Method and device for detection of device loophole information and computer device
A technology for testing equipment and equipment, which is applied in the field of network security, and can solve problems such as property loss, safety issues that cannot be ignored, and equipment manipulation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
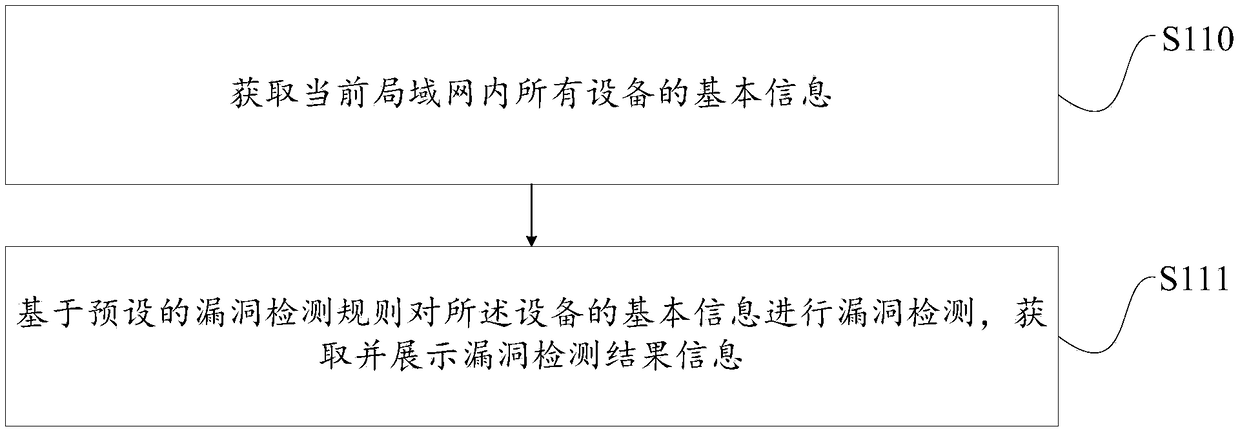
[0080] This embodiment provides a method for detecting device vulnerability information, such as figure 1 As shown, the methods include:
[0081] S110, obtaining basic information of all devices in the current local area network;
[0082] The current local area network in this embodiment mainly includes the home local area network. Since there are more and more smart devices in the home network, some devices have security risks. In order to achieve security protection, it is necessary to obtain all devices in the network for vulnerability detection. Then First, you need to obtain the basic information of each device. Among them, the equipment may include: mobile phones, computers, IPADs, routers, cameras, sweeping robots, and children's watches.
[0083] As an optional embodiment, since the network protocol used by each device may be different, obtaining the basic information of all devices in the current local area network includes: using a standard network protocol to iden...
Embodiment 2
[0126] Embodiment two
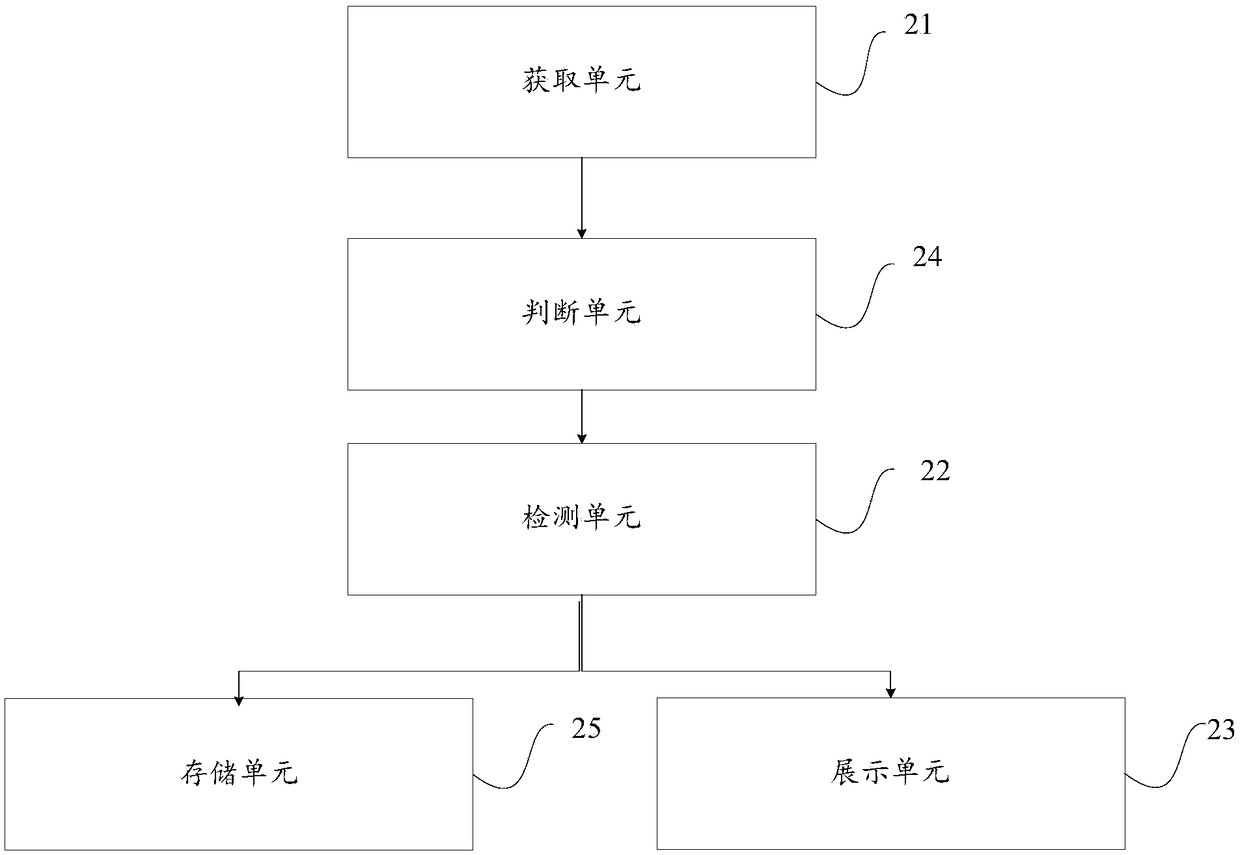
[0127] This embodiment provides a device for detecting device vulnerability information, such as figure 2 As shown, the device includes: an acquisition unit 21, a detection unit 22 and a display unit 23;
[0128] The obtaining unit 21 obtains basic information of all devices in the current local area network. The current local area network in this embodiment mainly includes the home local area network. Since there are more and more smart devices in the home network, some devices have security risks. In order to achieve security protection, it is necessary to obtain all devices in the network for vulnerability detection. Then The acquisition unit 21 first needs to acquire the basic information of each device. Among them, the equipment may include: mobile phones, computers, IPADs, routers, cameras, sweeping robots, and children's watches.
[0129] As an optional embodiment, since the network protocols used by each device may be different, the obtainin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com