Image data leakage prevention method, device and equipment
An image data, anti-leakage technology, applied in the direction of instruments, biological neural network models, character and pattern recognition, etc., can solve the problem of security protection of key data that cannot be imaged
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
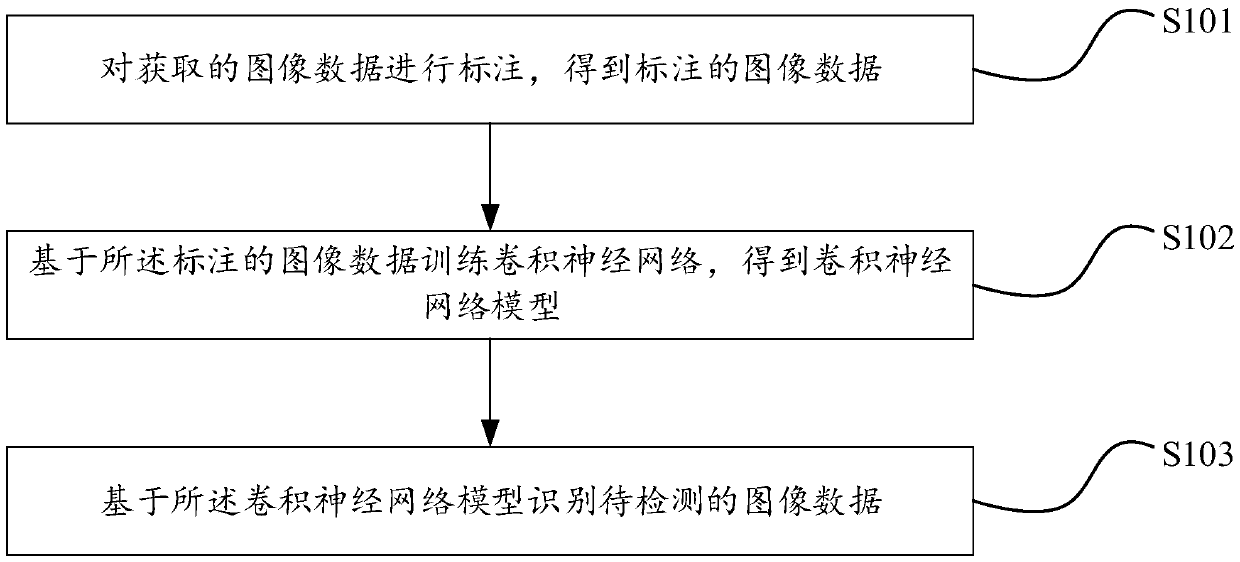
[0046] An embodiment of the present invention provides an image data leakage prevention method, such as figure 1 shown, including:
[0047] Step S101: labeling the acquired image data to obtain the labeled image data;
[0048] In order to obtain the convolutional neural network model, sample data is first required for model training. This step acquires image data and marks the data to be recognized in the image data, that is, the image data to be recognized and the key data of the recognized image data are marked out. It is mainly to mark out some representative image data, such as various distorted images, or image data with cartoons, characters, etc. In order to facilitate the later training of the convolutional neural network model.
[0049] Step S102: training a convolutional neural network based on the labeled image data to obtain a convolutional neural network model;
[0050] Put the labeled image data and the key data of the image data into the convolutional neural n...
Embodiment 2
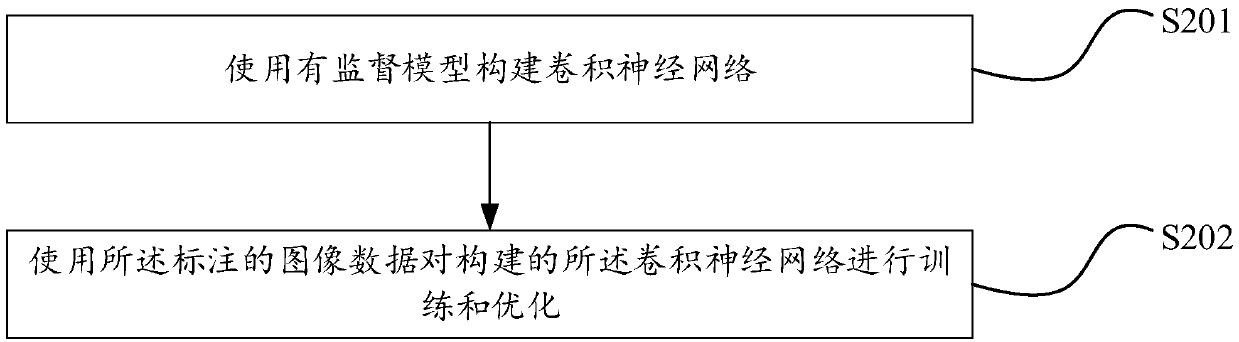
[0074] Such as Figure 4 As shown, an embodiment of the present invention provides an image data leakage prevention device, including:
[0075] Annotation module 401: for annotating the acquired image data to obtain the annotated image data;
[0076] In order to obtain the convolutional neural network model, the sample data is first required for model training. This step acquires the image data, and marks the data to be recognized in the image data, that is, the image data to be recognized and the key data of the recognized image data are marked out. , so as to facilitate the later training of the convolutional neural network model.
[0077] Training module 402: for training a convolutional neural network based on the labeled image data to obtain a convolutional neural network model;
[0078] Put the labeled image data and the key data of the image data into the convolutional neural network to train the convolutional neural network, so as to obtain the trained convolutional ...
Embodiment 3
[0095] An embodiment of the present invention provides an electronic device. The electronic device includes: a memory, a processor, and a computer program stored in the memory and operable on the processor. The computer program is executed by the processor. The method steps of Embodiment 1 are realized during execution.
[0096] The processor can be a general-purpose processor, such as a central processing unit (Central Processing Unit, CPU), a digital signal processor (Digital Signal Processor, DSP), an application-specific integrated circuit (Application Specific Integrated Circuit, ASIC), or configured One or more integrated circuits implementing embodiments of the invention. Wherein, the memory is used to store executable instructions of the processor; the memory is used to store program codes and transmit the program codes to the processor. Memory can include volatile memory (Volatile Memory), such as random access memory (Random Access Memory, RAM); also can include non...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com