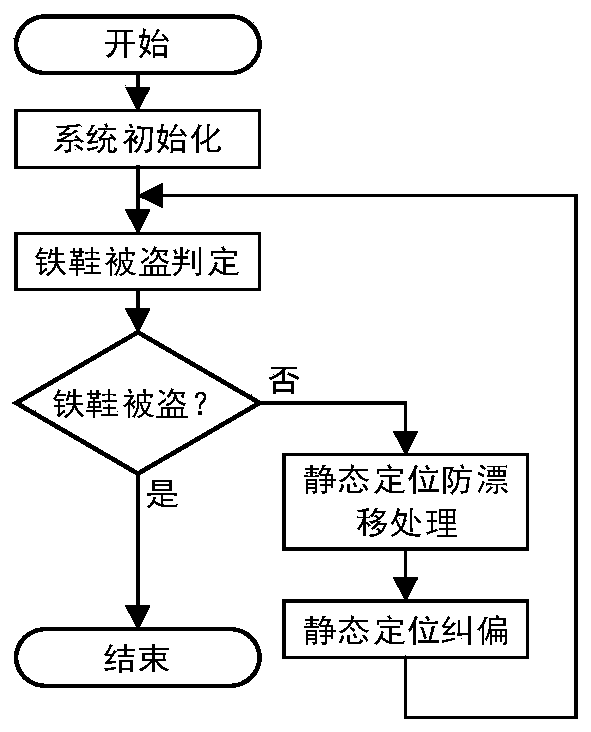
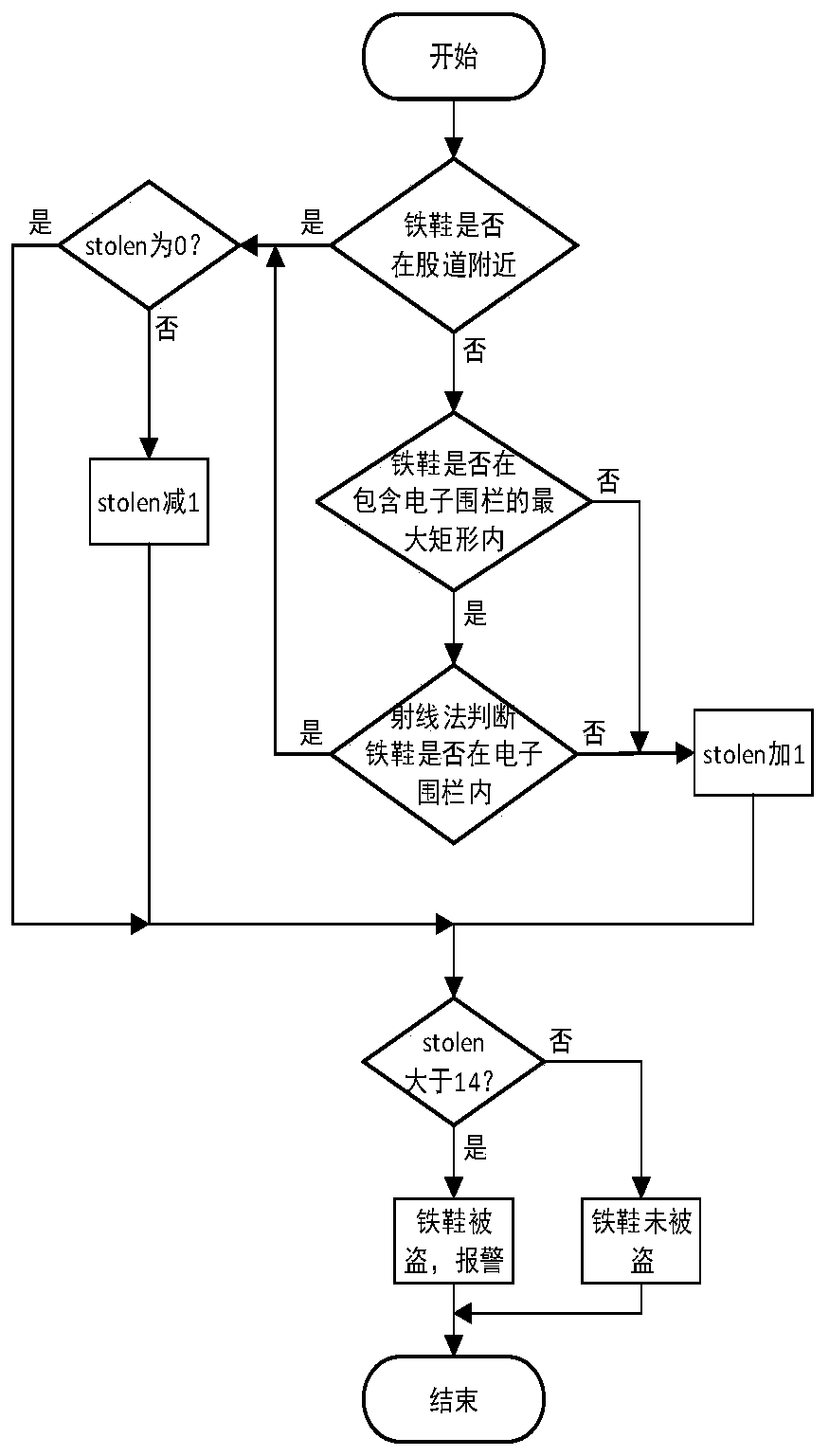
ActiveCN110406565AHigh positioning accuracyEasy to identifySatellite radio beaconingRailway signalling and safetyCorrection algorithmMetallurgy
The invention discloses a positioning, deviation correcting and theft judging method of an intelligent iron shoe. The positioning, deviation correcting and theft judging method comprises four steps ofsystem initialization, intelligent iron shoe theft judgment, intelligent iron shoe static positioning anti-drift treatment and intelligent iron shoe static positioning deviation correcting. Accordingto the intelligent iron shoe theft judgment algorithm, the intelligent iron shoe theft identification precision is improved layer by layer, the intelligent iron shoe theft state is judged quickly andaccurately, and the calculation amount of the intelligent iron shoe during theft judgment can be effectively reduced, so that the purpose of reducing energy consumption is achieved; the intelligent iron shoe static deviation correction algorithm maps the intelligent iron shoe positioning coordinates to the tracks on which the intelligent iron shoe is placed, so that the influence of GPS positioning errors on intelligent iron shoe state display is reduced. The positioning, deviation correcting and theft judging method of the intelligent iron shoe is suitable for judging the theft state of a railway station and correcting the deviation of the positioning information of the railway station after the intelligent iron shoe is applied to the railway station, which greatly improves the safety ofthe station and relieves the management pressure of personnel in the station.
Owner:南京富岛信息工程有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com