File safe protection system and method thereof
A security protection and file technology, which is applied in the transmission system and key distribution, can solve the problems that it is difficult to prevent malicious attacks on terminal equipment, cannot effectively resist security threats, and cannot manage keys in a centralized manner, so as to facilitate security audits, avoid identity authentication and Session key negotiation process, the effect of ensuring file confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
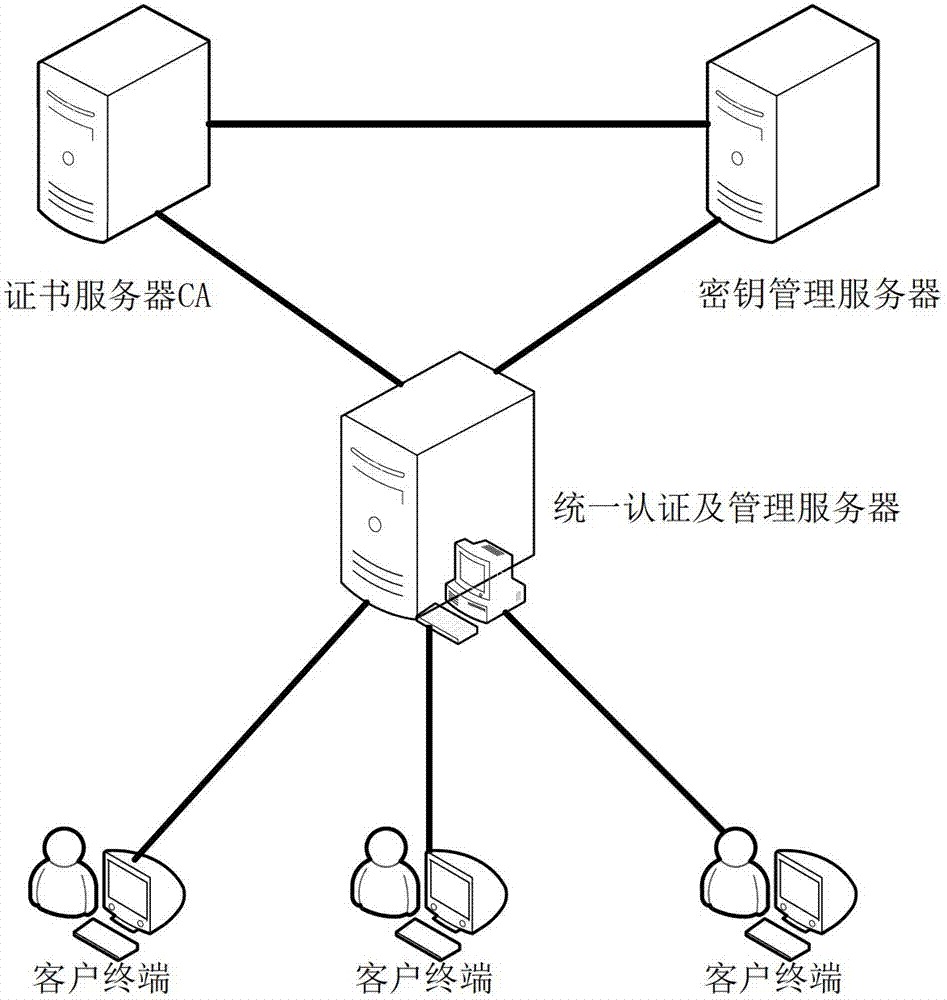
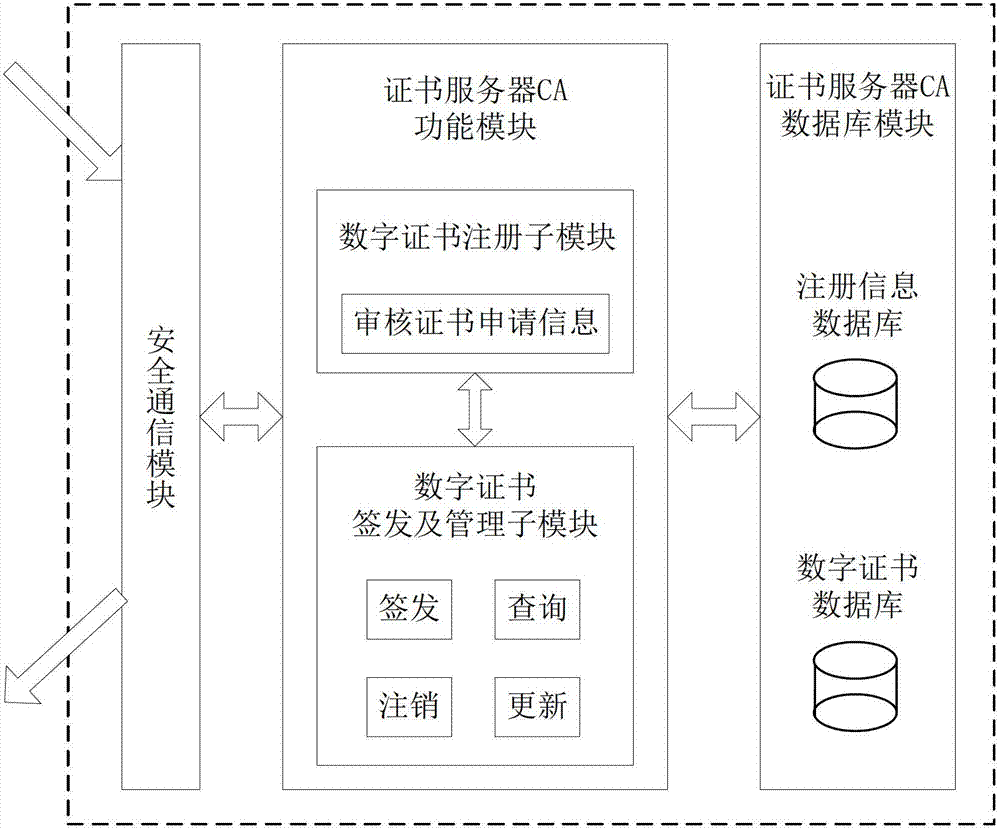
[0054] refer to figure 1 , The file security protection system of the present invention includes: a unified authentication and management server, a certificate server CA, a key management server and a client terminal. The unified authentication and management server, the certificate server CA and the key management server are directly connected to each other to form the server side of the system. The unified authentication and management server is the intermediate node of the entire system. It is directly connected to the client terminal, and all of the client terminal Business requests are processed or forwarded through the unified authentication and management server, among which:
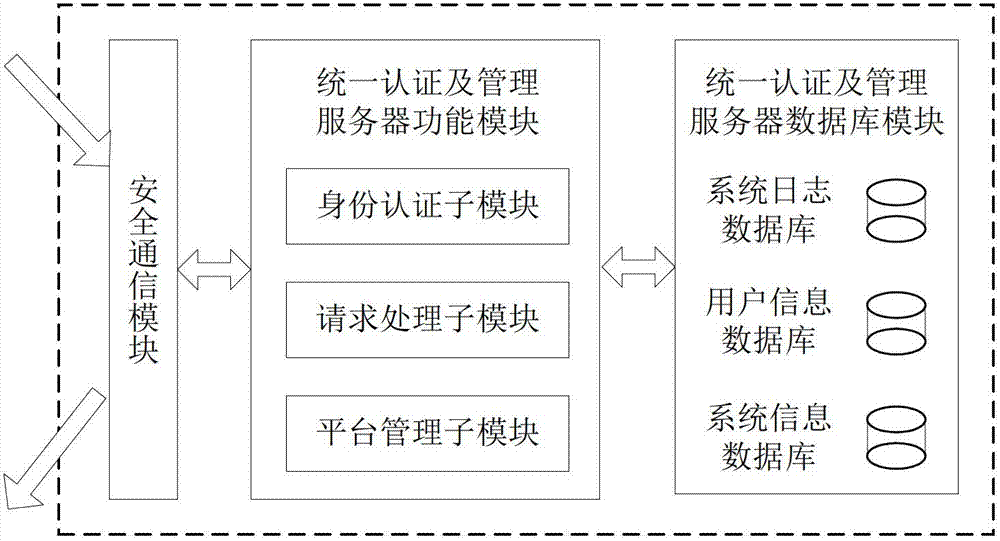
[0055] The unified authentication and management server is used to receive the service request of the client terminal, and communicate with the certificate server CA or the key management server according to the service request, and complete the processing of the following service requests:
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com