Authentication method, re-authentication method and communication device
A technology of authentication and authentication keys, applied in the field of communication, can solve problems such as increasing the complexity of RS, and achieve the effect of ensuring validity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
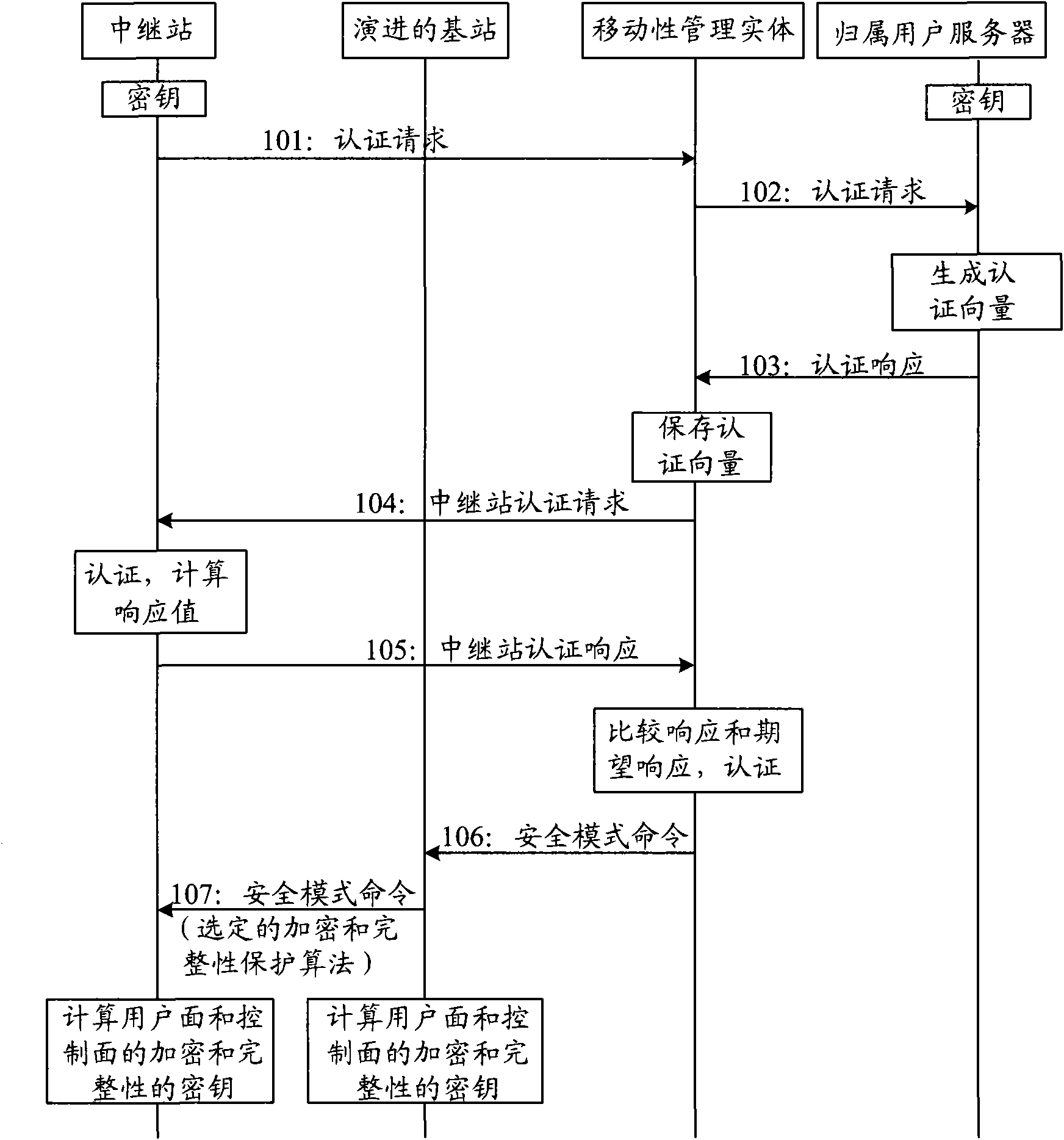
[0060] In the embodiment of the present invention, the following methods can be used to implement secure network access of the RS, and the RS does not need to be equipped with a USIM card, which will be described in detail below with reference to the accompanying drawings.
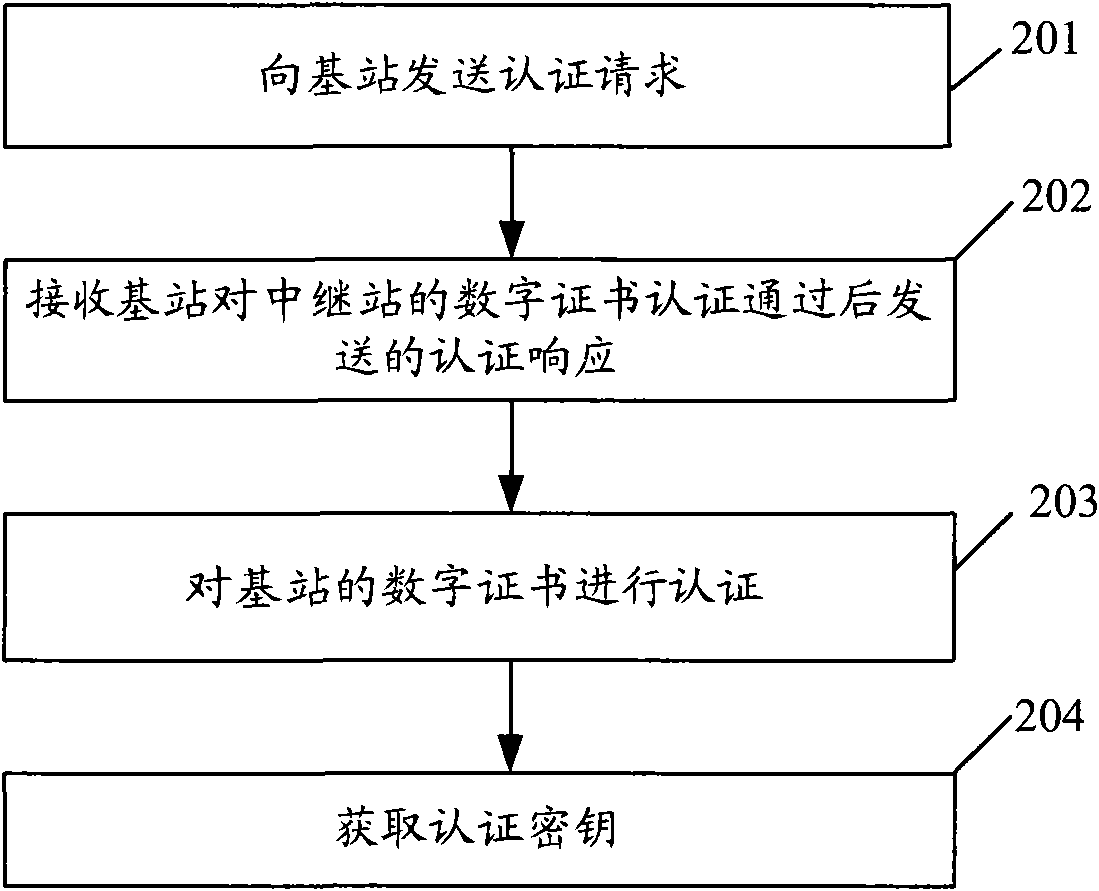
[0061] see figure 2 , an authentication method, comprising:
[0062] Step 201: Send an authentication request to the base station, where the authentication request includes the digital certificate of the RS;
[0063] An authentication request can also be sent to the eNB. After the RS is introduced, various systems that support the digital certificate authentication method can authenticate the RS. Therefore, the eNB in the subsequent embodiments refers to a base station that can support the digital certificate authentication method.
[0064] The authentication request includes the digital certificate of the RS, such as the X.509 digital certificate, the capability of the RS, the signature of the RS on t...
Embodiment 2
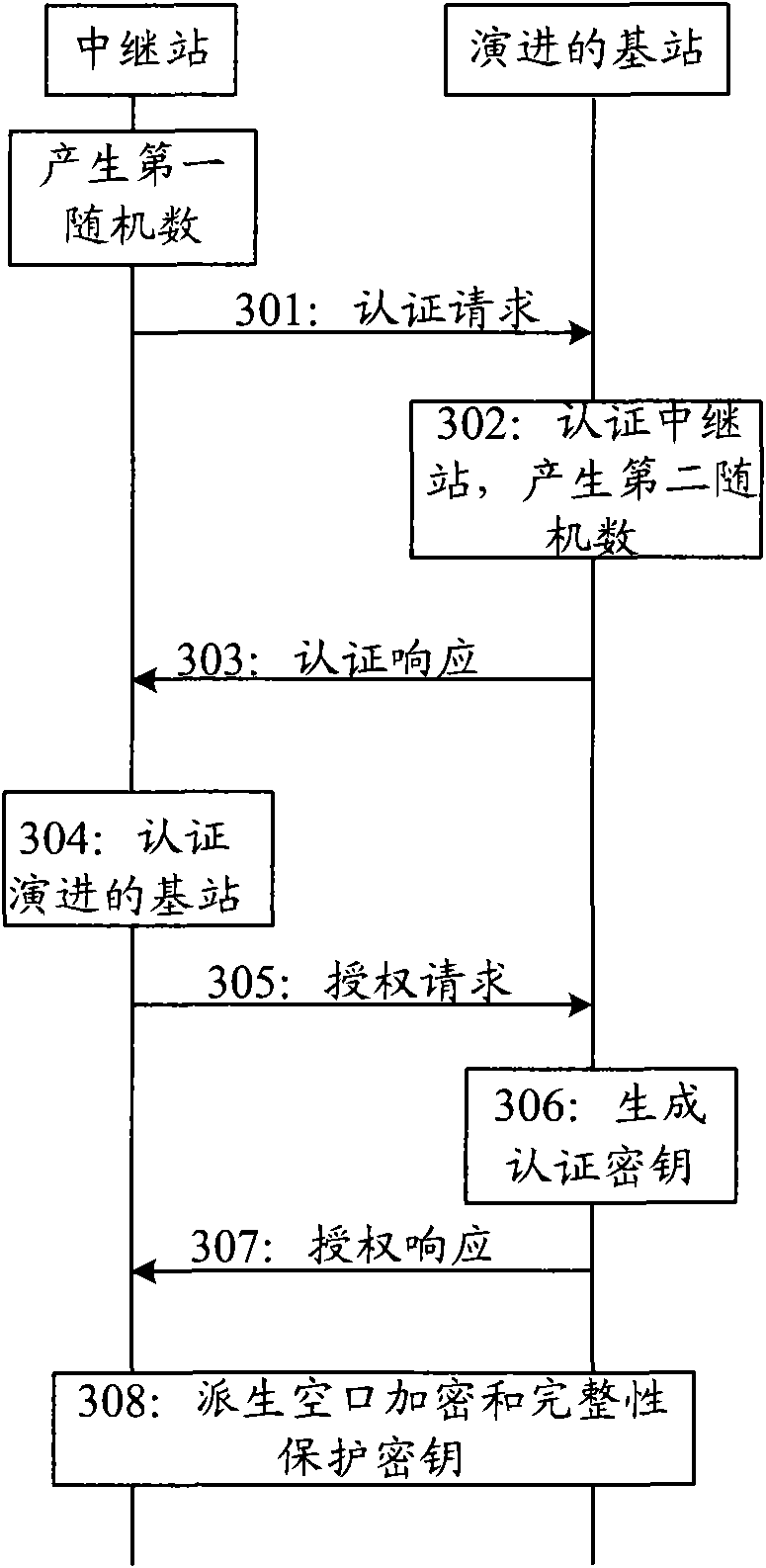
[0074] In this embodiment, after the two-way authentication is completed between the RS and the eNB, the eNB derives an authentication key and sends it to the RS. After the RS is introduced, various systems that support digital certificate authentication can authenticate the RS, so the eNB in this embodiment can be a base station. A detailed description will be given below in conjunction with the accompanying drawings. see image 3 , the specific steps for implementing the method of Embodiment 2 are described in detail below:
[0075] Step 301: RS sends an authentication request to eNB;
[0076] The authentication request can be included in the authentication request message. The authentication request includes the digital certificate of the RS, such as the X.509 digital certificate, the capability of the RS, the signature of the digital certificate by the RS, and the first random number RAND1 randomly generated by the RS. Capabilities are encryption / integrity protection ...
Embodiment 3
[0095] In this embodiment, after the eNB completes the one-way authentication of the RS, the eNB derives the authentication key and issues it to the RS. After the RS is introduced, various systems that support digital certificate authentication can authenticate the RS, so the eNB in this embodiment can be a base station. A detailed description will be given below in conjunction with the accompanying drawings.
[0096] see Figure 4 , the specific steps of the method for implementing the third embodiment are described in detail below:
[0097] Step 401 is the same as step 301 and will not be repeated here.
[0098] Step 402: eNB authenticates RS, generates RAND2, and eNB generates authentication key AK;
[0099] The eNB authenticates the RS digital certificate through the received signature and RAND1. After the authentication is passed, the authentication of the RS on the network side is completed. The eNB generates the authentication key AK, and uses the eNB private key to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com