Method of controlling network access and its system
A network access and control method technology, applied in the field of endpoint security access control, can solve problems such as access control of endpoints that cannot be accessed, and achieve the effects of reducing maintenance costs, ensuring identity legitimacy, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
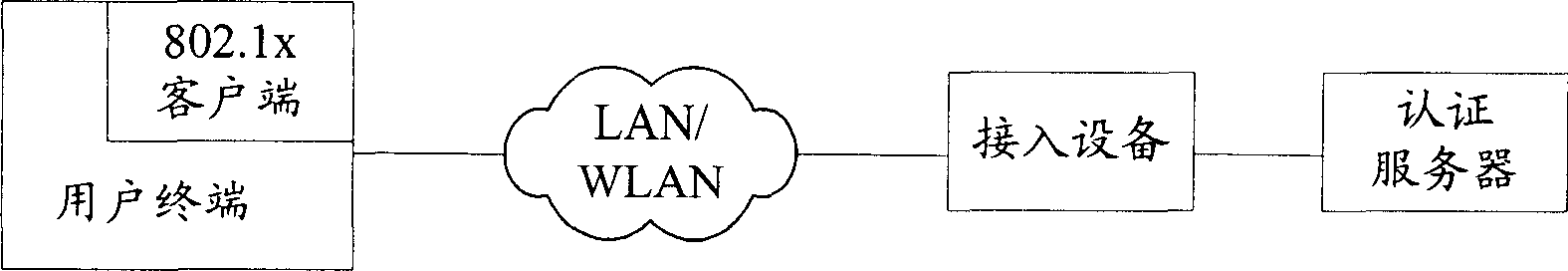
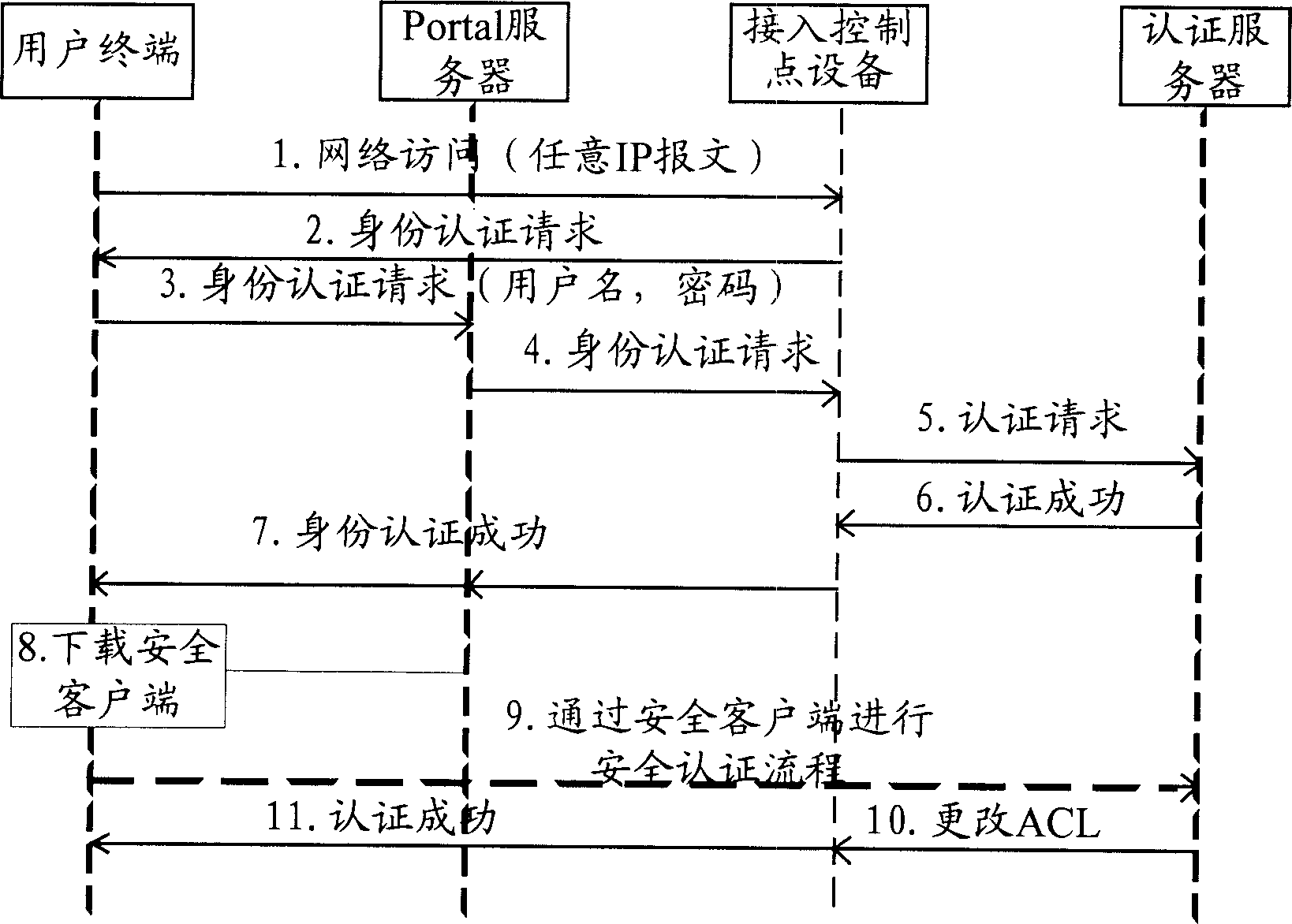
[0067] The core of the present invention is to integrate the advantages of traditional Portal / Web authentication and client authentication, and use the extended Portal protocol to perform mandatory user identity authentication for non-http / https protocol access under the Web authentication mode. For users who only access the Internet through Web authentication, control their access rights so that they can only access the isolated area of the user network, that is to say, only allow the user to access restricted network resources, such as domain name servers, patch servers, virus servers, etc.; Provide users with the download link of the security client through the web page; and check the security status of the user terminal through the security client. The user terminal performs operations such as virus database repair and patch installation; mandatory security authentication is performed for user non-http / https protocol access, so that users who pass the security authenticat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com