Linux operating system file read-write transparent encryption and decryption method
A technology of transparent encryption and decryption and operating system, which is applied in the field of transparent encryption and decryption of file reading and writing, and can solve problems such as high code complexity and incompatibility with the Arm platform
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be specifically introduced below in conjunction with the accompanying drawings and specific embodiments.
[0028] The method for reading and writing transparent encryption and decryption of files in the Linux operating system comprises the following steps:
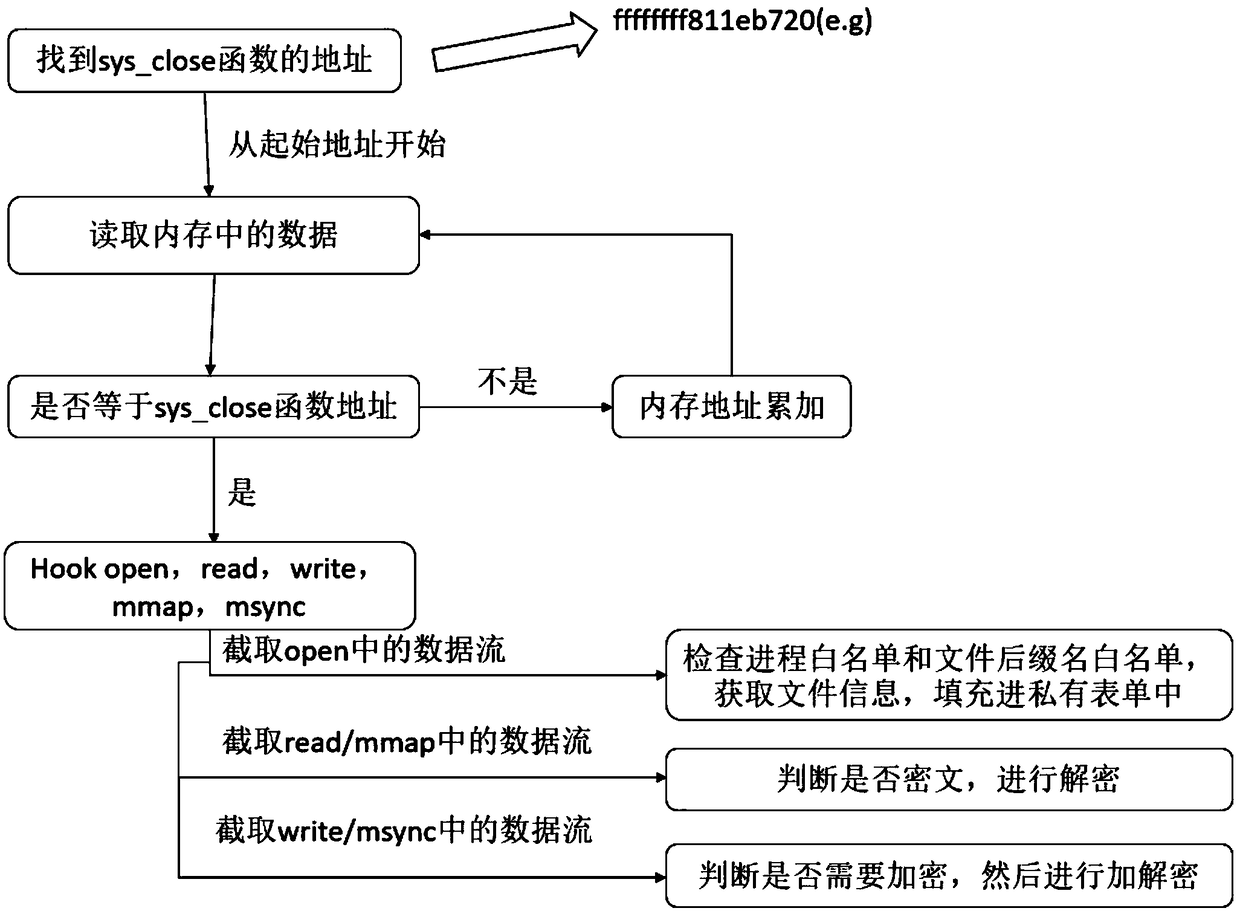
[0029] Step 1, find the address of the sys_close function; as an embodiment, the address of the sys_close function includes: 0xffffffff811eb720 on the ubuntu14.04 system, 0xffffffffb5840370 on the ubuntu16.04 system, and 0xffffffff803338c8 on the winning Kylin system.
[0030] Step 2: Start from the starting address of the memory, read the data in the memory, and perform matching. If the content is the address of the system call sys_close, the matching is successful, and the next step is performed; if not, the matching fails, and the next block of memory is read in the data and match it.
[0031] Step 3: After the matching is successful, the system calls open, read, write, mmap, and msync...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com