Method for improving security of user management system by adopting layering defense mode
A technology for system security and user management, which is applied in the field of using layered defense mode to improve user management system security. , The effect of small impact on system performance and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
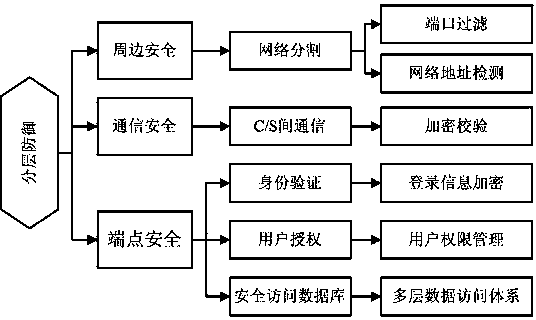
[0035] Such as figure 1 As shown, the present invention adopts a layered defense mode to improve the security of the user management system, and adopts three levels of peripheral security, communication security, and endpoint security to construct a layered defense system, thereby improving the ability of the user management system to resist attacks. Including the following steps,
[0036] S1: Peripheral security, that is, separate the internal network of the user management system that needs to be protected from the open network through network segmentation, making it a safe and controlled network. The specific implementation process is as follows:
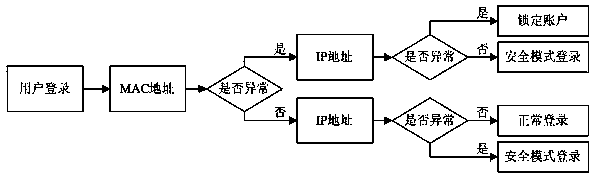
[0037] S11: Port filtering: During the actual operation of the user management system, data interaction between the browser and the server is required, so when the firewall creates access r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com