External terminal protection device and protection system based on file monitoring service
A kind of protective equipment, external technology, applied in the direction of transmission system, electrical components, etc., can solve problems such as damage, system misoperation, and influence of enterprises and institutions, and achieve the effect of ensuring safe transmission, improving safety performance, and reducing safety risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
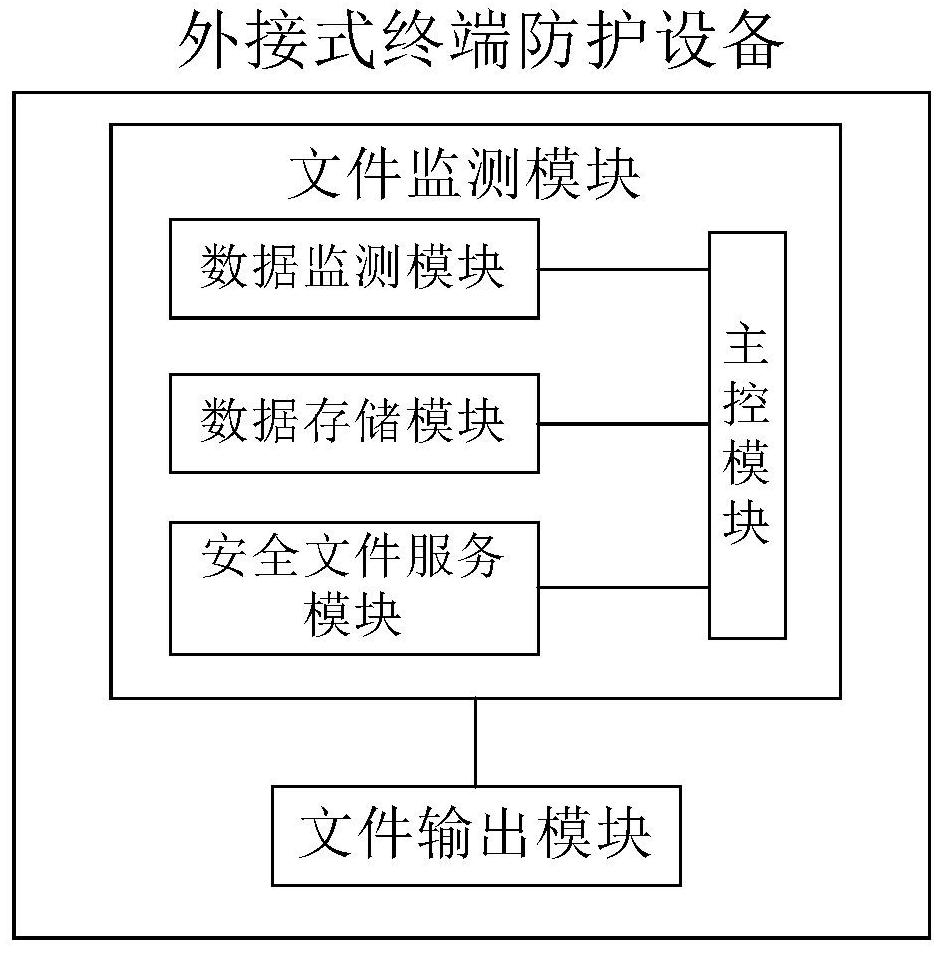
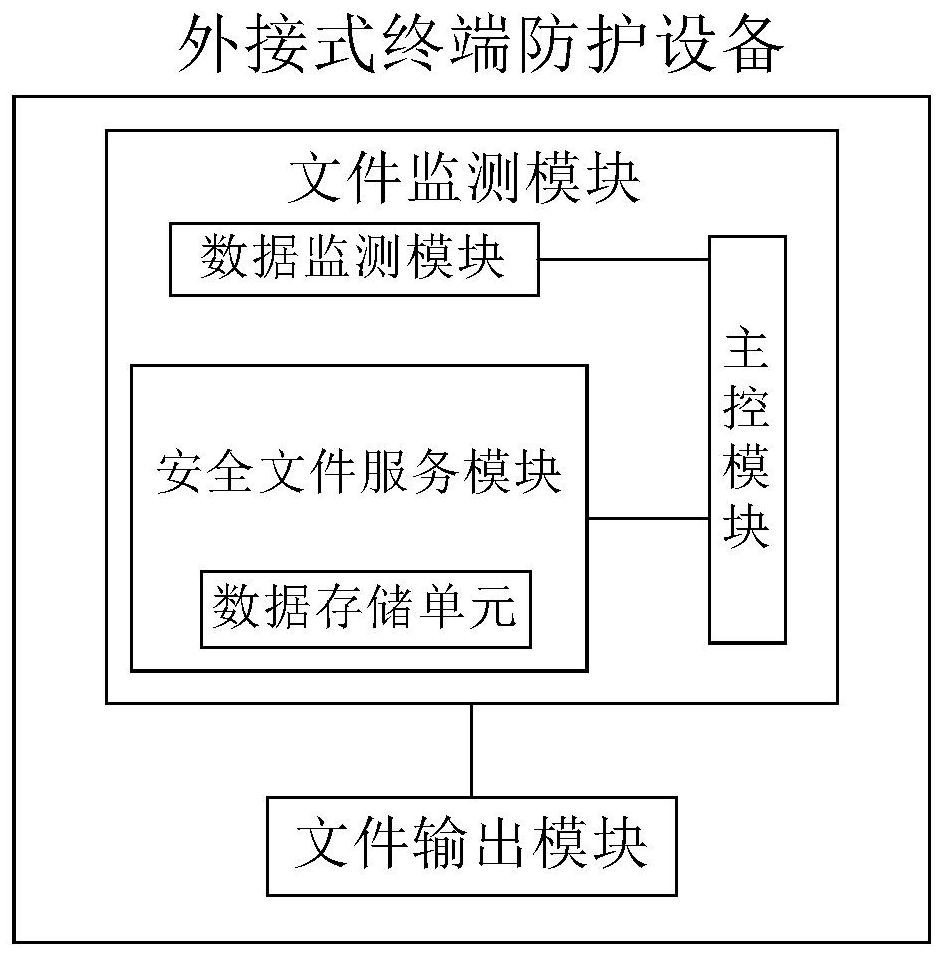
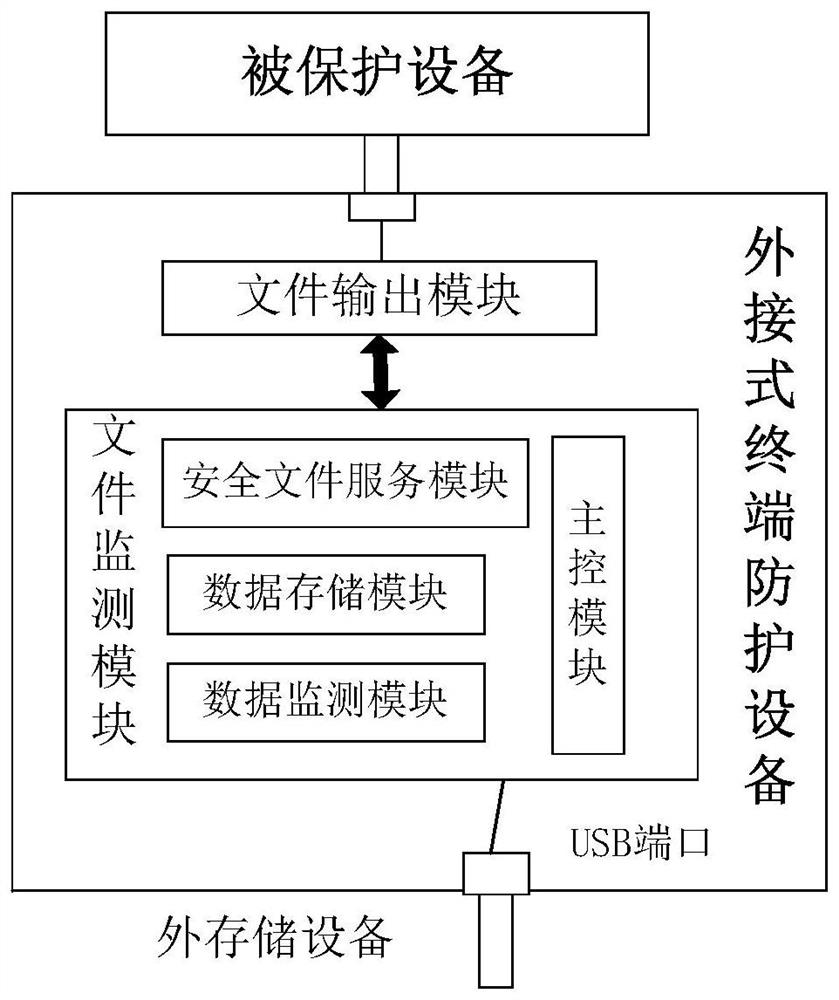
[0029] Below, see figure 1 , figure 2 and image 3 An embodiment of the external terminal protection device based on the file monitoring service of the present invention is described.
[0030] In this example, the external terminal protection device of the present invention is externally connected to the protected device, and the external terminal protection device includes a file monitoring module and a file output module, wherein the file monitoring module can be connected to an external storage device for The external storage device and the file data contained in it are monitored safely; the file output module is connected with the protected device through the internal interface or port, and transmits the file data to the protected device.
[0031] figure 1 A schematic block diagram of the internal structure of the external terminal protection device based on the file monitoring service of the present invention.
[0032] Such as figure 1 As shown, the file monitoring ...
Embodiment 2
[0063] see Figure 4 and Figure 5 , the present invention also provides a protection system, the external terminal protection device A described in Embodiment 1 of the present invention, wherein the secure file service module establishes a secure communication connection with the file output module to transmit confidential data and retrieve files data, and transmit the file data to the protected device B.
[0064] It should be noted that, in Embodiment 2, descriptions of the same parts as in Embodiment 1 are omitted.
[0065] Preferably, in order to further realize the electrical safety between connected devices, targeted design is also carried out:
[0066] 1) The interface or port adopts a current-limiting and pressure-limiting design
[0067] The electrical safety protection of the terminal protection equipment mentioned in the scheme means that the equipment function uses hardware design to prevent the damage of strong discharge equipment, and introduces a current-limi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com