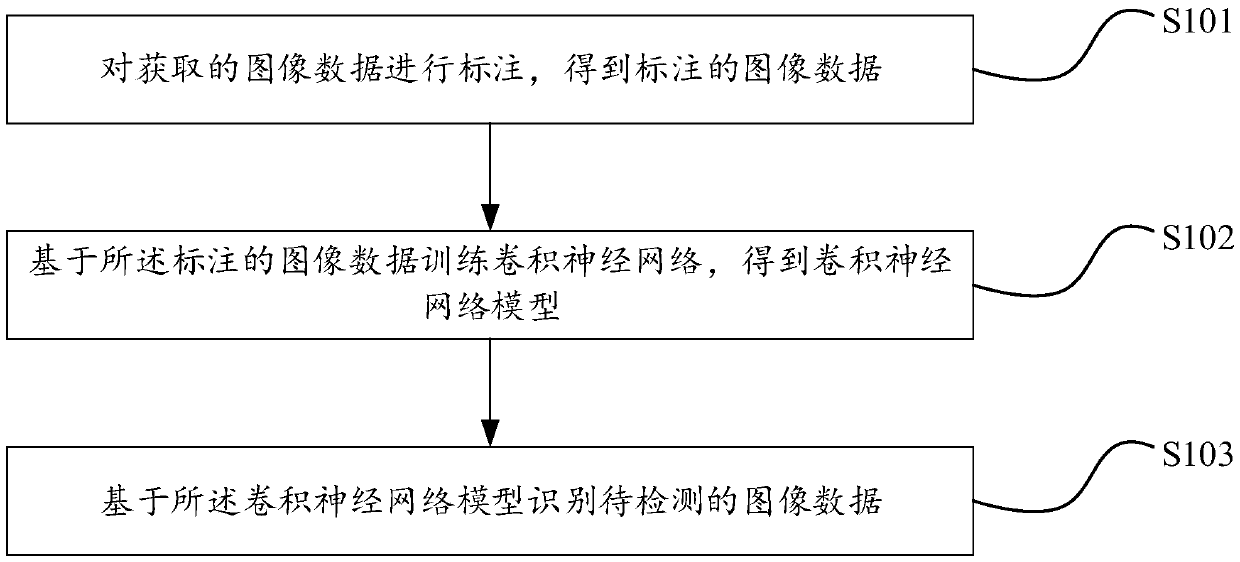
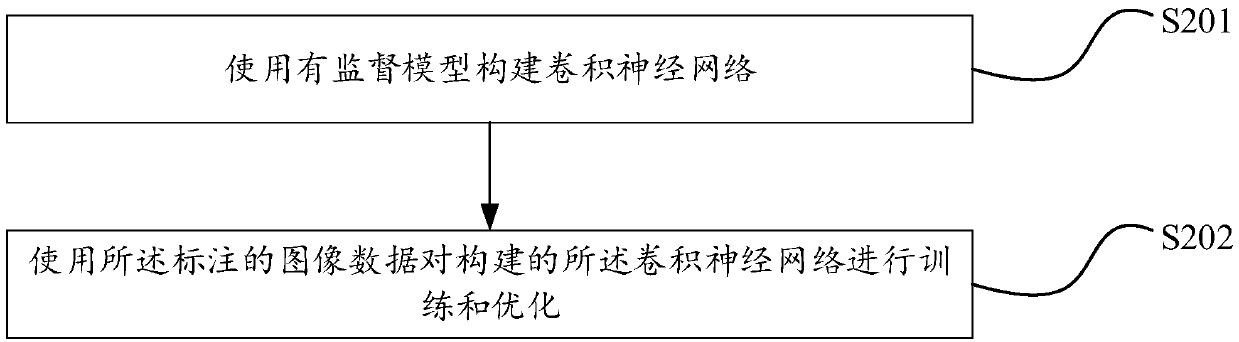
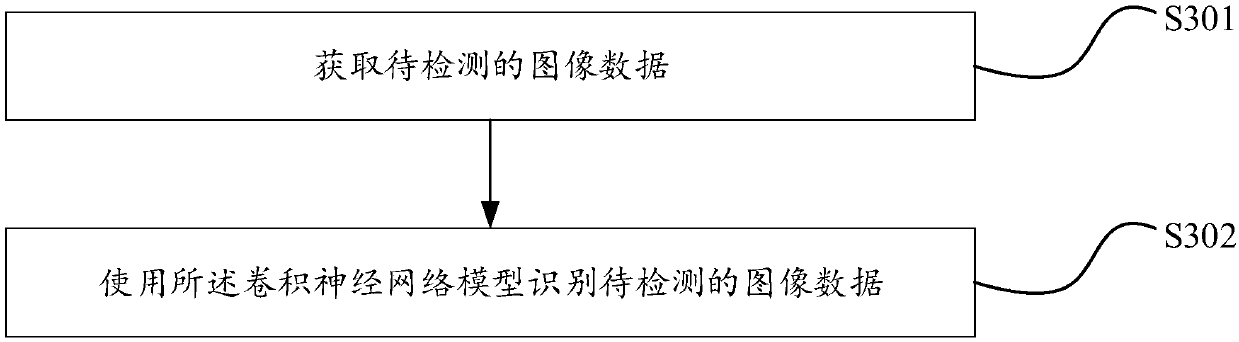
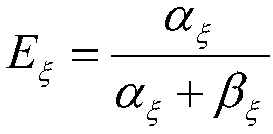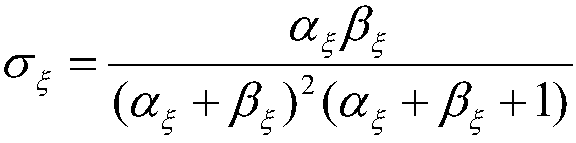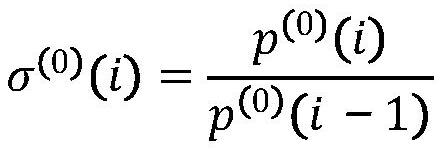Patents
Literature
75results about How to "To achieve the purpose of security protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
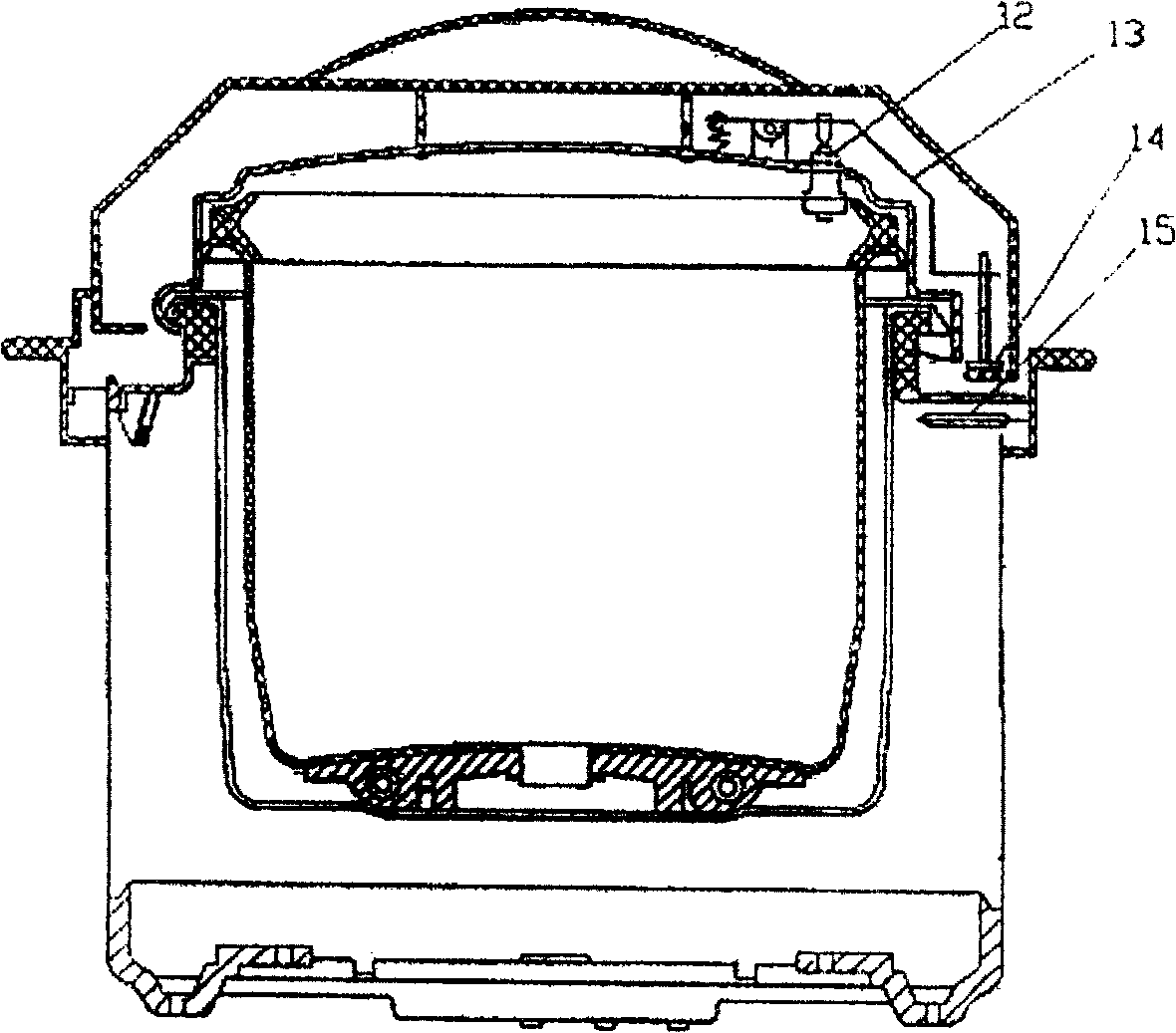
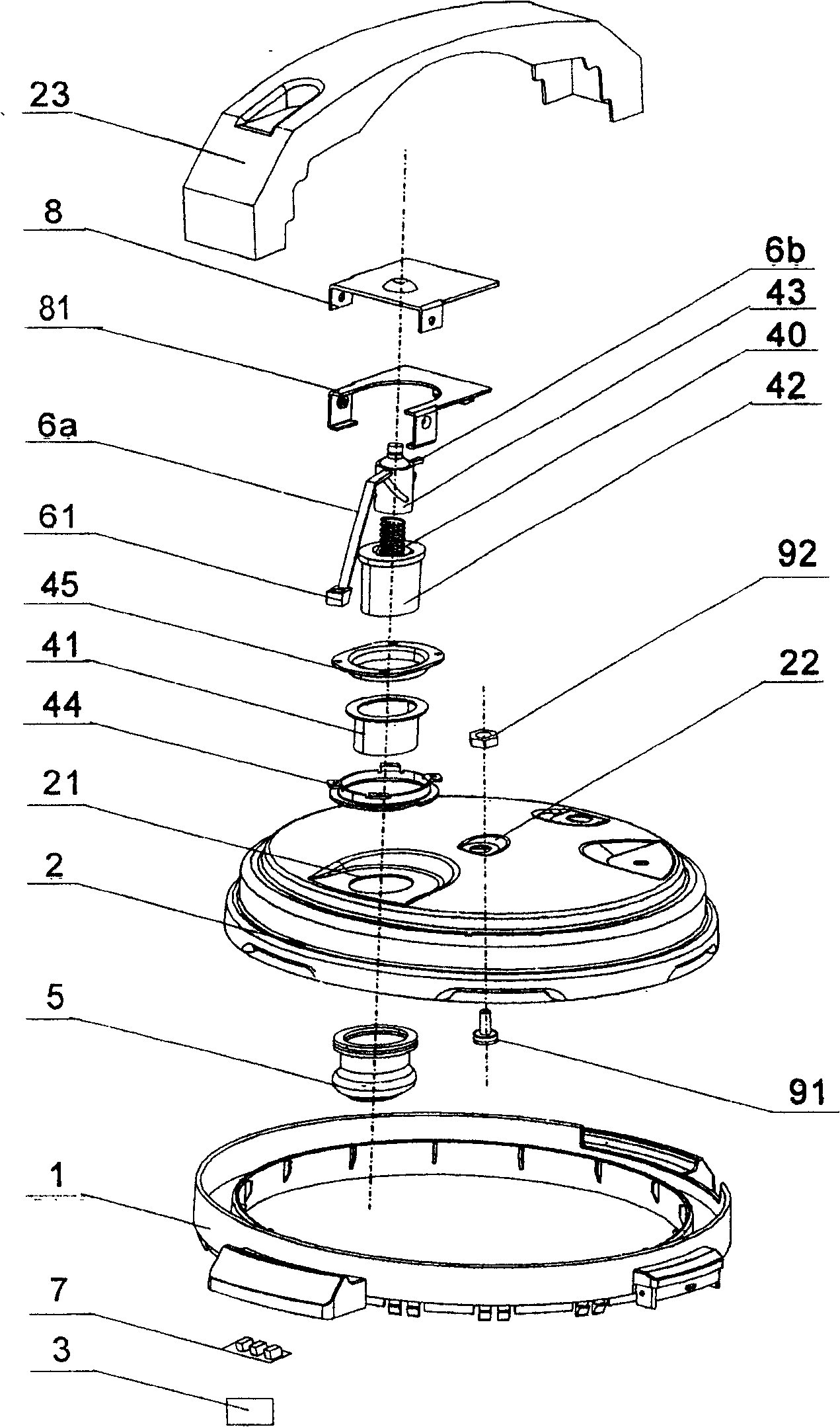
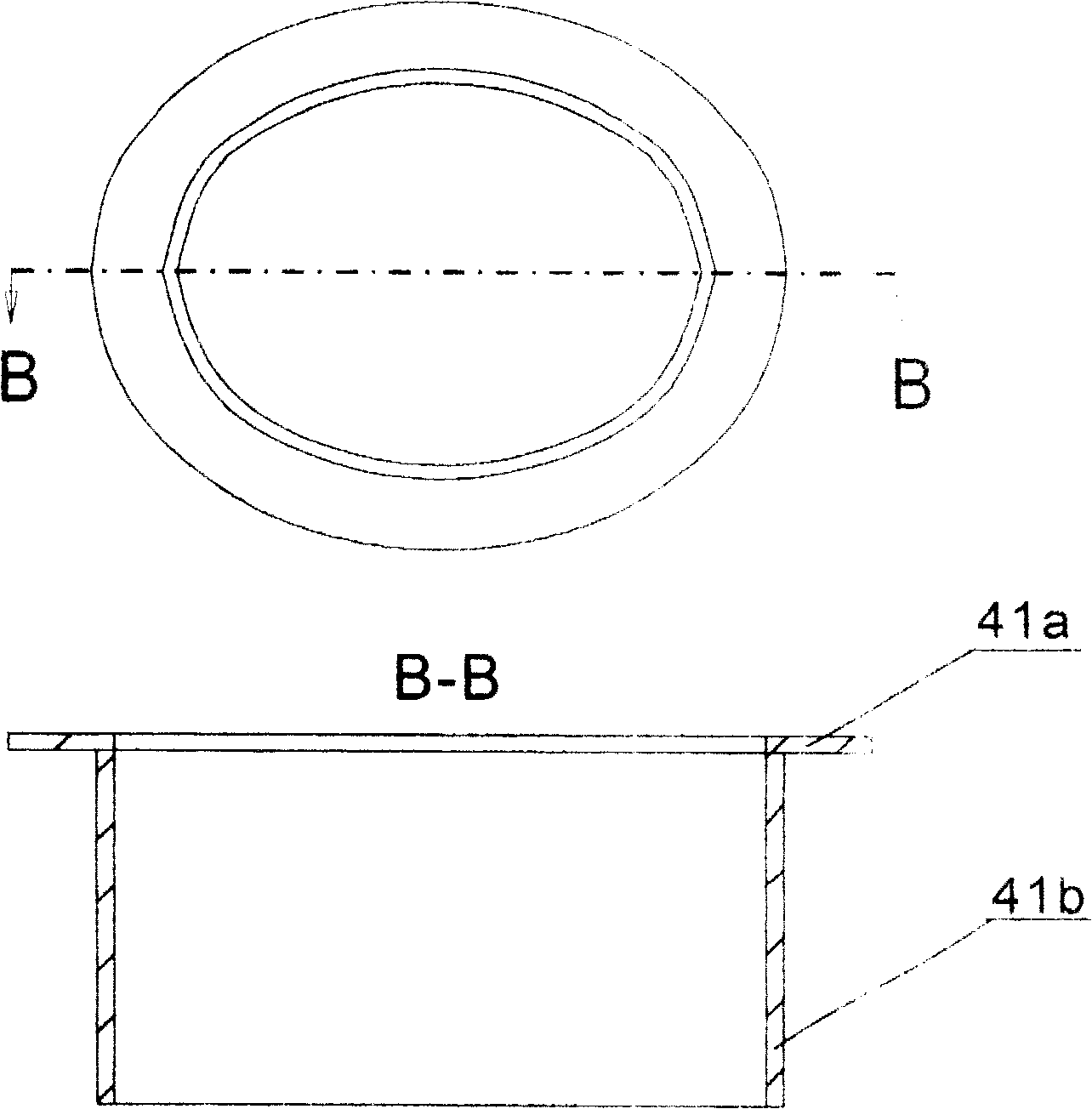
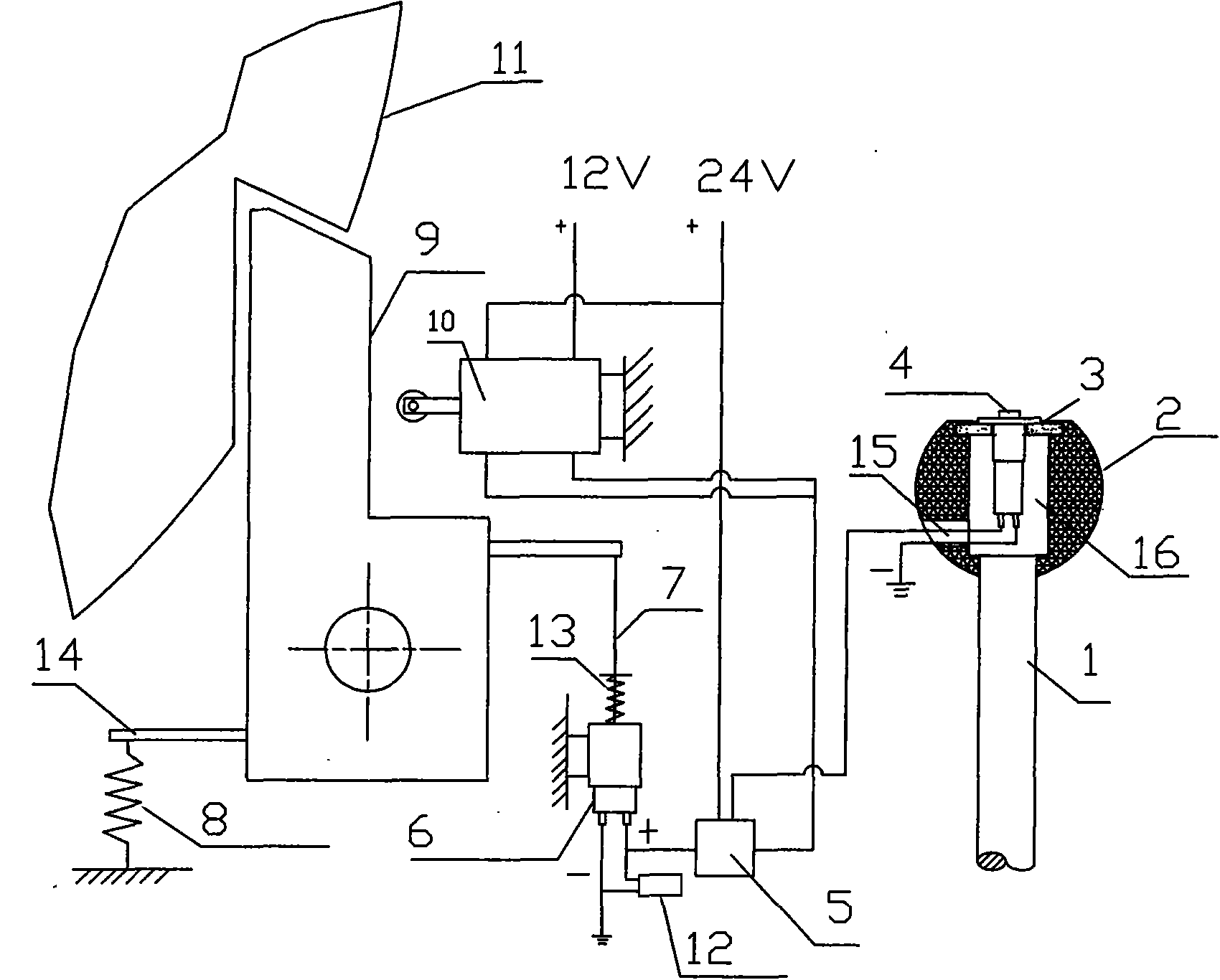
Electric pressure cooker
An electric pressure cooker is composed of a cooker body with control circuit and sensor on its top edge, and a cover with an elastic sealing sleeve and a pressure driver consisting of lining sleeve embedded in said elastic sealing sleeve, an axially moving piston and a rotary part driven by said piston and with fixed long arm and inductor.
Owner:FOSHAN FUSHIBAO ELECTRICAL APPLIANCE TECH
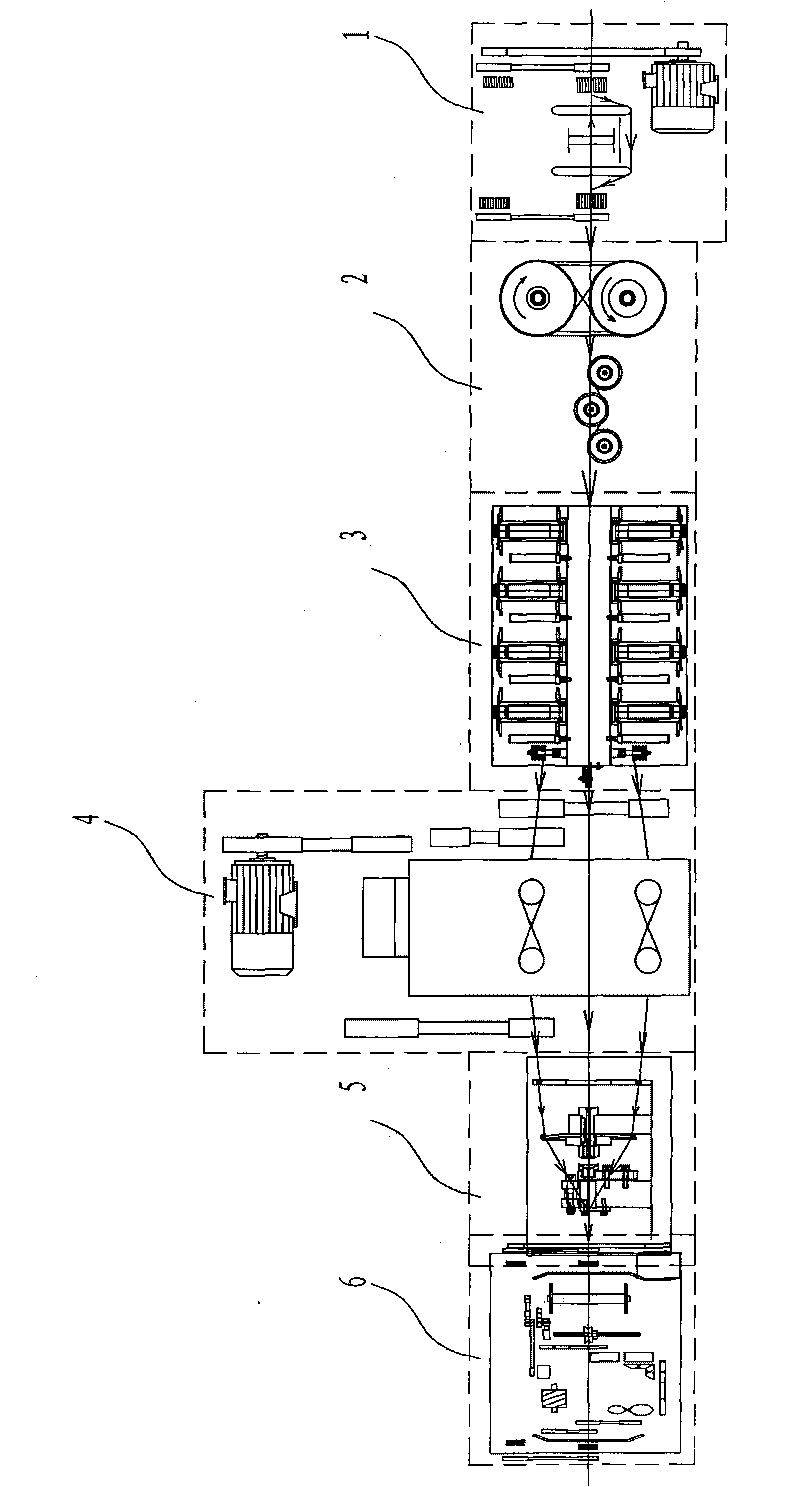
Double twisting rope laying machine
The invention discloses a double twisting rope laying machine which comprises a core wire laying machine, a core wire tension mechanism, a surface wire laying mechanism, a single wire pre-twisting machine, a wire collecting mechanism and a wire-rewinding machine arranged sequentially, wherein the core wire tension mechanism comprises a broken wire detecting device, a wire roller, a tension control device and a tension detecting device; the core wire output tension is detected by the tension detecting device, and if the tension exceeds a set tension range, the core wire output tension is adjusted by the tension control device to realize accurate control of the core wire laying tension; and the single wire pre-twisting machine comprises a motor, a transmission component and a plurality of groups of rotor components which are arranged at the front surface and the back surface of a stand. Through the rotation of each group of rotor components, the single wire pre-twisting process is realized and the single wire stress is eliminated, thereby being favorable to twisting and forming, and finally, the twisted cords have good straightness, stable residual torsion and high product quality and is difficult to loose; and the specifications of the producible cords are 3+9+15*0.22, 3+9+15*0.175 and 0.25+(6+12)*0.22.
Owner:江苏泰隆机电科技有限公司
Monitoring method for App behaviors in Android system
InactiveCN105844157AImprove the protective effectTo achieve the purpose of security protectionPlatform integrity maintainanceRelevant informationAddress book
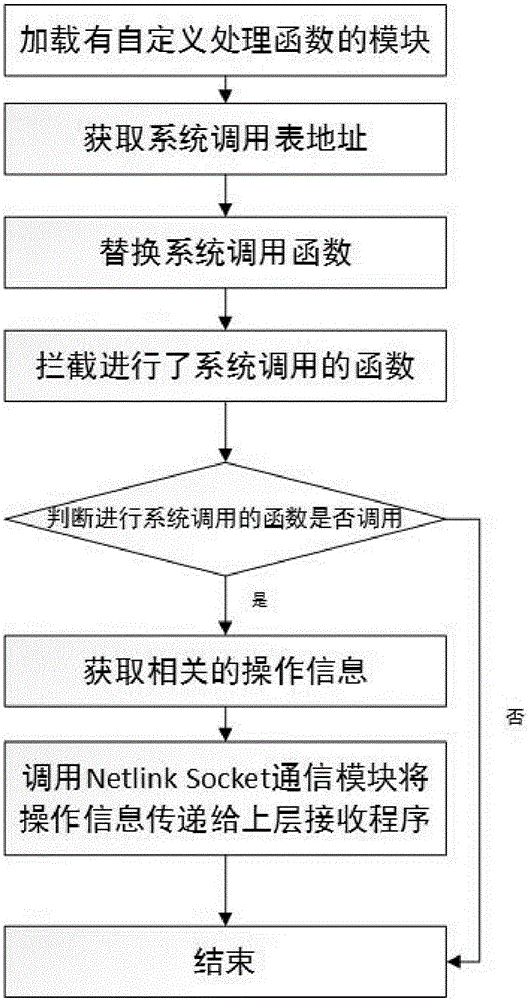
The invention discloses a monitoring method for App behaviors in an Android system. The method comprises the steps as follows: firstly, writing a kernel module, and performing cross compilation by writing of own Android kernel module; secondly, loading the module into the Android system, and intercepting specific functions (such as functions for reading related information of address books and the like) to obtain corresponding system call information including information about reading through which process and the like; thirdly, returning the corresponding recorded information to an application layer and forming corresponding monitoring log files to achieve system calling interception and monitoring of the whole Android system. According to the monitoring method, monitoring can be performed on system calling generated in both the application layer and a Native layer, and compared with existing monitoring methods for the application layer, the monitoring method has the advantages that protection can be more thorough, and the security protective property on mobile phones is higher; users are enabled to know behaviors of installed software thoroughly, thereby being capable of discovering malicious acts of the software timely.
Owner:北京鼎源科技有限公司
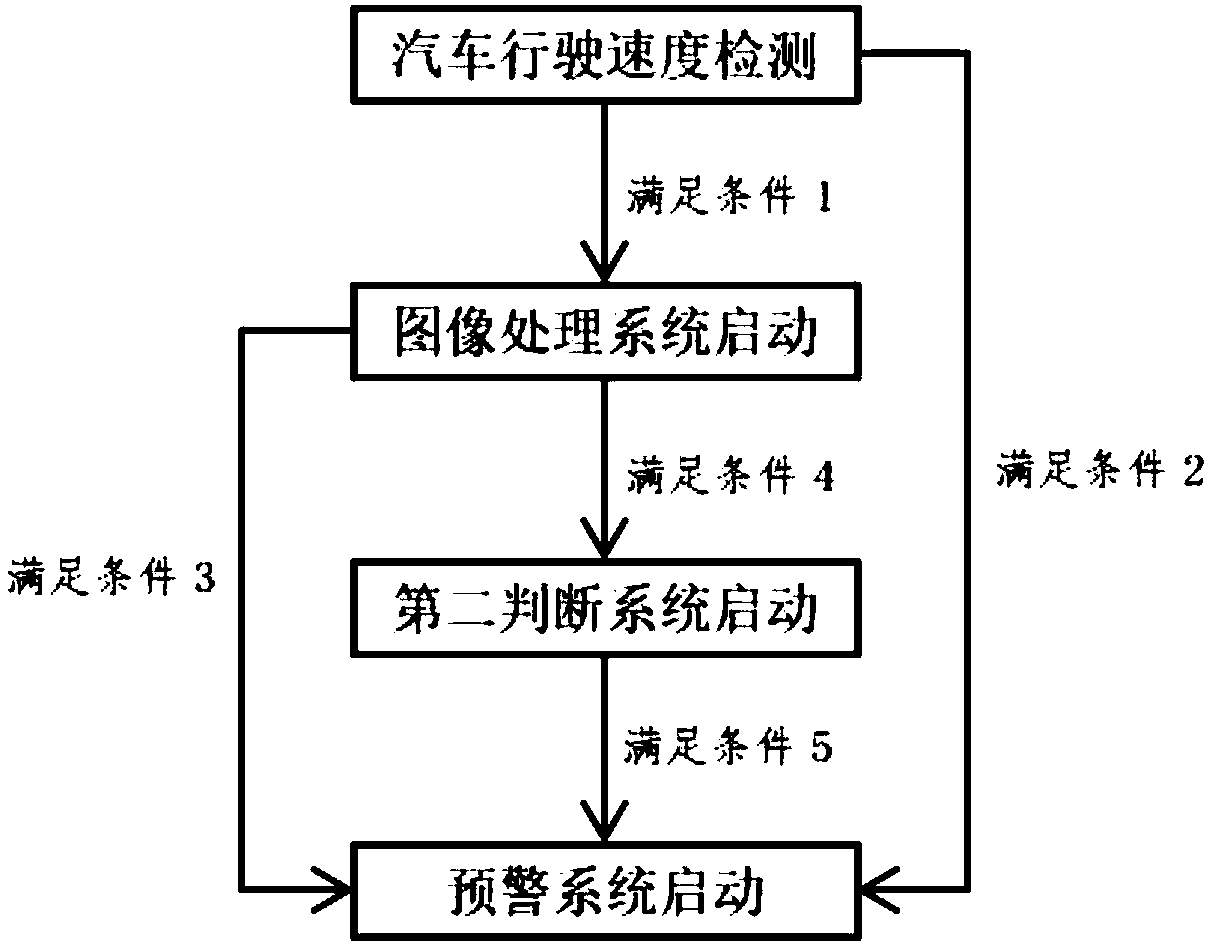
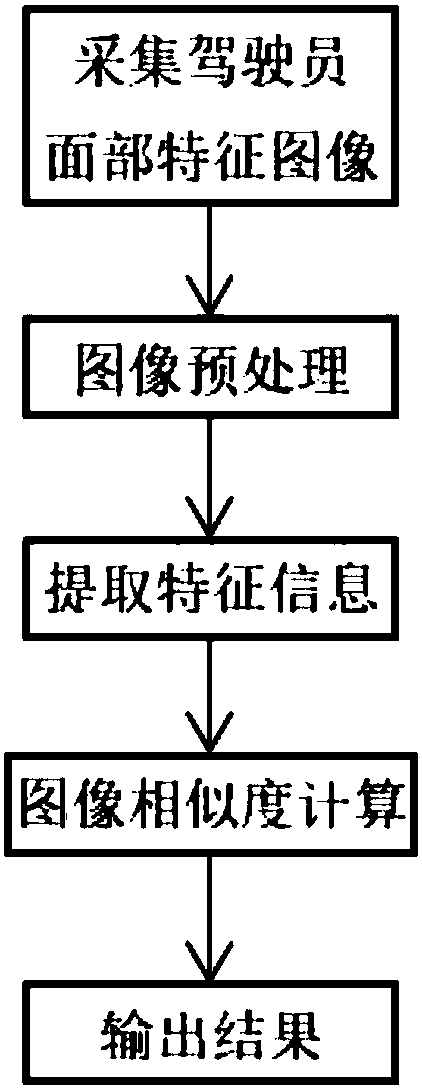
Unsafe automobile driving detection device and method based on image identification
ActiveCN108372785ATo achieve the purpose of security protectionFactors that prevent traffic accidentsTractorsAlarmsCar drivingImaging processing
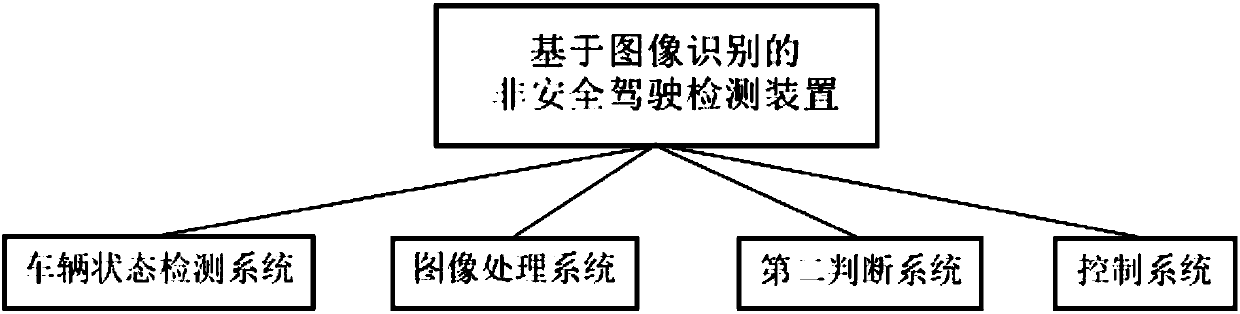
The invention provides an unsafe automobile driving detection device and method based on image identification. The device comprises a vehicle state detection system, an image processing system, a second judgment system and a control system. The method comprises the steps that facial images of a driver in a fatigue state and a drunkenness state are collected to form an expression library; a vehiclestate is detected, and the image processing system or the control system is triggered according to a condition; the facial images of the driver are analyzed, and the control system or the second judgment system is selectively triggered according to the similarity of facial feature images of the driver and facial feature images of the expression library; the second judgment system collects physical information in a cab, and the control system is triggered if it is judged that the driver is in an unsafe driving state at this moment; the control system is started to conduct corresponding controlover vehicles according to different unsafe driving states, and an alarm sends out a voice prompt. According to the unsafe automobile driving detection device and method, a driver can be early warnedof any possible traffic accident, and the occurrence of traffic accidents is effectively prevented.
Owner:JILIN UNIV
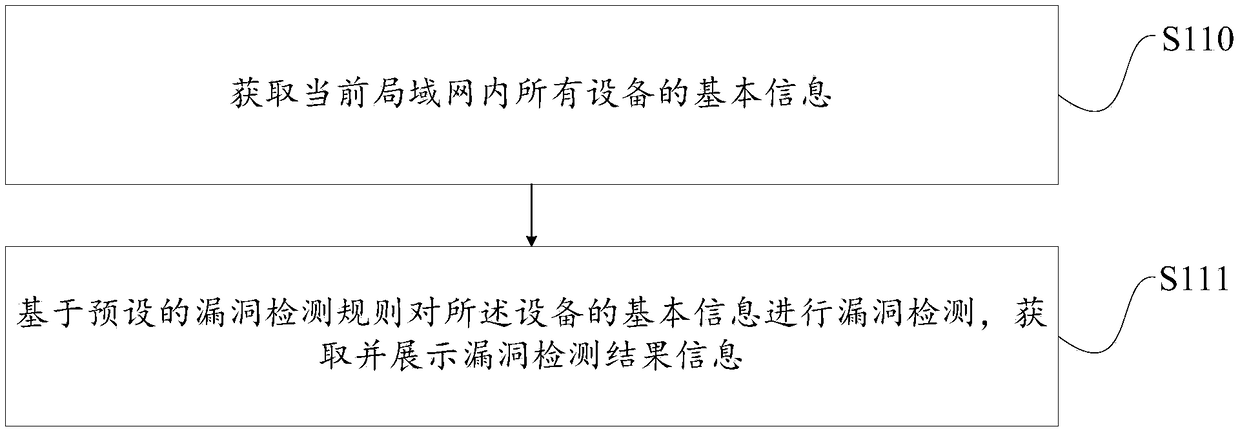
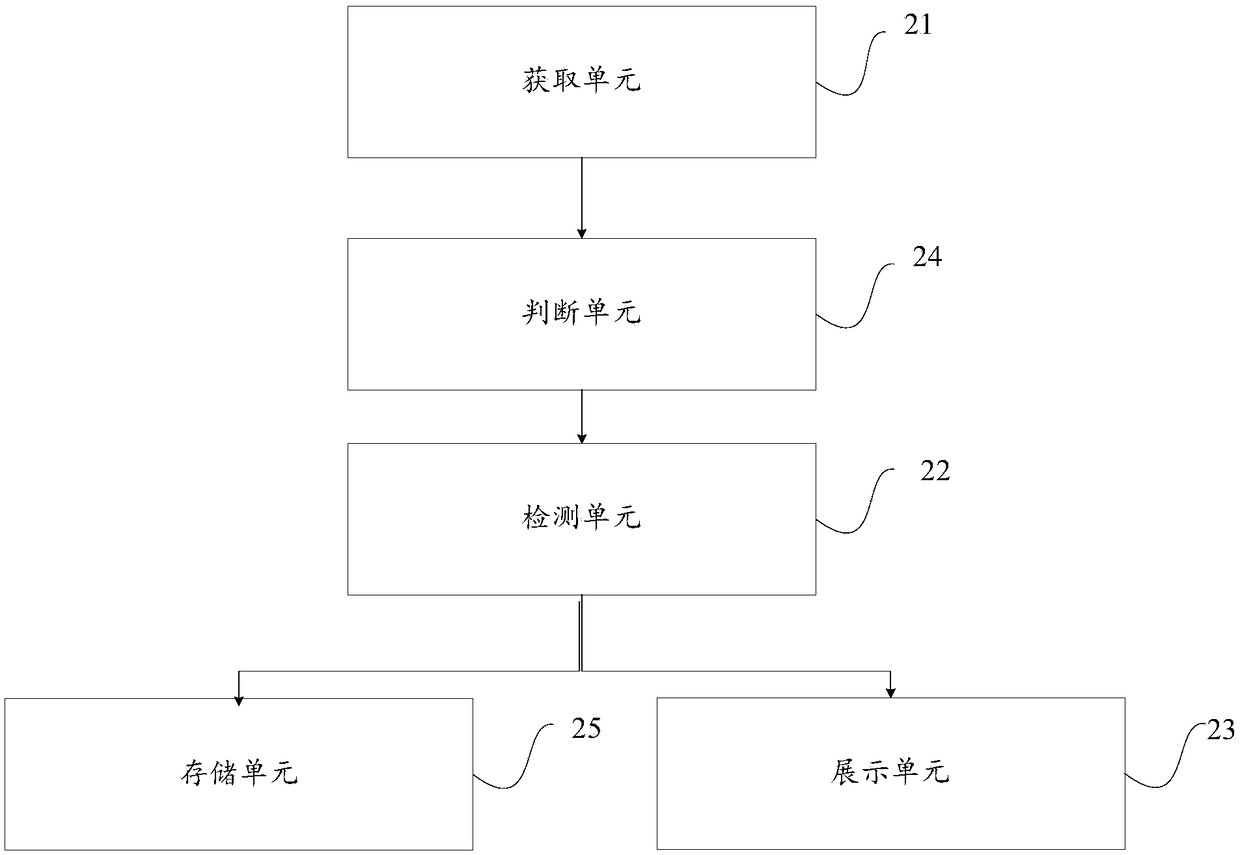
Method and device for detection of device loophole information and computer device
PendingCN109194615ATo achieve the purpose of security protectionTransmissionEmbedded systemVulnerability
The embodiment of the invention provides a method and a device for detection of device loophole information and a computer device. The method comprises the steps of: obtaining basic information of allthe devices in a current local area network; performing loophole detection for the basic information of all the devices based on a preset loophole detection rule, and obtaining and displaying loophole detection result information; and finally, performing detection of the loophole information of all the devices in the current local area network, and displaying the loophole detection result information of each device to users so as to perform safety early warning of the users and achieve the purpose of the safety protection.
Owner:BEIJING QIHOO TECH CO LTD
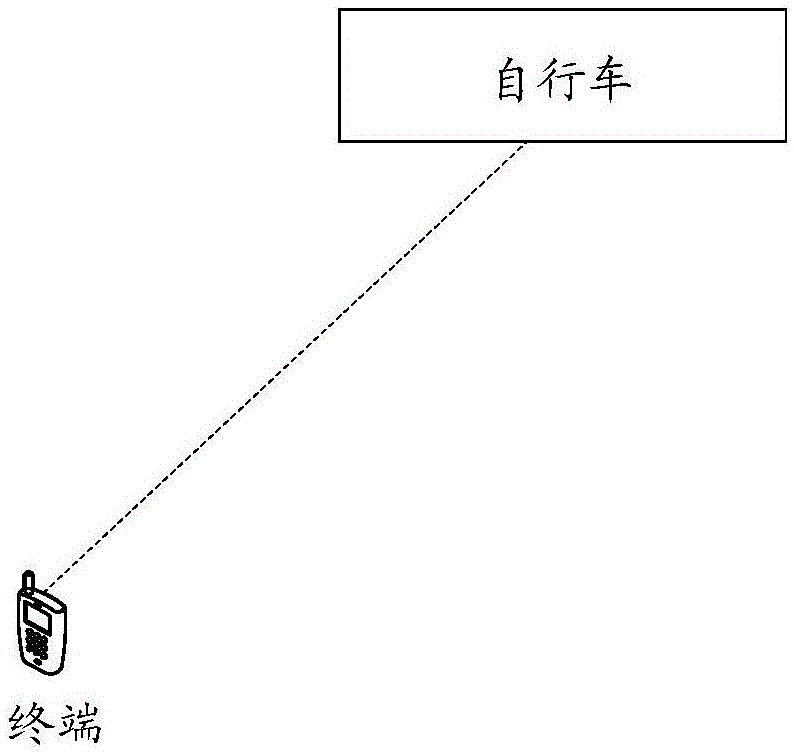
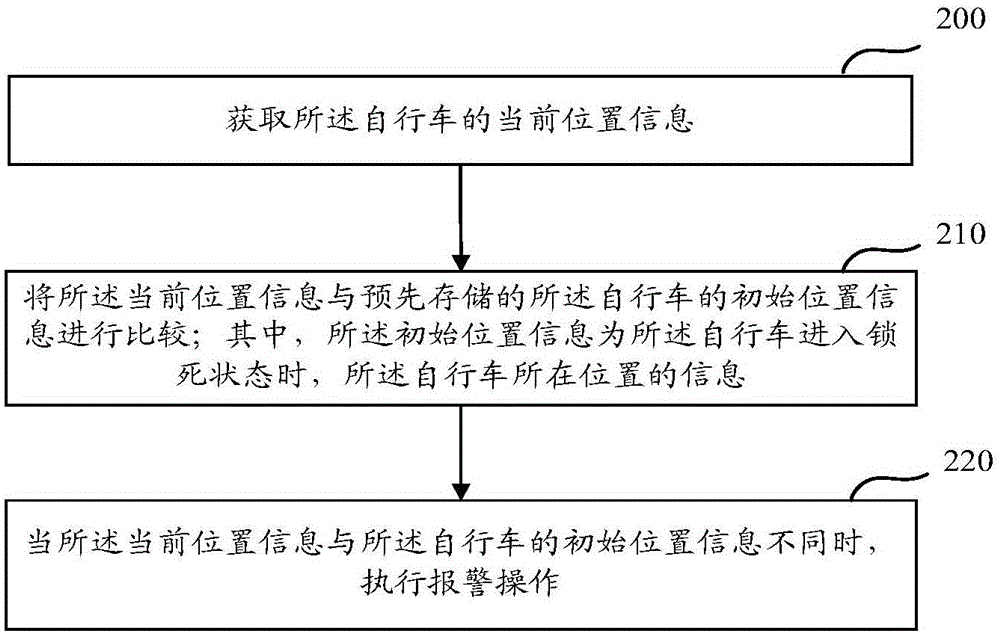
Theft preventing method and device for bicycle
InactiveCN105882804AImprove anti-theft performanceTo achieve the purpose of security protectionAnti-theft cycle devicesAnti-theft devicesSimulationReal-time computing
Owner:LETV SPORTS CULTURE DEV (BEIJING) CO LTD
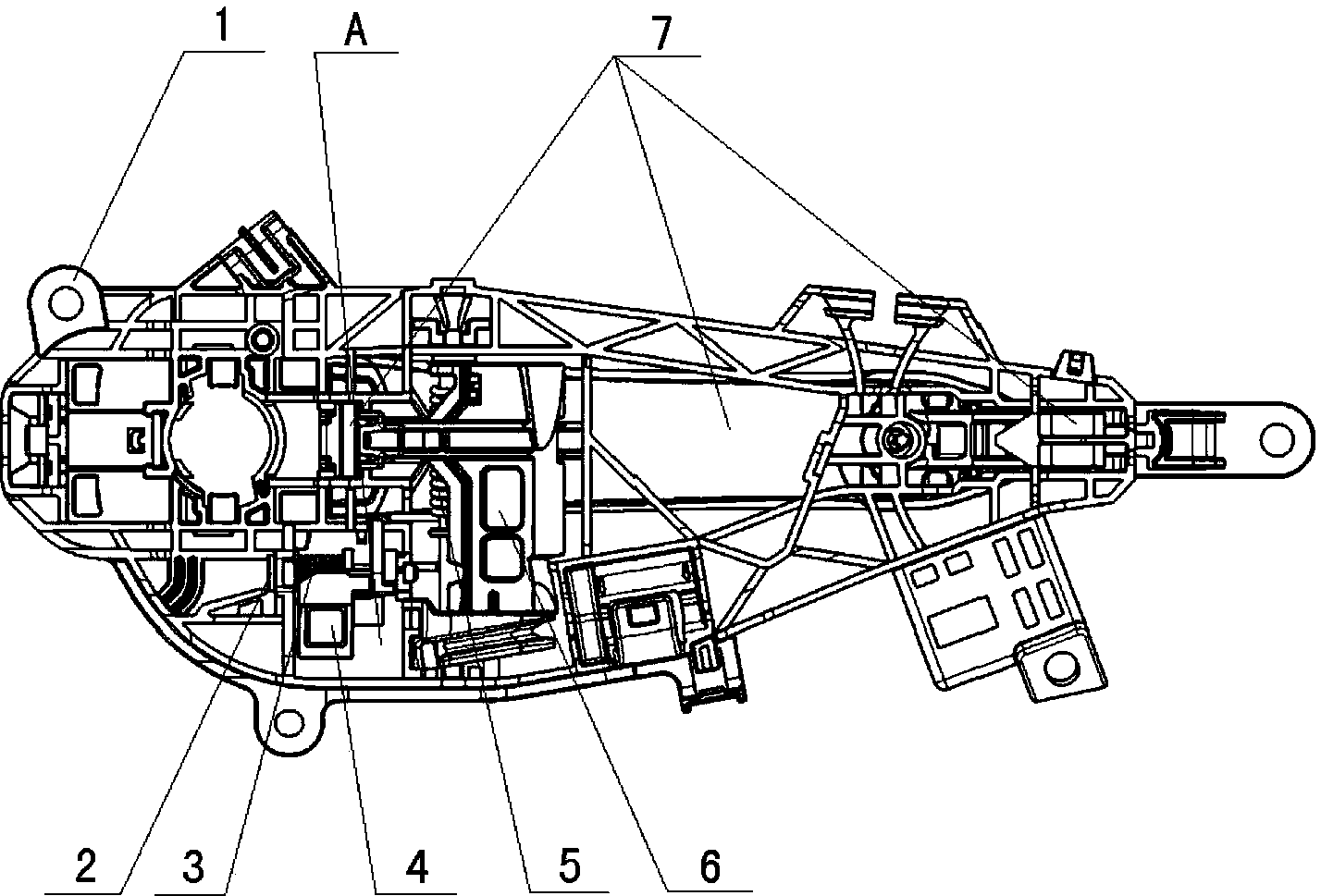
Locking mechanism for preventing interlink impact inertia accidental vehicle door opening
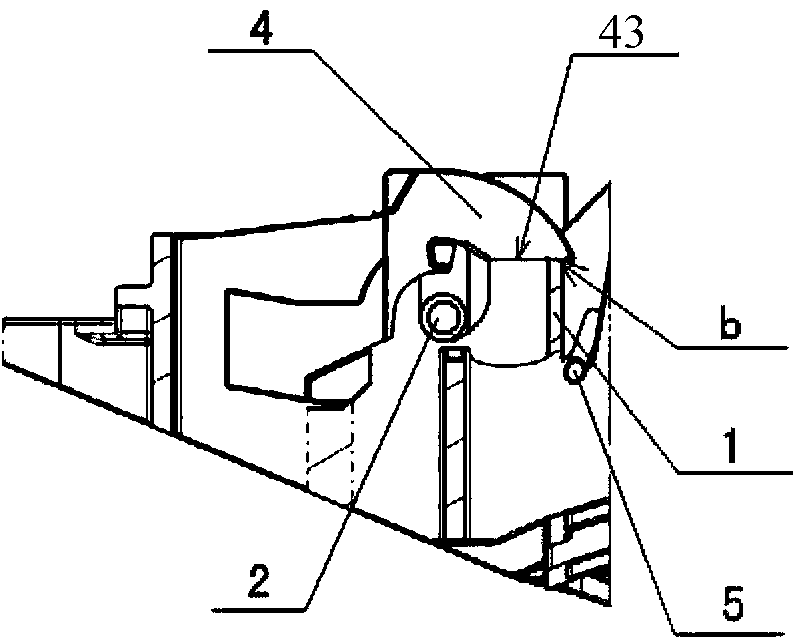
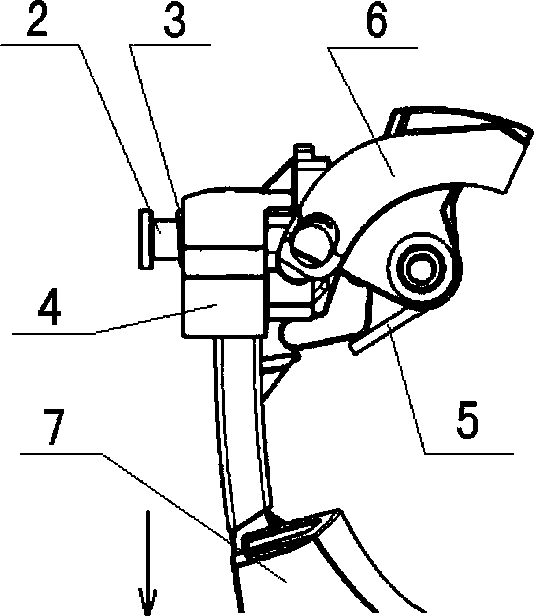
ActiveCN104120916ATo achieve the purpose of security protectionEasy to useAccident situation locksHandle fastenersLocking mechanismEngineering
The invention relates to the field of handle bases for vehicles, in particular to a locking mechanism for preventing interlink impact inertia accidental vehicle door opening. The locking mechanism for preventing interlink impact inertia accidental vehicle door opening comprises a base (1) and a handle body (7) and is characterized by further comprising a rotating shaft (2), a locking return torsional spring (3), an inertia locking block (4), a balance return torsional spring (5) and a balance block (6), a locking block groove is formed in the base (1), and the two ends of the locking return torsional spring (3) abut against the locking block groove and the inertia locking block (4) respectively; the inertia locking block (4) is composed of a lock block (41), a lock wheel (42) and a lock claw (43); a balance block groove is further formed in the base (1), the two ends of the balance return torsional spring (5) abut against the balance block groove and the balance block (6) respectively, and the lock claw (43) right faces the balance block (6). The locking mechanism is simple in structure, convenient to install, high in adaptability, safe and reliable.
Owner:烟台霍富汽车锁有限公司
Information processing method and terminal thereof
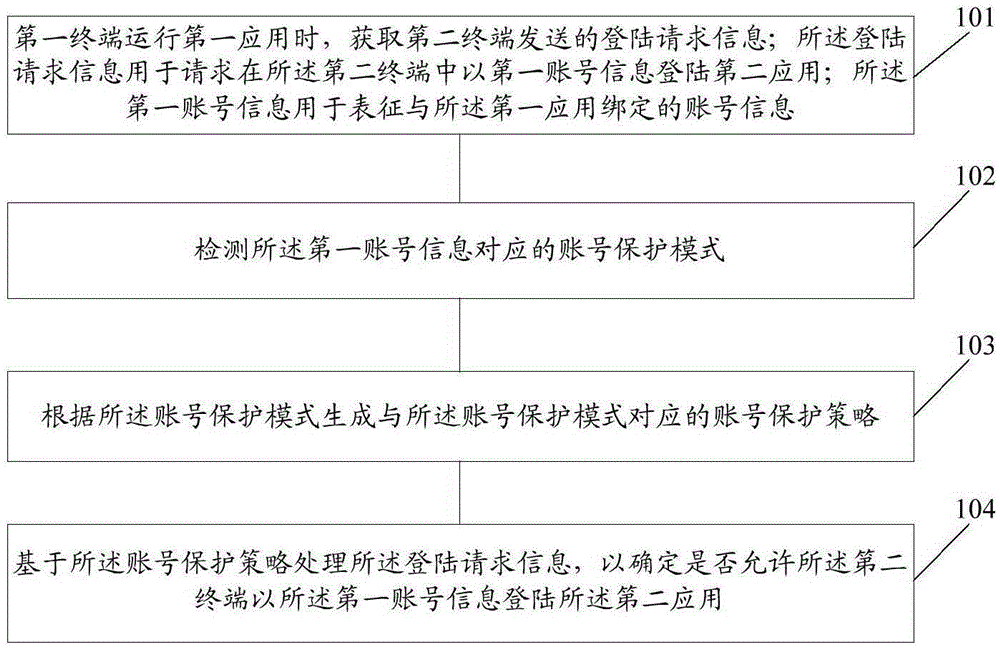
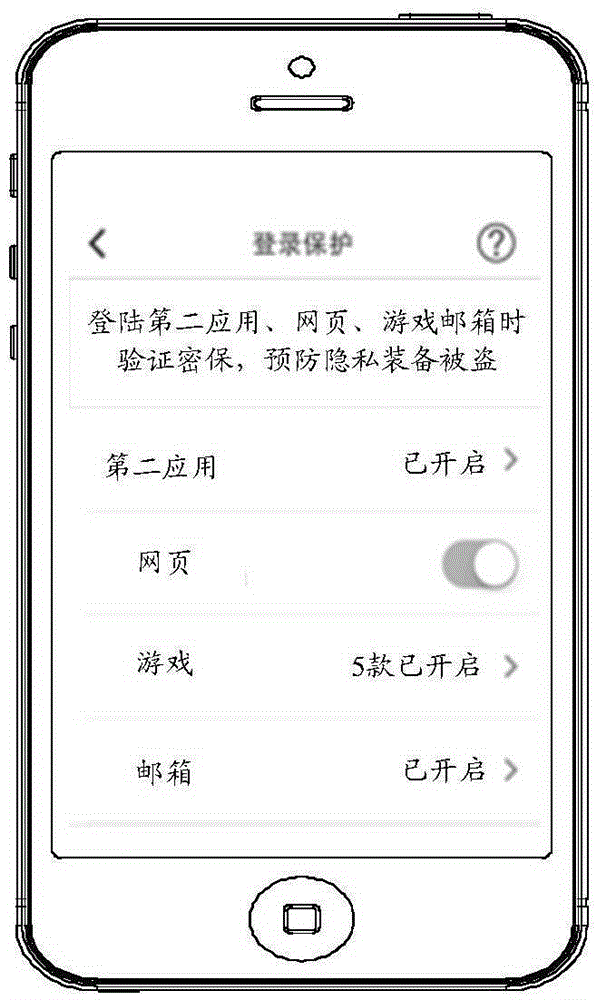
ActiveCN105429943ATo achieve the purpose of security protectionTransmissionInformation processingComputer terminal
The embodiment of the invention discloses an information processing method and a terminal thereof. The method comprises: when a first terminal running a first application, obtaining the registration request information sent by a second terminal, wherein the registration request information is used for requesting registering a second application with first account number information in the second terminal, and the first account number information is used for representing the account number information bonded to the first application; detecting an account number protection mode corresponding to the first account number information; according to the account number protection mode, generating an account number protection strategy corresponding to the account number protection mode; and processing the registration request information based on the account number protection strategy, so as to determine whether allowing the second terminal to register the second application with the first account number information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
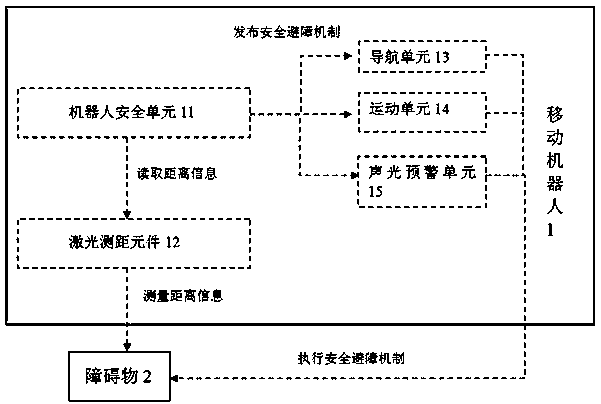
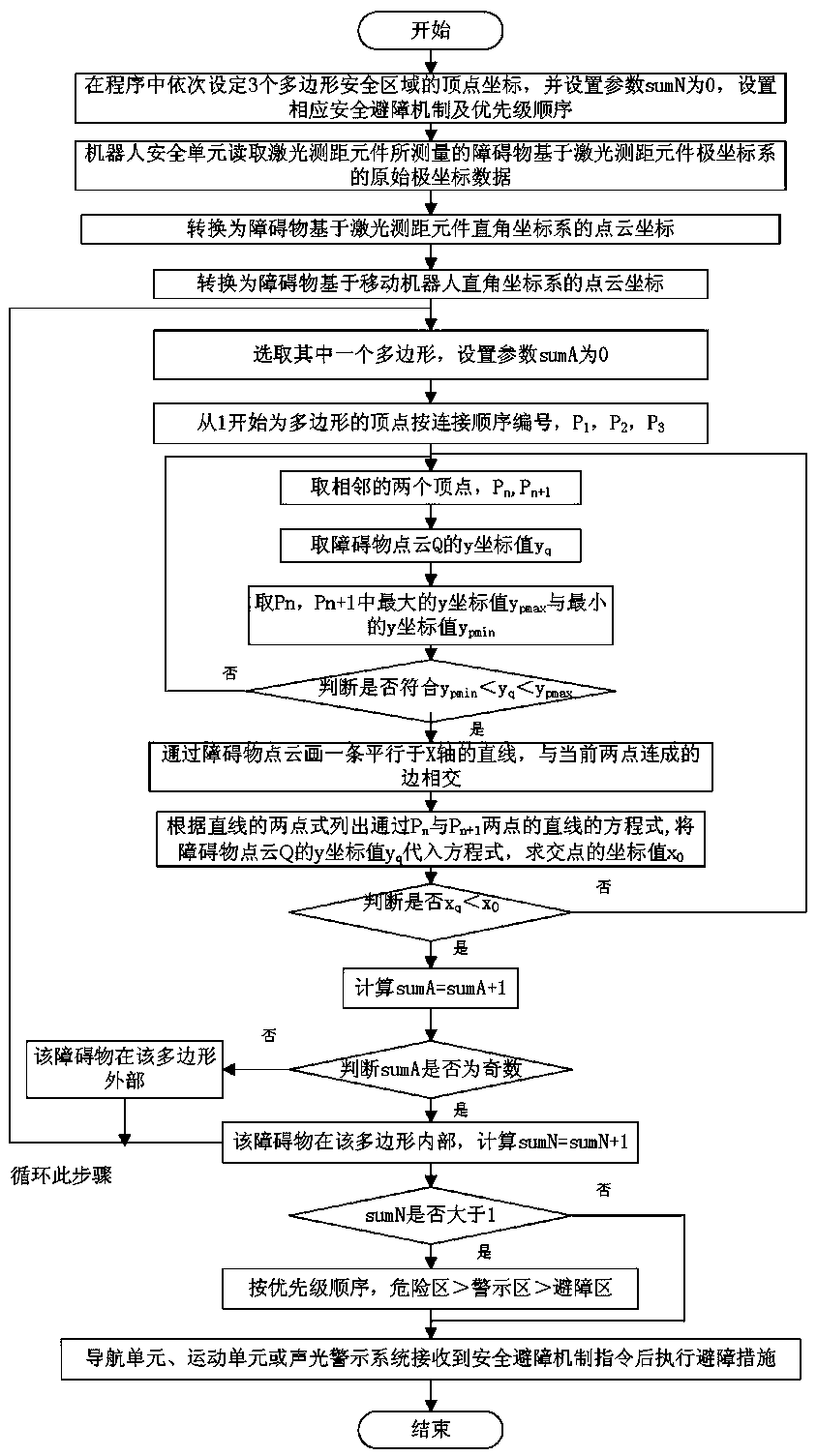
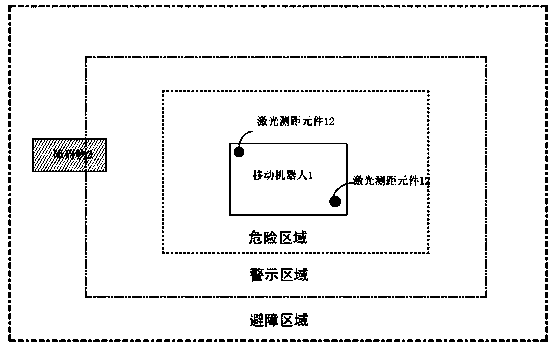
Mobile robot virtual safety protection area protection system and method
ActiveCN110874102AGuaranteed operating efficiencyTo achieve the purpose of security protectionControl safety arrangementsPosition/course control in two dimensionsLaser rangingData transformation
The invention discloses a mobile robot virtual safety protection area protection system and method. The system comprises a mobile robot, a robot safety unit and a laser ranging element, the robot safety unit is used for setting ranges of different virtual safety protection areas and safety obstacle avoidance mechanisms of the robot in different areas; the laser ranging element measures the distance information of an obstacle; and the robot safety unit reads the distance data measured by the laser ranging element, converts the distance data into a data value in the same coordinate system with the virtual safety protection areas through coordinate conversion, judges the area where the obstacle is located through adoption of an algorithm, and executes the corresponding safety obstacle avoidance mechanism according to a priority principle; and under the condition that the safety requirement is met, the cost is reduced, safe use of the small laser ranging element on the robot is achieved, the safety distance can be flexibly adjusted, and the safety requirement of the robot in different application scenes is met.
Owner:TIANJIN LIANHUI OIL GAS TECH CO LTD
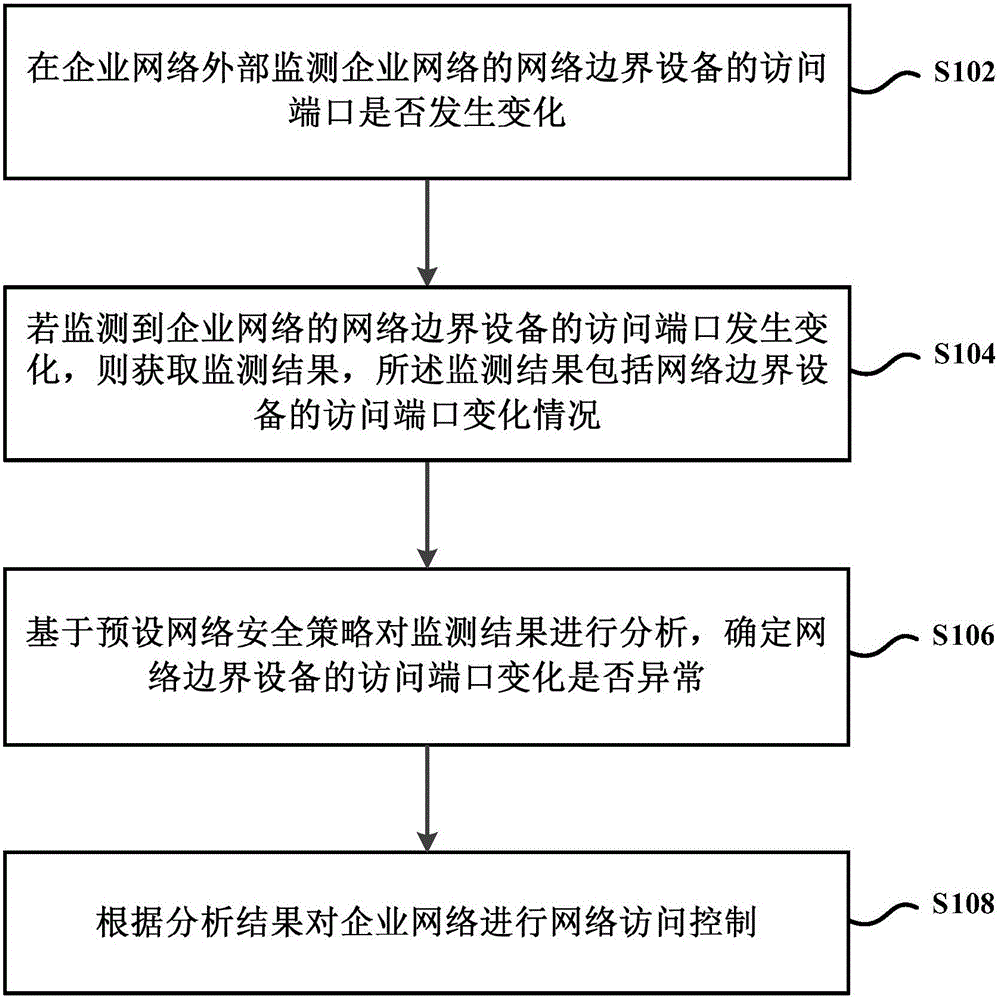
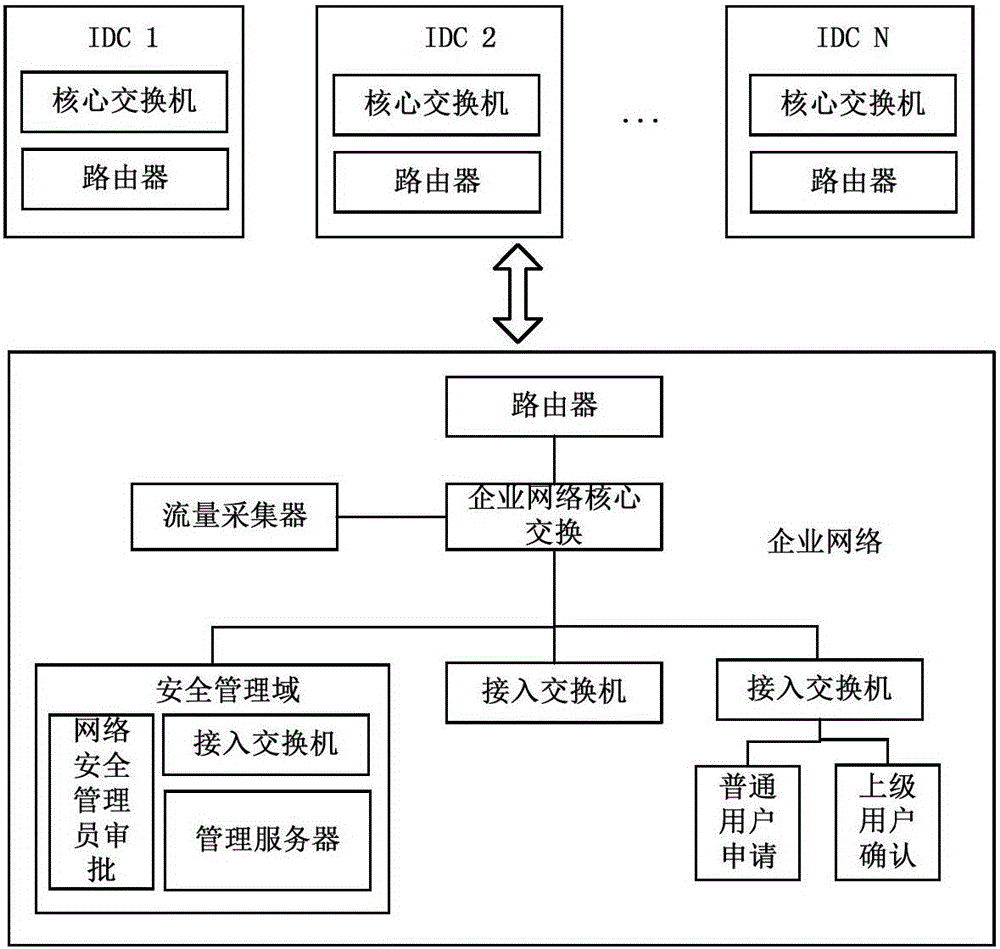
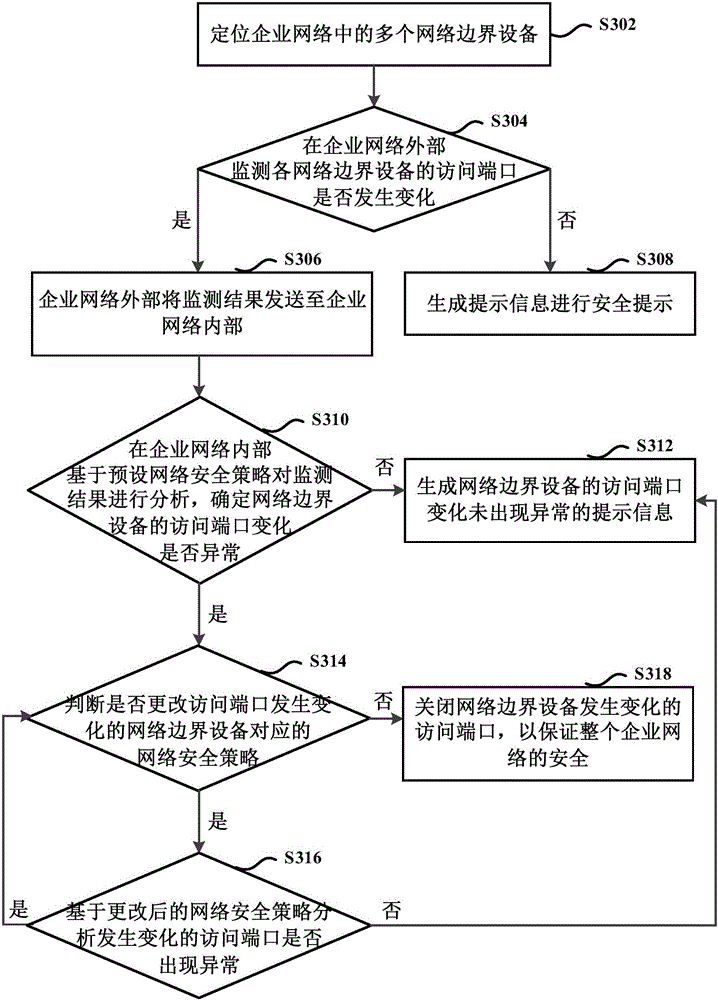
Enterprise network access control method and device
ActiveCN106060040ATo achieve the purpose of security protectionRealize monitoringTransmissionNetwork Access ControlSecurity policy
The present invention provides an enterprise network access control method and device. The method comprises: monitoring whether the access port of a network boundary device of an enterprise network has changes at the exterior of the enterprise network or not; if it is monitored that the access port of a network boundary device of an enterprise network has changes at the exterior of the enterprise network, obtaining a monitoring result, wherein the monitoring result includes the access port change condition of the network boundary device; analyzing the monitoring result based on the presetting network safety strategy, and determining whether the access port changes of the network boundary device are abnormal or not; and performing network access control of the enterprise network according to the analysis result. According to the embodiment of the invention, the enterprise network boundary protection condition is controlled in real time and the enterprise network is safely protected.
Owner:BEIJING PIPAXING TECH CO LTD
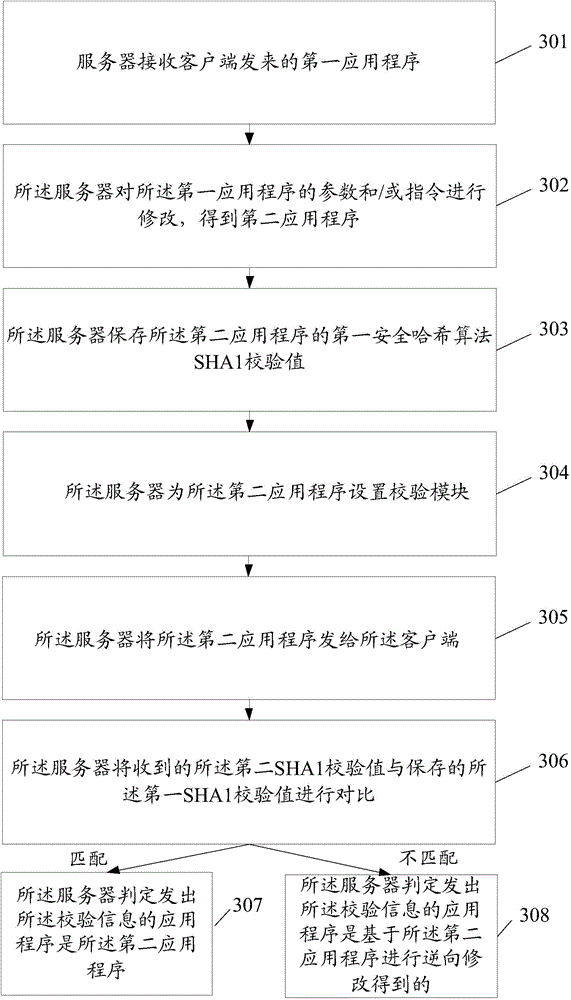
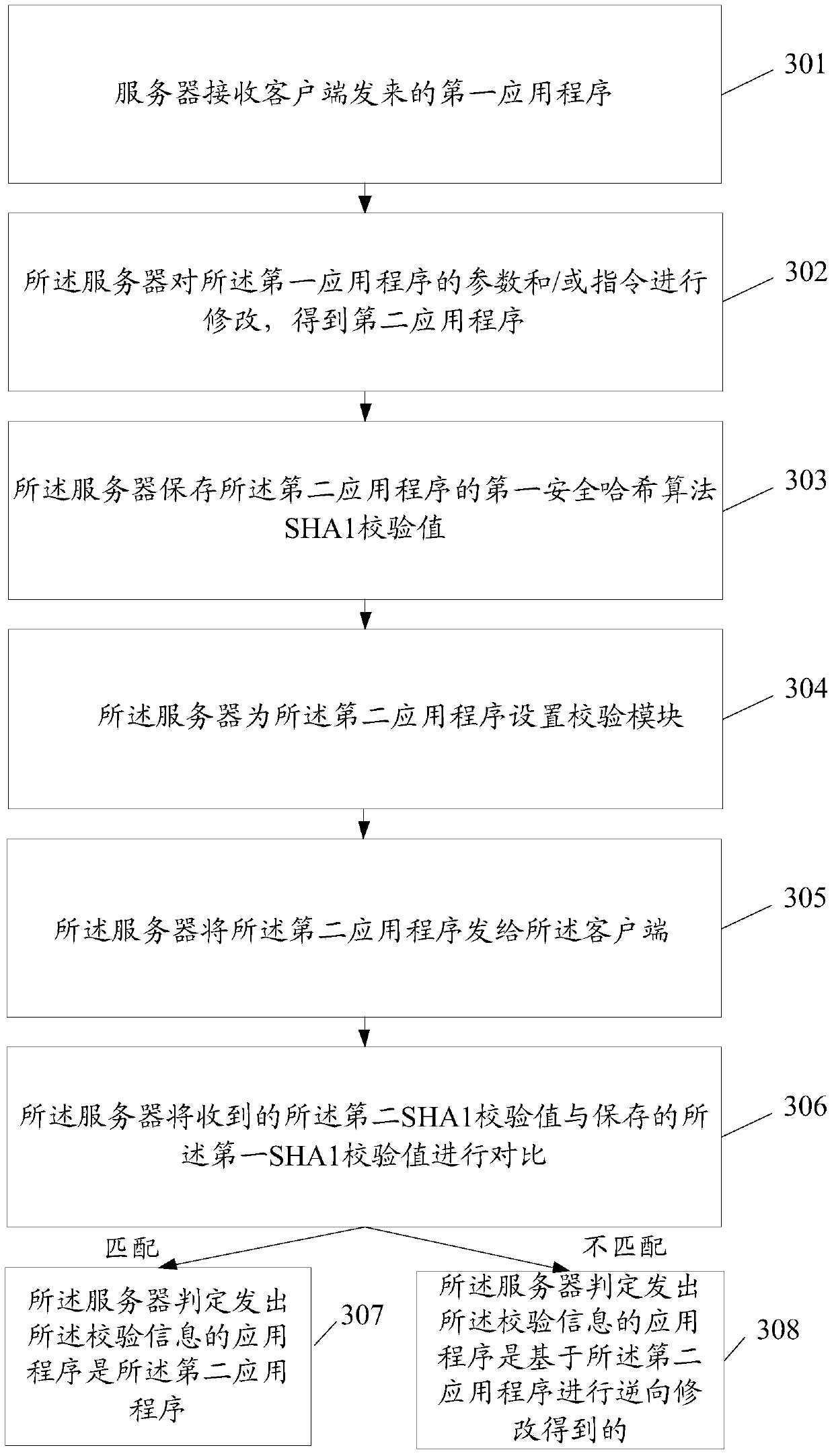
Safety protection method of application programs and server
ActiveCN105678120ATo achieve the purpose of security protectionPrevent decompilationTransmissionProgram/content distribution protectionApplication softwareComputer science
The invention discloses a safety protection method of application programs and a server. The method comprises following steps: receiving a first application program sent from a client by the server; collecting parameters / instructions of the first application program by the server in order to obtain a second application program such that the second application program can normally operate and enable a reverse tool to exit by fault when the reverse tool is utilized for analyzing the second application program; and sending the second application program to the client by the server.
Owner:CHINA MOBILE COMM GRP CO LTD
Method and system adopting number of image elements as security code
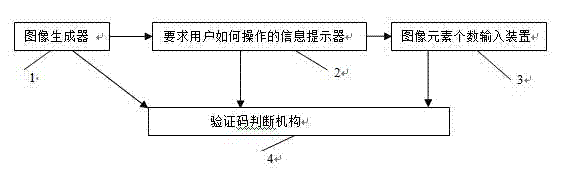
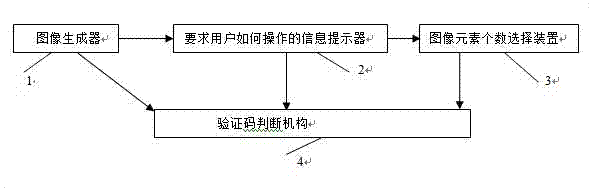
InactiveCN102882681AEasy to identifyOvercome correct parsingUser identity/authority verificationInput deviceOperational requirements
The invention discloses a method and a system adopting the number of image elements as a security code. The system comprises an image generator, an information prompter for requiring users to operate, an image element number input device and a security code judgment mechanism, and is characterized in that the image generator generates at least one image, the information prompter for requiring users to operate generates prompt information to ask the users to input the number of specified image elements in corresponding images, the users input the numbers of the specified image elements corresponding to the images through the image element number input device according to the operational requirements, and the security code judgment mechanism judges whether the numbers of the specified image elements of the corresponding images, input by the users, are all correct or not, if yes, determines that the users receive security code approvals and otherwise, determines that the users do not receive security code approvals. The method and the system have the remarkable effect that the designs of image elements in various different forms can be completely identified easily by people but hardly by machines.
Owner:张仁平
Crane safety mechanism control system
InactiveCN101830401ATo achieve the purpose of security protectionLow costSafety gearControl systemElectrical control
The invention provides a crane safety mechanism control system. The system is arranged on a crane in an electric control mode of a pawl, and the pawl is pulled by controlling an electromagnet in the system so as to fulfill the aim of achieving safety protection on the crane. The system has the advantages that: the aim of achieving safety protection on the crane is fulfilled; improvements are made on used equipment, so the cost is low; and the system is simple and convenient to operate and has sensitive action after modification.
Owner:CHINA FIRST METALLURGICAL GROUP
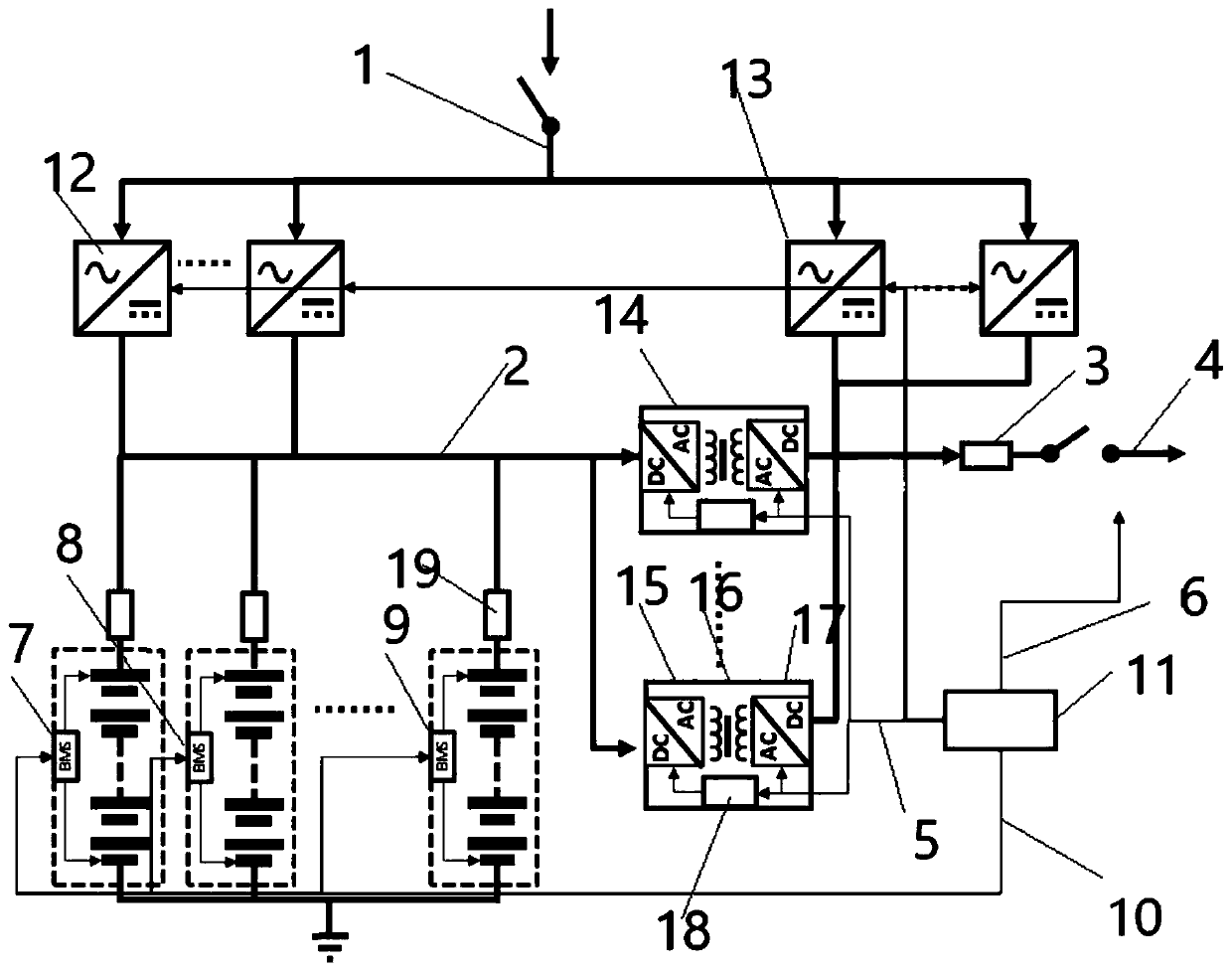
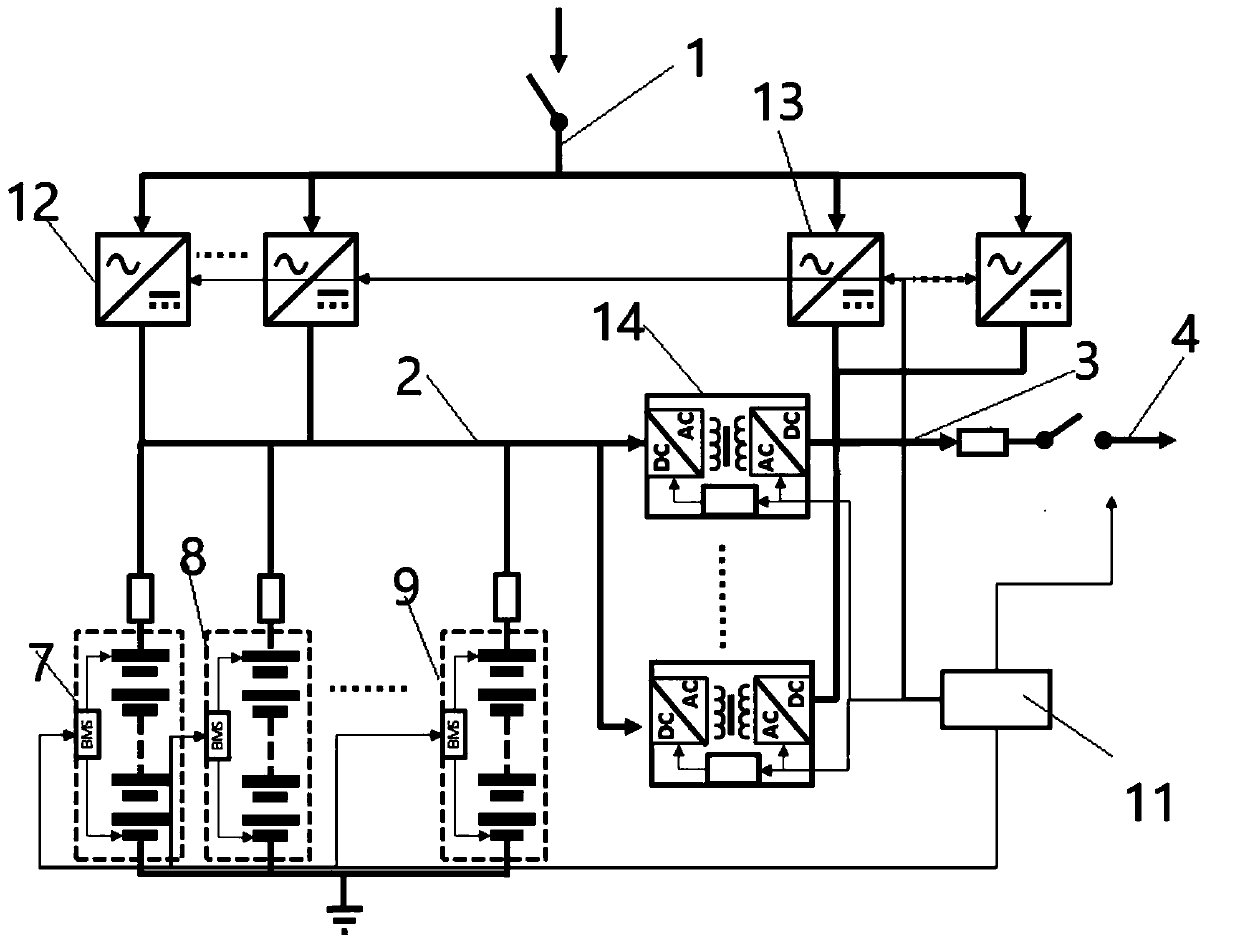
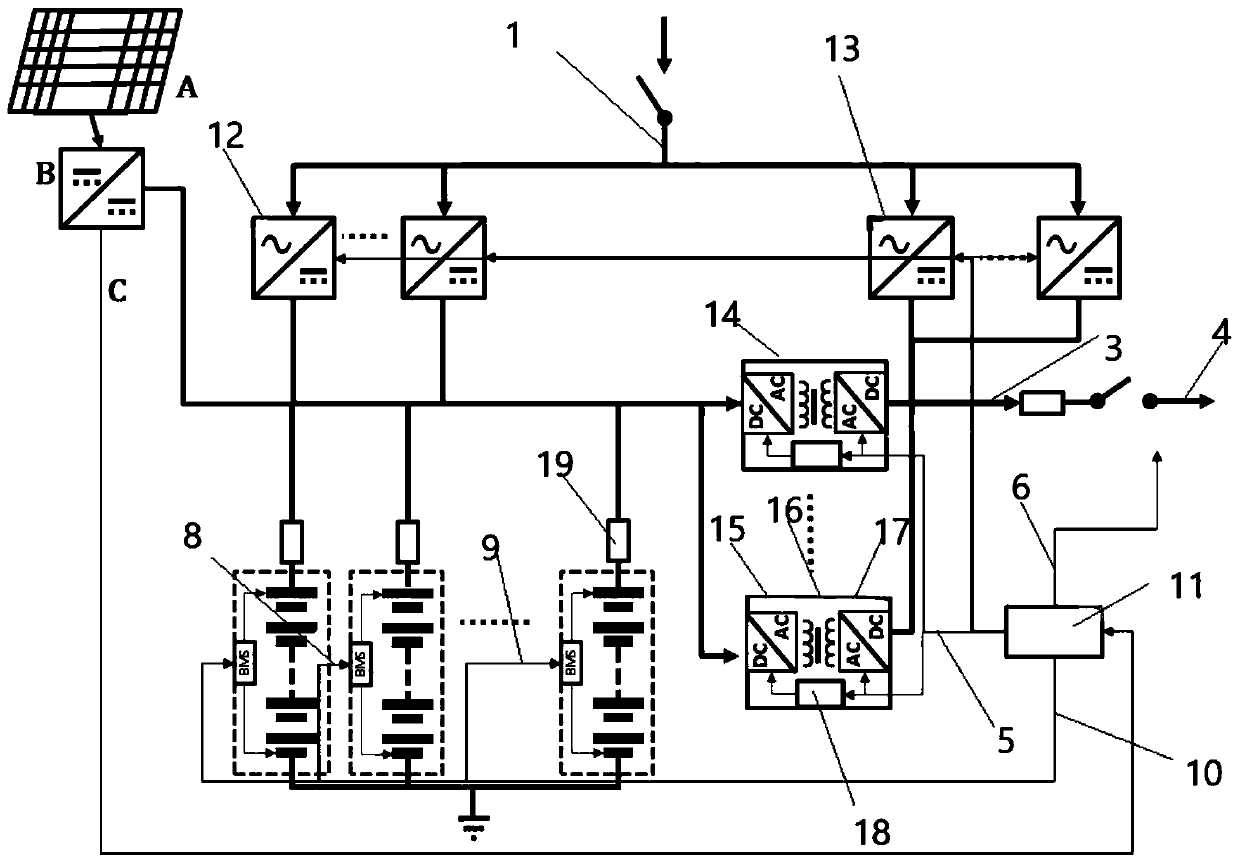
Energy storage charging system
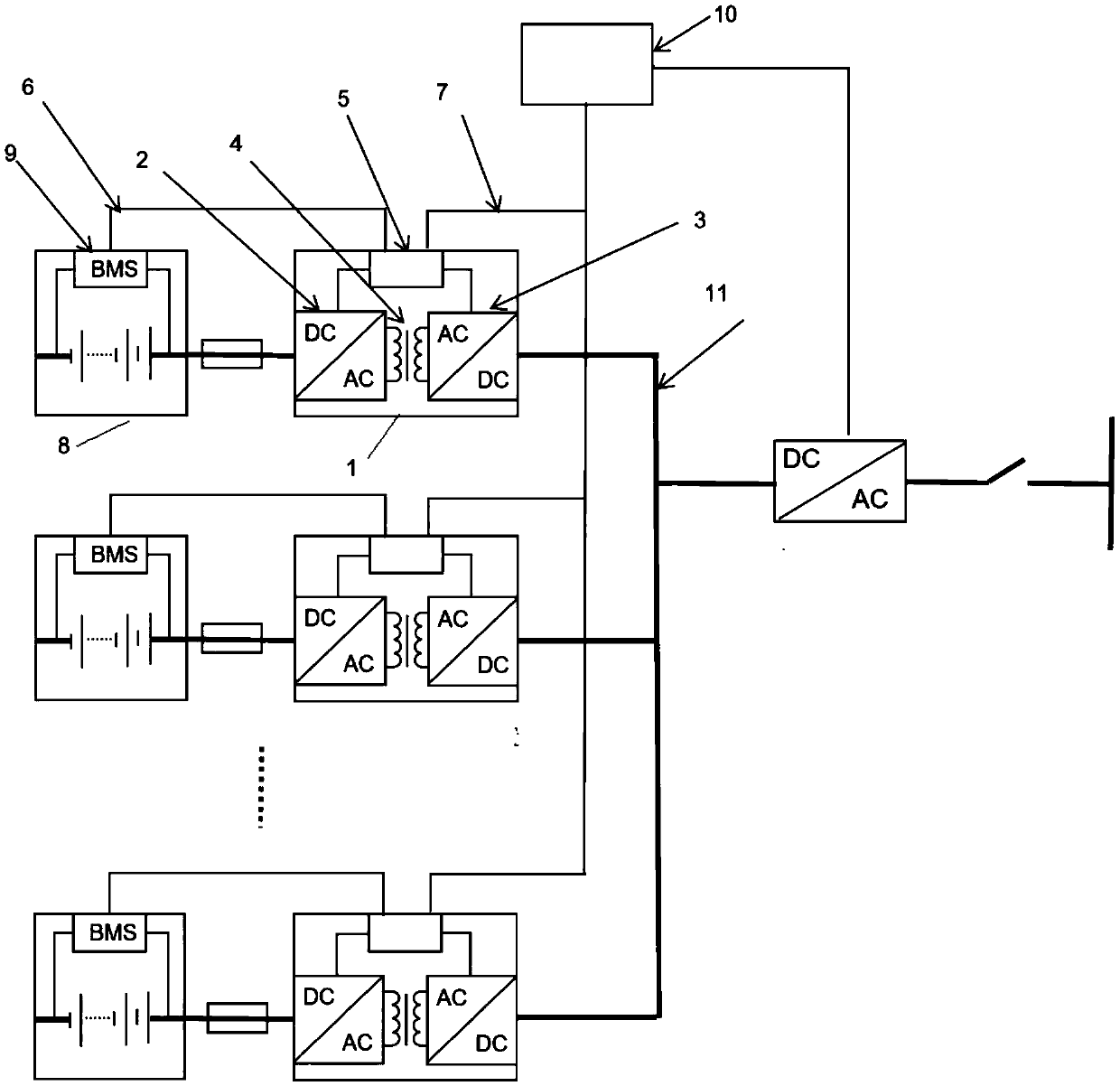
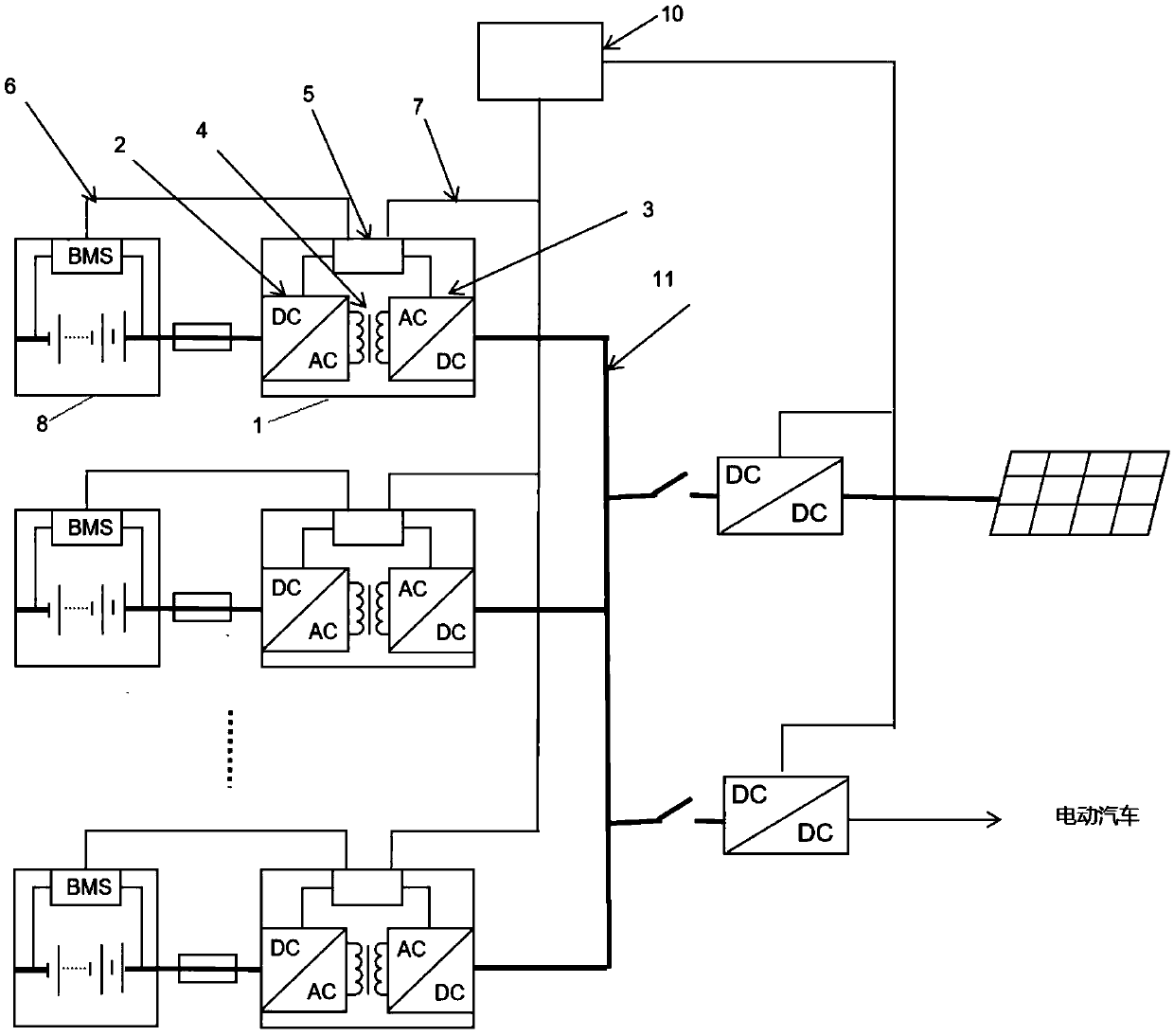
PendingCN109921496AReduce fault currentTo achieve the purpose of security protectionDc network circuit arrangementsCharging stationsEngineeringElectric vehicle
The invention discloses an energy storage charging system, which comprises an AC / DC converter and a DC / DC converter, wherein the high-frequency isolation conversion AC / DC converter takes power from power grid to supply power to a load, and the high-frequency isolation conversion DC / DC converter discharges power from battery to supply power to the load. The energy storage charging system is chargedby converting the charging ACDC into direct current electric energy, and meanwhile, the high-frequency isolated DCDC conversion device can discharge electricity to the load power supply bus, and simultaneously, the ACDC connected with the alternating current converts the alternating current electric energy into direct current electric energy to the load power supply bus to supply power to the load. The charging ACDC is isolated through the high-frequency isolation transformer, and the electric energy passing through a transformer is adjusted, so that the charging voltage and current of the direct-current bus to an energy storage device are adjusted; and a power supply DCDC is isolated through the high-frequency isolation transformer, the electric energy passing through the transformer isadjusted, and the power supply voltage and current of the load power supply bus are adjusted, so that the purpose of charging an electric vehicle or other types of loads is achieved.
Owner:SHENZHEN YINGFEIYUAN TECH CO LTD
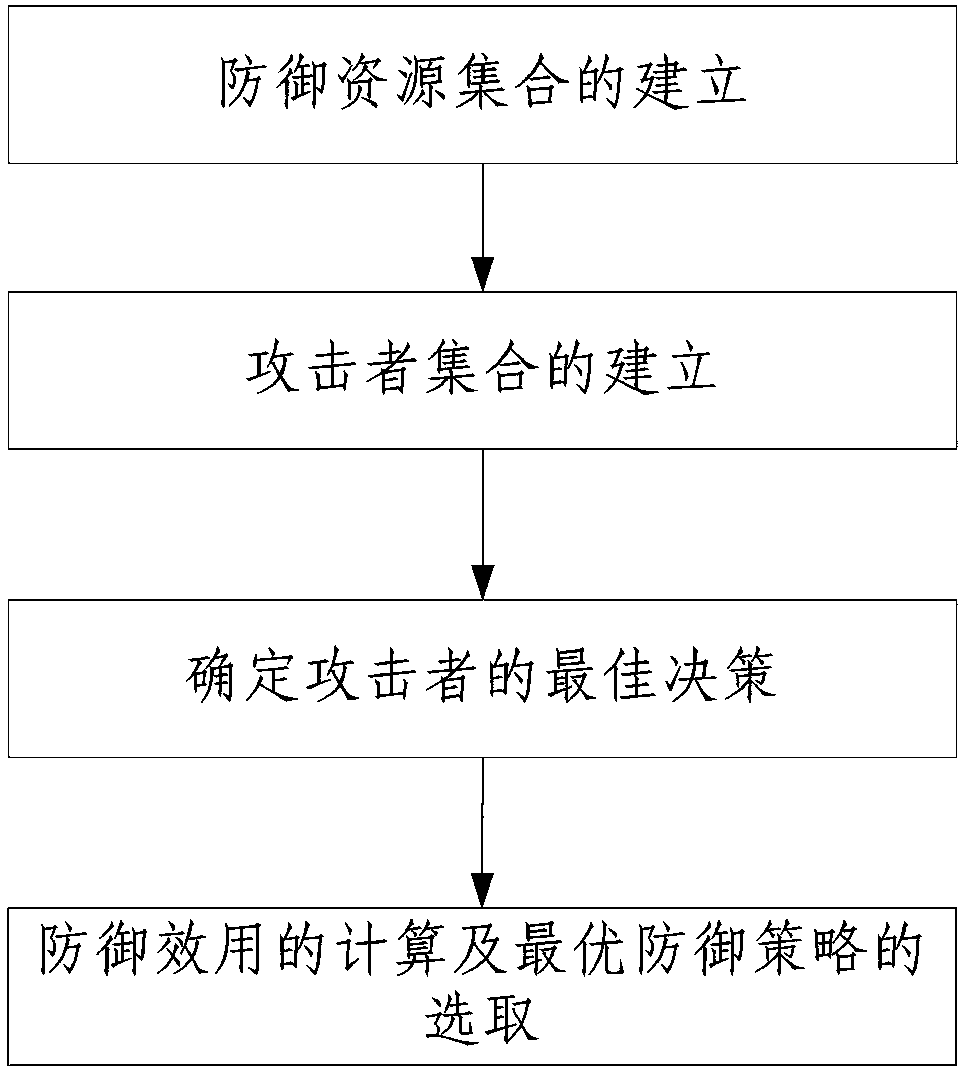
Website defense strategy selection method based on offensive and defensive gaming
ActiveCN108322478AThe method steps are simpleReasonable designTransmissionOptimal decisionComputer science
The invention discloses a website defense strategy selection method based on offensive and defensive gaming. The method comprises the following steps: 1. establishing a defense resource set; 2, establishing an attacker set; 3, determining best decision of an attacker; and 4, calculating a defense utility and selecting the optimal defense strategy. The method of the invention has simple steps, reasonable design and convenient implementation, the best decision of the attacker is obtained through multiple simulated attacks, thereby obtaining the optimal defense strategy of the defender, being closer to the real offensive and defensive gaming process, and improving the accuracy and practicability of selecting the website defense strategy.
Owner:XIAN UNIV OF POSTS & TELECOMM
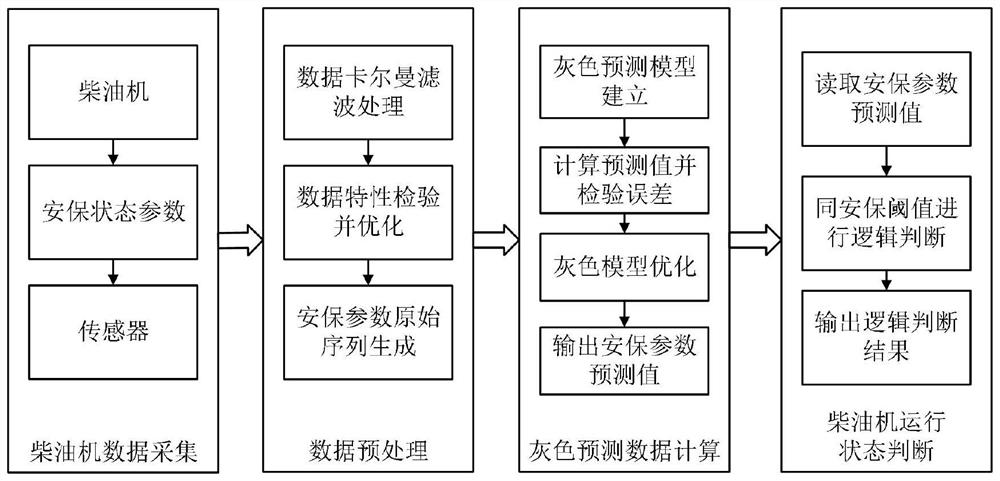
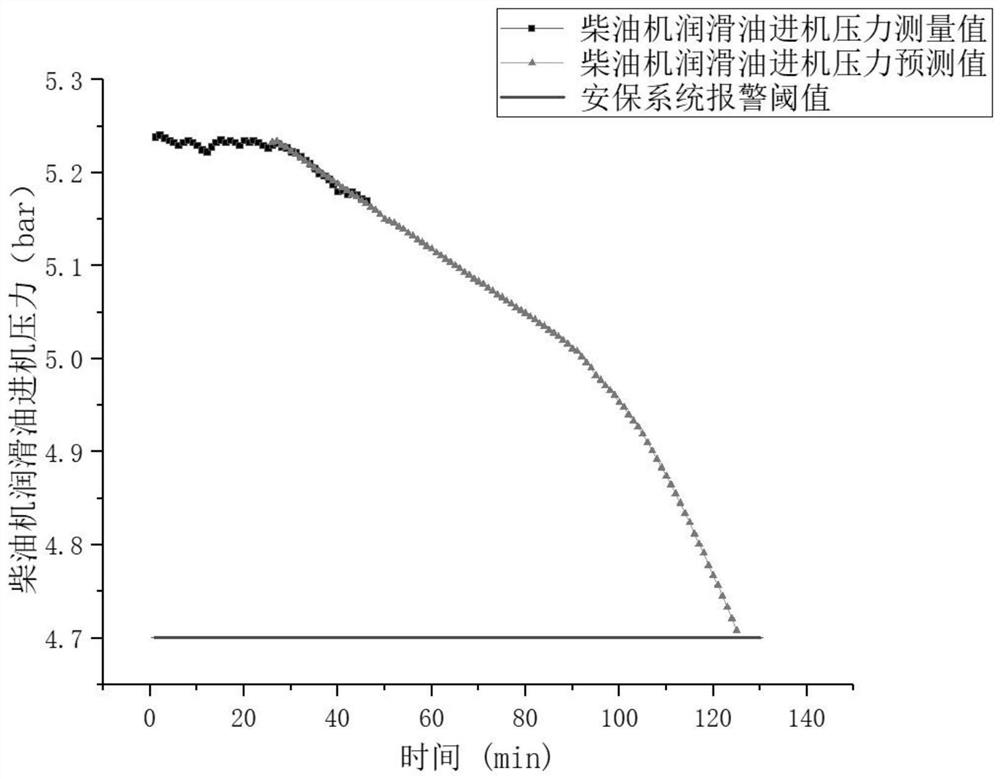
Diesel engine lubricating oil feeding security parameter prediction method based on grey theory
InactiveCN111855219ATo achieve the purpose of security protectionGuaranteed operational safetyInternal-combustion engine testingComplex mathematical operationsError checkingPredictive function
The invention relates to a diesel engine lubricating oil feeding security parameter prediction method based on a grey theory, which belongs to the technical field of diesel engine safety prediction. The method comprises the steps of firstly collecting the operation data of the diesel engine lubricating oil feeding pressure and temperature, and carrying out the Kalman filtering of the operation data, then, according to the modeling steps of the grey prediction model, achieving the prediction function of diesel engine operation data and acquiring a prediction result, checking the grey predictionmodel by using a relative error checking method, optimizing the grey model by using a residual error method if the grey prediction model does not meet the fourth-level checking index until the grey model meets the fourth-level and higher-level indexes, and outputting accurate prediction data, and on the basis that the relative error of the prediction data is verified to be qualified, performing logic discrimination on the prediction result and a diesel engine alarm threshold, and outputting a prediction state result to an upper computer. According to the method, the change trend of the dieselengine lubricating oil feeding parameters can be effectively predicted, and the future working state of the diesel engine lubricating oil system is reasonably predicted.
Owner:HARBIN ENG UNIV
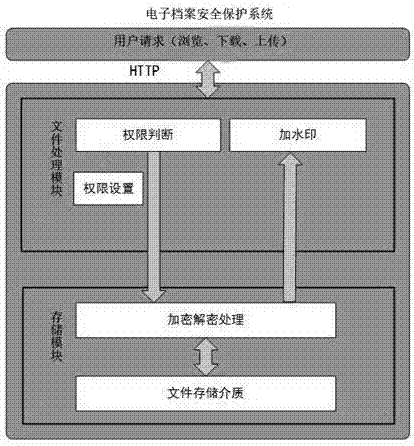
Electronic archive safety protection system
InactiveCN107343009APrevent leakageTo achieve the purpose of security protectionTransmissionDocument handlingComputer module
The invention discloses an electronic archive safety protection system including a user terminal, a file processing module, and a storage module, wherein after a user logs in to the user terminal, the user terminal sends a login request to the file processing module, the file processing module decrypts the encrypted file in the storage module after determining the login user's permission, and then pushes the encrypted file to the user terminal and adds a watermark to the file.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
High-frequency isolation conversion energy storage system
PendingCN109672260AReduce fault currentTo achieve the purpose of security protectionBatteries circuit arrangementsDc source parallel operationEnergy storageMutual influence
The invention discloses a high-frequency isolation conversion energy storage system, which comprises high-frequency isolation conversion two-way DC / DC conversion devices and a direct current bus, wherein a first connecting point of each two-way DC / DC device is connected with an energy storage device; a second connecting point is connected to the direct current bus; through the two-way DC / DC devices, electric energy in the energy storage devices can be subjected to two-way alternating with the direct current bus through high-frequency isolation conversion. A plurality of energy storage devicesare isolated from the high-frequency isolation transformers of the two-way conversion devices subjected to high-frequency isolation from the direct current bus; the electric energy passing through a transformer is limited, so that the fault current of the direct current bus is reduced; the goal of safe protection is achieved; the plurality of groups of energy storage devices are connected with thebus through respectively independent two-way isolation conversion devices; the differences among different energy storage devices cannot generate mutual influence; the energy storage devices with different properties can even be used in a combined way.
Owner:SHENZHEN YINGFEIYUAN TECH CO LTD
Monitoring and protecting device and system and method of electrical load
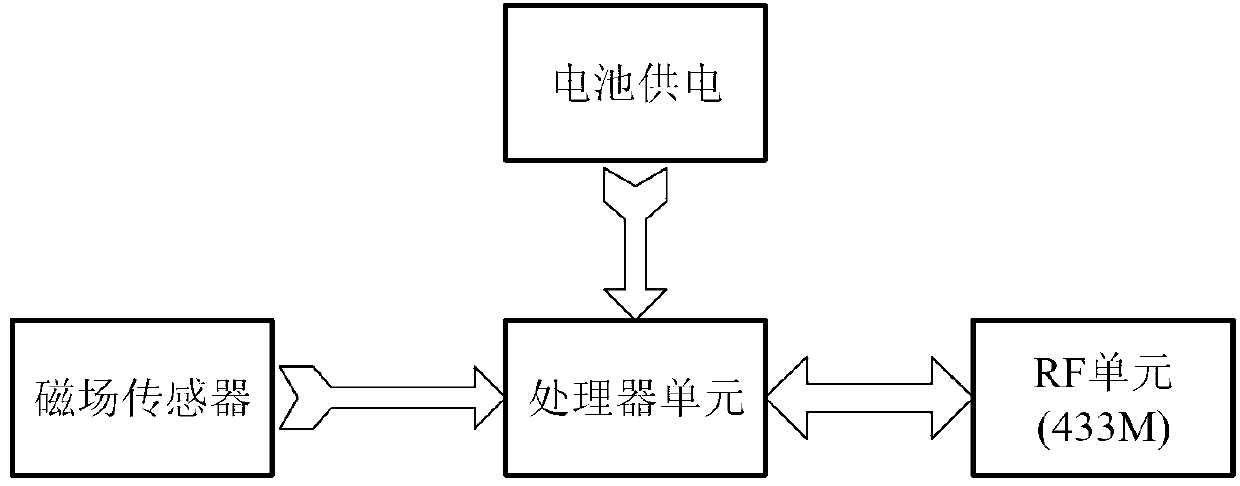
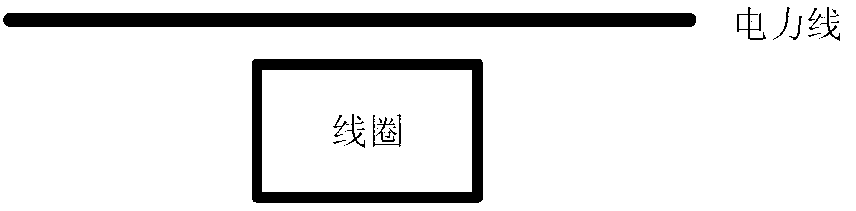
ActiveCN102981441ATo achieve the purpose of security protectionProgramme controlComputer controlElectromagnetic fieldCalibration coefficient
The invention discloses a monitoring and protecting device, a system and a method of electrical load. The system comprises a magnetic field collecting device and an electrical load monitoring and protecting device. The magnetic field collecting device and the electrical load monitoring and protecting device are communicated in a wireless manner. After the scheme is adopted, an electromagnetic field of a primary side electric transmission line of a special transformer user is measured through the magnetic field collecting device, current value by pre-set magnetic field-current switch calibration coefficient is obtained and is transmitted to the electrical load monitoring and protecting device, electrical load monitoring can be achieved by a manner of comparing the power of the primary side with the power of a secondary side through the electrical load monitoring and protecting device, and therefore defects of complicated installation and low acceptability of users of an existing load monitoring device are solved. In addition, safe protection of electric equipment is achieved by utilizing identity authentication information of the users and an electric lock, and locking and unlocking of the electric lock can be controlled by using unique identity authentication information, and therefore the purpose of the safe protection of the electric equipment is achieved.
Owner:STATE GRID CORP OF CHINA +2
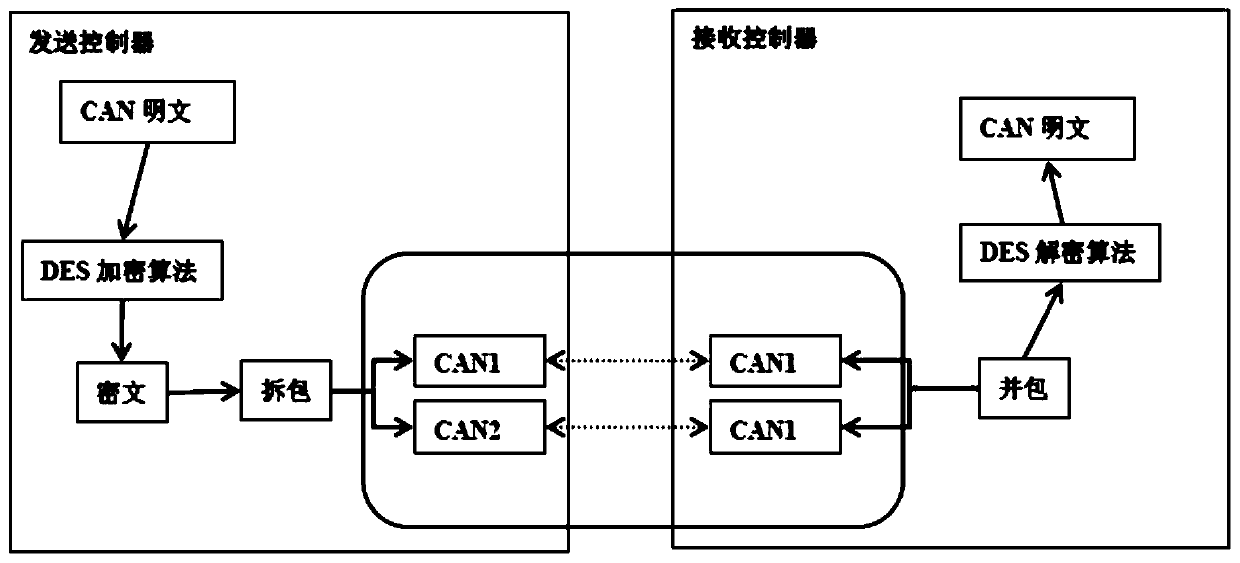
Drive-by-wire chassis CAN network encryption method
InactiveCN111314275AImplement encryptionFast implementation of encryption functionsBus networksEngineeringBus mastering
The invention discloses a drive-by-wire chassis CAN network encryption method, and the method comprises the following steps: a sending controller encrypts a CAN message plaintext by using a DES encryption algorithm to form a CAN encrypted message; the sending controller splits the encrypted message according to a specified rule; the signals are simultaneously sent to a receiving controller throughtwo paths of CAN; and the receiving controller merges the messages according to a specified rule, obtains a CAN plaintext through a DES decryption algorithm, and realizes bus control and informationinteraction.
Owner:NANJING GOLDEN DRAGON BUS
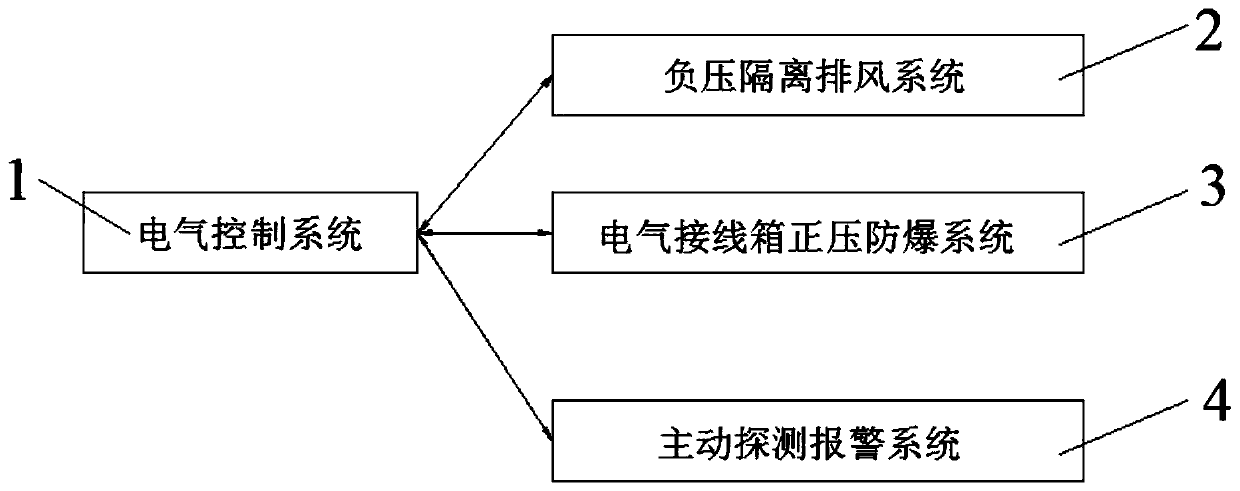
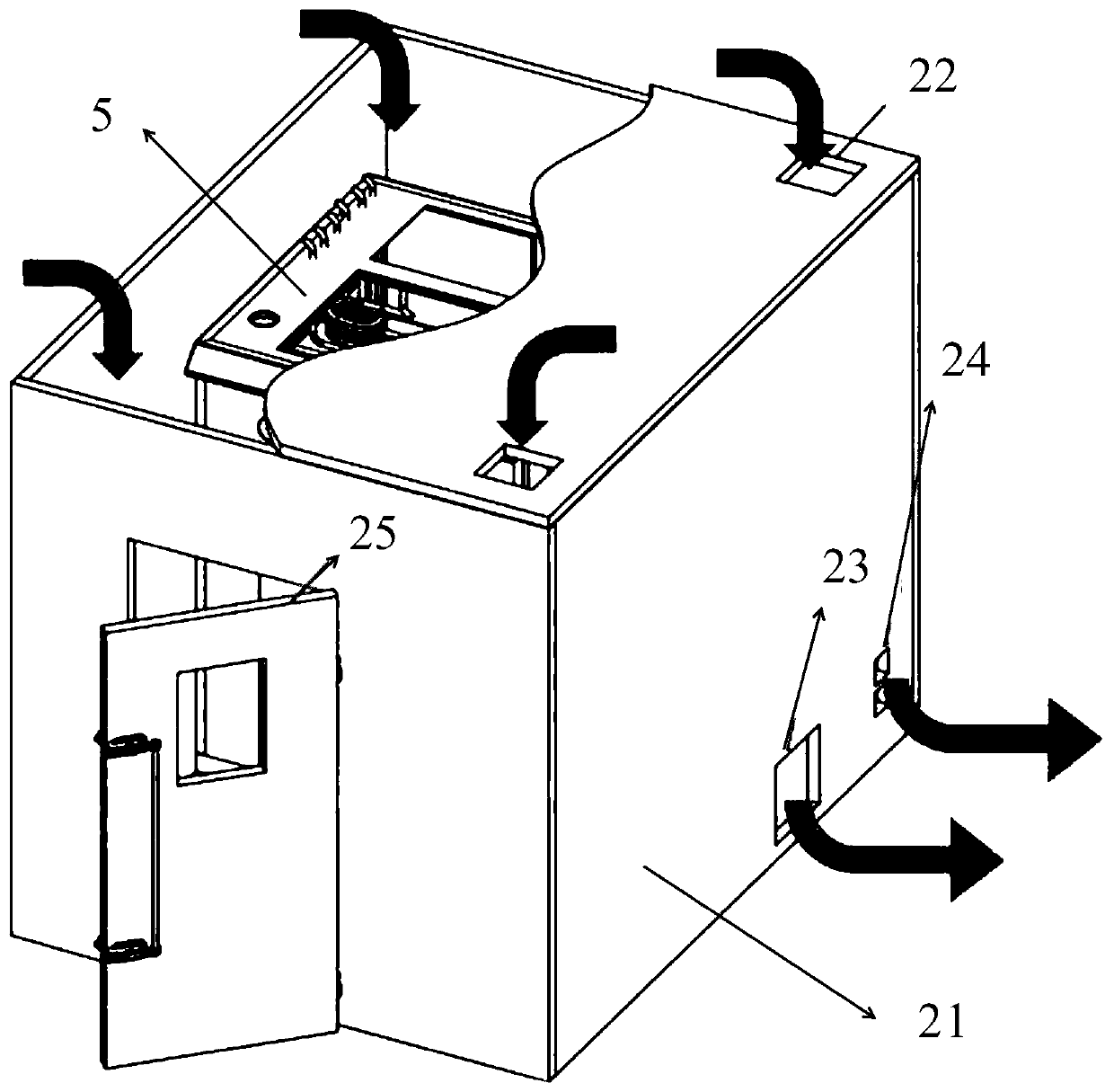
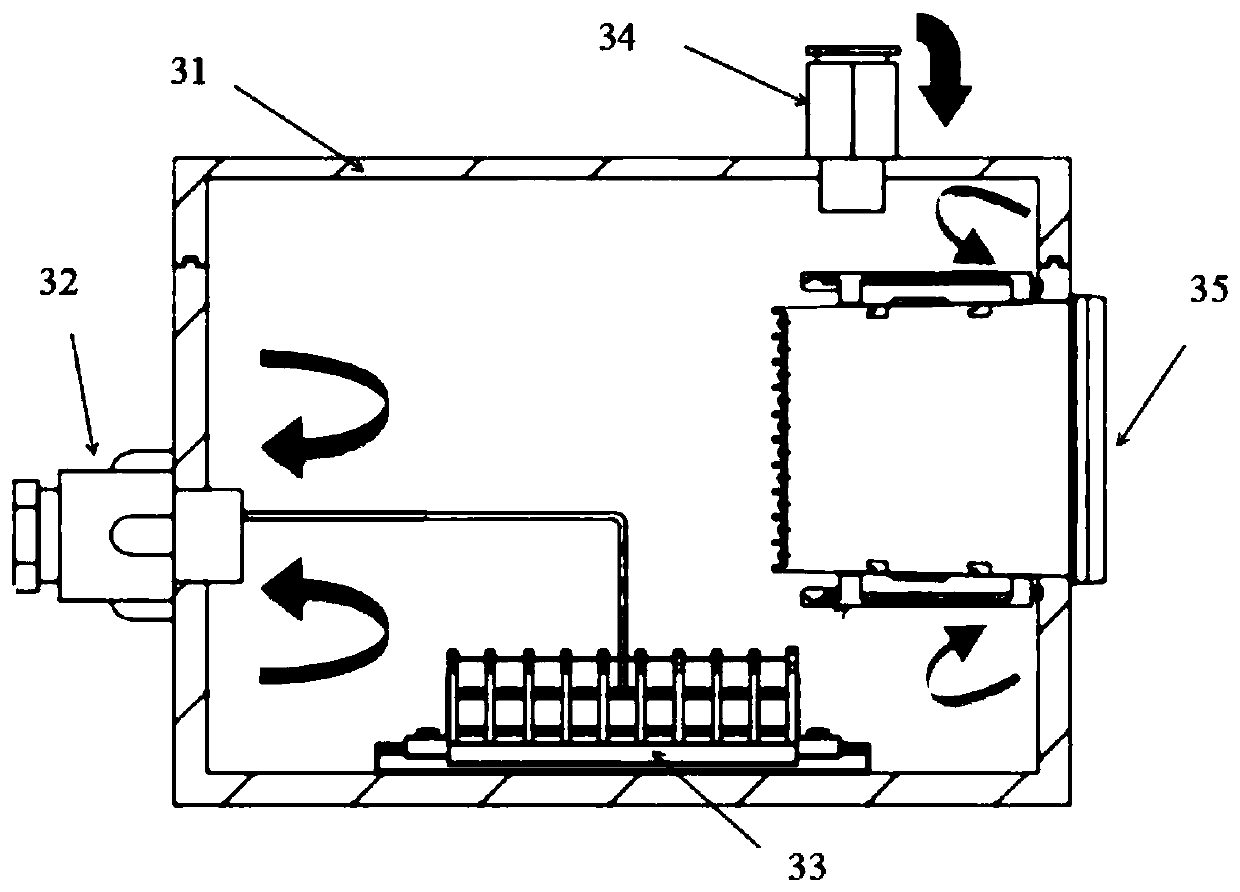
Explosion protection system of refrigerating equipment adopting combustible refrigerant and safety design method
PendingCN111457631AAvoid taking toTo achieve the purpose of security protectionFire rescueSpecial buildingElectrical junctionMonitoring site
The invention belongs to the technical field of refrigerating equipment and particularly relates to an explosion protection system of refrigerating equipment adopting a combustible refrigerant and a safety design method. The explosion protection system comprises a negative pressure isolation exhaust system, an electrical junction box positive pressure explosion protection system and an active detection alarm system connected with an electrical control system separately. The refrigerating equipment body containing the combustible refrigerant is in the negative pressure environment; in the caseof leakage, the combustible refrigerant is discharged outdoors according to the assigned flow direction and a passage to rapidly reduce the concentration of the combustible refrigerant gas near the refrigerating equipment body; a non-explosion-proof testing instrument or a sensor stayed in an anti-explosion area is arranged in the positive pressure environment to effectively prevent the leaking combustible refrigerant from being in contact with an ignition source; and a plurality of monitoring points are arranged at the pipes possibly leaking of the refrigerating equipment body to actively monitor the concentration of the combustible refrigerant gas near the refrigerating equipment body in real time, and when the concentration is abnormal, sound-light alarm is timely sent out and a forcingexhaust system is started.
Owner:广州东弛自动化设备有限公司
Three-in-one detecting pre-warning device and detecting method for oil field crude oil storage tank
InactiveCN109867053AImprove delivery efficiencyTo achieve the purpose of security protectionLarge containersTank wagonsSolenoid valveSoftware system
The invention relates to the technical field of crude oil detection, in particular to a three-in-one detecting pre-warning device and detecting method for an oil field crude oil storage tank. The device comprises a hydraulic upper pressure sensor, a hydraulic lower pressure sensor, a temperature sensor, an analog signal acquisition unit, a core processing unit, a power supply module, a field display module, a wireless communication output module, a wireless communication receiving module, an in-situ sound-light alarm device, a liquid inlet solenoid valve, an electric heating control unit, a monitoring host and a monitoring software system. The three-in-one detecting pre-warning device has the beneficial effects that: the detecting pre-warning device takes a three-in-one sensing structure to perform real-time detection on the temperature, the pressure and the liquid level of the storage tank, realizes in-situ and remote display of data as well as in-situ sound-light alarm pre-warning and remote record and analysis of data, and promotes a loading signal to solve the problems such as late data monitoring, high operation and maintenance cost and oil overflow potential safety hazards inthe prior art. The detecting method can reduce operation and maintenance cost of the oil field crude oil storage tank, especially a remote oil well crude oil storage tank.
Owner:BINZHOU UNIV
Drive, code discrimination and coupling integration micro electromechanical code lock
InactiveCN101644114ASimple structureGuaranteed uptimeNon-mechanical controlsPuzzle locksGear wheelEngineering
The invention relates to a drive, code discrimination and coupling integration micro electromechanical code lock, comprising a shell, a pawl, a ratchet wheel, photoelectric inductors, an upper stator,a lower stator, spindles and counter-intervention meshing gears, wherein the pawl and the ratchet wheel are arranged at the outer side of the uppermost surface of the shell, the ratchet wheel is installed on the spindles, the pawl is installed on the shell and is embedded into a tooth groove of the ratchet wheel, two spindles penetrate through the code lock, the lower stator, the counter-intervention meshing gears and the upper stator are arranged in the shell and are sequentially connected in series to the spindles, and the photoelectric inductors are respectively arranged in the shell corresponding to the positions of the counter-intervention meshing gears. By using a drive, code discrimination and coupling integration micro electromechanical structure, the invention integrates three parts of a drive, a code discrimination mechanism and a coupler into one part, therefore, the structure of code lock dynamics is reduced, the installation is convenient, and the reliability is higher.
Owner:SHANGHAI JIAO TONG UNIV
Hidden security and protection monitoring device
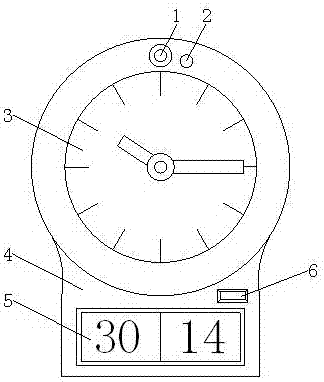
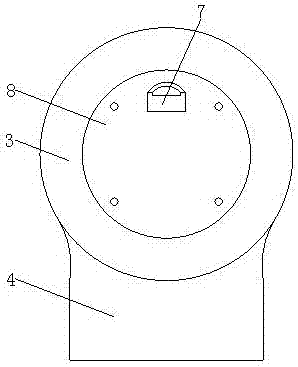
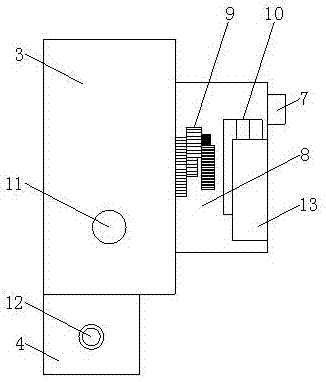
InactiveCN107959832ATo achieve the purpose of security protectionImprove aestheticsTelevision system detailsMechanical clocksDisplay deviceCombustible gas
The invention discloses a hidden security and protection monitoring device, which comprises a clock disc, a base and a rear seat. A high-definition micro-camera and an infrared detector are sequentially arranged from left to right and are positioned above a watch hand arranged on the front surface wall of the clock disc. The base is fixedly connected with the lower surface wall of the clock disc.A temperature and humidity display is arranged on the front surface wall of the base. A signal receiving screen is arranged on one side of the temperature and humidity display. A rear hook is fixedlyarranged on the rear seat arranged on the rear surface wall of the clock disc. A combustible gas detector is arranged on the side wall of the clock disc. A watch hand rotating gear arranged in the rear seat is fixedly connected with a pointer on the clock disc. According to the invention, due to the arrangement of the high-definition micro-camera, the clock disc, the base, the temperature and humidity display and the rear seat, the problems of complex equipment, troublesome installation, not attractive appearance, poor affinity, bad invisibility, easily caused false alarm, single function andthe like in the prior art are solved. Meanwhile, the problem that the diversified life requirements of people cannot be met is also solved.
Owner:西安龙之梦网络信息有限公司
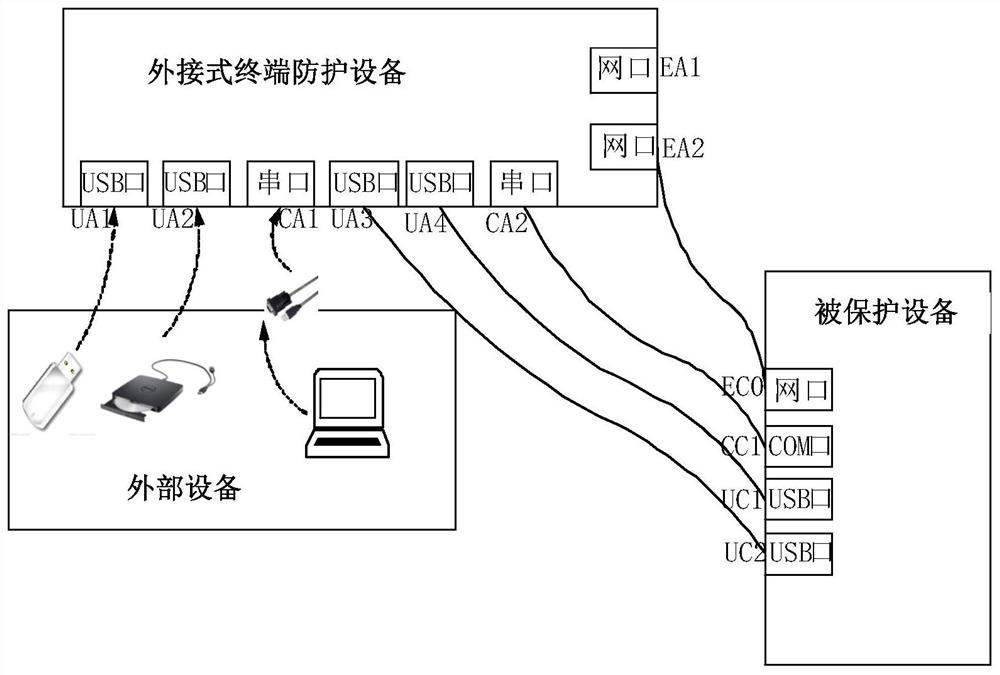
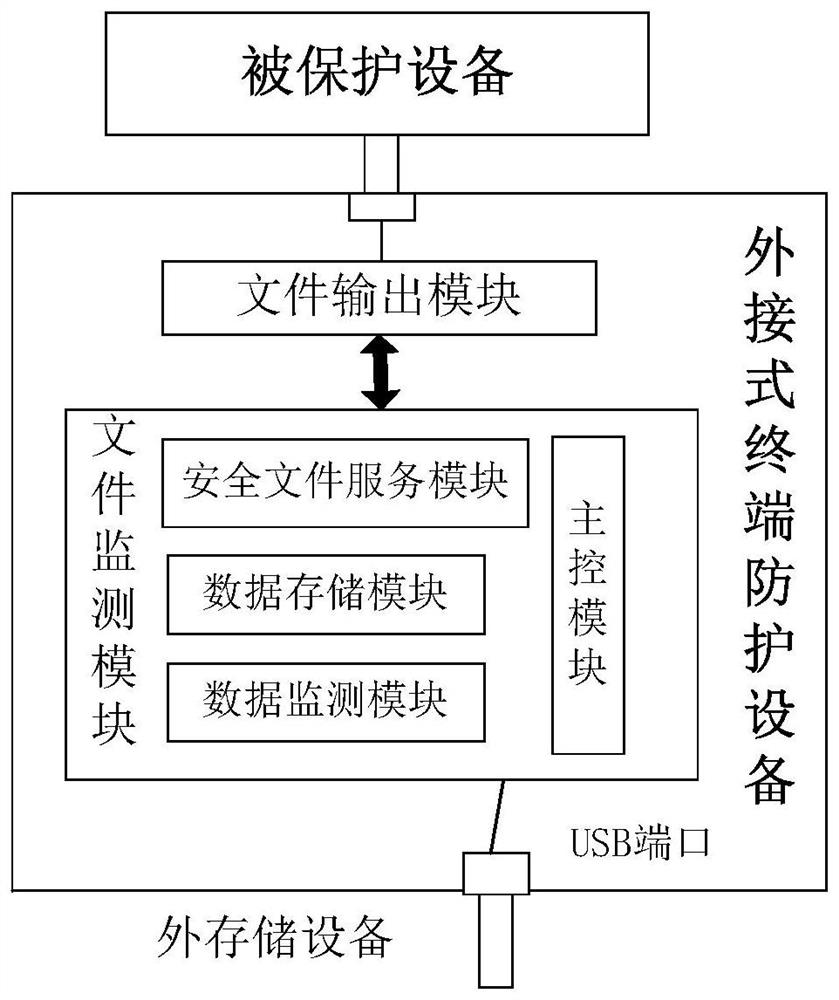
External terminal protection equipment and protection system comprising identity information verification
PendingCN111898167AReduce system security risksSolve potential safety hazardsDigital data protectionInternal/peripheral component protectionReal time acquisitionComputer security
The invention discloses external terminal protection equipment and a protection system comprising identity information verification. The external terminal protection equipment comprises: a plurality of external interfaces used for being connected with one or more external equipment and a piece of protected equipment respectively; the identity information acquisition module that is used for acquiring identity information of a user in real time; the file monitoring module that is connected with the identity information acquisition module, is used for verifying the identity information, and is also used for controlling the security authentication of external equipment accessed to the external interface; and the file transmission module that is connected with the file monitoring module and isused for transmitting the file data imported by the external equipment to the protected equipment under the control of the file monitoring module. According to the invention, the purpose of performingsafety protection on the protected equipment without installing safety protection software on the protected equipment can be achieved, and the safety risk of the system is greatly reduced by verifying and determining the identity and the use permission of the current operator.
Owner:北京中科麒麟信息工程有限责任公司
An application security protection method and server
ActiveCN105678120BTo achieve the purpose of security protectionPrevent decompilationTransmissionProgram/content distribution protectionApplication securityOperating system
The invention discloses a safety protection method of application programs and a server. The method comprises following steps: receiving a first application program sent from a client by the server; collecting parameters / instructions of the first application program by the server in order to obtain a second application program such that the second application program can normally operate and enable a reverse tool to exit by fault when the reverse tool is utilized for analyzing the second application program; and sending the second application program to the client by the server.
Owner:CHINA MOBILE COMM GRP CO LTD
Image data leakage prevention method, device and equipment
PendingCN109598267ATo achieve the purpose of security protectionPositive technical effectCharacter and pattern recognitionNeural architecturesImaging dataConvolution
The invention discloses an image data leakage prevention method, an image data leakage prevention device and image data leakage prevention equipment. The method comprises the steps: carrying out the marking of the obtained image data, and obtaining marked image data; Training a convolutional neural network based on the labeled image data to obtain a convolutional neural network model; And identifying to-be-detected image data based on the convolutional neural network model; AND training the convolutional neural network, and identifying the to-be-detected image data by using the trained convolutional neural network model. The convolutional neural network is applied to leakage protection of the image data, content recognition is performed on the image data to be protected, and key data partsin the image are recognized, so that the purpose of performing safety protection on the key data of the image is achieved. And a positive technical effect is achieved.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Safety system for building hoist
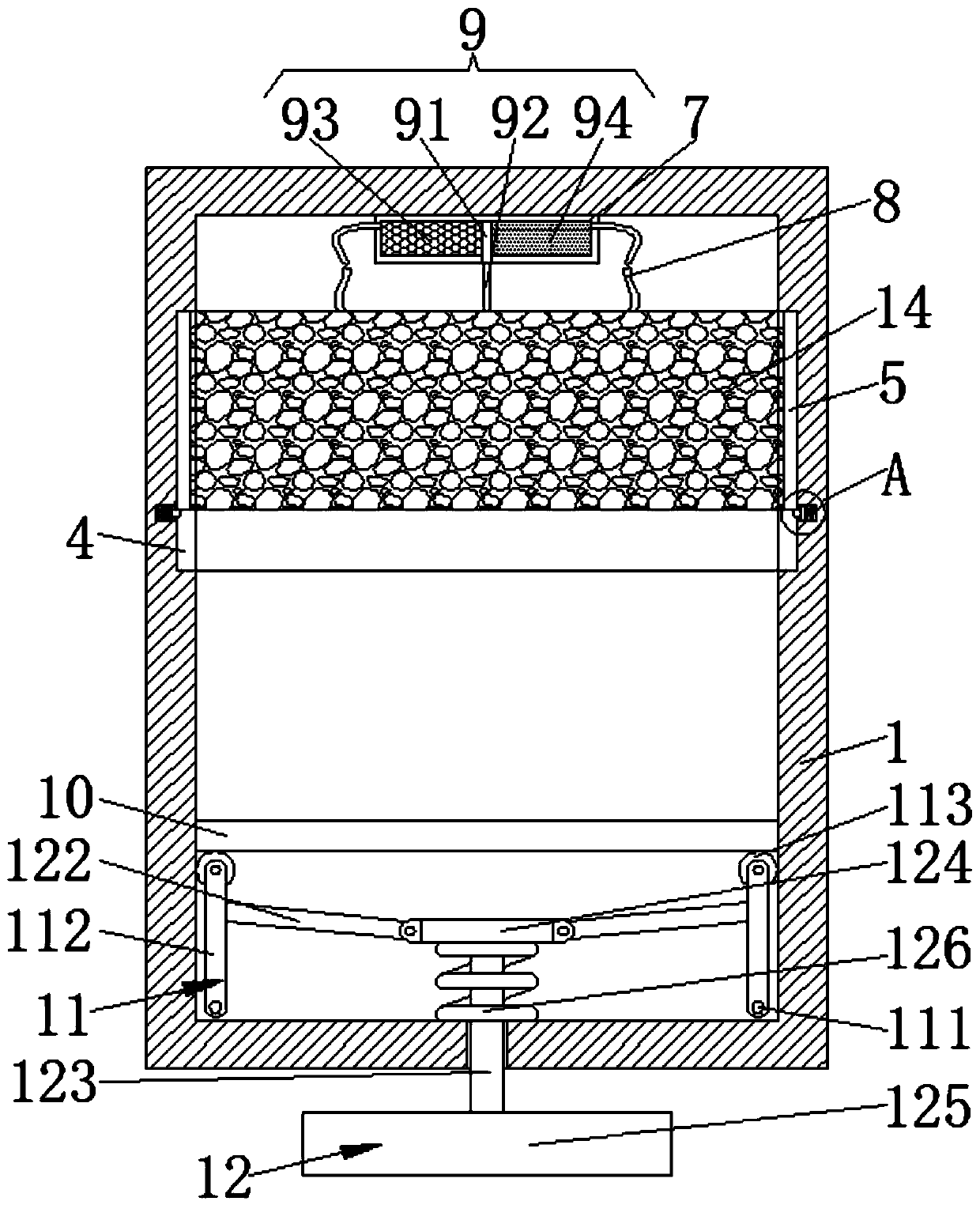
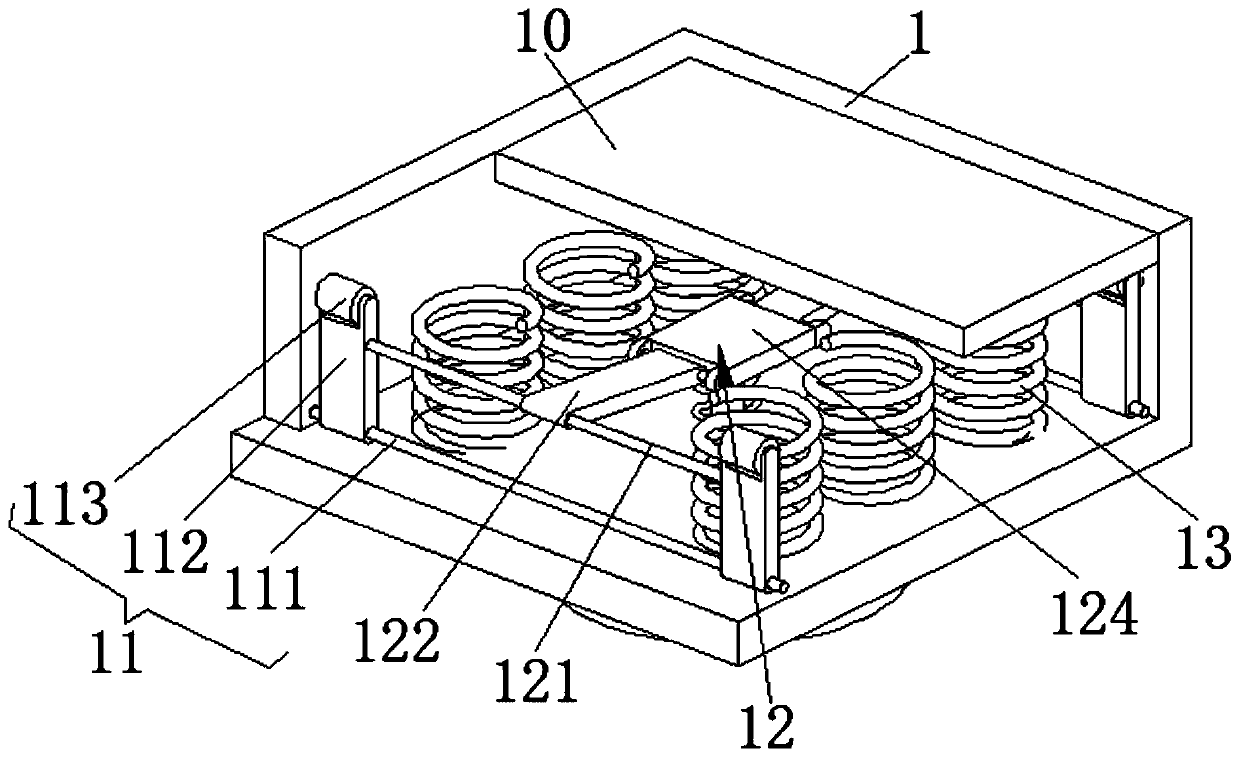
The invention discloses a safety system for a building hoist. The safety system comprises a lifting cabinet, a cabinet door mechanism is arranged on the front side of the lifting cabinet, automatic push-out mechanisms are arranged on the front sides of the two sides of the lifting cabinet, and a U-shaped groove is formed in an inner cavity of the lifting cabinet. When the lifting cabinet suddenlystops, a blocking mechanism cancels blocking of a U-shaped air bag, the U-shaped air bag moves downwards in the inner cavity of the U-shaped groove due to inertia, and an air outlet mechanism rapidlyinflates the U-shaped air bag through movement of the U-shaped air bag, so that the U-shaped air bag rapidly expands to protect main parts of constructors, the aim of protecting safety of the constructors is achieved; and under the action of inertia, a support unloading mechanism pulls a supporting mechanism to move to cancel supporting for a bearing carrier plate, the bearing carrier plate descends and makes contact with a third spring, the third spring plays a role in buffering the bearing carrier plate, the lower limbs of the constructors and cargos can be protected, and therefore the purpose of safety protection is achieved.
Owner:南京高立特种装备有限公司
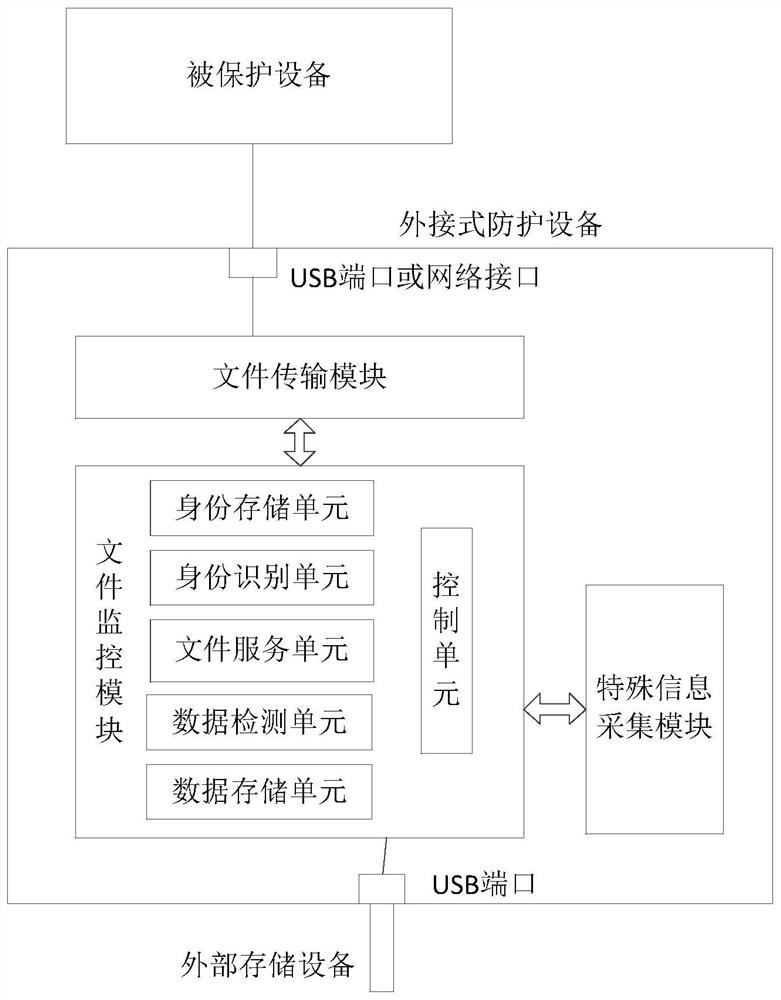
External terminal protection device and protection system based on file monitoring service
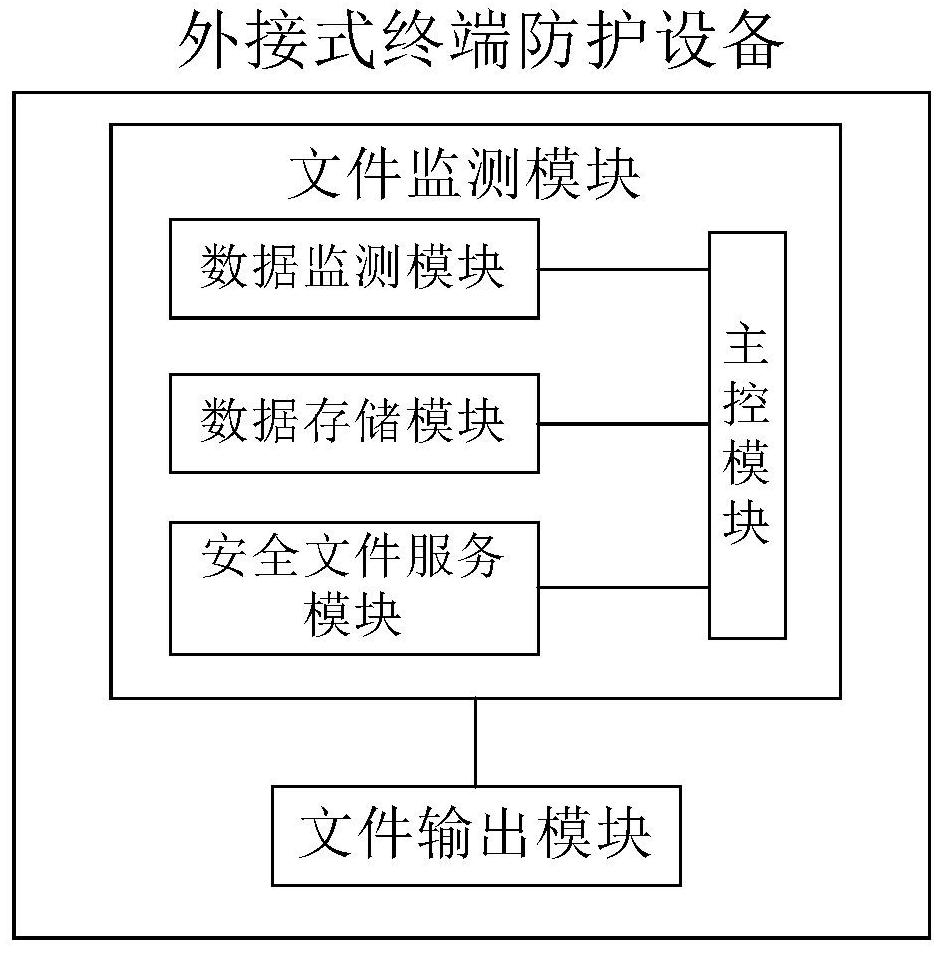
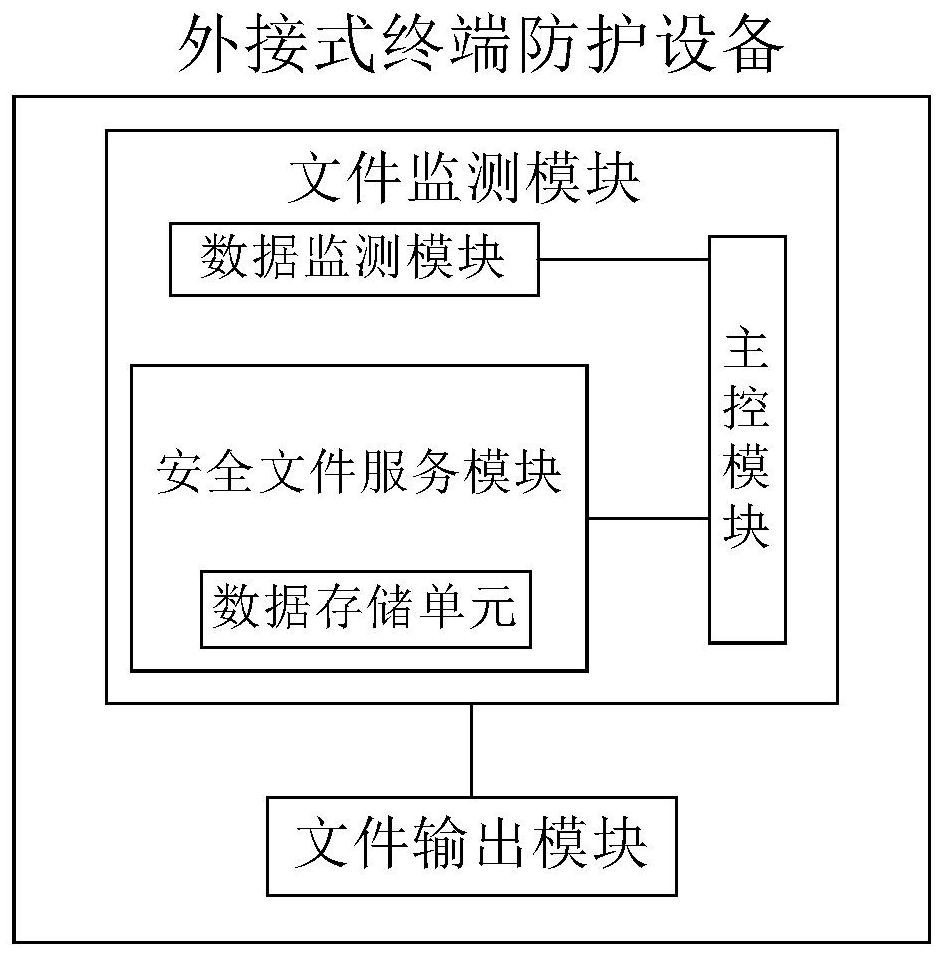
ActiveCN111885179AReduce security risksRealize security monitoringTransmissionExternal storageSecure transmission
The invention provides an external terminal protection device and protection system based on file monitoring service. The equipment comprises a file monitoring module which can be connected with external storage equipment and is used for carrying out safety monitoring on the external storage equipment and file data contained in the external storage equipment, wherein the file monitoring module comprises a data monitoring module, a safety file service module and a main control module, the safety file service module is used for managing and transmitting file data, and the main control module isused for controlling monitoring, management and transmission of file data; and a file output module which performs confidential data transmission with the security file service module to call securityfile data, and transmits the security file data to the protected equipment. According to the invention, the security monitoring of the external storage device and the file data contained in the external storage device can be realized, and the security risk of the protected device is greatly reduced while the secure transmission of the file data is ensured.
Owner:北京中科麒麟信息工程有限责任公司
Novel lane control warning device
InactiveCN103903461AImprove effectivenessImprove securityArrangements for variable traffic instructionsElectric transmission signalling systemsCapacitanceAudio power amplifier
Provided is a novel lane control warning device. A central control module is connected with an onboard dialing module, an audio power amplifier module, a red and blue flashing module, an LED drive module, a DC-DC module, a feedback module, a resistor R and capacitor S485 communication module, a data storage module and an information collection module interface. The audio power amplifier module is connected with a horn, the red and blue flashing module is connected with a red and blue flashing lamp circuit board module, the LED drive module is connected with an LED circuit board module, the DC-DC module is connected with an external power source module, an information collection module 1 is connected with a photosensitive sensor, and a 485 communication module is connected with a data bus. The central control module sends signals to the LED drive module to lighten LED distribution points in the LED circuit board module in a default state, the feedback module sends the current display state to an external monitoring center, the monitoring center sends state information to be displayed to the data bus, the resistor R and the capacitor S485 communication module communication module of an LED lane indication sign receive corresponding data, and the purpose of safety protection is achieved.
Owner:陕西高速电子工程有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com