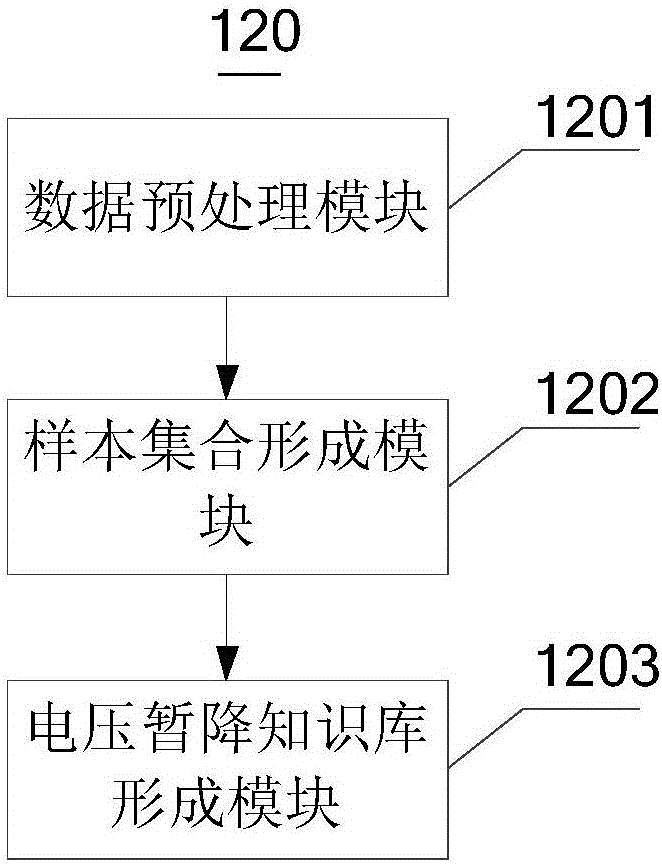
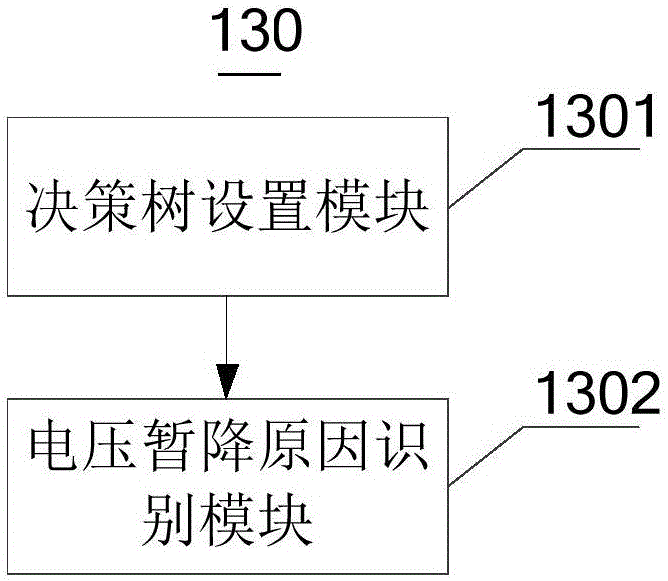
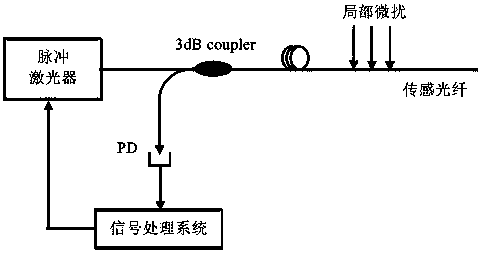
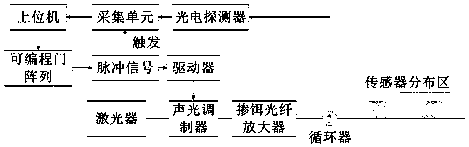
Patents
Literature
52results about How to "Prevent illegal intrusion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safety authentication method and system for wireless network
InactiveCN101959191AAvoid safety hazardsSecurity certification is validSecurity arrangementAuthentication systemWeb authentication
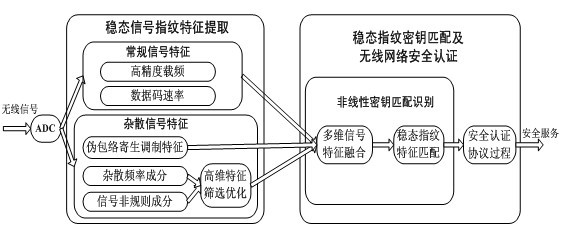
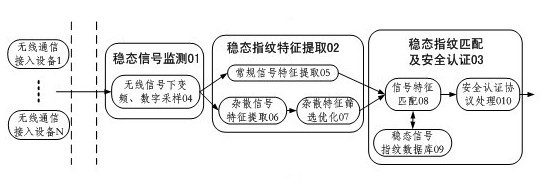
The invention discloses a safety authentication method and a safety authentication system for a wireless network. The system comprises a signal fingerprint monitoring and processing module and a wireless network access authentication module at an access point. The method comprises the following steps that: at a network access point, the signal fingerprint monitoring and processing module performsdown-conversion and digitized sampling on a detected steady-state communication signal and extracts the conventional signal characteristic and the spurious signal characteristic of the steady-state signal by a communication signal processing method; after a higher-dimension spurious signal characteristic is reduced and optimized, the conventional signal characteristic and the spurious characteristic are fused into a steady-state signal fingerprint; and a signal fingerprint matching and safety authentication module matches the monitored steady-state fingerprint of unknown communication equipment and provides a corresponding safety strategy service according to a recognition result by a network authentication protocol. The method and the system are used for performing safety authentication on wireless communication equipment and enhancing the safety of a wireless communication network in combination with a software authentication system and have the characteristics of high concealment, high stability and safe management.
Owner:HUAZHONG UNIV OF SCI & TECH
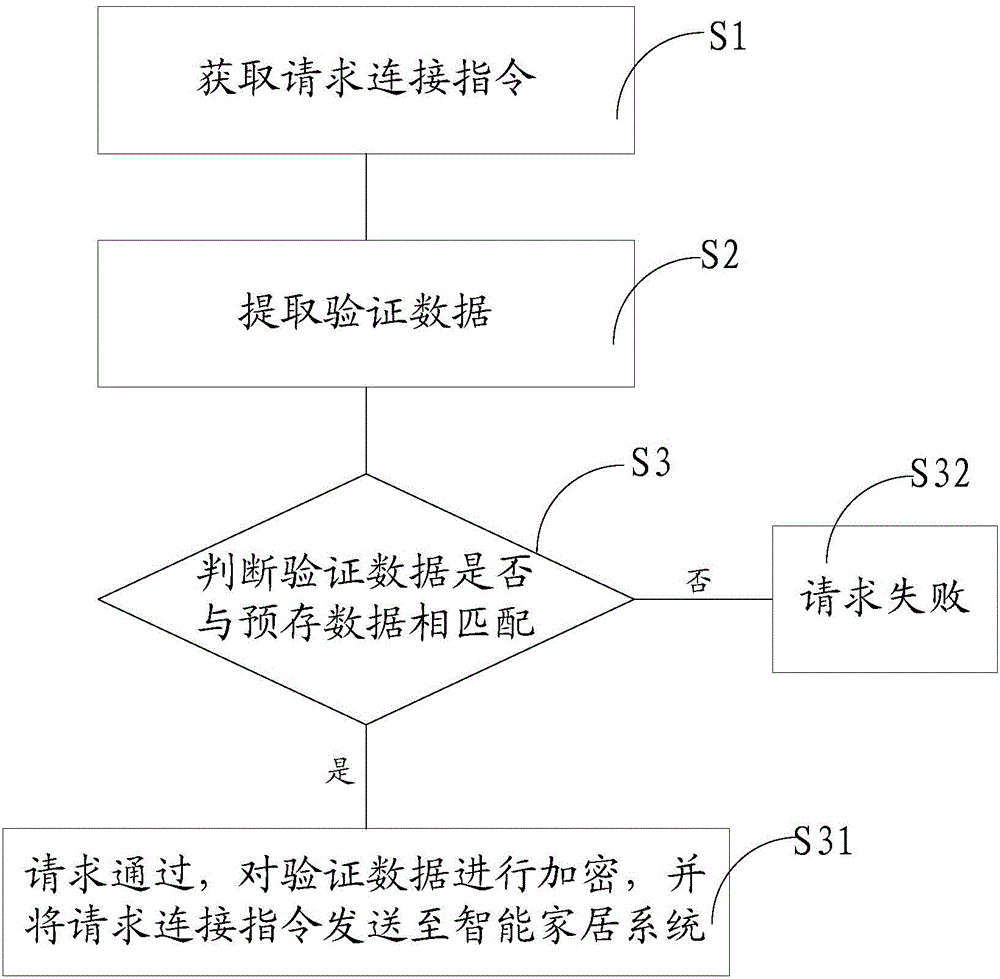
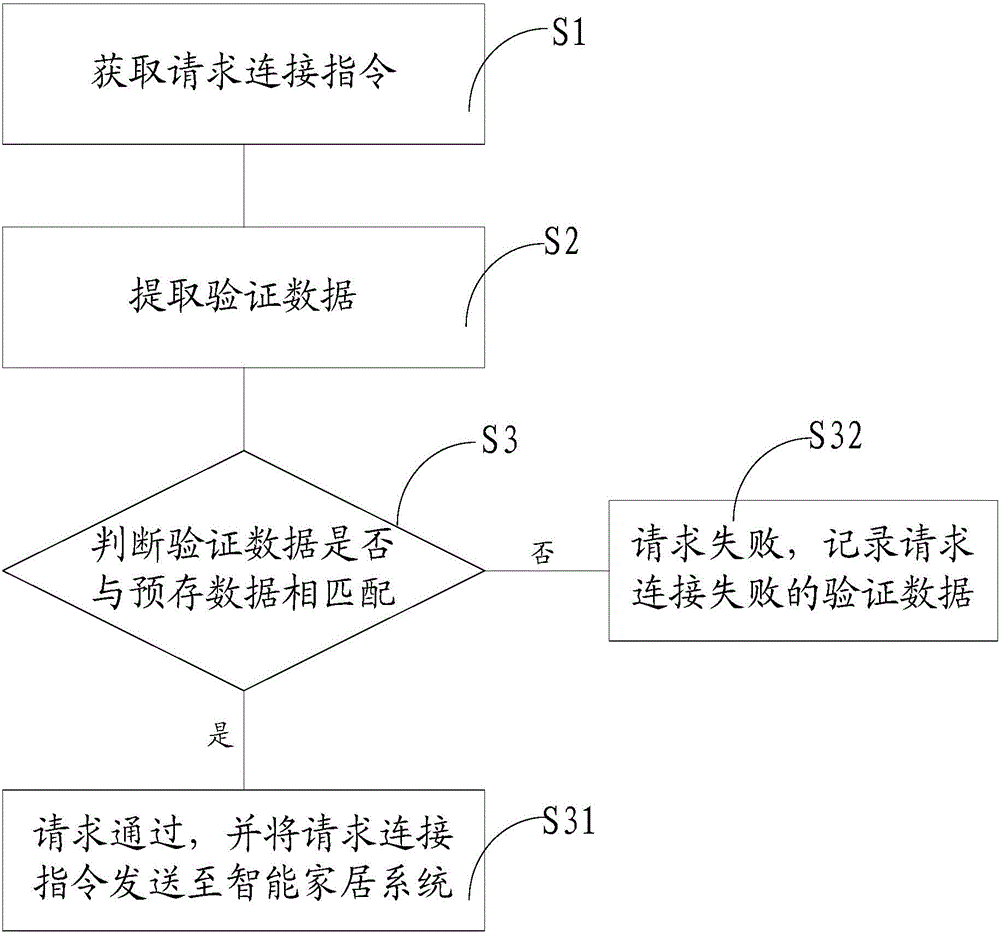
Connection method and connection device for intelligent housing system
InactiveCN104394050AImprove securityPrevent illegal intrusionData switching by path configurationReal-time computingComputer science
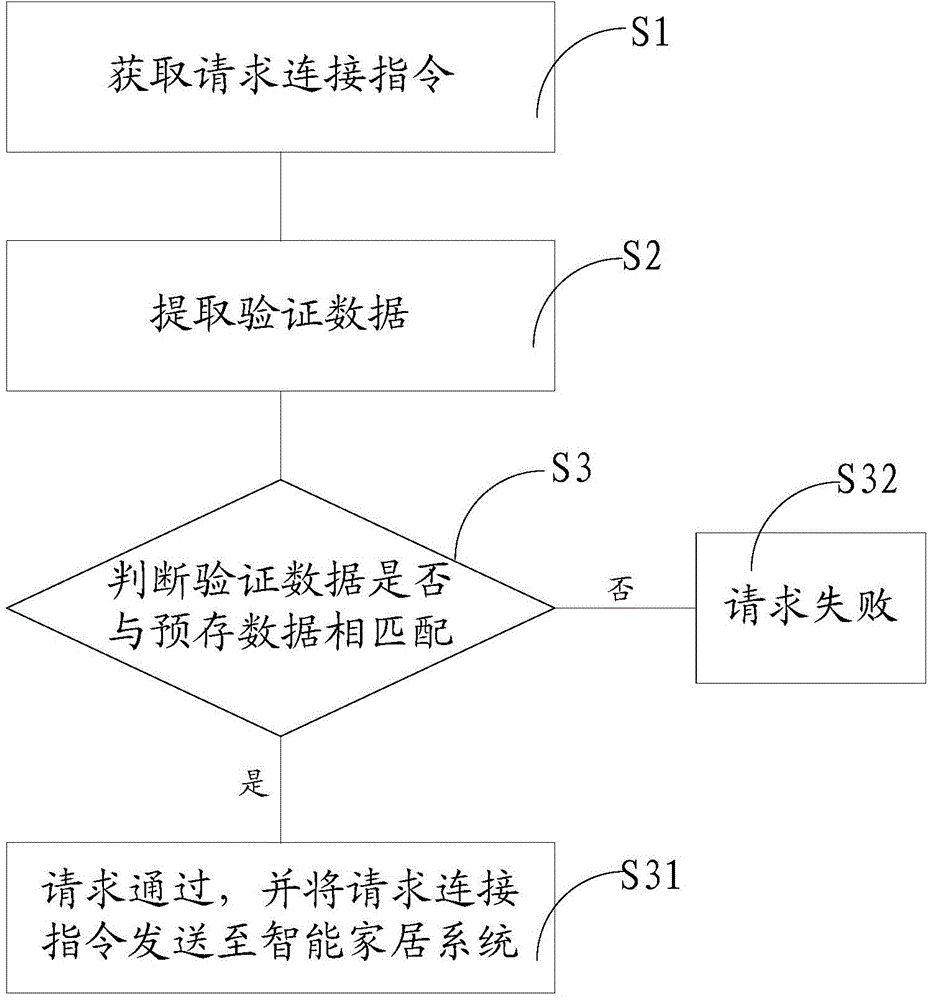
The invention discloses a connection method and connection device for an intelligent housing system. The method includes the steps of obtaining a connection request instruction, wherein the connection request instruction includes verification data; extracting the verification data from the connection request instruction; judging whether the verification data are matched with pre-stored data or not, showing that the request succeeds and sending the connection request instruction to the intelligent housing system if the verification data are matched with the pre-stored data; showing that the request fails if the verification data are not matched with the pre-stored data. In this way, before a control terminal is connected with the intelligent housing system, whether the control terminal is a legal control terminal or not needs to be judged at first; in other words, after the control terminal sends the connection request instruction, the connection device obtains the verification data from the connection request instruction, whether the verification data are matched with the pre-stored data or not is then judged, and whether the request succeeds or not is decided. By means of the technical scheme, the safety of the connection of the intelligent housing system is improved, and the situation of the illegal intrusion is effectively avoided.
Owner:GREE ELECTRIC APPLIANCES INC OF ZHUHAI
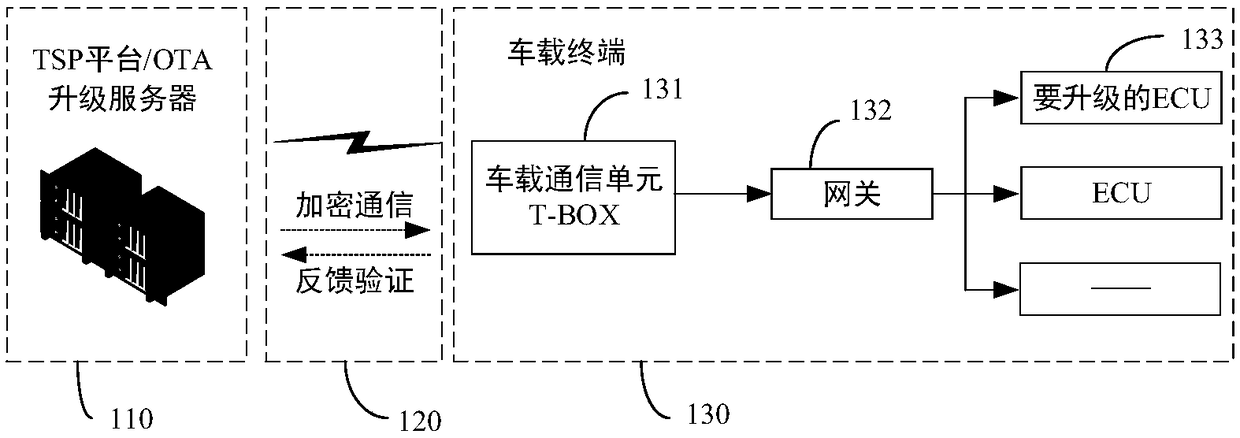
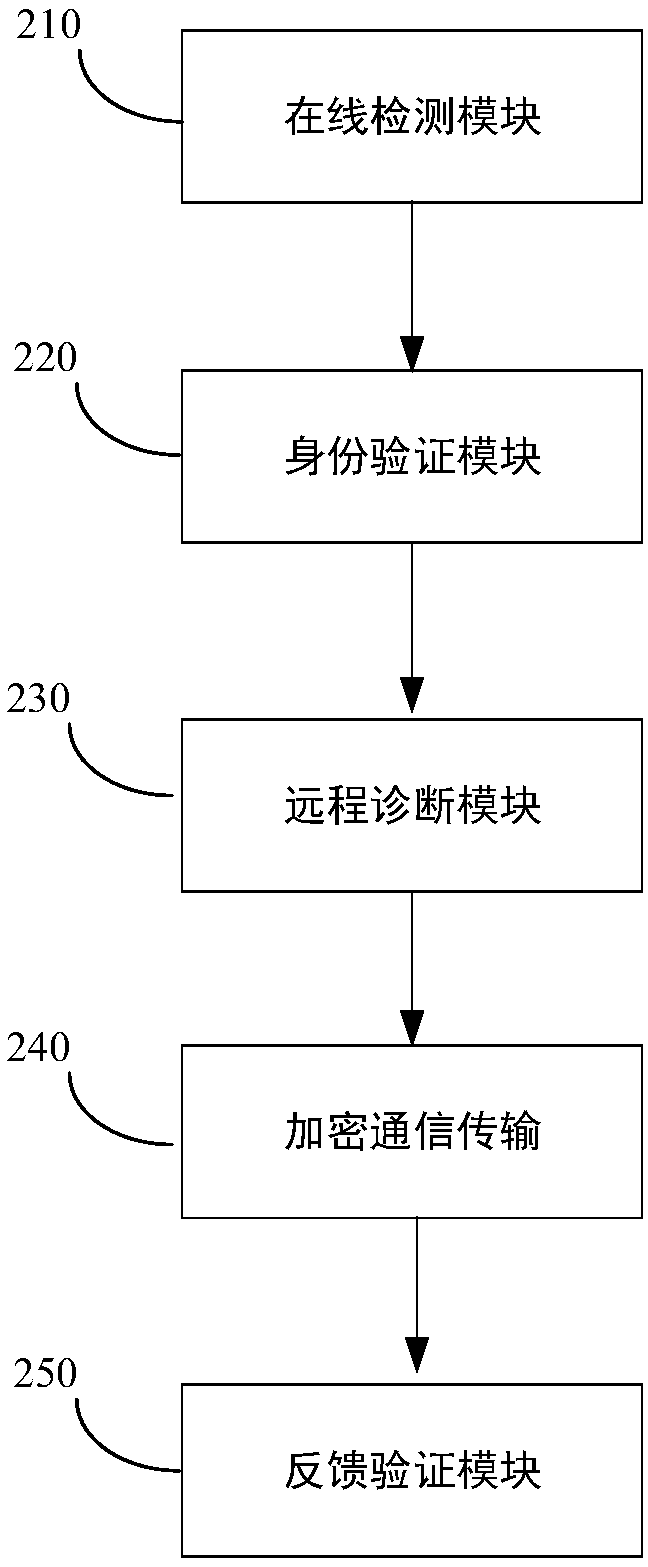
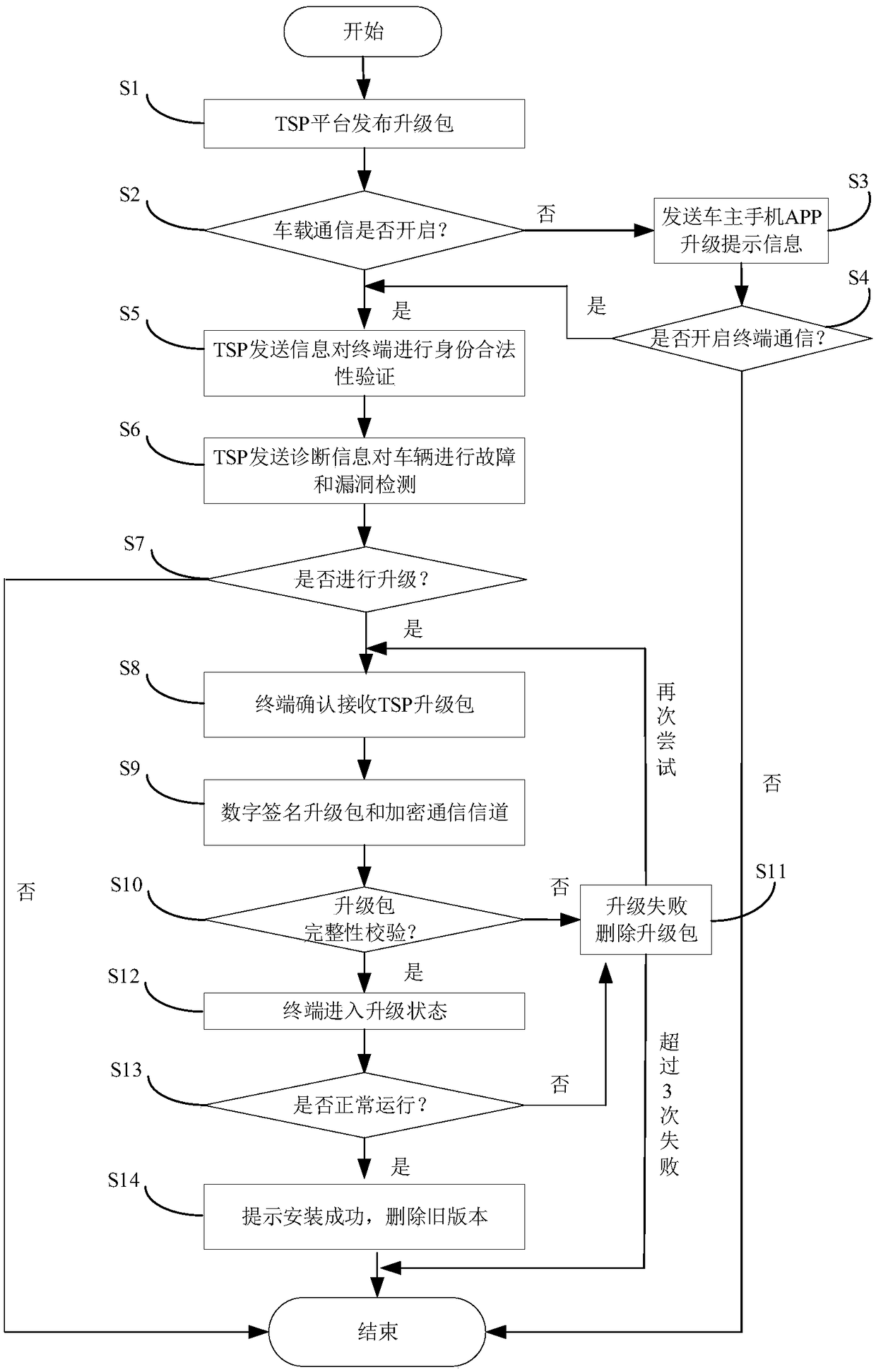
Working method of server, vehicle terminal upgrading method and vehicle terminal upgrading system
InactiveCN108923933APrevent malicious tamperingPrevent illegal intrusionUser identity/authority verificationSecure transmissionComputer module
The invention provides a working method of a server, and the working method comprises the following steps: the server issues an upgrading package; the server judges whether a communication channel ofa vehicle terminal is turned on; if the communication channel of the vehicle terminal is turned on, the server encrypts the upgrading package, and transmits the encrypted upgrading package to the vehicle terminal through the communication channel by a secure transmission mode. According to the method provided by the invention, by functions of an encrypted communication module and a feedback verification module, malicious tampering to the upgrading package or an installation package caused by illegal attacking is avoided, consequently, illegal invasion of the tampered upgrading package to the vehicle terminal, a power control unit, a vehicle owner personal privacy, an information entertainment system, and so on, can be avoided, a problem of existence of hidden security danger in a remote upgrading process of motor vehicles is eliminated, and security and reliability of downloading the upgrading package over the air is guaranteed.
Owner:BEIHANG UNIV
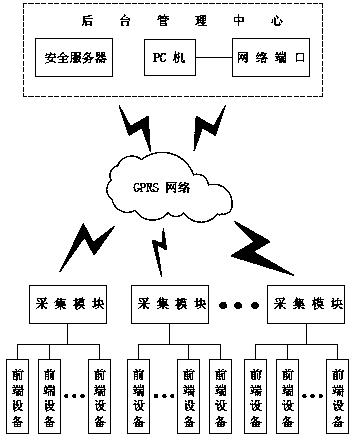
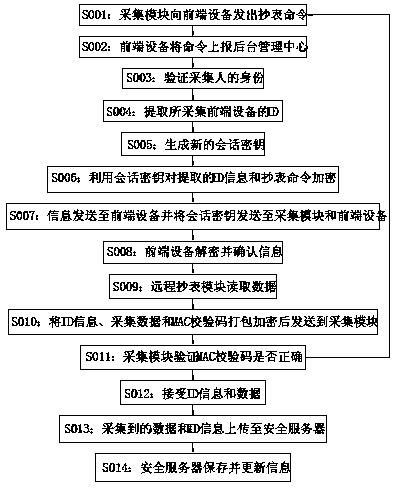
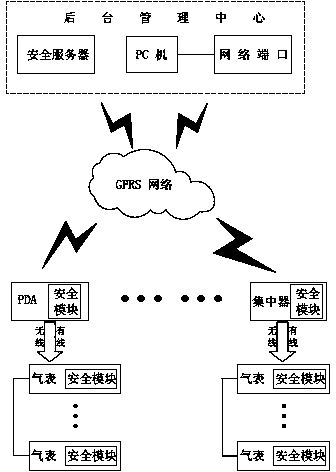
Remote safe meter reading method
ActiveCN103778773AImplement identity authenticationRealize functionElectric signal transmission systemsUser identity/authority verificationSecurity levelRemote meter reading
The invention discloses a remote safe meter reading system, comprising a background management center, a collection module and front-end equipment. A remote safe meter reading method comprises the following processes: 1) sending a meter reading command by the collection module; 2) reporting the command to the background management center; 3) validating the identity of a gatherer; 4) extracting an identity (ID) of the collected front-end equipment; 5) generating a new session key; 6) encrypting the extracted ID information and metering reading command; 7) transmitting information to the front-end equipment, and transmitting the session key to the collection module and the front-end equipment; 8) decrypting and confirming information by the front-end equipment; 9) reading data by the remote meter reading module; 10), packaging and encrypting the ID information, collected data and MAC check code and then transmitting to the collection module; 11) receiving the ID information and data; 12) uploading the data to a safety server; and 13) storing and updating information by the safety server. The functions of identity authentication and data encryption are achieved in the remote meter reading process, and the security level is greatly improved.
Owner:山东微分电子科技有限公司
Method for encrypting wireless sensor network in intelligent medical system
ActiveCN104486758AEnsure safetyBlock read and write operationsTransmissionSecurity arrangementComputer hardwareEncryption
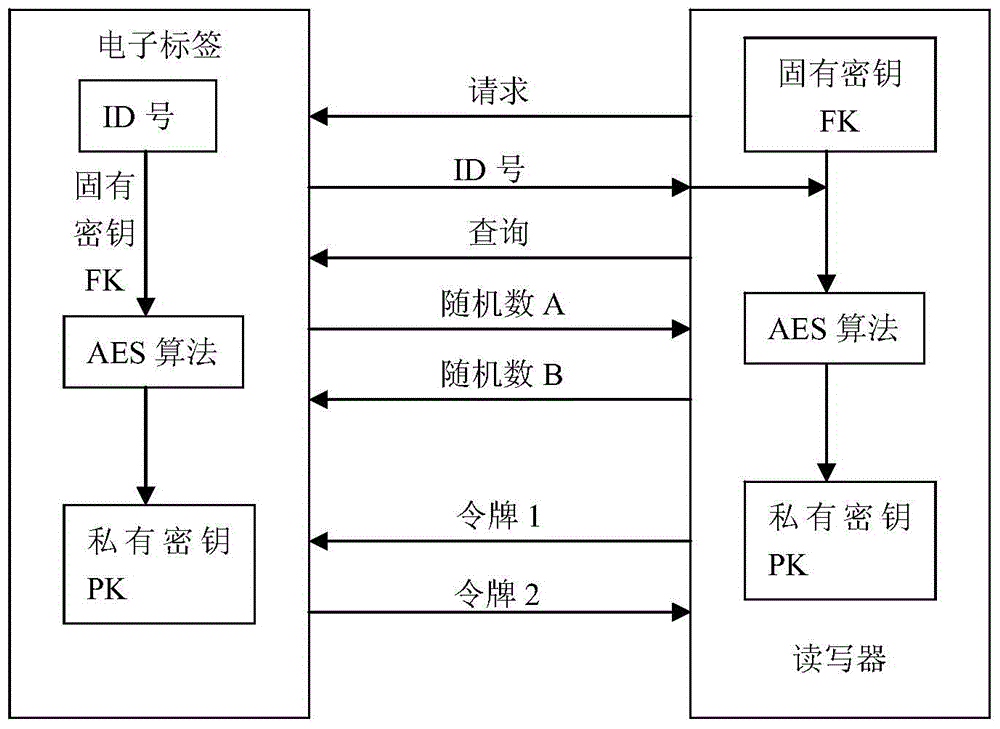
Disclosed is a method for encrypting a wireless sensor network in an intelligent medical system. Firstly, the operation of writing information is carried out in an electronic tag, then sensitive information in an RFID tag is encrypted through a bidirectional authentication protocol of an AES encryption algorithm and a message encryption mechanism to improve system security, and an attacker is prevented from eavesdropping messages.
Owner:和宇健康科技股份有限公司
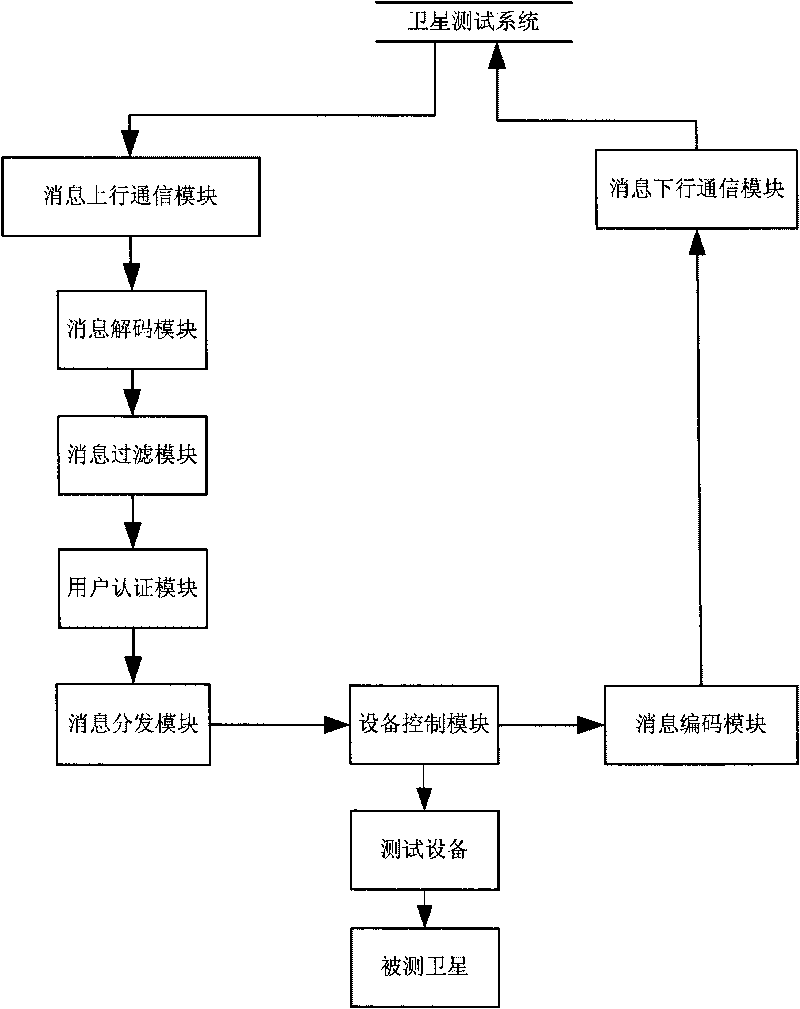
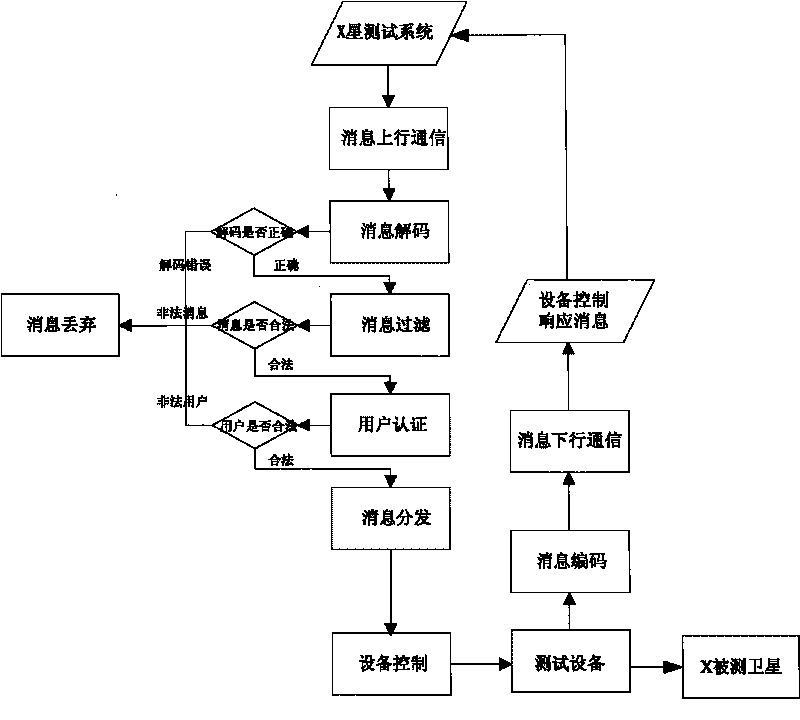
Distributed test control system suitable for small satellite
ActiveCN101729563AEasy Test SwitchingMonitor the test situationUser identity/authority verificationCode moduleControl system
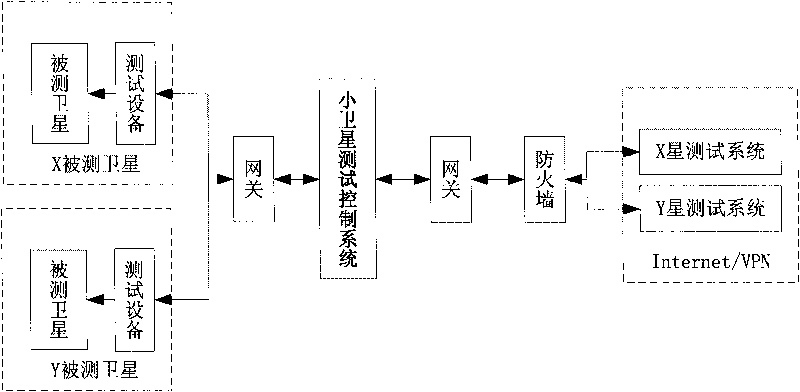
The invention discloses a distributed test control system suitable for a small satellite, which comprises a message uplink communication module, a message decoding module, a message filtering module, a user authentication module, a message distribution module, a device control module, a message coding module and a message downlink communication module. The distributed test control system uses a unified test control mechanism to ensure that only one gateway is arranged between a tested object and all test systems and between a test device and all the test systems, so the distributed test control system can effectively prevent outside illegal invasions and ensure the reliability and the safety of tests; besides, the distributed test control system can realize multi-satellite parallel tests to ensure that a tester can perform test switching easily and monitor test conditions of all satellites, the test work not only can be performed on a test special network but also can be performed on a local area network even the internet so as to realize real distributed tests. By using the distributed test control system, test device resources can be allocated reasonably, and the test cost can be reduced.
Owner:AEROSPACE DONGFANGHONG SATELLITE +1
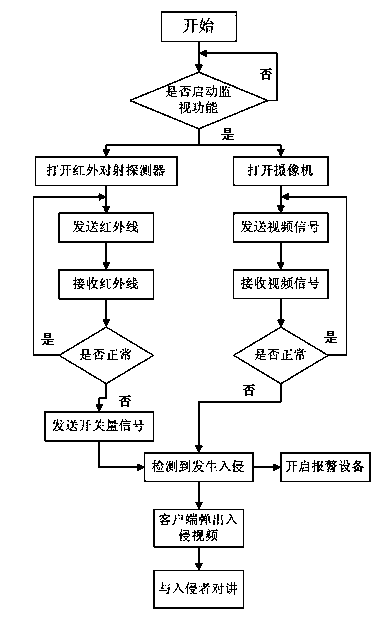
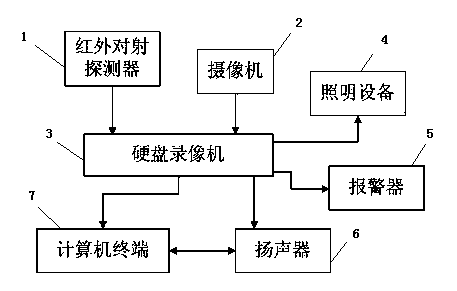
Unattended alarm prompting method and device
The invention relates to an unattended alarm prompting method and a device. The method comprises the following steps: (1) infrared signals of an infrared intrusion detector receiver change, and the infrared intrusion detector sends switching value signals to a hard disk video recorder; (2) a camera outputs video signals to the hard disk video recorder; (3) the hard disk video recorder receives the switching value signals or / and the video signals change, alarm equipment is controlled to start, and alarm signals are outputted to a computer terminal; and (4) popup of an alarm point video is carried out automatically by the computer terminal and alarm information is given. According to the method and the device of the invention, through combination of video detection of the infrared intrusion detector and the hard disk video recorder, illegal intrusion is monitored by using dual-protection line, stability is high and the precision is high; and by the combined alarm of the alarm equipment and the dynamic video, illegal intrusion can be prevented timely and effectively, part of manual work can be replaced, and management cost is reduced.
Owner:上海景鸿保安服务股份有限公司
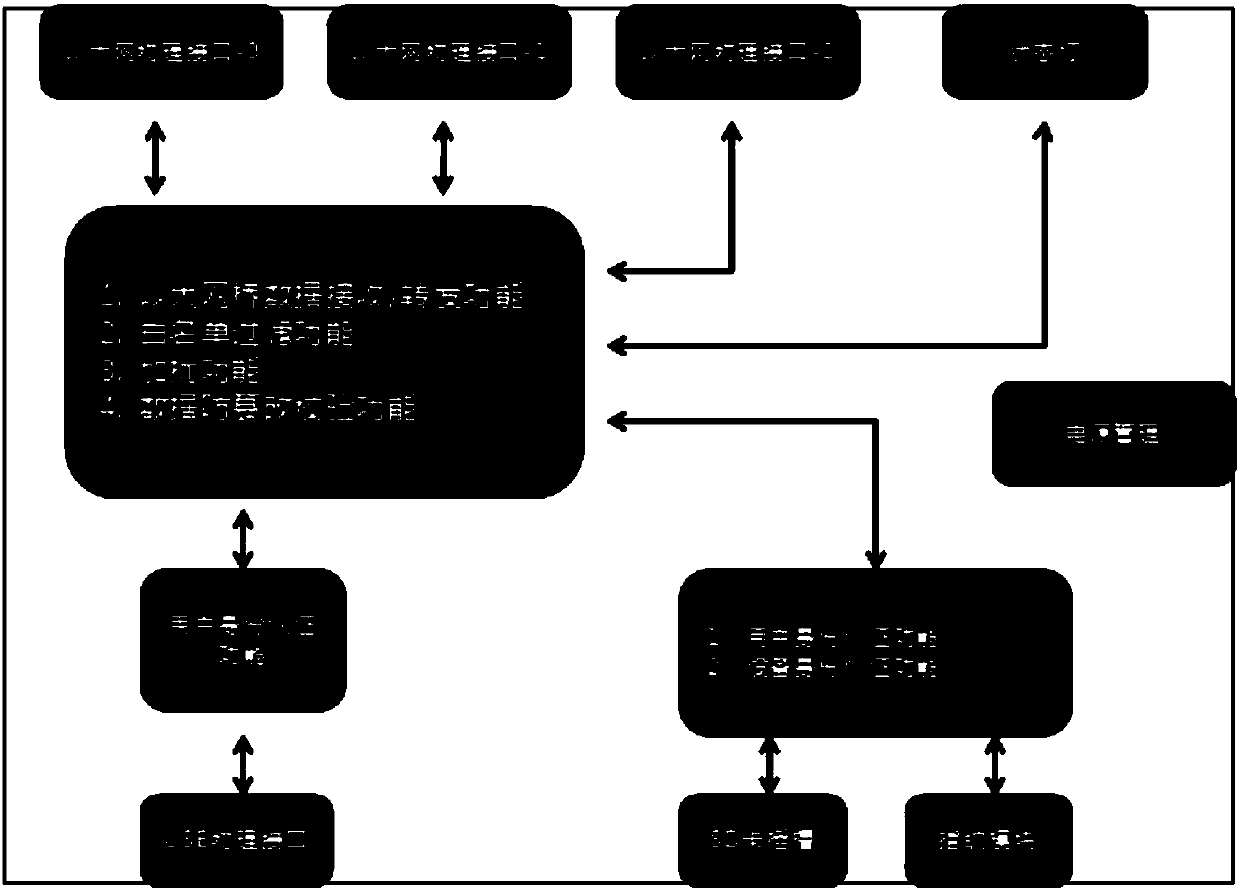
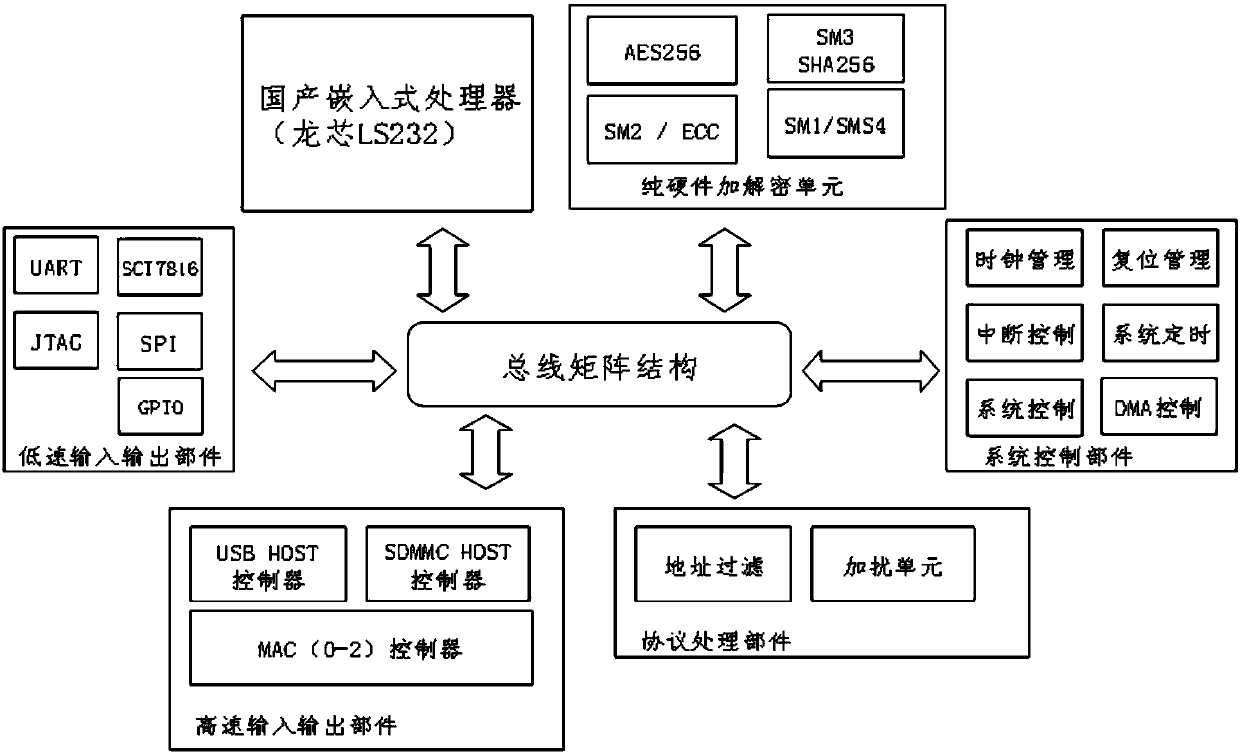
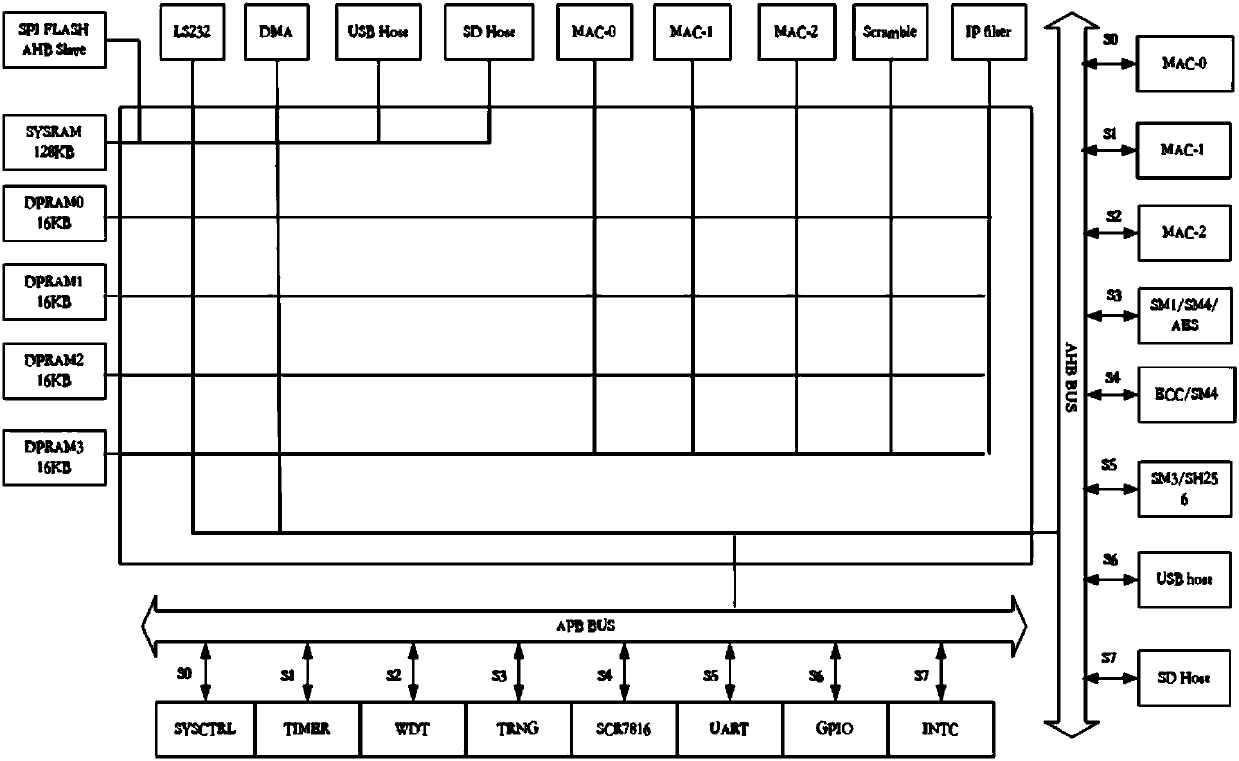
Secure Ethernet bridge scrambling terminal based on national cryptographic algorithm
ActiveCN107612679AImprove performanceHighly integratedData switching detailsEncryption apparatus with shift registers/memoriesTamper resistanceTerminal equipment
The invention relates to a secure Ethernet bridge scrambling terminal based on a national cryptographic algorithm. The terminal includes an Ethernet bridge data receiving / forwarding function, a whitelist filtering function, a scrambling function, a data tamper-proofing verification function, a terminal equipment authentication function and a user use authentication function. According to a security protection scheme that is simple and practicable, is convenient to deploy, and has high cost performance, provided by the invention, the risks of deployed Ethernet terminal equipment and open network data backhaul terminal equipment can be solved by adopting a secure Ethernet bridge scrambling technology based on the national cryptographic algorithm.
Owner:郑州中科集成电路与系统应用研究院
Intelligent lock
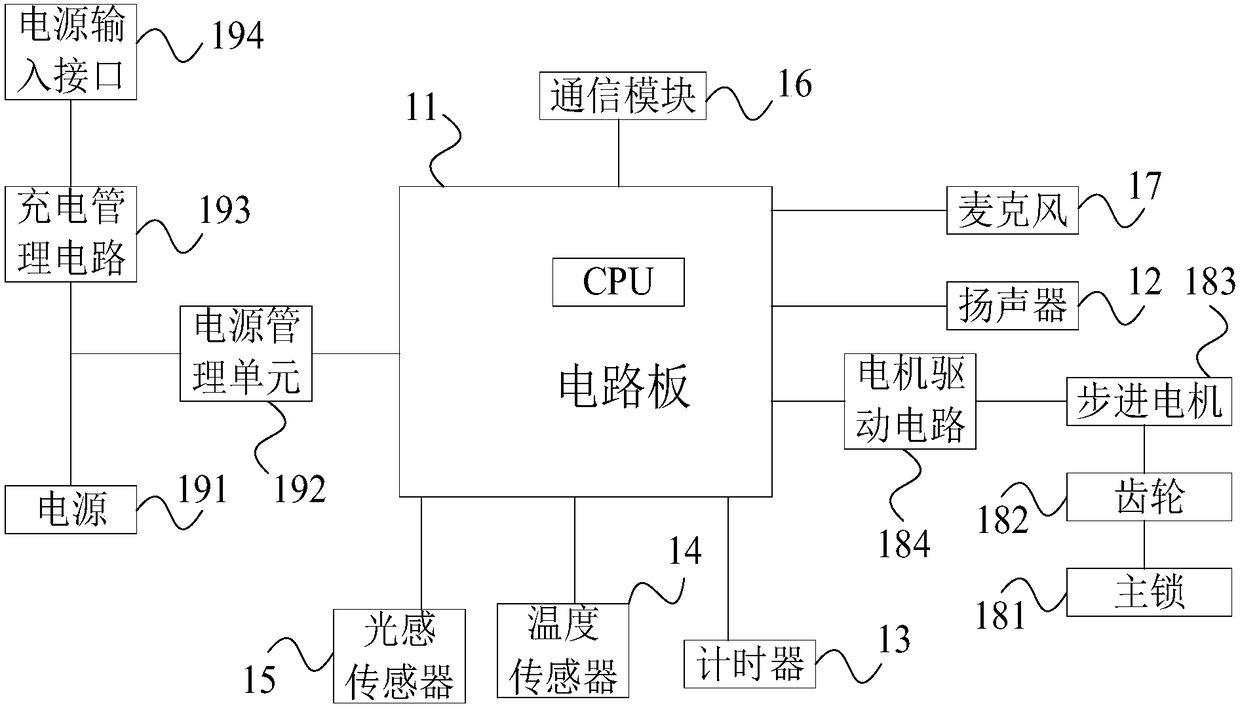
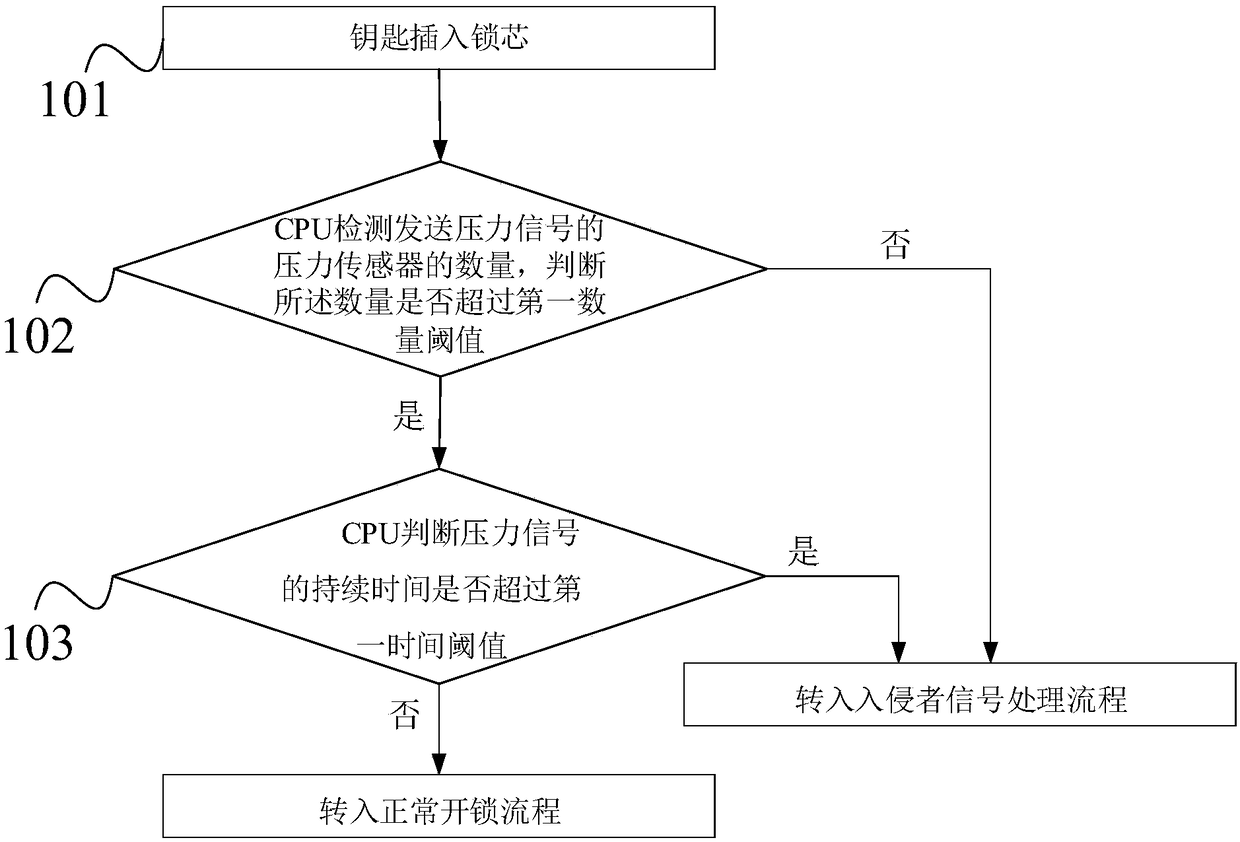
ActiveCN108222678APrevent illegal intrusionImprove securityNon-mechanical controlsForce sensorPressure sensor
The invention discloses an intelligent lock. The intelligent lock comprises a lock body, a lock cylinder and a key. The lock cylinder is arranged in the lock body, and the lock body is internally provided with a CPU. The lock cylinder is internally provided with a plurality pin tumblers, and each pin tumbler is correspondingly connected with a pressure sensor. The key is provided with a pluralityof contactors, the contactors trigger the pin tumblers after the key is inserted into the lock cylinder, the pin tumblers exert pressure on the correspondingly connected pressure sensors after being triggered, and the pressure sensors send pressure signals to the CPU after detecting the pressure signals; and the CPU detects the action that the key is inserted into the lock cylinder through the pressure signals sent by the pressure sensor, the CPU detects the number of the pressure sensors and judges whether the number exceeds a first number threshold value or not, and if not, an alarm signal is given. According to the intelligent lock, intelligent detection can be carried out on the key, the alarm is given when it is detected that the key does not conform to requirements or the lock is unlocked for a long time, illegal invasion of an invader is prevented, and a very good antitheft function is achieved.
Owner:SIMCOM WIRELESS SOLUTIONS SHANGHAI
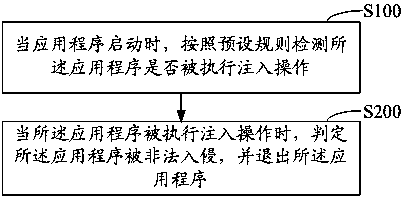
Method for detecting illegal invasion of application program, storage medium and terminal equipment
InactiveCN110321703APrevent illegal intrusionImprove stabilityPlatform integrity maintainanceTerminal equipmentComputer terminal
The invention discloses a method for detecting illegal invasion of an application program, a storage medium and terminal equipment, and the method comprises the steps: detecting whether an injection operation is executed for the application program or not according to a preset rule when the application program is started; and when the injection operation is executed on the application program, judging that the application program is illegally invaded, and exiting the application program. The injection operation of the application program is monitored, and when the injection operation is monitored, the application program is judged to have illegal invasion, so that the current application program can exit, the application program is prevented from being illegally invaded, and the stabilityand the safety of the application program of the mobile terminal are improved.
Owner:北京智游网安科技有限公司
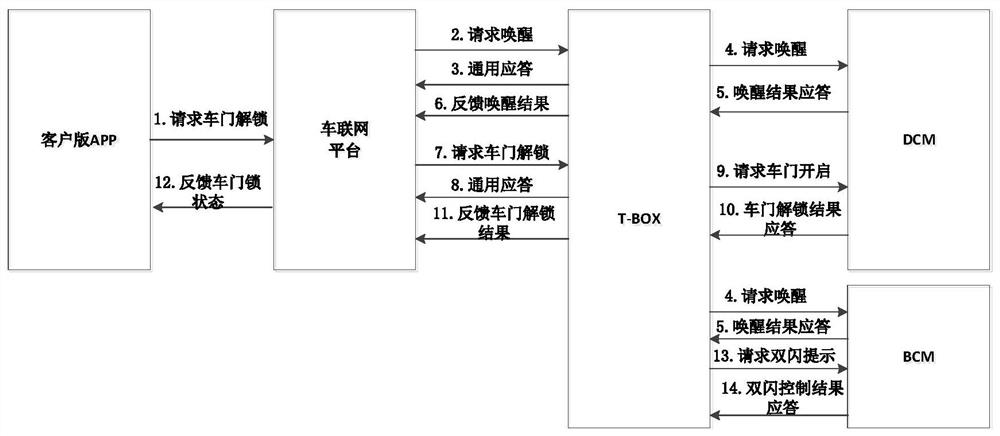
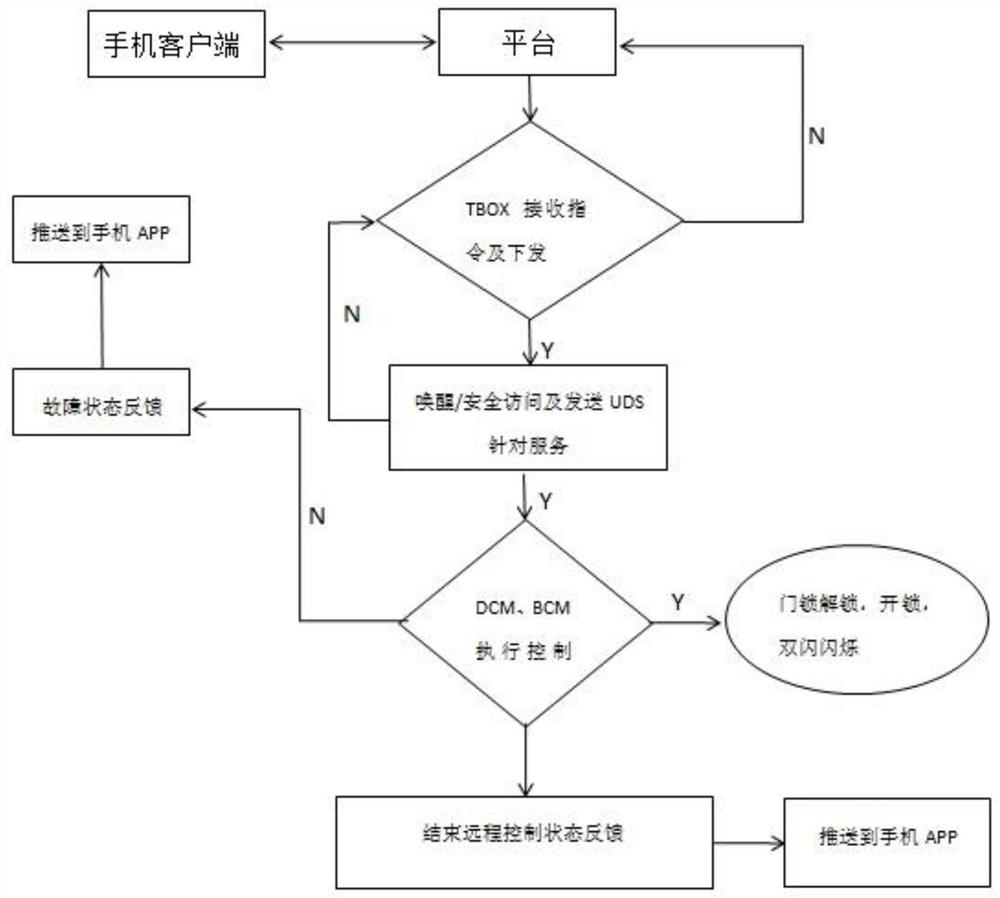
Remote vehicle door control system
ActiveCN112037379AHigh degree of intelligenceImprove securityUser identity/authority verificationIndividual entry/exit registersIn vehicleControl system
The invention discloses a remote vehicle door control system. The remote vehicle door control system comprises a remote control module used for sending a vehicle door unlocking instruction and receiving a vehicle door unlocking state, an Internet of Vehicles platform used for sending the vehicle door unlocking instruction with verification and authentication information and feeding back a receivedvehicle door unlocking state to the remote control module, a vehicle-mounted terminal module used for carrying out safety verification after receiving the vehicle door unlocking instruction and sending the vehicle door unlocking instruction with verification and authentication information to a vehicle body control module after the verification succeeds, and the vehicle body control module used for carrying out safety verification after receiving the vehicle door unlocking instruction, controlling a vehicle door to be unlocked after the verification is successful, and feeding back the vehicledoor unlocking state to the vehicle-mounted terminal module. Safety verification is carried out during vehicle door unlocking information communication, local illegal invasion door opening is effectively avoided, and the safety of vehicle door control is greatly improved.
Owner:DONGFENG COMML VEHICLE CO LTD
Alarm linkage method for security system
InactiveCN109215264AEasy to archiveEasy to analyzeClosed circuit television systemsBurglar alarmAlarm messageEngineering
The invention relates to an alarm linkage method for a security system. The method comprises the following steps: remotely arming and disarming through an alarm device, supporting virtual zone setting, and supporting a pre-planning operation of arming / disarming; supporting a linkage map, a linkage video, a linkage large screen, a linkage sound and photoelectric device, a linkage processing device,and a linkage communication device through various linkage schemes for various types of alarms; dealing with the situation by linkage or communication equipment, the alarm is considered to require vigilance after reviewing by the on-duty personnel; and supporting the query statistics of the alarm information, and displaying the results in the form of a list and an icon, and exporting them in various file forms to facilitate the archiving and analysis of the alarm information.
Owner:CHINA CHANGFENG SCI TECH IND GROUPCORP
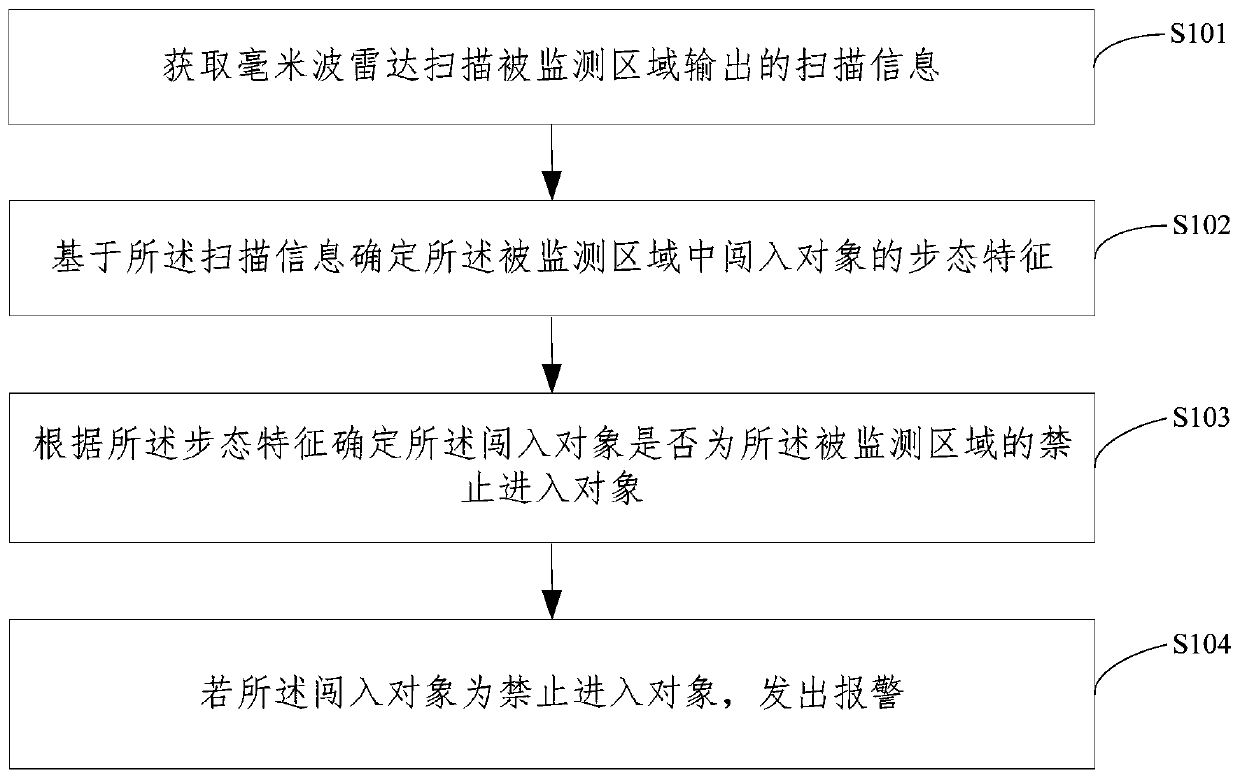
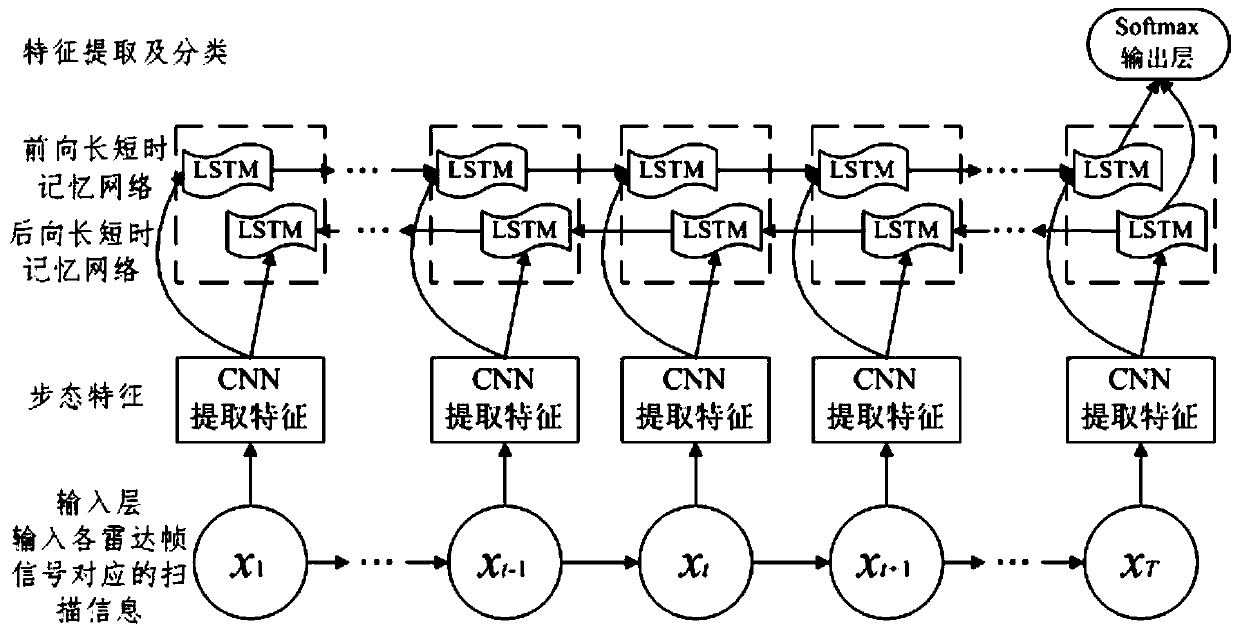
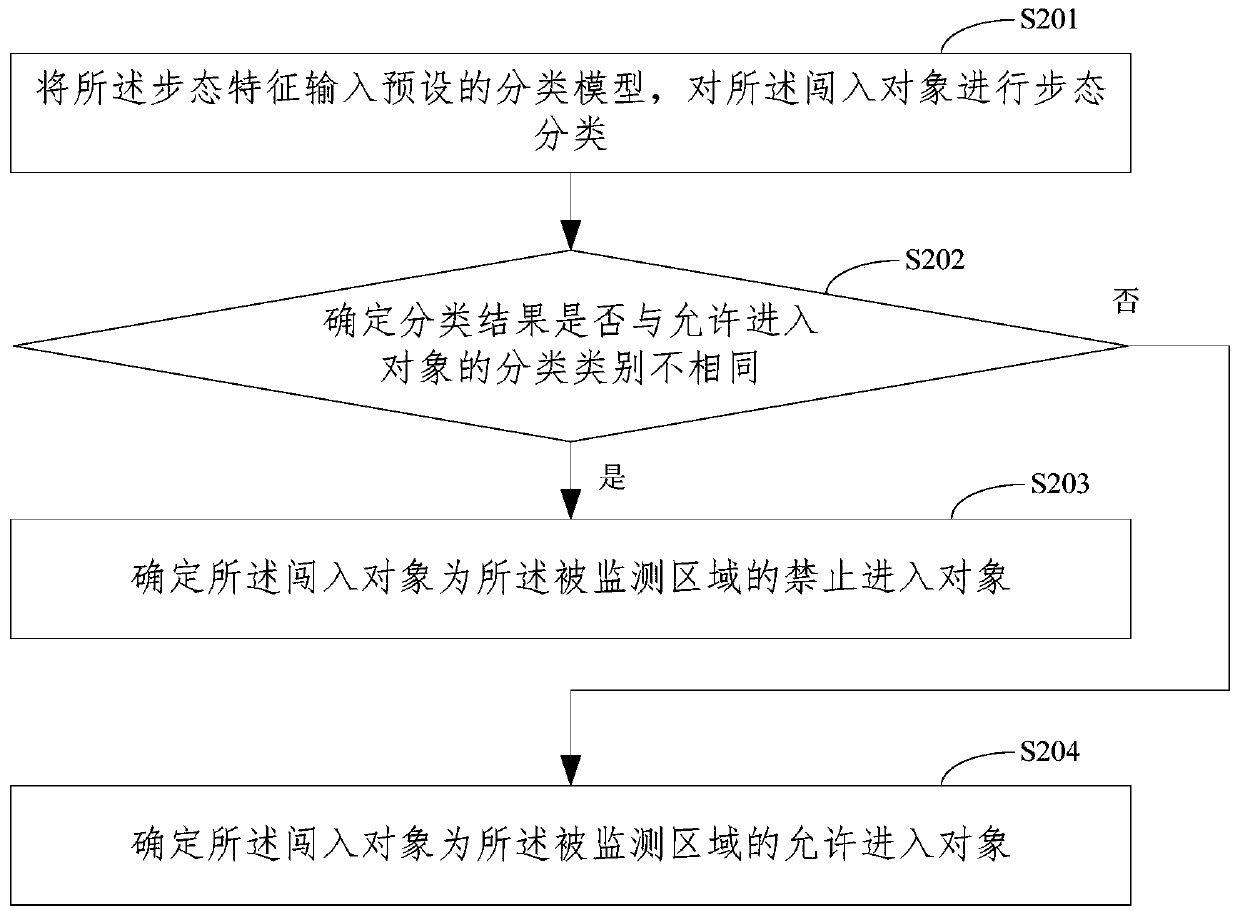
Region monitoring method and device, electronic equipment and storage medium
The invention relates to a region monitoring method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring scanning information output by scanning amonitored region by a millimeter-wave radar; determining gait characteristics of an intruding object in the monitored region based on the scanning information; determining whether the intruding object is an object forbidden to enter the monitored region or not according to the gait characteristics; and if the intruding object is an object forbidden to enter, giving an alarm. According to the embodiment of the invention, whether the intruding object is the entry forbidding object or not can be determined according to the gait characteristics of the intruding object, and when the intruding object is the entry forbidding object, an alarm can be given out, so that responsible personnel in the monitored area can arrive at the scene as soon as possible, and the safety of the specific monitoredarea is guaranteed.
Owner:GREE ELECTRIC APPLIANCES INC +1
Device search and location method and intelligent linkage management method
InactiveCN108052660ASolve the problem of large security risks in operation and maintenanceRealize 3D visualization displayData processing applicationsGeographical information databasesDevice failureComputer science
The invention relates to a device search and location method and an intelligent linkage management method. The method includes the following steps that machine-room parameter information of each machine room is obtained, according to the machine-room parameter information, internal parameter information of each machine room is obtained, and according to the internal parameter information of each machine room, a 3D visualized environment is built; attribute information of equipment in machine rooms is obtained, and according to the attribute information of equipment, an equipment database is built; retrieval content is obtained, according to the retrieval content, data in the equipment database is called to be compared with the retrieval content, and the content of successful comparison isdisplayed. The problems that failure of the equipment in a traditional machine room can not be quickly searched, maintenance can not be timely conducted and thus operation and maintenance of the machine room has many potential safety hazards are solved, 3D visualization display of an equipment cabinet in the machine room is achieved, dynamic calling and equipment inspection can be achieved, the service life of the equipment is prolonged and management work of the equipment are enhanced.
Owner:王开富
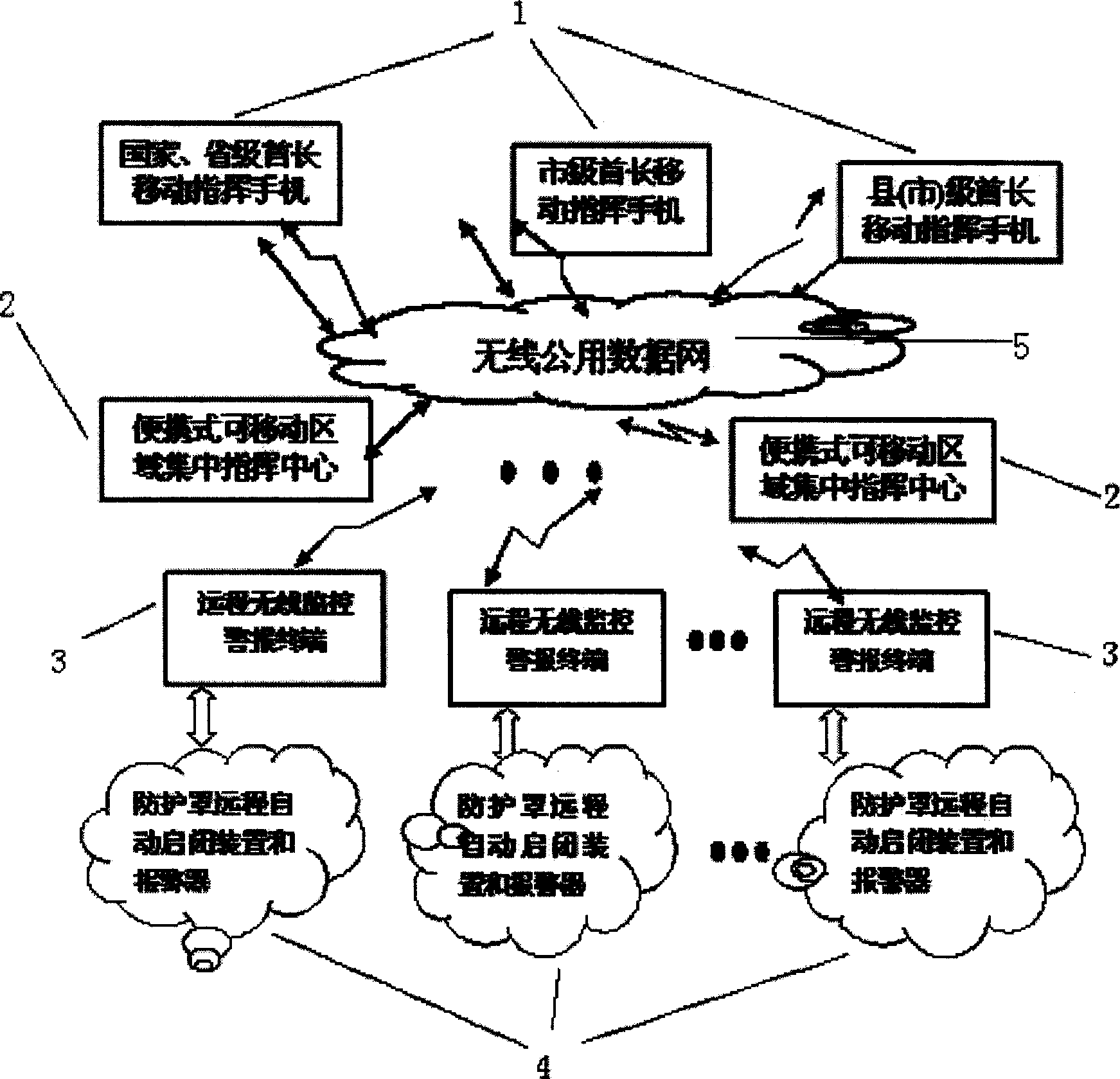
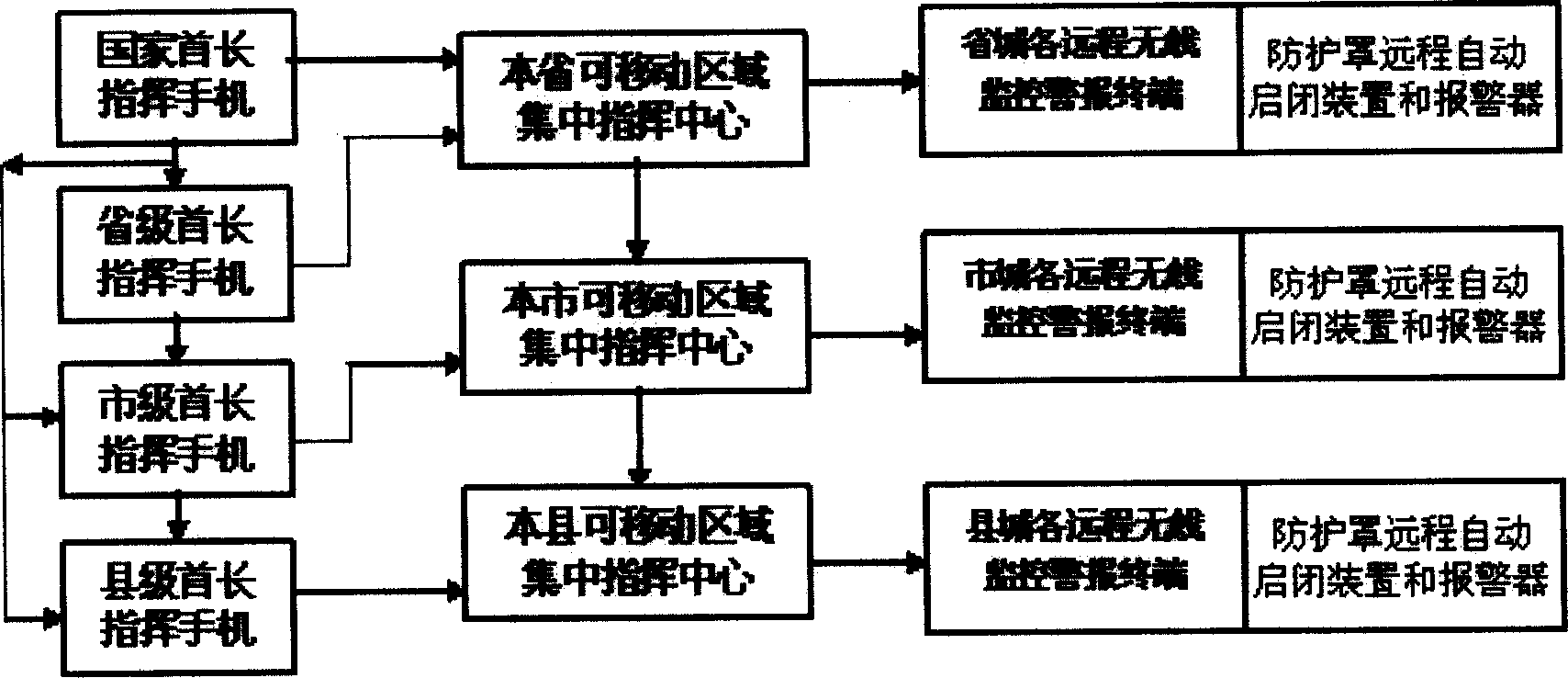
Multistage wireless remote antiaircraft alarm centralized command and control system
InactiveCN1756282AInnovative ideasWell-structuredTelephonic communicationControl systemPublic network
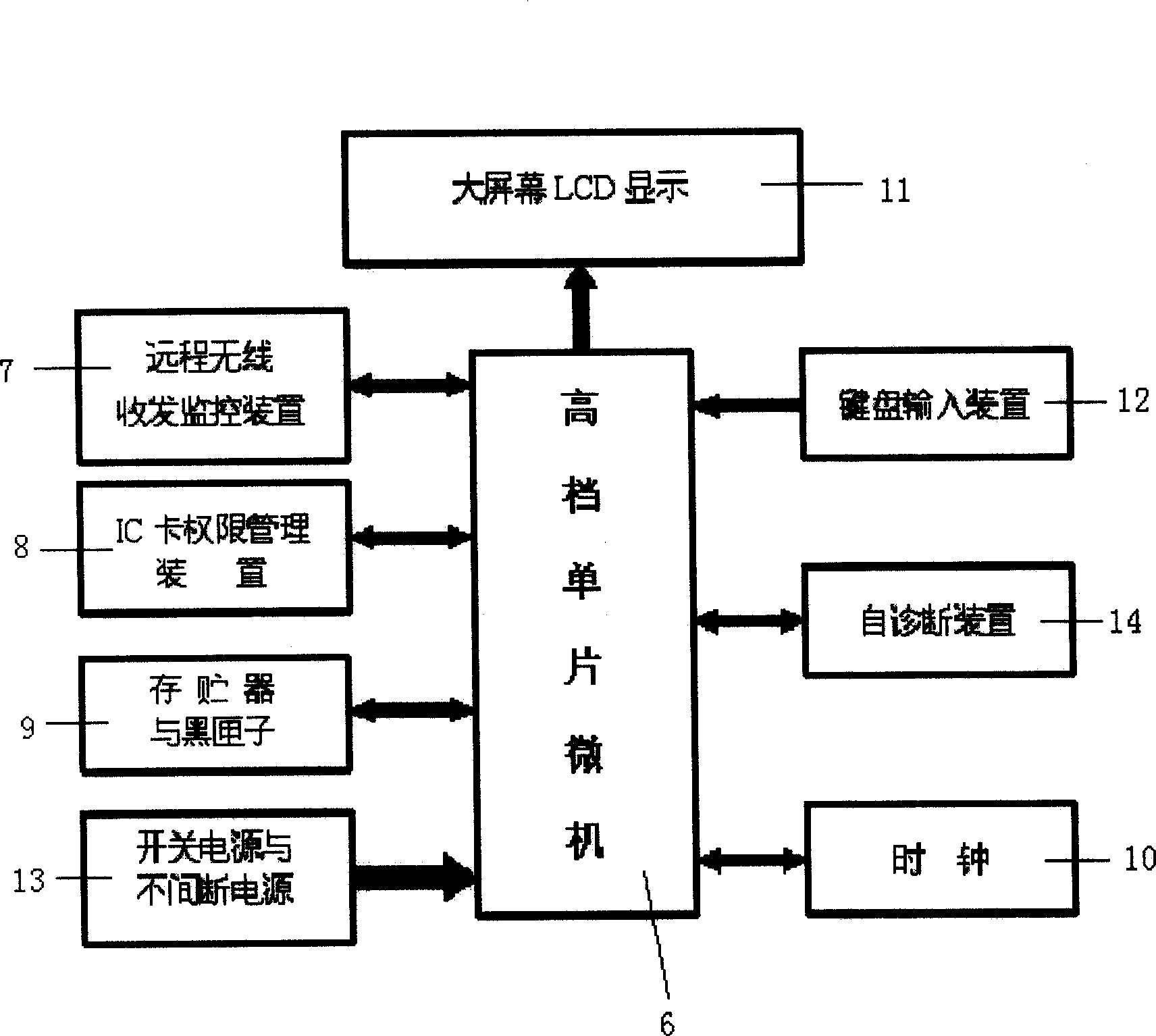
The multi-layer wireless promote airproof alarm integrated command and control system comprises: all levels director command mobile phone 1 to connect to following local center 2 for double-direction data exchange according to set right with wireless public network, portable promote wireless local integrates command center 2 to connect to local promote wireless monitor alarm terminal for single-direction data transmission with wireless public data network, promote wireless monitor alarm terminal 3, shield promote auto-start-break device and alarm 4 connected with terminal 3. This invention is real time, reliable, security and low cost.
Owner:曹晓克
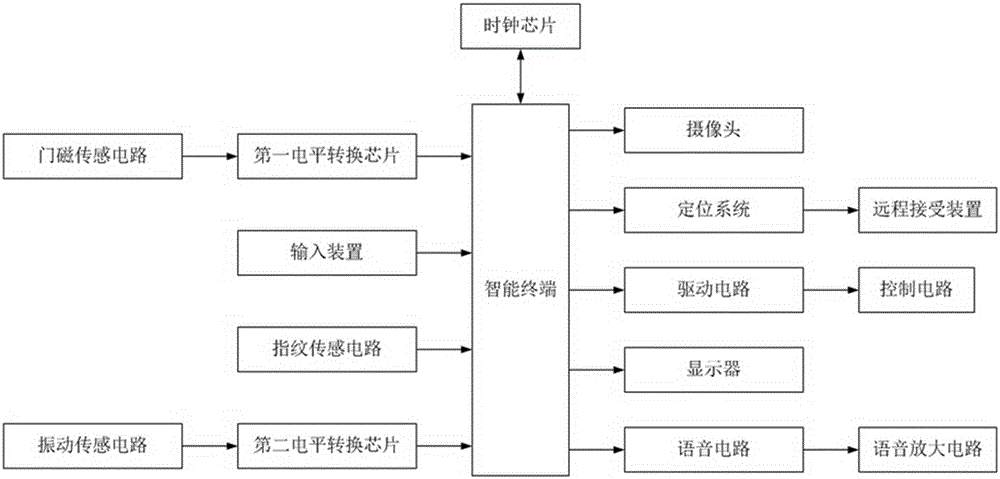
Intelligent entrance guard system
InactiveCN104134264AImprove securityPrevent illegal intrusionCharacter and pattern recognitionIndividual entry/exit registersMagnetoFingerprint
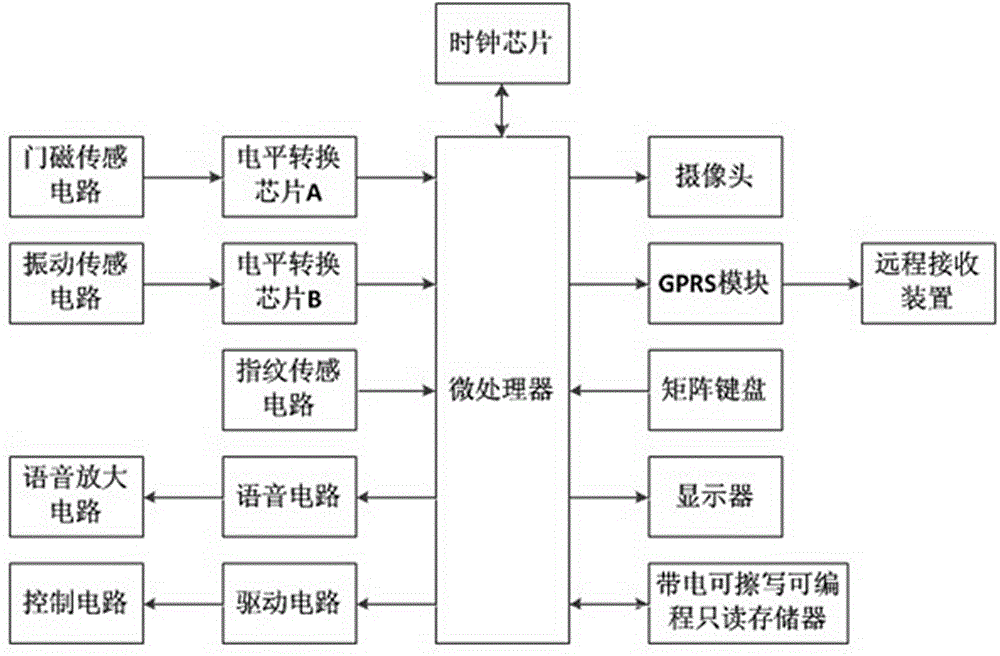
The invention discloses an intelligent entrance guard system which comprises a microprocessor, as well as a level switch chip A, a level switch chip B, a fingerprint sensing circuit, a speech circuit, a drive circuit, a clock chip, a camera, a GPRS (general packet radio service) module, a matrix keyboard and a display, which are connected with the microprocessor respectively. The level switch chip A is connected with a door magneto-sensing circuit, the level switch chip B is connected with a vibration sensing circuit, the fingerprint sensing circuit is mounted on the outer surface of a key on the matrix keyboard, the drive circuit is connected with a control circuit, and the GPRS module is connected with a remote receiving device. By mounting the fingerprint sensing circuit on the outer surface of the key on the matrix keyboard, the fingerprint sensing circuit can be hidden to greatly improve the security of the intelligent entrance guard system; through the combination of a coded lock and fingerprint recognition, a door can be opened only under the condition that both the code lock and a fingerprint are right, so that trespass can be prevented effectively.
Owner:CHENGDU XINXIN INFORMATION TECH
Energy monitoring system for Internet of things
InactiveCN109309733ASolve wasteLow costTechnology managementResourcesData transformationThe Internet
The invention discloses an energy monitoring system for the Internet of things, and belongs to the technical field of energy monitoring. The energy monitoring system comprises an equipment acquisitionsystem, an energy monitoring platform system and a client system, wherein the equipment acquisition system digitizes and structuralizes a field environment through front-end equipment; the energy monitoring platform system is a computing and processing cloud center of the energy monitoring system for the Internet of things, and converts data acquired by the front-end equipment into equipment information, an equipment status and equipment data by centralized data processing and calculation; and the client system provides real-time energy information or historical energy data viewing and retrieval by intuitive and visual graphics, textual information and process status diagrams. The energy monitoring system can be installed on site, follows the principle of low power design, has a remote management function, and is convenient for deployment and upgrading. The safety of enterprise production information is fully ensured. The transmission of industrial standard protocols can be finished,and illegal intrusion and other network attacks can also be prevented.
Owner:南京物盟信息技术有限公司
A novel unattended system in power distribution room
InactiveCN109193369AEasy access to viewFriendly experienceBoards/switchyards circuit arrangementsCircuit arrangementsData acquisitionVia device
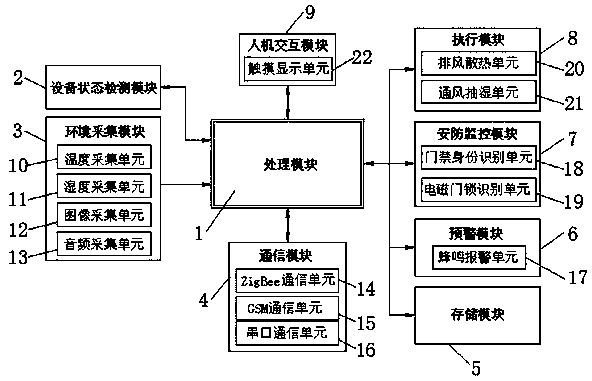
The invention discloses a novel unattended system of a power distribution room, comprising a processing module, a device state detection module, an environment acquisition module, a communication module, a storage module, an early warning module, a security monitoring module, an execution module and a man-machine interaction module. The invention collects the data of the power distribution room through the equipment state detection module and the environment acquisition module in advance, When the temperature or humidity in the power distribution room is high, heat dissipation, dehumidification and ventilation of the distribution room are carried out through an execution module, at the same time, the access condition is monitor in real time by the security monitoring module, Unlawful intrusions are eliminated, In addition, through the man-machine interaction module and the communication module, it is convenient for the user to visit the terminal and the fixed interface, which enhancesthe security function of the unattended power distribution room, effectively protects the safety of the power distribution room equipment, and has comprehensive functions, reduces the proportion of labor force and time, and is friendly to the users.
Owner:合肥多元节电科技有限公司
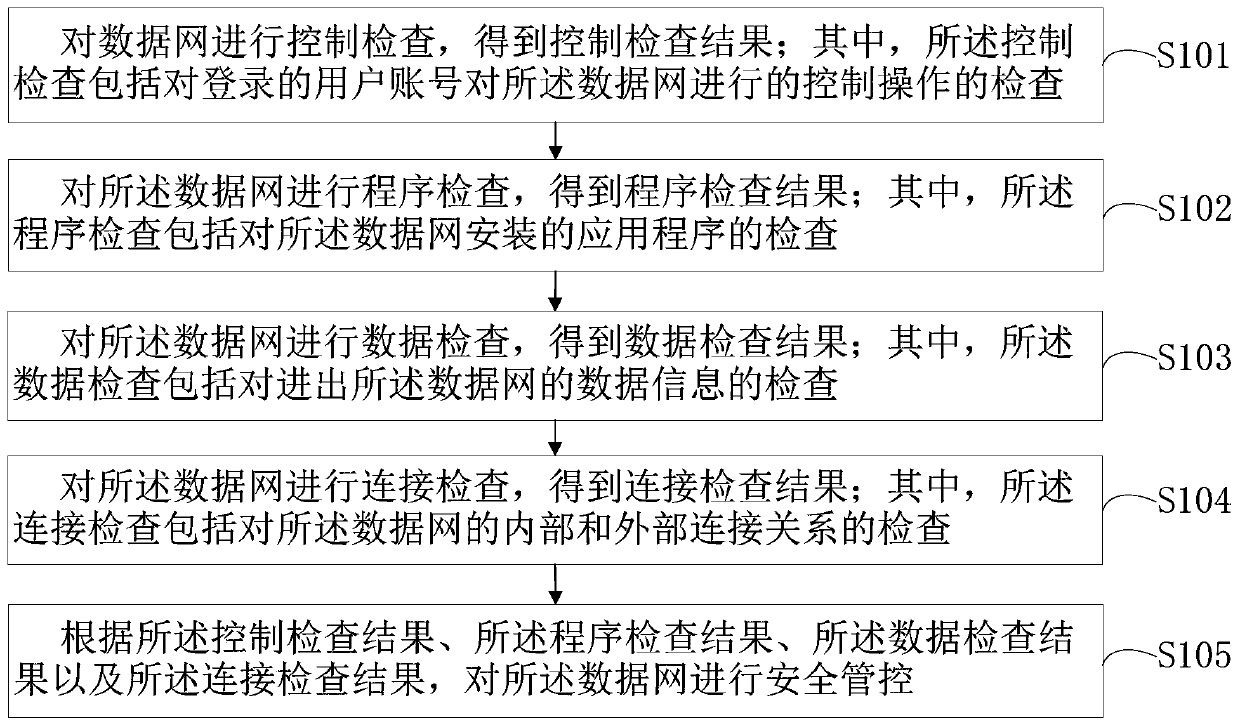
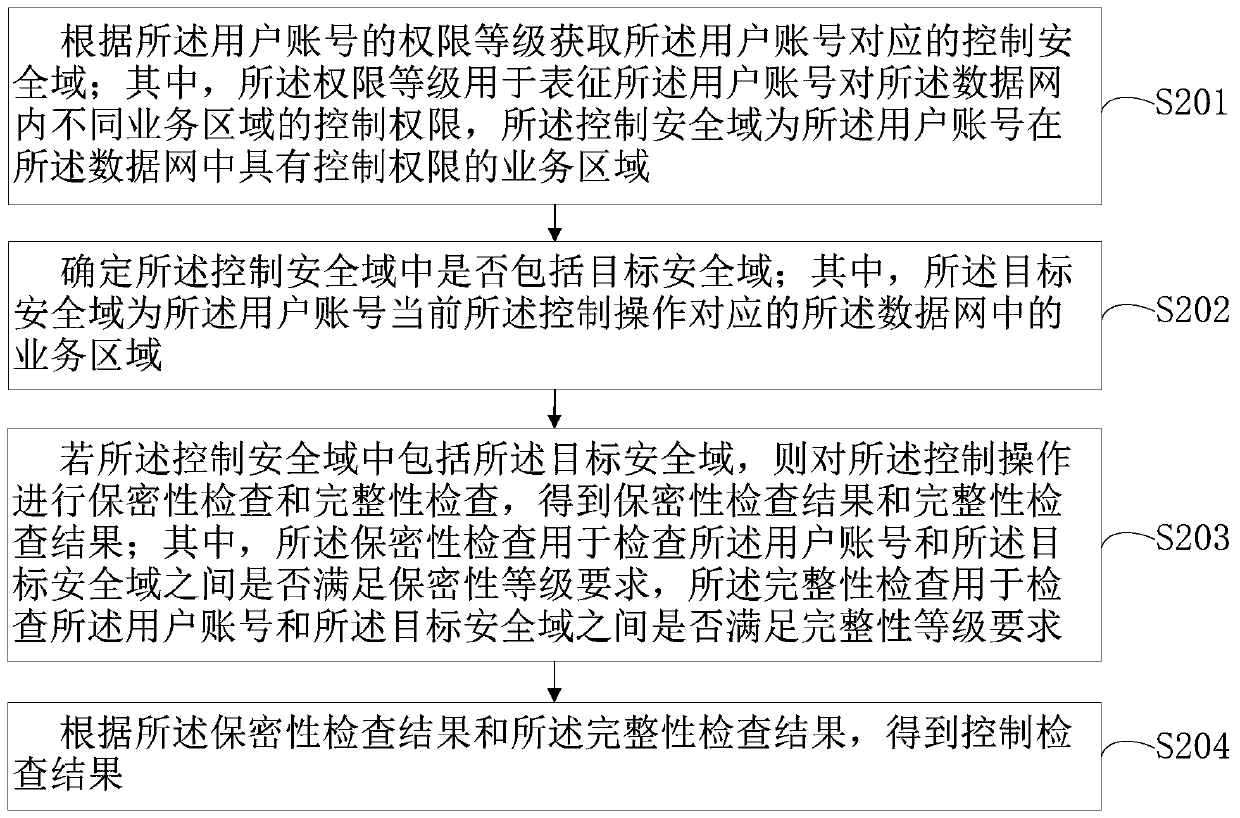
Data network security protection method and device, computer equipment and storage medium
ActiveCN110933054AImplement environmental security checksImplement boundary security checksTransmissionDatabaseData Web
The invention relates to a data network security protection method and a device, computer equipment and a storage medium, and the method comprises the steps: carrying out the control check of a data network, and obtaining a control check result; wherein the control check comprises check of a control operation performed on the data network by the logged-in user account; performing program inspection on the data network to obtain a program inspection result; wherein the program inspection comprises inspection of an application program installed in the data network; performing data check on the data network to obtain a data check result; wherein the data inspection comprises inspection of data information entering and exiting the data network; performing connection check on the data network to obtain a connection check result; wherein the connection check comprises check of an internal and external connection relationship of the data network; and performing security management and controlon the data network according to the check result. Internal and external comprehensive protection of the railway signal safety data network is realized, the closure and independence of the railway signal safety data network are ensured, and the railway signal safety data network has high-grade safety protection capability.
Owner:BEIJING SWJTU RICHSUN TECH
Automatic intelligent anti-theft door device
InactiveCN105096434AImprove securityEliminate theftIndividual entry/exit registersSpecial door/window arrangementsKey pressingPassword
The invention discloses an automatic intelligent anti-theft door device. The automatic intelligent anti-theft door device comprises an intelligent terminal, a first level switch chip, a second level switch chip, a fingerprint sensing circuit, a voice circuit, a driving circuit, a clock chip, a camera, a locating system, an input device and a displayer, wherein the first level switch chip, the second level switch chip, the fingerprint sensing circuit, the voice circuit, the driving circuit, the clock chip, the camera, the locating system, the input device and the displayer are connected with the intelligent terminal. The first level switch chip is connected with a door magnetism sensing circuit, the second level switch chip is connected with a vibration sensing circuit, the fingerprint sensing circuit is installed on the outer surfaces of keys of the input device, the driving circuit is connected with a control circuit, and the locating system is connected with a remote receiving device. As the fingerprint sensing circuit is installed on the outer surfaces of the keys of the input device, a fingerprint recognition circuit can be concealed, and the safety of the automatic intelligent anti-theft door device is greatly improved; as a password lock is combined with fingerprint recognition, only when passwords and fingerprints are correct, can a door be opened, and illegal invasion is effectively prevented.
Owner:CHENGDU LEWEISI TECH
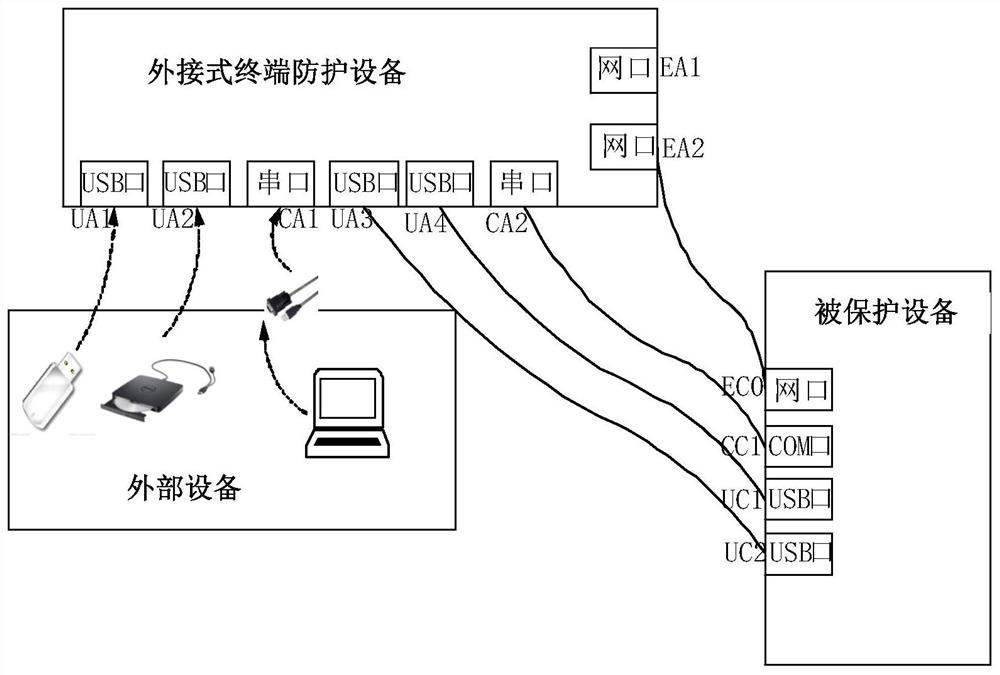
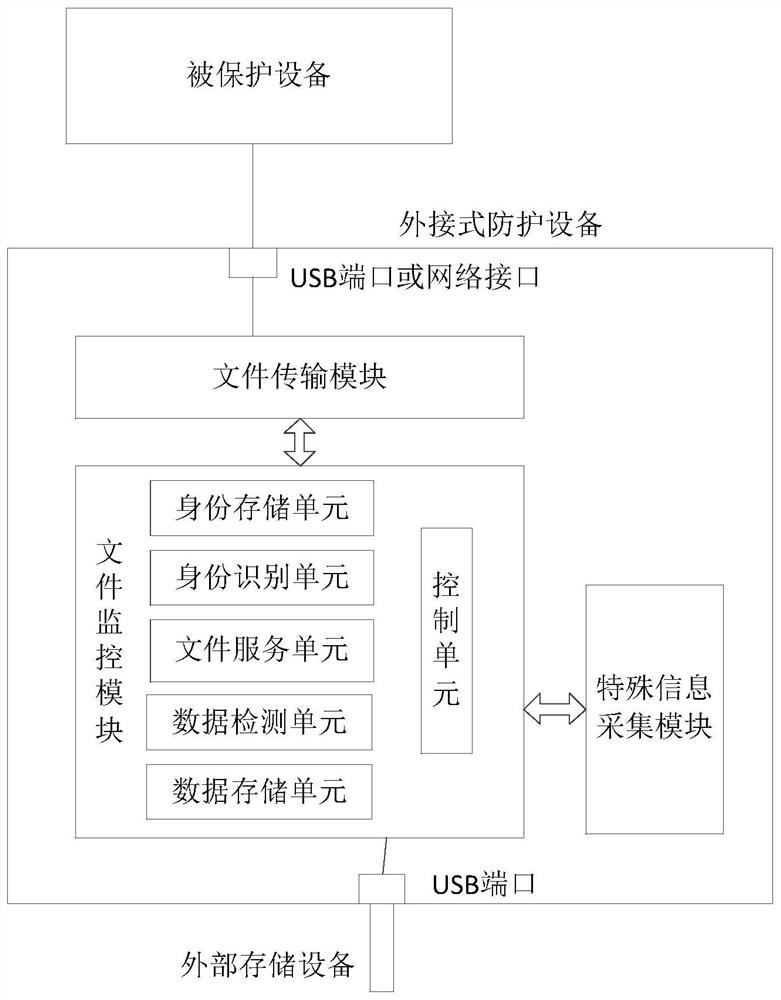
External terminal protection equipment and protection system comprising identity information verification
PendingCN111898167AReduce system security risksSolve potential safety hazardsDigital data protectionInternal/peripheral component protectionReal time acquisitionComputer security
The invention discloses external terminal protection equipment and a protection system comprising identity information verification. The external terminal protection equipment comprises: a plurality of external interfaces used for being connected with one or more external equipment and a piece of protected equipment respectively; the identity information acquisition module that is used for acquiring identity information of a user in real time; the file monitoring module that is connected with the identity information acquisition module, is used for verifying the identity information, and is also used for controlling the security authentication of external equipment accessed to the external interface; and the file transmission module that is connected with the file monitoring module and isused for transmitting the file data imported by the external equipment to the protected equipment under the control of the file monitoring module. According to the invention, the purpose of performingsafety protection on the protected equipment without installing safety protection software on the protected equipment can be achieved, and the safety risk of the system is greatly reduced by verifying and determining the identity and the use permission of the current operator.
Owner:北京中科麒麟信息工程有限责任公司
Power quality intelligent comprehensive optimization device with field vibration wireless alarming function
InactiveCN107069746AEnsuring drop compensation effectLower latencyActive power filteringReactive power adjustment/elimination/compensationPower qualityCapacitance
The invention provides a power quality intelligent comprehensive optimization device with a field vibration wireless alarming function. A DVR (Dynamic Voltage Restorer) converter, a first DC capacitor and an APF (Active Power Filter) converter are in parallel connection to form a first compensation loop for voltage compensation; a DVR converter, a second DC capacitor and a second APF converter are in parallel connection to form a second compensation loop for harmonic processing and reactive power compensation; a load compensator is used for recording parameters such as starting, operation and removing of a specific load; a DC voltage fluctuation suppressor is used for suppressing DC voltage of the first DC capacitor and the second DC capacitor; and a network controller is used for controlling voltage compensation of the first compensation loop, controlling harmonic processing and reactive power compensation of the second compensation loop and providing a corresponding compensation algorithm according to a parameter change rule in the load compensator. Thus, voltage drop is compensated in the case of power grid voltage drop, harmonic processing and reactive power compensation are carried out in the case of no drop, the voltage fluctuation can be suppressed to acquire a high-quality output waveform, and the power consumption quality compensation speed is improved for the user.
Owner:WENZHOU POLYTECHNIC
Anti-intrusion intelligent security system and detection and recognition method thereof
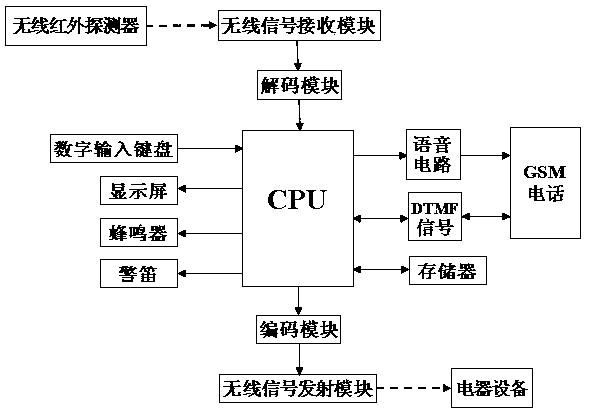
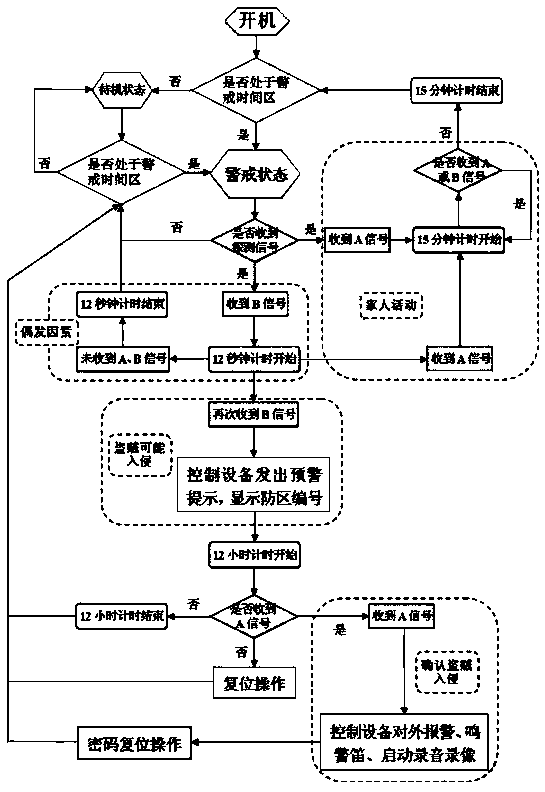
PendingCN109360360APrevent illegal intrusionEnsure living safetyBurglar alarm short radiation actuationDigital inputInfrared detector
The invention discloses an anti-intrusion intelligent security system and a detection and recognition method thereof. The security system comprises a CPU, a wireless signal receiving module, a wireless signal transmitting module, an encoding module, a decoding module, a plurality of wireless infrared detectors, a digital input keyboard, a display screen, a buzzer, a siren, and a memory. The wireless signal receiving module is wirelessly connected to the wireless infrared detector. The decoding module is connected between the wireless signal receiving module and the CPU. The encoding module isconnected between the CPU and the wireless signal transmitting module. The wireless signal transmitting module is wirelessly connected to other electrical devices. The digital input keyboard, displayscreen, buzzer, siren and memory are all connected to the CPU. The security system of the anti-intrusion intelligent security system can intelligently identify family activities or thief intrusion, can issue an early warning before the thief has entered the home, can send an alarm and transmit an audio and video when the thief enters the home to prevent illegal invasion and ensure the safety of living.
Owner:吴佳奇
House safety protection system
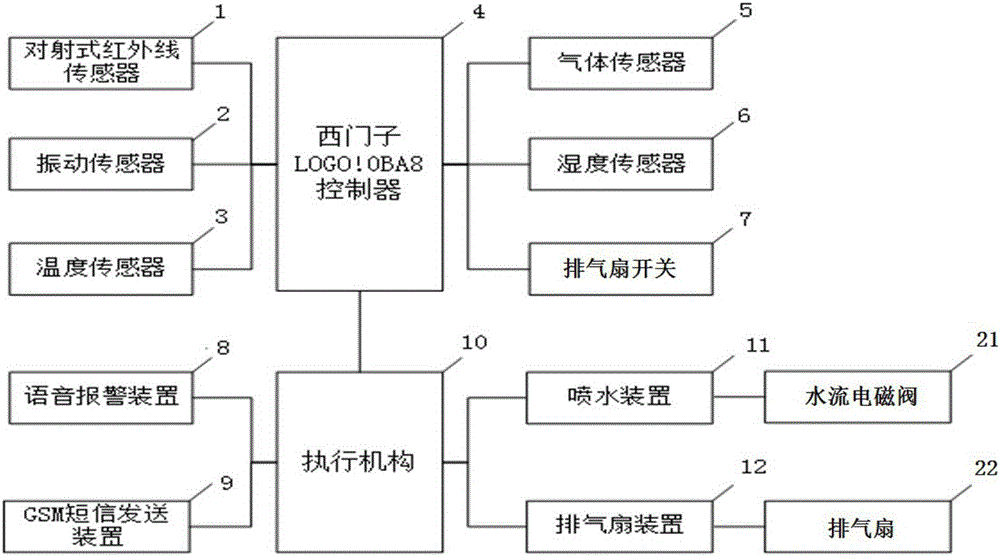
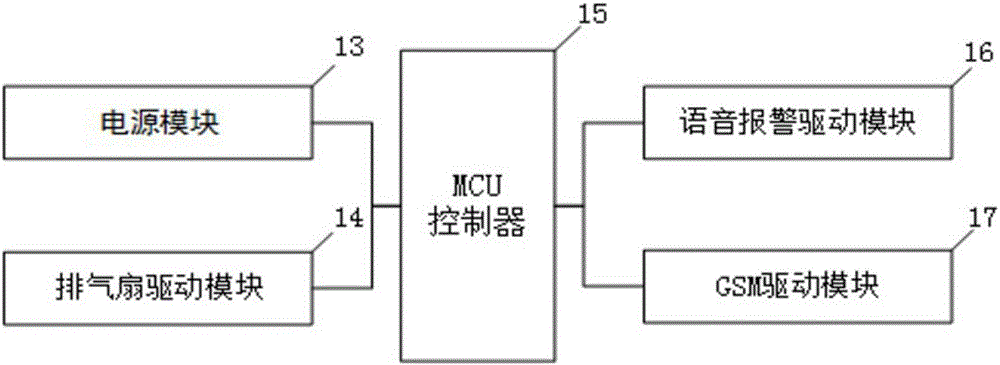
PendingCN106843186AEnsure safetyImprove securityComputer controlProgramme total factory controlControl systemHome security
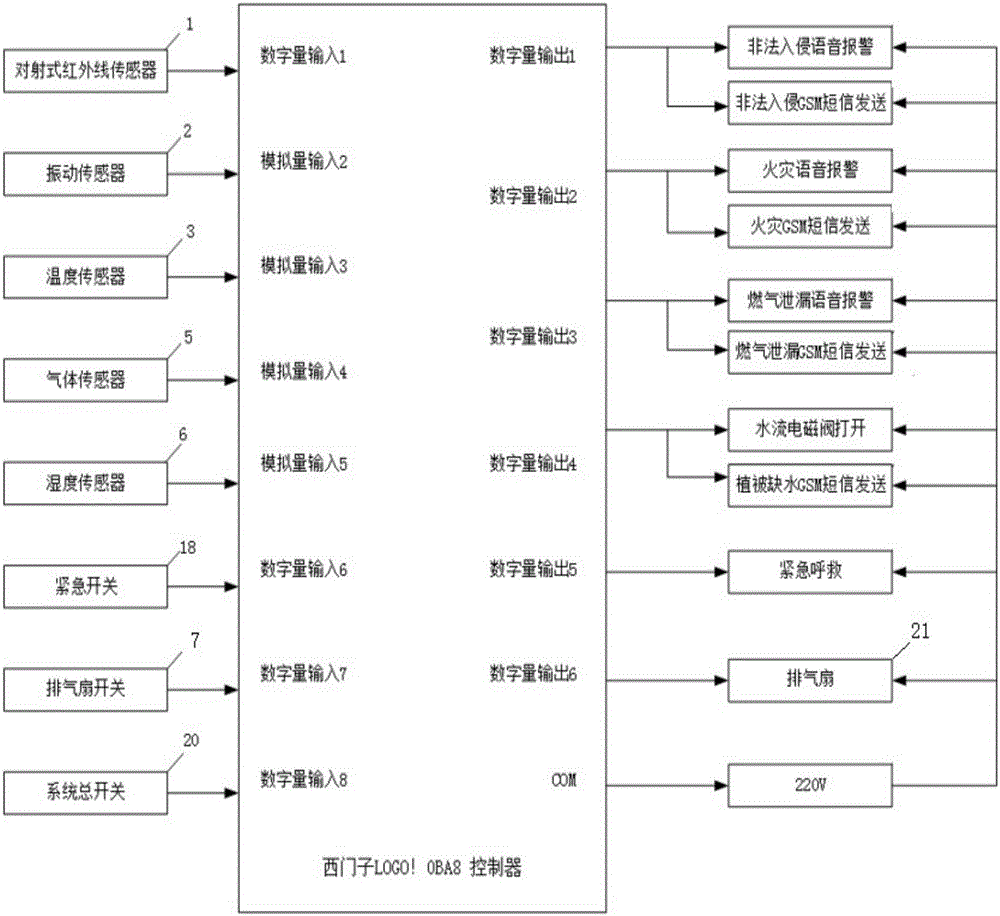
The invention discloses a house safety protection system. The system includes a control system and sensors which are electrically connected with the control system, and the control system is provided with a Siemens LOGO!0BA8 controller; each sensor includes an opposite-type infrared sensor, a vibration sensor, a temperature sensor, a gas sensor and a humidity sensor; the sensors are separately electrically connected with an analog input end of the Siemens LOGO!0BA8 controller; an analog output end of the Siemens LOGO!0BA8 controller is separately connected with and controls a voice alarming device, a GSM message sending device, a water spraying device and an exhaust fan device. According to the house safety protection system, the house safety protection problems such as housebreaking and theft, indoor fires, gas leakage and water shortage of rare vegetation can be effectively solved, the personal safety and property safety of inhabitants are improved, and the living quality of the inhabitants is improved.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
Method for protecting programs in micro-power wireless information acquisition system
ActiveCN103001944APrevent illegal intrusionNo copyingKey distribution for secure communicationNetwork managementMicropower
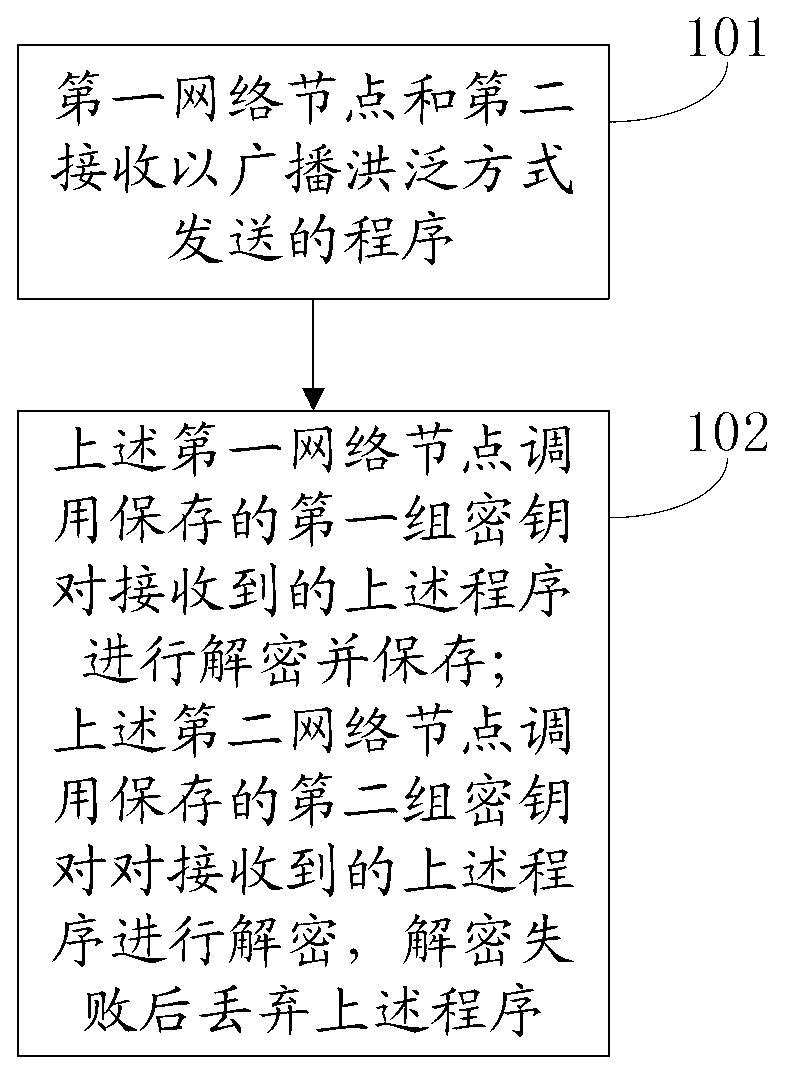
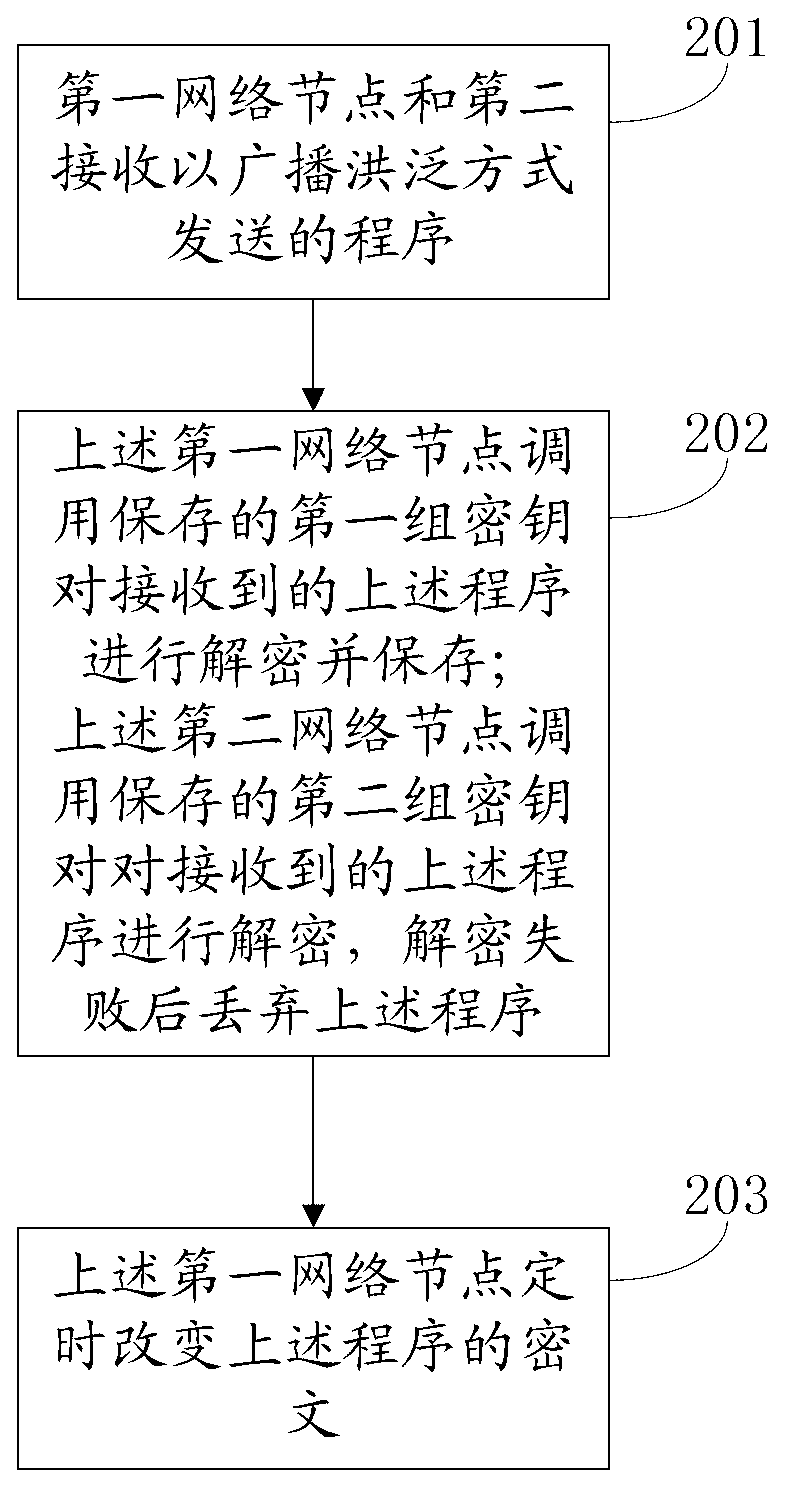
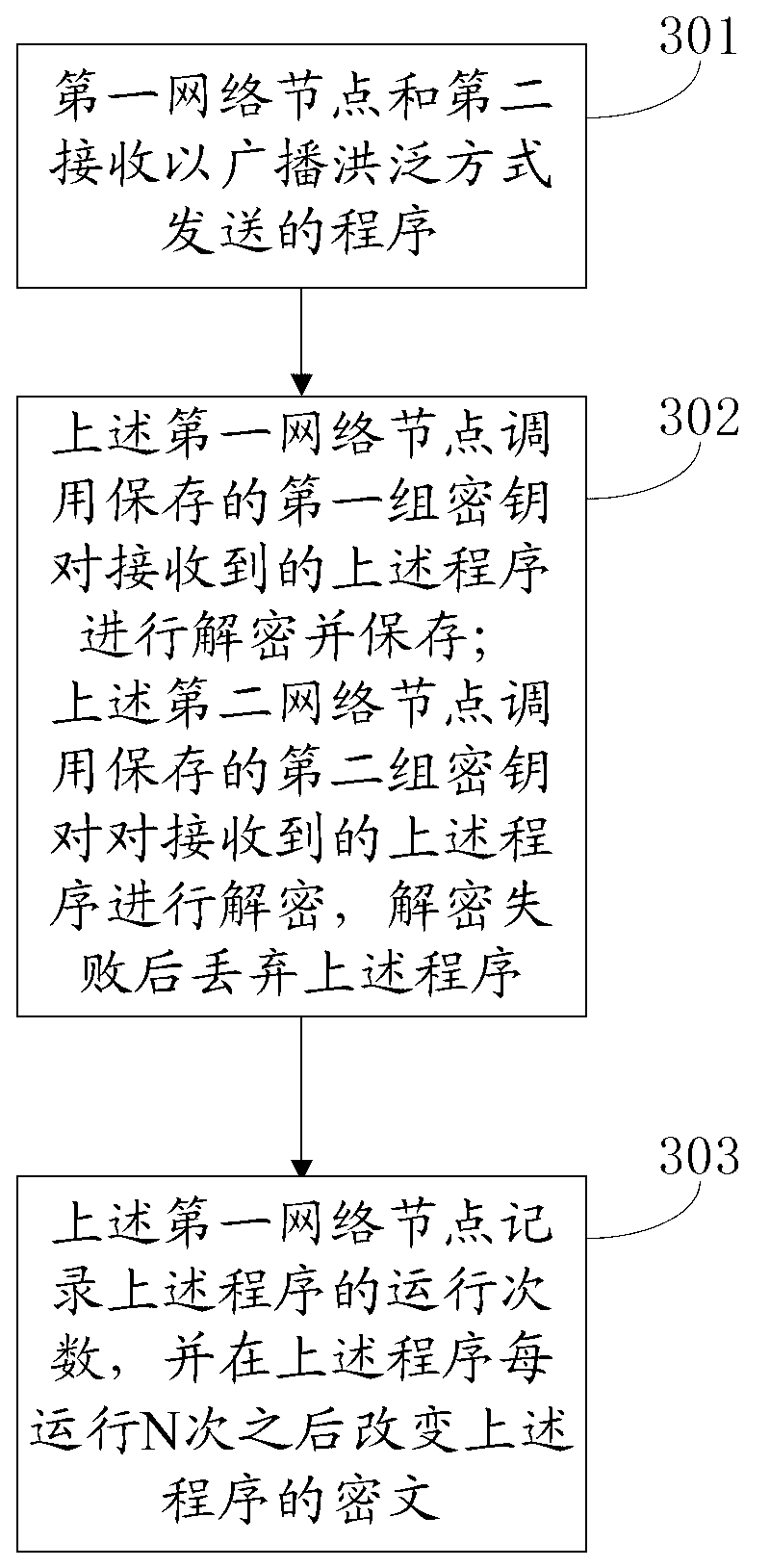
An embodiment of the invention relates to the technical field of communication, and discloses a method for protecting programs in a micro-power wireless information acquisition system. The method includes steps that a first network node and a second network node receive a program transmitted in a broadcast flooding mode; the program is encrypted by a network management center before being transmitted and has first groups of secrete keys, and the first groups of secrete keys are only stored in the first network node and the network management center; the first network node and the second network node are optional two network nodes in the micro-power wireless information acquisition system; the first network node calls the stored first group of secrete keys to decrypt the received program and stores the received program; and the second network node calls a stored second group of secrete keys to decrypt the received program, and the program is discarded if the program fails to be decrypted. The method has the advantages that the programs can be prevented from being illegally copied and maliciously intruded, and safety protection is effectively carried out for the programs.
Owner:SHENZHEN FRIENDCOM TECH DEV
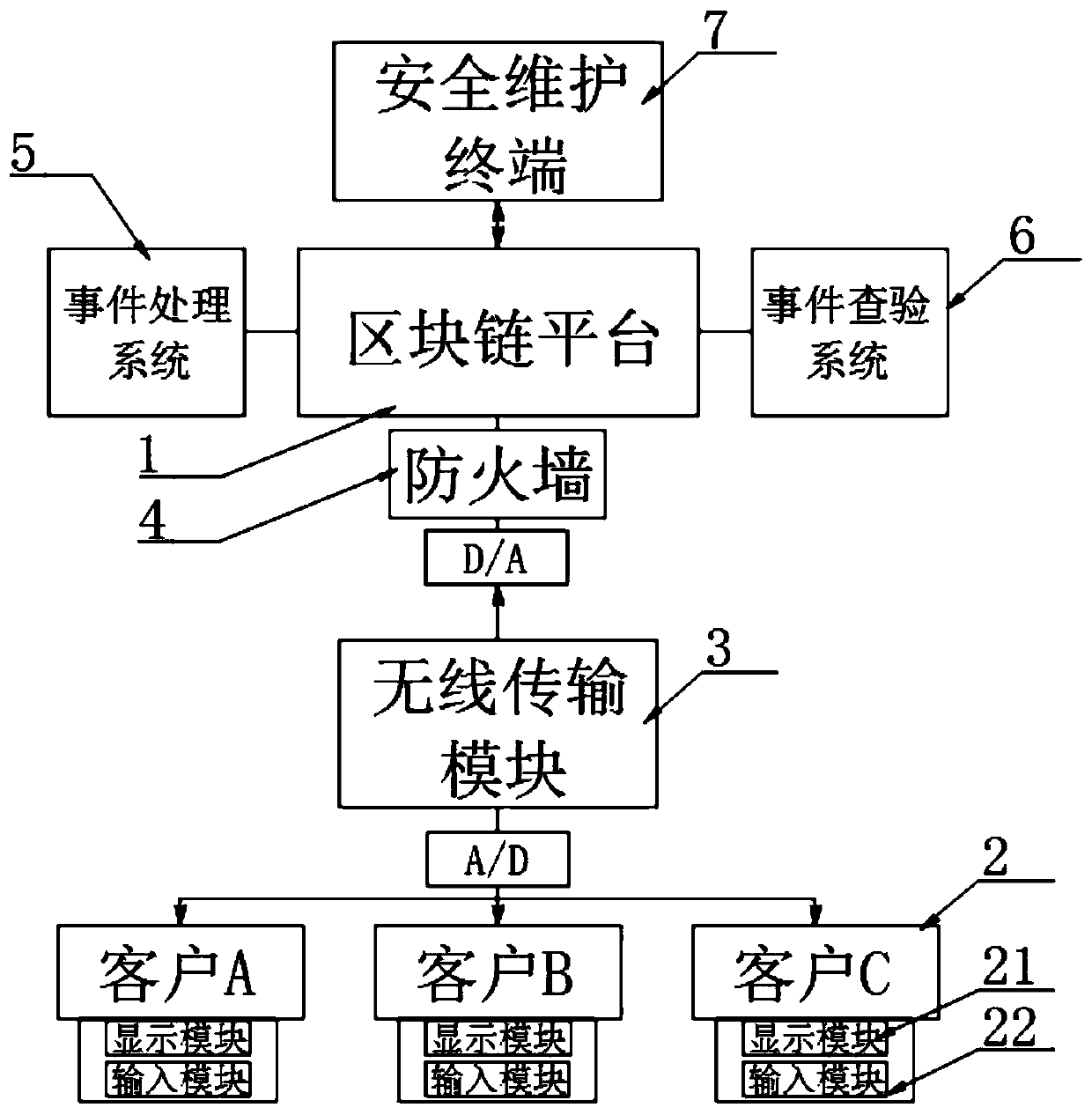
Blockchain data transmission platform convenient for region accuracy
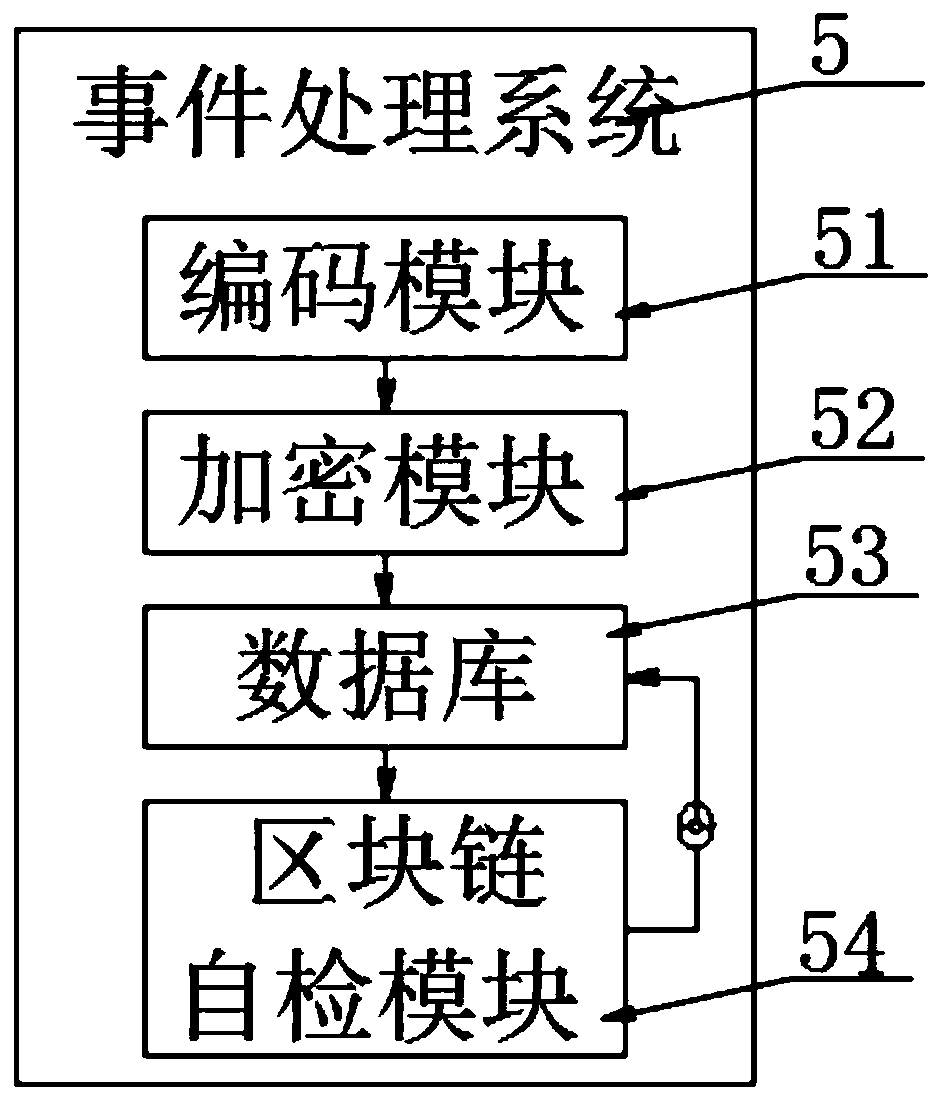
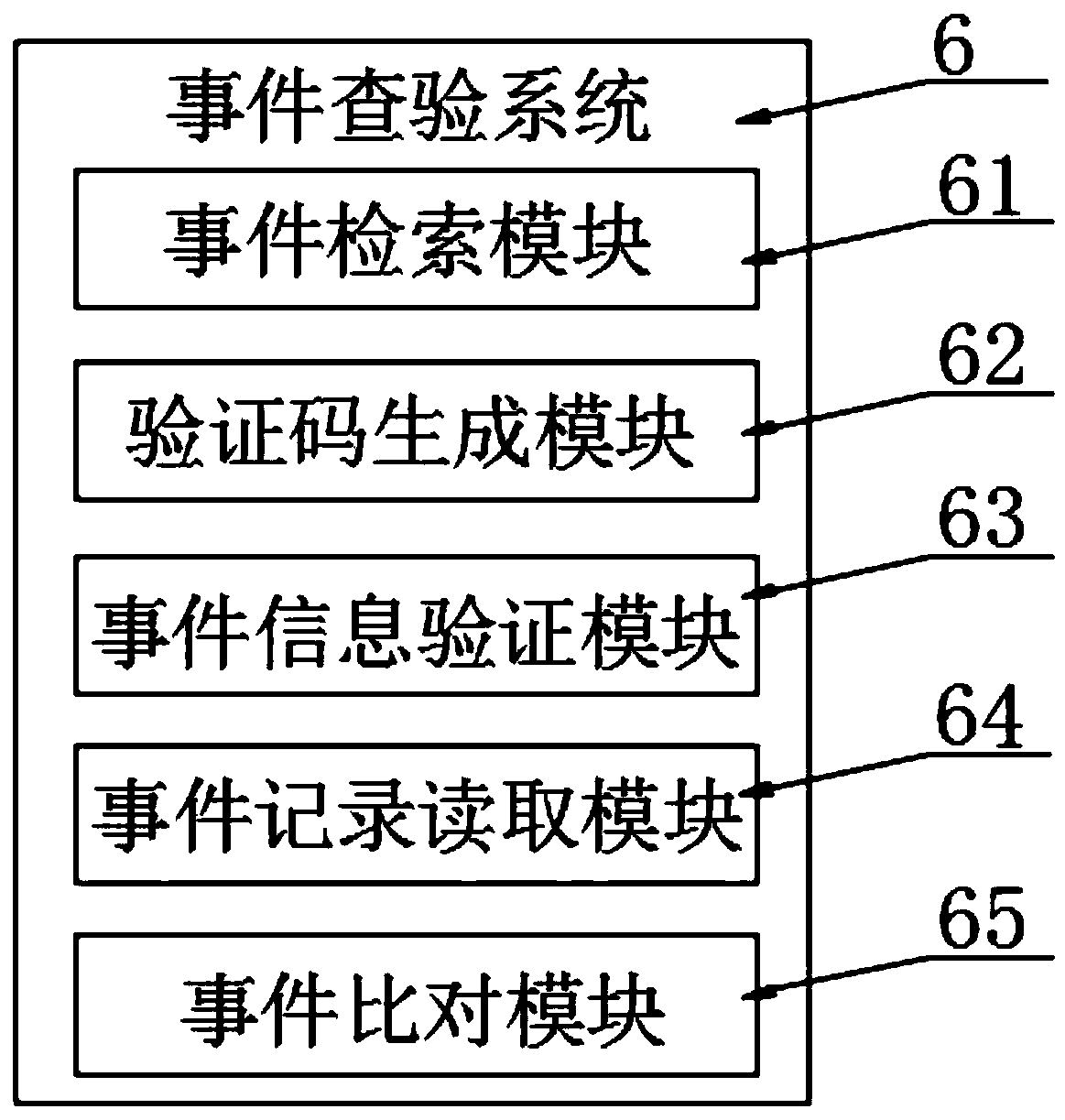
The invention discloses a blockchain data transmission platform convenient for region accuracy, and specifically relates to the technical field of blockchains. The blockchain data transmission platform comprises a block chain platform, the connection end of the block chain platform is provided with a plurality of uniformly distributed clients, the clients are electrically connected with the blockchain platform through a wireless transmission module, the connection end of the block chain platform is provided with a firewall, and the block chain platform is internally provided with an event processing system and an event checking system. According to the invention, the coding module, the encryption module and the block chain self-checking module are matched to organize the events into timelines, and the timelines are encrypted and stored; information processing vulnerabilities can be avoided, and the accuracy of transaction records is improved; the event retrieval module retrieves the reference compressed file according to the input keyword and obtains the event viewing qualification according to the verification code, and the event record reading module extracts the event encryptedfile, decodes and interprets the event encrypted file and sends the event encrypted file to the client, so that quick search of blockchain data is facilitated, and the accuracy of transaction information reference is improved.
Owner:力当高(上海)智能科技有限公司
Three-phase unbalanced governance device with on-site vibration alarm function and realization method thereof
InactiveCN106529806AAvoid dependencePrevent illegal intrusionPolyphase network asymmetry elimination/reductionResourcesPower qualityCharacteristic type
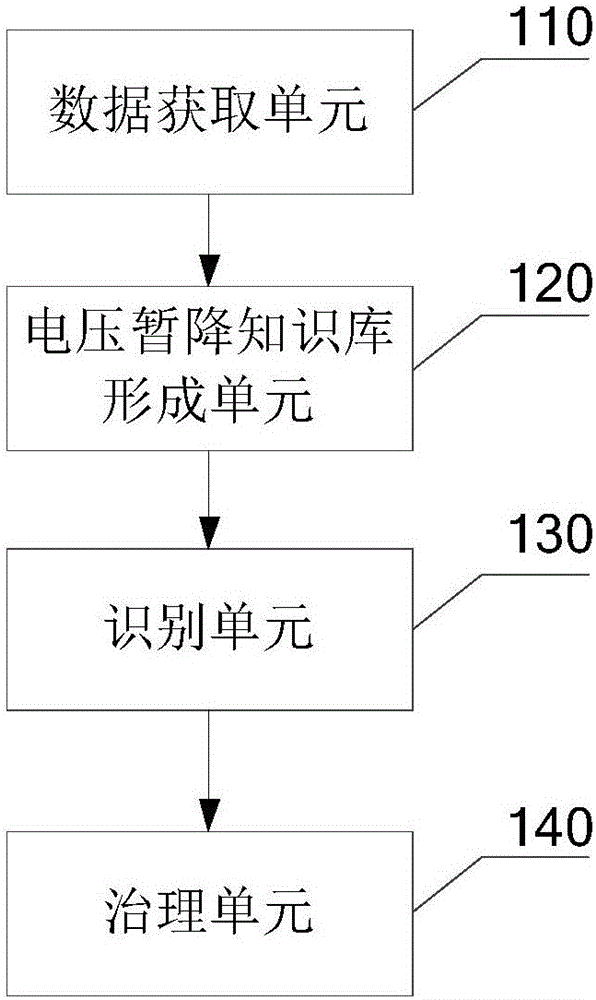
The invention provides a three-phase unbalanced governance device with an on-site vibration alarm function and a realization method thereof. A data acquisition unit is used to acquire the current characteristic data of a power grid. A voltage dip knowledge base forming unit extracts data with the same characteristic type with the characteristic data from historical data, classifies the extracted data to form a sample set according to a preset class attribute, and further screens out data which meet a predetermined condition from the sample set to form a voltage dip strong association rule knowledge base. According to the current characteristic data of the power grid, a recognition unit determines the current voltage dip reason of the power grid in the voltage dip strong association rule knowledge base. A governance unit determines a power grid power quality governance compensation scheme according to the current voltage dip reason, and compensates the user side voltage according to the power grid power quality governance compensation scheme. According to the invention, the dependence on waveform is avoided; and based on the analysis of the historical data, a strong association rule in historical voltage dip is excavated to realize the prediction and governance of the possibility of future voltage dip.
Owner:WENZHOU POLYTECHNIC
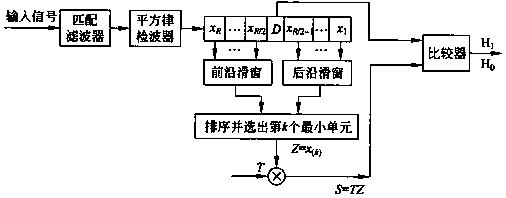
Sliding window principle-based optical fiber segmented hydrophone system
InactiveCN108279443APrevent illegal intrusionImprove accuracyOptical detectionBurglar alarm by disturbance/breaking stretched cords/wiresDigital signal processingErbium doping
The invention discloses a sliding window principle-based optical fiber segmented hydrophone system. The system mainly comprises an optical fiber, a laser, an erbium-doped fiber amplifier (EDFA), an APD, an ADC, a DSP, and an upper computer. The optical fiber is arranged in an underwater protective region. The laser is used for emitting light waves. The erbium-doped fiber amplifier (EDFA) is used for amplifying optical pulses. The APD is used for converting photoelectric signals. The ADC is used for converting electric signals into digital signals. The DSP is used for processing digital signals. The upper computer is used for further processing identification signals and displaying the alarm. Due to the fact that the underwater environment is complex and the detection distance is long, thesegmented detection is carried out on the change of the Ryleigh scattering waveform by adopting the sliding window principle. Therefore, the influence of the complex environment on system detection accuracy is eliminated to the maximum extent. The detection principle of the system is provided and carried out based on the processing of ordered samples in a reference sliding window. The processing flow is as follows: determining the length of an optimal sliding window according to an experiment, sorting samples through a front-edge sliding window and a rear-edge sliding window, figuring out an intermediate value as a reference sliding window value, adopting a difference value between a current point and the reference sliding window value as a vibration value, and determining the invasion type, the invasion position and other information through analyzing the vibration value.
Owner:光子瑞利科技(北京)有限公司
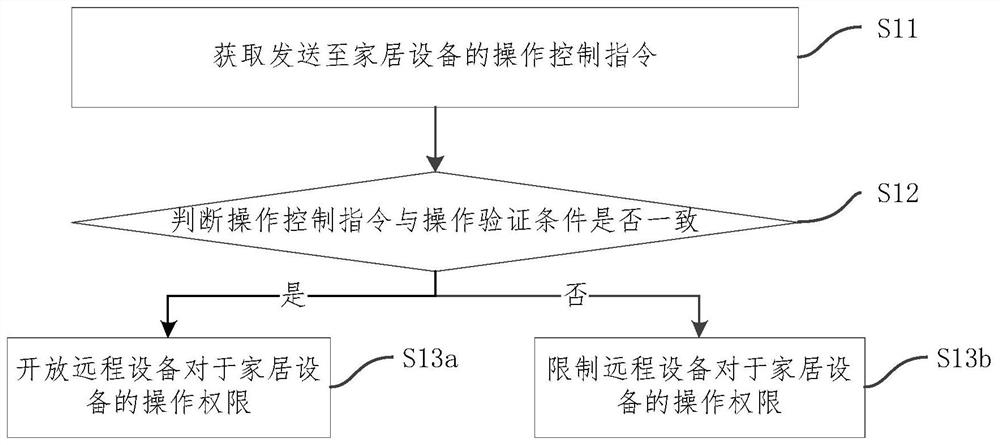
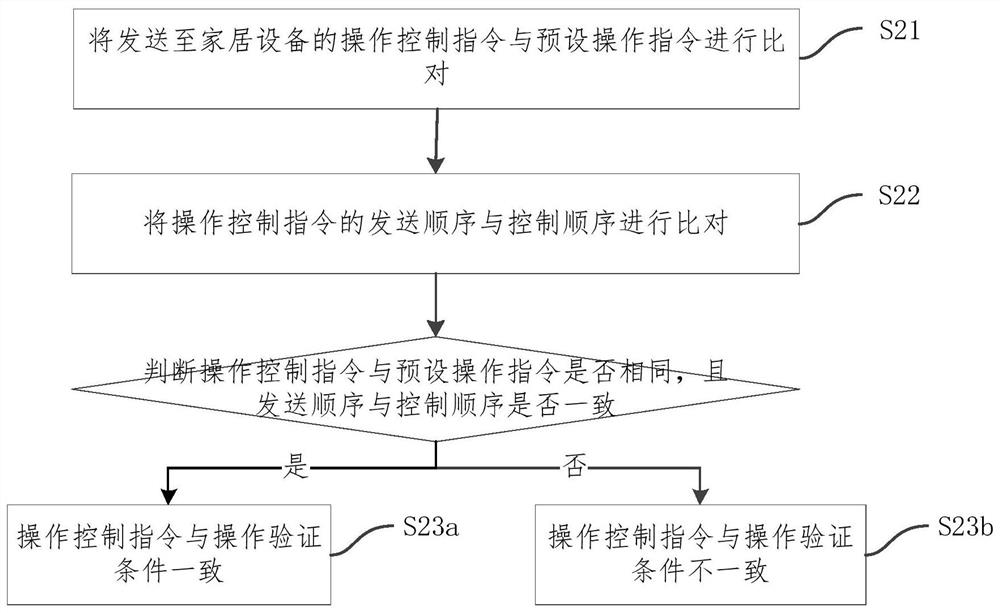
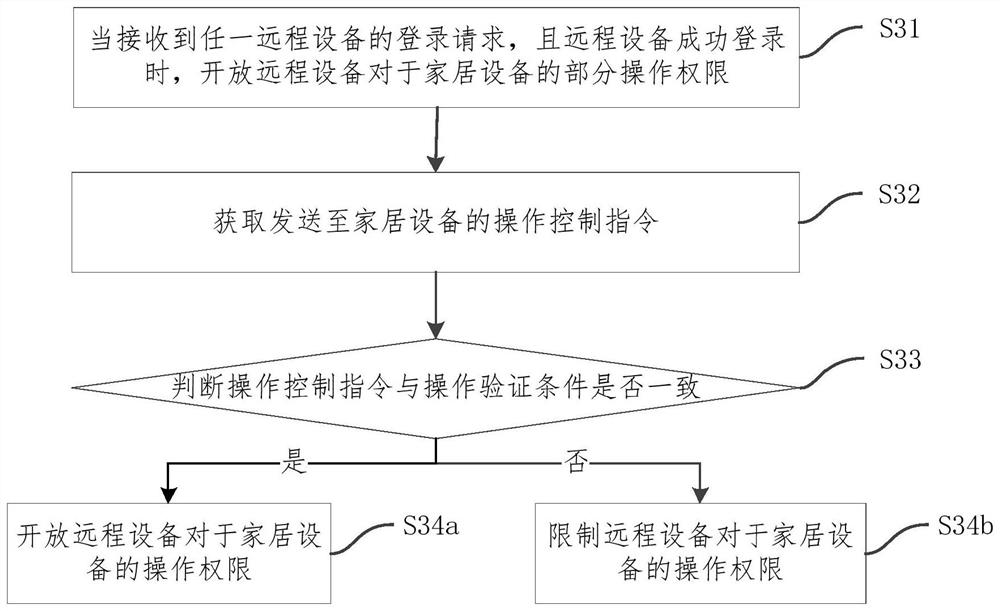
Equipment control authority acquisition method, device and system and storage medium
InactiveCN112600743APrevent illegal intrusionImprove securityData switching by path configurationInstrumentsRemote controlControl engineering
The invention relates to an equipment control authority acquisition method, device and system and a storage medium. The acquisition method comprises the following steps: obtaining an operation controlinstruction sent to household equipment; judging whether the operation control instruction is consistent with the operation verification condition or not; if the operation control instruction is consistent with the operation verification condition, opening the operation authority of the remote equipment to the home equipment; and if the operation control instruction is not consistent with the operation verification condition, limiting the operation authority of the remote equipment to the household equipment. According to the scheme, when the remote device obtains the control right, the operation control instruction sent to the household equipment is obtained, the operation control instruction is compared with the preset operation verification condition, and the operation authority of theremote device to the household equipment is controlled according to the comparison result of the operation control instruction and the preset operation verification condition. The remote control authority of the household equipment is obtained by operating on the household equipment, so that the household equipment is prevented from being illegally invaded, and the safety of the smart home is improved.
Owner:GREE ELECTRIC APPLIANCES INC +1
IPTV template file tamper-proofing method and system
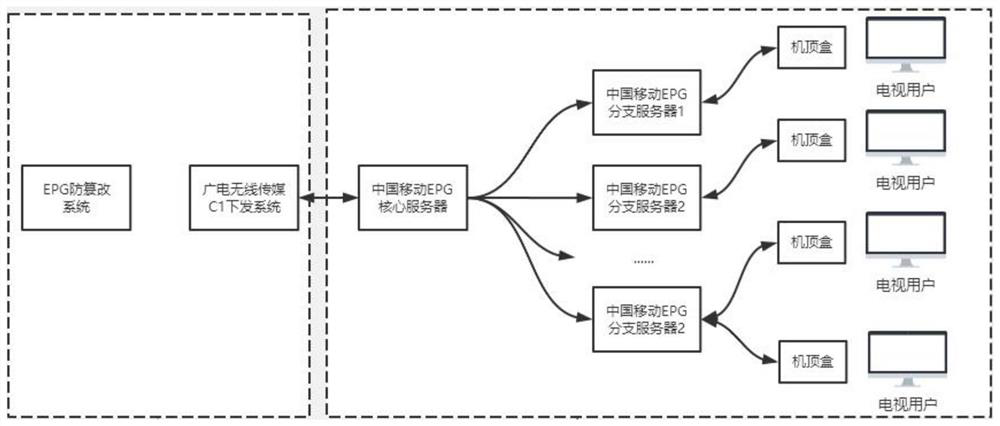
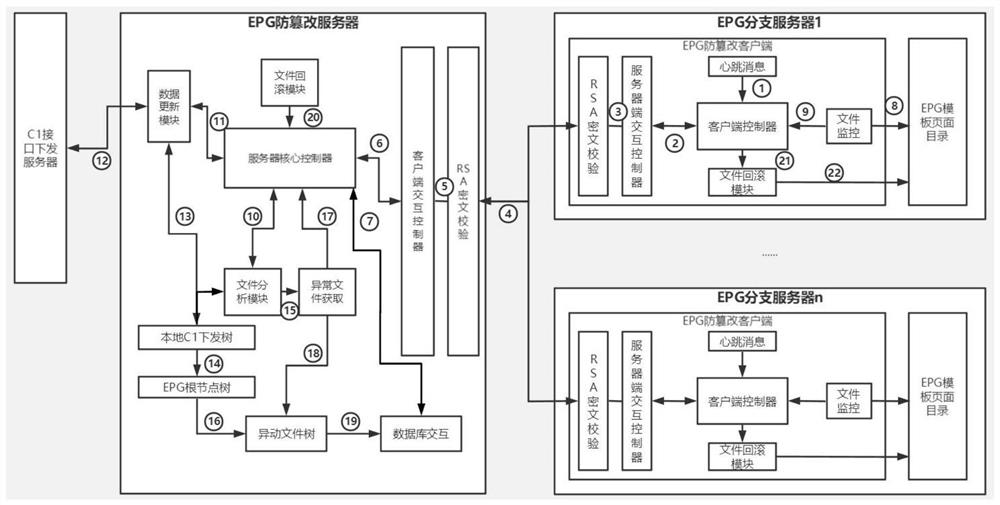
ActiveCN112135165AQuick rollback operationPrevent illegal intrusionSelective content distributionTamper resistanceSystems management
The invention relates to an IPTV template file tamper-proof method and system, and the system comprises an EPG tamper-proof server and an EPG tamper-proof client, wherein the EPG tamper-proof server is configured at a system management end, and the EPG tamper-proof client is configured at an EPG branch server. According to the invention, a verified system issuing file is forwarded to the EPG branch server through the EPG tamper-proof server; the EPG tamper-proof client monitors the change of the template file in the EPG branch server in real time and returns the change file, and the EPG tamper-proof server performs secondary verification, so the continuous tracking of the issued file is realized, and illegal tampering of the playing content of the television terminal is prevented.
Owner:河北广电无线传媒股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com