Patents
Literature
573 results about "Protected mode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
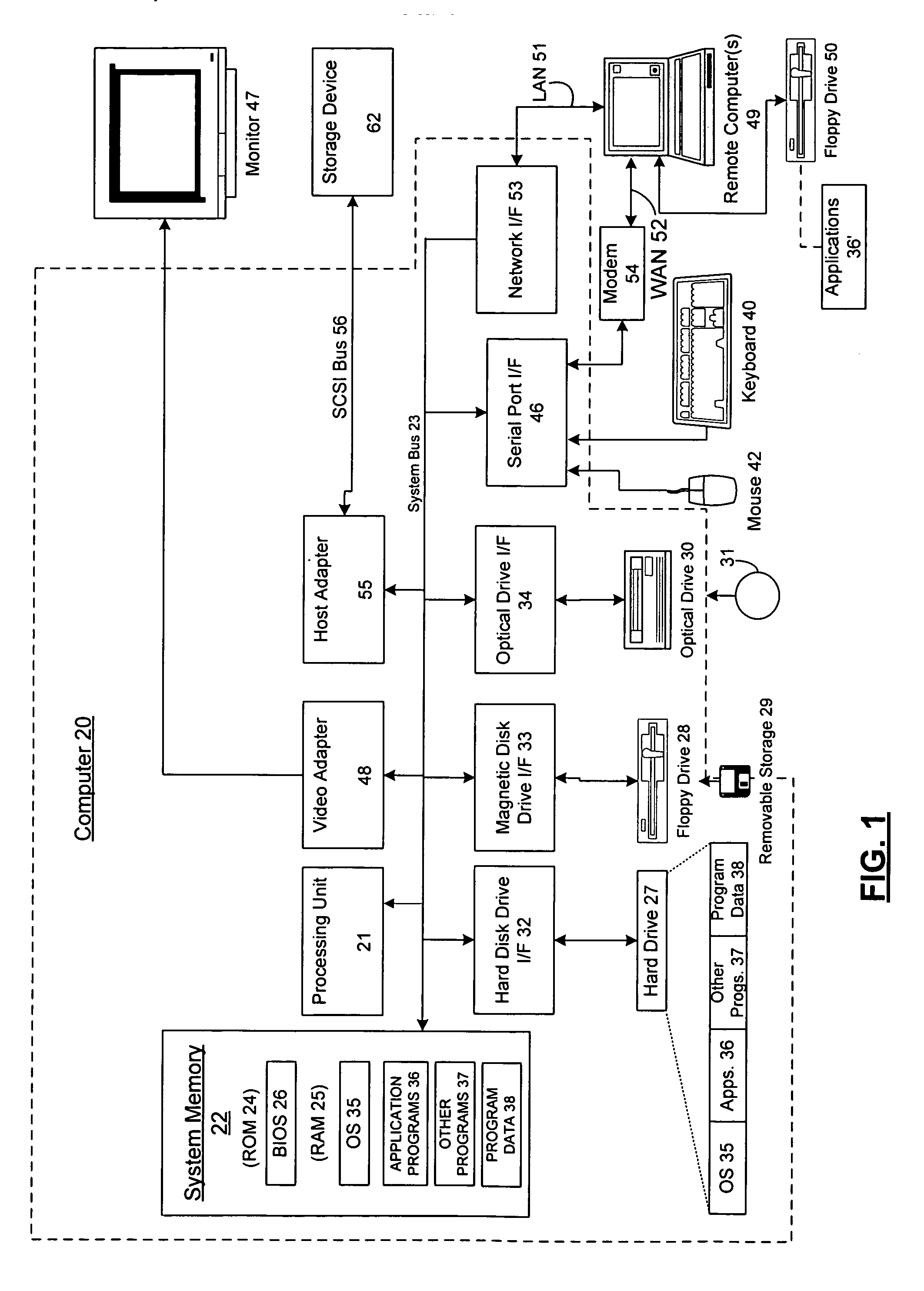
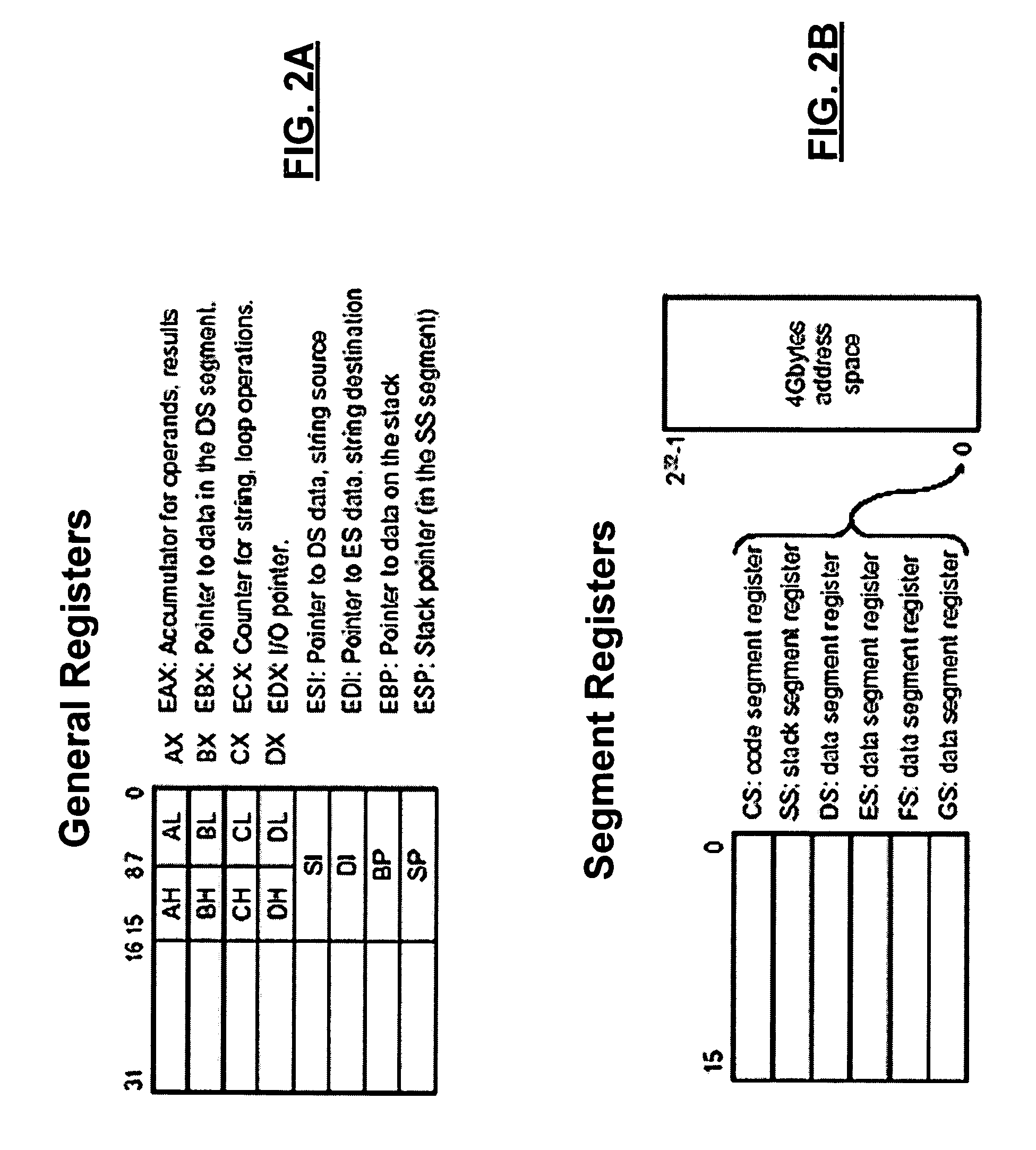
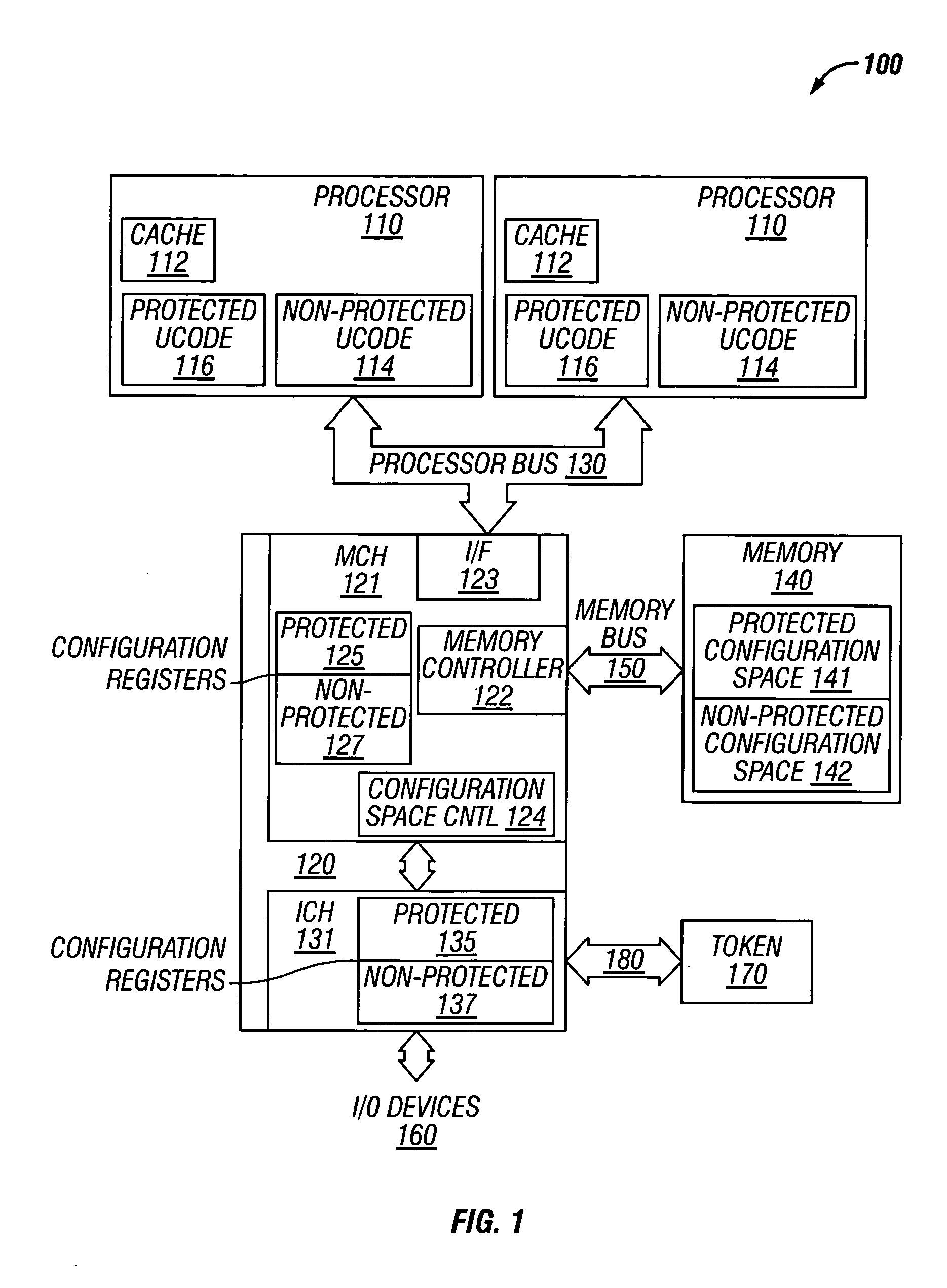
In computing, protected mode, also called protected virtual address mode, is an operational mode of x86-compatible central processing units (CPUs). It allows system software to use features such as virtual memory, paging and safe multi-tasking designed to increase an operating system's control over application software.
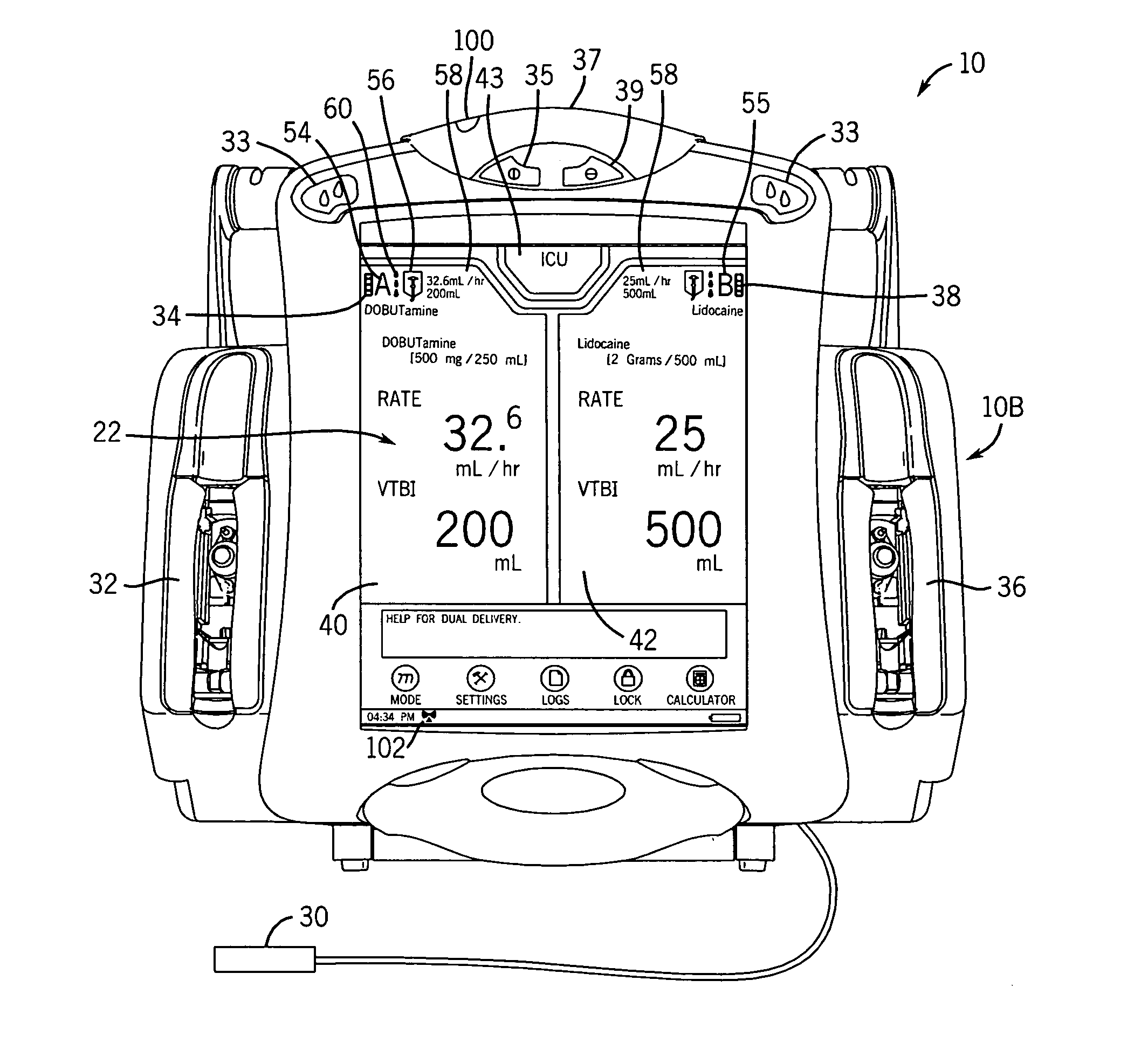
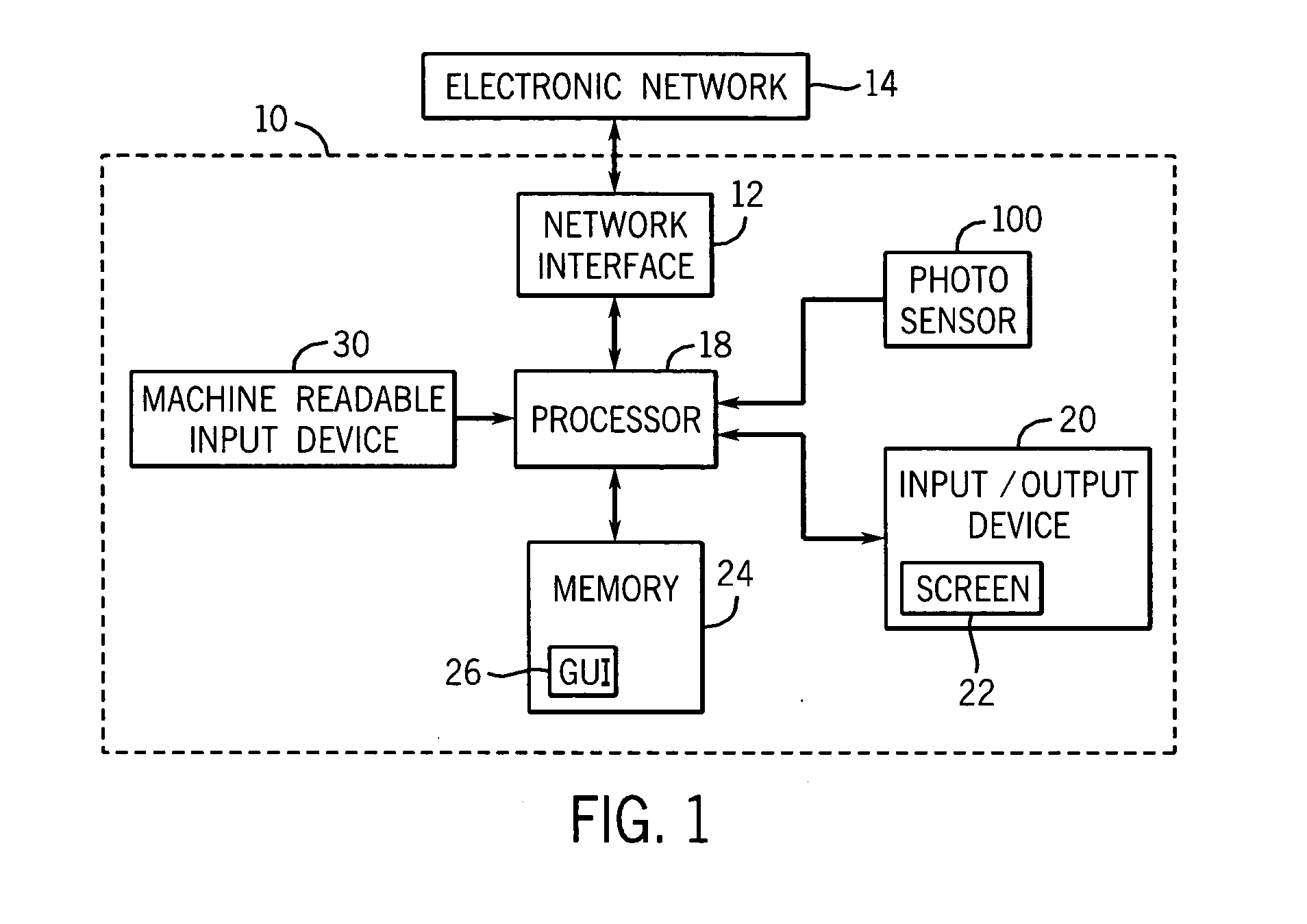
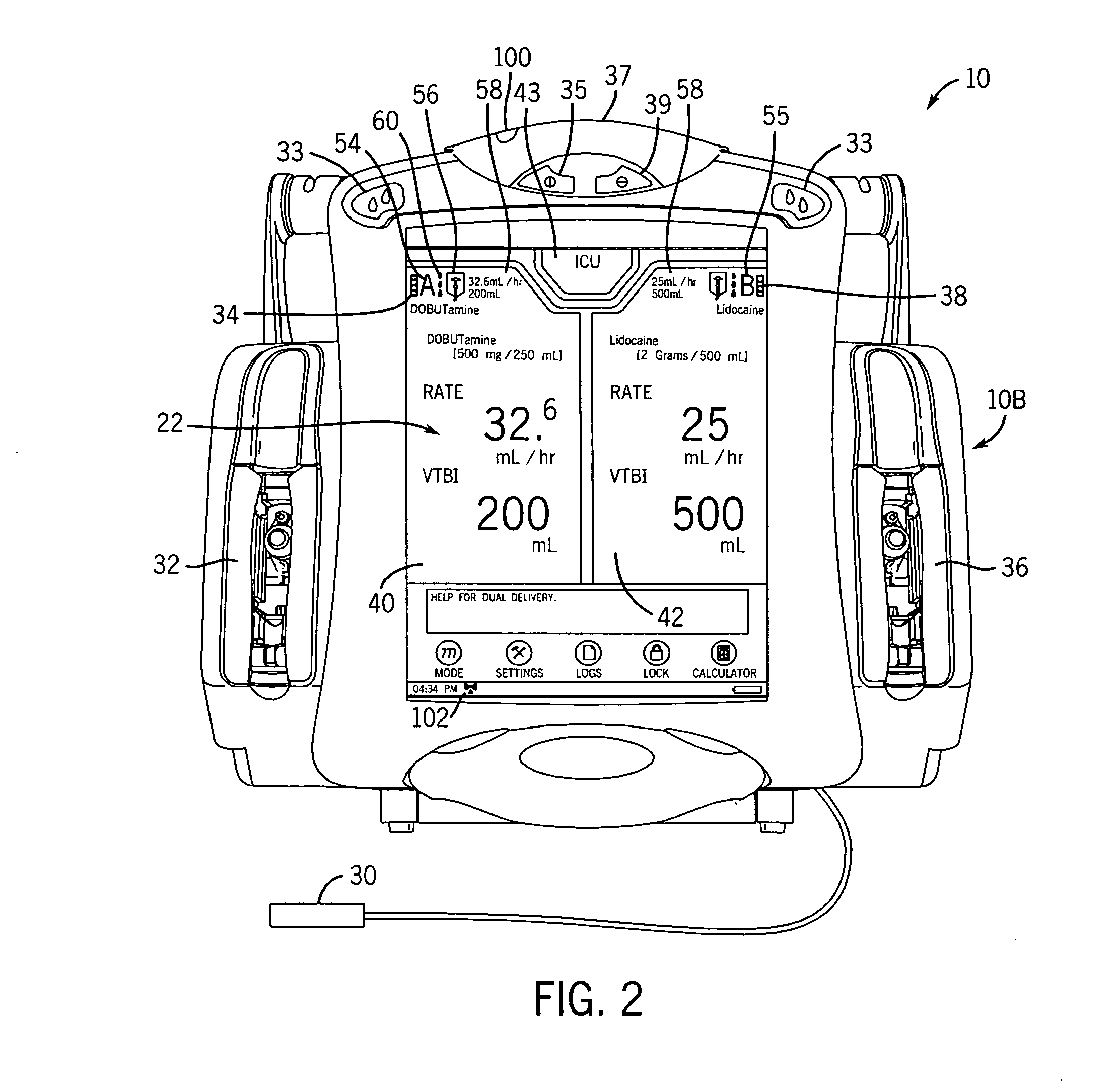
User interface improvements for medical devices
ActiveUS20060229557A1Smooth and quick and efficient maneuveringData processing applicationsLocal control/monitoringOperant conditioningUser interface
A method and apparatus is disclosed for operating a medical device with a screen having an improved graphical user interface, which selectively reallocates screen display for both single and multi-channel pumps. Channel indicators associate operation information with a specific delivery channel. Patient or drug order verification is facilitated with a rendering of the patient or the entire drug order / label on the screen. Decimal numbers are presented in vertically offset decimal format. A dual function button cancels the current operation and, after a delay, clears entered parameters. An area sensitive scrollbar cycles through information at various speeds. Screen brightness is adjusted based on an ambient light detector. A screen saver mode activates based on several operating conditions. The screen is incorporated in a removable user interface.
Owner:ICU MEDICAL INC
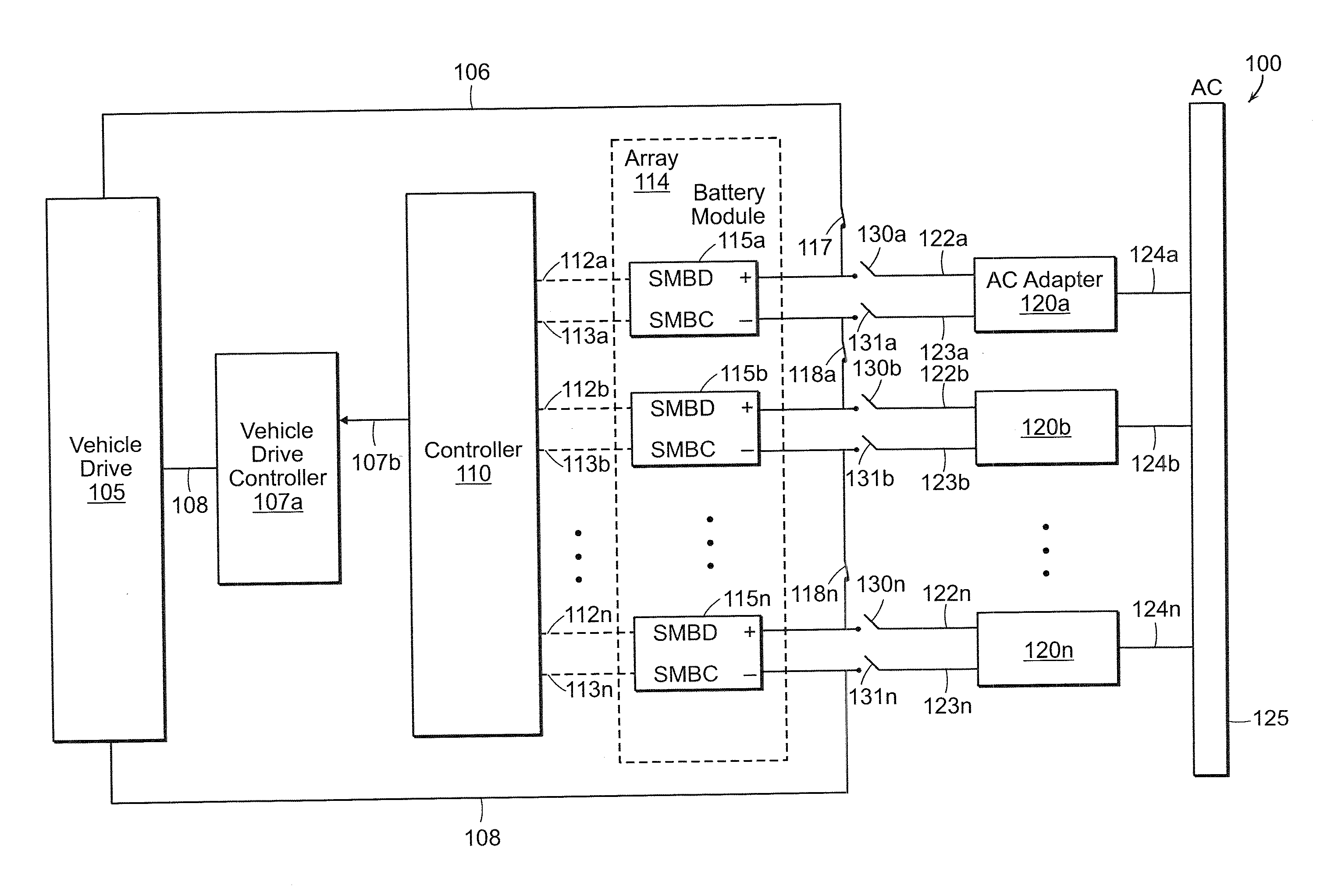
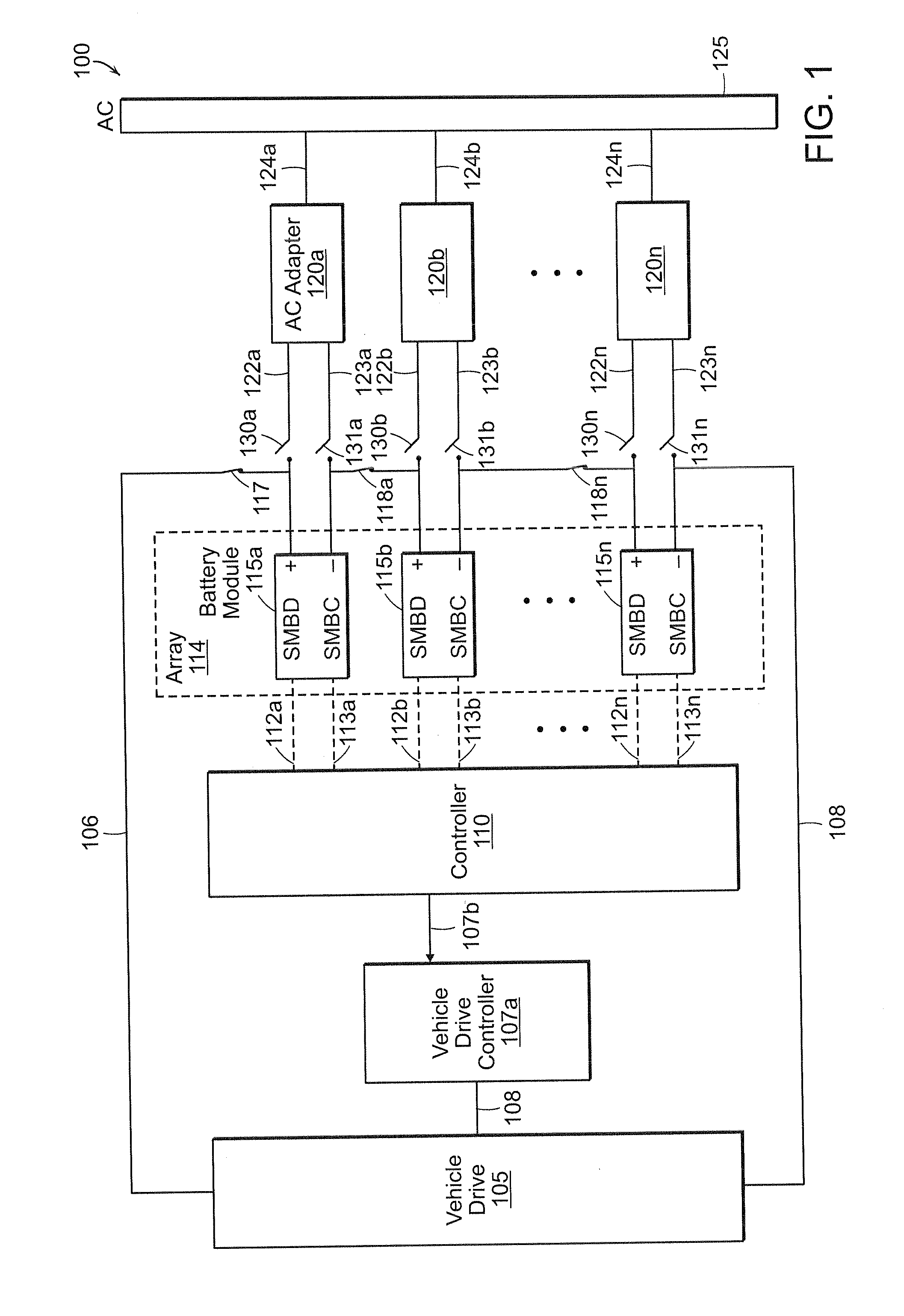
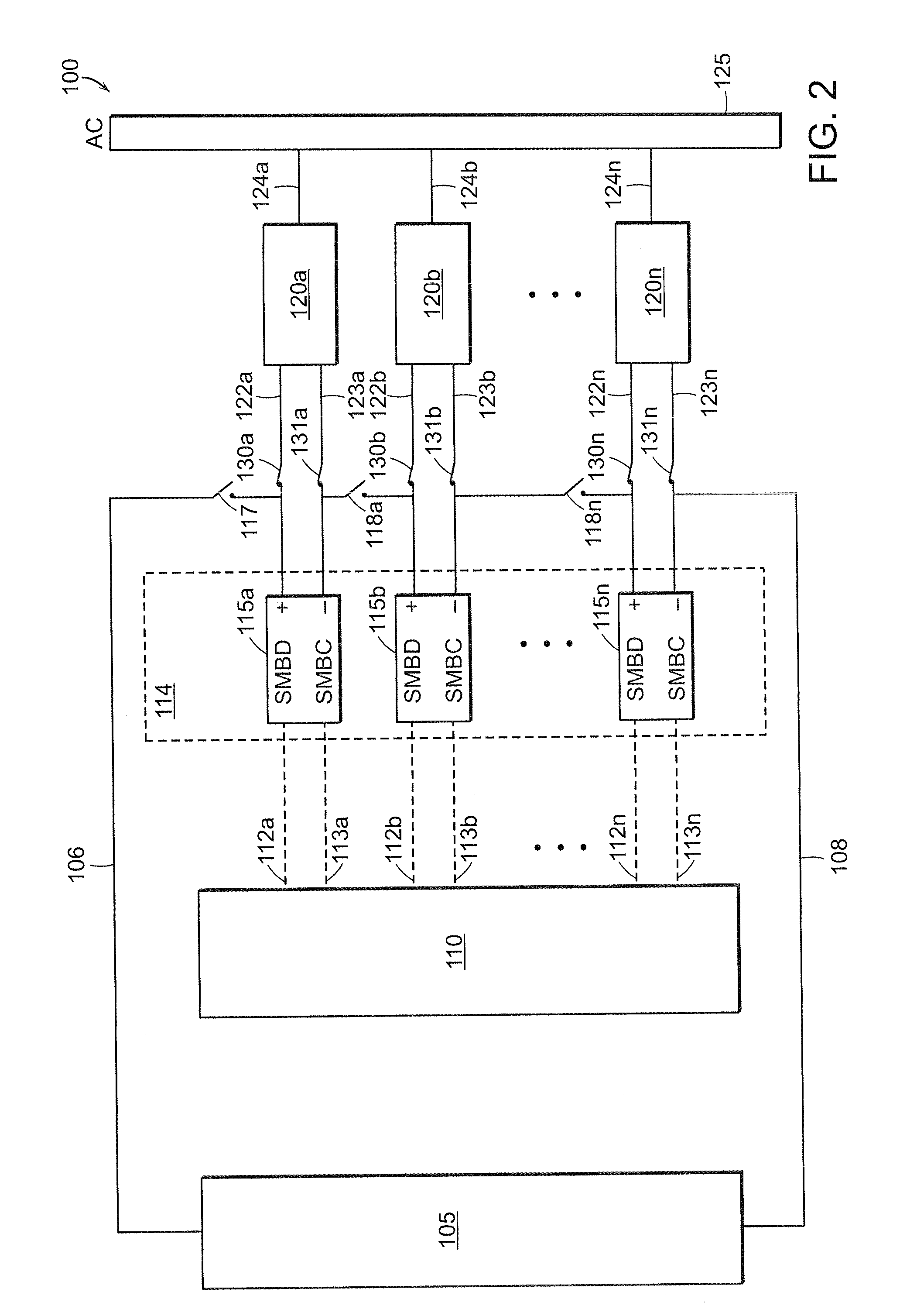
Li-ion battery array for vehicle and other large capacity applications
InactiveUS20100121511A1Improve reliabilityMinimize timeCharge equalisation circuitDigital data processing detailsElectrical batteryComputer module
A large battery array, particularly for use in an electric vehicle, is formed of multiple modules, each containing plural battery cells and module management electronics. Each battery module has a nominal output voltage in the range of about 5 volts to about 17 volts. A controller communicates with individual battery modules in the array and controls switching to connect the modules in drive and charging configurations. The module management electronics monitor conditions of each battery module, including the cells it contains, and communicates these conditions to the controller. The module management electronics may place the modules in protective modes based upon the performance of each module in comparison to known or configurable specifications. The modules may be pluggable devices so that each module may be replaced if the module is in a permanent shutdown protective mode or if a non-optimal serviceable fault is detected.
Owner:BOSTON POWER INC
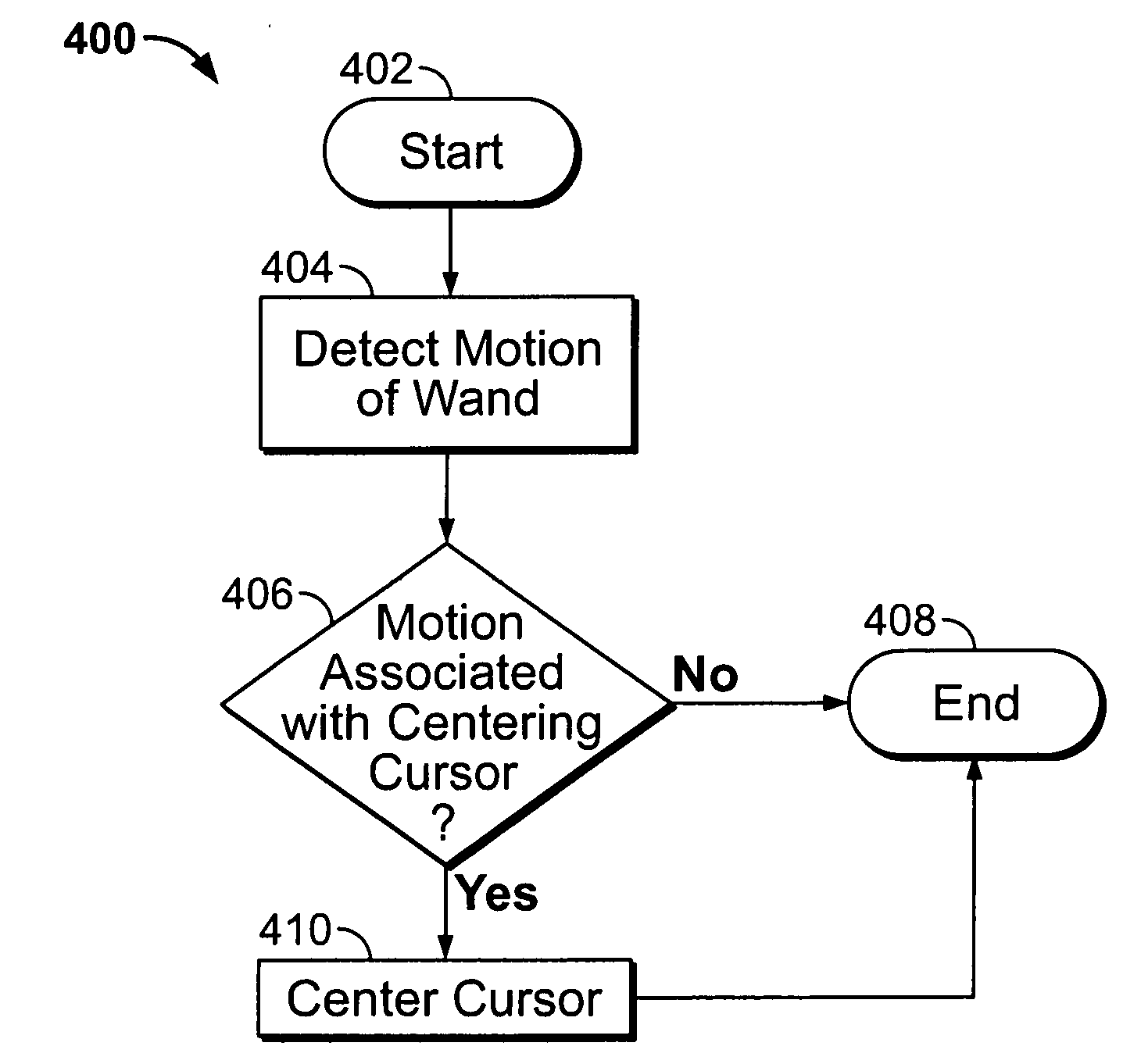
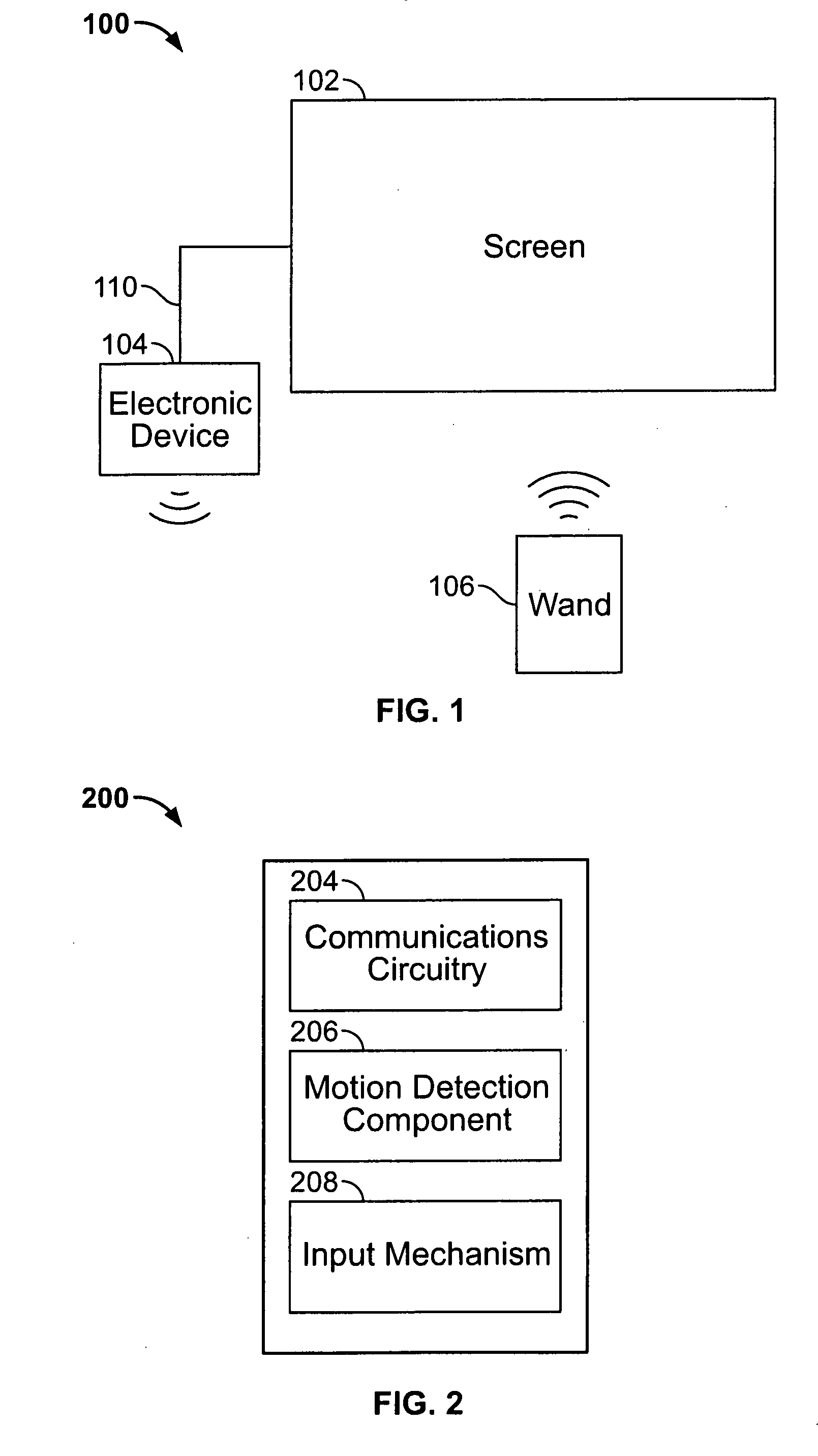
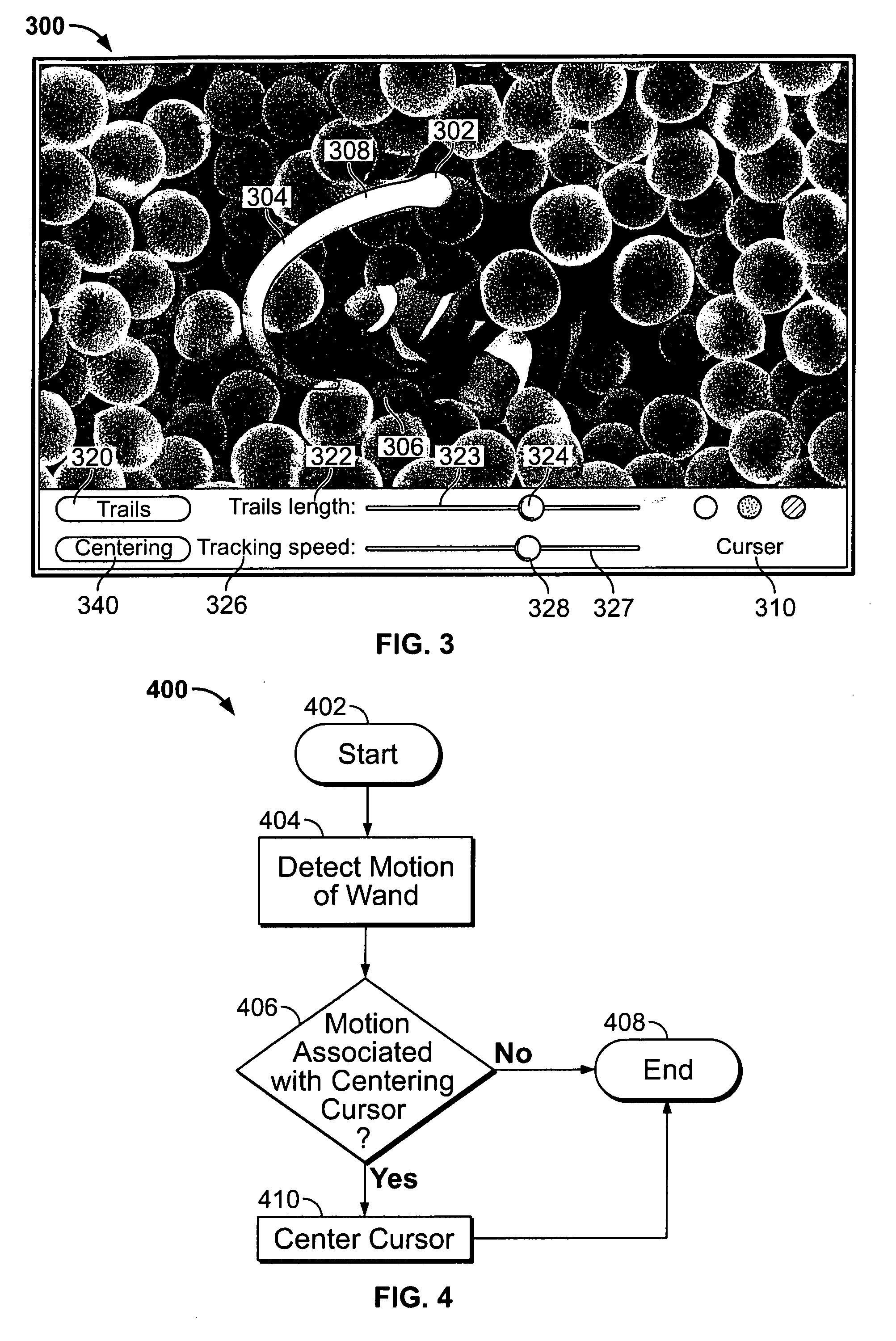
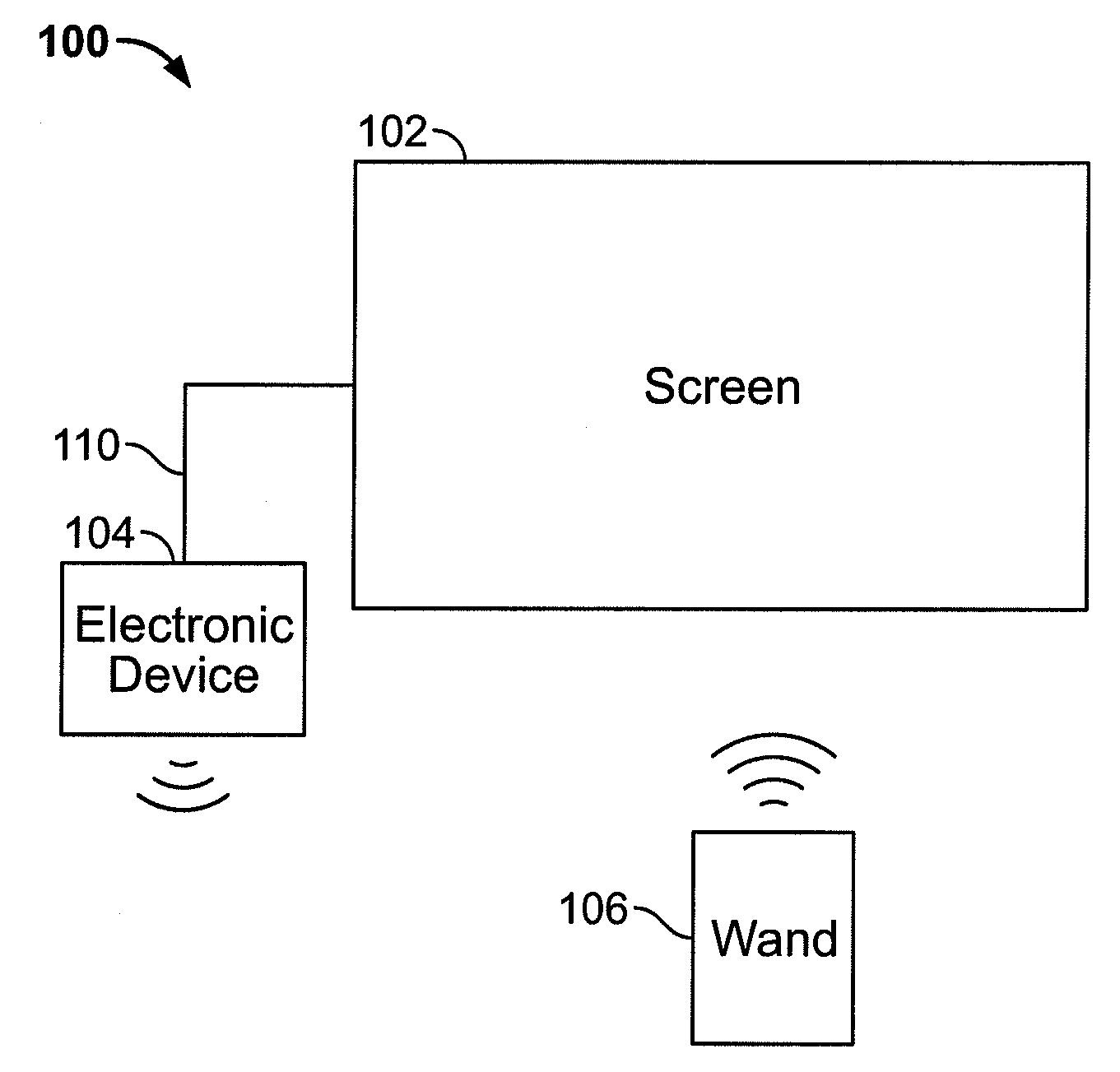
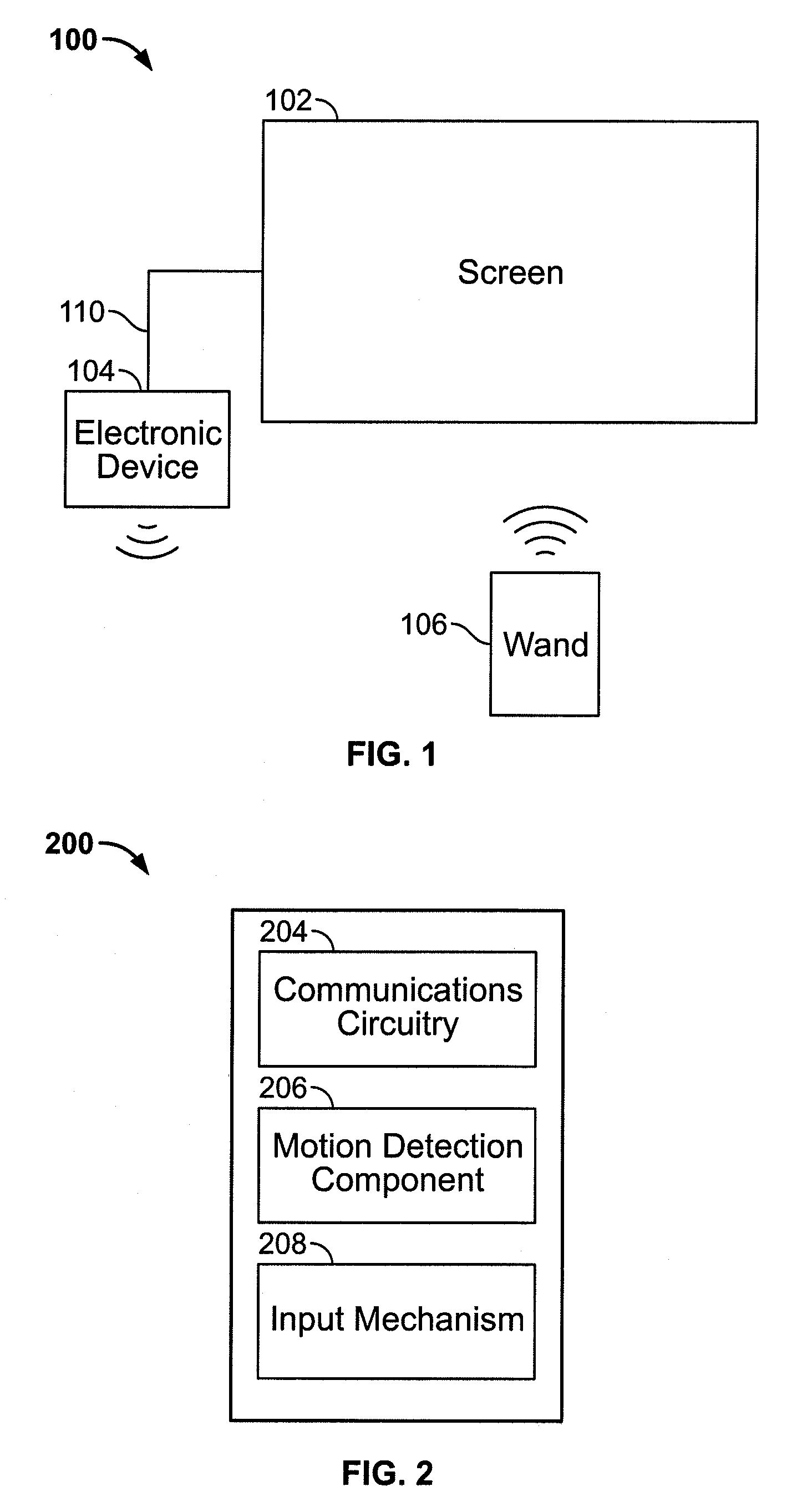
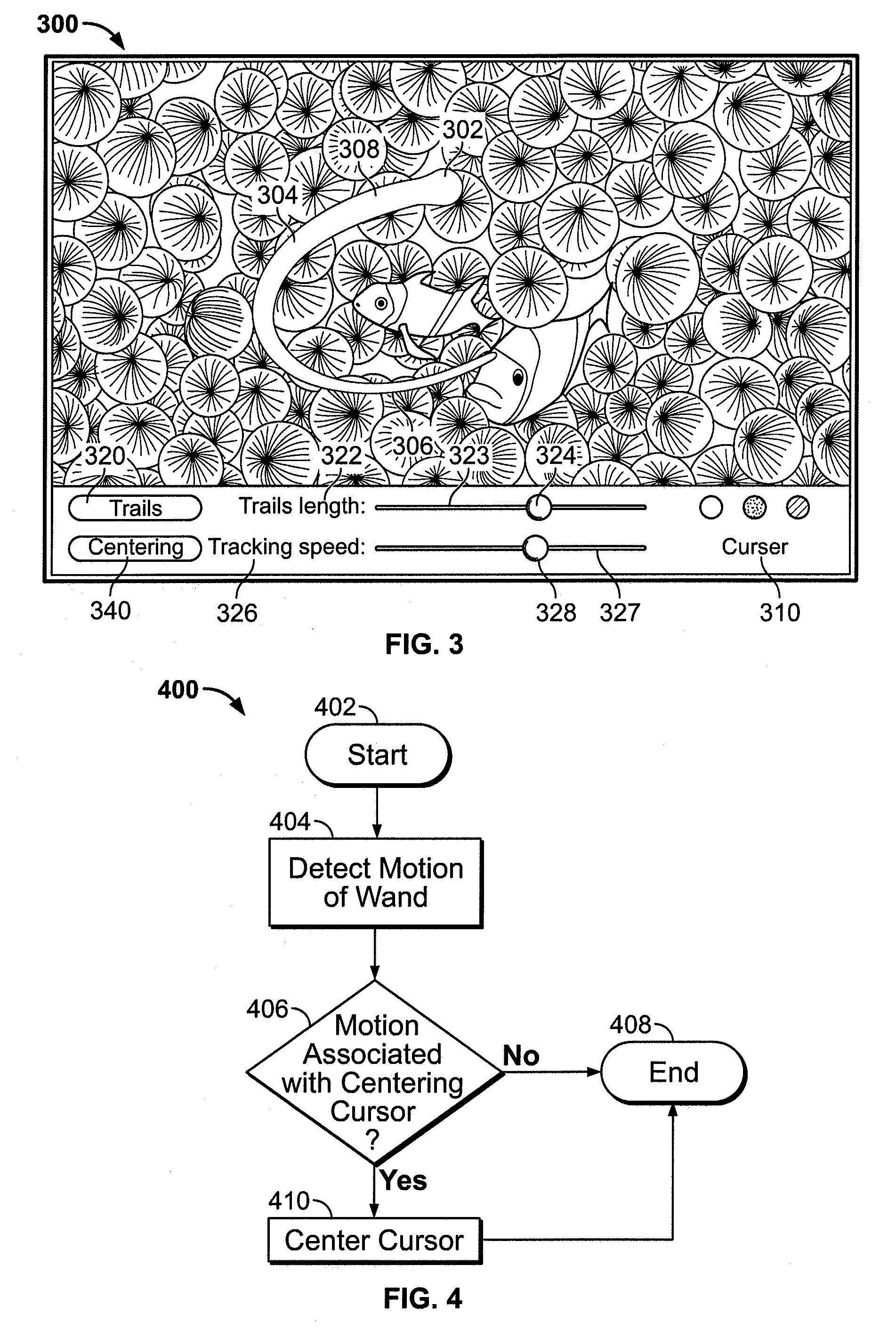
Scrolling displayed objects using a 3D remote controller in a media system
ActiveUS20090158203A1Reduced resourceInput/output processes for data processingComputer graphics (images)User input
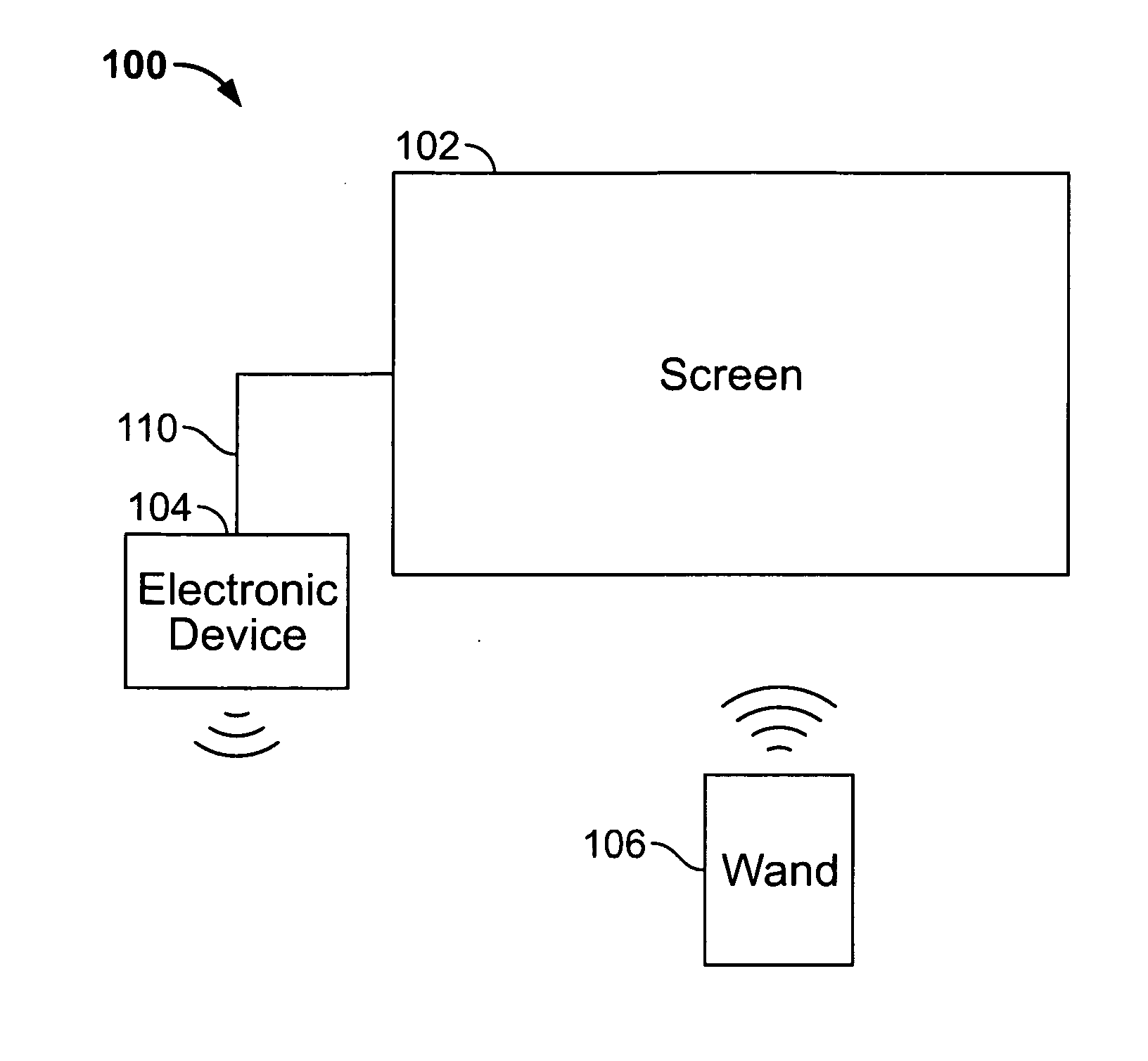
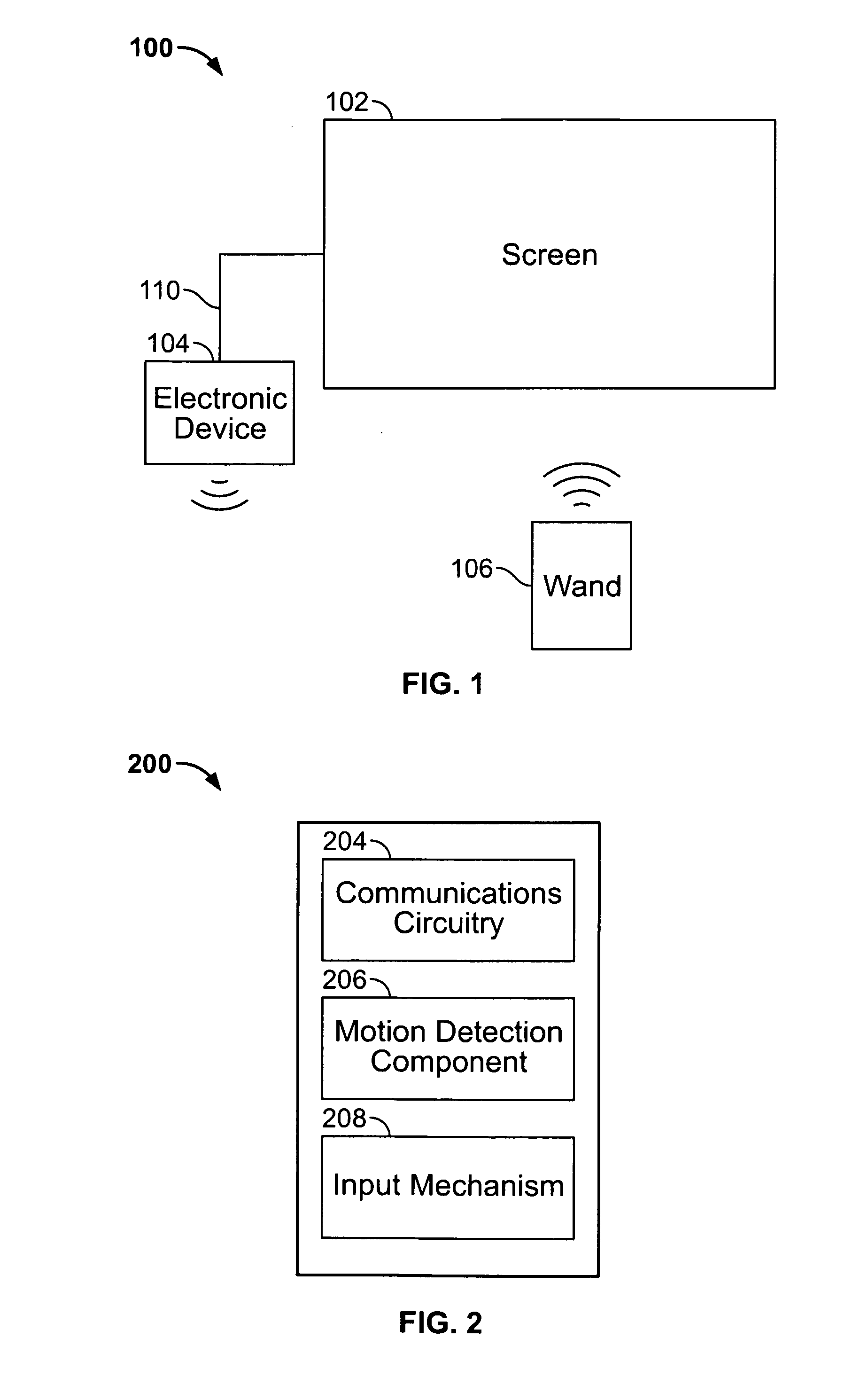
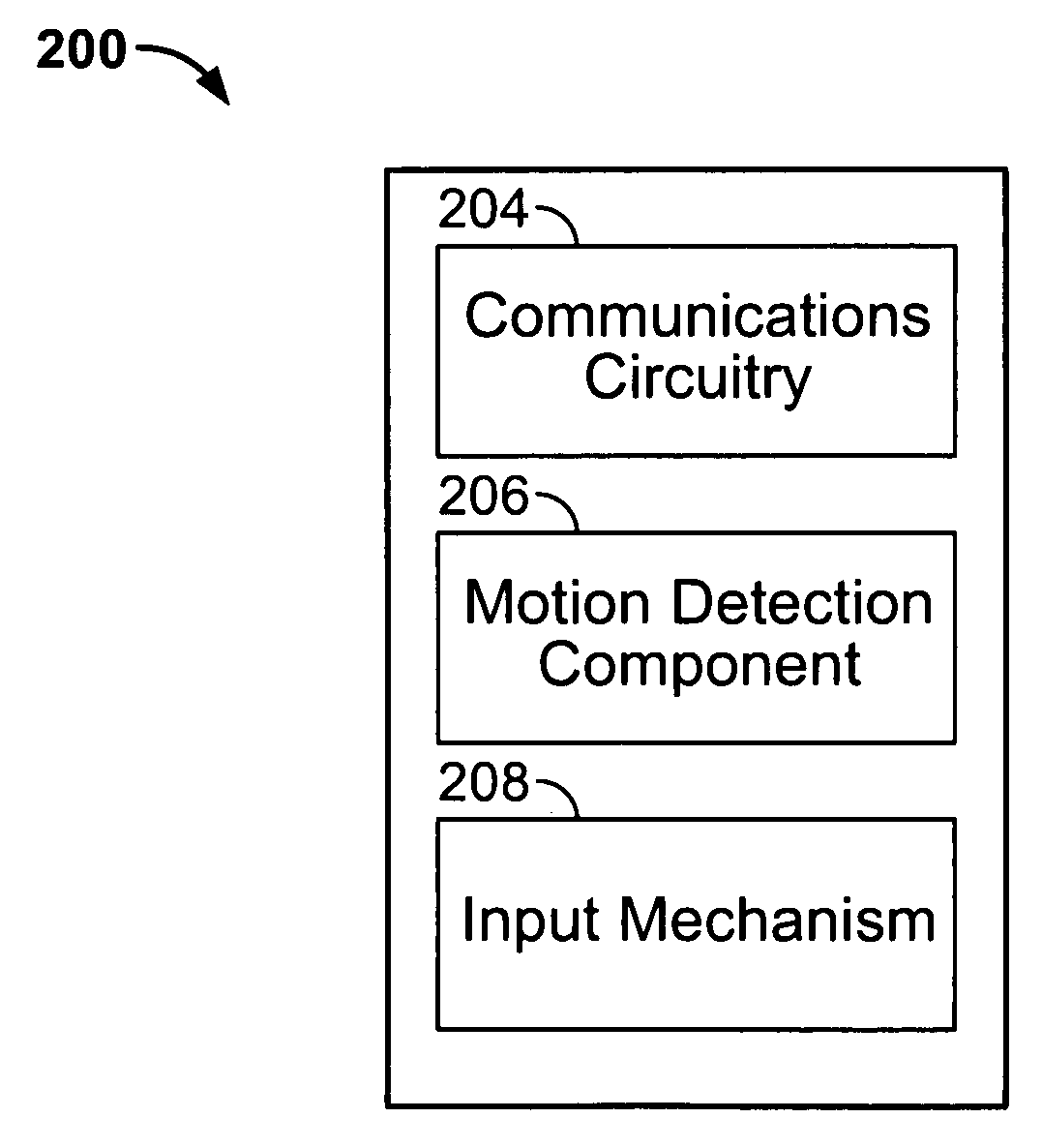
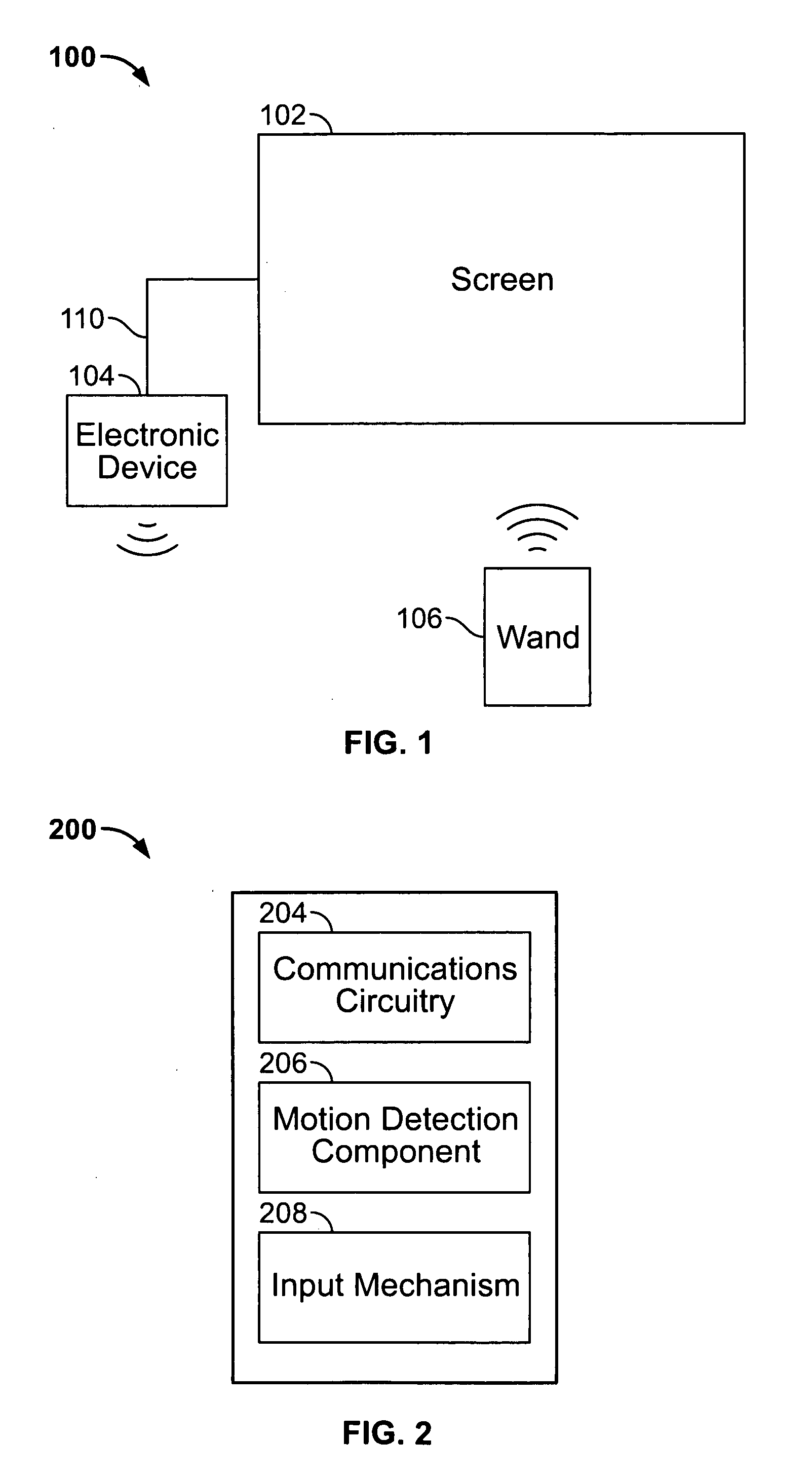
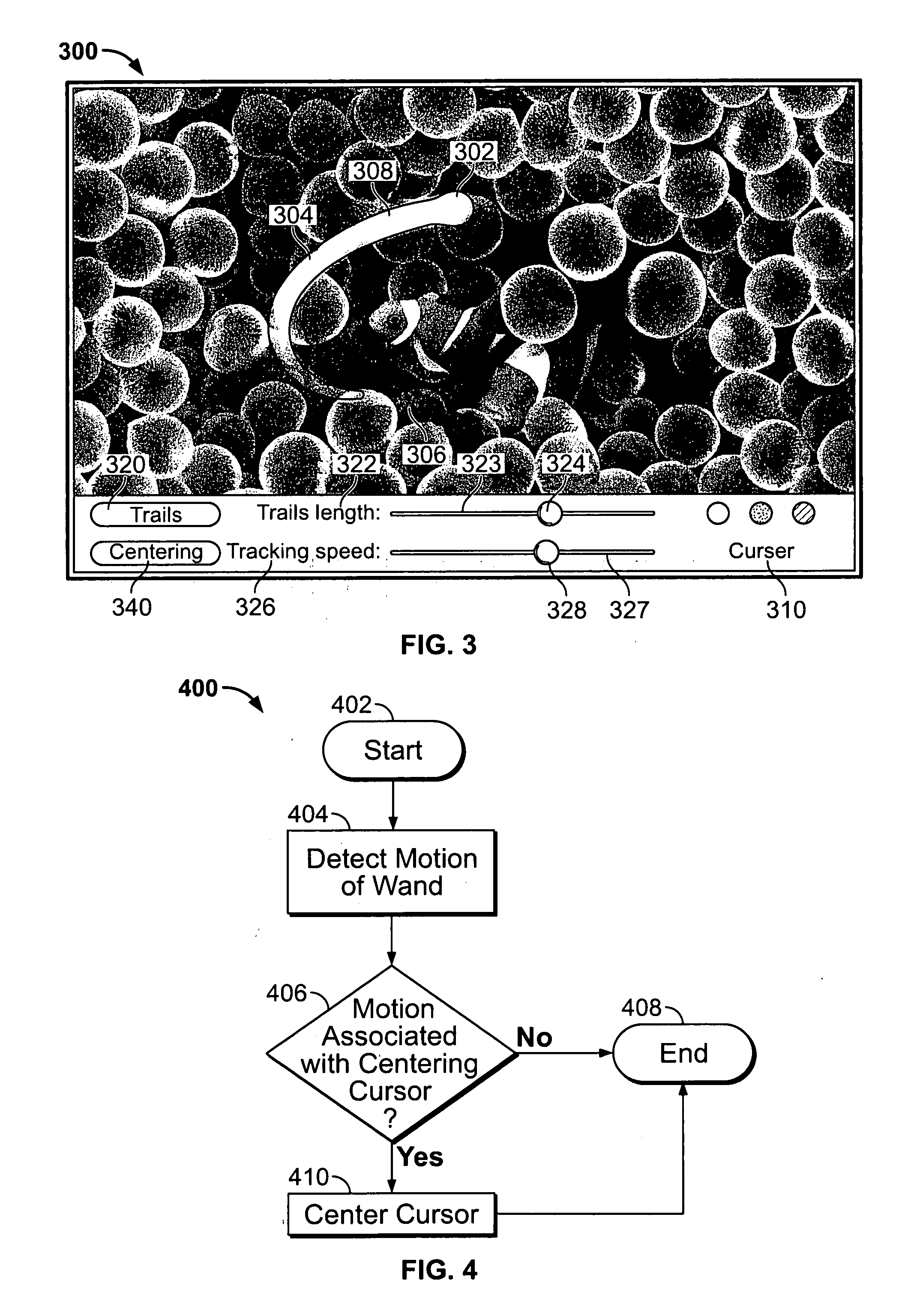
An electronic device associated with a remote wand controlling the operations of the electronic device is provided. The wand may include a motion detection component operative to provide an output reflecting the motion of the wand to the electronic device, such that the movements of a cursor displayed by the electronic device may be related to the output of the motion detection component. The wand may also include an input mechanism operative to receive user inputs. Using the input mechanism, the wand may detect a user's inputs and direct the electronic device to zoom or scroll displayed objects. The electronic device may display a screen saver by which the user may select particular media items for playback while remaining in the screen saver mode. In some embodiments, the electronic device may display video with a scroll bar that includes a preview window of the video.
Owner:APPLE INC
Interactive and dynamic screen saver for use in a media system
InactiveUS20090158222A1Reduced resourceVideo data retrievalSpecial data processing applicationsUser inputComputer graphics (images)
An electronic device associated with a remote wand controlling the operations of the electronic device is provided. The wand may include a motion detection component operative to provide an output reflecting the motion of the wand to the electronic device, such that the movements of a cursor displayed by the electronic device may be related to the output of the motion detection component. The wand may also include an input mechanism operative to receive user inputs. Using the input mechanism, the wand may detect a user's inputs and direct the electronic device to zoom or scroll displayed objects. The electronic device may display a screen saver by which the user may select particular media items for playback while remaining in the screen saver mode. In some embodiments, the electronic device may display video with a scroll bar that includes a preview window of the video.
Owner:APPLE INC
Scroll bar with video region in a media system
ActiveUS20090153389A1Reduced resourceTelevision system detailsElectric signal transmission systemsComputer graphics (images)User input
An electronic device associated with a remote wand controlling the operations of the electronic device is provided. The wand may include a motion detection component operative to provide an output reflecting the motion of the wand to the electronic device, such that the movements of a cursor displayed by the electronic device may be related to the output of the motion detection component. The wand may also include an input mechanism operative to receive user inputs. Using the input mechanism, the wand may detect a user's inputs and direct the electronic device to zoom or scroll displayed objects. The electronic device may display a screen saver by which the user may select particular media items for playback while remaining in the screen saver mode. In some embodiments, the electronic device may display video with a scroll bar that includes a preview window of the video.
Owner:APPLE INC
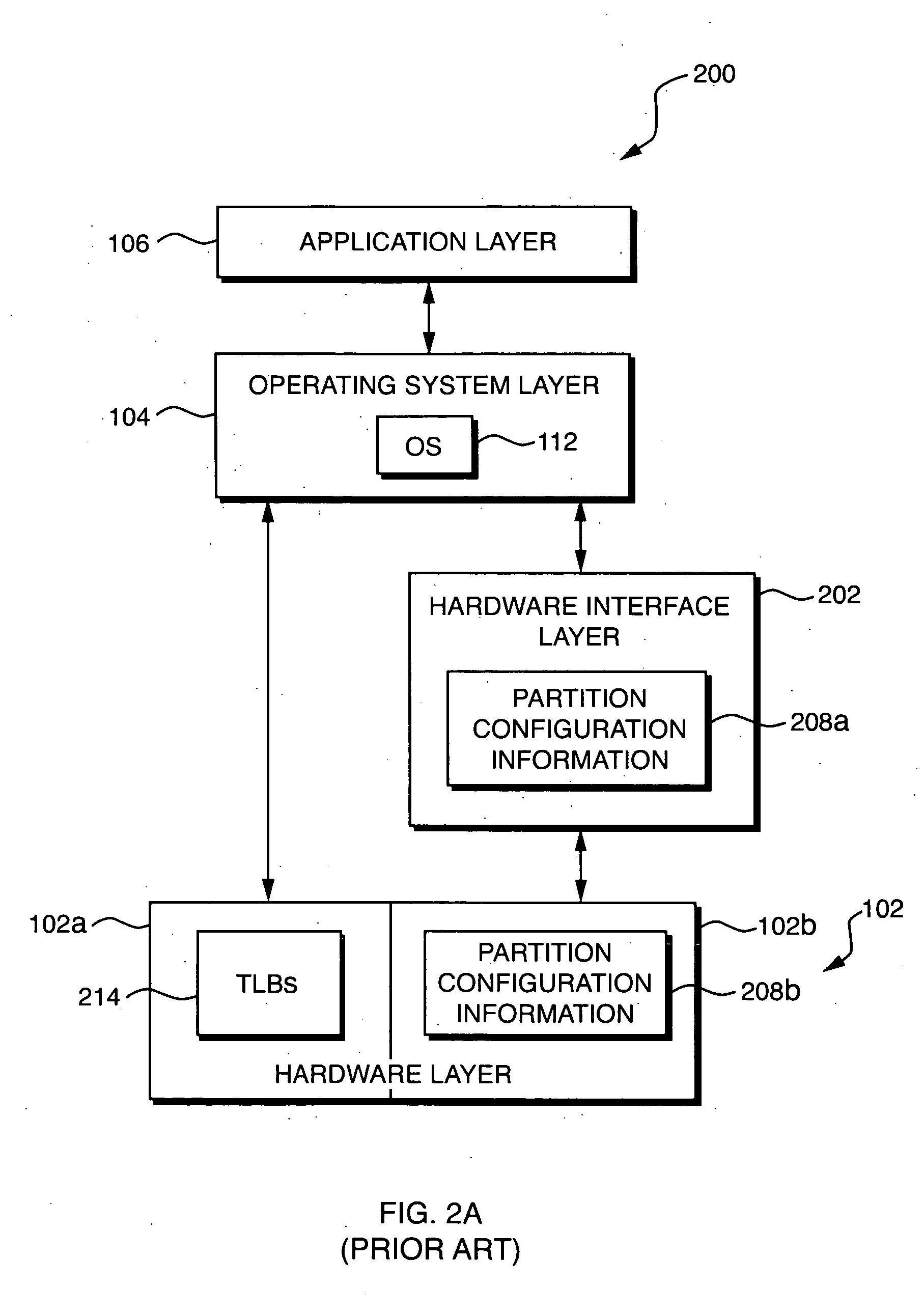
Systems and methods for improving the x86 architecture for processor virtualization, and software systems and methods for utilizing the improvements
InactiveUS20050076186A1Correct shortcomingGeneral purpose stored program computerSoftware simulation/interpretation/emulationSoftware systemProtected mode
The present invention is directed to improvements to the processor architectures, and more specifically the x86 architecture, to correct shortcomings in processor virtualization. Several embodiment of the present invention are directed to the utilization of at least one virtualization control bit to determine whether the execution of a specific instructions cause a privilege-level exception (e.g., GP0) when executed outside of a privilege ring (e.g., outside of ring-0). Several additional embodiments are directed to the utilization of a virtual assist register to implement at least one virtual assist feature. And several additional embodiments are also directed to utilization of a bit for enabling a virtual protected mode that, when a processor in running in a protected mode, causes said processor, which is otherwise executing as if it is running in protected mode, to execute normally with exceptions to handle special virtualization challenges.
Owner:MICROSOFT TECH LICENSING LLC
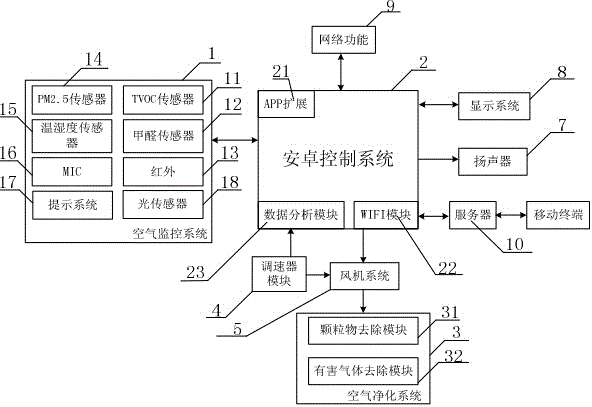
Intelligent air purification control system and method
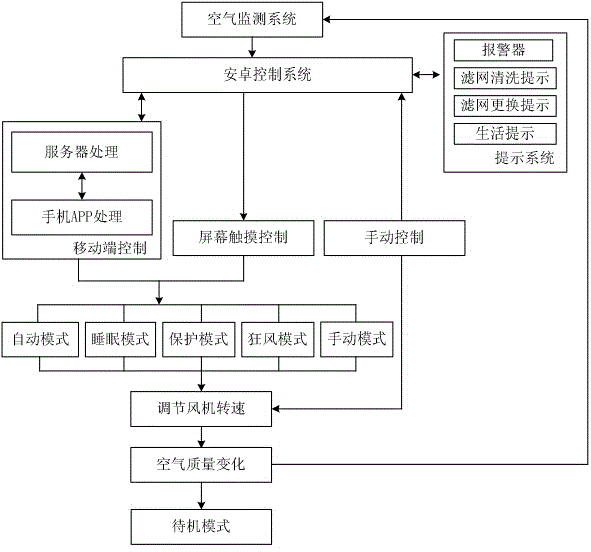
ActiveCN104819510AGuaranteed uptimeAvoid harmMechanical apparatusSpace heating and ventilation safety systemsAir monitoringControl system
The invention relates to an intelligent air purification control system and method. No intelligent air purification control systems and methods with complete functions exist at present. The intelligent air purification control system comprises an air purification system, a fan system and a shell. The intelligent air purification control system is characterized by further comprising an air monitoring system, an android control system, a speed governor module, a loudspeaker, a display system, a network function module and a server. A TVOC sensor, an infrared sensor, an MIC sensor and an optical sensor are arranged in the air monitoring system. An APP extension module, a WIFI module and a data analysis module are arranged in the android control system, and the air monitoring system, the network function module, the display system, the loudspeaker, the server, the fan system and the speed governor module are connected with the android control system. The intelligent air purification control method is characterized by comprising an automatic mode, a sleep mode, a protection mode, a fierce wind mode and a manual mode. The intelligent air purification control system is reasonable in structure and complete in function.
Owner:UCHEER PURIFICATION & POLLUTION CONTROL TECH ZHEJIANG CO LTD
Program execution apparatus, control method, control program, and integrated circuit
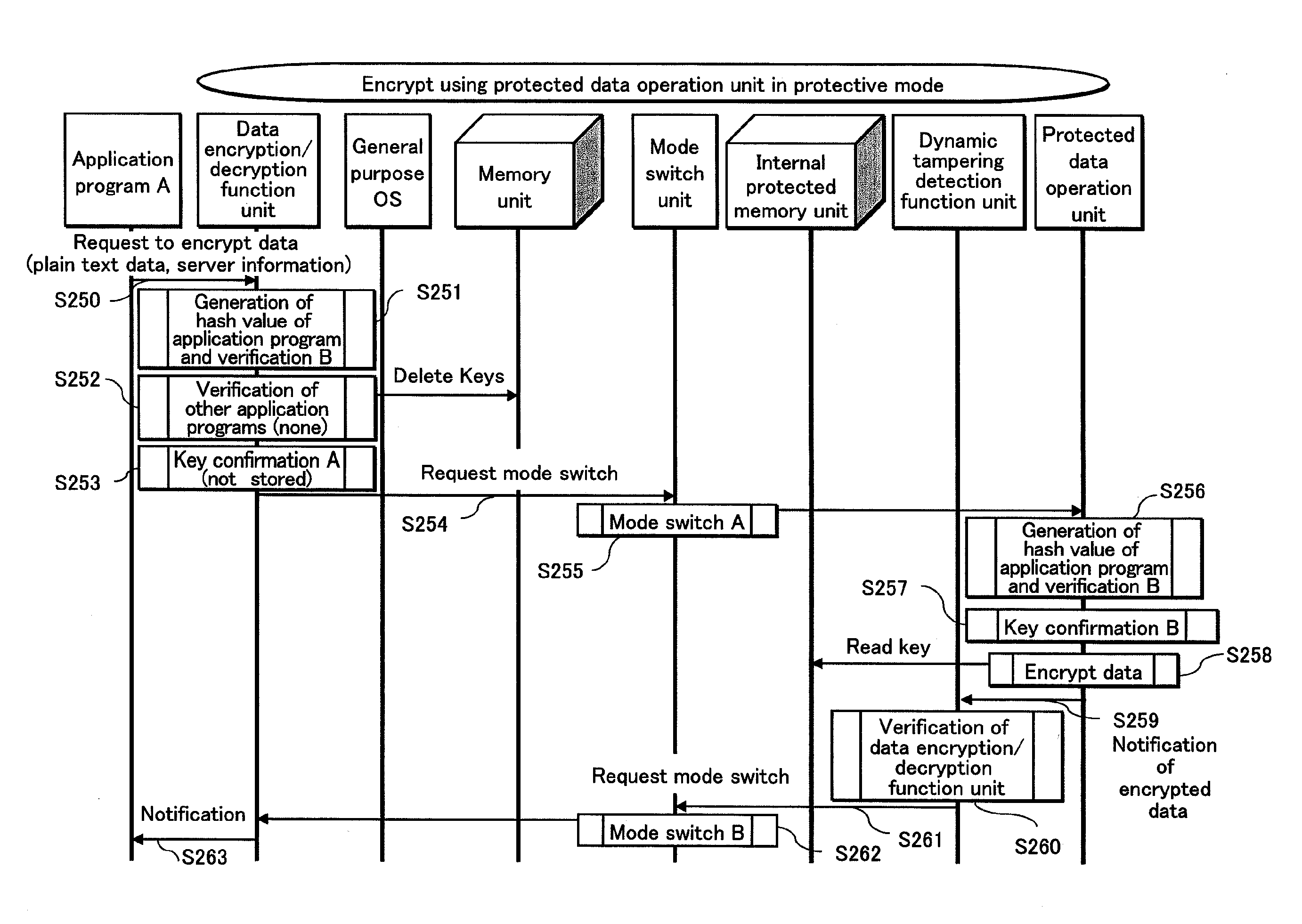
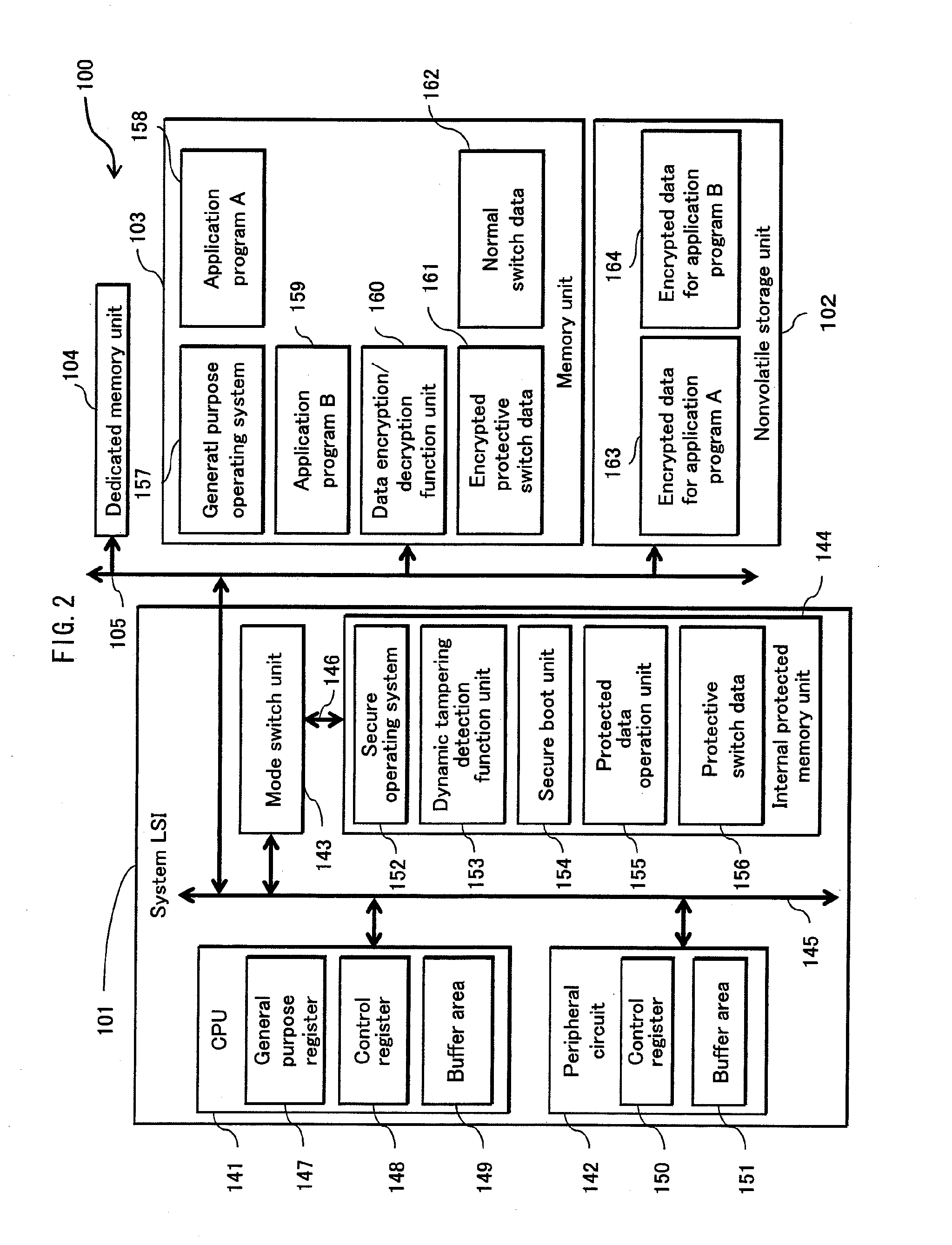
InactiveUS20100174919A1Securing confidentialityReduce overheadUnauthorized memory use protectionHardware monitoringInformation processingConfidentiality
Information processing apparatus 100 ensures confidentiality of encryption and reduces overhead associated with processing not directly related to the encryption. The information processing apparatus 100 includes: application program A158 that includes an instruction for encryption which uses a key; tampering detection unit 135x that detects tampering of the program; CPU 141 that operates according to instructions and outputs a direction for encryption upon detecting the instruction for encryption; data encryption / decryption function unit 160 that controls switching to the protective mode according to the direction; and protected data operation unit 155 that stores a key in correspondence with the program, outputs the key in the protective mode, and controls switching to the normal mode, and the data encryption / decryption function unit 160 executes the encryption in the normal mode using the received key.
Owner:SOVEREIGN PEAK VENTURES LLC
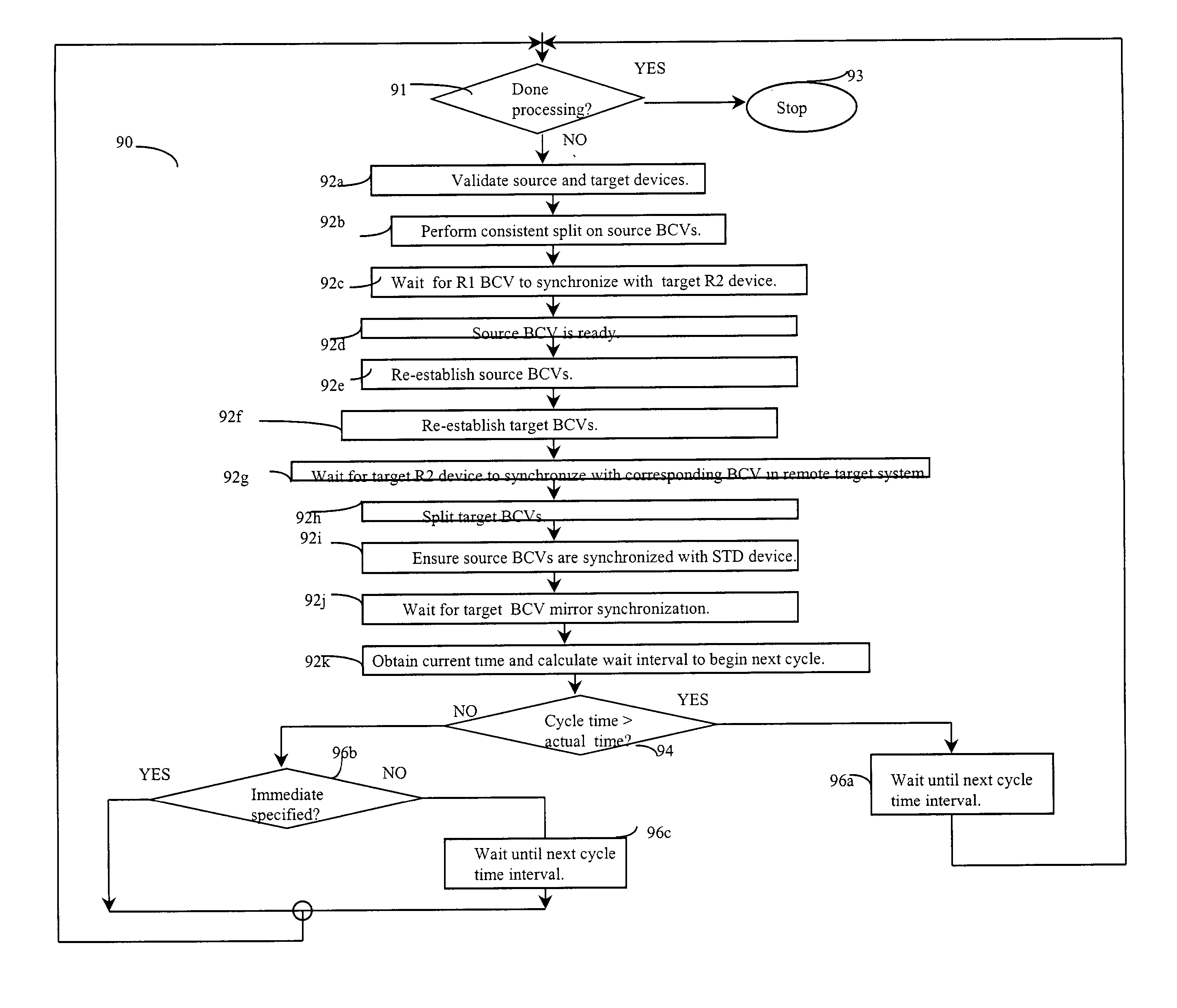
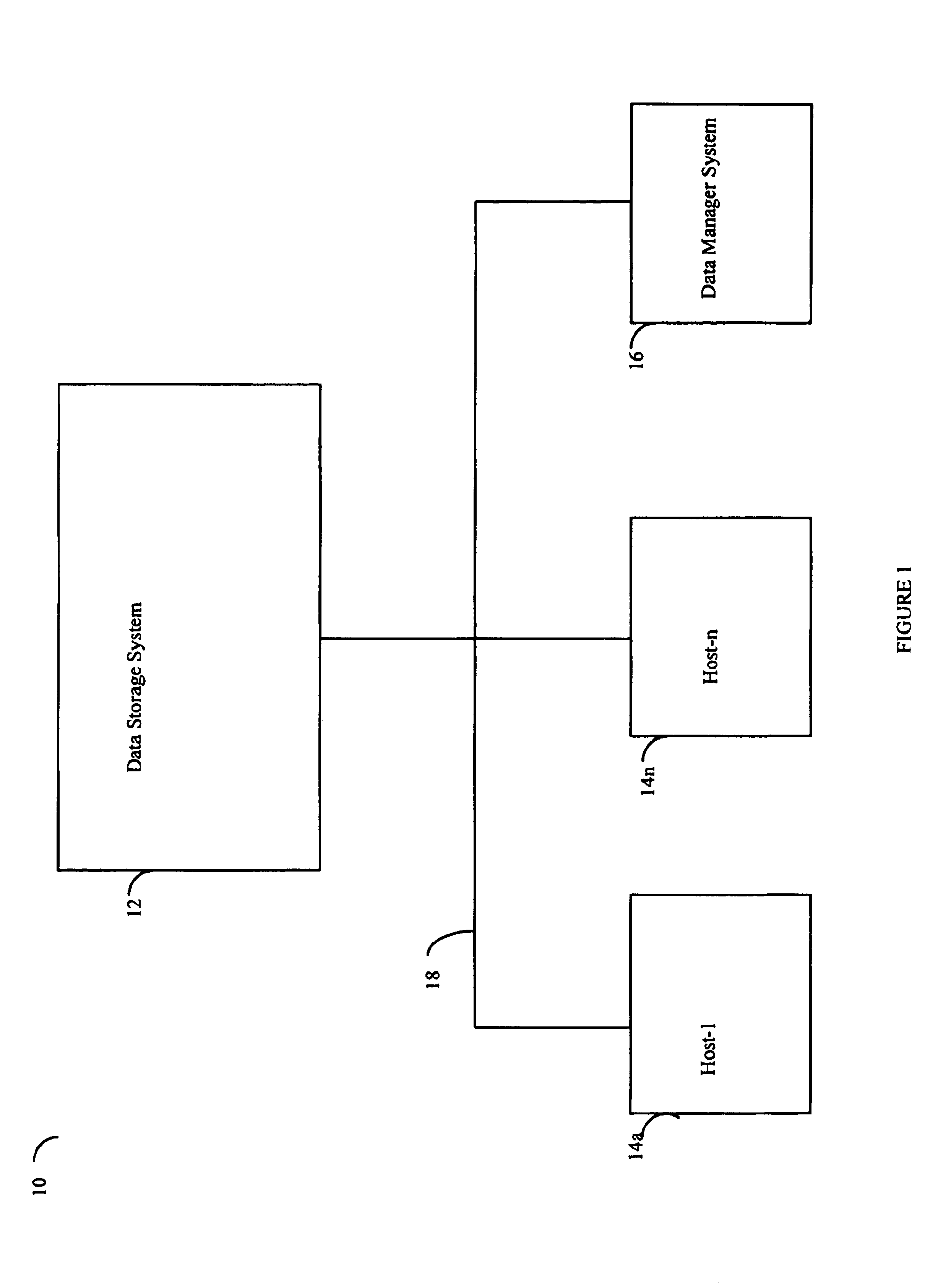
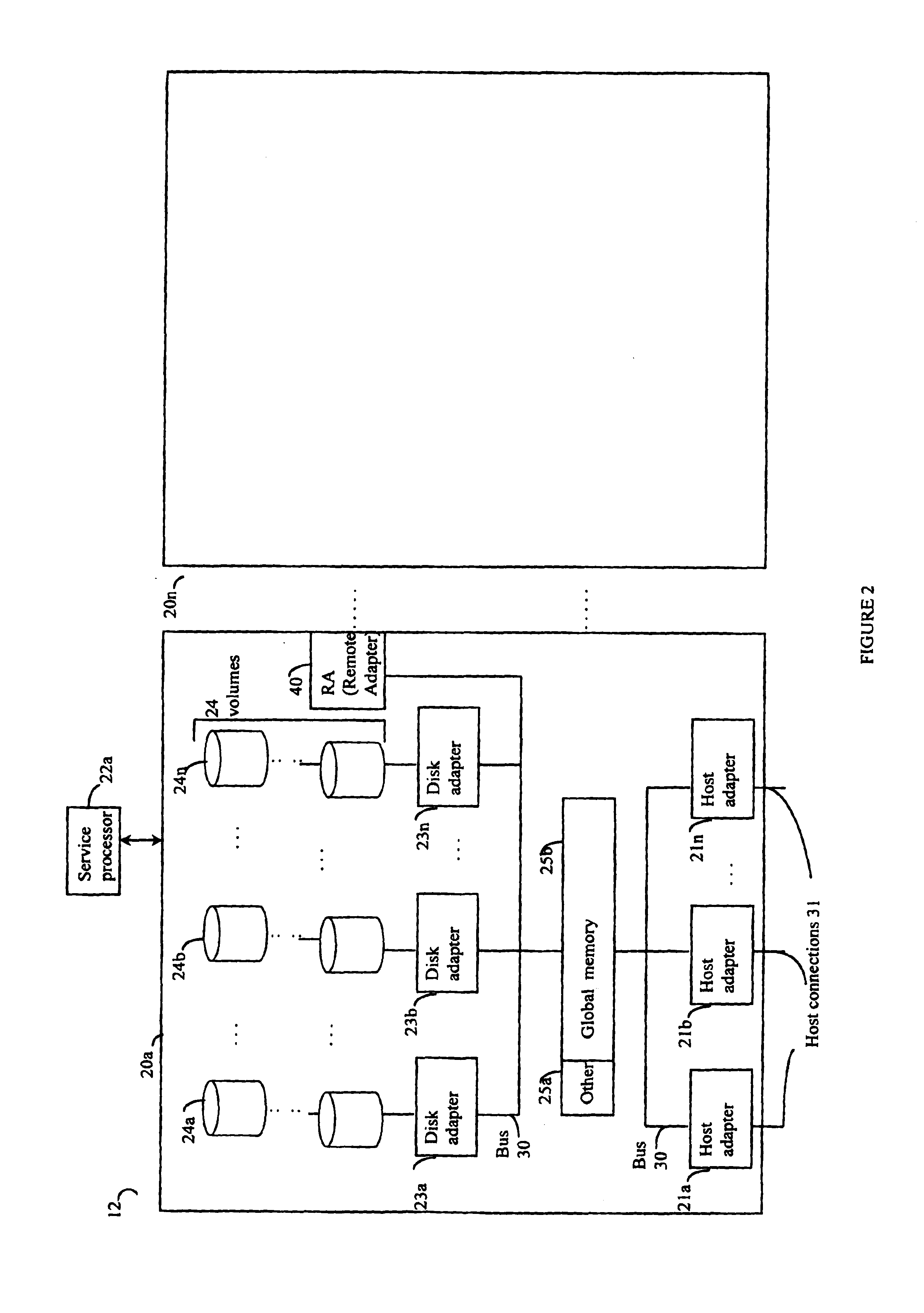
Storage automated replication processing
InactiveUS20040039888A1Data processing applicationsRedundant operation error correctionProtected modeSystem usage
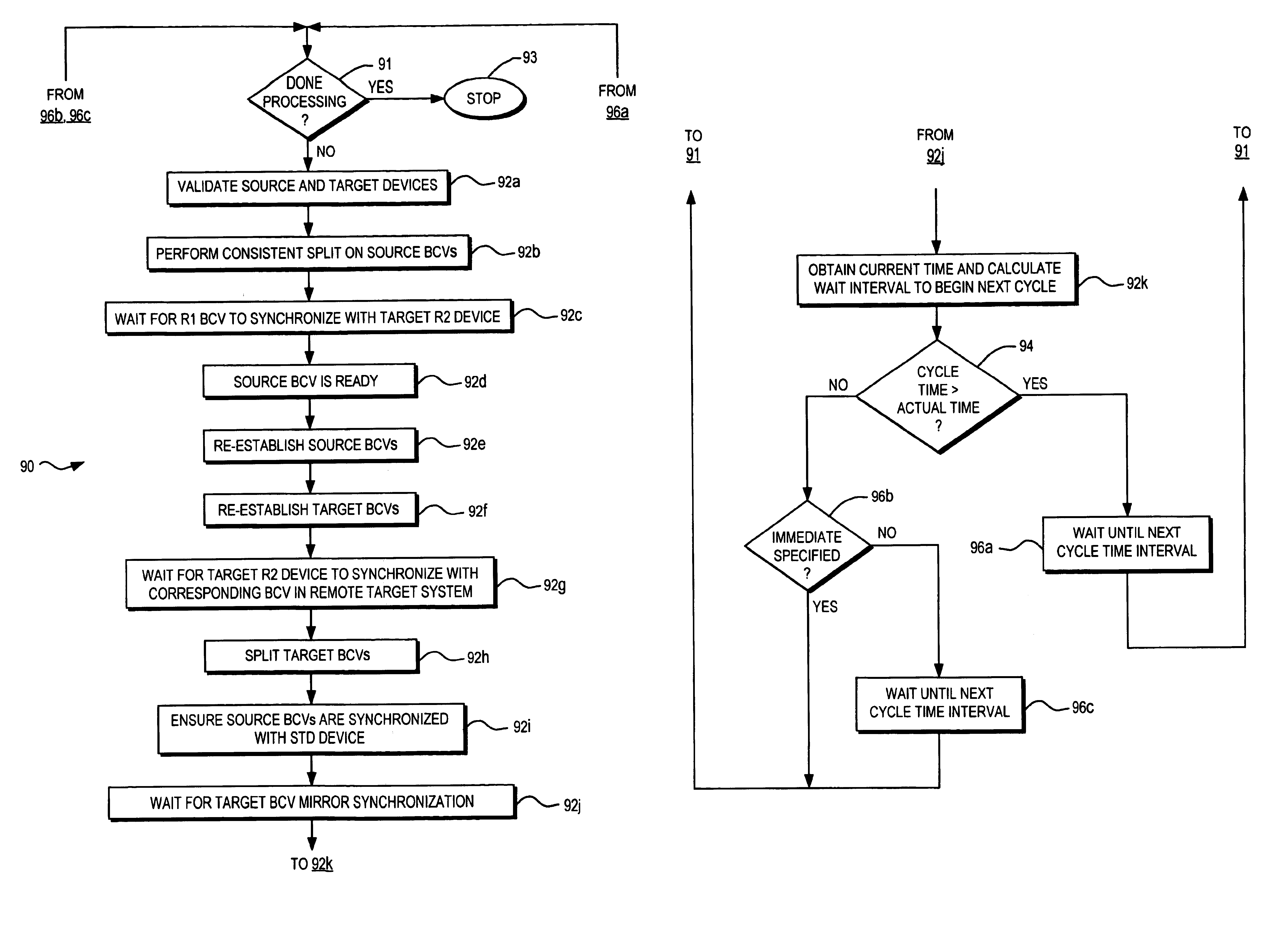
Described are techniques used in performing data replication processing. Data is replicated on a recovery site from a production site. When a disaster occurs, the state of the replication processing is determined and a restart copy of the data is made available from the recover site. Processing continues based on whether protection mode is desired such that the system executes using the recovery site as the restart with a replicated copy of the data. Data is propagated from the recovery site to the production site to resume operations and replication processing originating from the production site.
Owner:EMC IP HLDG CO LLC
Notification mechanisms on a control device
InactiveUS6937225B1Frequency-division multiplex detailsTime-division multiplexTouch PerceptionProtected mode
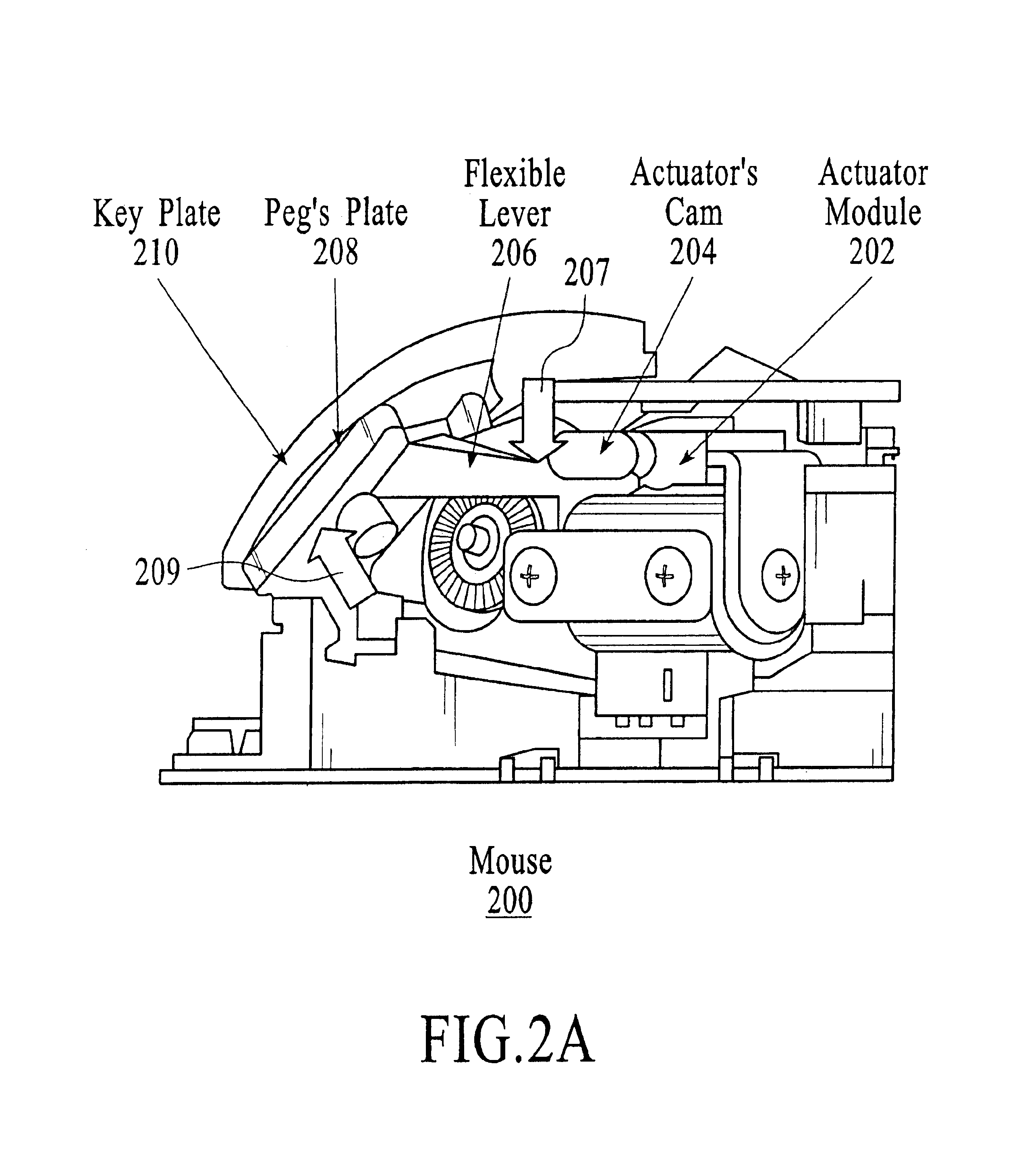
The method and system serve to notify the user of an event through a control device. Active notification takes place even when the computer sound and screen are disabled, for example, when in a power saving mode or screen saving mode. Notification may include visual notification, audio notification, vibratory notification, or tactile notification. Tactile notification can also serve to provide a private notification system which will not alert or disturb other people in the vicinity of the user. Such tactile notification can be provided by means of a texture change in the surface of the control device. One way in which this could be done is by raising a plurality of pegs through the surface of a control device to change its texture.
Owner:LOGITECH EURO SA
Computer system resource access control
ActiveUS20060031679A1Digital data protectionProgram/content distribution protectionInternet privacyOperation mode
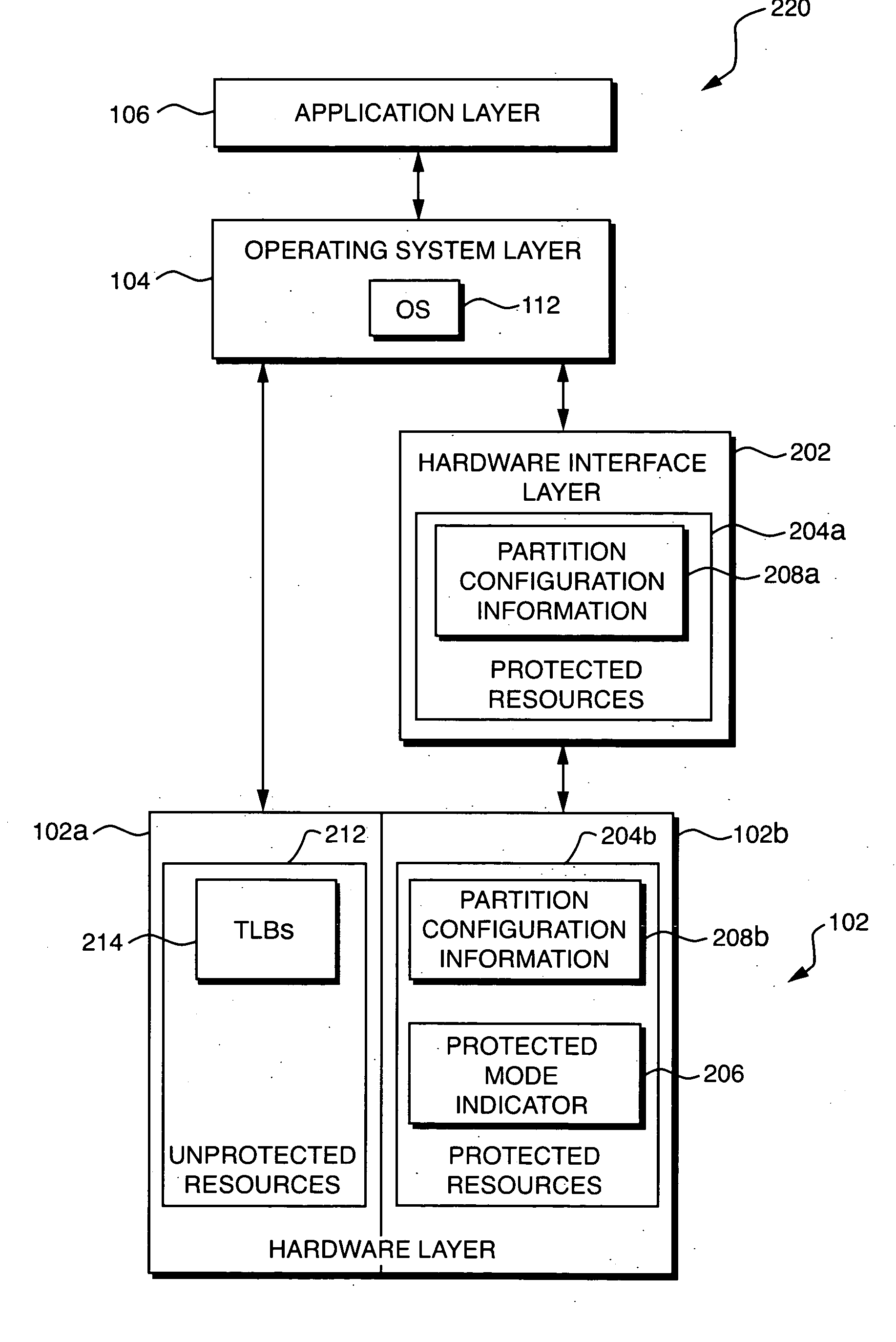
In a computer system including a plurality of resources, techniques are disclosed for receiving a request from a software program to access a specified one of the plurality of resources, determining whether the specified one of the plurality of resources is a protected resource, and, if the specified one of the plurality of resources is a protected resource, for denying the request if the computer system is operating in a protected mode of operation, and processing the request based on access rights associated with the software program if the computer system is not operating in the protected mode of operation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Catheter insertion apparatus with a needle tip protective system
The present invention relates to a catheter insertion apparatus with a needle protective system to protect a user from an inadvertent needle stick. One aspect of the invention provides for withdrawing a contaminated needle into a protected mode within the handle of the catheter apparatus. Another aspect of the invention provides for a frangible coupling link that prevents fixation of the apparatus into the duty ready mode after the needle has entered the protected mode. Another aspect of the invention relates to providing a transport mode whereby the apparatus is in a compact state with the catheter unit and the needle unit positioned inside the hollow handle, thereby reducing the costs associated with packaging and transportation.
Owner:SERPOMED
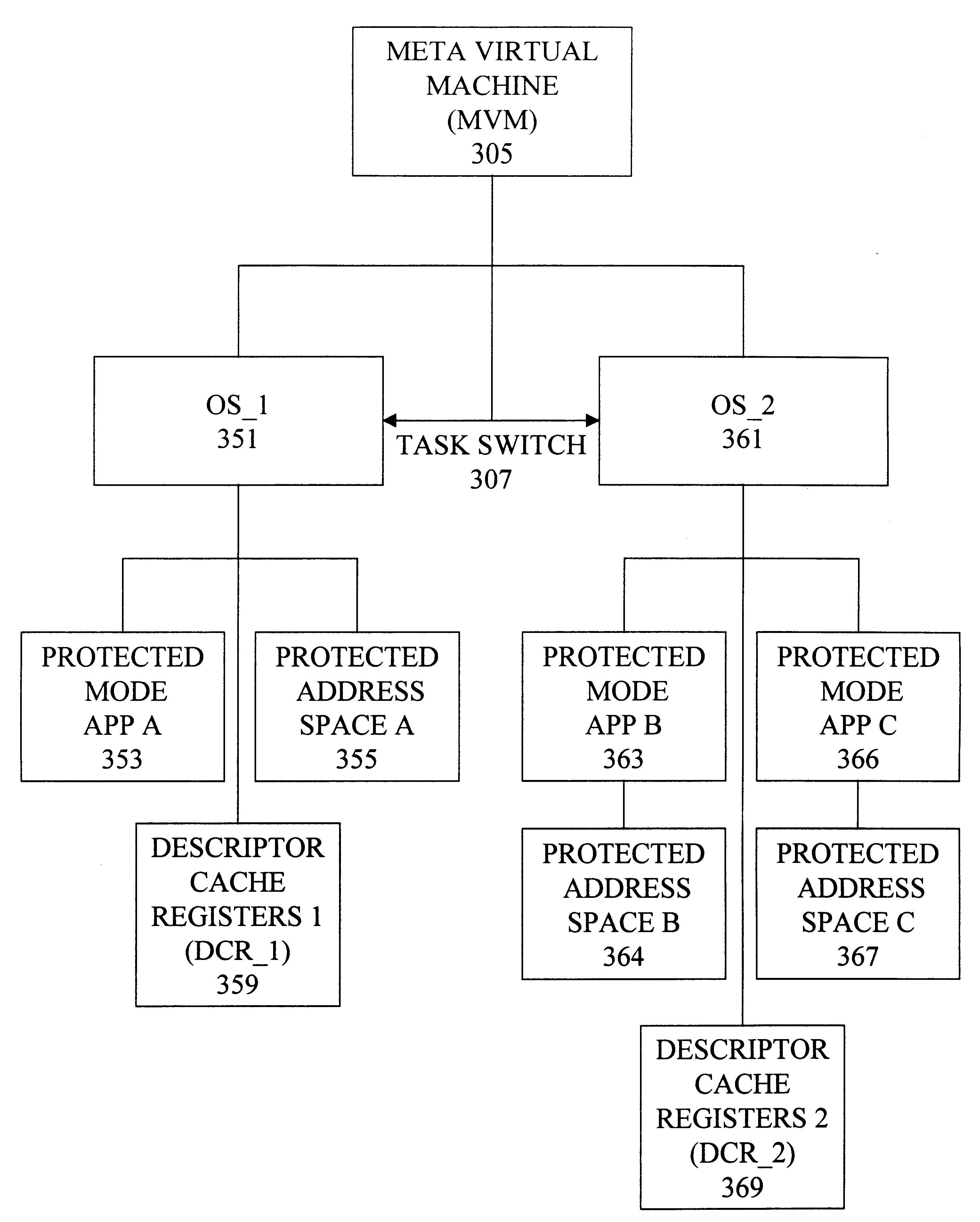
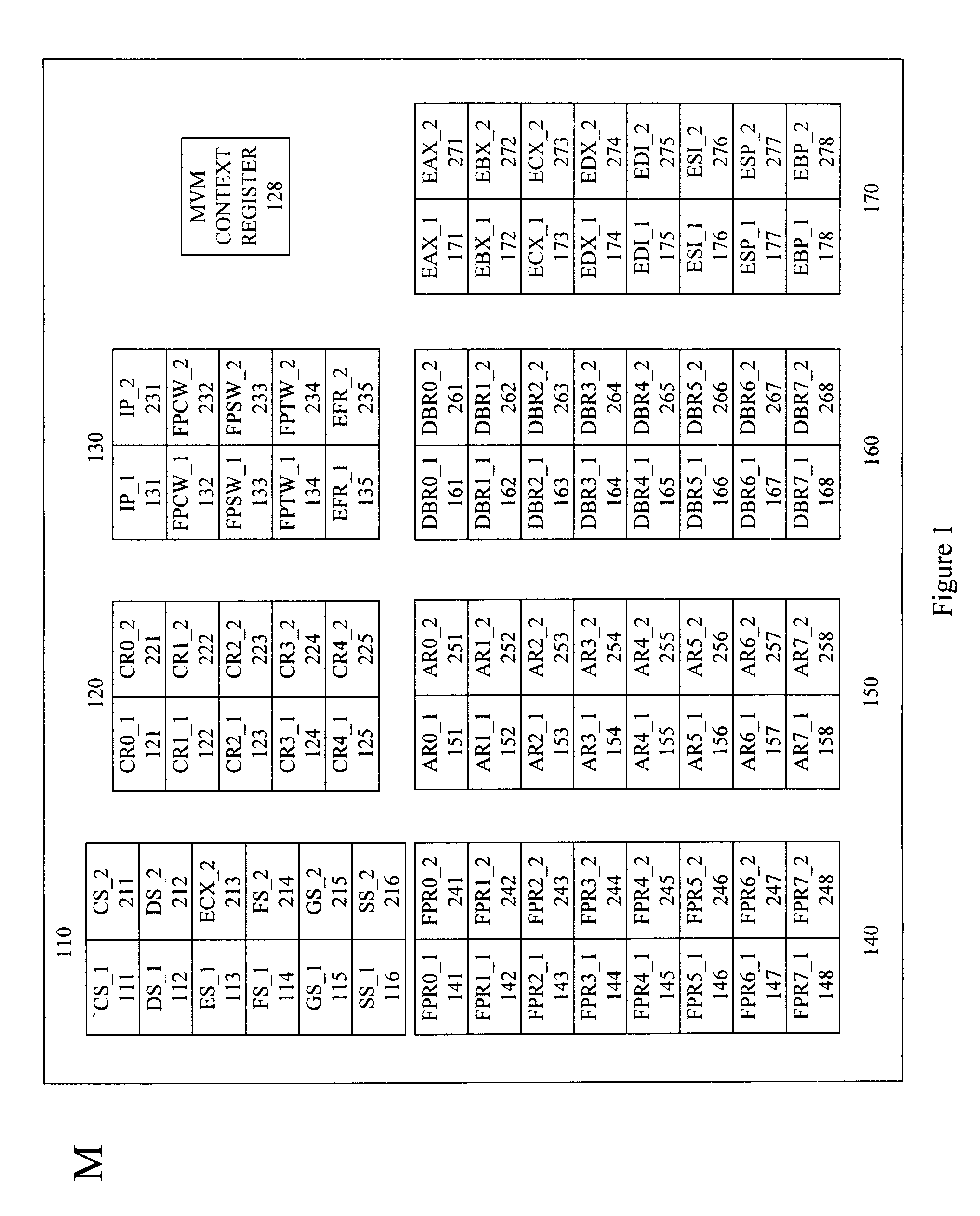
Multiple protected mode execution environments using multiple register sets and meta-protected instructions
InactiveUS6751737B1Volume/mass flow measurementUser identity/authority verificationOperational systemProcessor register
A system is provided that contains multiple control register and descriptor table register sets so that an execution context switch between X86 protected mode operating systems can be performed with minimal processing overhead. Upon receipt of a protected instruction determined to be a meta-protected instruction, the system calls a meta virtual machine (MVM) that performs the functions necessary to shift execution contexts.
Owner:GLOBALFOUNDRIES INC
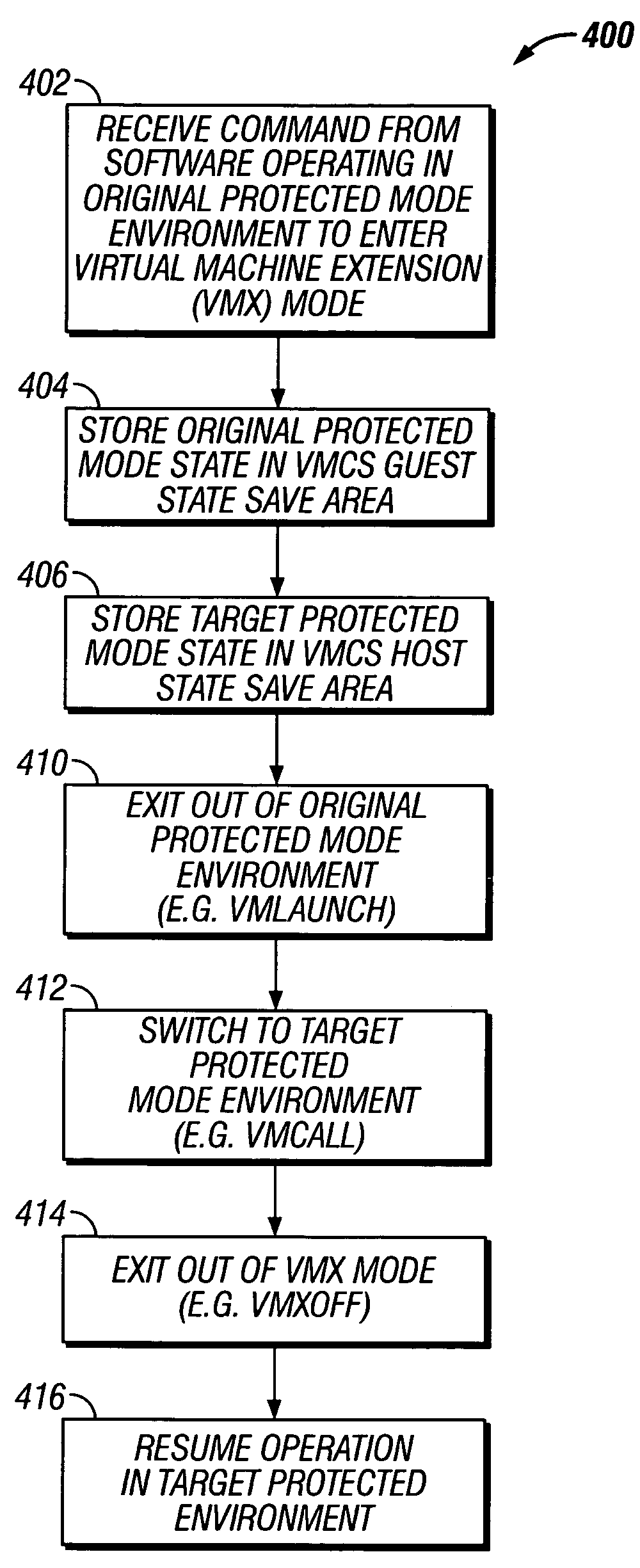
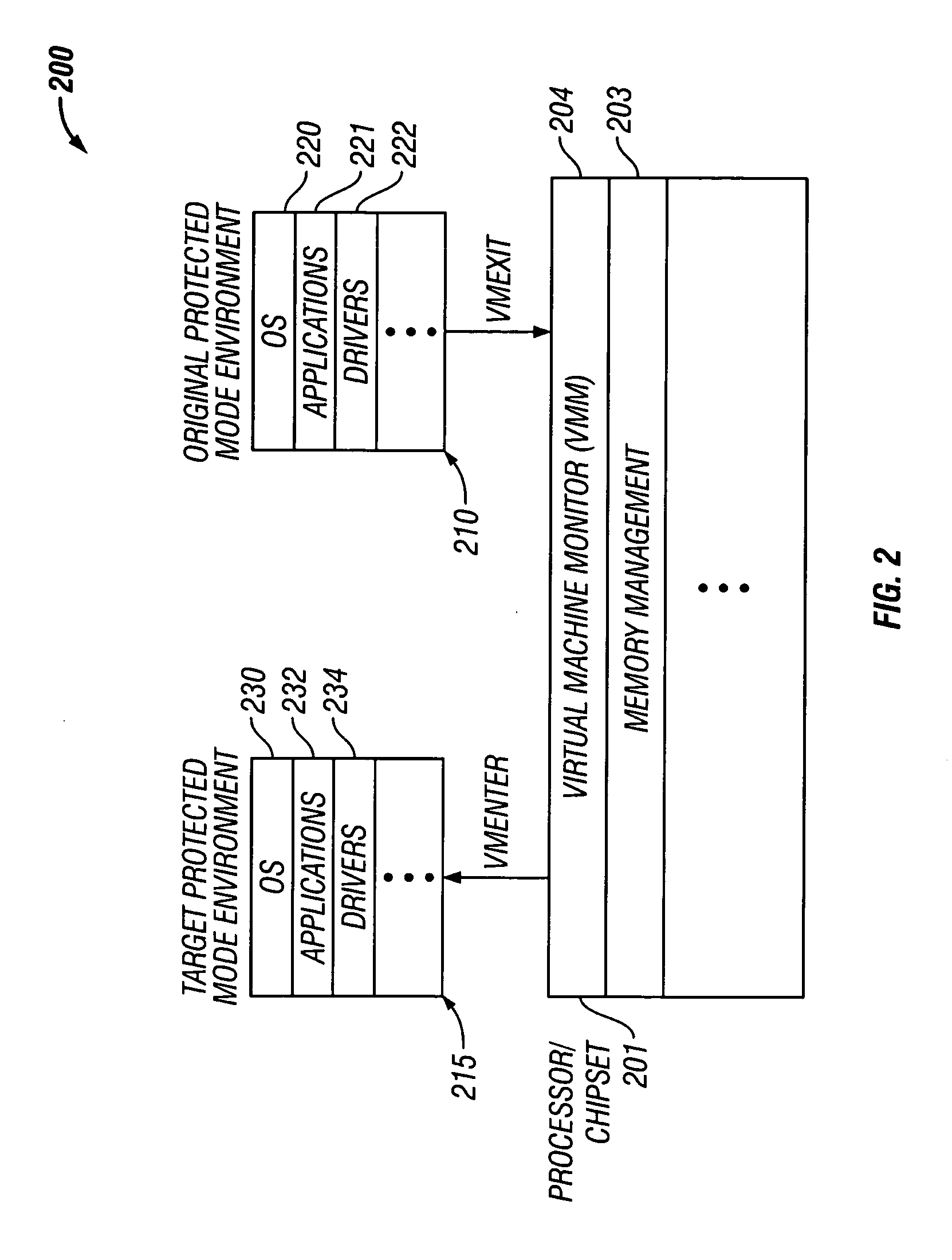
Switching between protected mode environments utilizing virtual machine functionality
ActiveUS20050223225A1User identity/authority verificationMultiprogramming arrangementsProtected modeVirtual machine
Disclosed is a processor having a normal execution mode and a host execution mode. A virtual machine monitor (VMM) operable in conjunction with the host execution mode creates at least one protected mode environment to operate guest software in a protected memory area. Responsive to a command to switch between protected modes, the VMM causes the processor to atomically switch between an original protected mode environment and a target protected mode environment. A virtual machine execution (VMX) mode may be utilized to enable virtual machine functionality for use in switching between protected modes.
Owner:INTEL CORP
Use of a remote controller Z-direction input mechanism in a media system
InactiveUS20090153475A1Reduced resourceInput/output for user-computer interactionTelevision system detailsUser inputControl electronics
An electronic device associated with a remote wand controlling the operations of the electronic device is provided. The wand may include a motion detection component operative to provide an output reflecting the motion of the wand to the electronic device, such that the movements of a cursor displayed by the electronic device may be related to the output of the motion detection component. The wand may also include an input mechanism operative to receive user inputs. Using the input mechanism, the wand may detect a user's inputs and direct the electronic device to zoom or scroll displayed objects. The electronic device may display a screen saver by which the user may select particular media items for playback while remaining in the screen saver mode. In some embodiments, the electronic device may display video with a scroll bar that includes a preview window of the video.
Owner:APPLE INC
Efficient Protection Mechanisms For Protecting Multicast Traffic in a Ring Topology Network Utilizing Label Switching Protocols
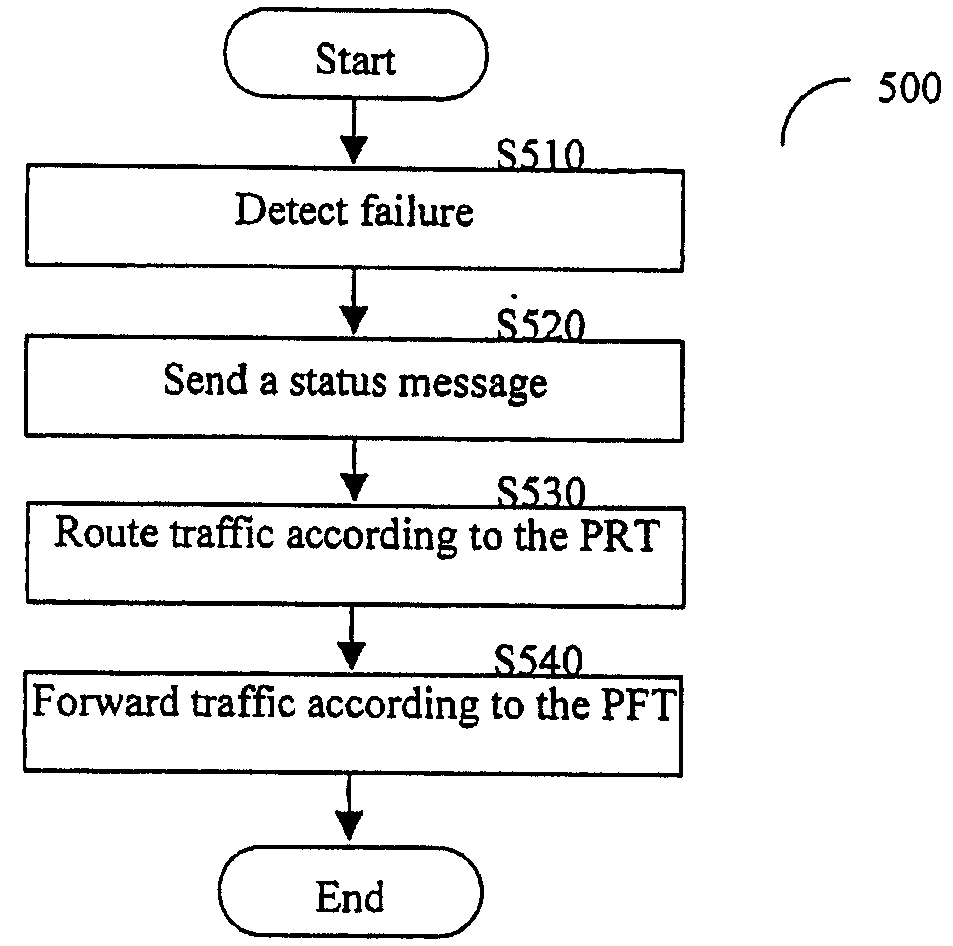
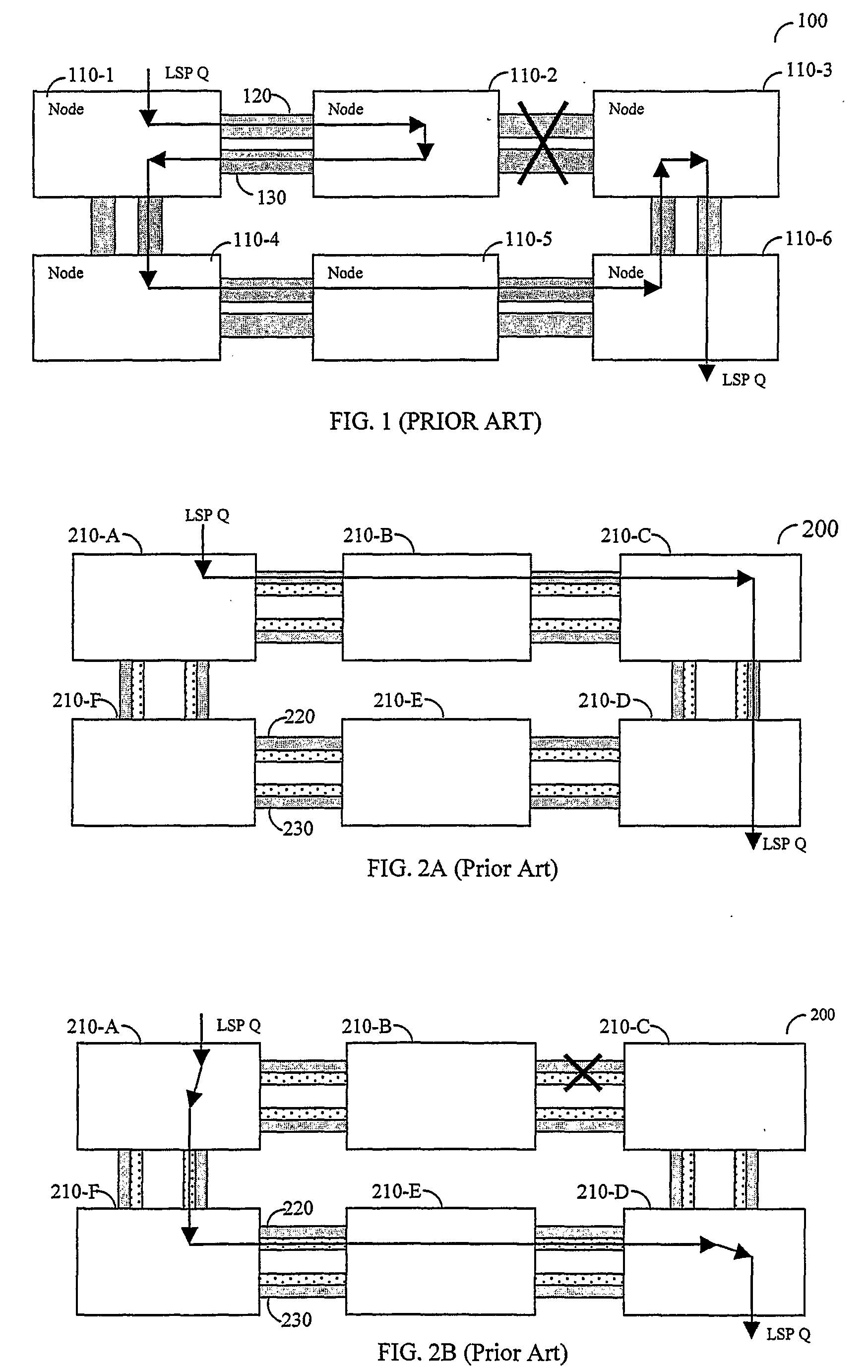
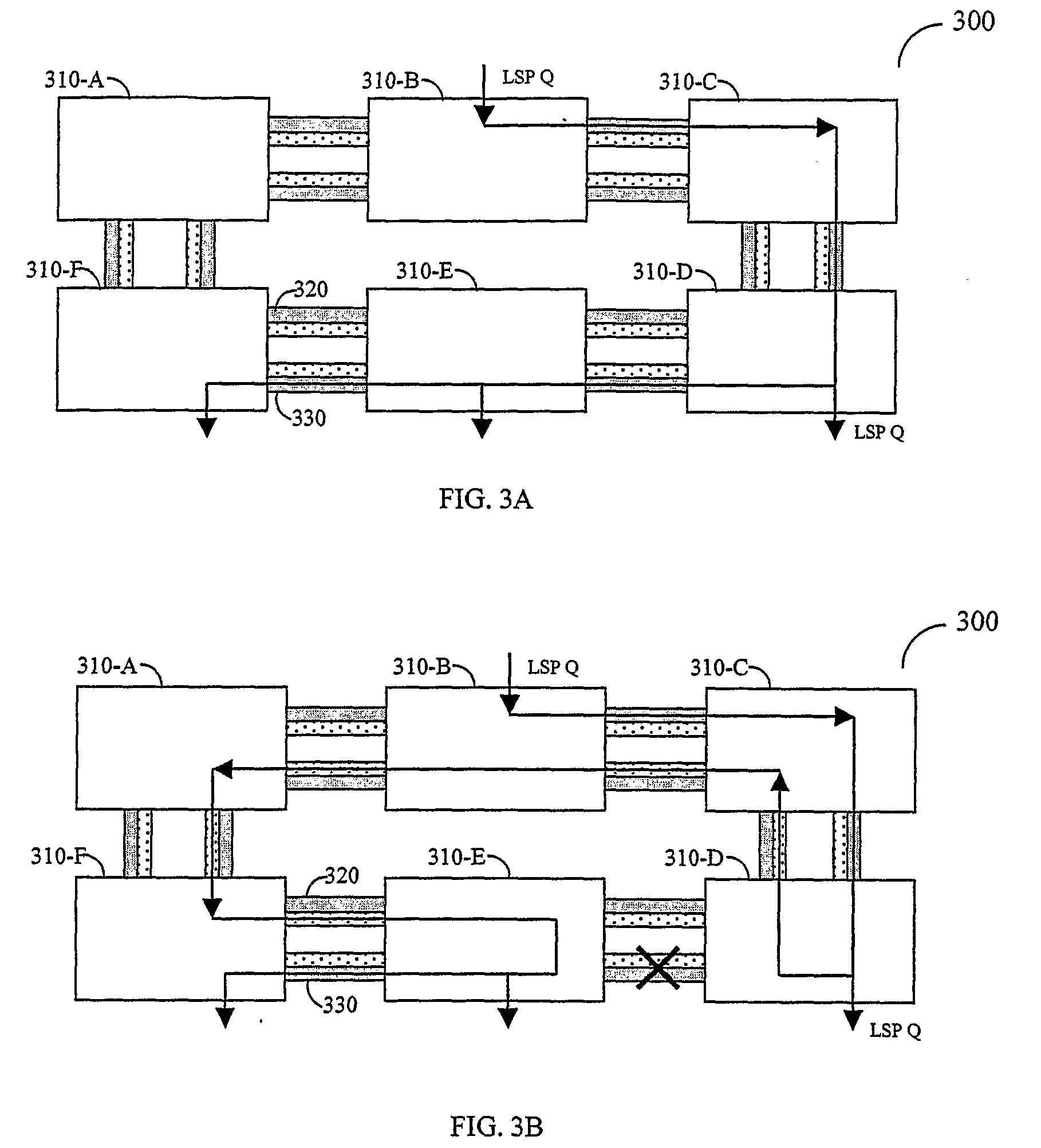
Efficient protection mechanisms for ring-based label-switching networks, such as multi-protocol label switching (MPLS) networks. The protection mechanisms are designed to protect point-to-multipoint label switching paths (LSPs). In steering ring protection embodiments, the nodes of the ring network are provided with pre-configured tables that enable each node to operate in both working mode and protection mode. The information required for each node to switch between the two modes in included in its respective table during the pre-configuration of the ring network. In wrapping ring protection embodiments, the wrapping is performed by assigning a unique LSP label to each LSP and further configuring each intermediate node in the ring network to transparently pass data packets including the unique LSP label. Upon detecting a failure in a network node, the data packets including the unique LSP label are switched to a protection ring.
Owner:ALCATEL LUCENT SAS
Software application break through a screen blanker
ActiveUS7689939B1Frequency-division multiplex detailsTime-division multiplexDisplay deviceProtected mode
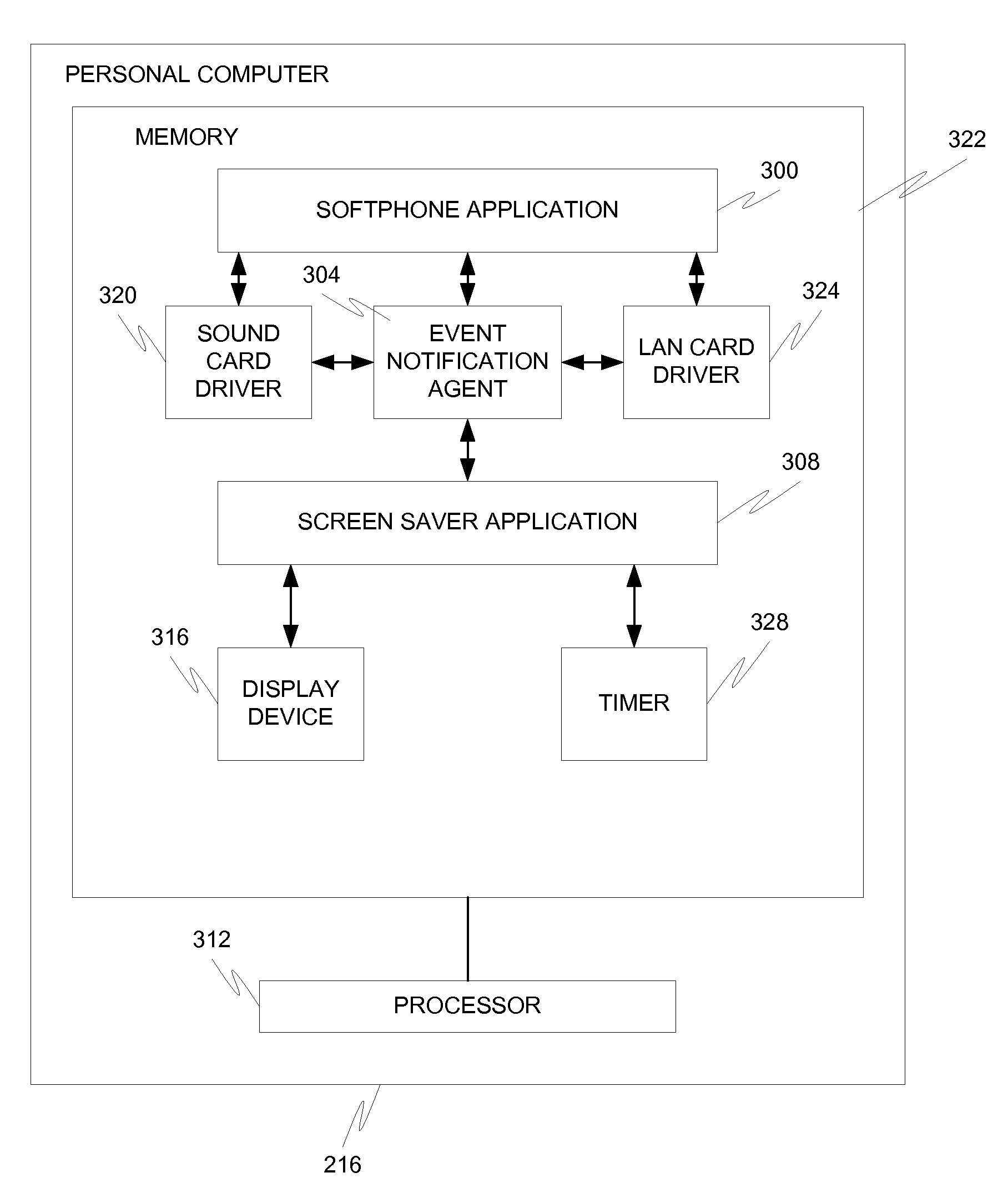
The present invention is directed to a personal computer that includes: a display device 316 for displaying image information and a processor 312 operable when the display device 316 is in a screen saver mode to (a) receive, from an application, at least part of which is executing on the personal computer 216, notification of the occurrence of an event; (b) determine if the event is a member of a defined set of events; and (c) when the event is a member of the defined set of events, display on the display image information associated with the event, wherein the displaying function occurs while the display is in the screen saver mode.
Owner:AVAYA INC
Storage automated replication processing
Described are techniques used in performing data replication processing. Data is replicated on a recovery site from a production site. When a disaster occurs, the state of the replication processing is determined and a restart copy of the data is made available from the recover site. Processing continues based on whether protection mode is desired such that the system executes using the recovery site as the restart with a replicated copy of the data. Data is propagated from the recovery site to the production site to resume operations and replication processing originating from the production site.
Owner:EMC IP HLDG CO LLC
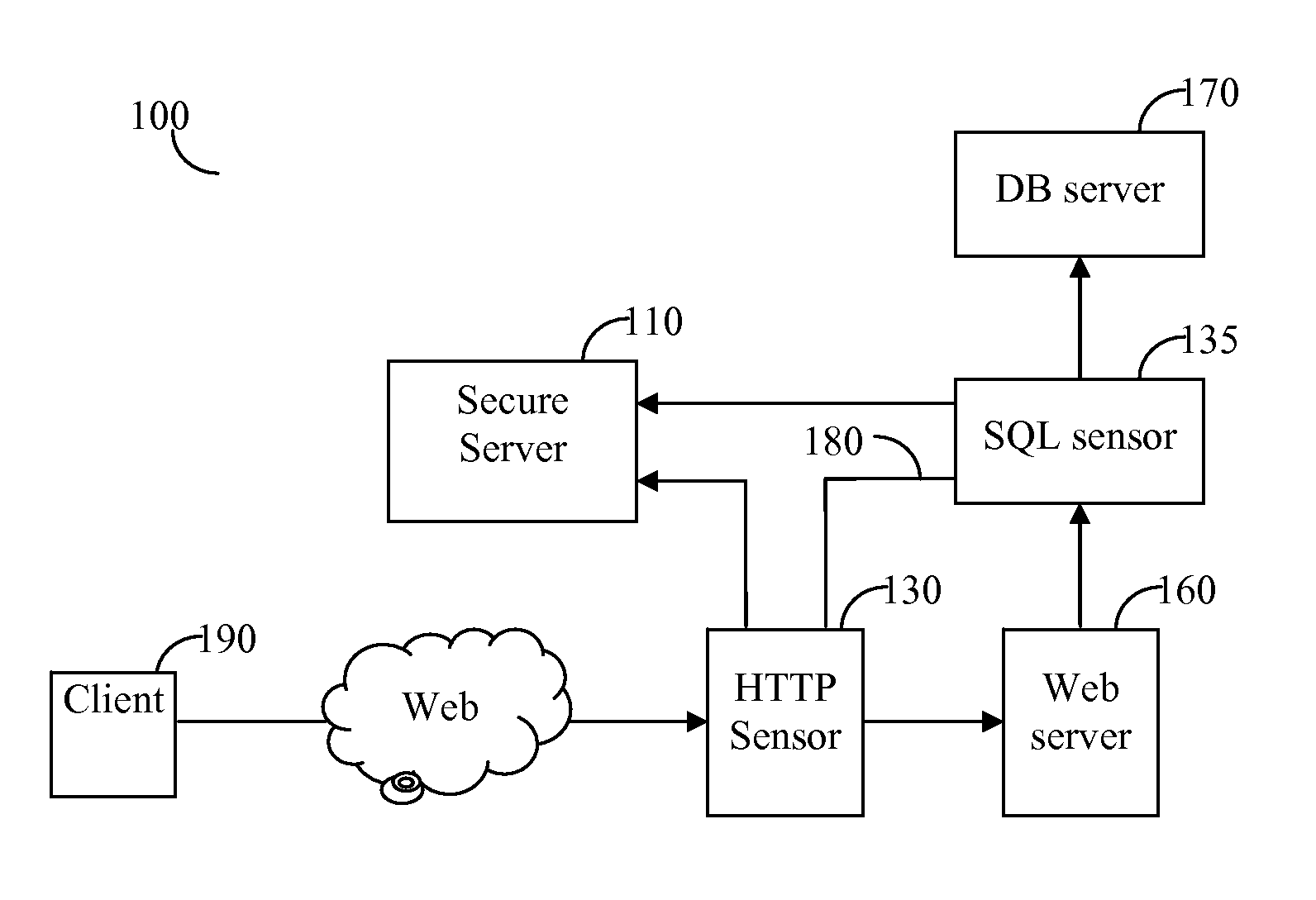
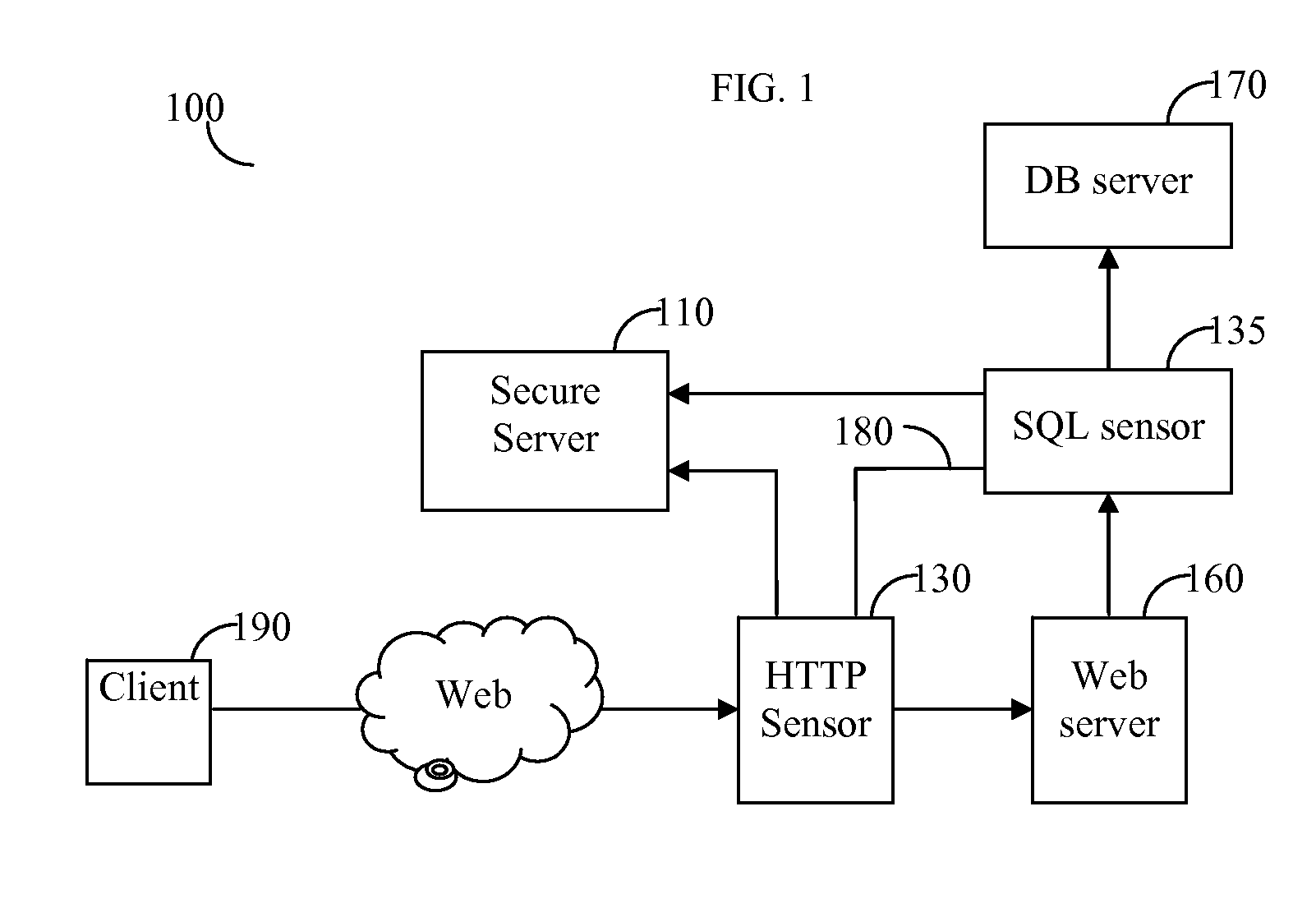
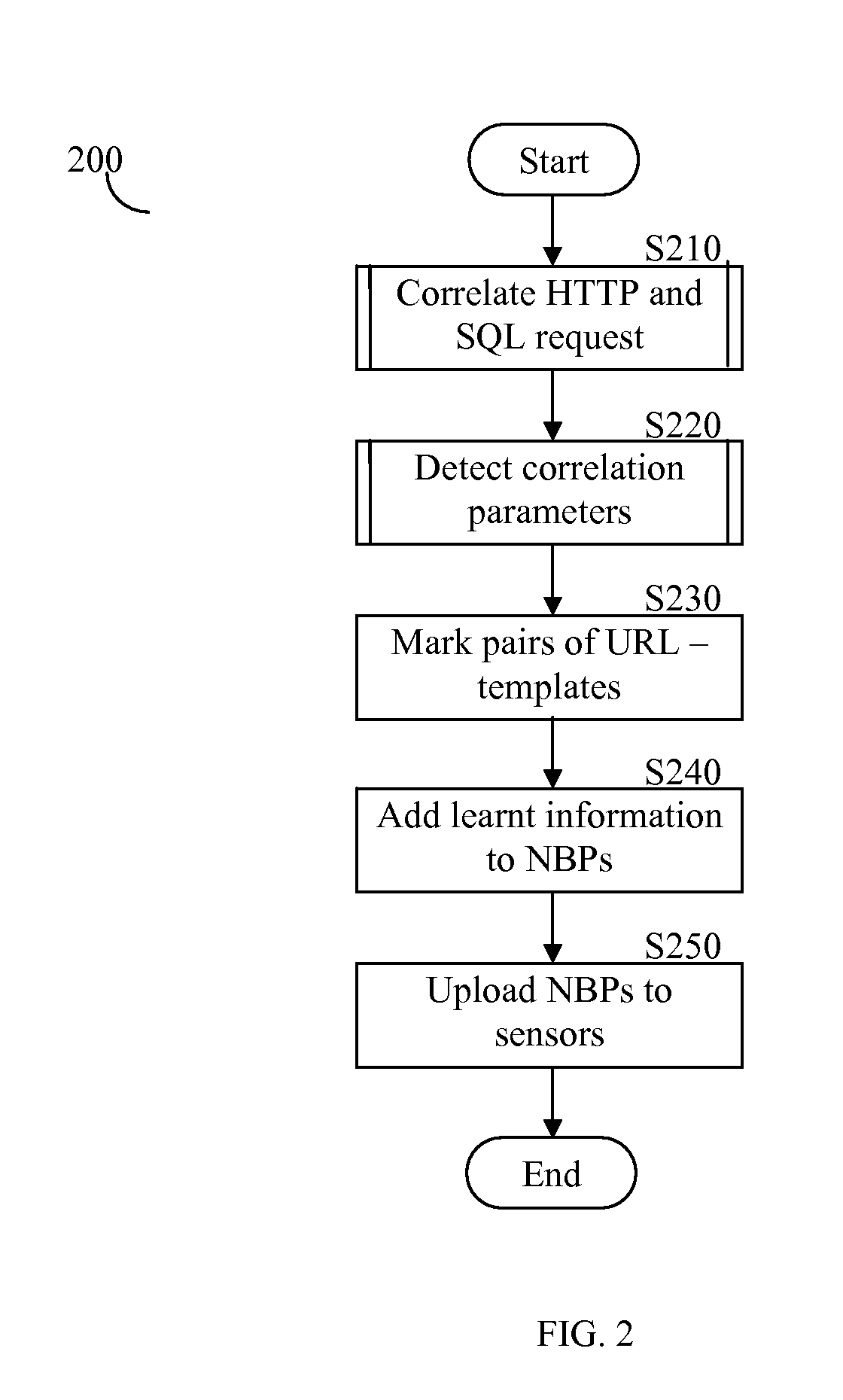
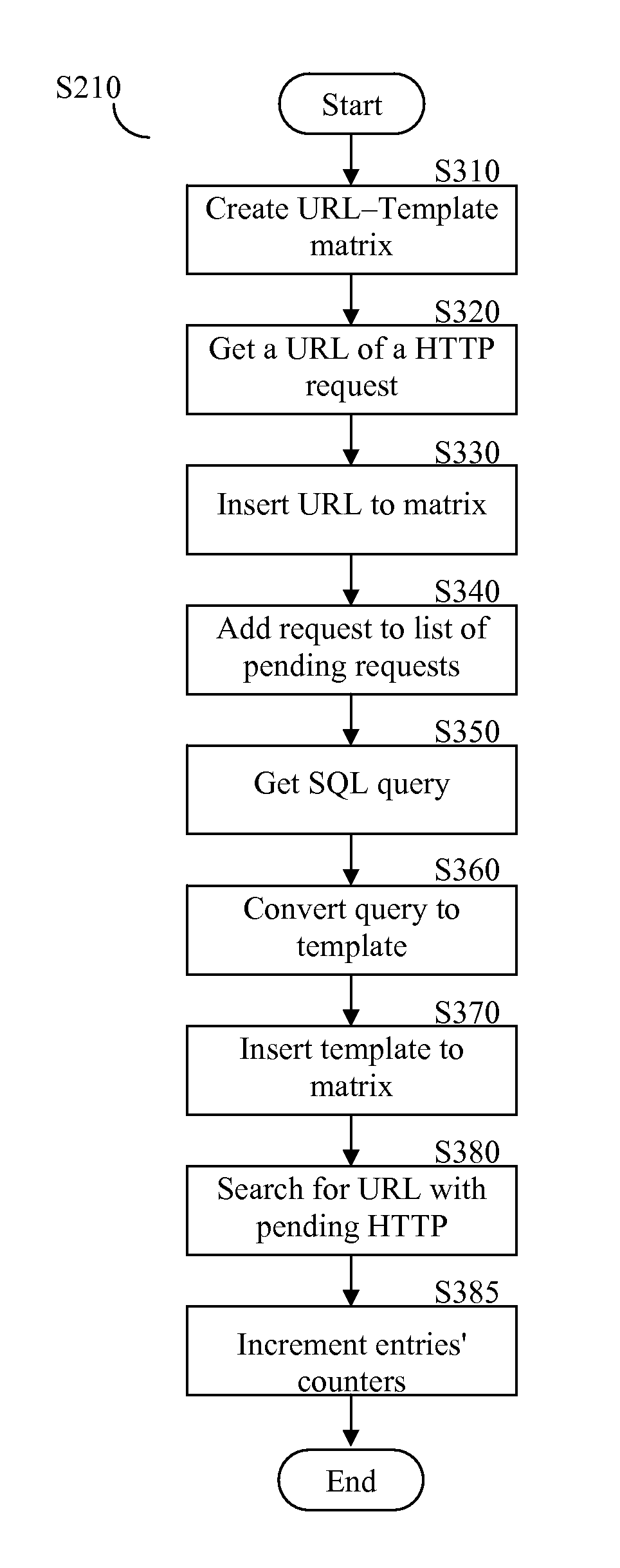
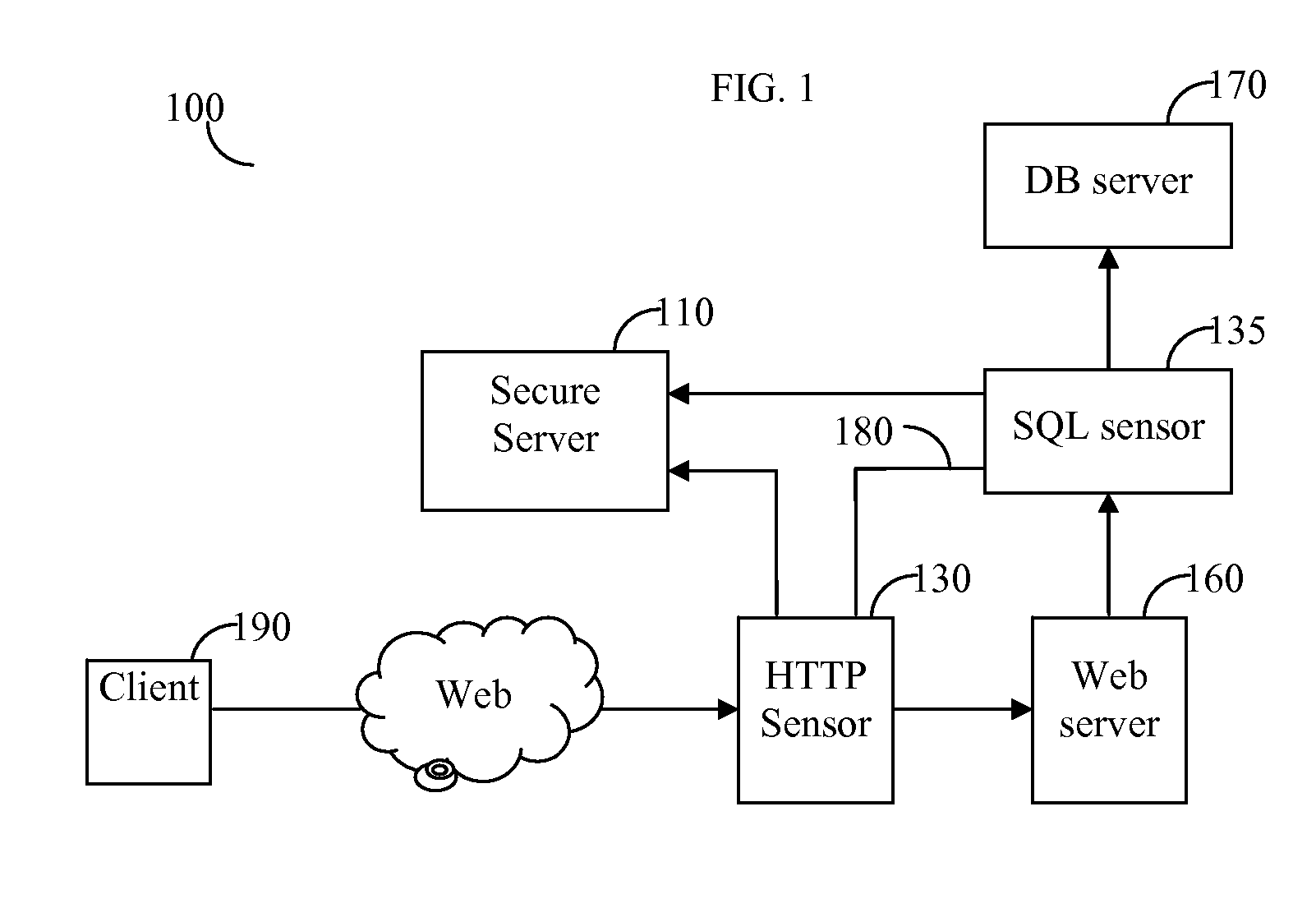
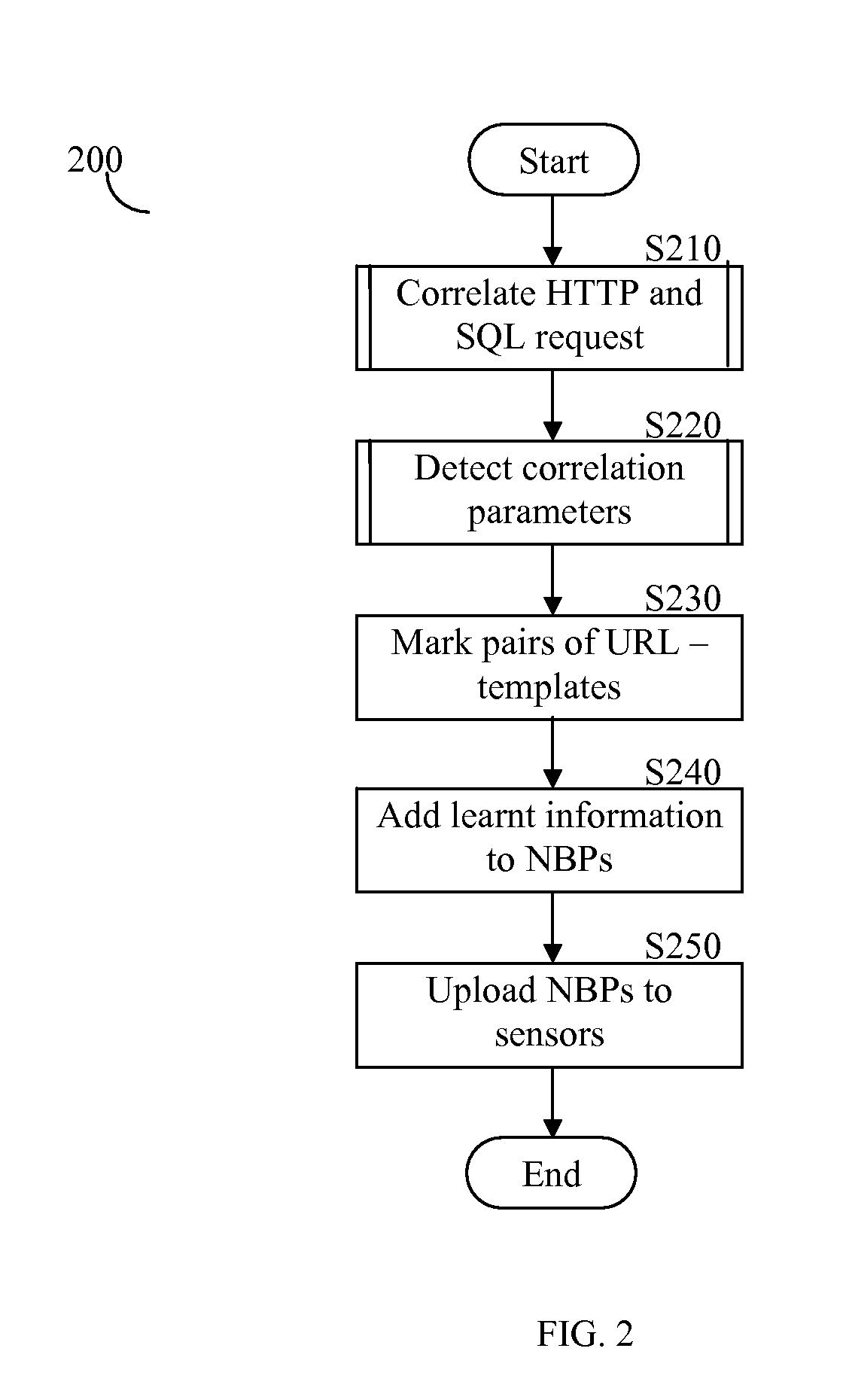
System and method for correlating between HTTP requests and SQL queries
ActiveUS20070136312A1Data processing applicationsWebsite content managementProtected modeUniform resource locator
The system and method correlate between hypertext transfer protocol (HTTP) requests and structured query language (SQL) queries. The system operates in two modes: learn mode and protect mode. In the learn mode, the system identifies pairs of uniform resource locators (URLs) and SQL templates, in addition to, pairs of correlation parameters and SQL queries. In the protect mode, for each incoming SQL query, the system binds to each submitted SQL query a session identifier (sessionID) of a corresponding HTTP request and the user identity of the user that submitted the query.
Owner:IMPERVA
SAR restart and going home procedures
Described are techniques used in performing data replication processing. Data is replicated on a recovery site from a production site. When a disaster occurs, the state of the replication processing is determined and a restart copy of the data is made available from the recover site. Processing continues based on whether protection mode is desired such that the system executes using the recovery site as the restart with a replicated copy of the data. Data is propagated from the recovery site to the production site to resume operations and replication processing originating from the production site.
Owner:EMC IP HLDG CO LLC
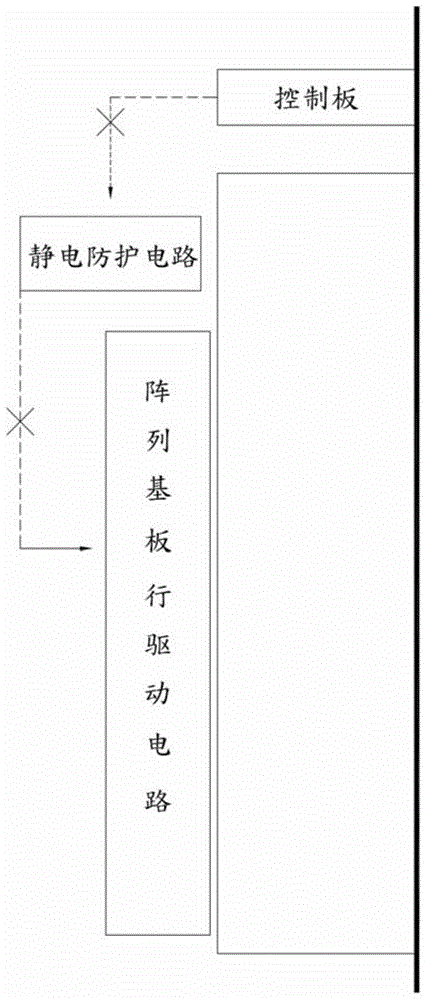
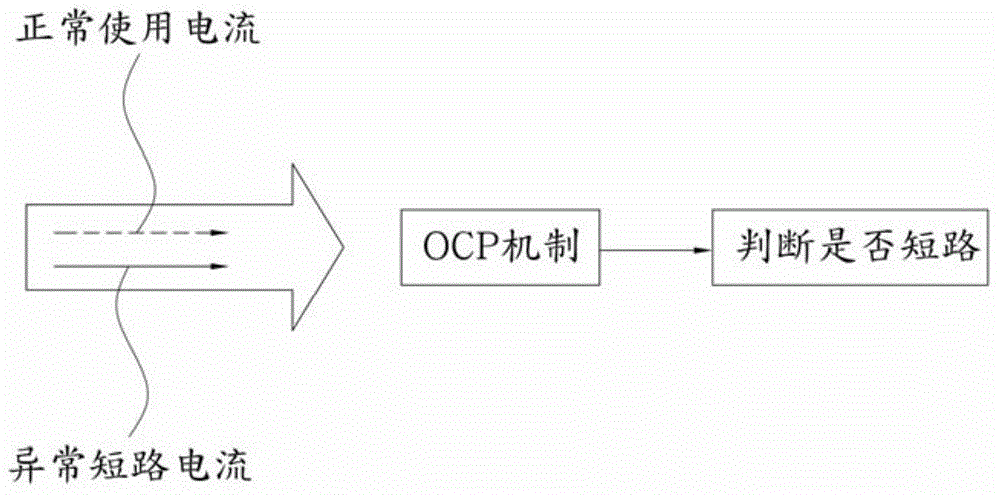
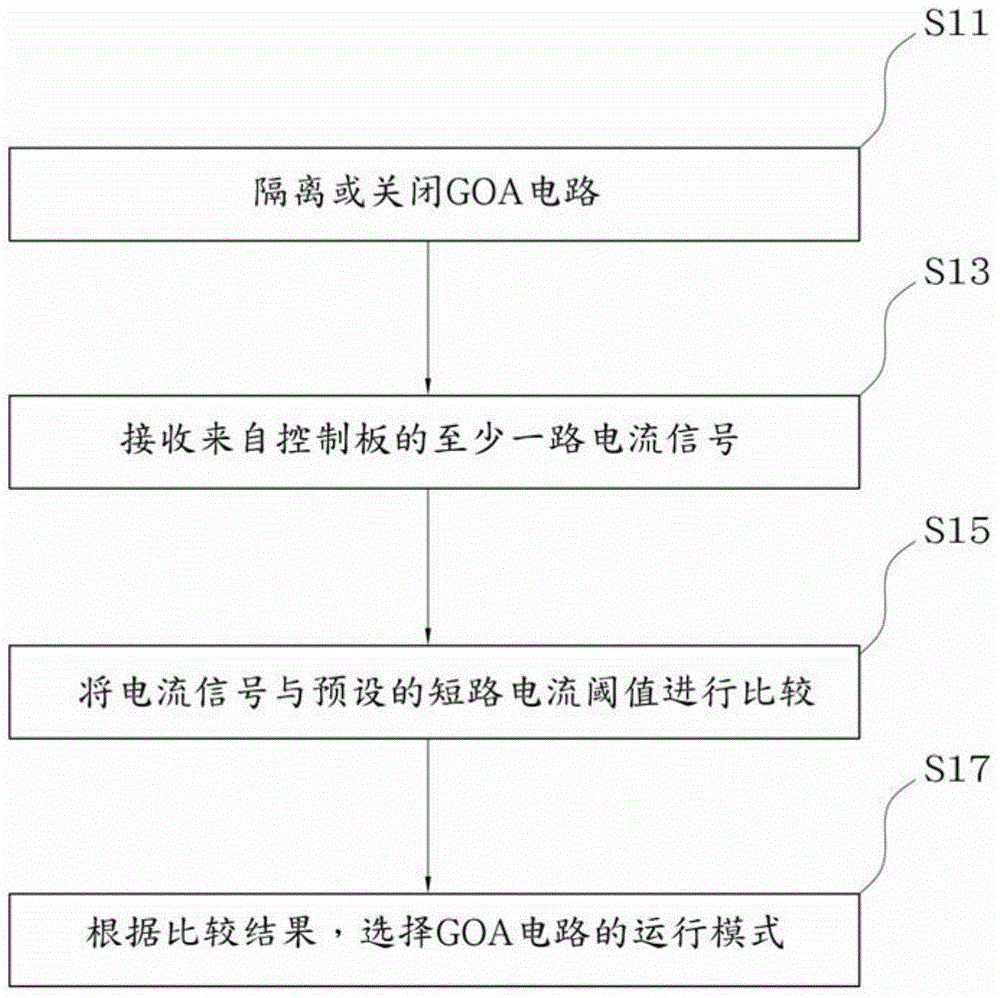
Driving control circuit and over-current protection method of GOA circuit thereof
InactiveCN104700811AImprove operational reliabilityAvoid accidental touch protection actionStatic indicating devicesCurrent thresholdOperation mode
The invention provides a driving control circuit and an over-current protection method of a GOA circuit thereof. The method comprises the steps of isolating or closing the GOA circuit; receiving at least one current signal from a control panel; comparing the current signal with a preset short circuit current threshold value; selecting the operation mode of the GOA circuit according to the comparison result; if the current signal is less than the short circuit current threshold, opening the GOA circuit to enter a normal working mode; if the current signal is more than or equal to the short circuit current threshold, keeping the GOA circuit closed to enter an over-current protecting mode. Compared with the prior art, the method has the advantages that the GOA circuit can be delayed to open or close, so that the short circuit protection mechanism can independently determine whether each current signal of the control plate exceeds the short circuit current threshold, the mistaken touch protection action caused by different current due to different plane display mode / three-dimensional display mode and different temperature can be avoided, and as a result, the operation reliability of the GOA circuit can be improved.
Owner:AU OPTRONICS CORP
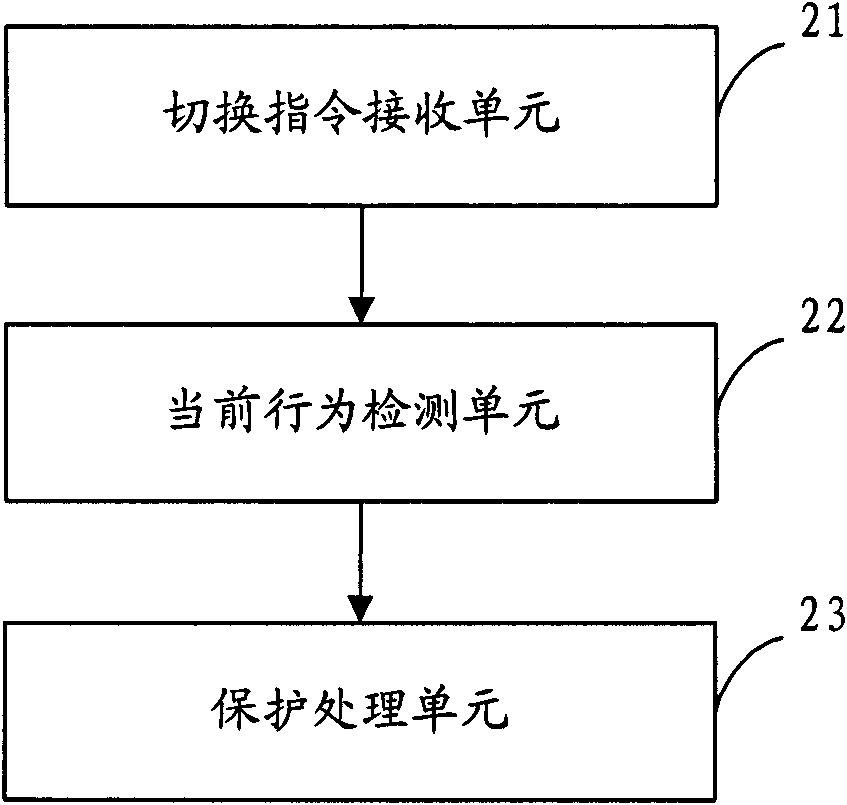
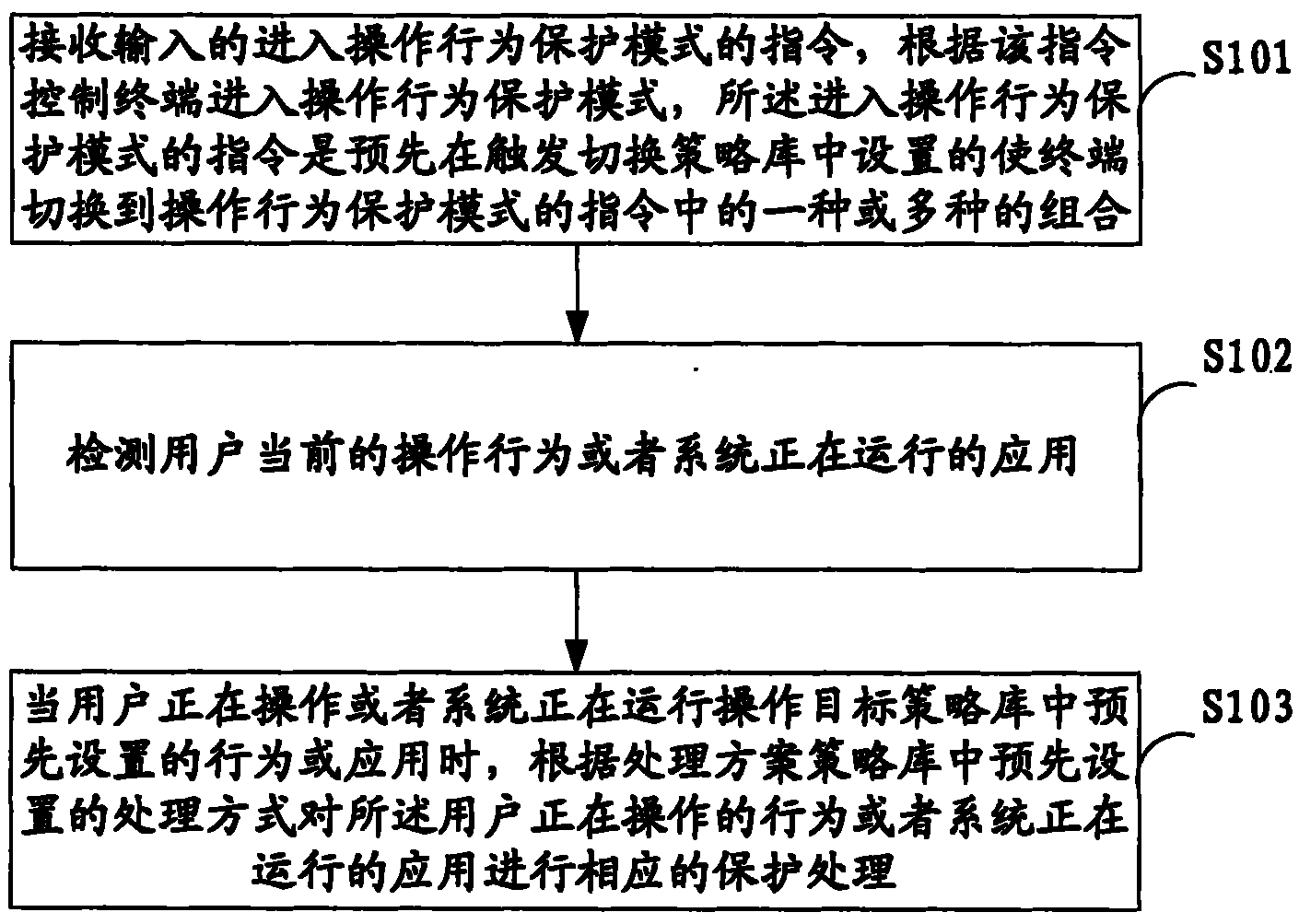
Method and device for protecting user behavior at operating terminal
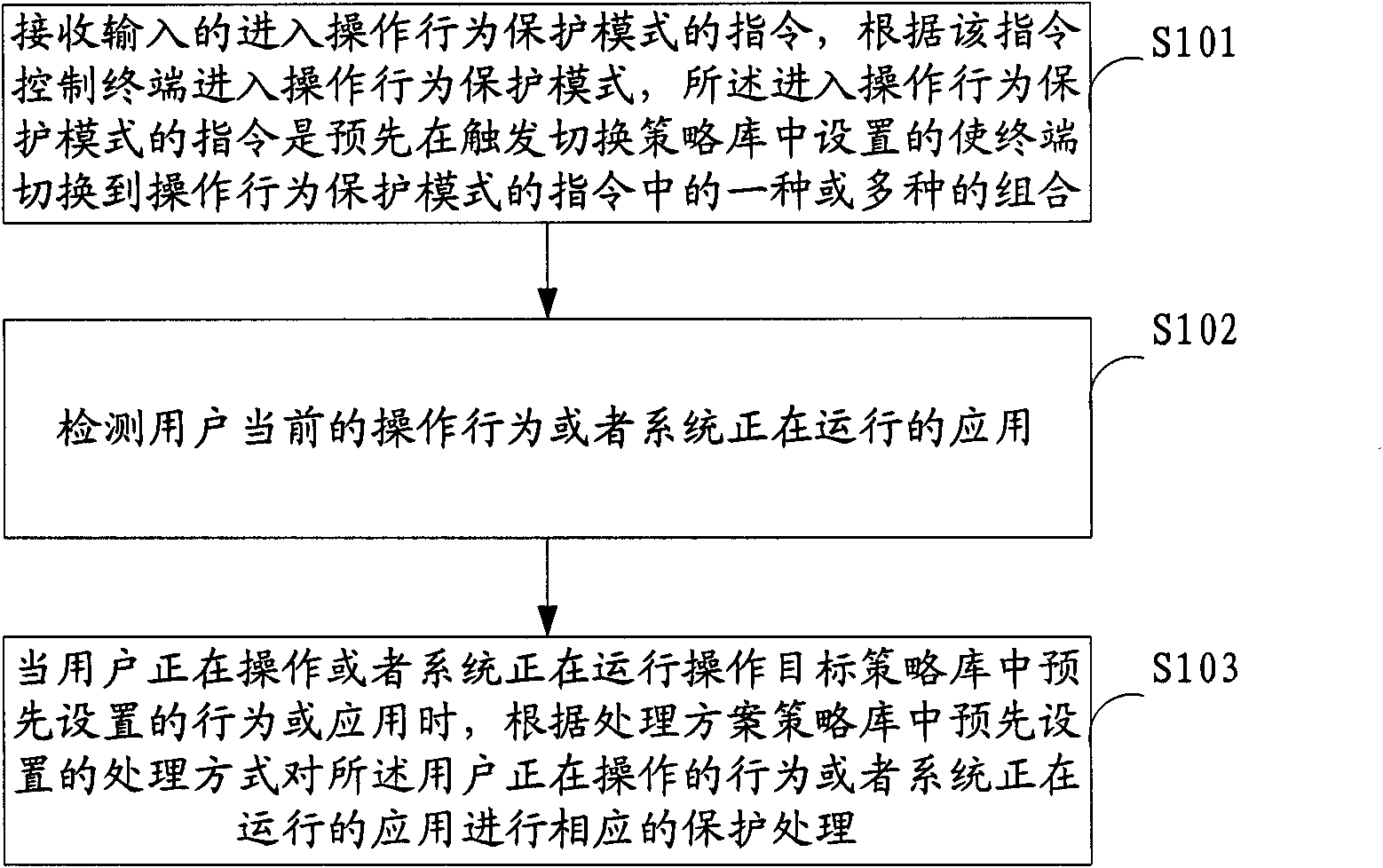
InactiveCN101867650ASolve the problem of manual deletionProtect operation terminal behaviorSubstation equipmentProtected modeElectrical and Electronics engineering
The invention, applicable to the technical field of communication, provides a method and a device for protecting the user behavior at an operating terminal. The method comprises the following steps: receiving an inputted instruction for entering an operating behavior protection mode, and controlling a terminal to enter the operating behavior protection mode according to the instruction, wherein the instruction for entering the operating behavior protection mode is particularly one instruction or the combination of various instructions preset in a triggering / switching strategy library for switching the terminal to the operating behavior protection mode; detecting the current operating behavior of a user or the application run by a system; and carrying out the corresponding protection treatment on the current operating behavior of the user of the application run by the system according to the treatment mode preset in the treatment scheme strategy library when the behavior or application preset in an operating target strategy library is operated by the user and run by the system. Accordingly, the invention can carry out the personalized data protection on the operating behavior of the user and various applications run by the system, thus ensuring higher expandability and flexibility.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
SAR restart and going home procedures
Owner:EMC IP HLDG CO LLC
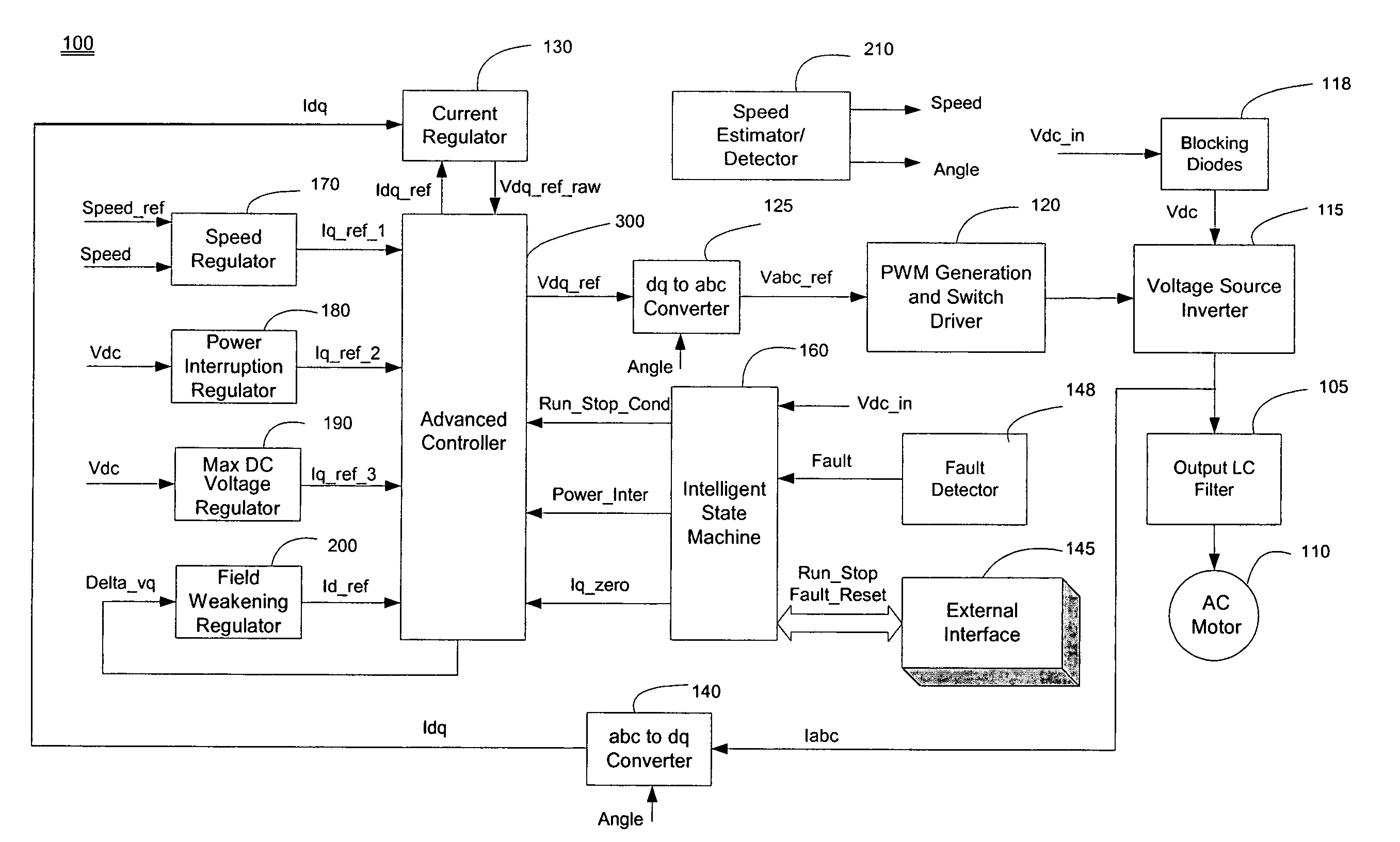
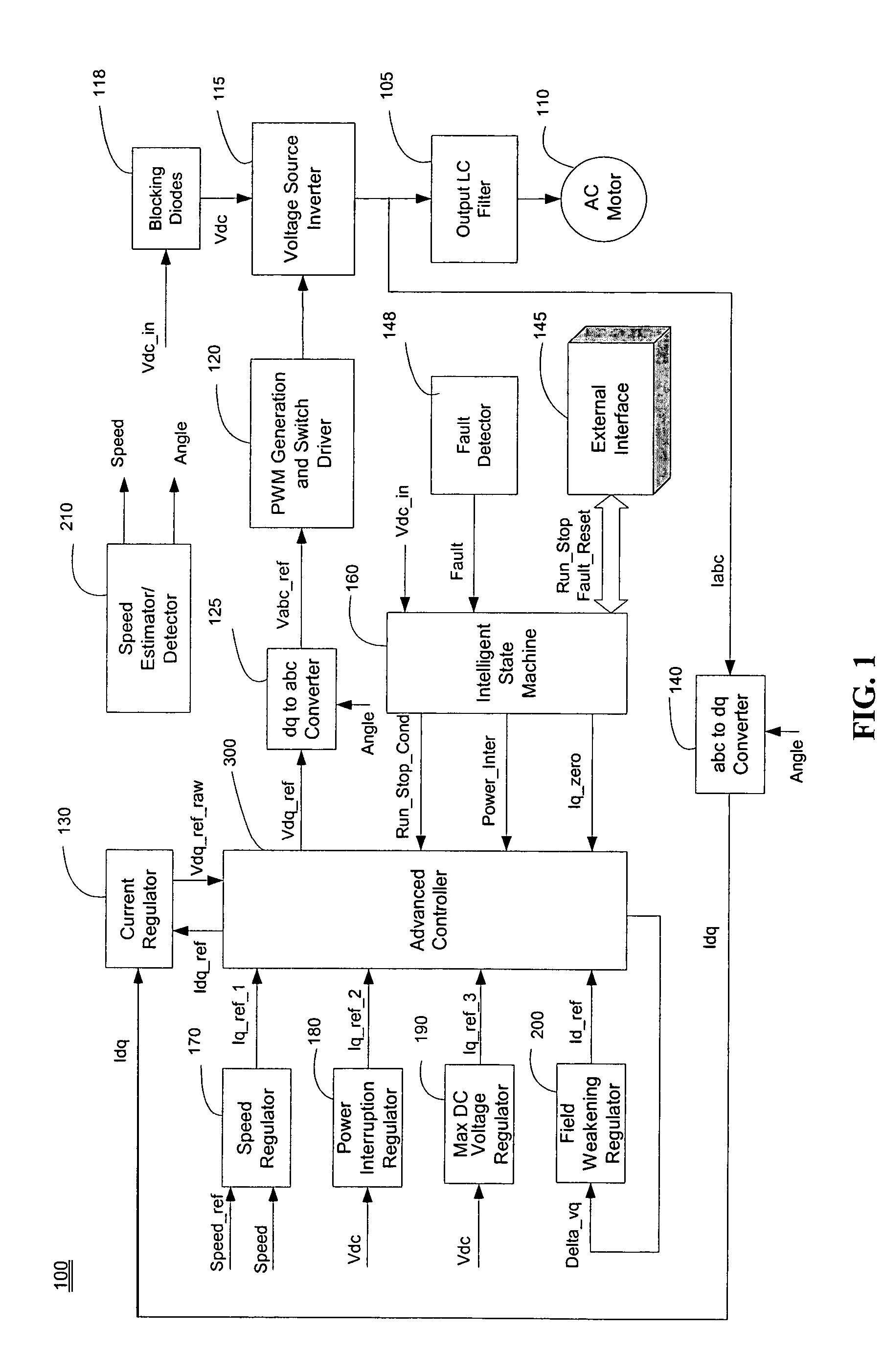
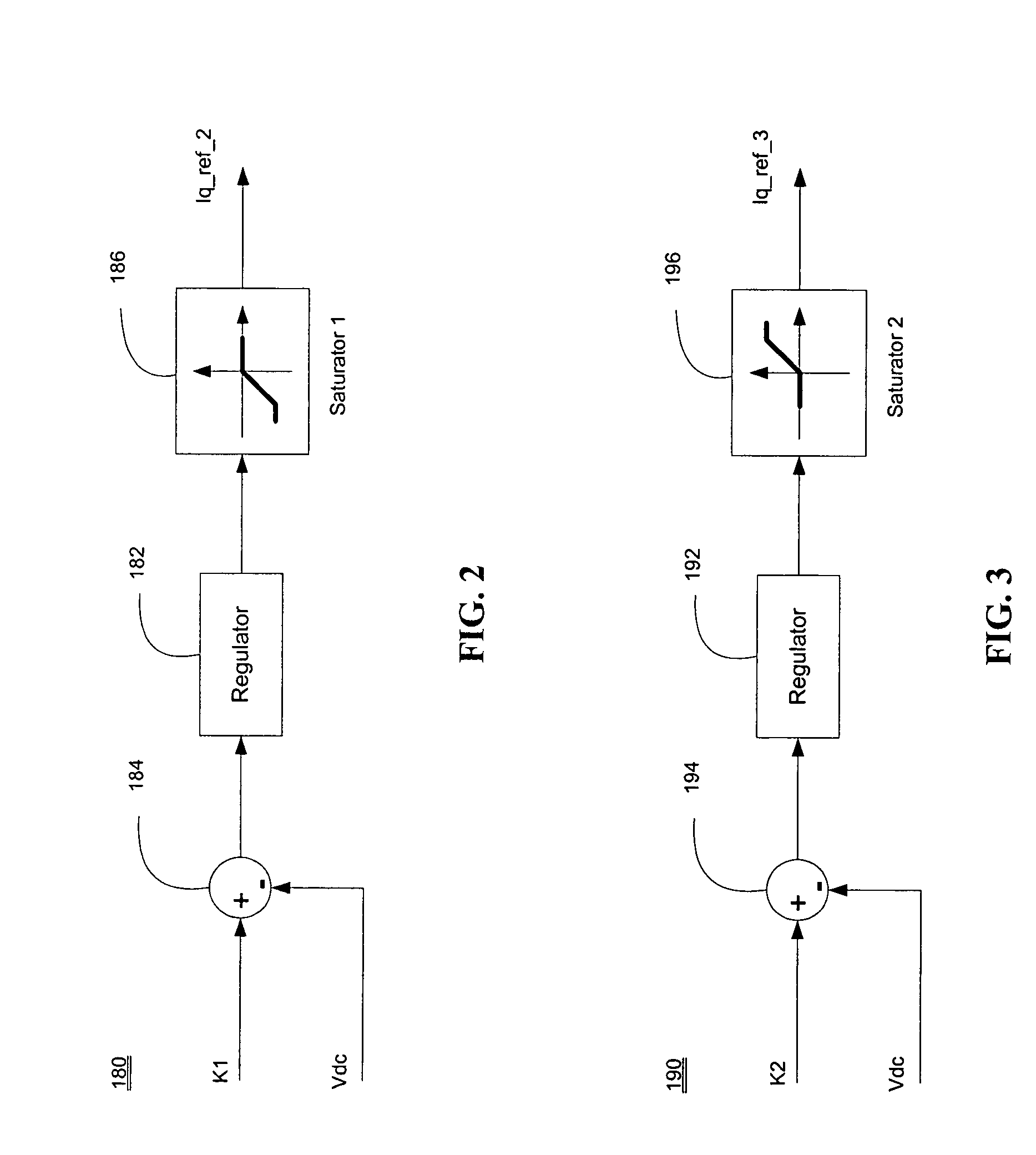
Advanced current control method and apparatus for a motor drive system
An apparatus controls a power converter of an AC motor drive system, the power converter outputting multi-phase AC current to an AC motor. The apparatus comprises: a state selecting unit; and an advanced controller. The state selecting unit selects an operation mode, from among a plurality of operation modes, for the AC motor based on system real-time operating conditions, the plurality of operation modes including a normal mode, a power interruption mode, a fault protection mode, and a power-up / down dynamic mode. The system operating conditions include DC voltage available to the power converter, motor load condition, and motor speed command. The advanced controller controls multi-phase AC current output from the power converter to the motor in accordance with the operation mode selected by the state selecting unit. The advanced controller generates a current control reference value that is based on the selected operation mode to achieve current control under various operating conditions of the motor drive system.
Owner:HONEYWELL INT INC
Drive method for embedded apparatus
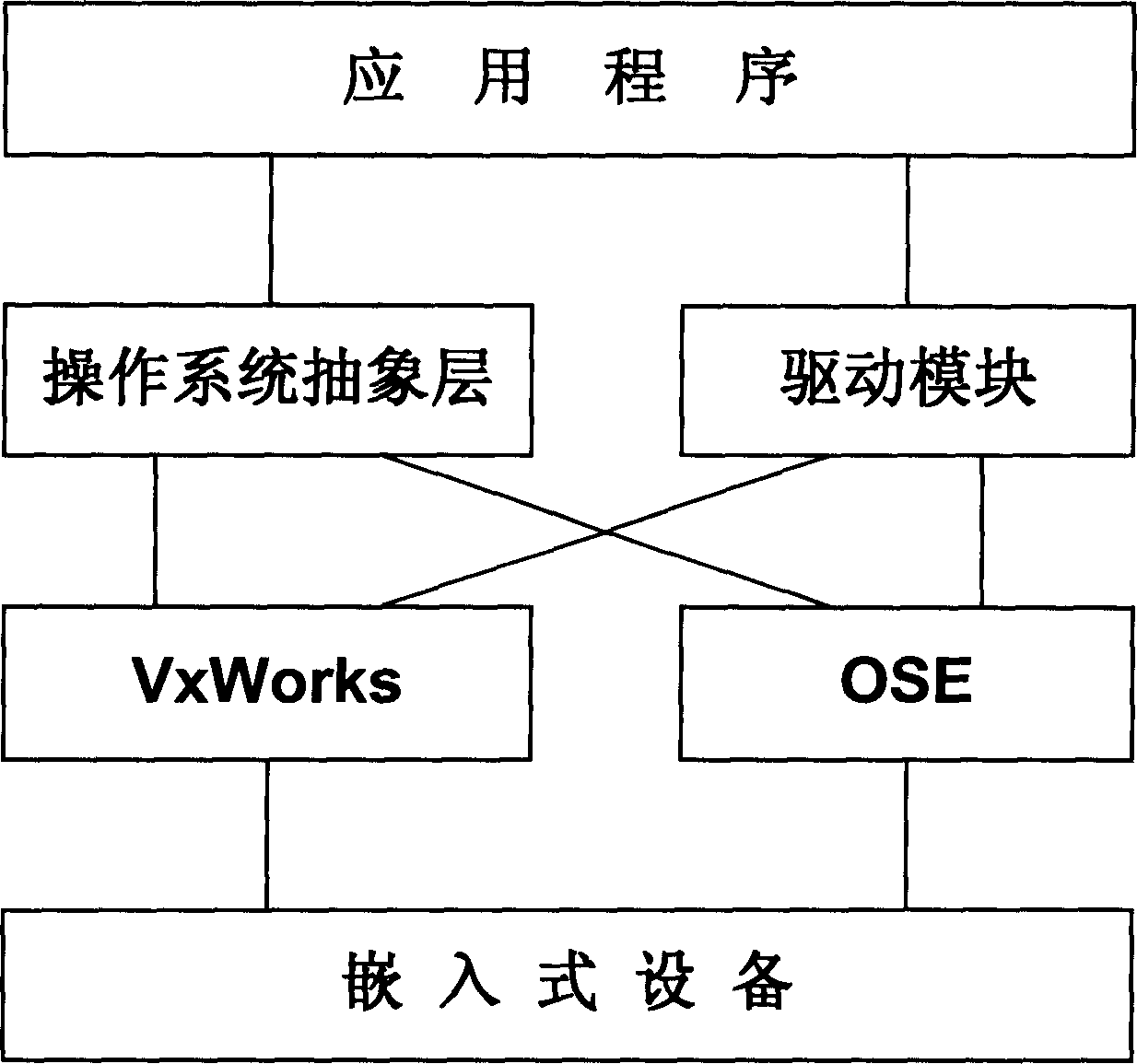
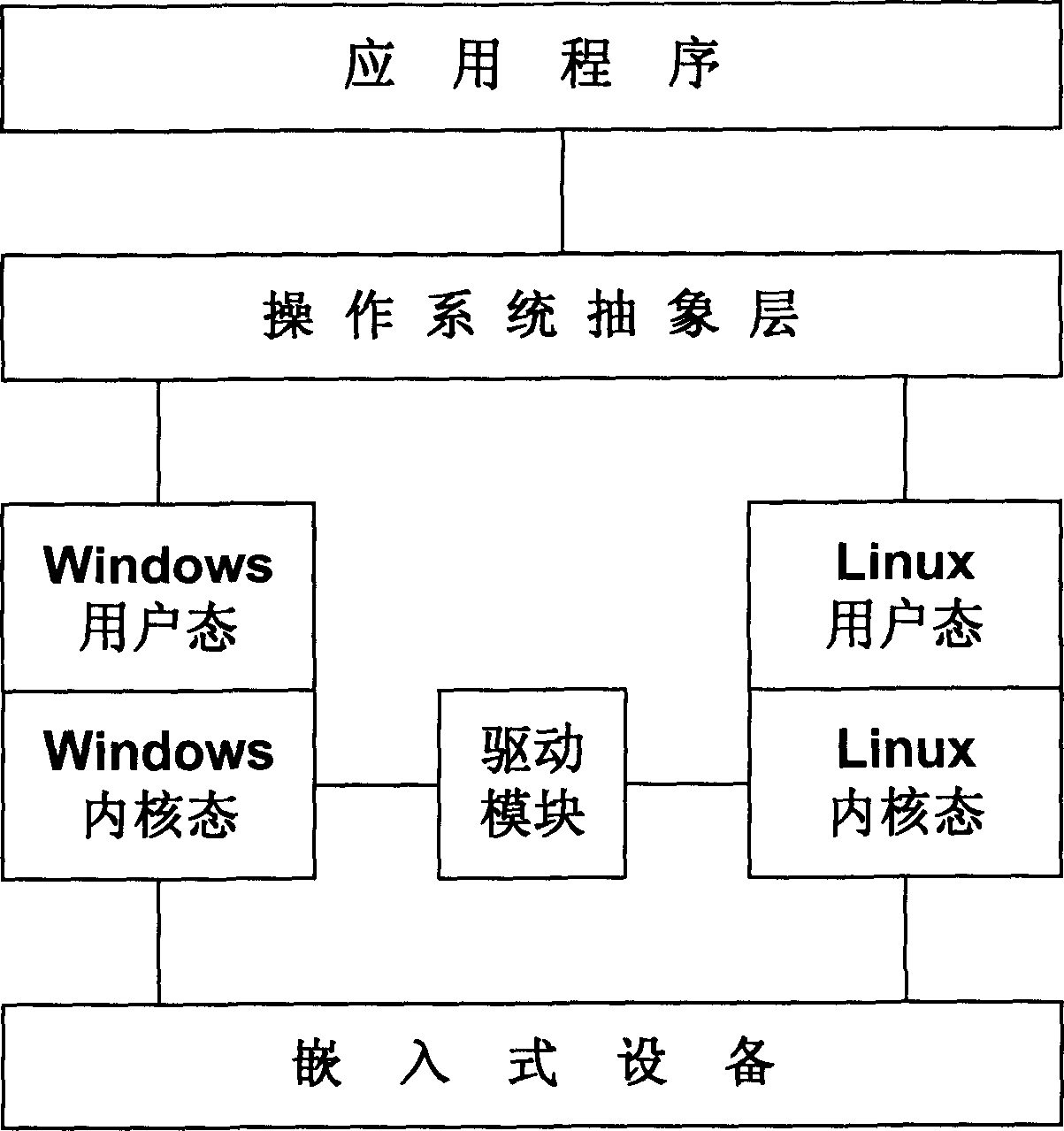
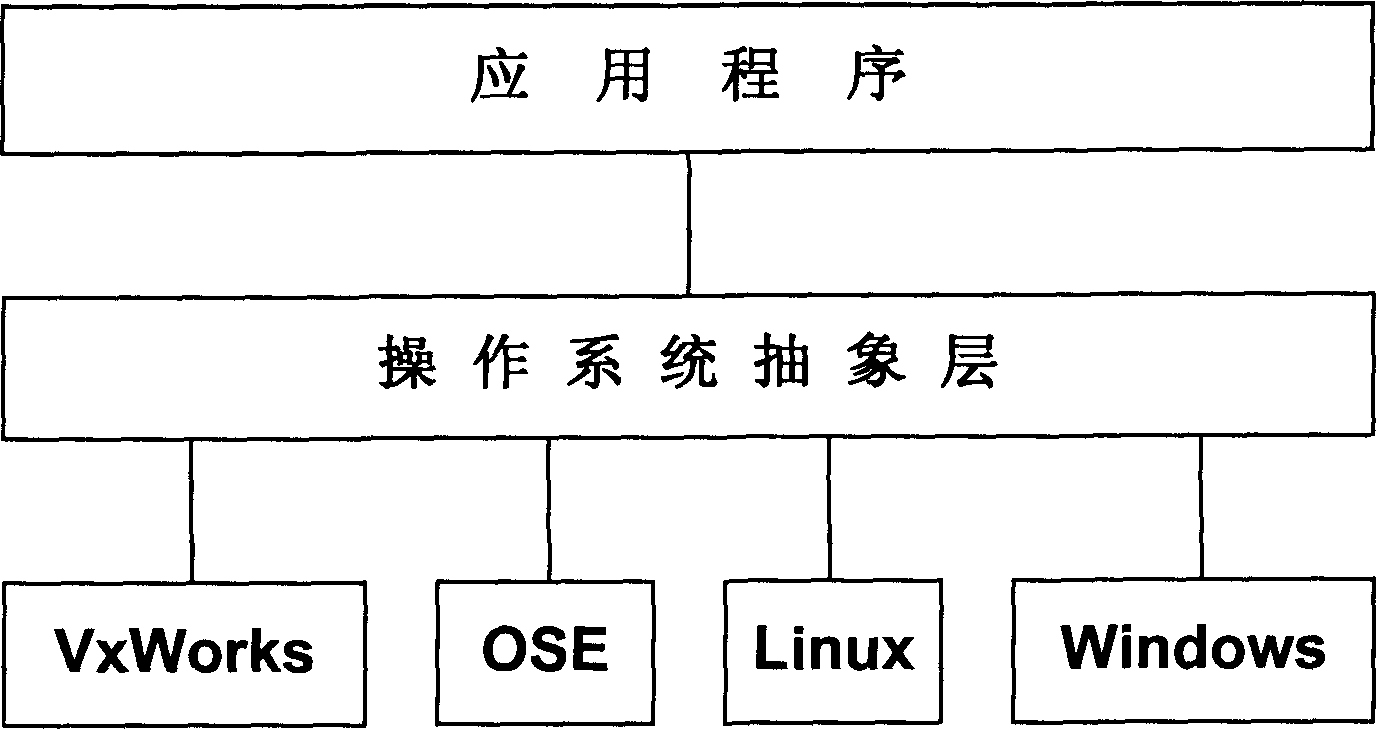
ActiveCN1866202AReduce switching timesImprove operational efficiencySpecific program execution arrangementsInformation controlOperational system
The disclosed drive method for embedded device in protective-mode OS comprises: packing application program of different OS into uniform OS abstract interface function; registering the embedded device as OS-supported virtual device to build the mapping between virtual device kernel-state memory space and drive mode user-state memory space; calling the drive module and OS interface function by application program to interact with the embedded device for information control and / or data by memory mapping. This invention improves system running efficiency.
Owner:DATANG MOBILE COMM EQUIP CO LTD
System and method for correlating between HTTP requests and SQL queries
ActiveUS7640235B2Data processing applicationsWebsite content managementProtected modeUniform resource locator
The system and method correlate between hypertext transfer protocol (HTTP) requests and structured query language (SQL) queries. The system operates in two modes: learn mode and protect mode. In the learn mode, the system identifies pairs of uniform resource locators (URLs) and SQL templates, in addition to, pairs of correlation parameters and SQL queries. In the protect mode, for each incoming SQL query, the system binds to each submitted SQL query a session identifier (sessionID) of a corresponding HTTP request and the user identity of the user that submitted the query.
Owner:IMPERVA
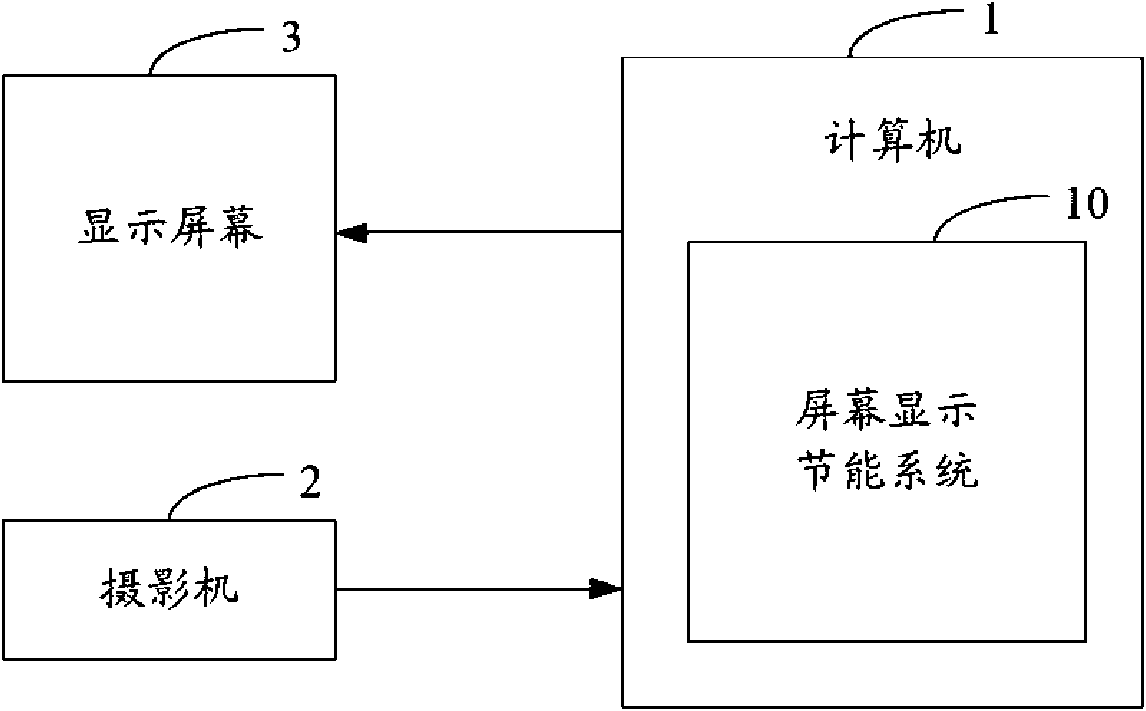
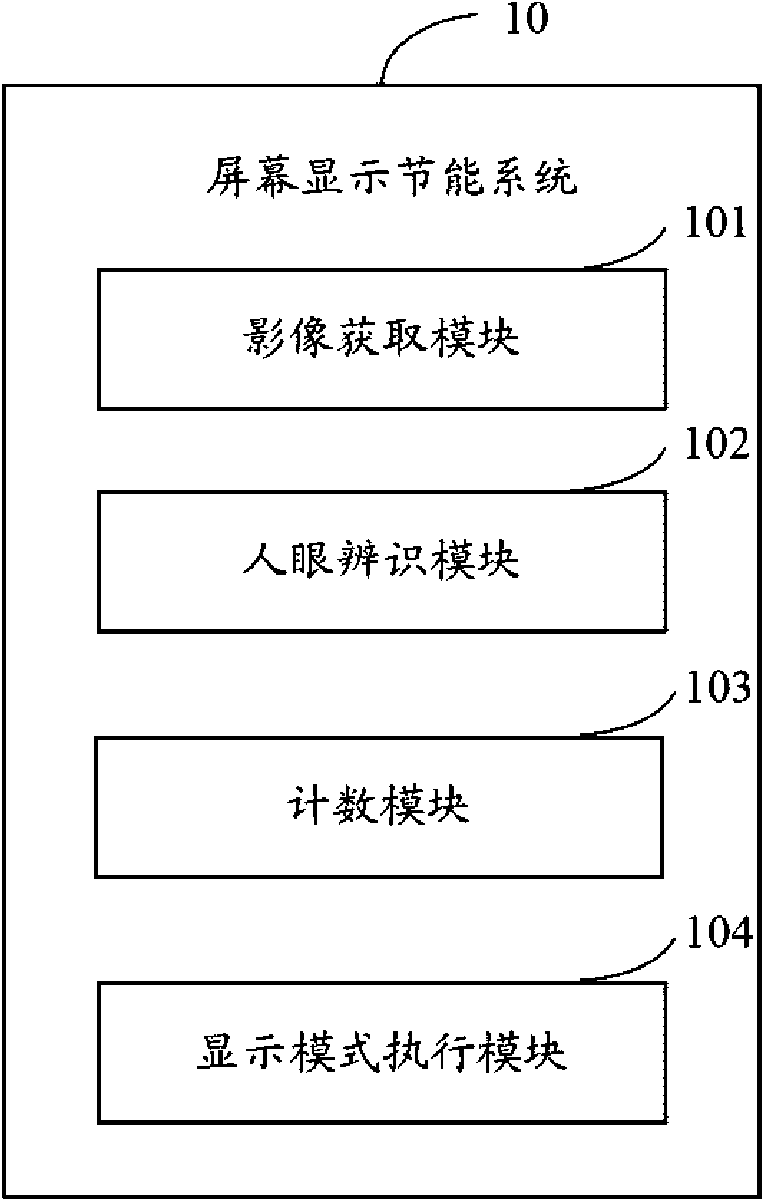
Energy saving system and method for screen display
InactiveCN101656060AAvoid the pitfalls of how long it has not been used as a benchmarkCathode-ray tube indicatorsProtected modeComputer science
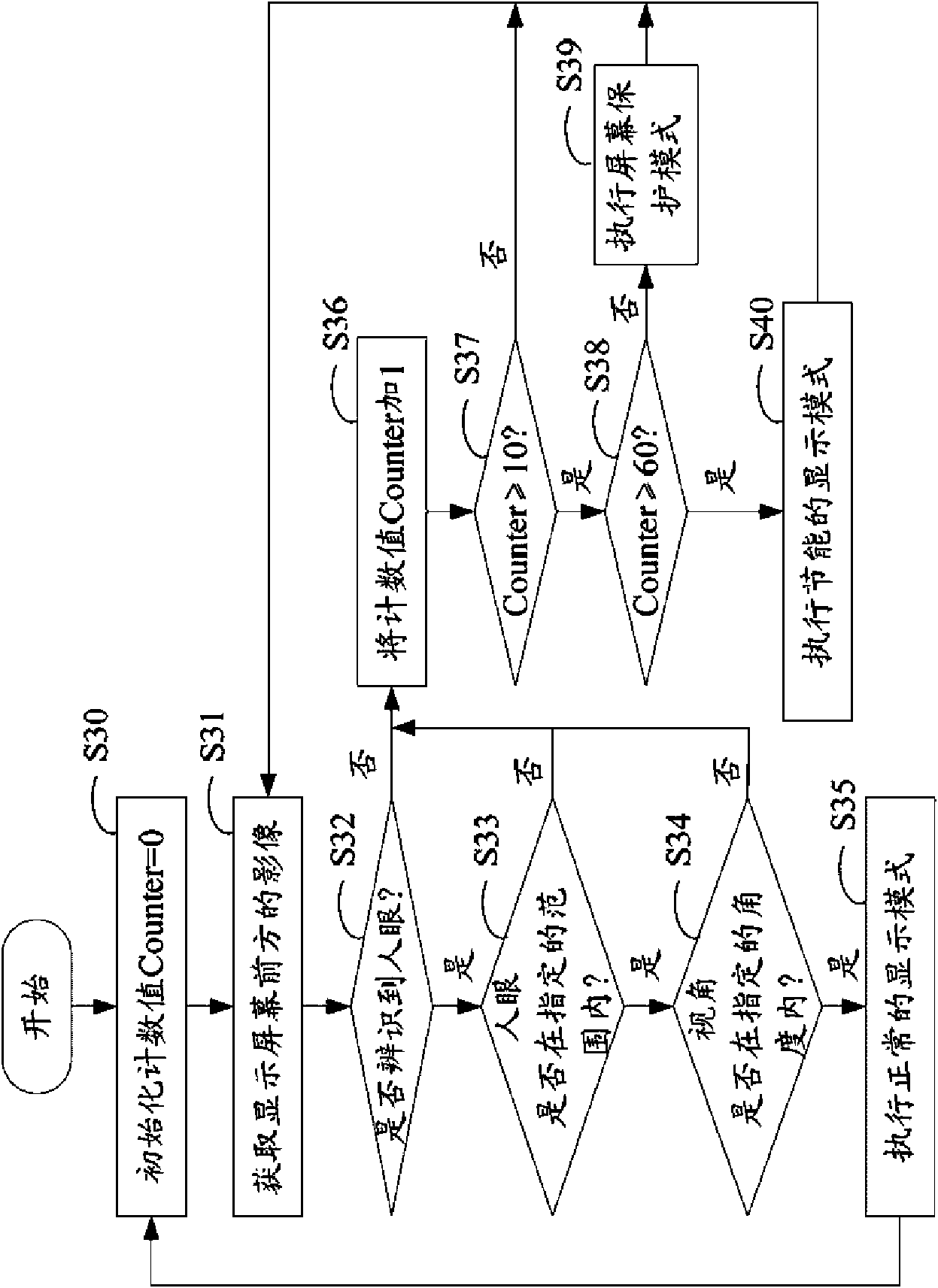
The invention provides an energy saving system and a method for screen display. The method comprises the following steps: setting and initializing a counter; starting a camera to obtain the images inthe specified range in front of the display screen; judging whether the human eyes watch the display screen; if yes, selecting the normal display mode for the display screen; if no, adding 1 second tothe counter every 1 second and detecting the counter in real time, if the counter is less than the first preset time, selecting the normal display mode for the display screen; if the counter is morethan or equal to the first preset time but less than the second preset time, selecting the screen saver mode for the display screen; if the counter is more than or equal to the second preset time, selecting the energy saving mode for the display screen and automatically turning off the display screen. Being implemented, the invention can enable the display screen to be in the energy saving state in real time by tracking the positions of the human eyes.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Mobile device loss prevention
ActiveUS8634808B1Electric signal transmission systemsUnauthorised/fraudulent call preventionValidation methodsProtected mode
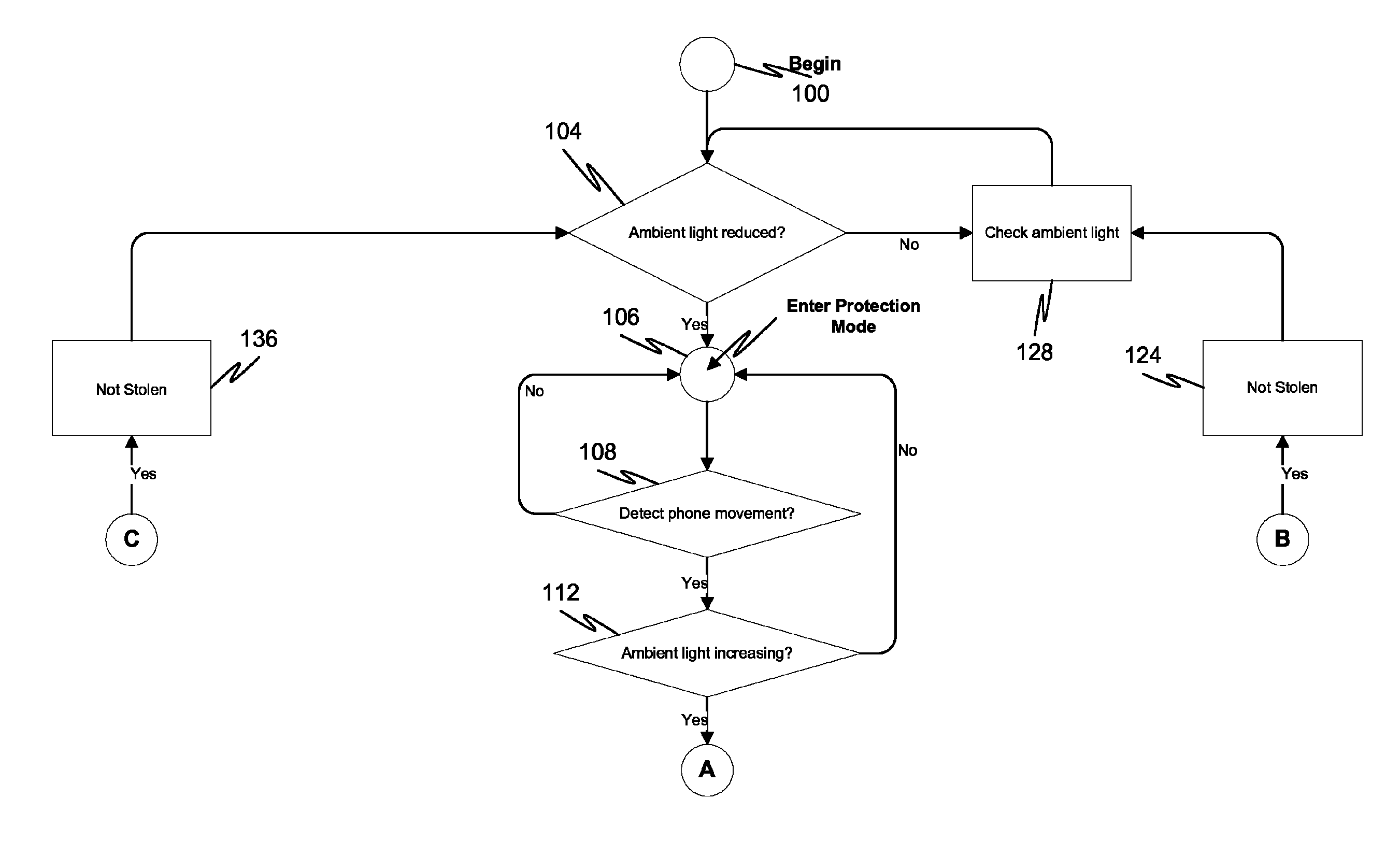
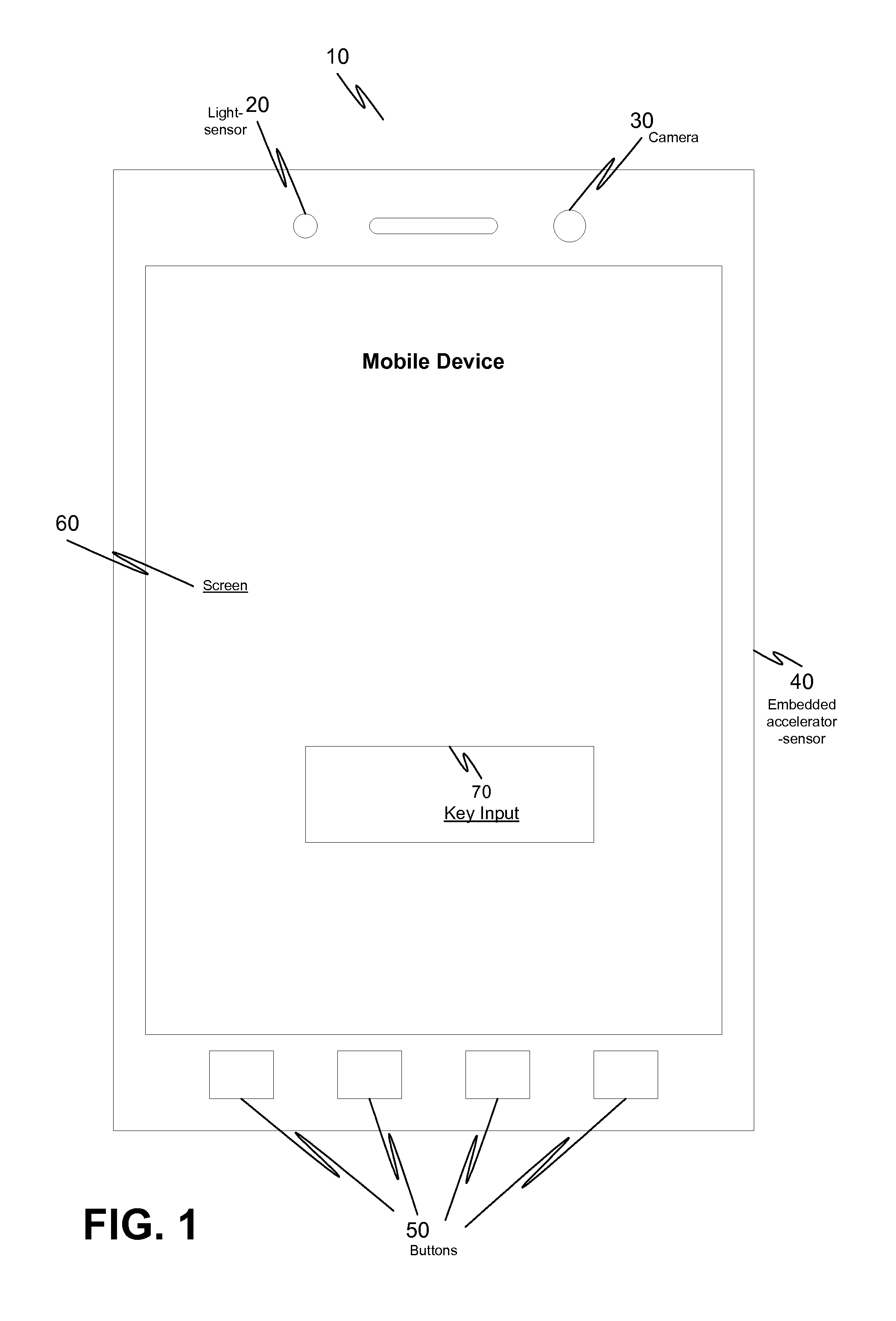
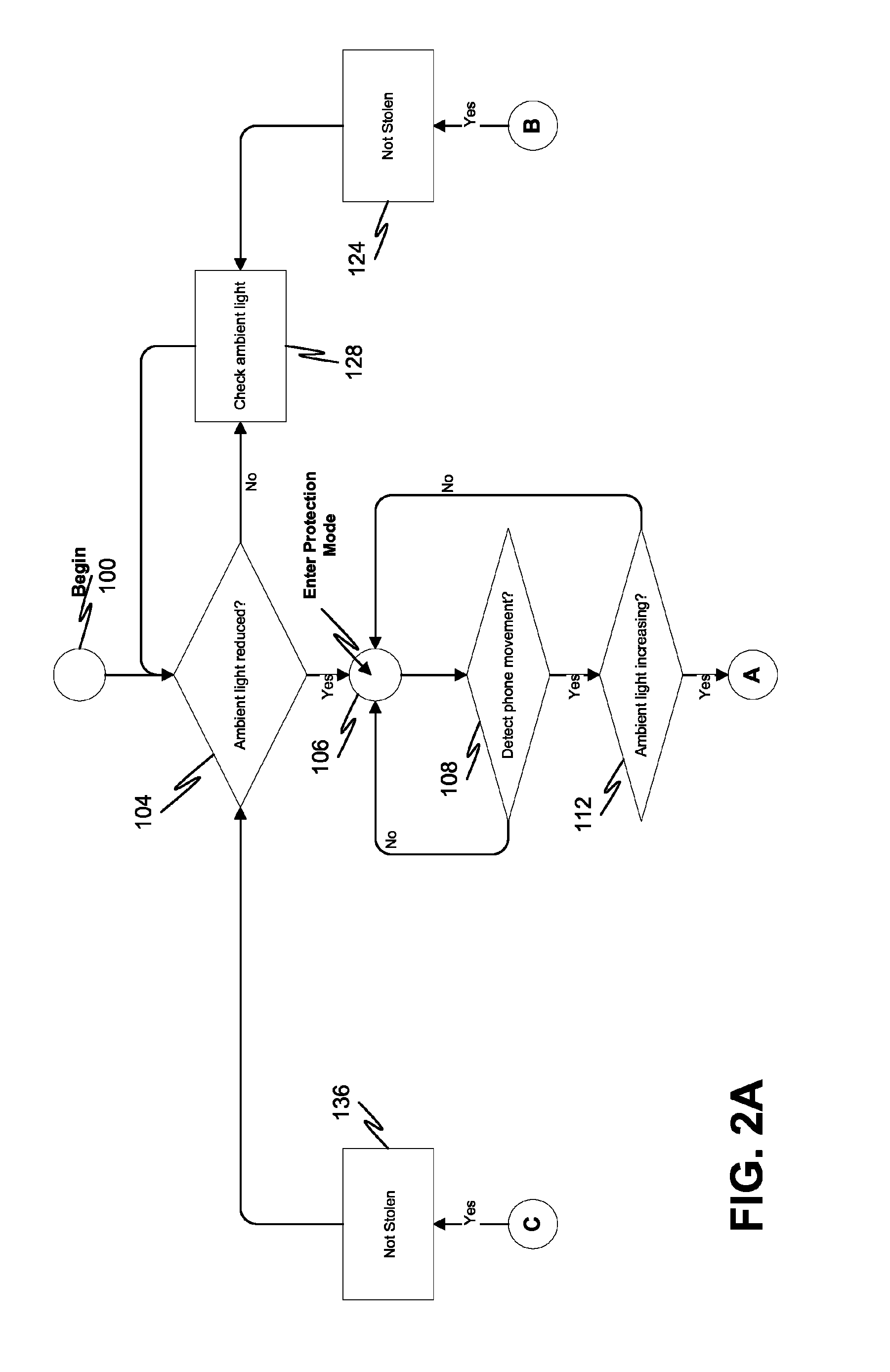
Collected information is analyzed by the mobile device to determine whether the device is displaced from the owner. The mobile device monitors and detects a reduction of ambient light to automatically enter into protection mode without manual activation. If an increase of ambient light and movement of the mobile device are both detected, then the device enters into authentication mode. Various techniques to verify the user's identity may be implemented in authentication mode. The user must correctly match an input key code, button combination, or an image recognition photograph against the stored information according to the method of verification chosen in each respective process. An alarm is activated if the device determines authentication is not received but may be disabled when the user's identity is verified after another authentication attempt.
Owner:TREND MICRO INC
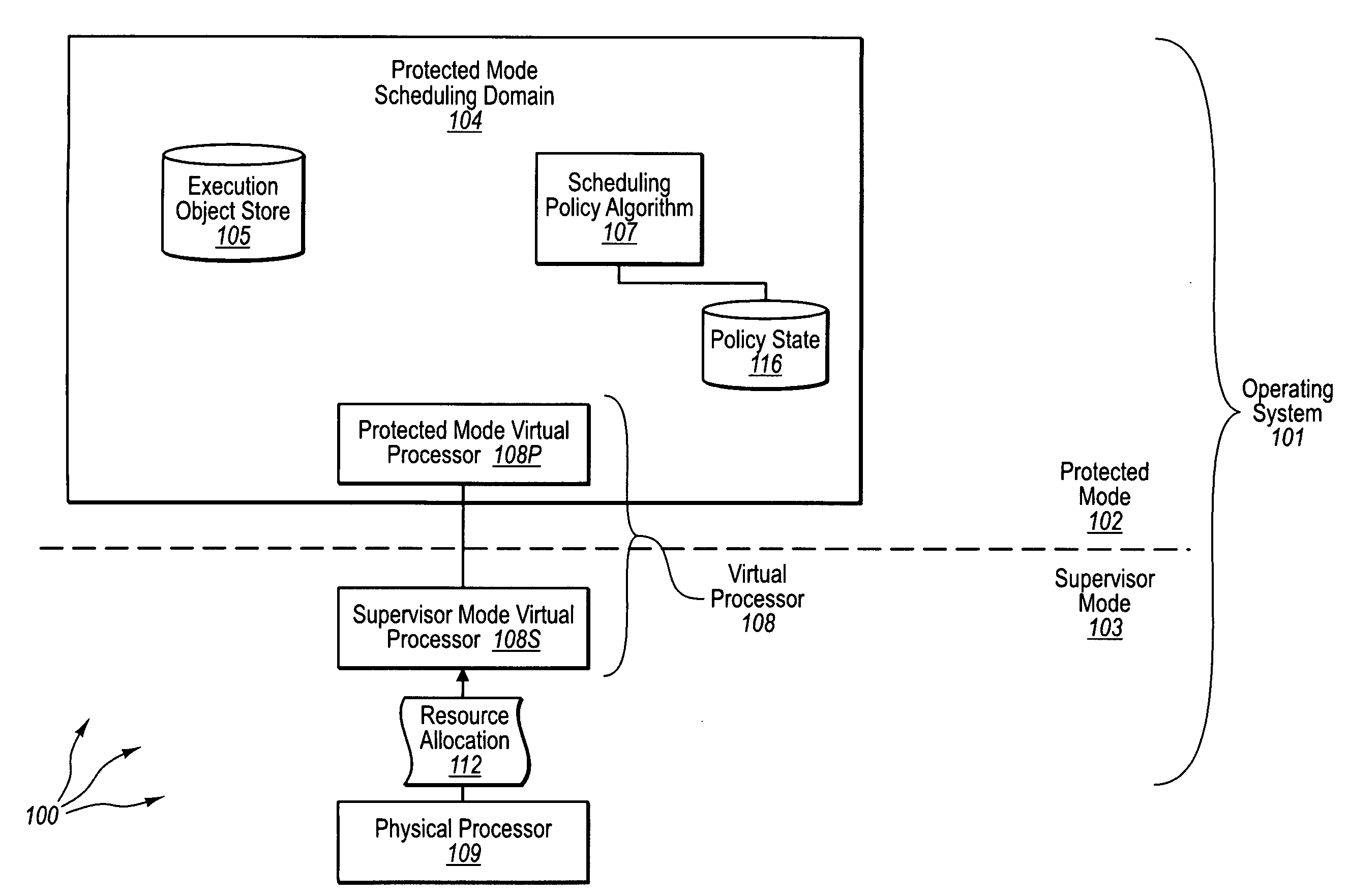
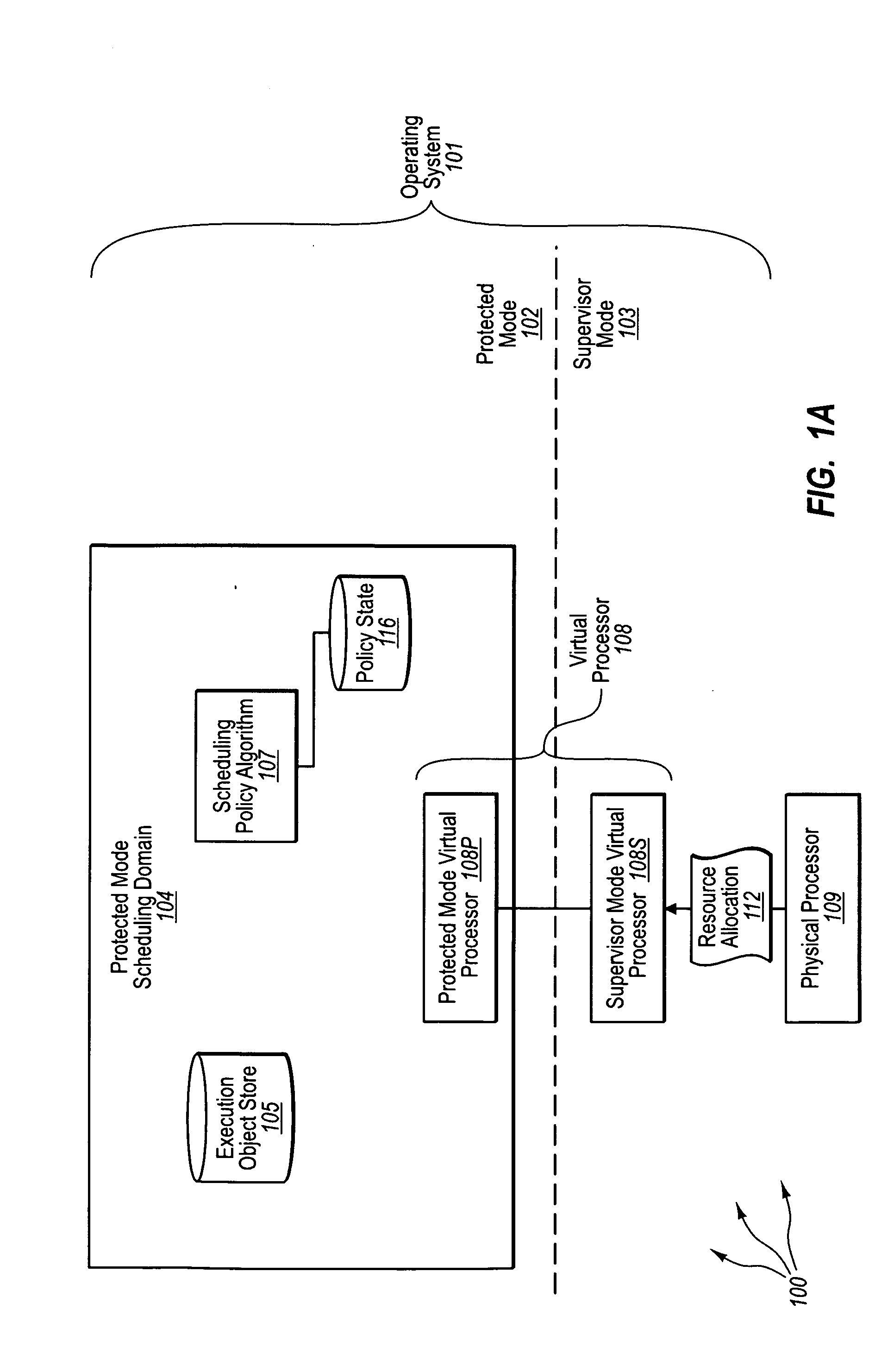
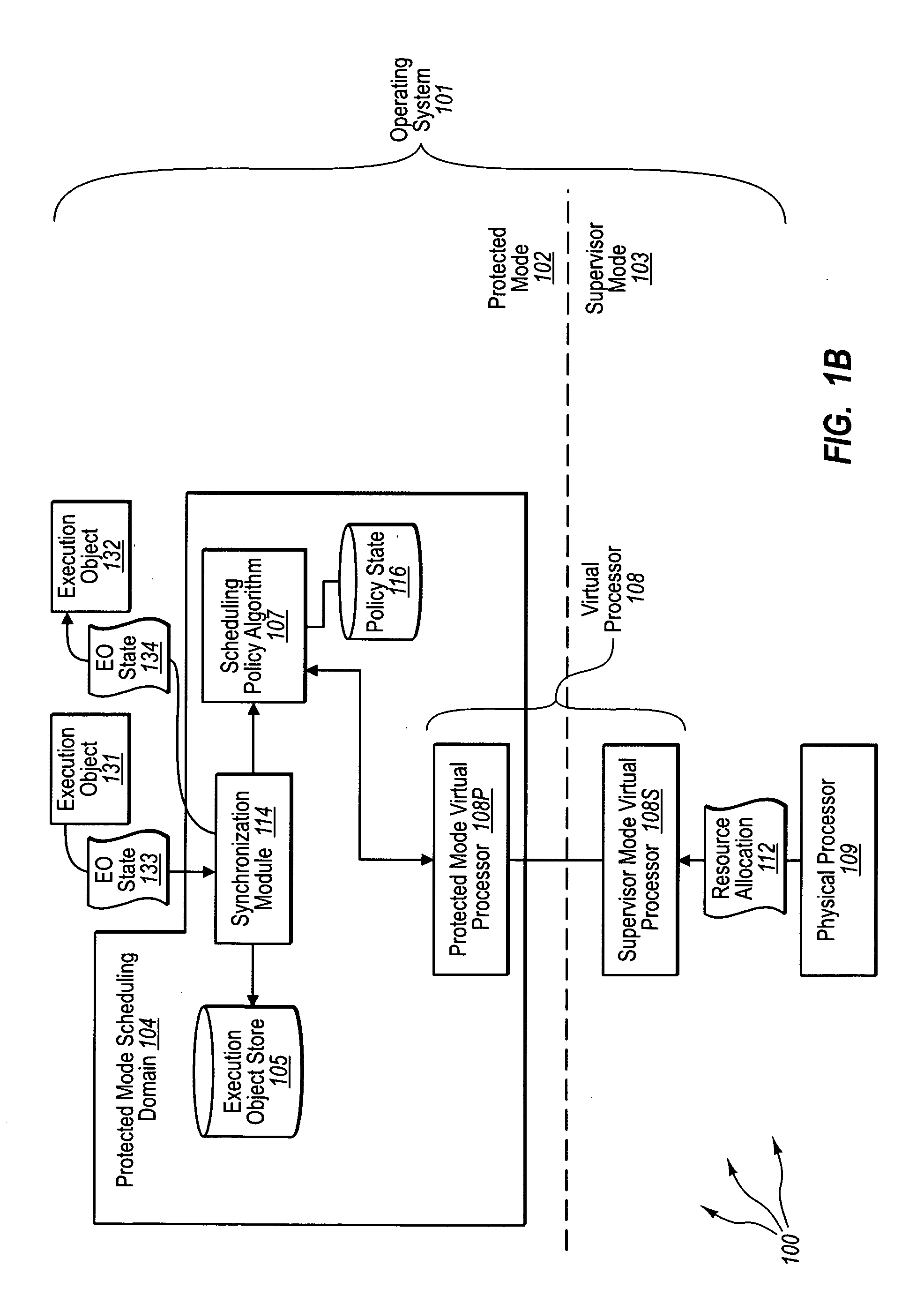
Protected mode scheduling of operations
ActiveUS20090328058A1Facilitates switching contextEasy to switchMultiprogramming arrangementsMemory systemsScheduling functionProtected mode
The present invention extends to methods, systems, and computer program products for protected mode scheduling of operations. Protected mode (e.g., user mode) scheduling can facilitate the development of programming frameworks that better reflect the requirements of the workloads through the use of workload-specific execution abstractions. In addition, the ability to define scheduling policies tuned to the characteristics of the hardware resources available and the workload requirements has the potential of better system scaling characteristics. Further, protected mode scheduling decentralizes the scheduling responsibility by moving significant portions of scheduling functionality from supervisor mode (e.g., kernel mode) to an application.
Owner:MICROSOFT TECH LICENSING LLC
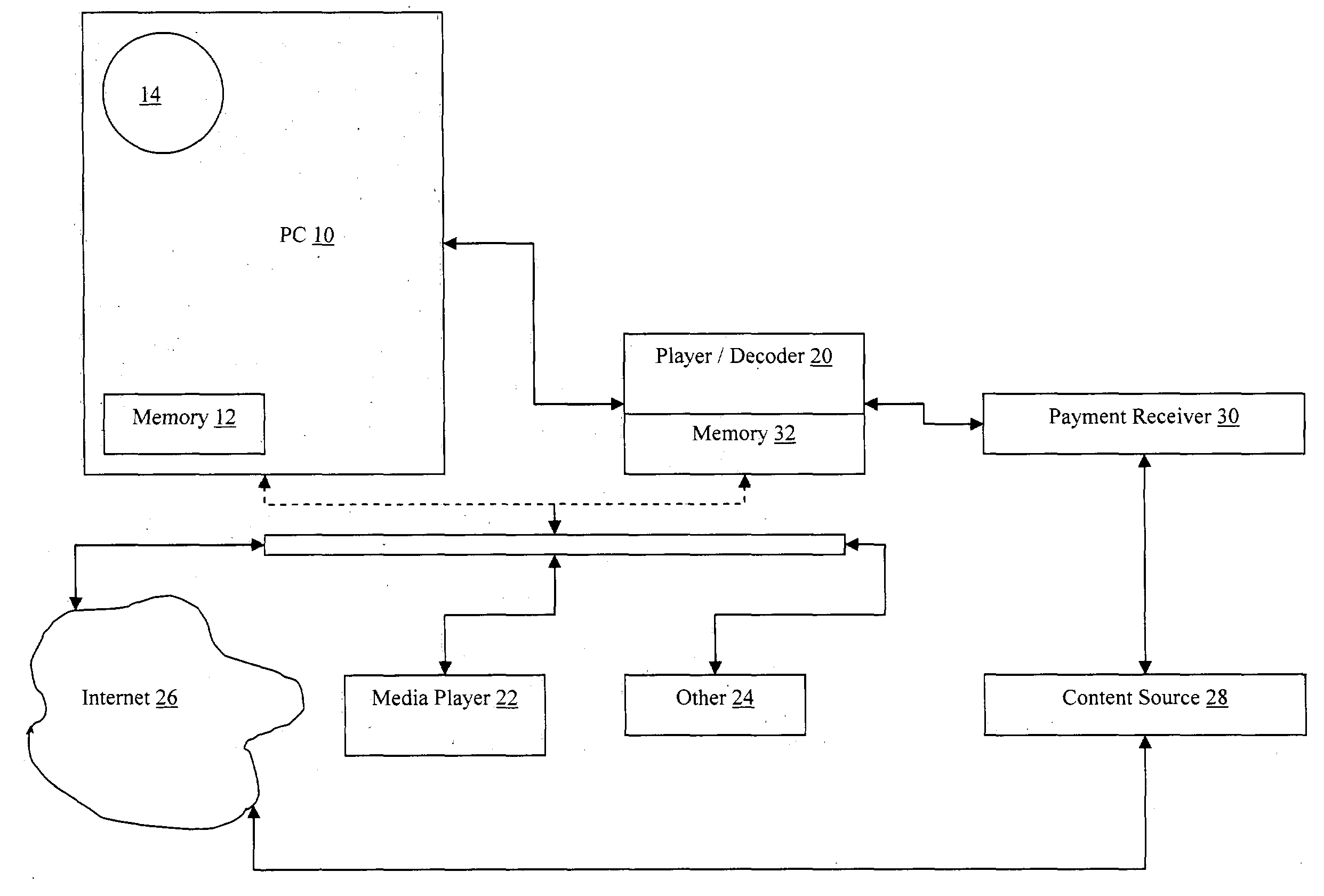
Music distribution apparatus and method
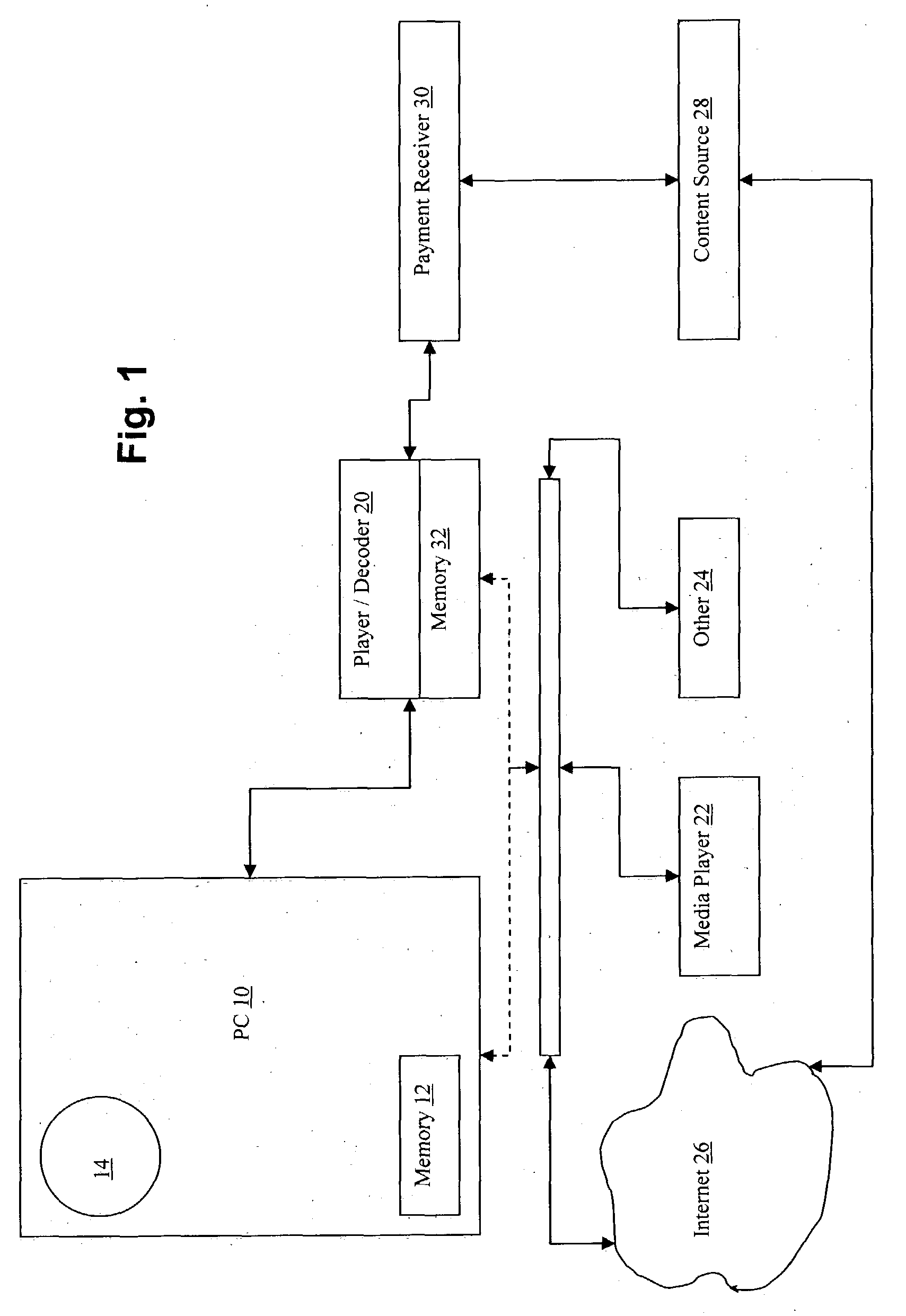
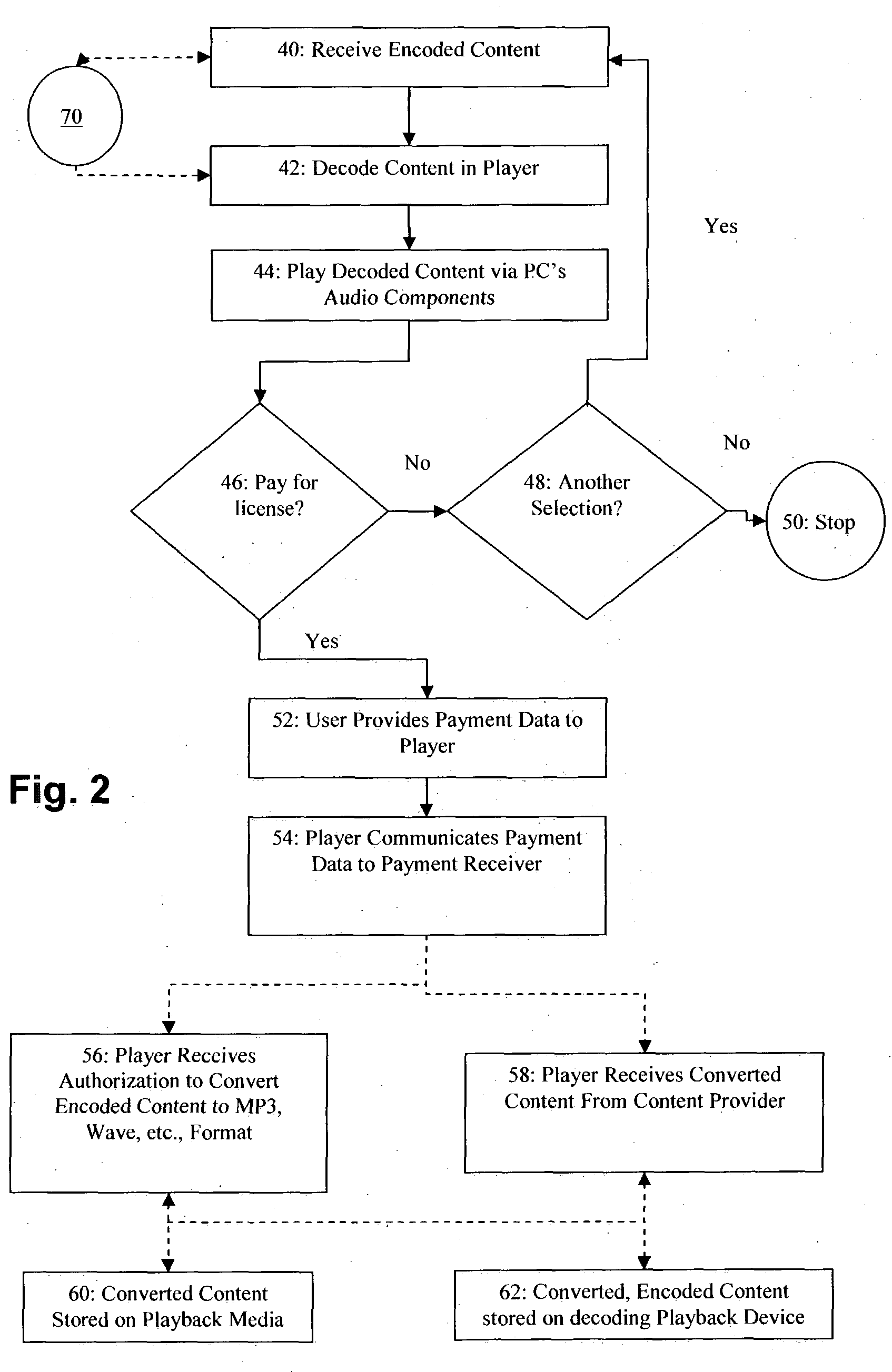
ActiveUS20050021414A1Computer security arrangementsMultiple digital computer combinationsPaymentRecordable CD
Digitally encoded content (e.g., music) is provided in a protected mode, along with a player that can unlock and / or decode this music on a user's personal computer (PC) for enjoyment only at their PC. Since the music is in a proprietary, protected form, the user cannot download to players for other formats, e.g., MP3 players, nor can a CD be burned for use external to the PC. If the user decides that they like the content and wants to use it on another playback device, e.g., a MP3 player, or copy it onto a CD-R for use in a standard audio player, the user can initiate a transaction for payment through the player. Once the transaction is completed, the player either converts or transforms the content into a format usable by the, e.g., MP3 player, or converts or transforms the content into wave format and writes it to a CD-R.
Owner:GATEWAY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com