Patents
Literature
51 results about "Endpoint security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
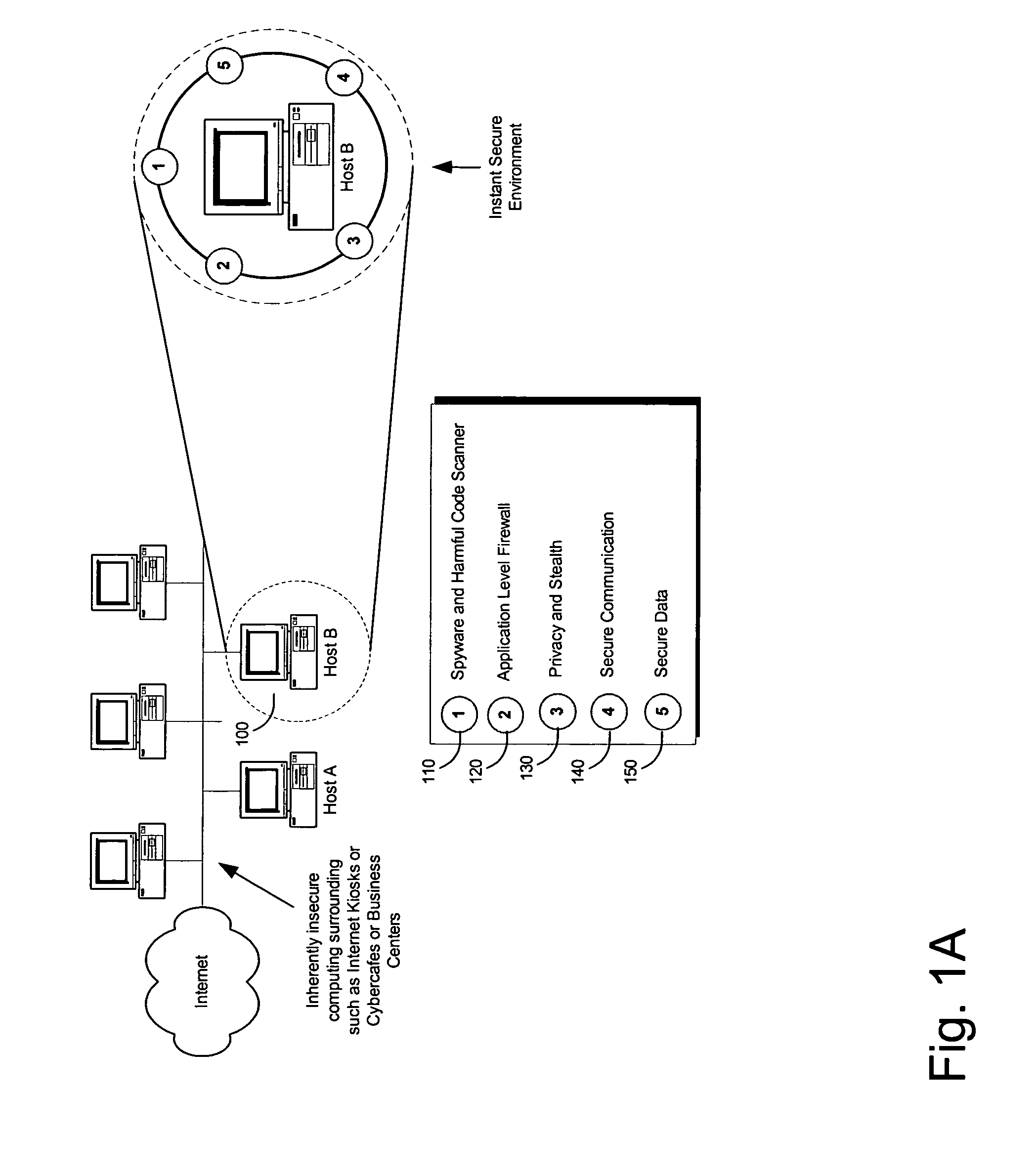
Endpoint security or endpoint protection is an approach to the protection of computer networks that are remotely bridged to client devices. The connection of laptops, tablets, mobile phones and other wireless devices to corporate networks creates attack paths for security threats. Endpoint security attempts to ensure that such devices follow a definite level of compliance to standards.
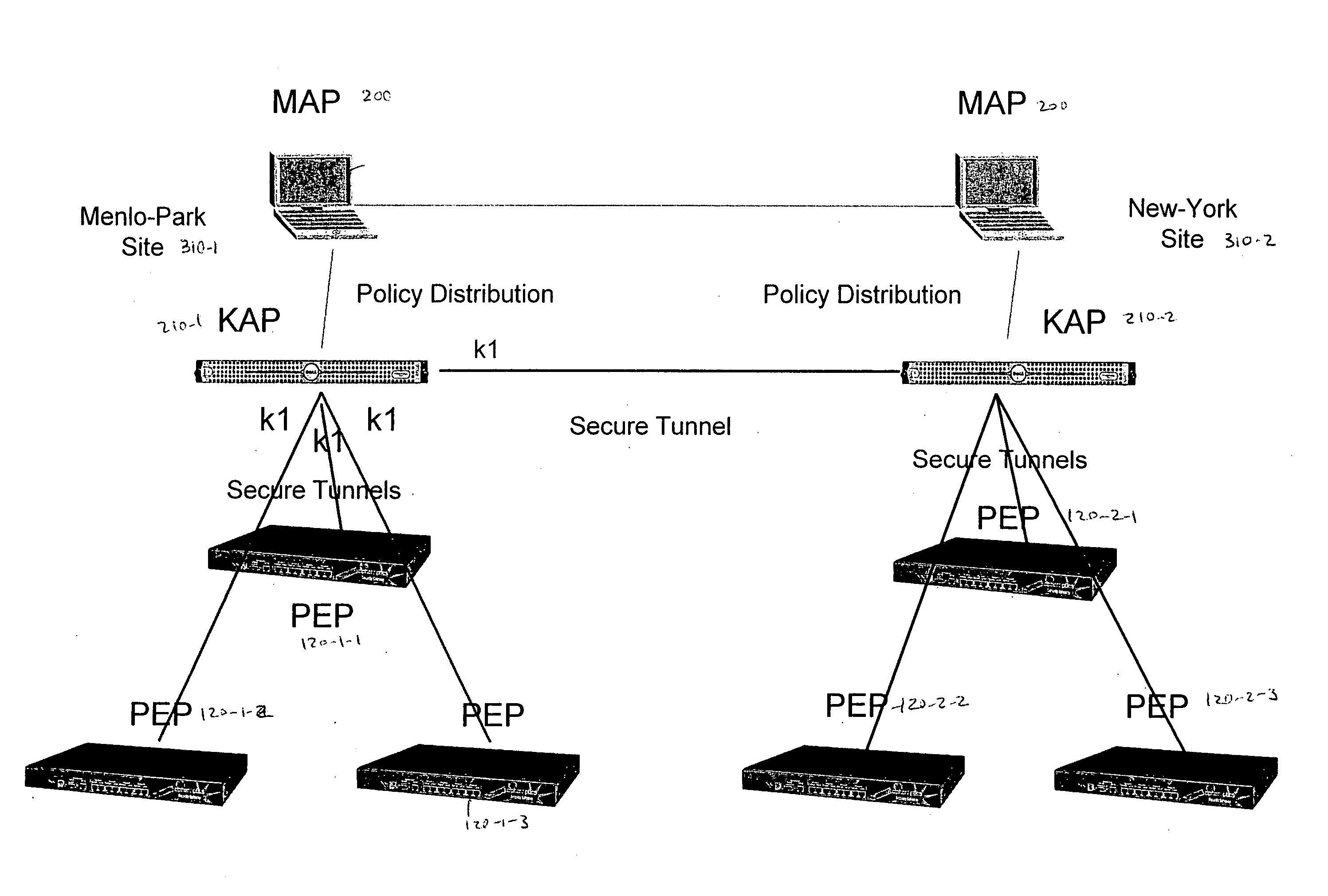
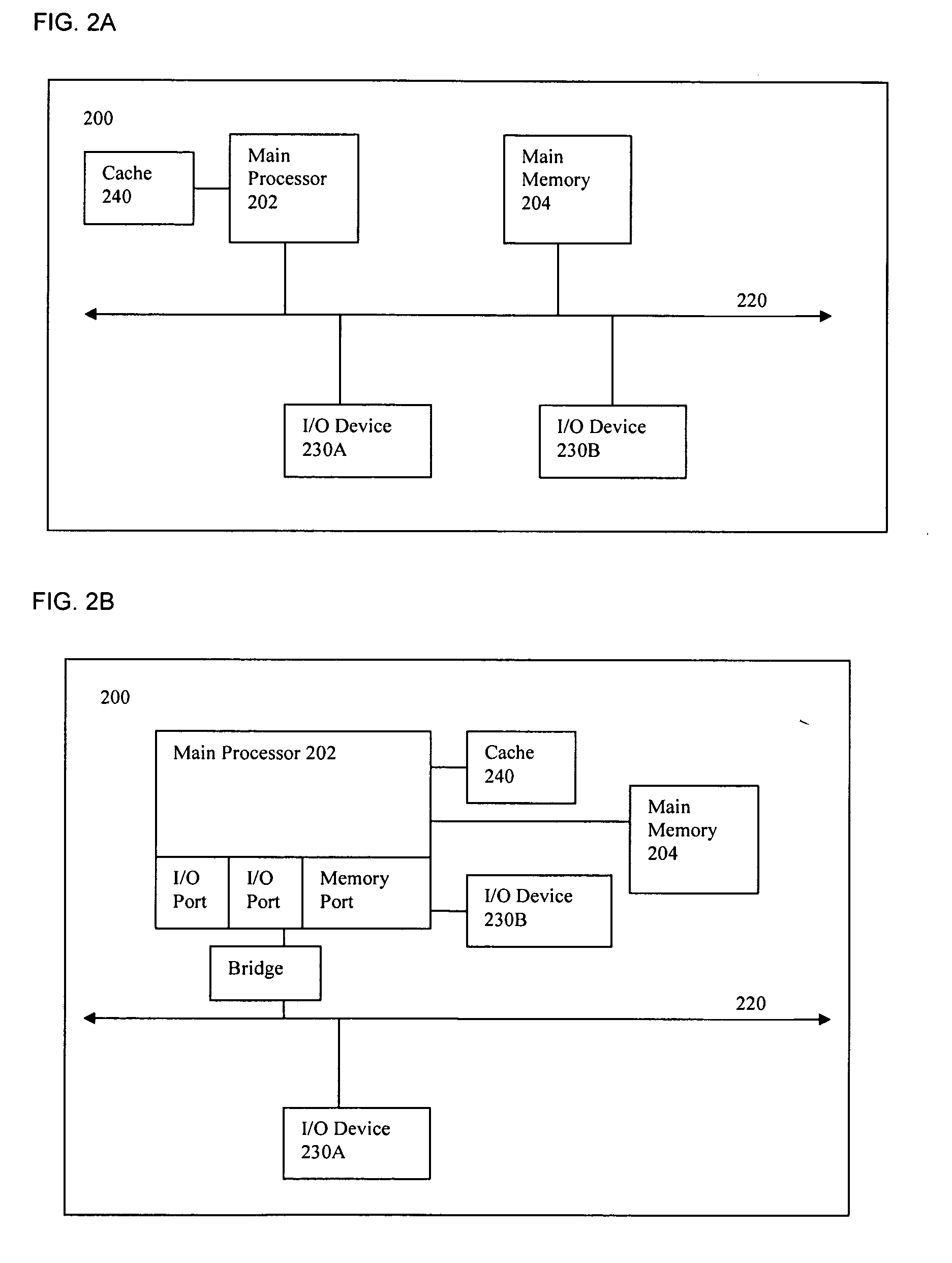
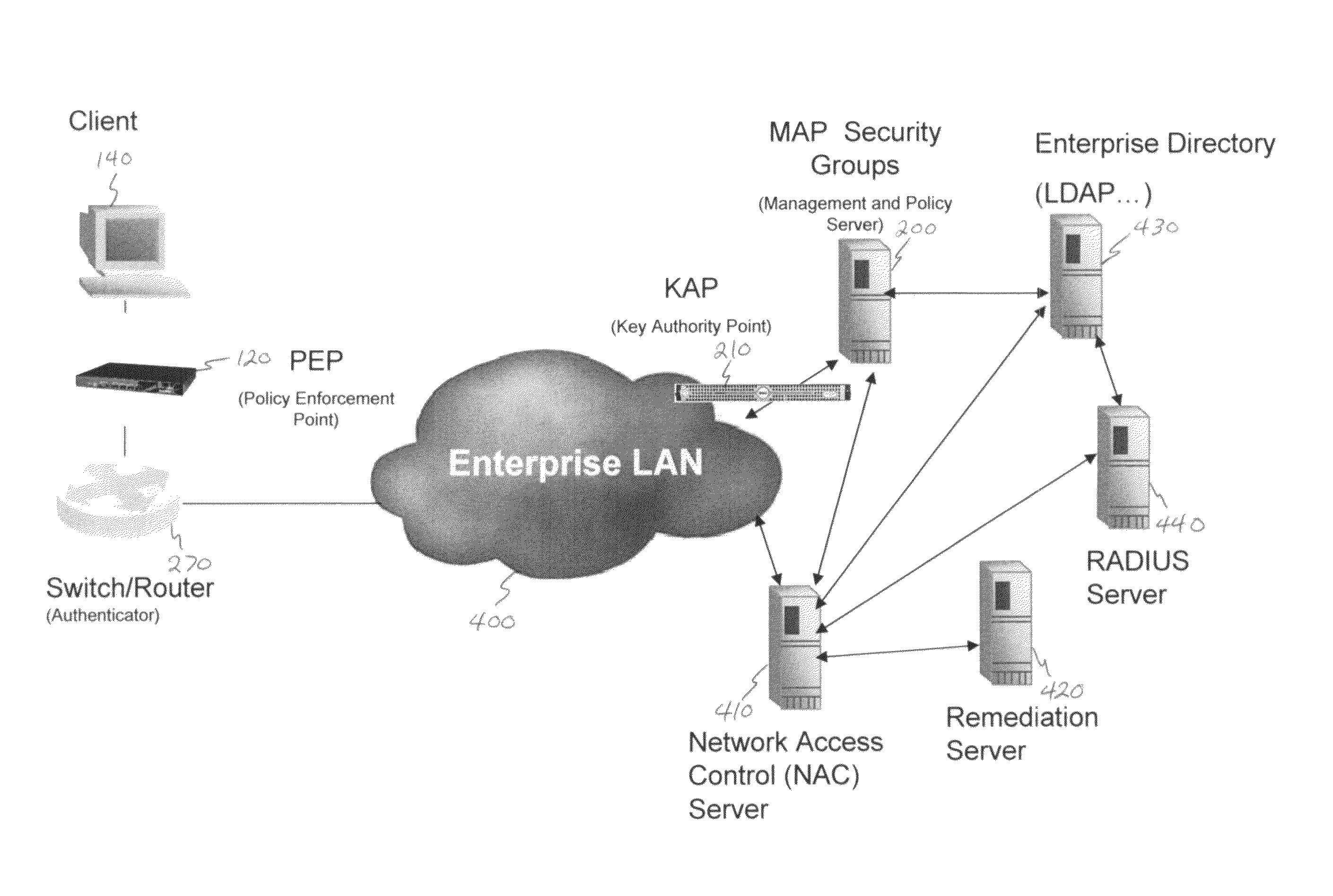
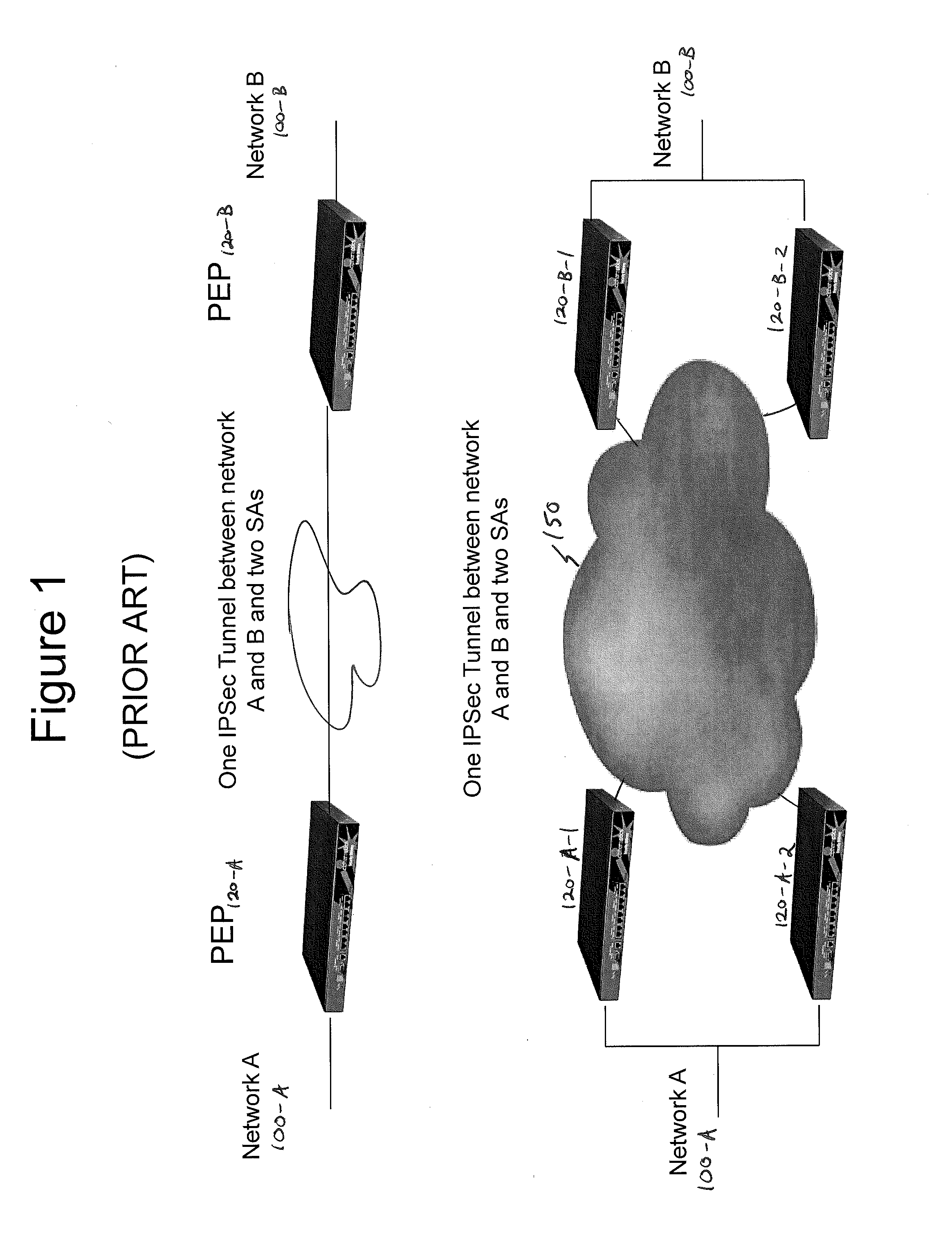
Deploying group VPNS and security groups over an end-to-end enterprise network
ActiveUS20080127327A1Key distribution for secure communicationDigital data processing detailsPrivate networkEndpoint security
Group Virtual Private Networks (Group VPNS) are provided for different types of machines in a data processing network. Security groups are defined by a security policy for each member. Security policies and encryption keys are deployed to members of a security group using an IPSec network infrastructure with authentication via VPN mechanisms. The group VPNs provide a trusted IP network that can leverage and co-exist with security access control technologies, such as endpoint security that controls client network access or application security that controls user access to enterprise applications.
Owner:CIPHEROPTICS
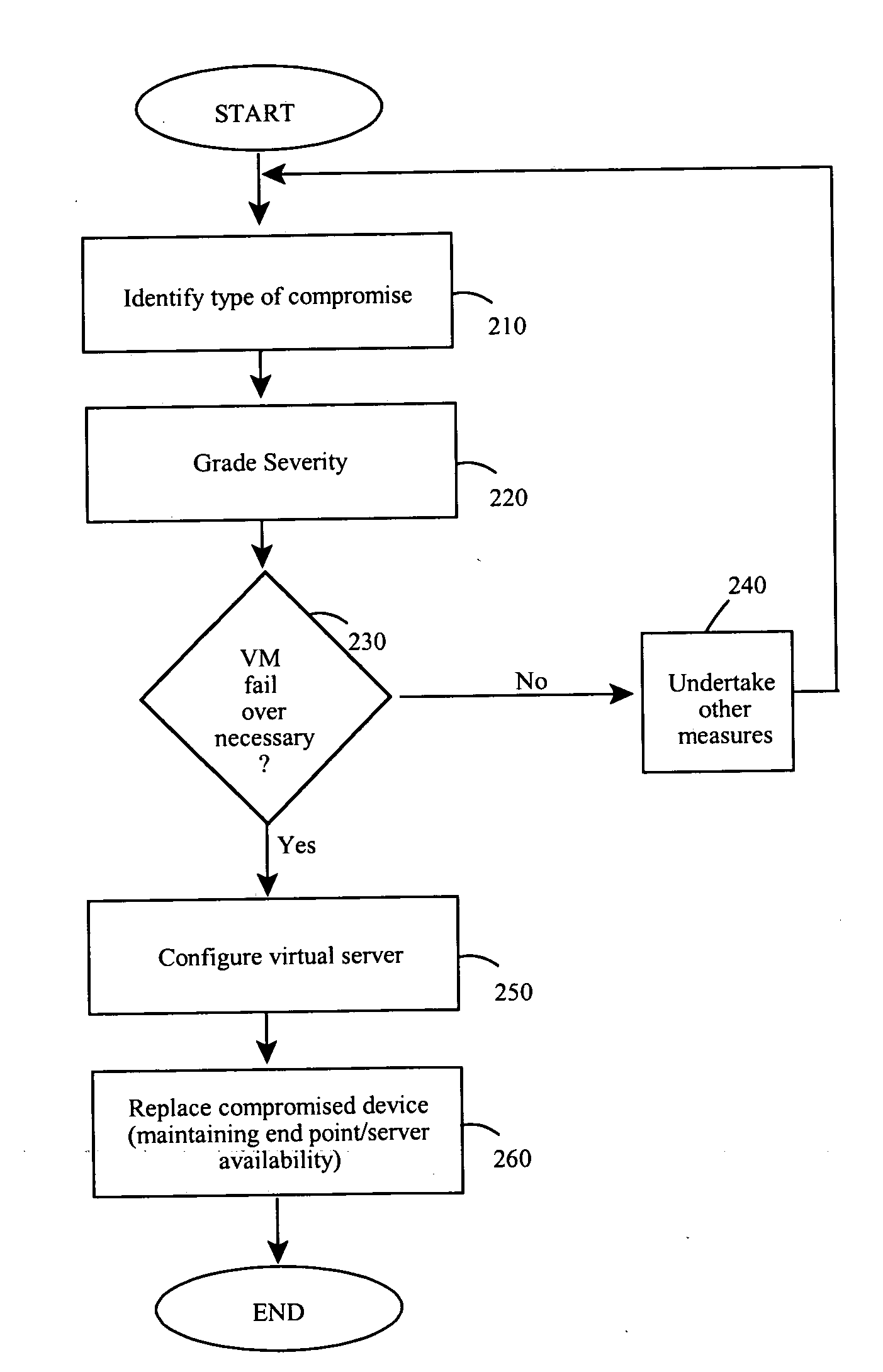
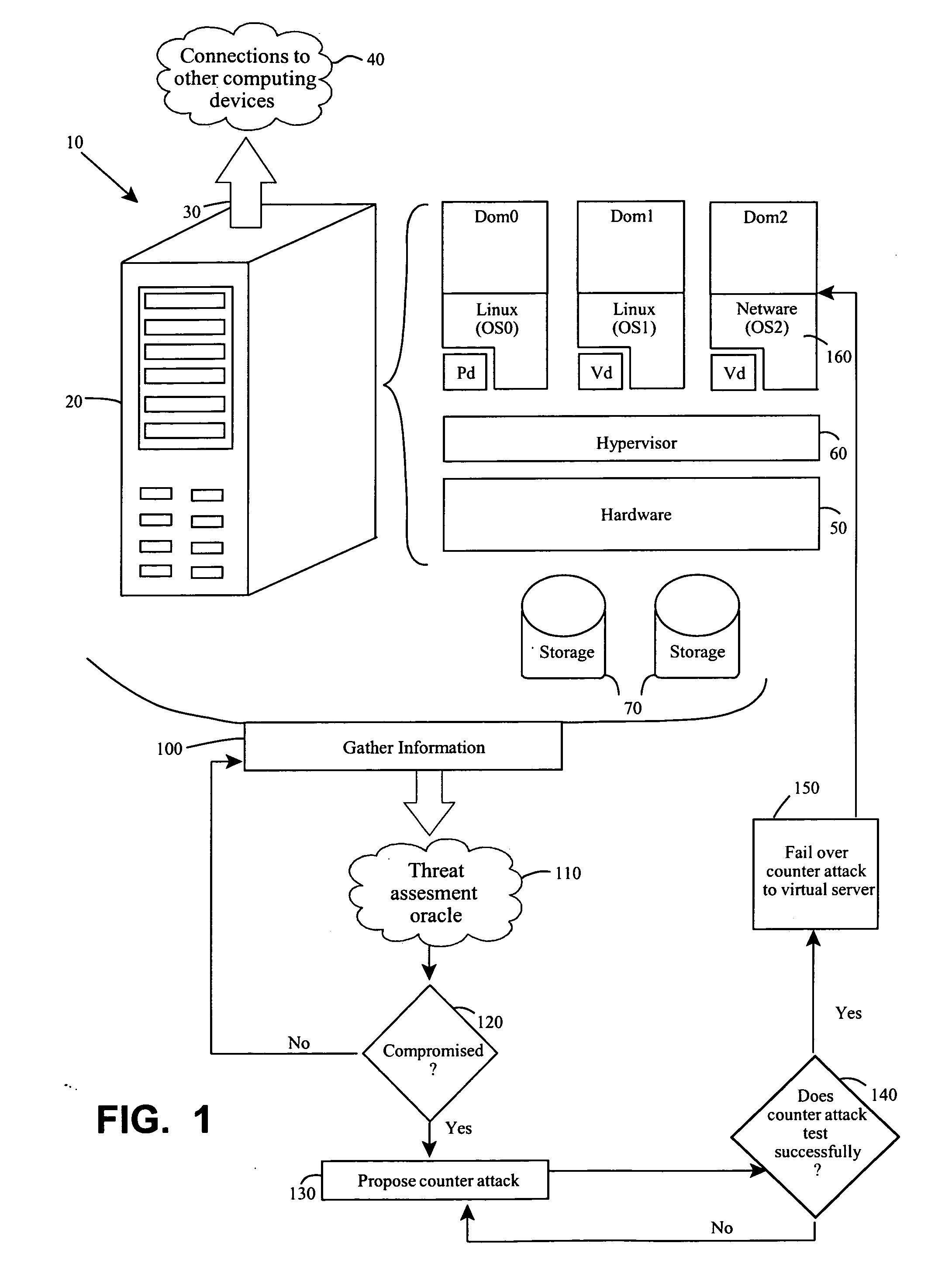
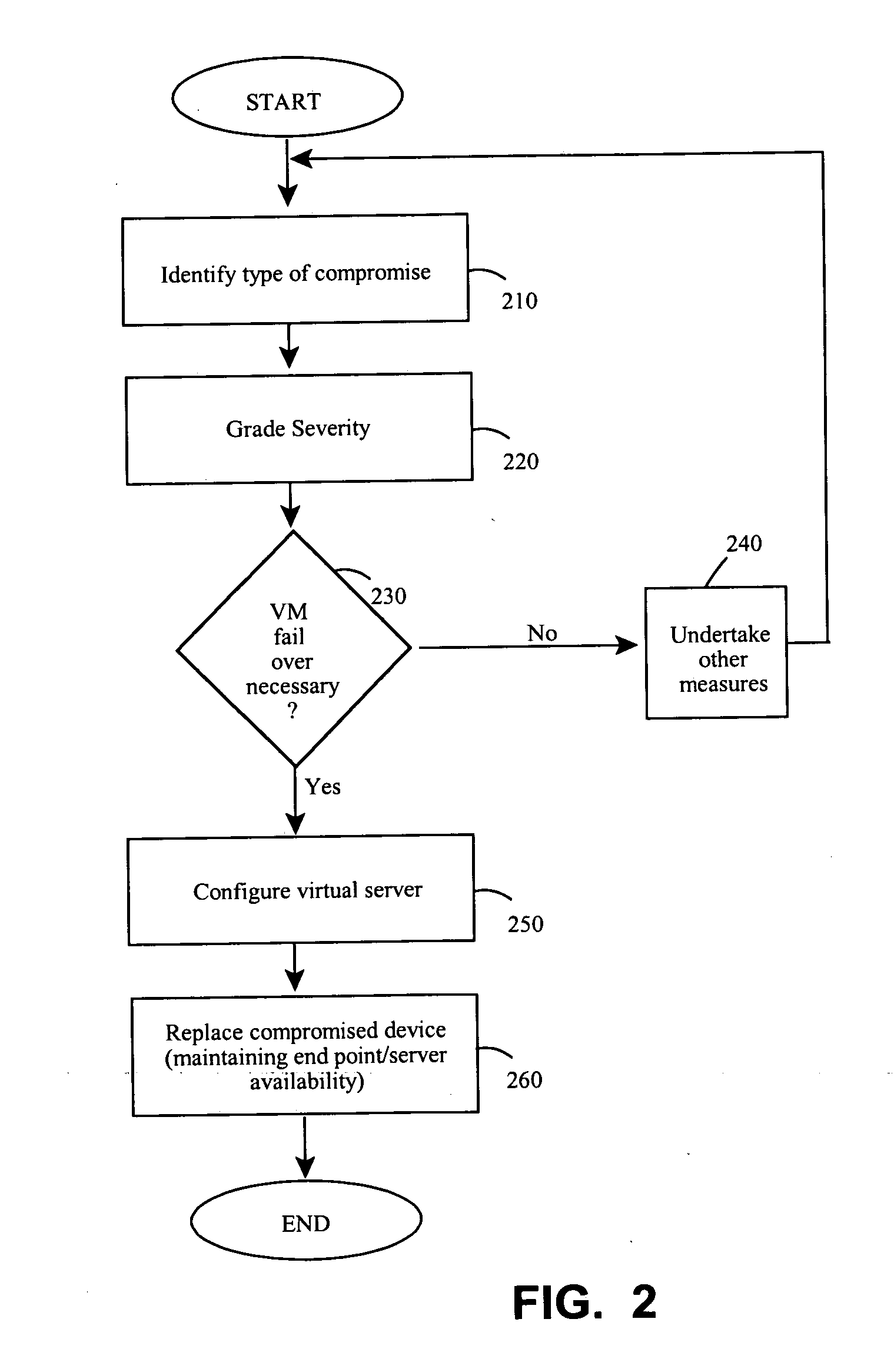
Endpoint security threat mitigation with virtual machine imaging
InactiveUS20110078797A1Quick changeMaintain availabilityMemory loss protectionError detection/correctionCountermeasureEndpoint security
Methods and apparatus involve the mitigation of security threats at a computing endpoint, such as a server, including dynamic virtual machine imaging. During use, a threat assessment is undertaken to determine whether a server is compromised by a security threat. If so, a countermeasure to counteract the security threat is developed and installed on a virtual representation of the server. In this manner, the compromised server can be replaced with its virtual representation, but while always maintaining the availability of the endpoint in the computing environment. Other features contemplate configuration of the virtual representation from a cloned image of the compromised server at least as of a time just before the compromise and configuration on separate or same hardware platforms. Testing of the countermeasure to determine success is another feature as is monitoring data flows to identifying compromises, including types or severity. Computer program products and systems are also taught.
Owner:NOVELL INC
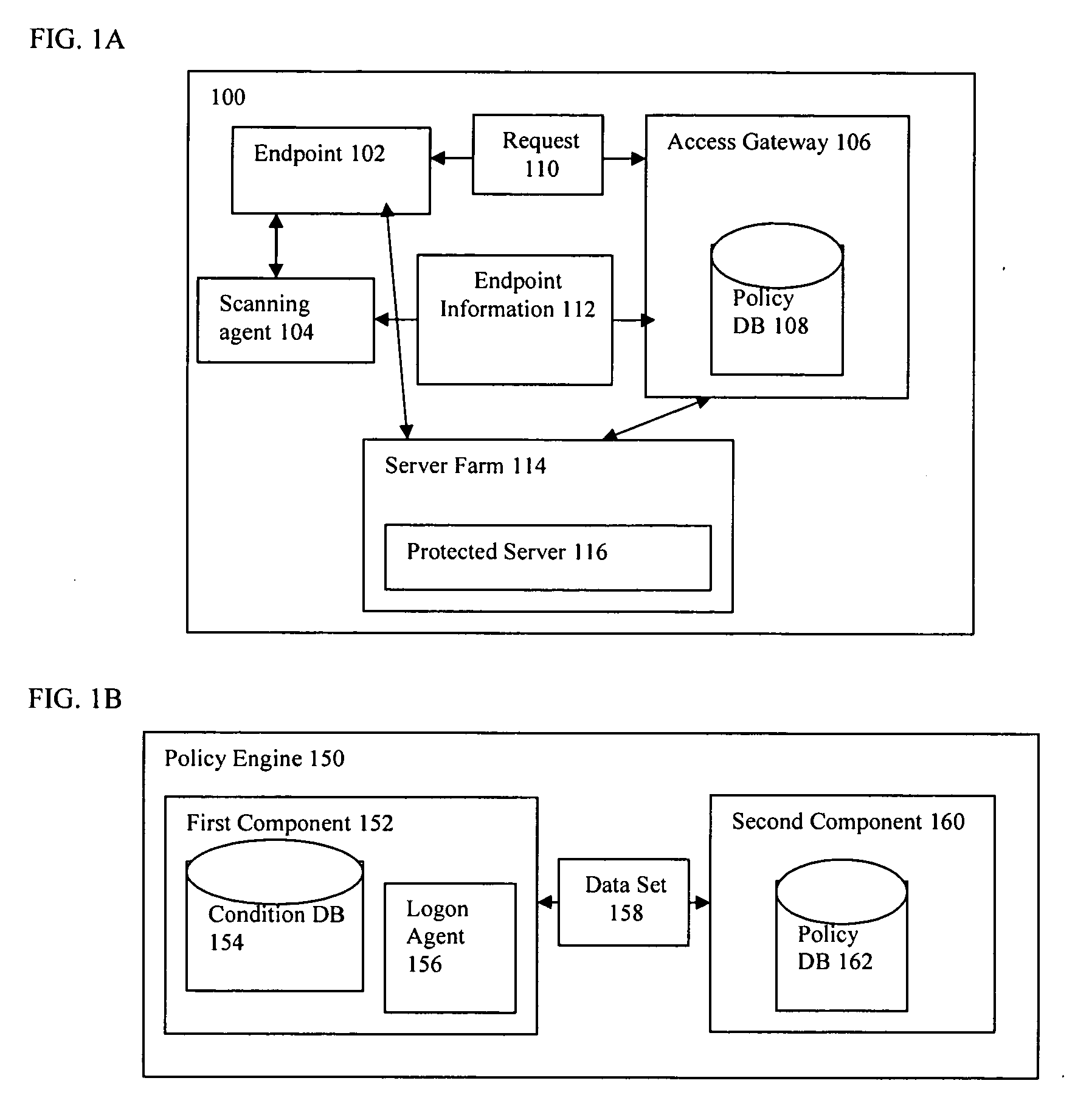
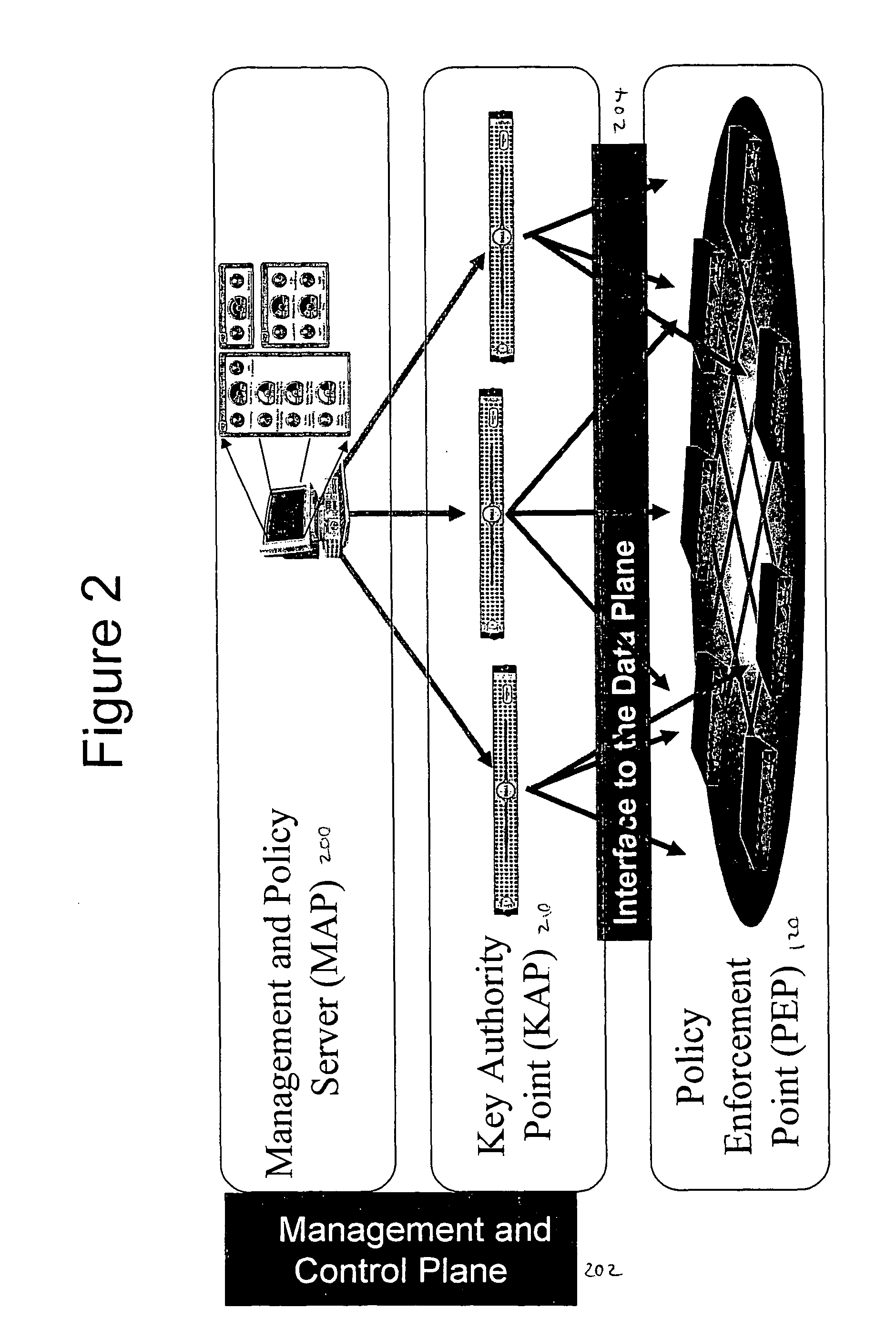
Method and system for verification of an endpoint security scan
InactiveUS20060174115A1Avoid manipulationVerify accuracyUser identity/authority verificationComputer security arrangementsEndpoint security
Owner:CITRIX SYST INC
Multi-service vpn network client for mobile device having integrated acceleration
ActiveCN102333306AConflict minimizationReduce in quantityTelephonic communicationConnection managementAnti virusOperational system
An integrated, multi-service network client for cellular mobile devices is described. The multi-service network client can be deployed as a single software package on cellular mobile network devices to provide integrated services including secure enterprise virtual private network (VPN) connectivity, acceleration, security management including monitored and enforced endpoint compliance, and collaboration services. Once installed on the cellular mobile device, the multi-service client integrates with an operating system of the device to provide a single entry point for user authentication for secure enterprise connectivity, endpoint security services including endpoint compliance with respect to anti-virus and spyware software, and comprehensive integrity checks. That is, the multi-service client provides a common user interface to the integrated services, and provides a VPN handler that interfaces with the operating system to provide an entry point for network traffic to which the integrated services can be seamlessly applied.
Owner:PULSE SECURE
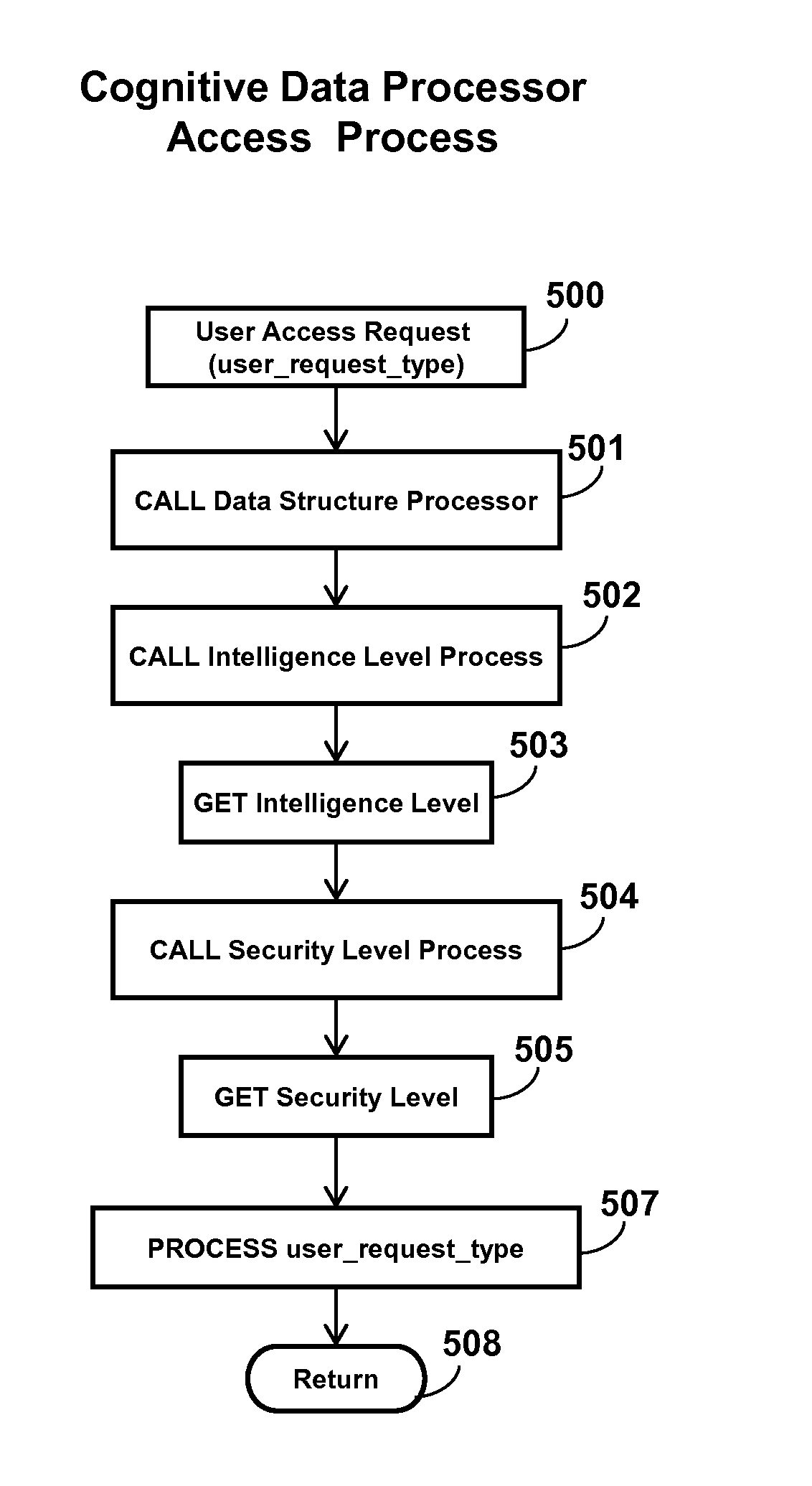
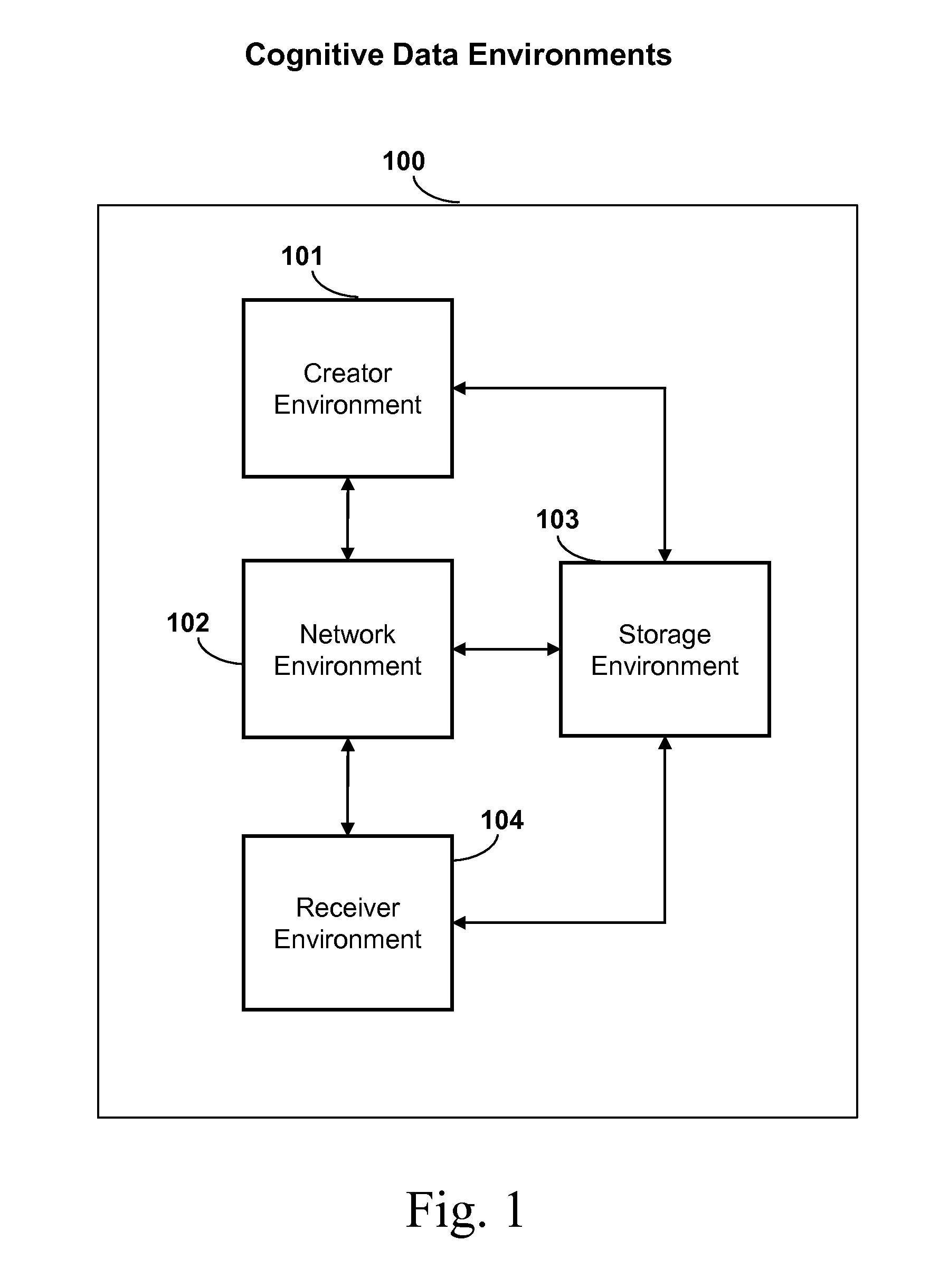
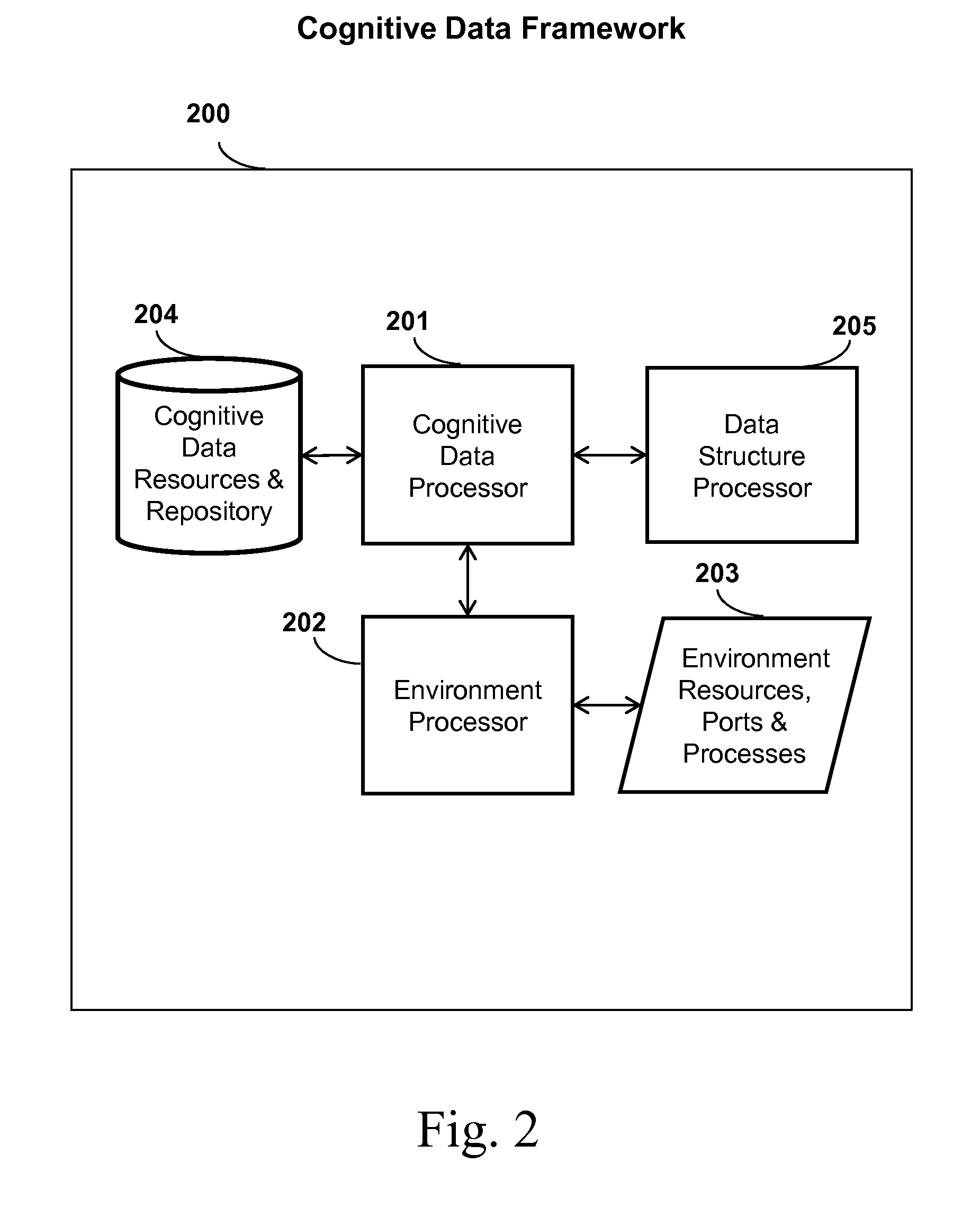
System, method, and apparatus for data, data structure, or encryption cognition incorporating autonomous security protection
InactiveUS20130133026A1Reduce errorsReduce incidenceDigital data processing detailsAnalogue secracy/subscription systemsCognitionSubject matter
Aspects of the inventive subject matter relate in general to systems, methods, and apparatus for data cognition that incorporates autonomous security protection and embedded intelligence. More particularly, the inventive subject matter relates to systems, methods, and apparatus utilizing cognitive data, cognitive encryption key(s), and cognitive data structures or protocols that can perform analyses and assessments, self-manage and / or self-organize, secure its environment, evaluate behavior, detect security problems, adapt, work in conjunction with network communication and protocols, alert the data creator of an urgent situation (Situation Awareness), and provide traceability, electronic forensics, and possess self-knowledge so it can be discovered, searched, and support data management, dynamic endpoint security, and be influenced by user behavior.
Owner:BURGESS SHELIA JEAN
Deploying group VPNS and security groups over an end-to-end enterprise network
ActiveUS8607301B2Key distribution for secure communicationDigital data processing detailsPrivate networkEndpoint security
Group Virtual Private Networks (Group VPNS) are provided for different types of machines in a data processing network. Security groups are defined by a security policy for each member. Security policies and encryption keys are deployed to members of a security group using an IPSec network infrastructure with authentication via VPN mechanisms. The group VPNs provide a trusted IP network that can leverage and co-exist with security access control technologies, such as endpoint security that controls client network access or application security that controls user access to enterprise applications.
Owner:CIPHEROPTICS
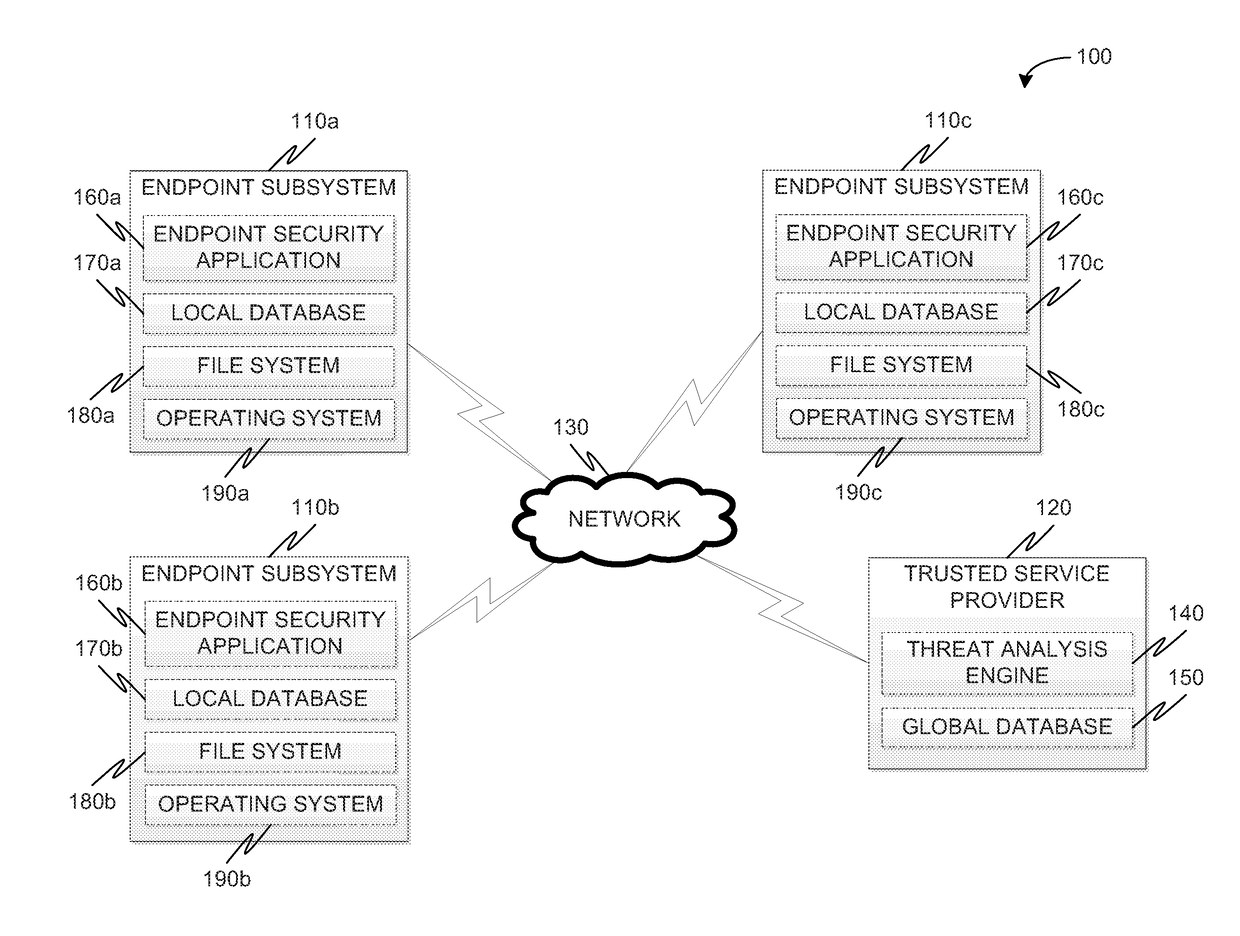
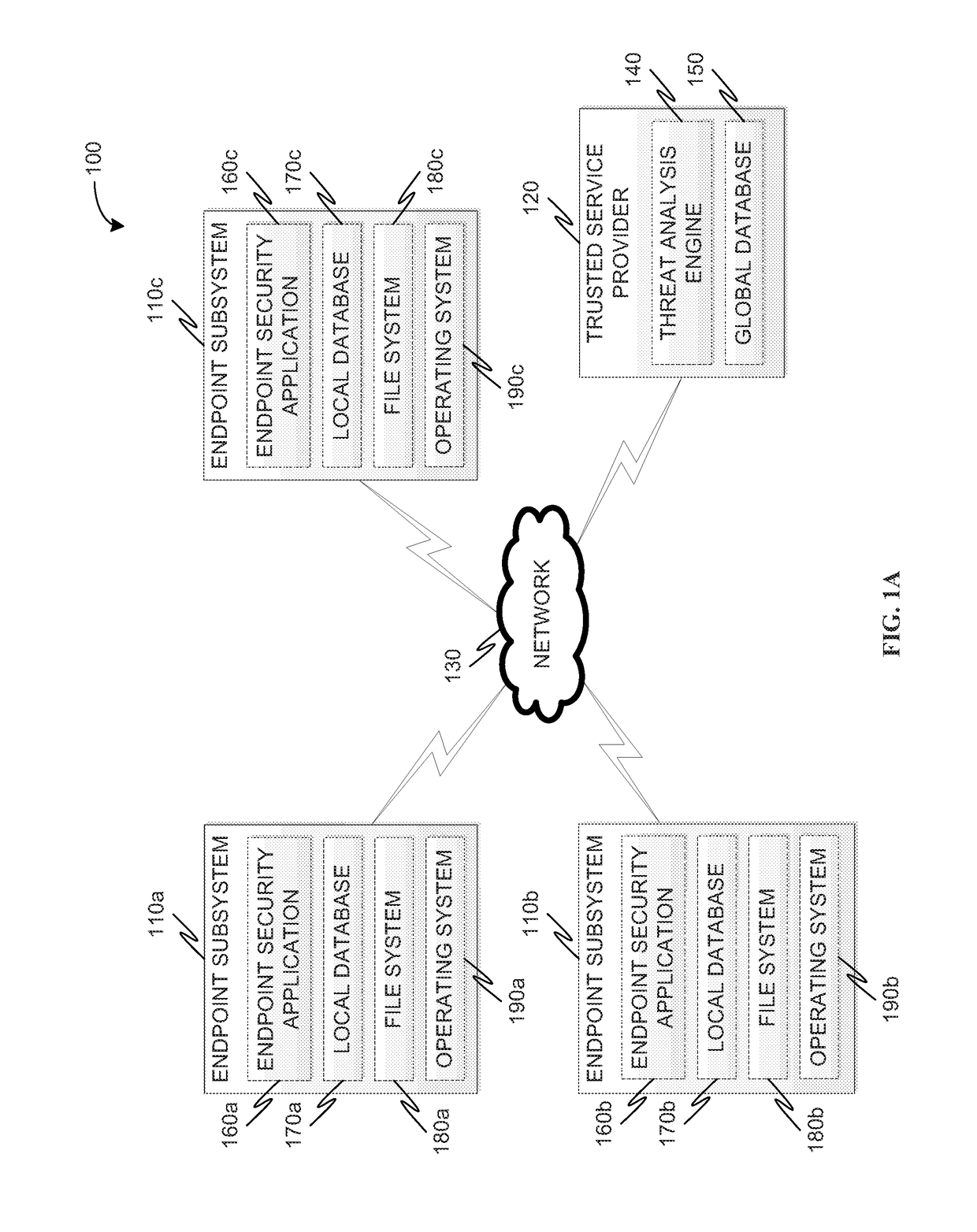
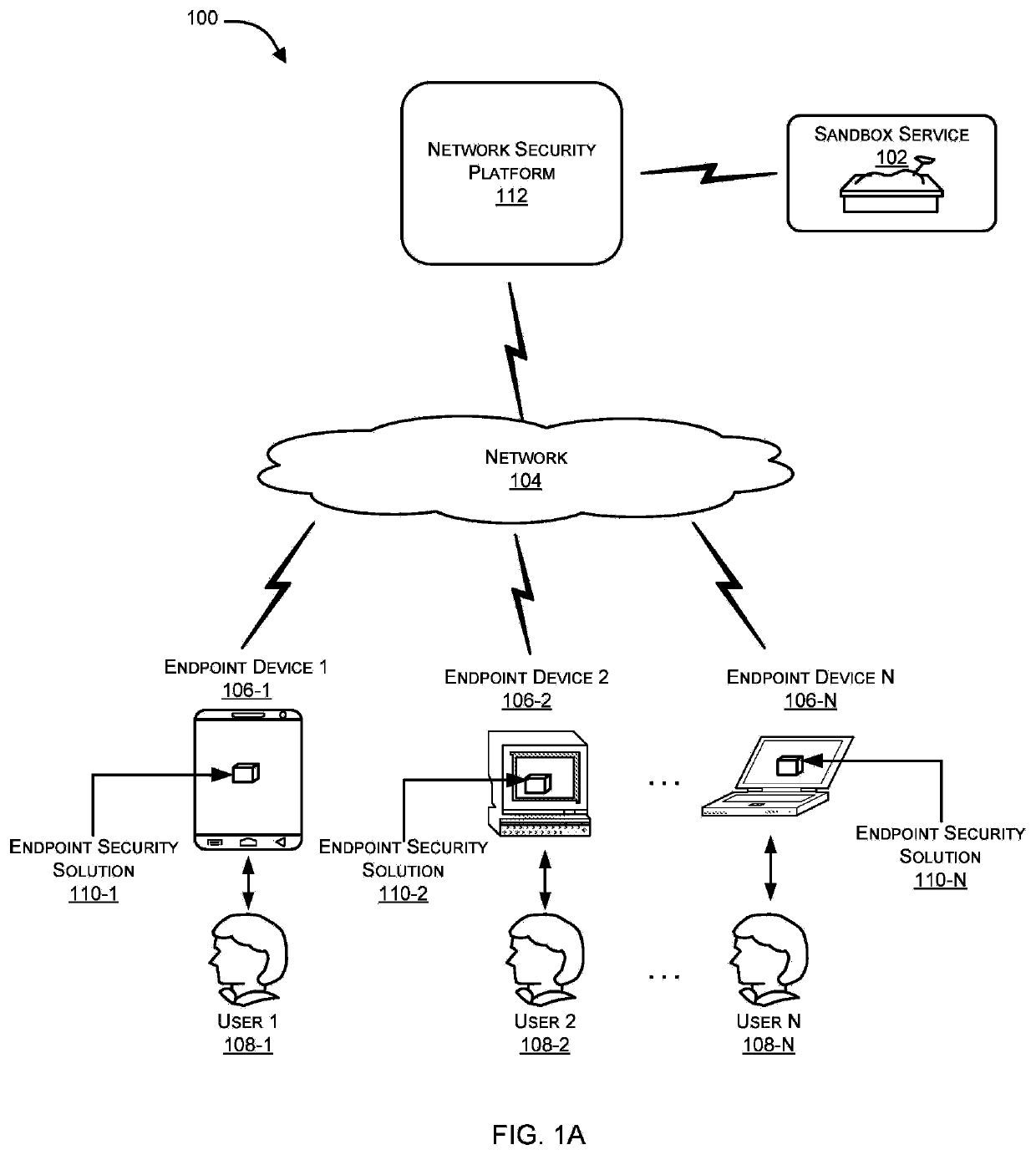
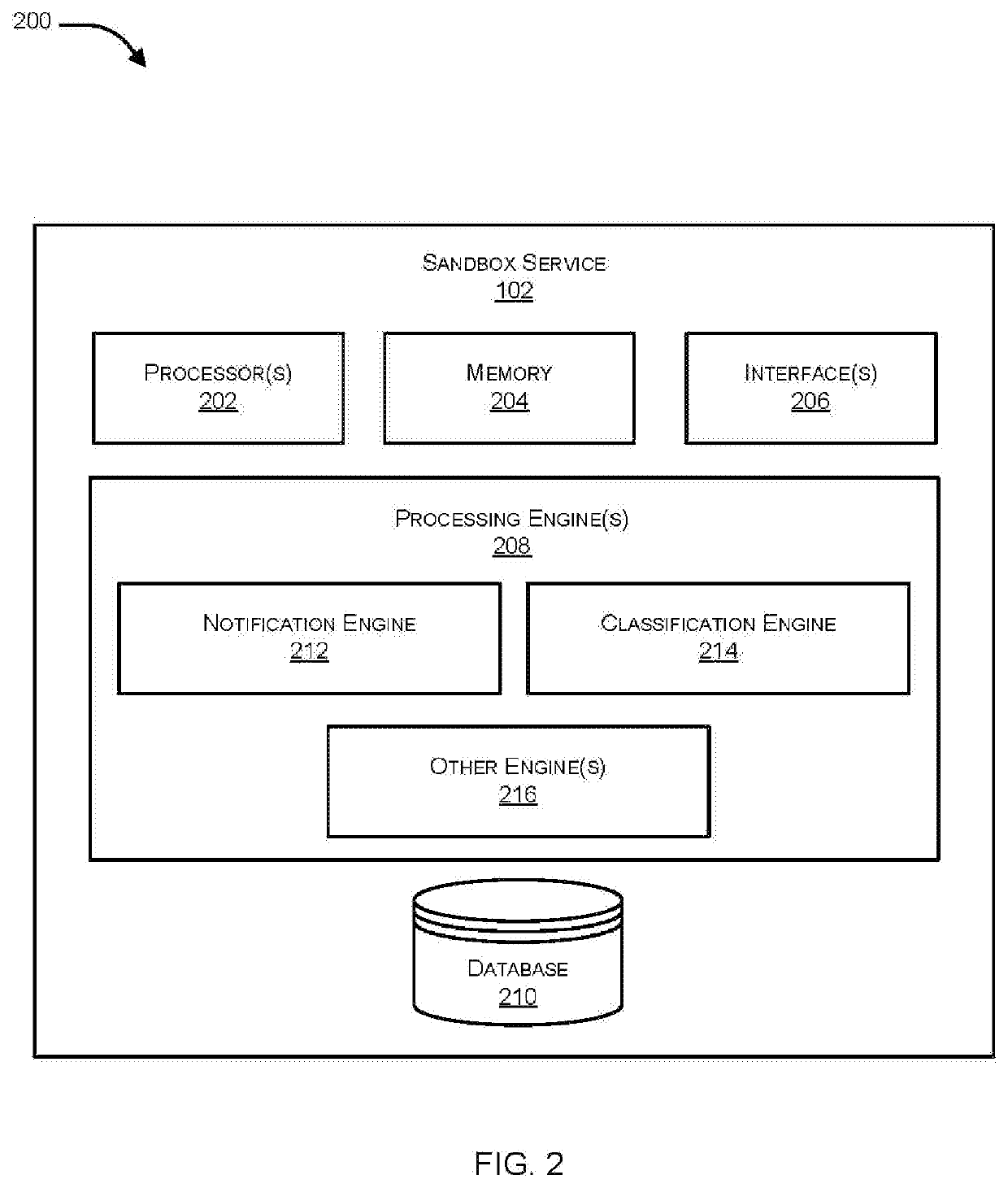
Sandboxing protection for endpoints
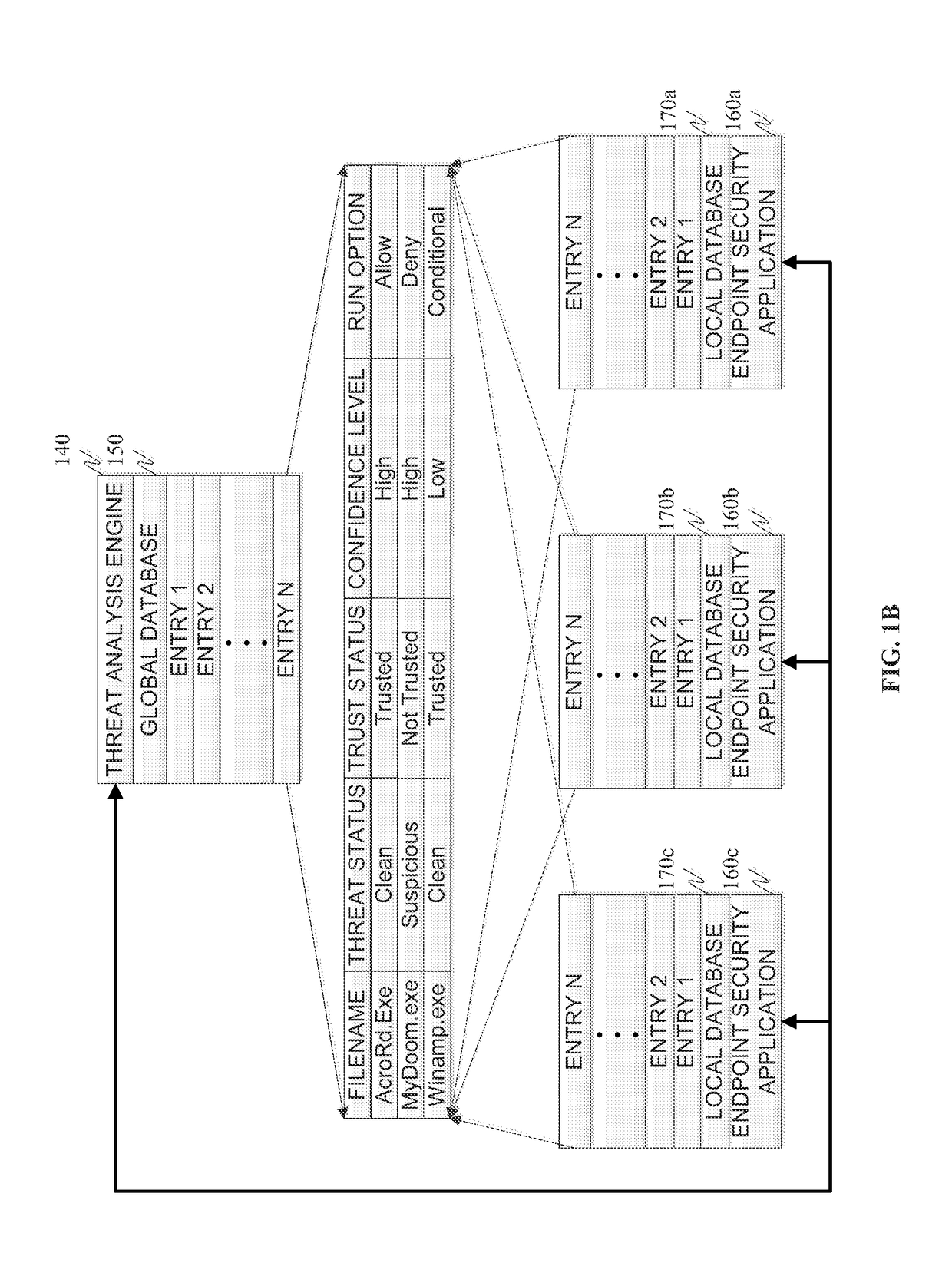
Methods and systems for integrating a sandboxing service and distributed threat intelligence within an endpoint security application are provided. According to one embodiment, The method includes file system or operating system activity relating to a file accessible to an endpoint system is monitored by an endpoint security application running on the endpoint system. The endpoint security application determines whether the file has been previously analyzed for a threat status. When a result of the determining is negative, then the endpoint security application requests the threat status by submitting the file to a remote threat analysis engine with a request to perform a threat analysis on the file. Based on the determined threat status, the endpoint security application selectively allows or disallows performance of the file system or operating system activity.
Owner:FORTINET
Method and system for verification of an endpoint security scan
InactiveUS8024568B2Avoid manipulationVerify accuracyUser identity/authority verificationComputer security arrangementsEndpoint security
Owner:CITRIX SYST INC
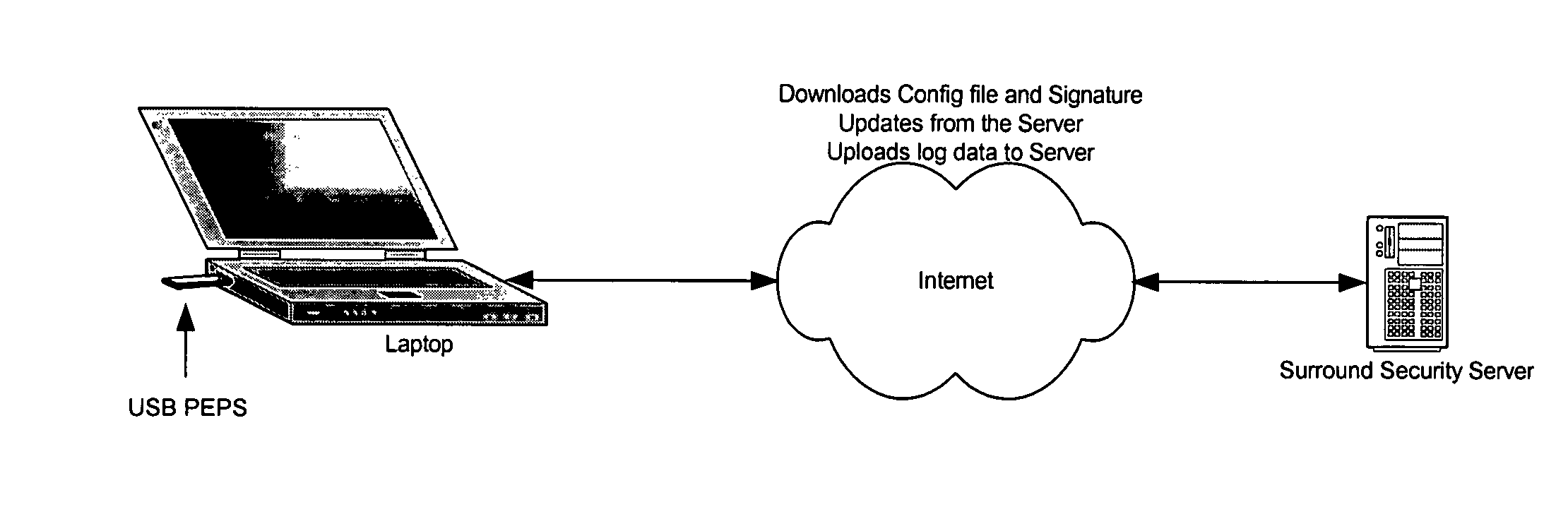
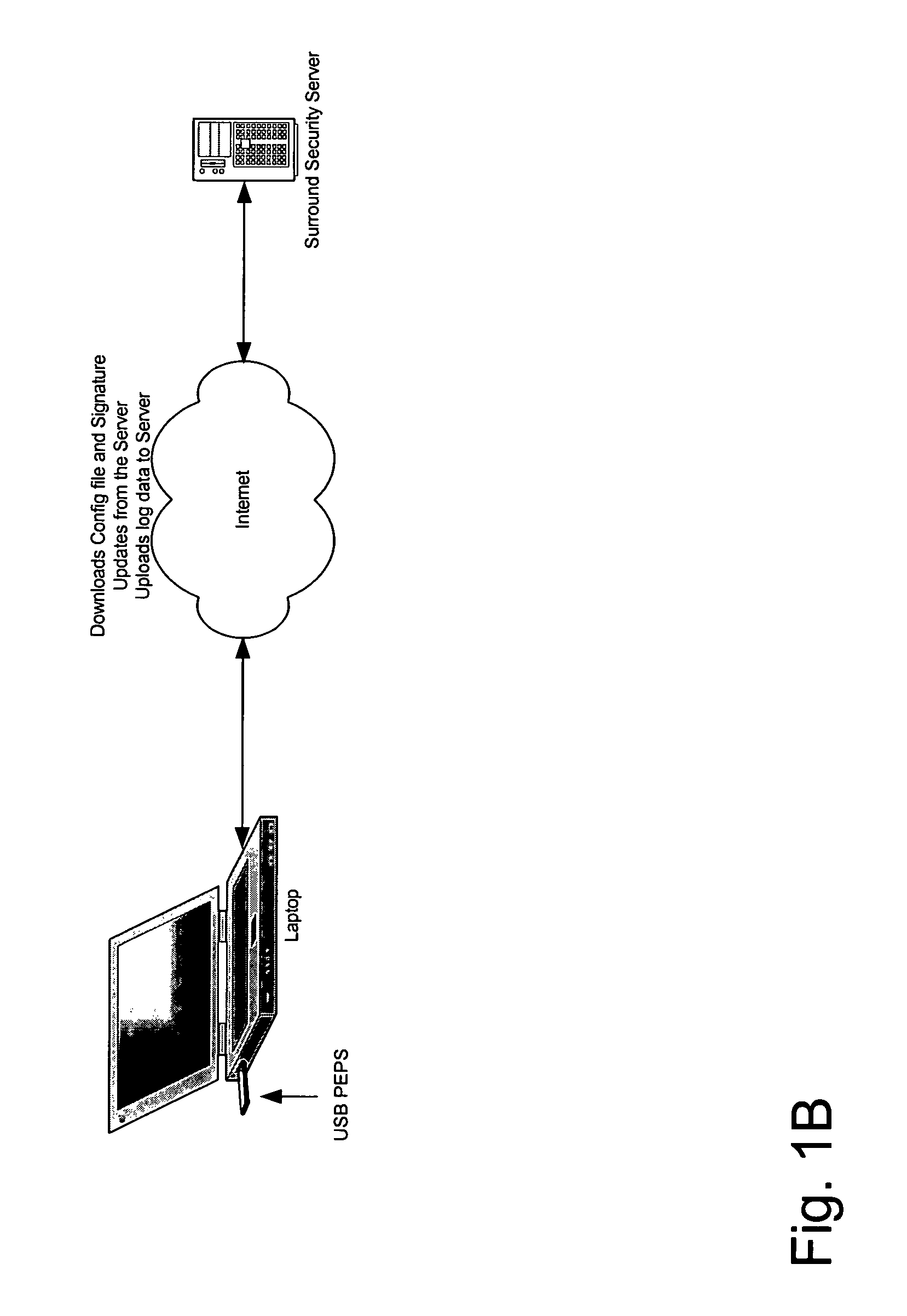
Method and apparatus for creating a secure anywhere system
A method and apparatus for providing portable end-point security are provided. In one embodiment, a PEPS system may include a PEPS processor having a memory operatively coupled thereto, the memory having stored therein instructions which when executed by the PEPS processor causes: an automatic loader to automatically trigger loading of the PEPS system; the PEPS system including a malicious software detector to scan a main memory of the computing system for malicious software; and wherein the malicious software detector performs a scan of the main memory of the computing system following triggering of the PEPS system by the automatic loader by comparing existing data in main memory of the computing system with indicia of malicious software.
Owner:REDCANNON SECURITY
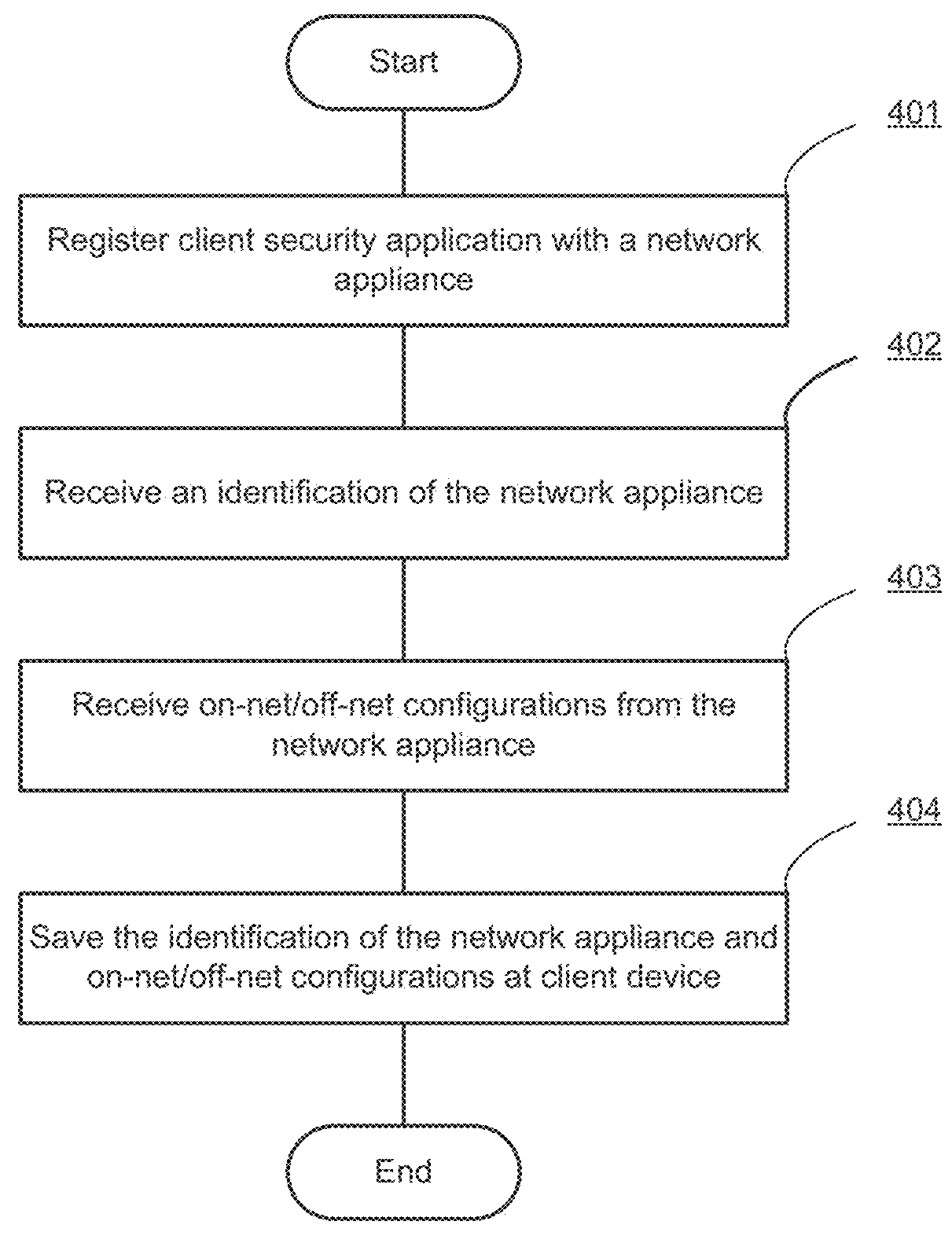
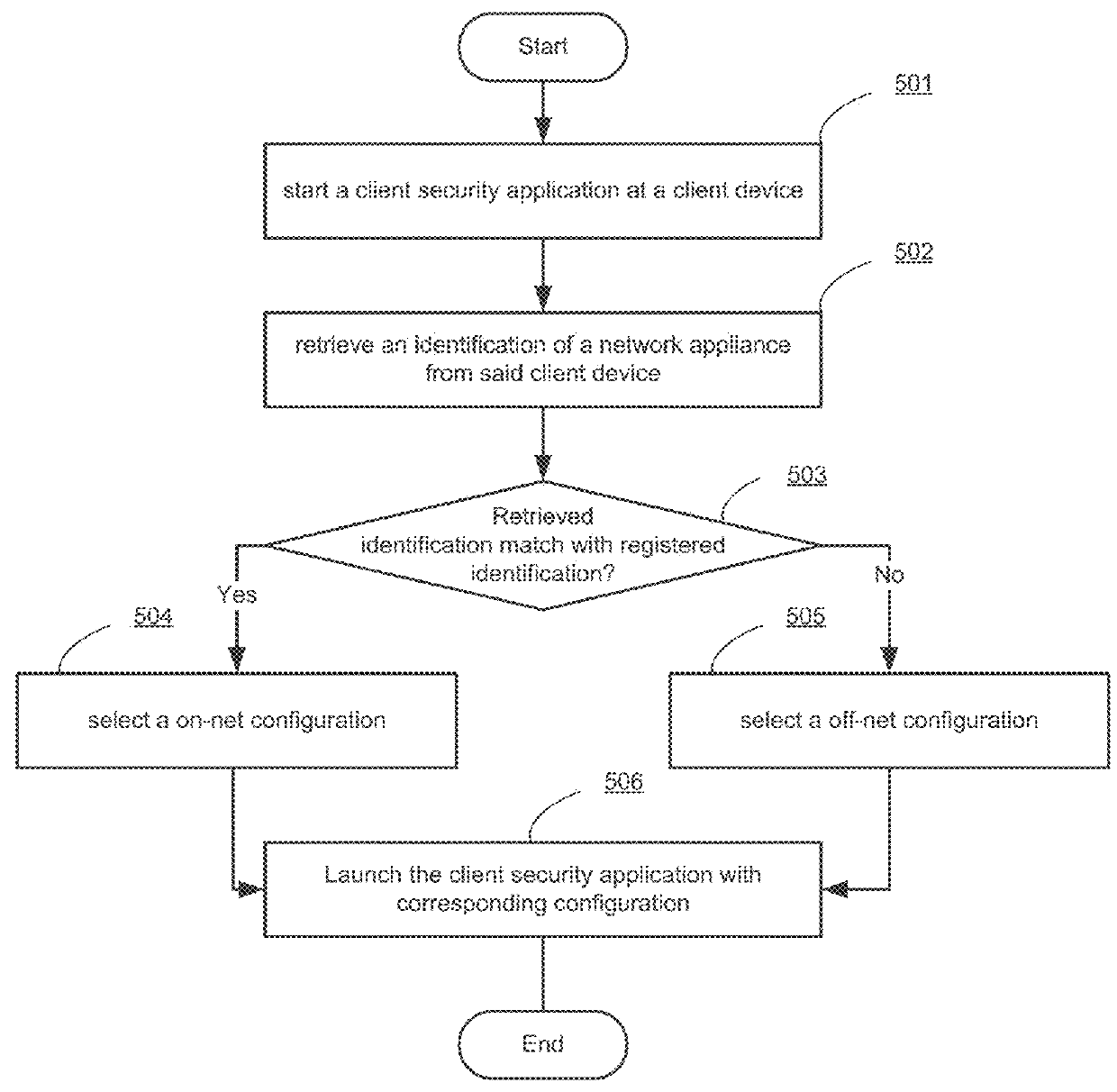
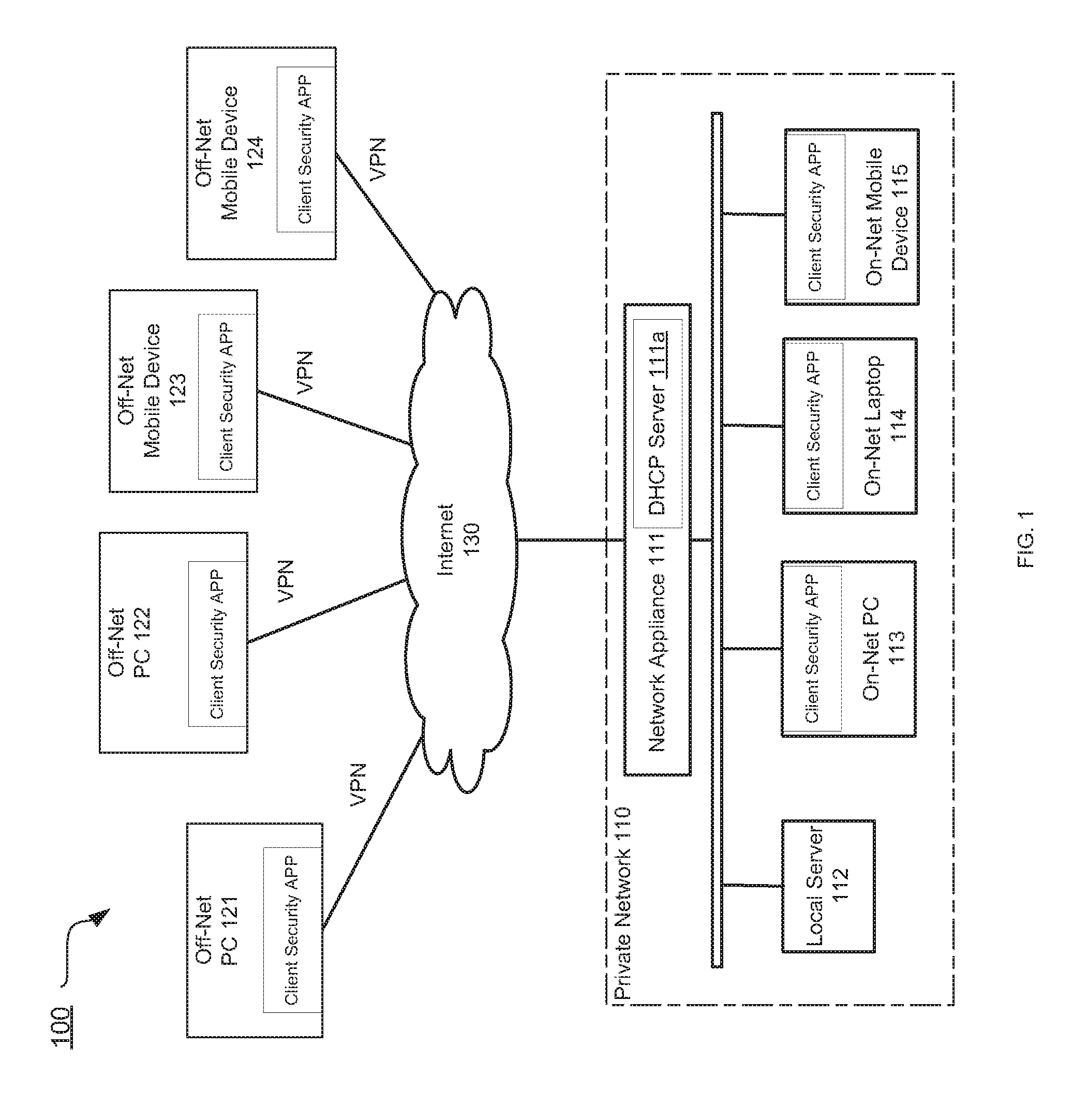
Automated configuration of endpoint security management
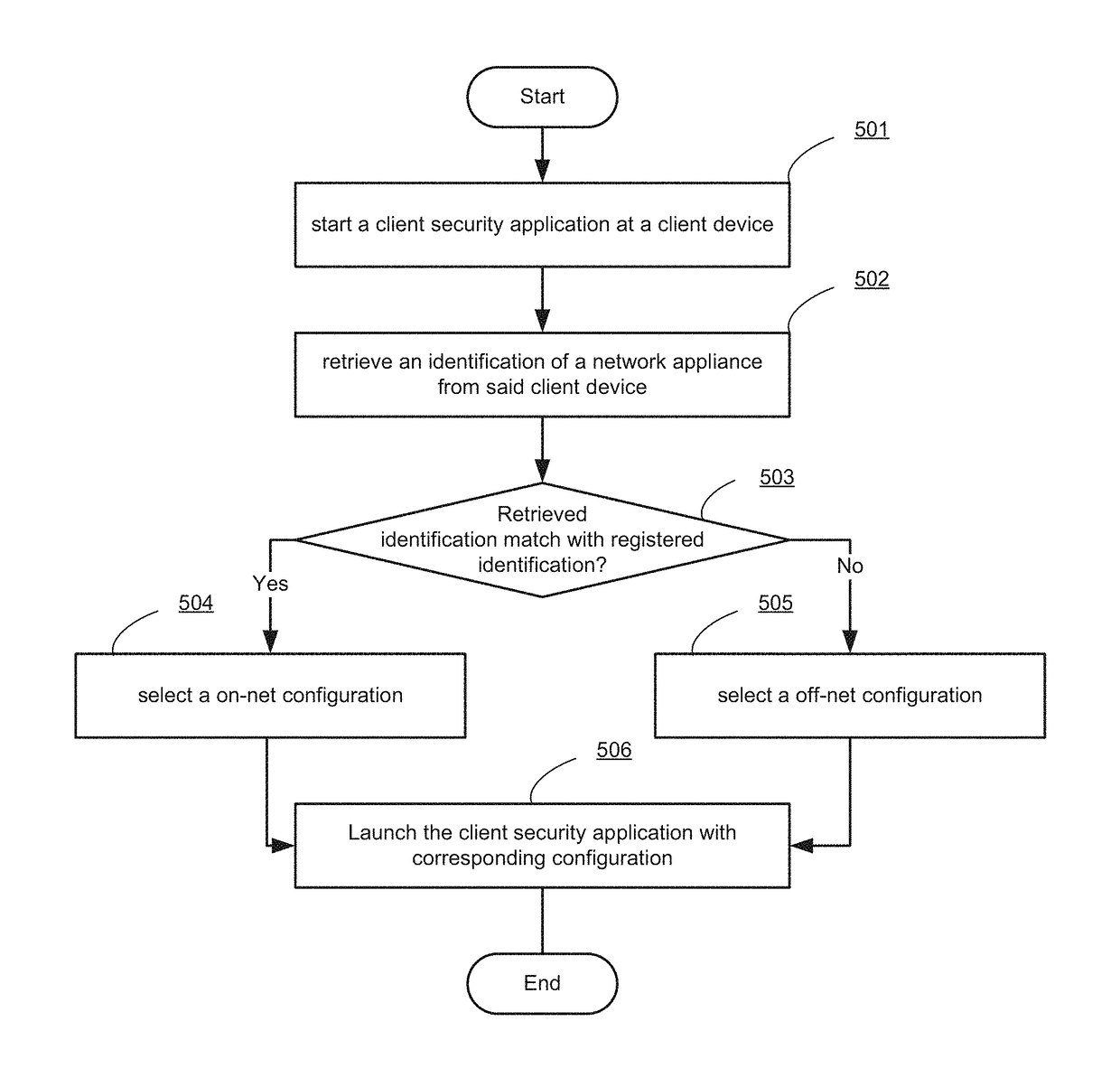
ActiveUS20160036780A1Multiple digital computer combinationsProgram controlAuto-configurationNetwork connection
Systems and methods for managing configuration of a client security application based on a network environment in which the client device is operating are provided. According to one embodiment, a network connection state of a client device with respect to a private network is determined by a client security application running on the client device. The client security application, then selects a configuration based on the determined network connection state. Finally, the client security application launches one or more functions of the client security application that are designated by the selected configuration.
Owner:FORTINET
Performing threat detection by synergistically combining results of static file analysis and behavior analysis
ActiveUS20210200870A1Highly-effective malware preventionSolve the high false positive rateEnsemble learningPlatform integrity maintainanceEndpoint securityData mining
Systems and methods are described for synergistically combining static file based detection and behavioral analysis to improve both threat detection time and accuracy. An endpoint security solution running on an endpoint device generates a static analysis score by performing a static file analysis on files associated with a process initiated on the endpoint device. When the static analysis score meets or exceeds a static analysis threshold, then a network security platform treats the process as malicious and blocks execution of the process. When the static analysis score is less than the static analysis threshold, then the endpoint security solution obtains a dynamic analysis score for the process. The network security platform treats the process as malicious and causes execution of the process to be blocked based on a function of the static analysis score and the dynamic analysis score.
Owner:FORTINET
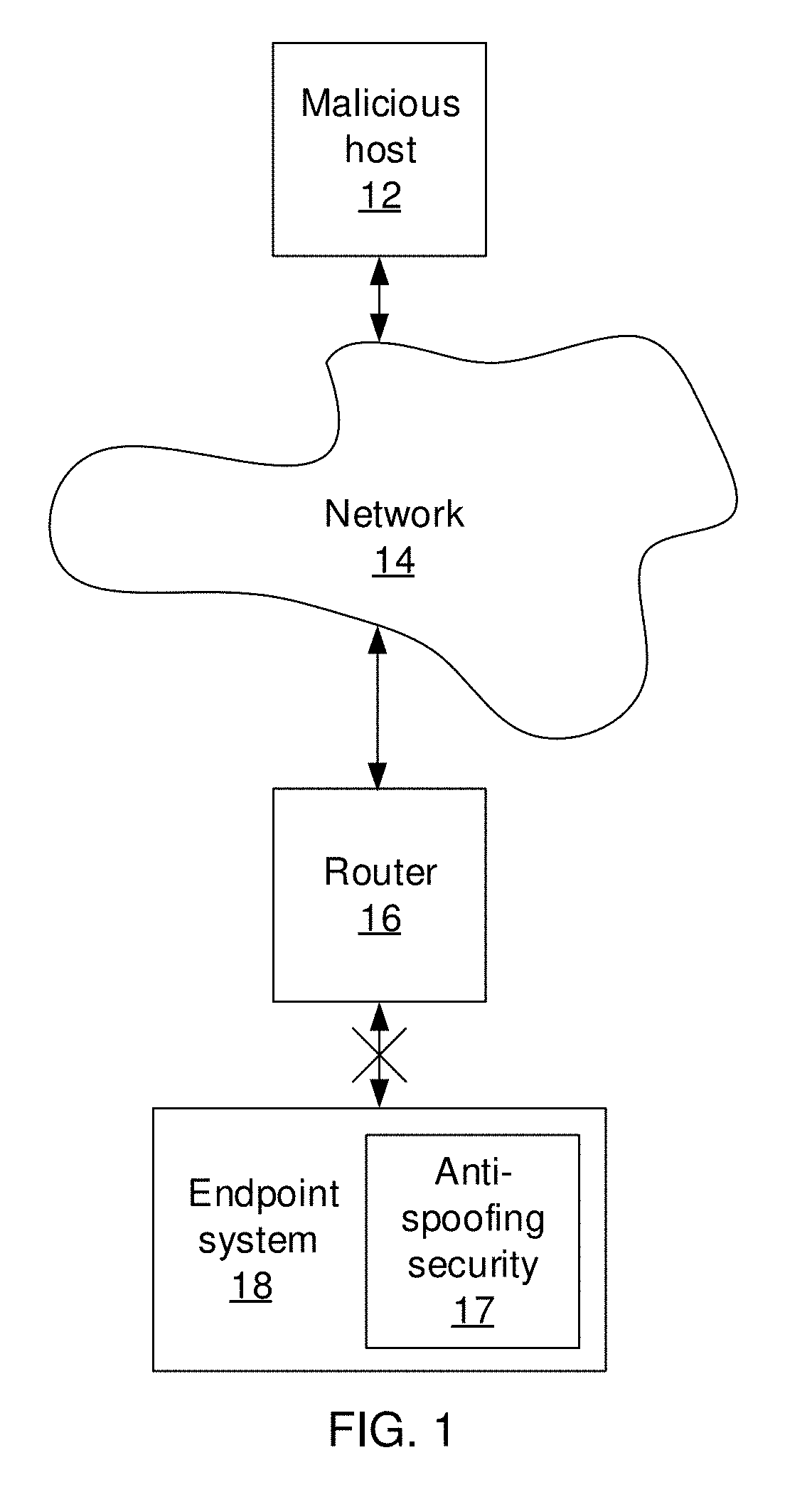
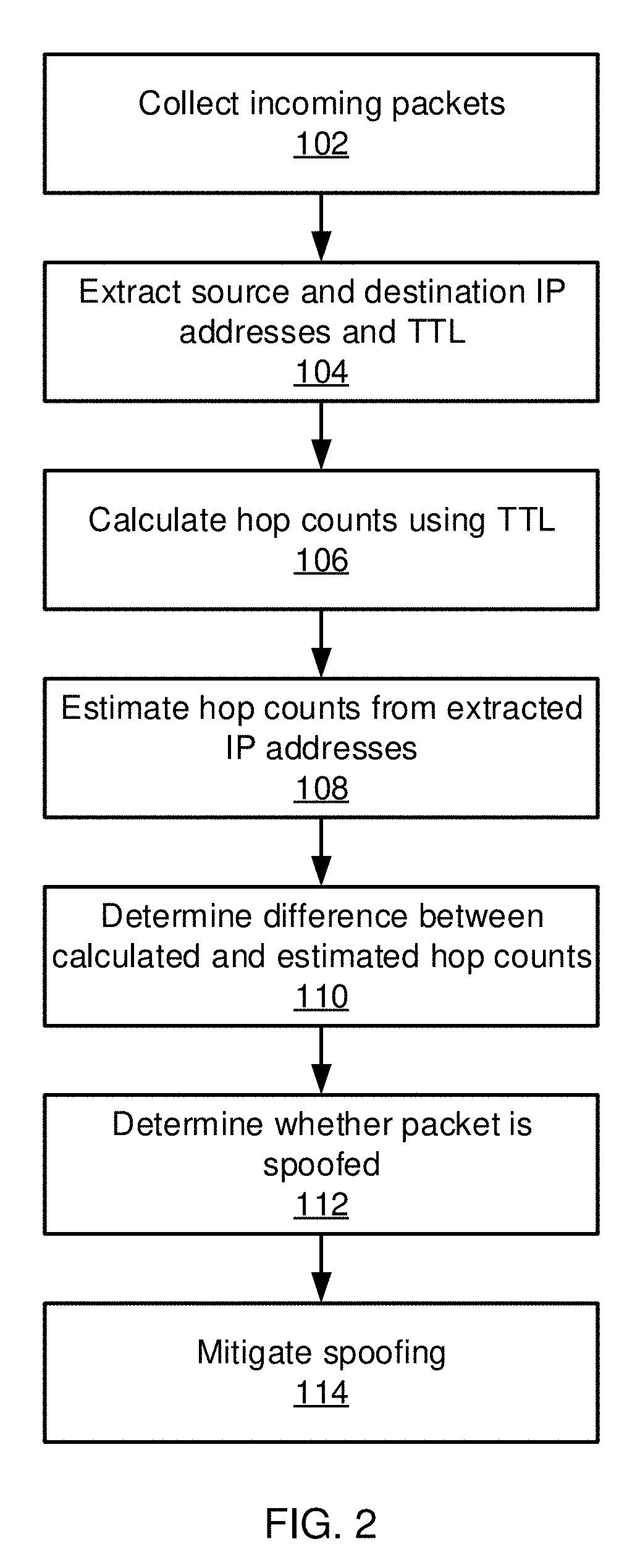
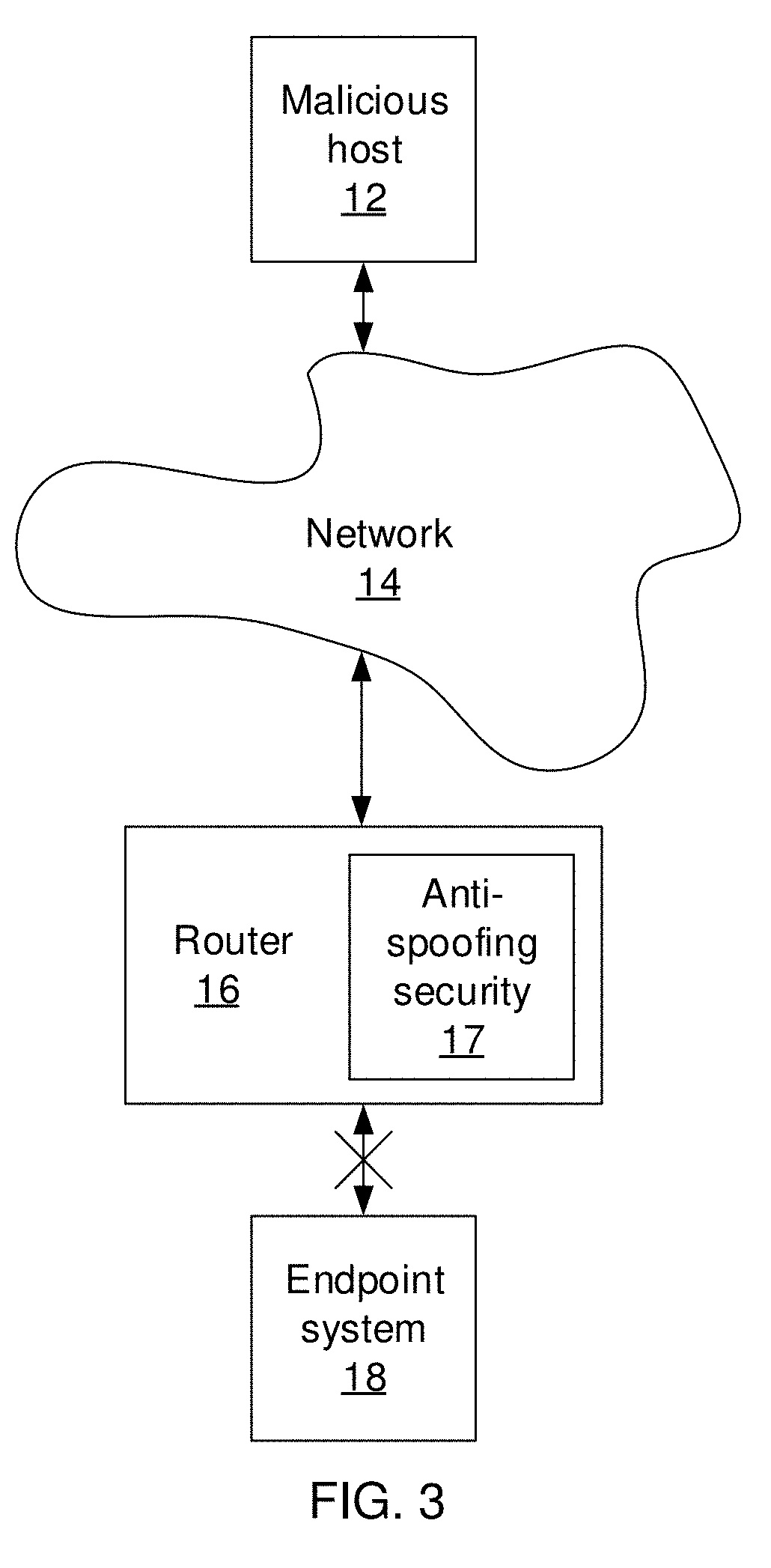
Network gateway spoofing detection and mitigation
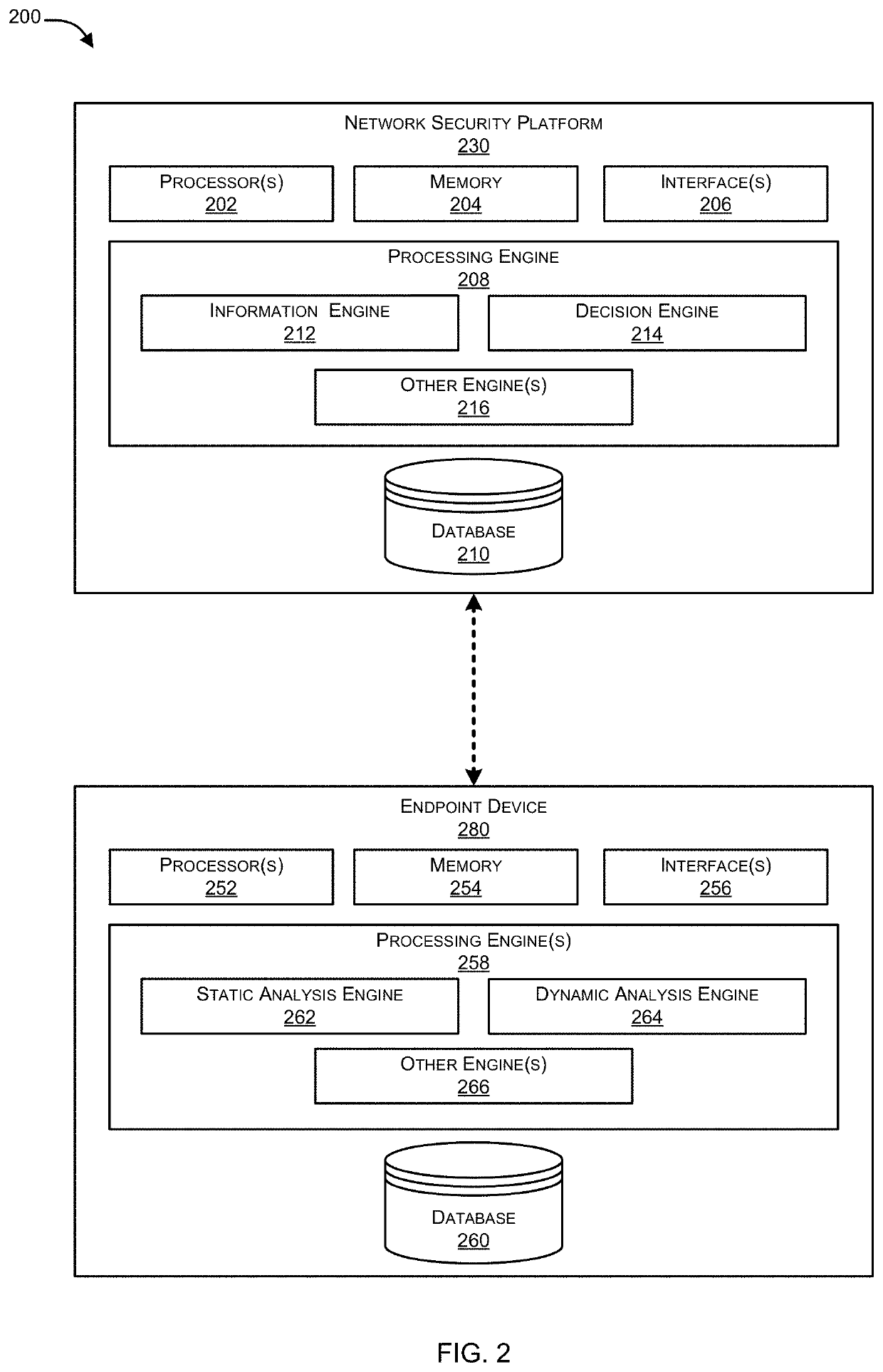
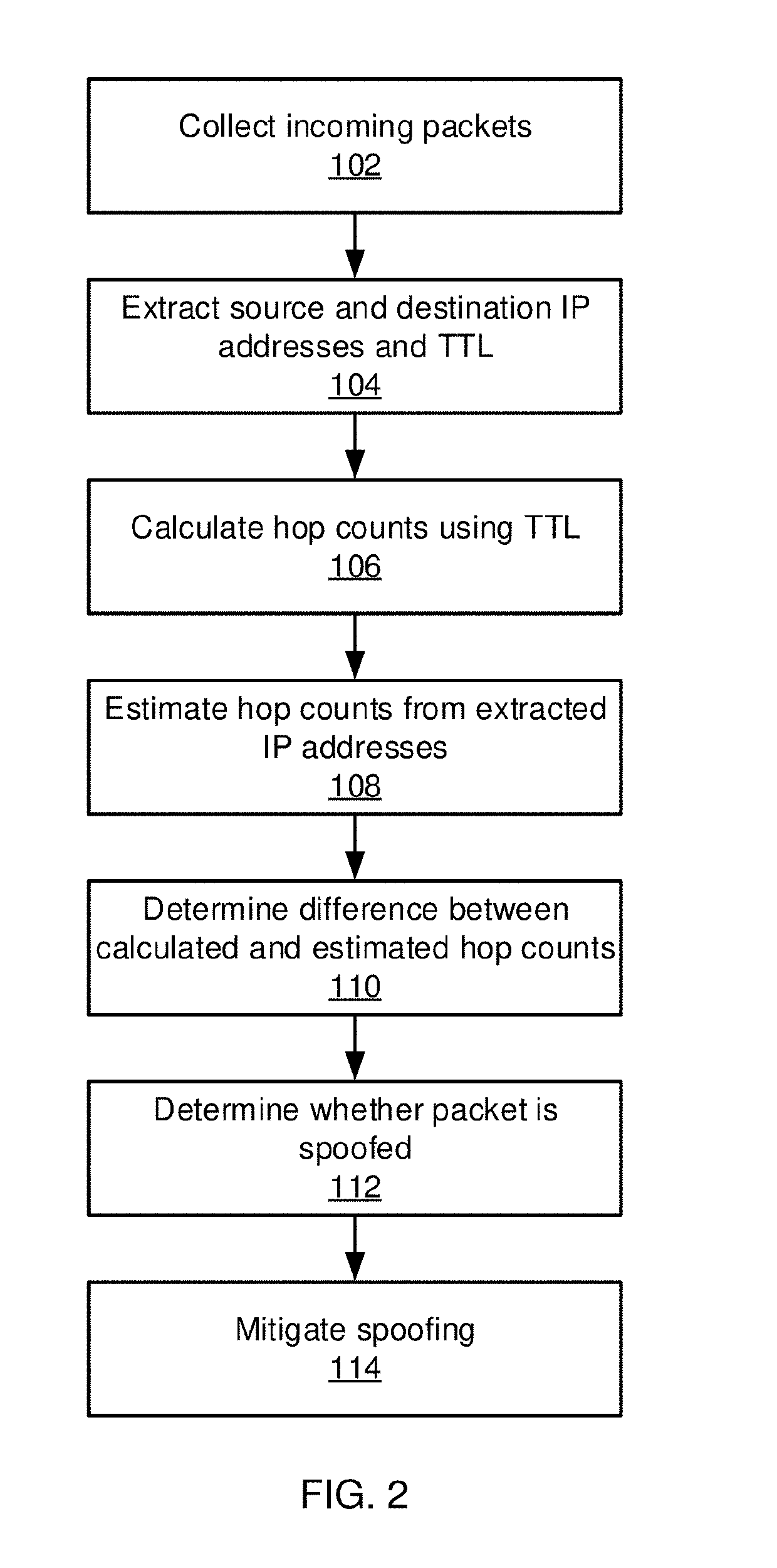
Endpoint security systems and methods include a distance estimation module configured to calculate a travel distance between a source Internet Protocol (IP) address and an IP address for a target network endpoint system from a received packet received by a network gateway system based on time-to-live (TTL) information from the received packet. A machine learning model is configured to estimate an expected travel distance between the source IP address and the target network endpoint system IP address based on a sparse set of known source / target distances. A spoof detection module is configured to determine that the received packet has a spoofed source IP address based on a comparison between the calculated travel distance and the expected travel distance. A security module is configured to perform a security action at the network gateway system responsive to the determination that the received packet has a spoofed source IP address.
Owner:NEC CORP
Network endpoint spoofing detection and mitigation
Endpoint security systems and methods include a distance estimation module configured to calculate a travel distance between a source Internet Protocol (IP) address and an IP address for a target network endpoint system from a received packet received by the target network endpoint system based on time-to-live (TTL) information from the received packet. A machine learning model is configured to estimate an expected travel distance between the source IP address and the target network endpoint system IP address based on a sparse set of known source / target distances. A spoof detection module is configured to determine that the received packet has a spoofed source IP address based on a comparison between the calculated travel distance and the expected travel distance. A security module is configured to perform a security action at the target network endpoint system responsive to the determination that the received packet has a spoofed source IP address.
Owner:NEC CORP
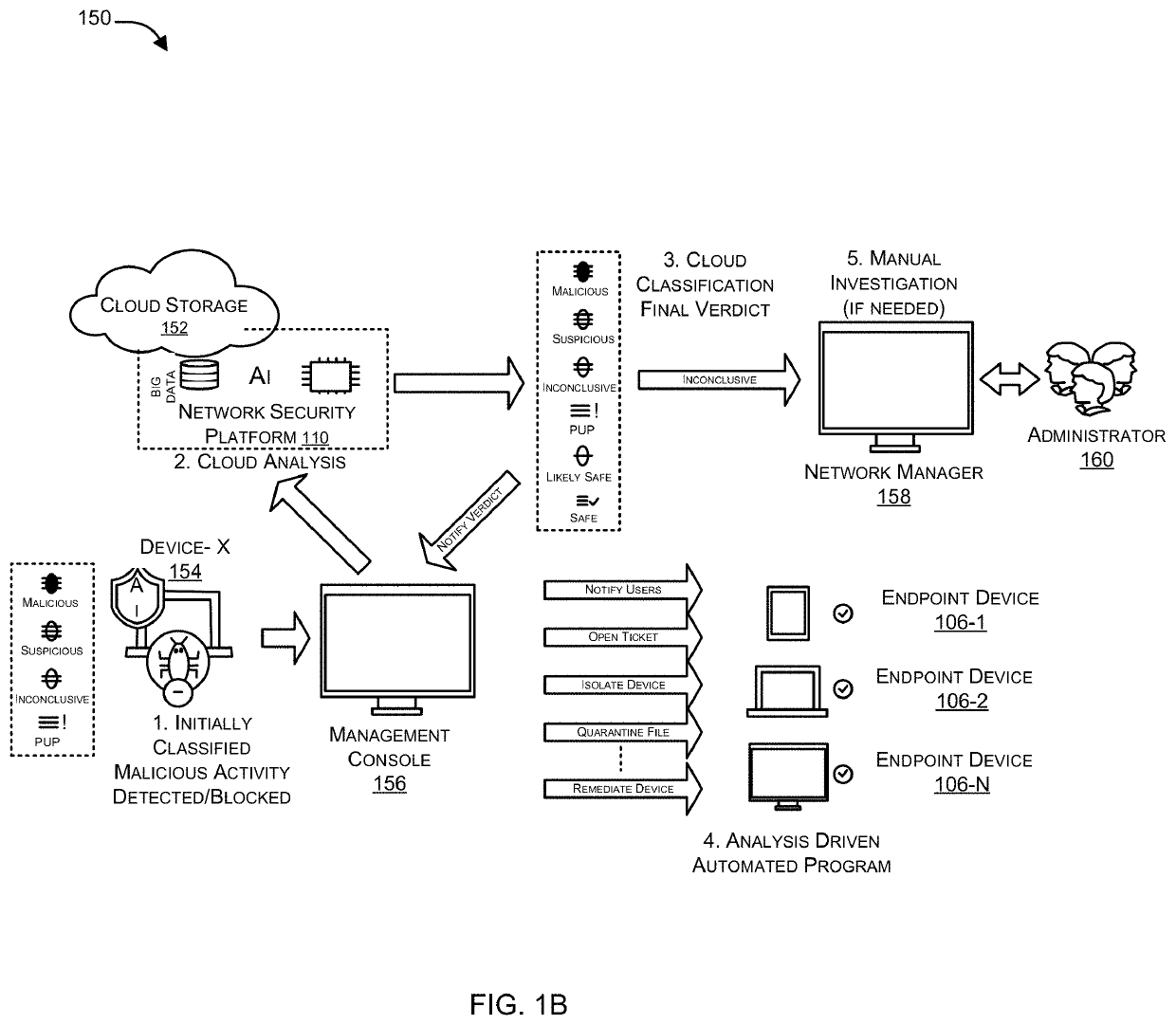
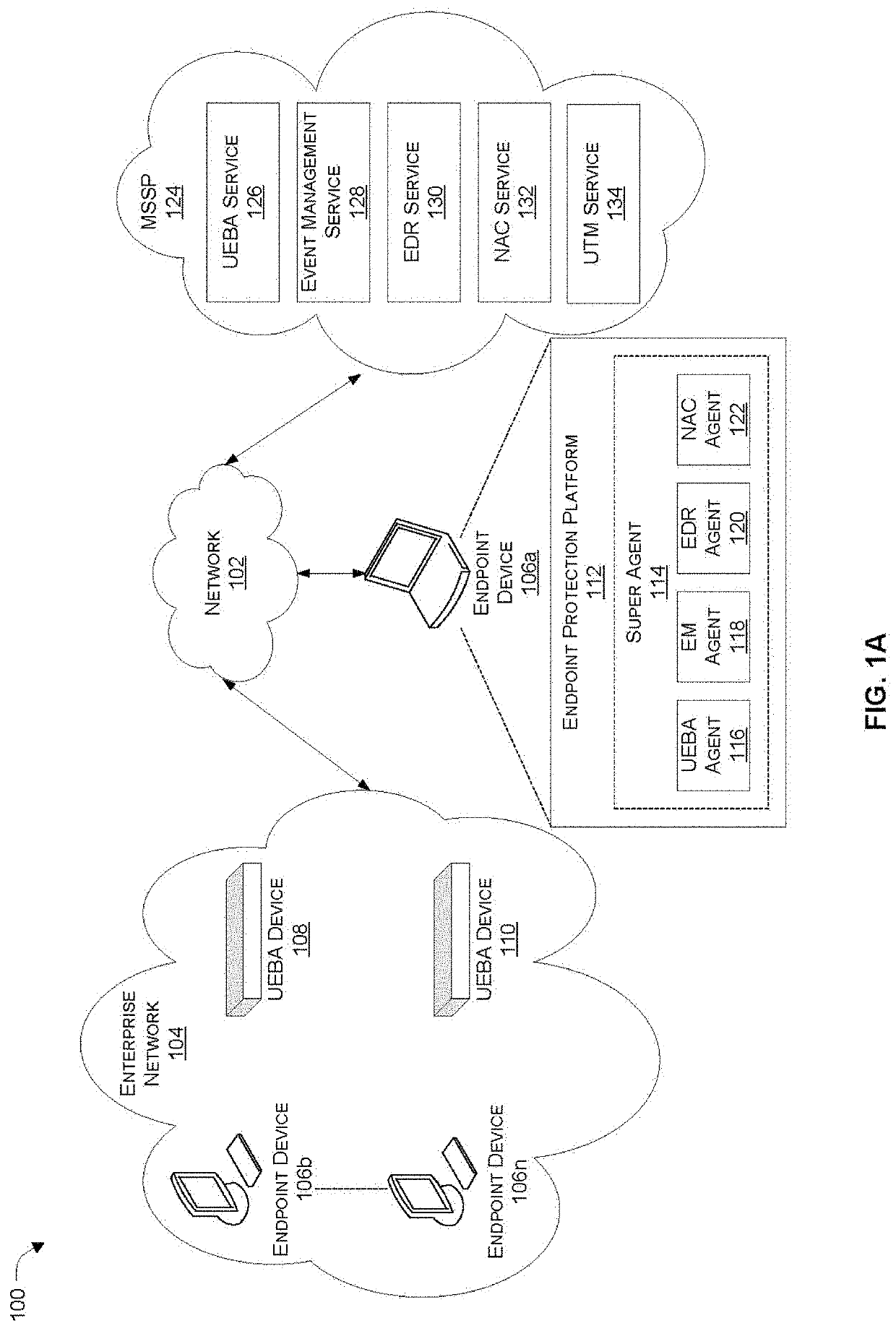
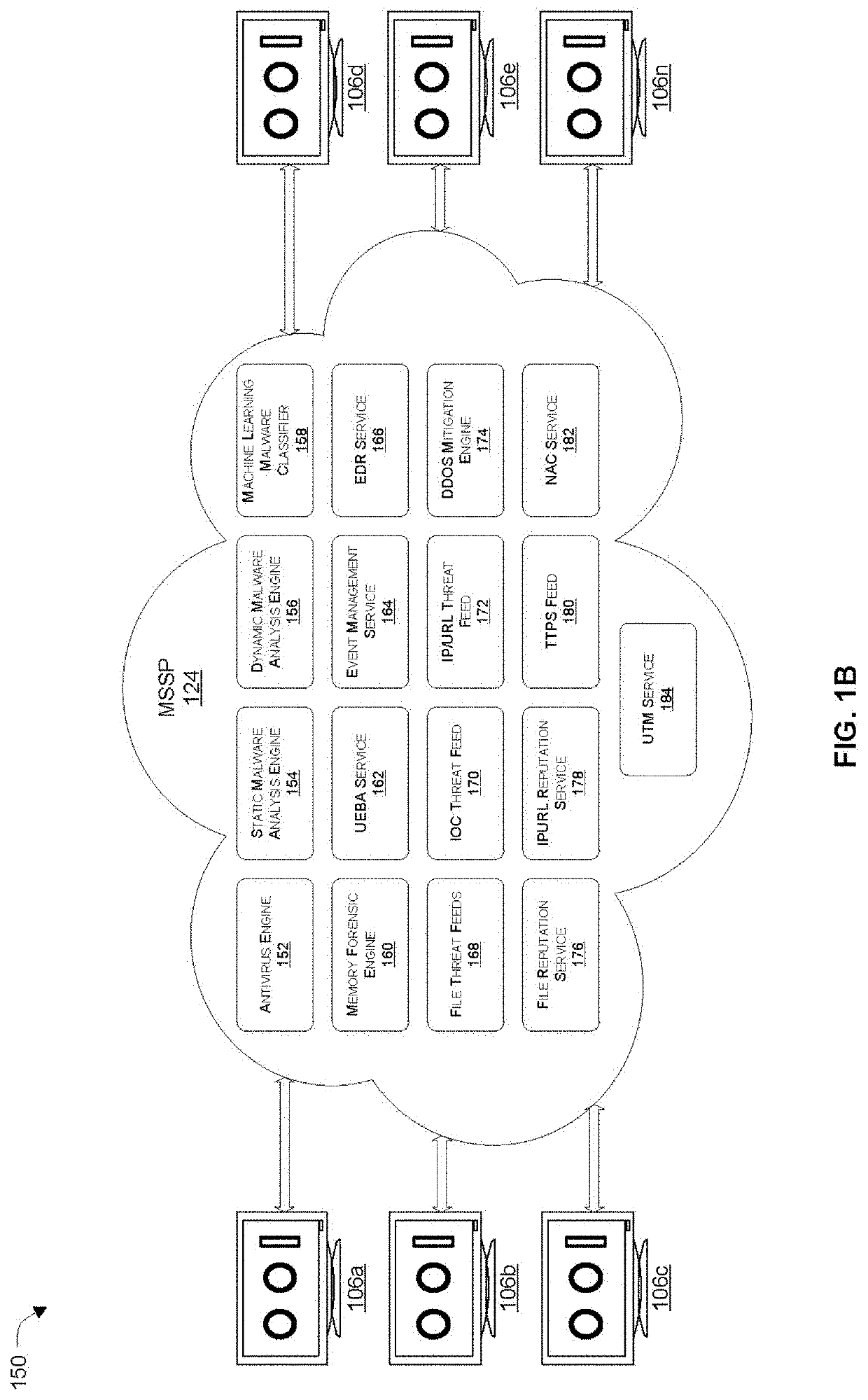
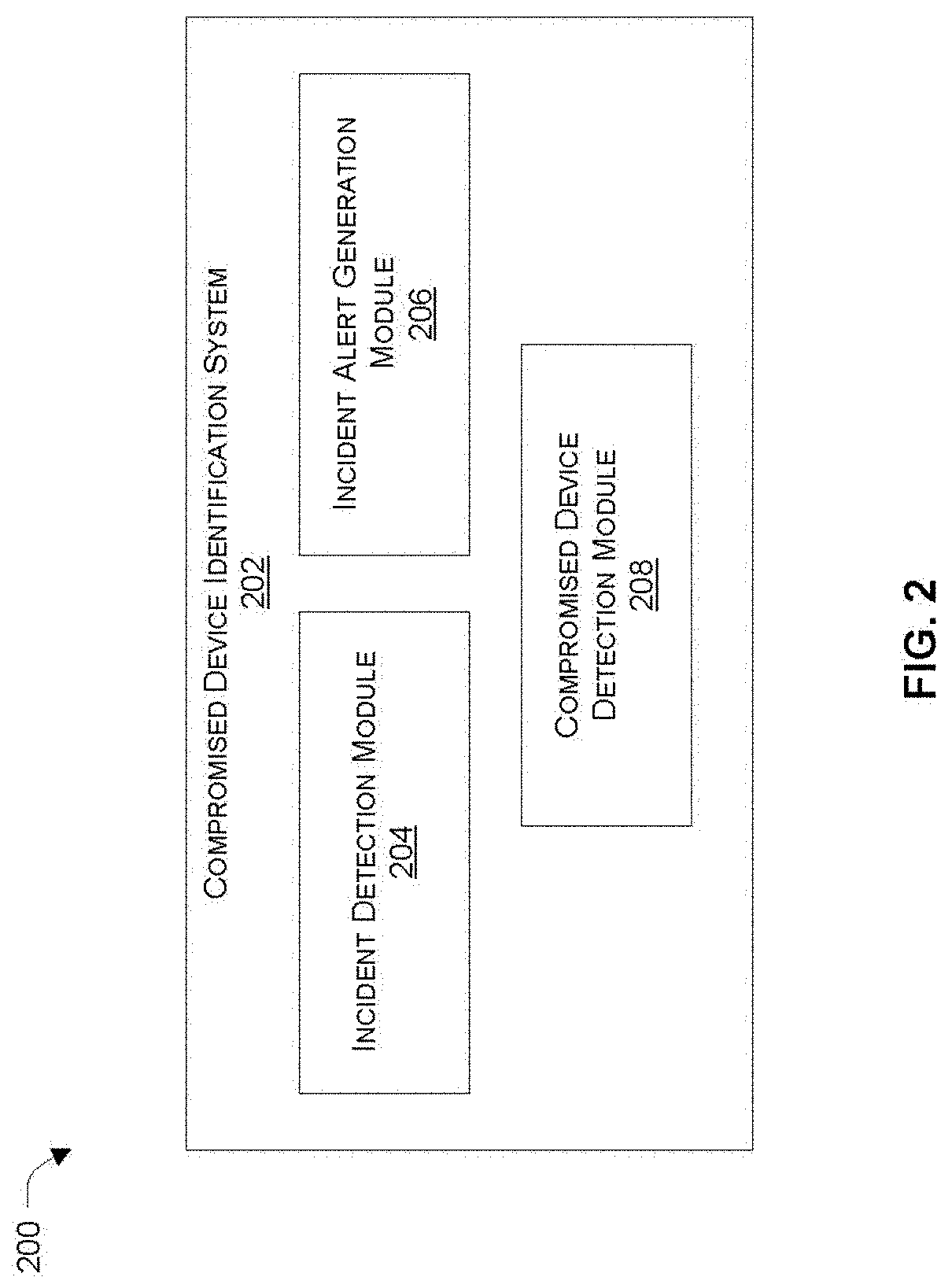
Facilitating identification of compromised devices by network access control (NAC) or unified threat management (UTM) security services by leveraging context from an endpoint detection and response (EDR) agent
Systems and methods are provided for synergistically combining network security technologies to detect compromised devices. According to one embodiment, an endpoint detection and response (EDR) agent of multiple endpoint security agents running on an endpoint device detects an incident. A security incident alert is generated by the EDR agent by proactively collecting data regarding the incident. Identification of a device coupled to a private network as potentially being compromised by a security service of a Managed Security Service Provider (MSSP) protecting the private network is facilitated by the EDR agent transmitting the security incident alert to the security service via a security agent of the multiple endpoint security agents corresponding to the security service.
Owner:FORTINET
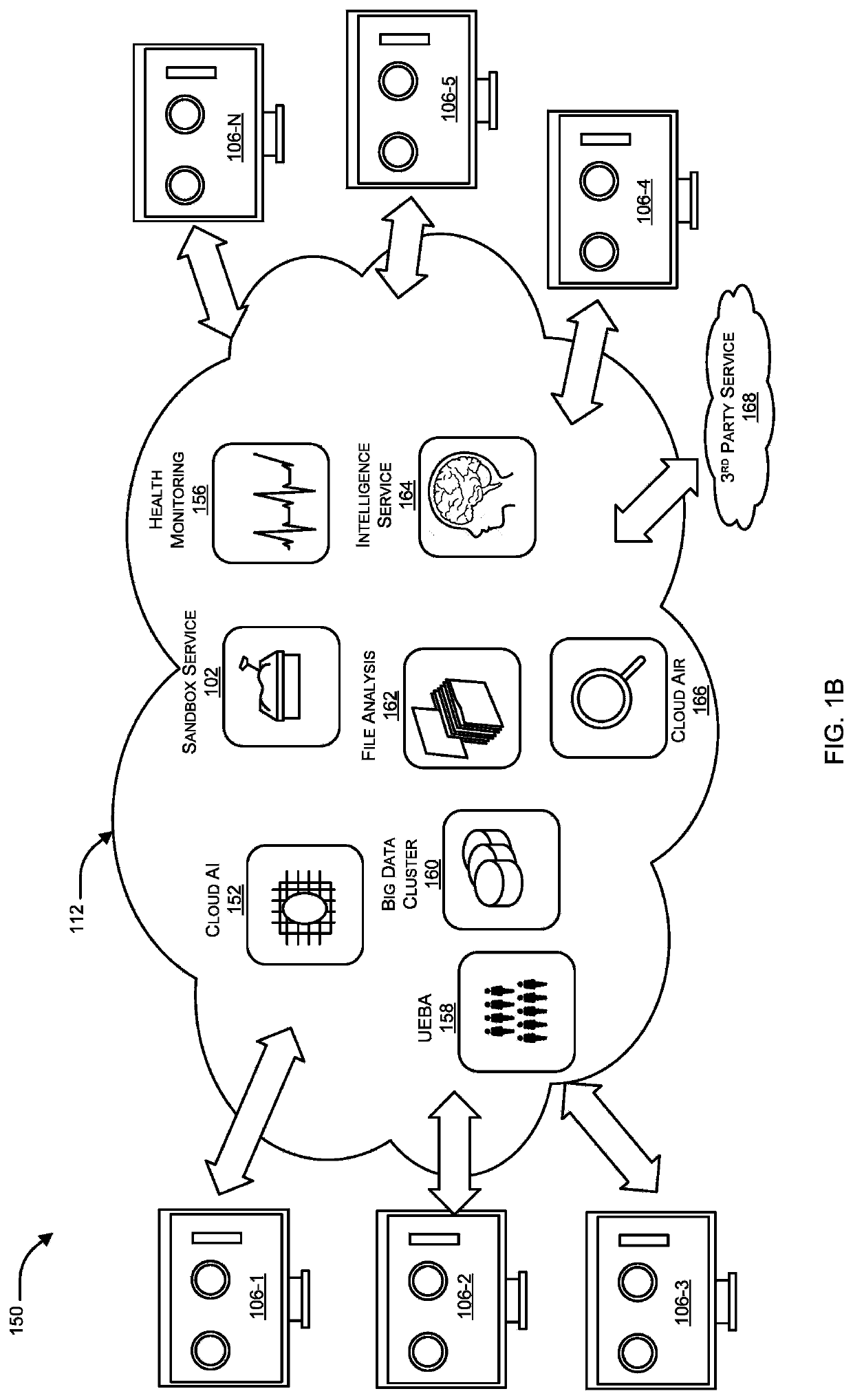
Malware detection by a sandbox service by utilizing contextual information
InactiveUS20210200859A1Improving malware detectionPlatform integrity maintainanceBusiness enterpriseSoftware engineering
Systems and methods for improving malware detection by a sandbox service by utilizing Endpoint Detection and Response (EDR) origin contextual information are provided. According to an embodiment, a sandbox service associated with a network security platform protecting an enterprise network receives a file associated with sandbox-evading malware, to be classified by the sandbox service, and contextual information related to the file. The file is received from an endpoint security solution of the network security platform running on an endpoint device of the enterprise network. The sandbox service classifies the file as being malware by detonating the sandbox-evading malware as a result of performing sandboxing on the file including emulating an environment of the endpoint device based on the contextual information.
Owner:FORTINET
Automated configuration of endpoint security management
ActiveUS20160044114A1Digital computer detailsData switching networksPrivate networkEndpoint security
Systems and methods for managing configuration of a client security application based on a network environment in which the client device is operating are provided. According to one embodiment, a network connection state of a client device with respect to a private network is determined by a client security application running on the client device. The client security application, then selects a configuration based on the determined network connection state. Finally, the client security application launches one or more functions of the client security application that are designated by the selected configuration.
Owner:FORTINET
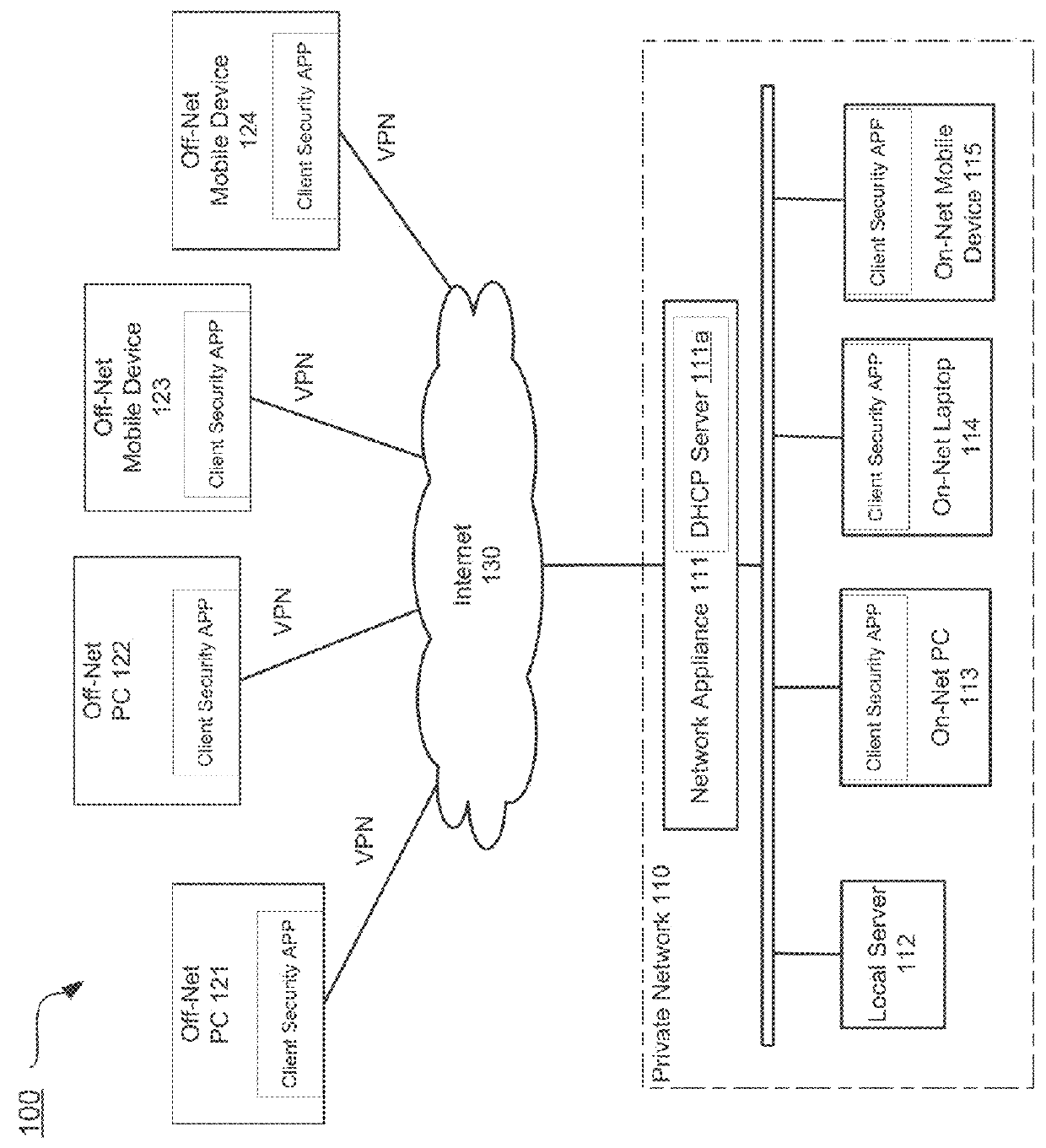
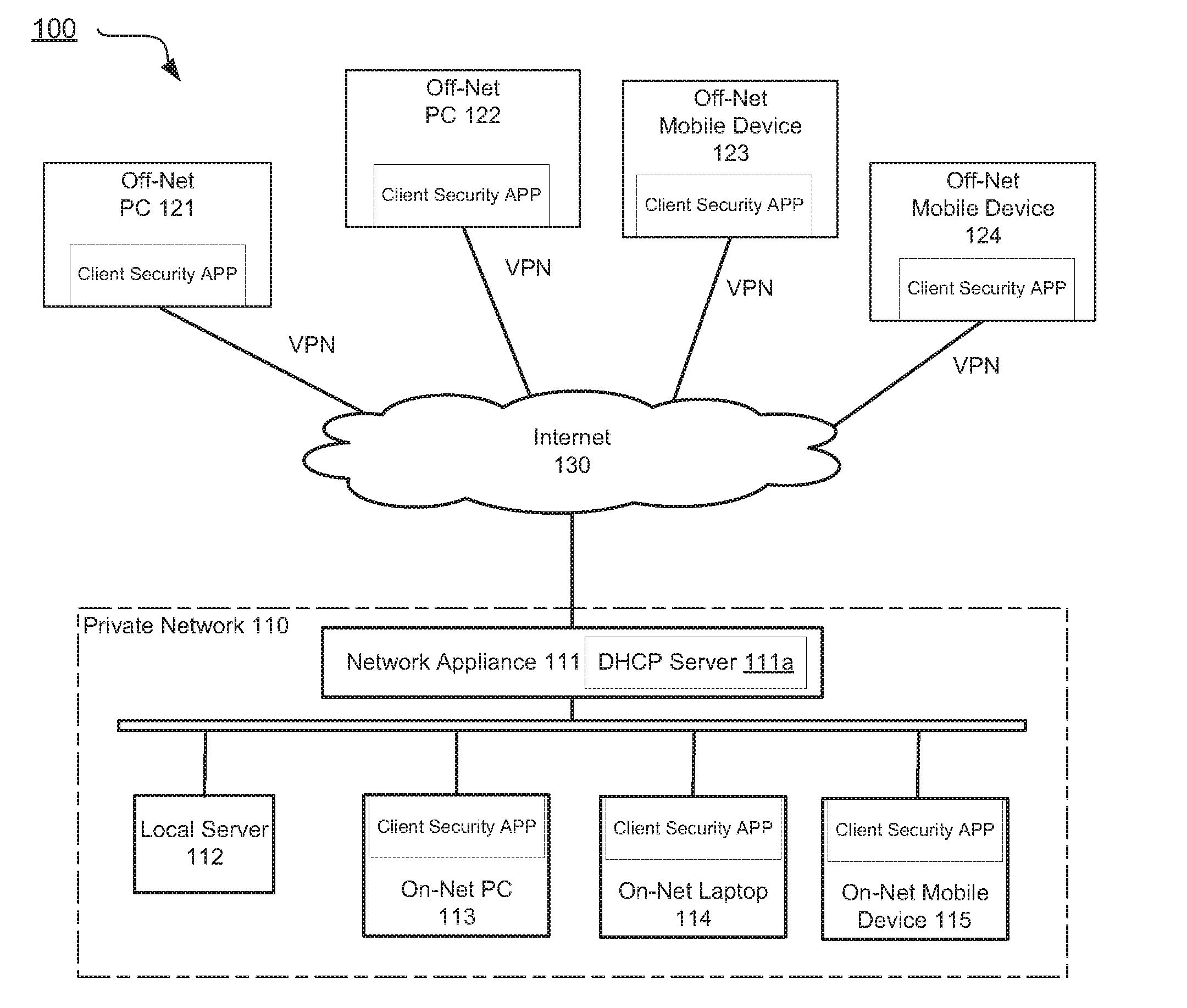
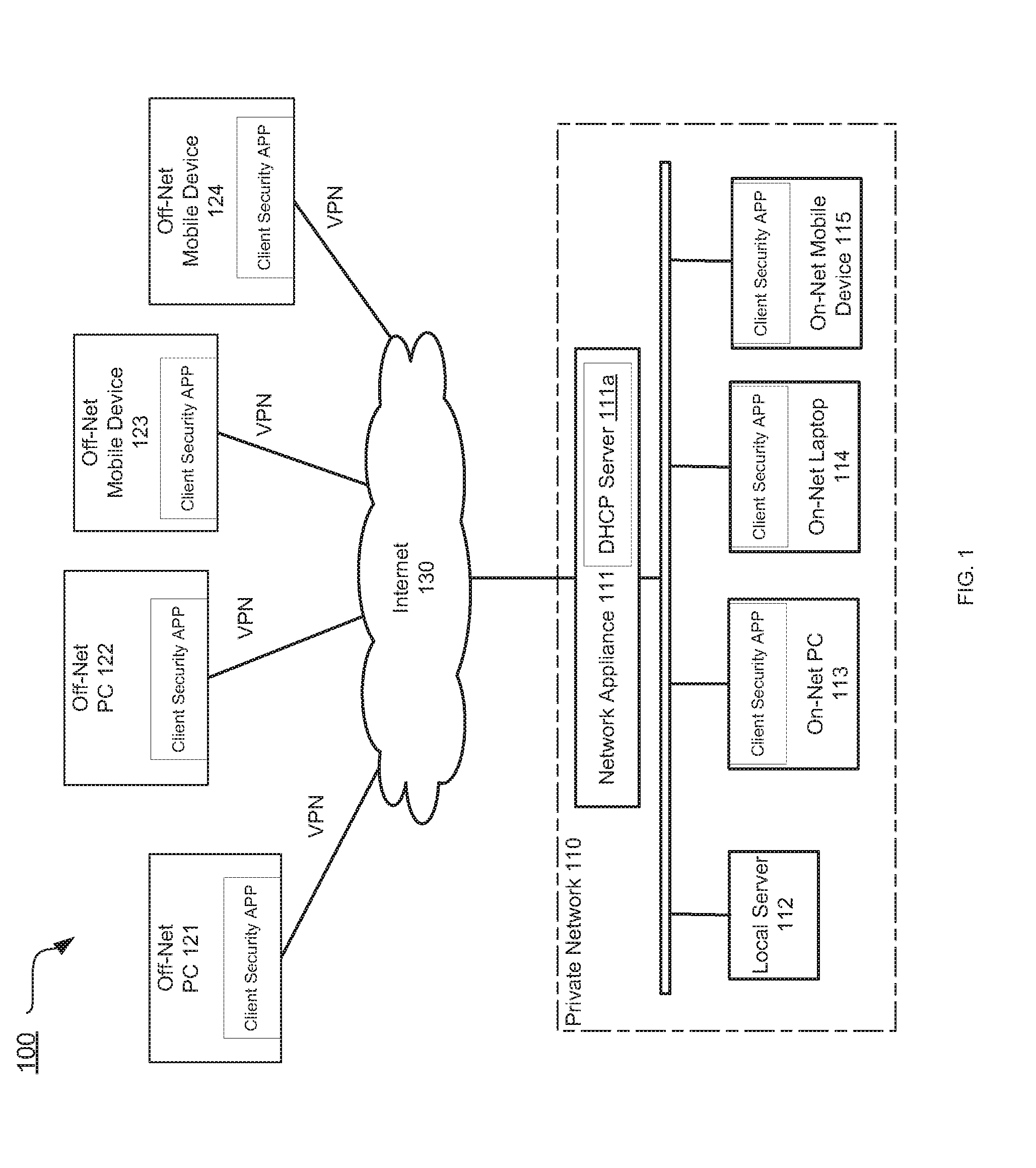
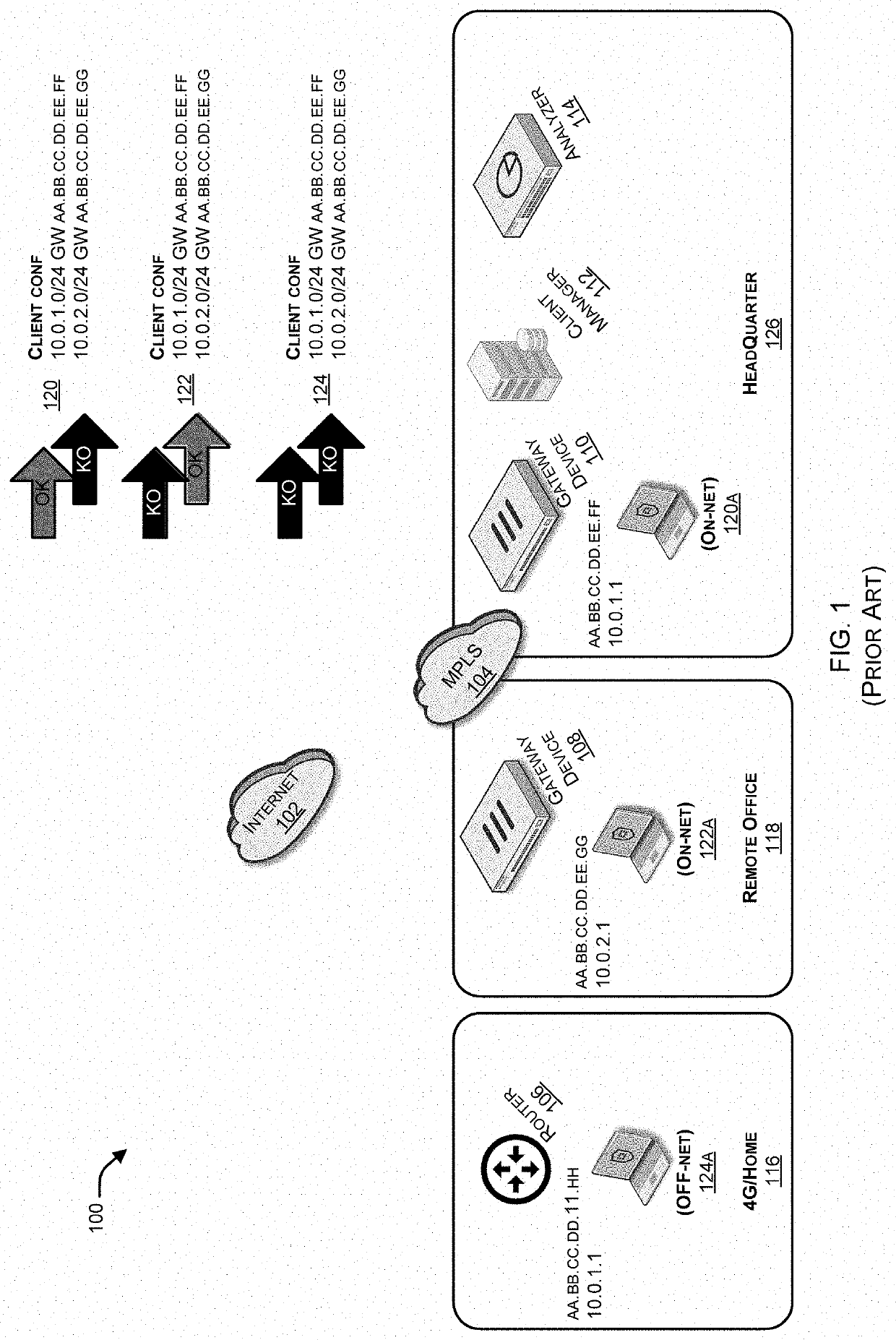
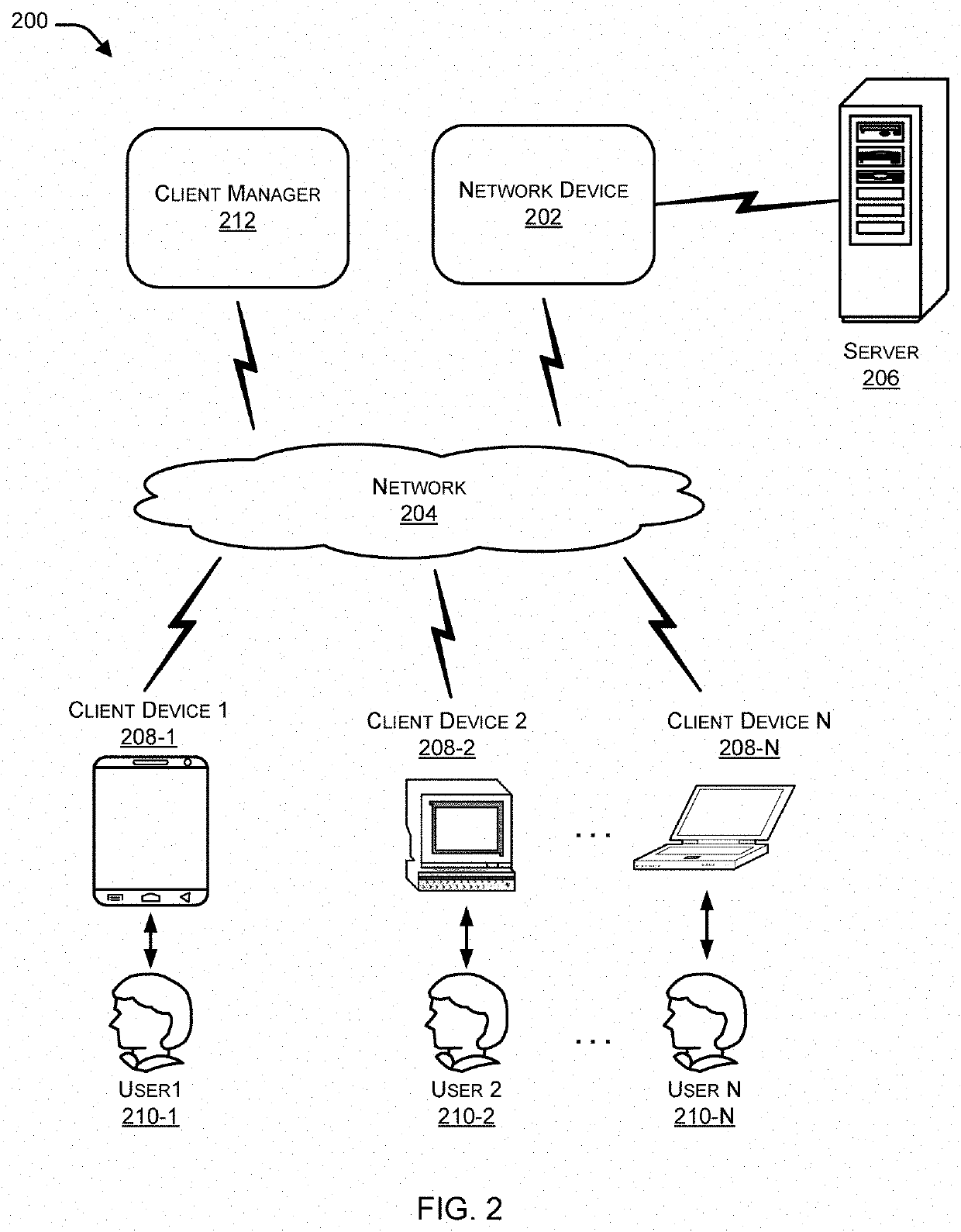
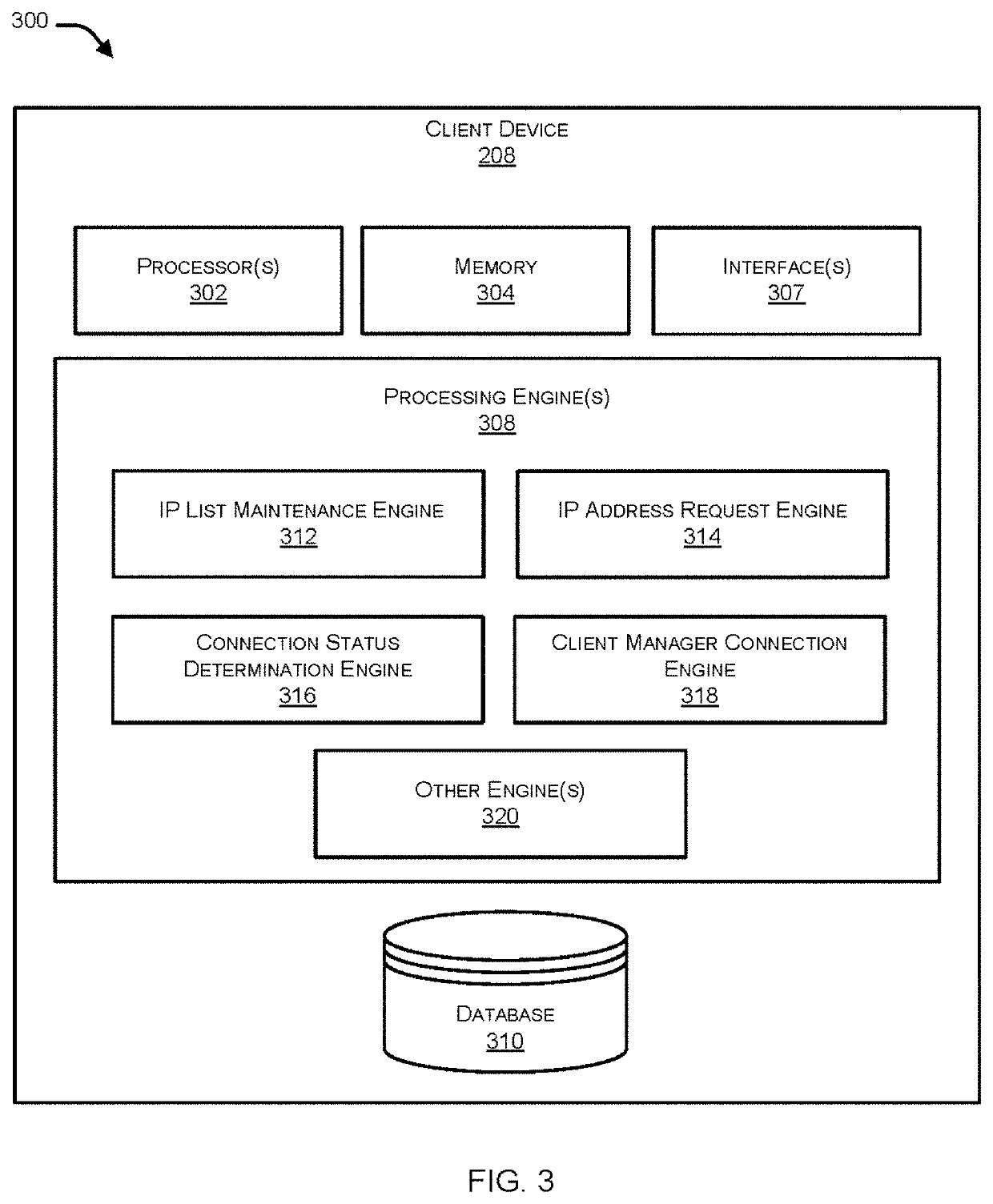
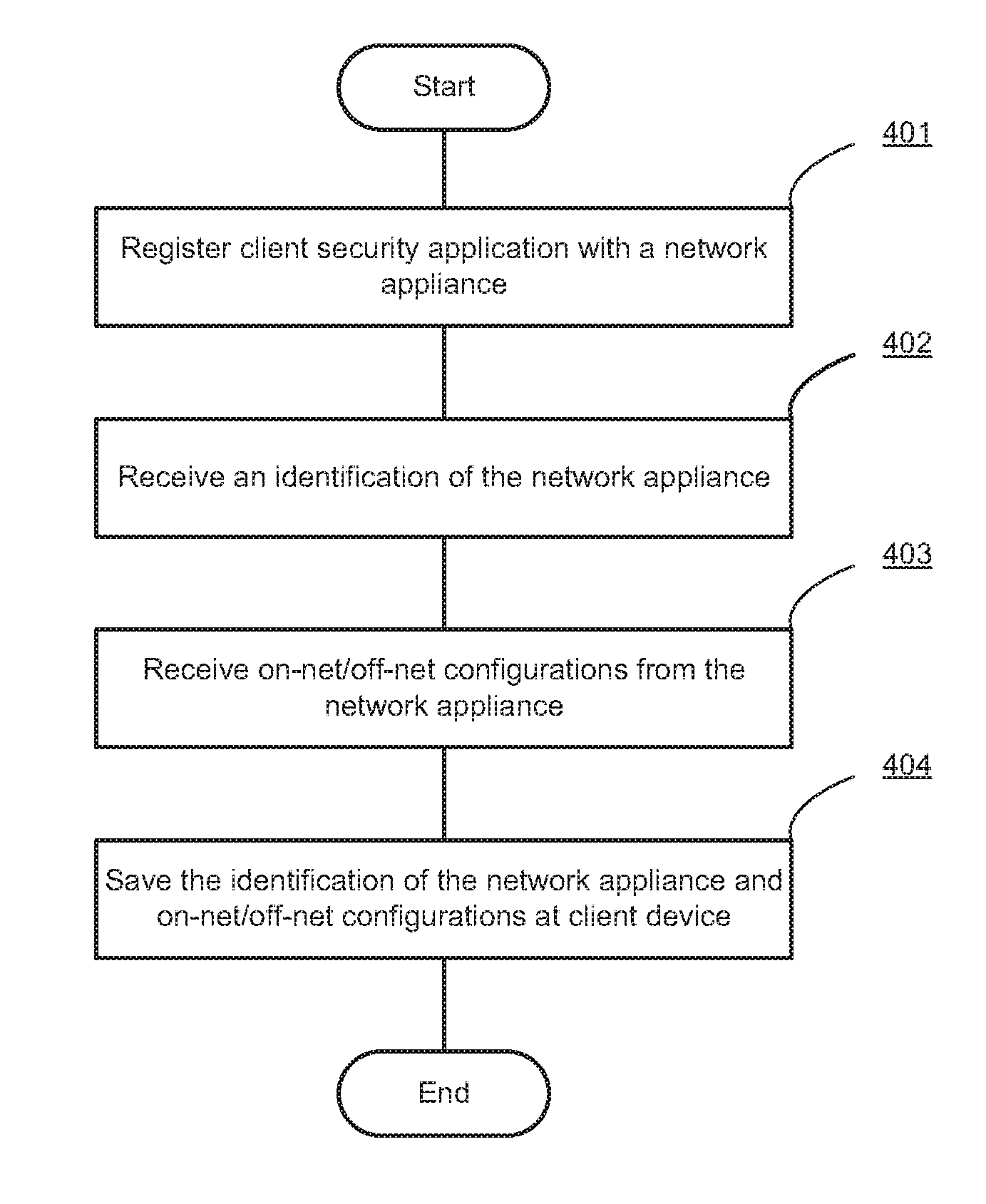
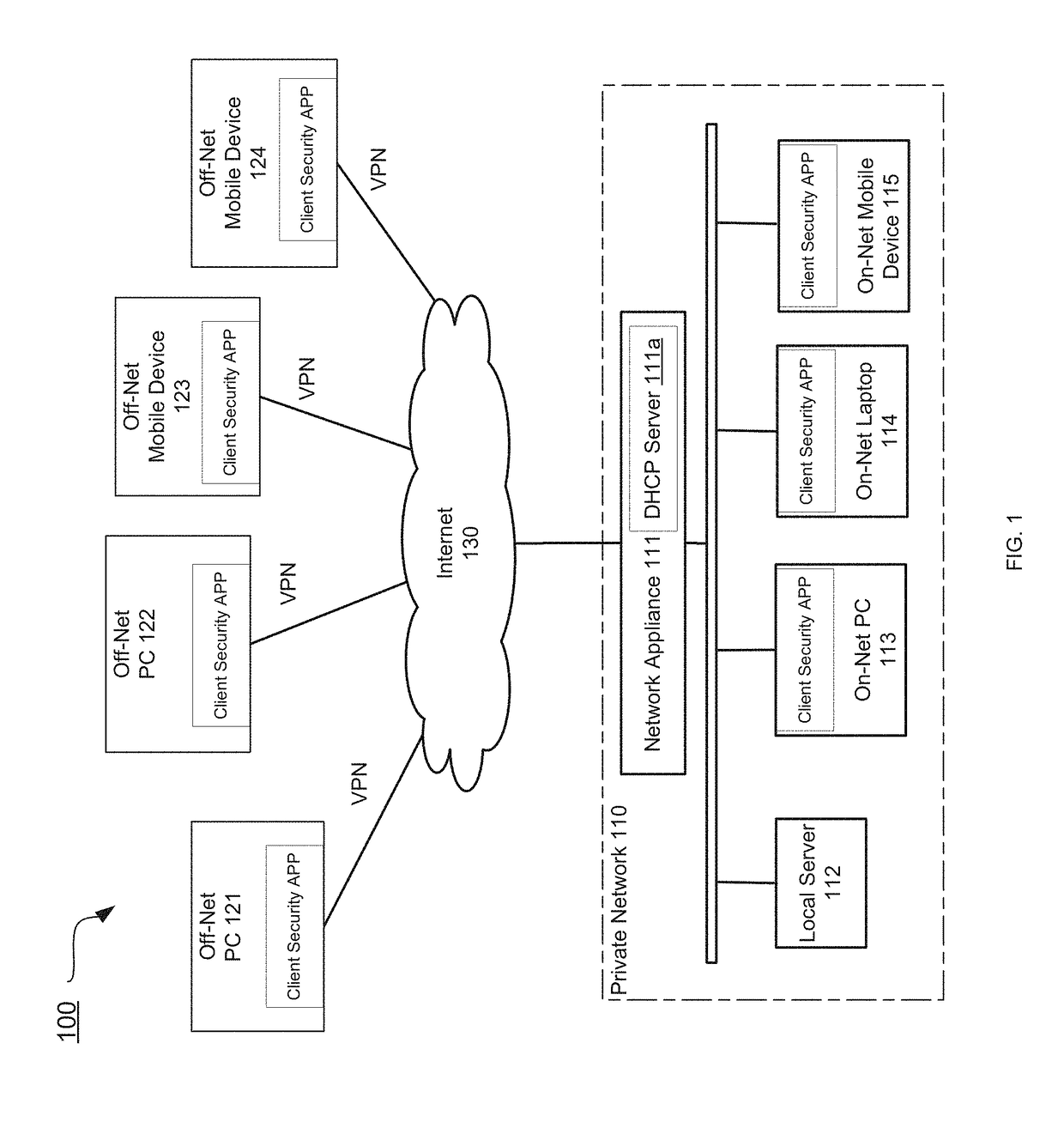
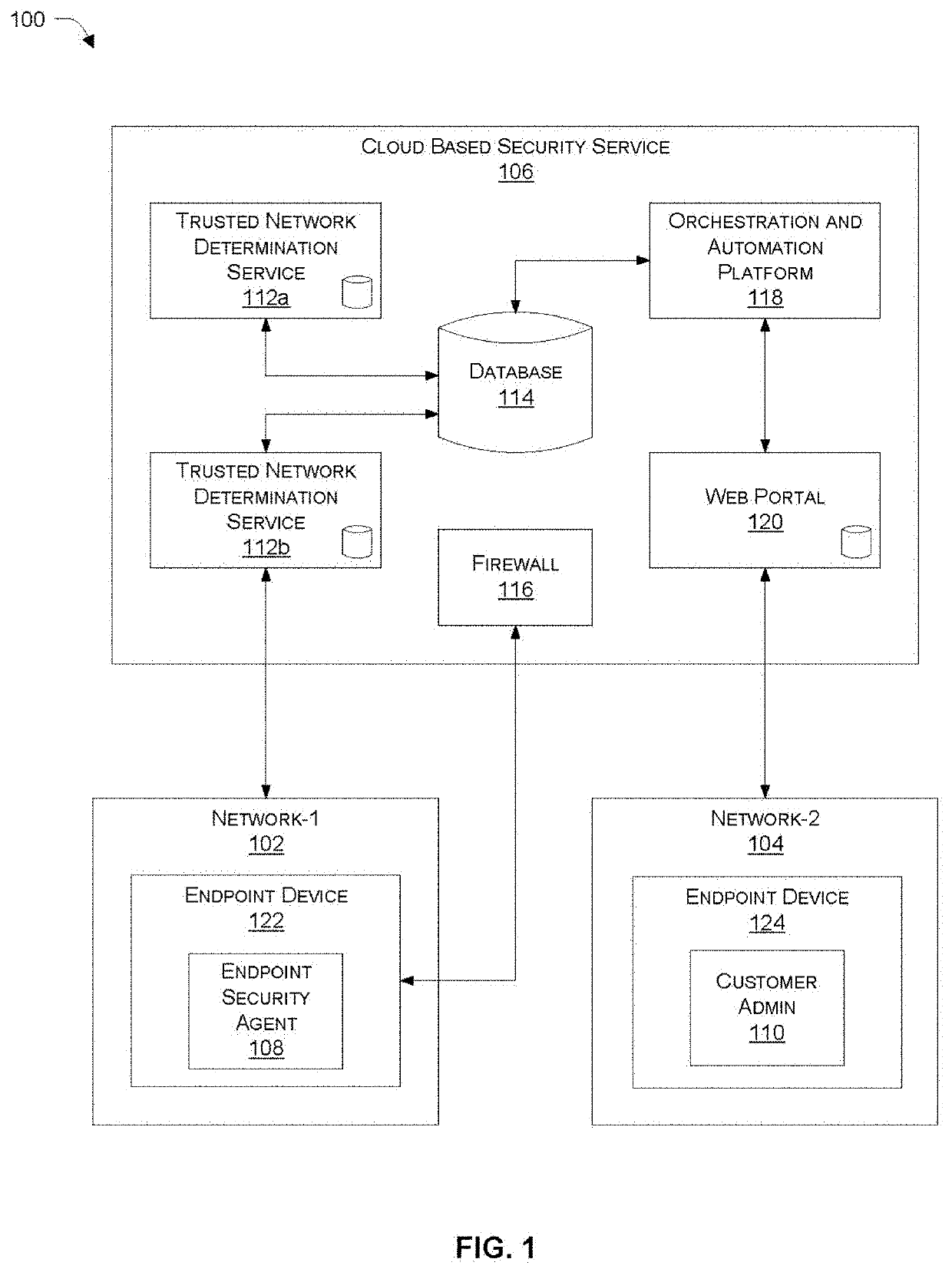
Determining on-net/off-net status of a client device
Systems and methods are described for determining an on-net / off-set status of a client device. An endpoint security program running on the client device maintains an enterprise public Internet Protocol (IP) list containing one or more ranges of public IP addresses associated with an enterprise network. Further, the endpoint security program sends a request to a cloud-based service for information regarding a public IP address of the client device. In response to the request, the endpoint security program receives from the cloud-based service a response containing the public IP address and determines a connection status of the client device with respect to the enterprise network by comparing the public IP address to the enterprise public IP list.
Owner:FORTINET
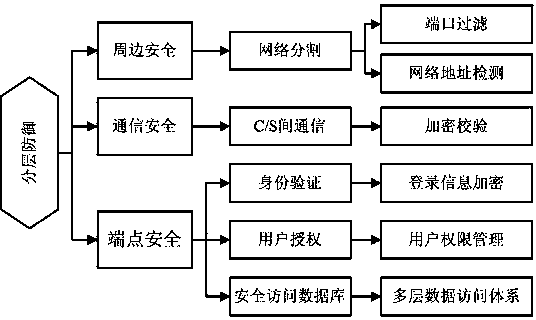
Method for improving security of user management system by adopting layering defense mode
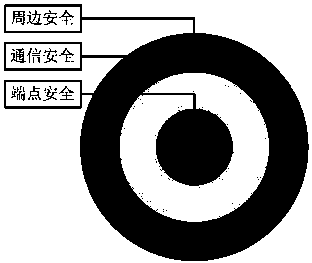
InactiveCN104065668AImprove performanceImprove securityData switching networksCommunications securityEndpoint security
The invention relates to a method for improving the security of a user management system by adopting a layering defense mode. According to the method, the layering defense mode is adopted for guaranteeing the security of the user management system, proper modes are adopted for many places in a network of the user management system to improve the security, and attacks are resisted from three aspects comprising the peripheral security, the terminal vertex security and the communication security, so that the system is flexible when resisting the hacker attacks, and the problem that single-point defense is breached easily can be effectively solved. According to the method, a mode of improving the security is purposefully adopted for the different areas of the network of the user management system, and the method has the advantages that the performance is stable and reliable, the security is high, and the influence on the system performance is small.
Owner:FUZHOU UNIV
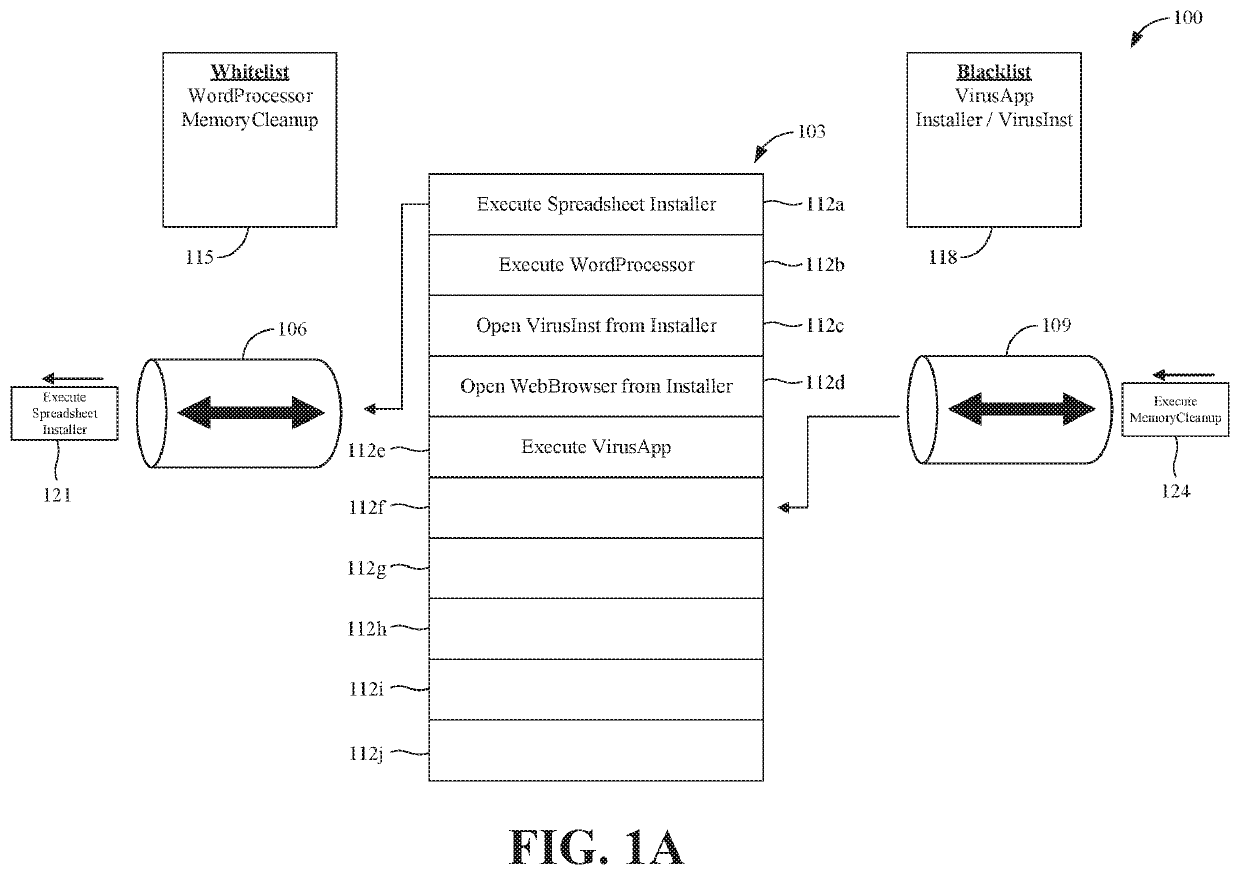
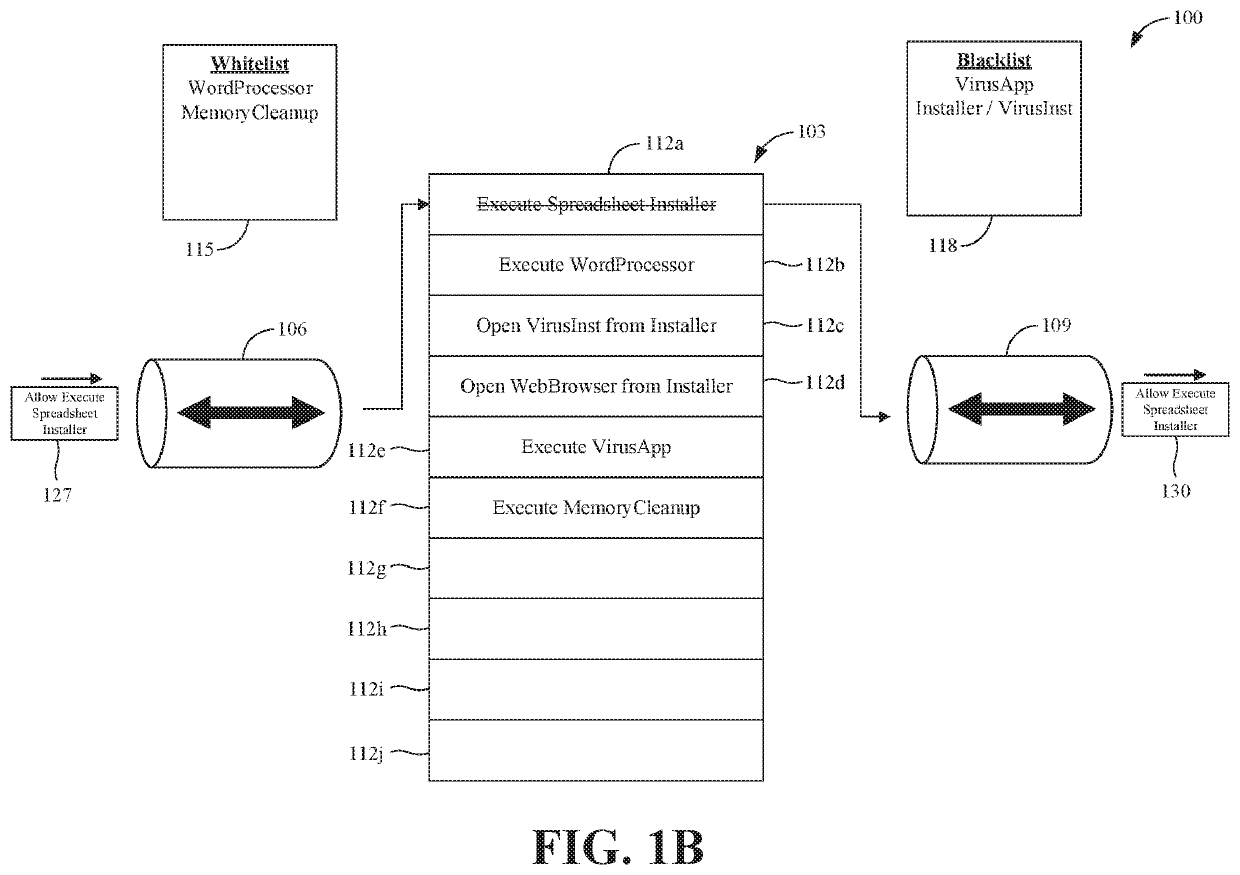
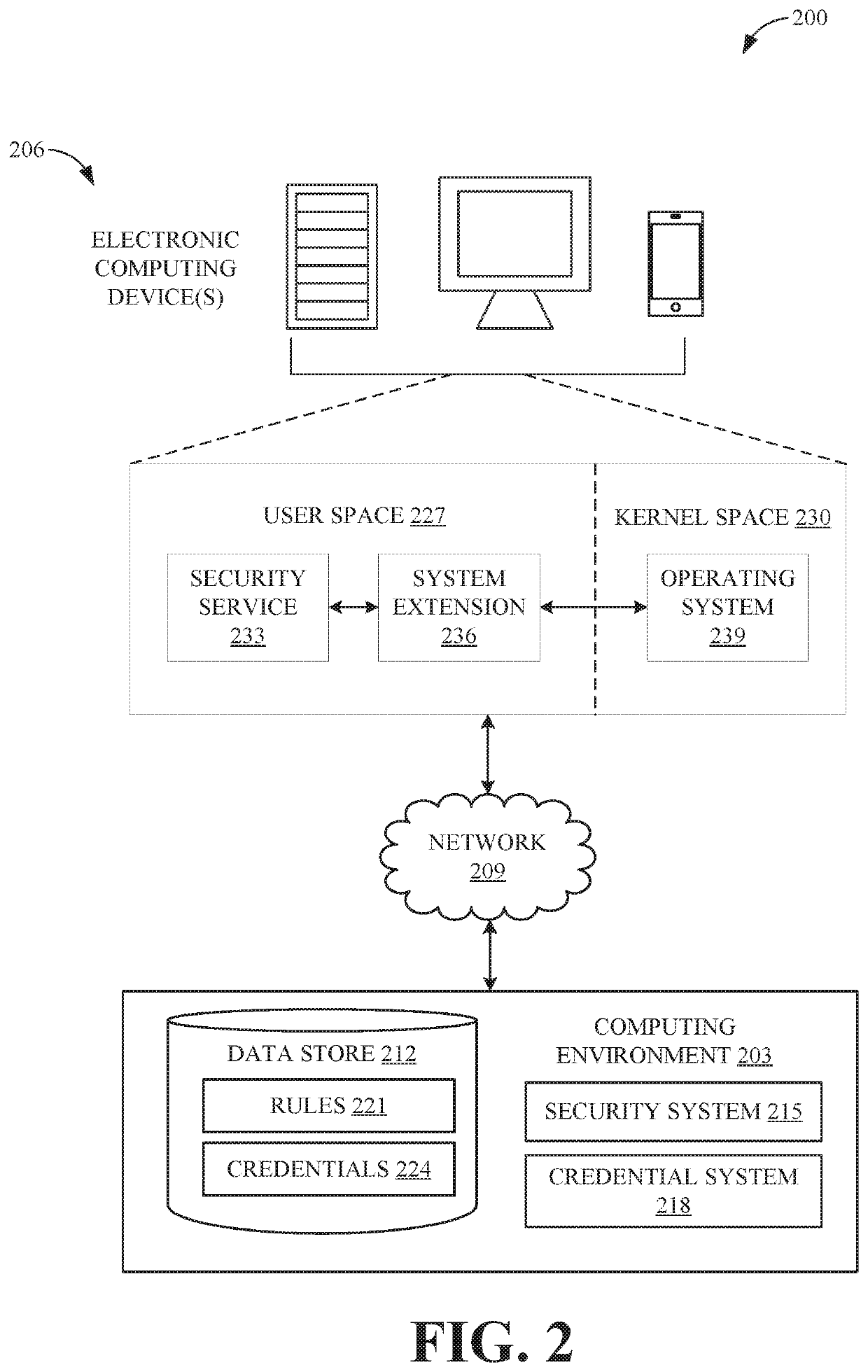
Systems and methods for event-based application control
ActiveUS20200394295A1Interprogram communicationPlatform integrity maintainanceOperational systemEvent type
Systems and methods are disclosed for event-based application control. A system extension is configured to leverage an endpoint security API for monitoring event activity within operating system kernel processes. The system extension registers with the endpoint security API particular event types for which the system extension would like to receive notifications. In response to receiving notifications regarding detected events corresponding to the registered event types, the system extension determines if the event, and its corresponding process, are safe and allowable to execute. In various embodiments, the system leverages whitelists, blacklists, and rules policies for making a safeness determination regarding the event notification. The system extension transmits this determination to the operating system via the endpoint security API.
Owner:BEYONDTRUST SOFTWARE
Automated configuration of endpoint security management
ActiveUS20150341311A1Multiple digital computer combinationsProgram controlPrivate networkEndpoint security
Systems and methods for managing configuration of a client security application based on a network environment in which the client device is operating are provided. According to one embodiment, a network connection state of a client device with respect to a private network is determined by a client security application running on the client device. The client security application, then selects a configuration based on the determined network connection state. Finally, the client security application launches one or more functions of the client security application that are designated by the selected configuration.
Owner:FORTINET
Automated configuration of endpoint security management
Systems and methods for managing configuration of a client security application based on a network environment in which the client device is operating are provided. According to one embodiment, a network connection state of a client device with respect to a private network is determined by a client security application running on the client device. The client security application, then selects a configuration based on the determined network connection state. Finally, the client security application launches one or more functions of the client security application that are designated by the selected configuration.
Owner:FORTINET
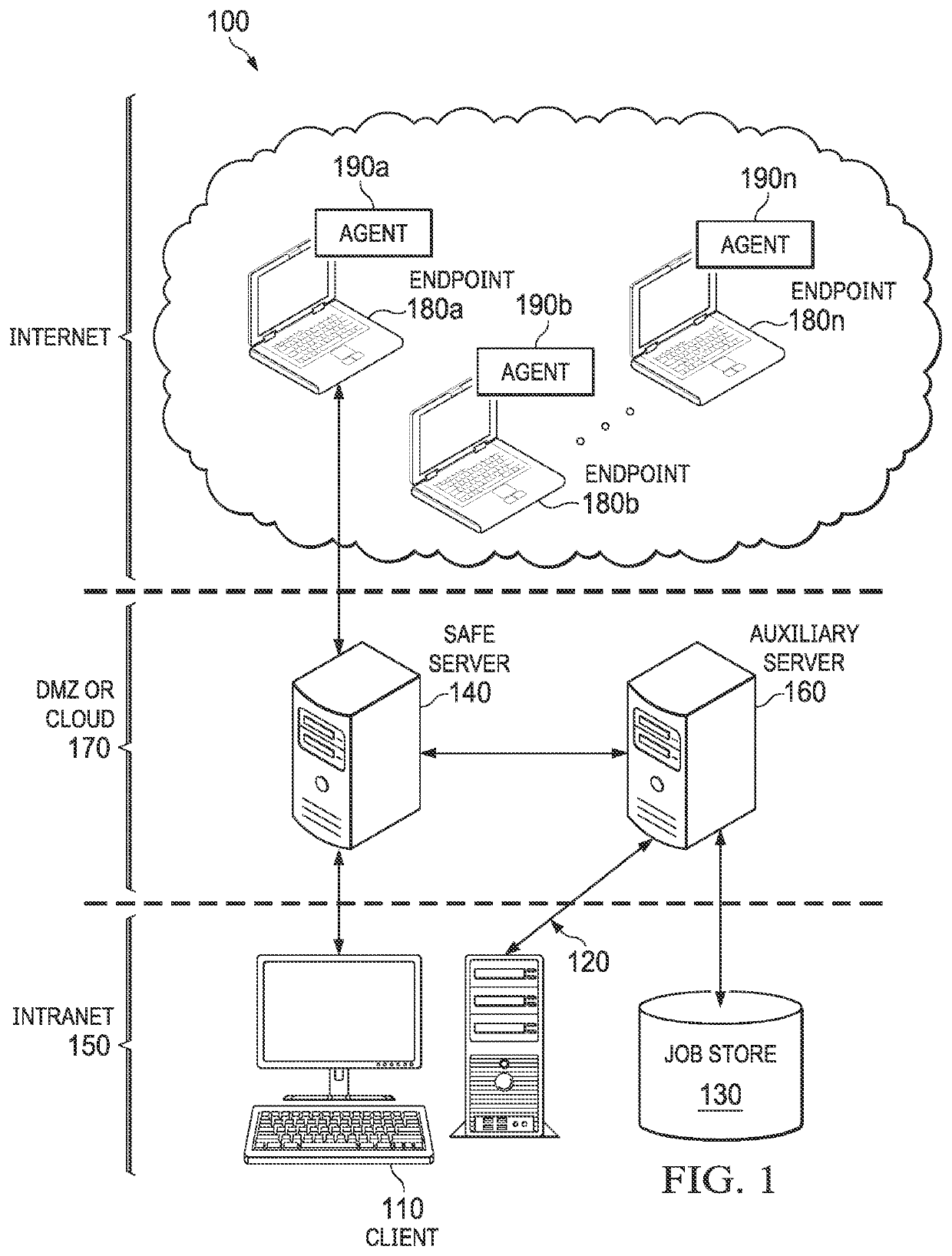
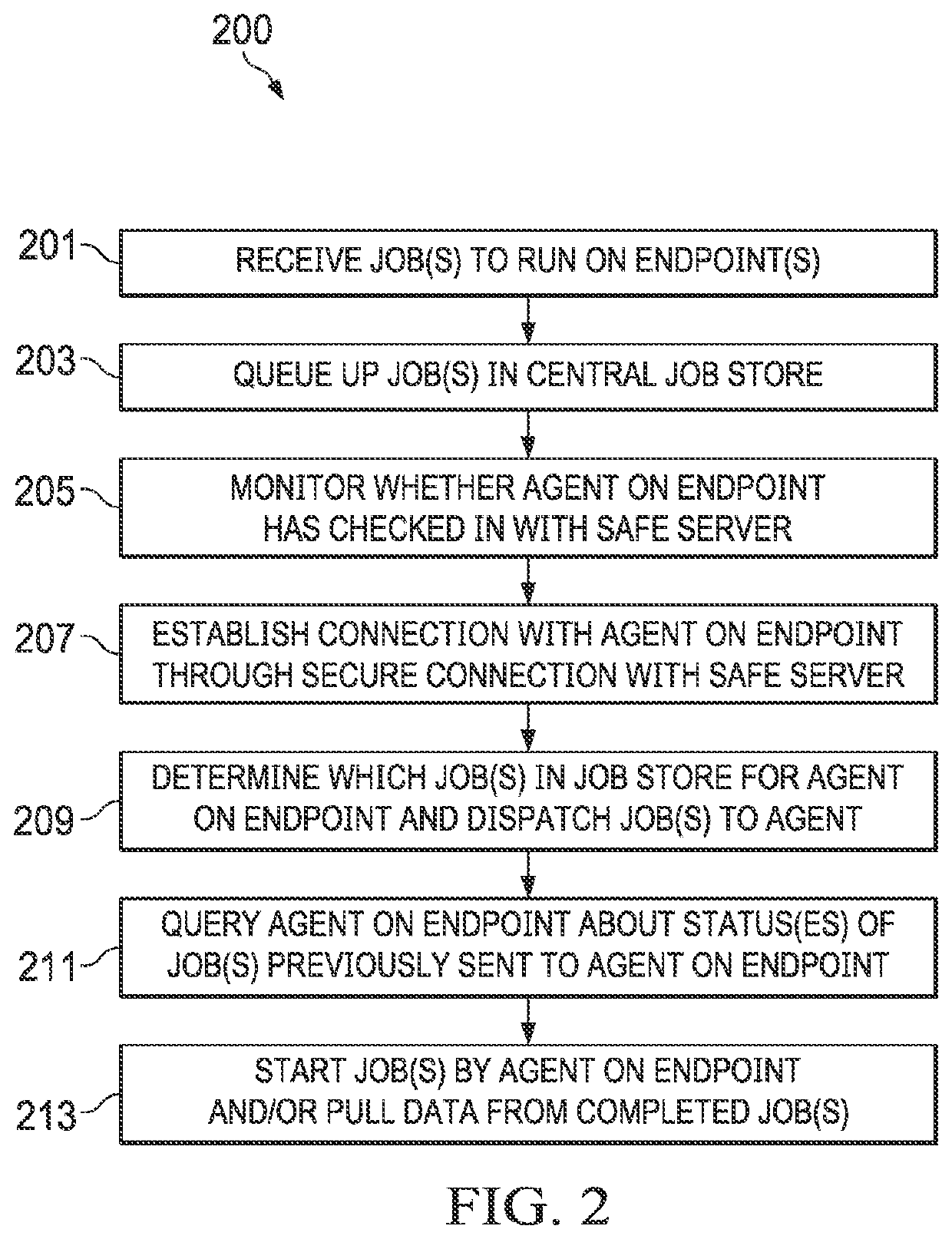
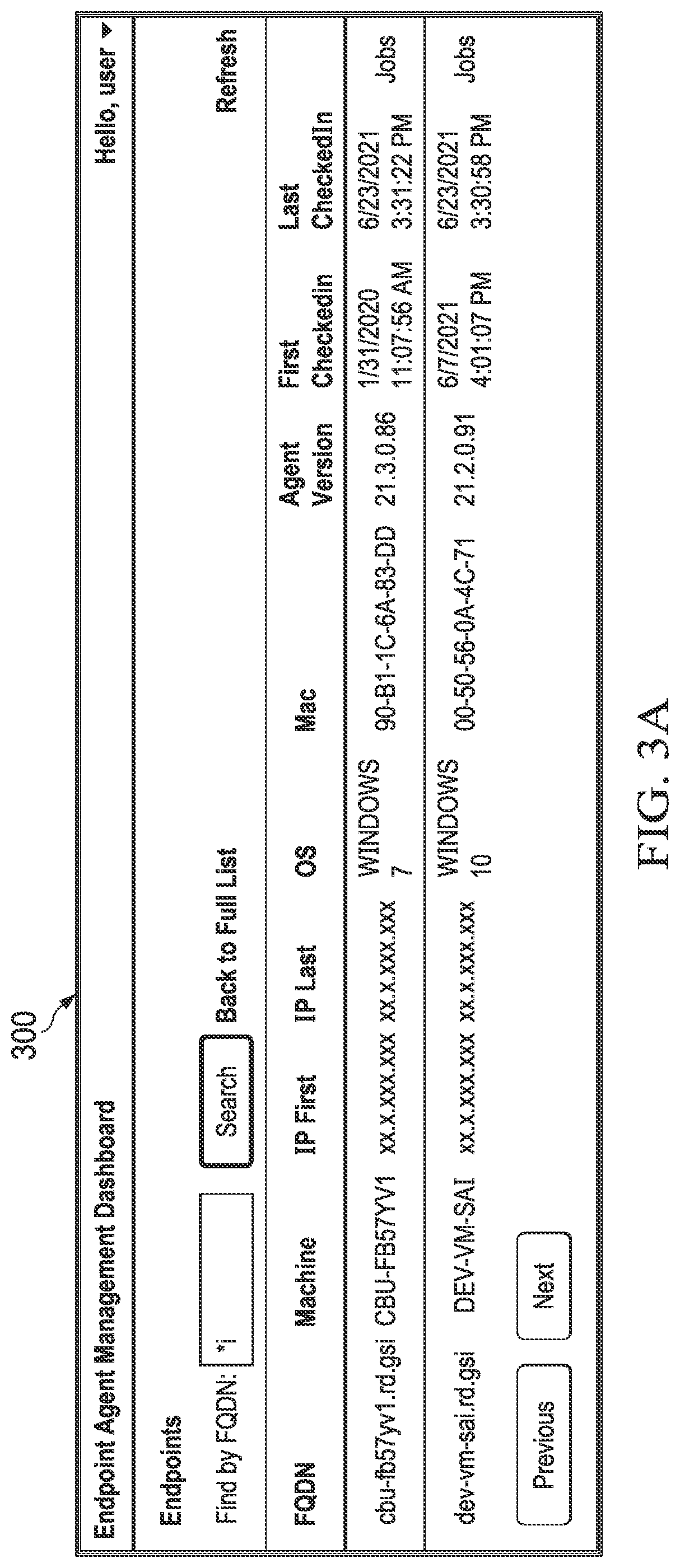
Endpoint agent management systems and methods for remote endpoint security
An endpoint security system having a Secured Authentication For Enterprise (SAFE) server is enhanced with an auxiliary service. The auxiliary service receives a request to run a job on an endpoint of an enterprise computer network, queues up the job in a central job store, and monitors whether an agent on the endpoint has checked in with the SAFE server. Responsive to the agent on the endpoint checking in with the SAFE server, the auxiliary service establishes, through a secure connection with the SAFE server, a connection with the agent on the endpoint and determines whether the agent has any jobs queued up in the central job store. If so, the auxiliary service dispatches the job from the central job store to the agent on the endpoint through the secure connection with the SAFE server and starts the job by the agent on the endpoint.
Owner:OPEN TEXT HLDG INC
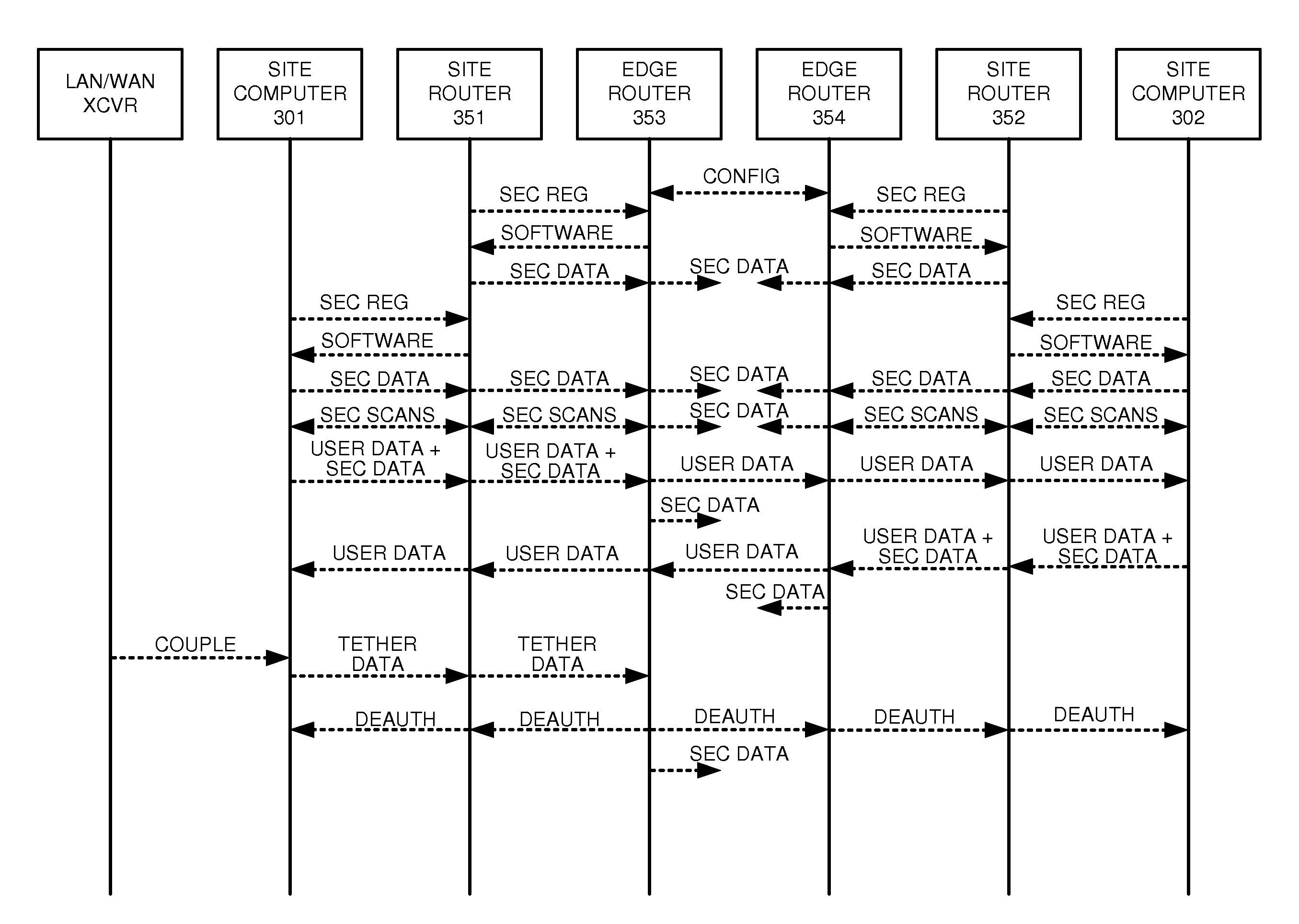
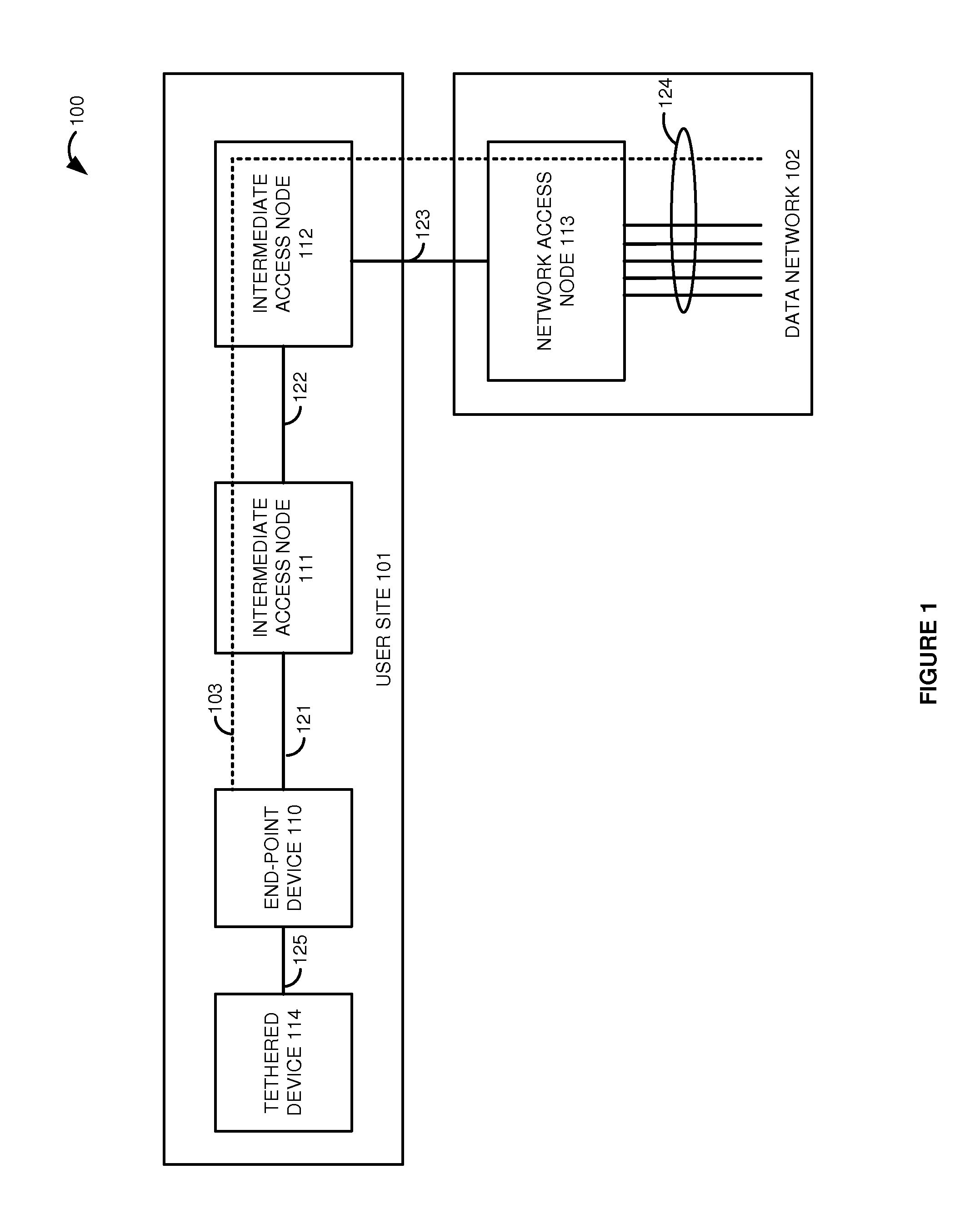
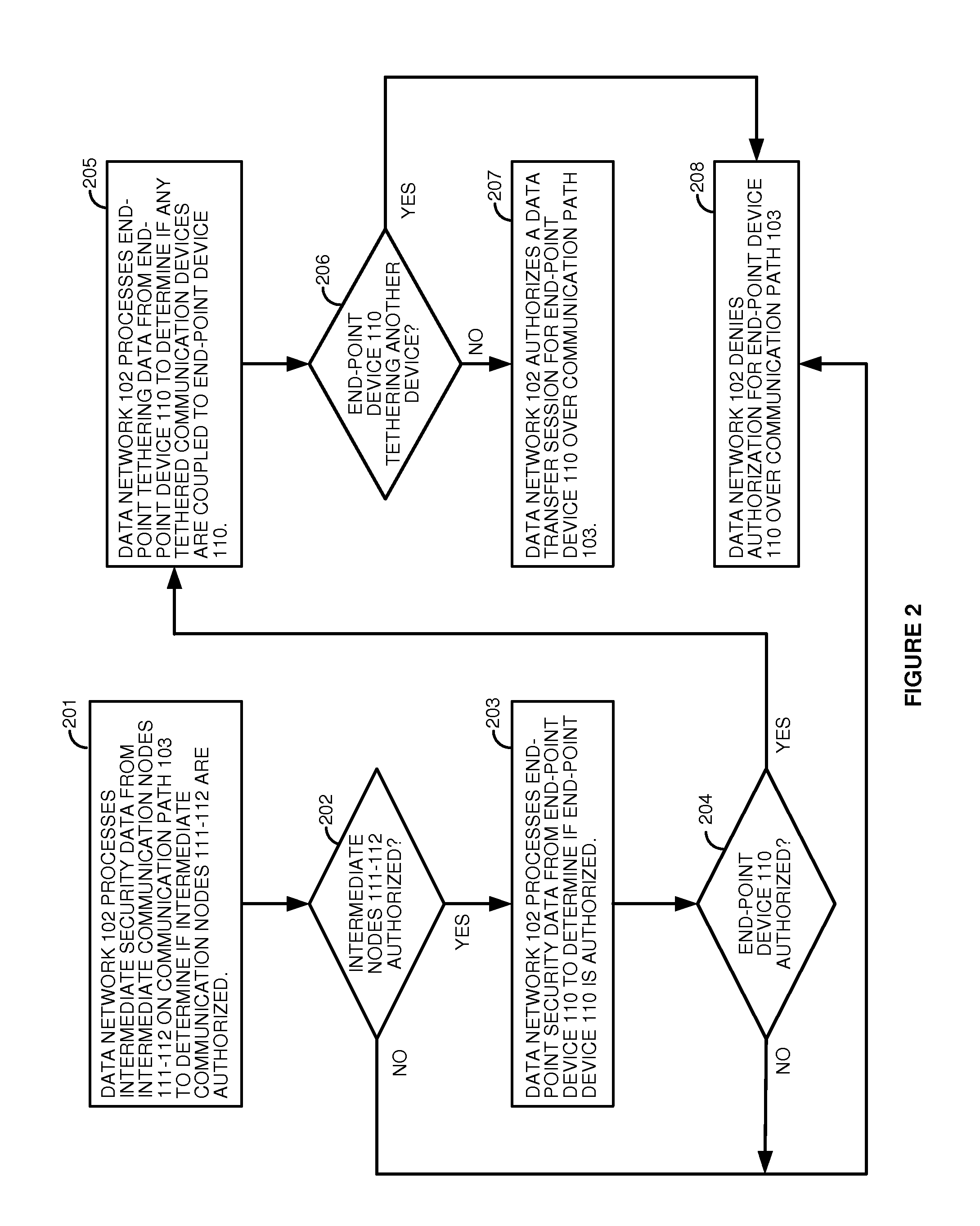
Secure communication paths in data networks with tethered devices
ActiveUS20160149880A1Digital data processing detailsMultiple digital computer combinationsSecure communicationEndpoint security
A communication network processes intermediate security data from intermediate access nodes on a communication path between a network access node and an end-point device to determine if the intermediate access nodes are authorized. If the intermediate access nodes are authorized, then the network processes end-point security data from the end-point device to determine if the end-point device is authorized. If the end-point device is authorized, then the network processes end-point tethering data from the end-point device to determine if any tethered communication devices are coupled to the end-point device. If the end-point device is not coupled to any tethered communication devices, then the network authorizes a data transfer session for the end-point device over the communication path. If the end-point device is coupled to a tethered communication device, then the network denies authorization for the data transfer session over the communication path for the end-point device.
Owner:T MOBILE INNOVATIONS LLC
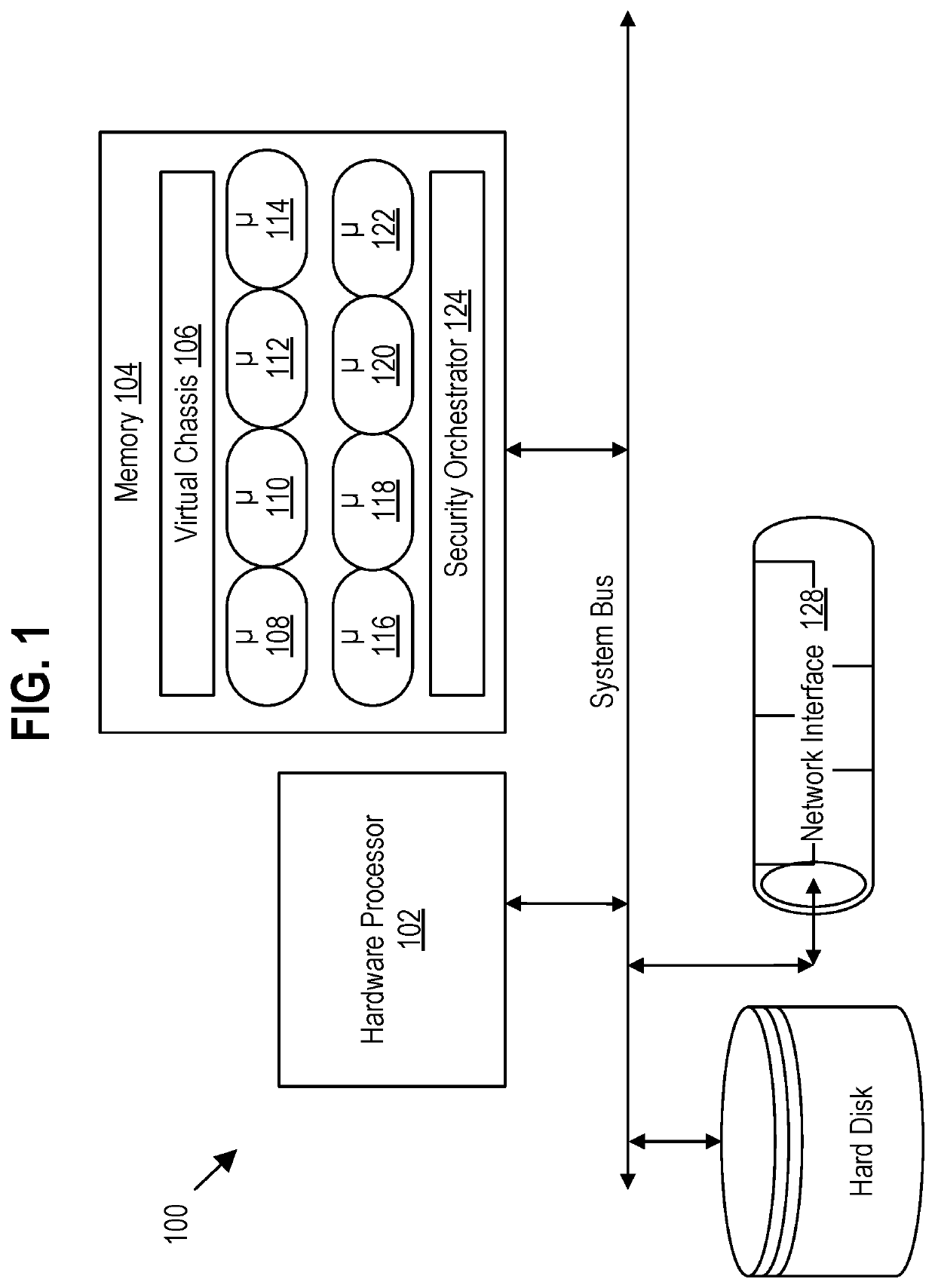
Systems and methods for managing endpoints and security policies in a networked environment
Systems, methods, and apparatuses enable deploying and executing a security policy on endpoints in a network. In an embodiment, a security orchestrator determines a set of endpoints in a network and determines transformed endpoints from the determined set of endpoints through an endpoint transformation process. The security orchestrator determines a connectivity vector for at least a first transformed endpoint and a second transformed endpoint, where the connectivity vector includes properties associated with the corresponding transformed endpoint. Using the properties from the connectivity vector of the first transformed endpoint, a security policy is generated and deployed to the first transformed endpoint. Based on a comparison of the connectivity vectors of the first and second transformed endpoints indicating a similarity between the first and second transformed endpoints, the security policy is further deployed to the second transformed endpoint.
Owner:FORTINET
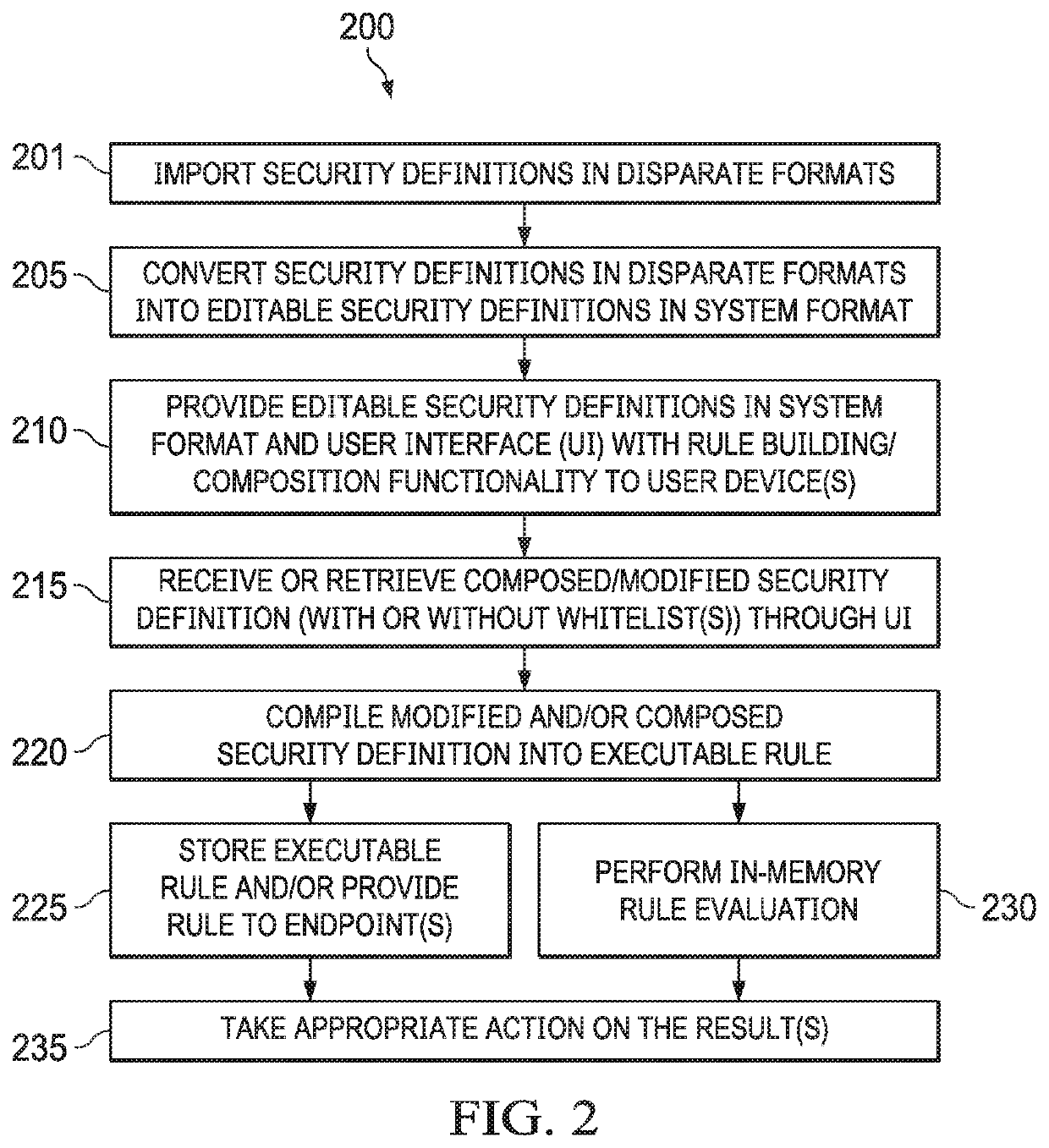
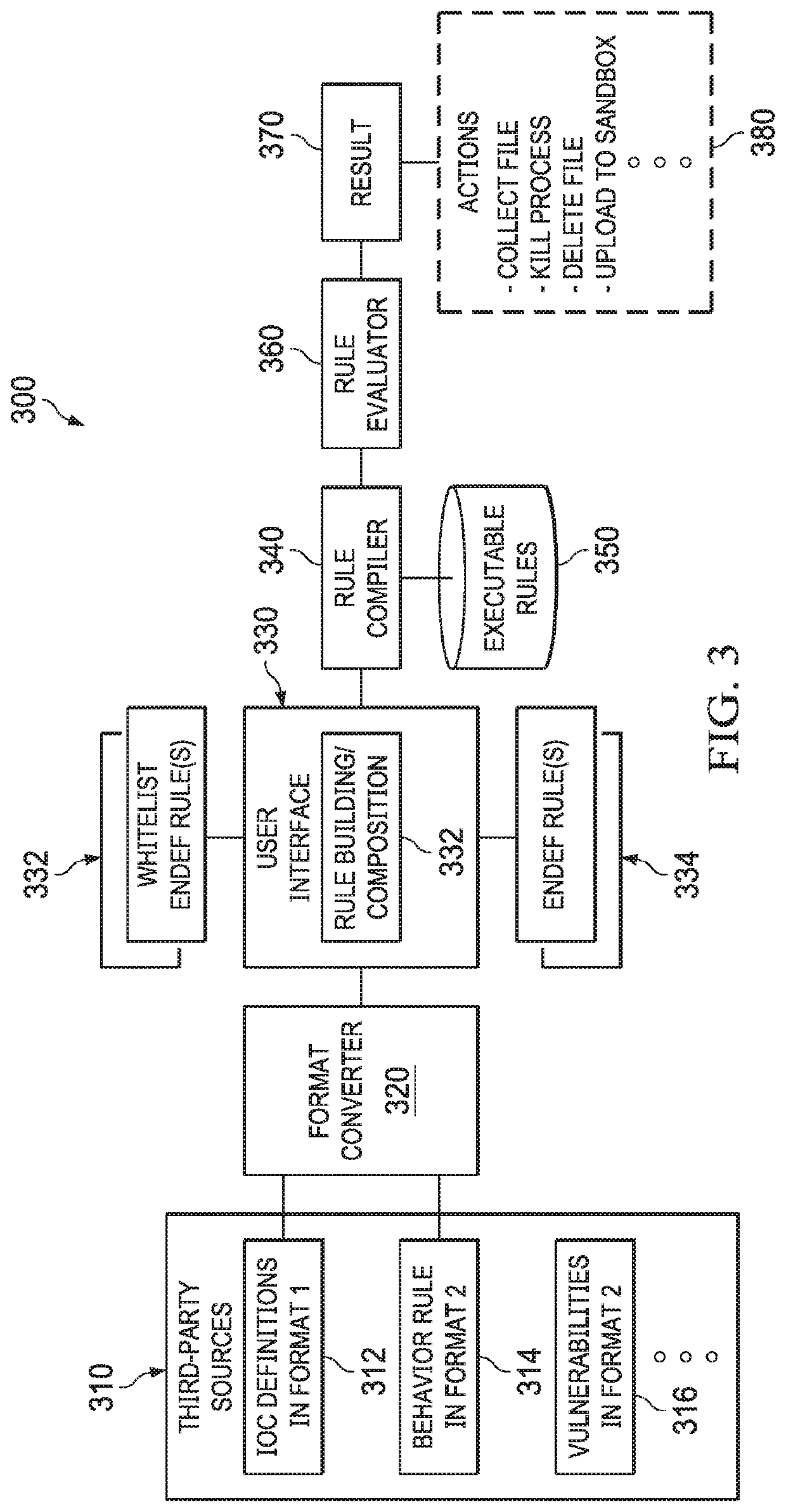
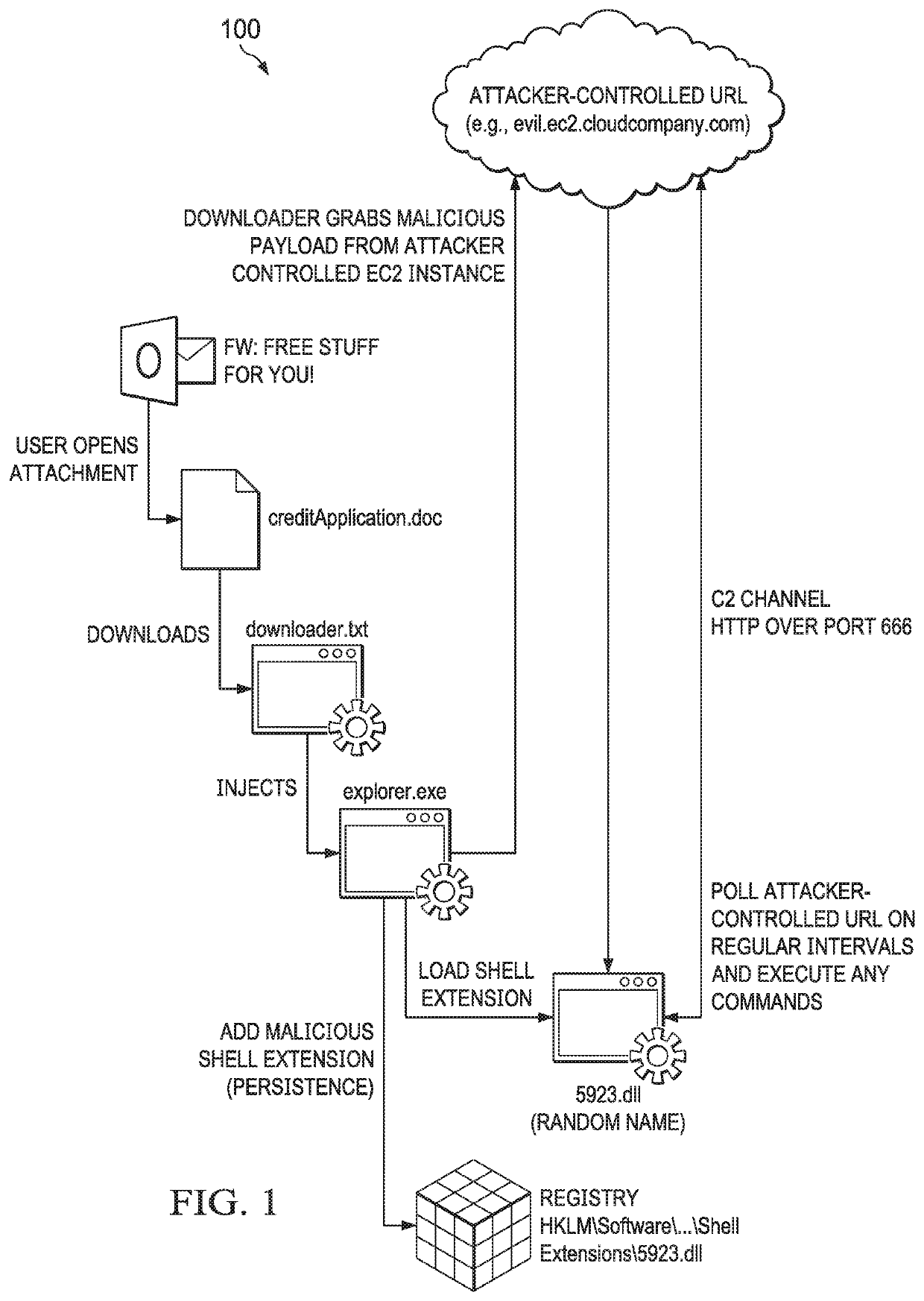
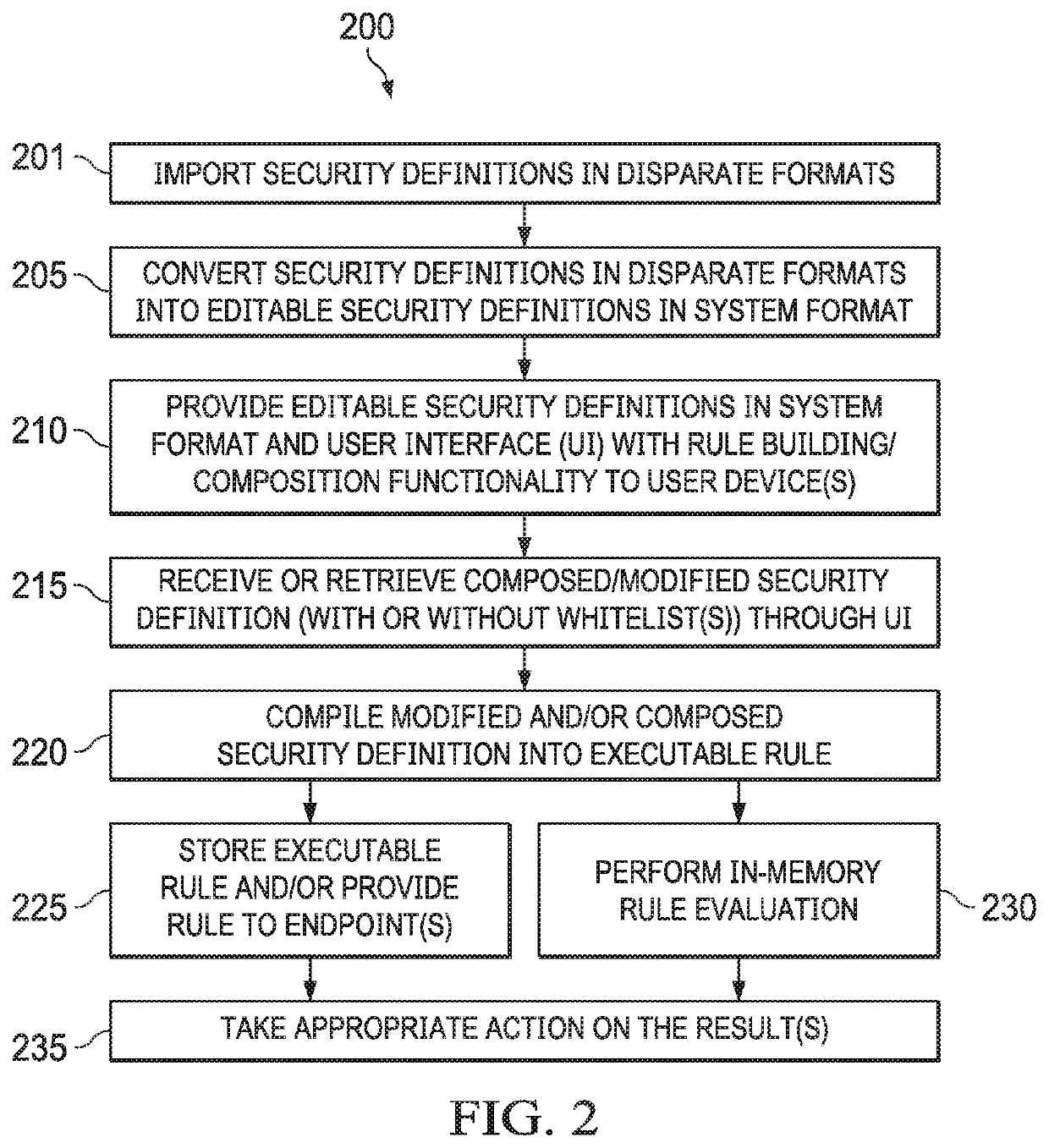
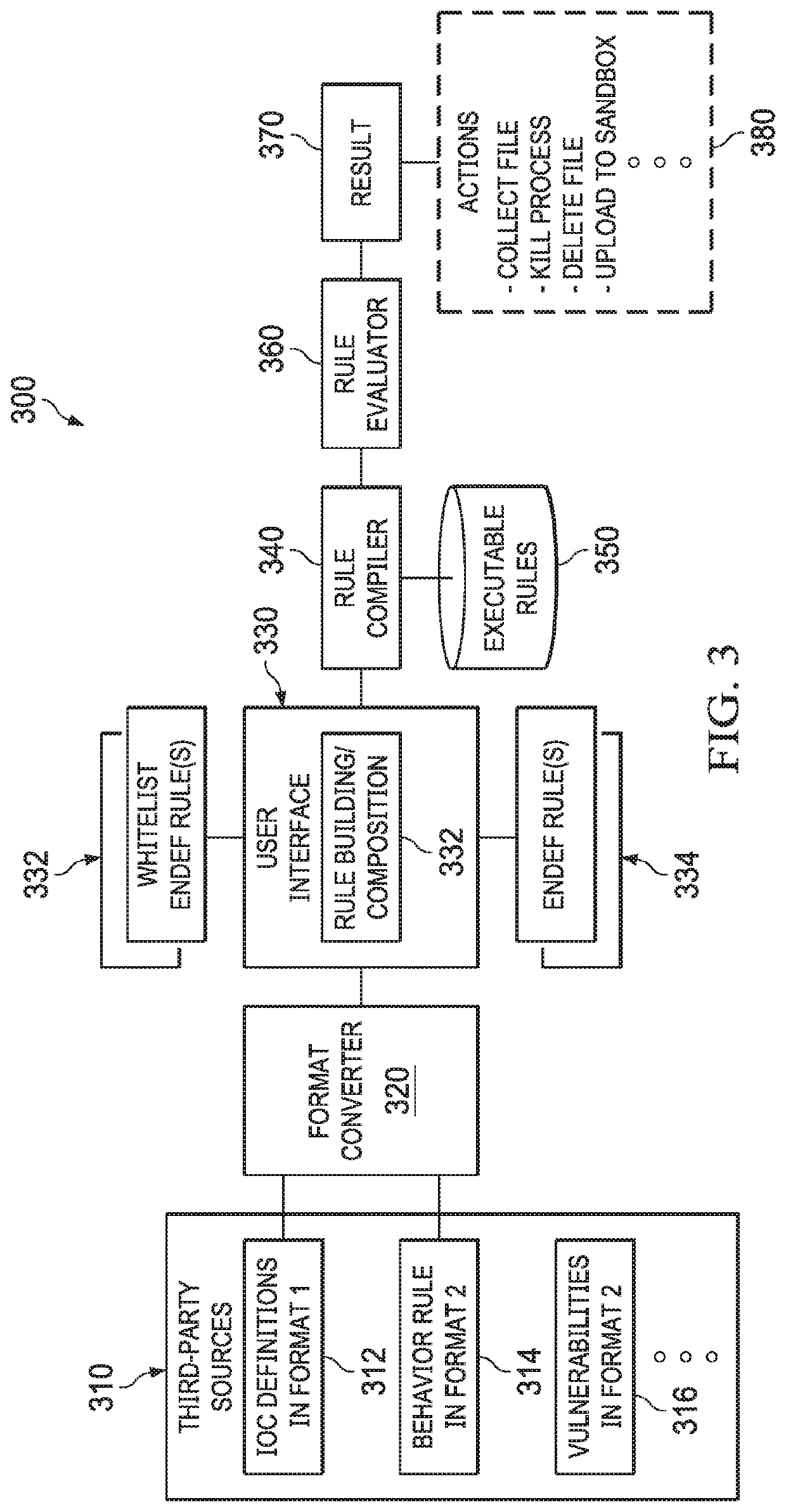
Systems and methods of information security monitoring with third-party indicators of compromise
An information security monitoring system can import indicators of compromise (IOC) definitions in disparate formats from third-party source systems, convert them into editable security definitions in an internal system format, and provide a user interface for composing or editing these security definitions with enhancements, including complex security definitions such as those having a nested Boolean structure and / or those that reference one or more security definitions, a behavioral rule, and / or a vulnerability description. One or more whitelists can be added to handle exceptions. Each composed or modified security definition is then compiled into an executable rule. The executable rule, when evaluated, produces a result indicative of an endpoint security action needed in view of an endpoint event that meets the composed or modified security definition.
Owner:OPEN TEXT HLDG INC
Systems and methods of information security monitoring with third-party indicators of compromise
An information security monitoring system can import indicators of compromise (IOC) definitions in disparate formats from third-party source systems, convert them into editable security definitions in an internal system format, and provide a user interface for composing or editing these security definitions with enhancements, including complex security definitions such as those having a nested Boolean structure and / or those that reference one or more security definitions, a behavioral rule, and / or a vulnerability description. One or more whitelists can be added to handle exceptions. Each composed or modified security definition is then compiled into an executable rule. The executable rule, when evaluated, produces a result indicative of an endpoint security action needed in view of an endpoint event that meets the composed or modified security definition.
Owner:OPEN TEXT HLDG INC
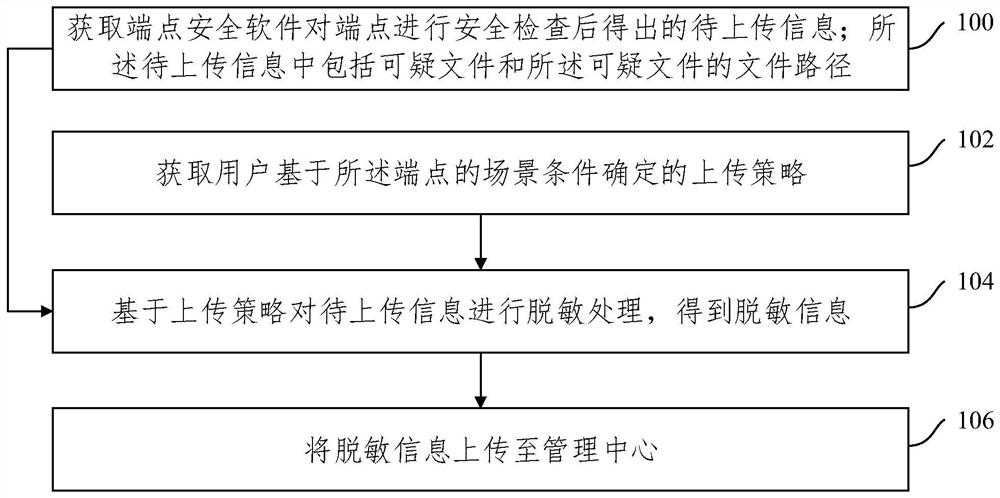
Endpoint file security check result information uploading method and device, equipment and medium
PendingCN114866532AReduce uploadReduce leakageDigital data protectionSecuring communicationSecurity softwareEndpoint security
The invention provides an endpoint file security check result information uploading method, apparatus and device, and a medium. The method comprises the steps of obtaining to-be-uploaded information obtained after endpoint security software performs security check on an endpoint; the information to be uploaded comprises a suspicious file and a file path of the suspicious file; acquiring an uploading strategy determined by a user based on the scene condition of the endpoint; performing desensitization processing on the to-be-uploaded information based on the uploading strategy to obtain desensitized information; and uploading the desensitization information to a management center. According to the scheme, the information to be uploaded is desensitized by using the uploading strategy, so that the desensitized information contains sensitive information as little as possible, and then the desensitized information is uploaded to the management center, so that the sensitive information uploaded to the management center can be reduced, and the leakage of the sensitive information is reduced.
Owner:HARBIN ANTIY TECH
Utilizing endpoint security posture, identification, and remote attestation for restricting private application access
Owner:ZSCALER INC
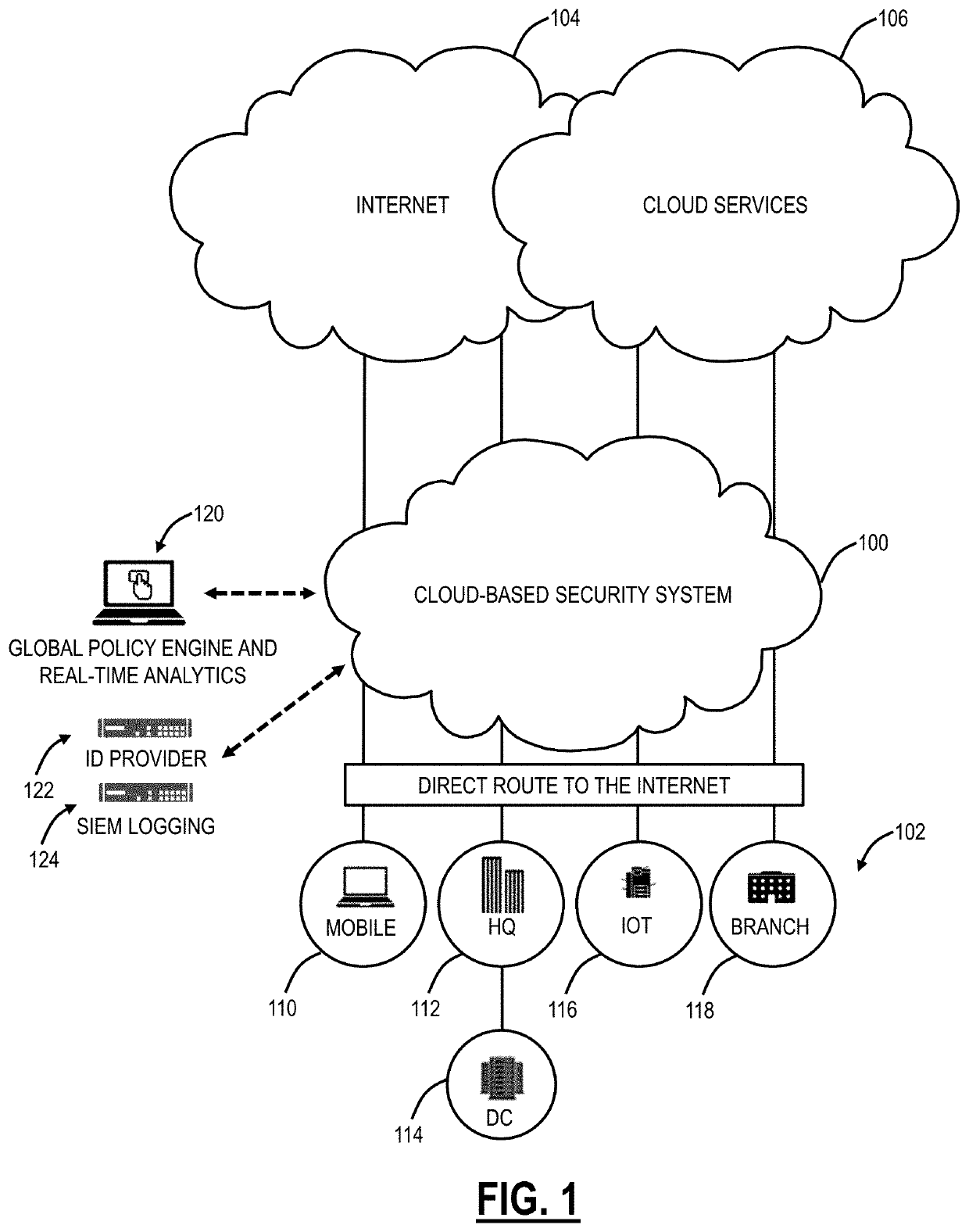
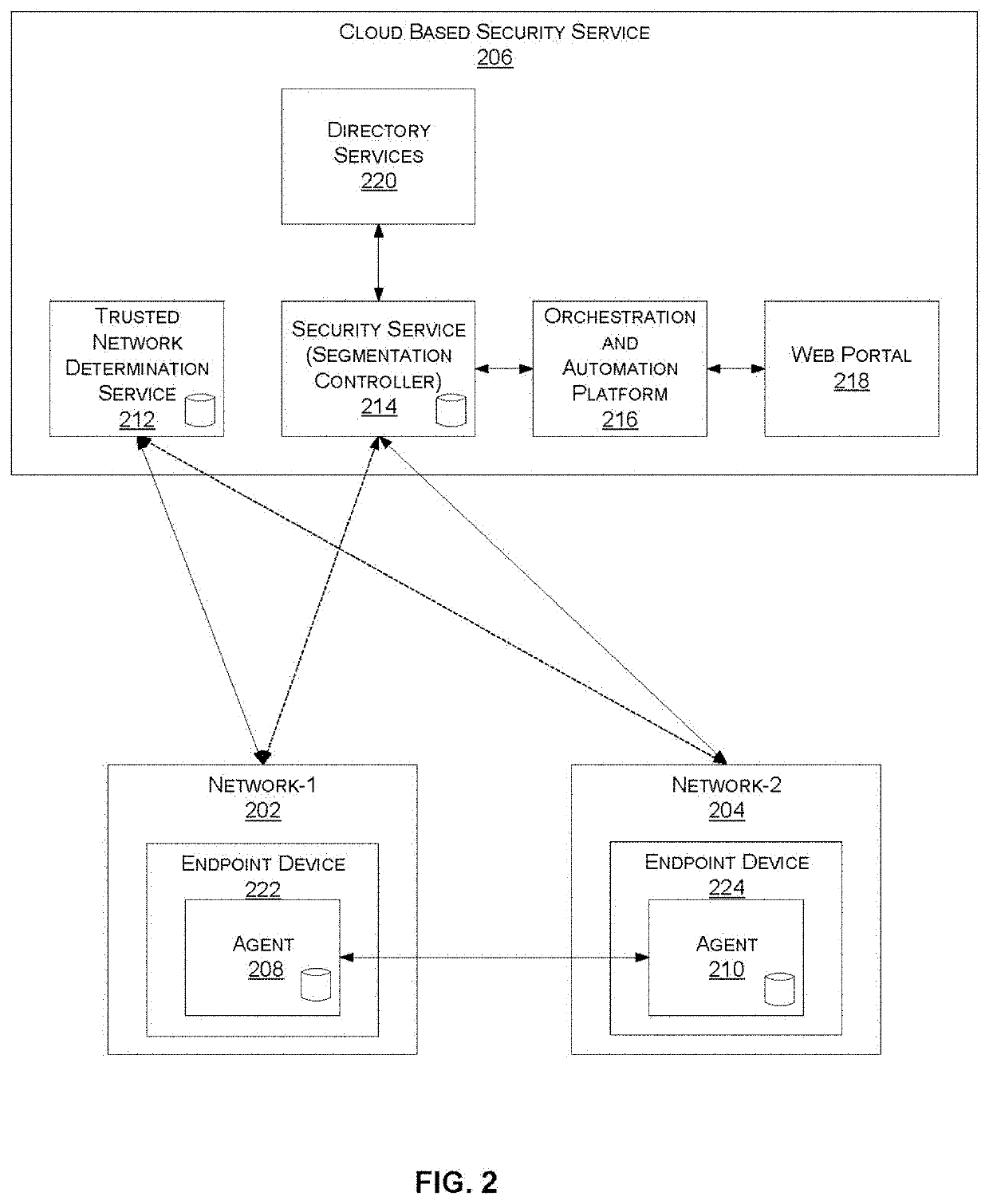
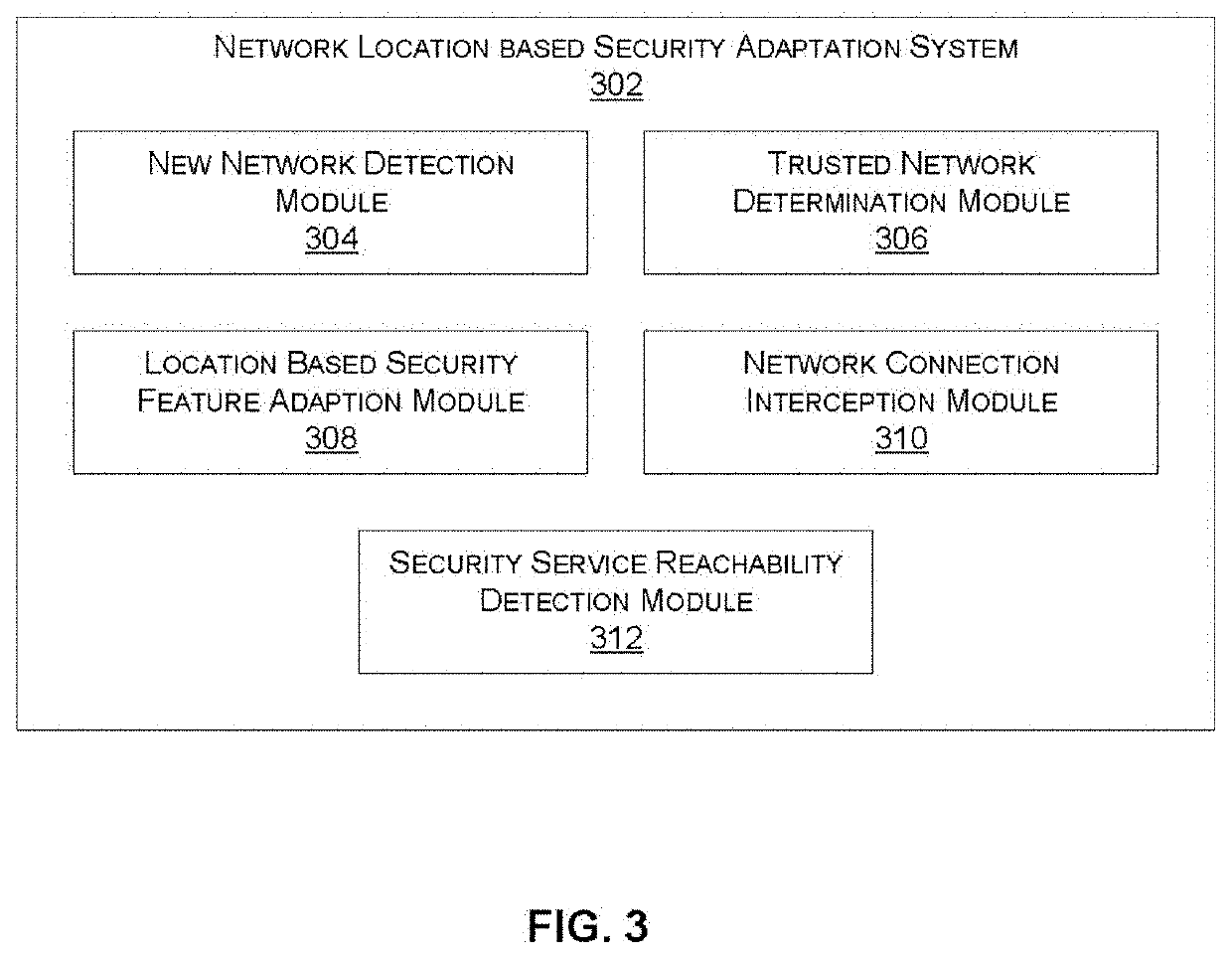
Adjusting behavior of an endpoint security agent based on network location
Systems and methods for adjusting the behavior of an endpoint security agent based on a network location are provided. According to an embodiment, an agent of an endpoint device detects whether the endpoint has moved to a new network by monitoring for changes to an IP address associated with the endpoint. When the detecting is affirmative, the agent further determines whether a trusted network determination service associated with a cloud-based security service is reachable. When the determining is affirmative, the agent further identifies whether the new network is among a set of trusted networks that have been previously registered with the cloud-based security service by querying the trusted network determination service. When the identifying is affirmative, a particular security feature on the endpoint is configured for operation within a trusted network and when the identifying is negative, the particular security feature is configured for operation outside of a trusted networks.
Owner:FORTINET
Secure, remote support platform with an edge device
ActiveUS20200311241A1Digital data protectionInternal/peripheral component protectionComputer hardwareEndpoint security
Owner:INFINITY TRIBE GRP INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com