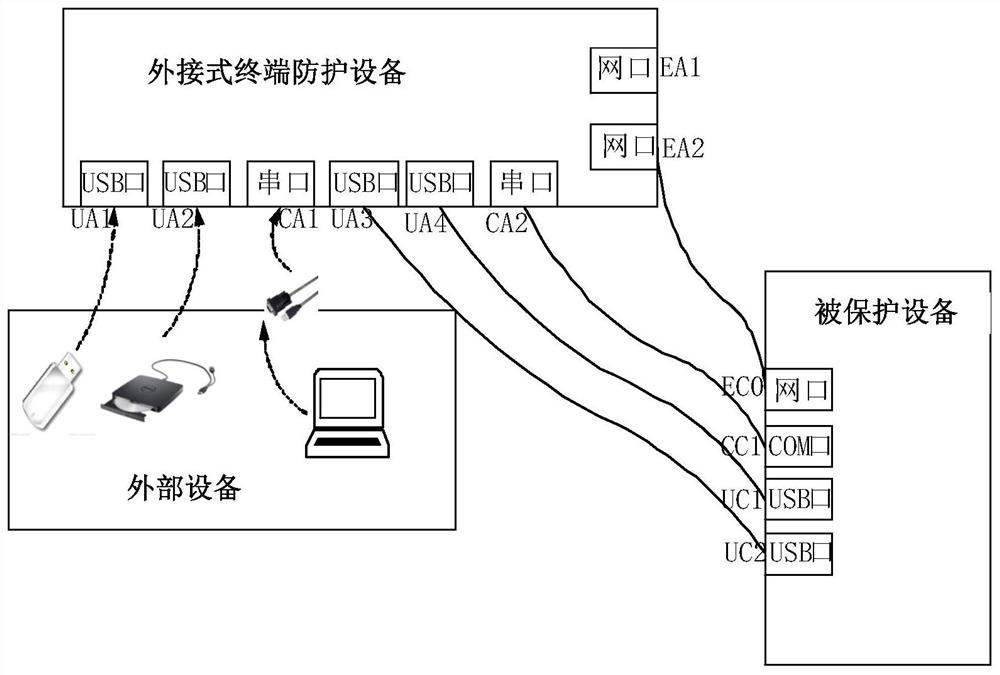
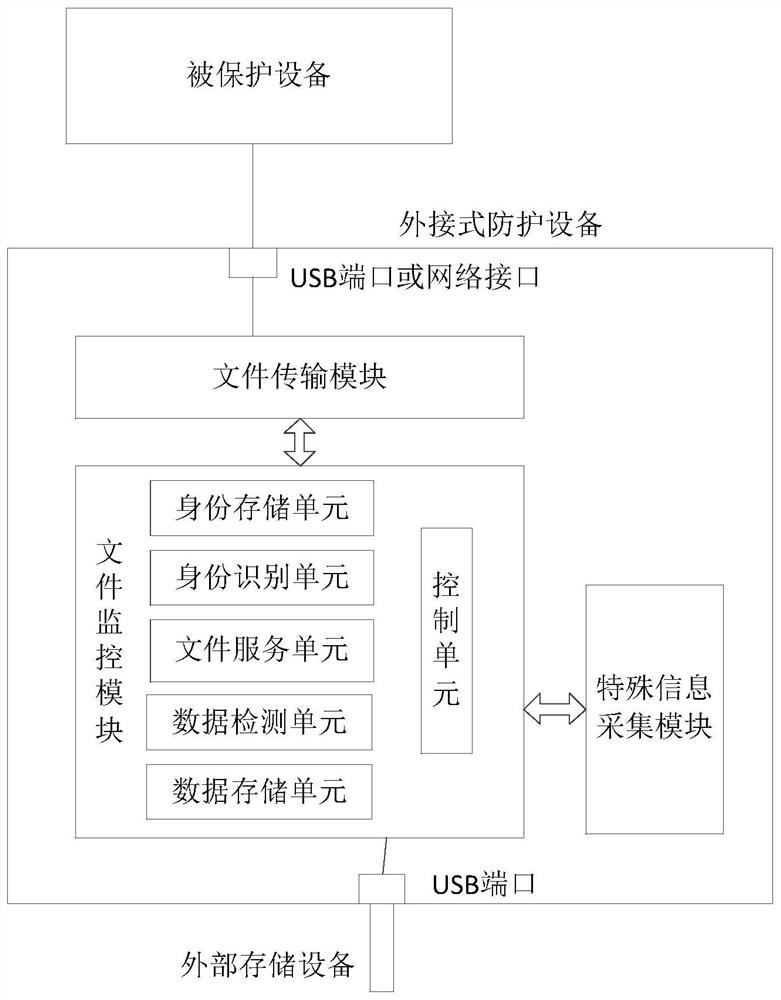
External terminal protection equipment and protection system comprising identity information verification
A technology of identity information and protective equipment, applied in the field of computer security, can solve problems such as damage, lack of security awareness, lack of identification ability, etc., to solve security risks, avoid illegal intrusion and theft, and reduce system security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0029] According to a preferred embodiment of the present invention, the file monitoring module includes:
[0030] The identity information storage unit is used to temporarily store the identity information of the user;
[0031] An identity recognition unit, configured to verify whether the user's identity information satisfies a preset access right.
[0032] According to a preferred embodiment of the present invention, the identity information storage unit is further configured to pre-store identity information of users satisfying access rights.
[0033] According to a preferred embodiment of the present invention, when the external interface is connected to an external device, the identity recognition unit matches the identity information collected from the user with the pre-stored identity information of the user who meets the access authority, if If the matching is successful, the user meets the access rights.
[0034] According to a preferred embodiment of the present i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com