Patents
Literature
553results about How to "Efficient sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
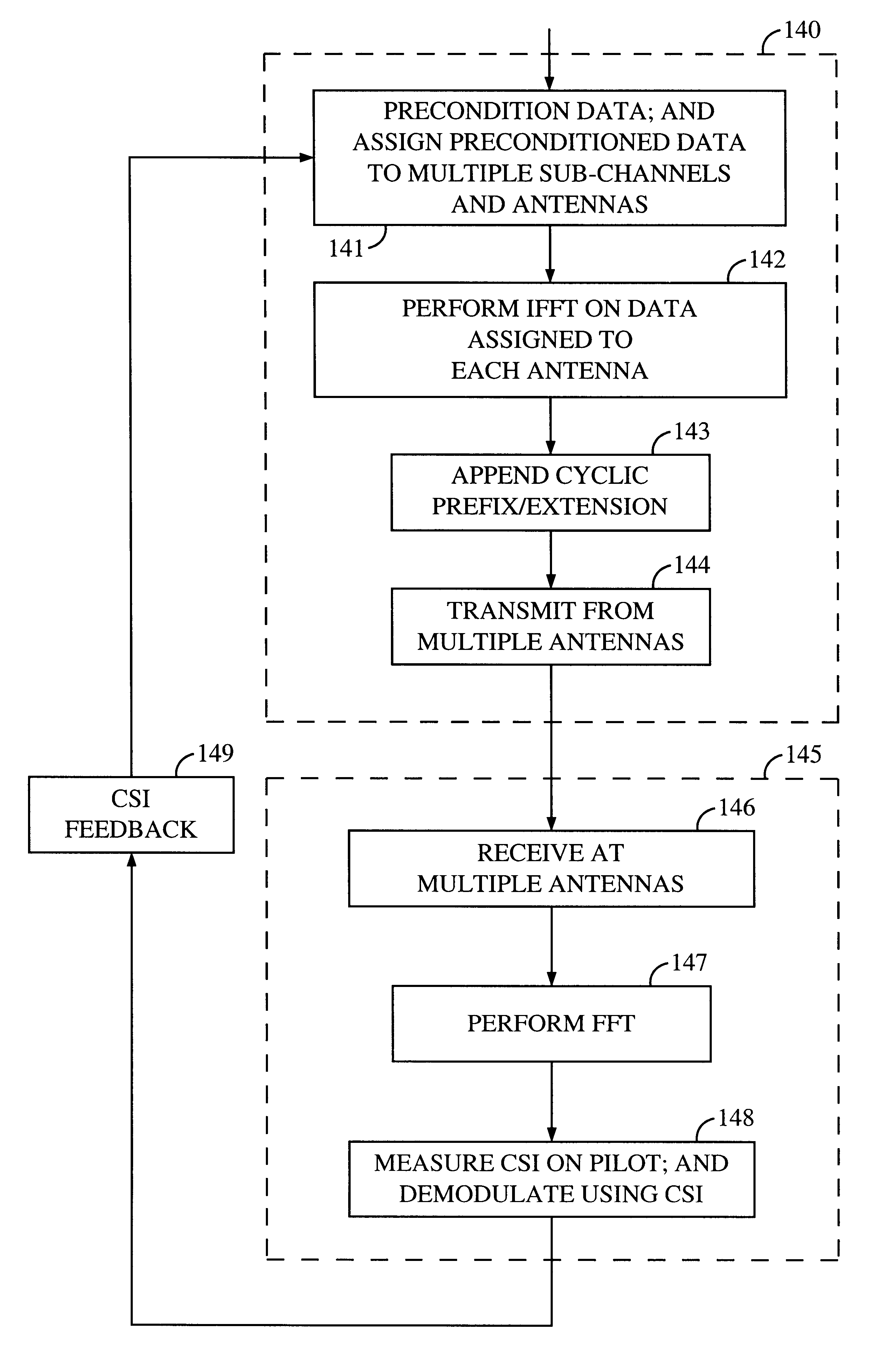
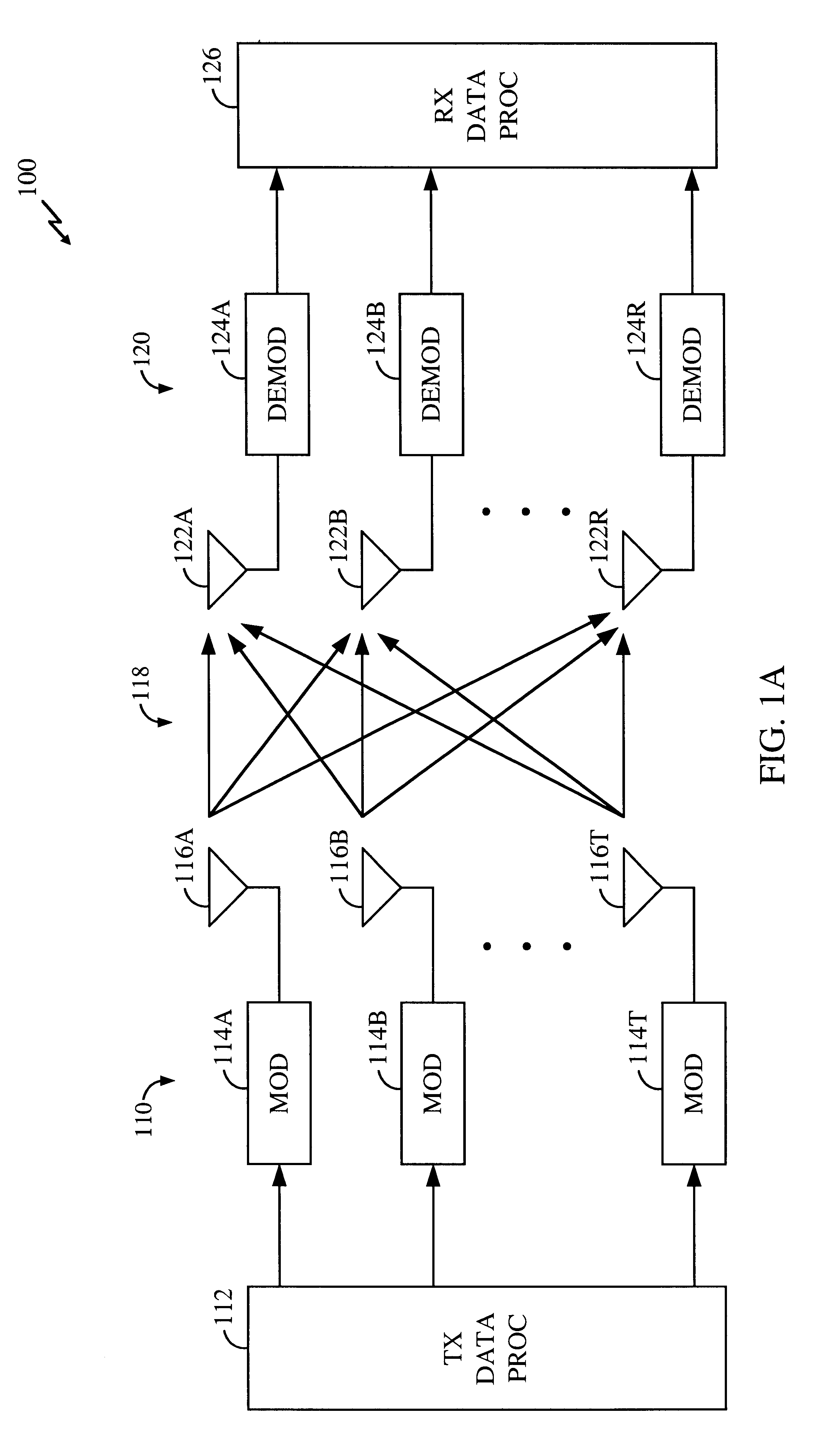
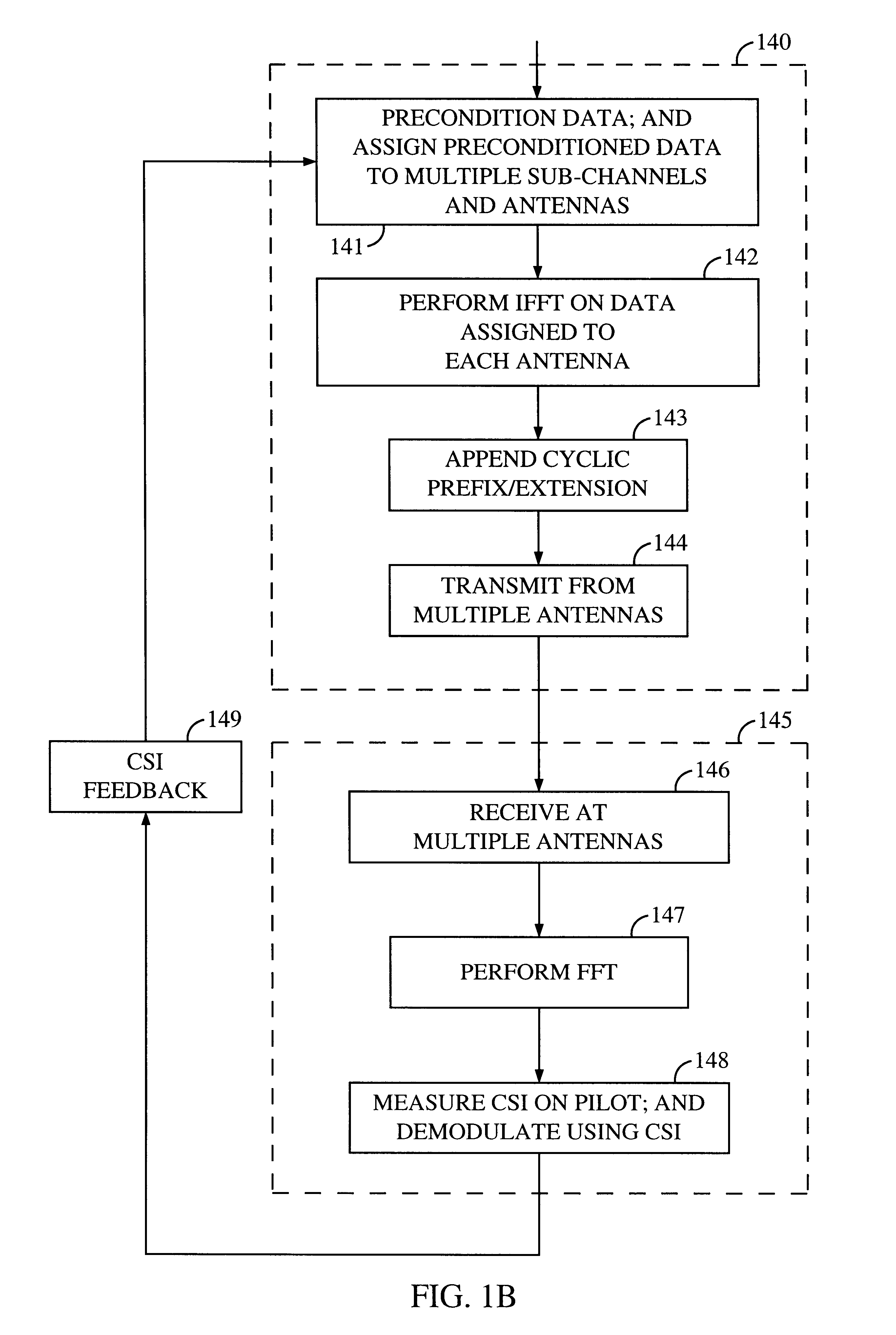
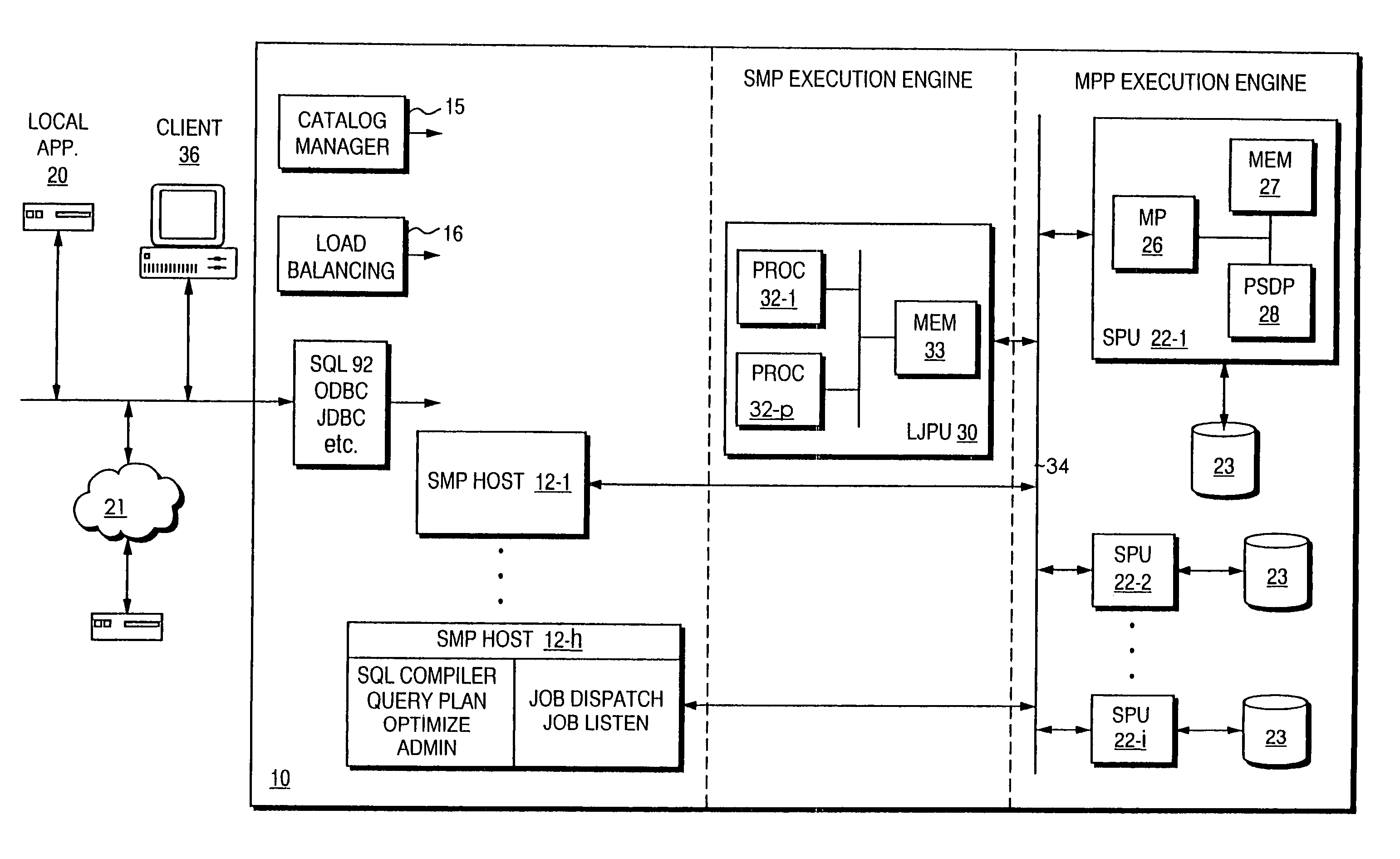
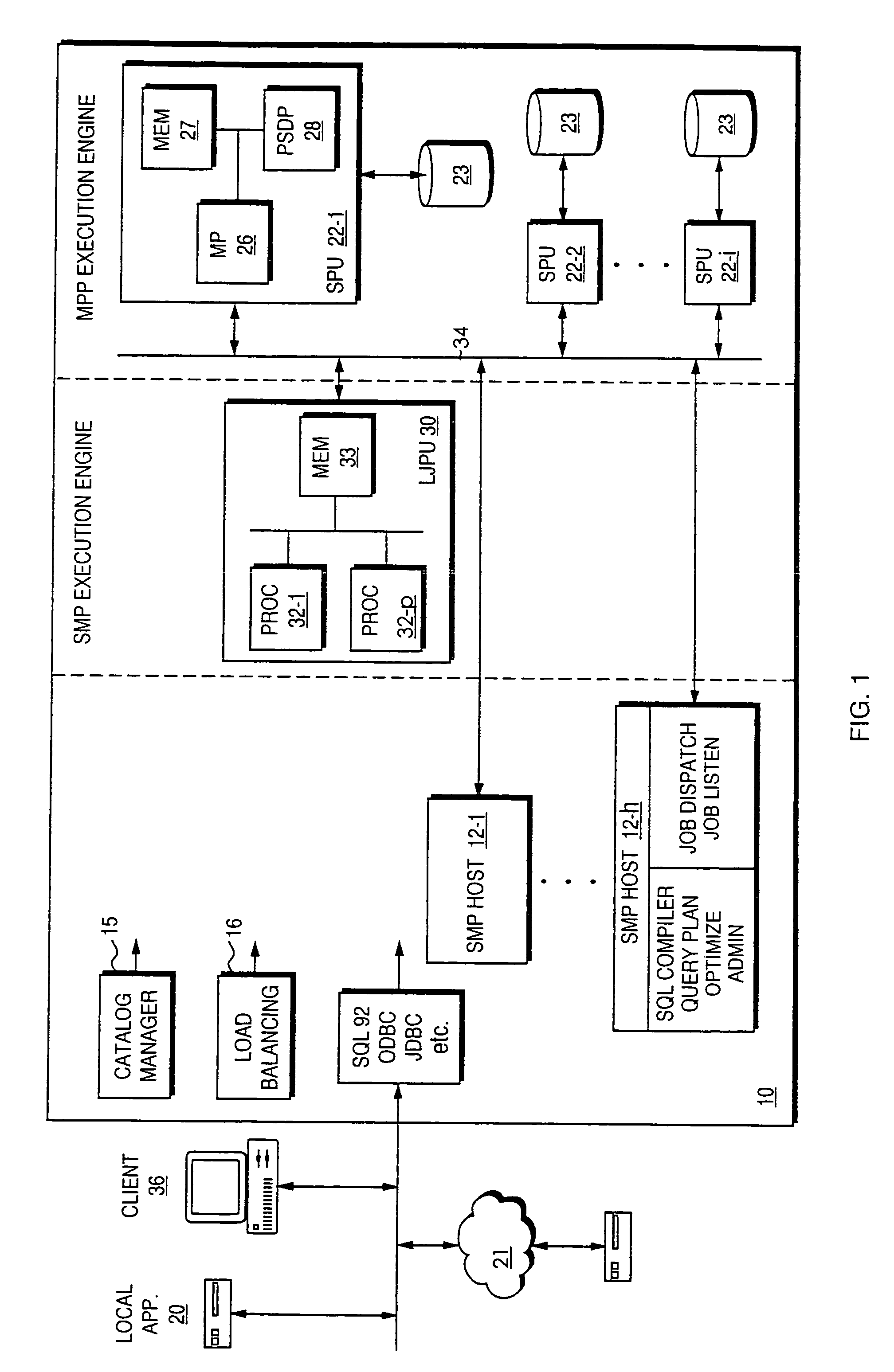
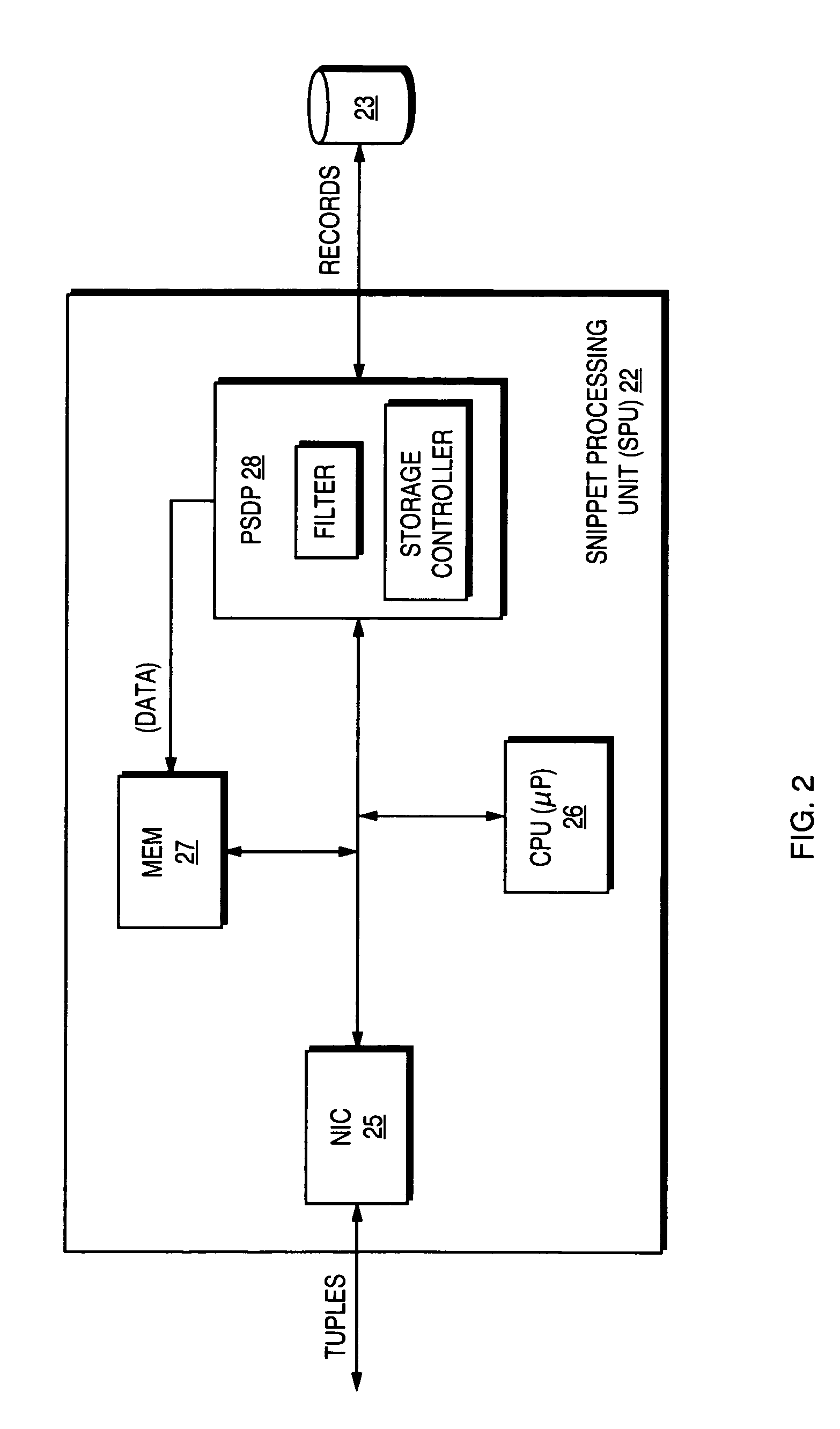
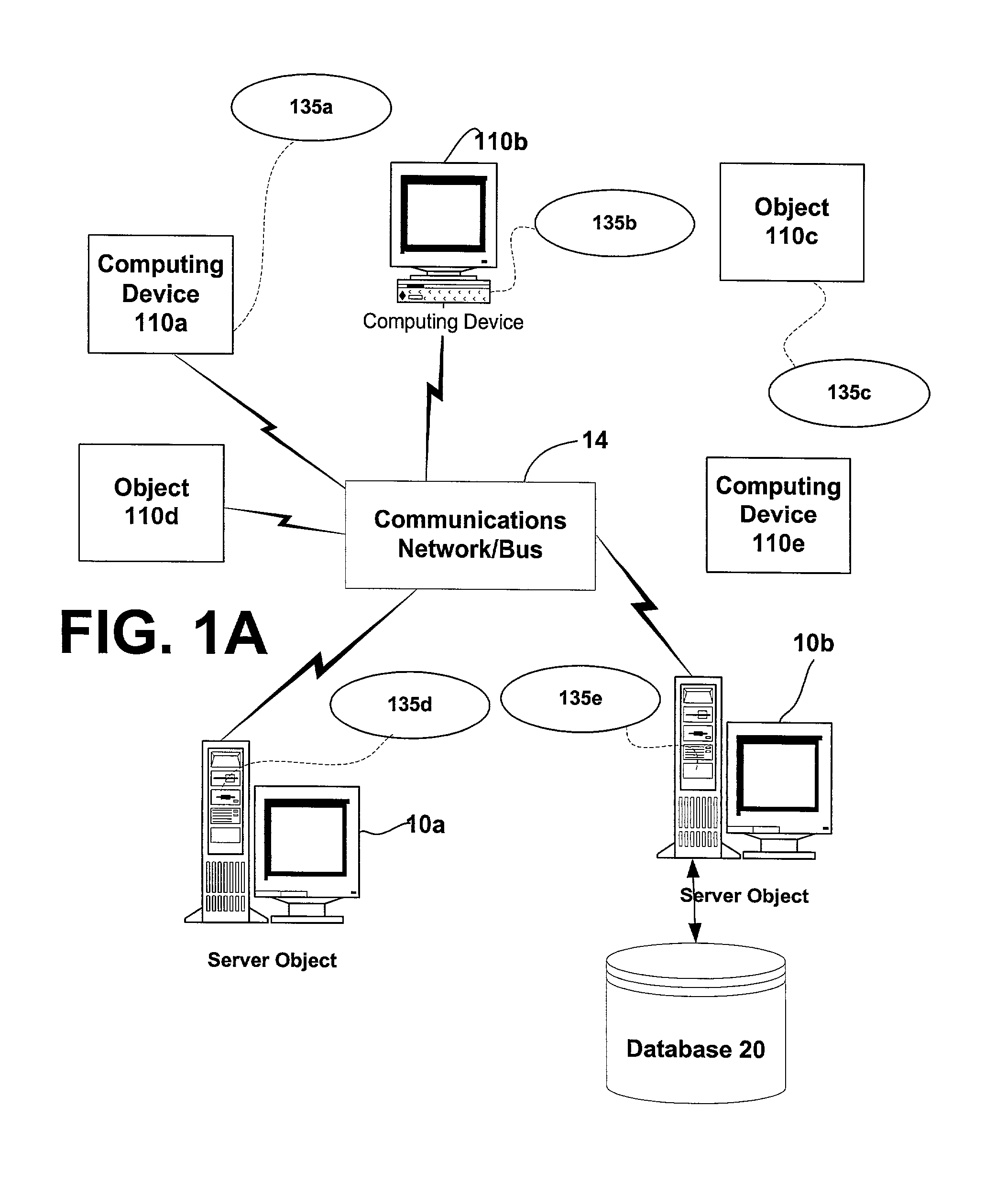
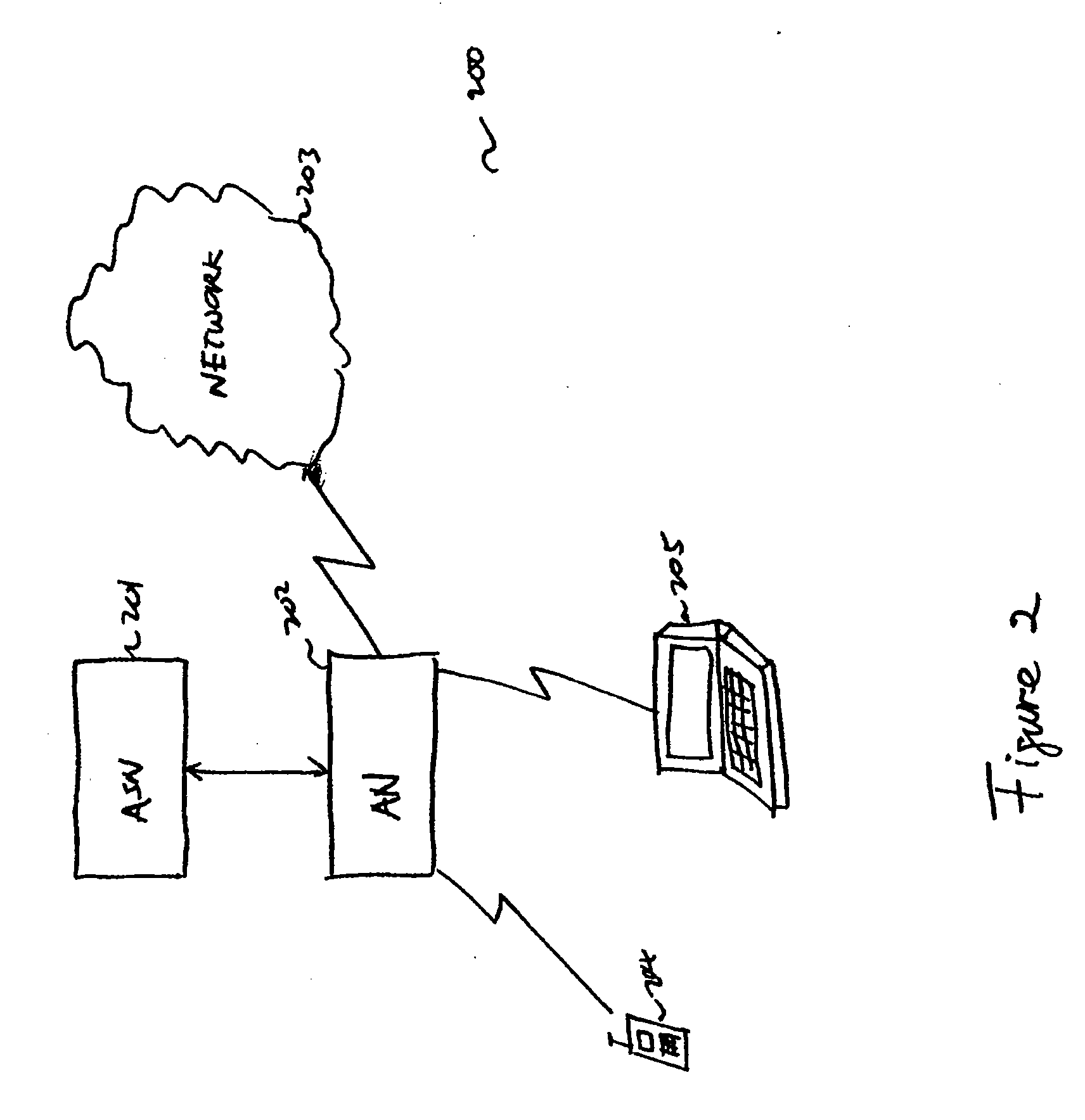
Method and apparatus for measuring reporting channel state information in a high efficiency, high performance communications system
InactiveUS6473467B1Efficient sharingInterference minimizationSpatial transmit diversityPolarisation/directional diversityChannel state informationCommunications system
Channel state information (CSI) can be used by a communications system to precondition transmissions between transmitter units and receiver units. In one aspect of the invention, disjoint sub-channel sets are assigned to transmit antennas located at a transmitter unit. Pilot symbols are generated and transmitted on a subset of the disjoint sub-channels. Upon receipt of the transmitted pilot symbols, the receiver units determine the CSI for the disjoint sub-channels that carried pilot symbols. These CSI values are reported to the transmitter unit, which will use these CSI values to generate CSI estimates for the disjoint sub-channels that did not carry pilot symbols. The amount of information necessary to report CSI on the reverse link can be further minimized through compression techniques and resource allocation techniques.
Owner:QUALCOMM INC
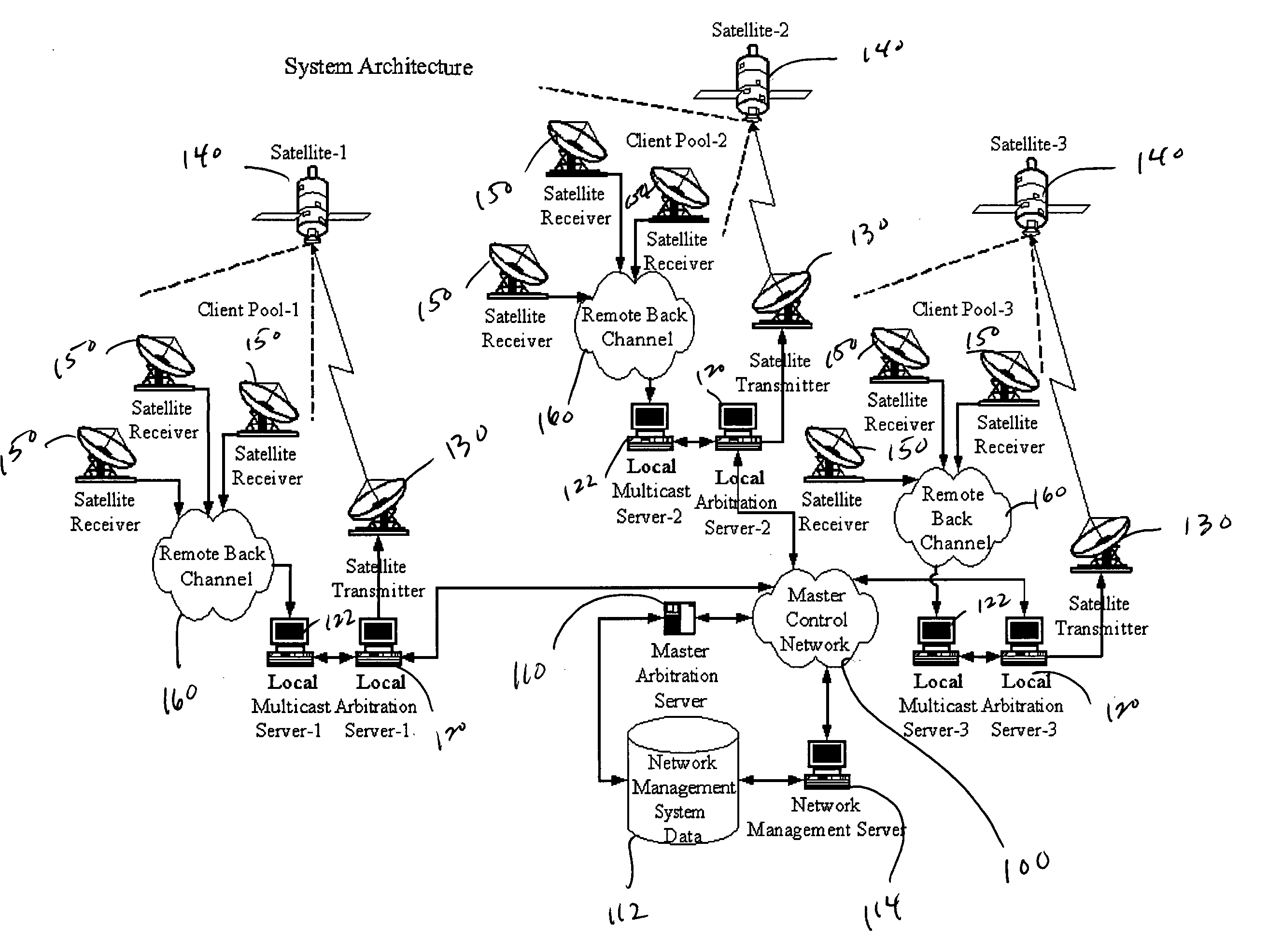
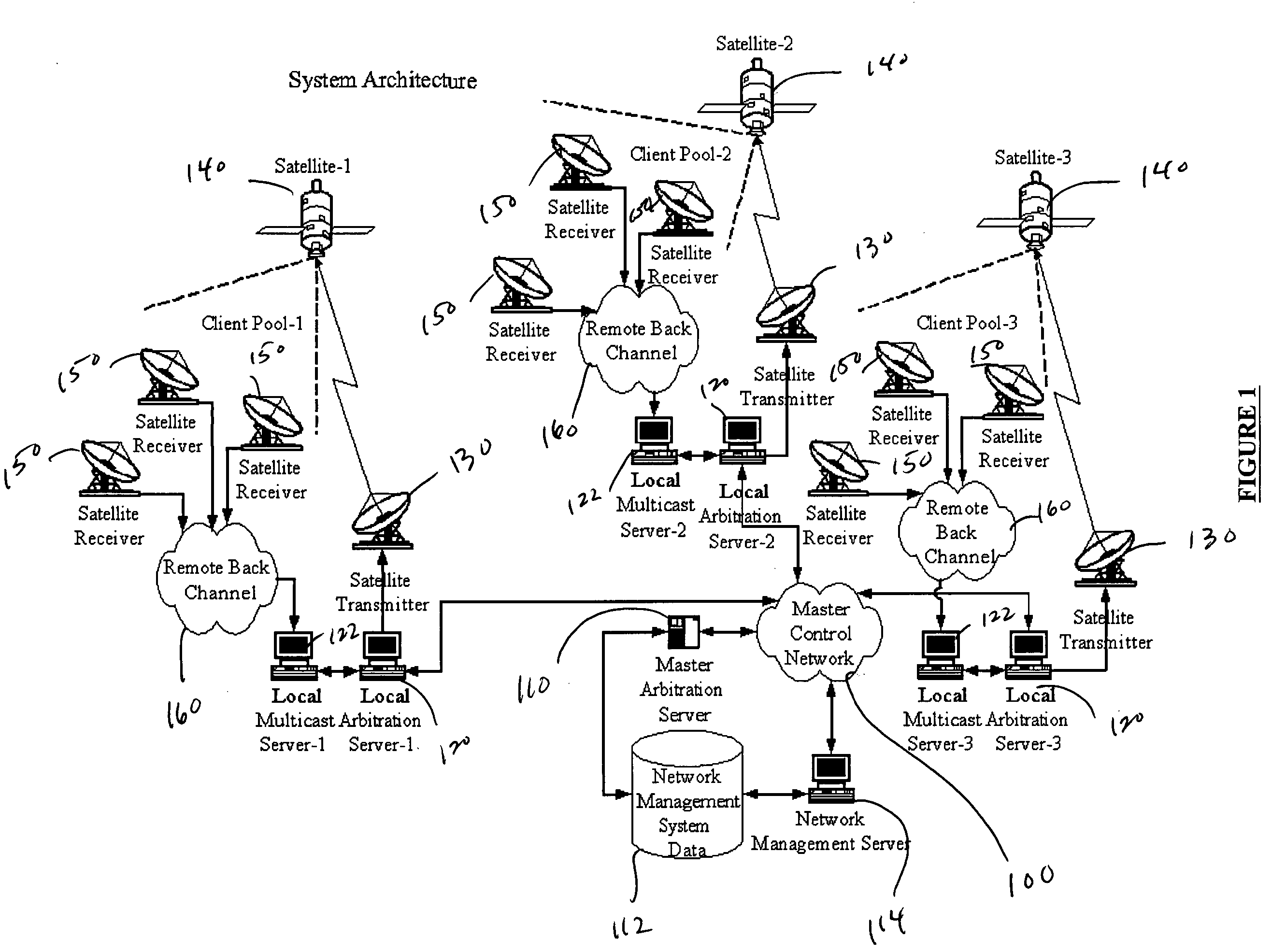
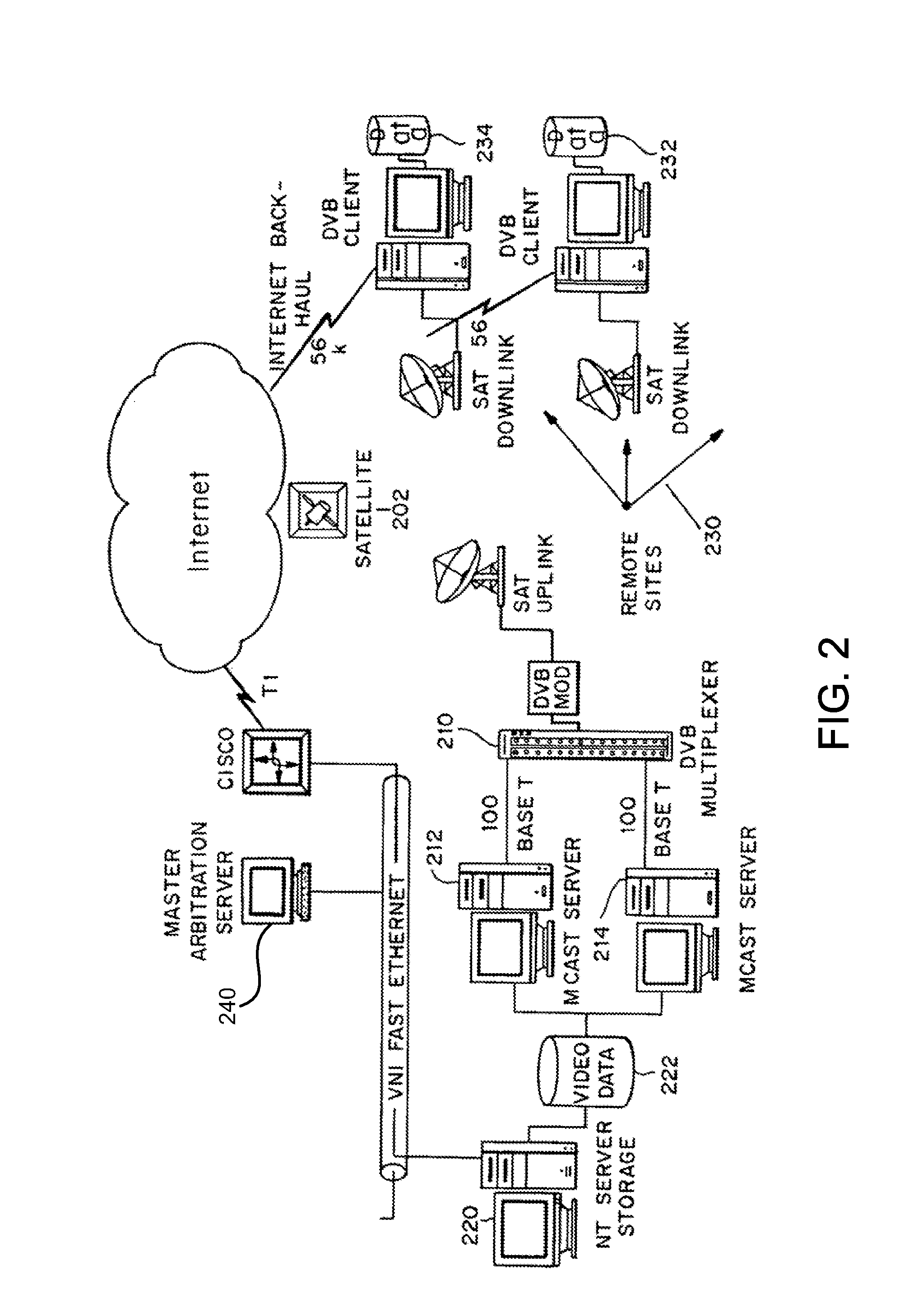
Multicast control systems and methods for dynamic, adaptive time, bandwidth,frequency, and satellite allocations
InactiveUS20050037706A1Improve transmission performanceMaximizing numberBroadcast with distributionNetwork traffic/resource managementControl systemThe Internet
Methods and systems to efficiently share multiple satellites and associated transponders or links among a network of uplinking earth stations are disclosed. An embodiment of this invention uses a terrestrial communications link, such as the Internet, to control access to the transponder or satellite links. Communications over this link may employ a TCP / IP protocol to connect the requesting uplinking earth stations with a centralized controller. This control system creates more efficient use of satellite resources and reduces the overall amount of time needed for transmitting data through the satellite. By reducing the overall amount of time needed for transmitting data, the control system may reduce the cost of using the satellite transponder capacity.
Owner:EXTREME REACH INC +1
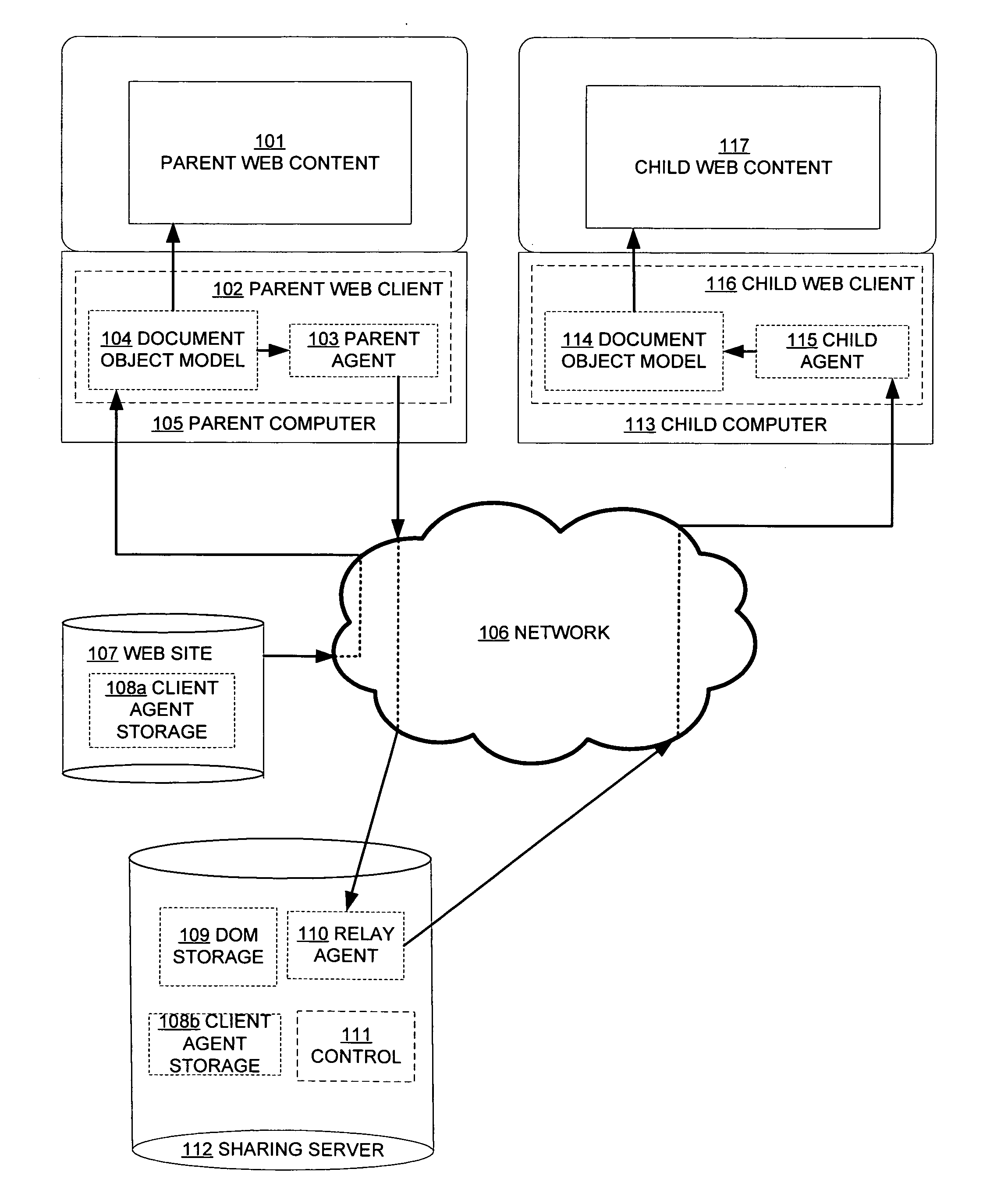
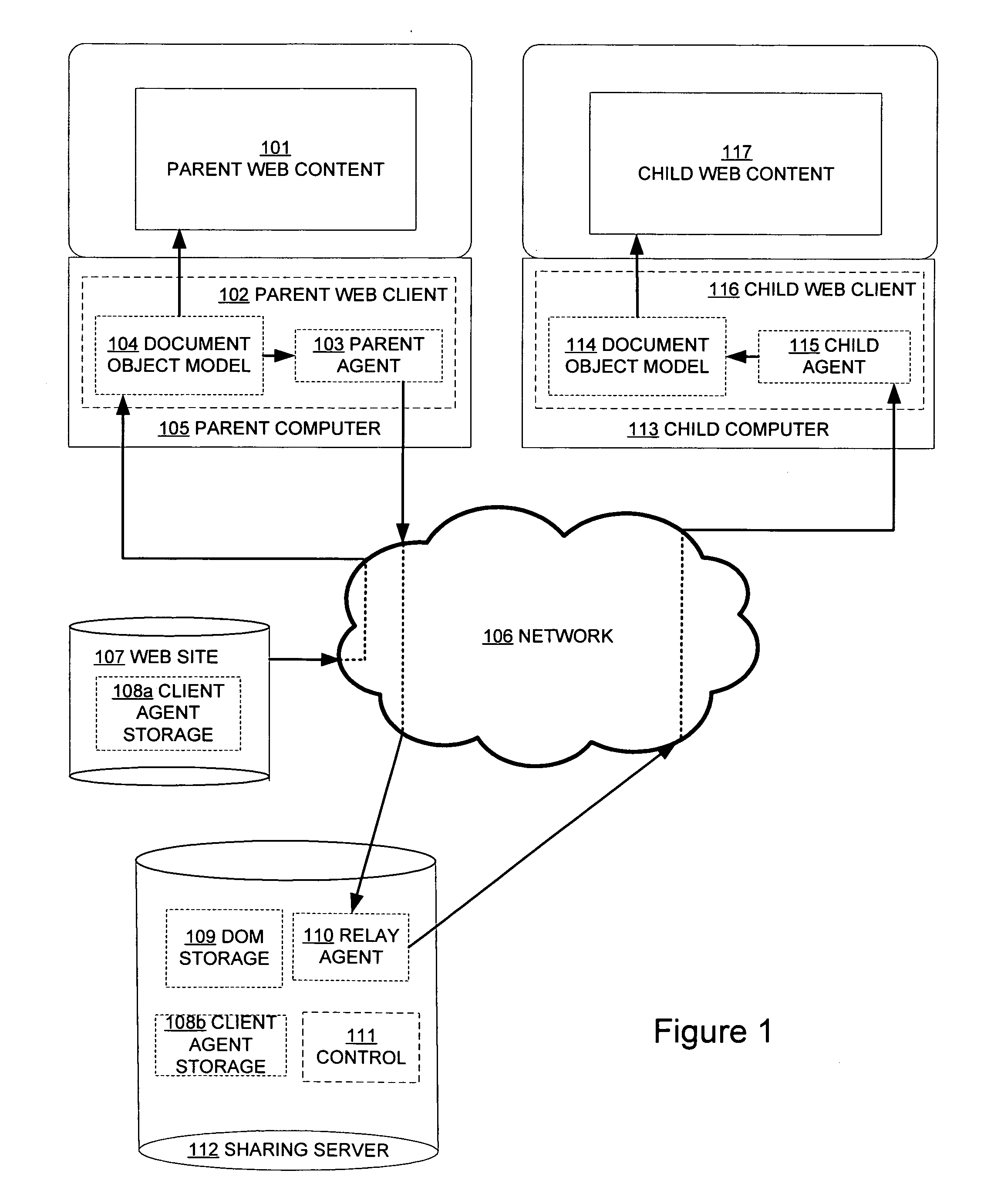
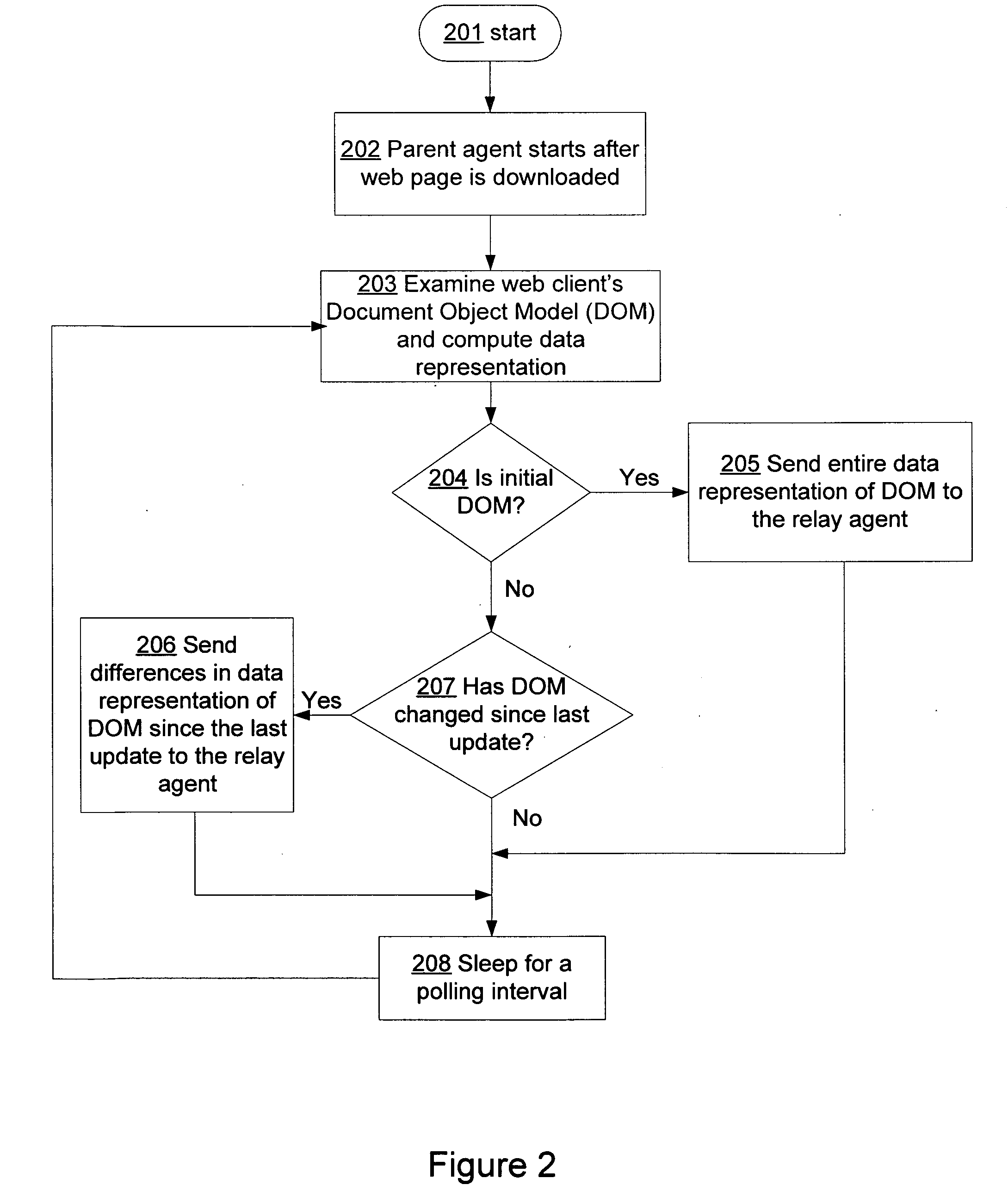
Method and system to share content between web clients
InactiveUS20090037517A1Accurate displayEfficient sharingMultiple digital computer combinationsWebsite content managementClient-sideClient state
A method and system for sharing content between web clients. Specifically, a client computes and transmits its displayed content and web client state to one or more other web clients, which display the content. This enables the web clients to share the exact displayed content, even in the presence of dynamic modifications of the content local to the client.
Owner:FREI RANDALL WAYNE
Stored value transaction system including an integrated database server
InactiveUS7216091B1Efficient sharingAvoiding duplicate recordFinanceMultiple digital computer combinationsDatabase serverIntegrated database
An integrated database and information server are provided that efficiently share information and tasks between various stored value programs. A server is configured to provide reusable objects and data structures that are suitably shared between various stored value products. A database at the server allows data to be shared between various programs so that each consumer associates with only one database record even though that consumer may use multiple shared value products. An exemplary common record for a consumer includes information relating to mailing addresses, preferred language, and the like. By integrating modules and avoiding duplicate records, the record communicates with all stored value programs, so the information does not need to be repeatedly entered into the database. Moreover, new stored value products are quickly and easily created through selection and arrangement of various shared objects preferably maintained within the database.
Owner:LIBERTY PEAK VENTURES LLC
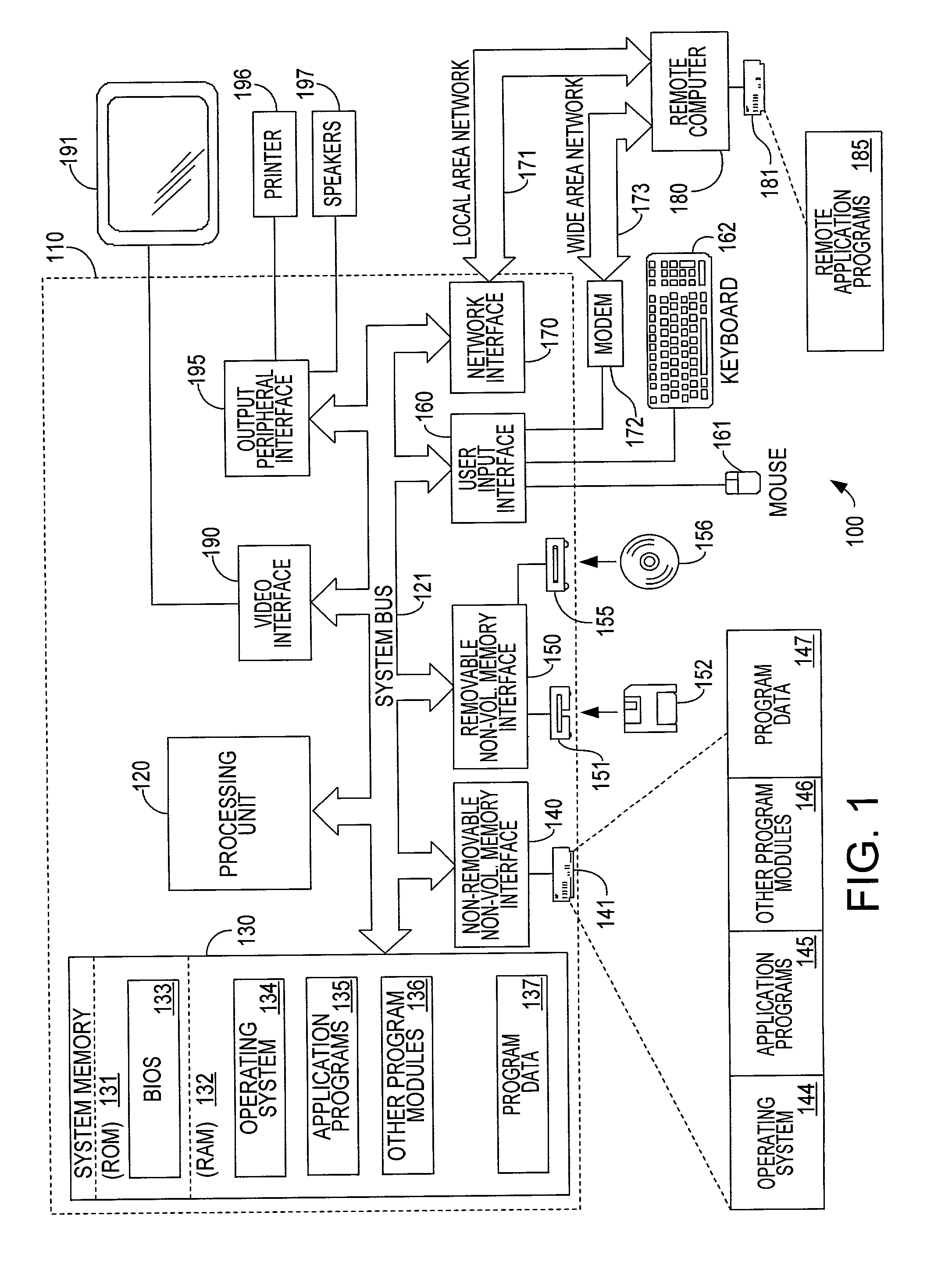
Graphics display system for multiple remote terminals
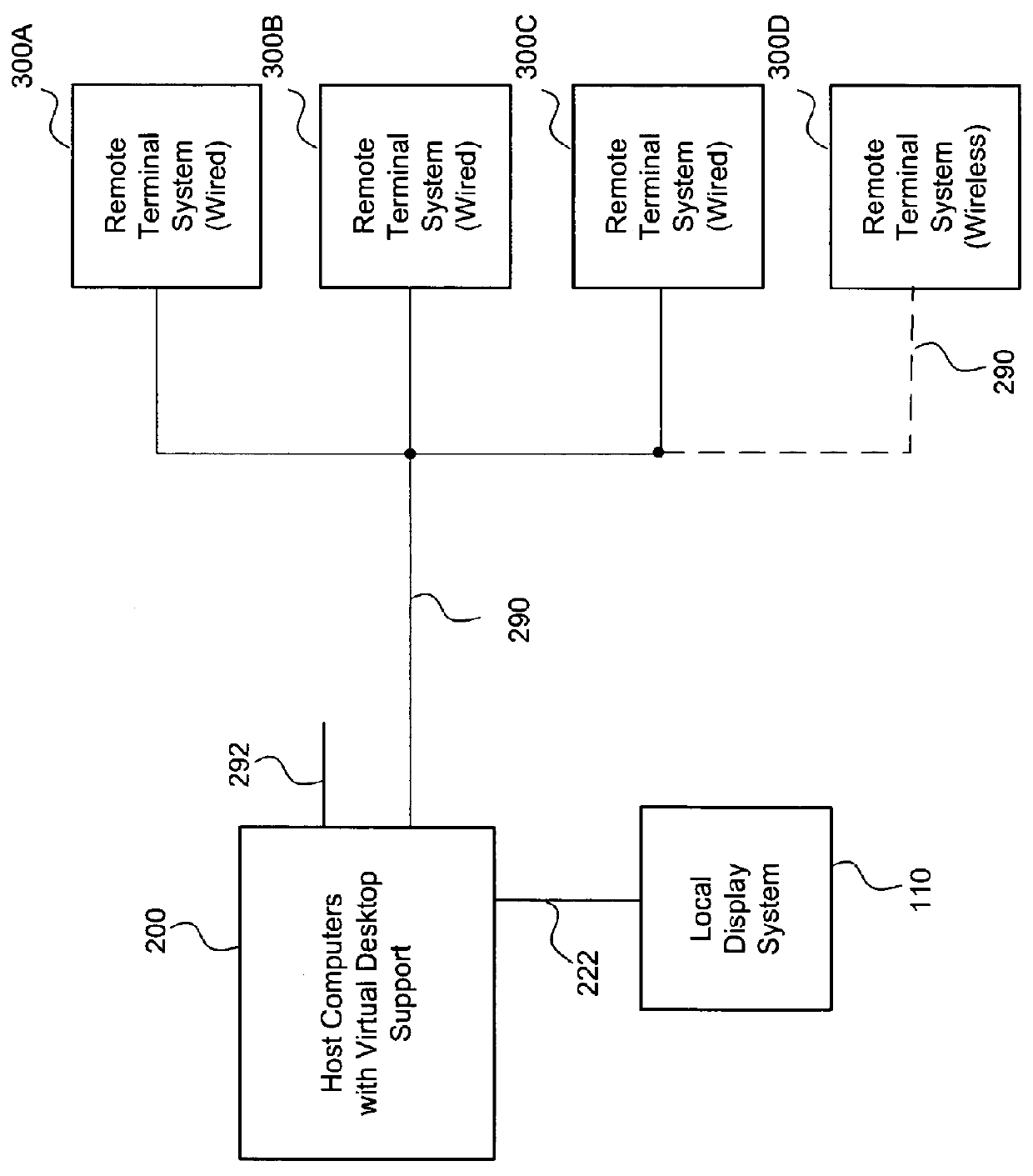
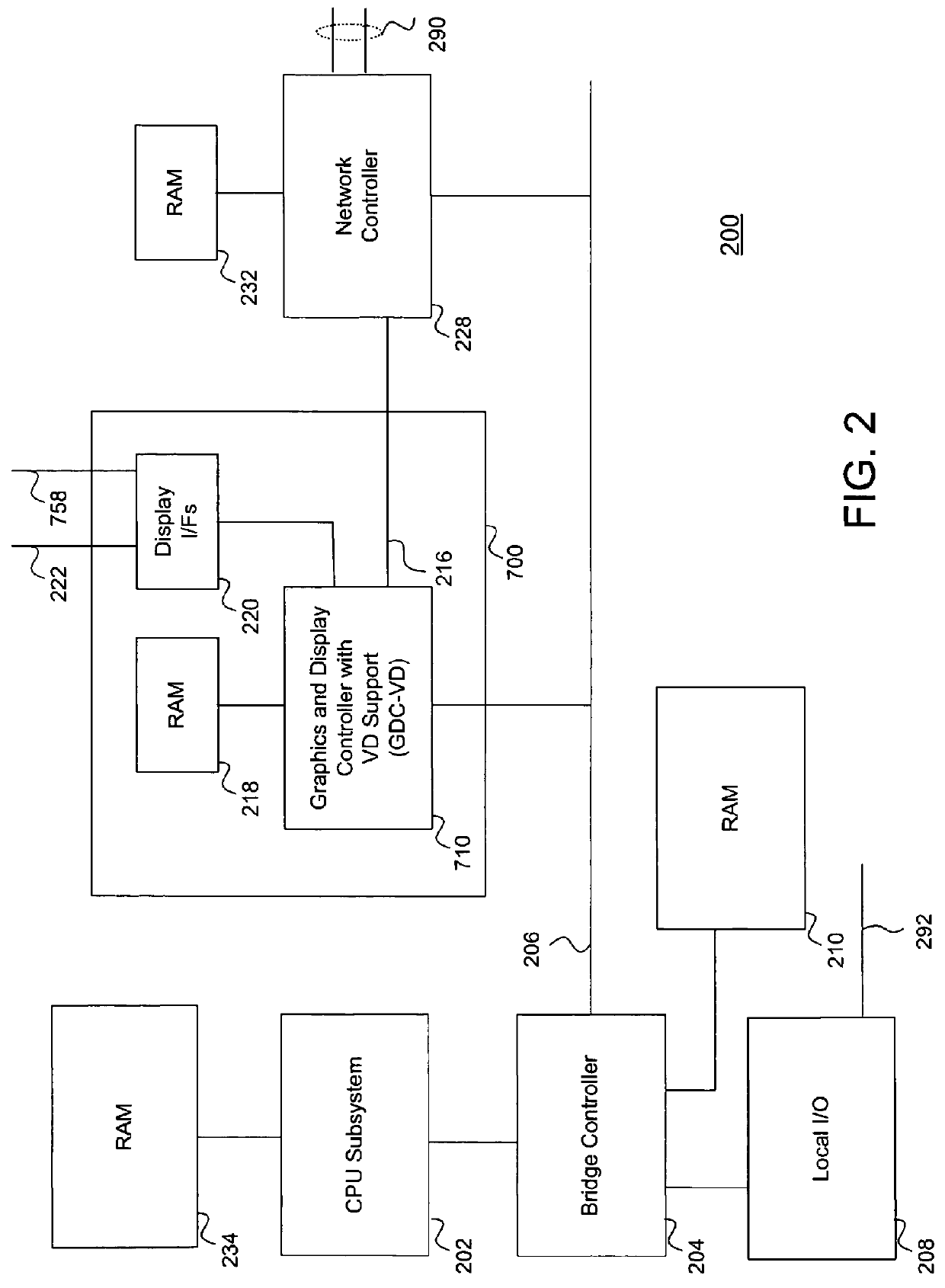
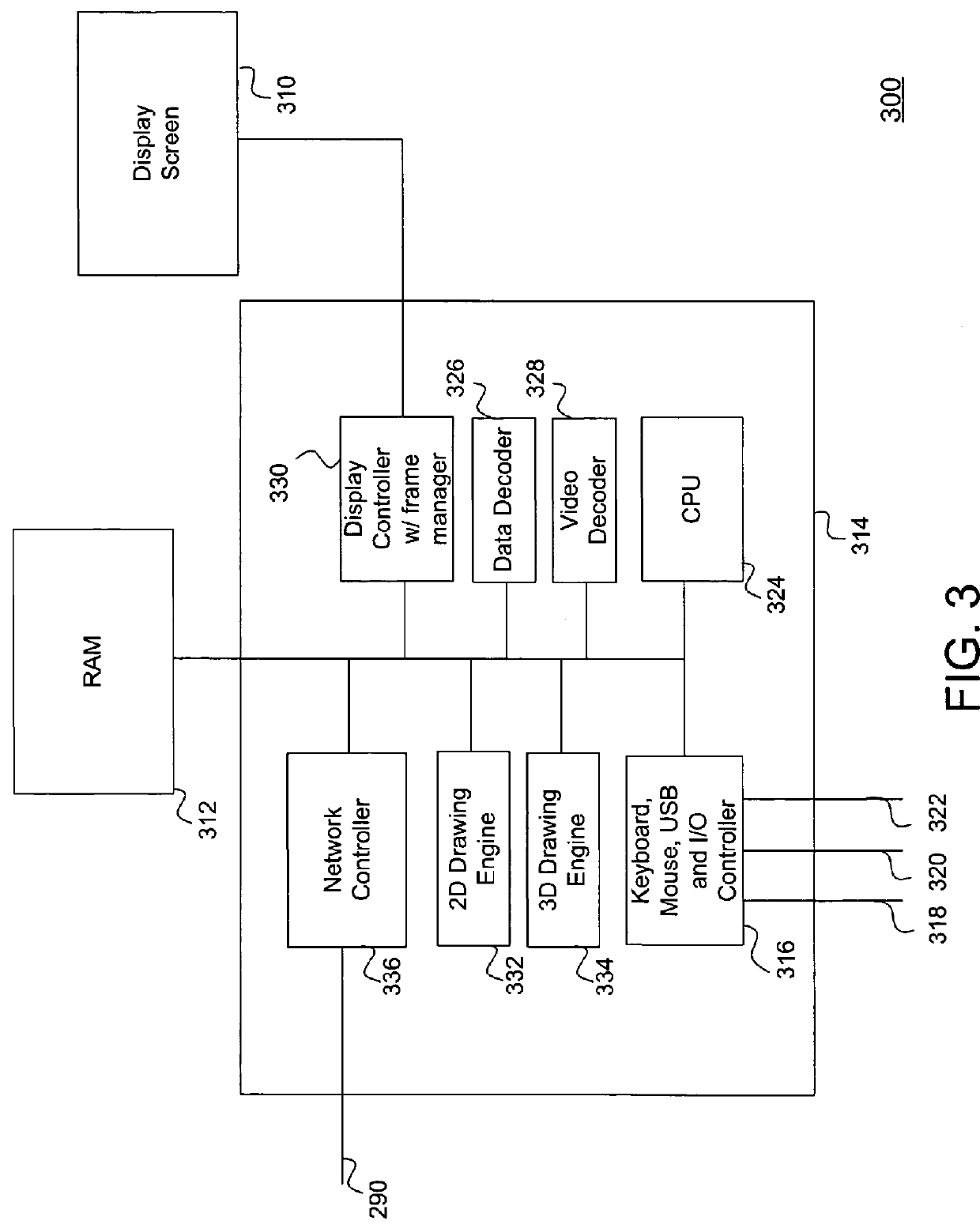
ActiveUS8200796B1Increase performanceMore computing resourceTelevision system detailsMultiple digital computer combinationsVirtual desktopMulti-monitor
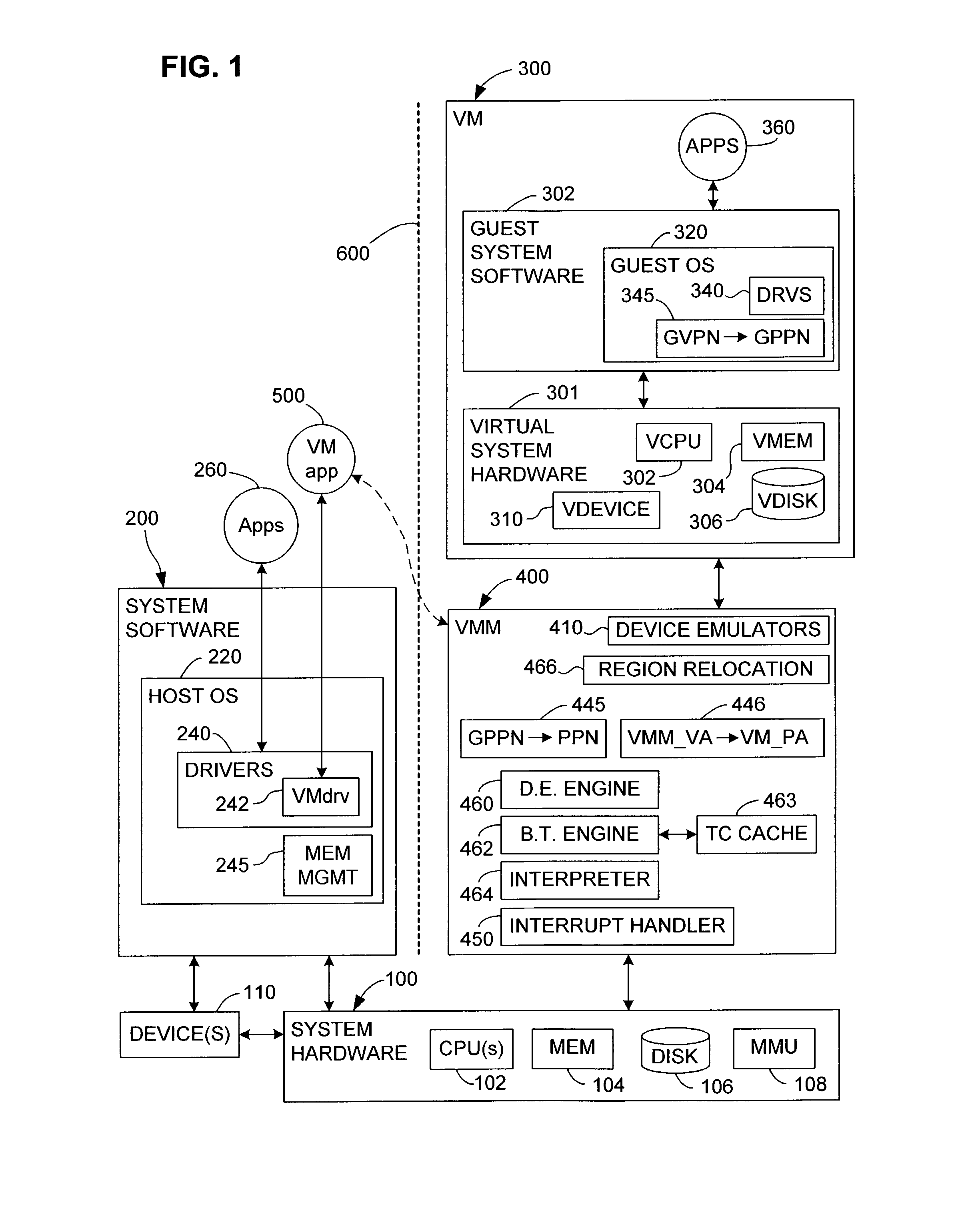
An efficient architecture for a virtual desktop system in a Virtual Machine Monitor (VMM) operating environment. In one embodiment, initially, a virtual desktop computer system utilizing one or more host computer systems provides one or more remote display systems with interactive graphics and video capabilities. The host computer system generally manages windows and frames that correspond to remote display systems and manages updating the remote display systems over a network connection. Preferred embodiments include a multi-display processor that is enhanced for VMM operating environments.VMM operating environments typically consist of different Virtual Machines (VMs) and a control layer known as the Virtual Machine Monitor (VMM) that manages the different VMs. Each VM is typically designed to be unaware of the existence of other VMs and the VMM is designed to provide the necessary abstraction, isolation and coordination between the different VMs to the physical platform hardware.
Owner:III HLDG 1
Method for automatically implementing special forms in an e-mail system
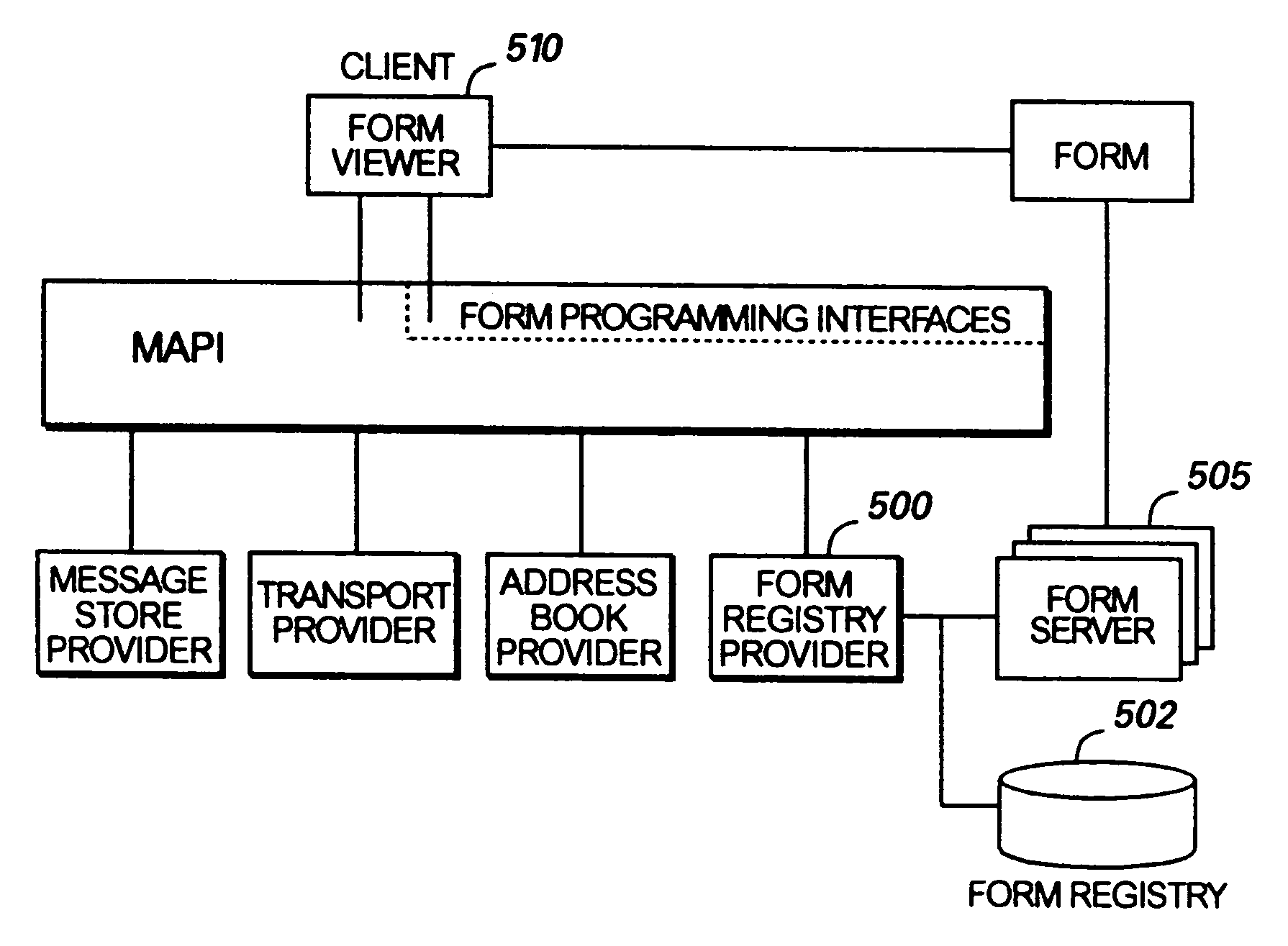
InactiveUS7010616B2Efficient sharingSimple processNatural language data processingMultiple digital computer combinationsDatabaseElectronic mail
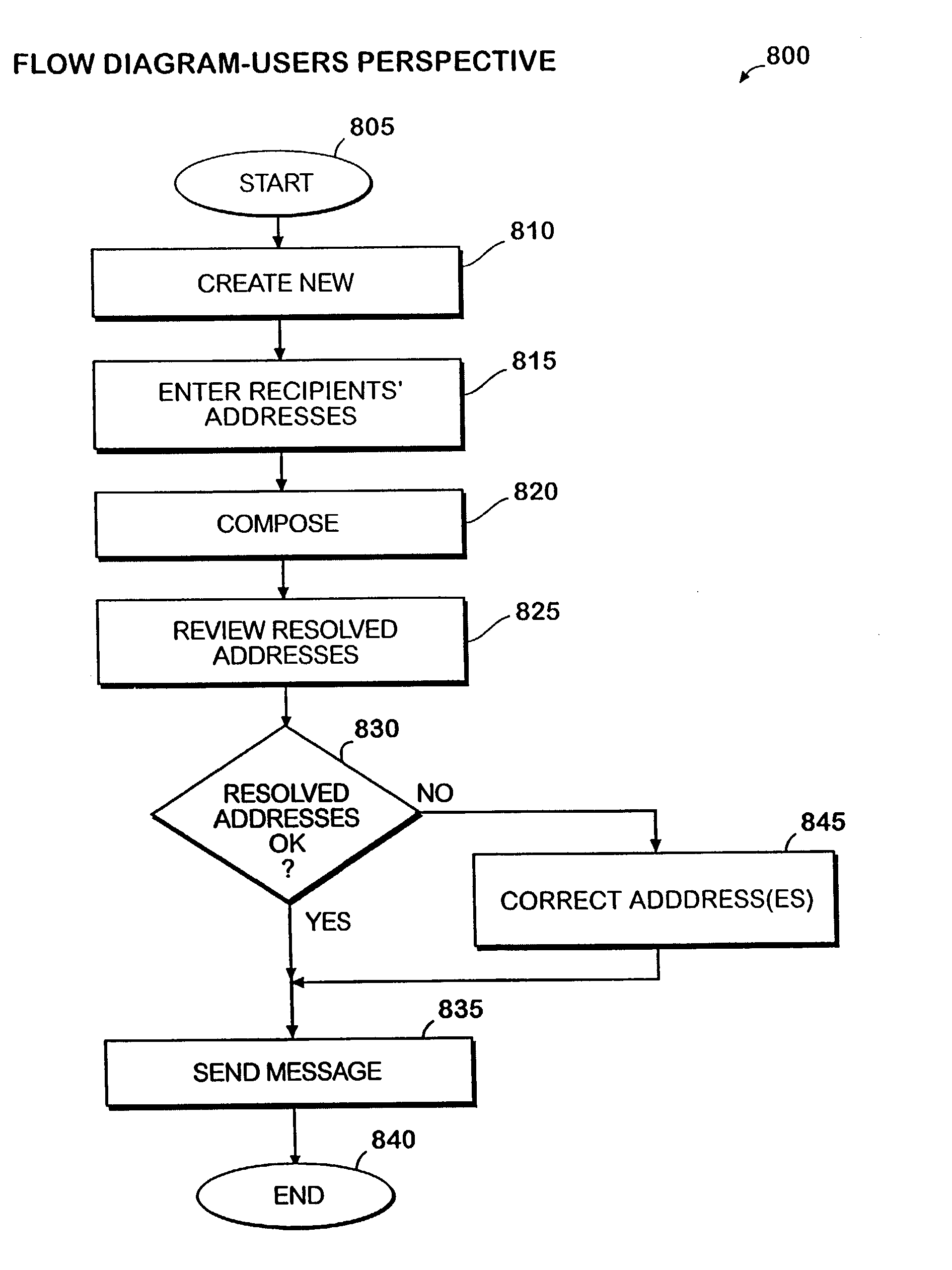
In an electronic mail system environment, a system and method for automatically checking recipients' names, providing message flags, providing custom forms, and providing an autoresponse feature. Recipients' names are resolved in the background, while the user of the e-mail system is composing the message. The user easily resolves ambiguous names by using a context menu. The resolved ambiguous names are automatically used to create nicknames, which are used to resolve ambiguous names in the future. Message flags allow a sender or recipient to identify required follow-up action and a deadline. The recipient may use the message flags to quickly determine which messages require follow-up action. The e-mail system notifies a recipient when a due date is approaching or when a follow-up action is past due. A custom forms feature allows a user to create and share custom forms without requiring the form to be published or installed by other user. The custom form's attributes are transmitted to the recipient as an element of the e-mail message. An autoresponse feature allows a sender to create a message that includes voting buttons corresponding to the possible responses to a query. A recipient replies by selecting one of the voting buttons. The recipient's vote is automatically tallied in the sender's copy of the message, thus allowing the sender to view a vote tally, a list of the recipients, and their response.
Owner:MICROSOFT TECH LICENSING LLC
Multicast control systems and methods for dynamic, adaptive time, bandwidth,frequency, and satellite allocations
InactiveUS7236738B2Additional satellite capacityOptimize resource allocationNetwork traffic/resource managementNetwork topologiesControl systemThe Internet
Methods and systems to efficiently share multiple satellites and associated transponders or links among a network of uplinking earth stations are disclosed. An embodiment of this invention uses a terrestrial communications link, such as the Internet, to control access to the transponder or satellite links. Communications over this link may employ a TCP / IP protocol to connect the requesting uplinking earth stations with a centralized controller. This control system creates more efficient use of satellite resources and reduces the overall amount of time needed for transmitting data through the satellite. By reducing the overall amount of time needed for transmitting data, the control system may reduce the cost of using the satellite transponder capacity.
Owner:EXTREME REACH INC +1
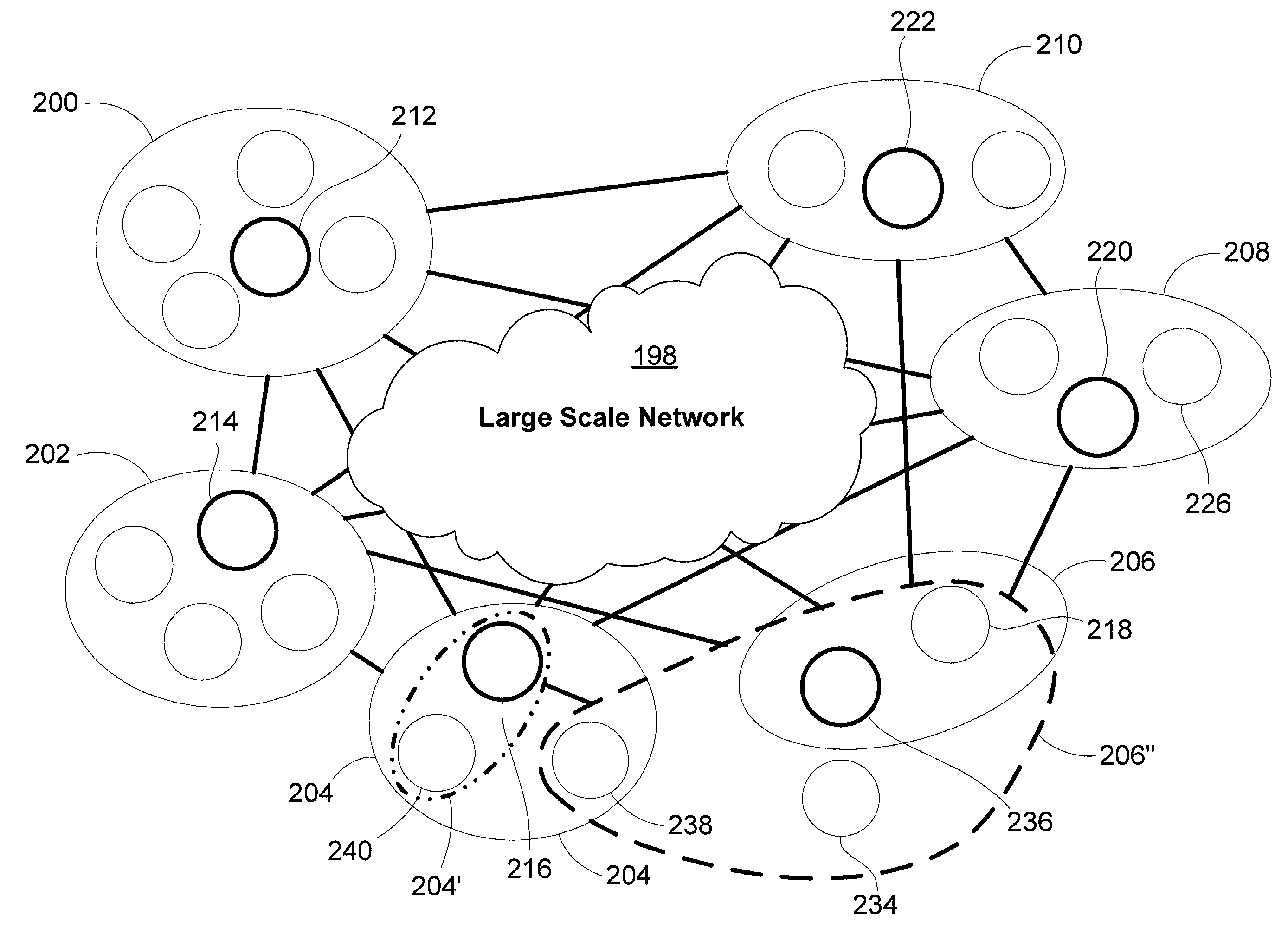
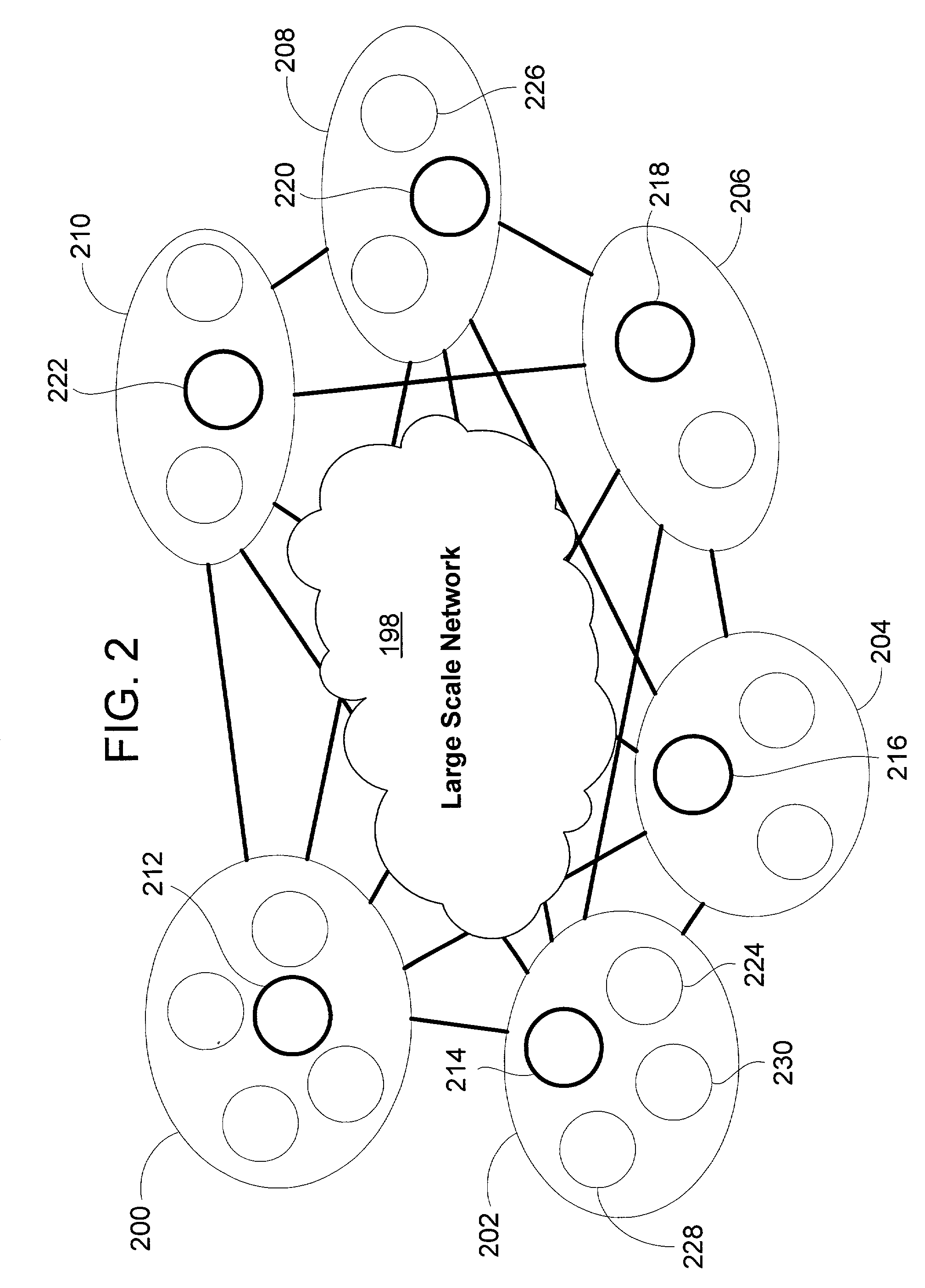
Peer-to-peer based network performance measurement and analysis system and method for large scale networks
ActiveUS7194002B2Improve balanceSlowed network performanceSpecial service provision for substationDigital computer detailsSelf formingGroup method
A network performance (e.g., latency and bandwidth) measurement infrastructure for large scale networks based on self-organized probing groups of devices. Each group of devices has a lead device that measures network characteristics, and then shares the measurement information with other devices. This grouping method reduces the amount of network bandwidth needed for adequate measurements, while still providing necessary information to individual devices. The system utilizes a novel multicast-based algorithm that is adopted for both intra-group and inter-group performance measurement. The measurement groups (MeGroups) are dynamic and self-forming, and use a set of heuristic algorithms to optimize the dynamic groupings.
Owner:MICROSOFT TECH LICENSING LLC
Virtualization system for computers with a region-based memory architecture
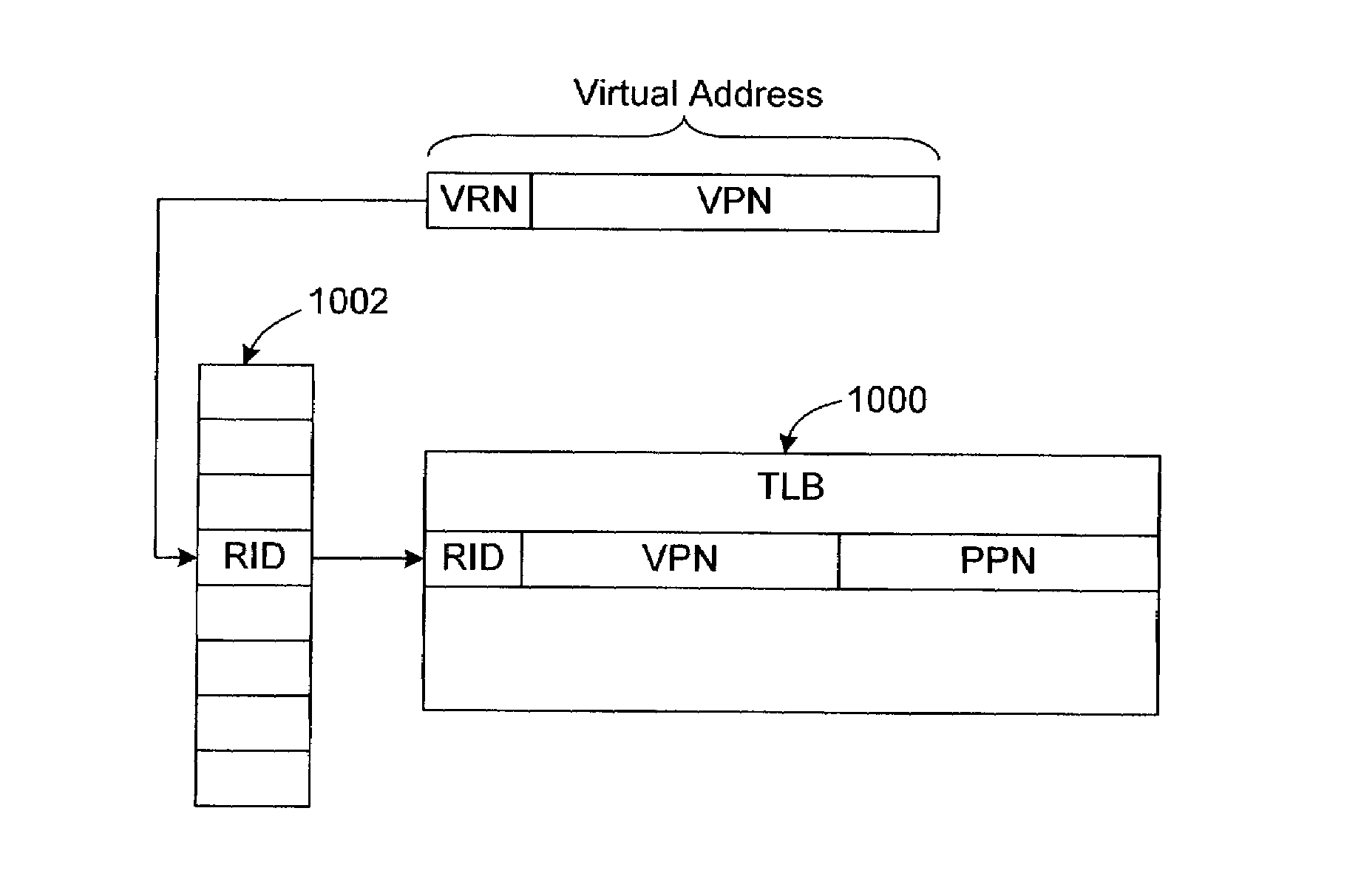
ActiveUS7089377B1Efficient sharingSoftware simulation/interpretation/emulationMemory systemsVirtualizationProcessor register
In a computer system with a non-segmented, region-based memory architecture, such as Intel IA-64 systems, two or more sub-systems share a resource, such as a virtual-to-physical address mapping and need to have overlapping regions of the virtual address space for accessing different physical addresses. Virtual addresses include a portion that is used to identify which region the issuing sub-system wants to access. For example, the region-identifying portion of virtual addresses may select a region register whose contents point to a virtual-to-physical address mapping for the corresponding region. To protect a second sub-system S2 from a first S1, whenever the S1 issues an address in a region occupied by S2, the region for the S2 is changed. This allows S1 to issue its addresses without change. In a preferred embodiment of the invention, S2 is a virtual machine monitor (VMM) and S1 is a virtual machine running on the VMM.
Owner:VMWARE INC
System and method for composing, processing, and organizing electronic mail message items
InactiveUS20030120737A1Efficient sharingSimple processNatural language data processingMultiple digital computer combinationsElectronic mailContext menu
In an electronic mail system environment, a system and method for automatically checking recipients' names, providing message flags, providing custom forms, and providing an autoresponse feature. Recipients' names are resolved in the background, while the user of the e-mail system is composing the message. The user easily resolves ambiguous names by using a context menu. The resolved ambiguous names are automatically used to create nicknames, which are used to resolve ambiguous names in the future. Message flags allow a sender or recipient to identify required follow-up action and a deadline. The recipient may use the message flags to quickly determine which messages require follow-up action. The e-mail system notifies a recipient when a due date is approaching or when a follow-up action is past due. A custom forms feature allows a user to create and share custom forms without requiring the form to be published or installed by other user. The custom form's attributes are transmitted to the recipient as an element of the e-mail message. An autoresponse feature allows a sender to create a message that includes voting buttons corresponding to the possible responses to a query. A recipient replies by selecting one of the voting buttons. The recipient's vote is automatically tallied in the sender's copy of the message, thus allowing the sender to view a vote tally, a list of the recipients, and their response.
Owner:MICROSOFT TECH LICENSING LLC
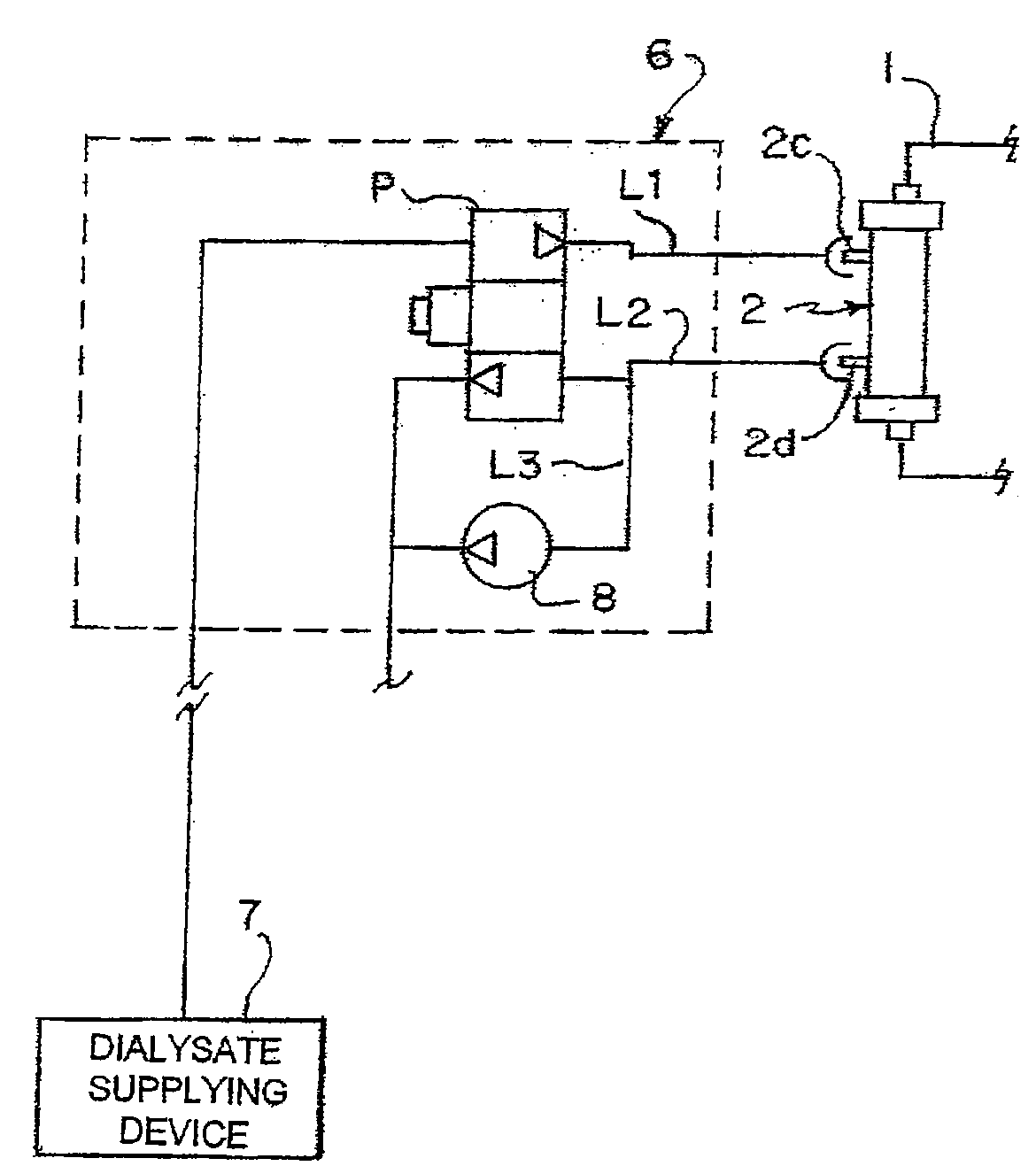
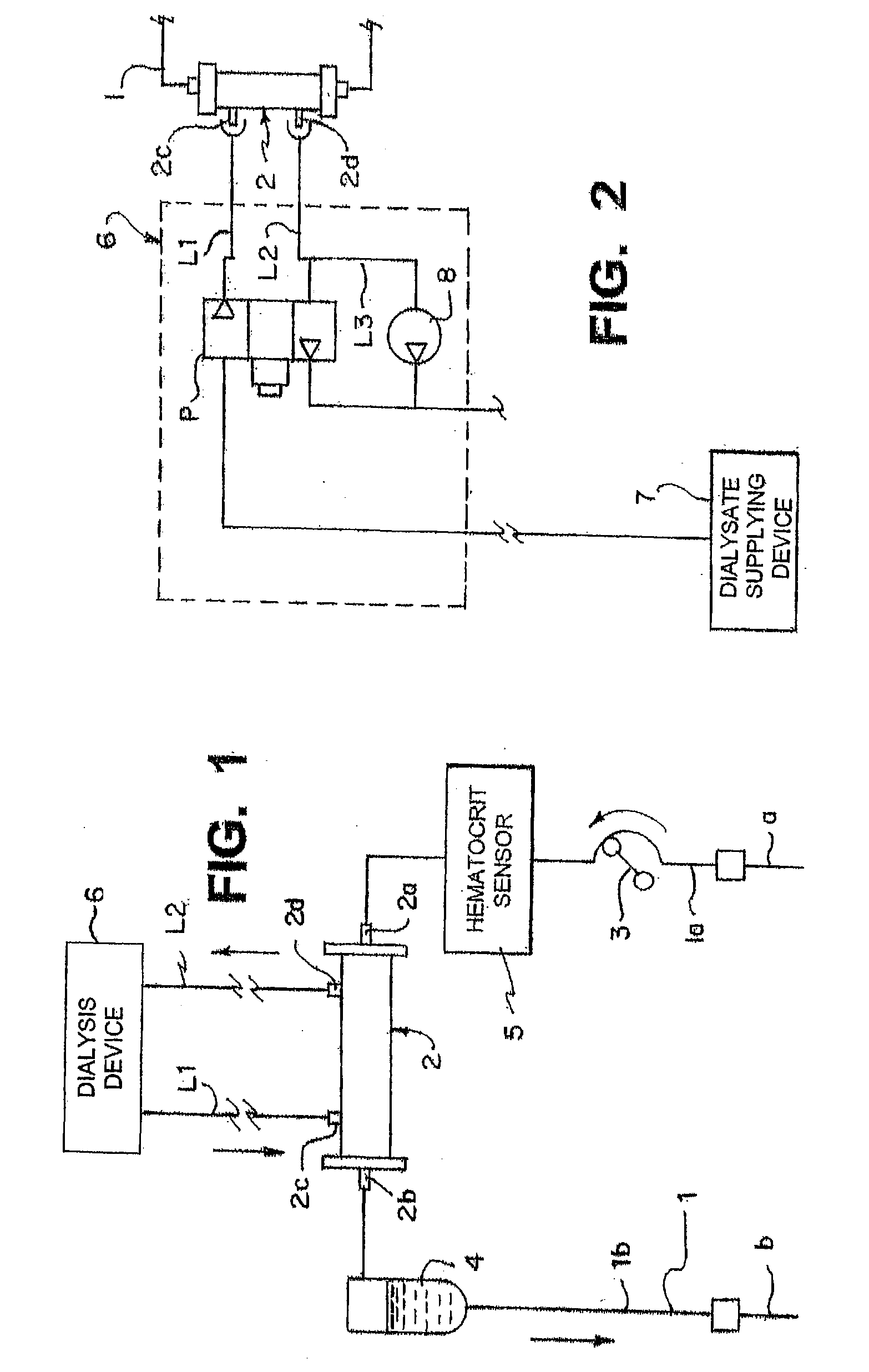
Hemodialysis apparatus and method for hemodialysis
InactiveUS20060226079A1Increase volumeEfficient sharingSemi-permeable membranesSolvent extractionExtracorporeal circulationHemodialysis
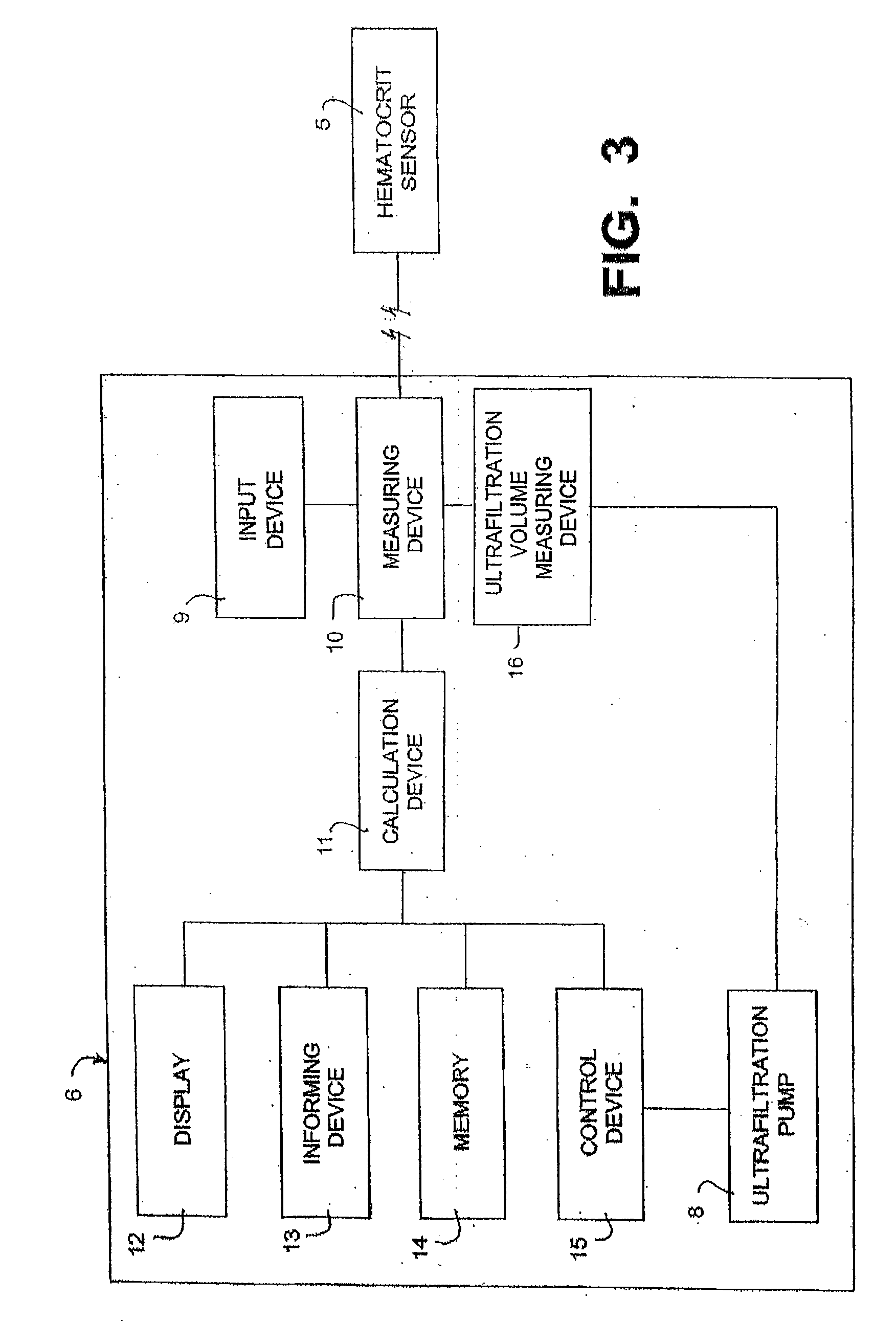
A hemodialysis apparatus includes a dialyzing device, a measuring device and a calculation device. The dialyzing device dialyzes and ultrafiltrates blood of a patient circulating extracorporeally to perform hemodialysis treatment. The measuring device measures a variation rate of a body weight of the patient and a variation rate of a predetermined blood benchmark during the hemodialysis treatment using the dialyzing device. The calculation device calculates, during the hemodialysis treatment, a parameter relating the variation rate of the body weight and the variation rate of the predetermined blood benchmark to each other, and correlating to a dry weight of the patient.
Owner:NIKKISO COMPANY
Router configured for outputting update messages specifying a detected attribute change of a connected active path according to a prescribed routing protocol
ActiveUS20050195835A1Easy to routeEfficient sharingEnergy efficient ICTData switching by path configurationData streamComputer science
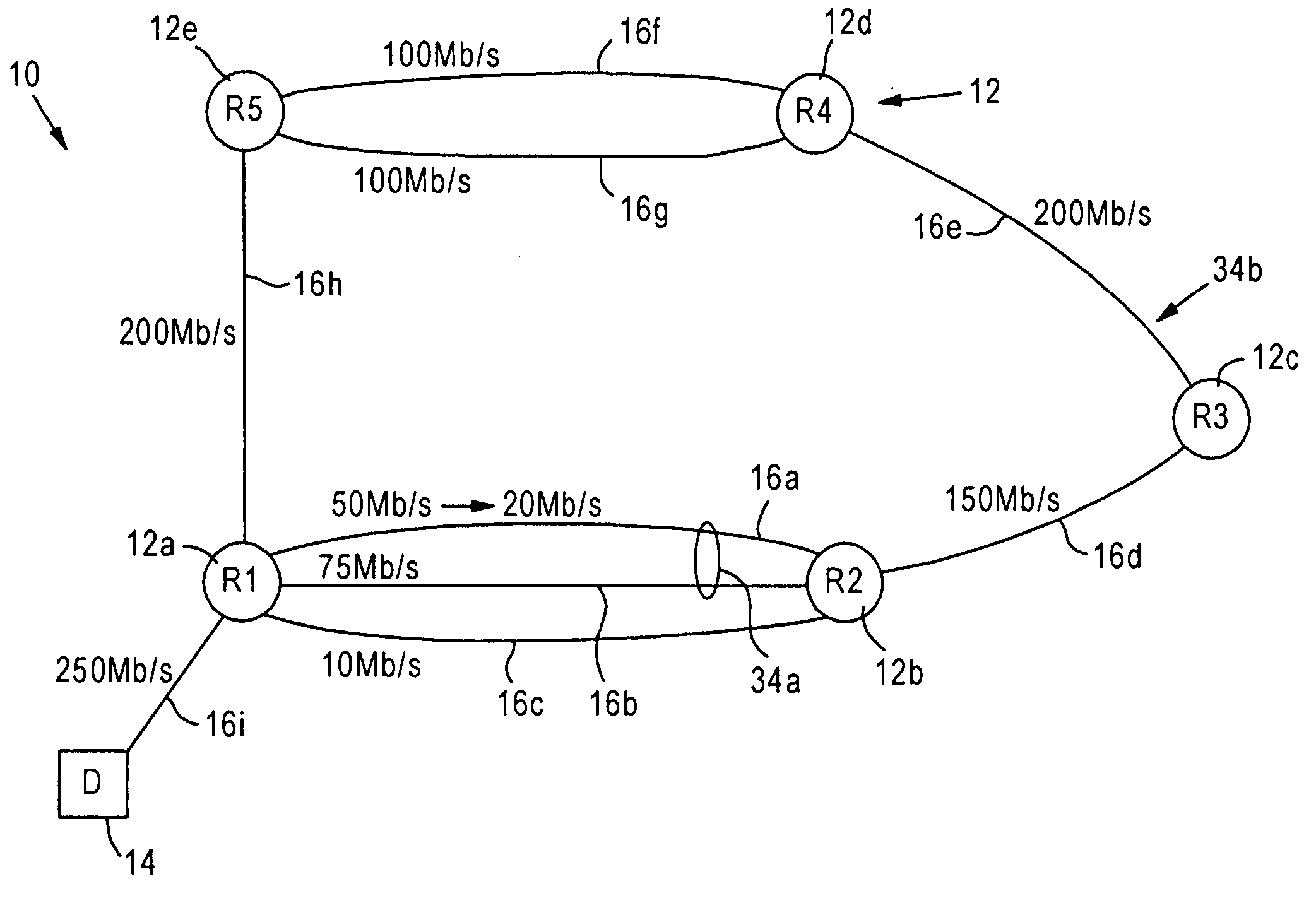
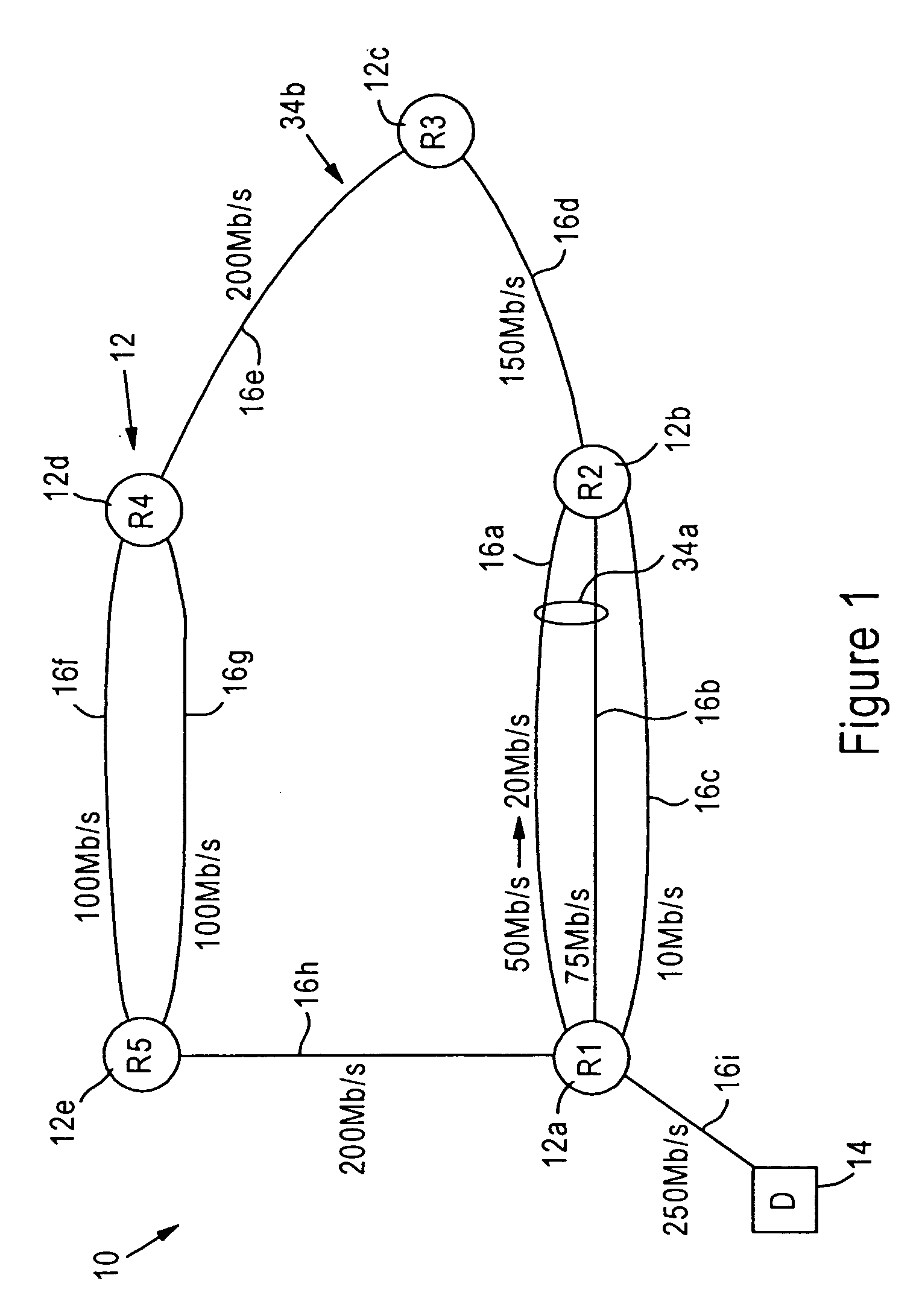
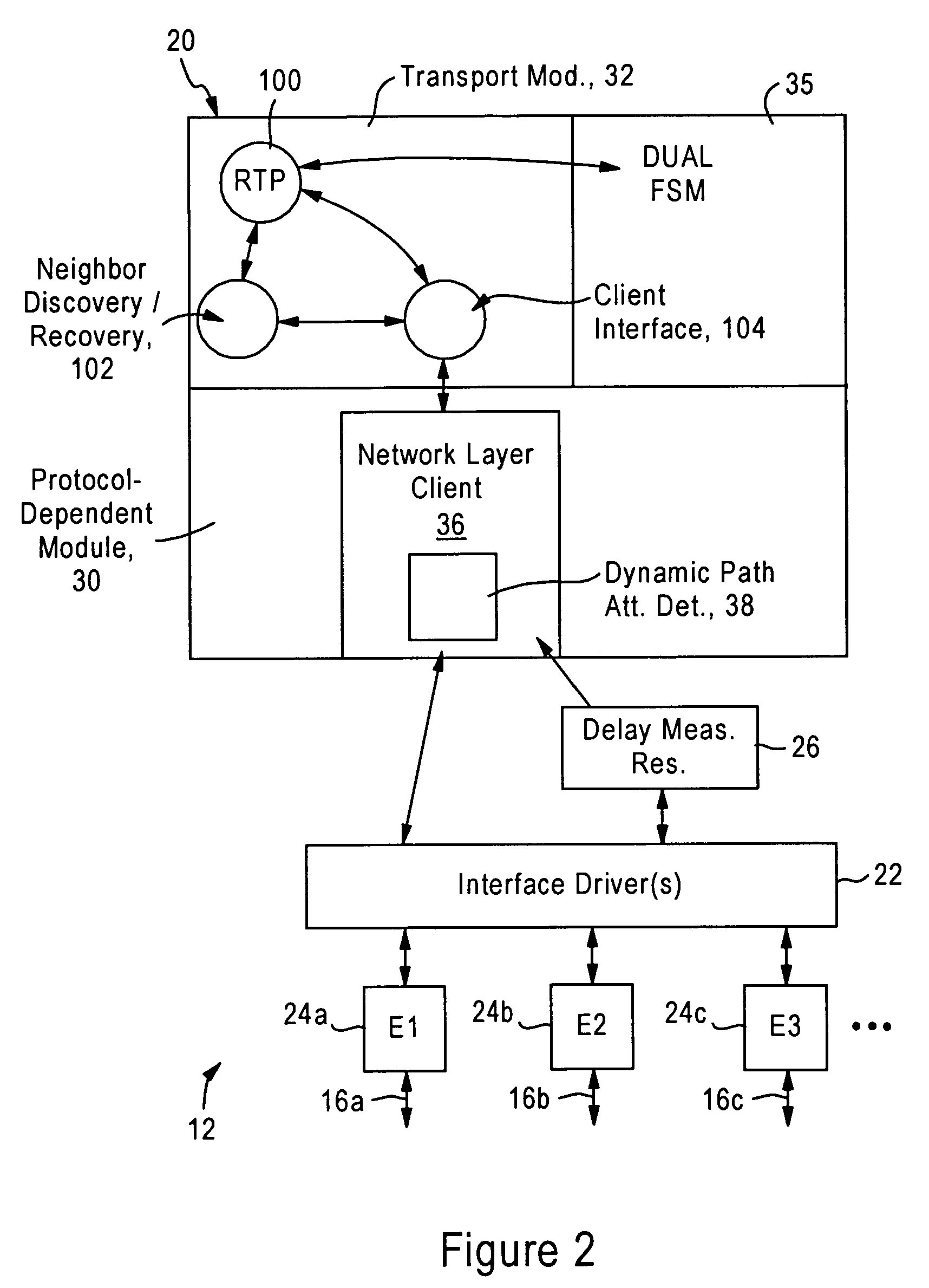
A first router is configured for monitoring prescribed attributes of an active path connected to the first router, and supplying an update message to a second router, according to a prescribed routing protocol such as Enhanced Interior Gateway Routing Protocol (EIGRP), that specifies a detected change by the first router in at least one of the prescribed attributes of the connected active path. Hence, the second router, in response to receiving the update message, can update an internal topology table based on the detected change in the active path connected to the first router, and selectively adjust an internal routing table based on the detected change relative to queuing policies for prescribed data flows.
Owner:CISCO TECH INC
Performing sequence analysis as a multipart plan storing intermediate results as a relation
InactiveUS7702610B2Reliable and high performance integrationReduce calculationMedical data miningData processing applicationsProgramming languageSequence analysis
A usage model and the underlying technology used to provide sequence analysis as part of a relational database system. Included components include the semantic and syntactic integration of the sequence analysis with an existing query language, the storage methods for the sequence data, and the design of a multipart execution scheme that runs the sequence analysis as part of a potentially larger database query, especially using parallel execution techniques.
Owner:INT BUSINESS MASCH CORP
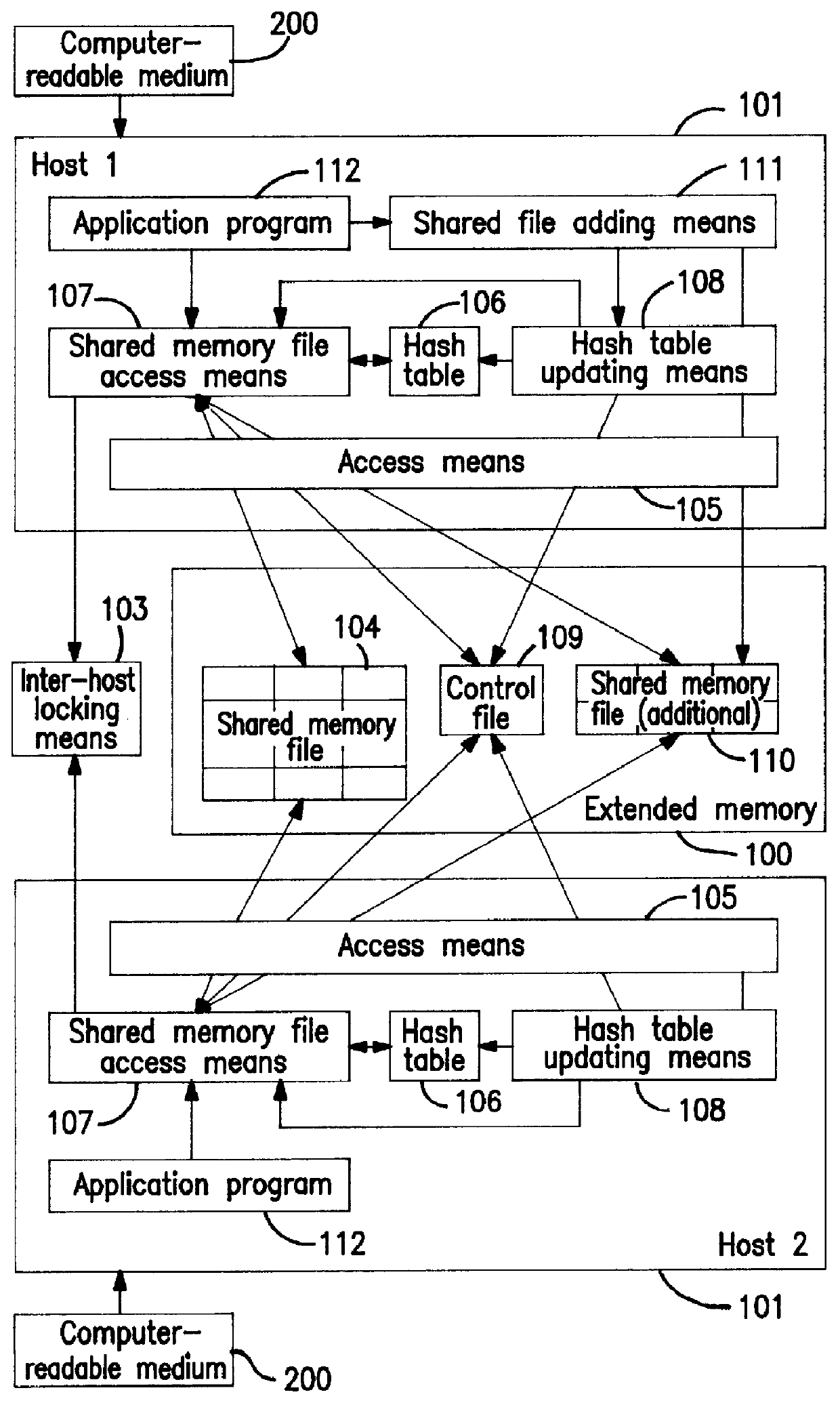
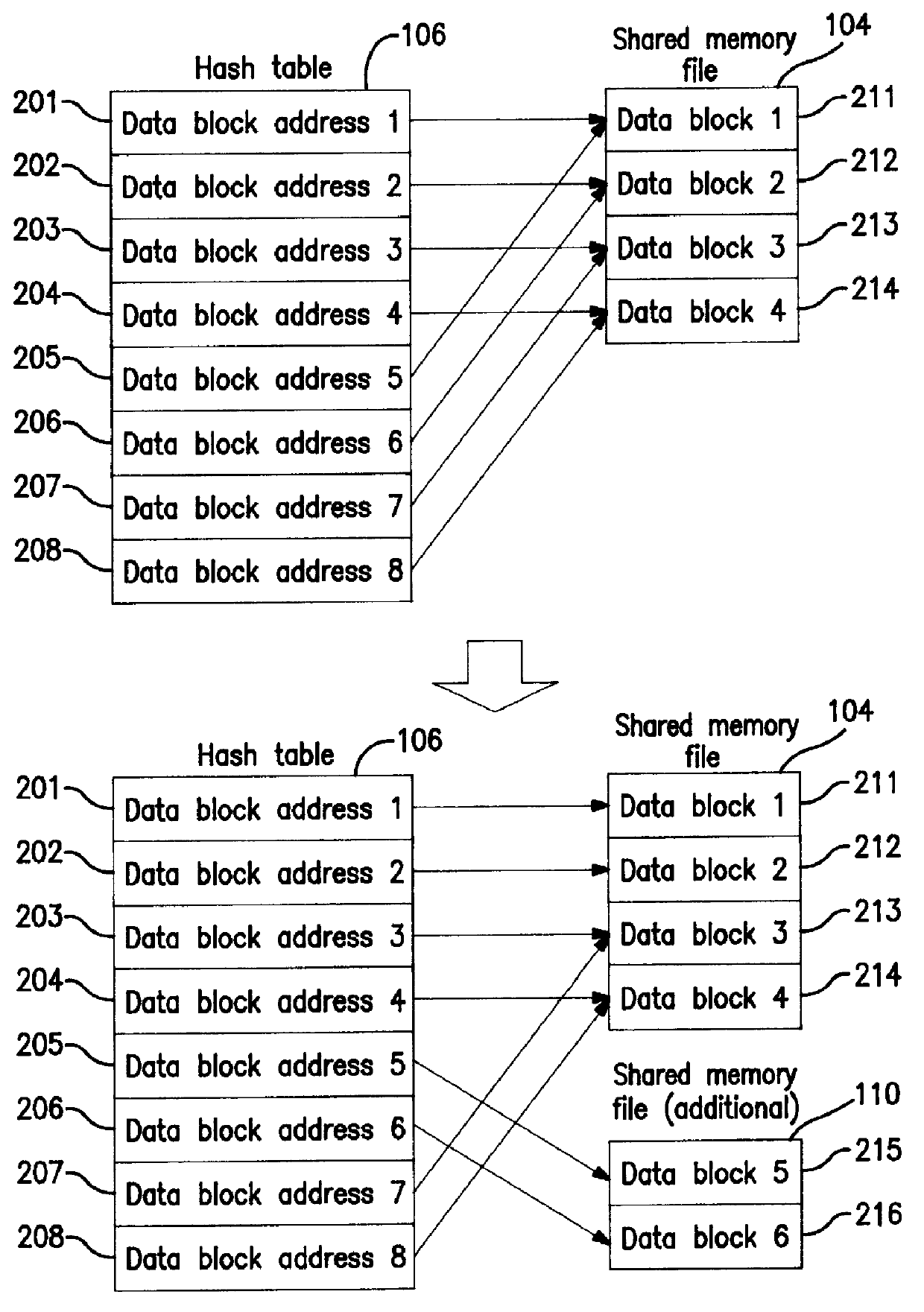
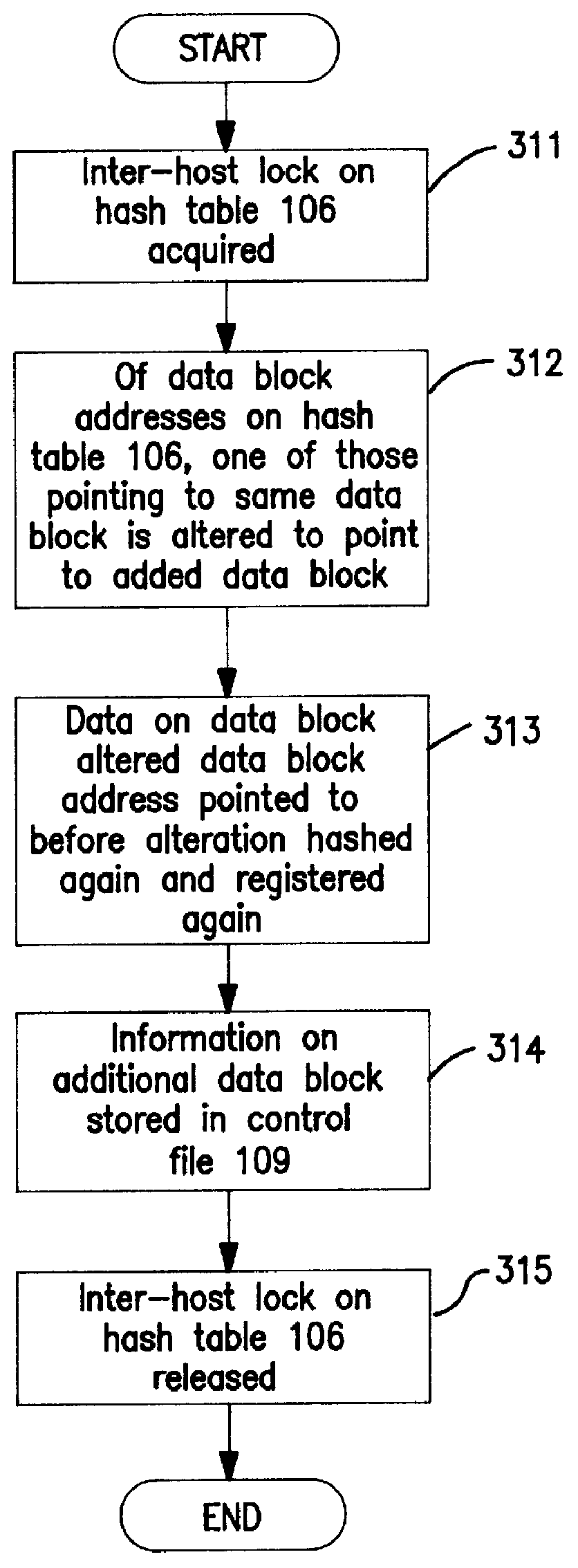
Dynamic adding system for memory files shared among hosts, dynamic adding method for memory files shared among hosts, and computer-readable medium recording dynamic adding program for memory files shared among hosts
InactiveUS6014730AEfficient sharingEasy to useProgram synchronisationMemory adressing/allocation/relocationHash tableFile sharing
In response to an extension request to a shared memory file 104, shared file adding means 111 allocates an (additional) memory file 110; inter-host locking means 103 locks a hash table 106; hash table updating means 108 checks the number of data blocks in the (additional) shared memory file, and updates the hash table 106 to alter one of the data block addresses, out of those stored in entries in the hash table 106, pointing to the same data block in the shared buffer 104 so as to point to a data block in the (additional) shared memory file 110; and the added shared memory file 110 is thereby made available for shared use.
Owner:NEC CORP
Working machine driving unit
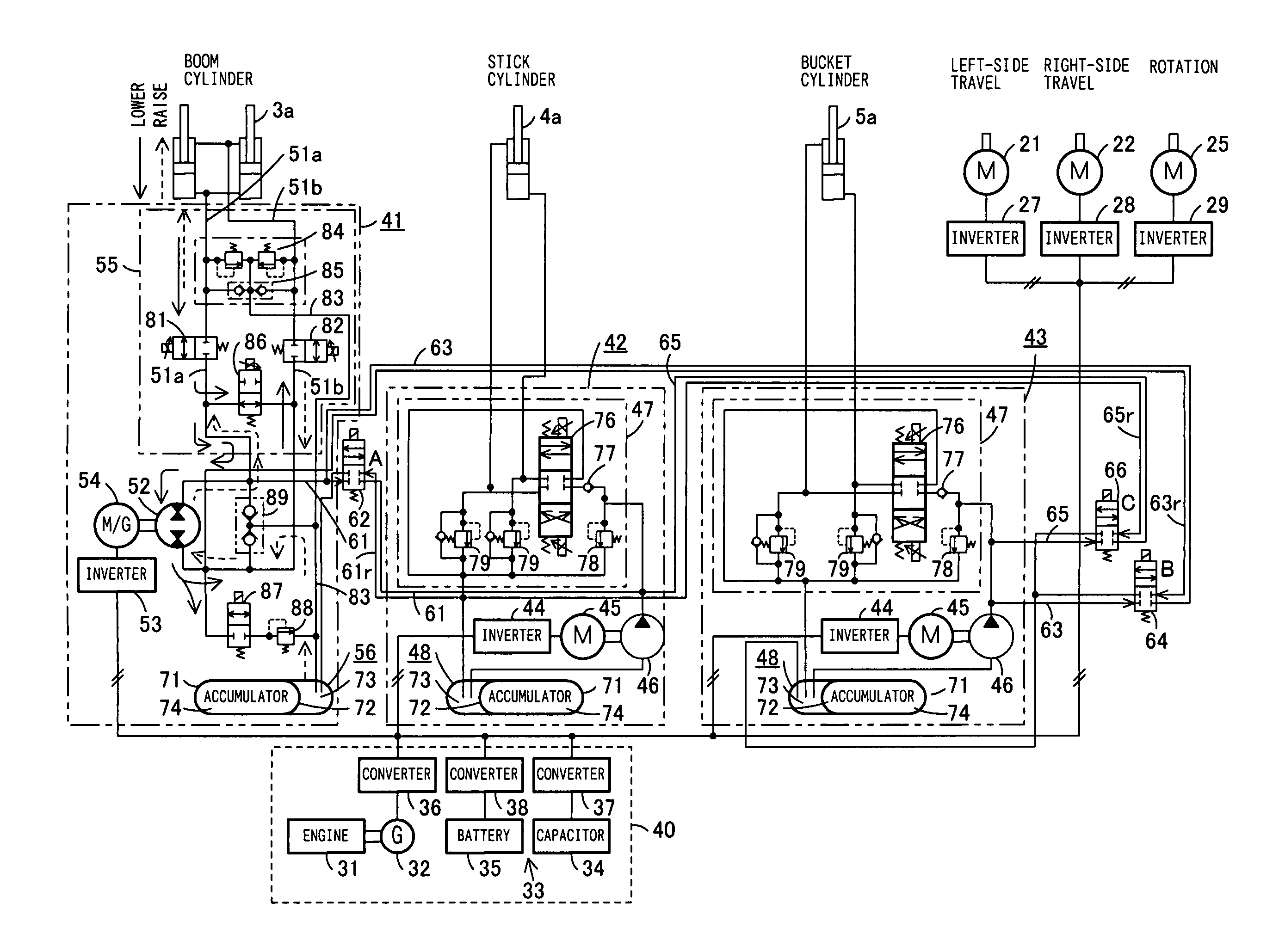
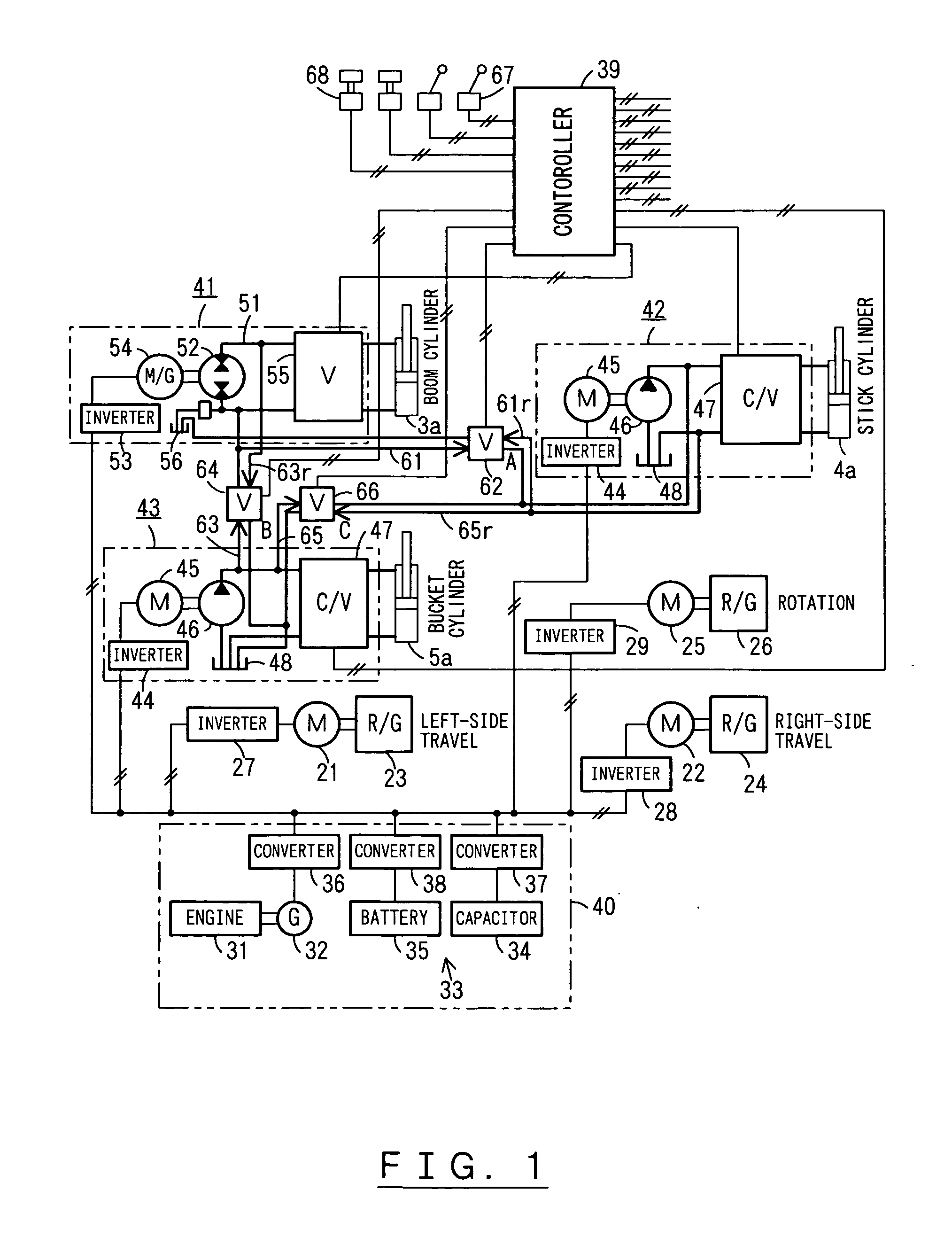
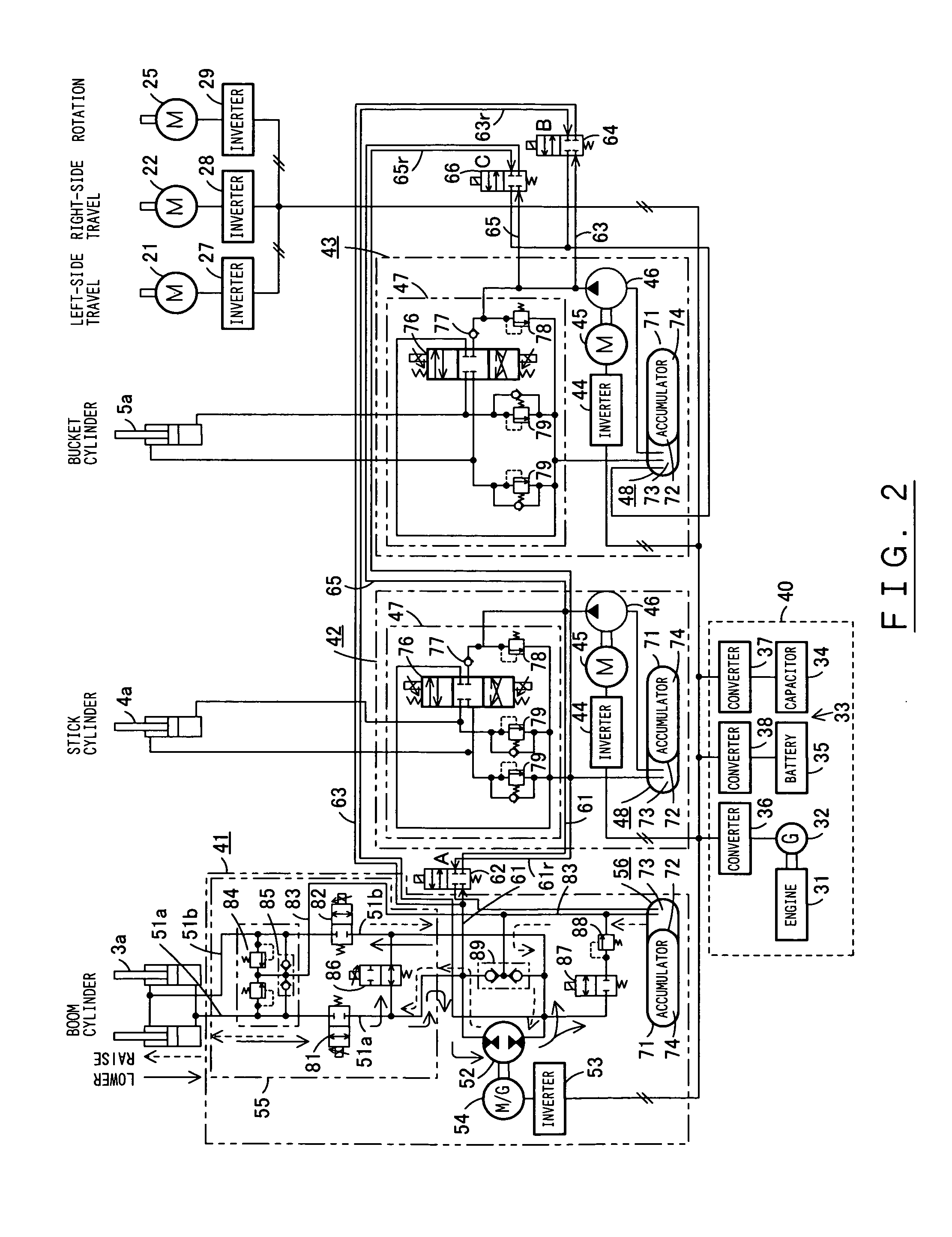
InactiveUS20050246082A1ShortfallEfficient sharingAnalogue computers for trafficServomotorsWork unitActuator
A driving device of a work machine includes a power generator adapted to be driven by an engine, and a power storage device for storing the electric power generated by the power generator. Electric motors and a motor generator, both adapted to be operated by electric power supplied from either one or both of the power generator and the power storage device respectively drive pumps and a pump motor. Supporting circuits for feeding supporting hydraulic oil are provided between a plurality of driving circuits that drive a plurality of hydraulic actuators of a working unit by oil hydraulics generated by the pumps and the pump motor. By enabling the plurality of driving circuits to effectively share excess energy, the invention makes possible a compact construction of a driving device of a work machine.
Owner:SHIN CATERPILLAR MITSUBISHI LTD CORP
Collaborative interaction method for unmanned plane cluster and visual navigation system of unmanned plane
ActiveCN102393747AReal-time planningReduce latencyInstruments for comonautical navigationPosition/course control in three dimensionsEvaluation resultCommunication quality
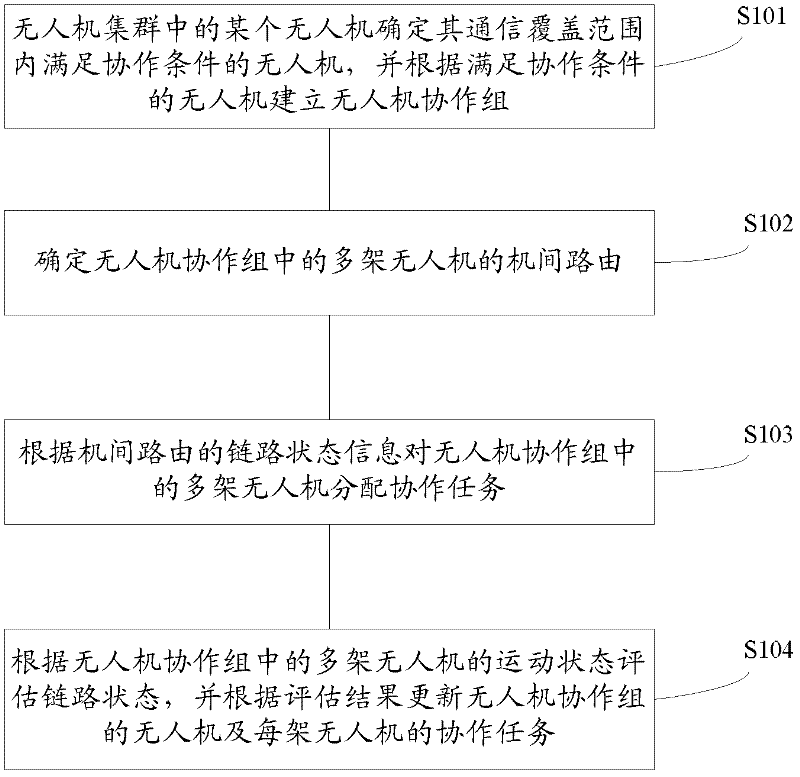
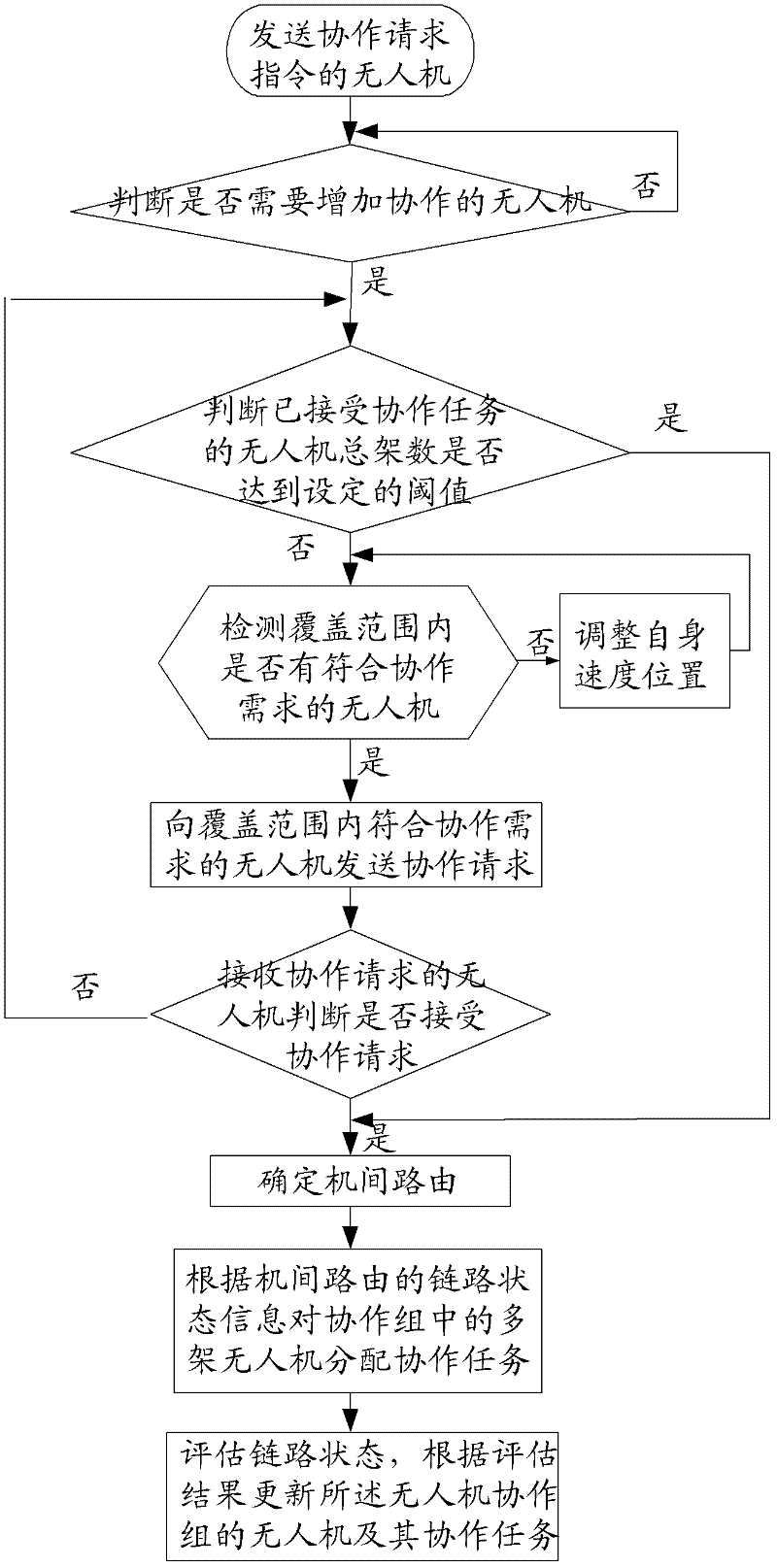
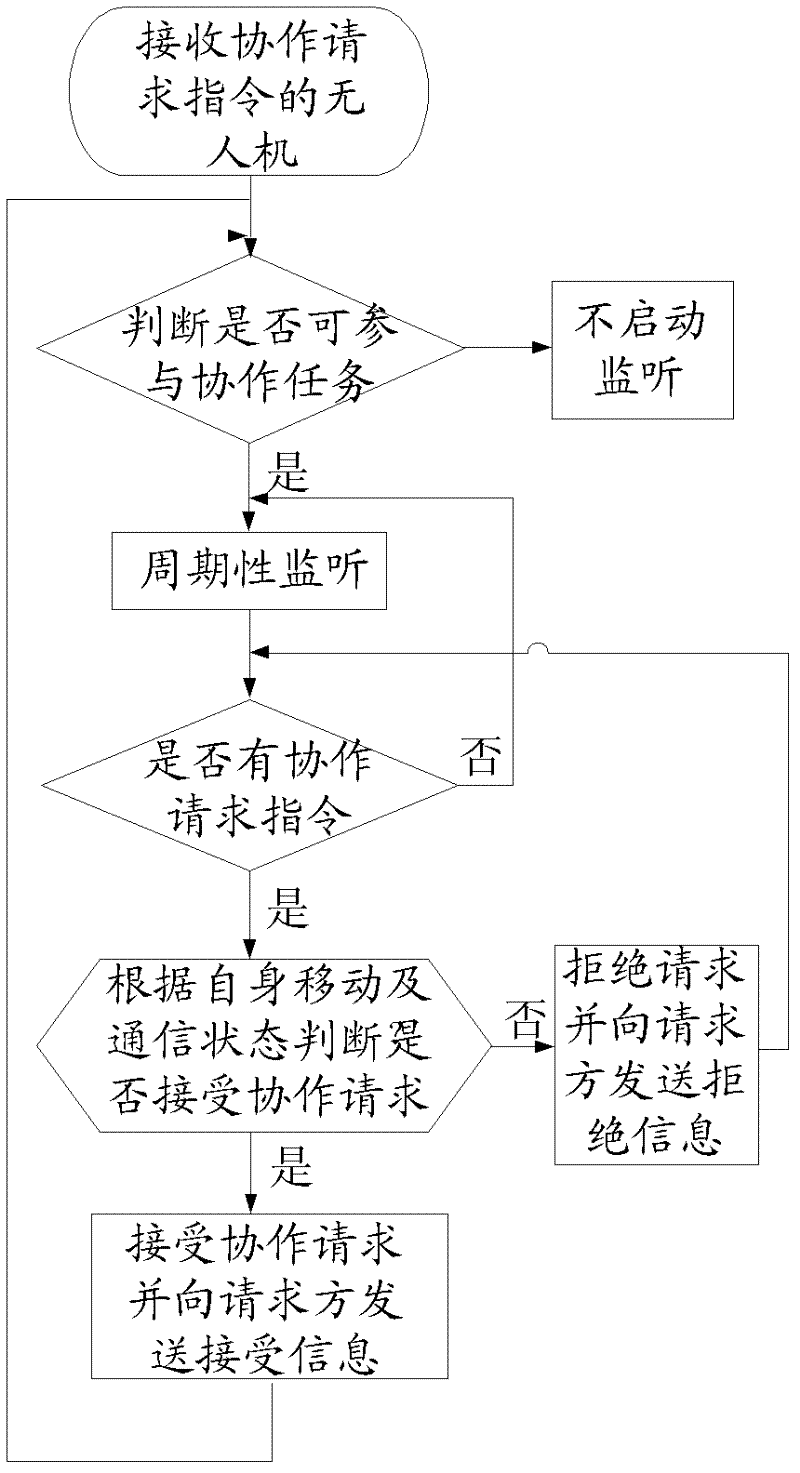
The invention discloses a collaborative interaction method for an unmanned plane cluster and a visual navigation system of an unmanned plane. The collaborative interaction method for the unmanned plane cluster comprises the following steps of: determining unmanned planes satisfying a collaborative condition in a communication coverage area of a certain unmanned plane by the unmanned plane in the unmanned plane cluster, and establishing an unmanned plane collaboration group according to the unmanned planes satisfying the collaborative condition; determining inter-plane routes of multiple unmanned planes in the unmanned plane collaboration group; allocating collaborative tasks to multiple unmanned planes in the unmanned plane collaboration group according to link state information of the inter-plane routes; and evaluating the link state according to the motion state of multiple unmanned planes in the unmanned plane collaboration group, and updating unmanned planes in the unmanned plane collaboration group and the collaborative task of each unmanned plane according to an evaluation result. The collaborative interaction method for the unmanned plane cluster is good in real-time, strong in reliability and high in communication quality, and can better adapt to an unmanned plane cluster communication environment during visual navigation.
Owner:TSINGHUA UNIV
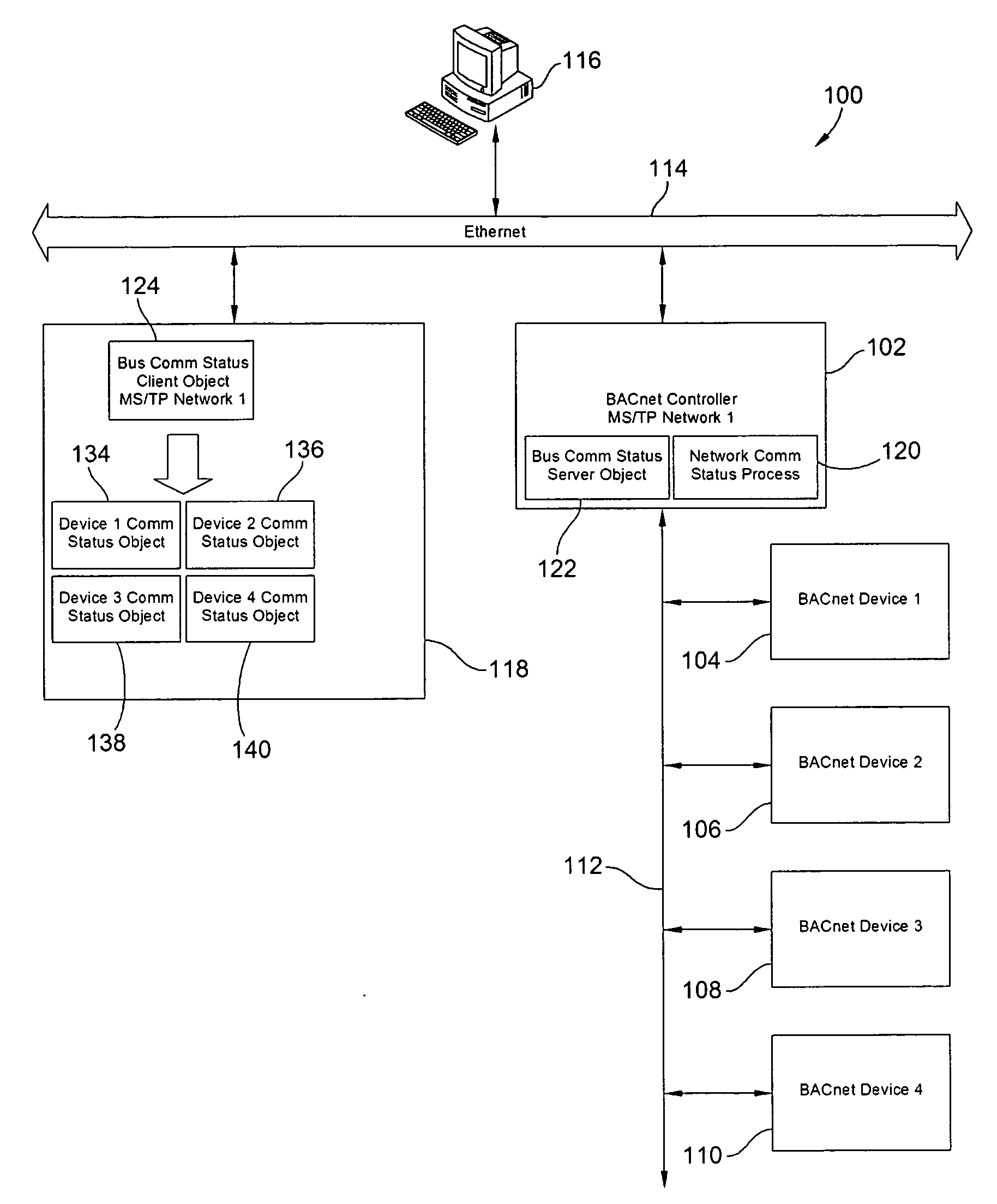
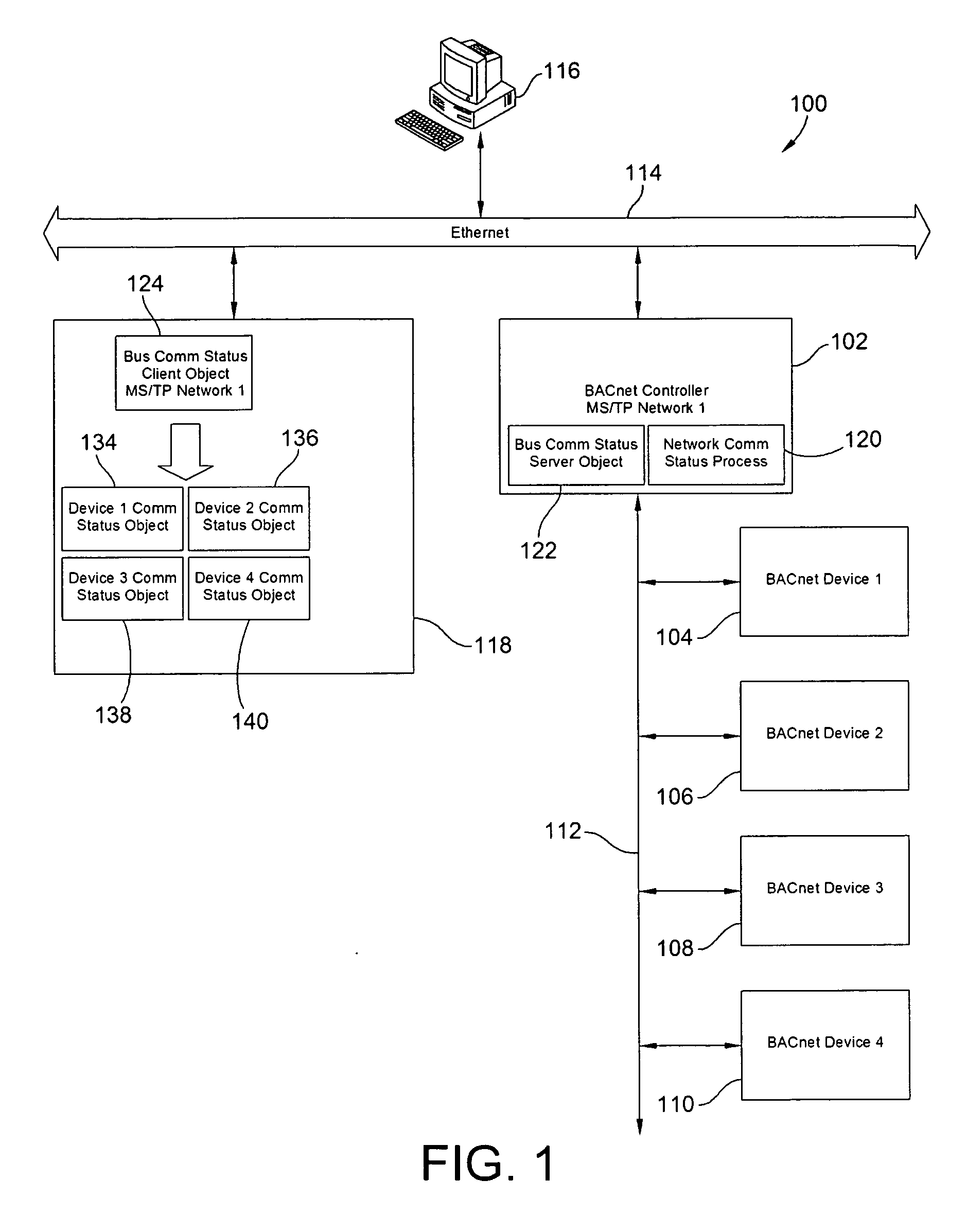
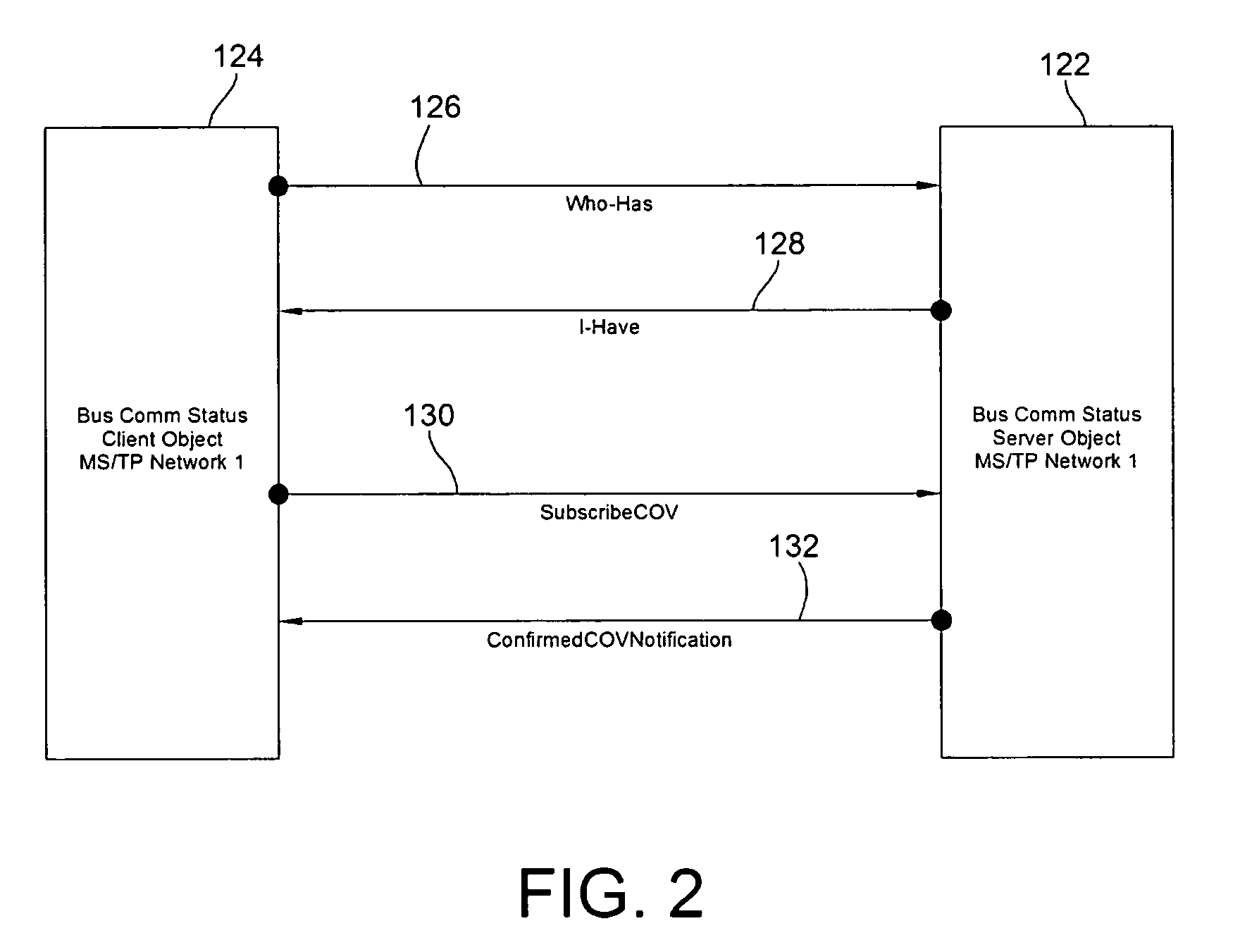
BACnet Communication Status Objects and Methods of Determining Communication Status of BACnet Devices
ActiveUS20090287736A1Effective monitoringEfficient sharingMultiple digital computer combinationsData switching networksGraphicsAuto-configuration
BACnet objects and methods for efficiently monitoring the communication status of networks and devices in a building automation and control system are presented. A pair of bus communication status objects, including a server object and a client object, provide the communication status of an MS / TP network as an OCTET String transmitted only upon a change of value (COV) of the communication status of a device on the network. Individual devices may be monitored with a device communication status object, in conjunction with or apart from the bus communication status objects. For MS / TP devices, automatic configuration and monitoring in a controller is provided. For other devices, a user interface is provided through a graphical tool to allow configuration to specify the desired device and / or network for monitoring.
Owner:SCHNEIDER ELECTRIC BUILDINGS LLC
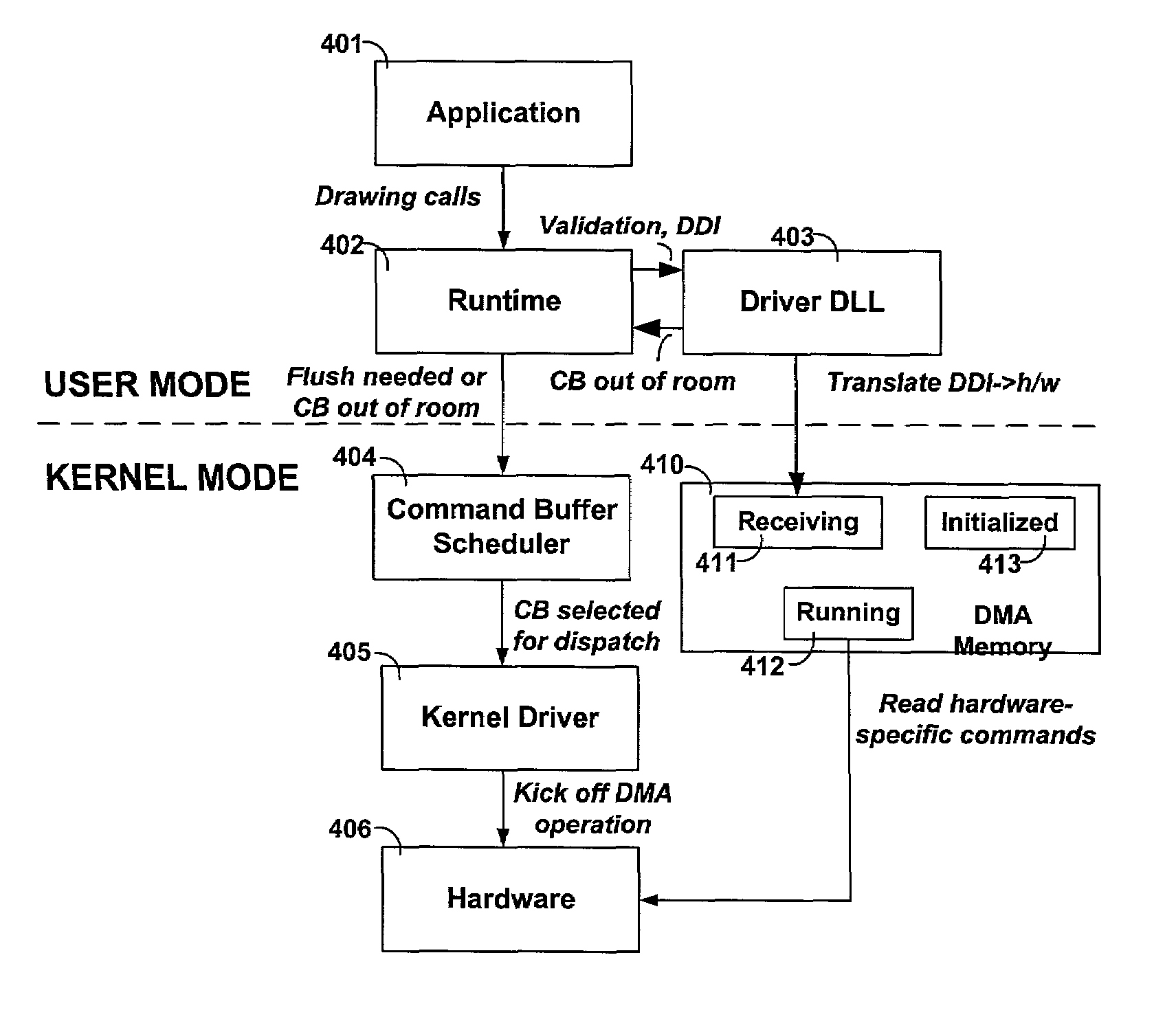
Methods and system for managing computational resources of a coprocessor in a computing system
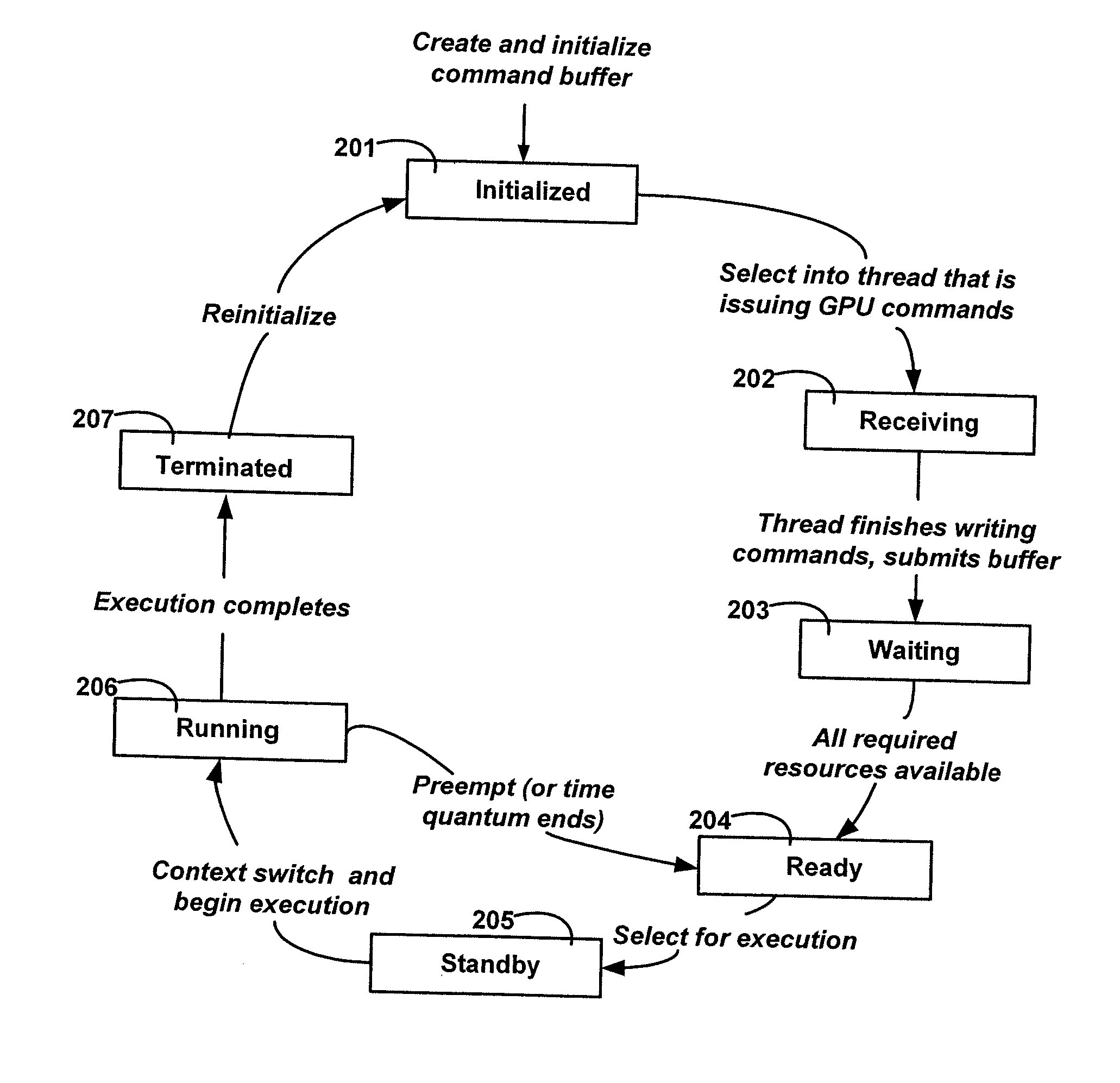
ActiveUS7234144B2Conducive to efficient executionEfficient sharingProgram initiation/switchingResource allocationGraphicsOperational system
Systems and methods are provided for managing the computational resources of coprocessor(s), such as graphics processor(s), in a computing system. The systems and methods illustrate management of computational resources of coprocessors to facilitate efficient execution of multiple applications in a multitasking environment. By enabling multiple threads of execution to compose command buffers in parallel, submitting those command buffers for scheduling and dispatch by the operating system, and fielding interrupts that notify of completion of command buffers, the system enables multiple applications to efficiently share the computational resources available in the system.
Owner:MICROSOFT TECH LICENSING LLC +1
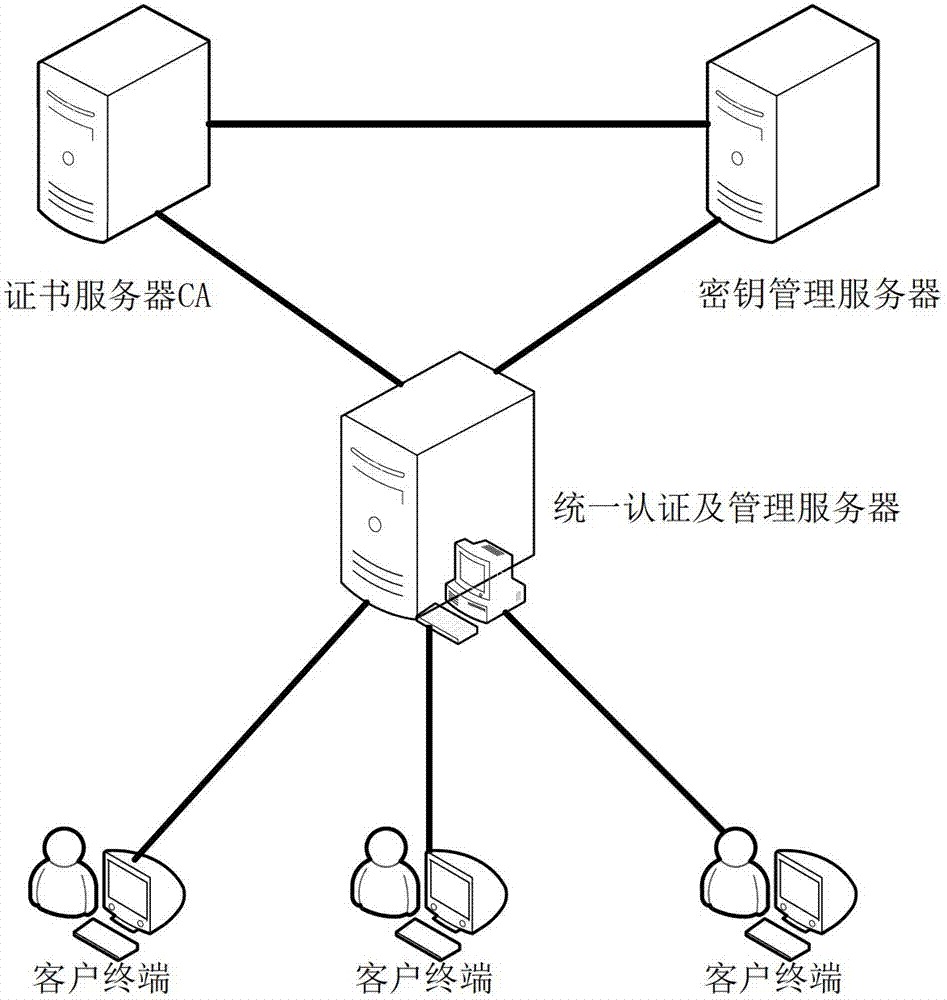
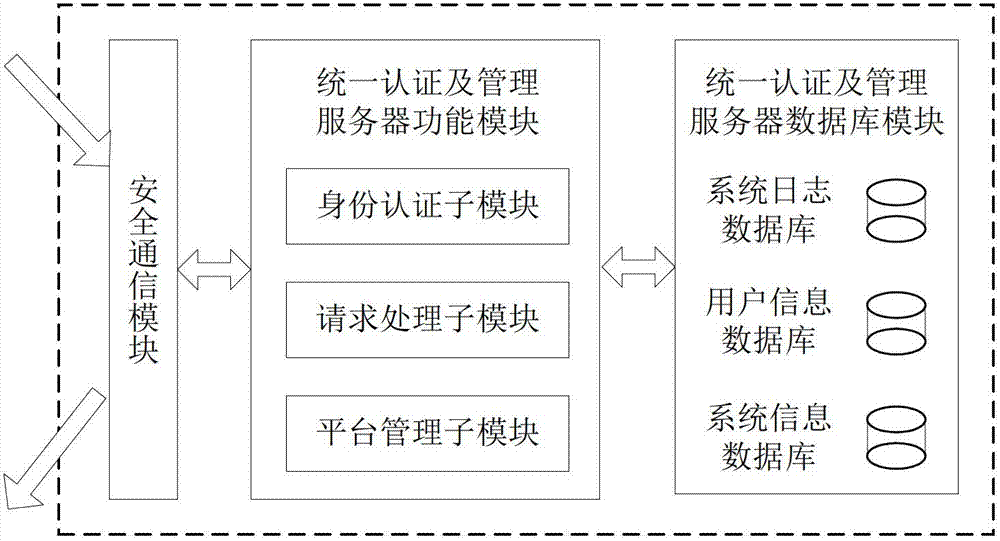
File safe protection system and method thereof
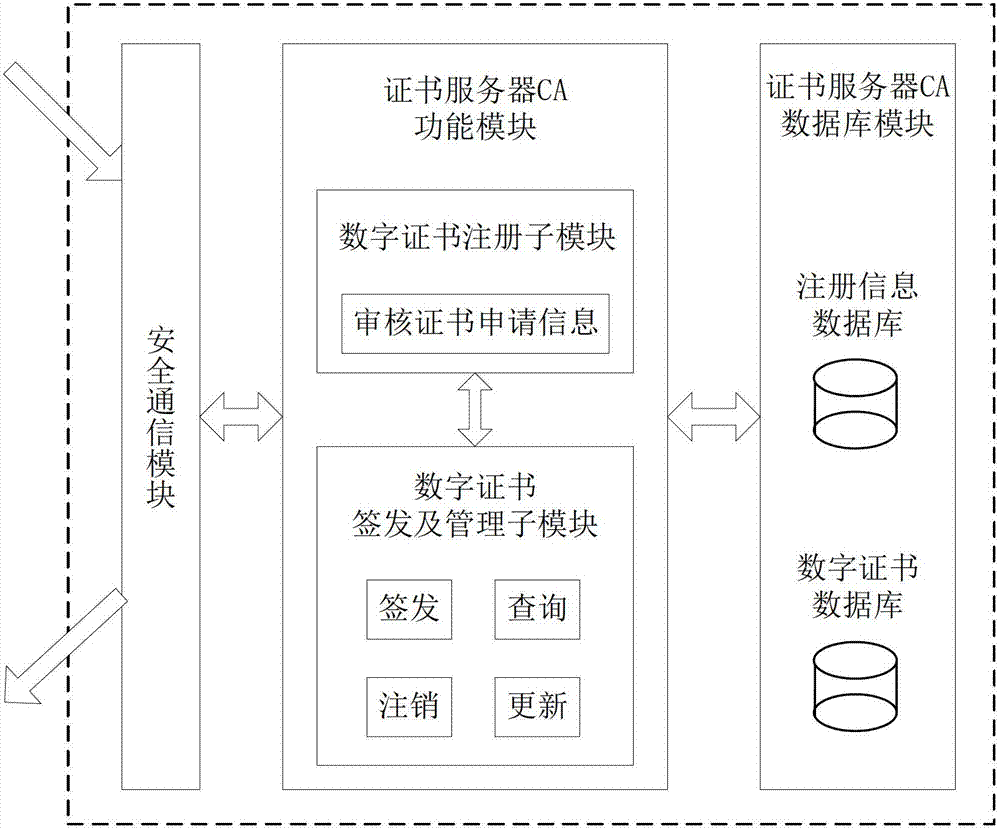
ActiveCN102970299ASimple structureEasy to buildKey distribution for secure communicationUser identity/authority verificationConfidentialityComputer terminal
The invention discloses a file safe protection system and a method, which mainly solves the problems of network illegal invasion, information stealing and tamping, impersonation and weak deny resistance in the conventional information system. The file safe protection system consists of a unified authentication and management server, a certificate server CA, a secret key management server and a client terminal; the unified authentication and management server is used as a middle node and is used for processing or transmitting a service request sent by the client terminal; the certificate server CA processes a certificate service request of the client terminal and provides basic support for identification; and the secret key management server processes the secrete key service requests of the client terminal and the certificate server CA, and is used for encrypting and decrypting a file for the client terminal and providing parameter support for a digital certificate signed by the certificate server CA. With the adoption of the file safe protection system and method provided by the invention, identification, confidentiality, integration and non-repudiation services can be provided; and the file can be safely protected in transmission, storage, sharing and access processes.
Owner:XIDIAN UNIV
Compensator for removing nonlinear distortion
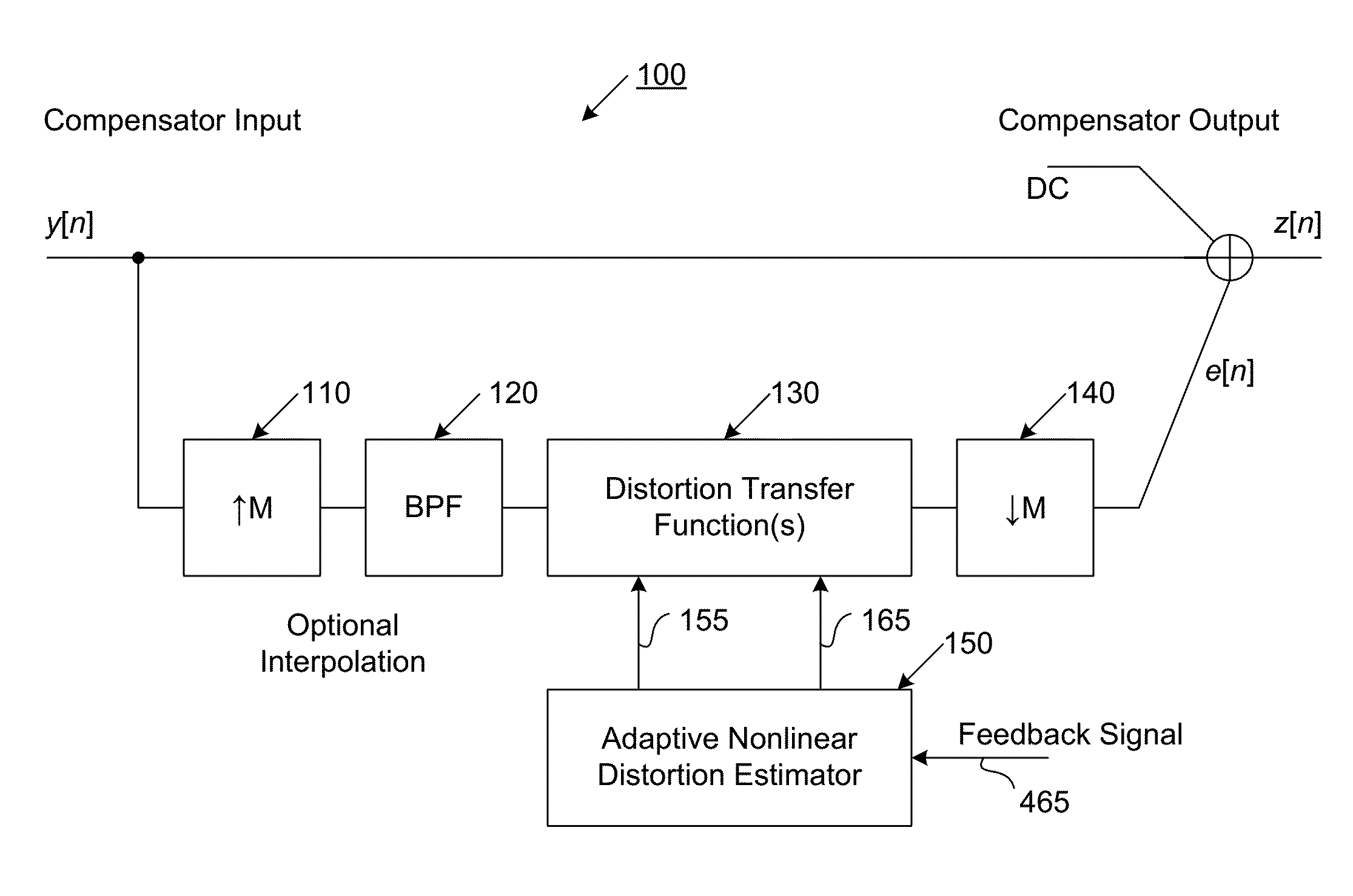
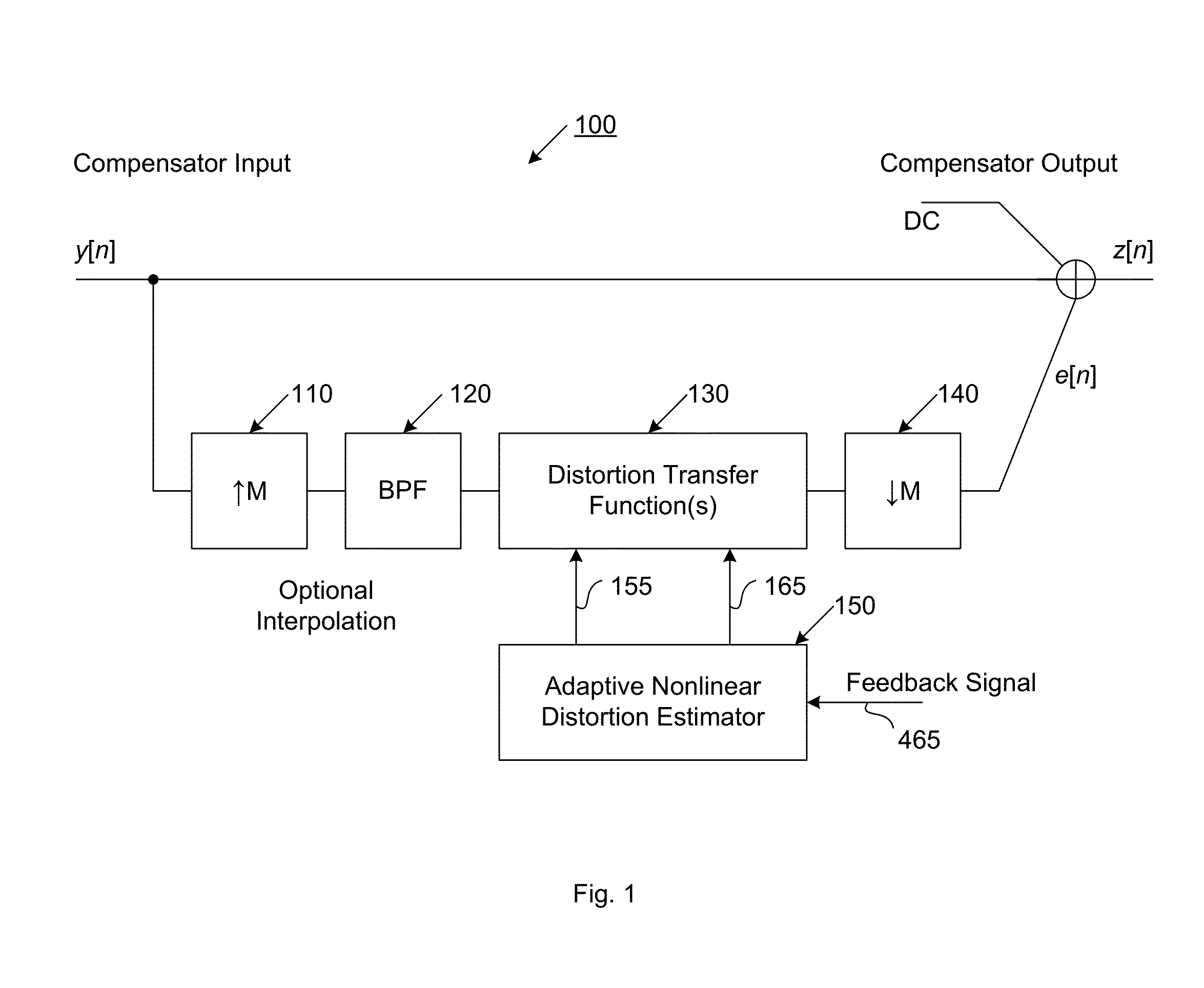
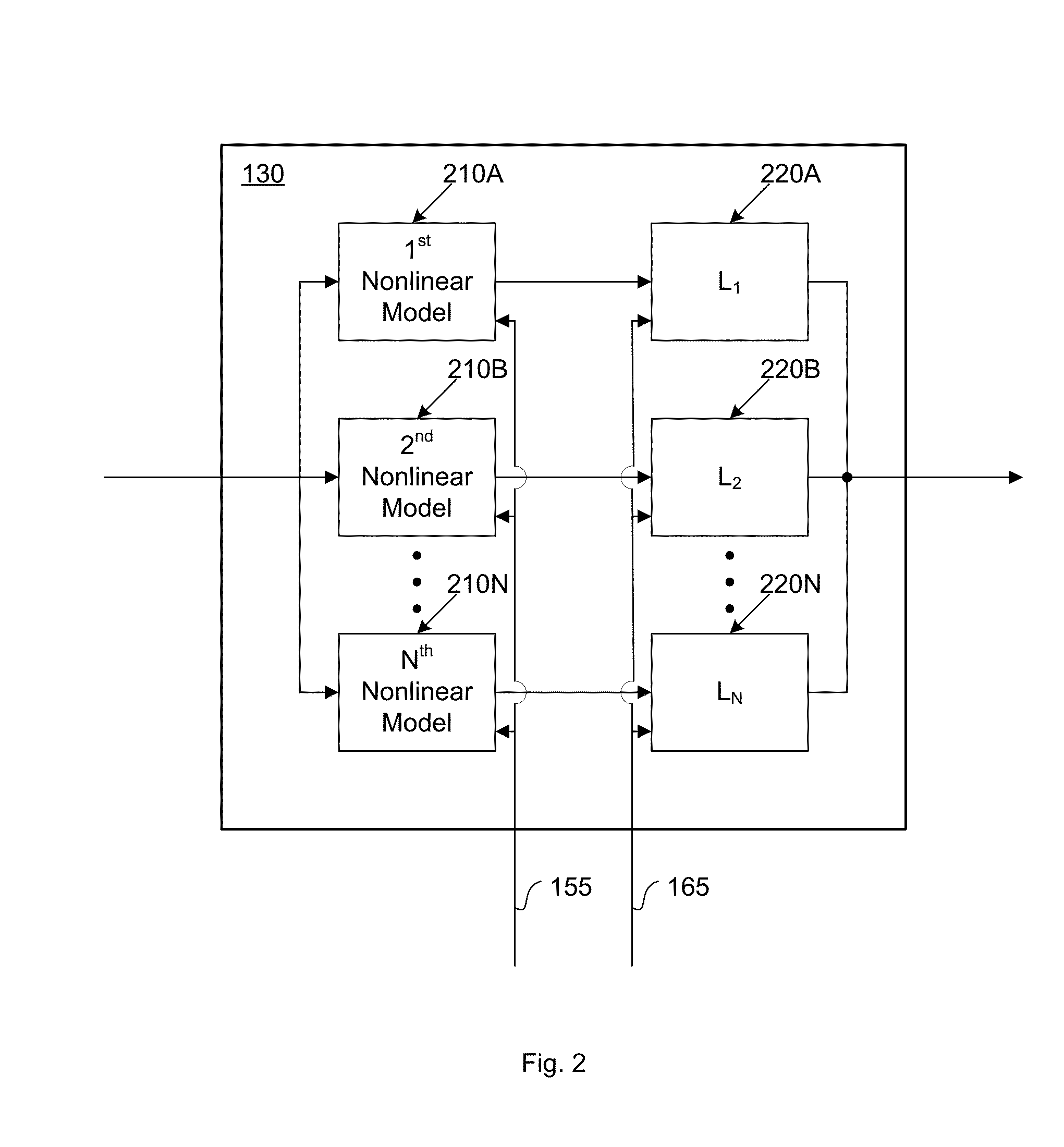
ActiveUS20160191020A1Easy to processReduce complexityChannel dividing arrangementsElectric signal transmission systemsNonlinear distortionComputation complexity
The present invention is a computationally-efficient compensator for removing nonlinear distortion. The compensator operates in a digital post-compensation configuration for linearization of devices or systems such as analog-to-digital converters and RF receiver electronics. The compensator also operates in a digital pre-compensation configuration for linearization of devices or systems such as digital-to-analog converters, RF power amplifiers, and RF transmitter electronics. The compensator effectively removes nonlinear distortion in these systems in a computationally efficient hardware or software implementation by using one or more factored multi-rate Volterra filters. Volterra filters are efficiently factored into parallel FIR filters and only the filters with energy above a prescribed threshold are actually implemented, which significantly reduces the complexity while still providing accurate results. For extremely wideband applications, the multi-rate Volterra filters are implemented in a demultiplexed polyphase configuration which performs the filtering in parallel at a significantly reduced data rate. The compensator is calibrated with an algorithm that iteratively subtracts an error signal to converge to an effective compensation signal. The algorithm is repeated for a multiplicity of calibration signals, and the results are used with harmonic probing to accurately estimate the Volterra filter kernels. The compensator improves linearization processing performance while significantly reducing the computational complexity compared to a traditional nonlinear compensator.
Owner:LINEARITY LLC
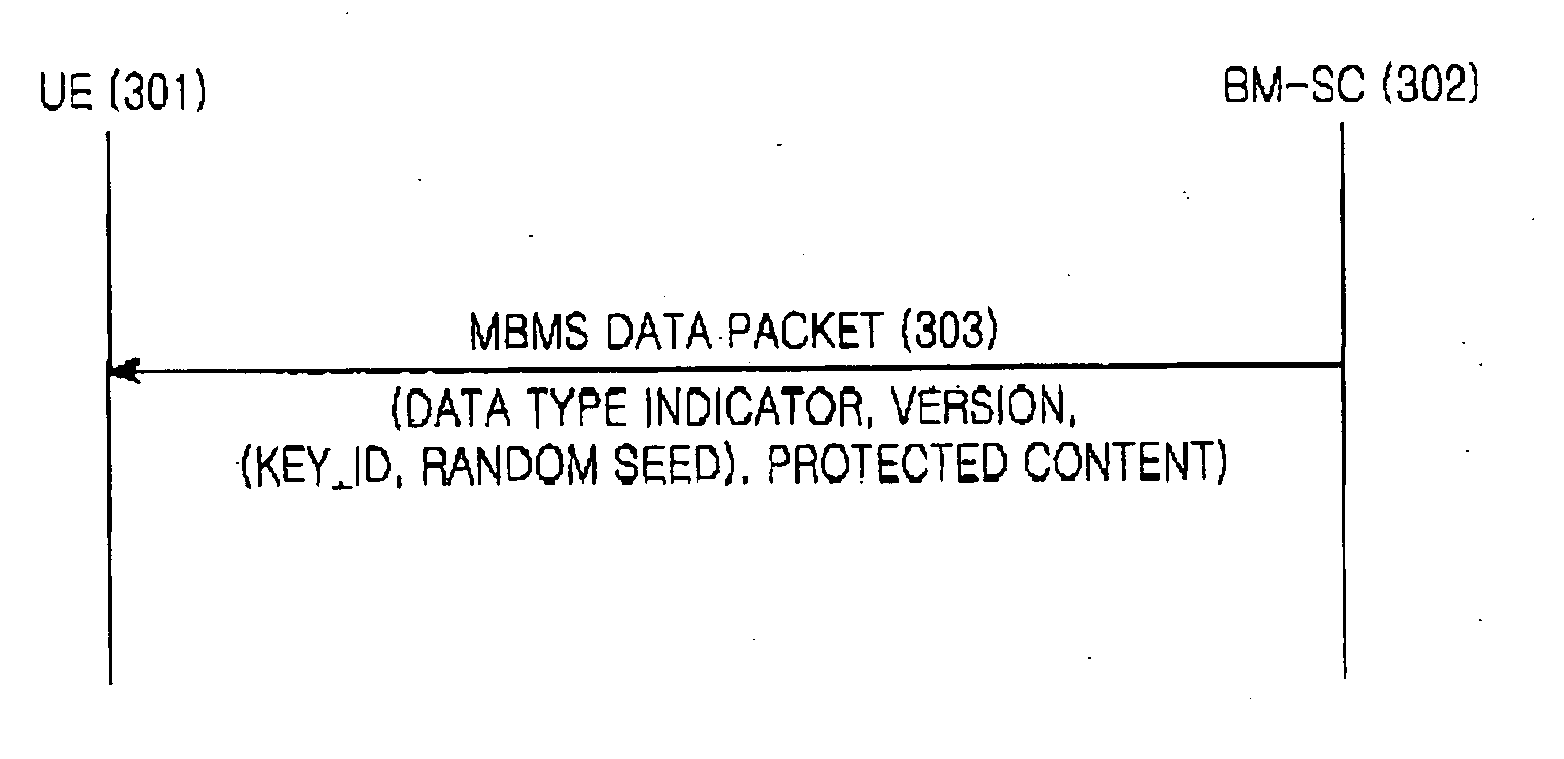
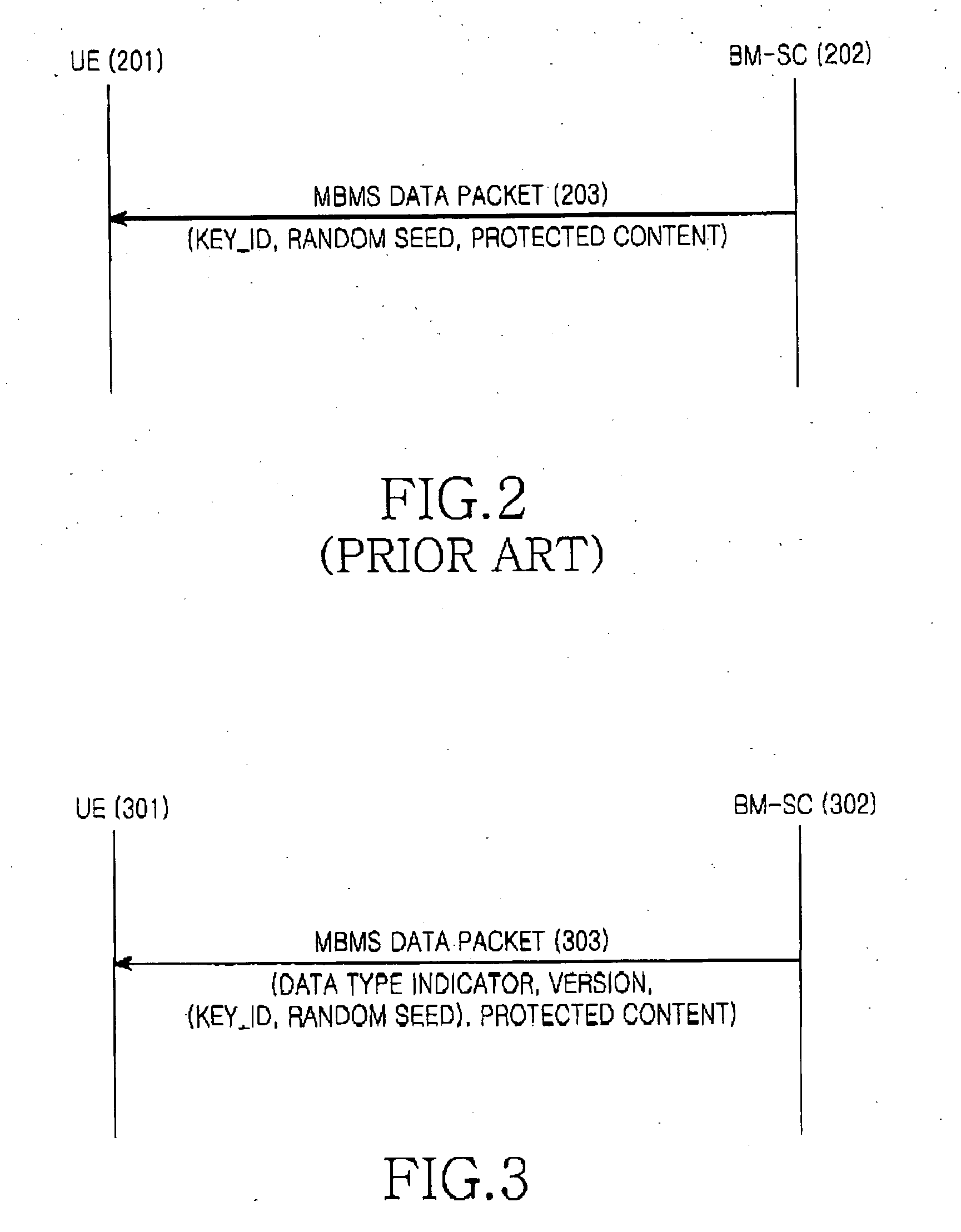
Method for transmitting and receiving control information for encryption in a mobile communication system supporting multimedia broadcast/multicast service
ActiveUS20050157876A1Effective protectionEfficient sharingKey distribution for secure communicationNetwork traffic/resource managementEncryptionMultimedia Broadcast Multicast Service
A method for minimizing overhead occurring caused by control information for encryption performed to protect MBMS data for an MBMS service in a mobile communication system. This method is implemented by distinguishing a case in which control information used for encryption is updated from another case in which the control information used for encryption is not updated, and transmitting different control information according to the distinguishment result. That is, when the control information used for encryption is not updated, only minimized control information is transmitted, and when the control information for encryption is updated, the entire updated control information is transmitted. Accordingly, the amount of control information transmitted along with MBMS data is minimized, contributing to an increase in the amount of MBMS data transmitted per unit time.
Owner:SAMSUNG ELECTRONICS CO LTD
Electronic certificate management method and related equipment
ActiveCN107231351ARealize distributed managementImprove storage reliabilityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesChain networkInformation security
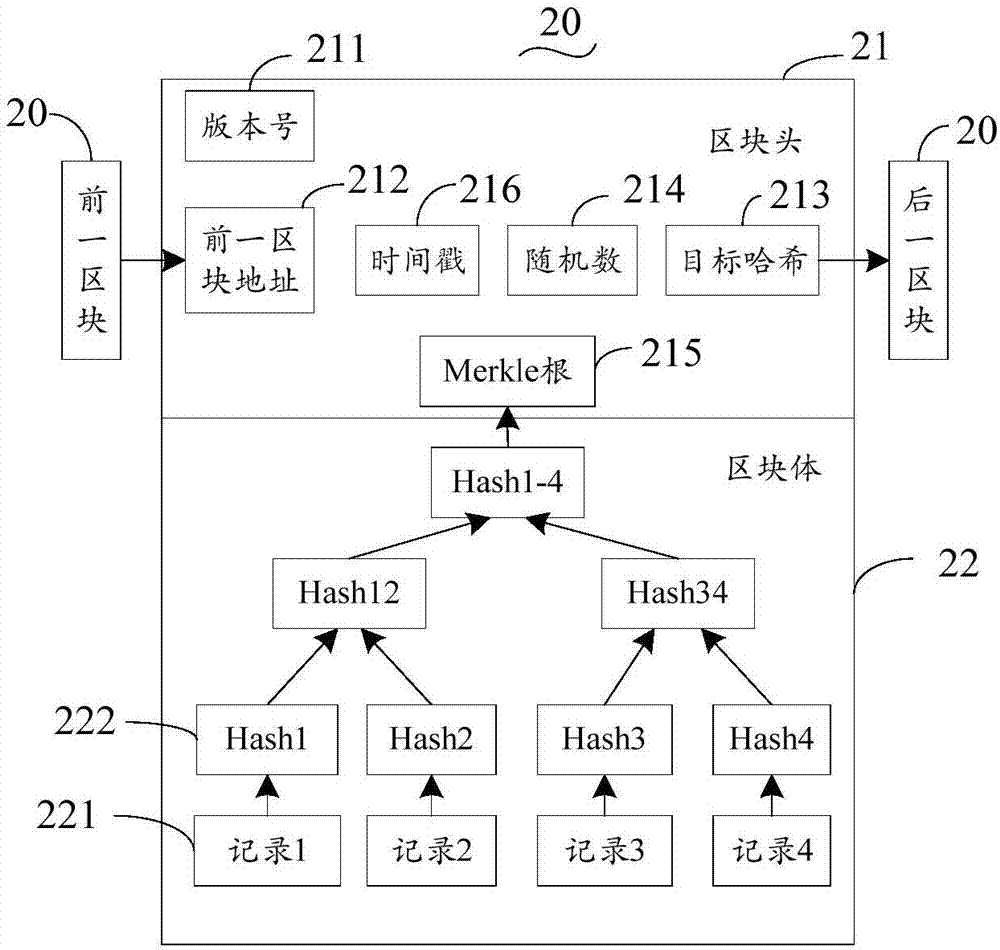
The invention discloses an electronic certificate management method and related equipment. The method comprises the steps as follows: the electronic equipment processes an electronic certificate in response to a received processing command; an encrypted processing record is broadcasted into a block chain network, thus allowing a node of the block chain network to store the encrypted processing record into a block chain of the block chain network. According to the scheme of the method provided by the invention, distributed management of the electronic certificate is achieved, storage reliability of the electronic certificate is improved, the risk of tampering or leaking certificate information is reduced, and information security and credibility of the electronic certificate are effectively ensured.
Owner:YGSOFT INC
Methods And System For Managing Computational Resources Of A Coprocessor In A Computing System
InactiveUS20070136730A1Conducive to efficient executionEfficient sharingProgram initiation/switchingMultiple digital computer combinationsGraphicsCoprocessor
Systems and methods are provided for managing the computational resources of coprocessor(s), such as graphics processor(s), in a computing system. The systems and methods illustrate management of computational resources of coprocessors to facilitate efficient execution of multiple applications in a multitasking environment. By enabling multiple threads of execution to compose command buffers in parallel, submitting those command buffers for scheduling and dispatch by the operating system, and fielding interrupts that notify of completion of command buffers, the system enables multiple applications to efficiently share the computational resources available in the system.
Owner:MICROSOFT TECH LICENSING LLC
Predictive ownership control of shared memory computing system data
ActiveUS20100281220A1Efficient sharingMemory architecture accessing/allocationMemory adressing/allocation/relocationData structureShared memory
A method, circuit arrangement, and design structure utilize a lock prediction data structure to control ownership of a cache line in a shared memory computing system. In a first node among the plurality of nodes, lock prediction data in a hardware-based lock prediction data structure for a cache line associated with a first memory request is updated in response to that first memory request, wherein at least a portion of the lock prediction data is predictive of whether the cache line is associated with a release operation. The lock prediction data is then accessed in response to a second memory request associated with the cache line and issued by a second node and a determination is made as to whether to transfer ownership of the cache line from the first node to the second node based at least in part on the accessed lock prediction data.
Owner:IBM CORP
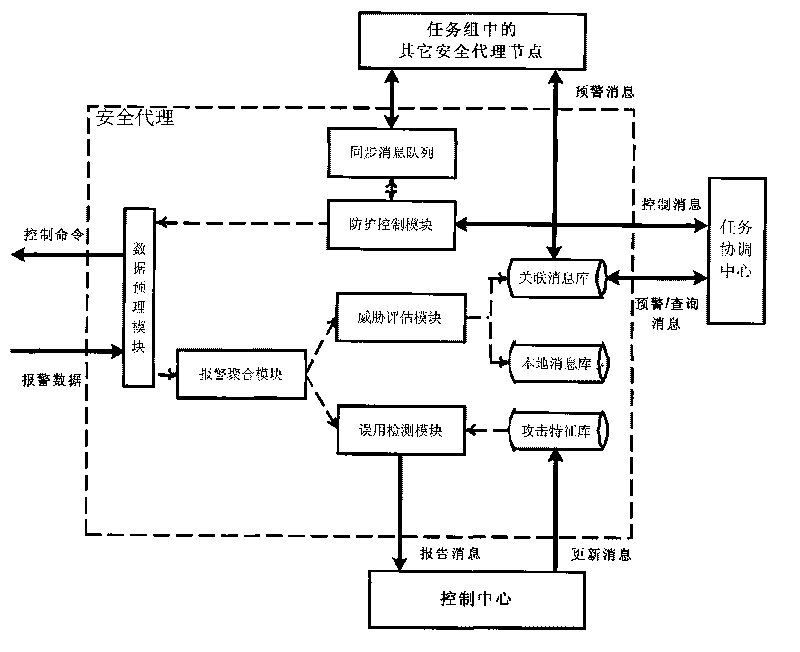
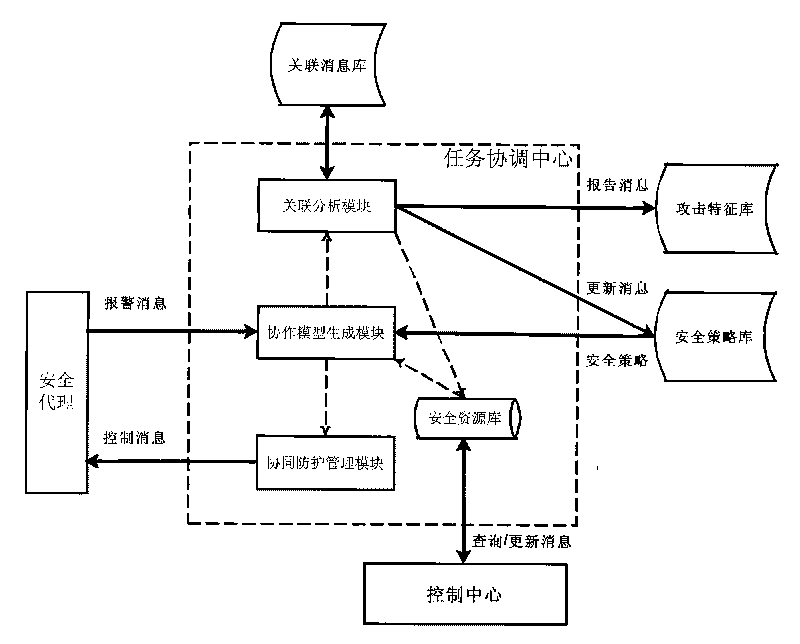
Cloud computing environment-based distributed network security pre-warning method
ActiveCN101719842AImprove survivabilityExtensible line strengthData switching networksData connectionNetwork security policy
The invention discloses a cloud computing environment-based distributed network security pre-warning method, which belongs to the technical field of network security. The method comprises that: a plurality of management domains are set, wherein each management domain comprises a control central node and more than one security proxy node, and the control central nodes are in peer connection; the security proxy nodes discover abnormal events through peripheral equipment, extract event information, generate warning messages and transmit warning information to the corresponding control central nodes; the control central nodes receive the warning messages transmitted by the corresponding security proxy nodes and the other control central nodes and combine the central nodes meeting a combination condition into a task group; the security proxy nodes in the task group are in the peer connection and one security proxy node serves as a task coordination central node to coordinate the security proxy nodes in the group to complete tasks together; and the task group is in data connection with the control central nodes through the task coordination central node.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Isomerization clinical medical information shared system and method
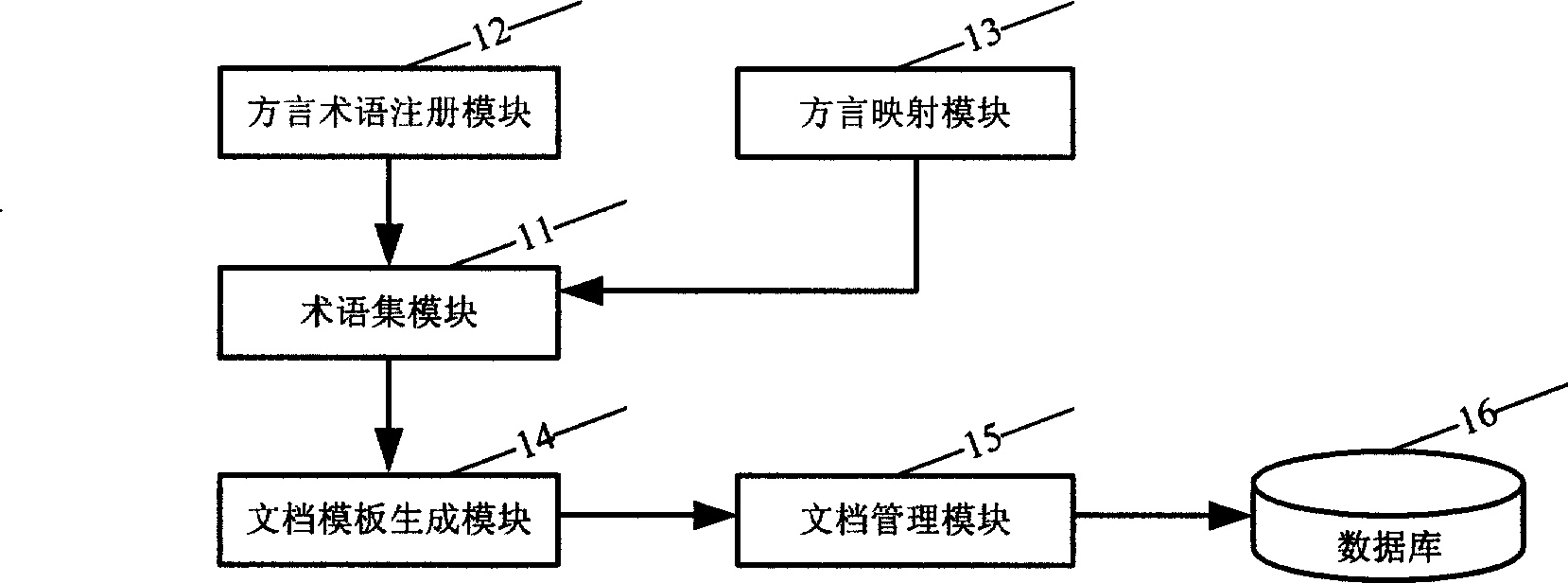
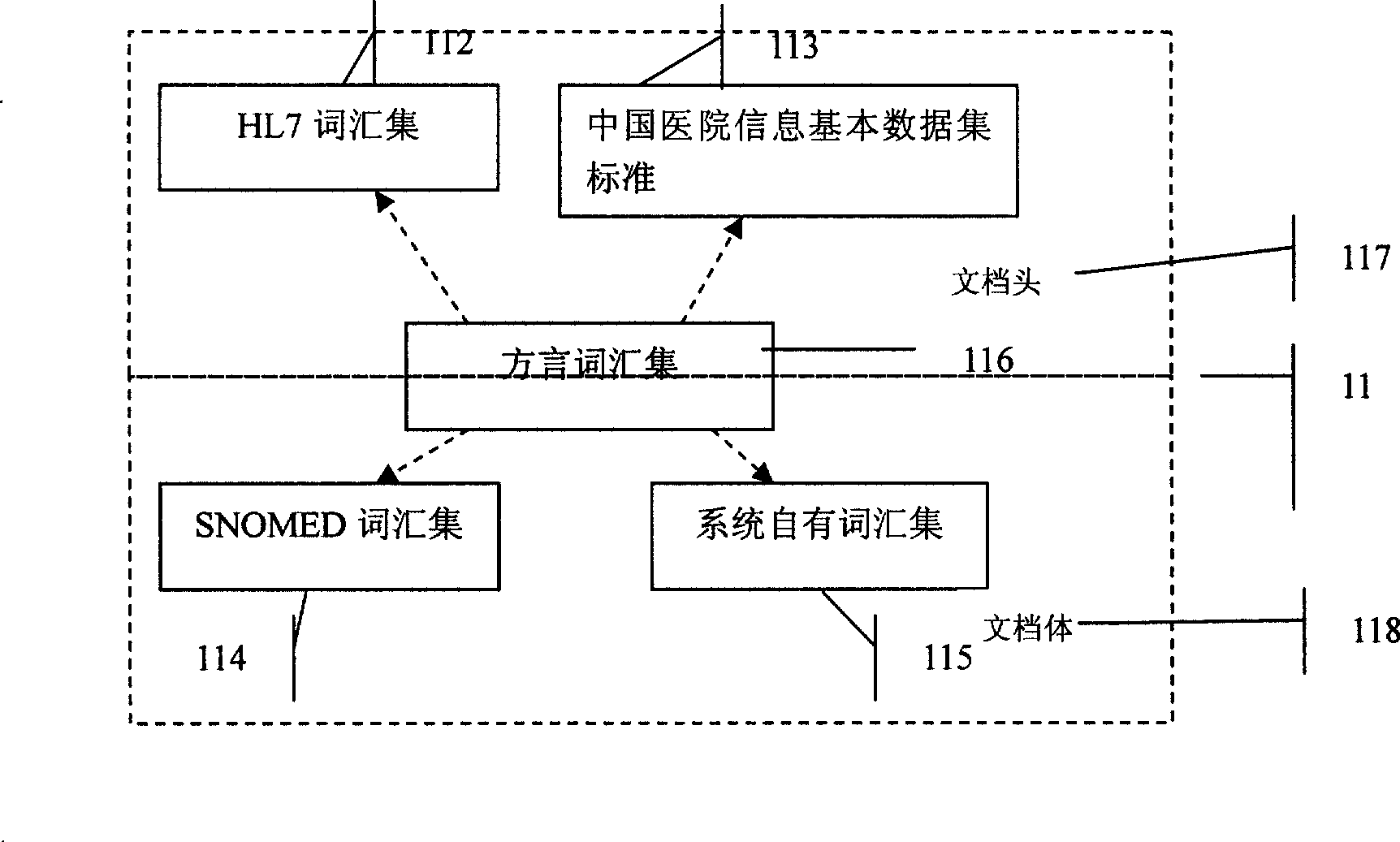
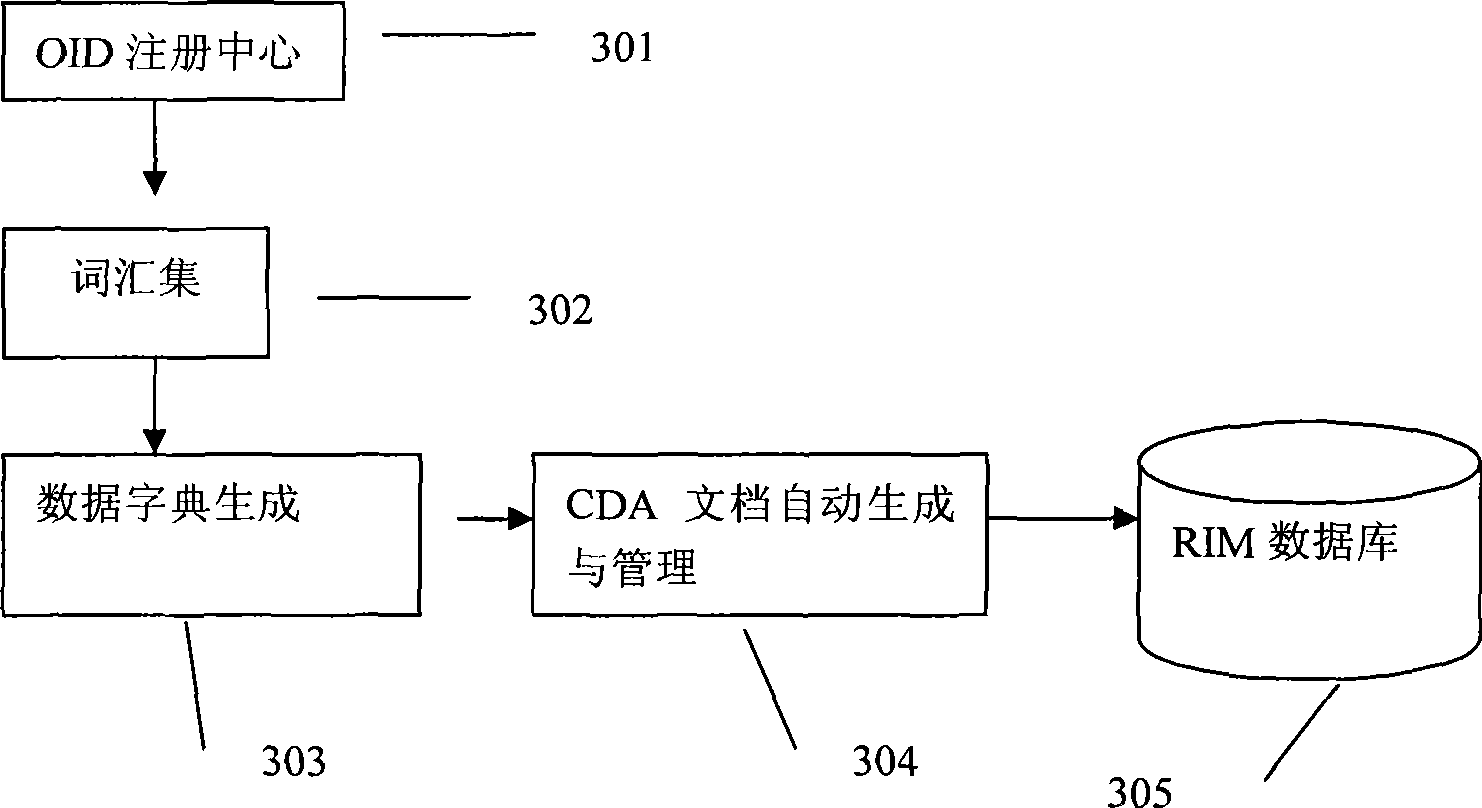
InactiveCN101452503AExpand coverageThe description is close to the real situationSpecial data processing applicationsIsomerizationDocument preparation
The invention discloses a system and a method for sharing isomerous clinic medical information. The system comprises a terminology module, a document template generating module, a document management module and a database for storing clinic data, wherein the terminology module, the document template generating module, the document management module and the database are connected with each other in turn; the terminology module is used for normalizing terminologies used in shared documents; the document template generating module is used for defining composition elements of standard clinic data documents and relations between various elements, automatically generating a document template, and collecting and managing metadata; and the document management module is used for managing the documents, wherein users manage the medical documents through the document management module, and perform input, correction and query operations and transmission and sharing of the documents. The system and the method realize automatic generation of the standard clinic documents through a clinic data dictionary and a standard document generation device, and finally establish a complete clinic document database through mapping to manage and share the standard clinic documents.
Owner:SHANGHAI CENT FOR BIOINFORMATION TECH
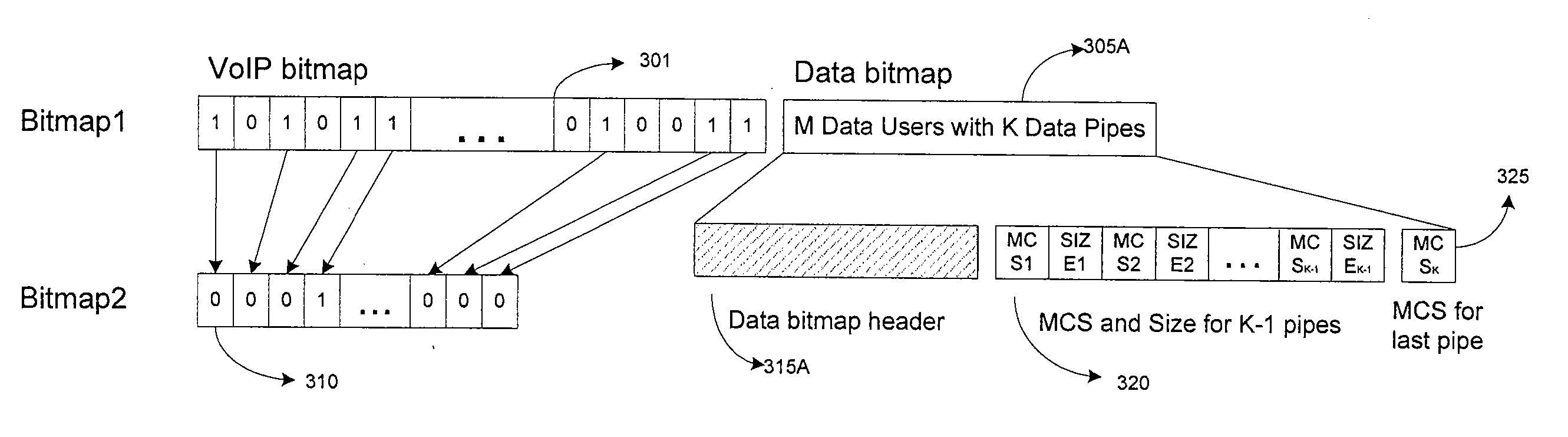
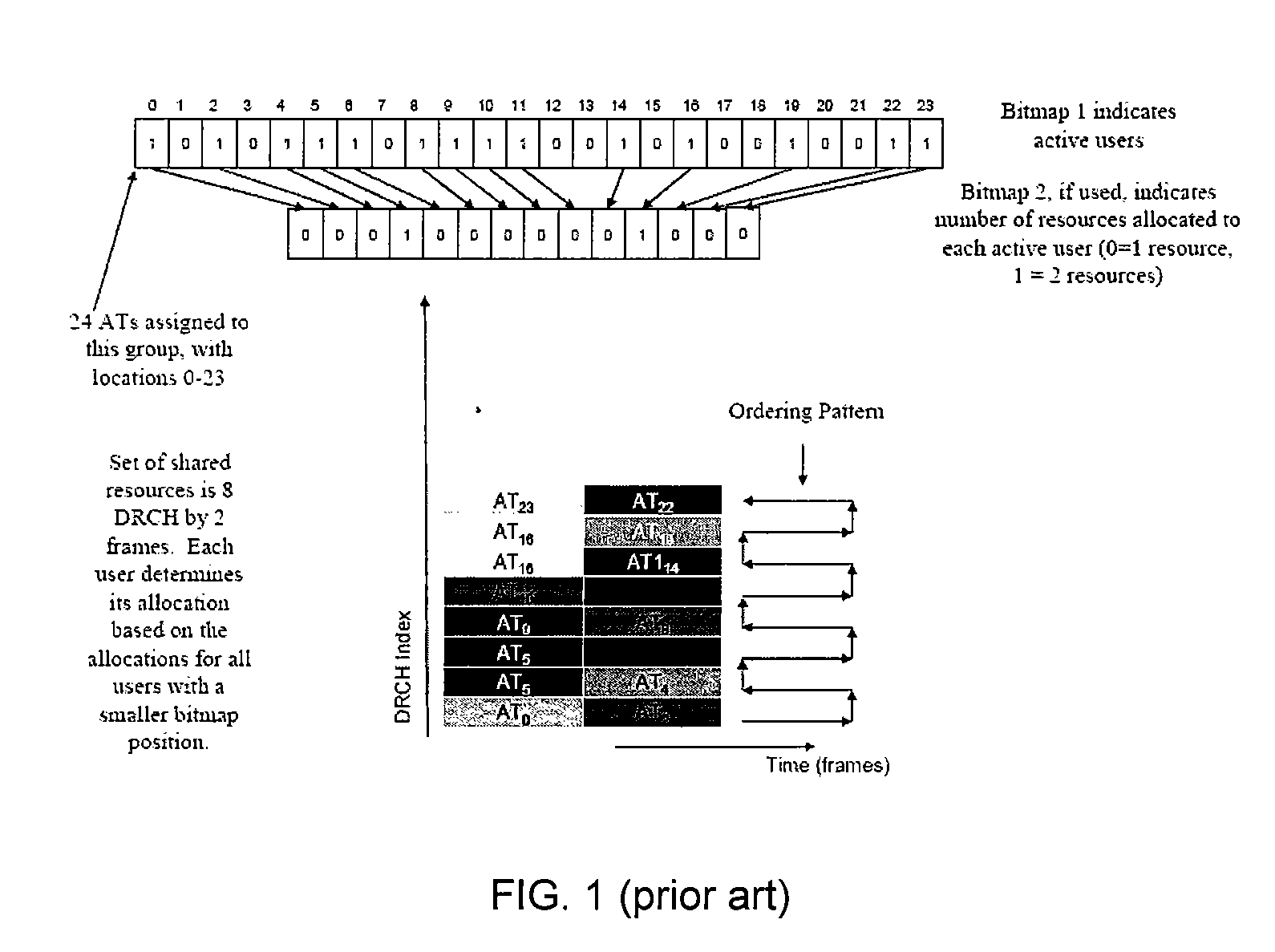
Method and system for sharing resources in a wireless communication network
ActiveUS20080095071A1ServeRaise priorityData switching by path configurationWireless communicationVoice communicationDistribution method
Method and system for sharing resources in a wireless communication network. According to an embodiment, the present invention provides a method for resource allocation. The method includes providing an access node that is configured to provide wireless access for both voice and data services. The method also includes providing at least a first access terminal that is configured to perform at least voice communication through the access node. Additionally, the method includes providing at least a second access terminal that is configured to perform at least data communication through the access node. The method further includes allocating a first portion of communication resources to the first access terminal. The method additionally includes allocating a second portion of communication of resources to the second access terminal. Furthermore, the method includes generating a group resource allocation message, which includes at least a first bitmap and a second bitmap.
Owner:FUTUREWEI TECH INC
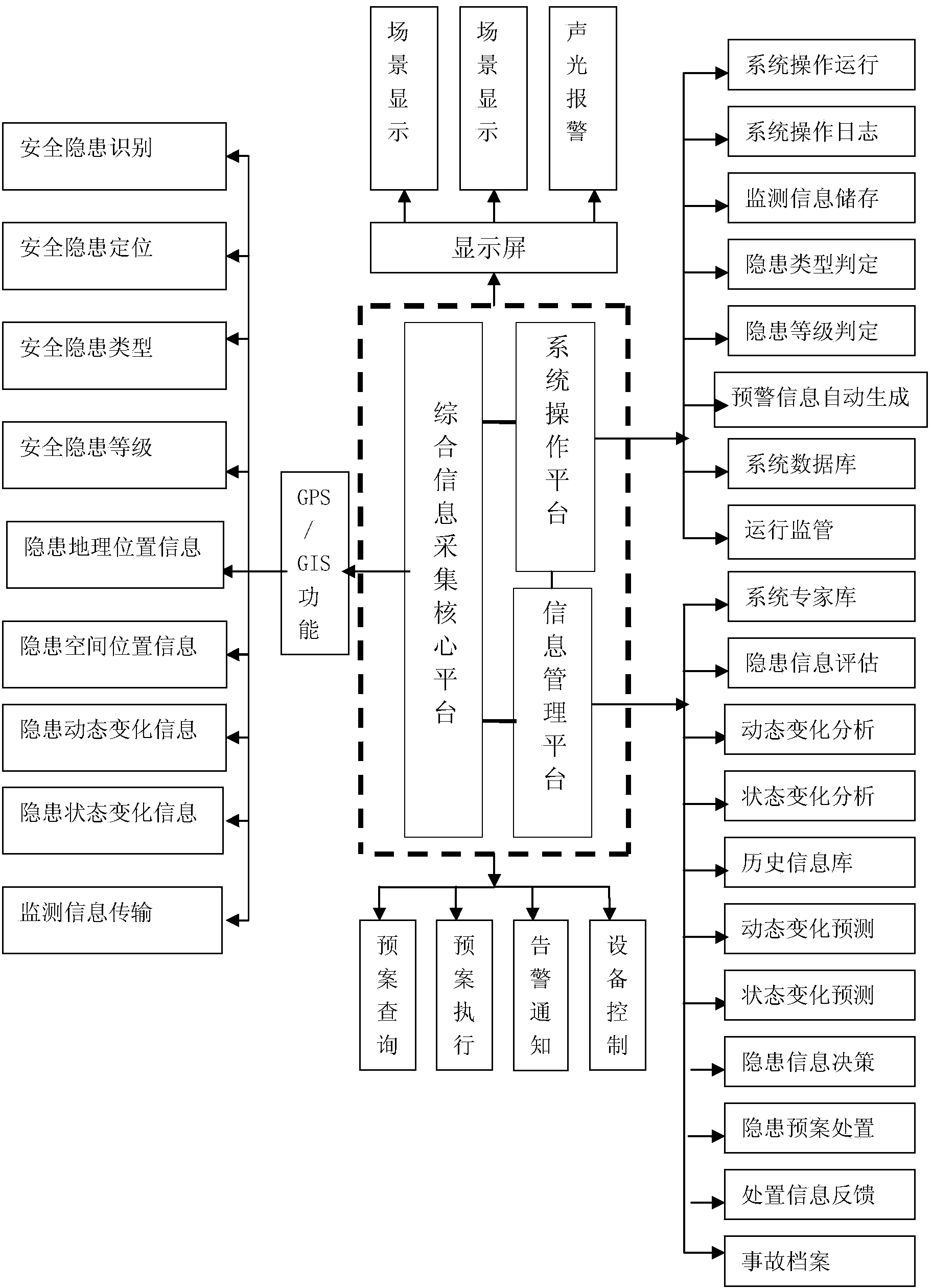
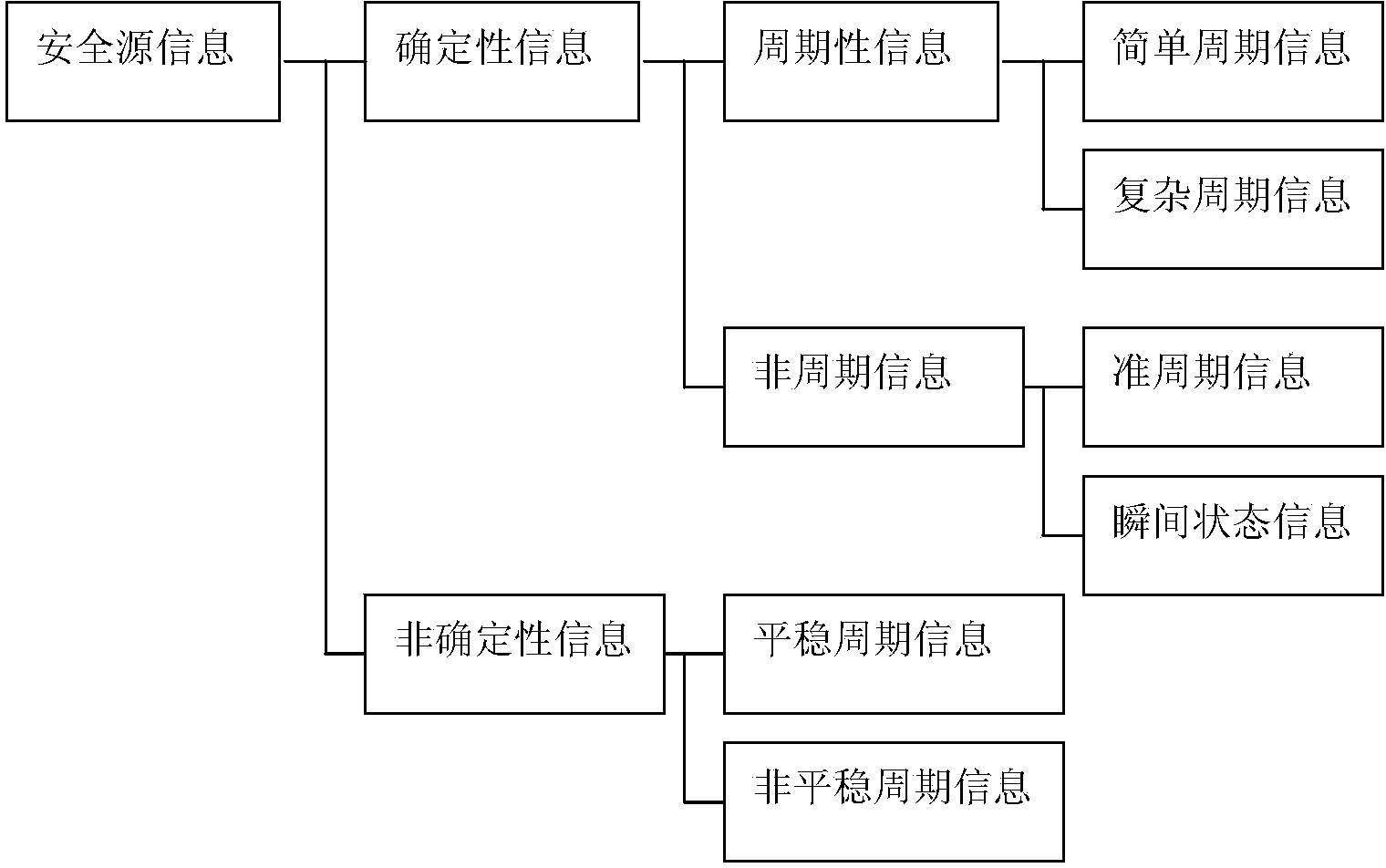
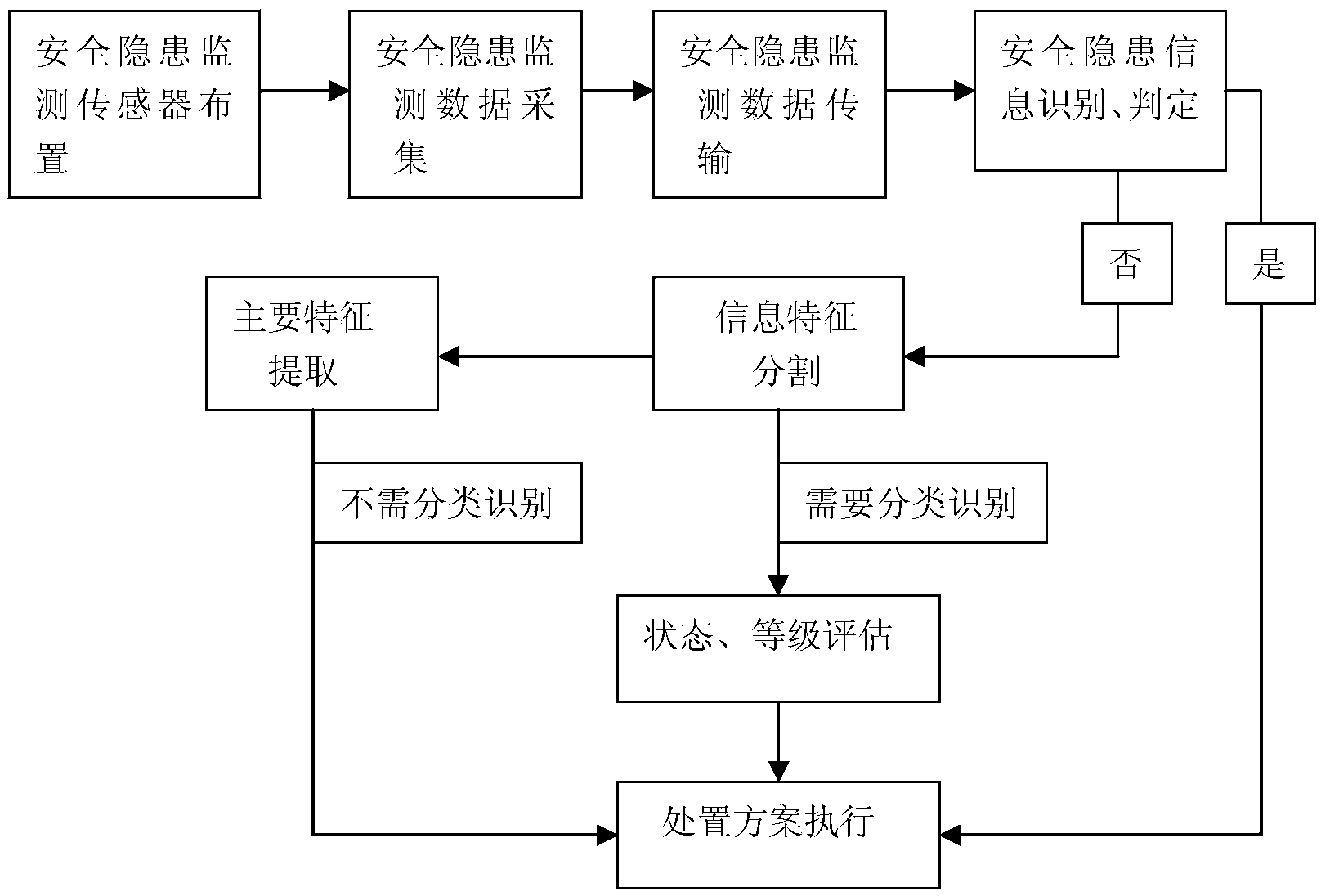
Internet of Things framework type system for monitoring and early warning of major accident potential safety hazards of water conservancy and hydropower project
ActiveCN103456136AMeet data sharingIn line with operating habitsData processing applicationsAlarmsState predictionData information
The invention belongs to the field of safety production and early warming emergency of construction of water conservancy and hydropower projects and relates to an Internet of Things framework type system and method for monitoring and early warning of major accident potential safety hazards of a water conservancy and hydropower project. According to the Internet of Things framework type system and method for monitoring and early warning of the major accident potential safety hazards of the water conservancy and hydropower project, information of the potential safety hazards which can cause a potential accident in the area of the water conservancy and hydropower project is recognized and positioned to determine the types and levels of the potential safety hazards, and judging of the types and levels of the potential safety hazards and information statistics are carried out; meanwhile, the geographic position, spatial position, dynamic change, state change and state prediction of monitoring points in the area are analyzed by combining with the historical information of the area, early warning information can be generated automatically after potential safety hazard information in the monitoring area is beyond a set alarm value, and comprehensive data information of the potential safety hazards in the area and early warning of the major accident potential safety hazards of the project are provided through communication transmission.
Owner:CHINA THREE GORGES CORPORATION
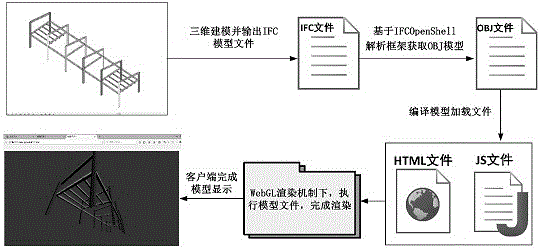
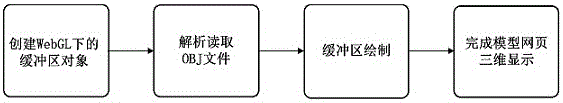
WebGL-based three-dimensional model display method and corresponding Web-BIM engineering information integration management system
InactiveCN105912655ARealize remote and different time interactionLow system requirementsProgram loading/initiatingGeographical information databasesDocument transformationSoftware engineering
The present invention relates to a WebGL-based three-dimensional model display method and a corresponding Web-BIM engineering information integration management system. The three-dimensional model display method comprises converting an IFC model file of a BIM engineering project into an OBJ model file; and displaying a three-dimensional model in a browser page supporting WebGL by using JavaScript program through OBJ-JavaScript interaction according to the OBJ model file obtained in the first step. The management system comprises a system database, and a data interaction module, a GIS integration module, an information query module, a user management module and a management decision support module which are respectively in communication connection with the system database. Web-3D browse of the BIM model is achieved by utilization of the WebGL technology.
Owner:SOUTHEAST UNIV
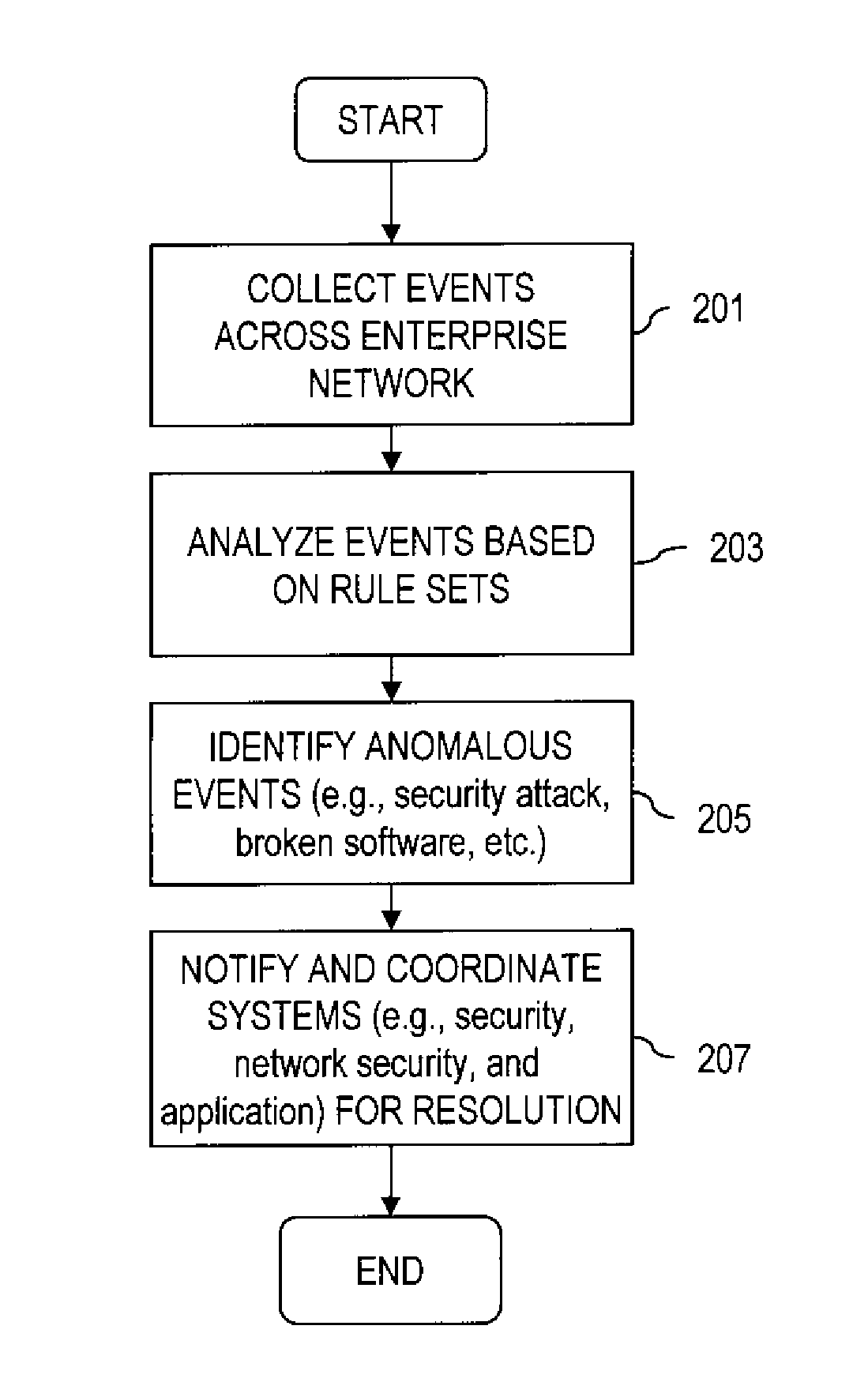
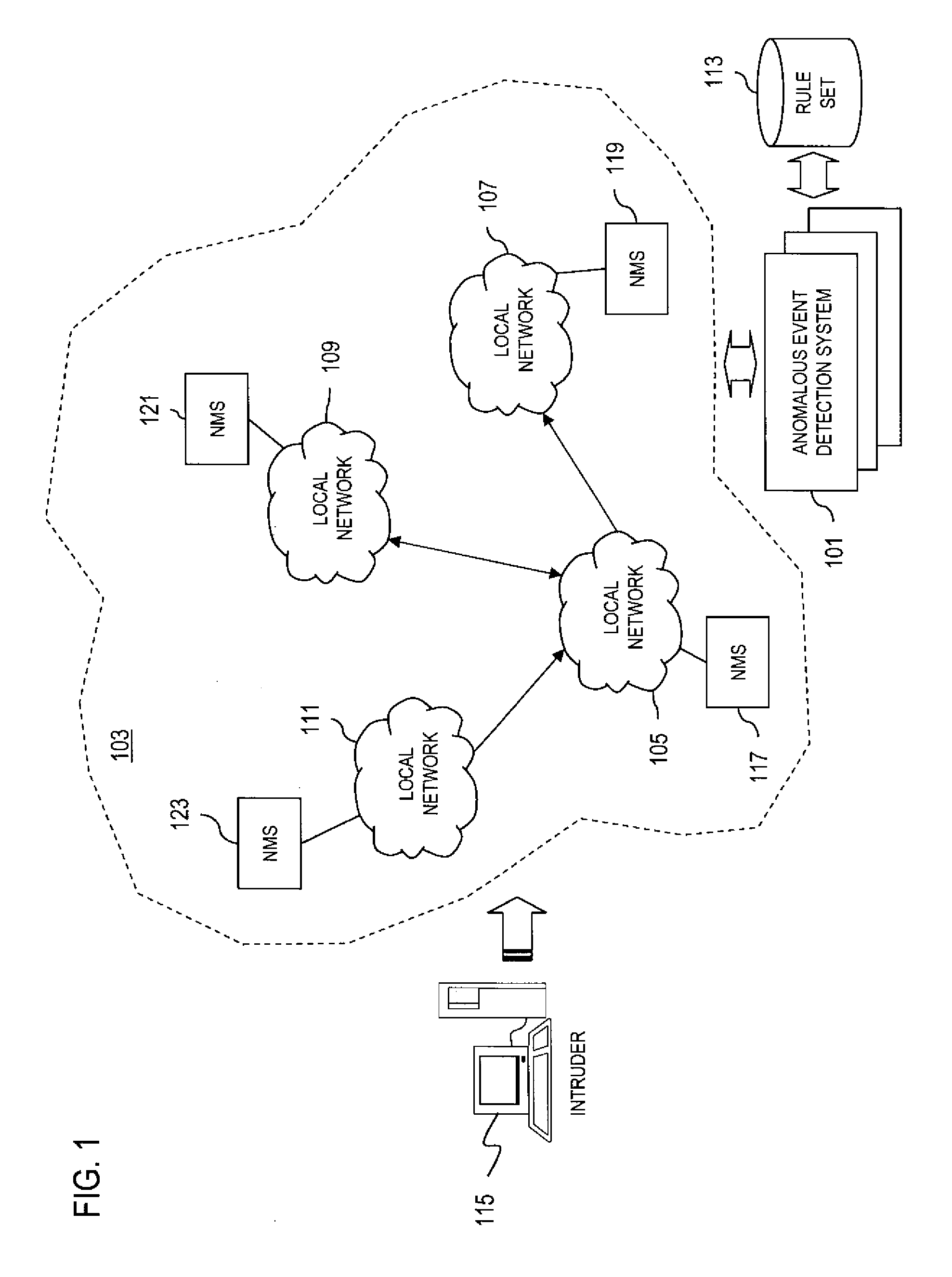
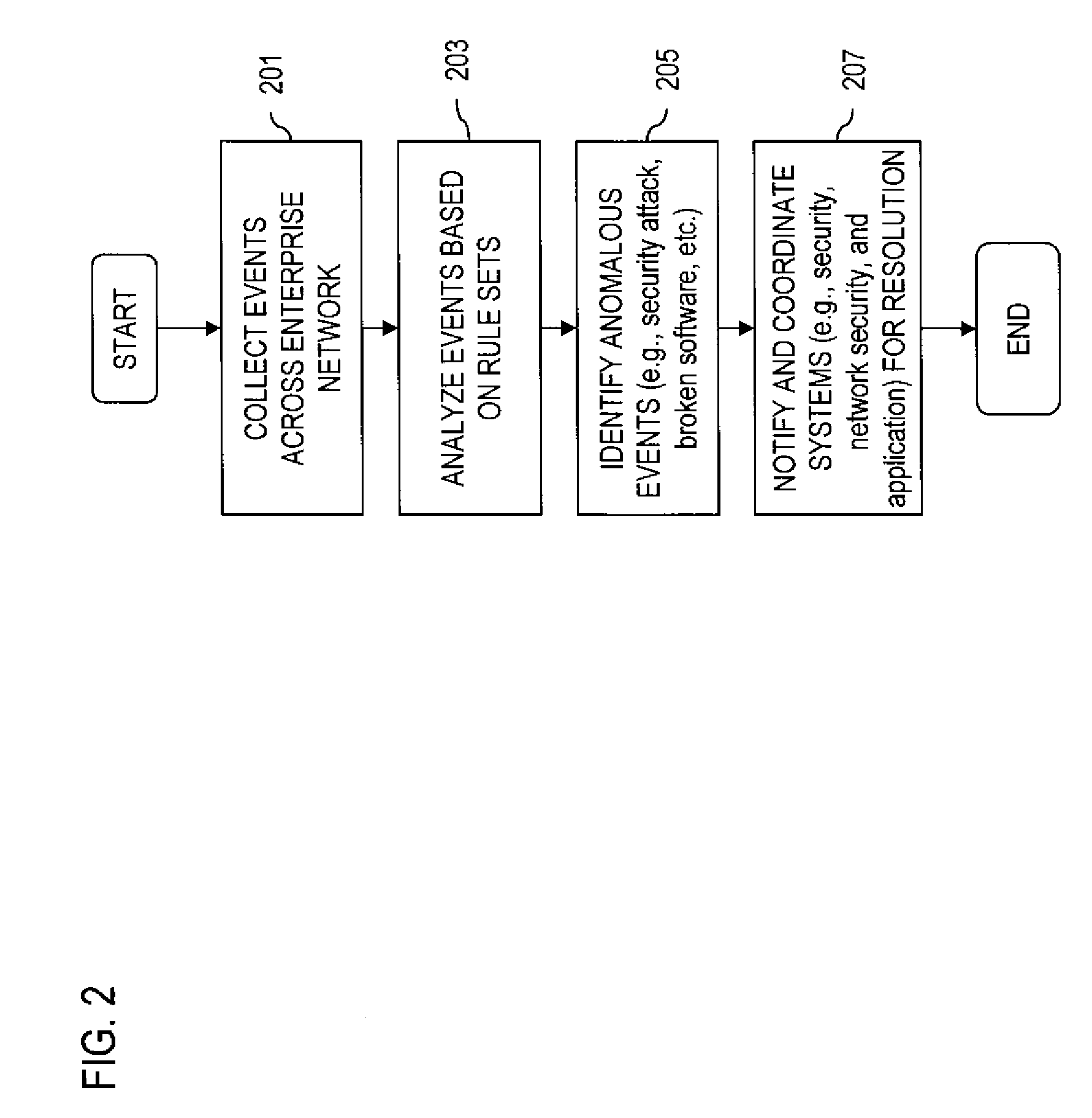
Secure self-organizing and self-provisioning anomalous event detection systems
InactiveUS20070094729A1Efficient sharingReduces false positiveMemory loss protectionError detection/correctionManaged security serviceAnomaly detection
An approach for providing managed security services is disclosed. A database, within a server or a pre-existing anomalous event detection system, stores a rule set specifying a security policy for a network associated with a customer. An anomalous detection event module is deployed within a premise of the customer and retrieves rule sets from the database. The anomalous detection event module monitors a sub-network of the network based on the rule sets. The anomalous event detection module is further configured to self-organize by examining components of the network and to monitor for anomalous events according to the examined components, and to self-provision by selectively creating another instance of the anomalous detection event module to monitor another sub-network of the network.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com