Patents
Literature
146results about How to "Avoid synchronization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
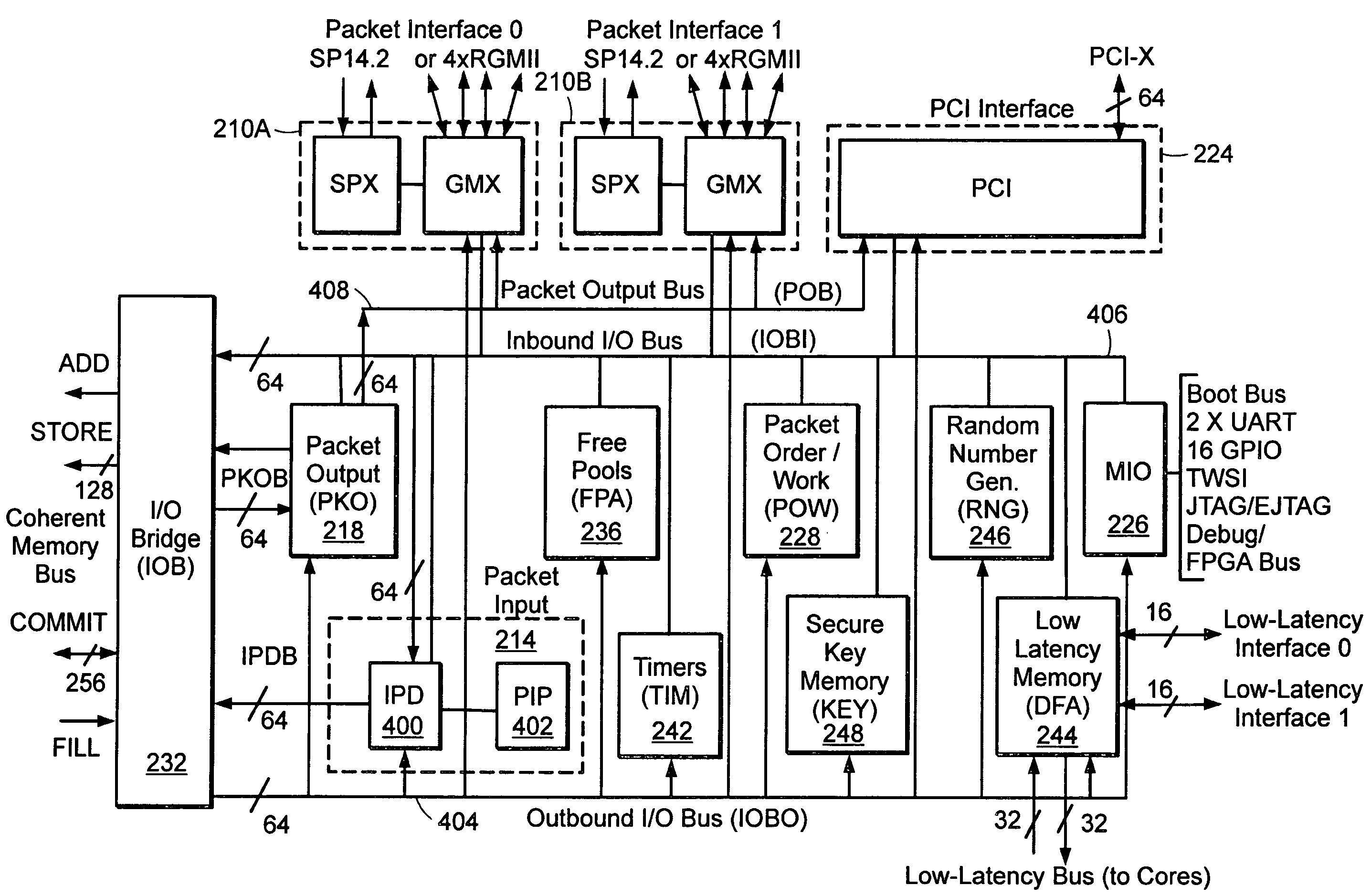
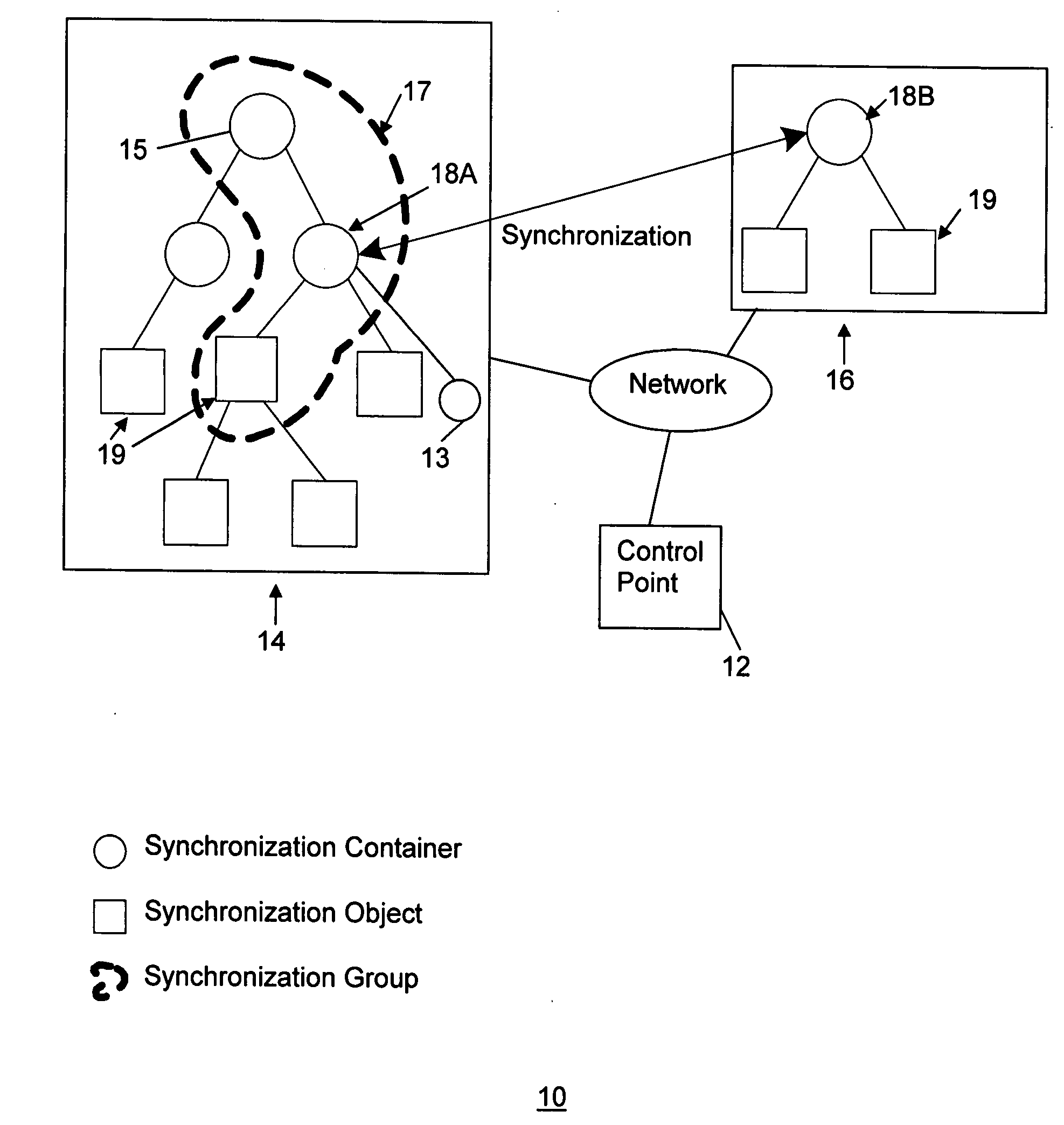
TCP engine
ActiveUS7535907B2Speed up the processSynchronizationTime-division multiplexData switching by path configurationTransport layerWire speed
A network transport layer accelerator accelerates processing of packets so that packets can be forwarded at wire-speed. To accelerate processing of packets, the accelerator performs pre-processing on a network transport layer header encapsulated in a packet for a connection and performs in-line network transport layer checksum insertion prior to transmitting a packet. A timer unit in the accelerator schedules processing of the received packets. The accelerator also includes a free pool allocator which manages buffers for storing the received packets and a packet order unit which synchronizes processing of received packets for a same connection.
Owner:MARVELL ASIA PTE LTD
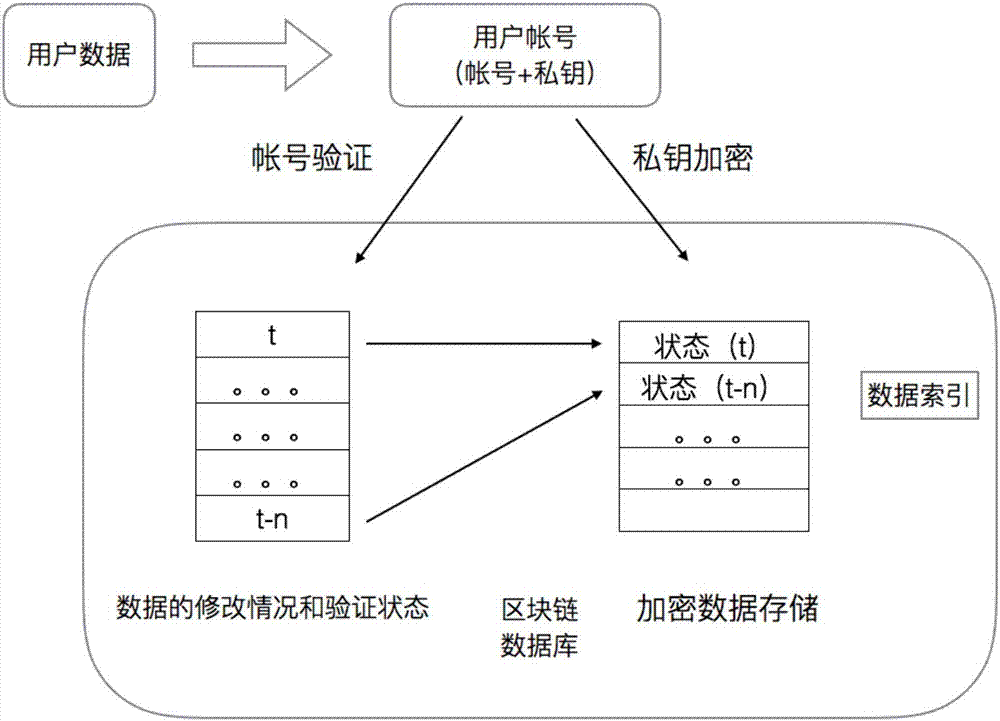
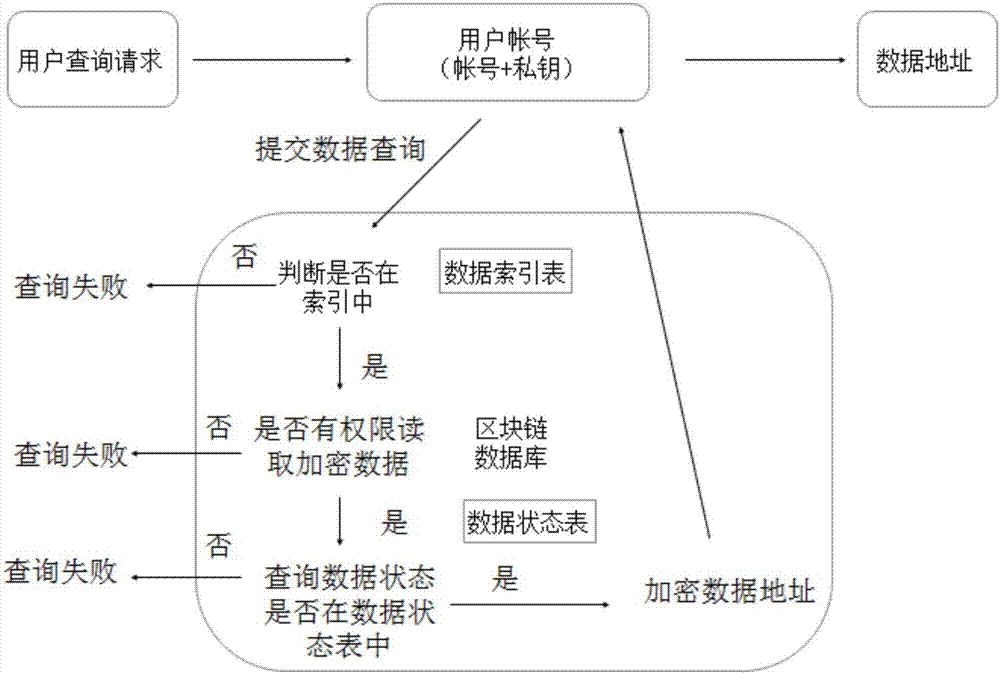
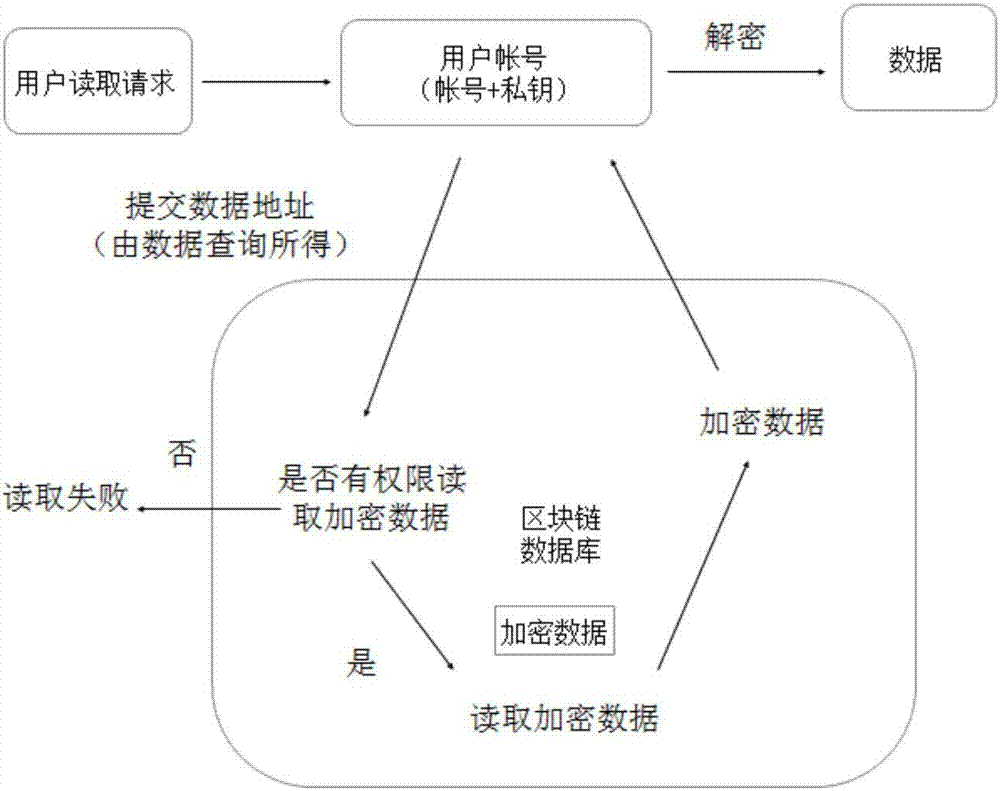
Blockchain-based database system and method of using same
ActiveCN107292181AFix permission issuesSolve the problem of excessive permissionsDigital data protectionSpecial data processing applicationsConfidentialityCentral database
The invention discloses a blockchain-based database system, comprising a client, an access server and a blockchain verification server. A method of using the blockchain-based database system comprises the steps of 1, registering a blockchain account on the blockchain verification server through the client, or registering, by the blockchain verification server itself, the blockchain account on the blockchain verification server, and acquiring a public key and a private key; 2, writing, by a user, data into the access server through the client; 3, transmitting, by the access server, a request to the blockchain verification server to perform data co-recognition; 4, submitting, by the user, a query request to the access server through the client to perform related query; 5, after the user obtains data query results, directly using, by the user, the results to read data, or otherwise the user having the need to perform data query; after data reading, unlocking the data by the user through his or her own account private key. The problems are solved that data in a central database are insecure and it is difficult for a distributed database to arrive at uniformity and data confidentiality.
Owner:无锡井通网络科技有限公司
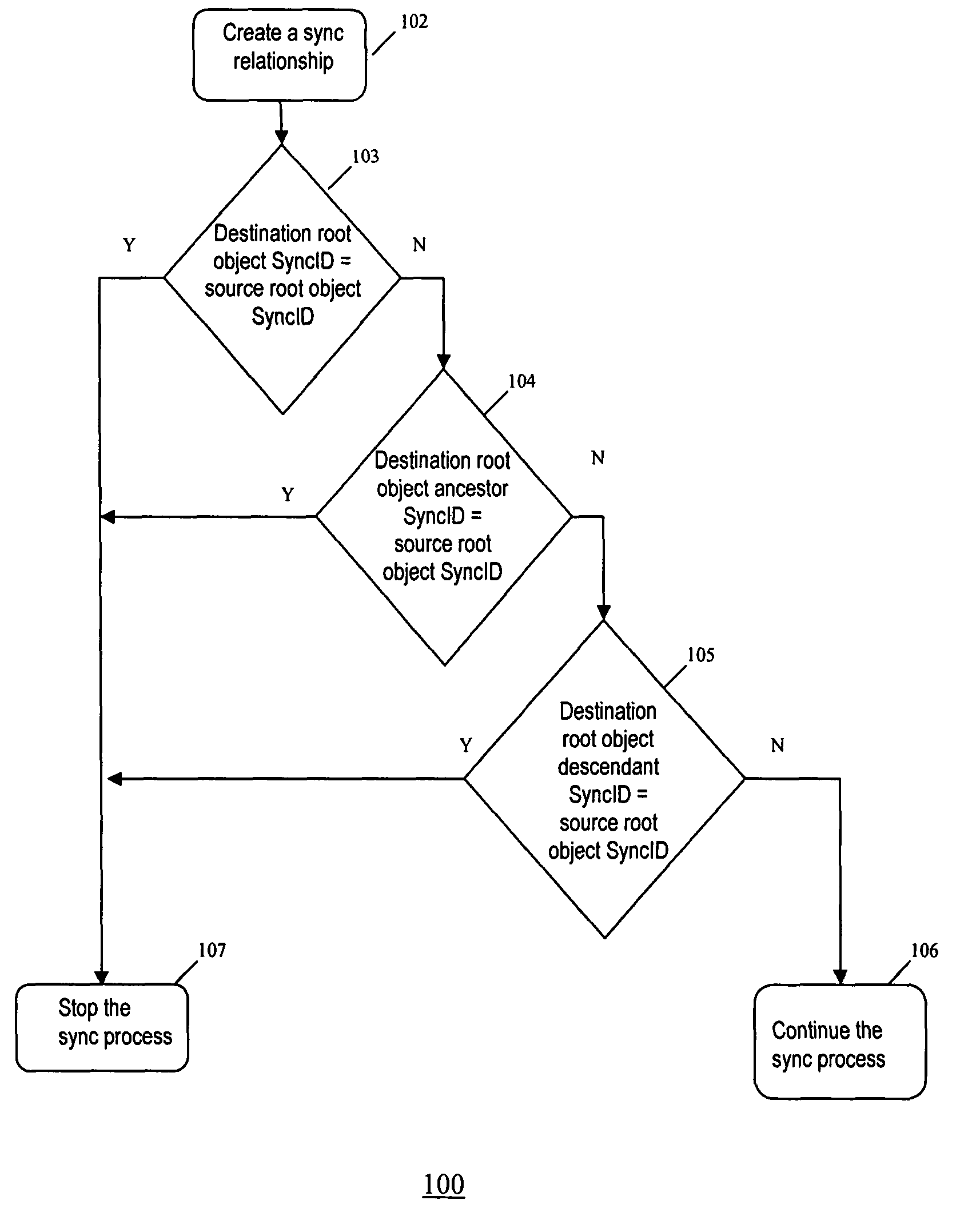
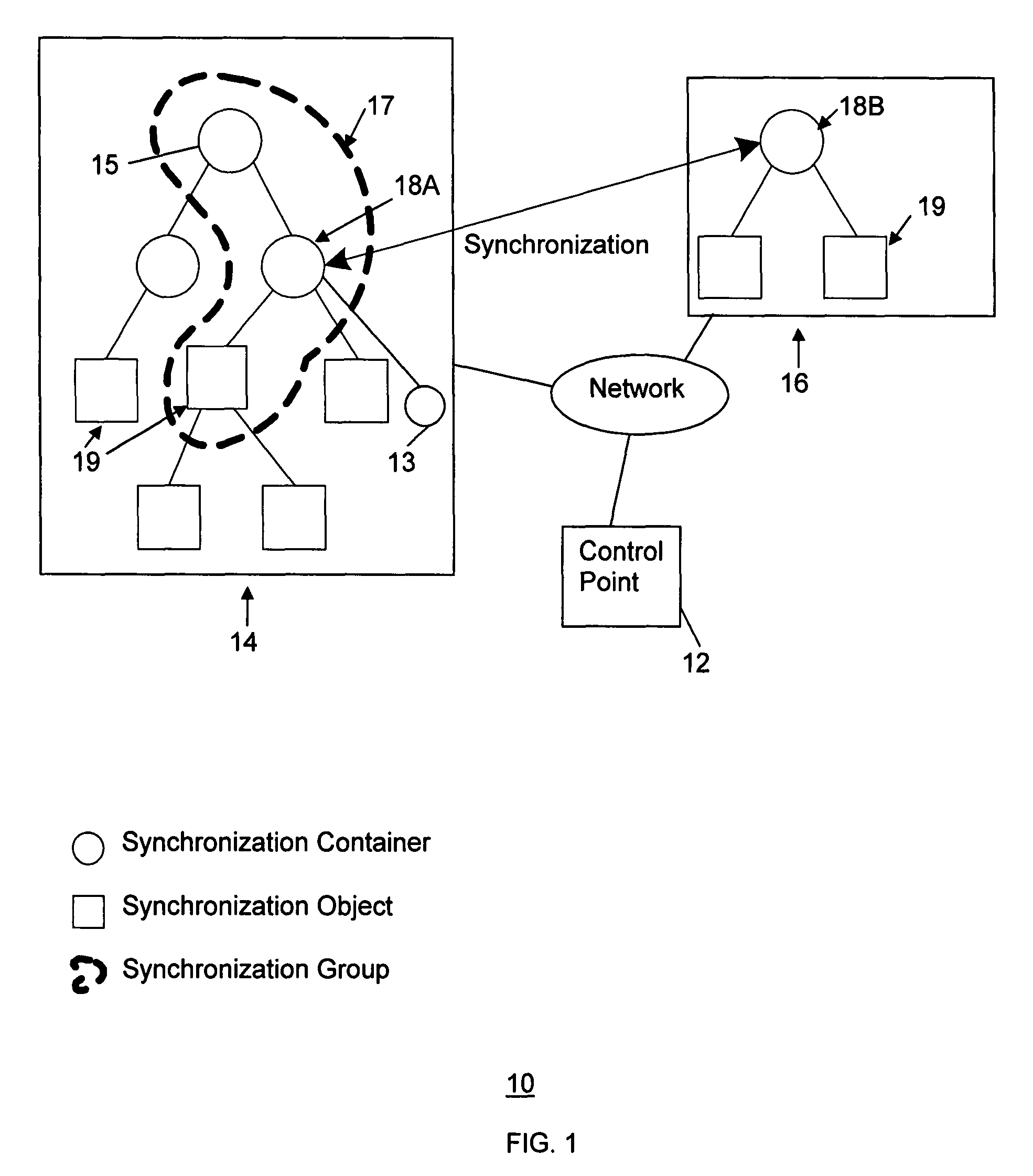
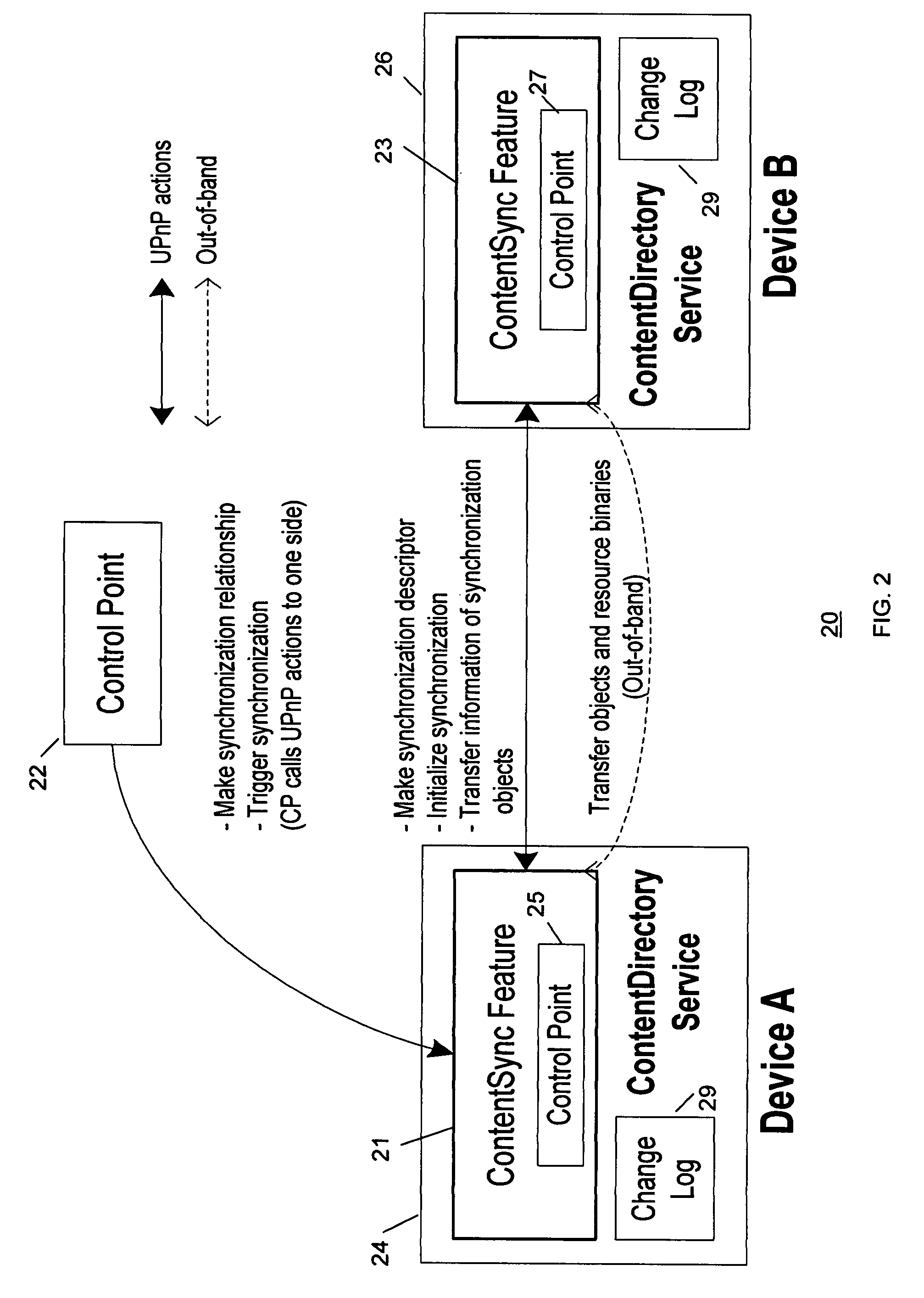
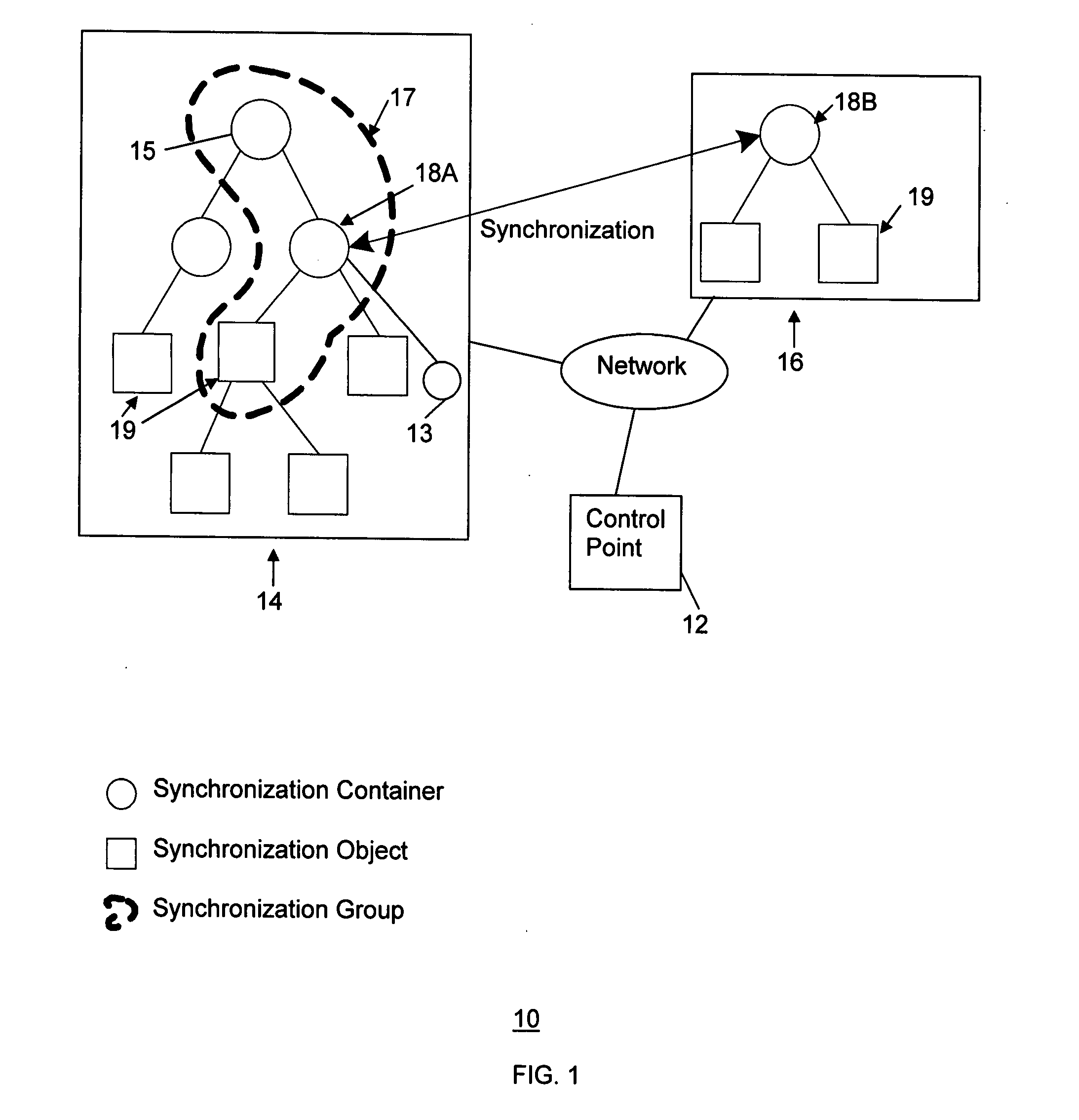
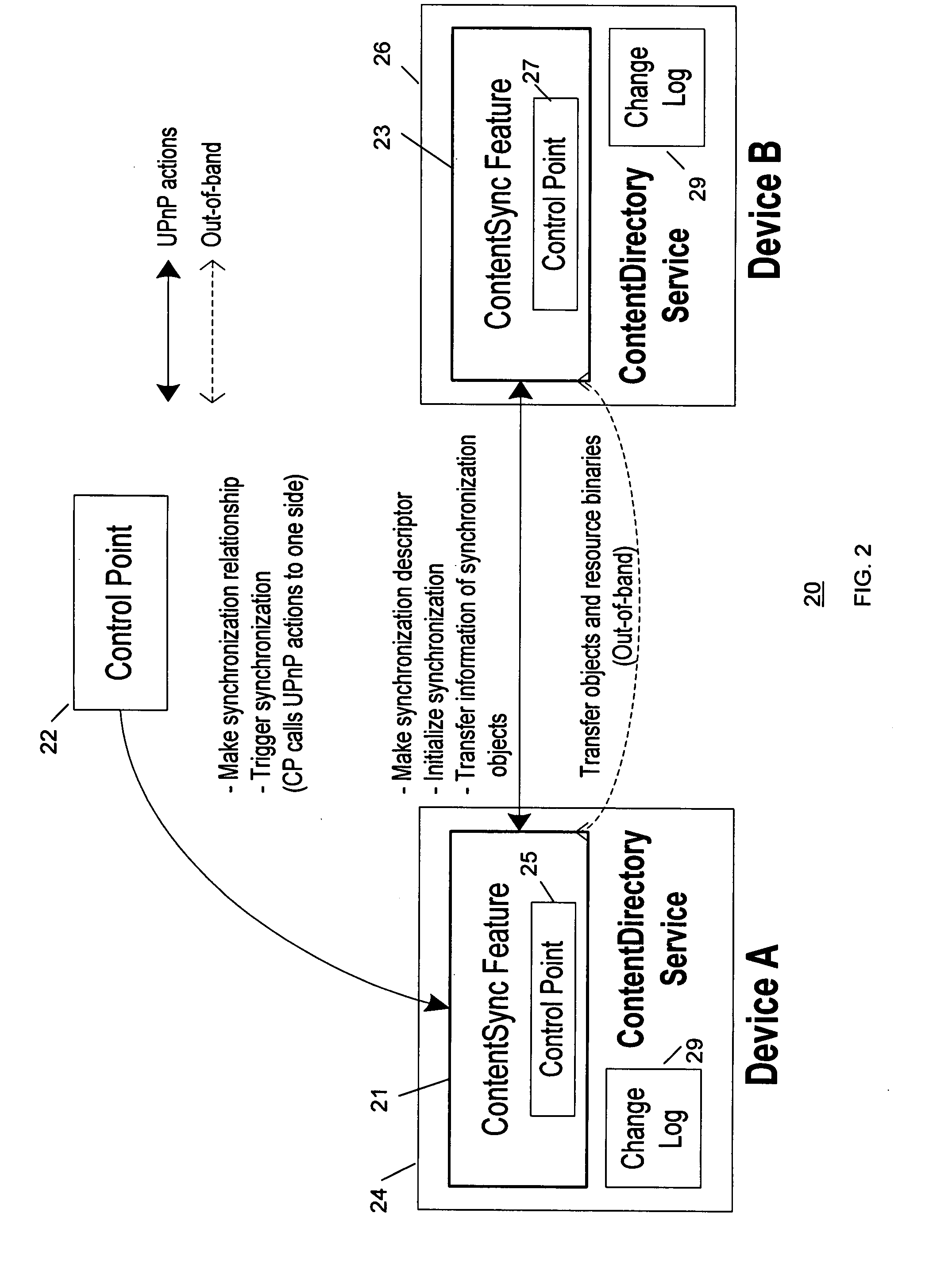
Method and system for content synchronization and detecting synchronization recursion in networks
InactiveUS7739411B2Detects and prevents synchronization recursionAvoid synchronizationDigital data processing detailsMultiple digital computer combinationsTransfer operationDistributed computing
A method and system implementing a process for content synchronization that detects and prevents synchronization recursion in CDS transfer operations. A synchronization relationship is formed between the CDS containers in multiple devices. Then content synchronization processes are performed based on that relationship to avoid synchronization recursion.
Owner:SAMSUNG ELECTRONICS CO LTD
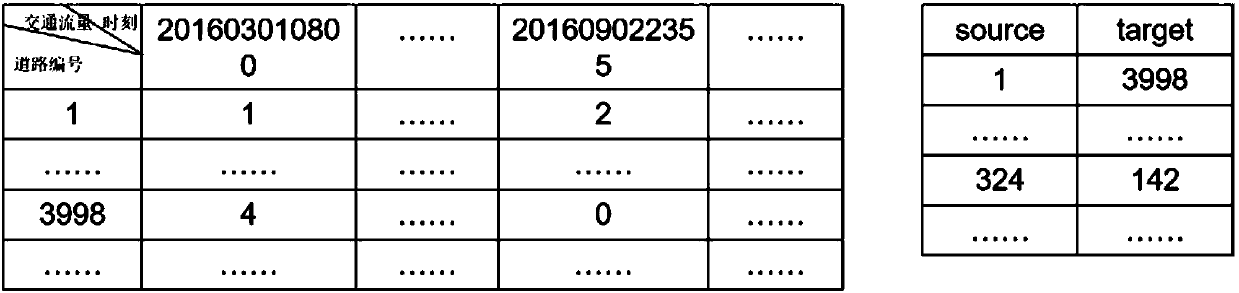
Traffic flow rate prediction method based on road clustering and two-layer two-way LSTM (long short-term memory)
InactiveCN107154150AImprove forecast accuracyIncrease training speedDetection of traffic movementCharacter and pattern recognitionTemporal informationMissing data
The invention discloses a traffic flow rate prediction method based on road clustering and two-layer two-way LSTM (long short-term memory). The method comprises the following steps of (1) providing a mode of using peripheral equalization on a loss value when the training data has a missing value, so that the missing data is filled; the prediction precision is improved; (2) providing a method of performing relevance clustering on the road according to the historical flow rate data; dividing the road into a plurality of groups; simultaneously utilizing the time information and the space information in the data preprocessing stage for improving the prediction precision; (3) designing a two-layer two-way LSTM deep neural network model for improving the prediction precision of the model; (4) providing a method of performing mass training and test on the network model; accelerating the training and test speed of the neural network model; (5) providing a multi-model fusion method for improving the prediction precision. The method provided by the invention has the advantages that the prediction speed and the prediction precision of the deep neural network model in an aspect of traffic flow rate prediction are accelerated and improved at the same time.
Owner:凯习(北京)信息科技有限公司
Method and system of synchronizing different media stream
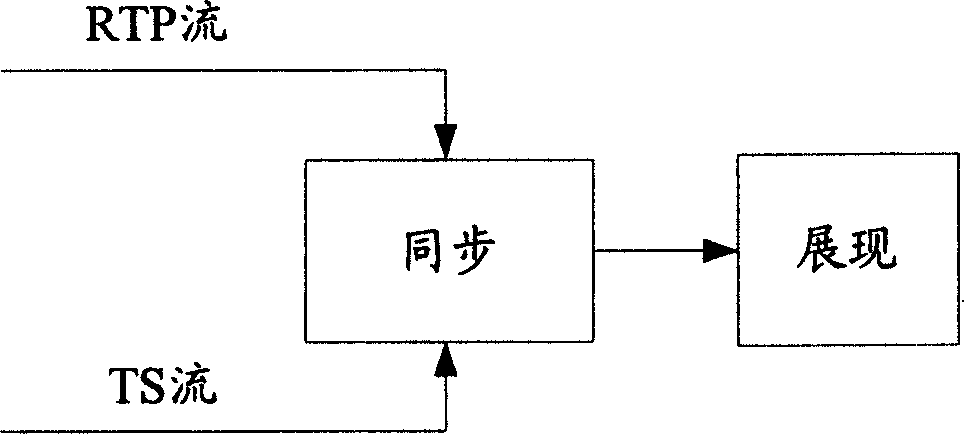
InactiveCN101179484AAvoid synchronizationResolve synchronizationTime-division multiplexSelective content distributionTemporal informationStreaming data
The invention discloses a synchrony method and a synchro system between different media streams. The invention includes the following steps: the first corresponding relationship between the first time information and the first display time of a first media stream data packet is established; the second corresponding relationship between the second time information and the second display time of a second media stream data packet is established; according to the corresponding relationship, the first media stream media stream data packet and the second media stream data packet are displayed simultaneously when a difference value between the first display time and the second display time is less than a threshold value. The invention realizes the synchrony of different media streams from a broadcast network program or from a broadband program, and solves a synchrony of media streams from different networks, and possesses a remarkable actual application effect and significance in the modern media stream technology.
Owner:HUAWEI TECH CO LTD
System for isolating first computing environment from second execution environment while sharing resources by copying data from first portion to second portion of memory
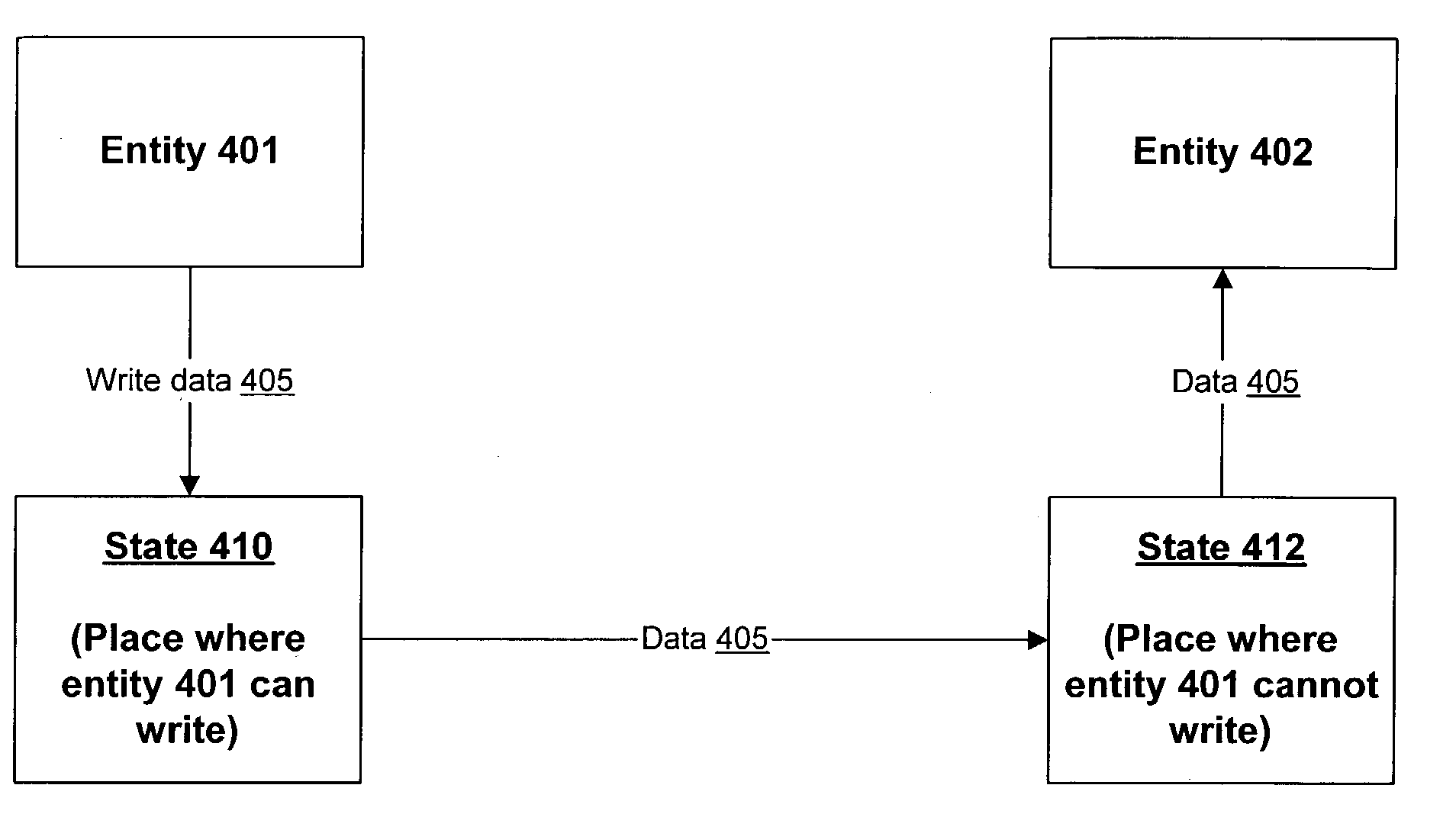
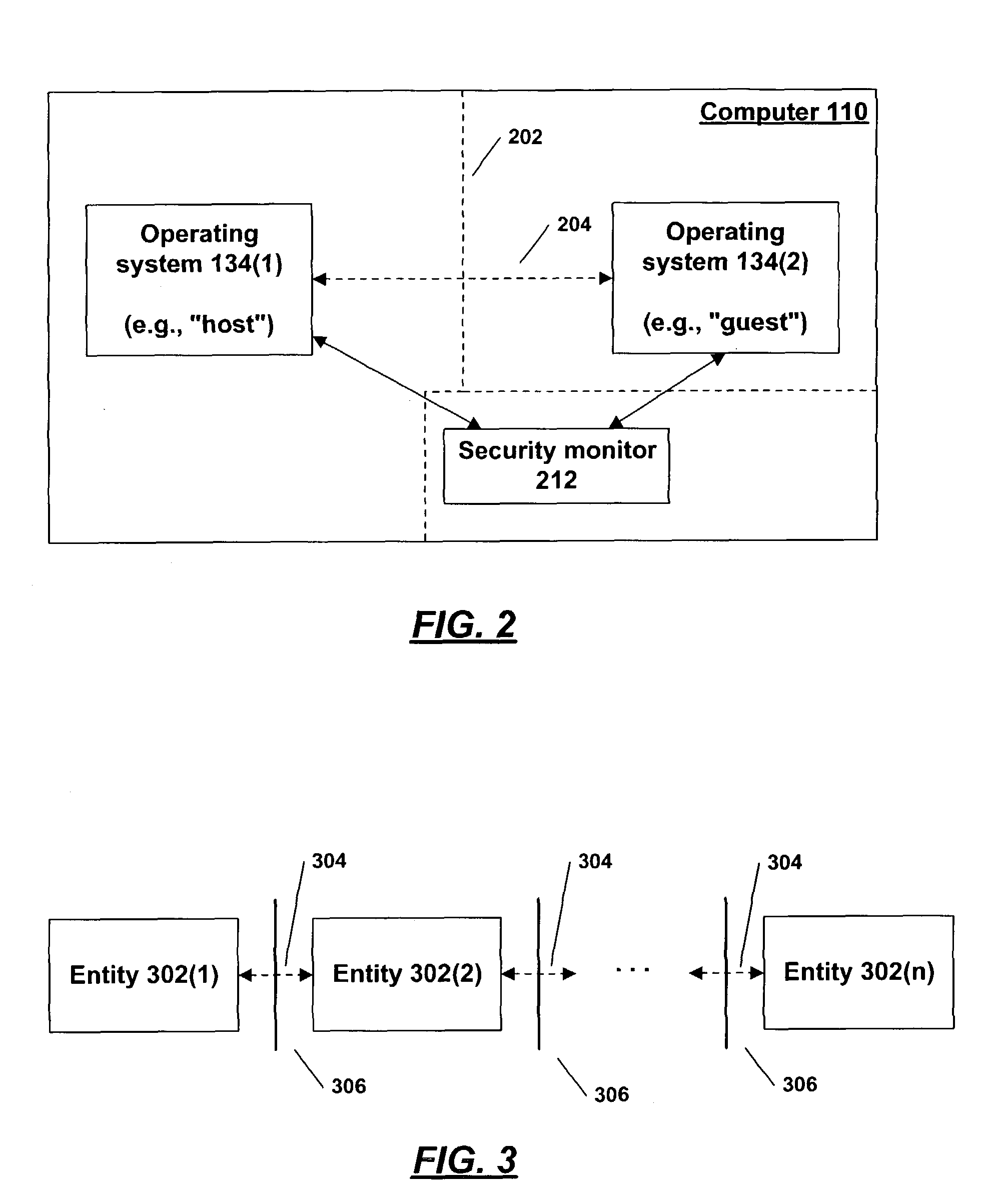
ActiveUS7788669B2Prevent abilityUndermine abilityMultiprogramming arrangementsSoftware simulation/interpretation/emulationDistributed computingShared resource
Techniques are disclosed to support hosting of a first operating system by a second operating system, where the first system provides at least some of the infrastructure for the second system. A facility is provided whereby the second system can receive data from the first system without the first system being able to modify that data. The second system may use the first system's scheduler by creating shadow threads and synchronization objects known to the first system, while the second system makes the final decision as to whether a thread runs. Separate memory may be allocated to both systems at boot time, or dynamically during their operation. The techniques herein may be used to protect the second system from actions arising in the first system. Preferably, the interaction between the first and second systems is facilitated by a security monitor, which assists in protecting the second system from the first.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for content synchronization and detecting synchronization recursion in networks
InactiveUS20080040511A1Detects and prevents synchronization recursionAvoid synchronizationMultiple digital computer combinationsTransmissionTransfer operationDistributed computing
A method and system implementing a process for content synchronization that detects and prevents synchronization recursion in CDS transfer operations. A synchronization relationship is formed between the CDS containers in multiple devices. Then content synchronization processes are performed based on that relationship to avoid synchronization recursion.
Owner:SAMSUNG ELECTRONICS CO LTD
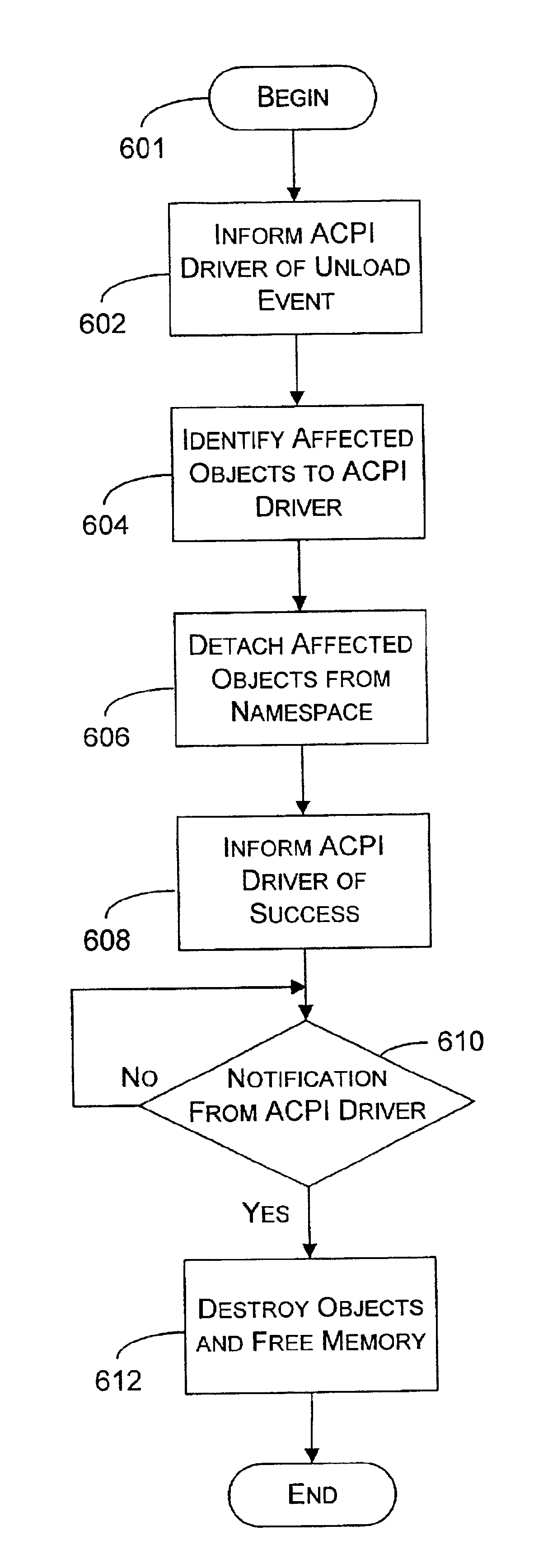
System and method for unloading namespace devices
InactiveUS6877018B2Avoid synchronization conflictAvoid collisionData processing applicationsDigital data processing detailsComputer scienceNamespace
An advanced configuration and power management system is described which supports an unload command by identifying those objects that are to be unloaded and, rather than simply attempting to delete the objects, detaches them from the namespace while keeping them in memory in a location accessible by the system. In this way, the system avoids the problem of trying to synchronize accesses to the objects, yet the objects not longer exist in the tree, so namespace collisions are avoided.
Owner:MICROSOFT TECH LICENSING LLC
Method for establishiing a synchronization or for establishing a connection between a mobile terminal and an access point
InactiveUS20060211402A1Reduce power consumptionMany pointsSynchronisation arrangementAssess restrictionBase stationCommunications system
Owner:ALCATEL LUCENT SAS
A method for clouding an SCADA system based on a Spring cloud micro-service architecture
InactiveCN109814909AFail-fast callAvoid synchronizationSoftware maintainance/managementService Component ArchitectureSCADA
According to a method for clouding an SCADA system based on a Spring cloud micro-service architecture, the SCADA system is developed according to the Spring cloud micro-service architecture, so that the SCADA system can be conveniently deployed on a cloud server. The method comprises the following steps of 1, creating a male parent; 2, carrying out the service discovery and registration; 3, arranging a service provider and a service consumer; 4, fusing the service; 5, configuring a center; 6, setting an API gateway; 7, performing distributed transaction consistency management; and 8, constructing the micro-service by using the Docker. According to the present invention, the Spring Boot is used for developing the application micro-service, and the functions of service discovery, service consumption, service fusing, API gateway, unified configuration center, distributed transaction consistency management and container construction can be effectively achieved.
Owner:NANJING GREEN NEW ENERGY RES INST CO LTD
Method and system for performing time synchronization between nodes in wireless communication system
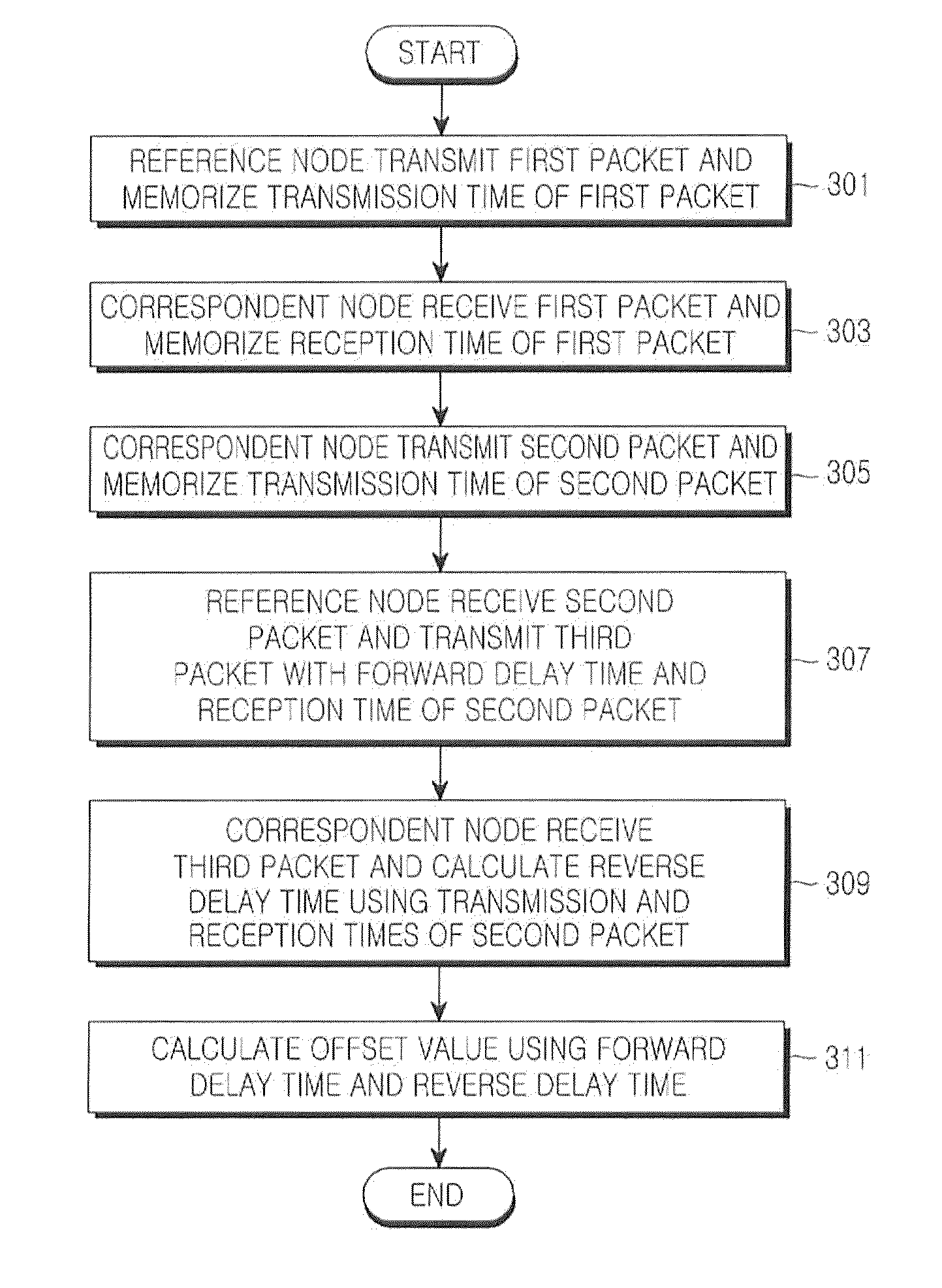
ActiveUS20100157975A1Preventing out-of-time synchronizationAvoid synchronizationSynchronisation arrangementNetwork topologiesData packCommunications system
A method is provided for synchronizing time between nodes in a wireless communication system. A reference node transmits a first packet to a correspondent node. Upon receiving the first packet, the correspondent node transmits a second packet with a reception time of the first packet recorded therein, to the reference node. Upon receiving the second packet, the reference node calculates a forward delay time using a transmission time and the reception time of the first packet. The correspondent node receives a third packet with the forward delay time from the reference node, and calculates a reverse delay time. The correspondent node calculates an offset value for the synchronization using the forward delay time and the reverse delay time.
Owner:SAMSUNG ELECTRONICS CO LTD
Three-dimensional flow field image measurement device and method adopting single lens
InactiveCN102798512ASimplify measurement systems and data processingReduce system costHydrodynamic testingPolarizerCMOS
The invention discloses a three-dimensional flow field image measurement device and method adopting a single lens, which are characterized in that a polarized light source is used for illuminating a flow field to be detected; light from a camera lens is divided into two paths through a light splitting prism and polaroids are respectively used for carrying out polarization detection for the two paths; two CCDs (Charge Coupled Device) or CMOS (Complementary Metal-Oxide-Semiconductor Transistor) image sensors are respectively used for imaging; a relative gray level of a corresponding tracer particle in two pictures can be used for judging whether the tracer particle is located in front of a focusing plane or in back of the focusing plane; the distance between the position of the tracer particle and the focusing plane is computed according to the size of a defocusing amount of the tracer particle of the single picture, so as to only determine a three-dimensional position of the tracer particle; and a movement fuzzy parameter is combined to further obtain a three-dimensional movement speed of the tracer particle, namely the information of a three-dimensional flow field is obtained. The three-dimensional flow field image measurement device and method adopting the single lens have the beneficial effects that the three-dimensional measurement of a transient flow field can be realized by only one camera lens, a measurement system and a data processing process are simplified, and the system cost is reduced.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
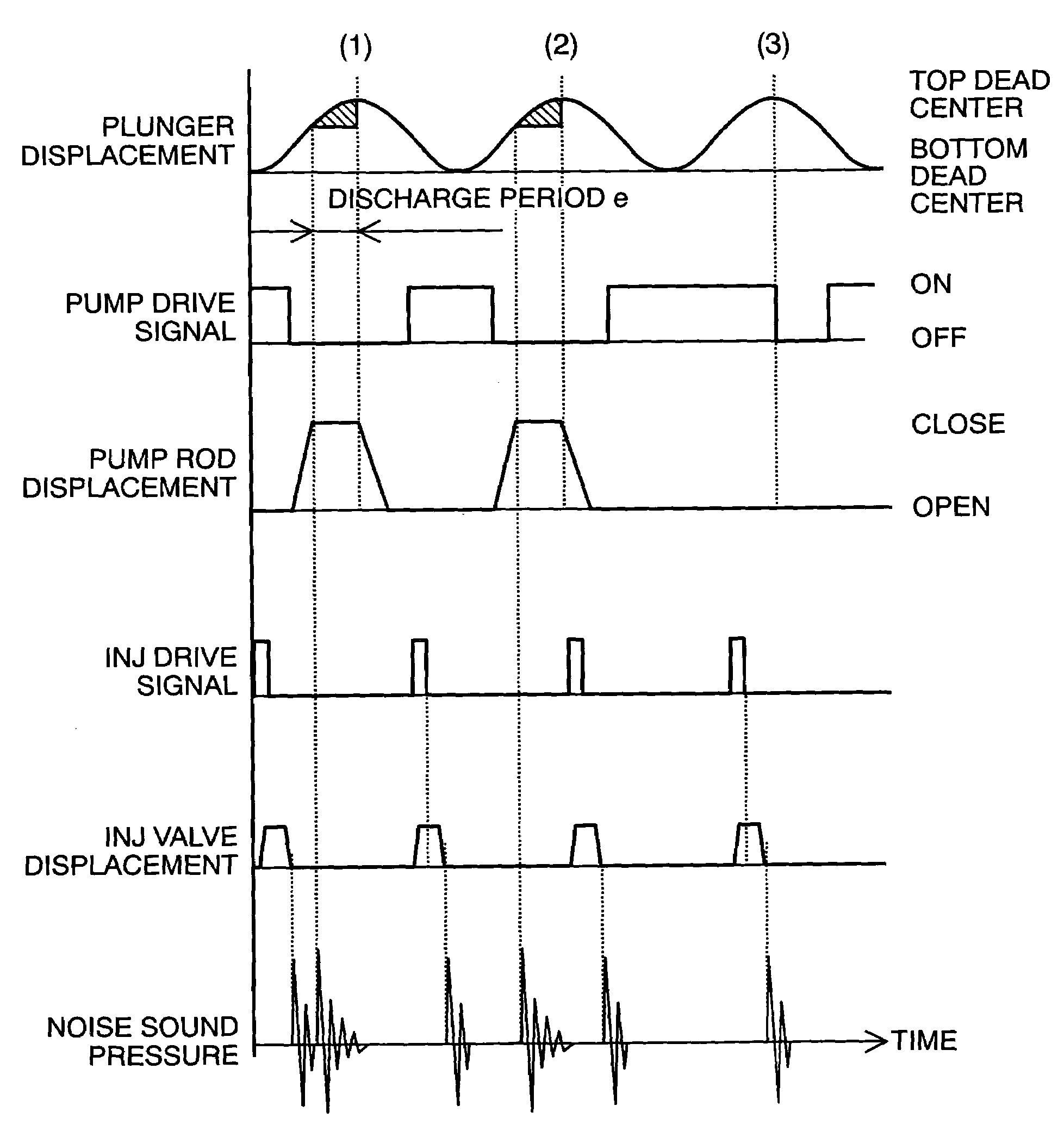
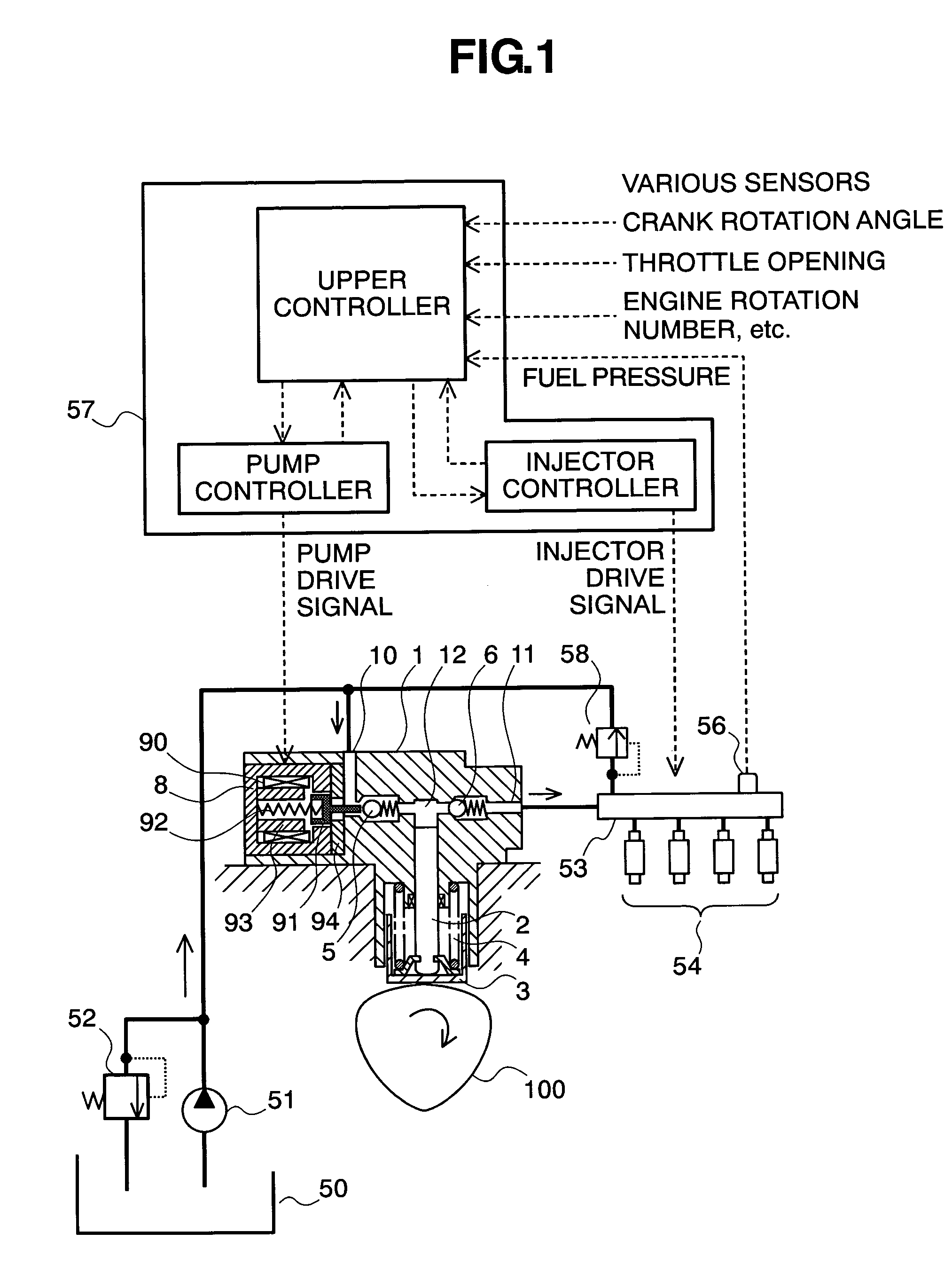
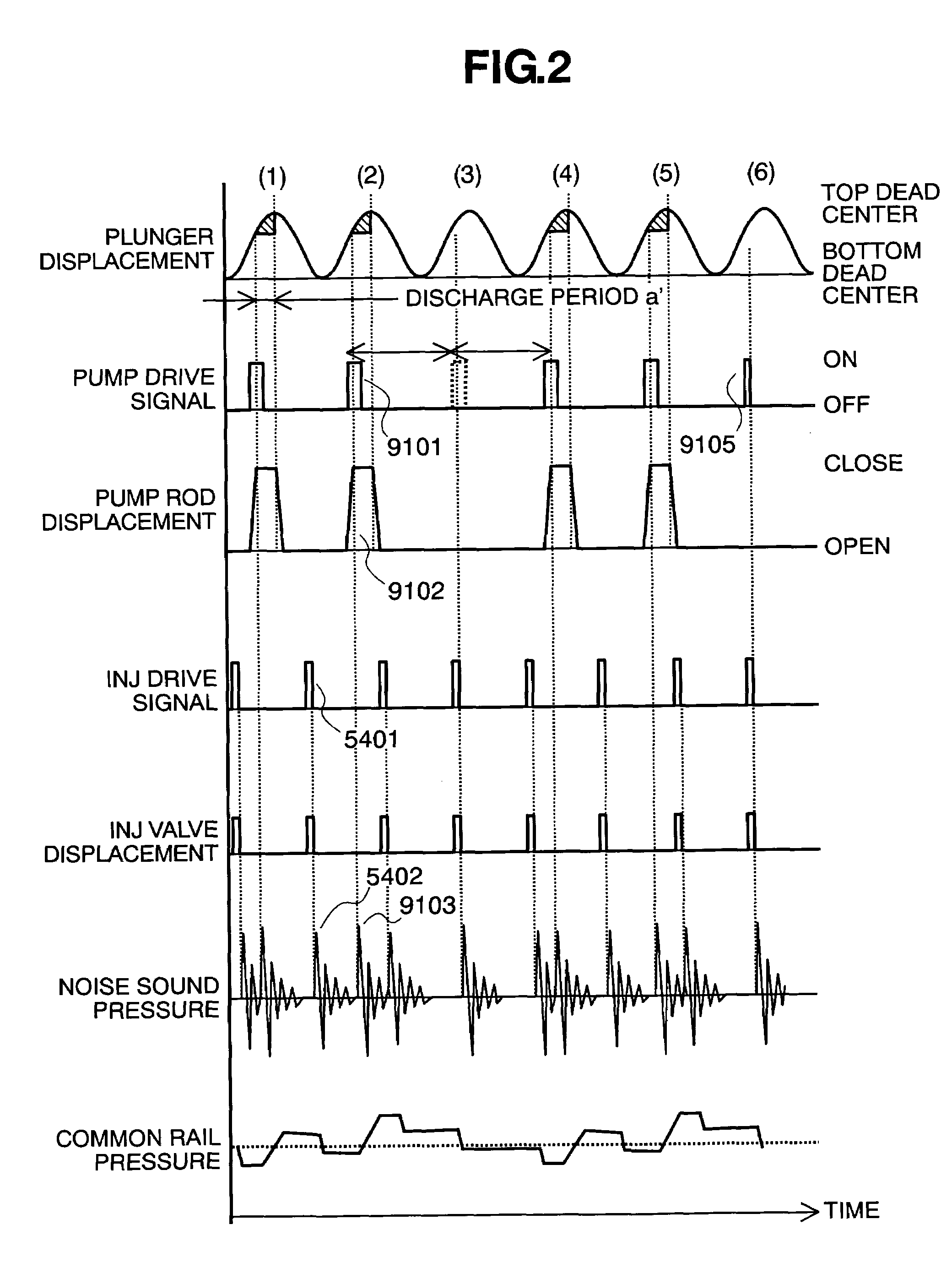
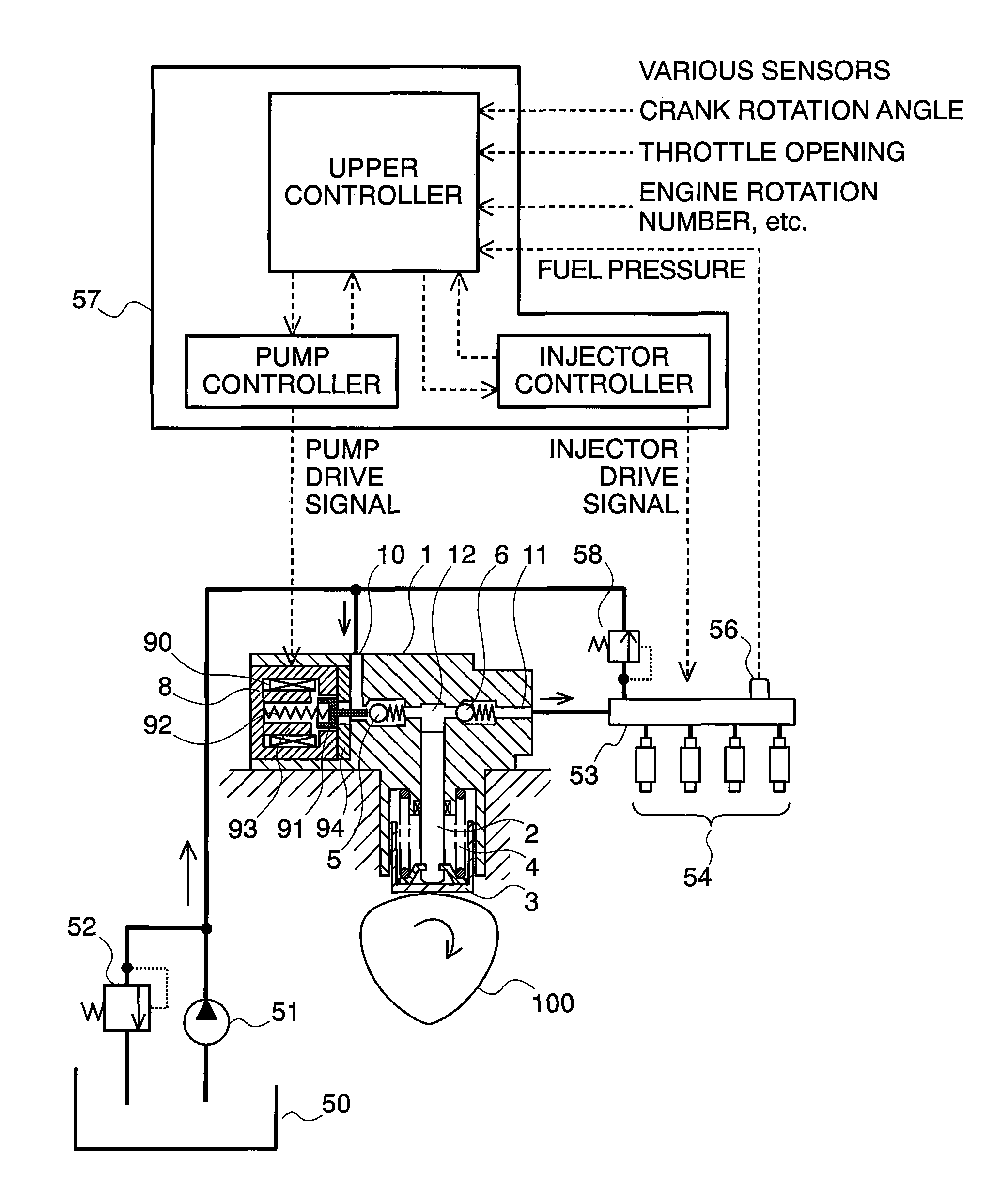
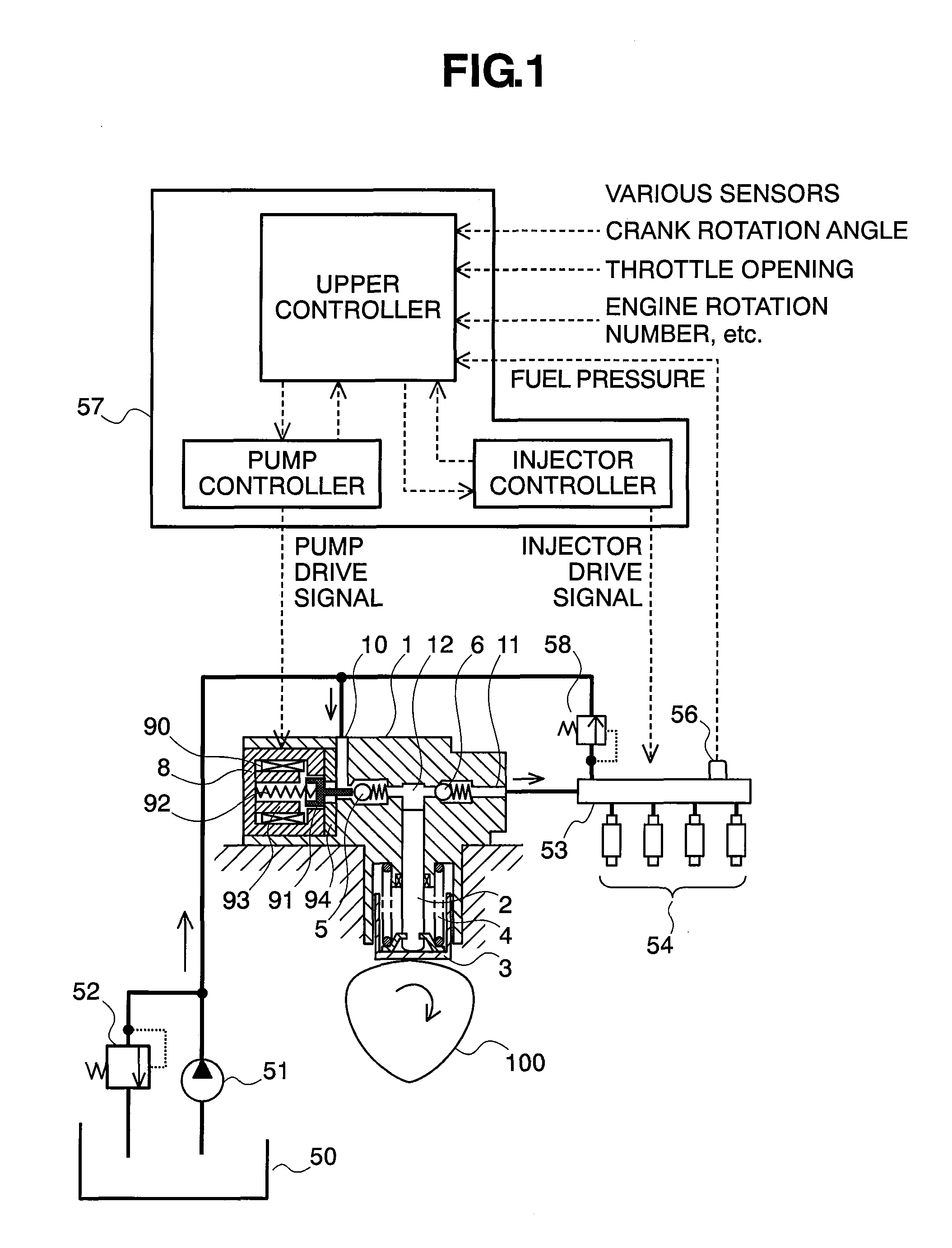
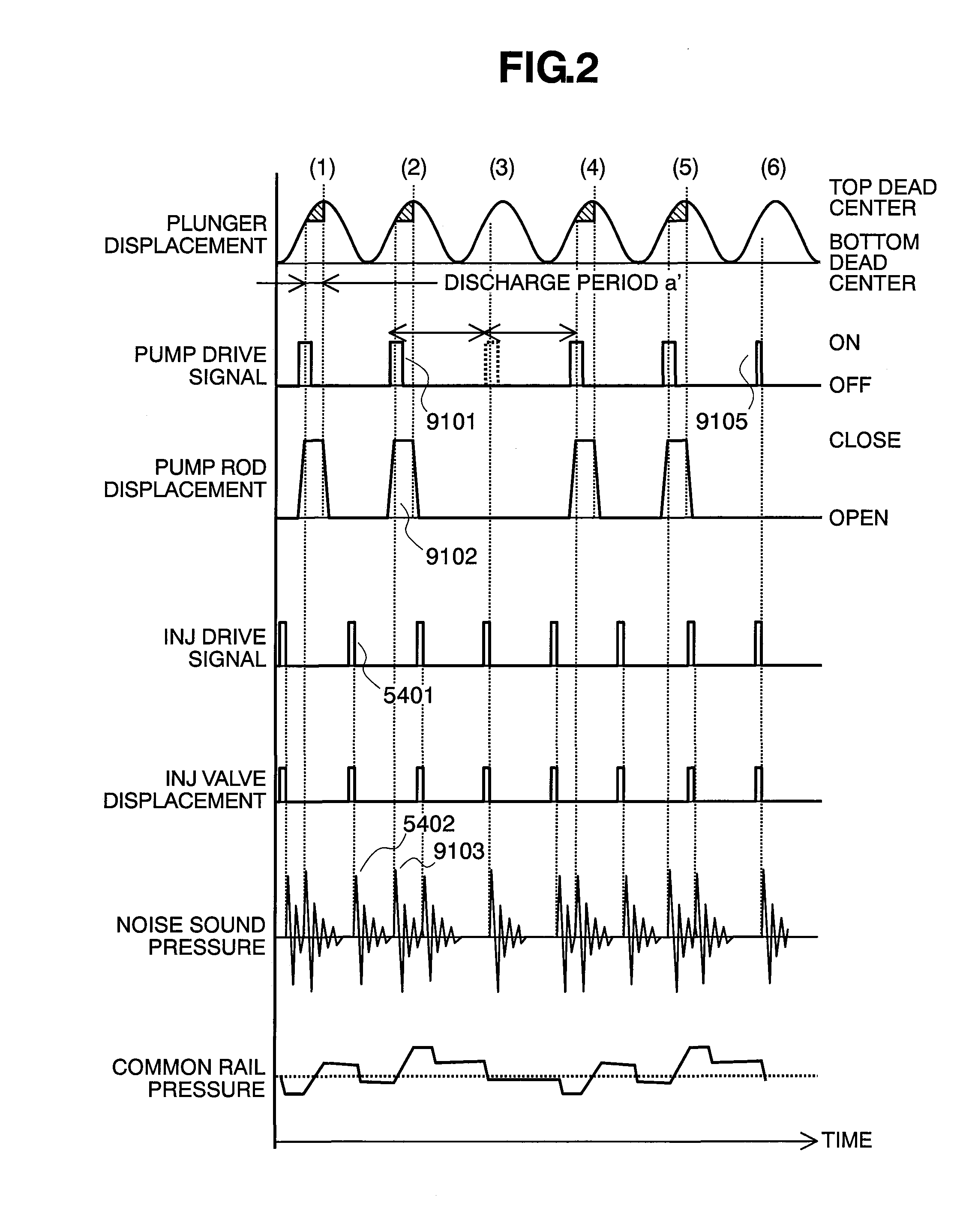
Controlling apparatus of variable capacity type fuel pump and fuel supply system
InactiveUS7559313B2Avoid synchronizationEliminate duplicationElectrical controlNoise reducing fuel injectionEngineeringFuel supply
Owner:HITACHI LTD
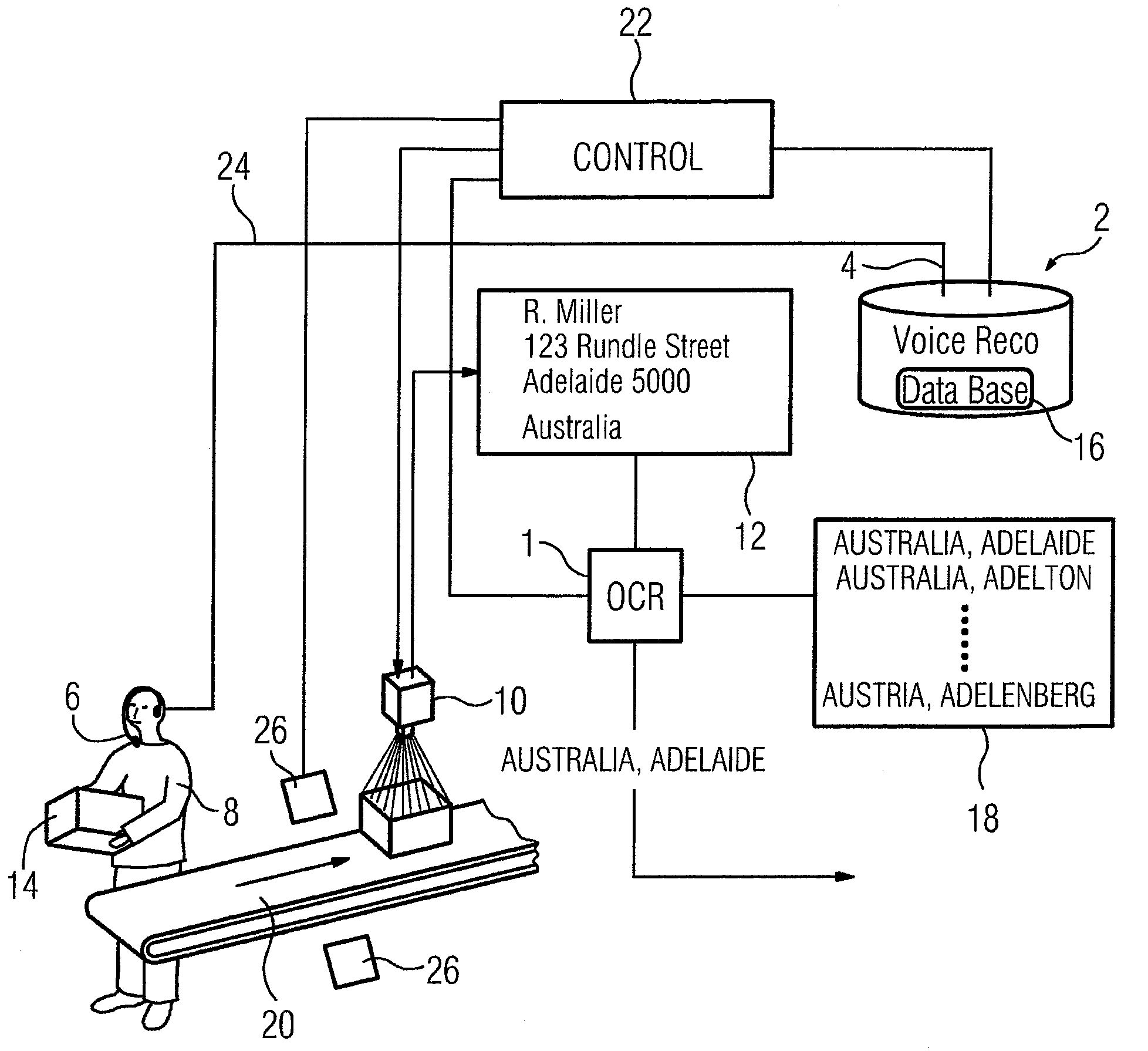
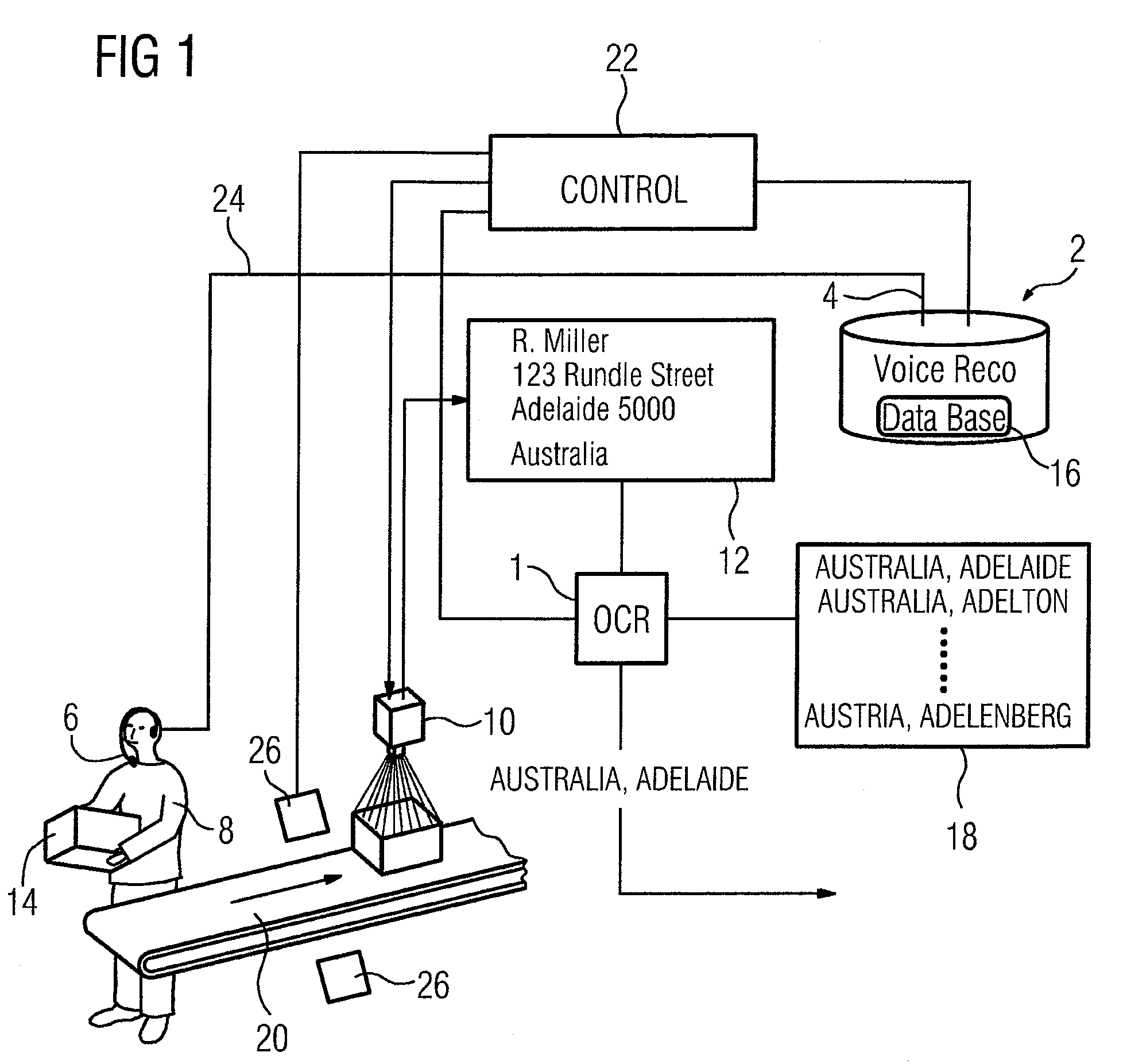
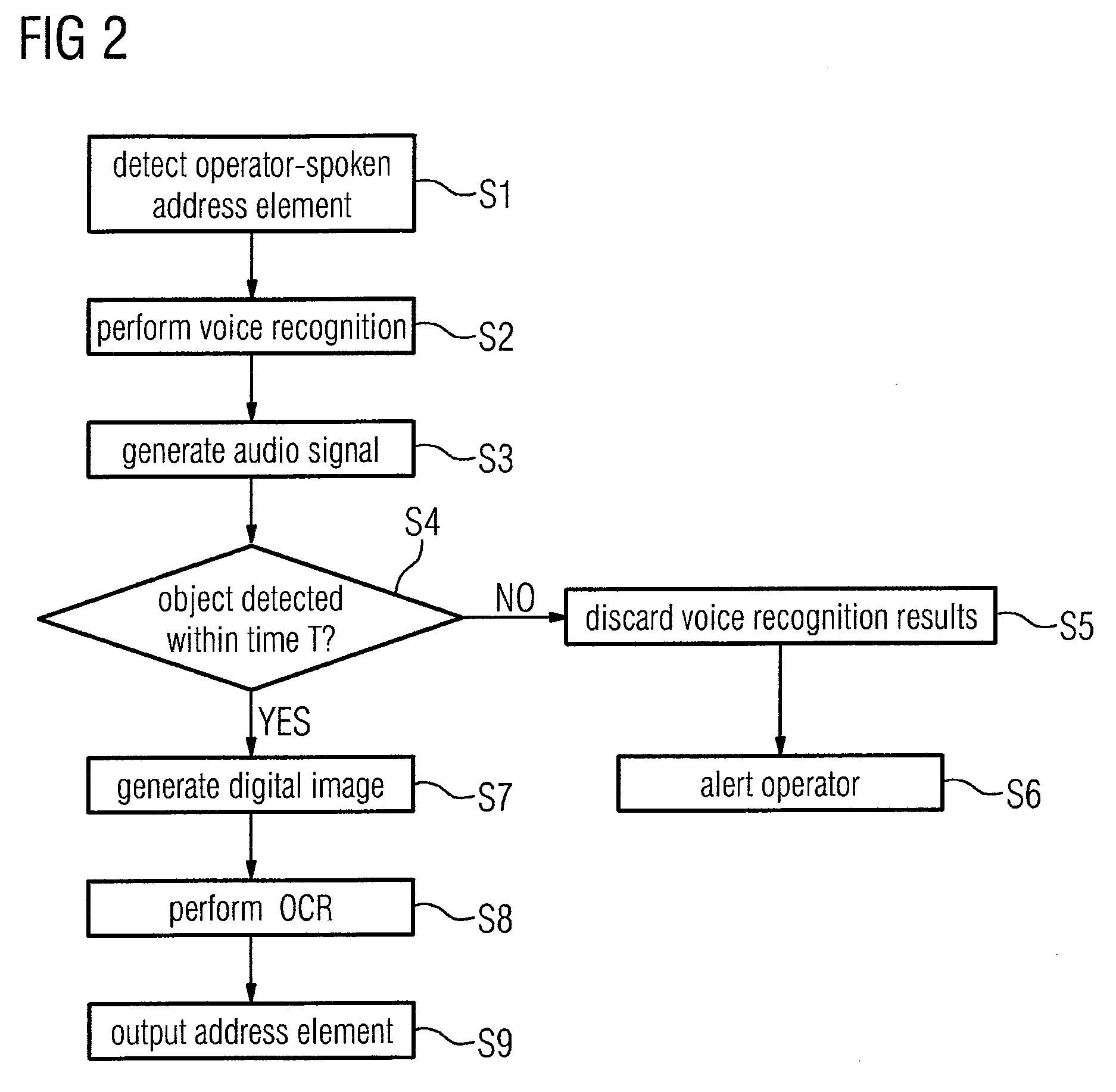
System and Method for Sorting Objects Using OCR and Speech Recognition Techniques
InactiveUS20090110284A1Reduce error rateEffective and accurateCharacter and pattern recognitionSpeech recognitionCharacter recognitionOptical character recognition
To perform character recognition on an object for automatic processing of the object in a processing system, where the object contains at least one character string of processing information, a character string spoken by an operator is processed by a speech recognition procedure to generate a candidate list containing at least one candidate corresponding to the operator-spoken character string. The candidate list and a digital image of an area containing the processing information are made available for an optical character recognition procedure. The OCR procedure is performed on the digital image in coordination with the candidate list to determine if a character string recognized by the OCR procedure performed on the digital image corresponds to a candidate in the candidate list. Any such corresponding candidate is outputted as the character string on the object.
Owner:SIEMENS AG
Controlling Apparatus of Variable Capacity Type Fuel Pump and Fuel Supply System
InactiveUS20090241908A1Avoid synchronizationEliminate duplicationElectrical controlNoise reducing fuel injectionFuel supplyFuel pump
A controlling apparatus of a variable capacity type fuel pump, for avoiding noises caused due to drive of the fuel pump and noises caused due to drive of injectors from overlapping or duplicating with each other in the timing thereof, wherein signals for driving the pump reduced, or the timing thereof is shifted forward / backward, within a specific timing where the o overlapping can be prospected, or a specific timing where they are determined to overlap or duplicate with each other.
Owner:HITACHI LTD
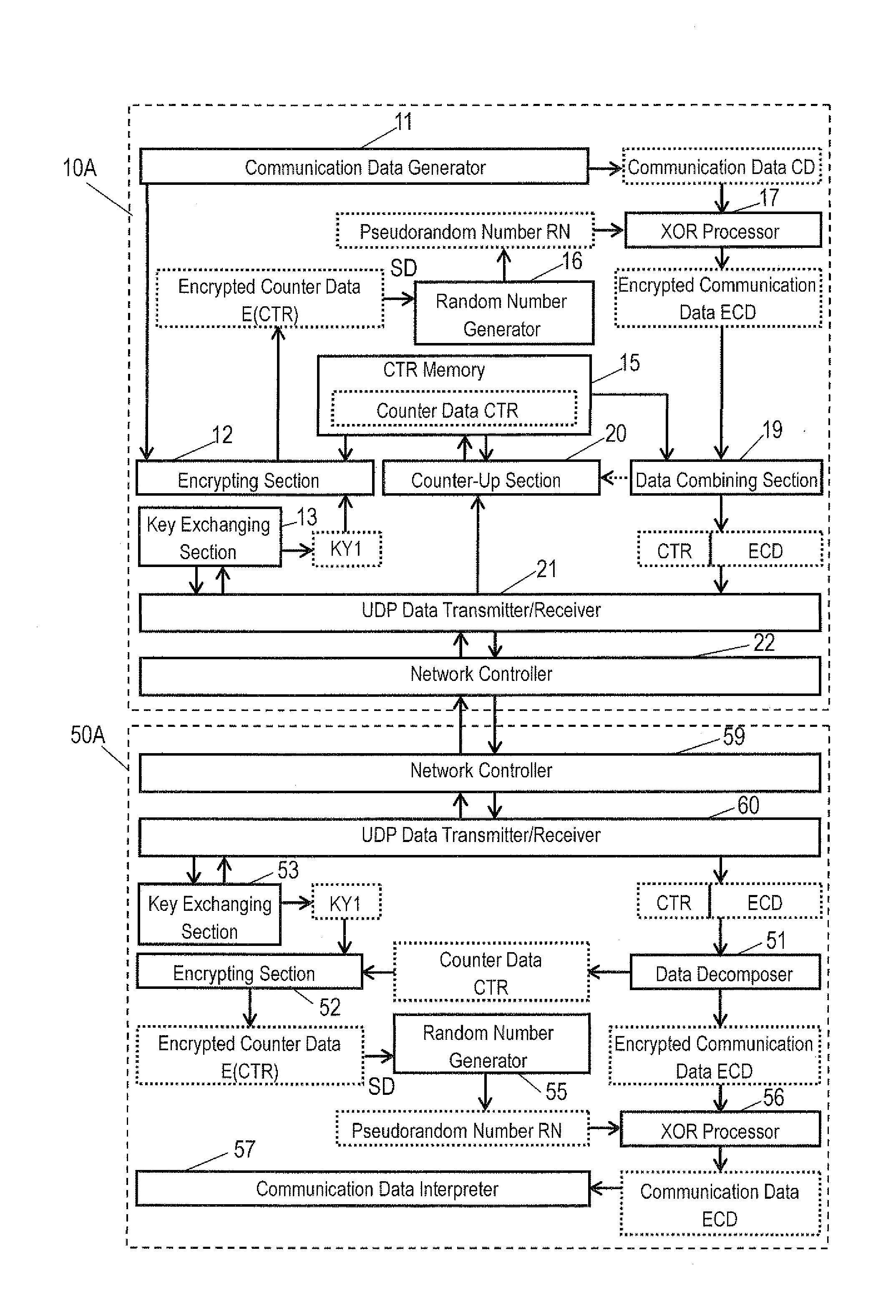
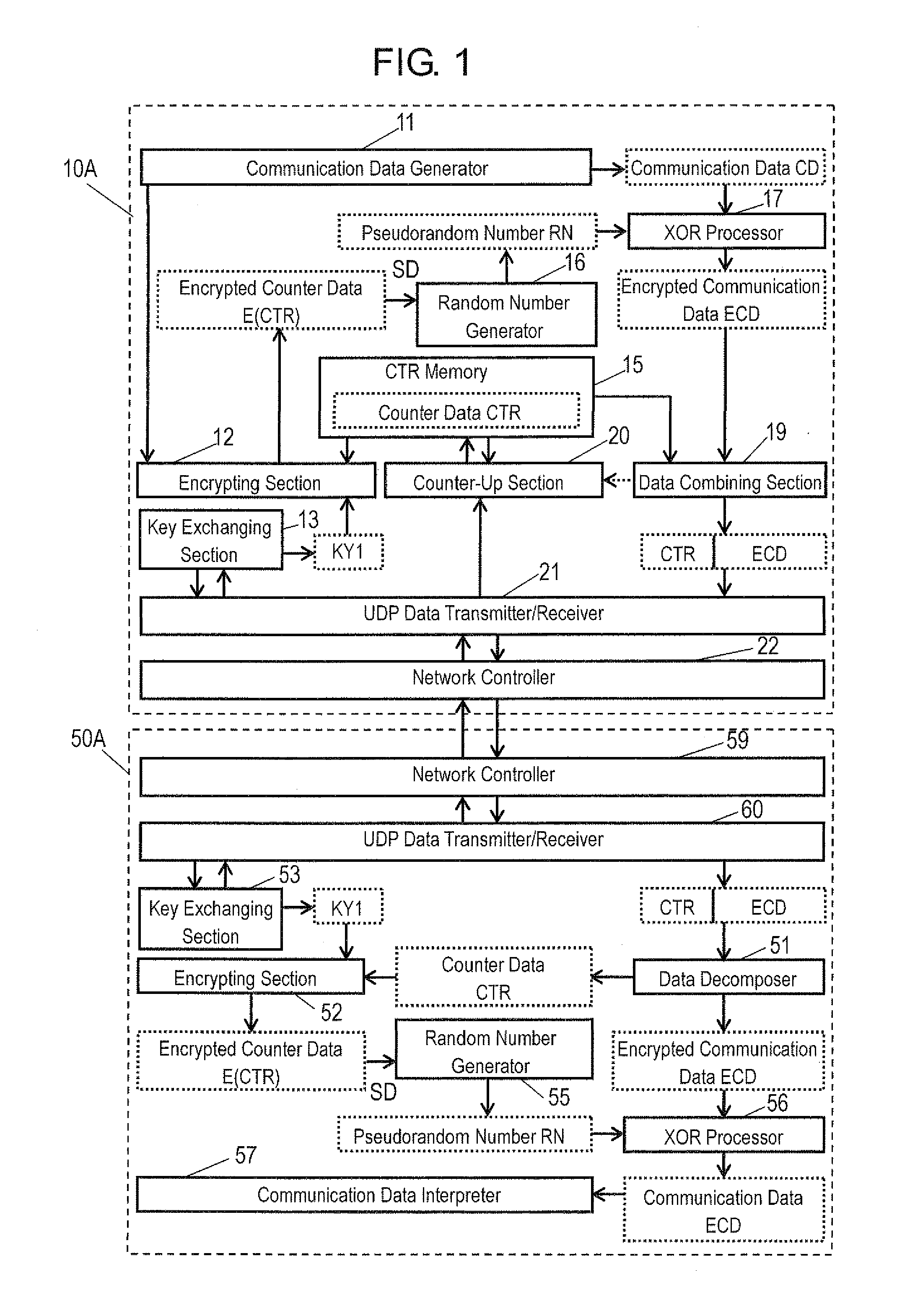
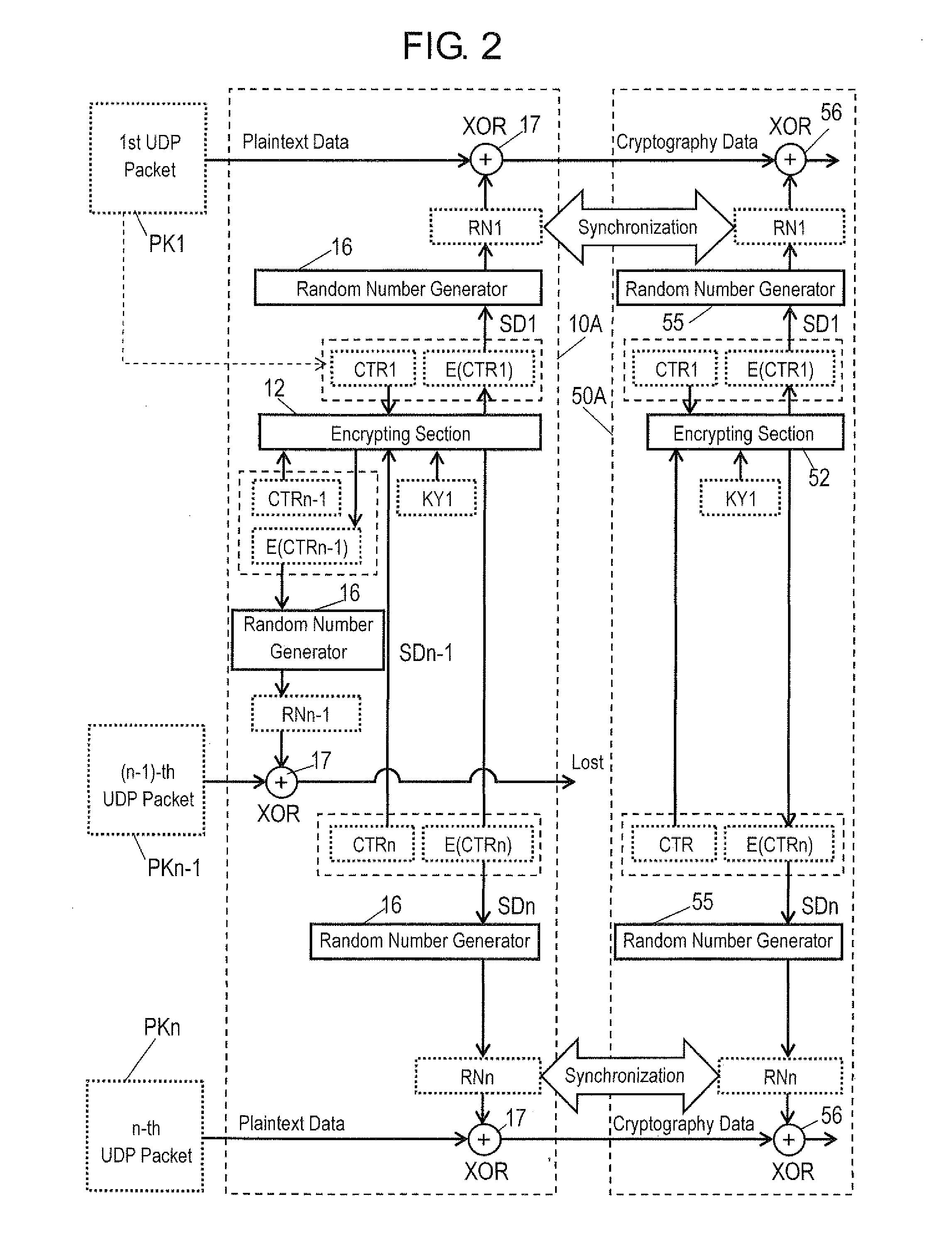
Decrypting apparatus, encrypting apparatus, decrypting method, encrypting method, and communication system
ActiveUS20120201383A1Avoid synchronizationSynchronising transmission/receiving encryption devicesSecret communicationData packCommunications system
A decrypting apparatus for decrypting cryptography data included in a packet includes a receiver, a key generator, and a decrypting section. The receiver receives a packet transmitted from an encrypting apparatus that executes an encrypting process. The key generator generates a key used for the encrypting process. The decrypting section decrypts cryptography data included in the packet received by the receiver with using the key generated by the key generator. In the decrypting apparatus, the packet received by the receiver includes packet information used for generating the key. The key generator generates the key with using the packet information.
Owner:PANASONIC CORP
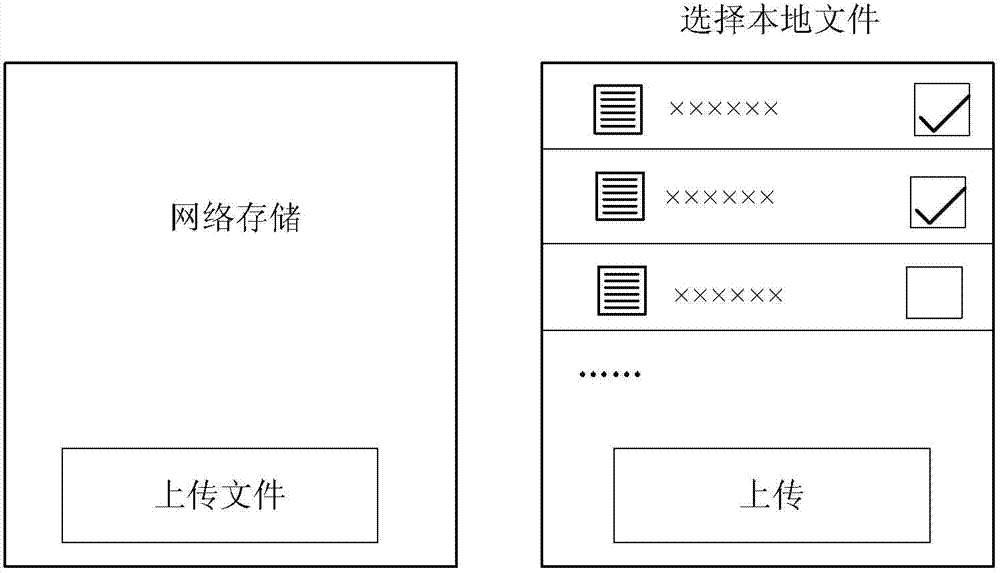
Document transmission method and device between terminal device and network server and terminal device
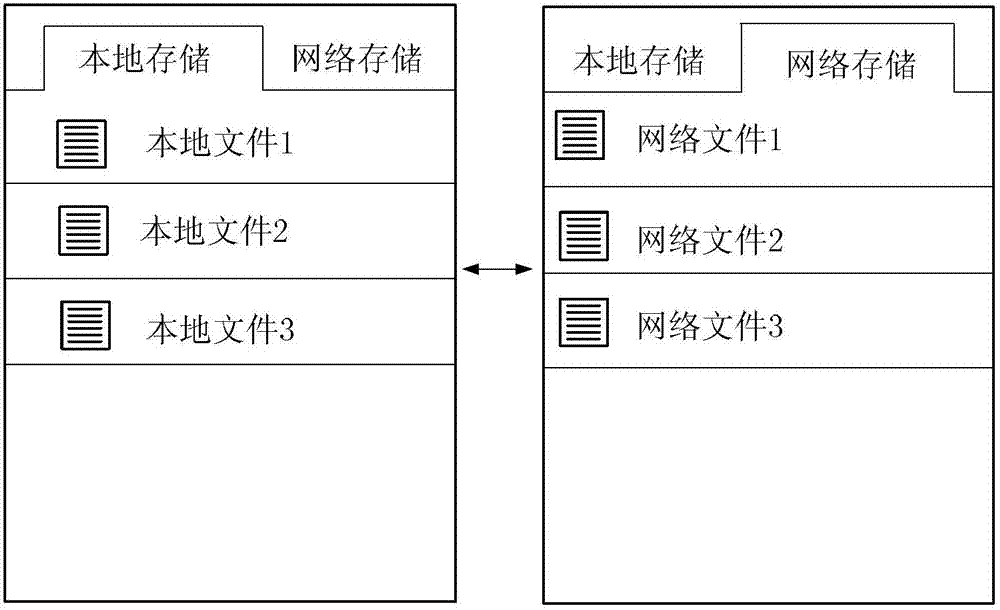
ActiveCN102957751AEasy to uploadEasy to downloadSubstation equipmentTransmissionTerminal equipmentComputer terminal
The invention provides a document transmission method between a terminal device and a network server. After an instruction that a user opens an interface is received, two windows are displayed on the terminal device simultaneously, a terminal file directory and a network terminal file directory are displayed respectively; or two tabs are provided on the same interface of the terminal device to correspond to the terminal file directory and the network terminal file directory respectively; the instruction that the user selects one of the two tabs is received, the file directory corresponding to the selected tab is displayed, and then the file directory corresponding to the other tab is hidden; after the instruction that the user selects a file from the terminal file directory or the network terminal file directory is acquired, the corresponding file is selected and operated assigned by the user, and then jumped to the terminal file directory or the network terminal file directory; and after the instruction for transmitting by the user is received, the selected file is transmitted to the network terminal or the terminal. The invention also provides a document transmission device between the terminal device and the network server, and the terminal device comprising the document transmission device.
Owner:BEIJING KINGSOFT CLOUD TECH CO LTD +1
Method for constructing cloud SCADA system based on Spring cloud micro-service architecture
InactiveCN110134374AFail-fast callAvoid synchronizationSoftware designSoftware simulation/interpretation/emulationSCADAService provider
According to a method for constructing a cloud SCADA system based on the Spring cloud micro-service architecture, the SCADA system is developed according to the Spring cloud micro-service architecture, so that the SCADA system can be conveniently deployed on a cloud server. The method comprises the following steps: 1, creating a parent project; 2, constructing service discovery and registration; 3, achieving service consumption and load balance; 4, realizing the service fusing; 5, creating configuration center service; 6, setting an API gateway; 7, performing distributed transaction consistency management; and 8, constructing the micro-service by using the Docker. The Spring Boot is used for developing the application micro-service, and the functions of service discovery, service consumption, service fusing, API gateway, unified configuration center, distributed transaction consistency management and container construction can be effectively achieved.
Owner:NANJING GREEN NEW ENERGY RES INST CO LTD
Method and system for managing metadata
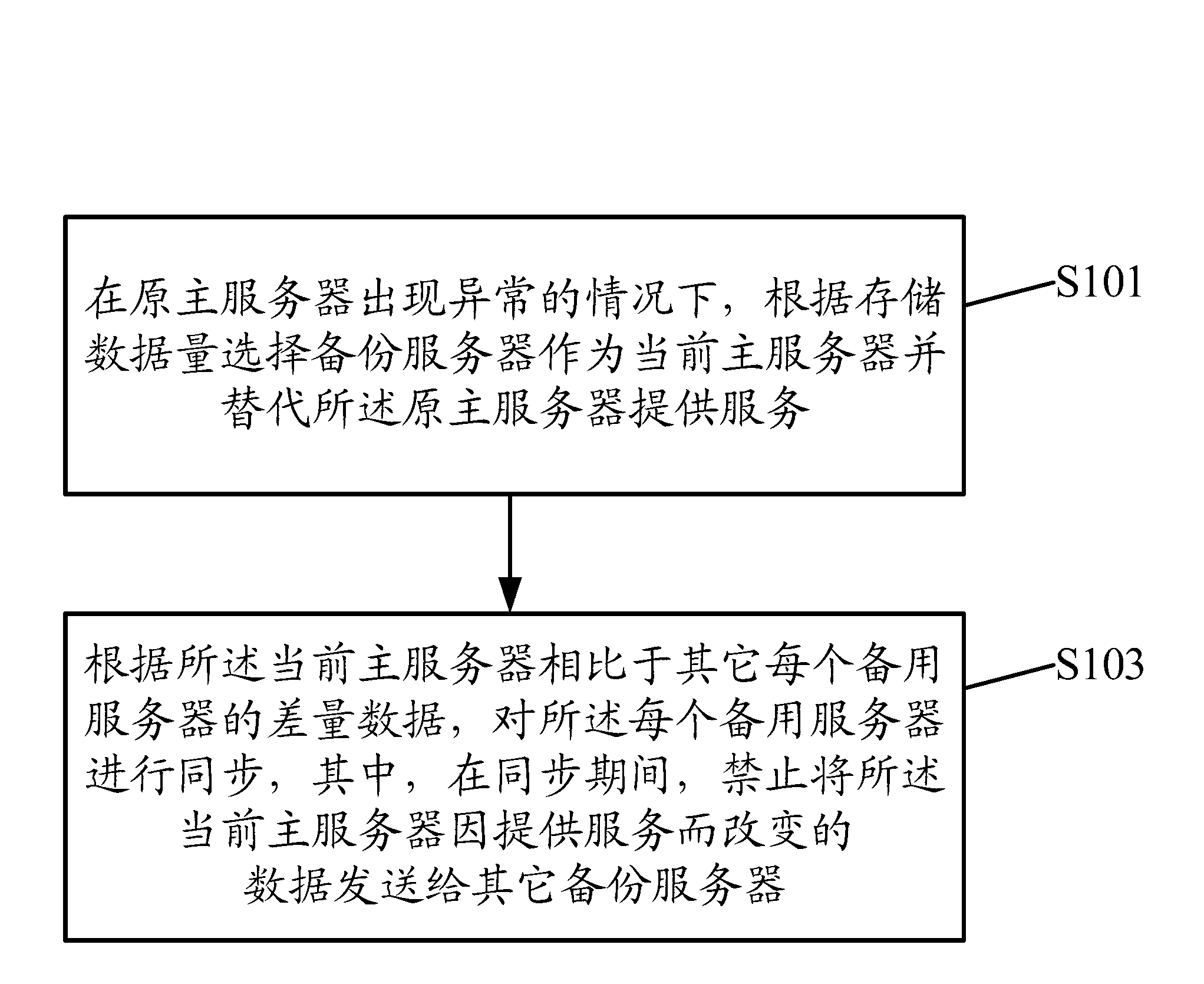
InactiveCN103235748AAchieve replacementAvoid synchronizationRedundant hardware error correctionData synchronizationDependability
The invention discloses a method and a system for managing metadata. The method includes that under the condition that an original main server is abnormal, a backup server is selected to be used as a current main server and replace the original main server to provide service according to storage data amount; and according to residual quantity data of the current main server compared with other standby servers, synchronization is conducted on each standby server. In a synchronization period, changed data of the current main server due to service providing is forbidden to be sent to other backup servers. By selecting the current main server and providing the service and by conducting data synchronization on the current main server and the backup servers, the current main server can conduct normal business takeover so as to achieve replacing among the main server and the backup servers effectively. In the synchronization period, the changed data caused by service providing is forbidden to be sent so as to prevent out-of-order data synchronization, the stability and the reliability of the system are guaranteed, and experience of users is improved.
Owner:DAWNING INFORMATION IND BEIJING
Misguiding encryption method capable of correcting pseudorandom sequence
ActiveCN102360414AAvoid synchronizationHeavy calculationDigital data protectionComputer hardwareCiphertext-only attack
The invention discloses an encryption method with a misguiding function, aiming at attacks such as secret key stealing, secret key holder seizing, rubber-hose cryptanalysis, ciphertext-only attack and the like. A pseudo secret key can be easily obtained through encryption with the method disclosed by the invention, thus a password analyzer can be misguided, the misguiding is determined by an internal secret key and comprises information for generating a secret key flow and correction information, and the misguiding effectiveness can be enhanced according to actual demands by using the correction information. For a special processing mode adopted by signs in a document, the specified signs can not be confused when possibly occurring in a text. A keyword database is needed during encrypting, internal encryption is subjected to keyword expansion by using the database, and the traditional encryption method is adopted in external encryption. The invention does not need the support of the database during encrypting so as to avoid the problem of synchronization of the database. The invention has a certain use value in the encryption application of various occasions, especially military.
Owner:广西创美信息技术有限公司
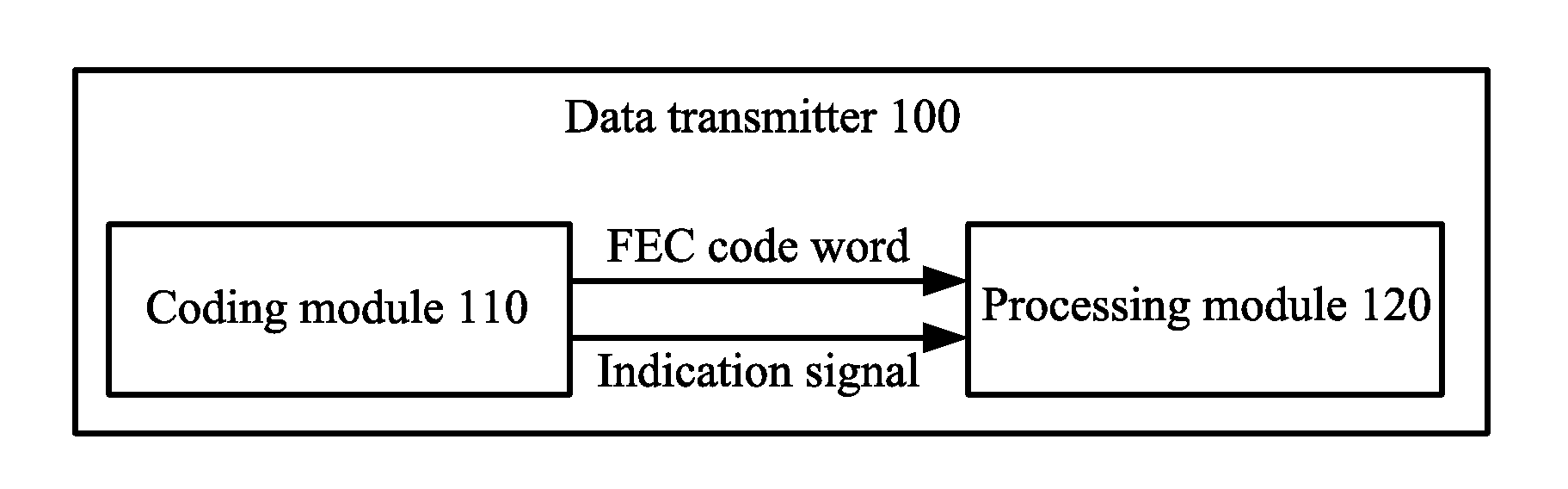
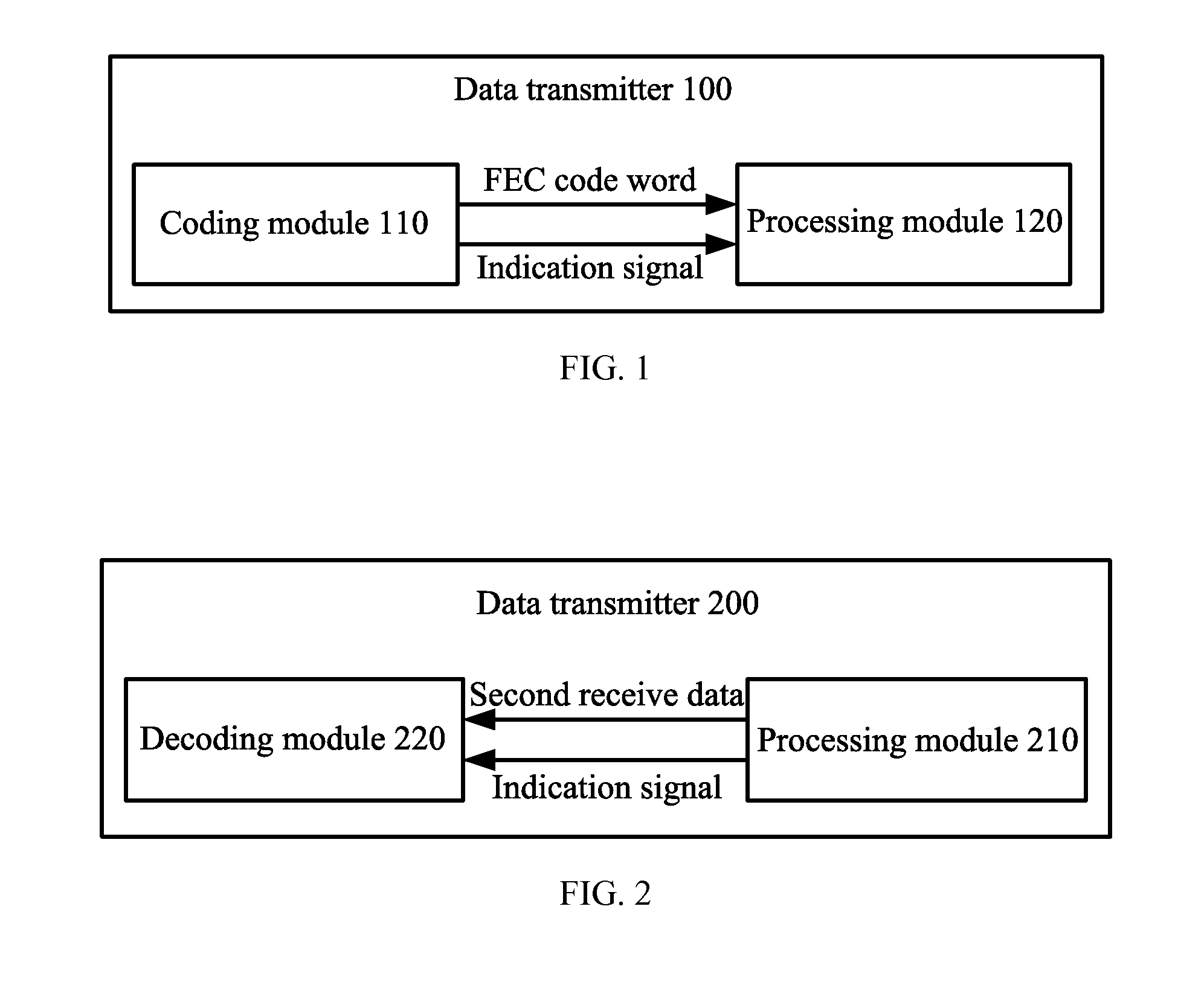
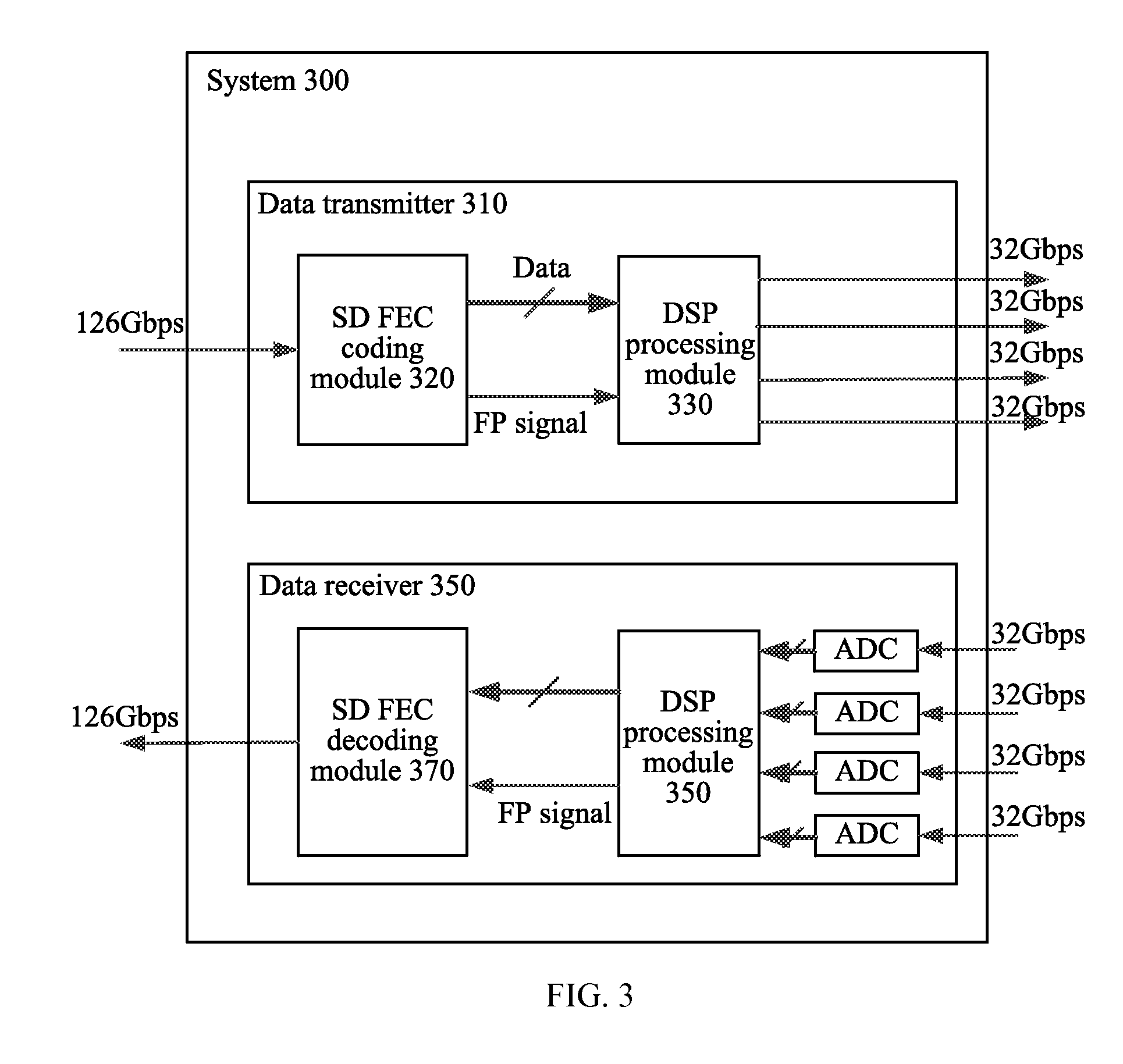
Data Transmitter, Data Receiver, and Frame Synchronization Method
InactiveUS20140237323A1Increase overheadEasy to useError preventionCode conversionCode moduleForward error correction
Embodiments of the present invention provide a data transmitter, a data receiver, and a frame synchronization method. The data transmitter includes a coding module and a processing module. The coding module is configured to perform forward error correction FEC coding on sent data to obtain an FEC code word, and to output the FEC code word and an indication signal for indicating a boundary position of the FEC code word to the processing module. The processing module is configured to insert a training sequence into the FEC code word according to the indication signal, so that a data receiver determines the boundary position of the FEC code word according to the training sequence.
Owner:HUAWEI TECH CO LTD
Apparatus and method for detecting packet of zero-padded OFDM signal
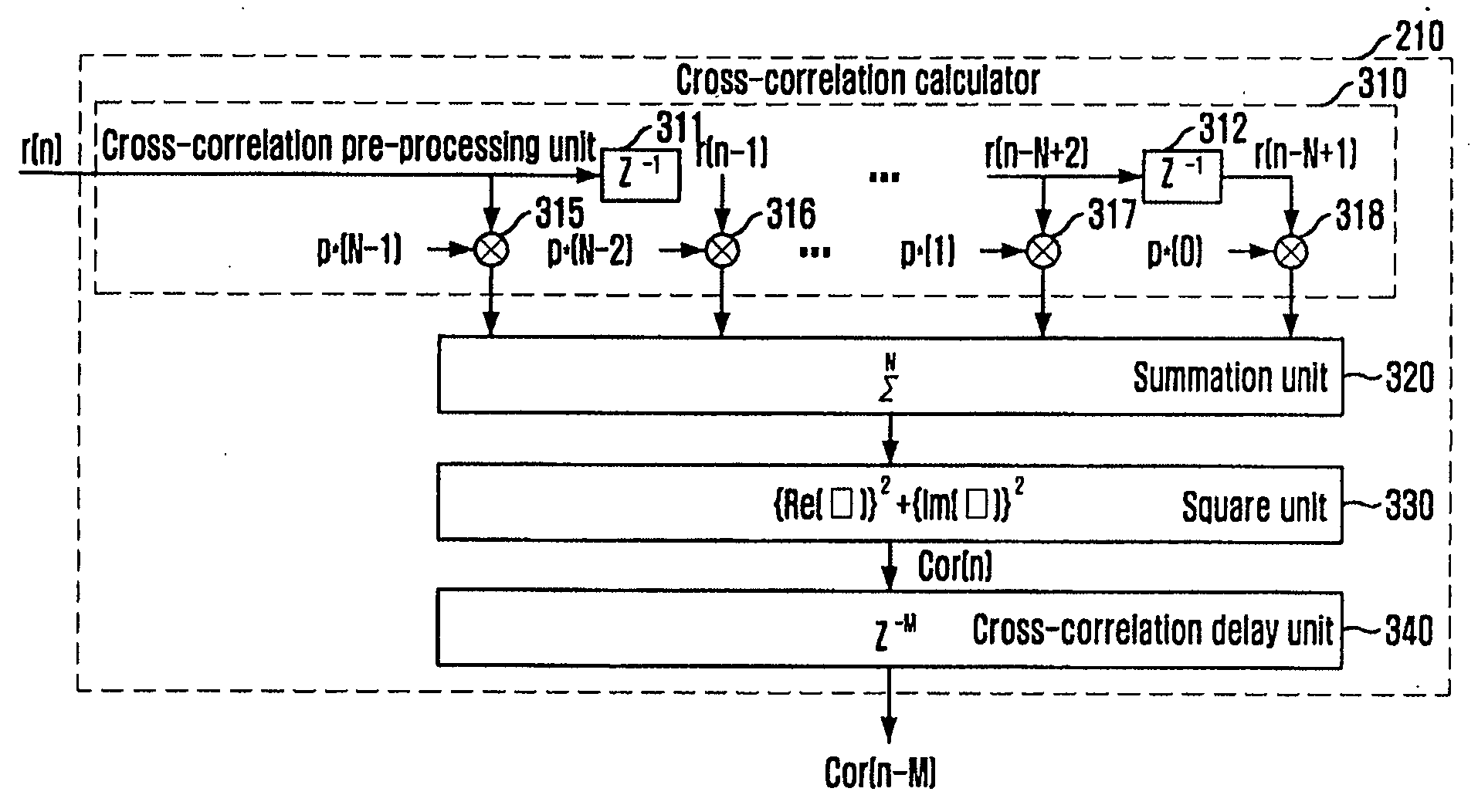
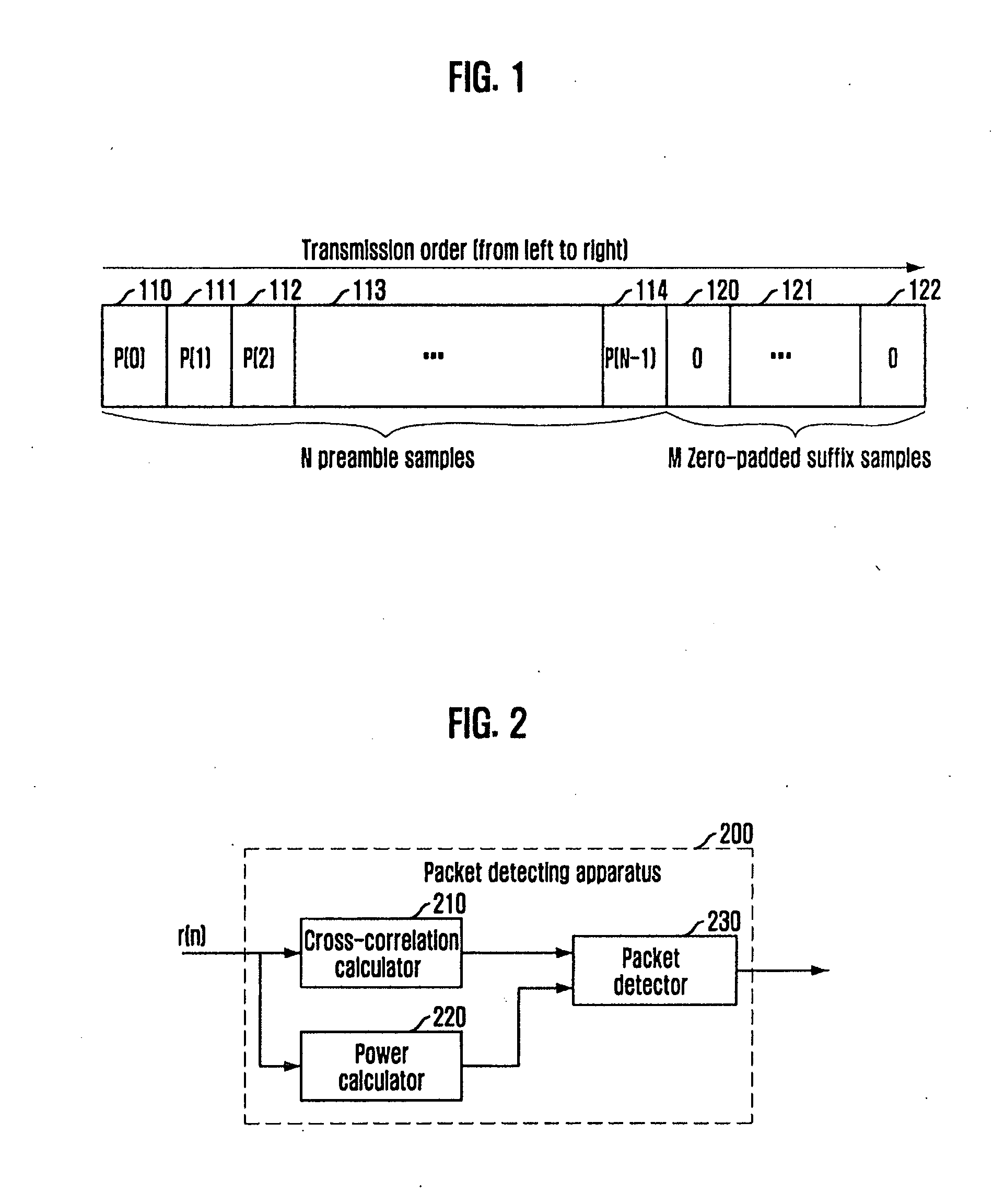
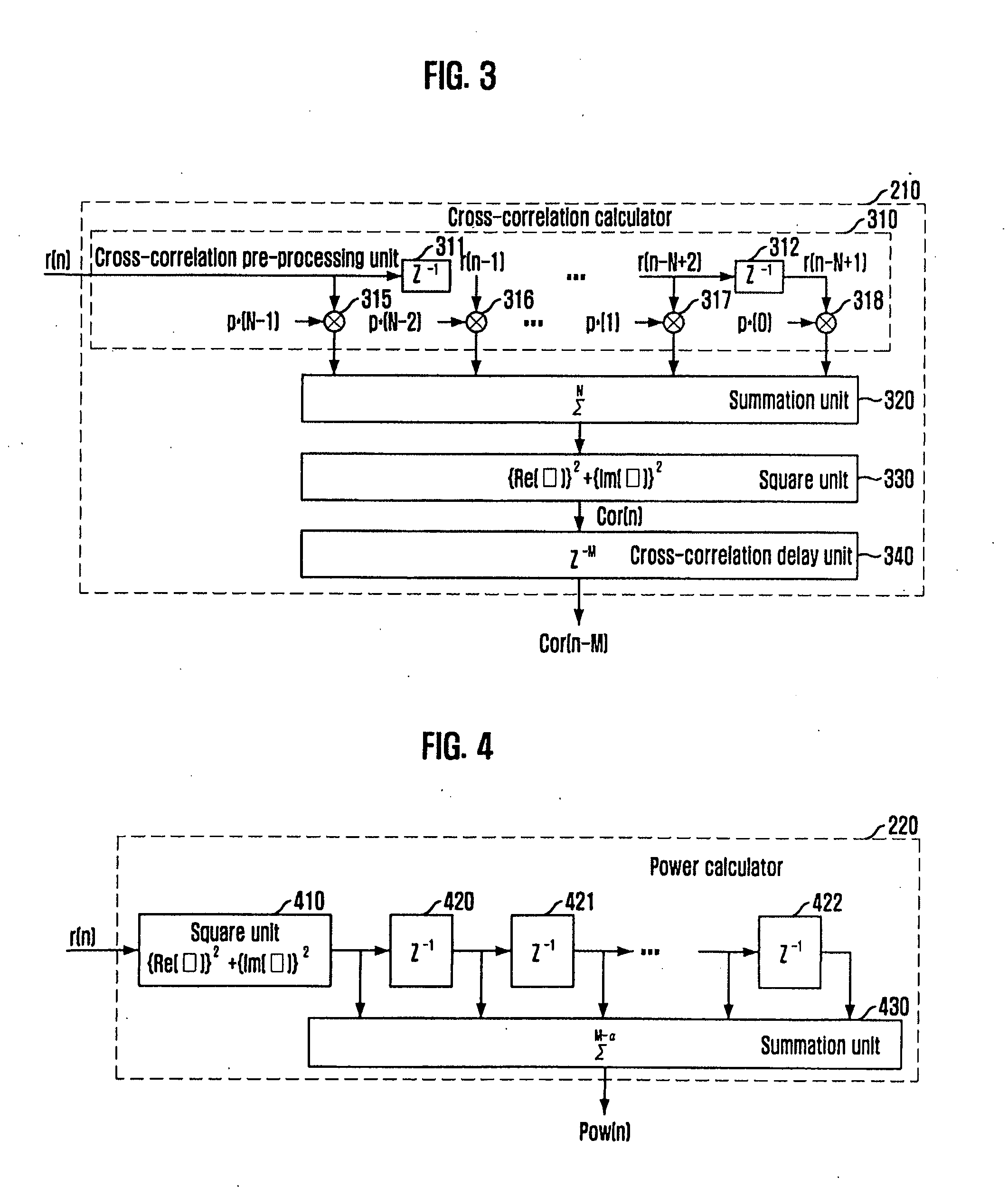
InactiveUS20090147667A1Improve detection rateAvoid synchronizationMulti-frequency code systemsOrthogonal multiplexFalse alarmSignal delay
Provided is an apparatus and method for detecting a packet of a zero-padded OFDM signal, which are capable of determining if a packet exists in a reception (RX) signal by comparing a cross-correlation value of an OFDM signal delayed by a predetermined sample time, e.g., a zero-padded sample time, with a power value of the RX signal, thereby increasing a packet detection probability and preventing a false alarm. The packet detecting apparatus includes: a cross-correlation calculator for calculating a cross-correlation value of a reception signal received from the outside and delaying the calculated cross-correlation value by a predetermined sample time; a power calculator for calculating a power value of the reception signal; and a packet detector for determining if a packet exists in the reception signal by comparing the delayed cross-correlation value with the calculated power value, and detecting the corresponding packet.
Owner:ELECTRONICS & TELECOMM RES INST
Throttle device
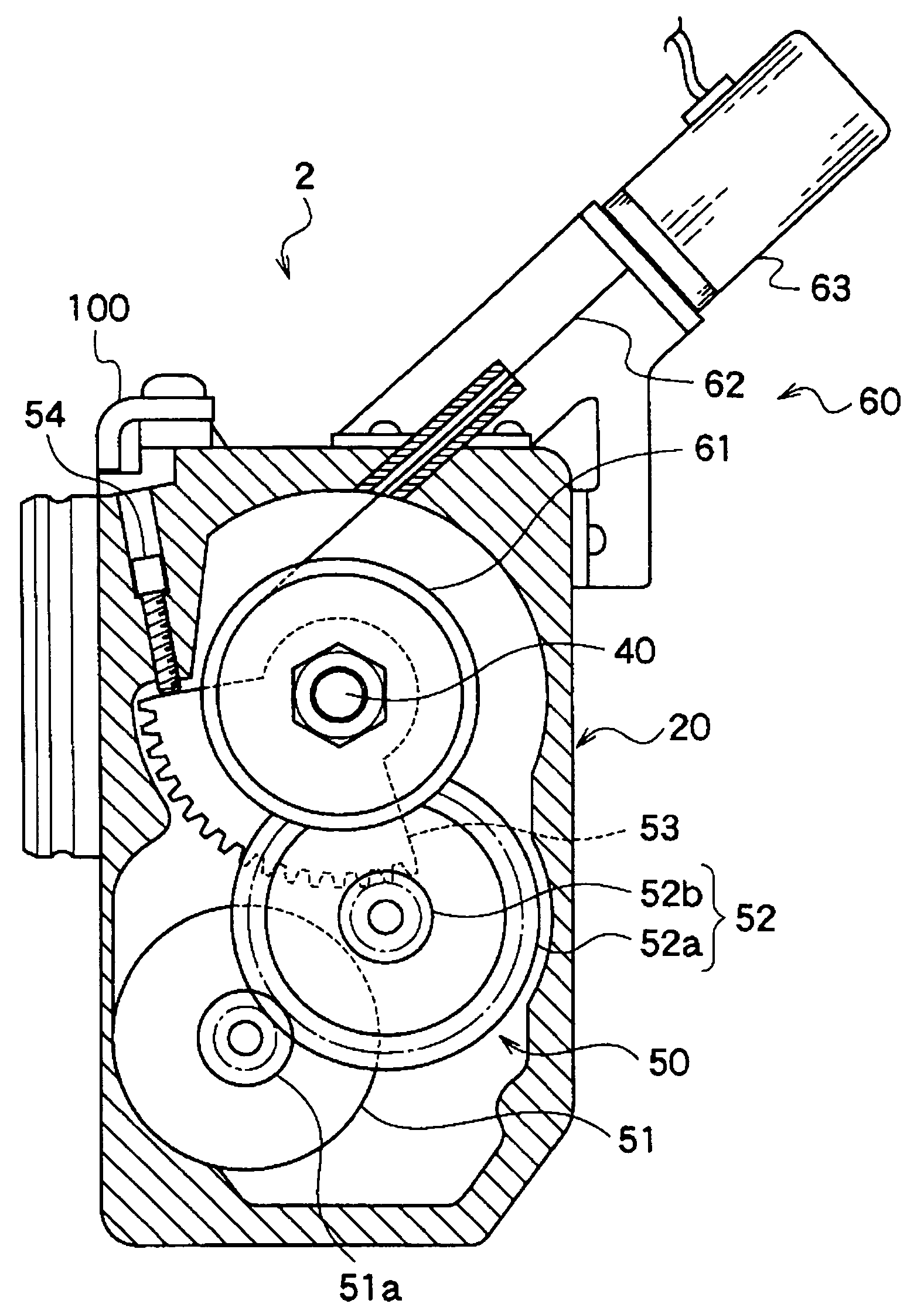
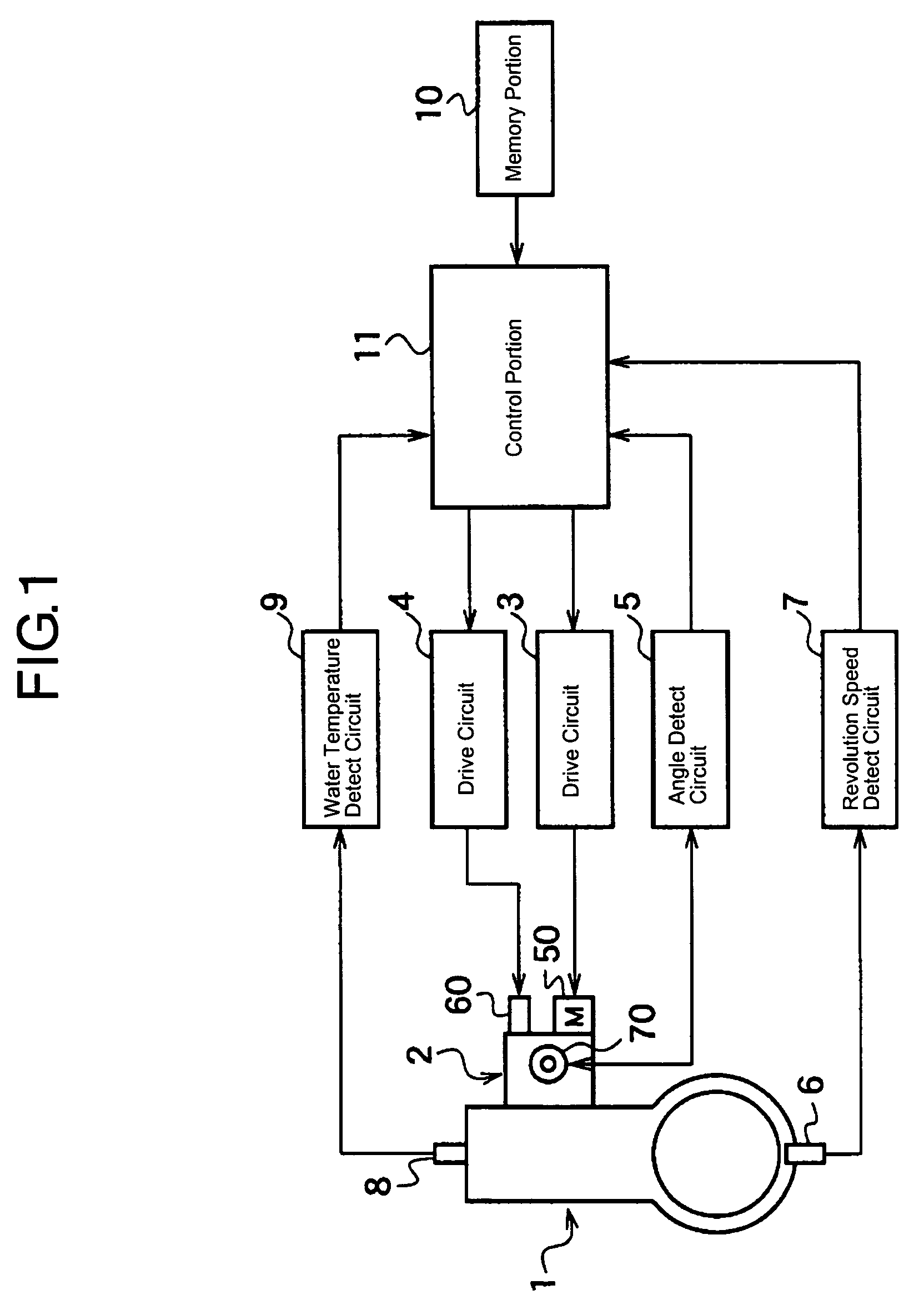
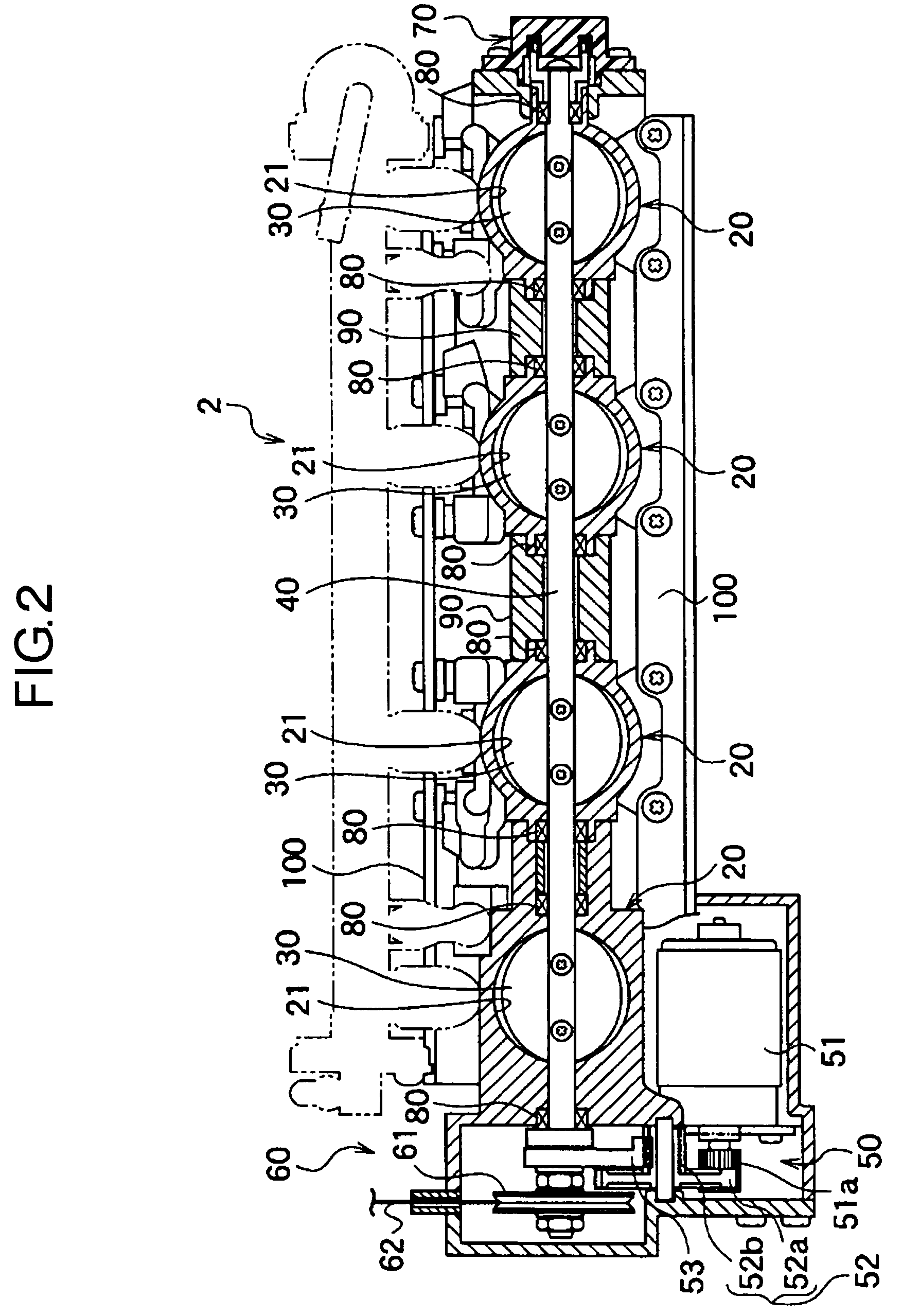
InactiveUS7156074B2Process stabilityAvoid synchronizationEngine controllersMachines/enginesRest positionSpring force
With the throttle apparatus of the present invention having a throttle valve 30 disposed at an intake passage, a throttle shaft 240 to open and close the throttle valve 30, a DC motor 51 to drive the throttle shaft 40, and so on, a second drive means 60 is disposed to exert return force to the throttle shaft 40 only for returning the throttle valve 30 to the rest position. With this structure, since return force is not exerted with a normal operation, load to the DC motor 51 is decreased, and an open-close operation can be preformed smoothly. By returning the throttle valve to the rest position utilizing other means than spring force, load to the motor is decreased, and open-close operation is smoothed.
Owner:MIKUNI CORP
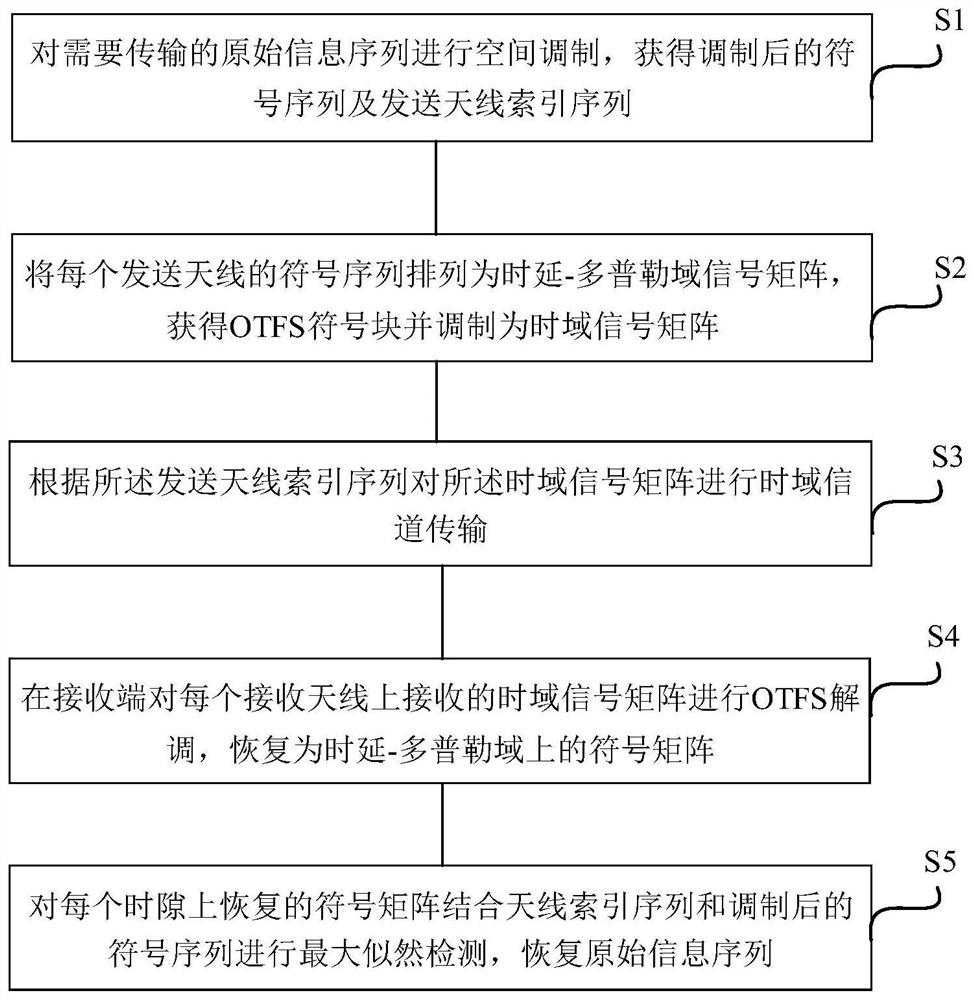
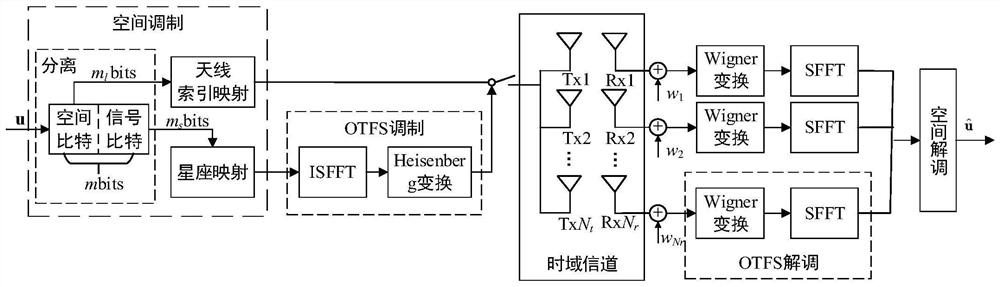
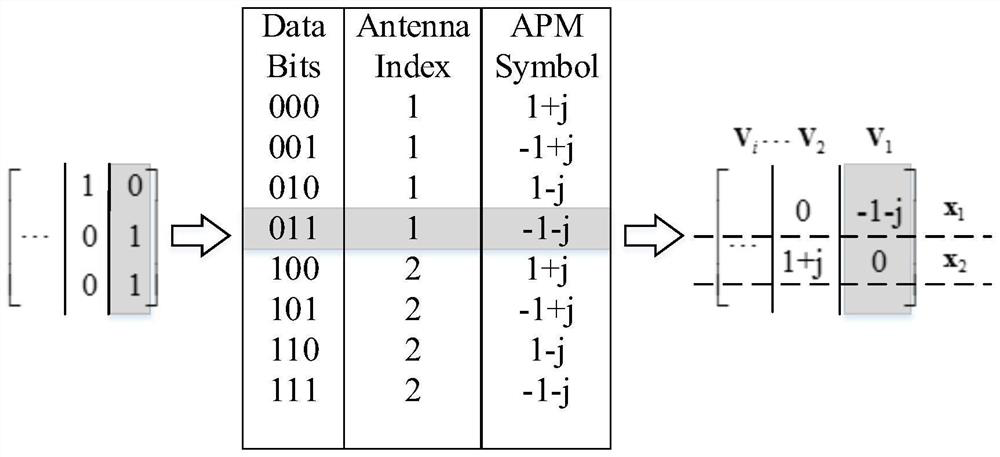
Multi-antenna OTFS modulation method and system based on spatial modulation
ActiveCN113810325AFight wellImprove spectral efficiencySpatial transmit diversityMulti-frequency code systemsTime domainMaximum likelihood detection
The invention discloses a multi-antenna OTFS modulation method and system based on spatial modulation, and the method comprises the steps: carrying out the spatial modulation of an original information sequence needing to be transmitted, and obtaining a modulated symbol sequence and a transmitting antenna index sequence; arranging the symbol sequence of each transmitting antenna into a time delay-Doppler domain signal matrix to obtain an OTFS symbol block, and converting the OTFS symbol block into a time domain signal matrix; performing time domain channel transmission on the time domain signal matrix according to the transmitting antenna index sequence; performing OTFS demodulation on the time domain signal matrix at a receiving end, and recovering the time domain signal matrix to be a symbol matrix on a time delay-Doppler domain; and performing maximum likelihood detection on the symbol matrix recovered on each time slot in combination with the antenna index sequence and the modulated symbol sequence, and recovering the original information sequence. According to the method, only one transmitting antenna is activated to transmit the data information in each time slot, so that the problems of mutual interference and synchronization between the antennas can be effectively avoided, and the complexity of a multi-antenna system receiver can be reduced.
Owner:XIDIAN UNIV
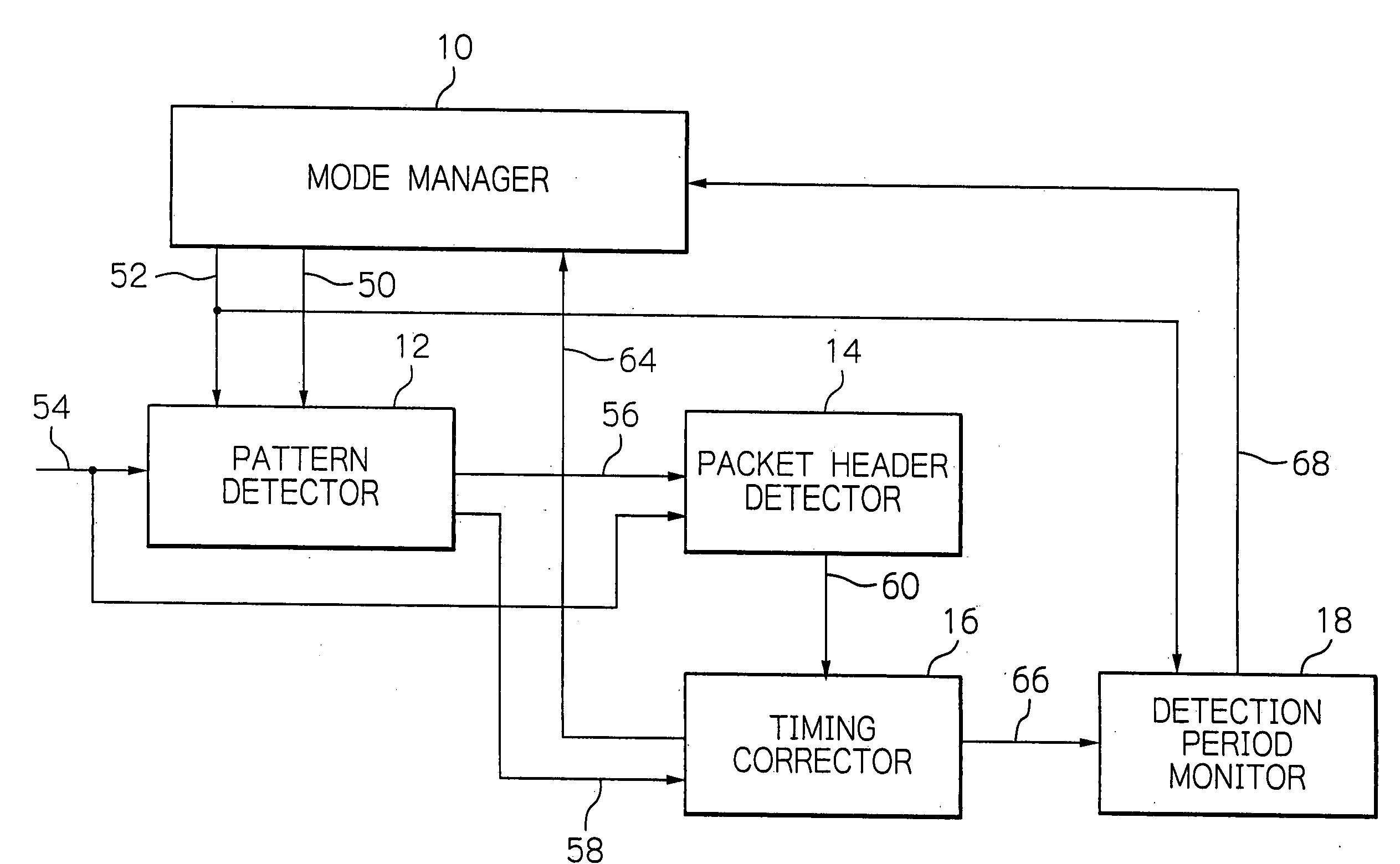
Device for preventing erroneous synchronization in wireless communication apparatus
ActiveUS20050135528A1Avoid disconnectionGood channel qualityElectronic circuit testingError detection/correctionComputer hardwareTelecommunications link
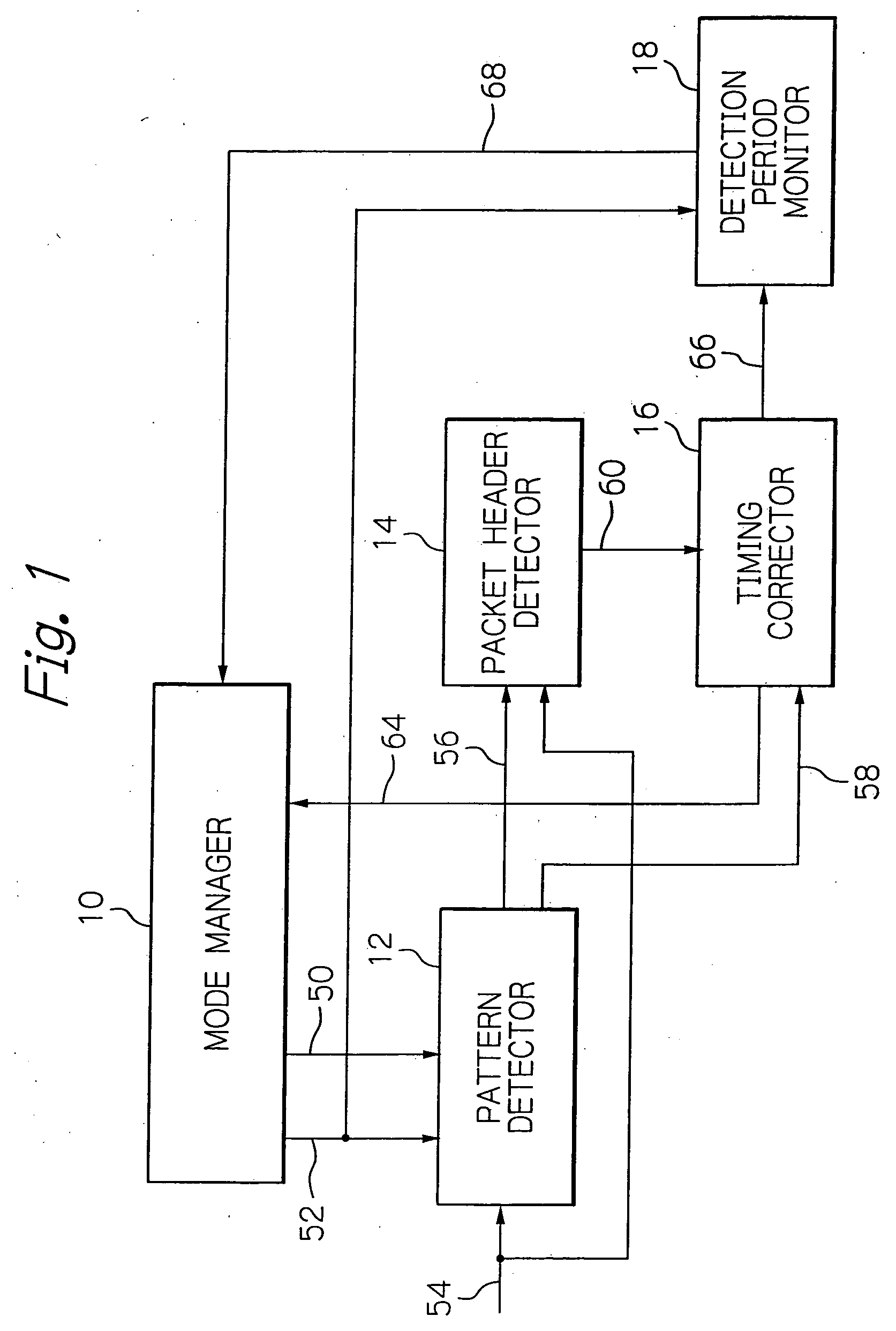
An erroneous synchronization preventing device includes a pattern detector detecting a sync pattern from received data with a broader sync window to output a sync detection notice and a sync timing. On receipt of the notice, a packet header detector checks an error in a header field of the received data, and, if detecting no error, outputs a header-normally-received notice, on receipt of which the timing corrector makes the inner timing synchronous with the sync timing to output a timing correction end notice. The mode manager in turn outputs a change notice. The pattern detector then detects the sync pattern with a narrower sync window. Unless the end notice is received within a predetermined period as from receipt of the change notice, a detection period monitor outputs an out-of-synchronism notice. The mode manager then outputs a restoration command for instructing detection of the sync pattern with the broader sync window. Disconnection of a communication link due to erroneous synchronization will be avoided.
Owner:LAPIS SEMICON CO LTD
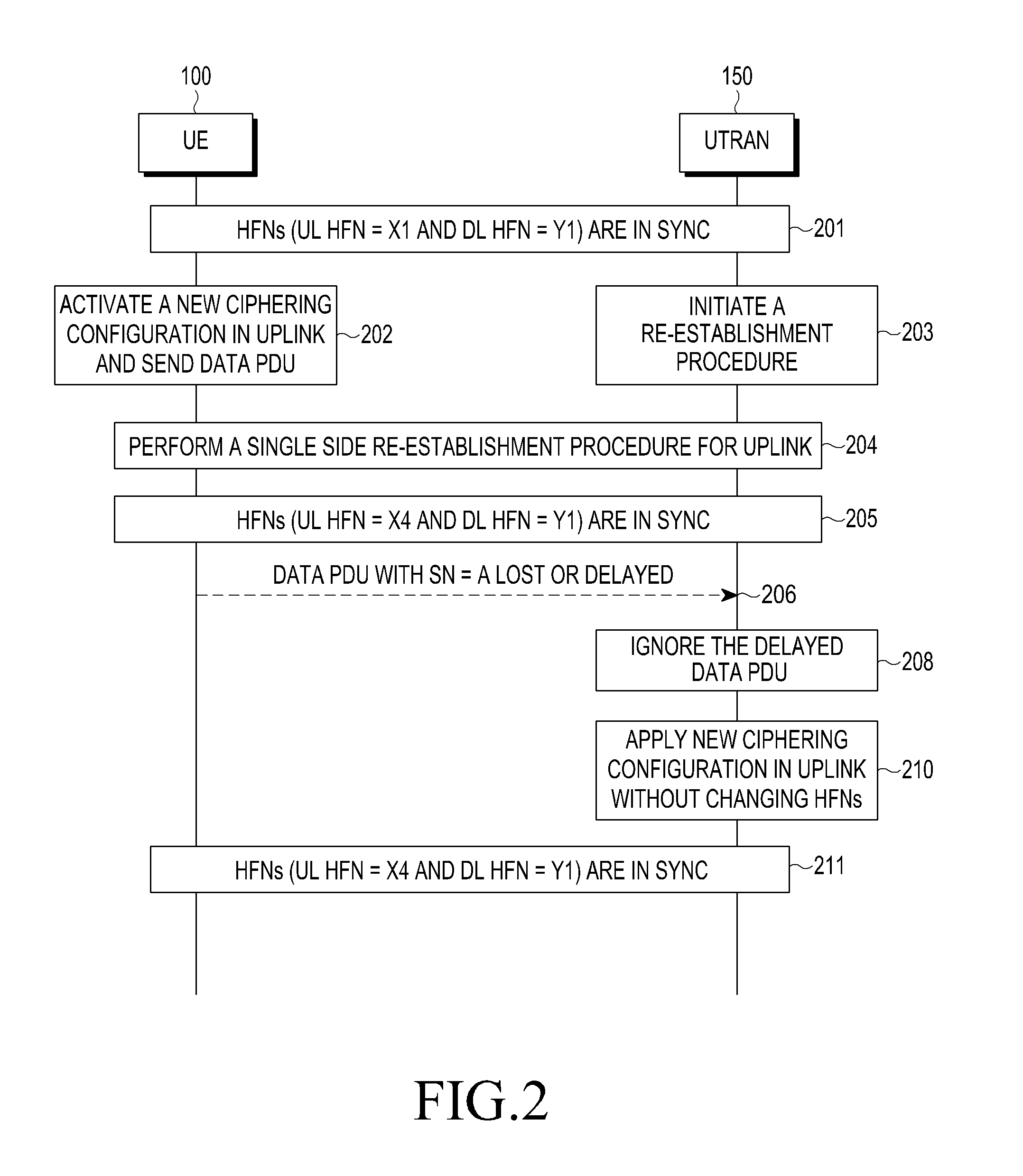
Method and apparatus for applying a ciphering configuration in a wireless communication network
ActiveUS20120183142A1Prevent synchronization lossAvoid synchronizationSynchronisation arrangementConnection managementComputer hardwareNetwork method
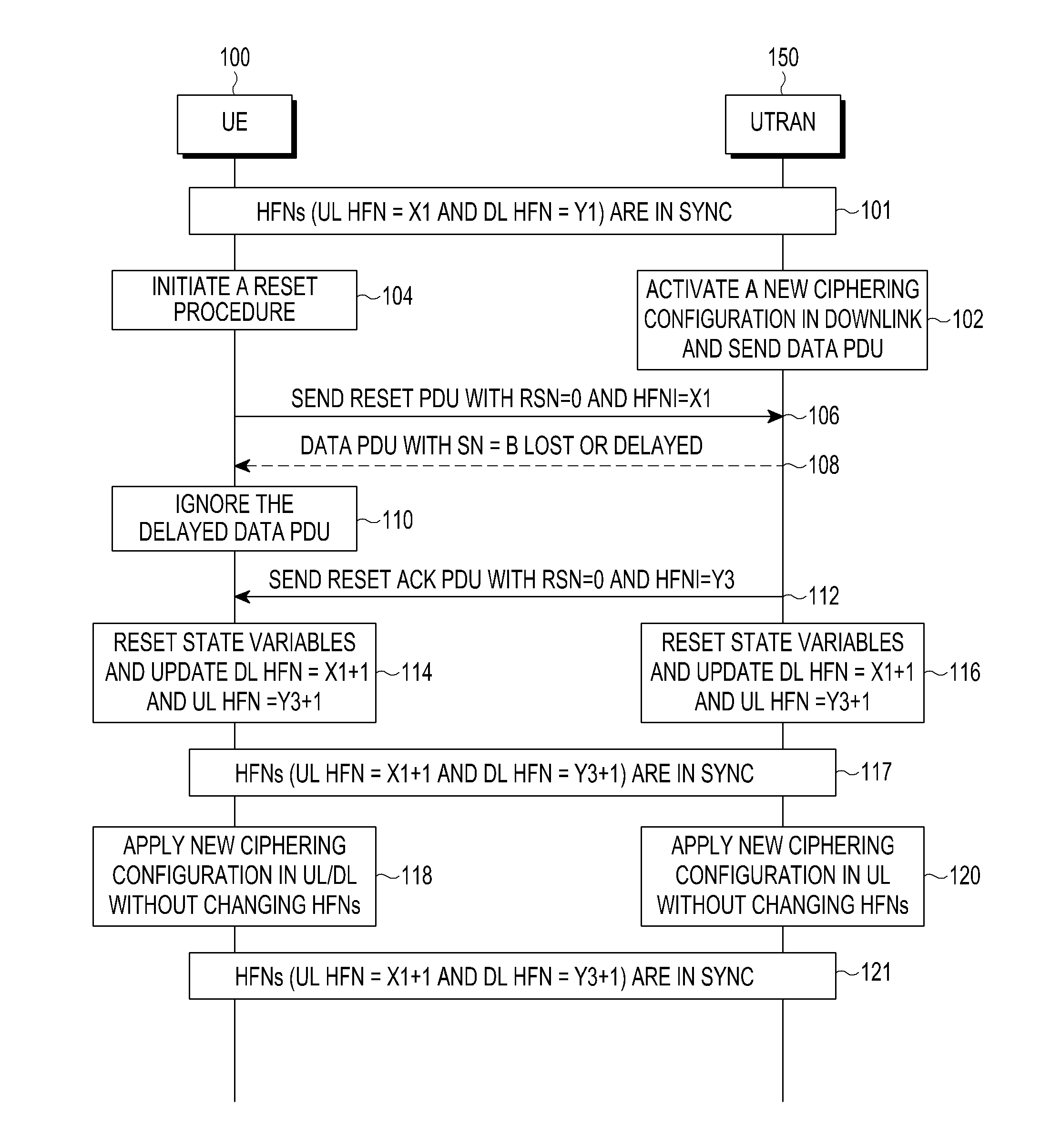
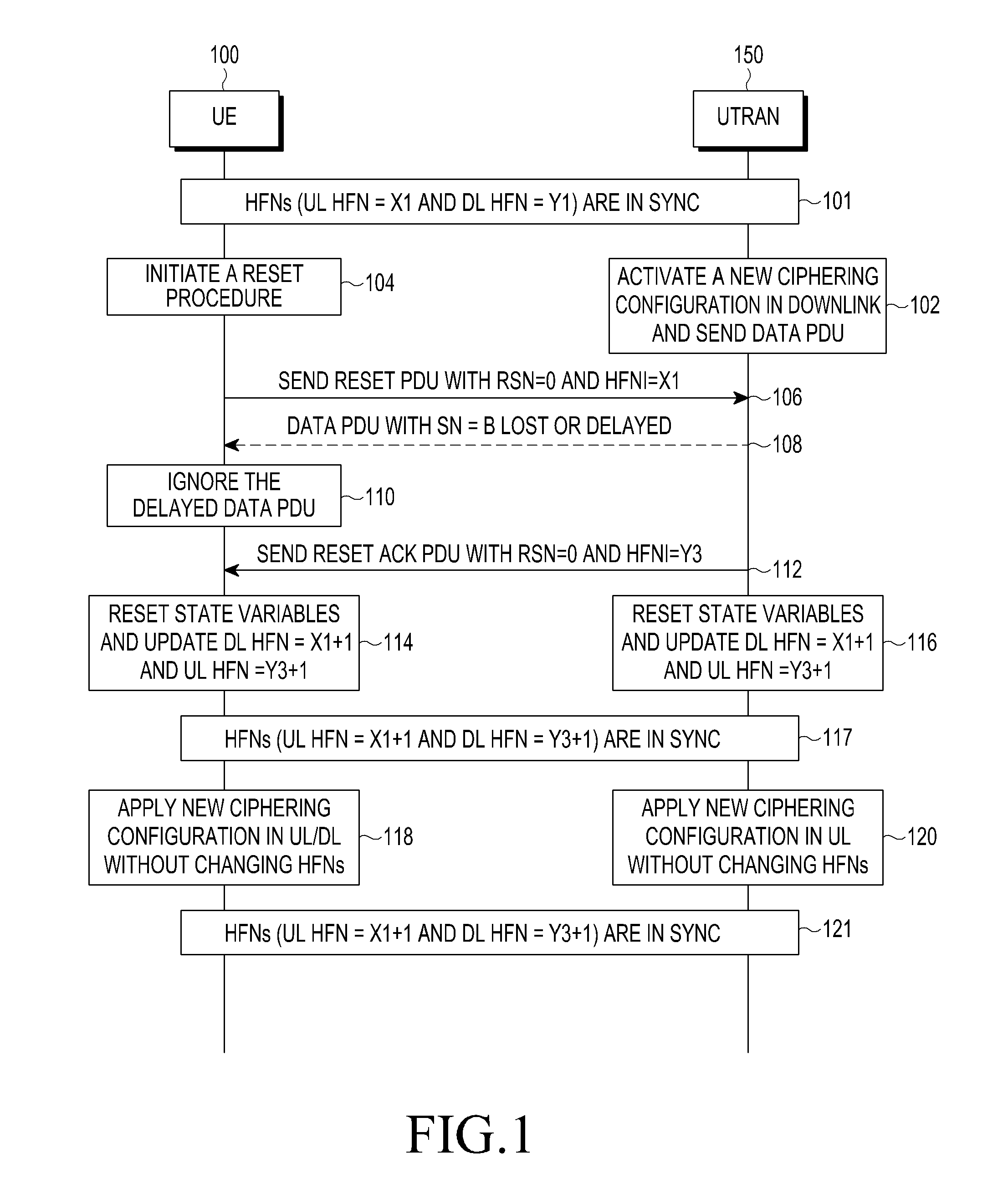
Methods and devices are provided for applying a ciphering configuration in a wireless communication network. The method includes initiating an entity reset procedure by a first entity in the wireless communication network; synchronizing Hyper Frame Numbers (HFNs) associated with the first entity and a second entity, respectively, during the entity reset procedure; and applying a new ciphering configuration by the first entity and the second entity, upon completing the entity reset procedure, without updating the synchronized HFNs associated with the first entity and the second network, respectively.
Owner:SAMSUNG ELECTRONICS CO LTD
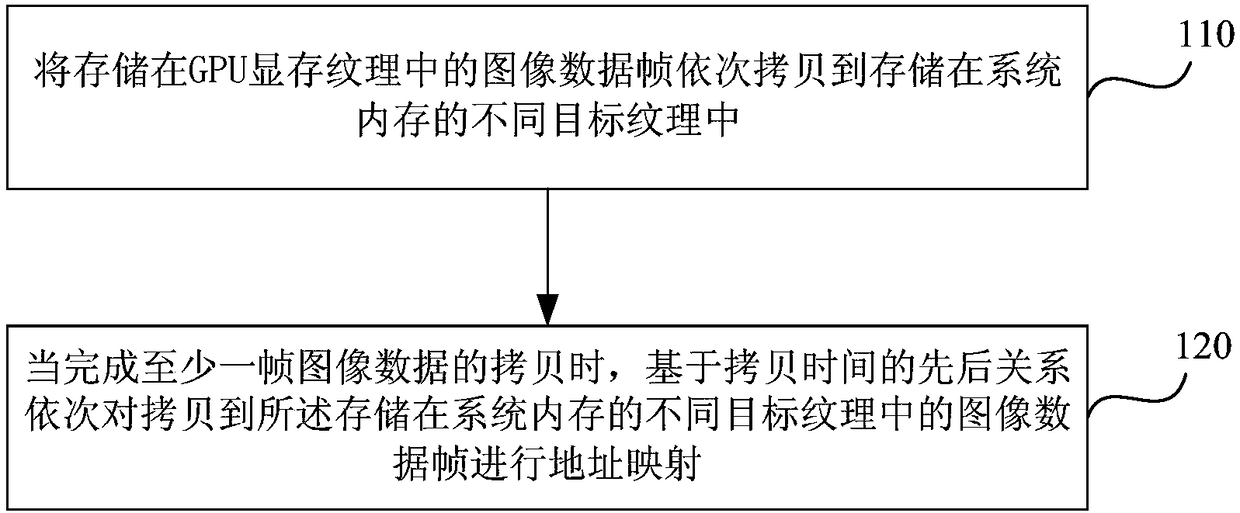
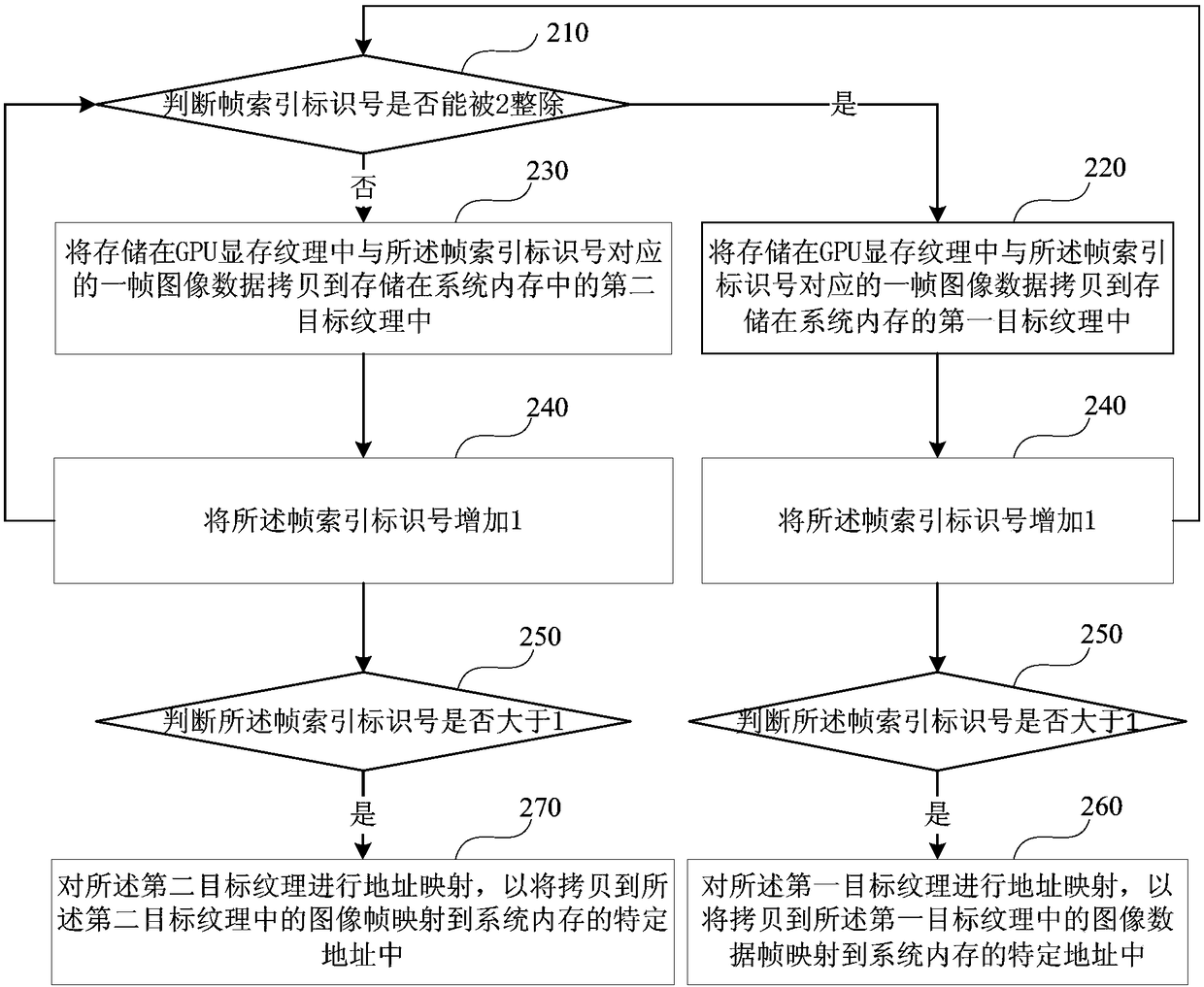
Method and device for copying GPU video memory textures to system memories and electronic equipment
ActiveCN108509272AAvoid synchronizationIncrease encoding frame rateResource allocationMemory adressing/allocation/relocationVideo memoryComputer graphics (images)
Embodiments of the invention disclose a method and device for copying GPU video memory textures to system memories and electronic equipment. The method comprises the following steps of: copying imagedata stored in a GPU video memory texture into different target textures stored in a system memory in sequence; and when the copy of at least one frame of image data is completed, carrying out addressmapping on image data frames copied into the different target textures stored in the system memory in sequence on the basis of an order relationship of the copy times. By adoption of the method, theefficiency of copying image resources stored in GPU video memory textures to system memories can be improved, so that the video encoding frame rate and video live streaming fluency are improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Data exchange method applied to BIOS (Basic Input Output System) and baseboard management controller (BMC)
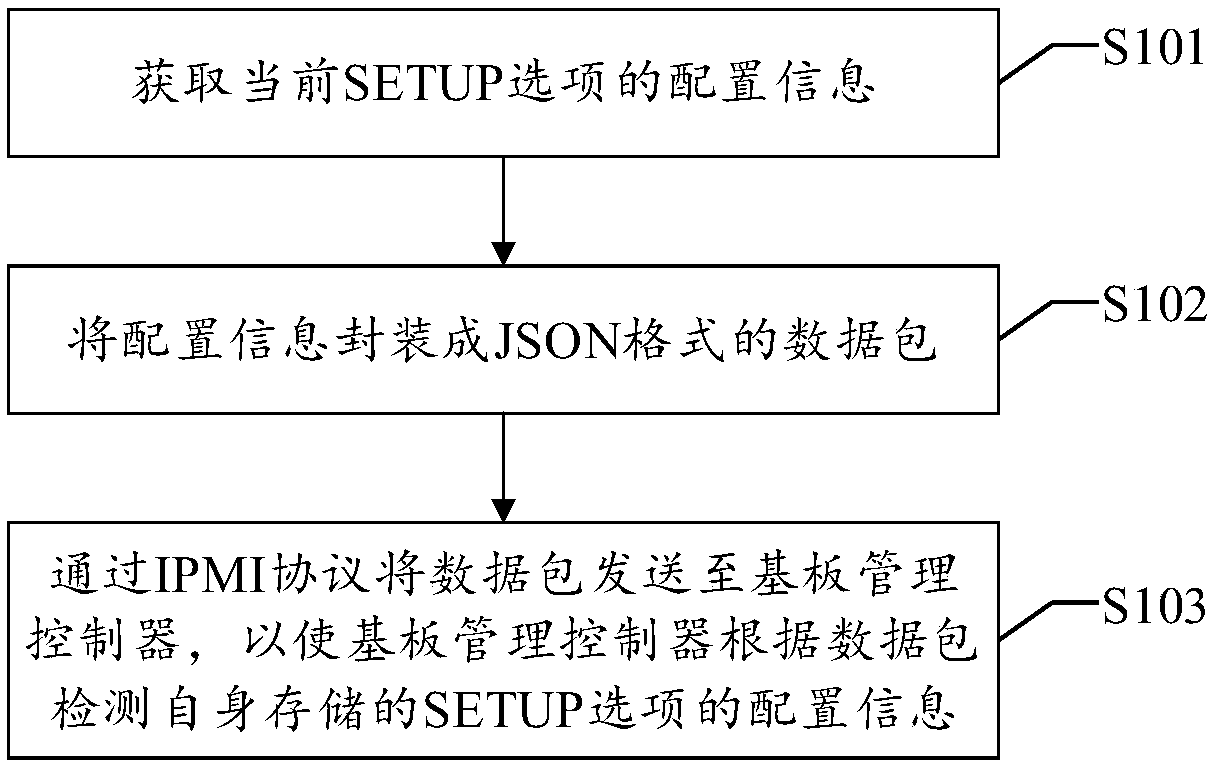
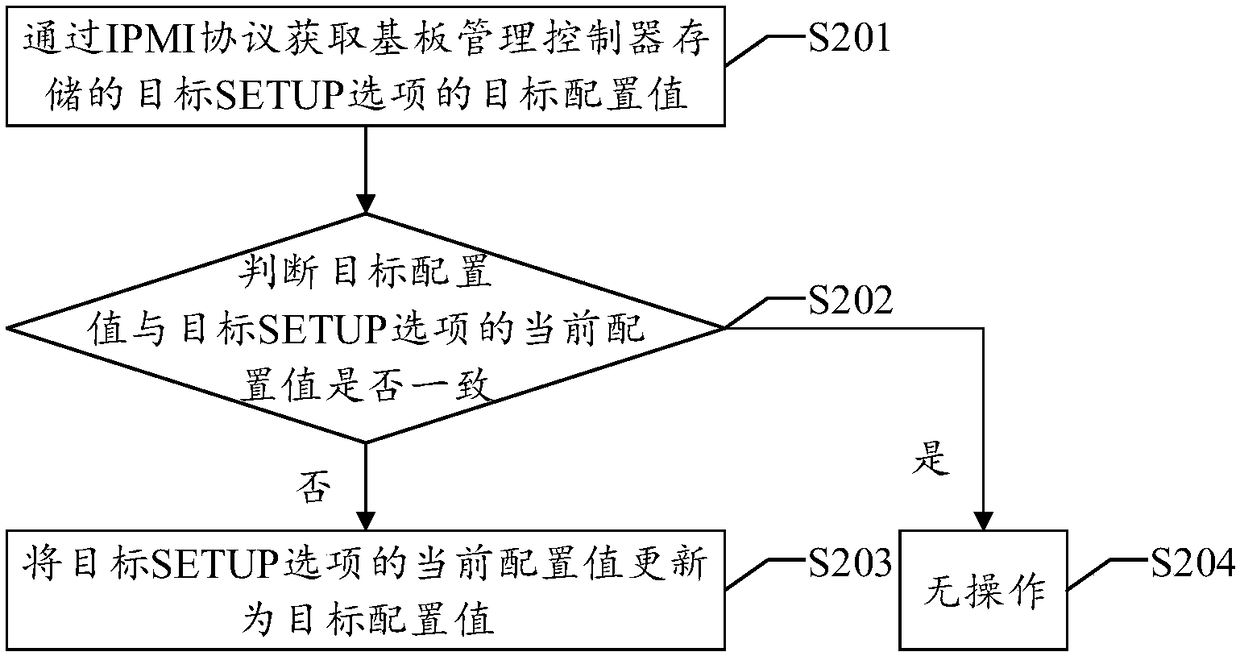
InactiveCN108170454ARealize data interactionAvoid synchronizationProgram loading/initiatingSoftware deploymentNetwork packetData exchange
The invention discloses a data exchange method applied to a BIOS (Basic Input Output System) and a baseboard management controller (BMC). The method includes: acquiring configuration information of current SETUP options; encapsulating the configuration information into a JSON (JavaScript Object Notation)-format data packet; and sending the data packet to the baseboard management controller throughan IPMI protocol to enable the baseboard management controller to detect configuration information of SETUP options, which are stored thereby, according to the data packet, wherein the configurationinformation includes at least the number of the current SETUP options of the BIOS, a name and a current configuration value of each option and configurable values of each option. Therefore, respectivemanual setting of the configuration information of the SETUP options of the BIOS and the baseboard management controller is avoided, work efficiency is improved, and times and costs are also saved. Correspondingly, a data exchange device and data exchange equipment applied to the BIOS and the baseboard management controller and a computer-readable storage medium disclosed by the invention also have the above-mentioned technical effects.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
MAC (Media Access Control) layer synchronizing method improved based on IEEE 802.16d
InactiveCN101800612AAvoid synchronizationTime-division multiplexRadio transmission for post communicationRadio frequencyMedia access control
The invention discloses an MAC (Media Access Control) layer synchronizing method improved based on IEEE 802.16d, which is used for realizing synchronization among nodes and synchronization between an MAC layer inside the nodes and radio frequency. The invention adopts the technical scheme as follows: realizing the synchronization among nodes by using a time stamp field in an MSH-NCFG message specified in a 802.16d protocol; and designing a primitive message for interaction between the MAC layer and the radio frequency to correctly realize the synchronization among nodes and the synchronization between the interiors of the nodes. The method is characterized by comprising the steps of clock synchronization of the interiors of the nodes, clock synchronization among nodes and processing of the time stamp field of neighboring nodes, wherein the clock synchronization among nodes comprises primary clock synchronization in network accessing and synchronous correction and maintenance after network accessing.
Owner:BEIJING JIAOTONG UNIV
Synchronous locking method and wireless telecommunication device
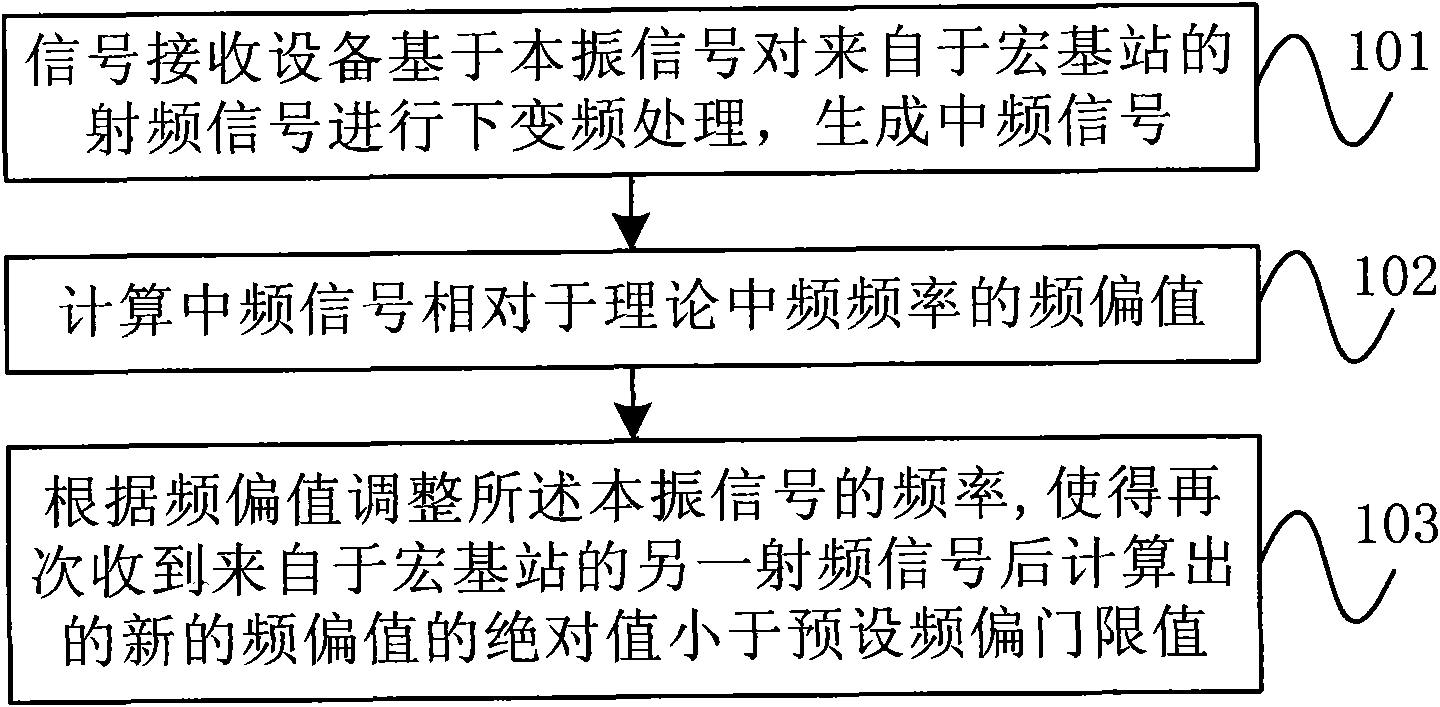
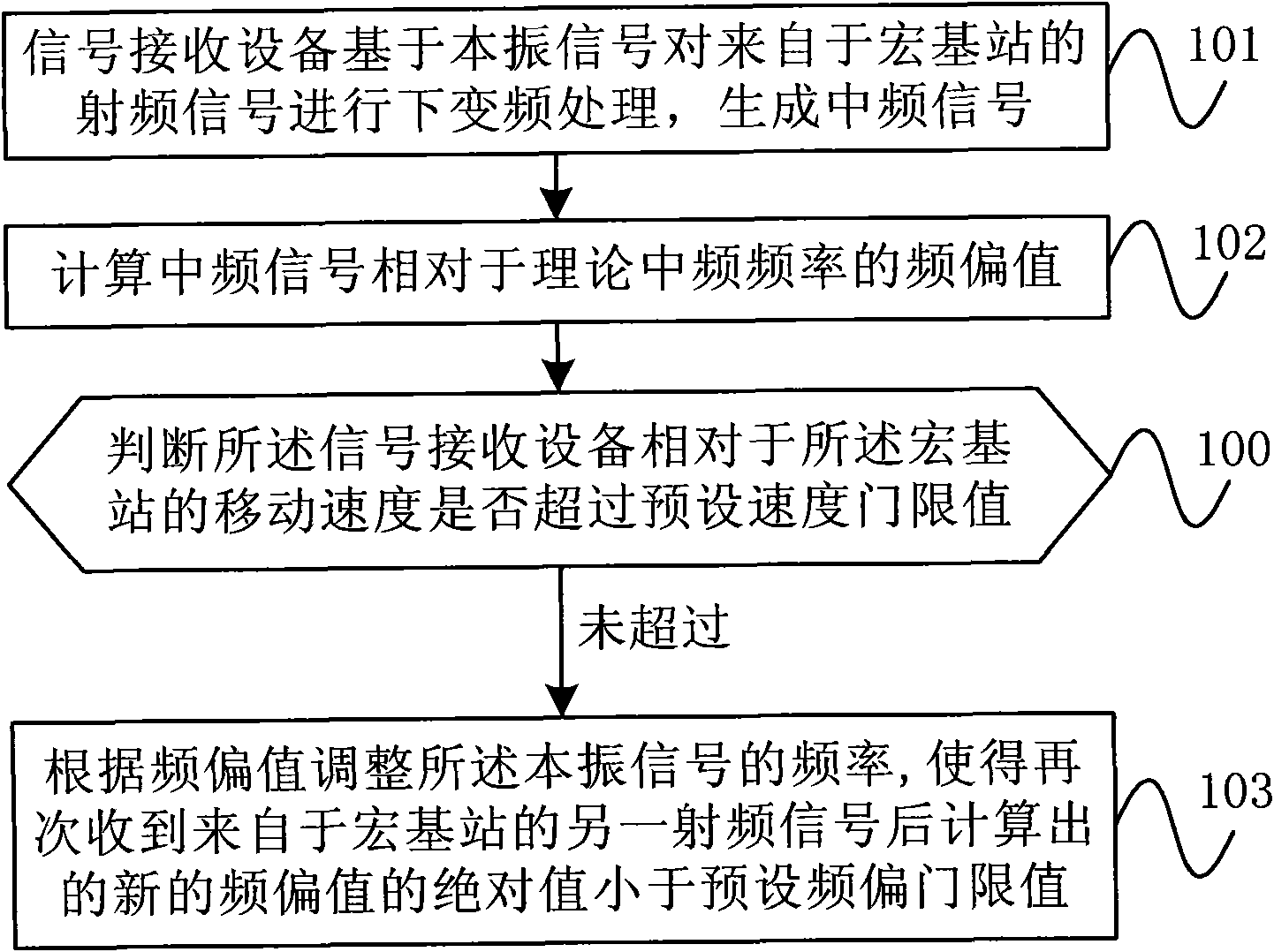
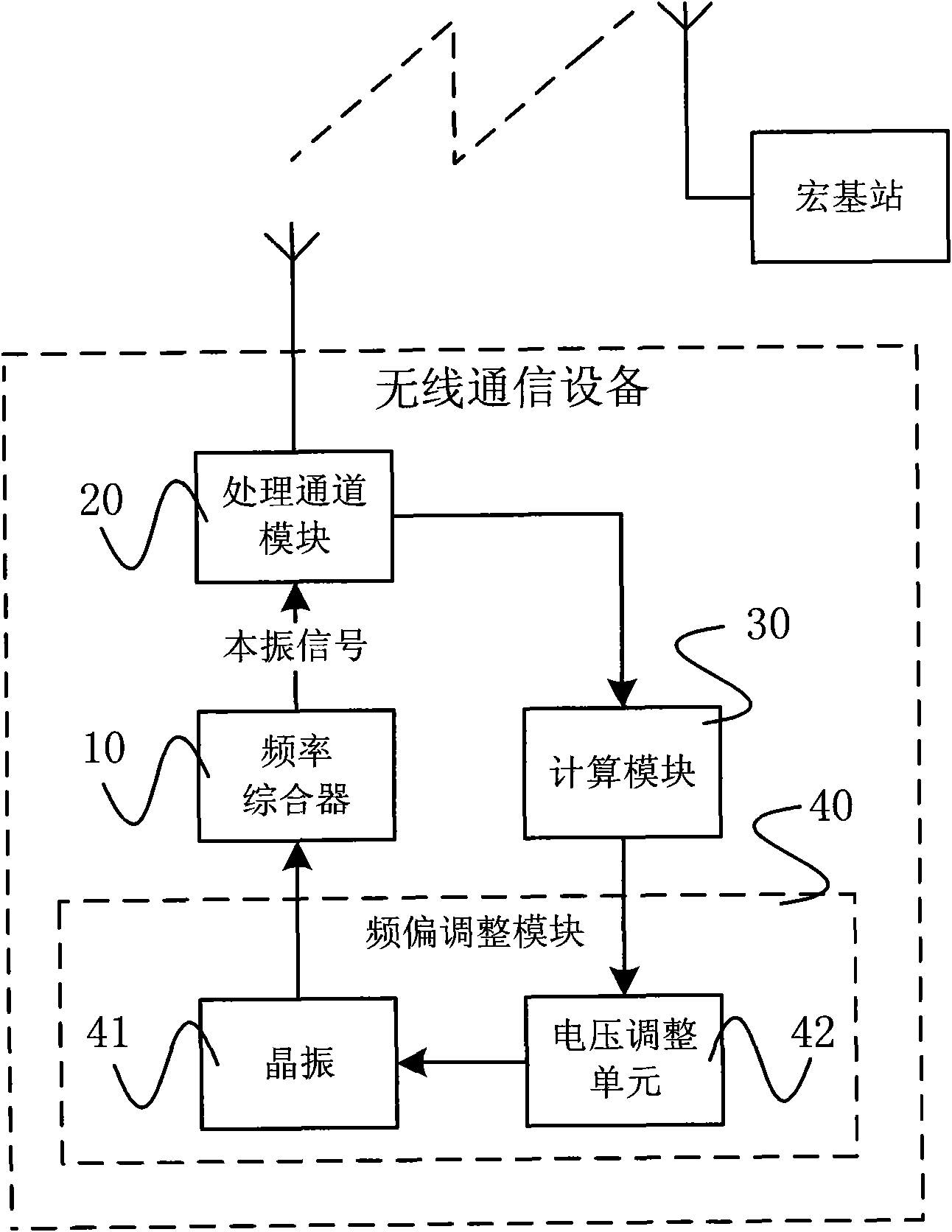
InactiveCN102404839AAvoid synchronizationGenlock preventionSynchronisation arrangementIntermediate frequencyRadio frequency signal
The invention provides a synchronous locking method and a wireless telecommunication device. The synchronous locking method includes that the wireless telecommunication device performs down-conversion processing on radio-frequency signals coming from an Acer stand based on local oscillation signals so as to generate intermediate-frequency signals, frequency deviation value of the intermediate-frequency signals relative to a theoretical intermediate frequency is calculated, and frequency of the local oscillation signals is regulated according to the frequency deviation value so as to lead the absolute value of a new frequency deviation value calculated after another radio-frequency signals coming from the Acer stand are received again is smaller than a preset frequency deviation threshold value. Based on the radio-frequency signals coming from the Acer stand, synchronous locking of a clock is achieved, out-of-step of the clock caused by failure of a global position system (GPS) is avoided, accuracy of the clock can be maintained in a long period, and accordingly stability and reliability of clock synchronization are improved. In addition, a GPS module is not needed to be arranged, thereby being favorable for simplifying design of a synchronous system, lessening size of the device and reducing production cost and construction complexity.
Owner:TD TECH COMM TECH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com