Character constant weight method
A role-determining, role-based technology, applied in the fields of instruments, electrical digital data processing, digital data processing components, etc., can solve problems such as rough security, complex configuration and management, and poor versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
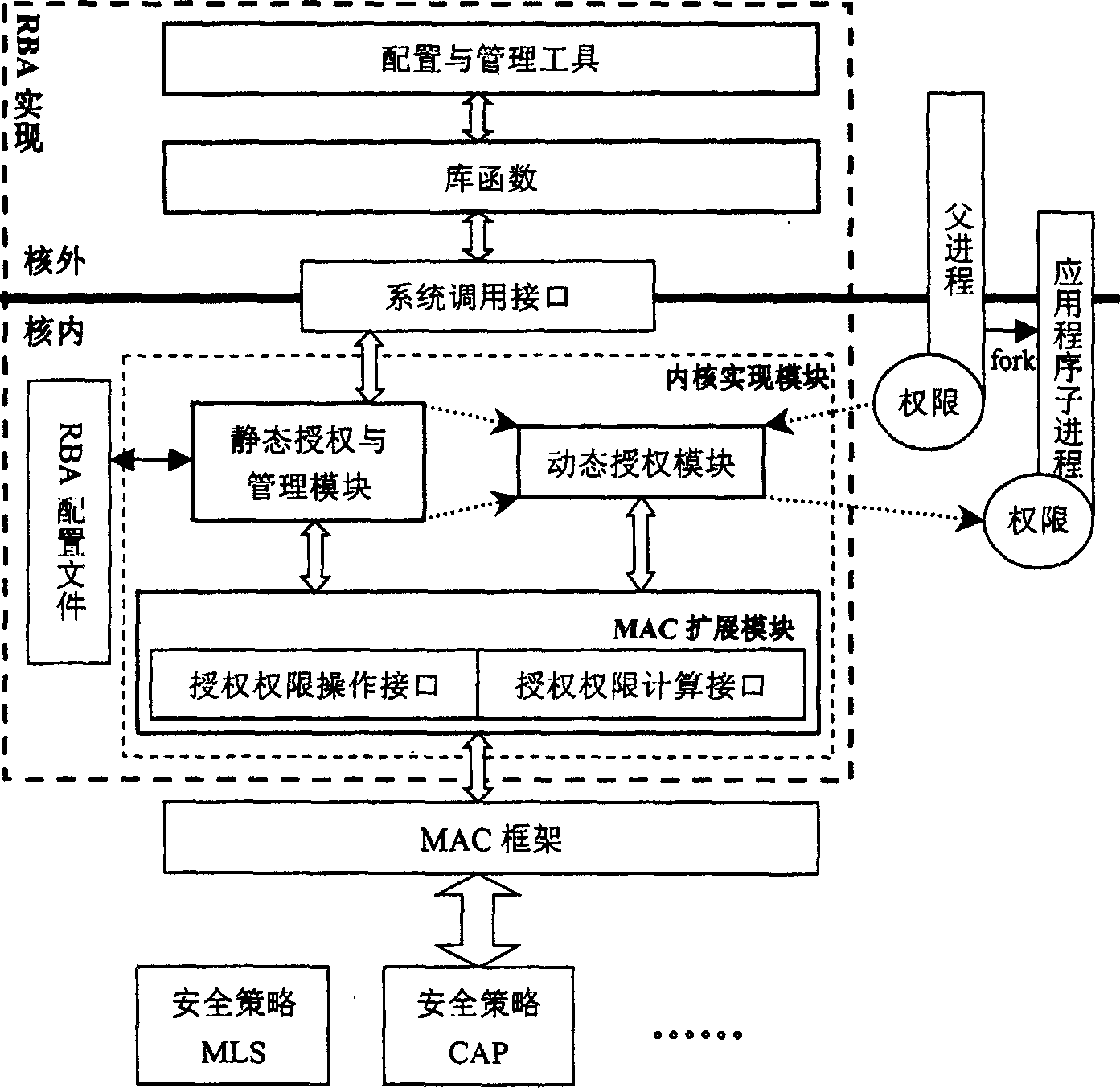
[0064] As shown in Figure 1, the content in the dotted box is the RBA implementation system. The RBA implementation system consists of RBA configuration files, kernel implementation modules, system call interfaces, library functions, and configuration and management tools.
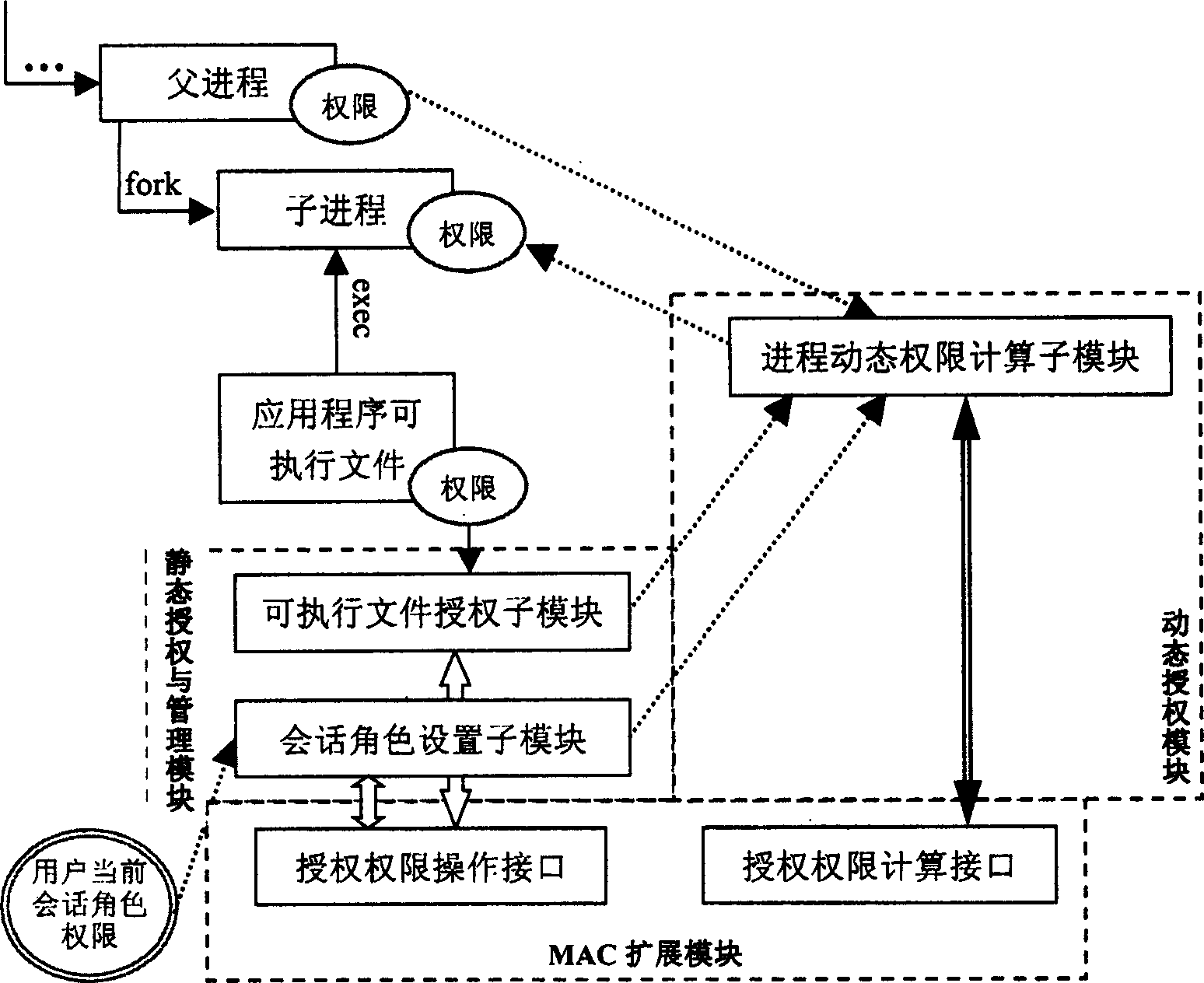
[0065] The kernel implementation module is composed of static authorization and management module, dynamic authorization module and MAC extension module. These modules work on the MAC of the operating system's mandatory access control framework.
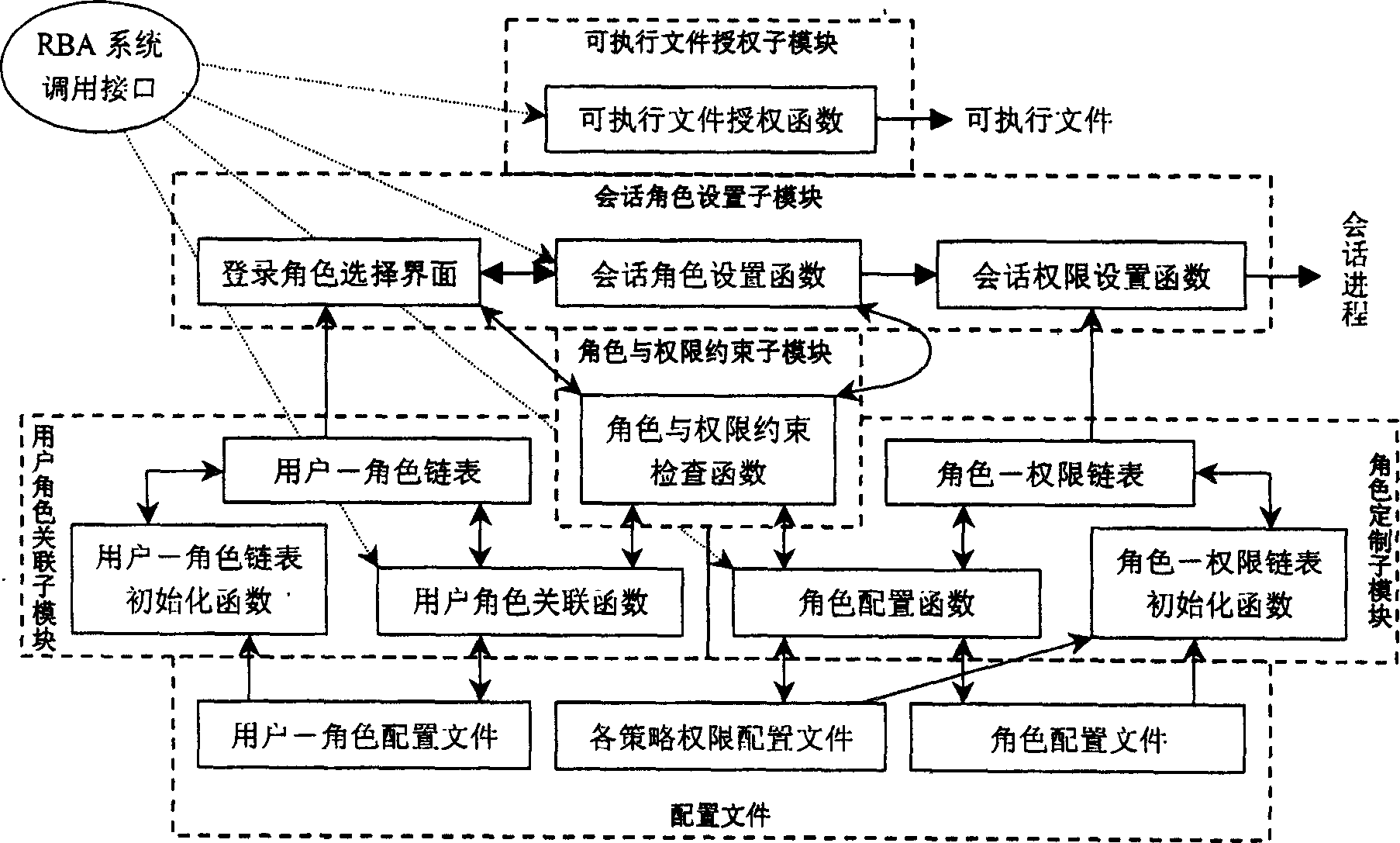
[0066] The administrator can use the configuration and management tool to call the service of the static authorization and management module through the system call interface to perform static authorization and management on the user, and the user's static authorization information is stored in the RBA configuration file. The static authorization and management module invokes the MAC extension module to process the permission-related information of the system, in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com