Honey pot deployment method
A honeypot and business technology, applied in the field of digital information transmission, can solve problems such as the inability to realize automatic port opening, achieve the effects of reducing manual deployment of nodes and honeypot deployment, improving log tracking, and simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
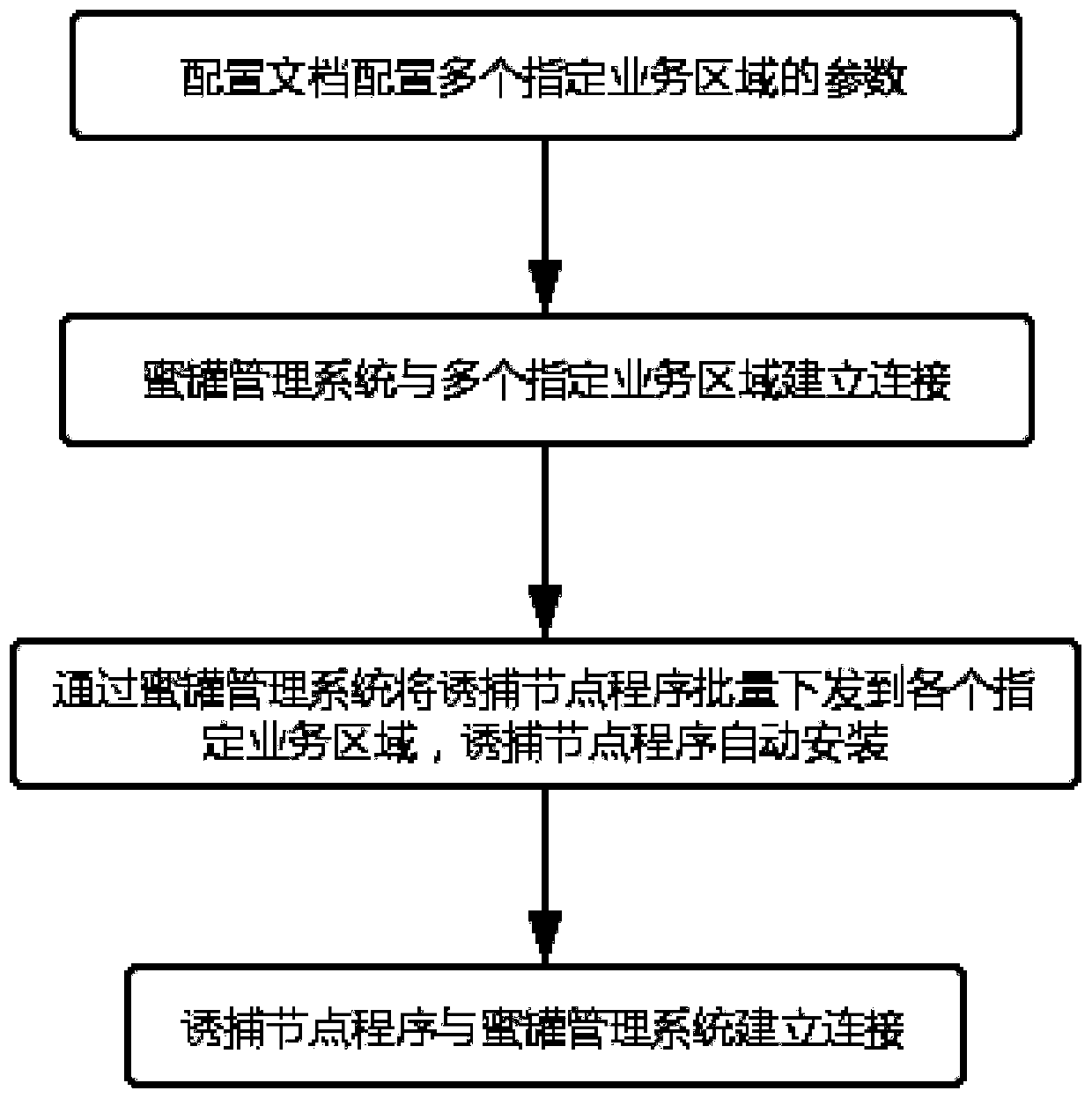
[0037] Such as figure 1 Shown is a honeypot deployment method, including the following steps:
[0038] S1. The configuration document configures parameters such as connection accounts, passwords, IP addresses and port numbers of multiple designated business areas, and classifies the designated business areas in the configuration document;
[0039] S2. The honeypot management system establishes connections with multiple designated business areas;
[0040] S3. The trapping node program is distributed to each designated business area in batches through the honeypot management system, and the trapping node program is automatically installed;
[0041] S4. The trapping node program establishes a connection with the honeypot management system;
[0042] S5. Open but not run all service application ports in multiple designated business areas;
[0043] Run the corresponding service application according to the behavior of the attacker, and close the ports of other service application...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com