Method for protecting programs in micro-power wireless information acquisition system
A micro-power wireless, information collection technology, applied in transmission systems and key distribution, can solve problems such as security risks and program leakage, and achieve the effect of preventing illegal intrusion and copying
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
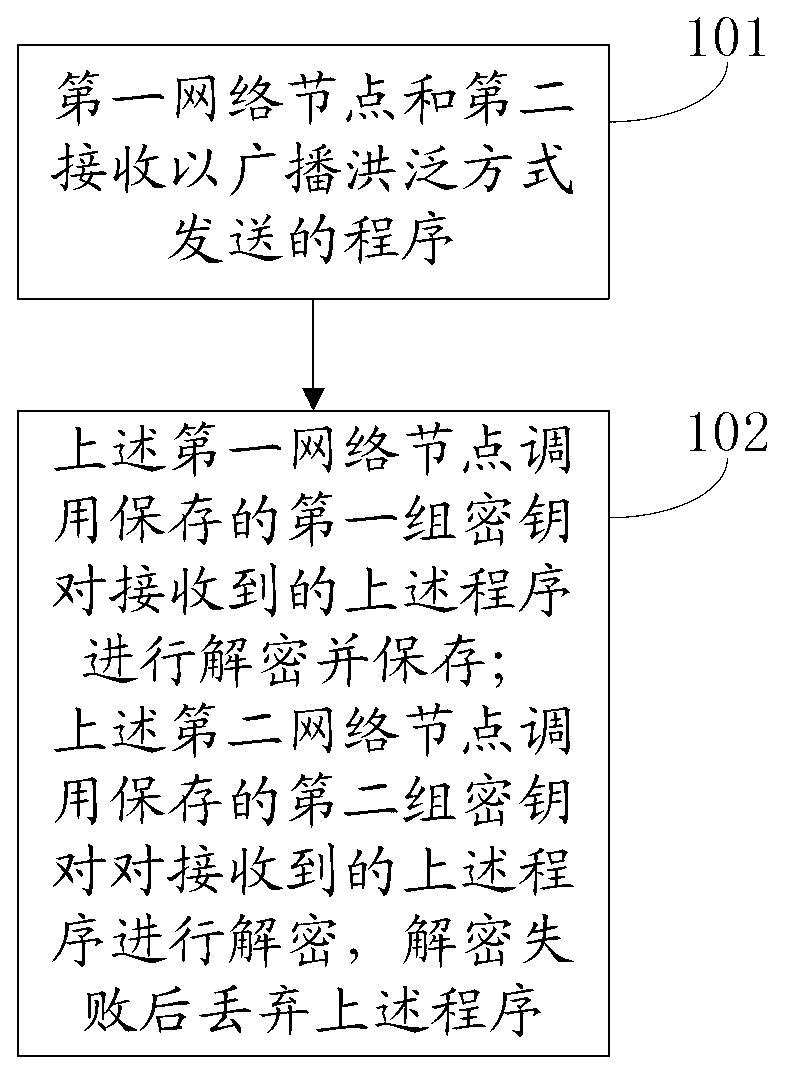
[0018] The invention provides a program protection method in a micro-power wireless information collection system, such as figure 1 shown, including the following steps:
[0019] 101. The first network node and the second network node receive the program sent in a broadcast flooding manner;
[0020] The first network node and the second network node are any two nodes in the micro-power wireless information collection system except the network management center;
[0021] The above-mentioned program is sent by the network management center in the form of broadcast flooding, and is encrypted by the above-mentioned network management center before sending. The key of the above-mentioned program is the first group of keys, and the above-mentioned first group of keys is only stored in the first network node and the network management center middle;
[0022] Further, the above-mentioned first group of keys includes at least two keys, and each group of the above-mentioned program ad...
Embodiment 2
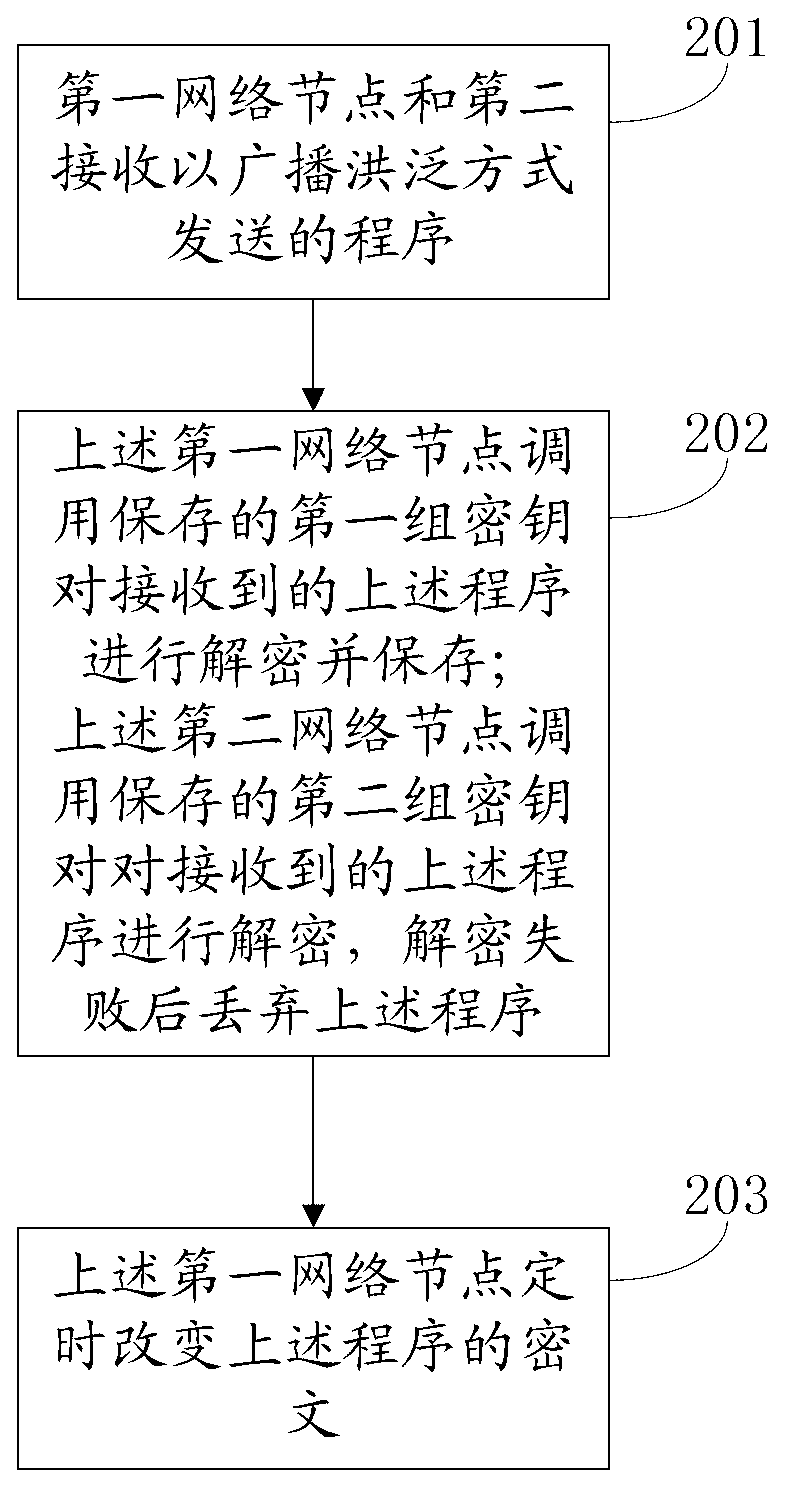
[0026] The invention provides a program protection method in a micro-power wireless information collection system, such as figure 2 shown, including the following steps:
[0027] 201. The first network node and the second network node receive a program sent in a broadcast flooding manner;
[0028] The first network node and the second network node are any two nodes in the micro-power wireless information collection system except the network management center;
[0029] The above-mentioned program is sent by the network management center in the form of broadcast flooding, and is encrypted by the above-mentioned network management center before sending. The key of the above-mentioned program is the first group of keys, and the above-mentioned first group of keys is only stored in the first network node and the network management center middle;
[0030] Further, the above-mentioned first group of keys includes at least two keys, and each group of the above-mentioned program ado...
Embodiment 3
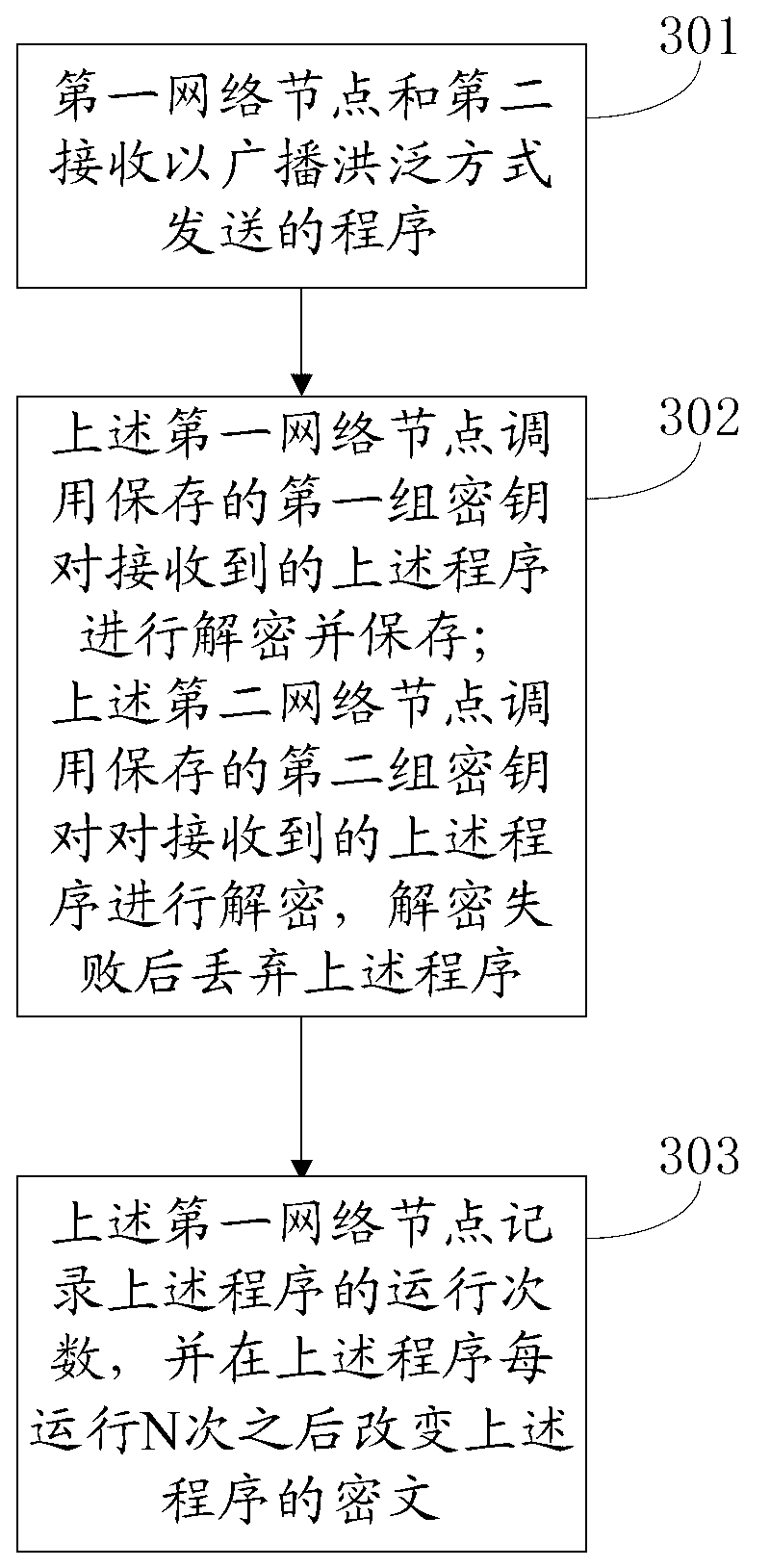
[0037] The invention provides a program protection method in a micro-power wireless information collection system, such as image 3 shown, including the following steps:
[0038] 301. The first network node and the second network node receive a program sent in a broadcast flooding manner;
[0039] The first network node and the second network node are any two nodes in the micro-power wireless information collection system except the network management center;
[0040] The above-mentioned program is sent by the network management center in the form of broadcast flooding, and is encrypted by the above-mentioned network management center before sending. The key of the above-mentioned program is the first group of keys, and the above-mentioned first group of keys is only stored in the first network node and the network management center middle;
[0041] Further, the above-mentioned first group of keys includes at least two keys, and each group of the above-mentioned program adop...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com