Cloud computing environment-based distributed network security pre-warning method
A technology of distributed network and cloud computing environment, applied in the field of distributed network and distributed network security early warning based on cloud computing environment, can solve the problems of no self-adaptation, inability to alarm data aggregation, selection of data sets, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The core technical content of the present invention will be described in further detail below through embodiments in conjunction with the accompanying drawings.
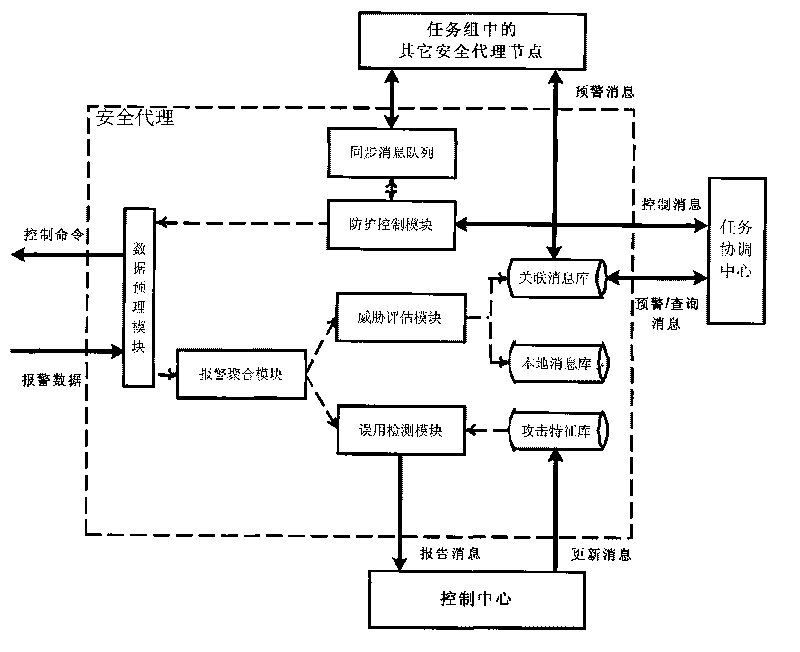
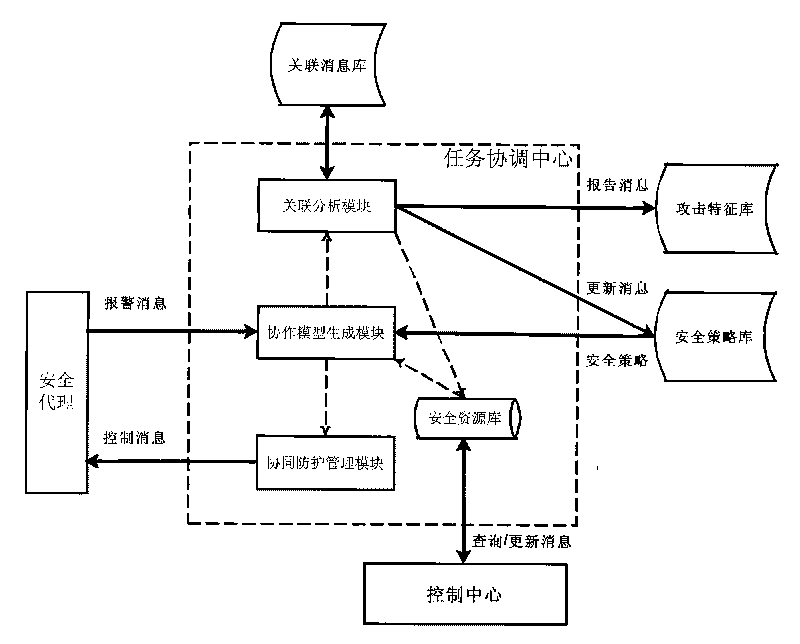
[0056] This embodiment describes a specific distributed network security early warning architecture based on cloud computing environment.
[0057] The architecture of this embodiment is a dynamic hierarchical architecture composed of a top-down three-layer peer-to-peer overlay network and three types of core nodes including a control center, a task coordination center and a security agent. The overall function of the prototype system built on it can be summarized as follows:
[0058] 1) Unify the alarm information from various network security protection facilities, and extract attack characteristics through collaborative correlation analysis of dynamic organization, so as to give early warning of local network intrusion or attack;
[0059] 2) Generate a global attack scenario graph and predict future attack ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com