Wireless network access method based on NFC certificateless authentication
A wireless network access, no certificate technology, applied in the direction of wireless communication, wireless communication service, public key of secure communication, etc., can solve the problems of security threats, such as existence and retention, to prevent eavesdropping, improve security, and simplify user The effect of the access network step
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
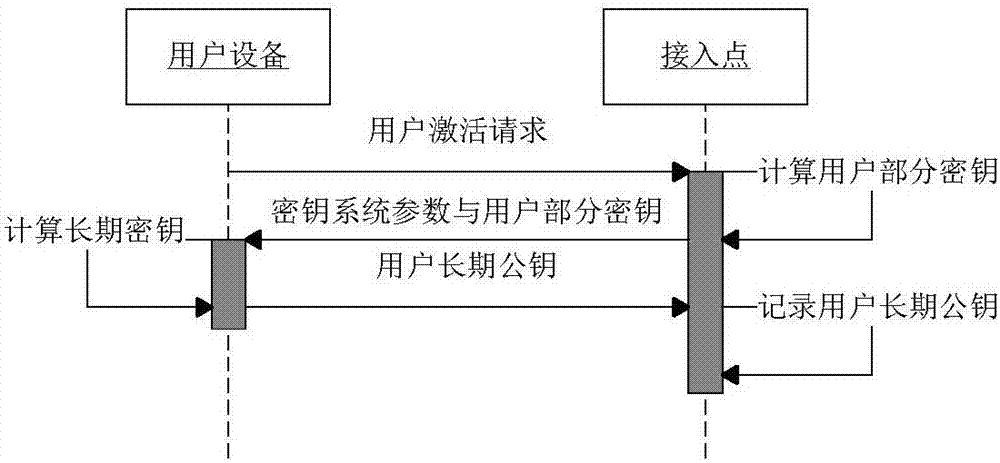
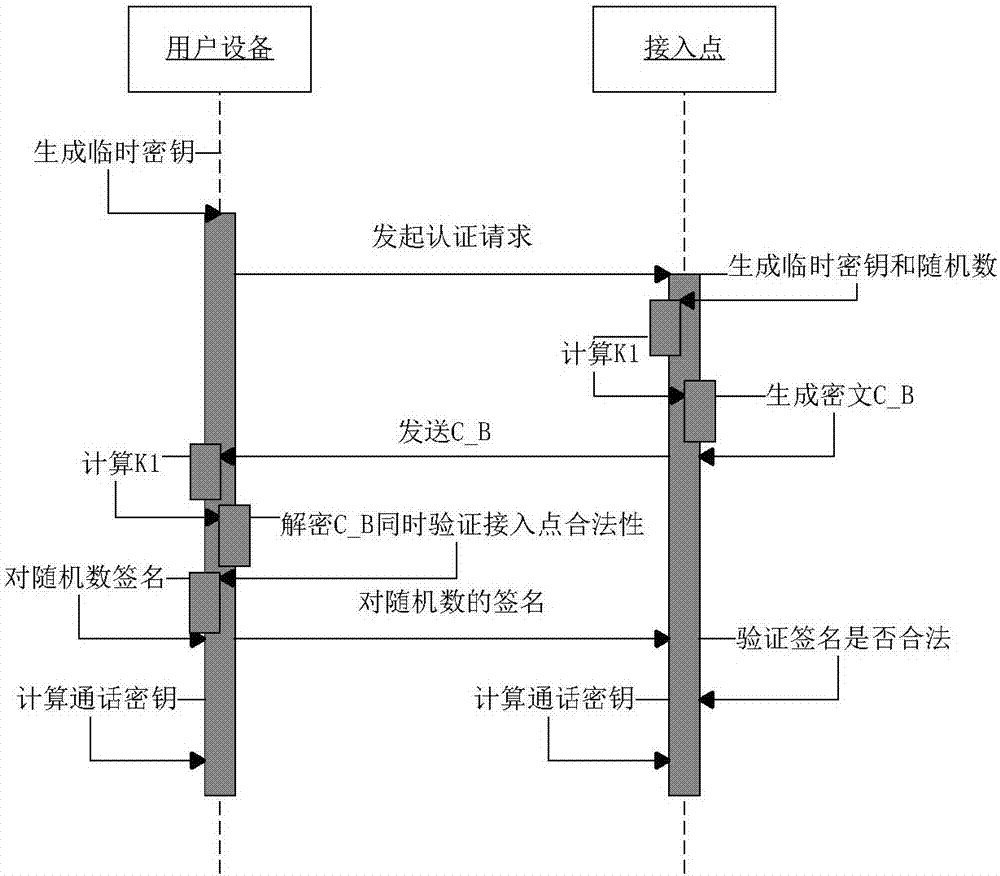
[0020] The present invention will be further described in detail below in conjunction with the embodiments and the accompanying drawings, but the embodiments of the present invention are not limited thereto.
[0021] First give the meaning of each symbol in this method:
[0022] ||: connection operation;
[0023] Y=xP: elliptic curve point multiplication operation, P is generator;
[0024] C B : the ciphertext generated by B;
[0025] m B : by C B decrypted plaintext;
[0026] E. K (): using K as the AES encryption operation of the encryption key;
[0027] D. K (): take K as the AES decryption operation of the decryption key;
[0028] sign(): digital signature operation.
[0029] (1) Access point initialization: AP sets security parameters k∈N, generates two large prime numbers p, q, and q|p-1. P is a generator of any order q of the additive cyclic group G on the elliptic curve. The AP randomly selects the master key Calculate the public key: Y=xP. Define two ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com