Information processing method and terminal thereof
An information processing method and terminal technology, applied in the field of information processing, can solve problems such as user security risks, password leakage, privacy leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
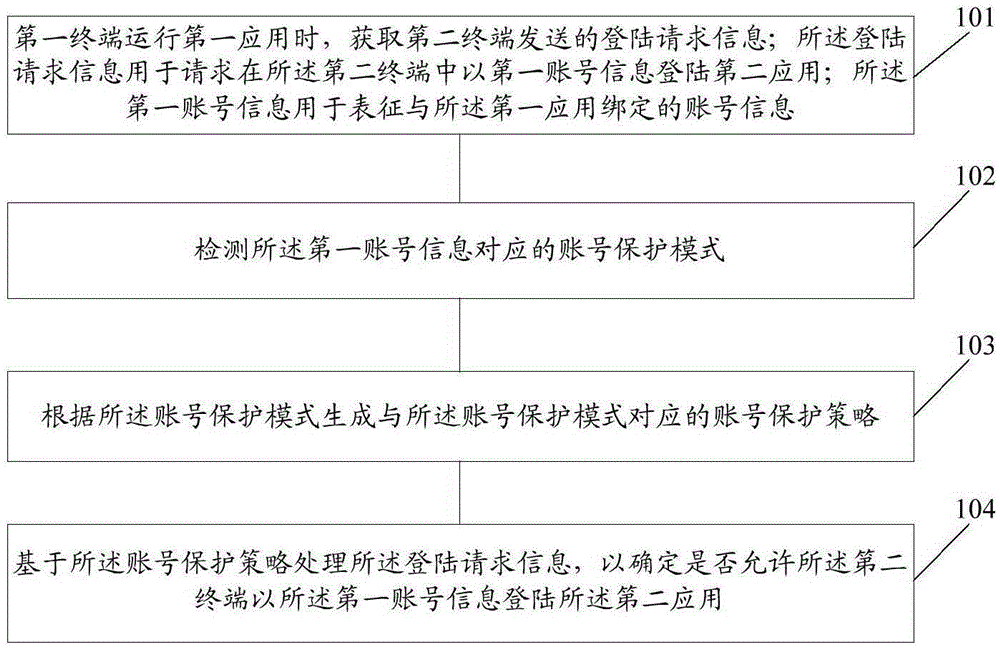
[0102] figure 1 It is a schematic diagram of the implementation flow of the information processing method of the embodiment of the present invention Figure 1 ; The method is applied to the first terminal, such as figure 1 As shown, the method includes:
[0103] Step 101: When the first terminal runs the first application, obtain the login request information sent by the second terminal; the login request information is used to request to log in the second application with the first account information in the second terminal; The account information is used to represent the account information bound to the first application;
[0104] In this embodiment, the first application may specifically be a software application that can provide security protection for account information; in a specific embodiment, the first account information is a user logging into a second application, such as a user logging into a social software name and password; the user can successfully log in ...
Embodiment 2
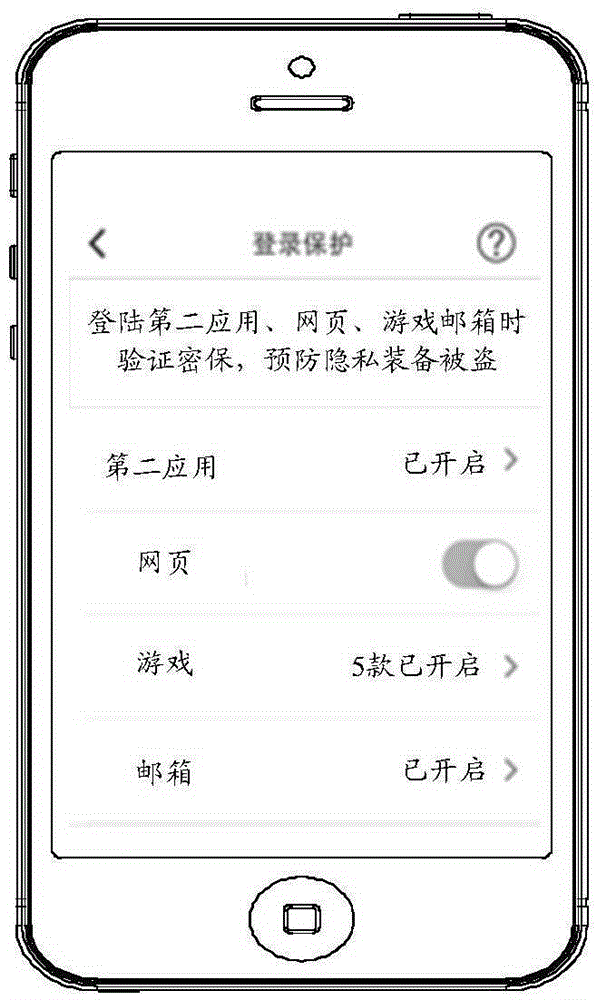
[0115] Based on the information processing method described in Method Embodiment 1, in this embodiment, the first application is provided with a verification list, and the verification list stores identification information corresponding to terminals that have undergone identity verification and passed the verification; Specifically, when the first terminal performs identity verification and passes the verification, the verification list stores the identification information corresponding to the first terminal. In this way, when the first terminal uses the first account information again When logging in to the second application, you can successfully log in to the second application without identity verification; that is, as long as the first account information can successfully log in to the second application in any other terminal, the The first application can obtain the terminal device information of the terminal that successfully logs in to the second application using the...
Embodiment 3
[0144] Figure 7 It is a schematic diagram of the implementation flow of the information processing method of the embodiment of the present invention Figure II The method is applied to the first terminal; in this embodiment, the account protection mode described in the first method embodiment includes: account lock mode and account unlock mode; Figure 7 As shown, the method includes:
[0145] Step 701: When the first terminal runs the first application, obtain the login request information sent by the second terminal; the login request information is used to request to log in the second application with the first account information in the second terminal; The account information is used to represent the account information bound to the first application;
[0146] Step 702: Detect the account protection mode corresponding to the first account information;
[0147] Step 703: When it is detected that the first account information corresponds to the account lock mode, genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com