Patents
Literature
603results about How to "Guaranteed synchronization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
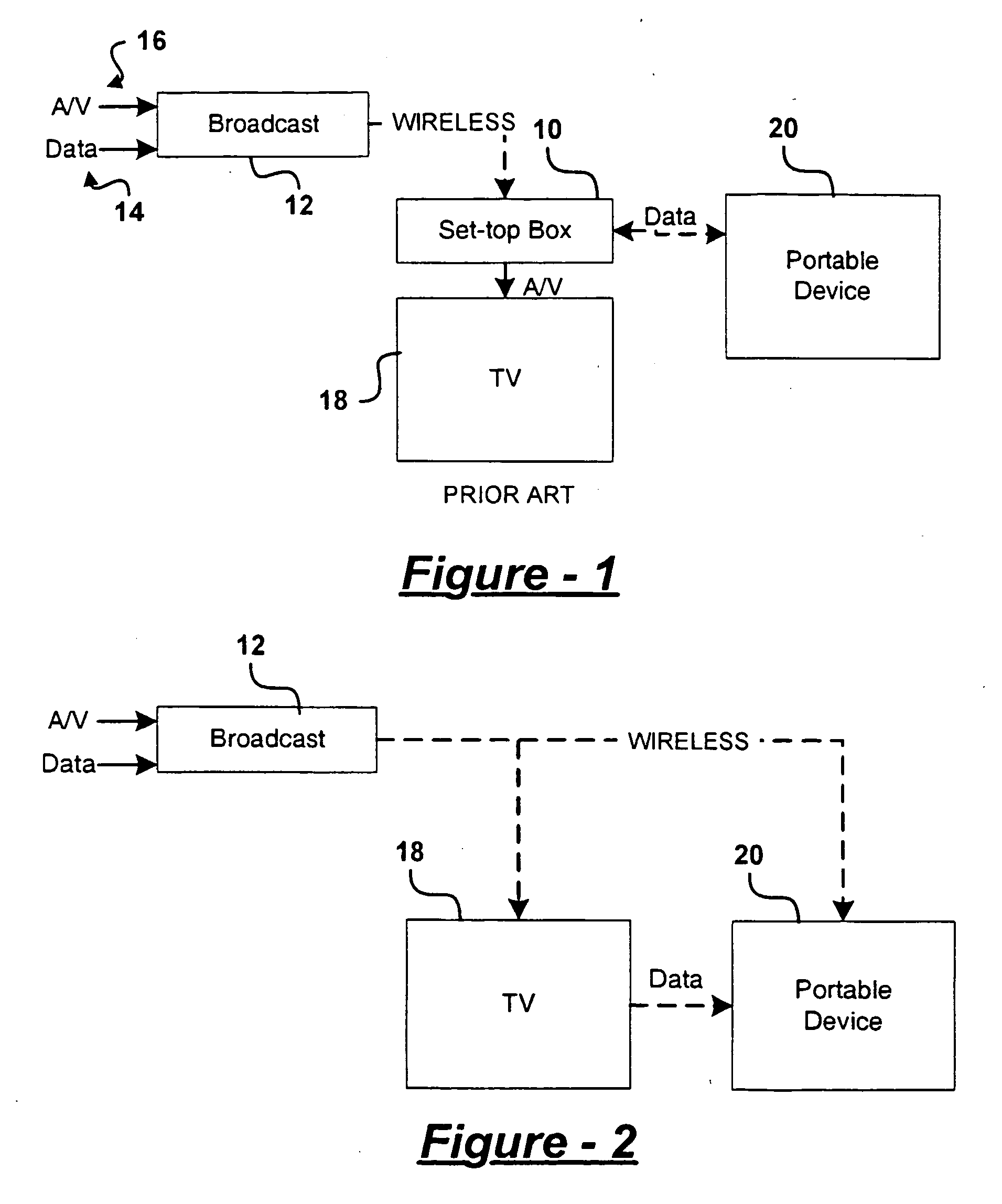
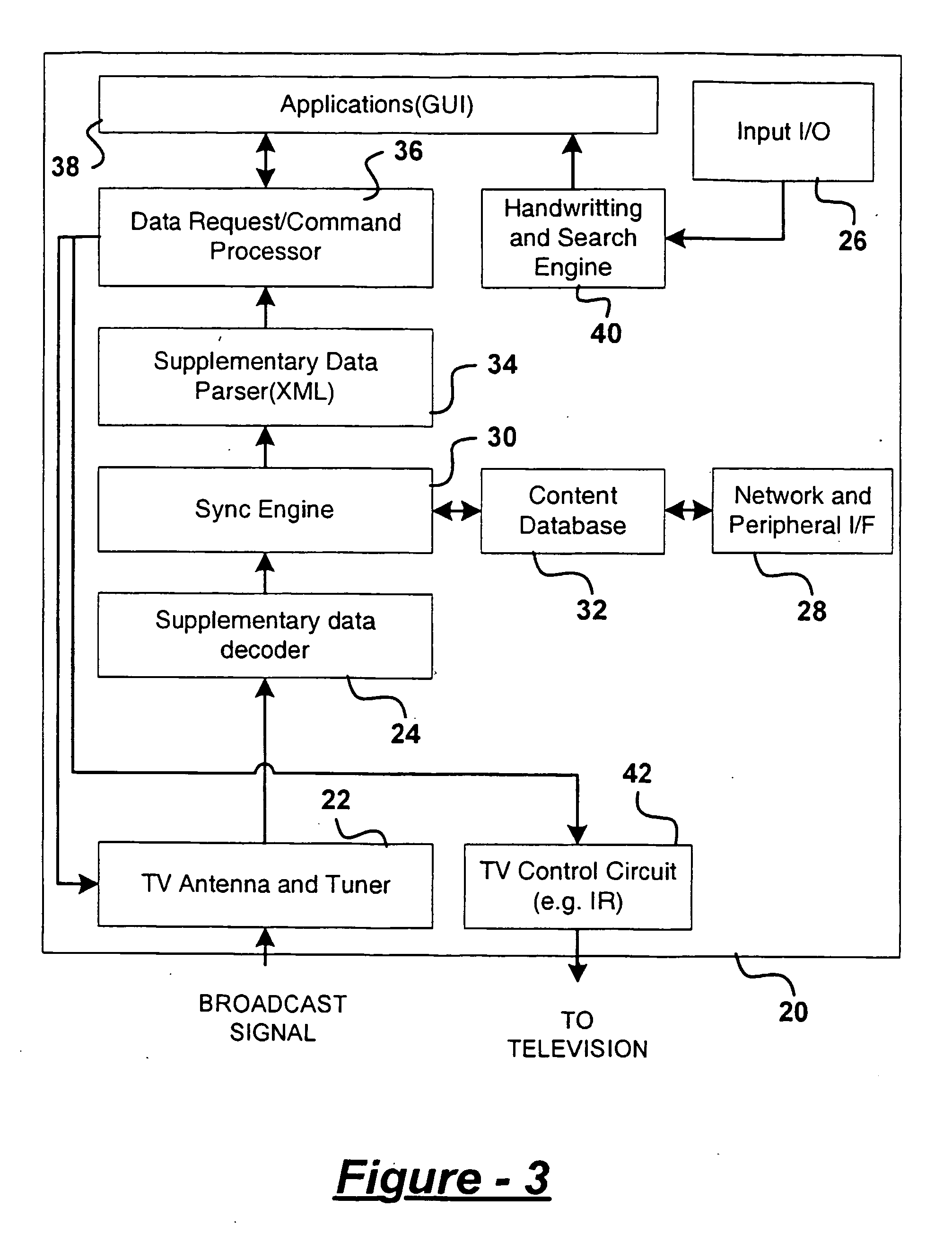
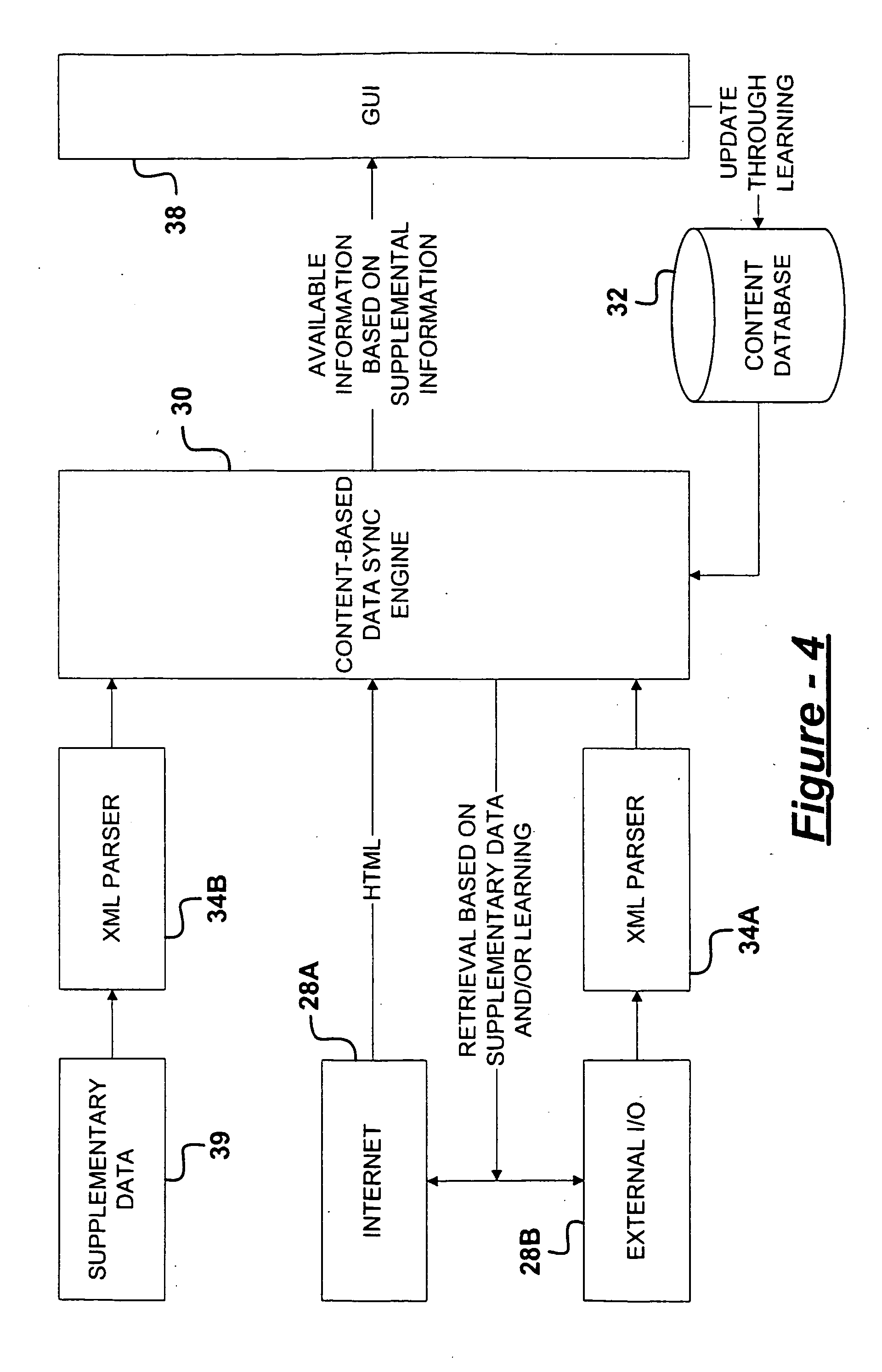
Portable device for viewing real-time synchronized information from broadcasting sources
InactiveUS20060064734A1Guaranteed synchronizationTelevision system detailsBroadcast systems characterised by tuner receiversDisplay deviceBroadcasting
A broadcast media viewing system includes a source of a broadcast stream including primary data providing primary media content and supplemental data providing supplemental information. A media content viewing mechanism decodes the primary data and renders the primary media content to a first active display. A portable device decodes the supplemental data and renders the supplemental information to a second active display.
Owner:MA YUE
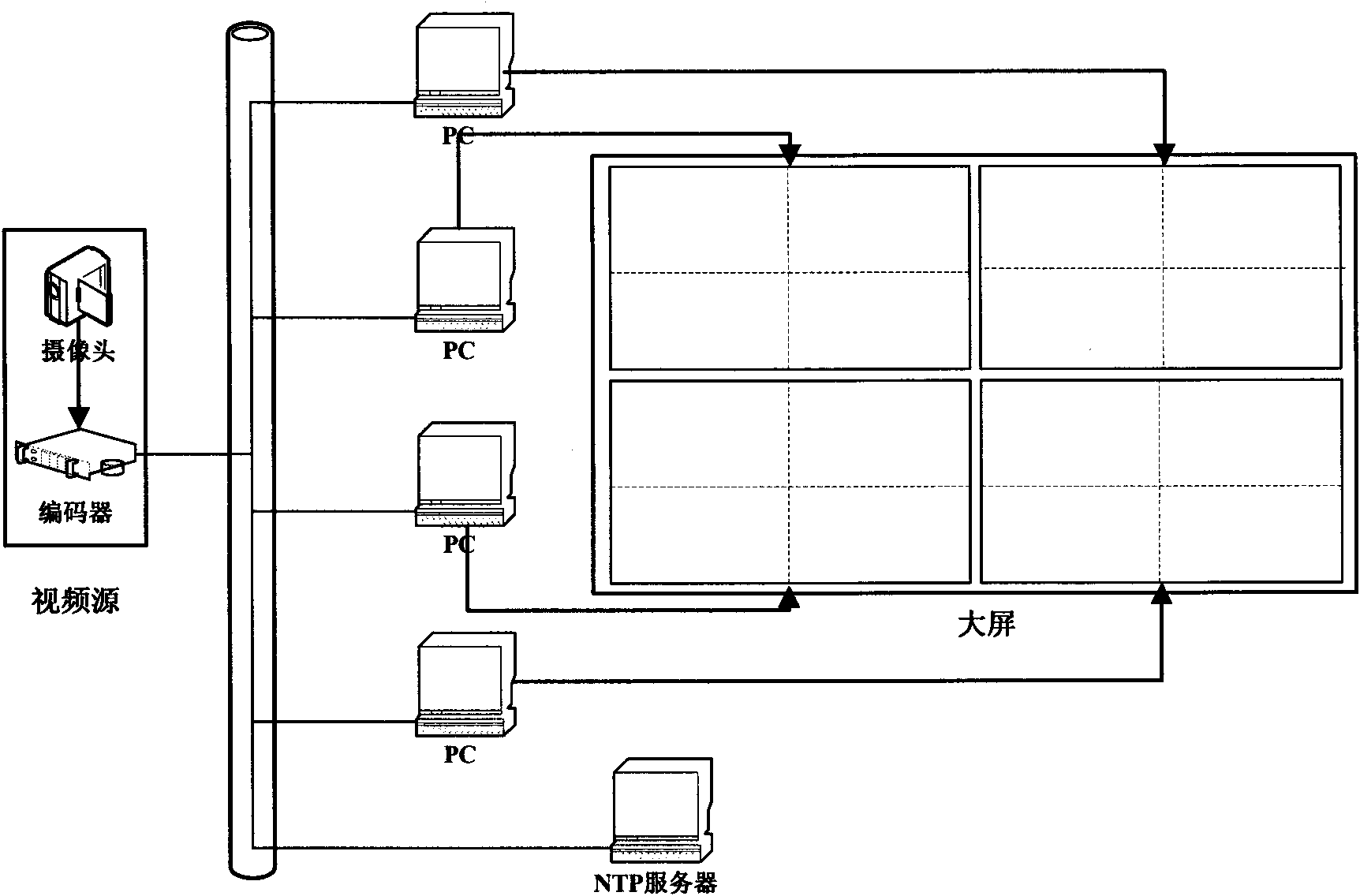
Large screen splicing method and system
ActiveCN101807389AGuaranteed synchronizationEnsure uniform and continuousCathode-ray tube indicatorsTelevision systemsTimestampImaging quality
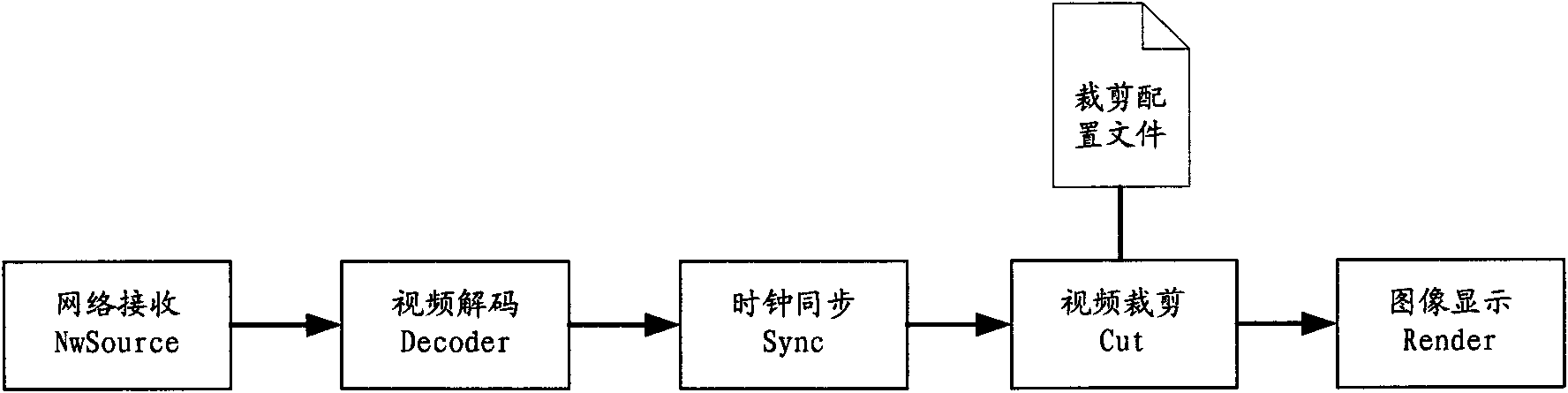
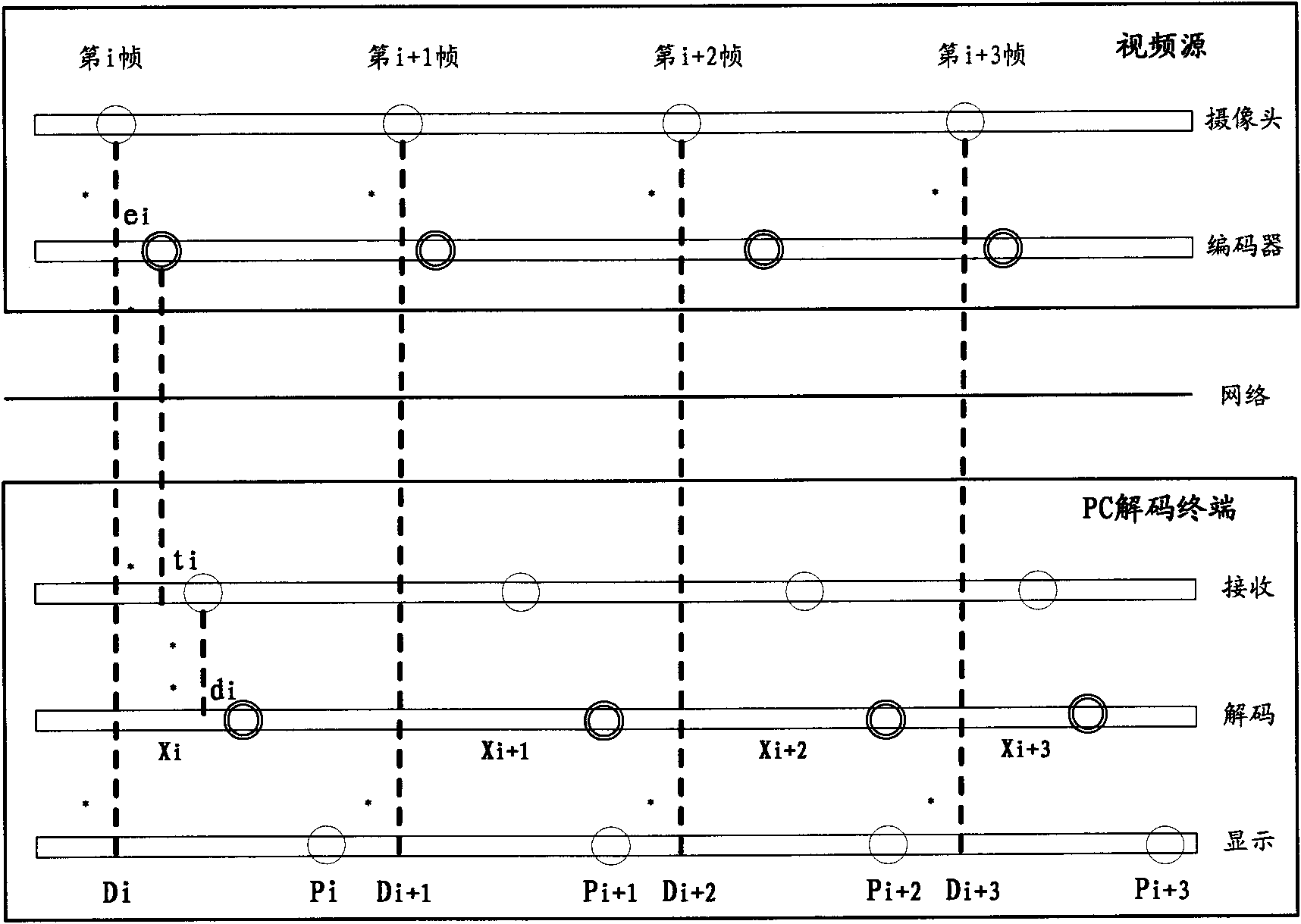
The invention discloses large screen splicing method and system, wherein the method comprises the following steps of: A, transmitting the same video stream to a plurality of PC (Personal Computer) decoding terminals connected through a network to ensure the synchronous transmission of data through the modes of UDP (User Datagram Protocol) multicasting transmission and the like; B, carrying out delay regulation on each PC decoding terminal through NTP (Network Time Protocol) clock synchronism and frame timestamp to ensure the image quality of a spliced large screen; and C, cutting and displaying part of the image by using each PC decoding terminal to ensure that the image of the spliced large screen is integral and non-overlapped. The invention realizes the infinite amplification on splicing the large screen through the infinite expansion of the PC terminal, realizes the flexible changes of the splicing size and the resolution ratio of the large screen through the arbitrary combination of the PC decoding terminals and ensures the synchronism of each part of the image of the spliced large screen as well as the uniformity and the continuity of the whole image through video delay regulation.
Owner:ENC DATA SERVICE CO LTD
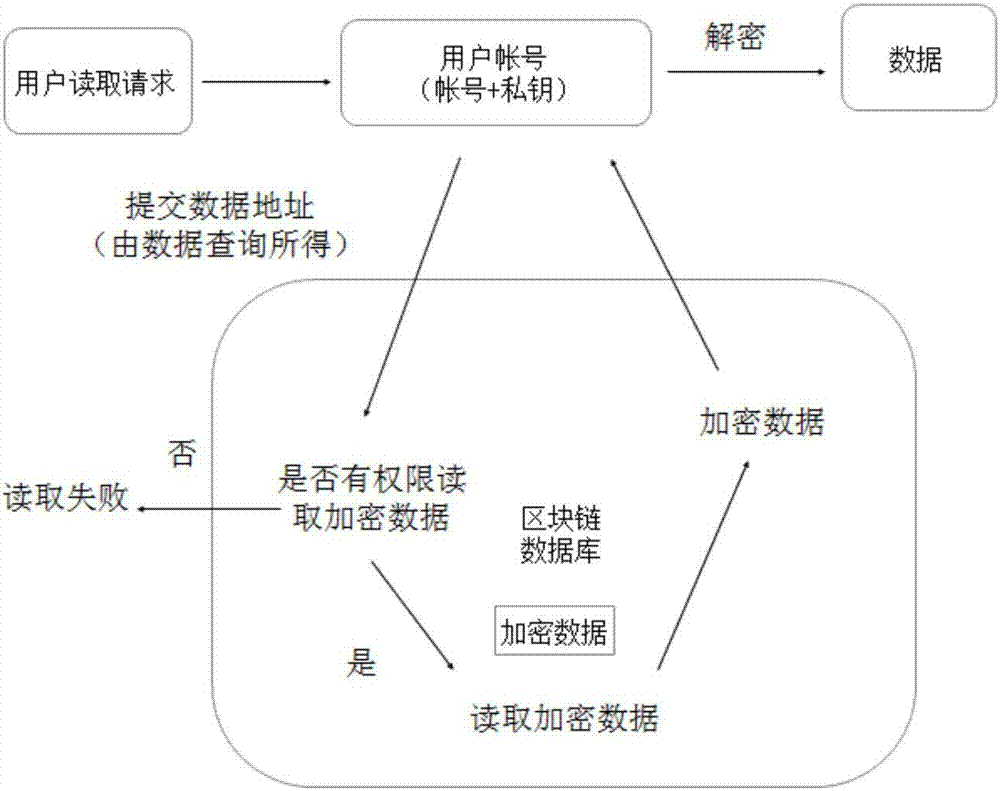
Blockchain-based database system and method of using same
ActiveCN107292181AFix permission issuesSolve the problem of excessive permissionsDigital data protectionSpecial data processing applicationsConfidentialityCentral database
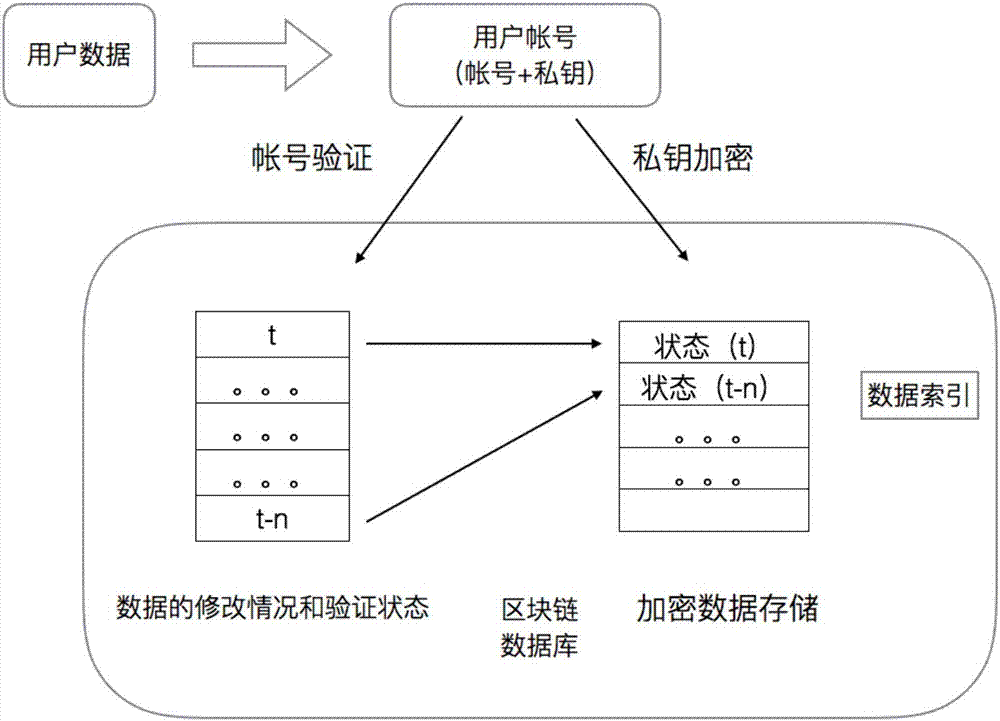
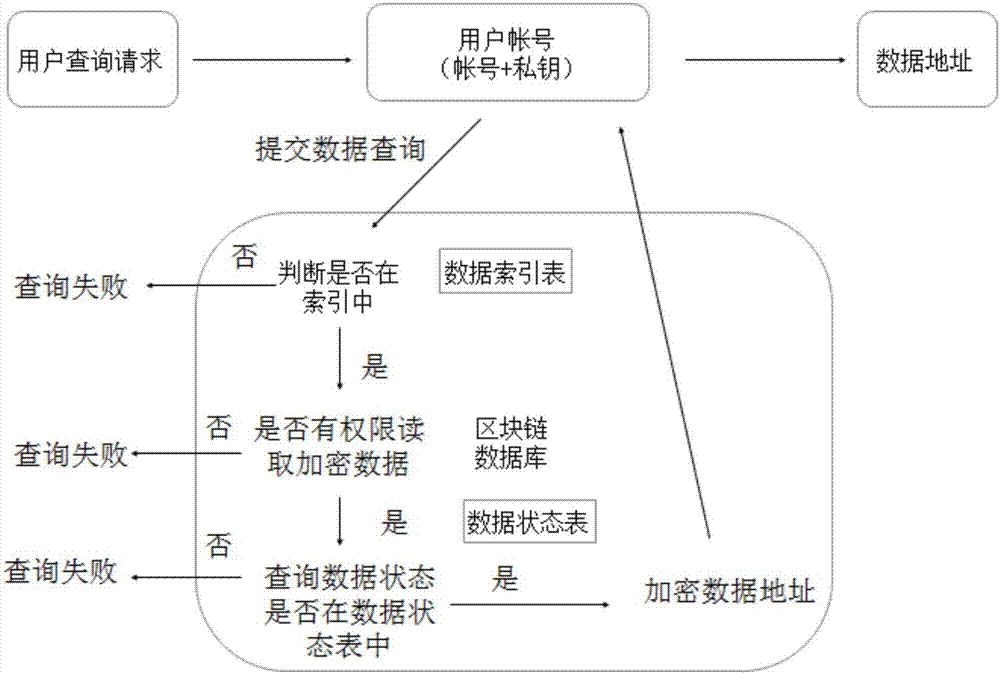
The invention discloses a blockchain-based database system, comprising a client, an access server and a blockchain verification server. A method of using the blockchain-based database system comprises the steps of 1, registering a blockchain account on the blockchain verification server through the client, or registering, by the blockchain verification server itself, the blockchain account on the blockchain verification server, and acquiring a public key and a private key; 2, writing, by a user, data into the access server through the client; 3, transmitting, by the access server, a request to the blockchain verification server to perform data co-recognition; 4, submitting, by the user, a query request to the access server through the client to perform related query; 5, after the user obtains data query results, directly using, by the user, the results to read data, or otherwise the user having the need to perform data query; after data reading, unlocking the data by the user through his or her own account private key. The problems are solved that data in a central database are insecure and it is difficult for a distributed database to arrive at uniformity and data confidentiality.
Owner:无锡井通网络科技有限公司
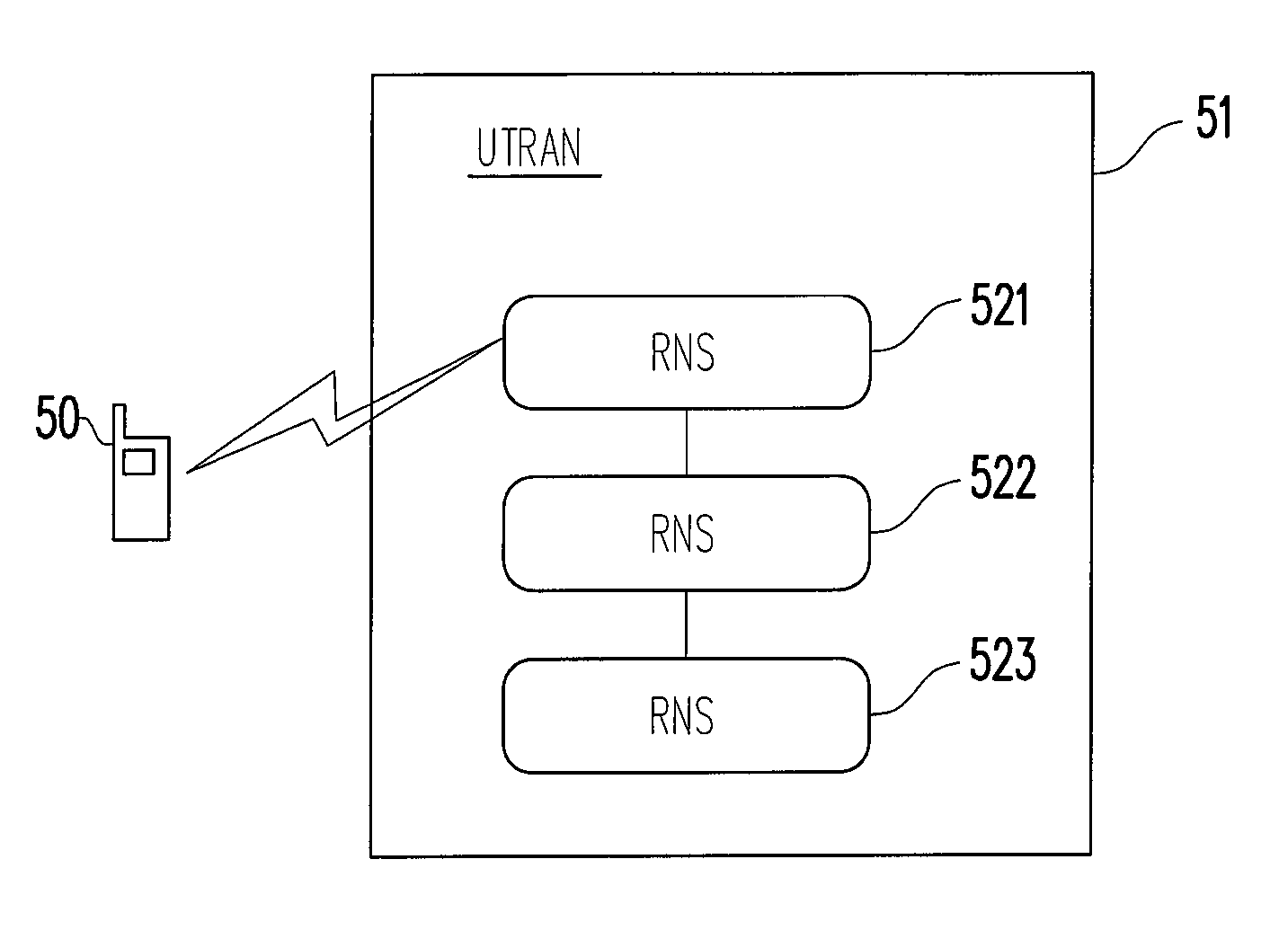
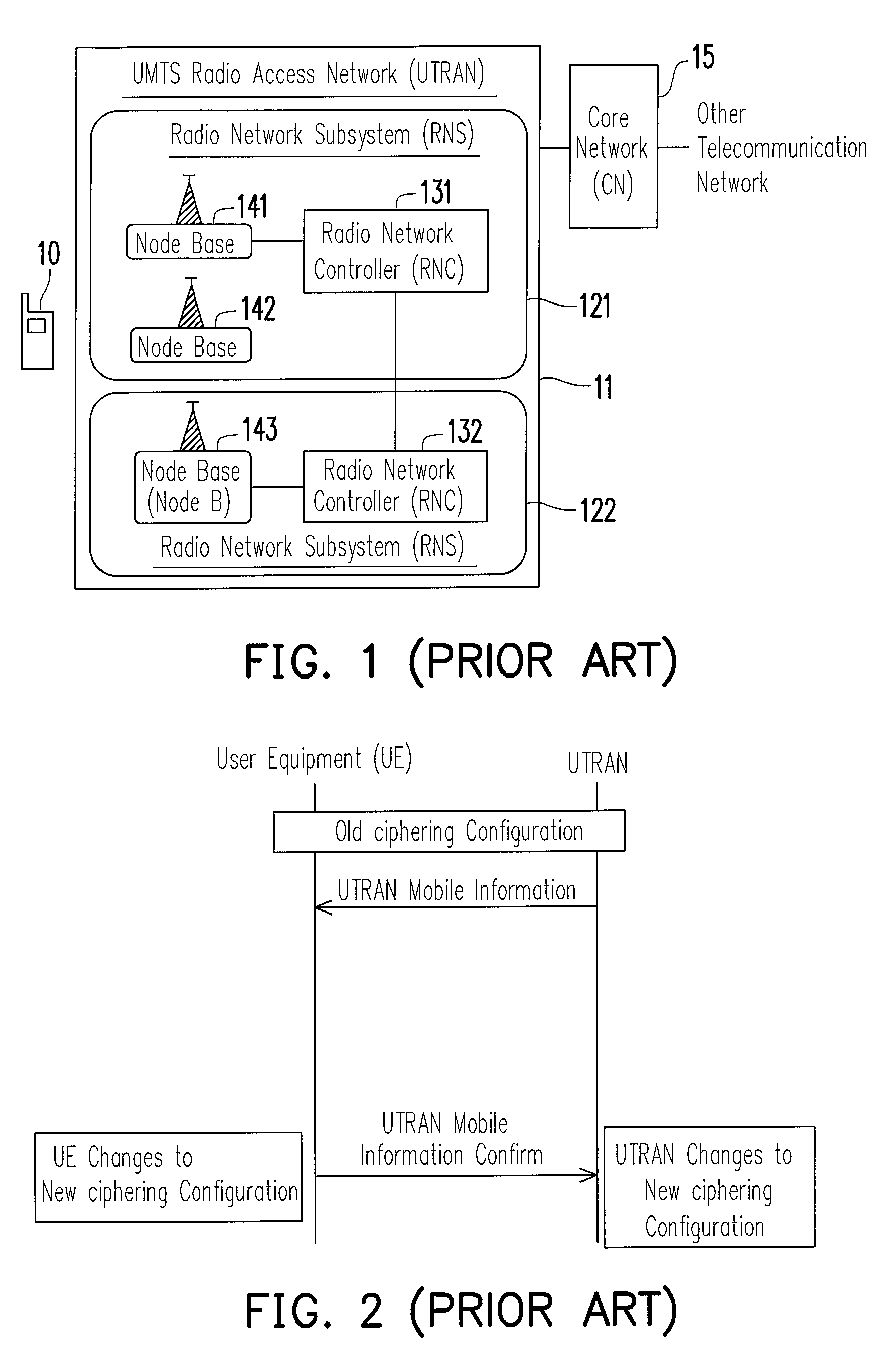
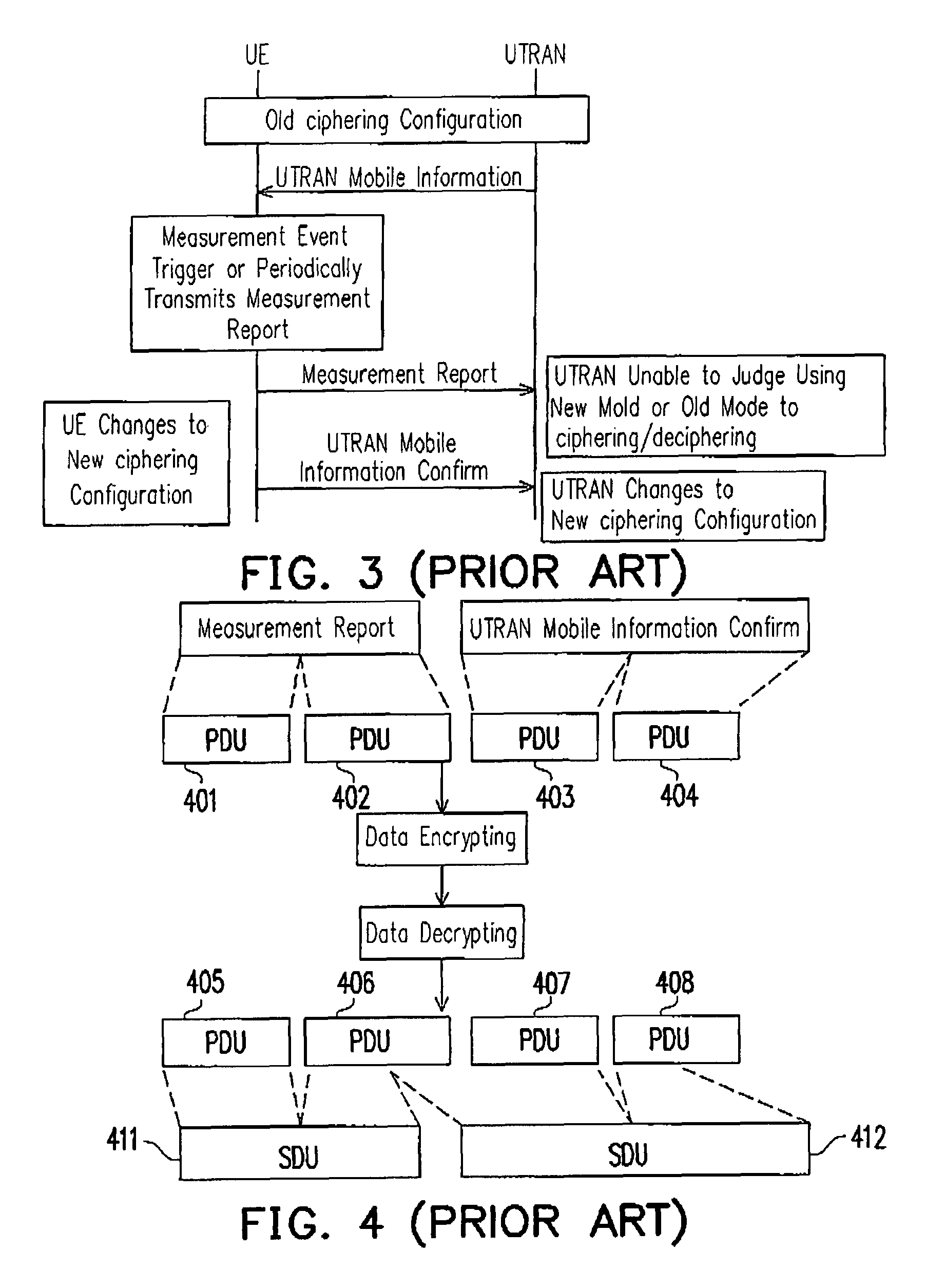
Communication system, user device thereof and synchronization method thereof
ActiveUS7817595B2Avoid dataReduce failureTime-division multiplexConnection managementCommunications systemRadio Link Control
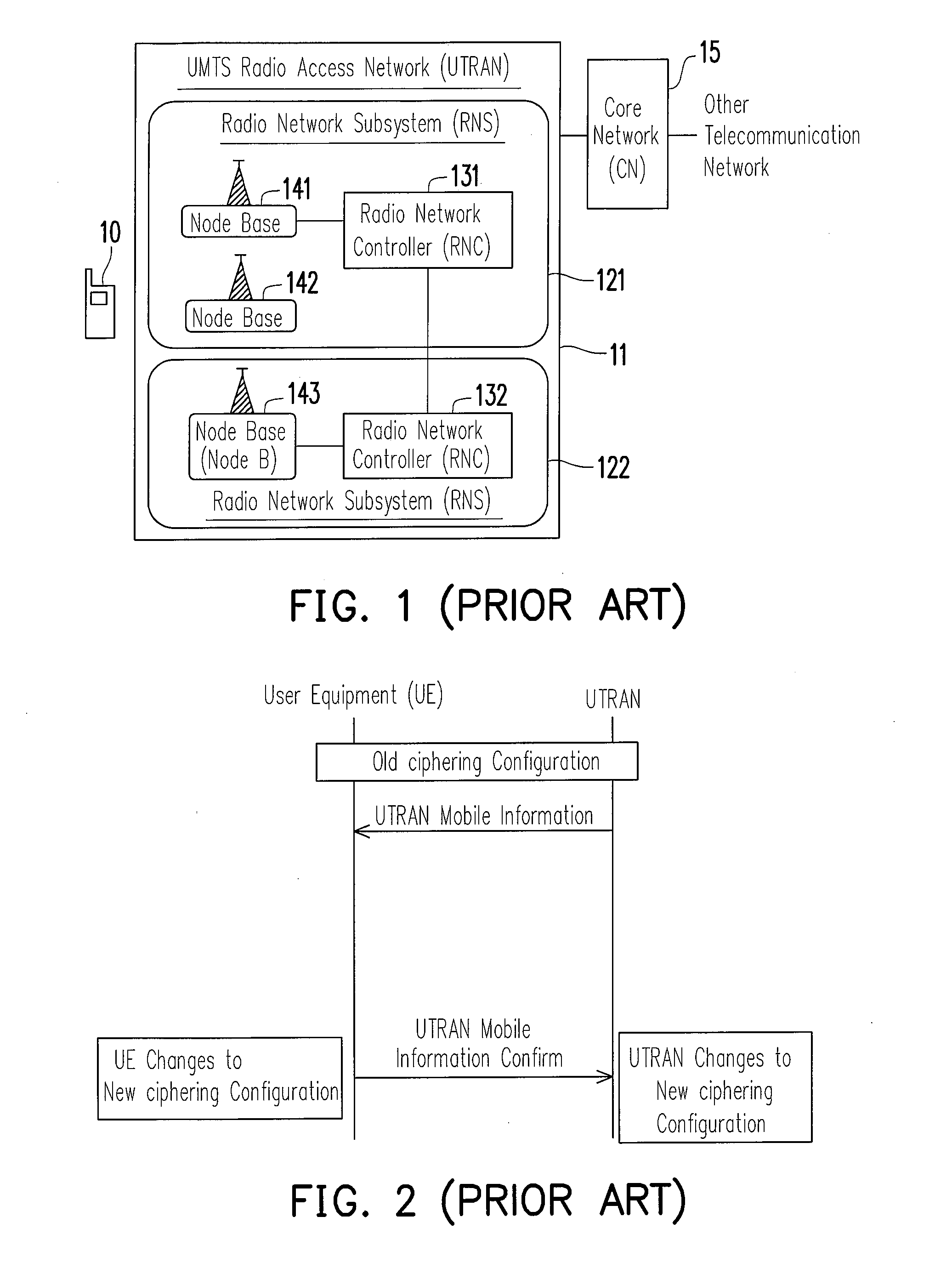
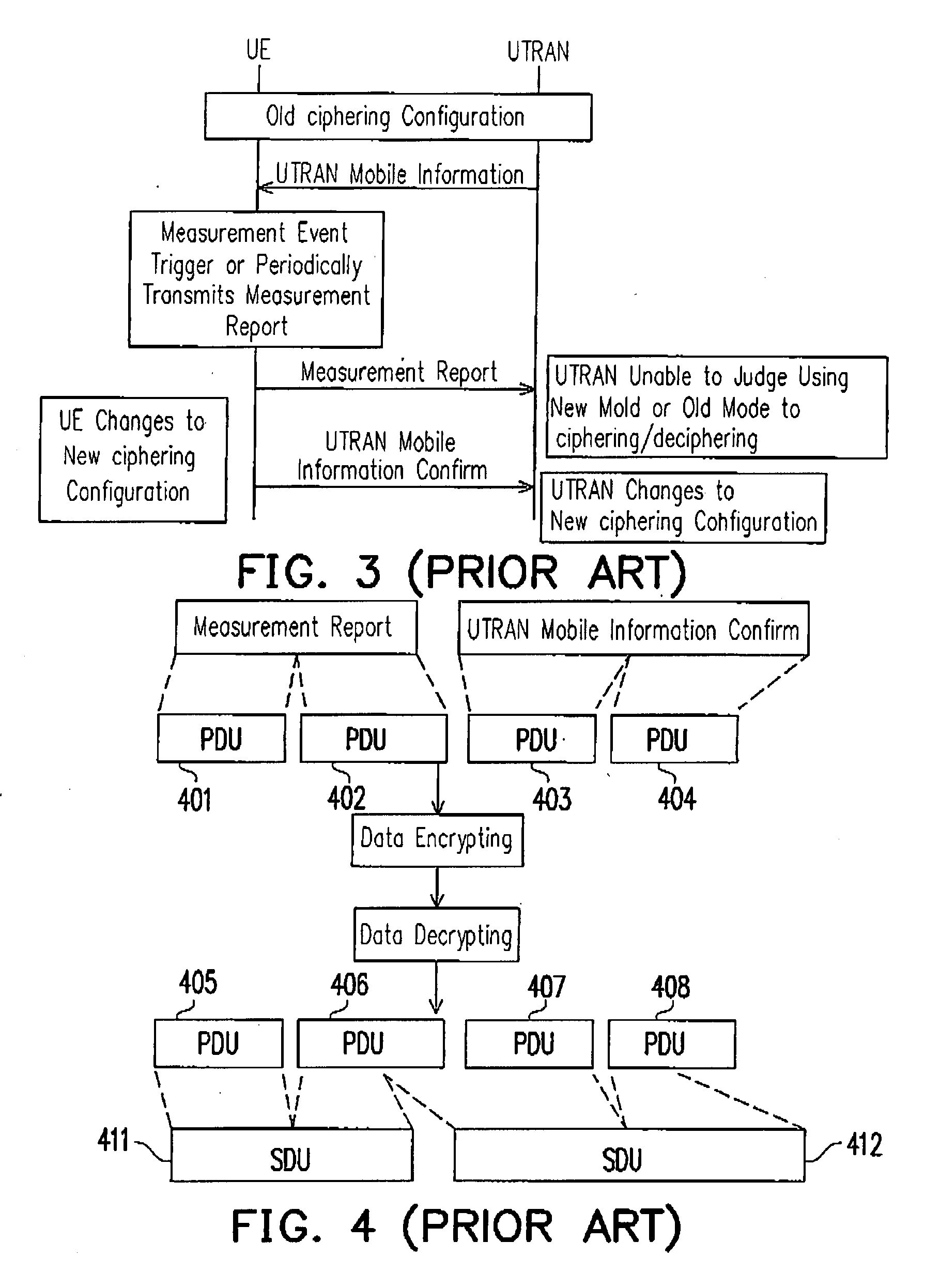
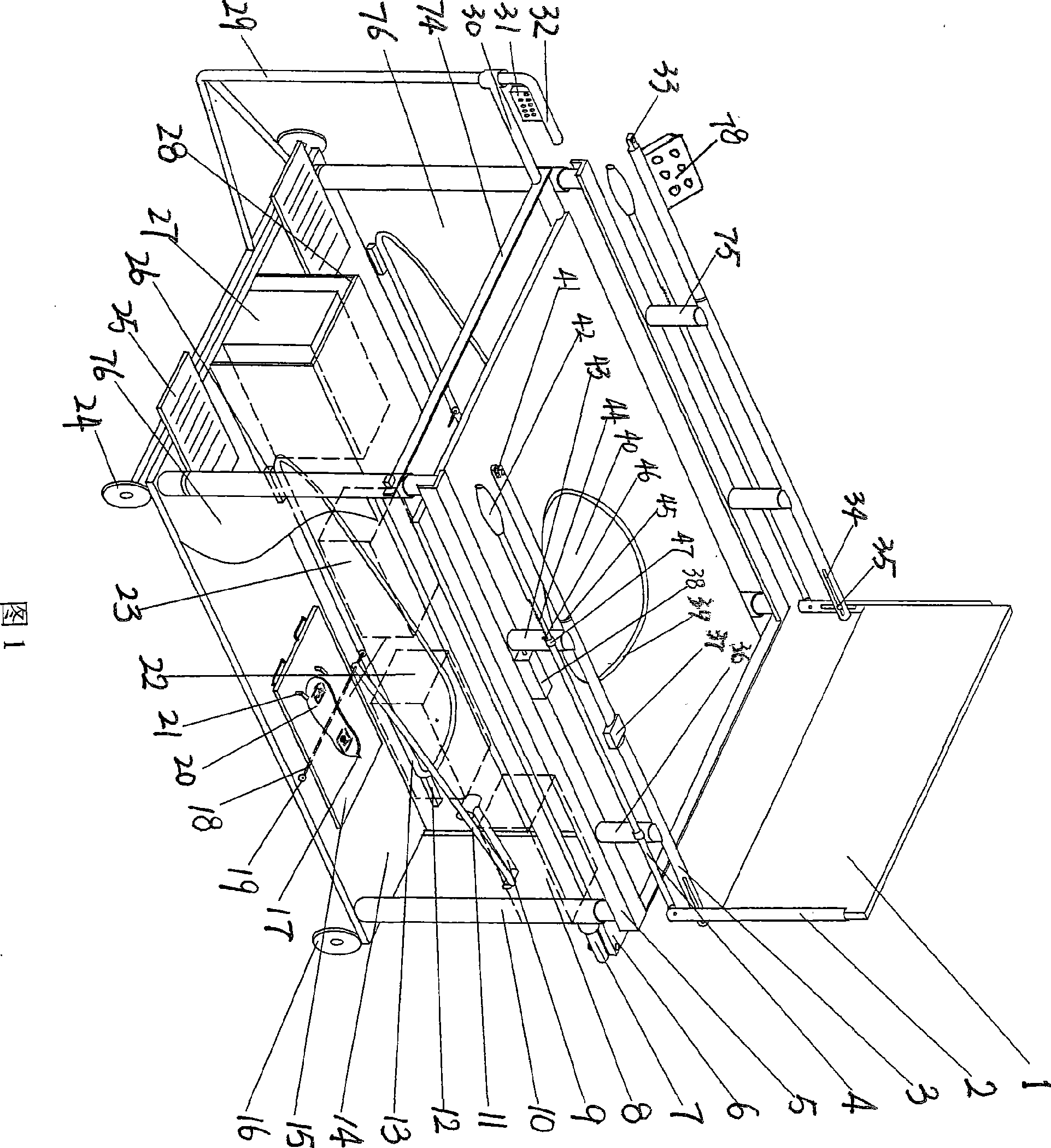
A communication system, user device thereof, and a synchronization method thereof are provided. The communication system includes a user device and a wireless network. A ciphering configuration information is transmitted to a user device. The user device and wireless network re-establishing the radio link control (RLC) entity of logical link. The user device changes to the new ciphering configuration immediately following the re-establishment of RLC entity according to the received ciphering configuration information and the wireless network changes to the new ciphering configuration.
Owner:HTC CORP
High dynamic range video imaging system and image generating method
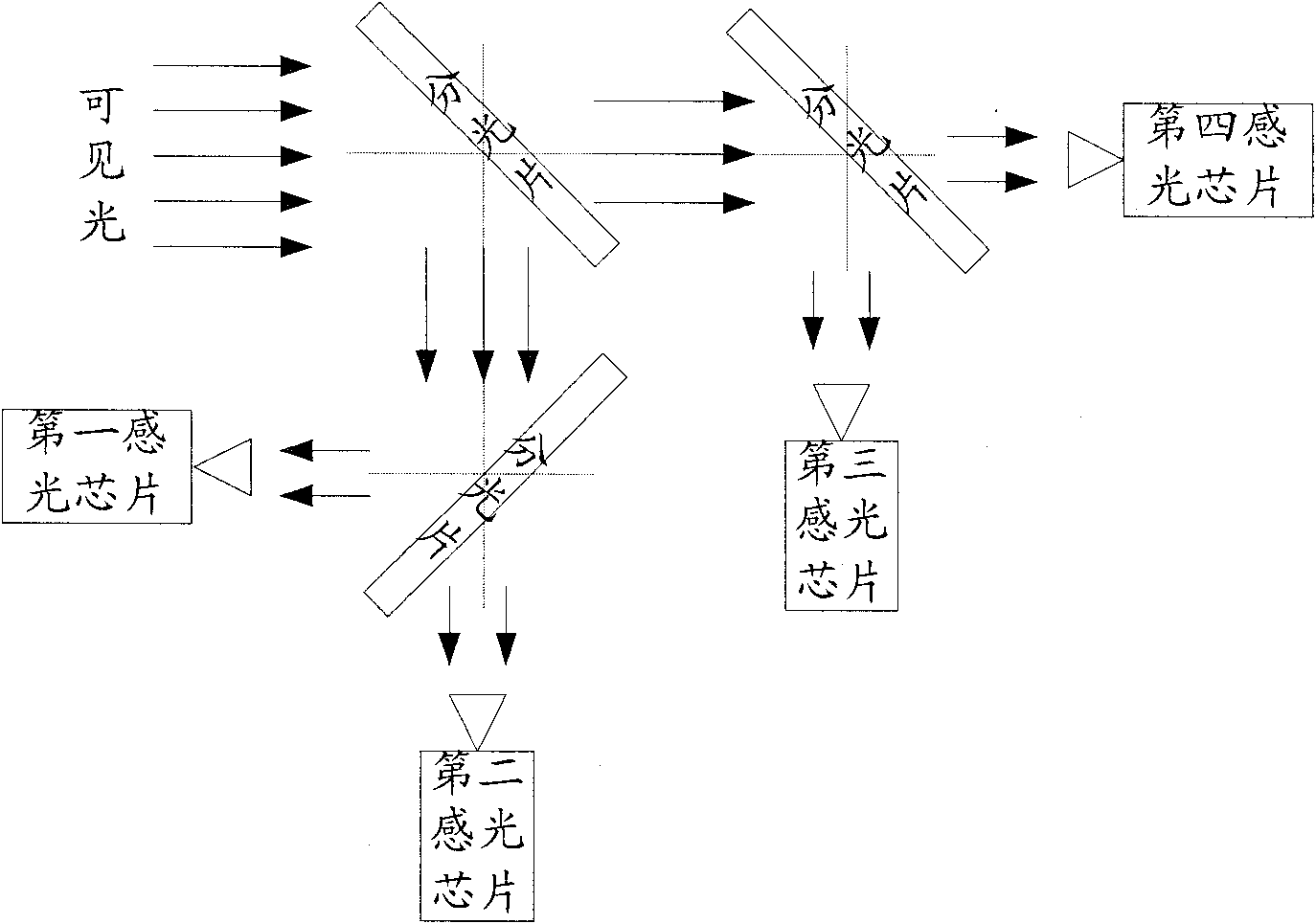
ActiveCN101888487AGuaranteed synchronizationGuaranteed real-timeImage enhancementTelevision system detailsCamera lensImaging processing
The invention relates to a high dynamic range video imaging system and an image generating method. The system comprises an optical lens, an image processing unit, at least an optical splitter and a plurality of sensitive chips. The optical splitter splits the incident light penetrating through the optical lens into a plurality of beams which enter the plurality of sensitive chips so as to obtain image data with different exposures. The image processing unit fuses the image data to generate high dynamic range images. Each sensitive chip used by the high dynamic range video imaging system fused by the plurality of sensitive chips has same specifications so that synchronization and instantaneity of photographing can be ensured. Meanwhile, the generated video image has obvious advantage in color and luminance uniformities and affluent visual information compared with single exposed image, can effectively solve the problems of underexposure, overexposure and color and luminance non-uniformities in traditional image pickup systems and has great market applicable foreground.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Video producing method, device and system
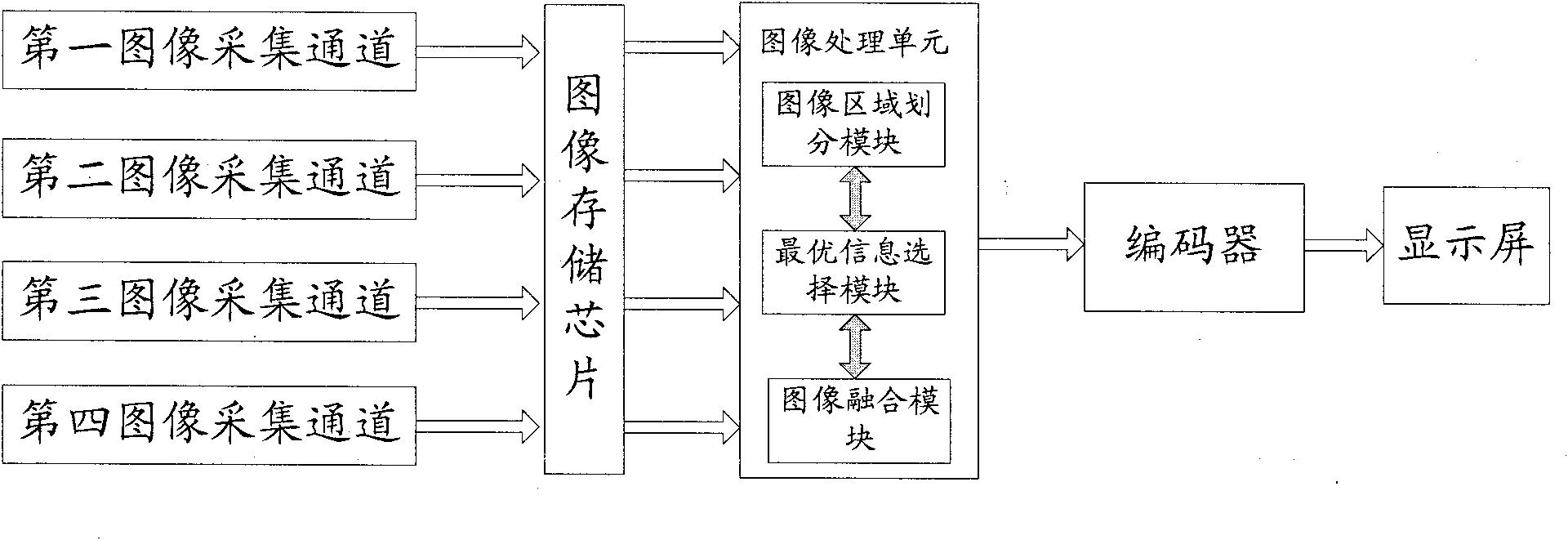
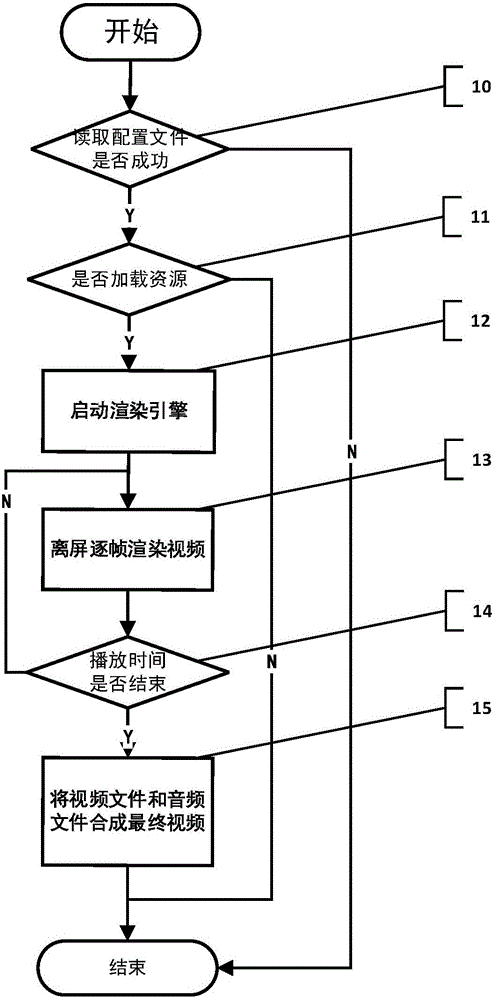
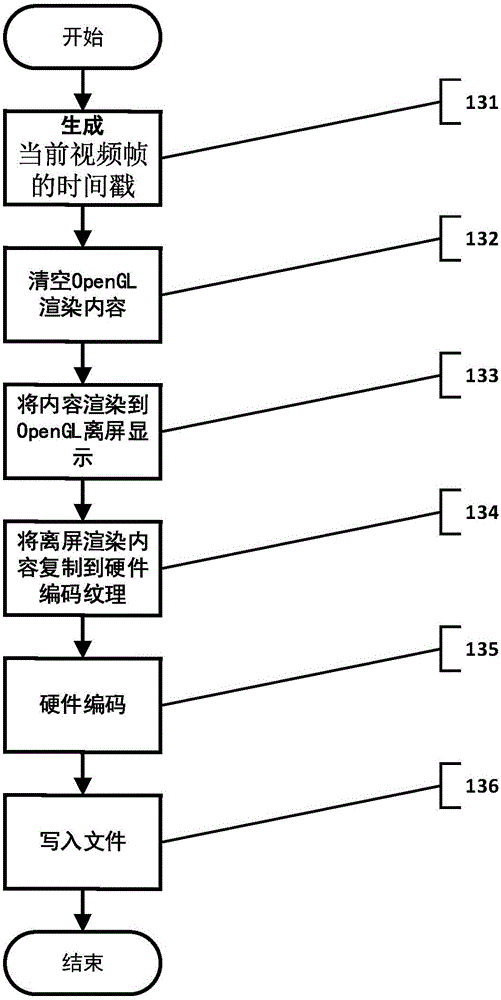
InactiveCN105933724AEasy to manage and deployReduce operating loadClosed circuit television systemsSelective content distributionAnimationVideo production
The invention belongs to the technical field of video production, and particularly relates to a video producing method, device and system. The video producing method comprises the following steps: reading a configuration file, and acquiring and loading resources for producing a video; starting a rendering engine, and initializing a hardware encoding-decoding environment and an OpenGL off-screen rendering environment; and performing frame-by-frame off-screen rendering to generate raw video streams. Through adoption of an off-screen rendering technology, video production can be run in the form of a background task without being limited by the screen resolution. Through frame-by-frame rendering based on decoding time, audio-video synchronization and animation smoothness of an output video are ensured. Moreover, hardware decoding is performed on videos supporting hardware decoding, and hardware screen capture is performed on content which is already rendered in an off-screen way, so that hardware resources are utilized fully; the CPU (Central Processing Unit) occupation rate in a video producing process is lowered; and the processing efficiency is increased.
Owner:FUJIAN STAR NET EVIDEO INFORMATION SYST CO LTD
Clock synchronization method among wireless network devices
ActiveCN106131947AGuaranteed synchronizationEnsure consistencySynchronisation arrangementTime-division multiplexSynchronous controlInterconnection
The invention provides a clock synchronization method among wireless network devices. The method comprises the steps that 1, a clock source device and at least one clock slave device are in network interconnection; 2, the clock source device obtains a reference clock, and the clock slave devices obtain unsynchronized reference clocks; 3, the clock source device interacts clock information with the clock slave devices through clock synchronization frames; 4, the clock source device transmits information containing the frequency and phase of the reference clock to the clock slave devices; the CPU processors in the clock slave devices calculate the reference clock of the clock source device and calibrate own reference clocks according to the reference clock; and the clock synchronization among the wireless network devices is realized through the steps. The synchronized reference clock can be used for synchronous scheduling of CPU system tasks, synchronous control of performance of instructions, high-precision synchronous measurement of external signals and synchronous measurement of high-speed moving objects, basic wireless take scheduling can be satisfied, and the synchronous awakening tasks of the devices in an ultra low-power-consumption application can be satisfied.
Owner:潘进
Synchronization method and device for MAC (Media Access Control) address table information of distributed network processing system
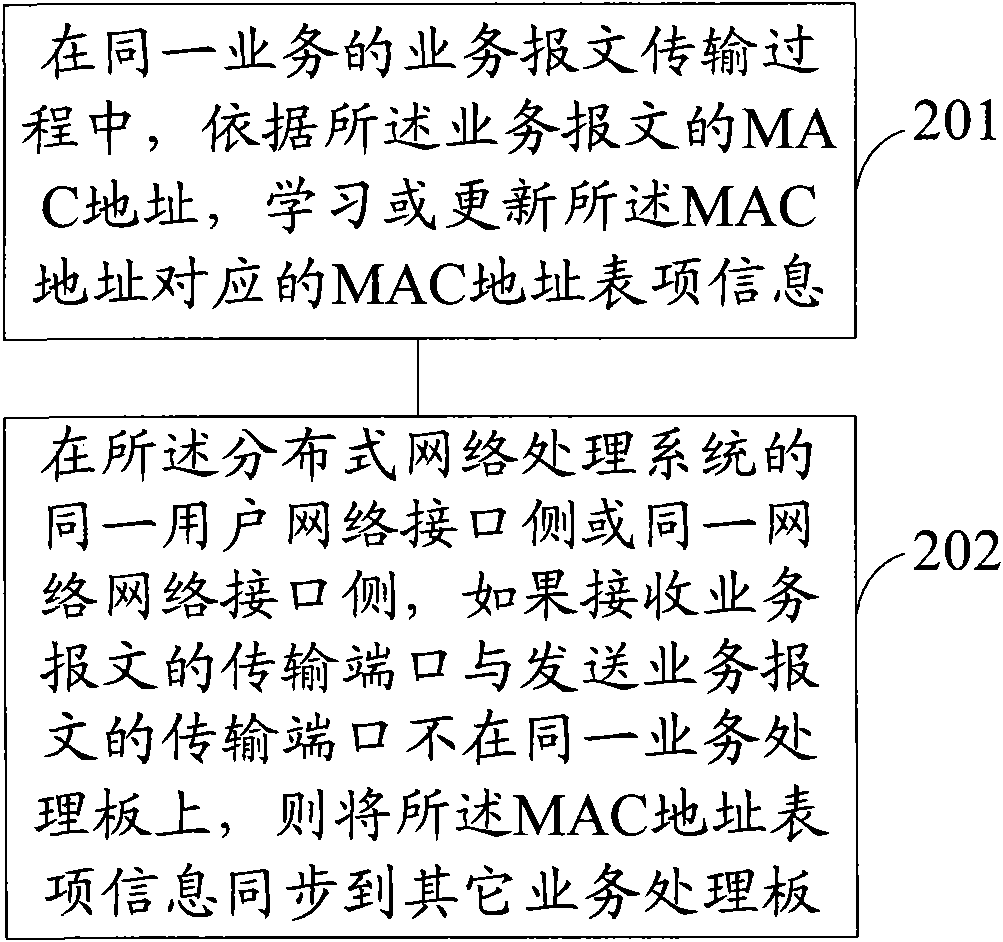
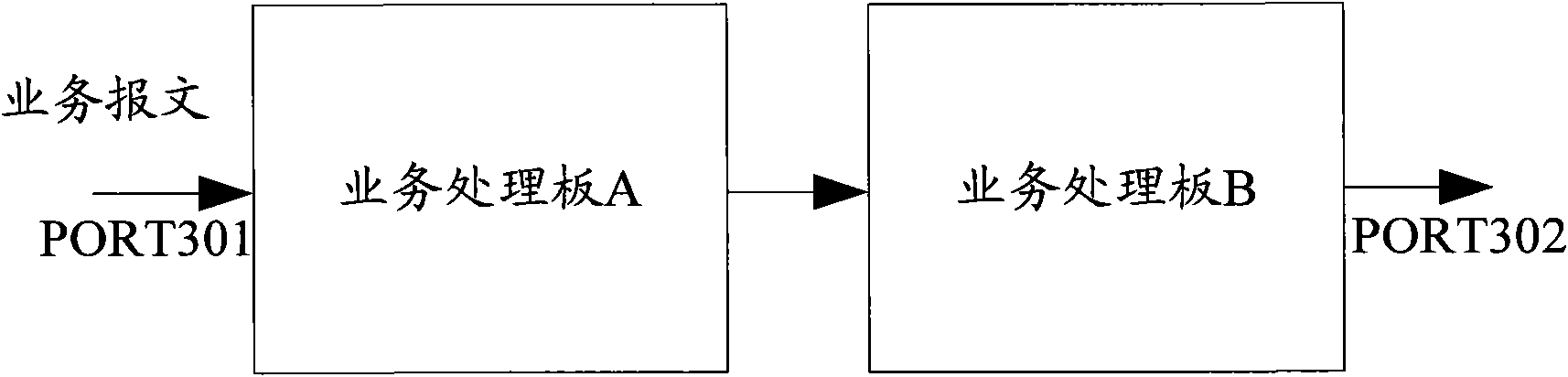
InactiveCN101820435AGuaranteed synchronizationGuaranteed transfer interruptionData switching networksTransfer procedureMedia access control
The embodiment of the invention provides synchronization method and device for MAC (Media Access Control) address table information of a distributed network processing system. In the method, during the transmission of a service message of the same service, a service processing board receiving the service message learns or updates the MAC address table information corresponding to the MAC address according to the MAC address of the service message, the MAC address table information is the corresponding relationship between the MAC address and the port of the service processing board; at the same user network interface side or the same network interface side of the distributed network processing system, the MAC address table information is synchronized to another service processing board of the distributed network processing system if the transmission port receiving the service message and the transmission port transmitting the service message are not located on the same service processing board. The efficiency for the synchronization of the MAC address table information is improved, and the space occupied by the MAC address table information is saved.
Owner:HUAWEI TECH CO LTD
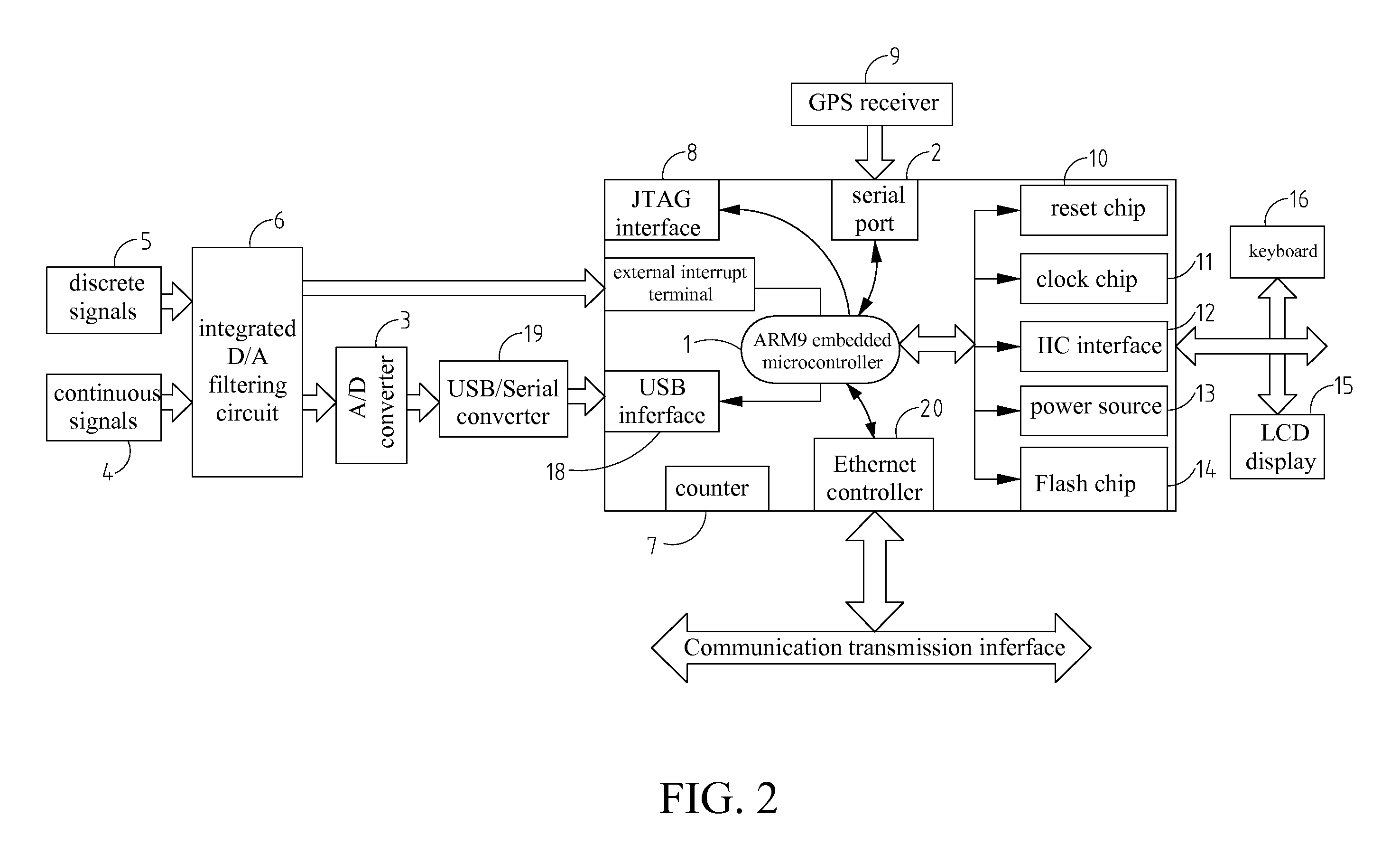
Distributed Networked Data Acquisition Device
InactiveUS20070174451A1Guaranteed synchronizationHigh precision machiningTariff metering apparatusDigital computer detailsGNU/LinuxData acquisition
A distributed networked data acquisition system having distributed networked data acquisition devices based on embedded Linux development platform having an ARM9 CPU is proposed. The system is defined as one or more distributed networked data acquisition devices together with a host. The host could dynamically display data and also coordinate and control the many distributed networked data acquisition devices. Each distributed networked data acquisition device is connected with the host by means of transmission media. The distributed networked data acquisition devices adopts the distributed data acquisition network to implement multi-point data acquisition having many distributed networked data acquisition devices working together and using several UTPs to connect with the distributed networked data acquisition devices in various distribution points. Each distributed networked data acquisition device can connect with different types of sensors, and each sensor can collect different types of continuous signals.
Owner:NORTHEASTERN UNIV
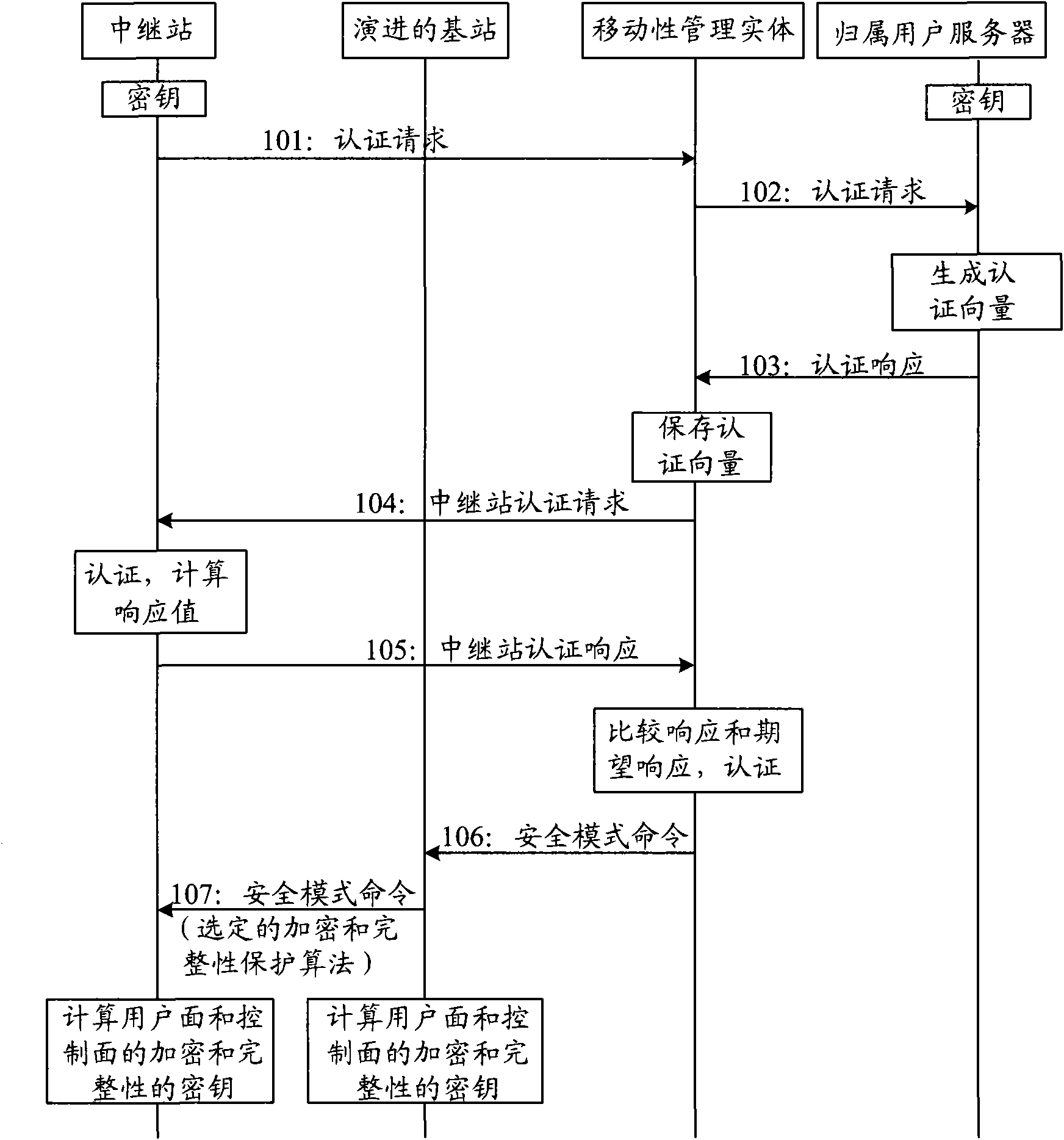
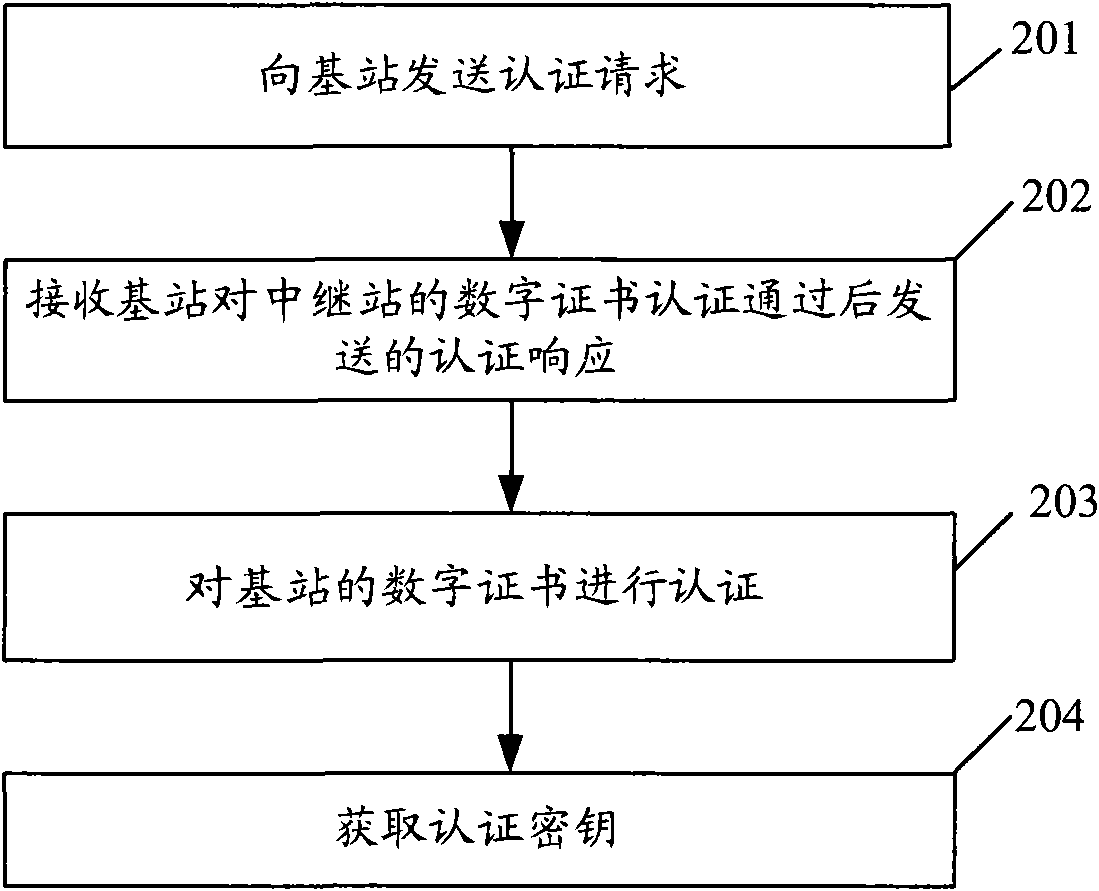
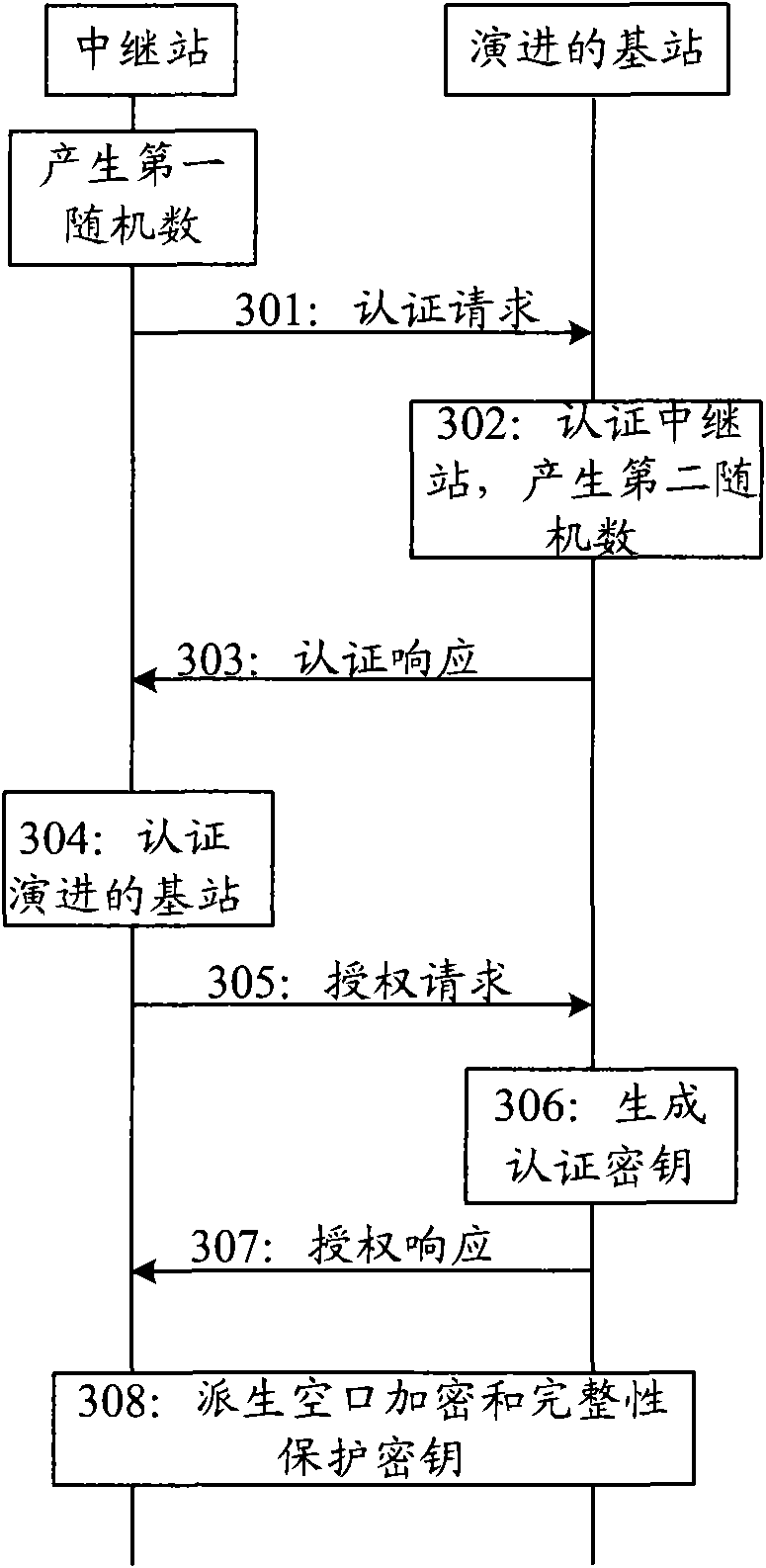
Authentication method, re-authentication method and communication device
InactiveCN101640886AGuaranteed synchronizationNetwork topologiesTransmissionSubscriber identity moduleCommunication device
The embodiment of the invention discloses an authentication method, a re-authentication method and a communication device. The authentication method comprises the following steps that: a relay stationsends an authentication request to a base station, wherein the authentication request contains a digital certificate of the relay station; a receiving base station sends an authentication response, wherein the authentication response contains the digital certificate of the base station and is sent after the digital certificate of the relay station passes through the authentication of the base station; and the digital certificate of the base station is authenticated and an authentication key is obtained. The authentication method sends the authentication request containing the digital certificate of the relay station through the relay station, receives the authentication response containing the digital certificate of the base station and authenticates by means of bidirectional authentication, thereby allowing the base station to complete a network complete access of the relay station without allocating a subscriber identity module card for the relay station. The re-authentication method provided by the embodiment of the invention can guarantee the effectiveness of the authentication key.
Owner:SHANGHAI HUAWEI TECH CO LTD
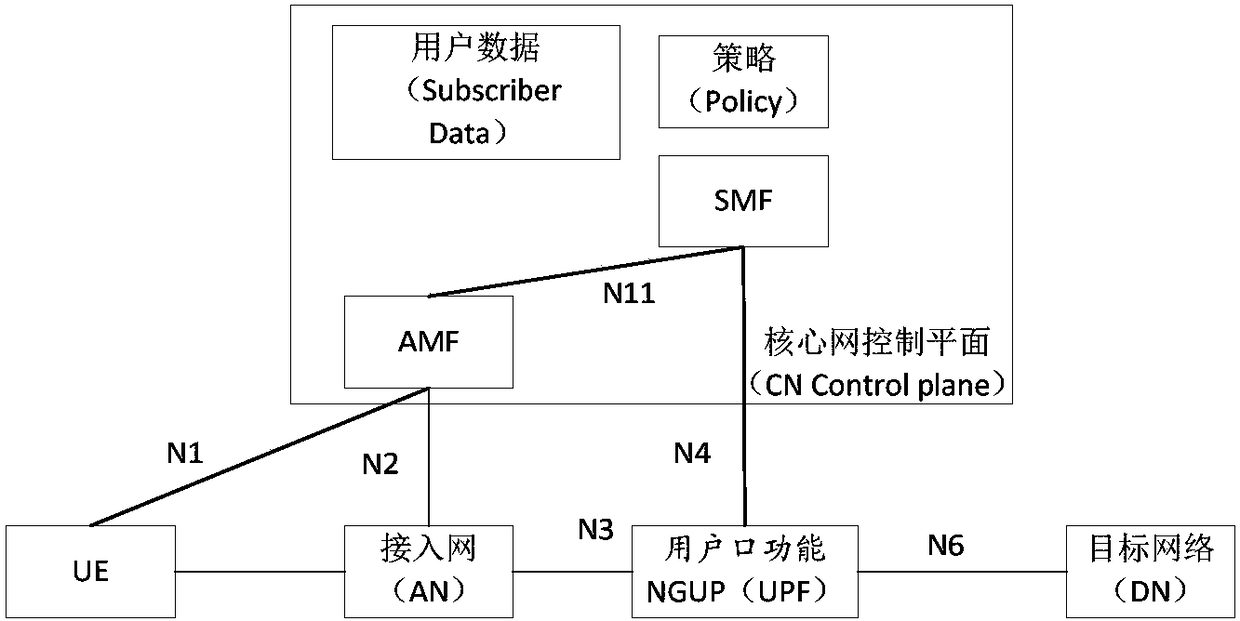
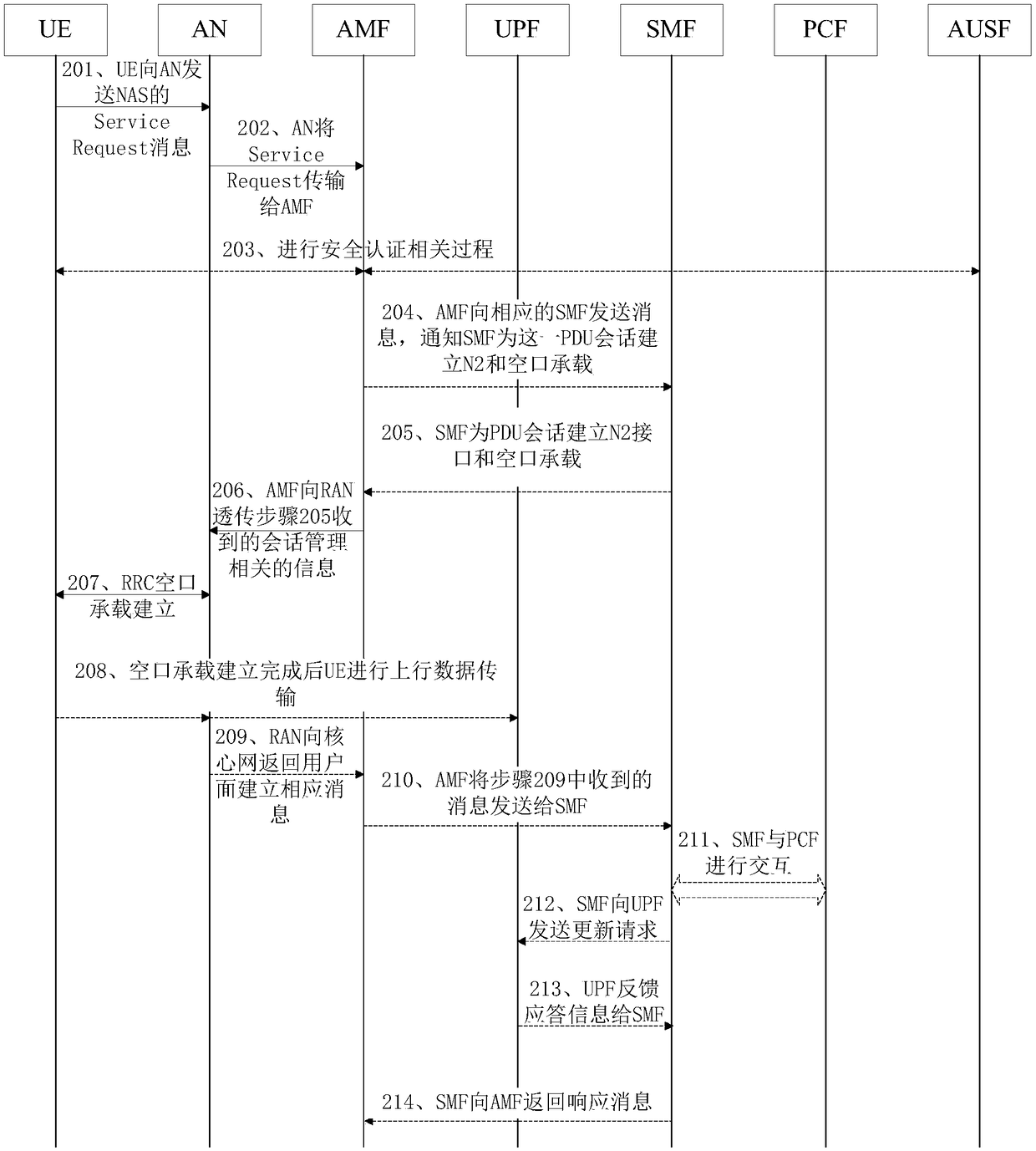
Session management method, terminal, management functional entity and access network node
The invention provides a session management method, a terminal, a management functional entity and an access network node, and relates to the technical field of communication. The session management method comprises the following steps: in a service request process, receiving a session establishment failure message fed back when a protocol data unit (PDU) session requested by the terminal is not established successfully on a network side, wherein the session establishment failure message includes session identification information; and performing deactivation of a session corresponding to thesession identification information. Through the scheme, the session establishment failure message is fed back to the terminal timely when the PDU session requested by the terminal is not established successfully on the network side, thereby solving the problem concerned with how to notify the terminal when a network refuses connection establishment of certain PDU sessions in a 5G service request process, ensuring synchronization of PDU sessions between the terminal and a core network side, and ensuring the reliability of network communication.
Owner:CHINA ACAD OF TELECOMM TECH
Security key context distribution method, mobility management entity and base station
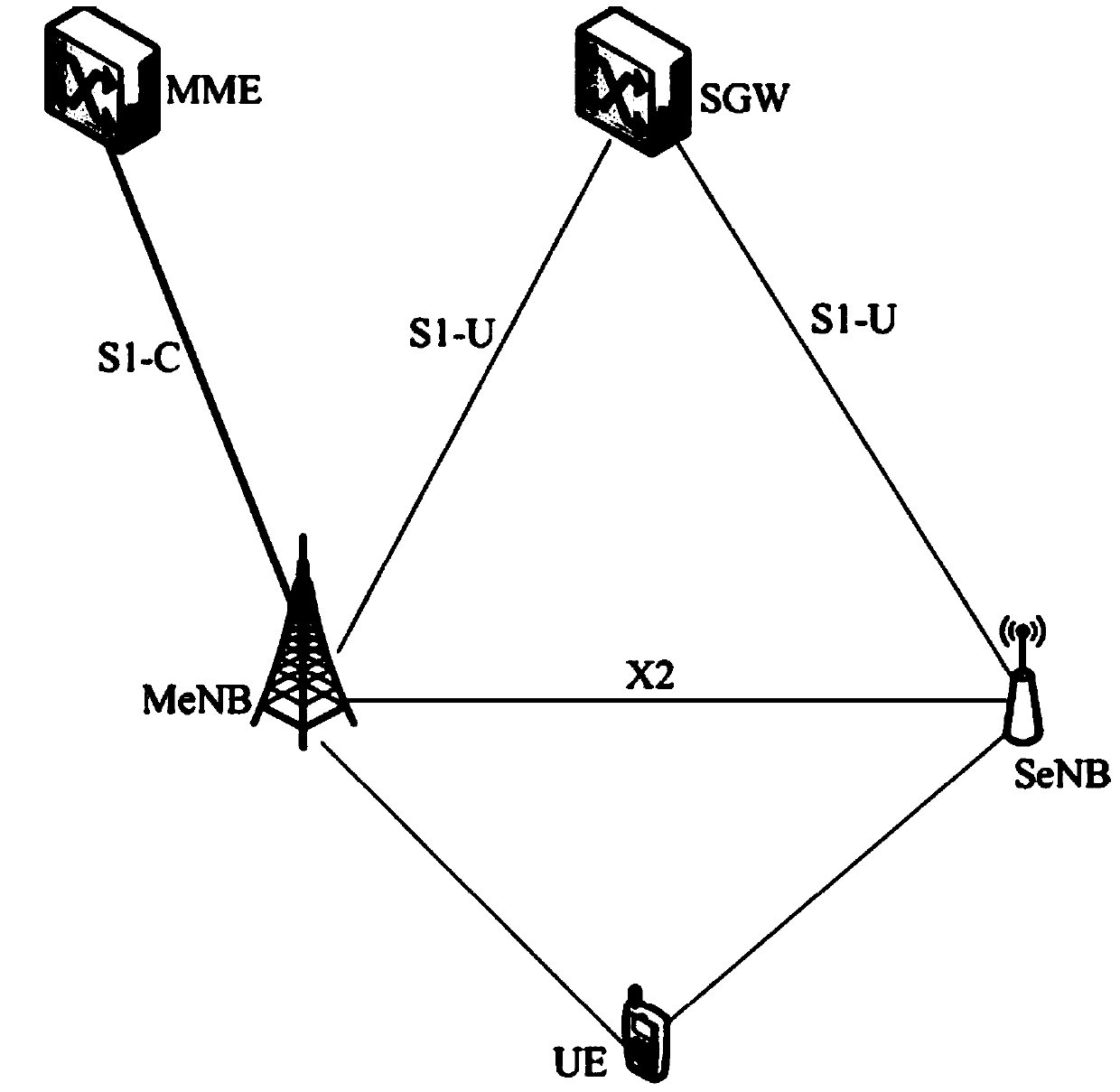
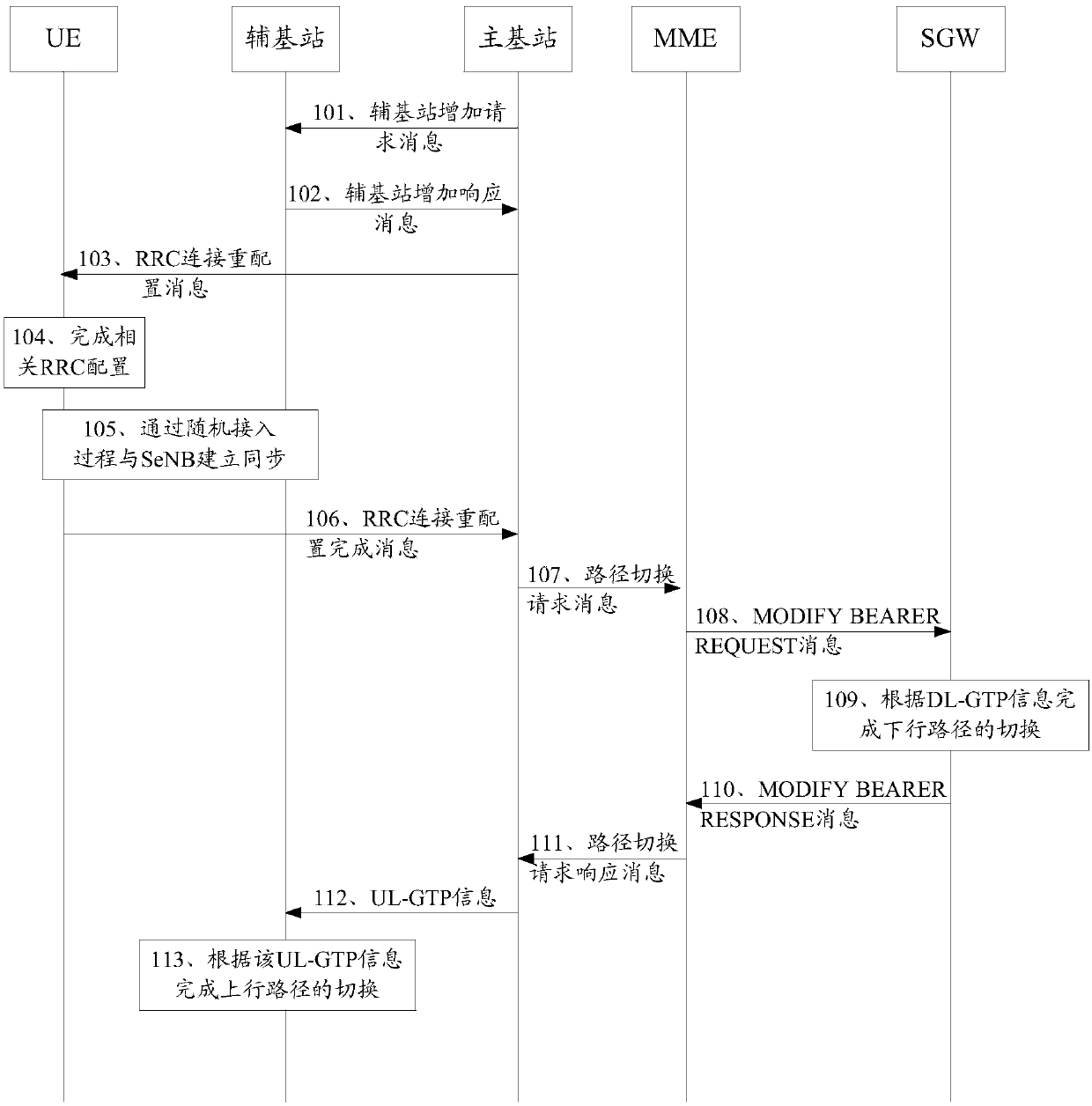
ActiveCN103747442AImprove reliabilityGuaranteed synchronizationNetwork topologiesConnection managementDistribution methodCarrier signal
The invention discloses a security key contextual distribution method, mobility management entity and base station, wherein, the security key contextual distribution method comprises: firstly, the mobility management entity receives a first instruction from a main base station, wherein the first instruction is used for the mobile management entity to request a path switching and indicate the path switching triggered by a inter-base station carrier aggregation; the path switching is processed according to the first instruction; the security keys context distribution method for the path switching is remained unchanged according to the first instruction, secondly, a second instruction is sent to the main base station, the security keys context distribution method is remained unchanged by indicating the main base station; or, the third instruction is sent to the main base station, a turning times of a counter of a next-hop chain of the security keys context distribution method is obtained by indicating the main base station. To be sure, the technical solution provided by the present invention can effectively improve the reliability of the path switching when the inter-base station carrier is aggregating.
Owner:HUAWEI TECH CO LTD
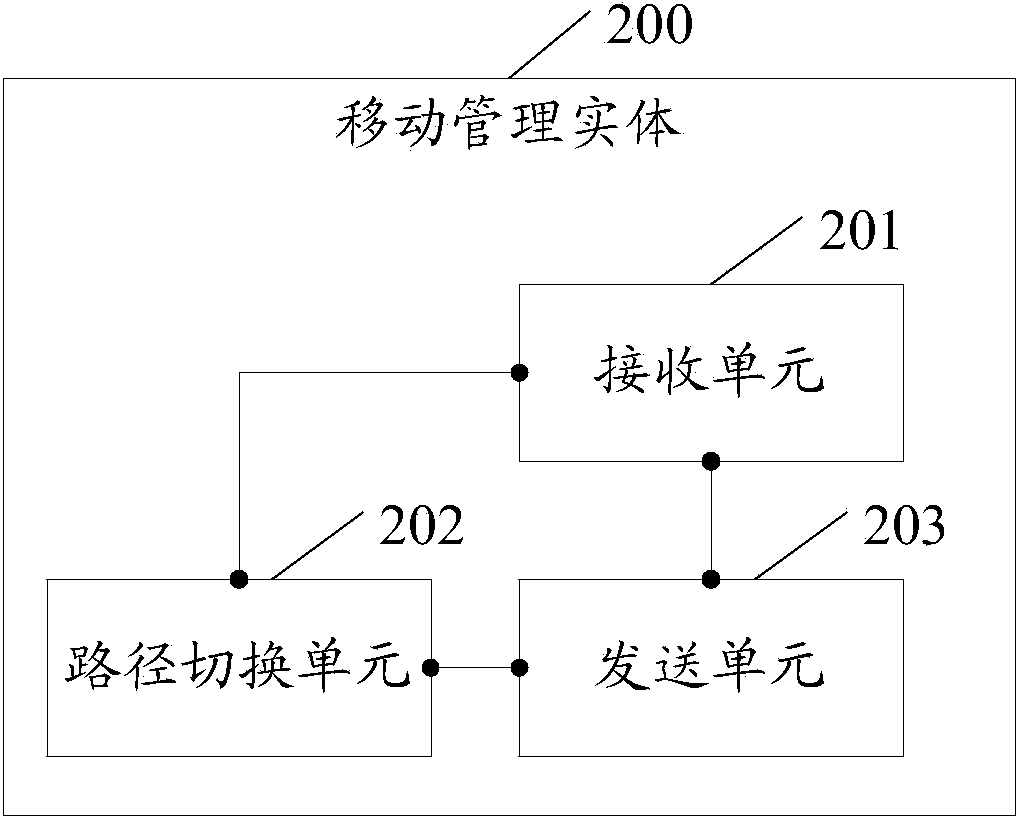
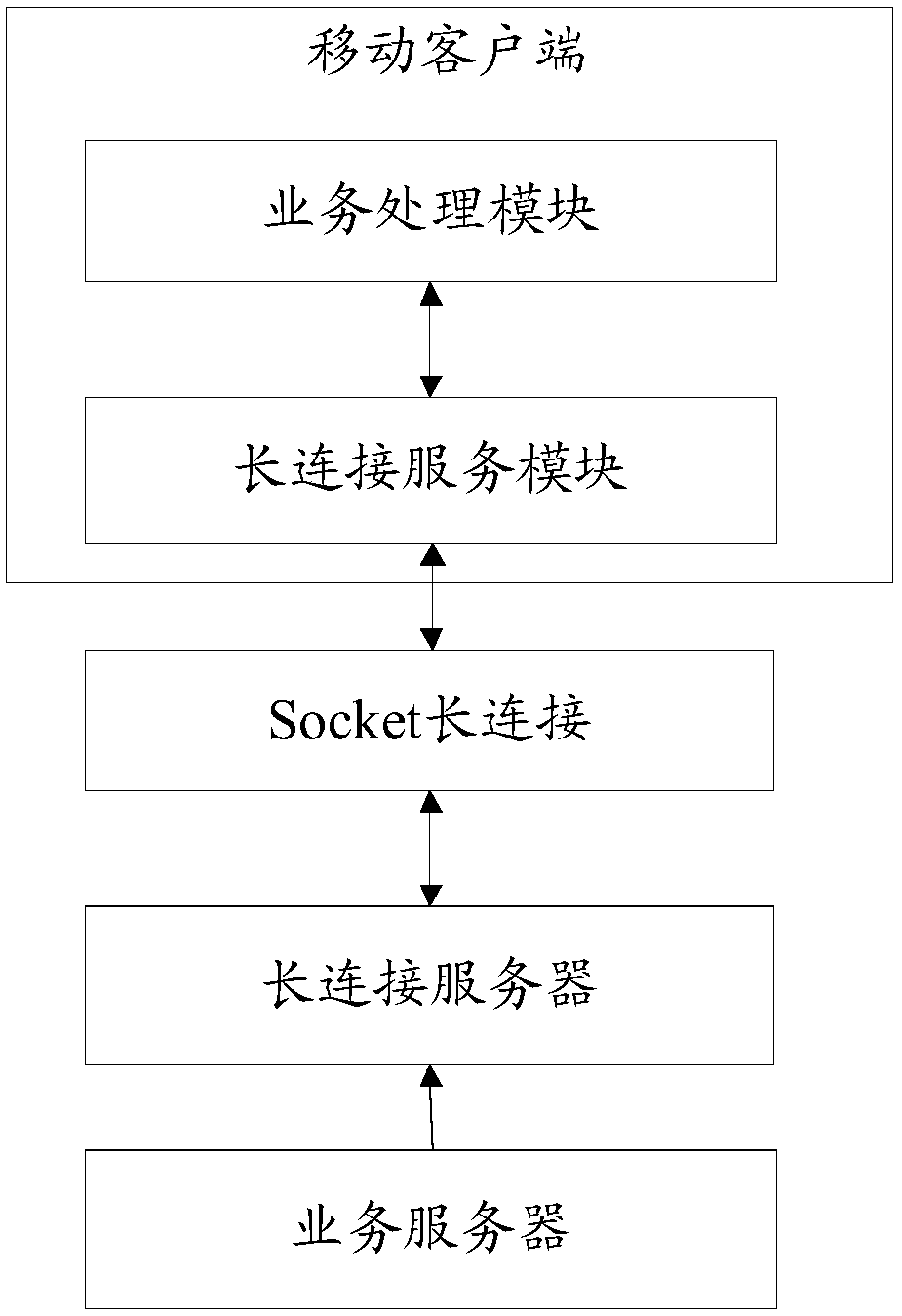
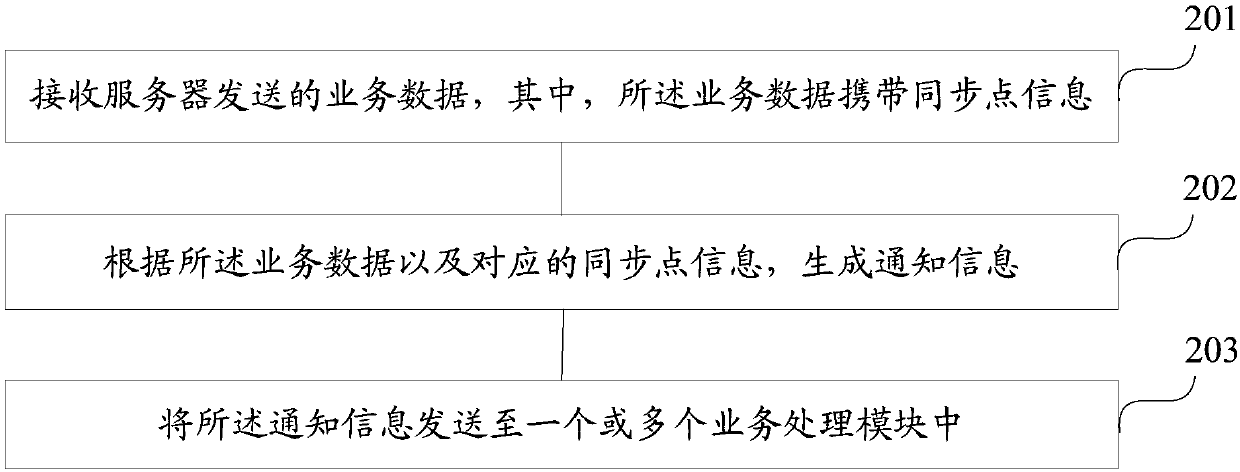
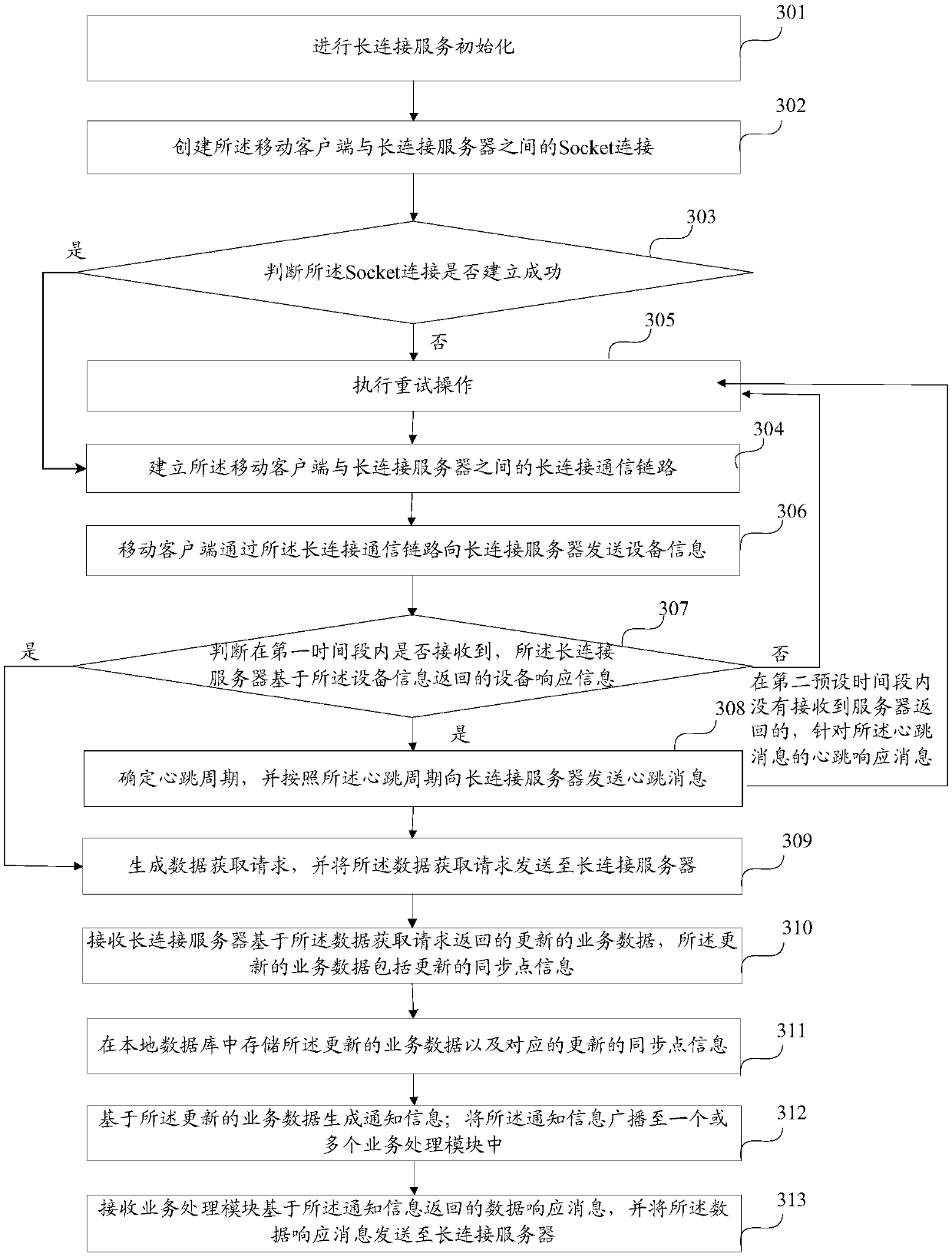
Method for establishing long connection between client and server, communication method and communication system
InactiveCN109660584AImprove usabilityGuaranteed synchronizationTransmissionCommunications systemCommunication link
Embodiments of the invention provide a method for establishing long connection between a client and a server, a communication method and a communication system. When the method is applied to the mobile client, the mobile client comprises a long connection service module and one or more service processing modules; and the long connection service module communicates with the long connection server through a long connection communication link. The method comprises the following steps: the long connection service module receives service data sent by the long connection server through the long connection communication link, wherein the service data carries synchronization point information; notification information is generated according to the service data and the corresponding synchronizationpoint information; and the notification information is sent to the one or more service processing modules. Based on the robust long connection communication link, the mobile client can receive the service data pushed by the server at any time, so that the availability of a long connection service is improved.
Owner:ALIBABA GRP HLDG LTD
Method and equipment for transmitting data
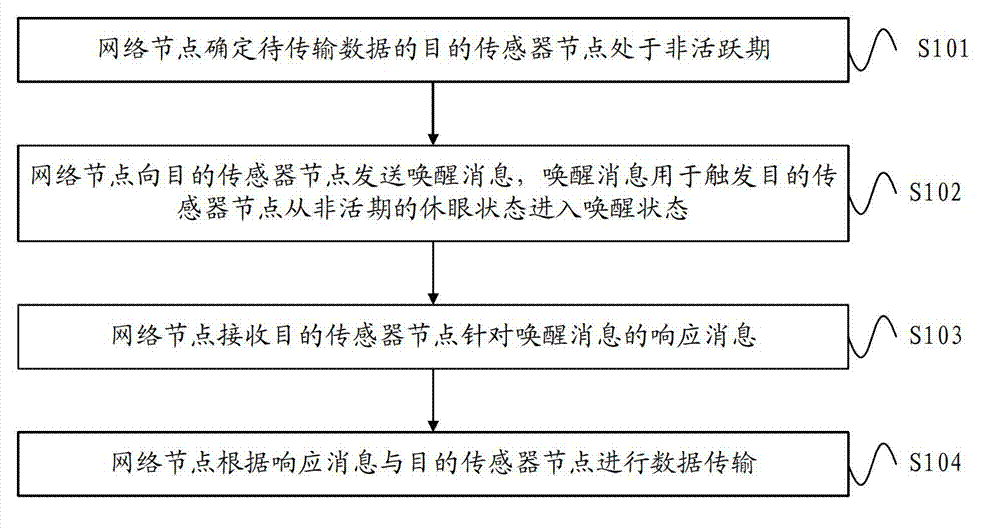
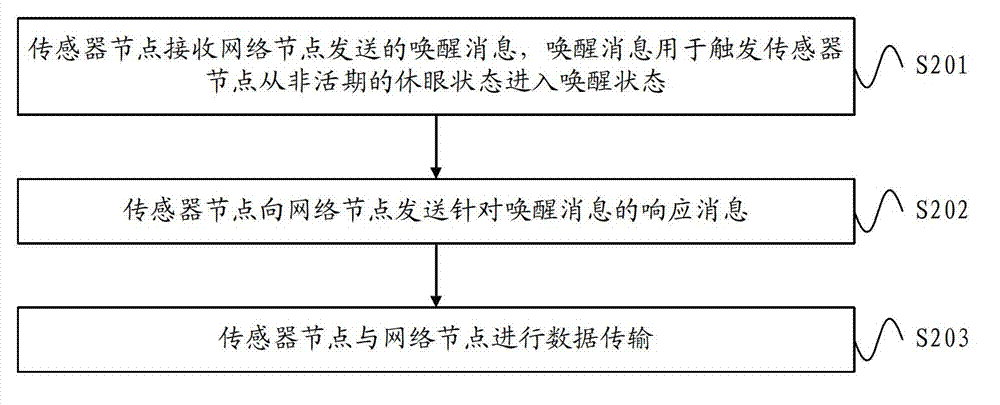
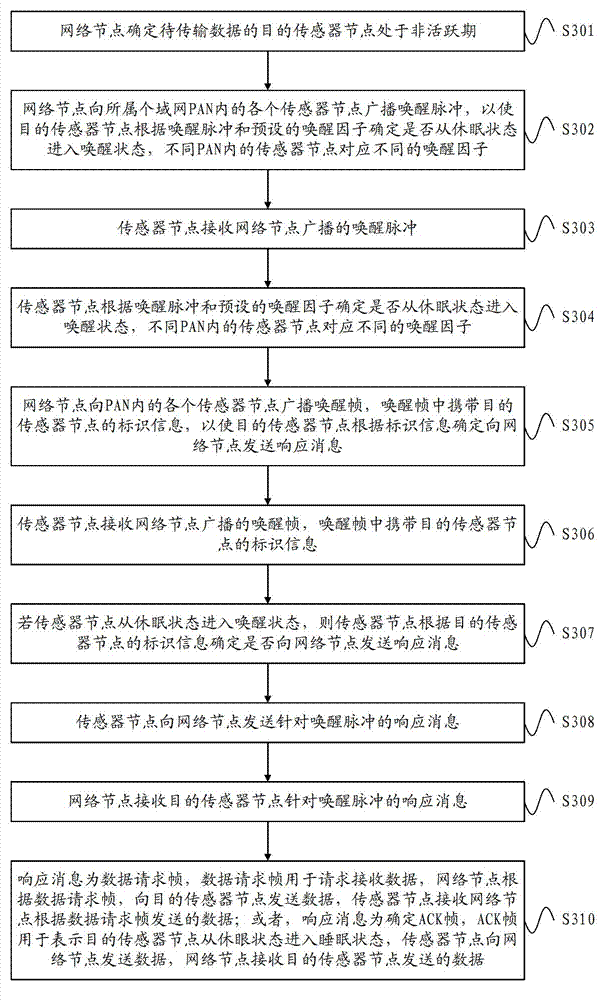
ActiveCN102892193AReduce latencyGuaranteed synchronizationPower managementSynchronisation arrangementSensor nodeData transmission
The embodiment of the invention provides a method and equipment for transmitting data. The method for transmitting the data comprises the following steps that: a network node determines that a target sensor node to which the data is transmitted is in an inactive period; the network nodes sends an awakening message to the target sensor node, wherein the awakening message is used for triggering the target sensor node to enter an awakened state from a dormant state in the inactive period; the network node receives a response message, which corresponds to the awakening message, which is sent by the target sensor node; and the network node transmits the data to the target sensor node according to the response message. According to the method and the equipment for transmitting the data, the network node sends the awakening message to the target sensor node which is in the inactive period to ensure that the target sensor node is awakened from the dormant state, and then the network node transmits the data to the target sensor node, so that the network node can transmit the data to the target sensor node without waiting for the next superframe active period when the target sensor node is in the inactive period, time delay of data transmission is shortened, and synchronization of the data transmission is guaranteed.
Owner:HUAWEI TECH CO LTD
Virtual reality display system fusing VR (Virtual Reality) with AR (Augmented Reality) and implementation method thereof
ActiveCN107340870AGuaranteed synchronizationQuality improvementInput/output for user-computer interactionGraph readingControl systemEyewear
The invention discloses a virtual reality display system fusing VR (Virtual Reality) with AR (Augmented Reality) and an implementation method thereof. The virtual reality display system comprises stereoscopic interactive display and sharing equipment and a control system. A user wearing stereoscopic display spectacles interacts with a virtual world in stereoscopic interactive display equipment by an interactive pen, a camera acquires an interactive posture of the user, and the virtual world is overlaid in a real world in an AR mode for display in general display equipment; and the control system comprises a server and a client, and the server is communicated with the client by a communication layer. According to the invention, VR and AR technologies are fused, immersive user experience is brought to a user by using a VR interactive technology, and meanwhile, the virtual world immersed before eyes of the user is shared to spectators in an AR mode so as to provide a high-quality virtual reality platform for exchange and communication of both parties.
Owner:深圳市未来感知科技有限公司
Method and system for network clock synchronous
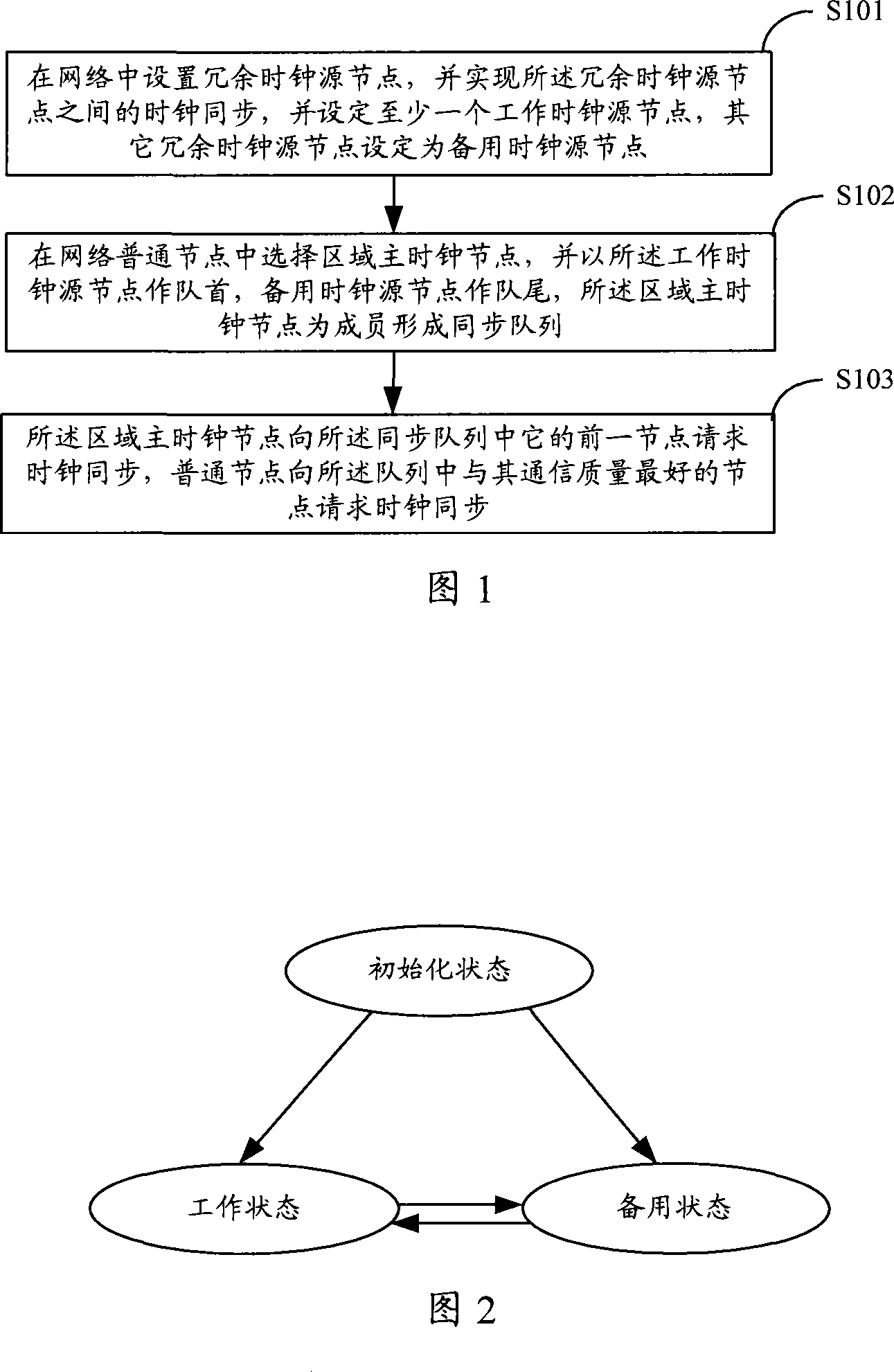
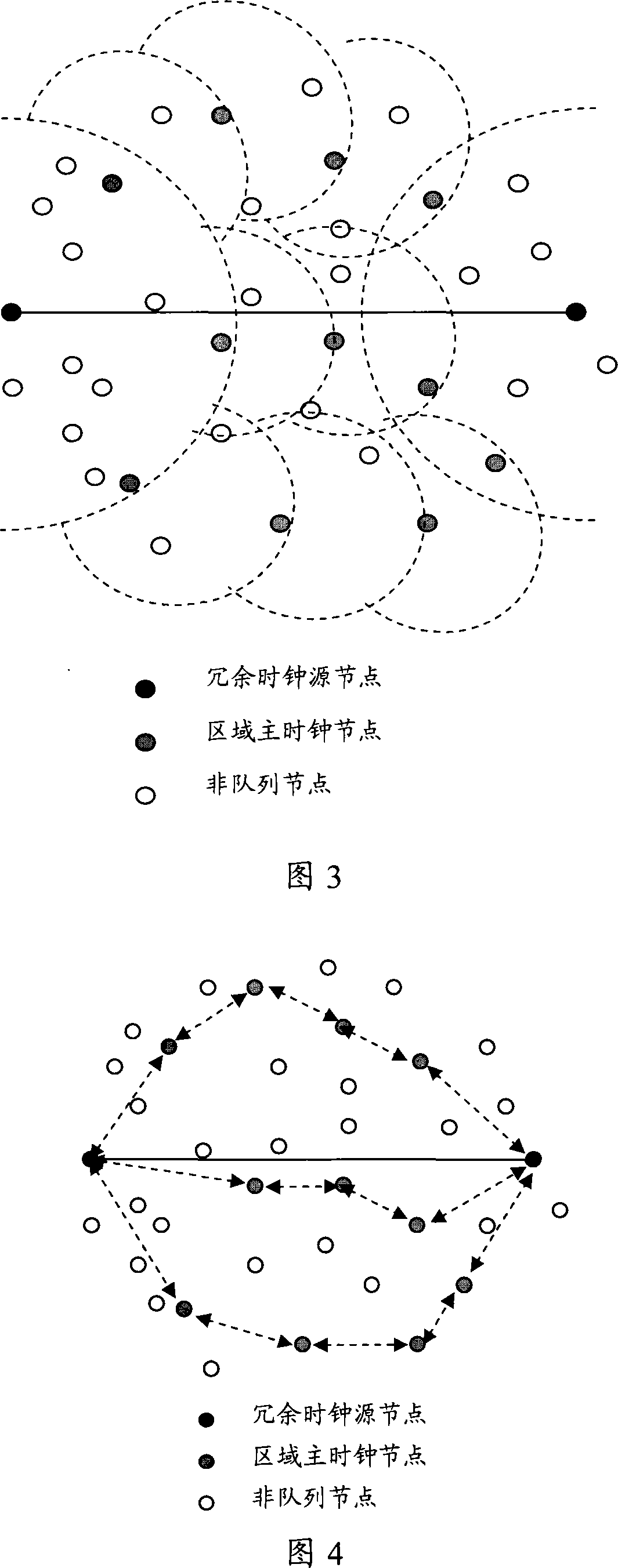
InactiveCN101090341APrevent crashAchieve synchronizationRadio transmission for post communicationData switching networksNetwork clockWireless sensor networking
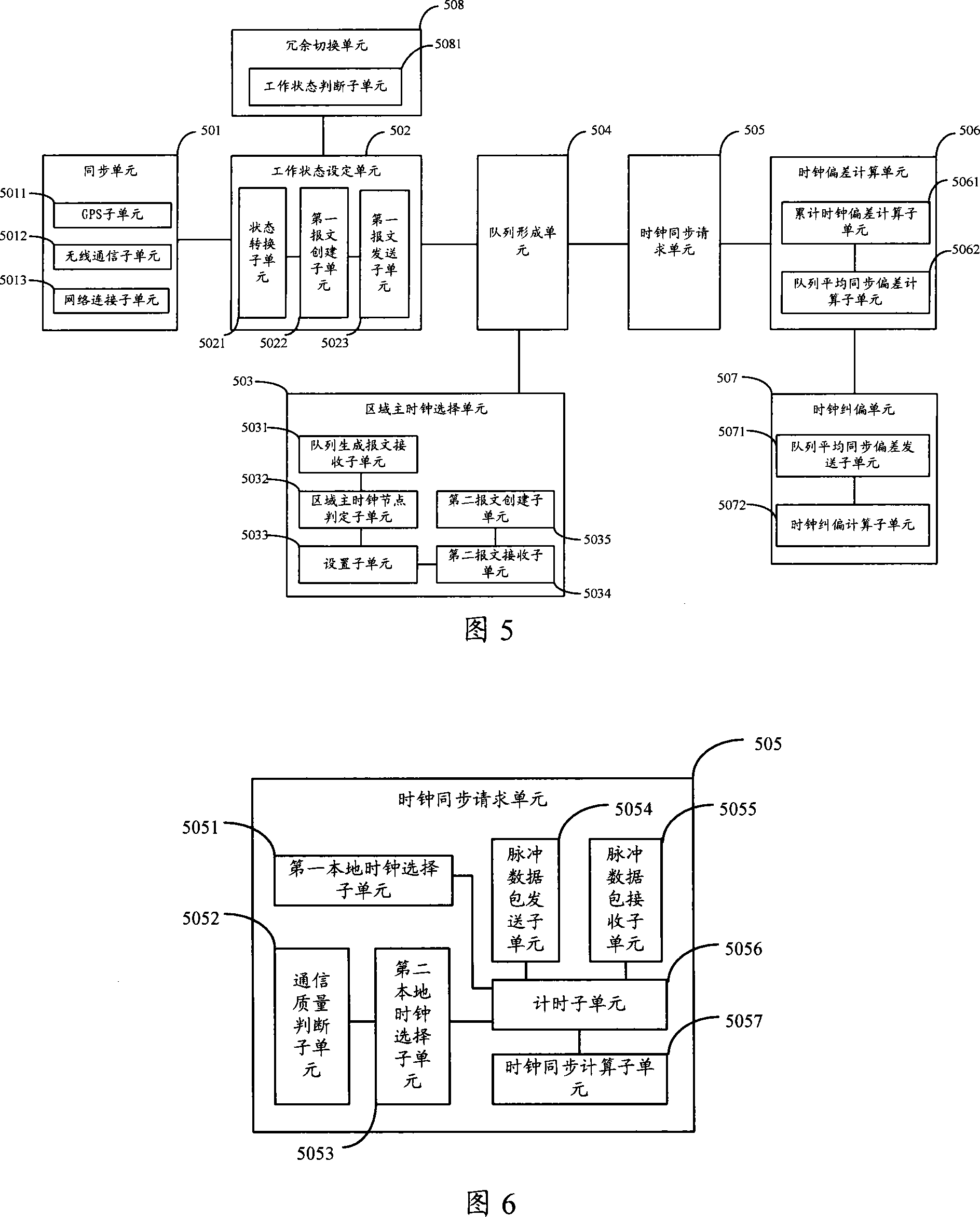
This invention discloses a method and a system for synchronizing network clocks, which sets synchronous source nodes with mutual redundance in a wireless sensor network to design them a working clock node and a backup clock source node and selects a regional master clock node in network node to form a synchronous queue, the network node asks for clock synchronization to the nodes in the synchronous queue, the backup clock source node computes the mean queue synchronous clock based on the difference between the local clock and the synchronous clock of the working clock node and sends it to the regional master clock node in the queue so as to realize clock rectification to the regional master clock.
Owner:SUPCON GRP +1
Method, apparatus implementing base station synchronization and base station
ActiveCN101384019AAchieve synchronizationLow costRadio/inductive link selection arrangementsRadio transmissionGps receiverBroadcasting
The invention discloses a method for realizing base station synchronization, which includes the following steps: a second base station defines a first base station according to indication information sent by other base stations; the second base station searches the position of a descending pilot frequency time slot (DwPTS) of the first base station and adjusts the position of the DwPTS according to the position of the searched DwPTS; the second base station reads a system frame number (SFN) from the broadcasting information of the first base station and updates the SFN to be the read SFN. In the invention, the second base station realizes synchronization among different base stations through building the time slot synchronization and frame synchronization with the first base station. Not every base station is needed to be provided with a GPS receiver, therefore, the system cost is greatly reduced. In addition, the realization of the invention can completely break away GPS, therefore, the synchronization among all the base stations can be still ensured when the GPS fails. The invention also discloses a device for realizing the synchronization of the base station and a relevant base station.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method and apparatus for synchronizing card without traffic in multi-card multi-standby mobile terminal
ActiveUS20120140709A1Shorten the timeAvoids drop from networkSynchronisation arrangementTime-division multiplexTraffic capacityFailure causes
A method and an apparatus for synchronizing card without traffic in multi-card multi-standby mobile terminal are disclosed. The method includes: receiving, by a non-traffic card, a synchronization channel signal from an adjacent network cell according to frequency point of a synchronization channel of the adjacent network cell prestored in the non-traffic card, when a traffic card is in traffic; if the receiving of the synchronization channel signal from the adjacent network cell fails, performing, by the non-traffic card, a full-frequency network searching after the traffic of the traffic card, for receiving a synchronization channel signal from a network cell of the network cells and establishing synchronization with the network cell corresponding to the synchronization channel signal. The method and apparatus avoid communication failures caused by the out-of-synchronization of non-traffic card during the traffic (i.e. service) of the traffic card.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Data synchronization method and data synchronization device
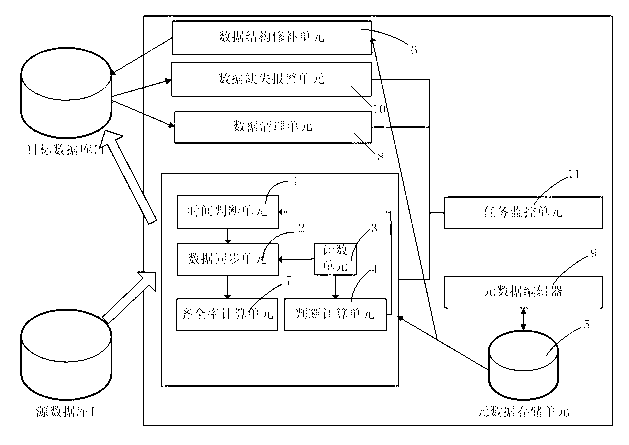
ActiveCN103186624AGuaranteed synchronizationIntegrity guaranteedTransmissionSpecial data processing applicationsData synchronizationFile synchronization
The invention provides a data synchronization method which is used for migrating data in a source database to a target database. The data synchronization method is characterized in that the data synchronization method comprises the following steps: judging whether current time is equal to or later than a data time point and delay time or not, if so, entering a data synchronization step, and otherwise, rejudging after waisting for certain time; synchronizing the data, i.e., migrating the data of the source database to the corresponding position of the target database; meanwhile, recording the number of migrated data strips; judging whether the strip number of data synchronization is greater than the product of the current experience strip number and a preset threshold as a coefficient, if so, ending migration, and otherwise, waiting a preset waiting time duration and then returning to the step of data synchronization; meanwhile, recording the accumulated waiting duration; recalculating to determine the experience strip number and delay time according to the number of the migrated data strips in the data synchronization record; and returning to a start step.
Owner:BOCO INTER TELECOM
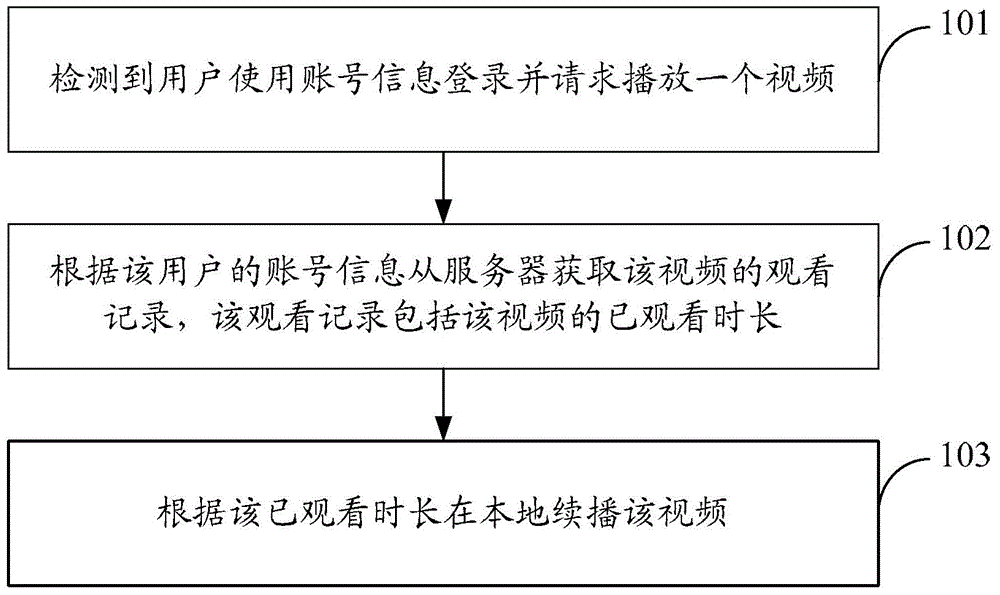
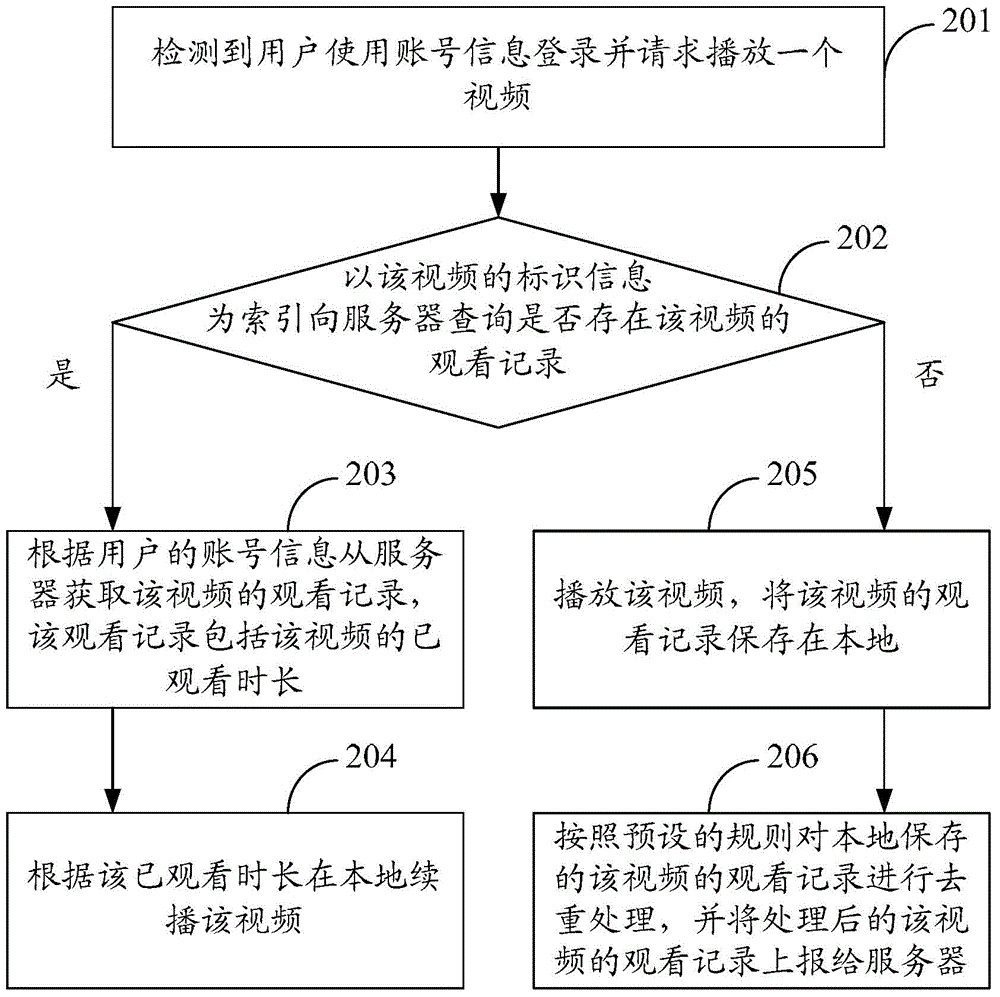
Video playing method, device and system
The invention discloses a video playing method, device and system, and belongs to the field of communication. The method is applied to a second client, and comprises the following steps: detecting that a user logs in with account information and requests to play a video; obtaining a watching record of the video from a server according to the account information of the user, wherein the watching record includes a watching time length of the video; and locally and continuously playing the video according to the watching time length, wherein the watching record of the video is reported to the server when the user plays the video with the account information at a first client last time. The device comprises a detecting module, an obtaining module and a responding module. The system comprises the first client and the second client. By virtue of the video playing method, device and system, the continuous playing of the same video can be realized when the user logs in through the different clients, so that the synchronization of the video on a plurality of devices is guaranteed, more use convenience is brought for the user, and the user experience is promoted.
Owner:TENCENT TECH (BEIJING) CO LTD
Method and device for time synchronization and maintaining based on frequency deviation estimation
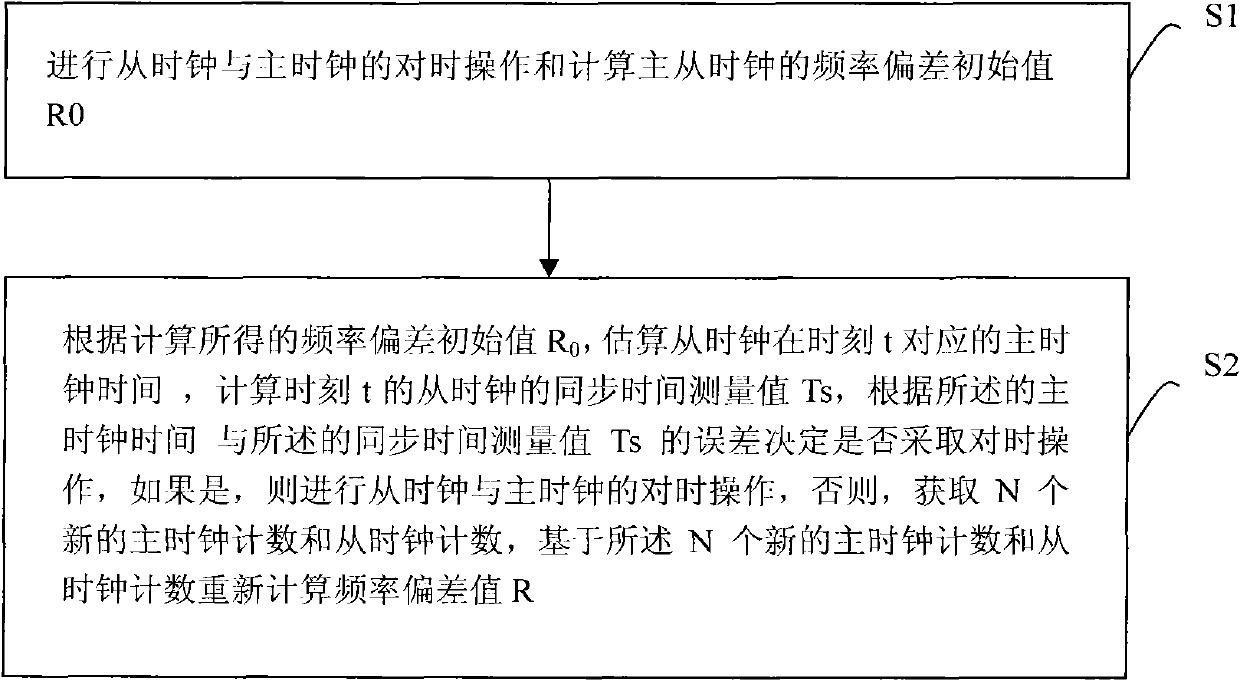
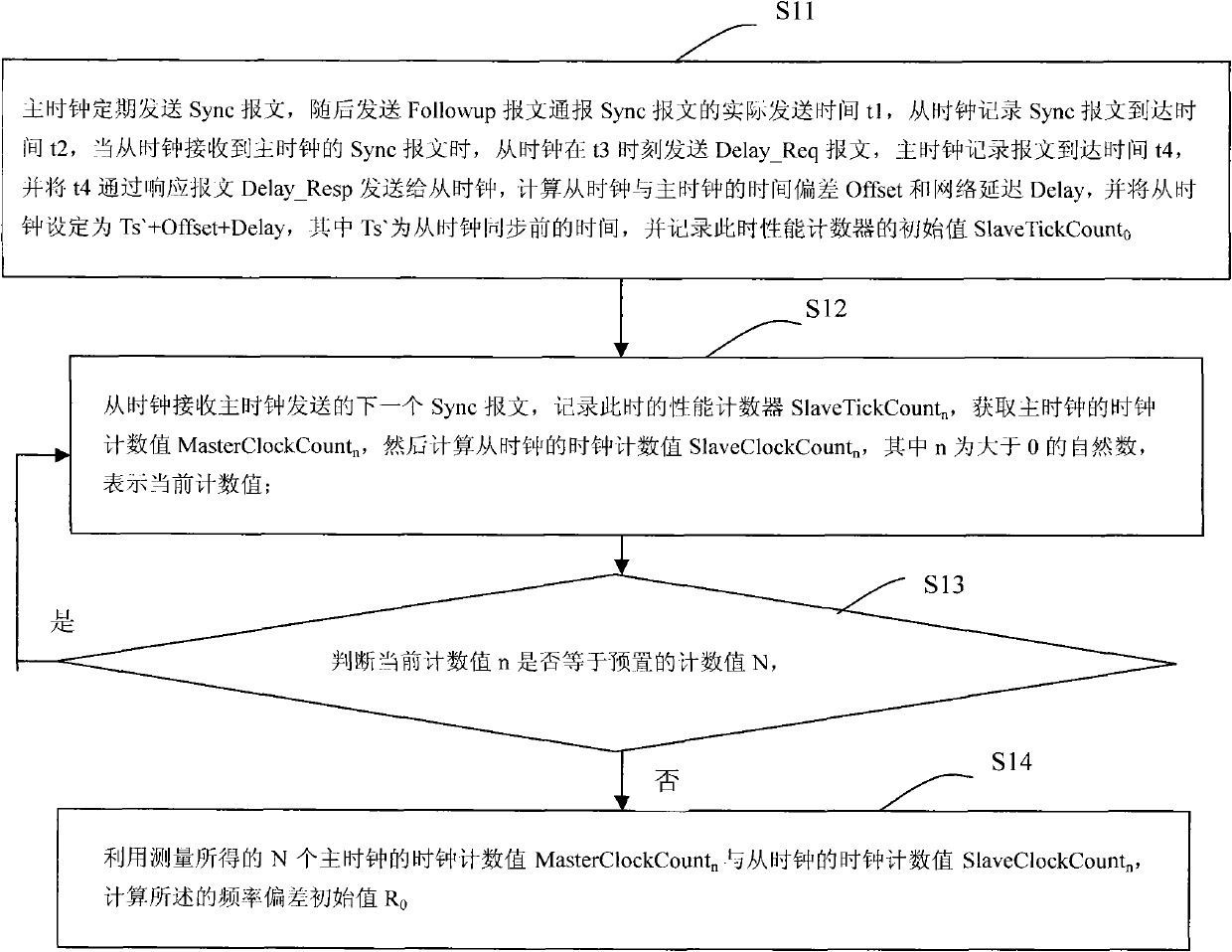
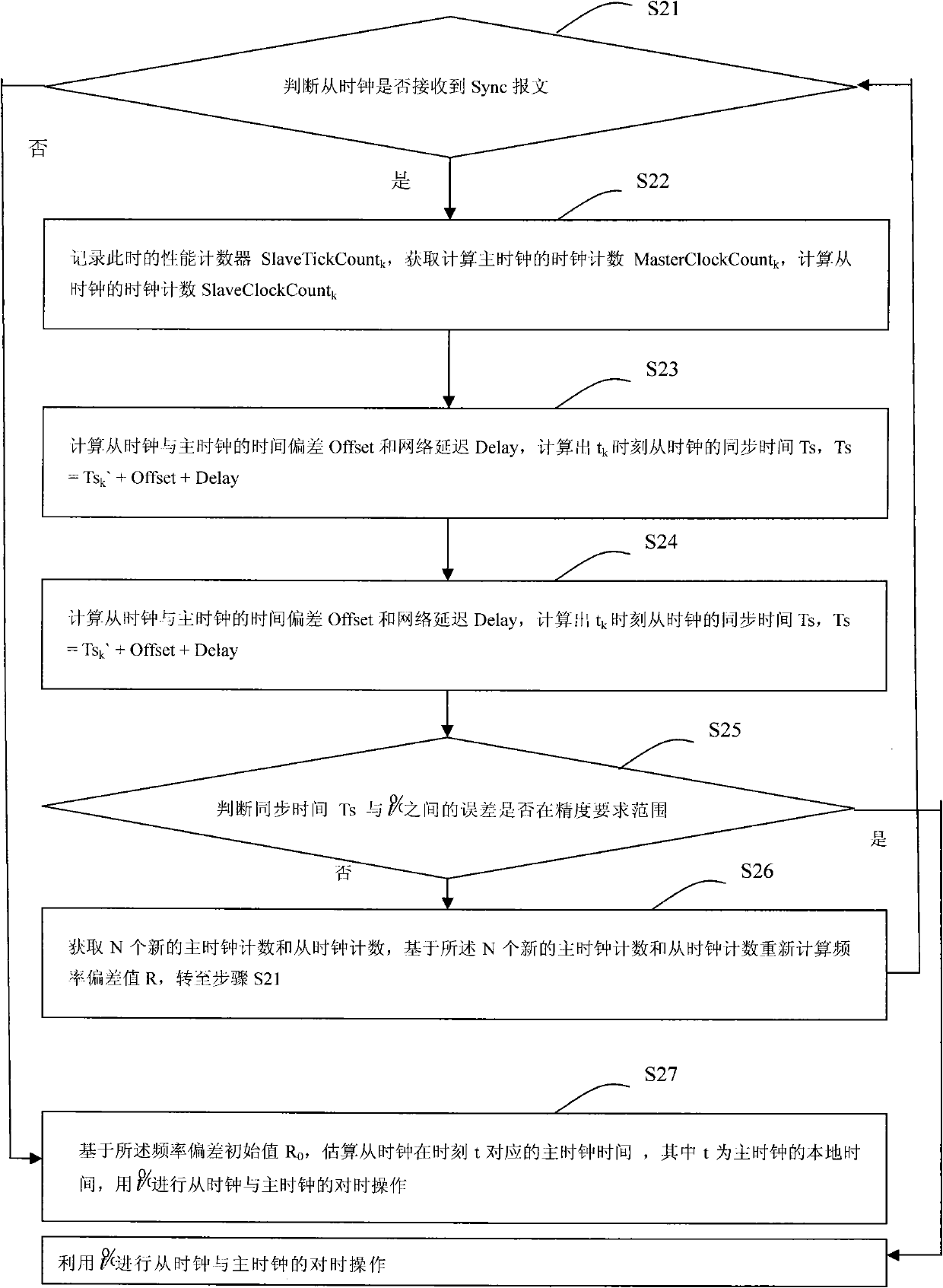
InactiveCN102480350AGuaranteed synchronizationHigh precisionSynchronising arrangementSlave clockFrequency deviation
The invention provides a method and a device for time synchronization and maintaining based on frequency deviation estimation. The method includes firstly, synchronizing time of a slave clock and a master clock and calculating a frequency deviation initial value R0 of the master clock and the slave clock; and secondly, estimating the corresponding time of the slave clock to the master clock at the moment t according to the calculated frequency deviation initial value R0, calculating the synchronization time measured value Ts of the slave clock at the moment t, determining whether synchronizing time or not according to the error of the master clock time and the synchronization time measured value Ts, if yes, synchronizing time of the slave clock and the master clock, and if not, acquiring N new master clock counts and slave clock counts to recalculating a frequency deviation value R based on the N new master clock counts and slave clock counts. By means of the method and the device for time synchronization and maintaining based on frequency deviation estimation, a distributive system can be more accurate in clock synchronization and more convenient in operation.
Owner:BEIJING INTERVISION SOFTWARE
Method for data migration of non-relational database HBase
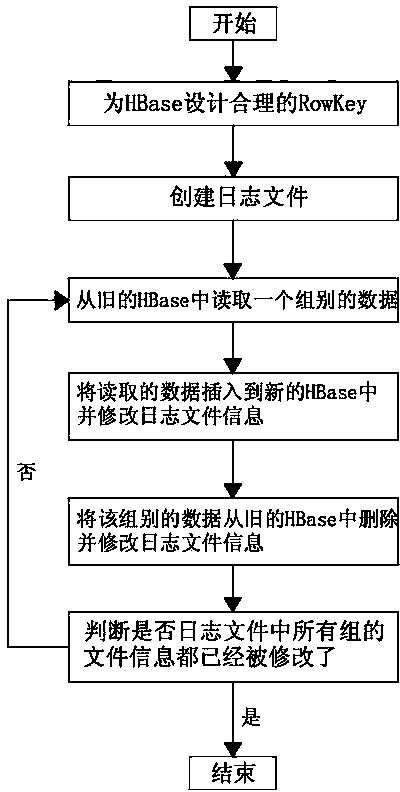
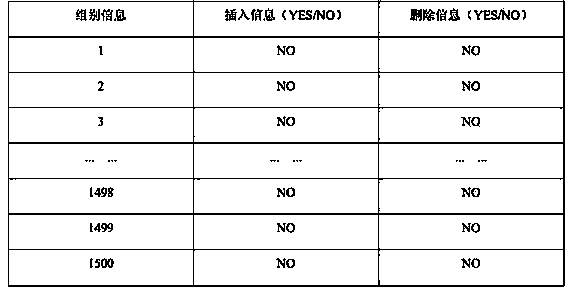
InactiveCN103514274AAccelerateEnsure data consistencySpecial data processing applicationsCheck pointData migration
The invention discloses a method for data migration of a non-relational database HBase. According to the method, by reading configuration file information of users, data within a time period designated by the users are migrated from an old HBase cluster to a new HBase cluster. The method has the advantages that by designing RowKey, group information and time information of the data are embodied on the RowKey, and whether the data corresponding to the RowKey are within a migration time range designated by the users can be directly identified by scanning the RowKey during data migration; groups serve as data migration units, every group serves as a check point, the range of the non-synchronous data between the old HBase cluster and the new HBase cluster can be rigidly controlled within one group when abnormal conditions occur, and time required for restoring data synchronization is reduced; log information is recorded in the data migration process to be used for treating the abnormal conditions in the data migration process, synchronization of the data between the old cluster and the new cluster is guaranteed, and data migration between the HBase clusters can be finished accurately and efficiently.
Owner:NINGBO DONGGUAN TECH
Frame structure, frame processing method and equipment and system for multi-hop access network
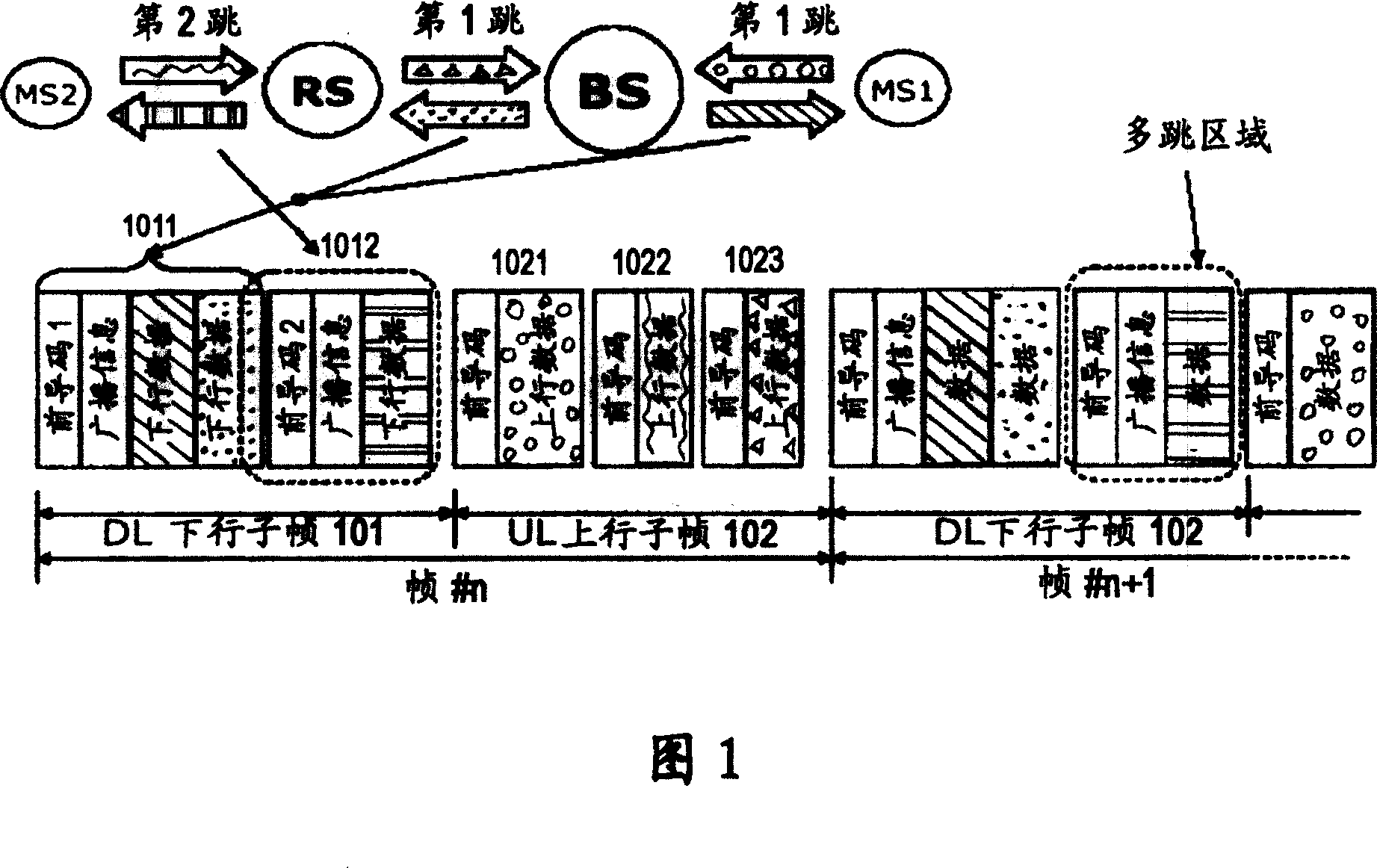
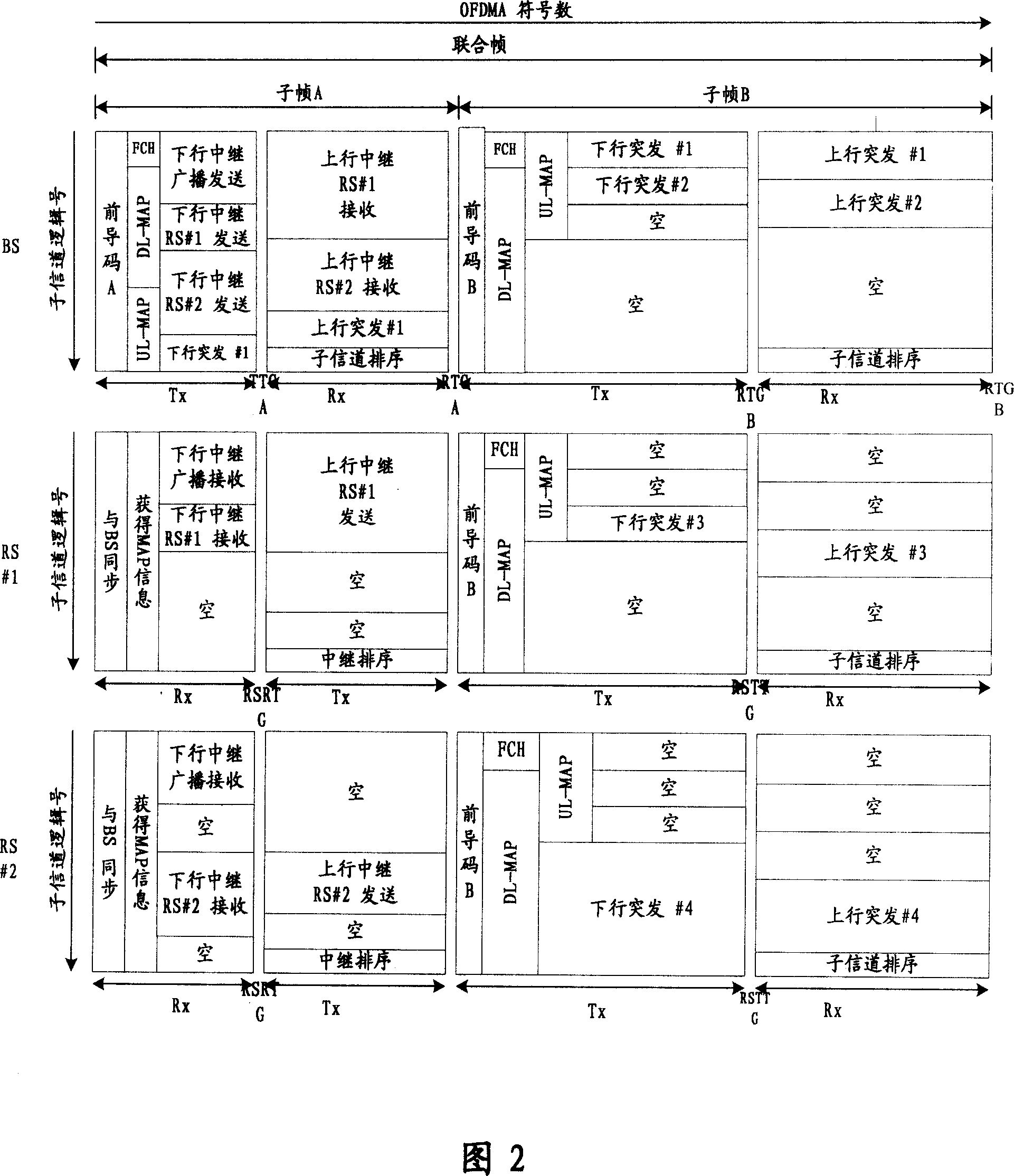
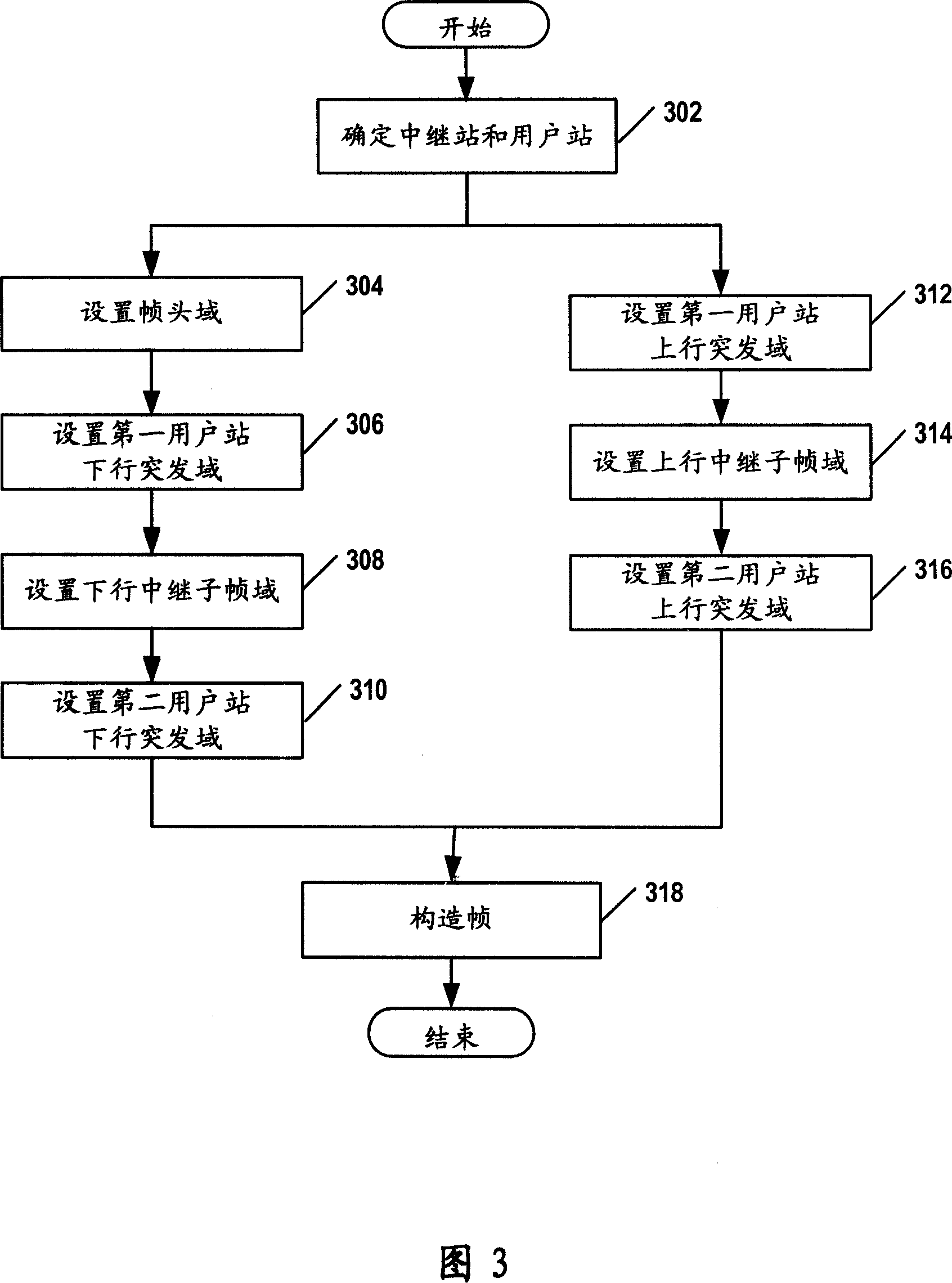
ActiveCN101064555AEasy to switchGuaranteed synchronizationSynchronisation arrangementNetwork topologiesAccess networkStation
The invention discloses a frame building method for multi-jumping switch network that includes following steps: determining the relay station and the user's station in the field of base station; setting the descending sub-frame; setting the ascending sub-frame; and building the completed frame according to the ascending sub-frame and the descending sub-frame, in the step of setting the descending sub-frame that includes the steps of setting the descending relay sub-frame of descending relay information; and in the step of setting the ascending sub-frame that includes the steps of setting the ascending relay sub-frame of ascending relay information. The invention also discloses the frame processing method and equipment to realize the method, base station, relay station and system. According to the invention, it can make sure the synchronization of all network, and reducing the switching operation. It can support the base station and the relay station with different frequency. Additionally, it reduces the delay of business transmission.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
Bridge influence line identification method and system
ActiveCN107588915AHigh precisionSuppresses unphysical fluctuationsSustainable transportationElasticity measurementMobile vehicleInfluence line
The invention discloses a bridge influence line identification method and system. The method comprises the following steps: (1) a mathematic model for influence line identification is built; (2) influence line identification is performed based on a B spline curve. According to the method, actual measurement information of moving vehicles and bridge response caused by the moving vehicles is used, regularization theories and a B spline curve construction method are adopted, a problem that influence line identification is excessively sensitive to errors such as measurement noise and the like canbe effectively alleviated; the method is high in identification precision and great in potential for subsequent projection application; compared with a conventional method, the method can be used forinfluence line identification directly based on actually measured dynamic bridge response data, the method is simple and fast in operation, the method can be used for real time monitoring of key indexes of a bridge and can help effectively suppress influence line fluctuation which is not in line with physical meaning, and influence line identification precision can be improved.
Owner:XIAMEN UNIV
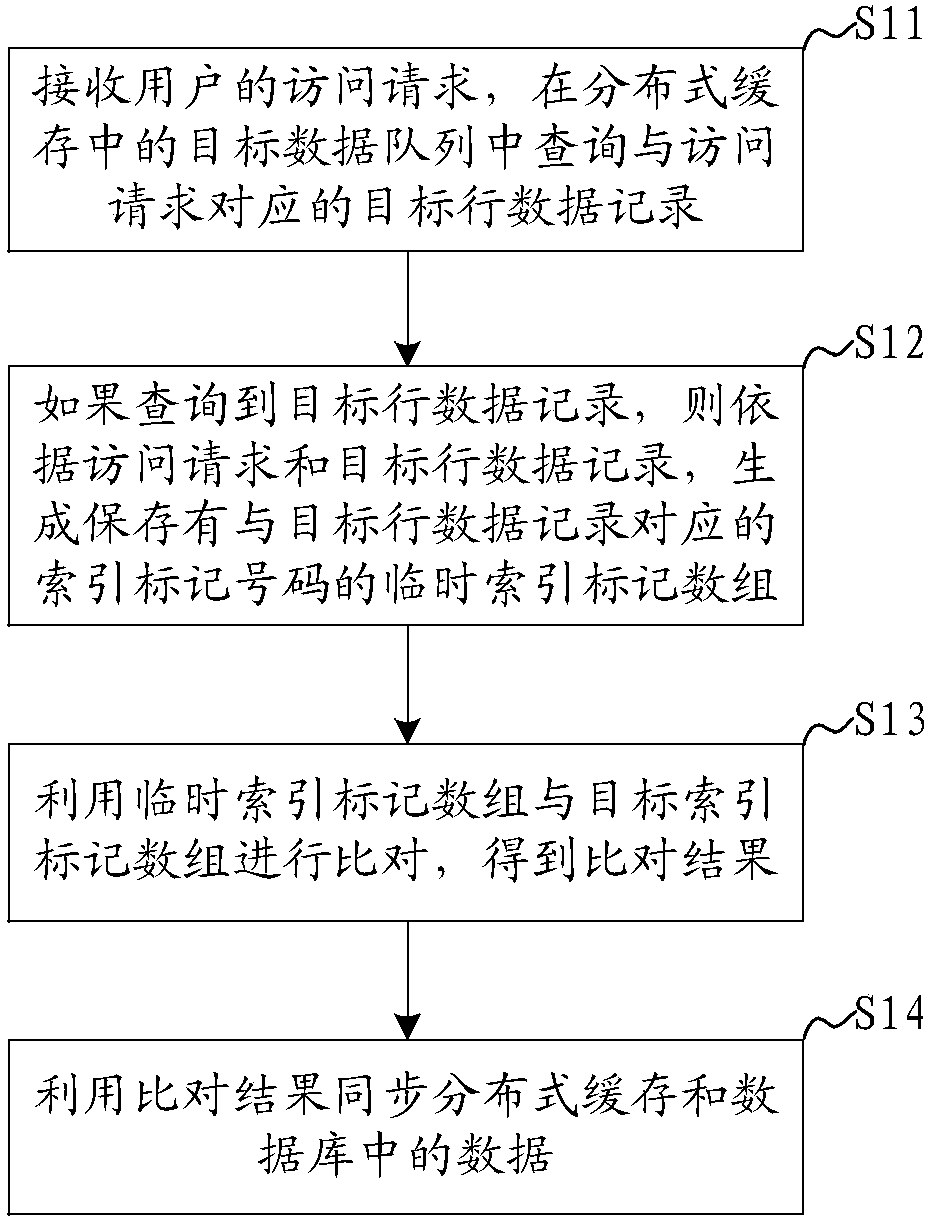
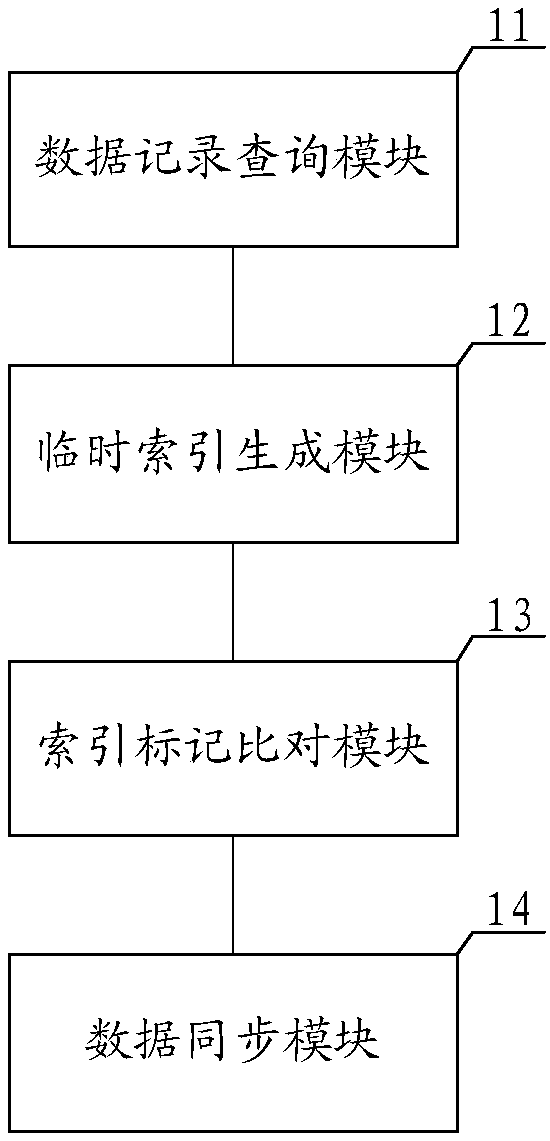
Database data access method, system and device and readable storage medium of computer
ActiveCN107832401AImprove hit rateAvoid mistakesDatabase updatingDatabase distribution/replicationArray data structureAccess method
The invention discloses a database data access method, system and device and a readable storage medium of a computer. The method includes the following steps that a target row data recording corresponding to a access request is searched in a target data queue in a distributed type cache; the target row data recording is searched, and according to the access request and a target row data recordingblock corresponding to the target row data recording, a temporary index mark array of an index mark number corresponding to the access request is generated and stored; the temporary index mark array is compared with a target index mark array, and a comparison result is obtained; according to the comparison result, data in the distributed type cache and a database are synchronized. According to themethod, high-accessibility data is pre-cached in the distributed type cache, the row data is recorded and segmented, a corresponding index mark is assigned to each row data recording block, the hit rate of the access request in the cache is improved, the error that the database is directly inquired according to the access request is avoided, and the high-accessibility frequency of the data is reduced.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Method, system and device for protecting data encryption in monitoring system
ActiveCN101448130AImprove securityImprove integrityAnalogue secracy/subscription systemsClosed circuit television systemsData streamData information
The invention relates to a method for protecting data encryption in a monitoring system. The method comprises the steps: only one identity key is arranged for each first device respectively; an encryption key corresponding to data information of the prior first device is obtained according to the identity key of the prior first device, the data information of the prior first device is encrypted by adopting the encryption key to generate the encryption data stream, and the encryption data stream is transmitted. In addition, the invention also discloses a monitoring system, a monitoring center and a first device for supporting data encryption protection. The technical scheme disclosed by the invention can enhance the security of the data information.
Owner:VIMICRO ELECTRONICS CORP
Cipher key replacing method, system and device
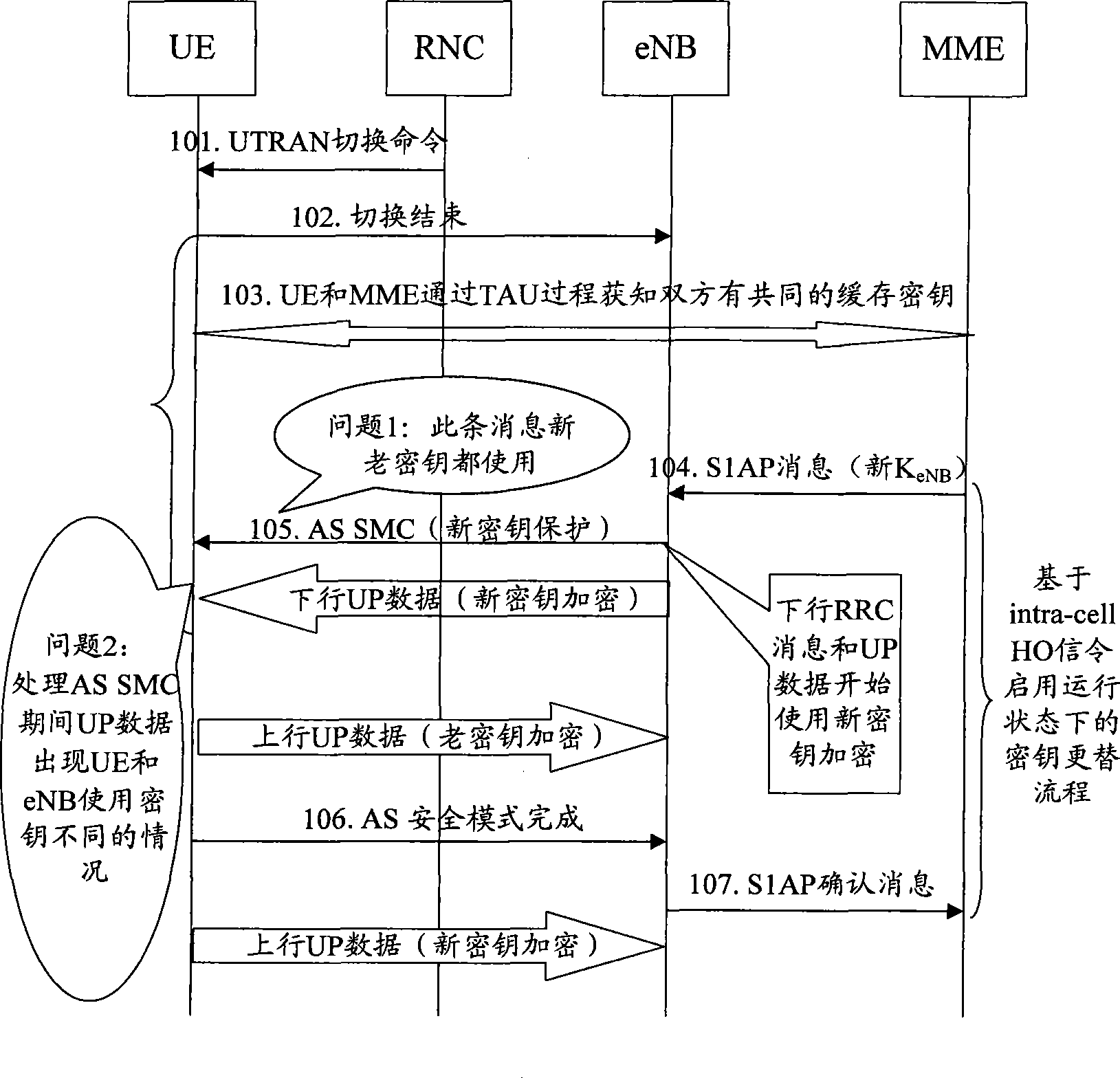
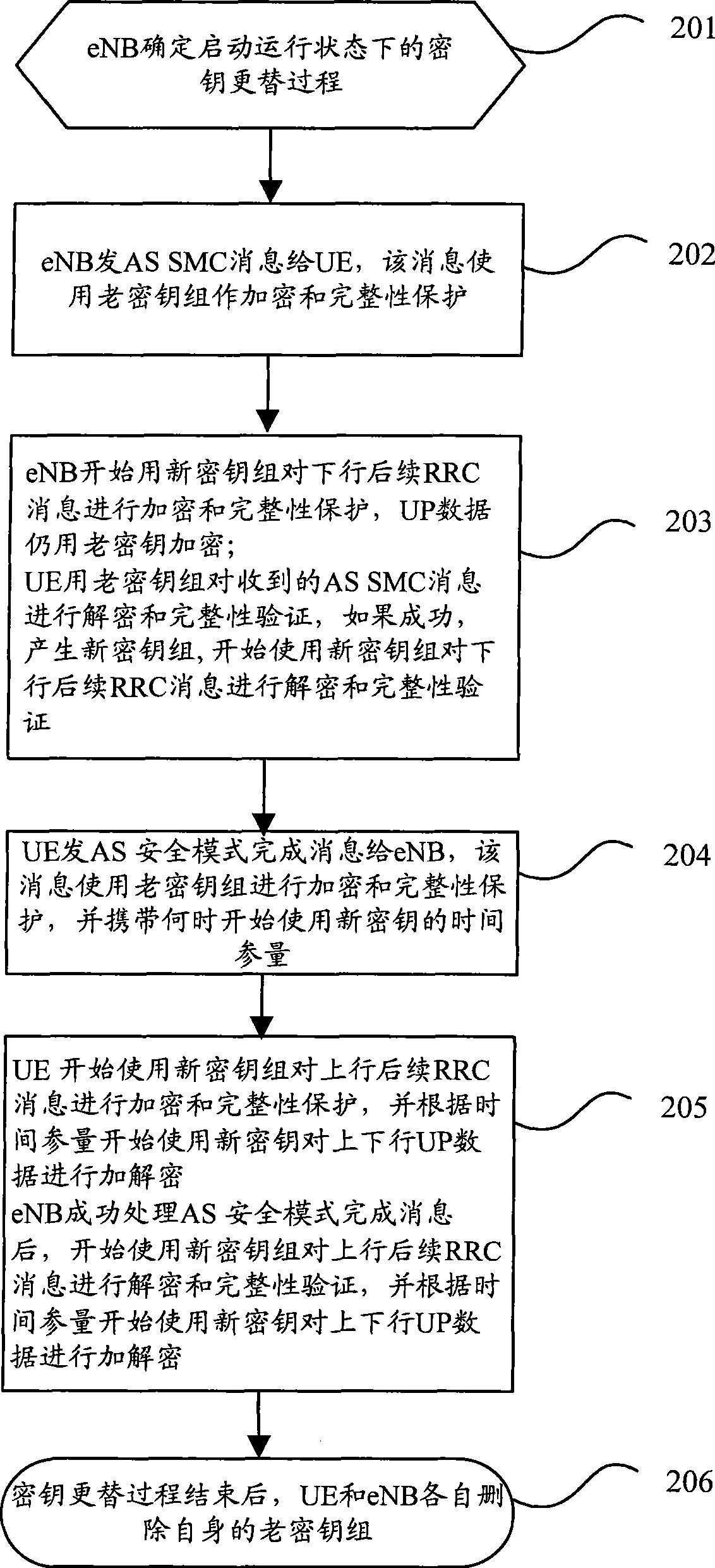
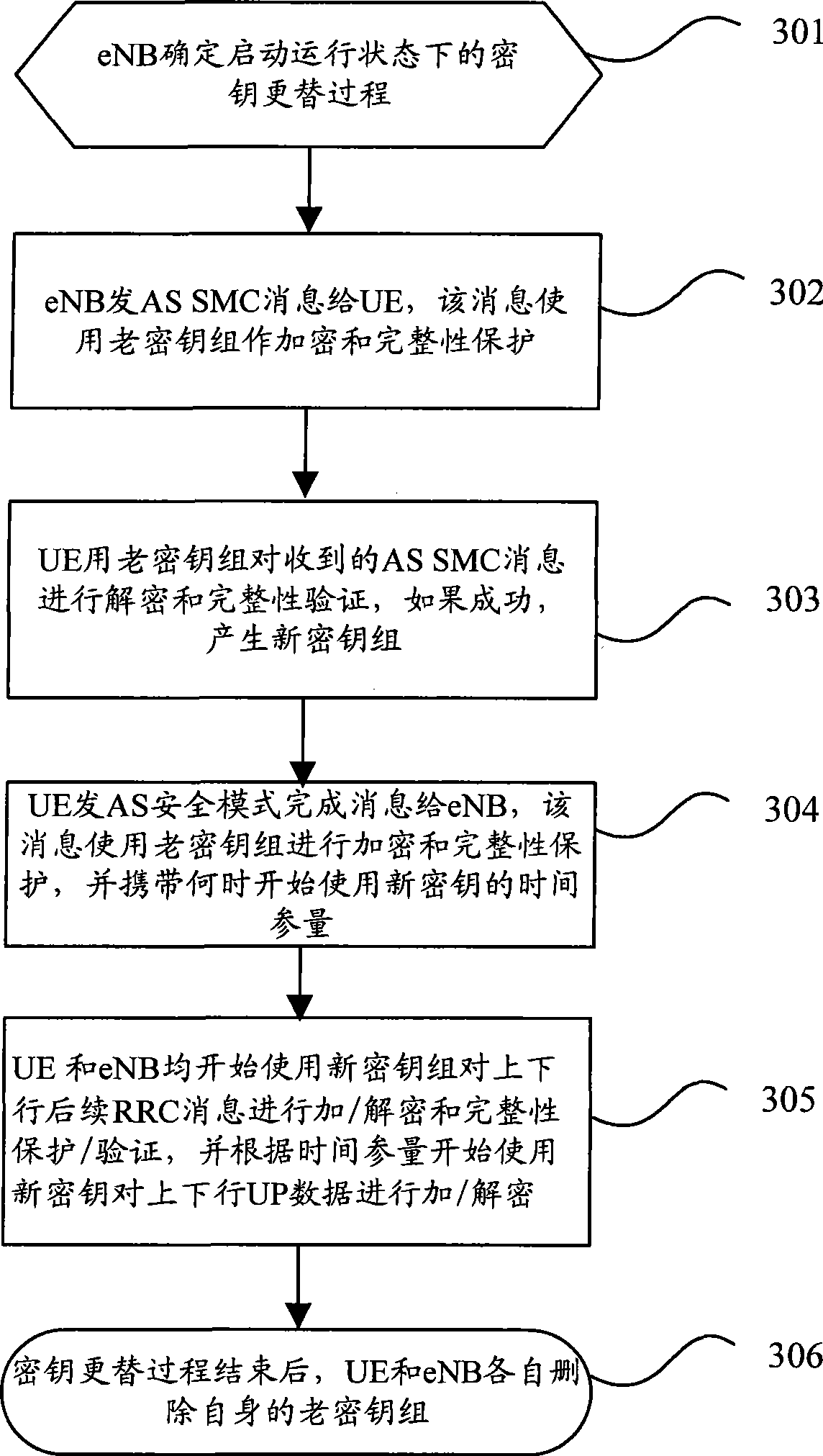
ActiveCN101478752AGuaranteed synchronizationImprove communication qualitySecurity arrangementCommunication qualityNetwork key
The invention discloses a key alternation method which comprises the following procedures: evolution nodes send access stratum safe mode command information which is encrypted and wholly protected through an old key set to user equipment; after successfully processing the access stratum safe mode information with the old key set, the user equipment sends the finished access stratum safe mode information which is encrypted and wholly protected through an old key set to the evolution nodes, and next, the user equipment begins encrypting or decrypting user plane data with a new key; after processing the finished access stratum safe mode information with the old key set, the evolution nodes begins encrypting or decrypting user plane data with a new key. The invention also discloses a key alternation system and the composition equipment. The invention can be used for ensuring that the key used by the user equipment is synchronous with the key used by the network user information when keys are alternated, thus avoiding user communication data from losing lead by the de-synchrony between the key used by the user equipment and the network key, and fatherly raising the communication quality of users.
Owner:ZTE CORP
Communication system, user device therof and synchronization method thereof
ActiveUS20080285538A1Reduce transmission failureReduce the probability of dropped callsTime-division multiplexConnection managementCommunications systemRadio Link Control
A communication system, user device thereof, and a synchronization method thereof are provided. The communication system includes a user device and a wireless network. A ciphering configuration information is transmitted to a user device. The user device and wireless network re-establishing the radio link control (RLC) entity of logical link. The user device changes to the new ciphering configuration immediately following the re-establishment of RLC entity according to the received ciphering configuration information and the wireless network changes to the new ciphering configuration.
Owner:HTC CORP
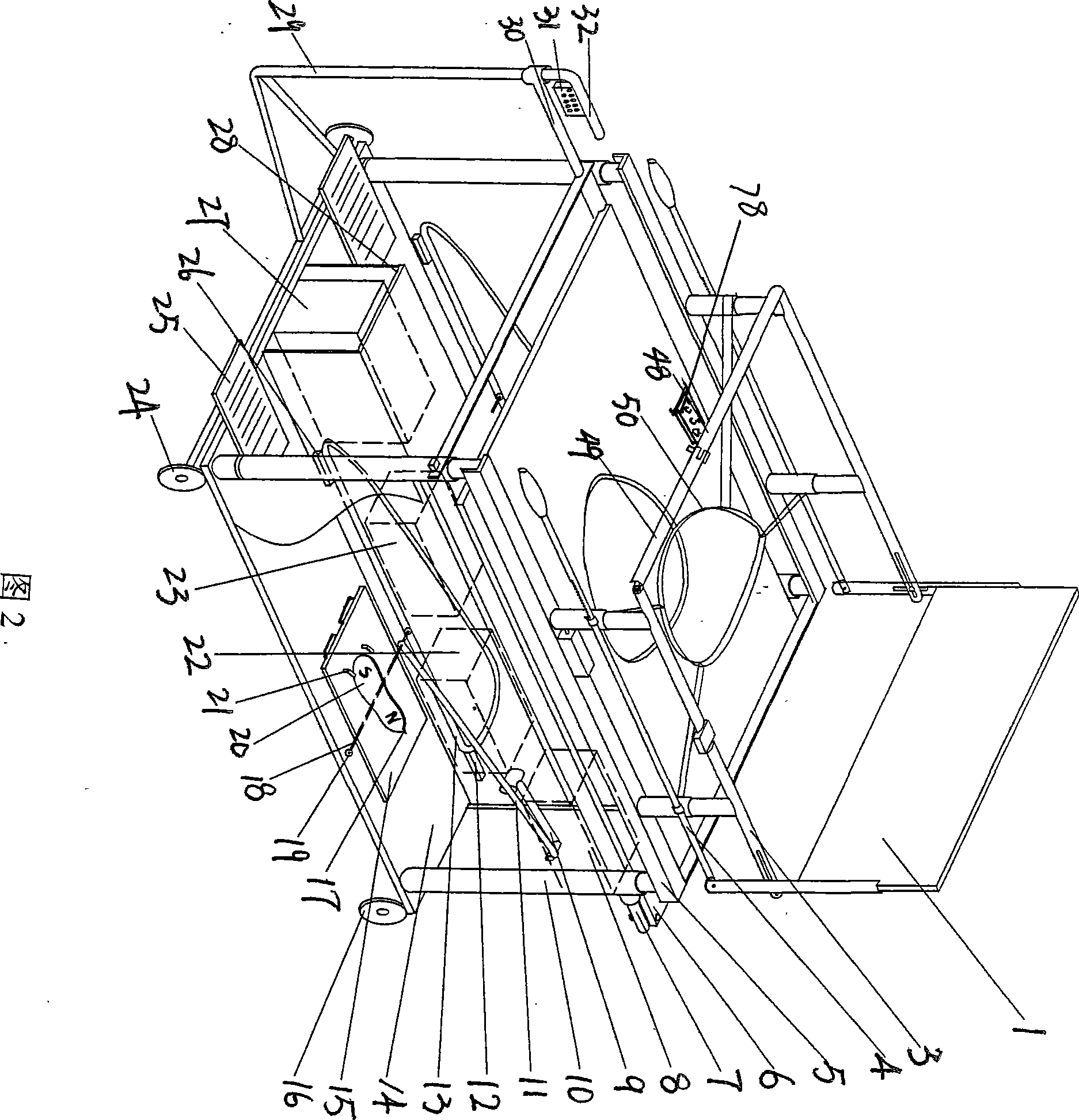
Self-nursing rehabilitation training trolley for hemiplegia patient
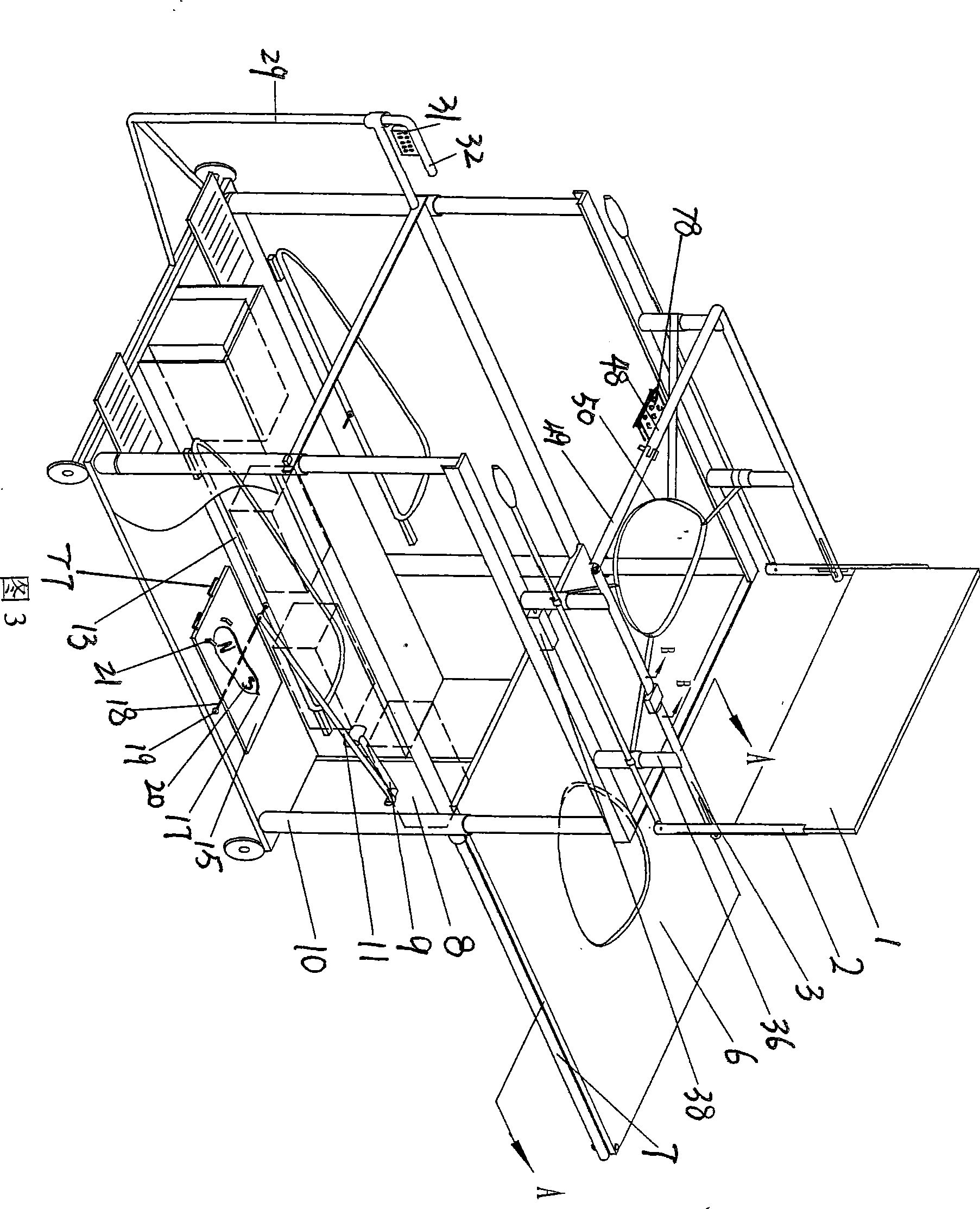
InactiveCN101438989AIncrease courageConfidenceChiropractic devicesWheelchairs/patient conveyanceSick personEngineering
The invention relates to a hemiplegic patient self nursing and rehabilitation training trolley which consists of a veering walking device used for moving, a lifting device used for relieving the bowels by self and for walking training, a swing training device arranged on a bracket and used for up-and-down and left-and-right training of sick arm, a walking training device that is used for simulating human walking and consists of a annular slideway, a pulley, a walking training footplate, a winch, a connecting rod and a walking training motor in a linkage way, a seat board device used for sitting and for relieving the bowels, a backrest adjusting device and an operating device. The invention provides a nurse type integral nursing device for the hemiplegic patient; the patient can walk or take rest, relieve the bowels by self on the trolley and carry out sick arm swinging training, and standing and walking training just by operating the device by the healthy arm, thereby encouraging the hemiplegic patient to take heart and build confidence to live; and no special person is required to take care of the patient always, thereby lightening the pressure of the family of the patient at the aspects of living, work, economy, spirit, etc.
Owner:阎国图
Access method and device for application system
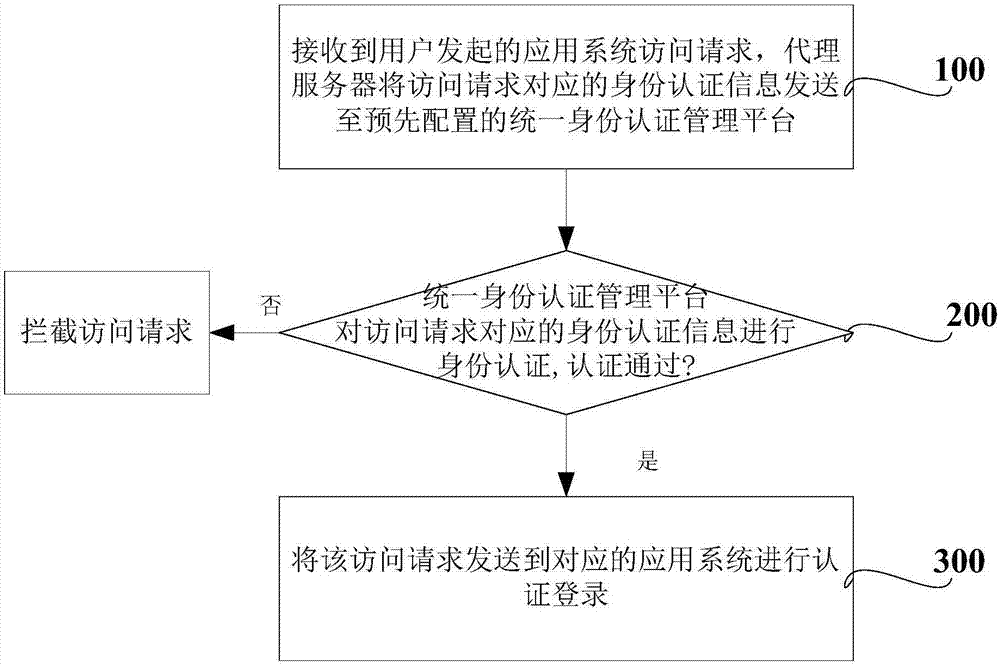
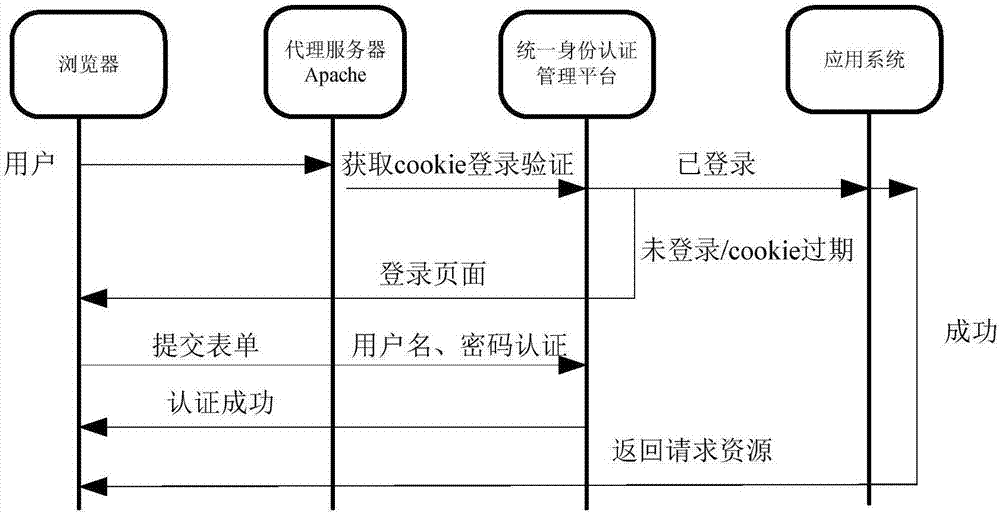
ActiveCN107277049ARealize unified managementGuaranteed synchronizationTransmissionAccess methodInternet privacy
The invention discloses an access method and device for an application system and relates to the technical field of multisystem login access. The access method for the application system comprises the following steps that a proxy server sends identity authentication information corresponding to an access request to a preconfigured unified identity authentication management platform to carry out identity authentication when the proxy server receives the access request of the application system, which is initiated by a user; and only when the identity authentication information corresponding to the access request passes the identity authentication of the preconfigured unified identity authentication management platform, the proxy server sends the access request to the corresponding application system to carry out login authentication.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com