Log check point recovery method applied to memory data base OLTP (online transaction processing)
A recovery method and checkpoint technology, applied in the field of database management, can solve problems such as affecting transaction execution speed and increasing database system overhead, and achieve the effects of improving speed, reducing impact, and reducing I/O burden.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
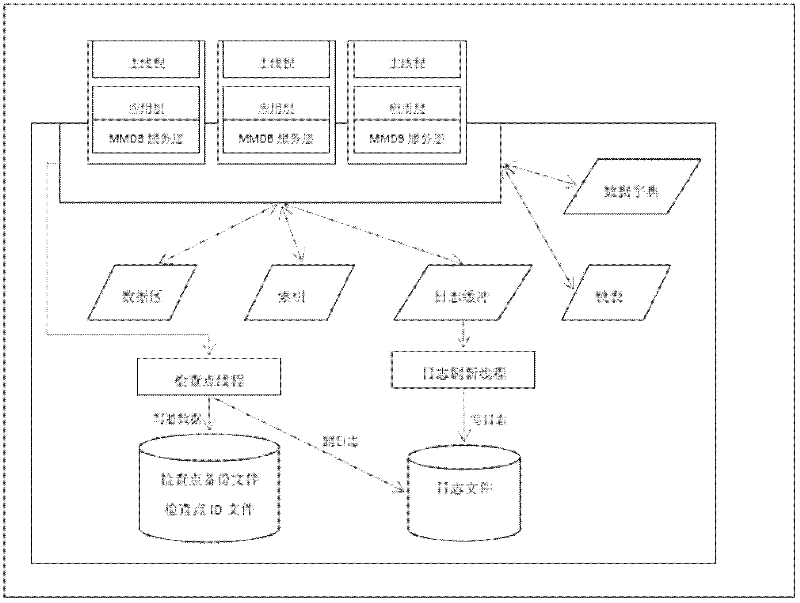
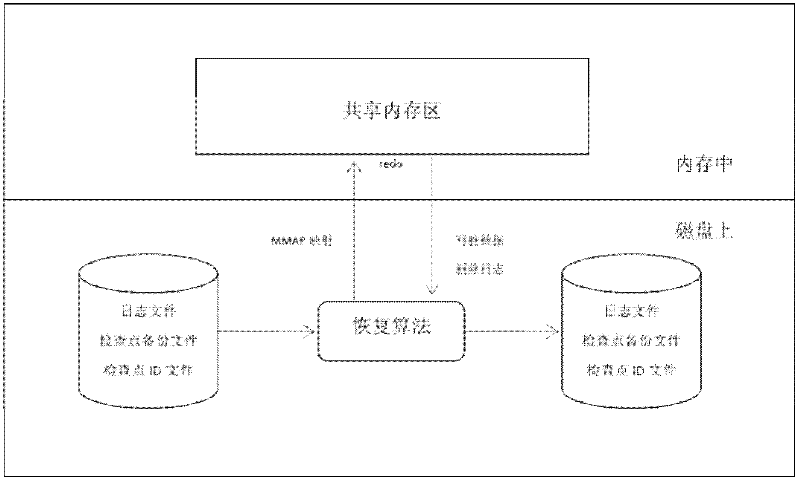
[0020] In order to realize fast recovery of the memory database after a crash, the present invention adopts a log checkpoint recovery method based on double-log double-checkpoint backup. Two sets of log files and two sets of checkpoint backup files can restore the database in turn. Even if the database crashes again during the checkpoint operation or during the recovery process, the correct version of the log and backup files can be selected again for recovery. The specific implementation link of the log checkpoint recovery method will be described in detail below.
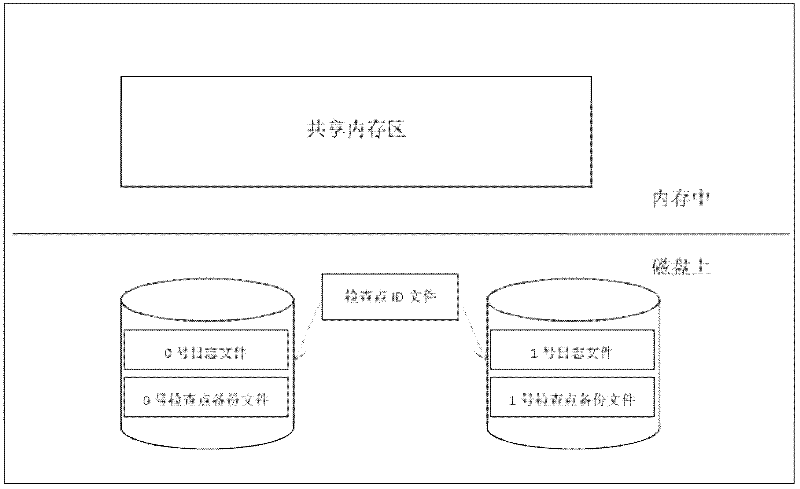
[0021] Such as figure 1 As shown, the log files and backup files on the disk can be divided into three types: redo log files, checkpoint ID files and checkpoint backup files.
[0022] When the database is working, it accepts the request from the client and generates a redo log file for each successfully executed DDL (Data Definition Language) statement and each successfully submitted DML (Data Manipulation Langu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com