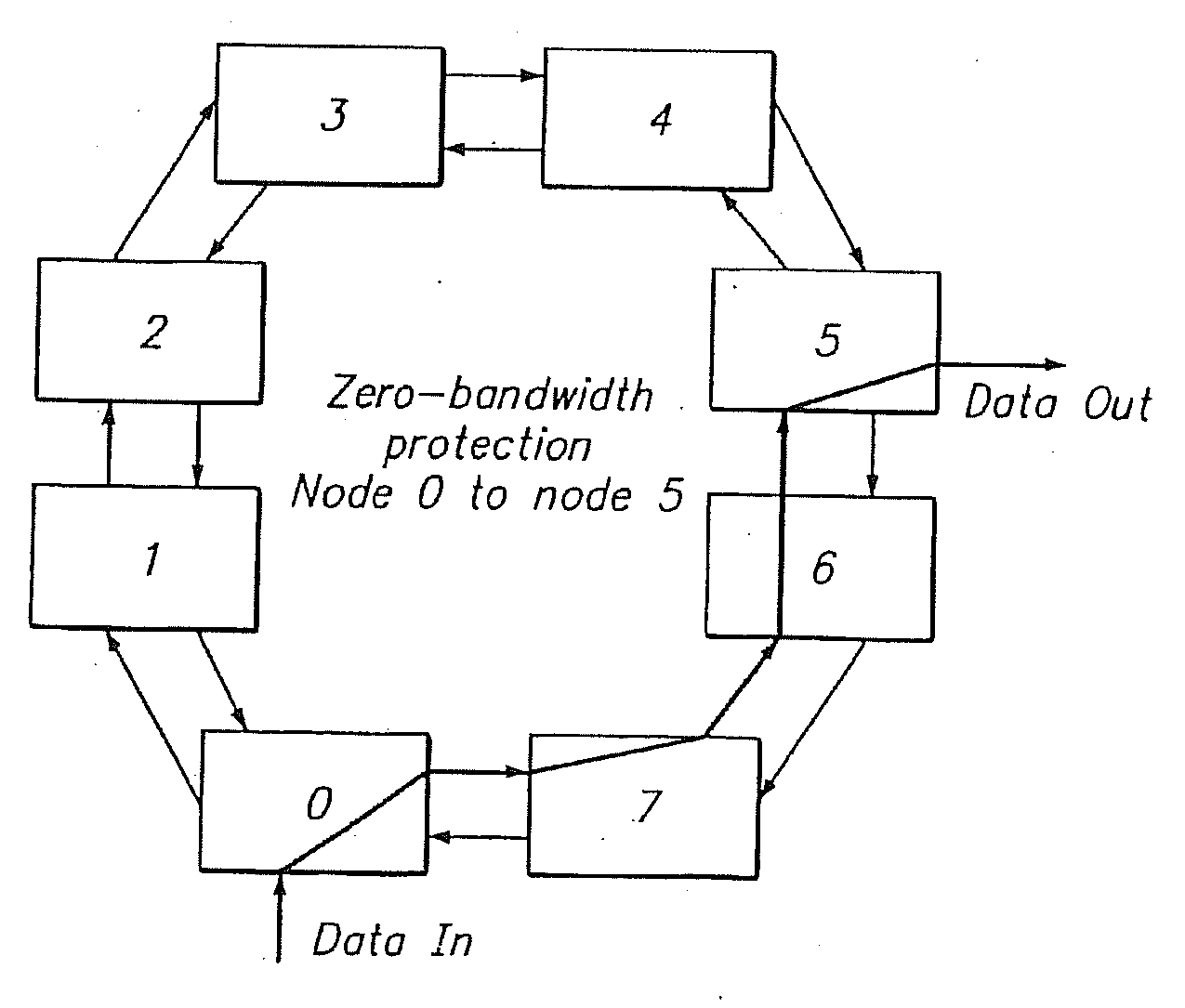
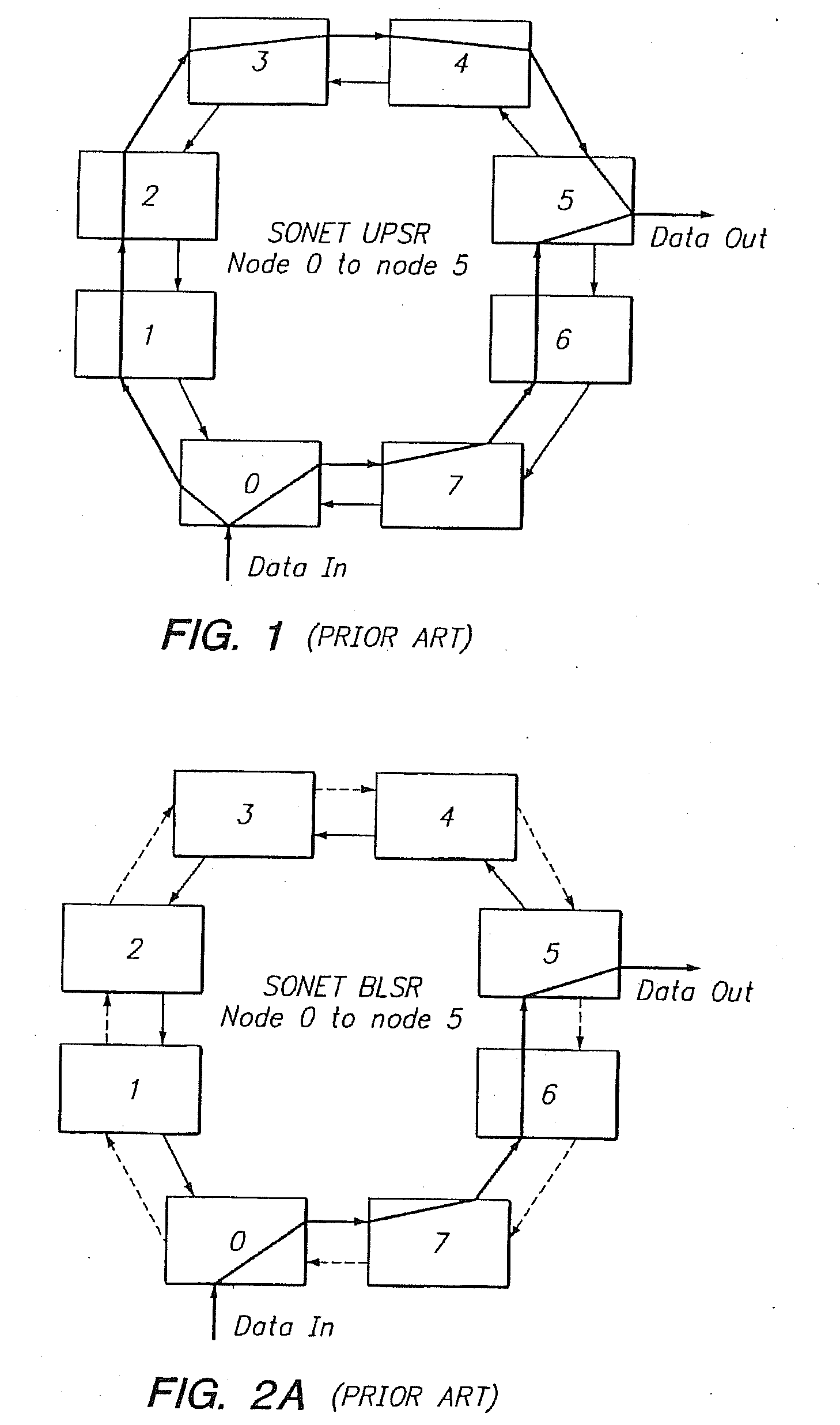
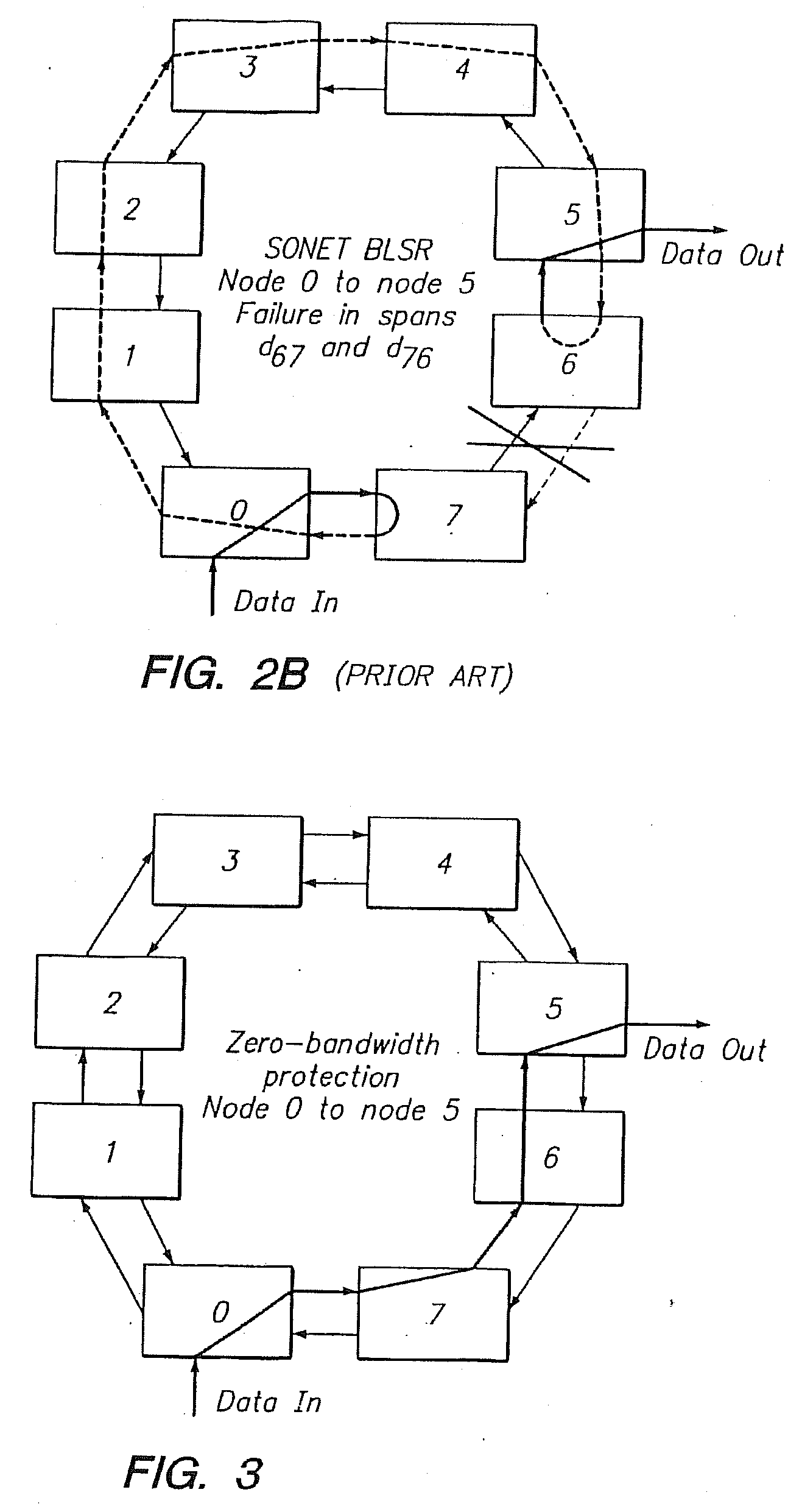
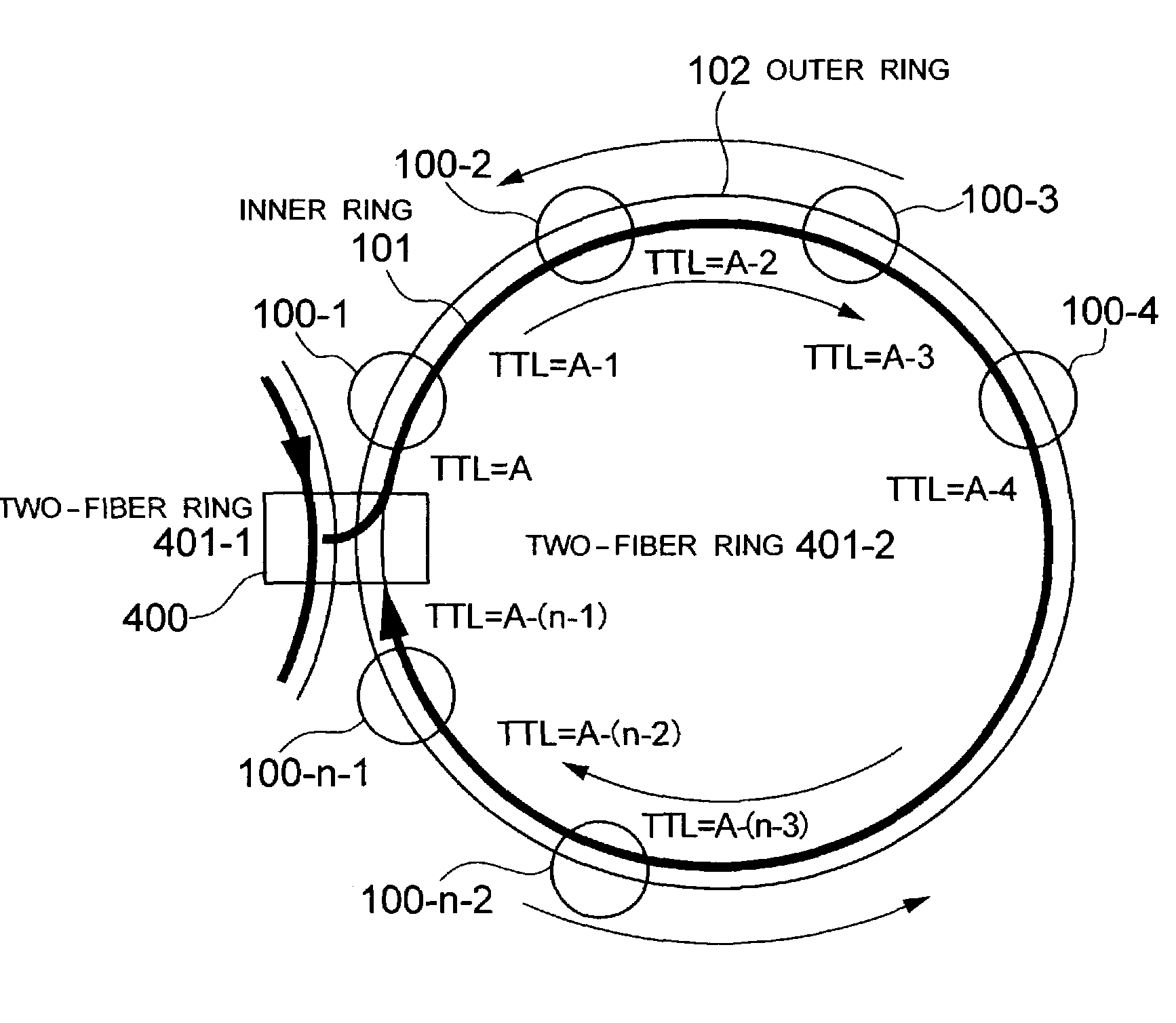
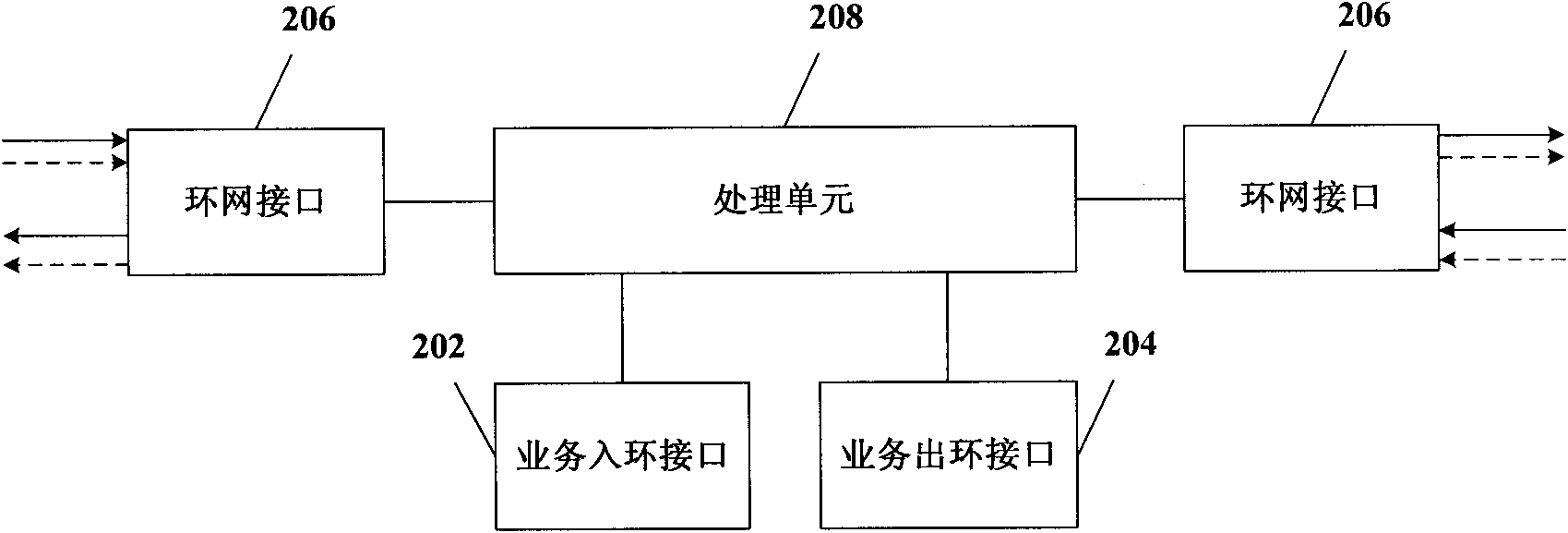
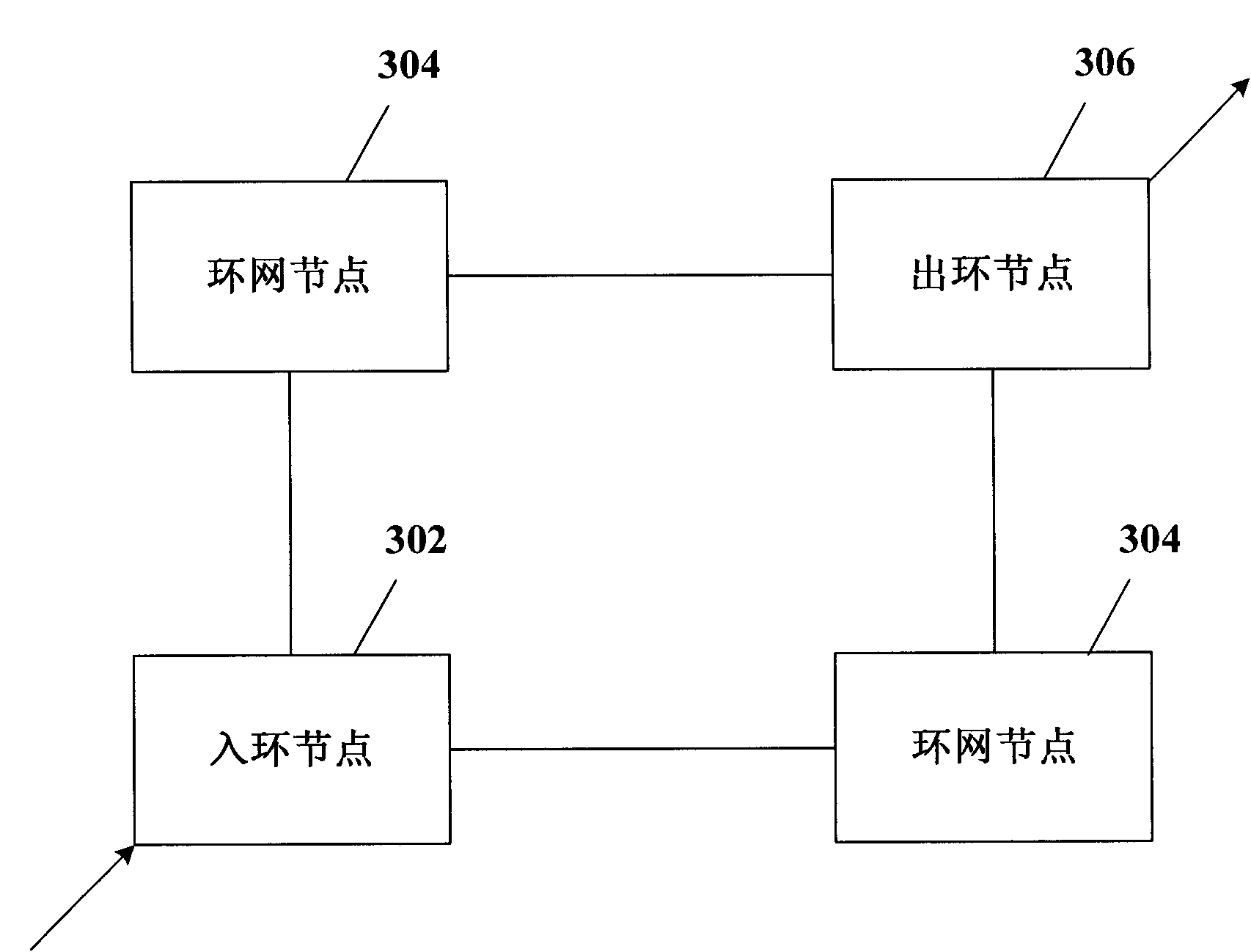
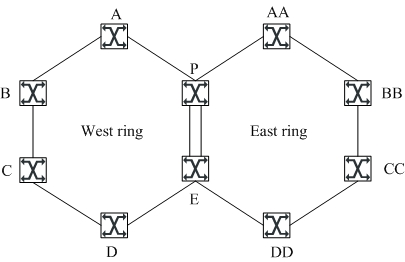
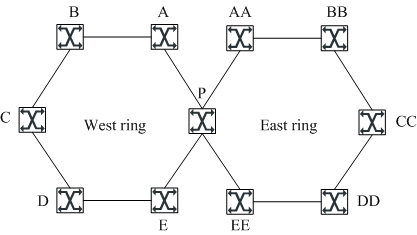
Patents
Literature
315 results about "Ring protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
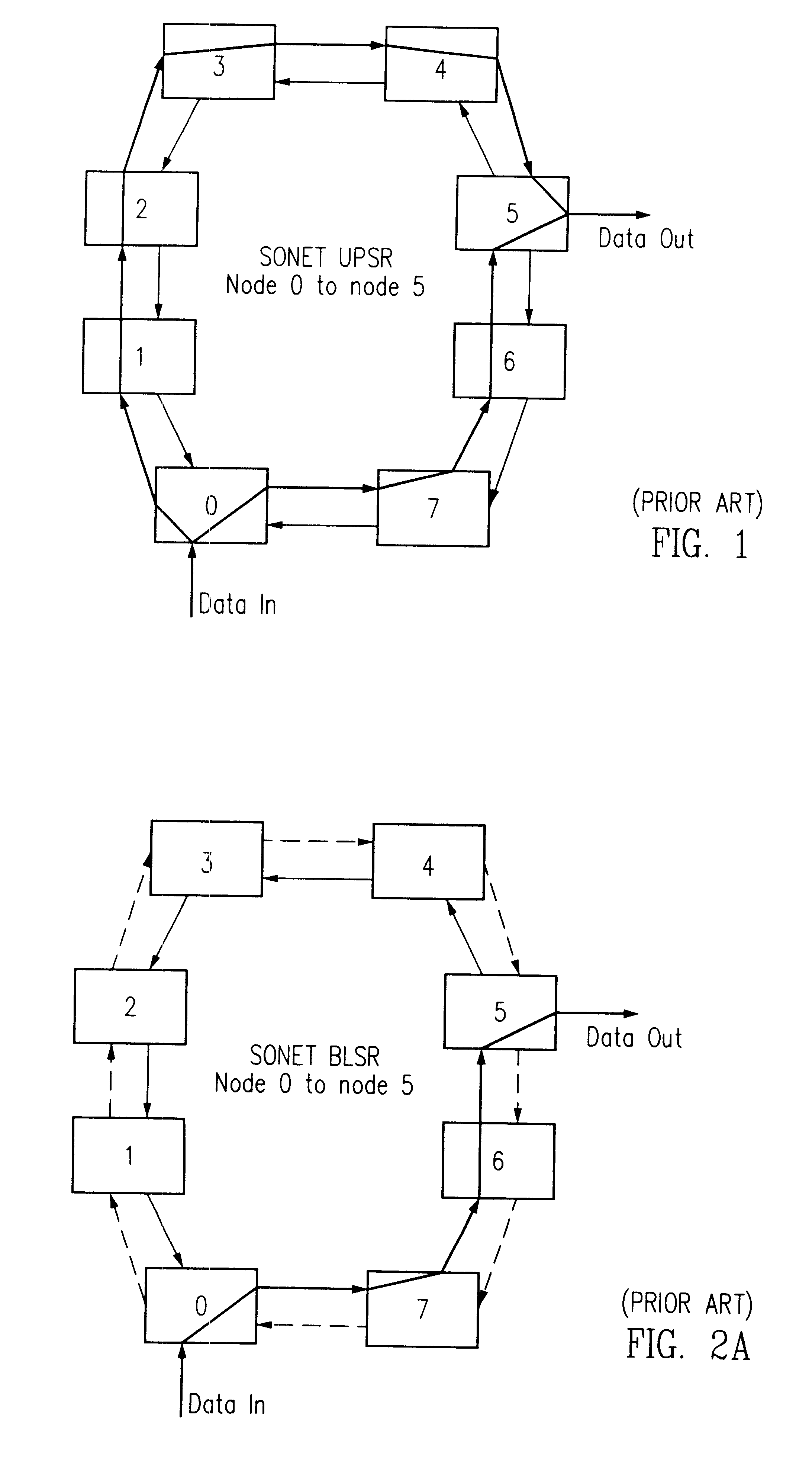
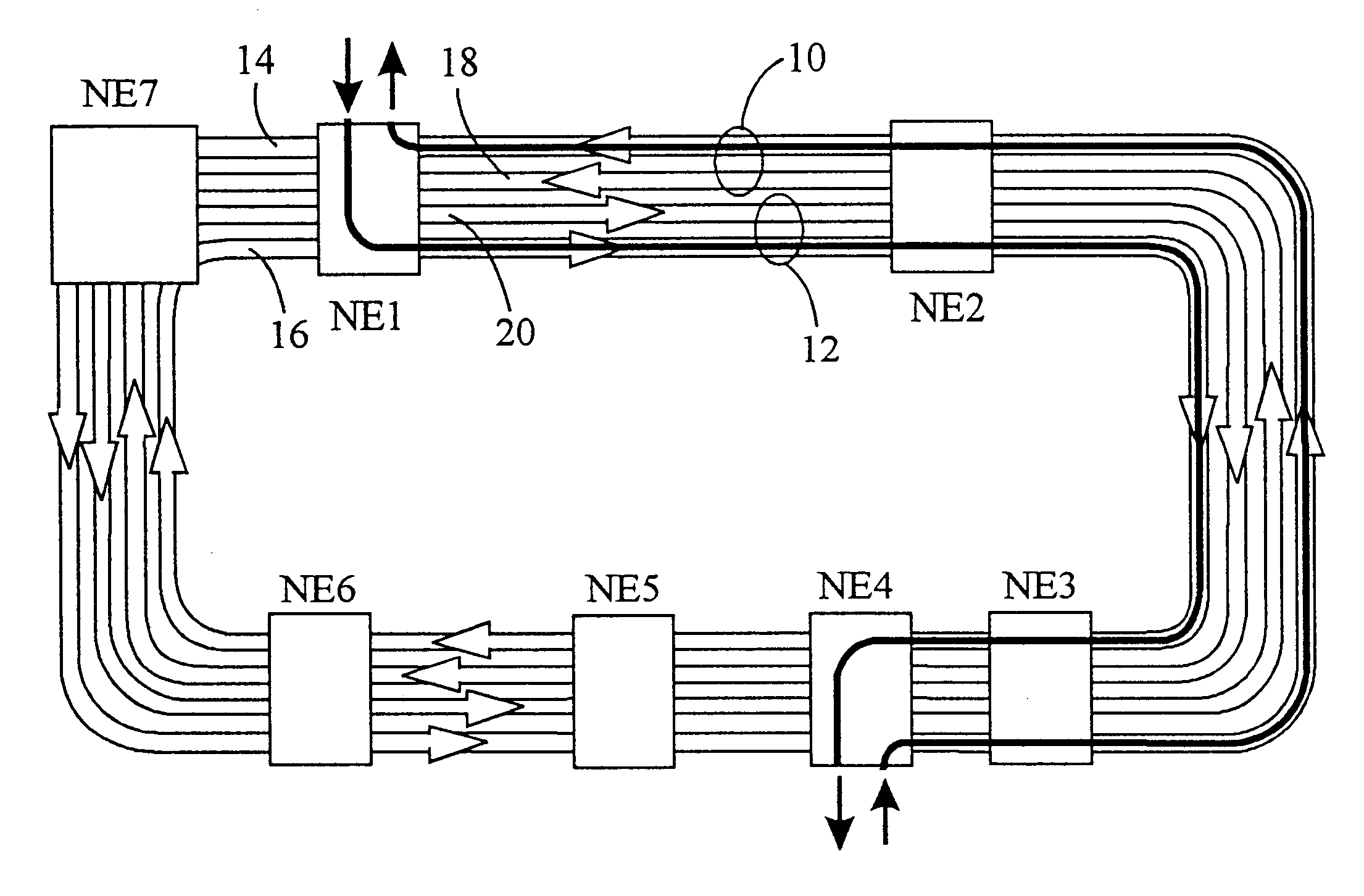
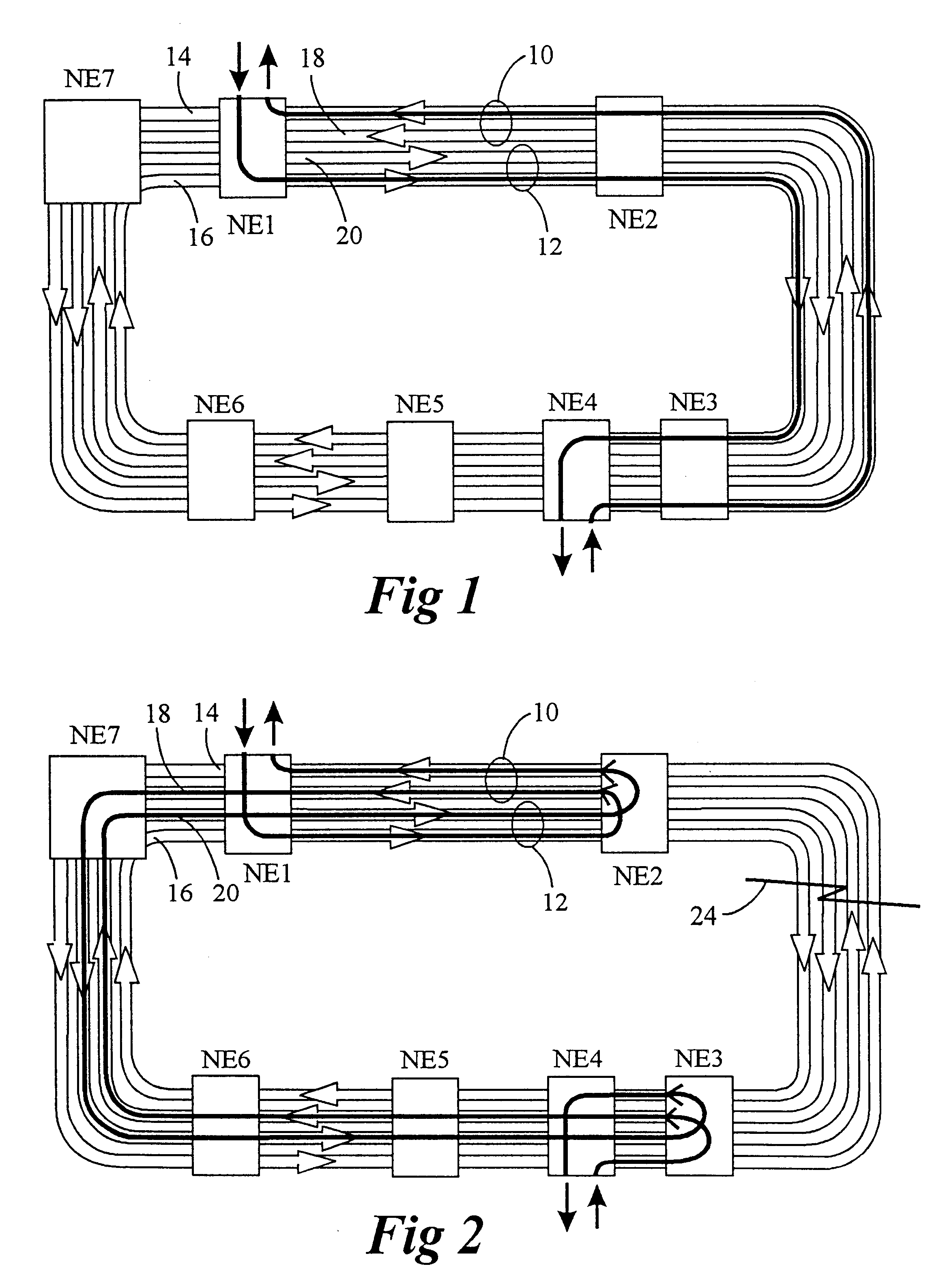
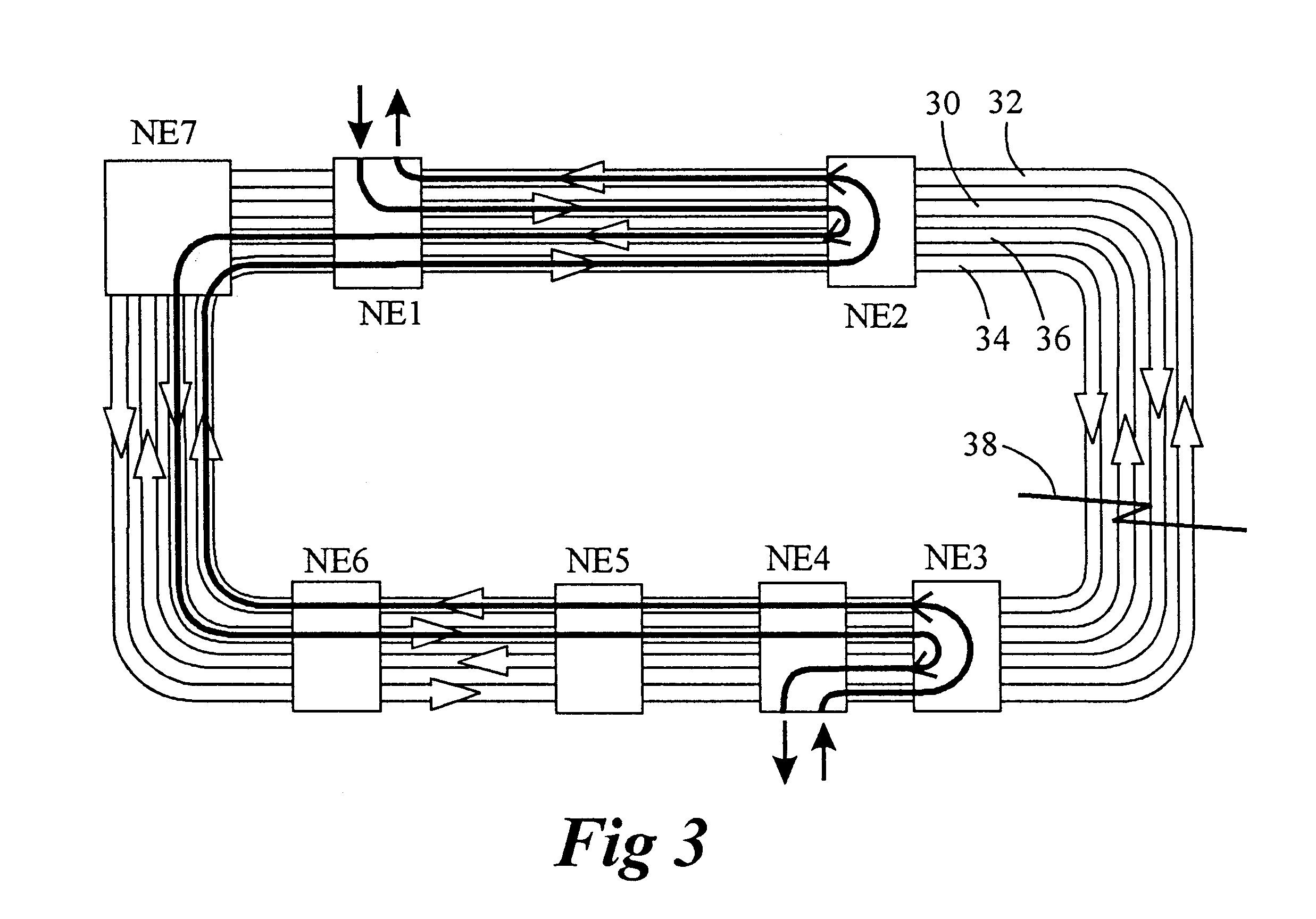
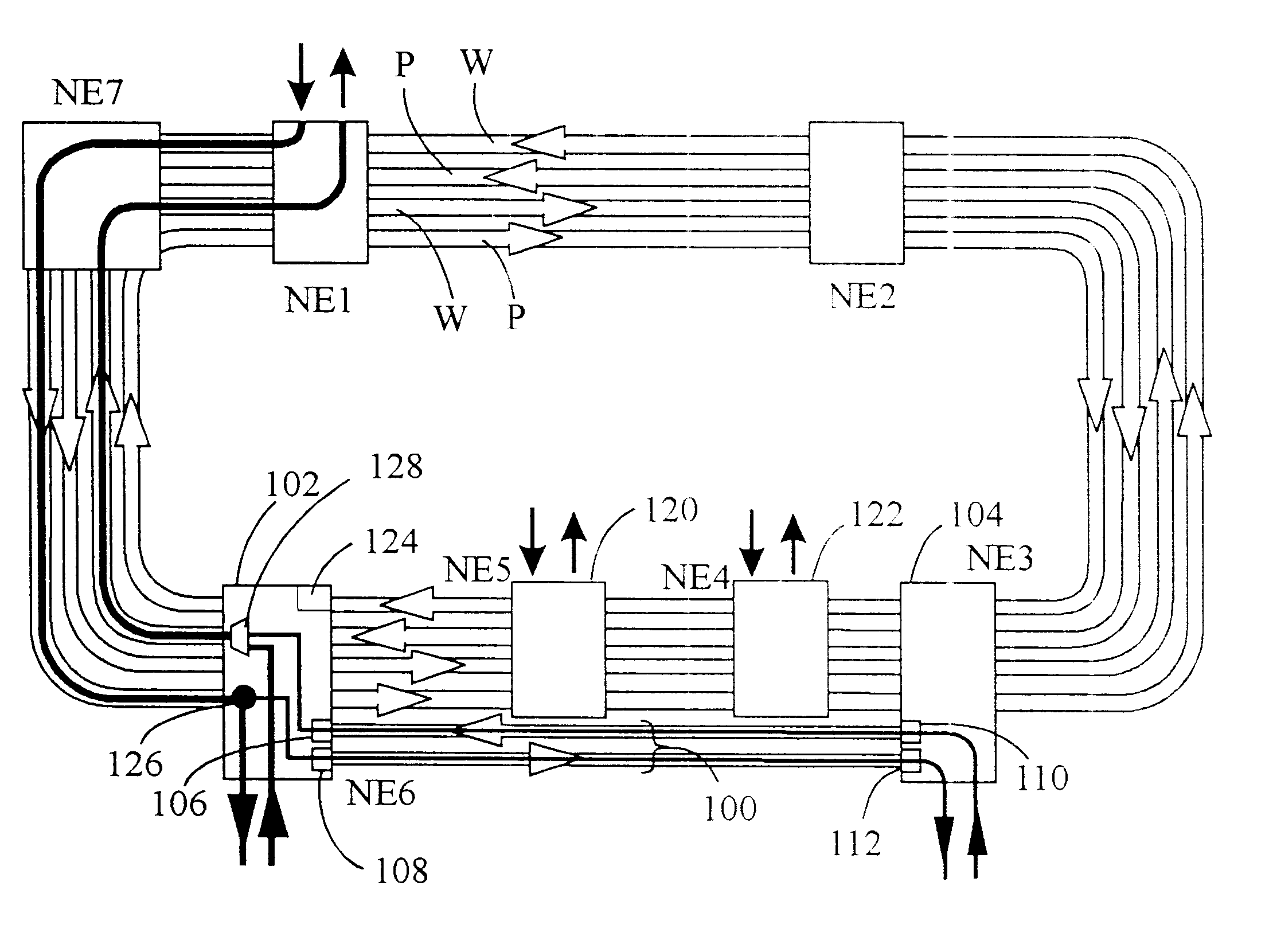
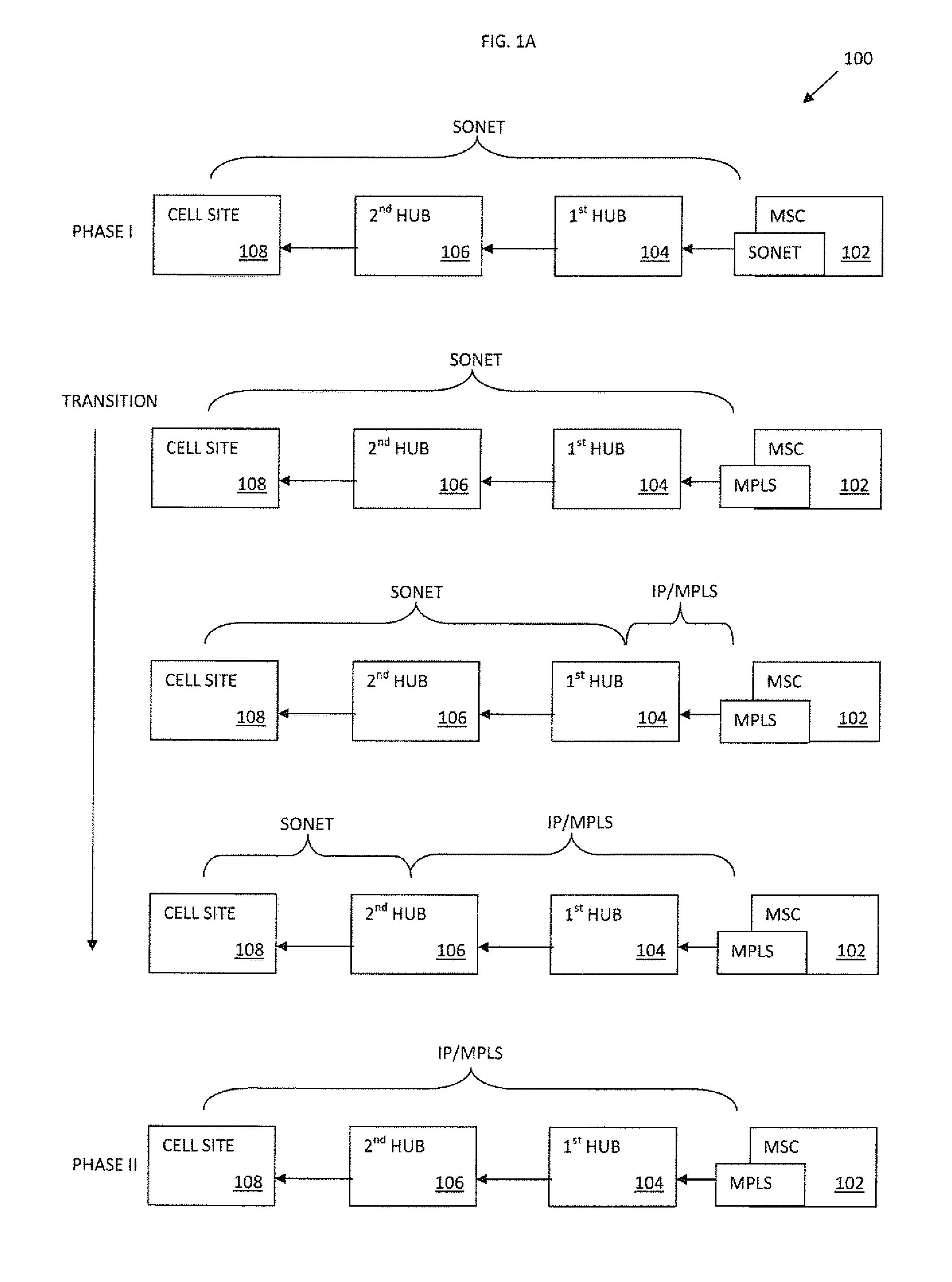
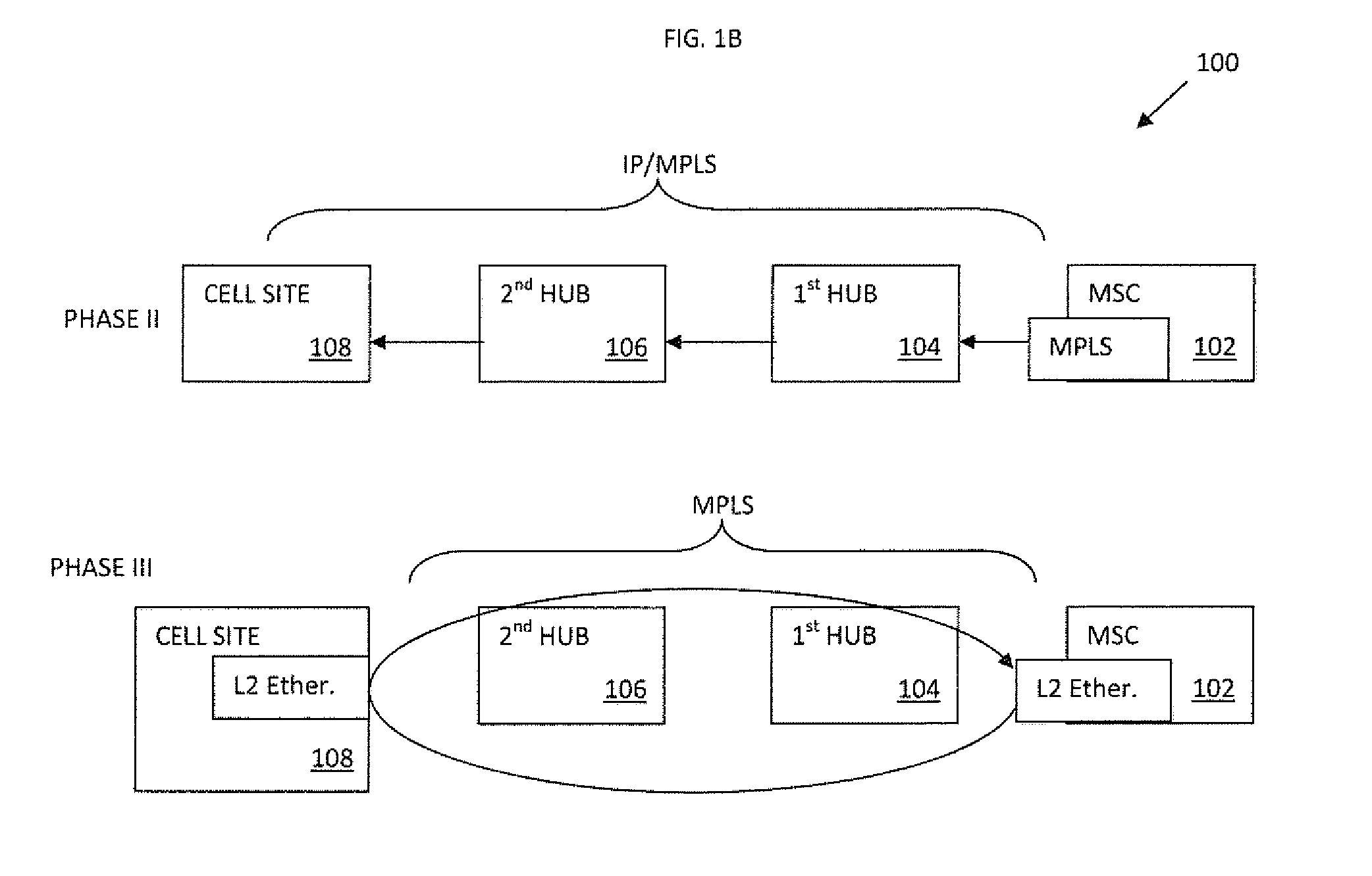
In a telecommunication network, a ring network affords fault tolerance to the network because there are two paths between any two nodes on the network. Ring protection is the system used to assure communication continues in the event of failure of one of the paths. There are two widely used protection architectures: 1+1 protection and 1:1 protection.
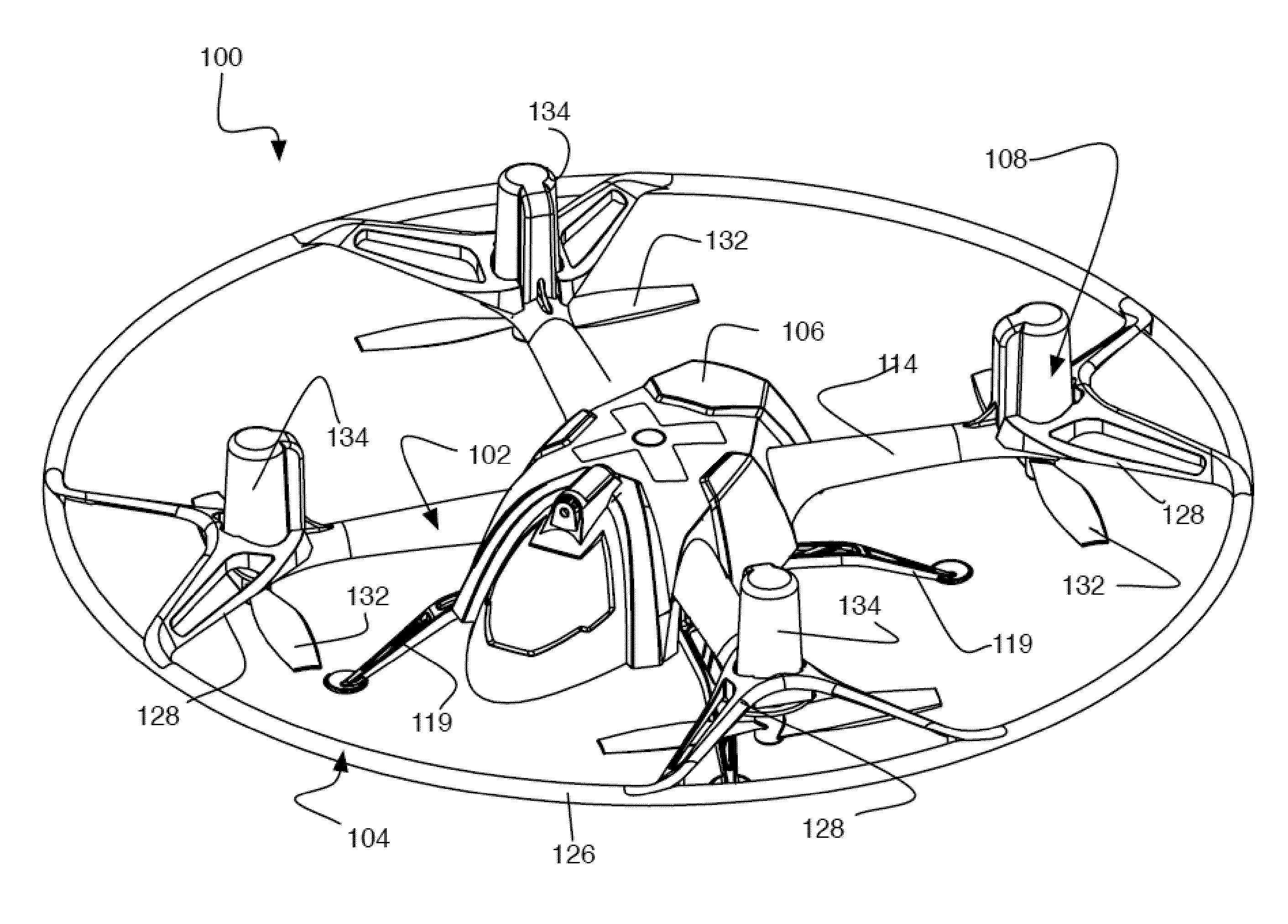
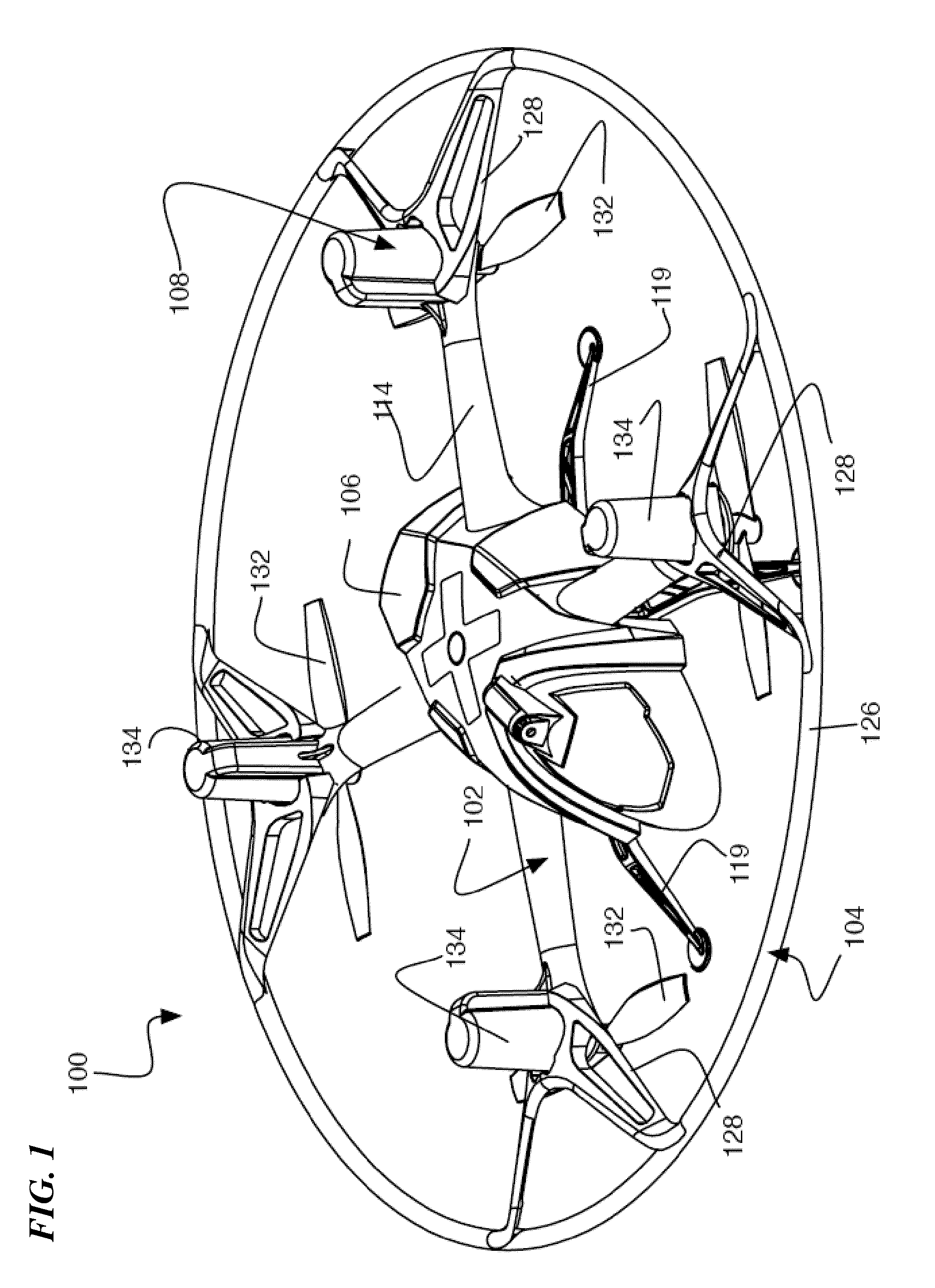
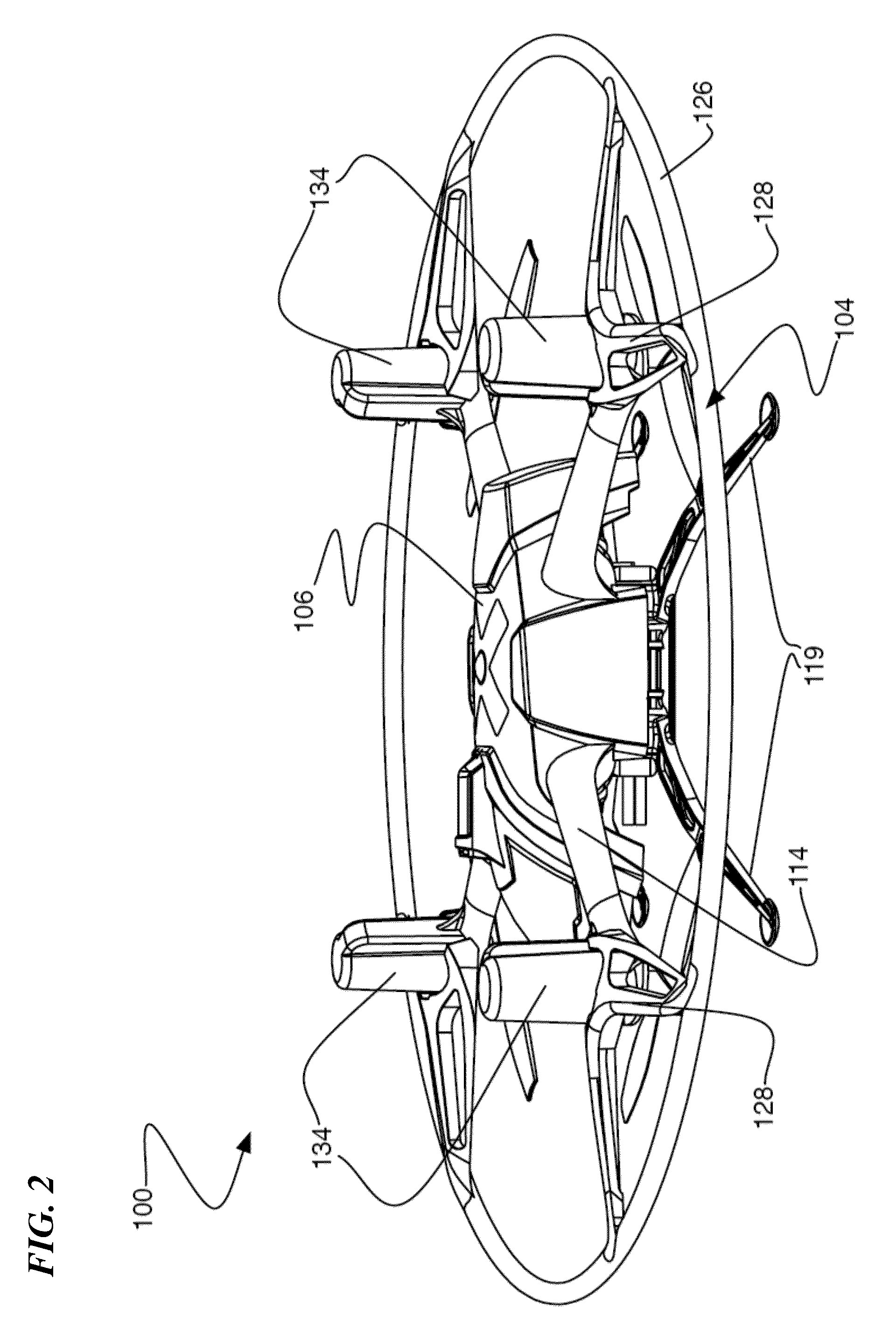
Remote-control flying copter and method
ActiveUS9004973B2Increase awarenessFlight safetyModel aircraftSelf-moving toy figuresDistal portionRemote control
A hovering remote-control flying craft having a molded frame assembly includes a plurality of arms extending from a center body with an electric motor and corresponding propeller on each arm. In various embodiments, the motor and propeller are mounted downward-facing at a distal portion of each arm with a motor cover over the motor. The center body can be formed of a two-piece molded structure that sandwiches a circuit board to provide structural support for the frame. The circuit board can include a plurality of tabs that facilitate mounting of wire connectors, and can also provide antennas and emitters for both IR and RF communications. In some embodiments, a removable safety ring protects the propellers from lateral contact.
Owner:QFO LABS
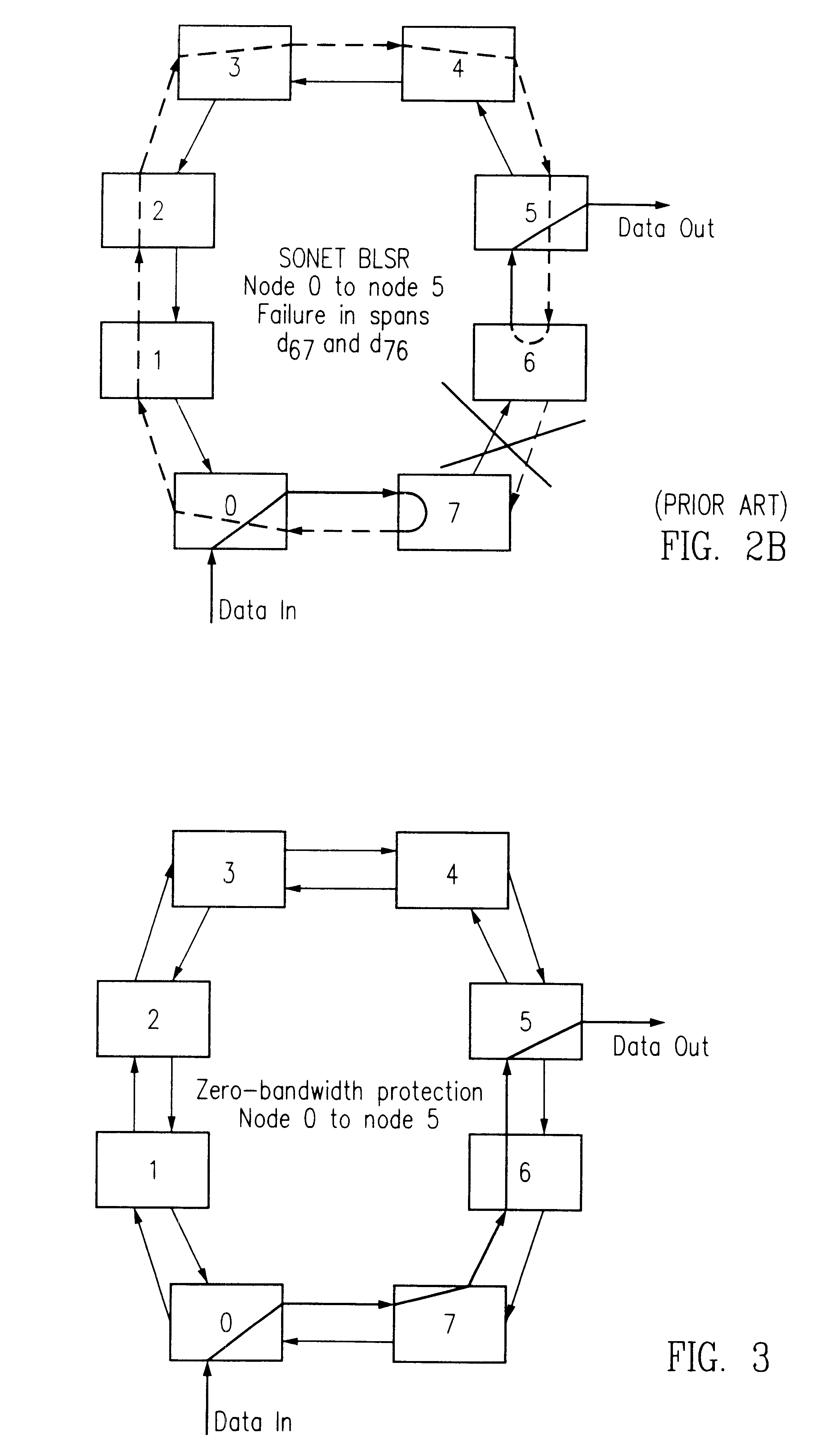
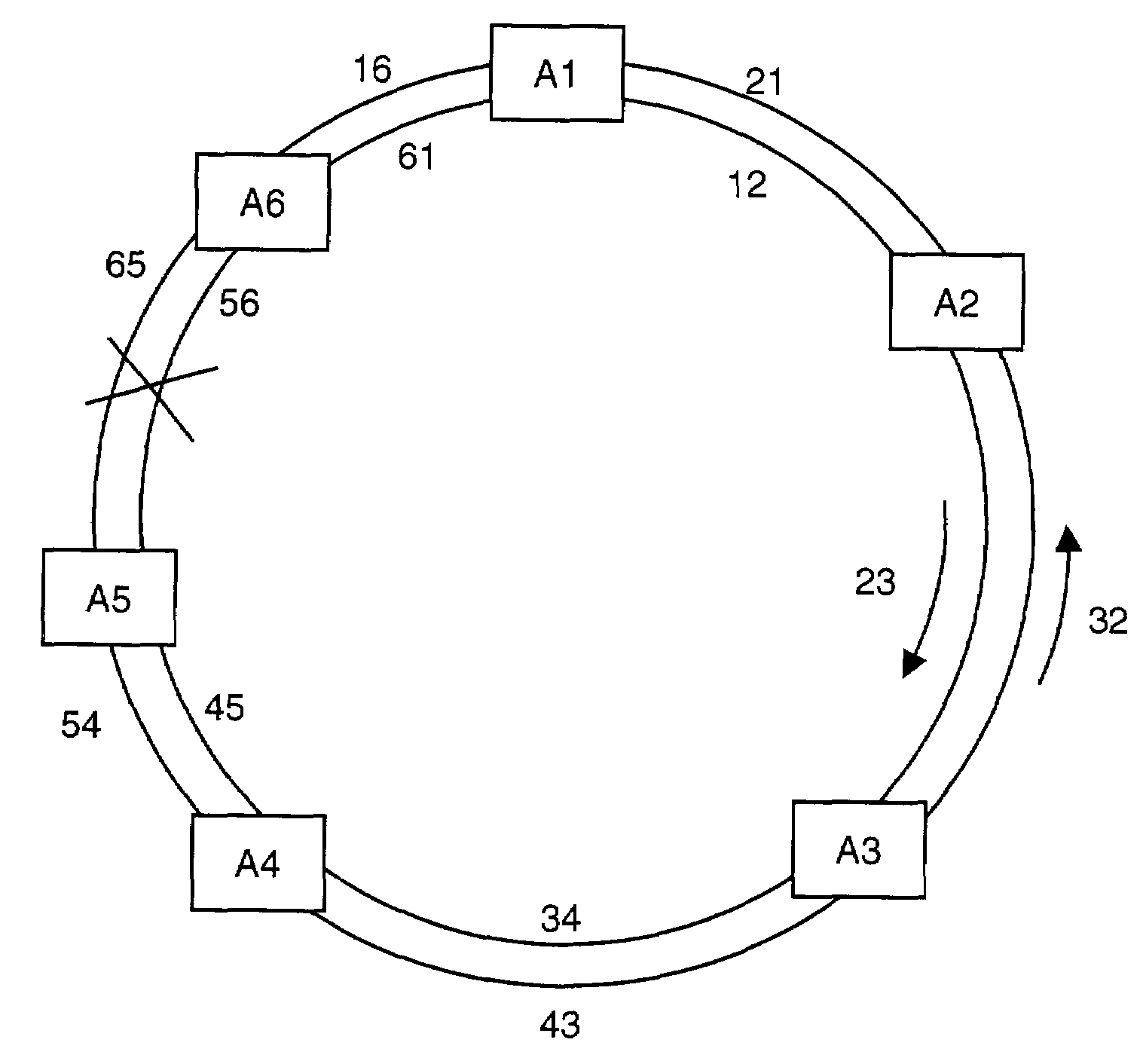
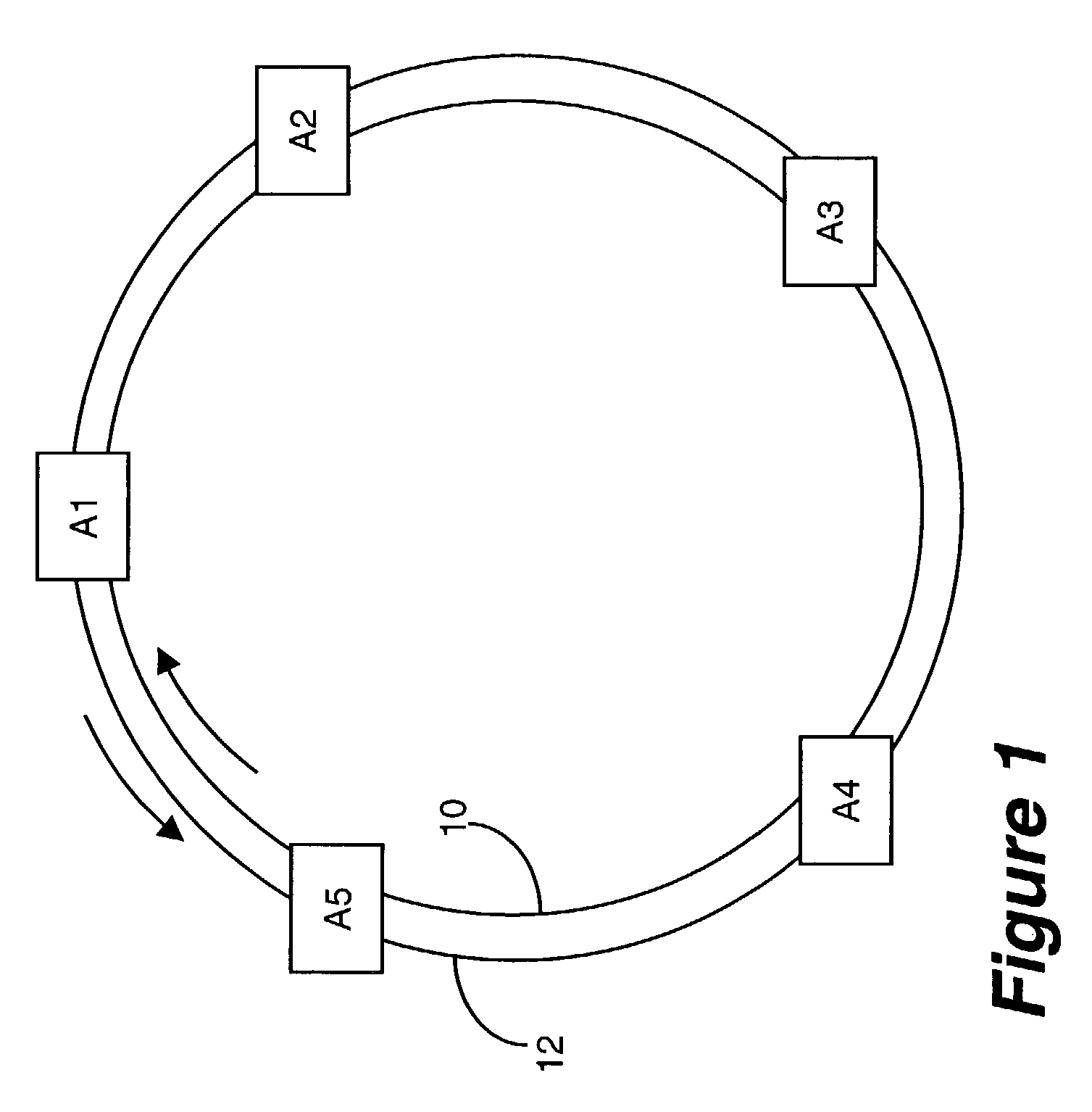
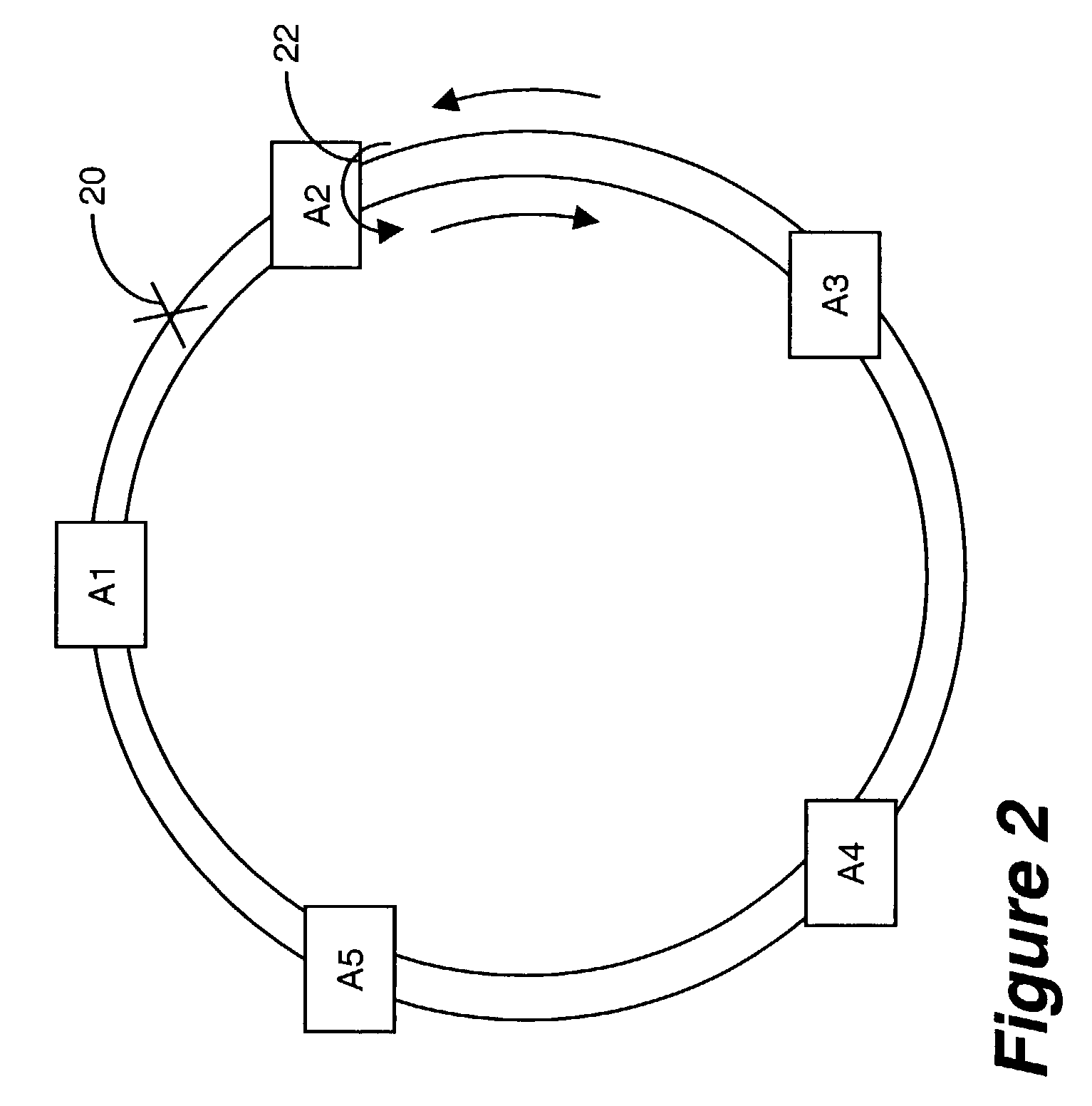
Dynamically allocated ring protection and restoration technique
The disclosed network includes two rings, wherein a first ring transmits data in a clockwise direction, and the other ring transmits data in a counterclockwise direction. The traffic is removed from the ring by the destination node. During normal operations (i.e., all spans operational), data between nodes flows on the ring that would provide the minimum number of hops to the destination node. Thus, both rings are fully utilized during normal operations. The nodes periodically test the bit error rate of the links (or the error rate is constantly calculated) to detect a fault in one of the links. The detection of such a fault sends a broadcast signal to all nodes to reconfigure a routing table within the node so as to identify the optimum routing of source traffic to the destination node after the fault. Since the available links will now see more data traffic due to the failed link, traffic designated as “unprotected” traffic is given lower priority and may be dropped or delayed in favor of the “protected” traffic. Specific techniques are described for identifying a failed link, communicating the failed link to the other nodes, differentiating between protected and unprotected classes of traffic, and updating the routing tables.
Owner:ADTRAN
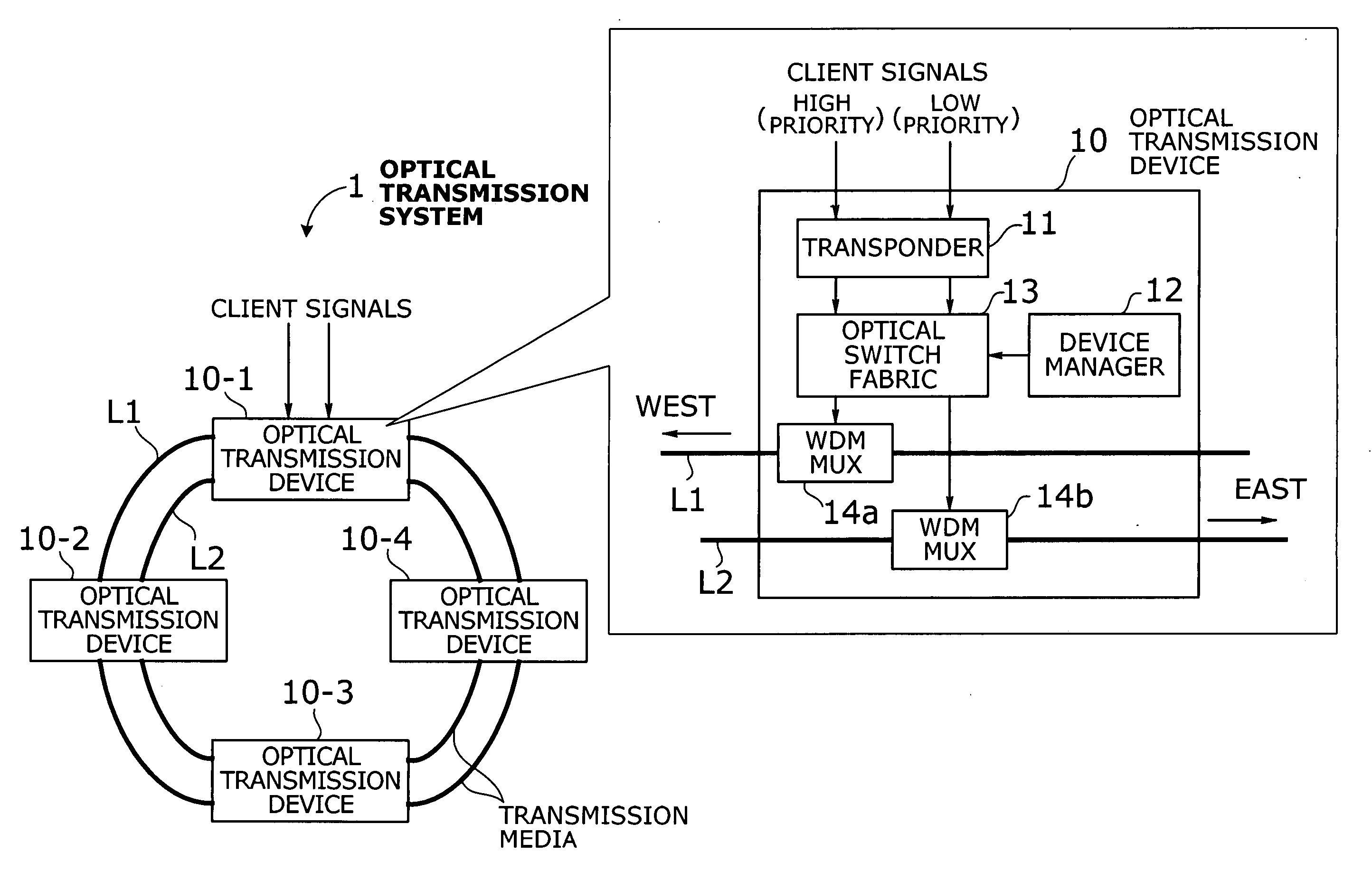
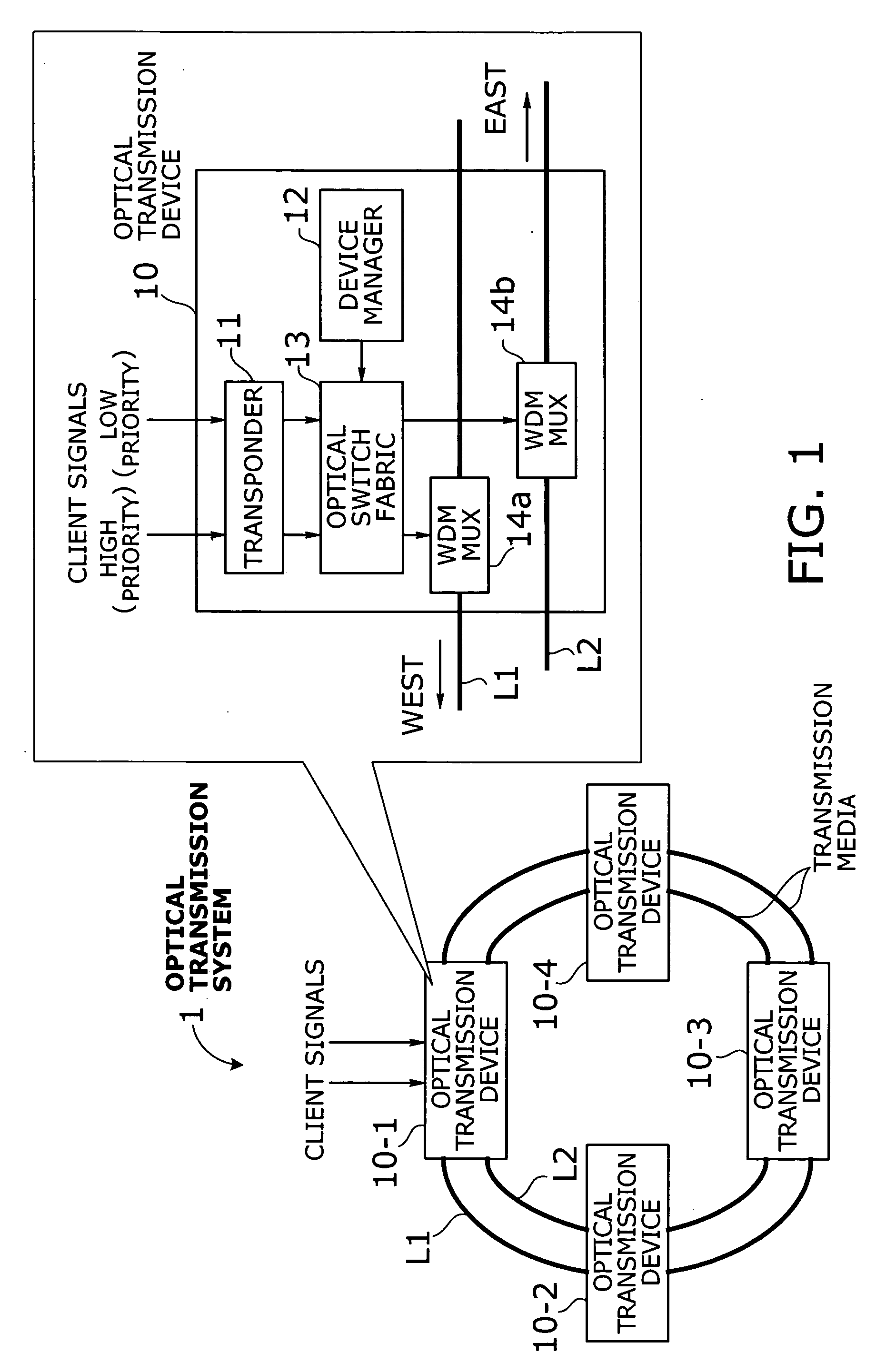
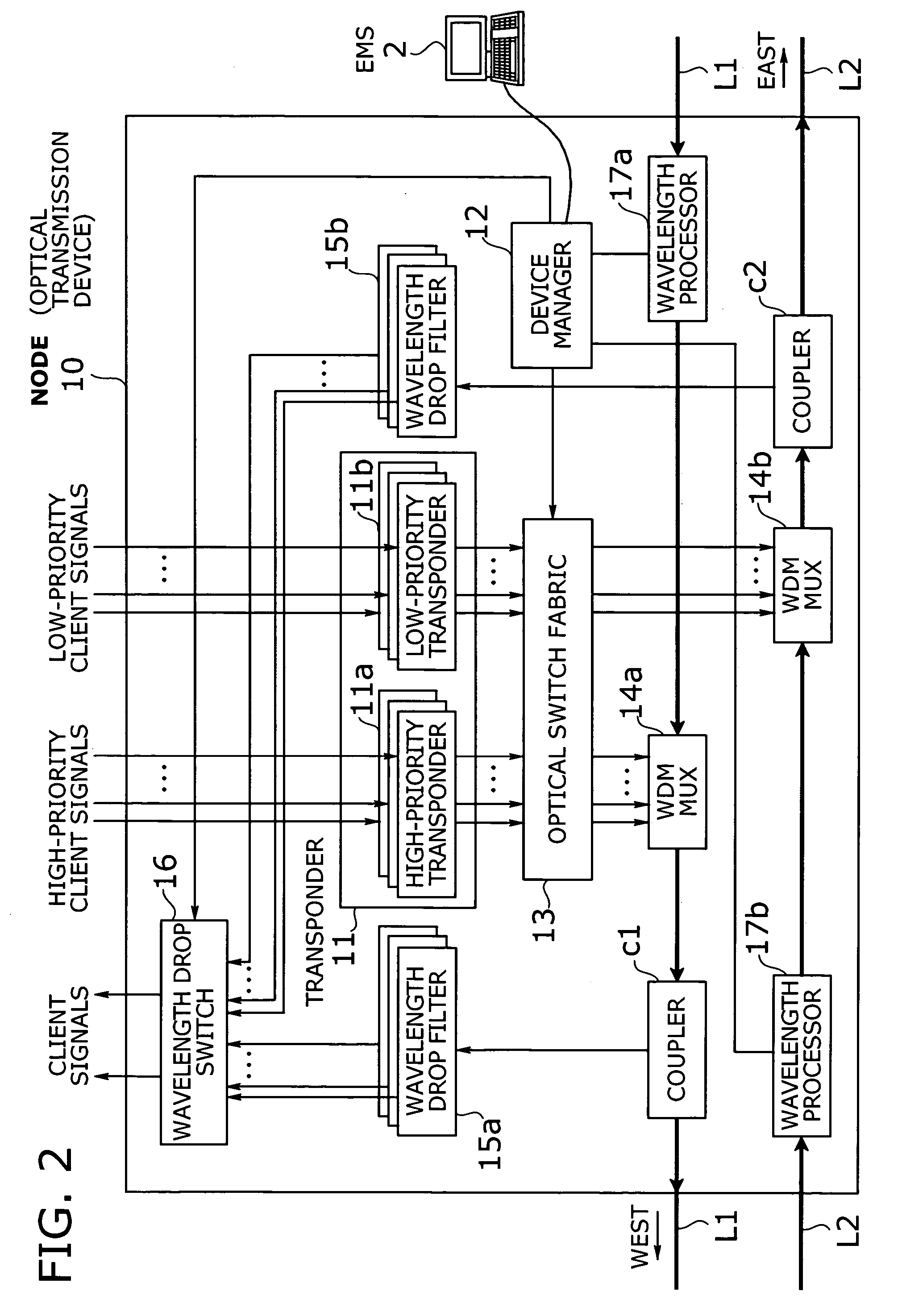
Optical transmission system with two-mode ring protection mechanism for prioritized client signals
InactiveUS20060013584A1Efficient use of bandwidthImprove fault toleranceRing-type electromagnetic networksWavelength-division multiplex systemsFault toleranceSurvivability
An optical transmission system that offers more efficient bandwidth usage in normal operation, as well as enhanced fault tolerance for higher service availability. A transponder converts high-priority and low-priority client signals into high-priority and low-priority wavelength signals to be added to network traffic. An optical switch fabric normally delivers high-priority and low-priority wavelength signals to high-priority and low-priority paths, respectively, where the two paths run in opposite directions. Such signals and paths are prioritized in terms of survivability against network failure. In case of a network failure, the optical switch fabric performs protection switching in either duplicate switching mode or path switchover mode depending on network failure information and drop wavelengths of each optical transmission device. In duplicate switching mode, high-priority wavelength signals are directed to both the high-priority and low-priority paths. In path switchover mode, they are routed to the low-priority path, instead of the high-priority path.
Owner:FUJITSU LTD
Efficient Protection Mechanisms For Protecting Multicast Traffic in a Ring Topology Network Utilizing Label Switching Protocols
Efficient protection mechanisms for ring-based label-switching networks, such as multi-protocol label switching (MPLS) networks. The protection mechanisms are designed to protect point-to-multipoint label switching paths (LSPs). In steering ring protection embodiments, the nodes of the ring network are provided with pre-configured tables that enable each node to operate in both working mode and protection mode. The information required for each node to switch between the two modes in included in its respective table during the pre-configuration of the ring network. In wrapping ring protection embodiments, the wrapping is performed by assigning a unique LSP label to each LSP and further configuring each intermediate node in the ring network to transparently pass data packets including the unique LSP label. Upon detecting a failure in a network node, the data packets including the unique LSP label are switched to a protection ring.
Owner:ALCATEL LUCENT SAS
Bandwidth reservation reuse in dynamically allocated ring protection and restoration technique
InactiveUS20090141621A1Maximize switching speedError preventionTransmission systemsRouting tableRing protection
The disclosed network includes two rings, wherein a first ring transmits data in a clockwise direction, and the other ring transmits data in a counterclockwise direction. The traffic is removed from the ring by the destination node. During normal operations (i.e., all spans operational), data between nodes can flow on either ring. Thus, both rings are fully utilized during normal operations. The nodes periodically test the bit error rate of the links (or the error rate is constantly calculated) to detect a fault in one of the links. The detection of such a fault sends a broadcast signal to all nodes to reconfigure a routing table within the node so as to identify the optimum routing of source traffic to the destination node after the fault.
Owner:ADTRAN
Multiring control method, node using the method, and control program
InactiveUS7324440B2Efficiently discardedError preventionFrequency-division multiplex detailsComputer architectureRing protection
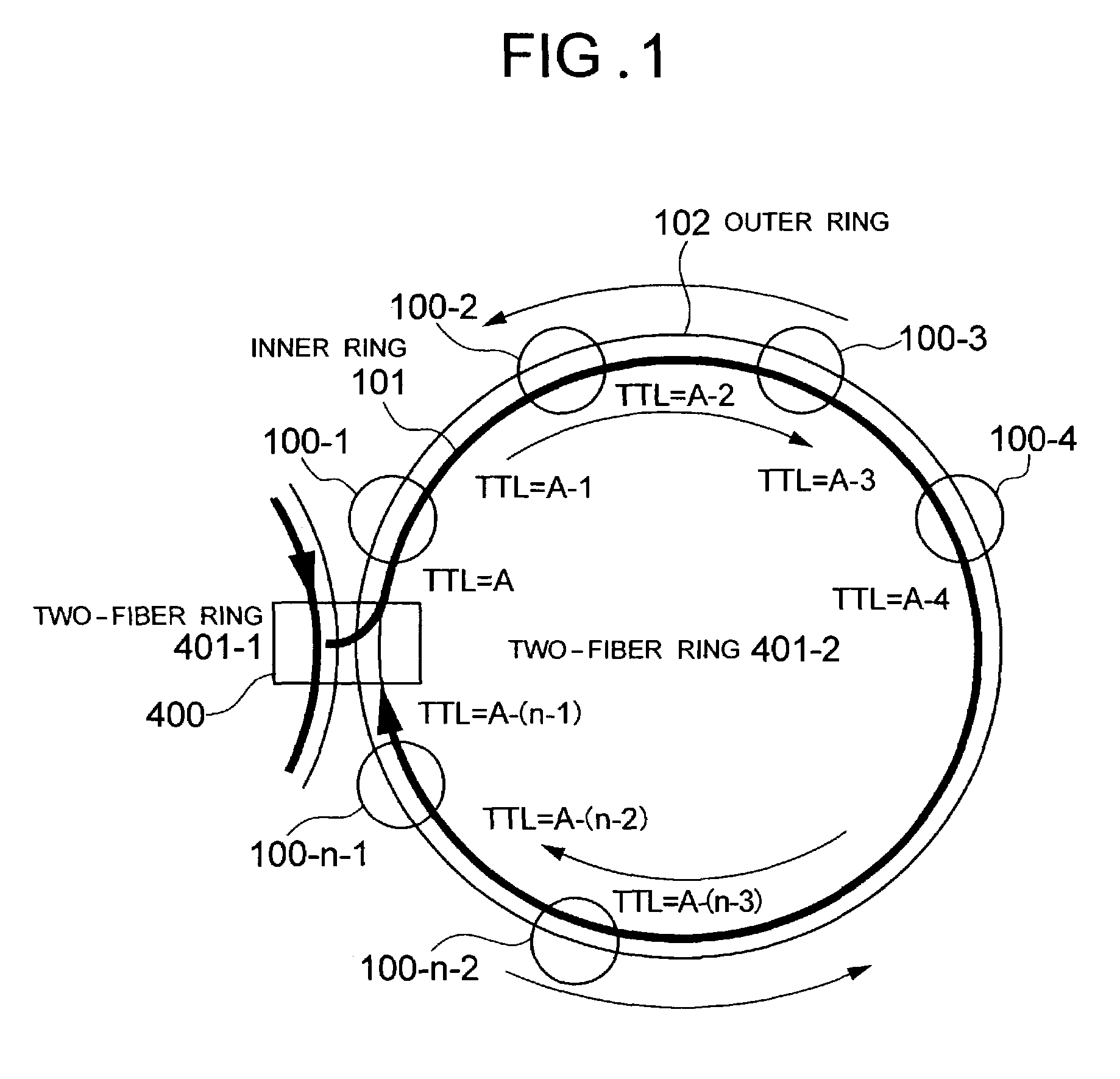
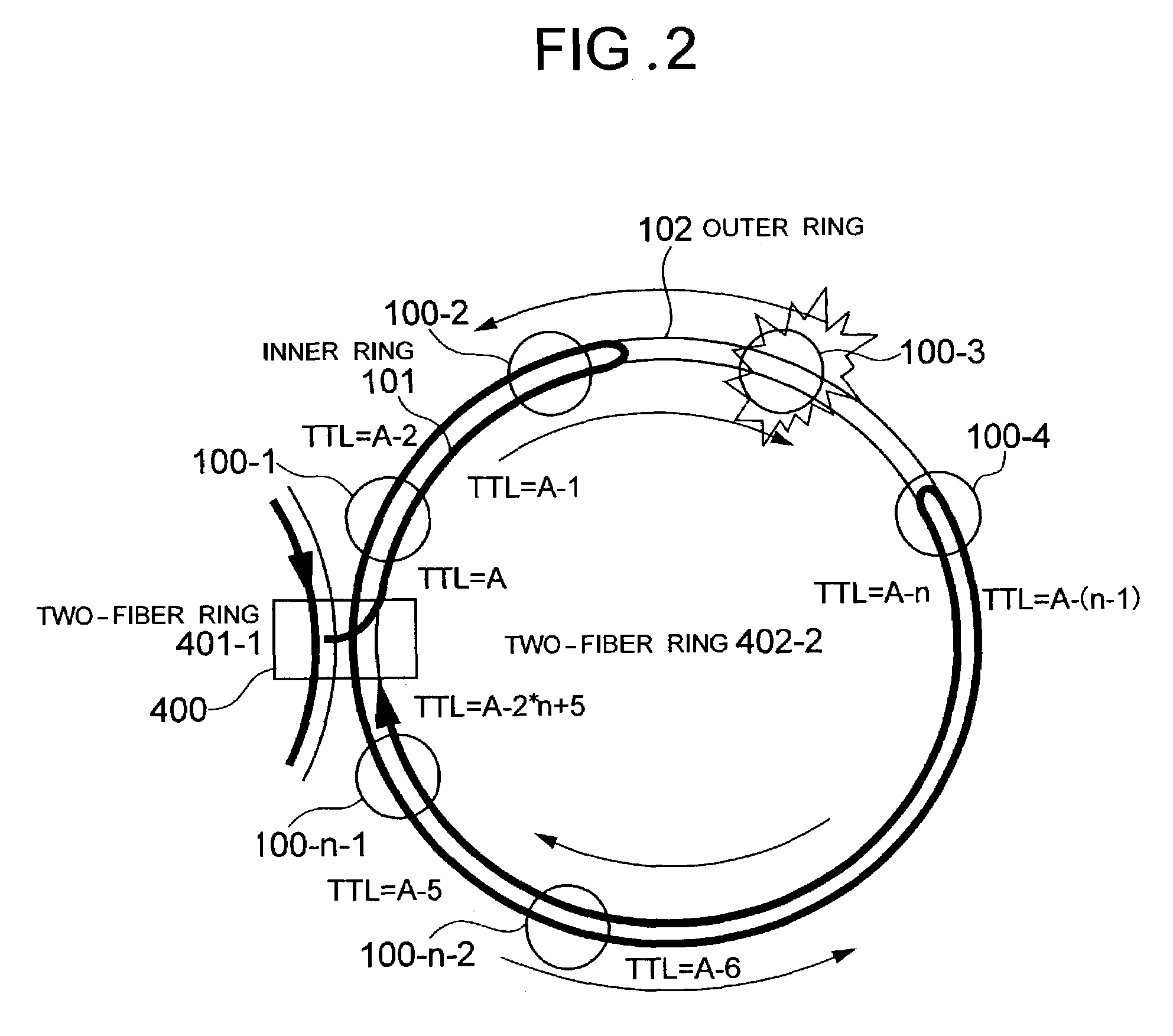
The invention enables protection of a ring frame transferred via an inter-ring bridge ring node when a fault occurs at the node in a multiring. Ring nodes form a ring protection domain to enable one ring node to be bypassed by using other ring nodes when a fault occurs at this ring node. The TTL value of ring frame to be transferred through the bypass is set to a value obtained by adding the number of hops h to the faulty ring node to a common initial value A in the same two-fiber ring to enable detection of a characteristic TTL value at a bypassing ring node. The bypass fur the ring frame is selected with reference to the characteristic TTL value at the bypassing ring node.
Owner:NEC CORP
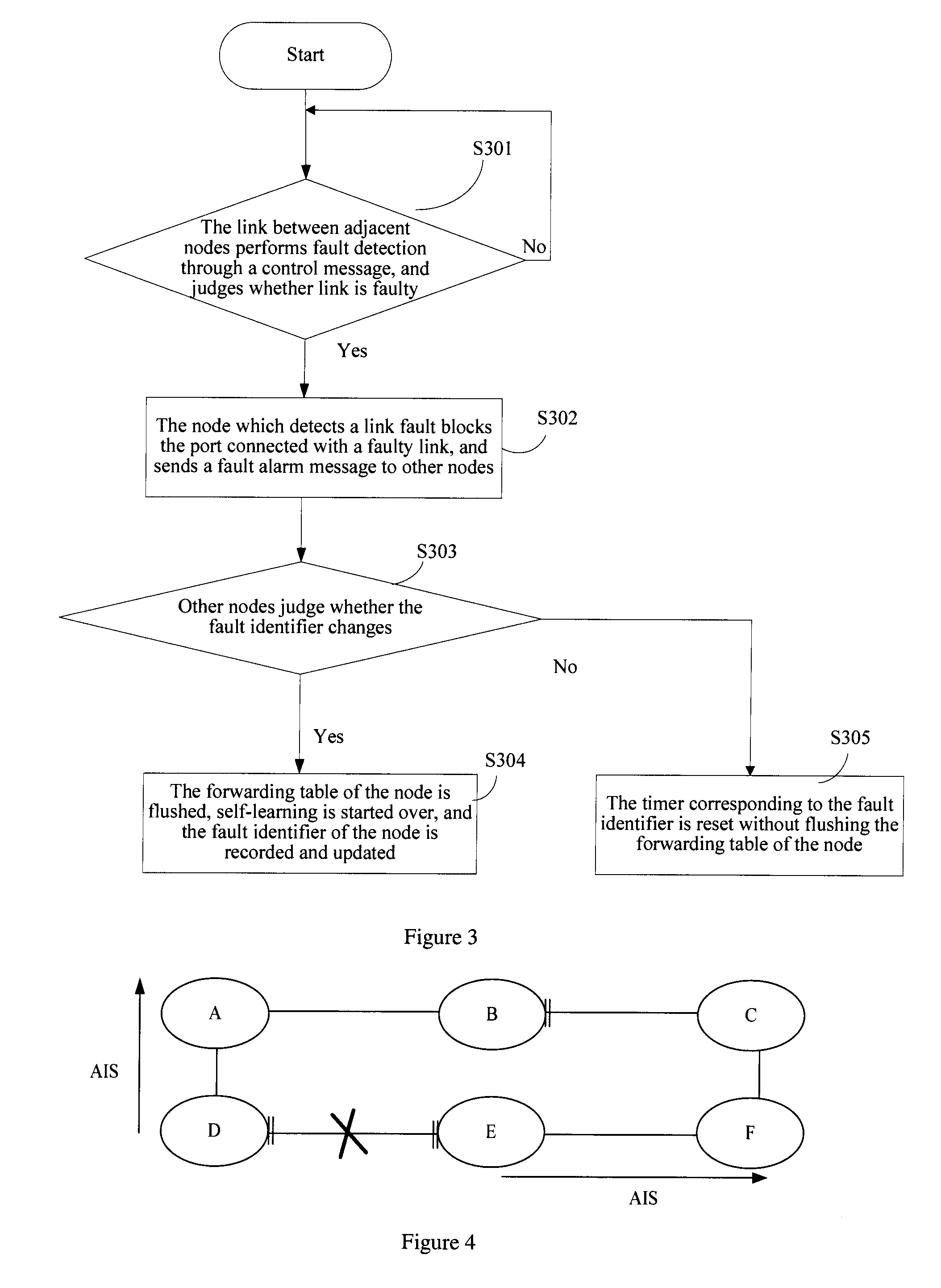
Method, apparatus and system for ring protection
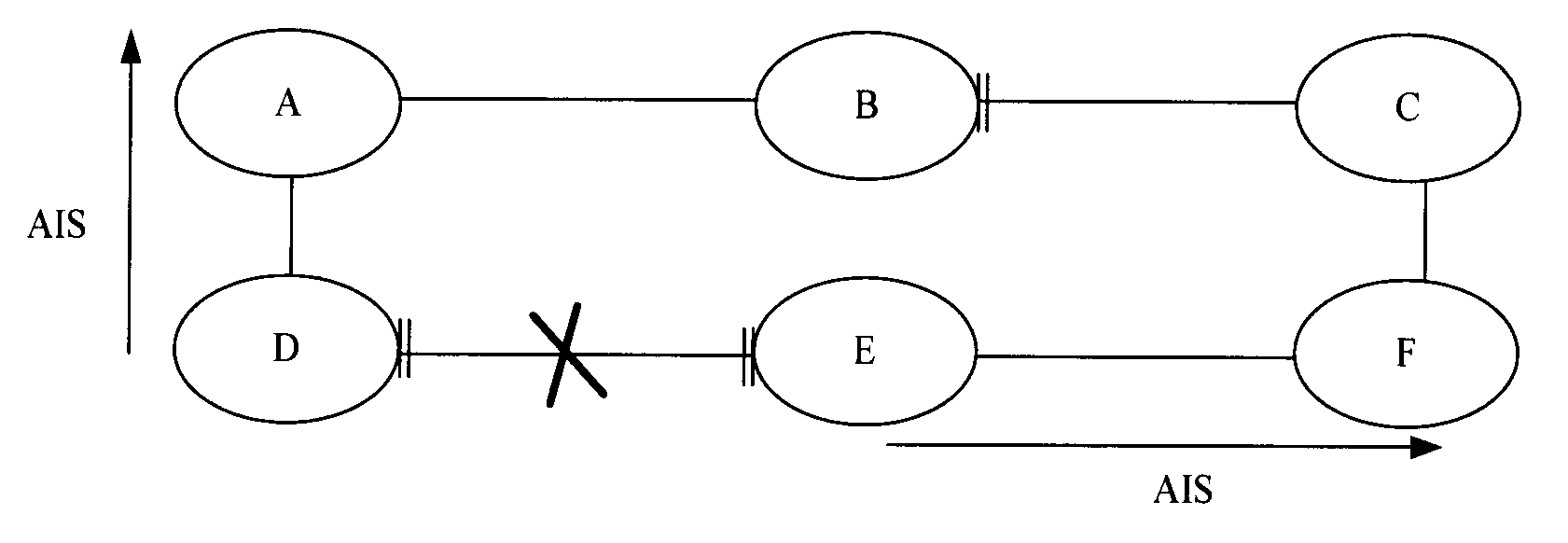
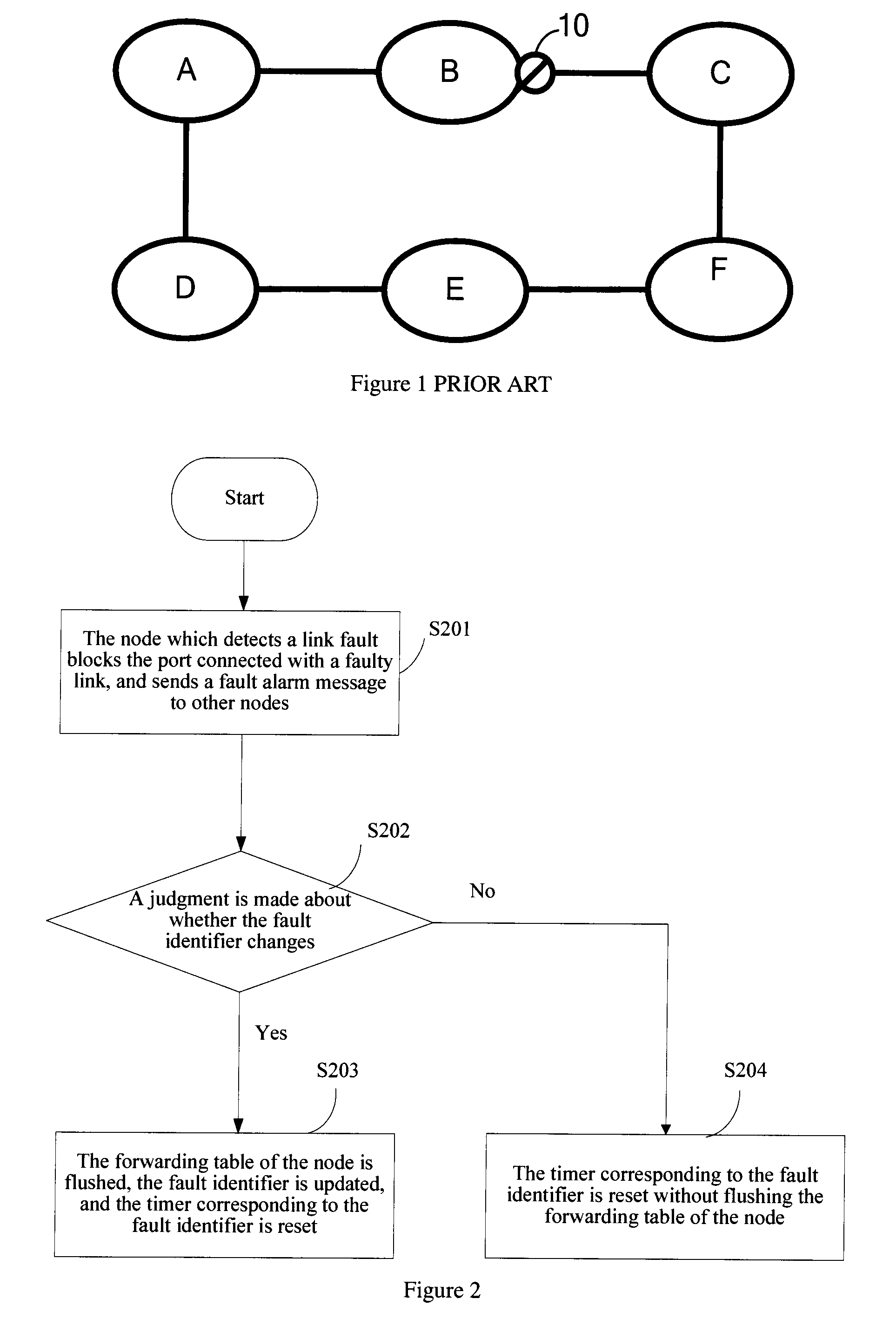
ActiveUS20090175166A1Avoid frequent clearing of a forwarding tableError preventionTransmission systemsAlarm messageRing protection
A method, apparatus and system for Ethernet Ring Protection (ERP) are disclosed. The system includes: a node which detects a link fault blocks the port connected with the faulty link after the link on the ring is faulty, and sends a fault alarm message to adjacent nodes; and the adjacent nodes judge whether the state of the node changes from the normal state to the faulty state according to the received fault alarm message, and clear the forwarding table of the node if such is the case.
Owner:HUAWEI TECH CO LTD
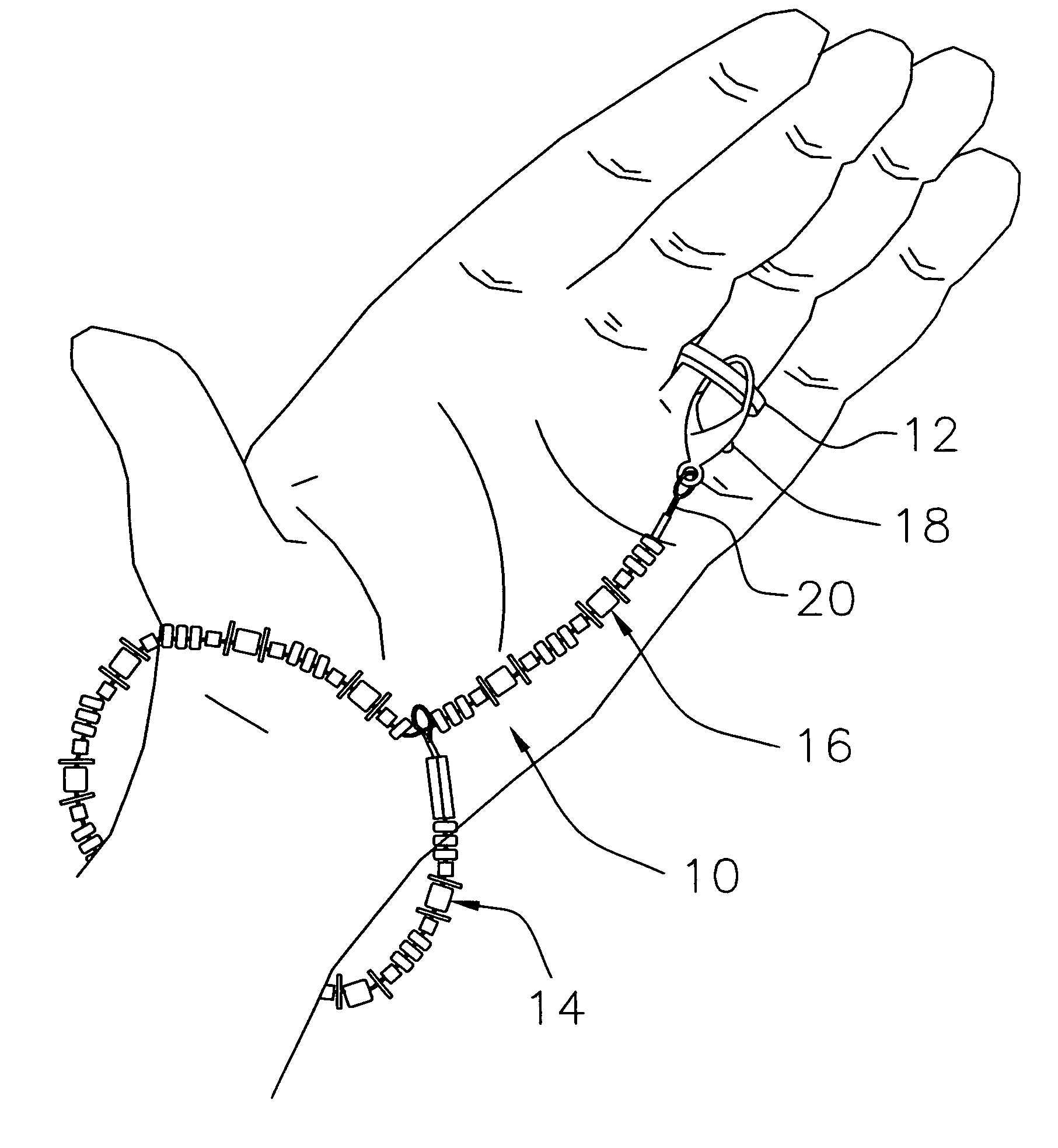
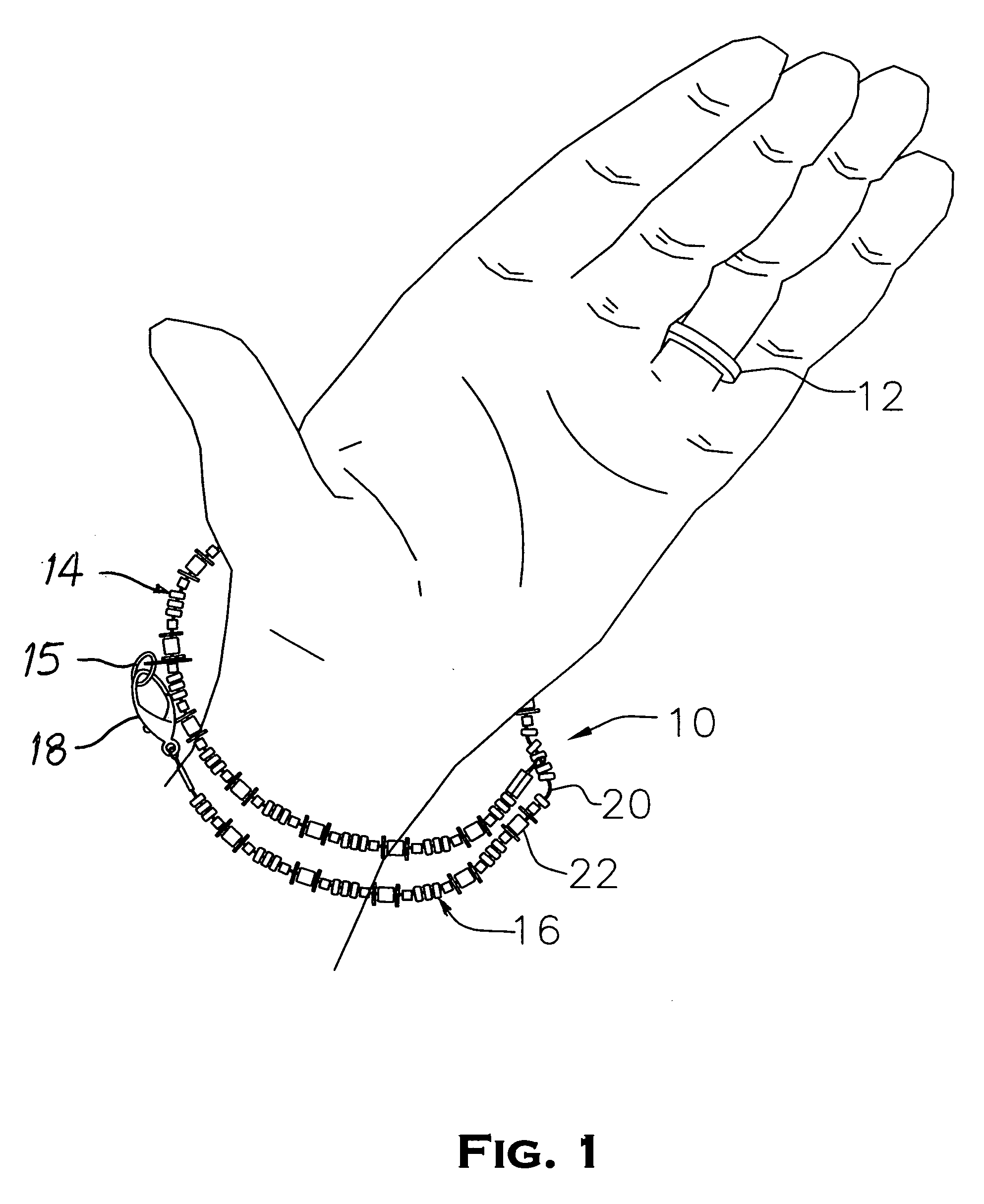
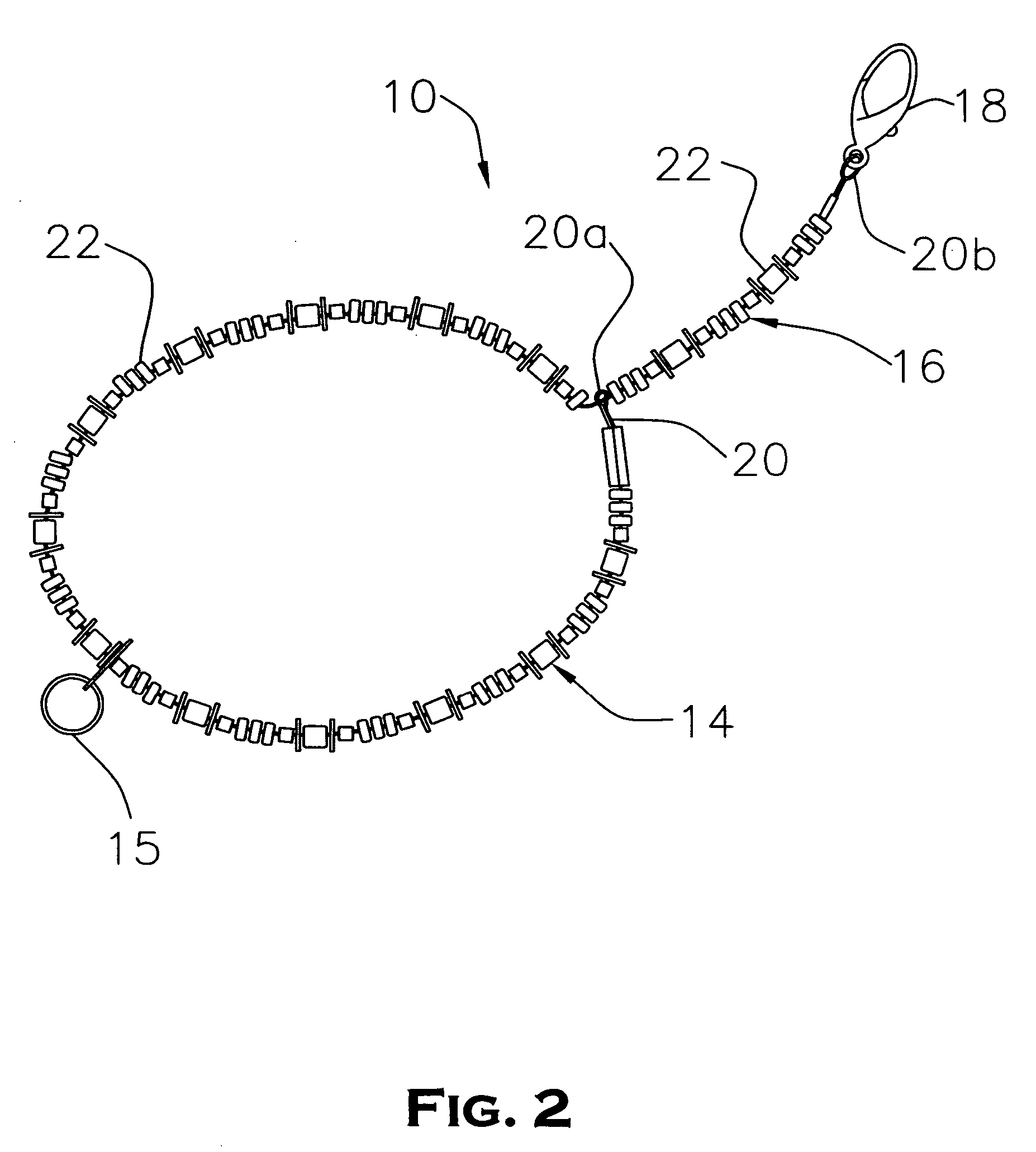
Extendable bracelet for ring protection
InactiveUS20060144083A1Stable positionEasy and attractive to wearBraceletsWrist-watch strapsSports activityClosed loop
An improved bracelet article is disclosed having a closed loop section adapted to be worn upon the wrist of a wearer and a continuous extension arm releasably connected about the loop section and extendable therefrom to engage a finger ring on the hand of the wearer and prevent its loss during physical activity. The closed loop section and the extension arm are integrally constructed from an elastic cord material threaded through a series of bead members arranged in a selected design pattern, the outer end of the extension arm having a clip member attached thereto. Under normal conditions, the extension arm is wrapped about the loop section and fastened thereto to provide a decorative bracelet to be worn on the wrist of the wearer. During the course of physical exercise or sports activity, the extension arm and its clip member are released from the loop section and stretched, preferably along the palm of the wearer, and fastened to the finger ring to prevent accidental removal and loss.
Owner:LAYTON MELISSA A
Optical inter-ring protection having matched nodes
The matched nodes provide protection for a failure in the connection between two bidirectional line switched rings. They use a secondary path in case of a primary path failure. The secondary path is set aside in either the working or protection bandwidth of the rings, thus wasting resources. The invention uses inter-ring protection mechanisms which do away with a specifically set aside secondary path between the primary and secondary nodes.
Owner:CIENA
Optical ring protection having matched nodes and alternate secondary path
InactiveUS6400859B1Wavelength-division multiplex systemsCoupling light guidesRing protectionComputer science
The matched nodes provide protection for a failure in the connection between two bidirectional line switched rings. They use a secondary path in case of a primary path failure. The secondary path is set aside in either the working or protection bandwidth of the rings, thus wasting resources. The invention uses a dedicated secondary path between the primary and secondary nodes. With the invention, no ring protection mechanisms are compromised and the ring bandwidth is not wasted. Middle nodes also realize full add / drop capabilities.
Owner:POPKIN FAMILY ASSETS L L C +1
Method For Realizing Many To Many Protection Switching Of Ring Network
ActiveUS20080107416A1Reliable networkImprove reliabilityError preventionFrequency-division multiplex detailsRing protectionLoop network
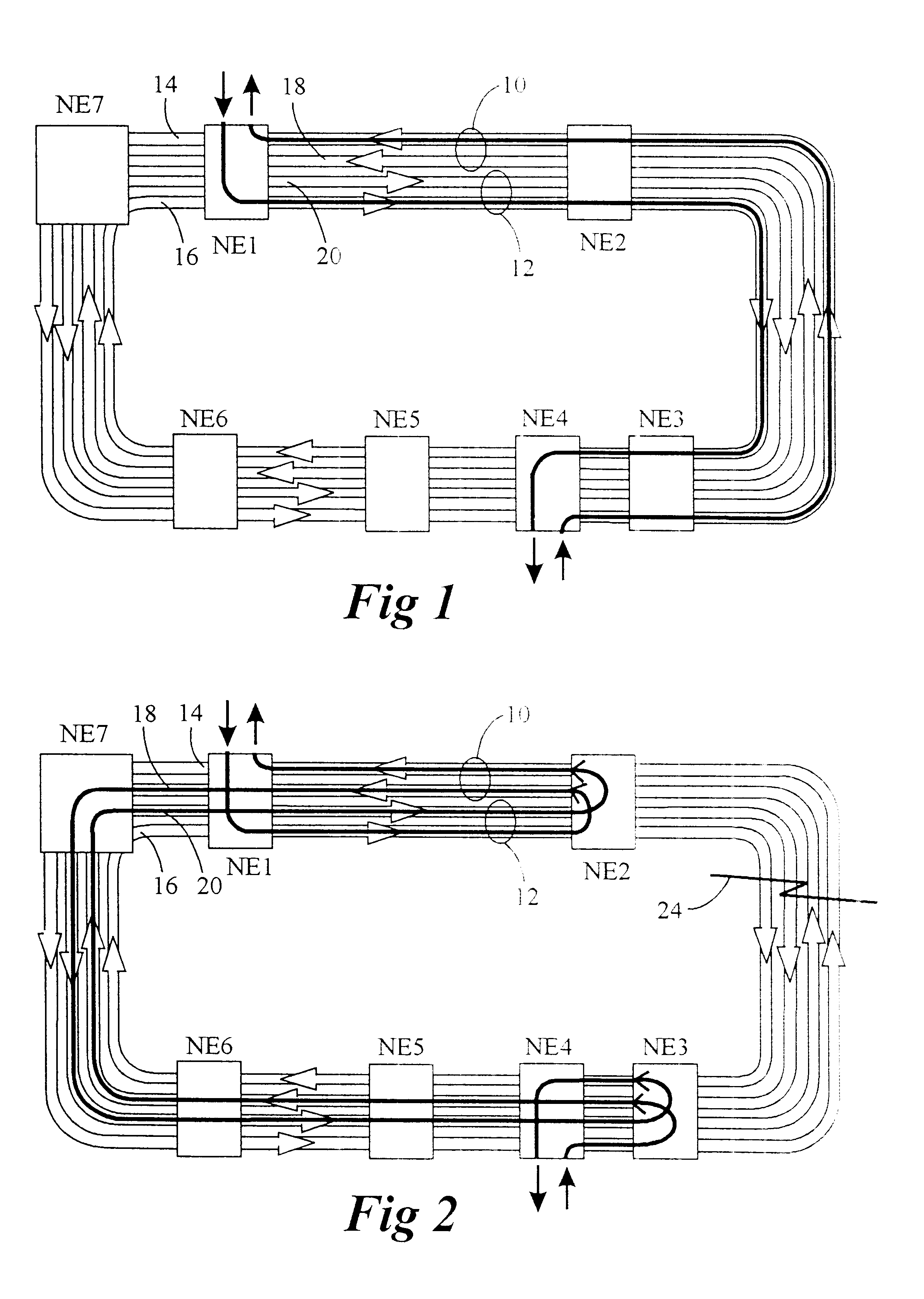
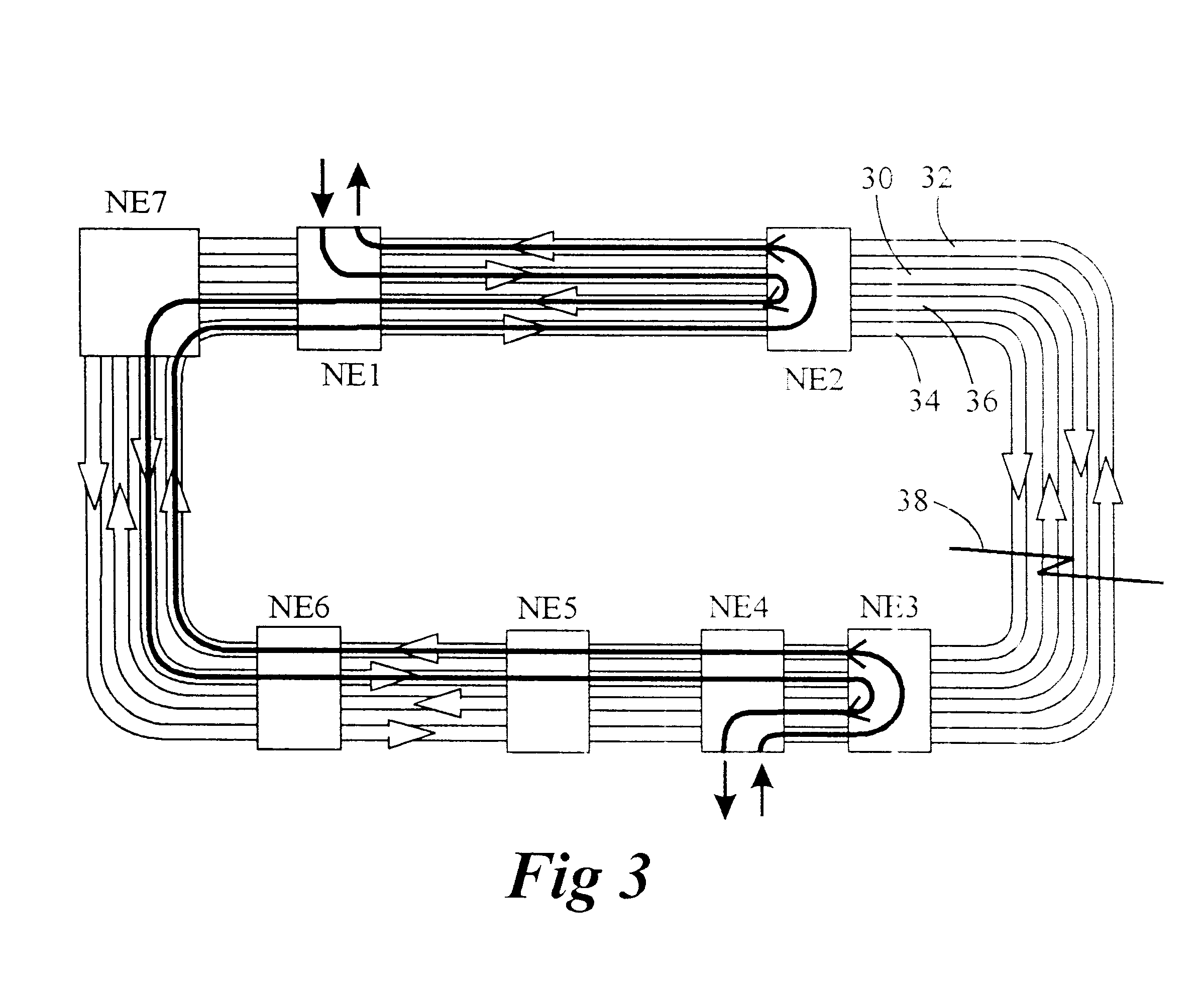
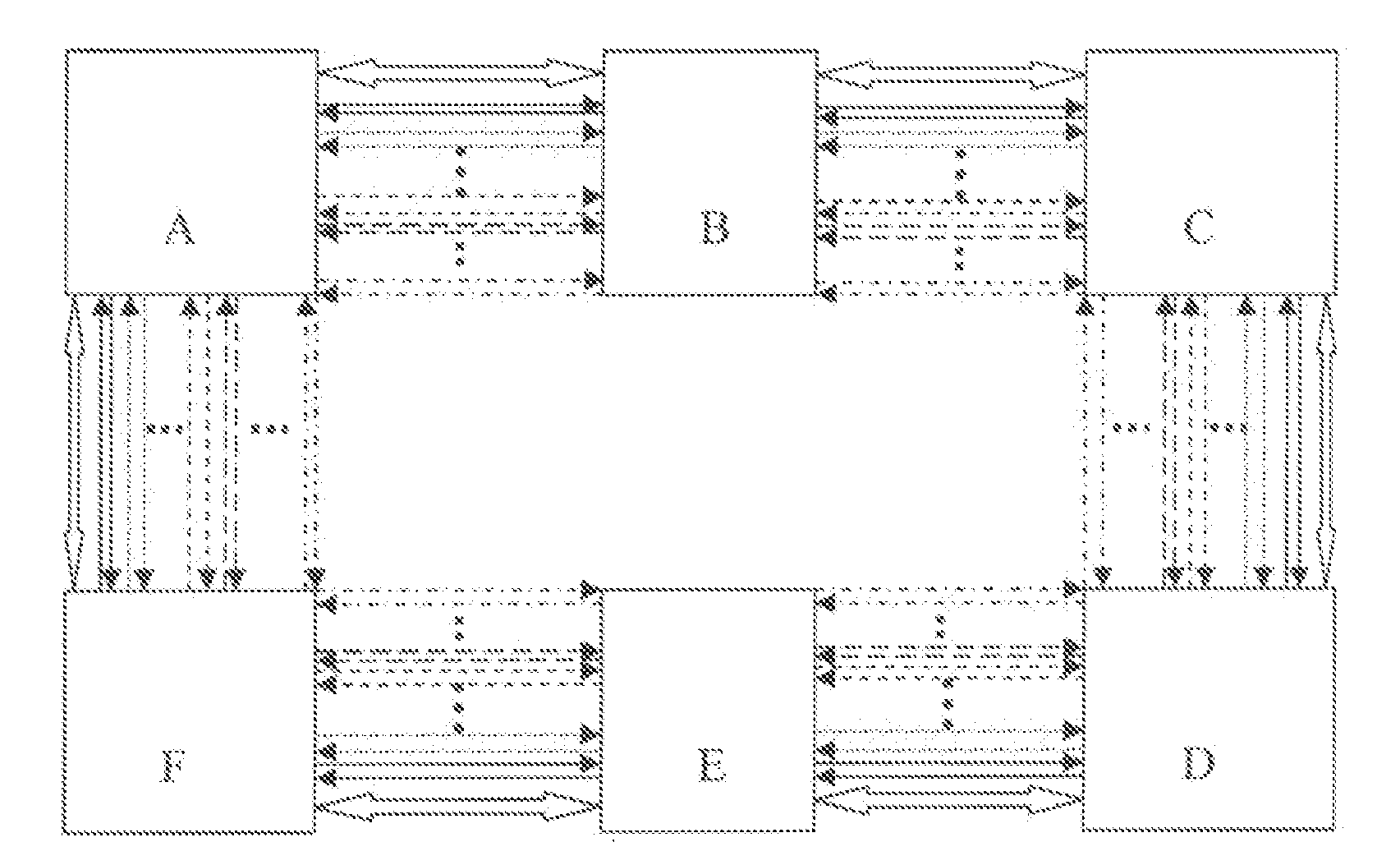
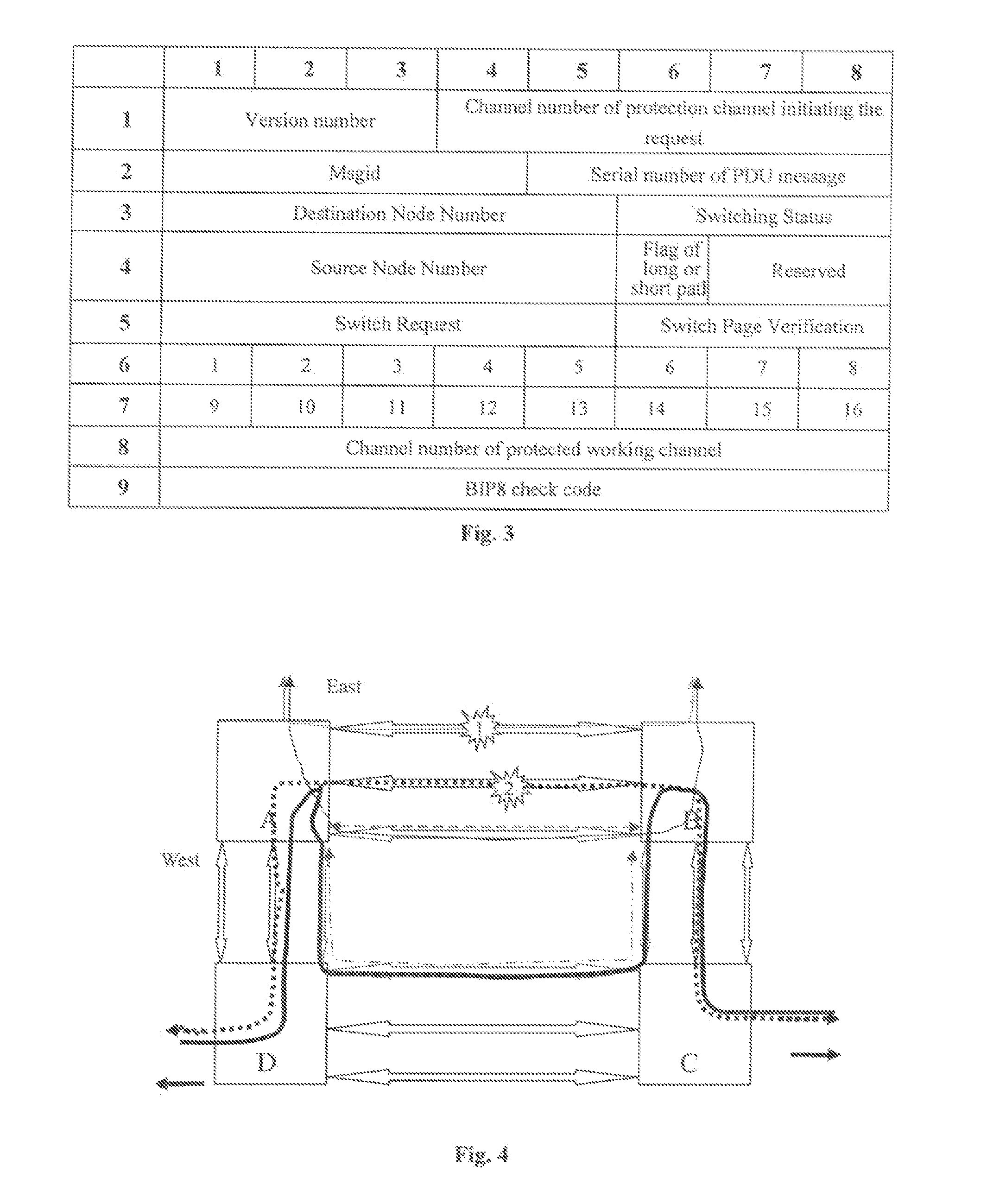
A method for realizing many to many protection switching operation of ring network including; determining information of a switch request of M:N protection switching of the ring network, a destination node of the switch request a source node of the switch request a flag of long or short path, a status of bridging and switching, a channel number of protected working channel and utilization condition of protection channels; carrying the information in a signaling and transferring it on the ring network; upon receipt of the signaling, performing the M:N protection switching of the ring network by a ring network node according to the information in the signaling. Therefore, the format of APS protocol signaling provided in this invention includes the information necessary for protection switching. This invention also provides an effective transmission approach of APS protocol signaling for protection switching.
Owner:HUAWEI TECH CO LTD
Processing method for loop network protection
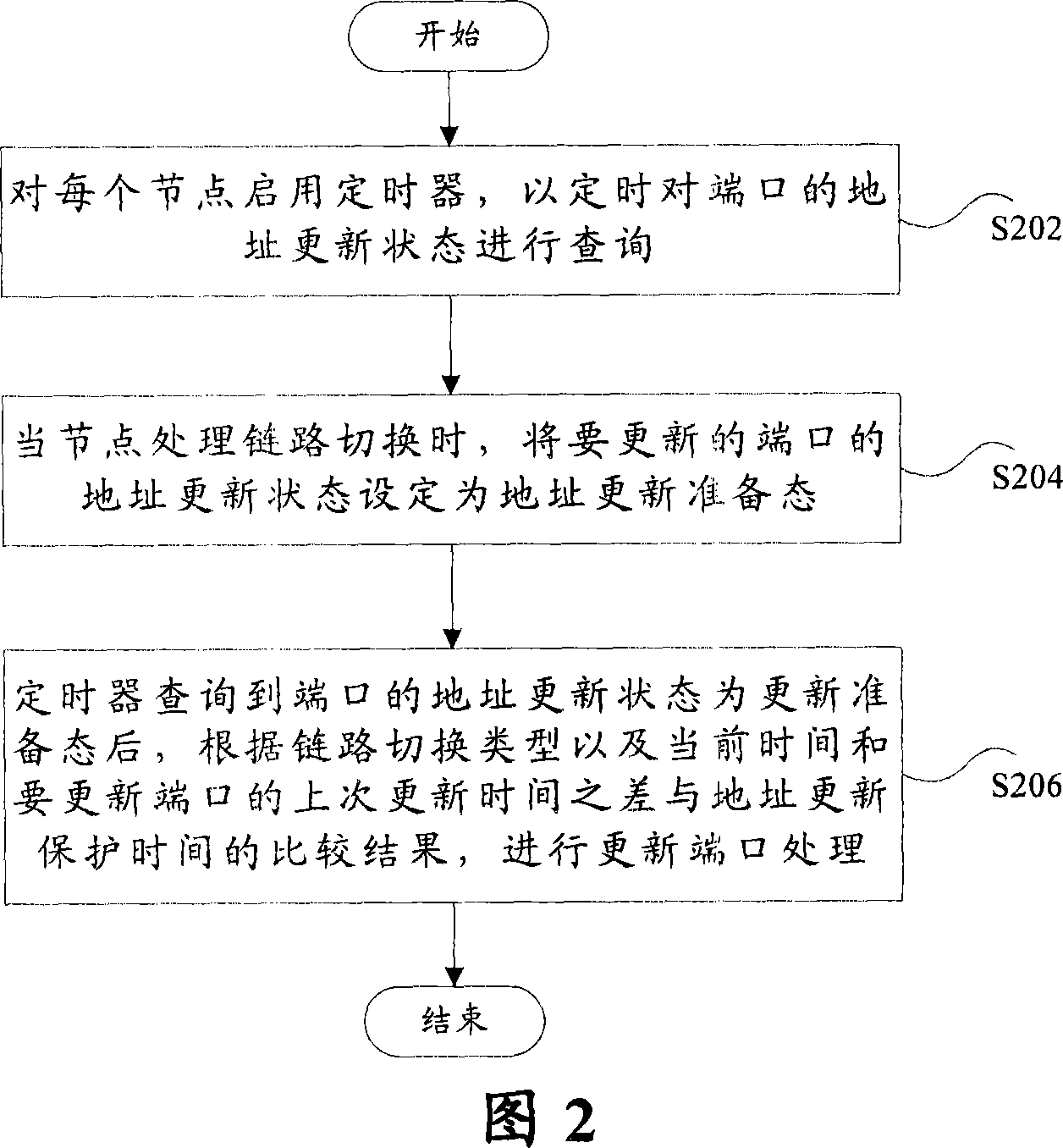
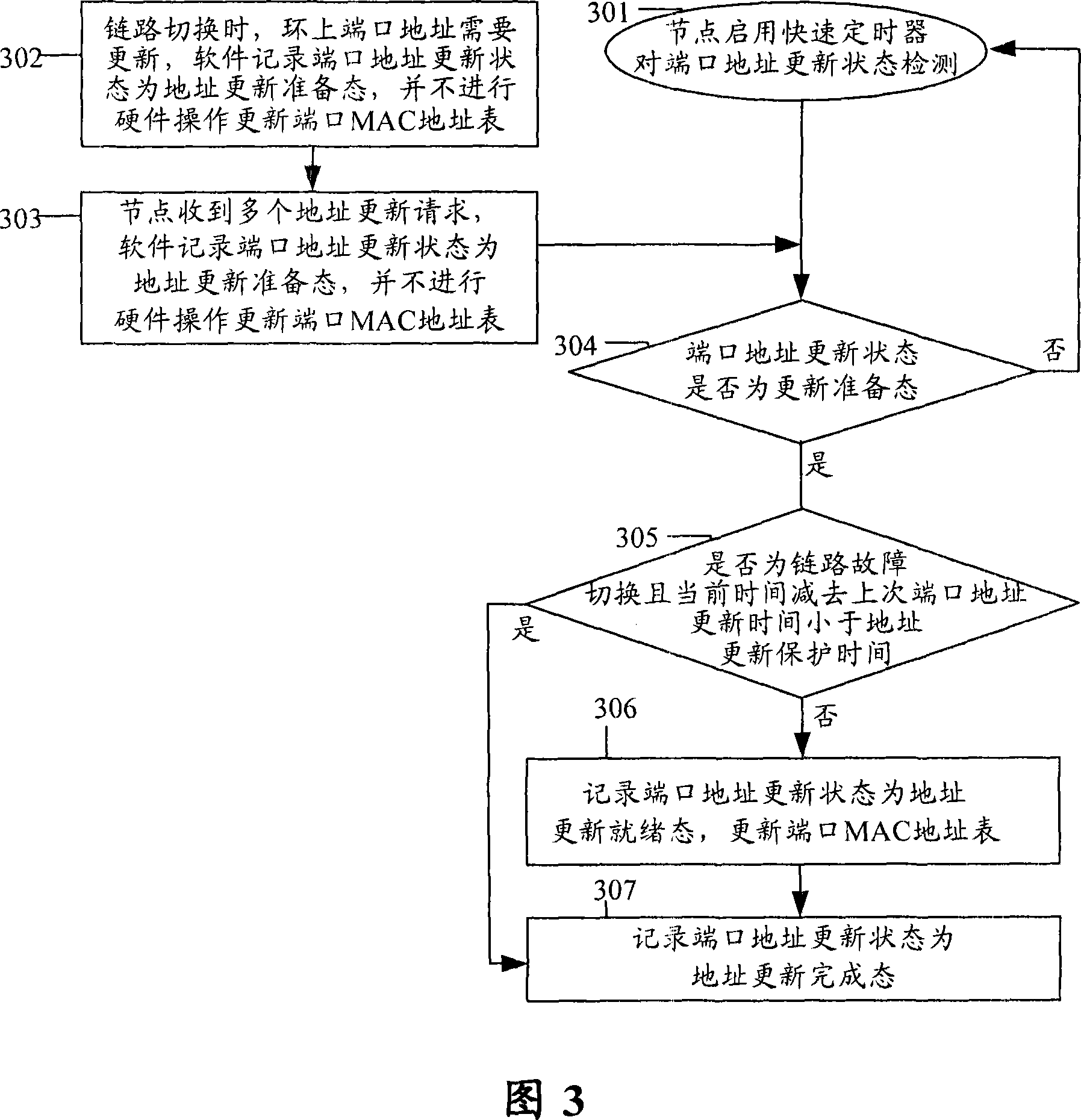
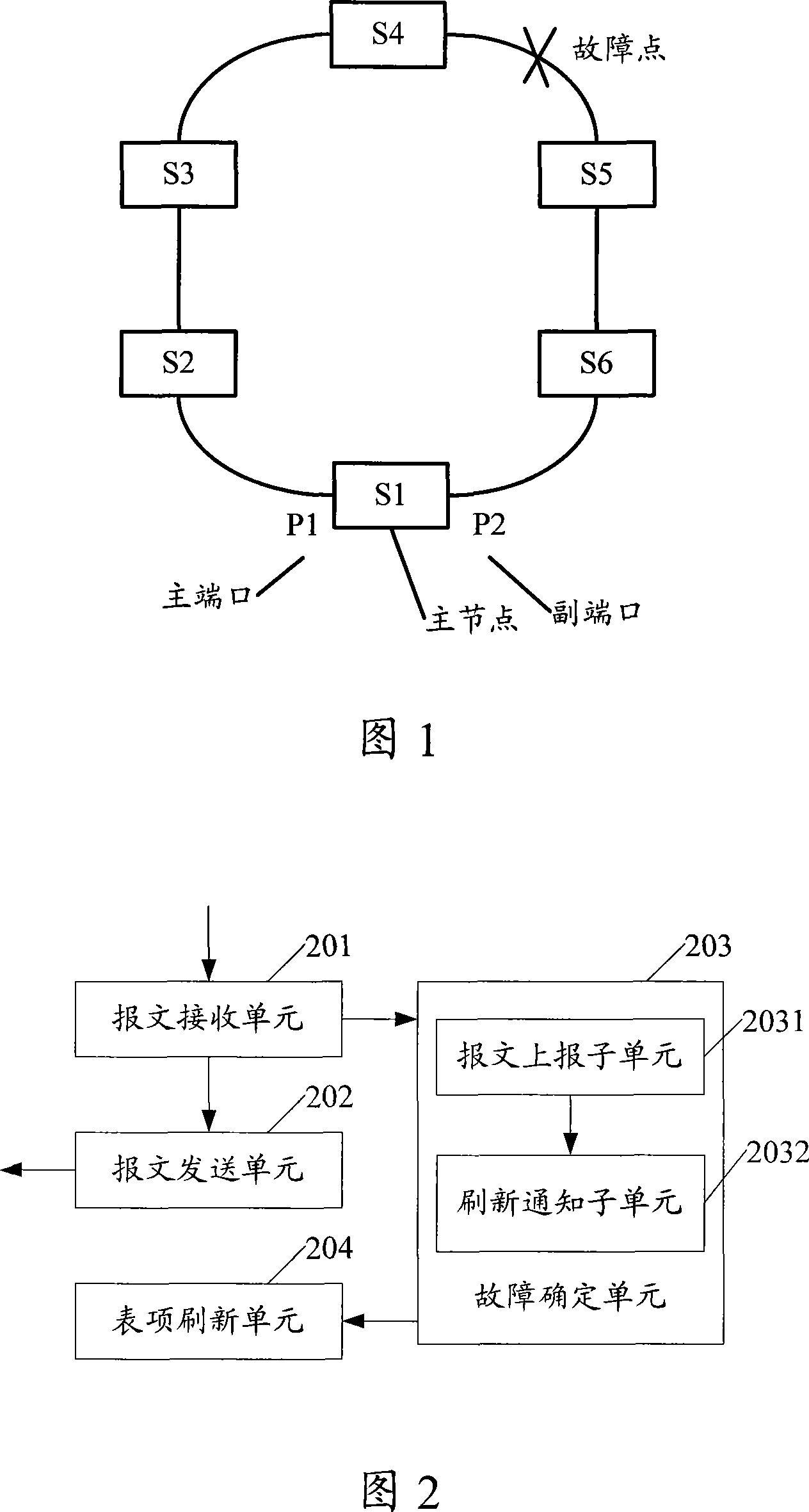
ActiveCN101035047AReduce the number of operationsImprove hardware efficiencyPulse modulation television signal transmissionError preventionReal time servicesRenewal time
The invention provides a ring protection processing method, comprising the steps of: starting a timer for each node and regularly inquiring about address updating state of each port; when node processing link is switched, setting the address updating state of an to-be-updated port as an address updating preparing state; and the timer finds the address updating state of the port is an updating preparing state and then makes port updating processing, according to the link type and the comparative result of the difference between the current time and last updating time of the to-be-updated port and the address updating protection time. And the invention quickly updates MAC address table of a port when making link switching, reducing number of hardware operating times and raising hardware efficiency, and fully using link resources, thus meeting the requirements of highly real-time services for ring protection systems.
Owner:ZTE CORP
Generalized service protection systems and methods
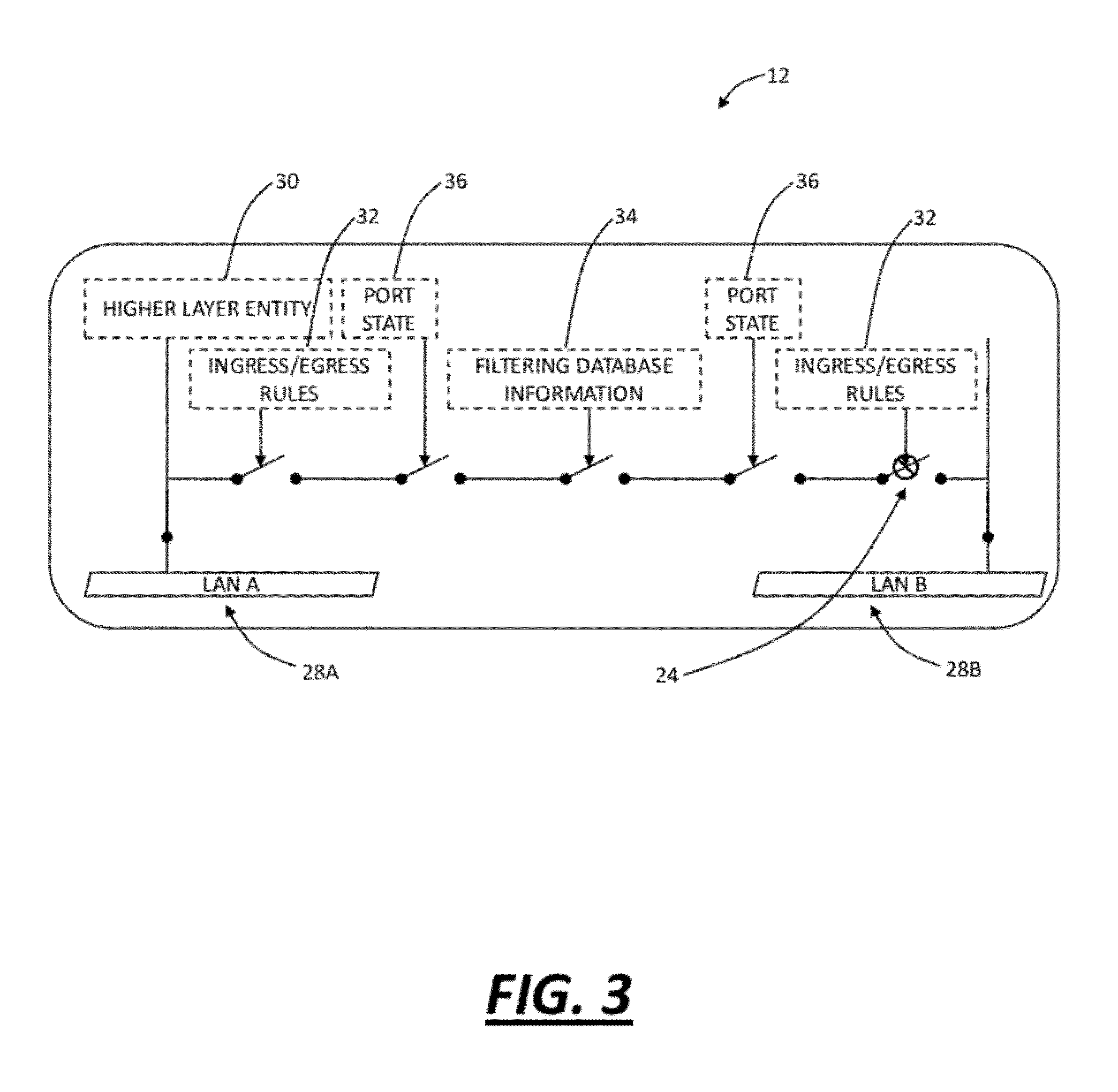
ActiveUS20130258840A1Multiplex system selection arrangementsError preventionForwarderProtection system
A node includes a first port configured to be selectively blocked and unblocked; a second port configured to be selectively blocked and unblocked; a forwarder between the first port and the second port; a management channel between the first port and the second port, wherein the selective blocking and unblocking of the first port and the second port is based on the management channel; and a data channel between the first port and the second port, wherein the data channel utilizes an arbitrary service identifier. A method can include operating a ring with Ring Protection Switching comprising a forwarding mechanism and a blocking mechanism that are independent and decoupled entities therebetween, wherein the ring includes a management channel and a data channel that each utilize an arbitrary service identifier.
Owner:CIENA
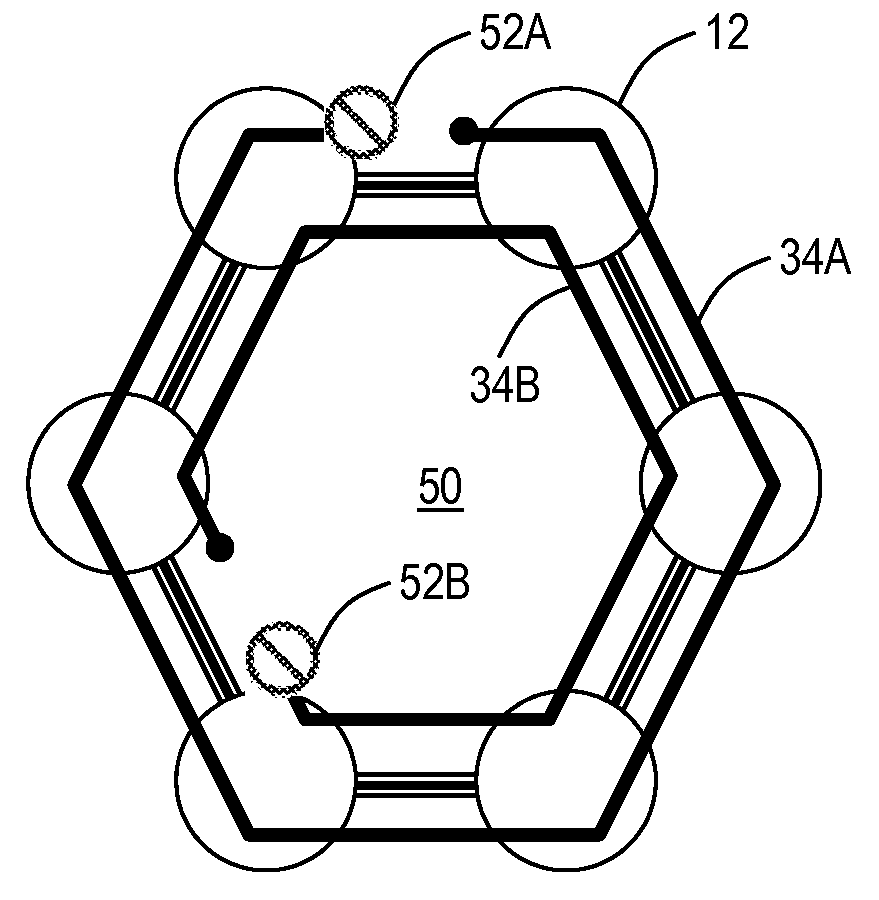
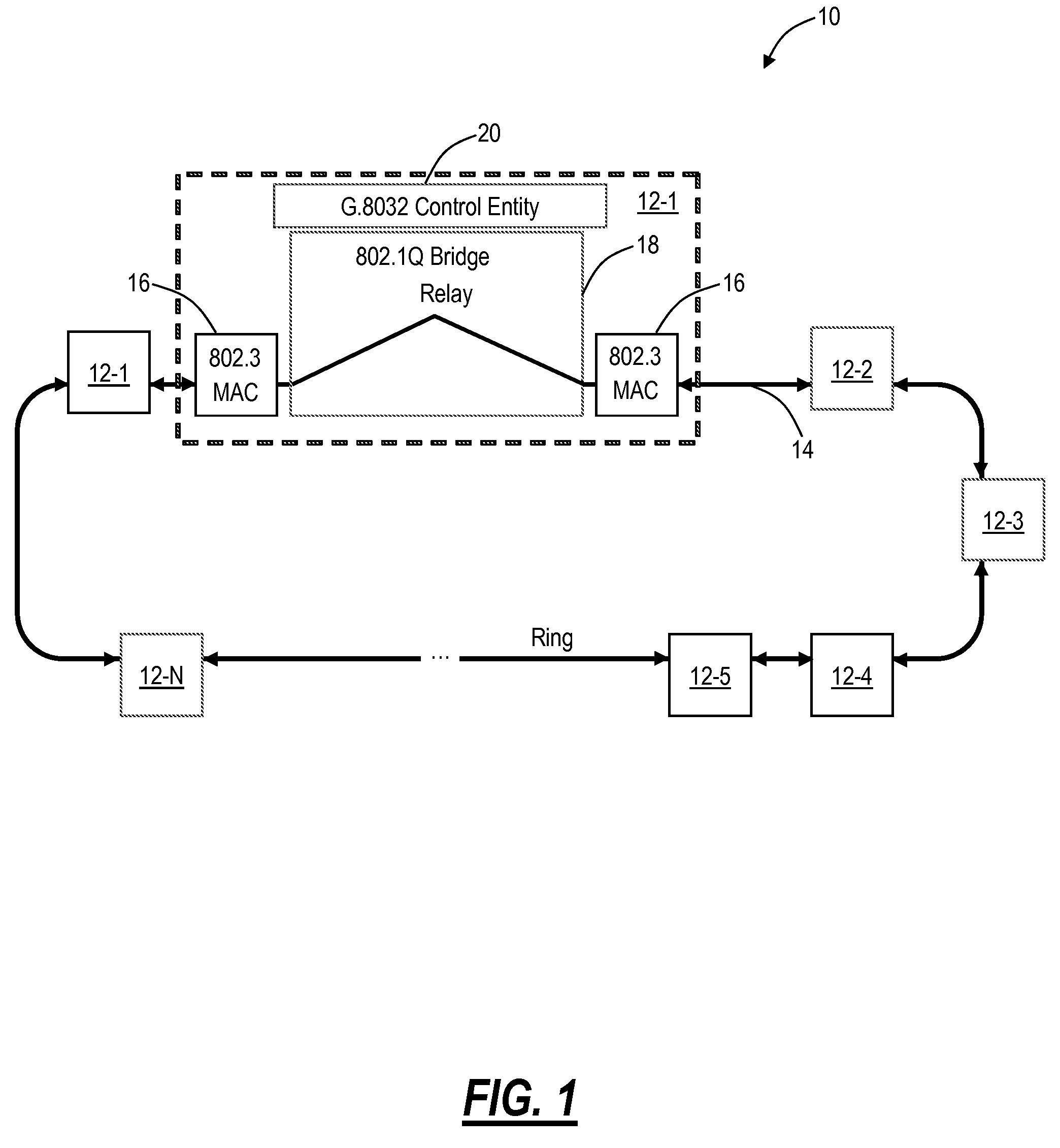
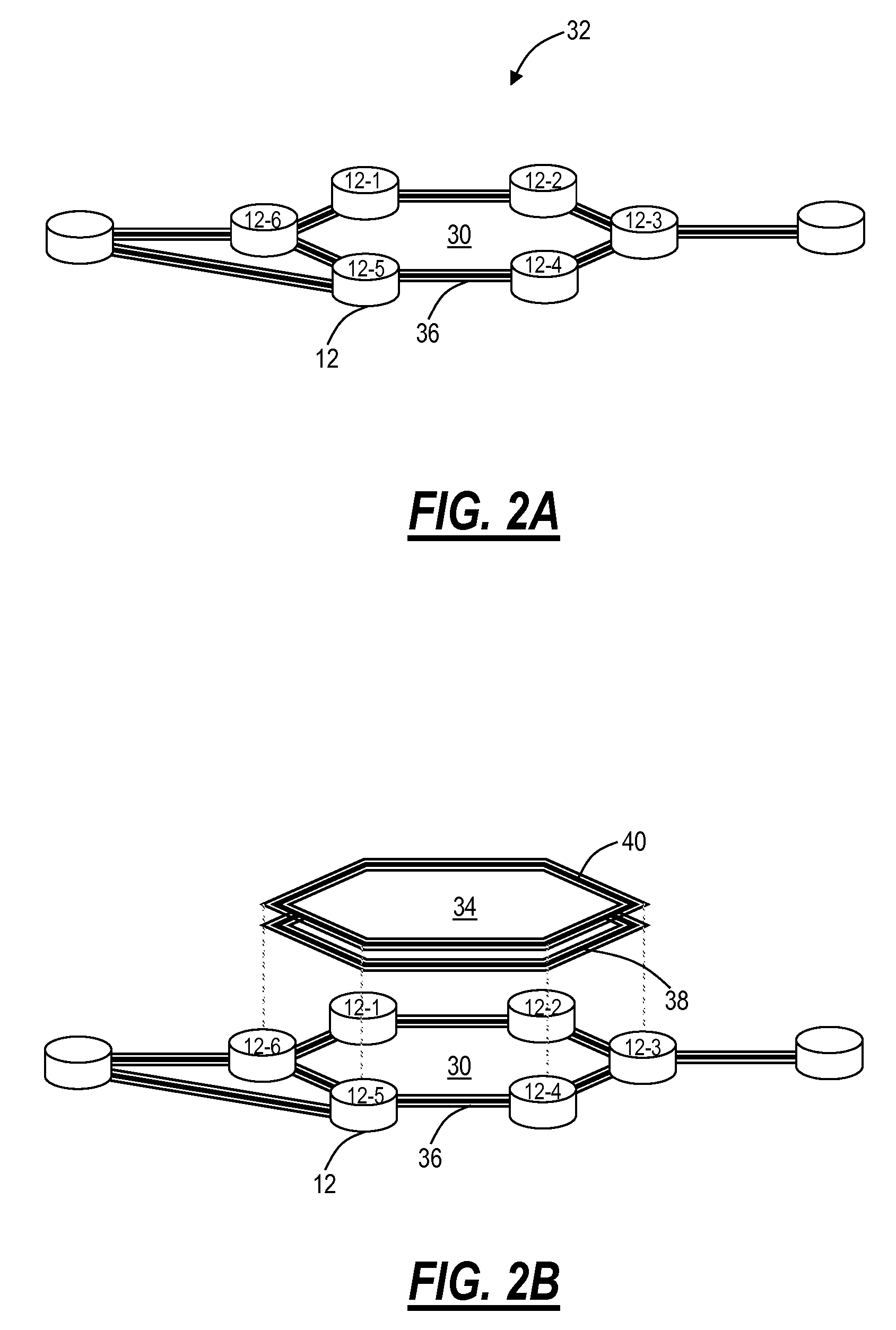
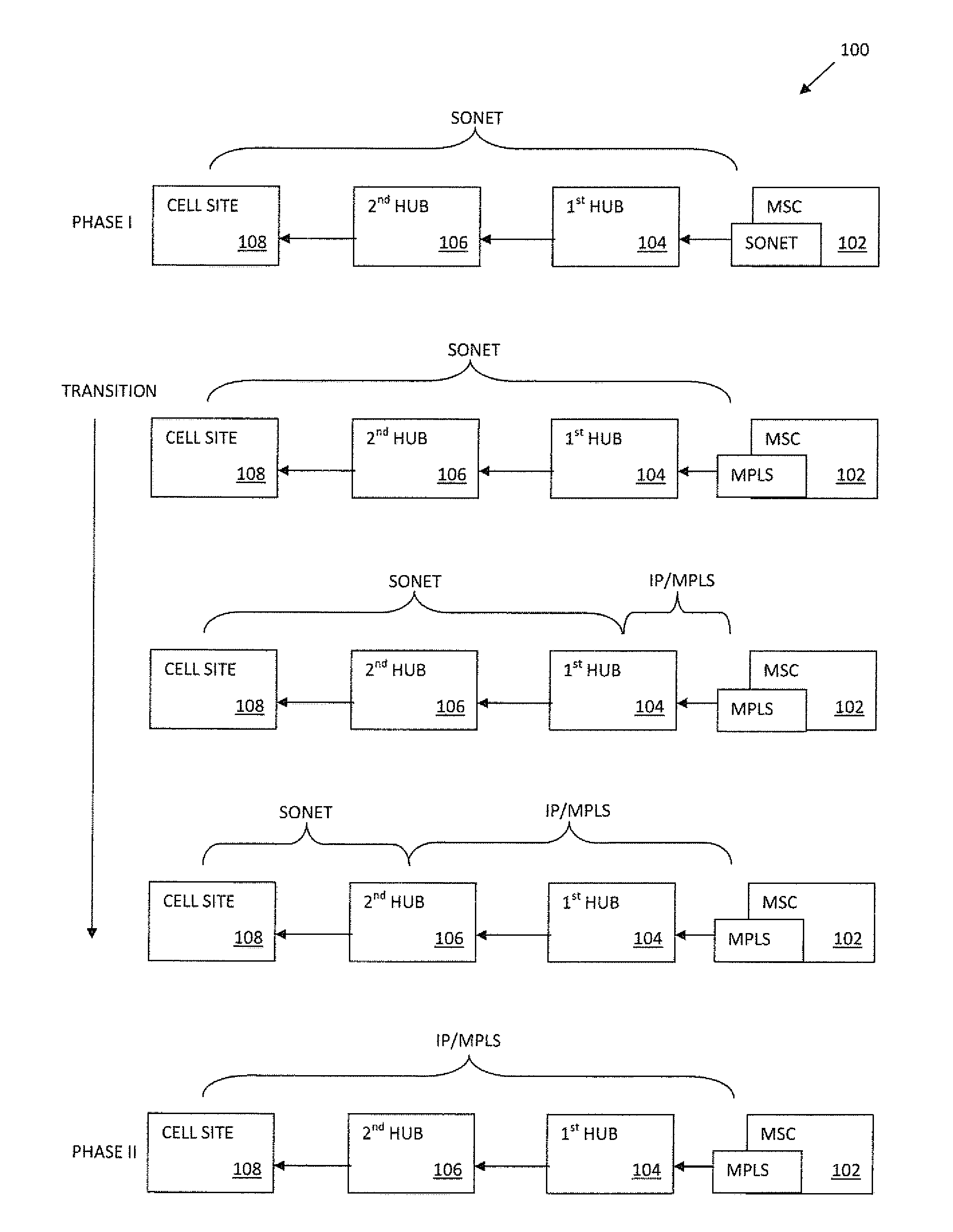
Apparatus and methods for intelligent deployment of network infrastructure based on tunneling of ethernet ring protection
ActiveUS20150036483A1Error preventionFrequency-division multiplex detailsMultiprotocol Label SwitchingCarrier Ethernet
Apparatus and methods for intelligent deployment and transition from a first network infrastructure to a second network infrastructure. Various embodiments of the present disclosure are directed to, among other things, methods and apparatus that leverage tunneling of Ethernet ring network technologies. In one exemplary embodiment, a modified implementation of the ITU-T G.8032 data link protocol is combined with Multiprotocol Label Switching (MPLS) transport networks to provide Carrier Ethernet and Retail Ethernet services. Unlike existing network infrastructure, the exemplary MPLS network aggregates traffic between the base station (BS) and mobile switching center (MSC) within a logical ring network topology.
Owner:TIME WARNER CABLE ENTERPRISES LLC
Method for automatically discovering Ethernet ring and generating ring
The invention discloses a method for automatically discovering an Ethernet ring and generating a ring as well as a method for implementing automatic protection on the ring based thereof. The method comprises the steps of: voting a network topology root node according to a spanning tree algorithm, transmitting a ring discovering message from a ring port to the outside through the main node of the ring, checking whether the source node of the message is self or not through the node receiving the ring discovering message, if not, then respectively transmitting the message out through every non-blocking port and adding self mark, an inlet port and an outlet port in the message, if so, then checking the integrality of the ring through a polling-based mechanism after the ring discovering is accomplished and combining with the port state monitoring to implement fault detection, and implementing ring protection switching during link fault and resuming when the fault disappears. The method for automatically discovering the Ethernet ring and generating the ring as well as the method for implementing automatic protection on the ring based thereof are based on spanning tree protocol and Ethernet ring protocol, can accomplish automatic ring discovering, collocation and protection on complex network topology, and can solve the dynamic change problem of the network topology, thereby realizing automatic Ethernet ring planning and maintaining, and adapting to the further evolution and development of the Ethernet ring.
Owner:FENGHUO COMM SCI & TECH CO LTD
Inter-ring protection for shared packet rings
A method for providing inter-ring protection in shared packet rings includes identifying an active node which is connected to a ring interconnect node on the same ring as the active node and connected to a peer node on a different ring with a ring interconnecting link. When the active node is in active mode and receives notification of a failure of the ring interconnecting link or peer node, the active node sends a message to the ring interconnect node so that the ring interconnect node switches from standby mode to active mode. The active node is then changed to standby mode.
Owner:CISCO TECH INC
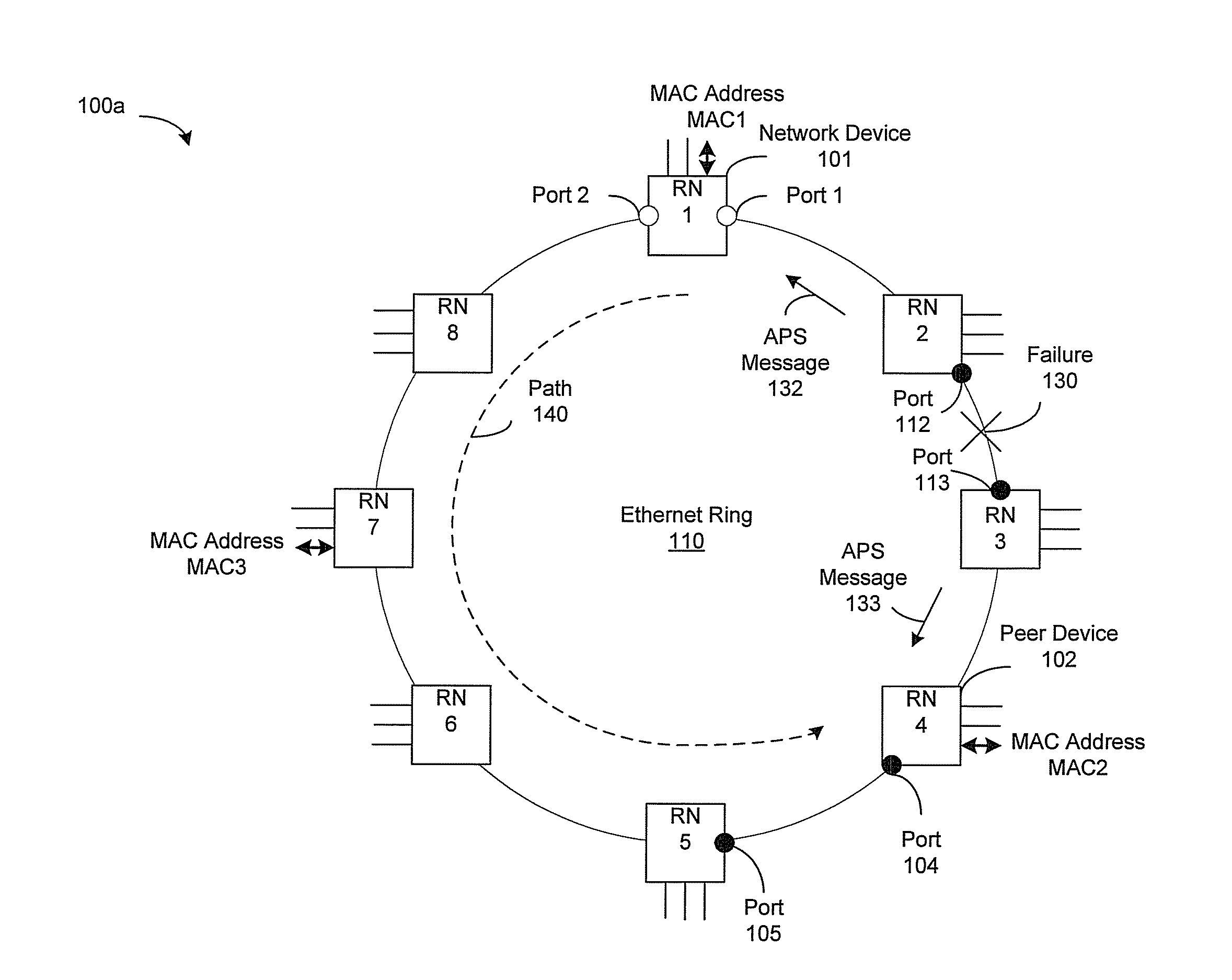
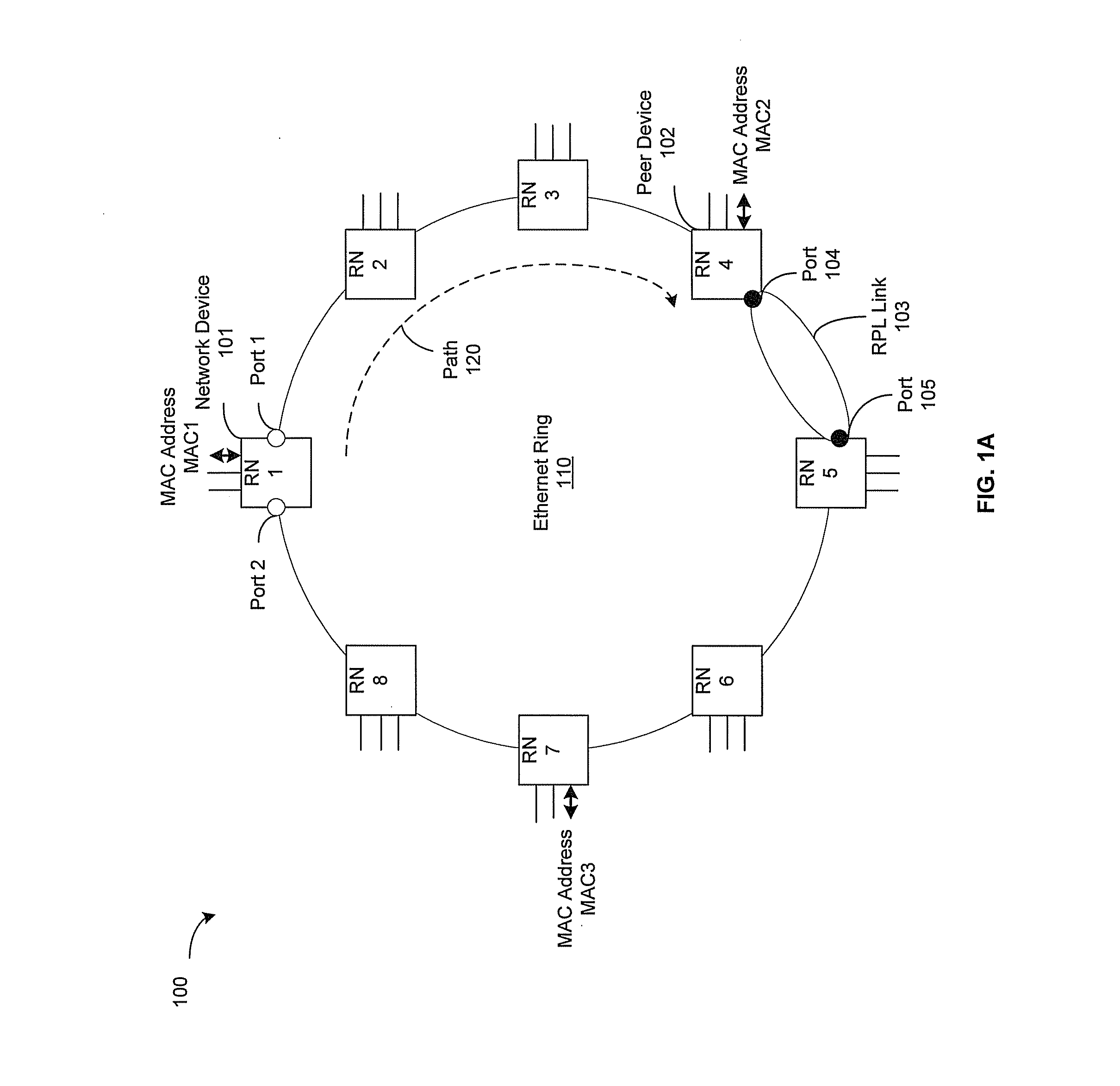
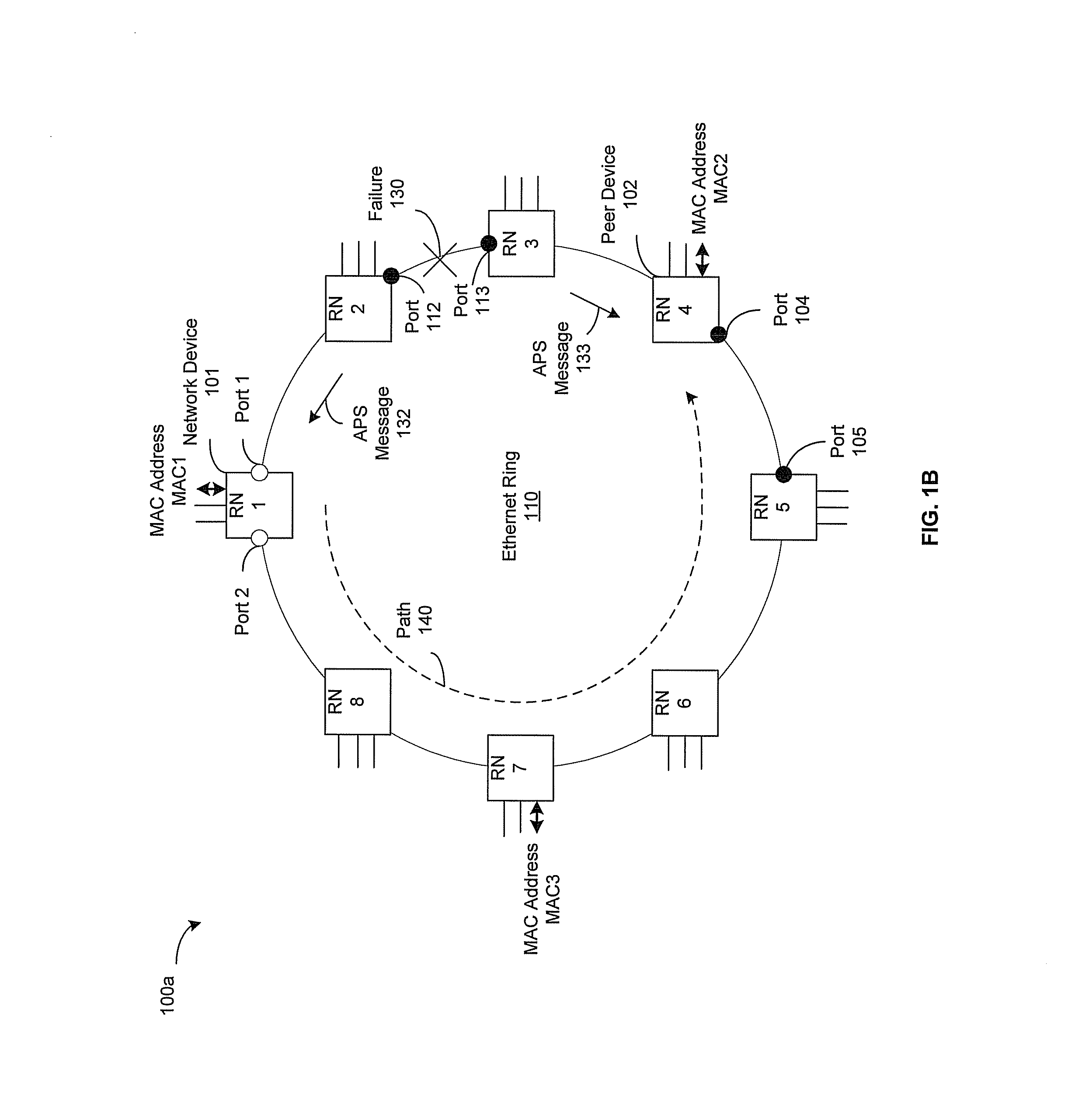
Ethernet Ring Protection without MAC Table Flushing
A network device located in an Ethernet ring may be operable to determine binding between a MAC address and a peer device in the Ethernet ring. The binding may indicate that the MAC address is behind the peer device. When an Ethernet ring failure occurs, the network device may be operable to update forwarding information based on a ring topology of the Ethernet ring, a position of the failure on the Ethernet ring and the binding. The forwarding information may indicate which ring port that is used on the network device to forward MAC frames to a destination corresponding to the MAC address. The network device may then forward the MAC frames based on the updated forwarding information. The Ethernet ring may utilize a VLAN frame format, a Q-in-Q frame format or a MAC-in-MAC frame format. The forwarding information may comprise a MAC table and / or a protection table.
Owner:AVAGO TECH INT SALES PTE LTD
Optical ring protection apparatus and methods
An optical communication system comprising plural optical communication paths, a passive optical coupler, and at least one optical node. The passive optical coupler has a plurality of inputs coupled through the passive optical coupler to an output of the passive optical coupler, and each input is coupled in a corresponding one of the optical communication paths. Each optical node comprises plural optical line terminals, each of which is interposed in a corresponding at least one of the optical communication paths. Each optical line terminal is operable to either (a) substantially prevent an optical signal propagating in that corresponding at least one optical communication path from reaching a corresponding input of the passive optical coupler through the at least one optical communication path, or (b) permit the optical signal to propagate in that corresponding at least one optical communication path towards the corresponding input of the passive optical coupler.
Owner:TELLABS OPERATIONS
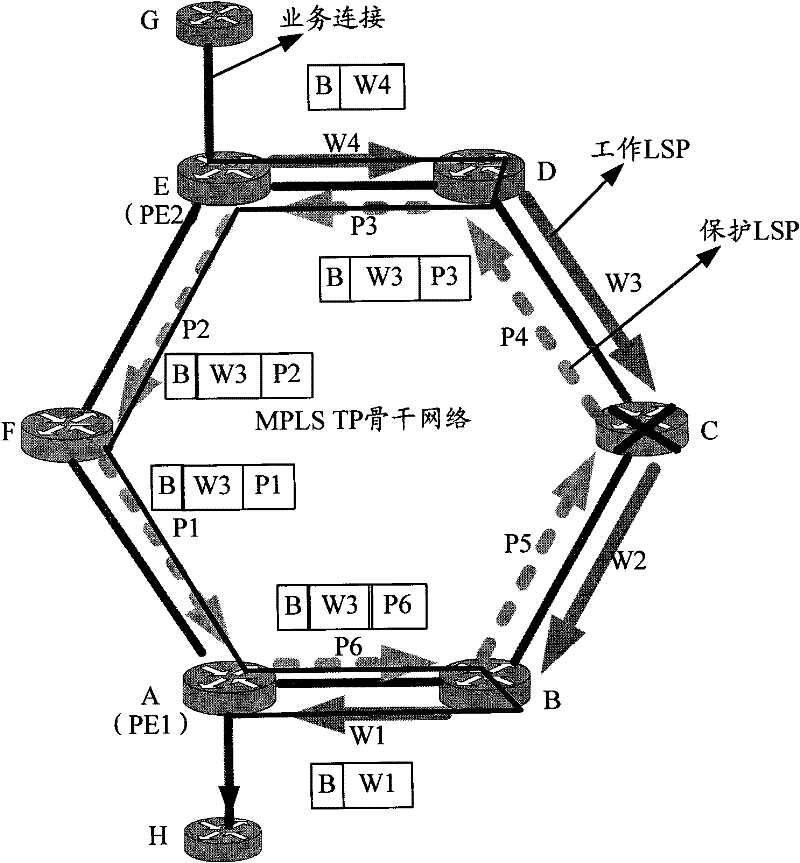
Ring protection switching method adopting multi-protocol label switching transport profile (MPLS TP) and node
ActiveCN102201985AEasy to deployReduce complexityData switching networksMulti protocolLabel switching
The invention discloses a ring protection switching method adopting a multi-protocol label switching transport profile (MPLS TP) and a node. The method comprises the following steps of: deploying a totally-enclosed protection LSP (Label Switching Path) on an MPLS TP ring, wherein the LSP is shared by all working LSPs and is in a direction opposite to all working LSPs, and different merging labels are distributed for every working LSP; when a first node receives a user message from a node outside the ring or the working LSPs under the condition that the first node and a second node on the ring are not communicated with an adjacent node, the first node on the protection LSP is a downstream node of the adjacent node and the second node is an upstream node of the adjacent node, pressing the merging label into the message or switching a working label on the message into the merging label and adding a protection label on the message; and when the message reaches the second node from the protection LSP and the protection label of the message is popped from the second node, switching the merging label of the message into the working label. Under the condition that only one protection LSP is used, the protection switching complexity is lowered.
Owner:NEW H3C TECH CO LTD
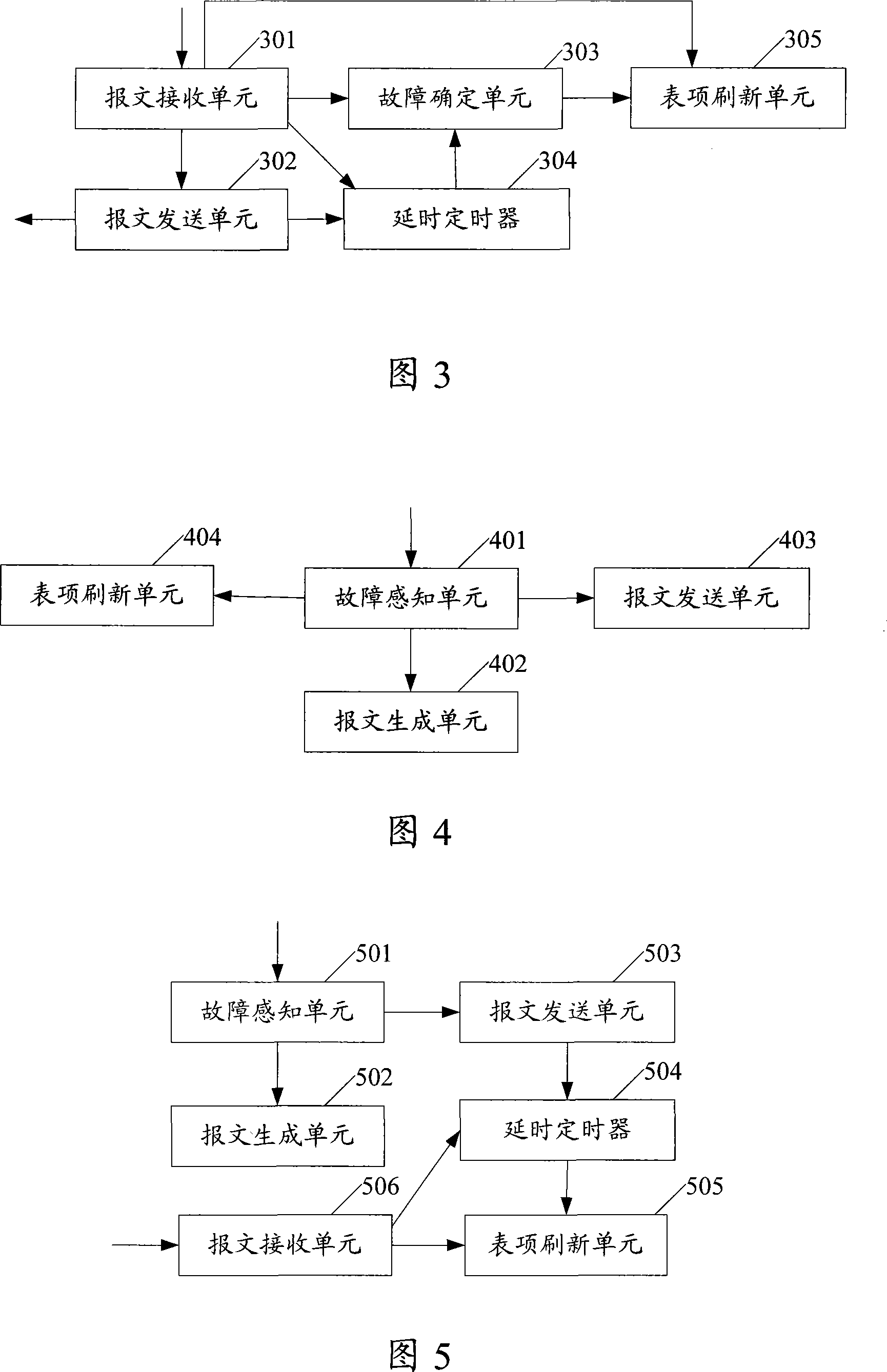
Ethernet loop network protection method and transmission node
The invention provides a method for Ethernet ring protection and transmission node of Ethernet ring. When fault occurs in the ring, the transmission node of the Ethernet ring which senses the fault generates message of Ethernet ring fault and sends the message of Ethernet ring fault in the ring and refreshes its own media access control item, or, a delay timer is started at the same time when the message of Ethernet ring fault is being sent. When the delay timer reaches the timing time-period, its own media access control item is refreshed. When other transmission nodes receive the message of Ethernet ring fault, the transmission nodes send the message of Ethernet ring fault and determine that fault really occurs in the ring according to the message of Ethernet ring fault. When fault really occurs in the ring, its own media access control item is refreshed, or, the delay timer is started at the same time when the message of Ethernet ring fault is being sent, when the delay timer reaches the timing time-period, its own media access control item is refreshed. Therefore, operation interrupt time caused by the untimely refreshment of the MAC item by the transmission nodes can be reduced.
Owner:NEW H3C TECH CO LTD
Environmental-friendly accessing method and environmental-friendly accessing network
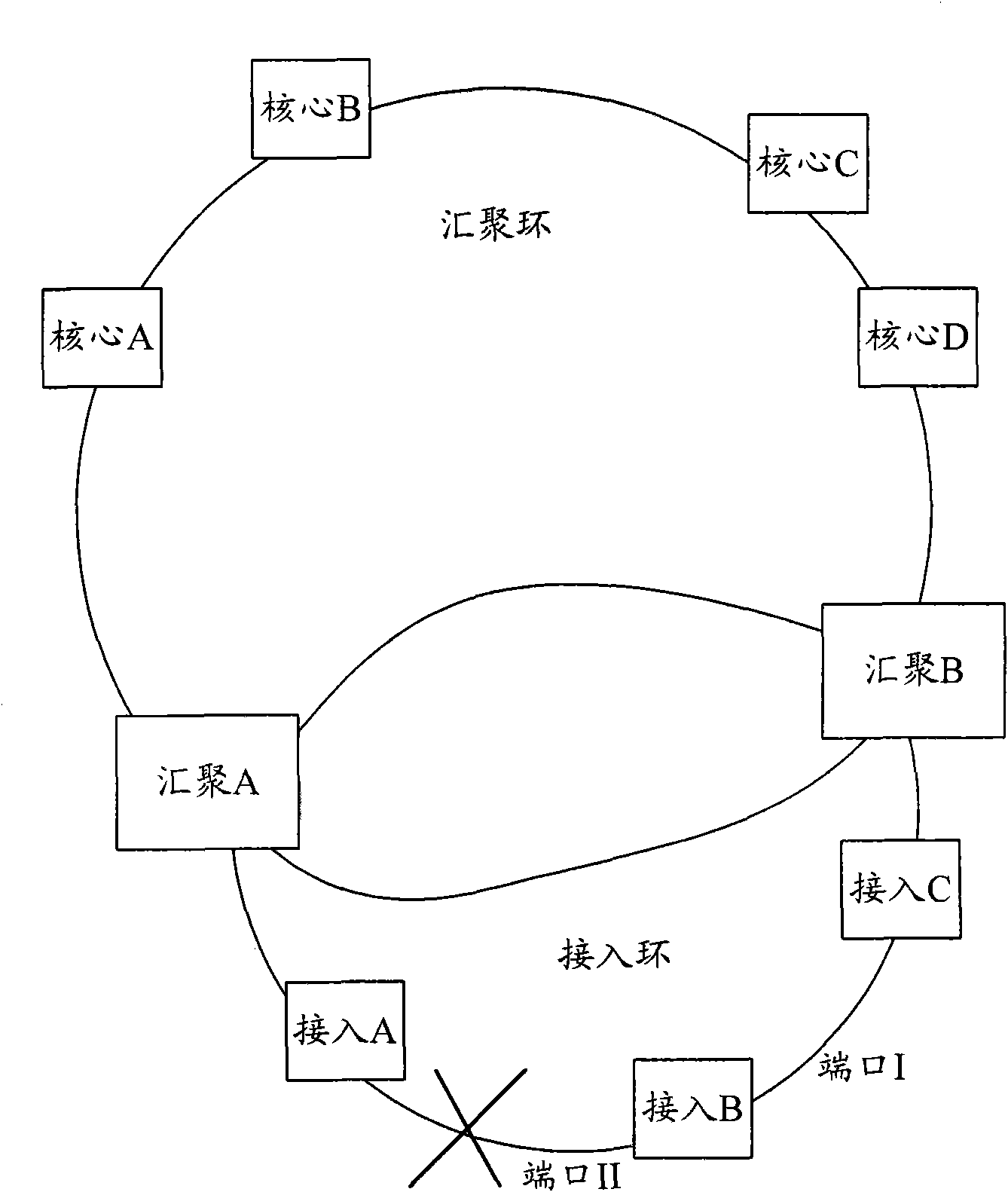
InactiveCN101800774AAvoid oscillationFast convergenceData switching networksAddress Resolution ProtocolComputer network
The invention discloses an environmental-friendly accessing method which comprises the following steps: forwarding only the message on the third layer by a convergence ring, forwarding only the message on the second layer by an access ring, and configuring dual gateways uplinked to a core node, wherein each access node of the access ring takes two convergence nodes as primary and standby gateways. The invention also discloses an environmental-friendly accessing network. Because the hardware in the access layer forwards the message on the second layer, no software needs to be started for learning routing. In addition, because the static primary and standby routing technology is used, the convergence time can be shortened, the fault-tolerant ability can be improved, the defect that virtual router redundancy protocol (VRRP) is used for backing up the primary gateway on two sides can be avoided. The invention can avoid the oscillation of the address resolution protocol (ARP) of the gateway, improve the stability of the system and save the resource of the central processing unit (CPU).
Owner:ZTE CORP
Systems and methods for scaling performance of ethernet ring protection protocol
The present disclosure provides systems and methods for scaling performance of Ethernet Ring Protection Protocol. Specifically, the systems and methods may apply to G.8032 and may provide protection switching control plane performance scaling benefits. In an exemplary embodiment, the present invention summarizes the per “virtual” ring control plane protocol into a single logical ring control plane protocol. Advantageously, the present invention transforms the G.8032 protocol from a per-virtual ring protocol to a per-logical ring control protocol. The mechanism / methodology that is used is to include minimal per-virtual ring instance information in to the Ring Automated Protection Switching (R-APS) (control) frames. Additionally, the present invention cleanly decouples the placement of the R-APS (control) channel block location on the ring from that of the virtual channel data blocks. Current G.8032 specifications tightly couple the location of each R-APS (control) channel block and the virtual channel block that it is managing.
Owner:CIENA
A method and device and system for quick rerouting in MPLS network
InactiveCN101192990AImprove communication performanceReduce storageData switching networksComputer networkProtection ring
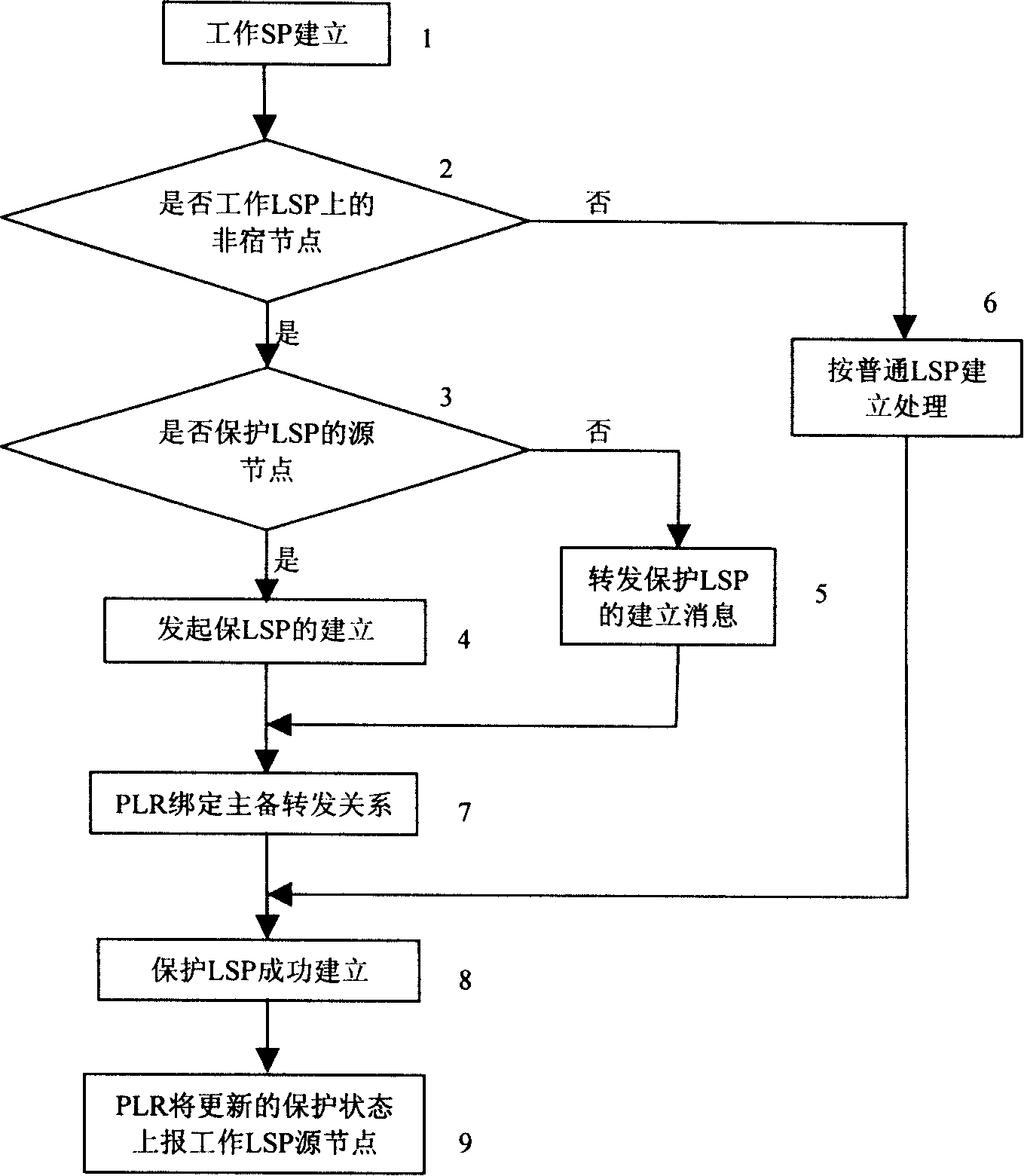
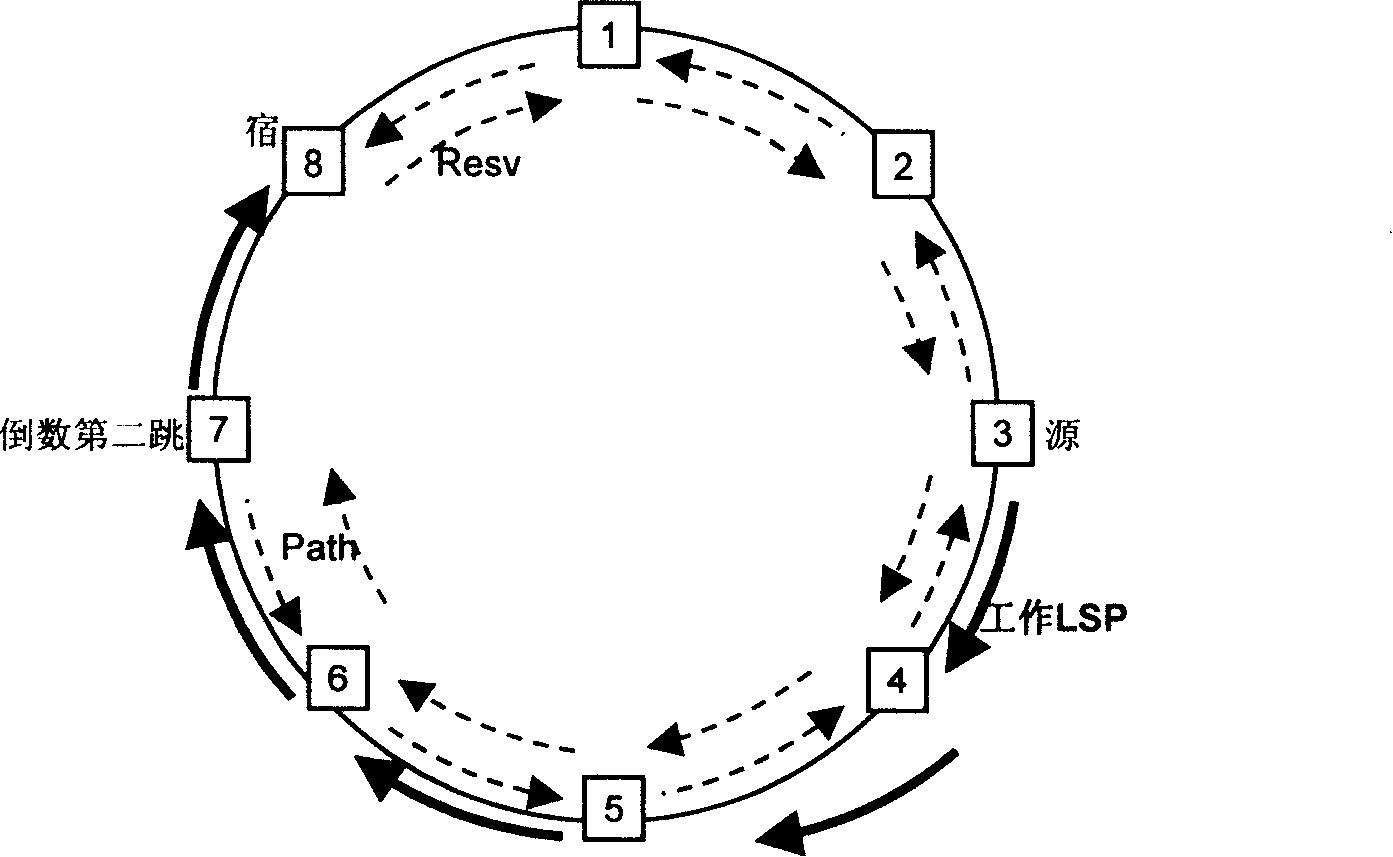
The invention provides a MPLS network quick rerouting realization method, device and system. The invention pertains to the communication field. The invention mainly comprises establishing protection LSP (label switched path) in the ring network topology by the source node of the protection LSP between the protection ring and the working LSP destination node so that the protection LSP can be used for realizing fast rerouting ring protection. Thus, the invention can realize fast rerouting protection of a plurality of nodes and link circuits only by establishing one protection LSP in the ring network topology. In prior art, a plurality of protection LSP is needed to realize fast rerouting protection of a plurality of nodes and link circuits. Therefore, information storage amount in node equipment is effectively reduced and bandwidth resource occupation in realizing fast rerouting protection can also be reduced.
Owner:HUAWEI TECH CO LTD
Topology discovery in a dual ring network
ActiveUS7599315B2Error preventionTransmission systemsTelecommunications networkResilient Packet Ring
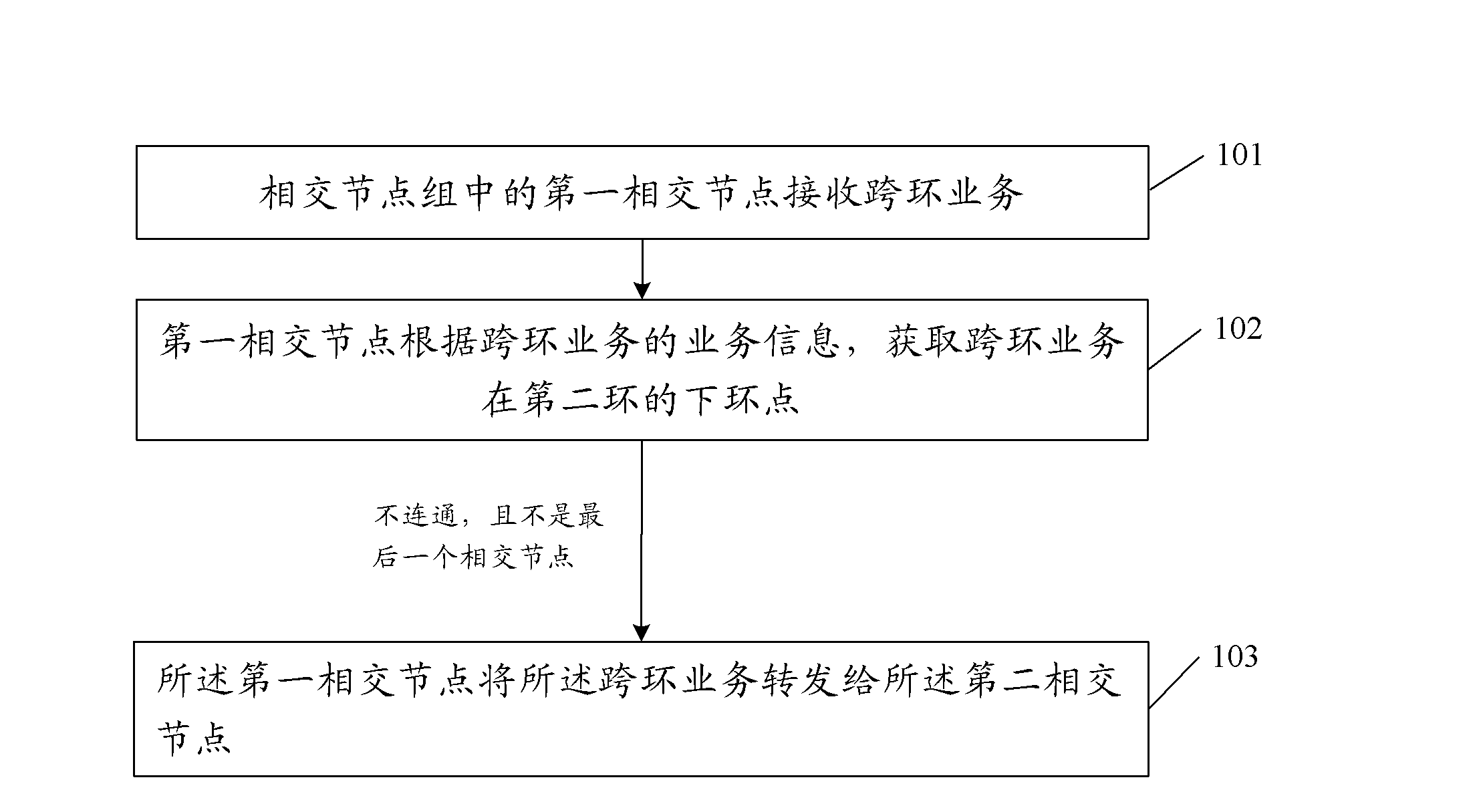
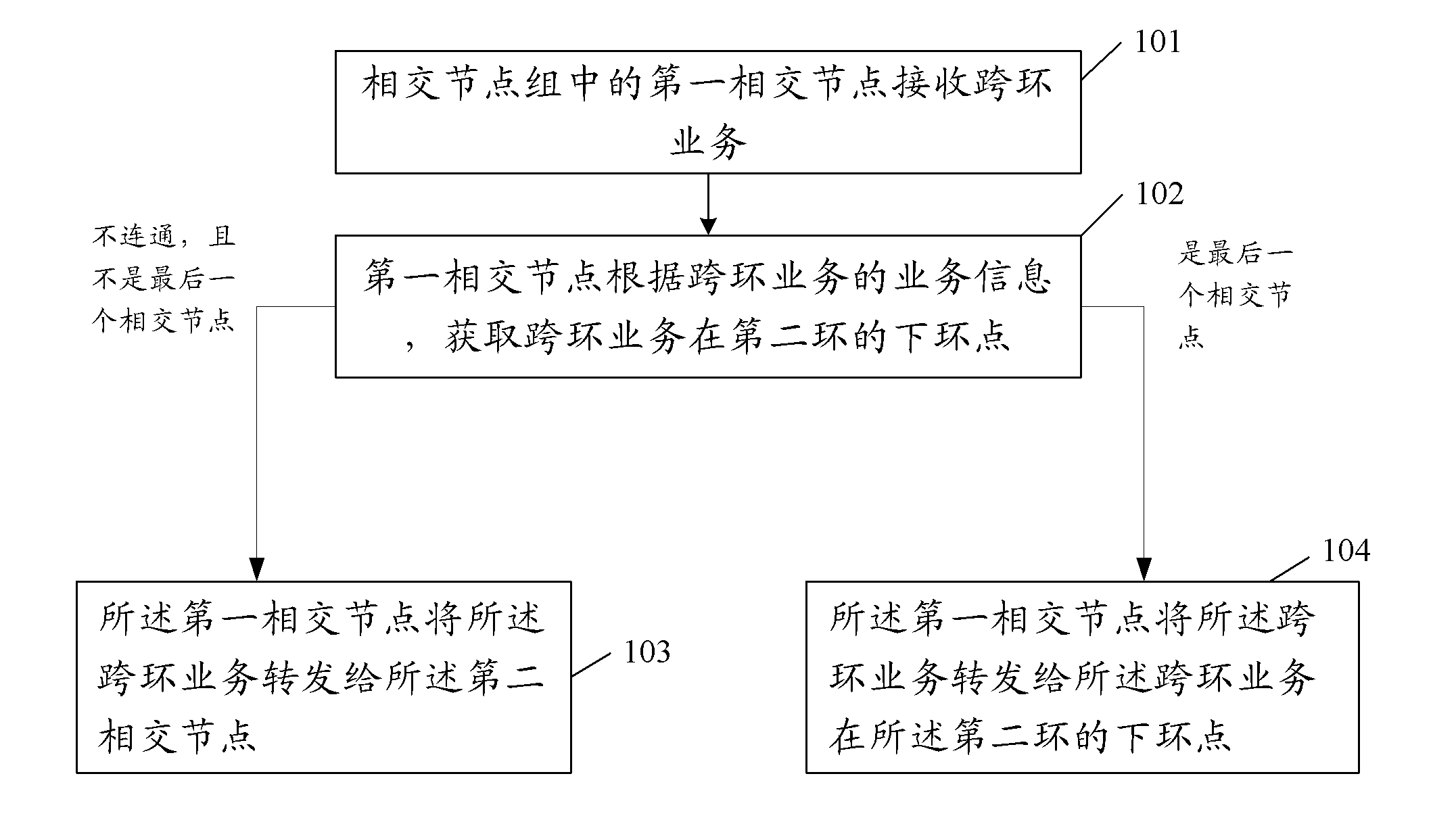
The resilient packet ring (RPR for short) is receiving much attention as a telecommunications network architecture. The RPR consists of dual counter-rotating ringlets and implements a ring protection scheme such as ring wrap and source steering. Topology discovery is an important aspect of the network management of the RPR. Herein described is a new topology discovery algorithm which performs in multiple phases. According to one phase of the algorithm, a station on the ring periodically exchange with only its neighboring stations a control messages containing a topology database. The topology database indicates addresses of stations on the ring and their link status. The algorithm should find applications not only in RPR but also other ring architectures.
Owner:WSOU INVESTMENTS LLC +1
Multiprotocol label exchanged ring network protection method, device and system
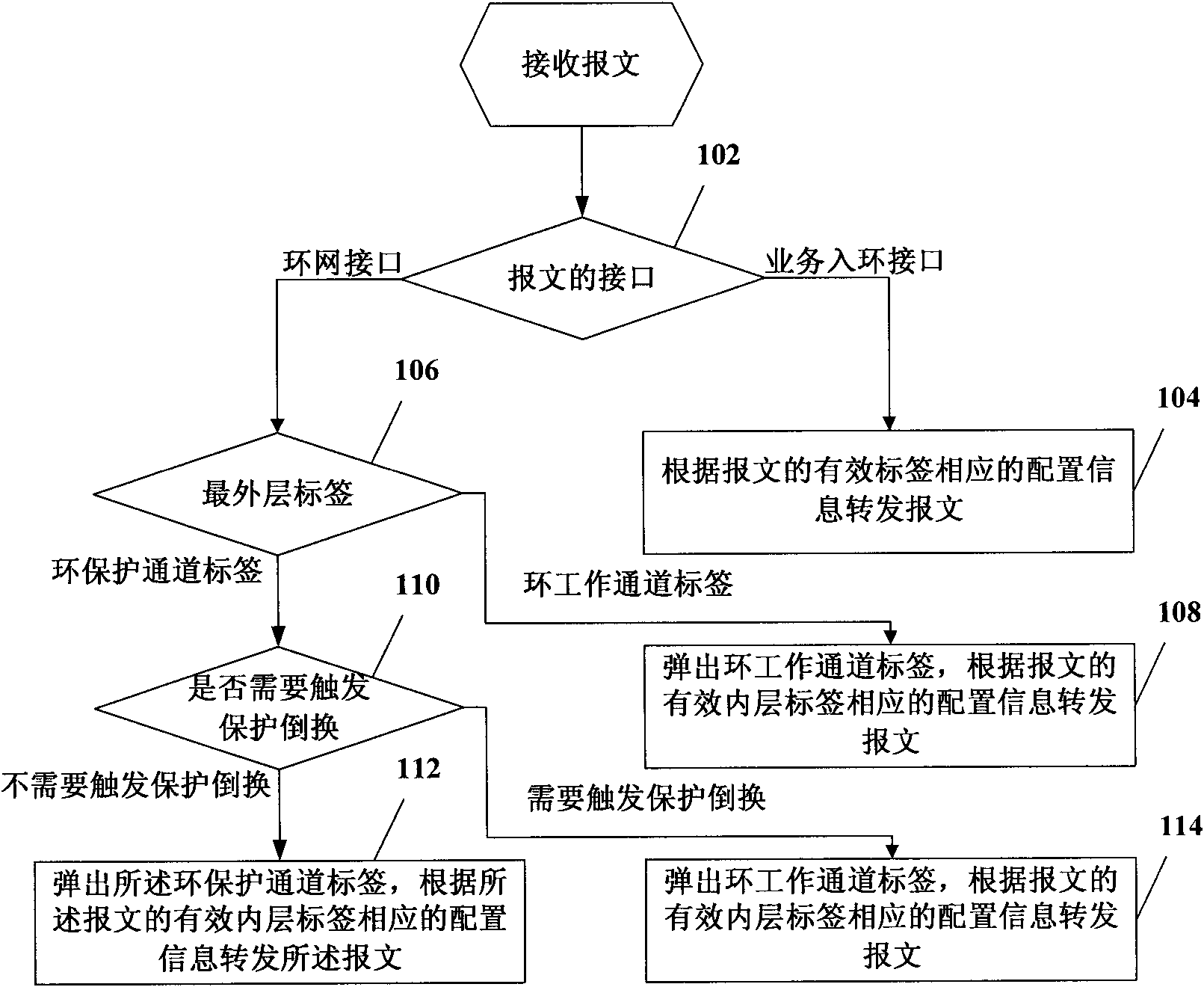
ActiveCN102035712ASolve the problem of complex configuration and high network resource overheadHigh costData switching networksMulti protocolRing protection
The embodiment of the invention aims at providing a multiprotocol label exchanged ring network protection method, device and system for solving the problems that the traditional ring network protection scheme of MPLS (Multi-Protocol Label Switching) has complex configuration and network resources have high expenditure. The system comprises a ring-inlet node, a ring network node and a ring-outlet node. By adopting the technical scheme provided by the embodiment of the invention, a message is forwarded according to configuration information of a ring network protection channel label instead of a non-service label when the outmost layer label of the message is the ring network protection channel label and an outgoing interface of the message is not protected and switched. The invention provides the same protection channel for messages of different service labels and solves the problems that the traditional ring network protection scheme of the MPLS has complex configuration and network resources have high expenditure.
Owner:HUAWEI TECH CO LTD
Intersected or tangent ring network protection method and system
ActiveCN102035714AAchieve protectionTwo-way protection implementation of protectionData switching networksStructural engineeringRing protection
The invention discloses intersected or tangent ring network protection method and system. A two-way working tunnel is allocated at an intersected or tangent node subjected to transannular guard; a ring network guard set is respectively established in each direction of the working tunnel; and TMSOAM detection is started in the directions of a two-way active link and a protection link. By adopting a two-way intersected or tangent ring network protection method based on T-MPLS (Transport Multi-protocol Label Switching) and provided by the invention, the interconnected link on a dual ring intersected or tangent node can be protected, the end-to-end protection of transannular service can be realized when an interconnected link has a fault, and the protection switching time is ensured to be not longer than 50ms.
Owner:ZTE CORP
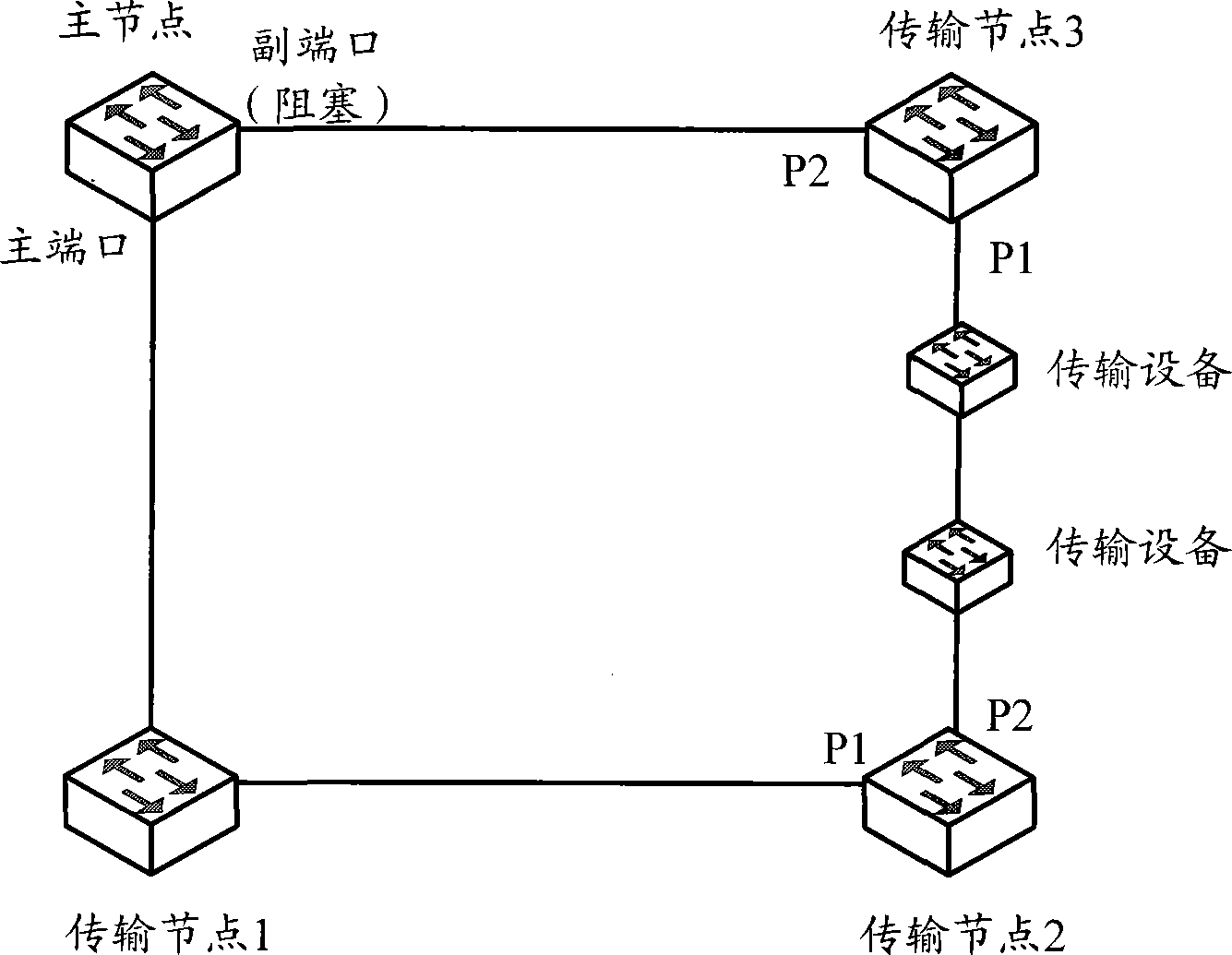
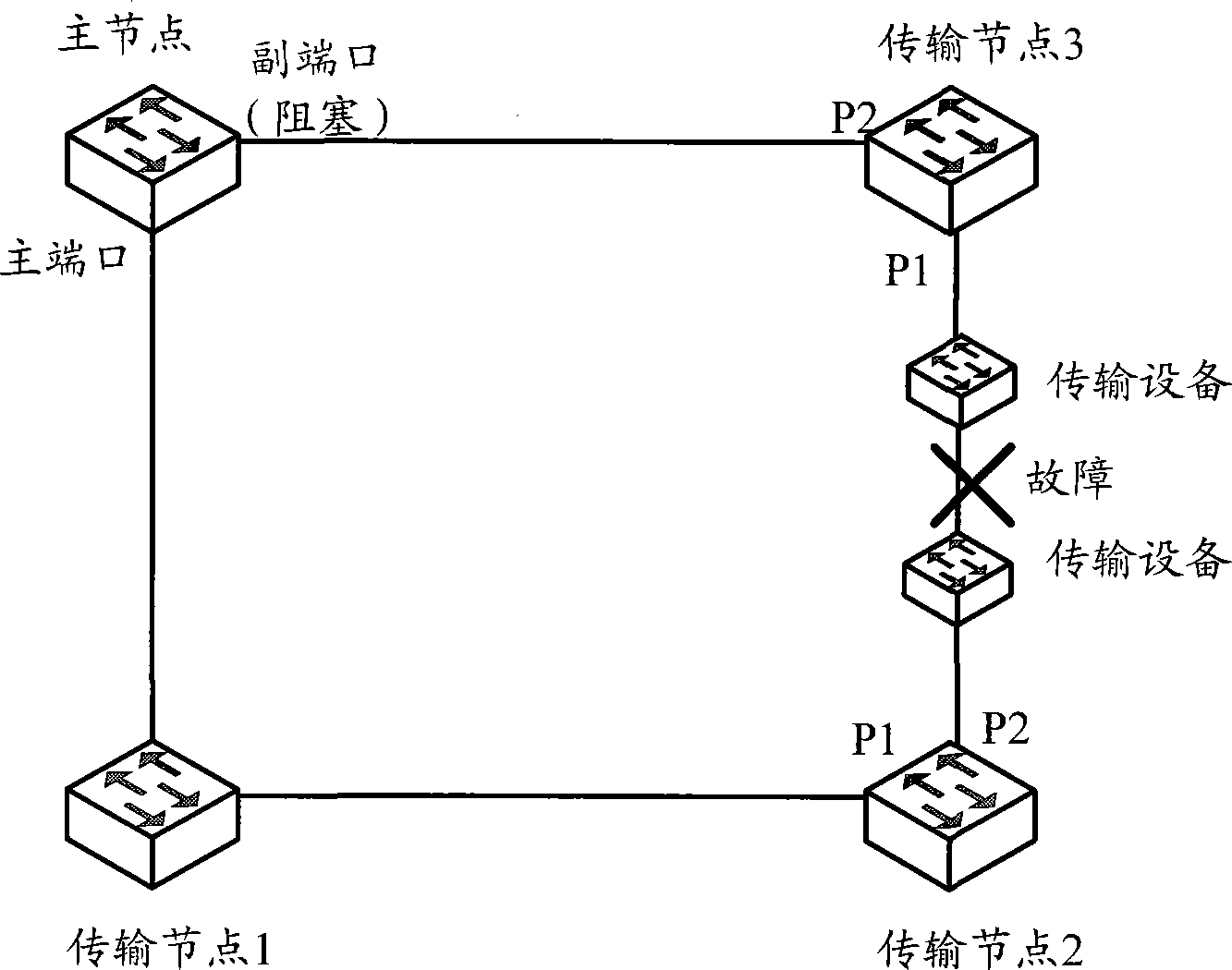
Method and apparatus for switching traffic of looped network
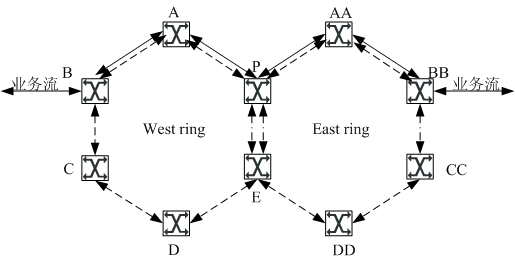
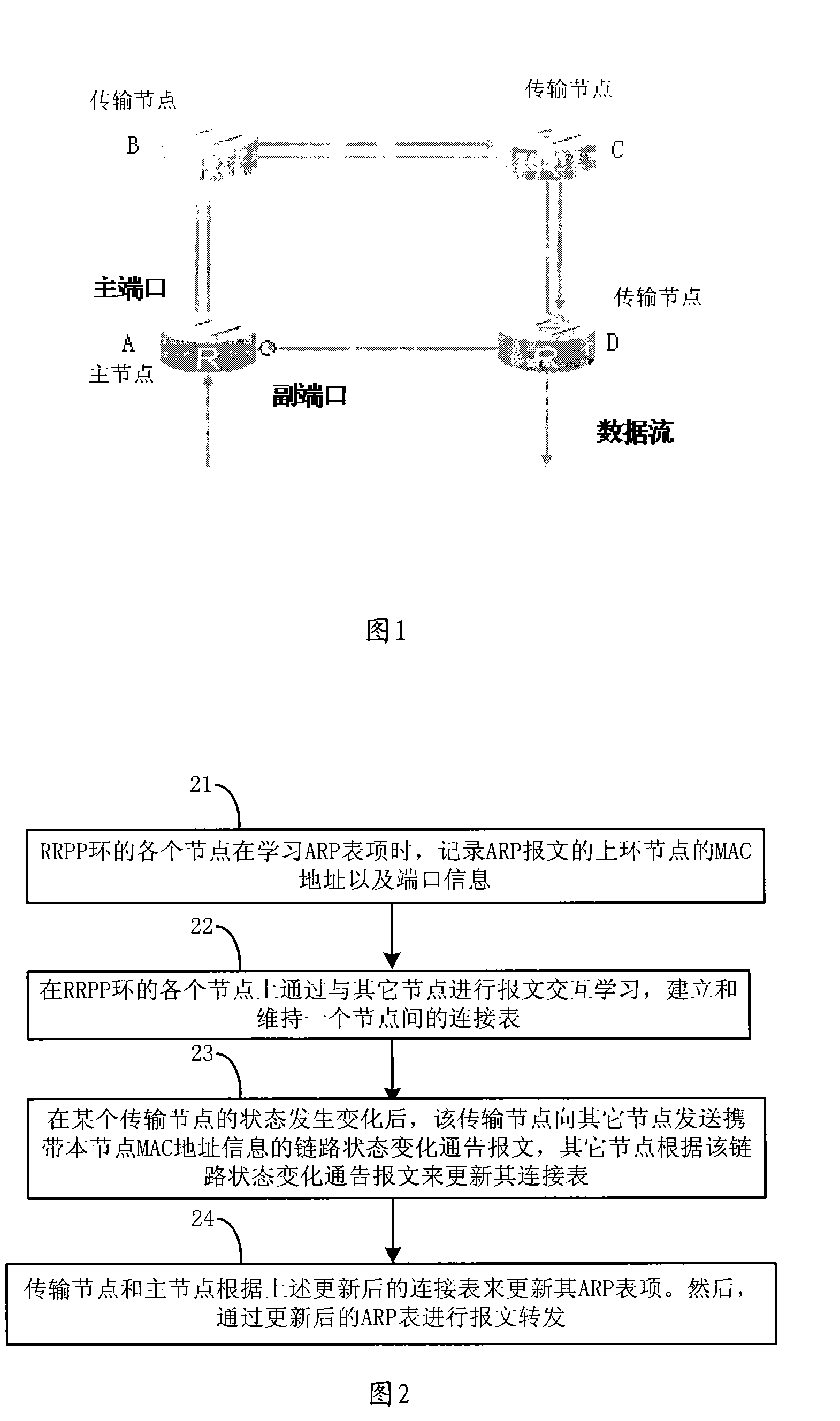
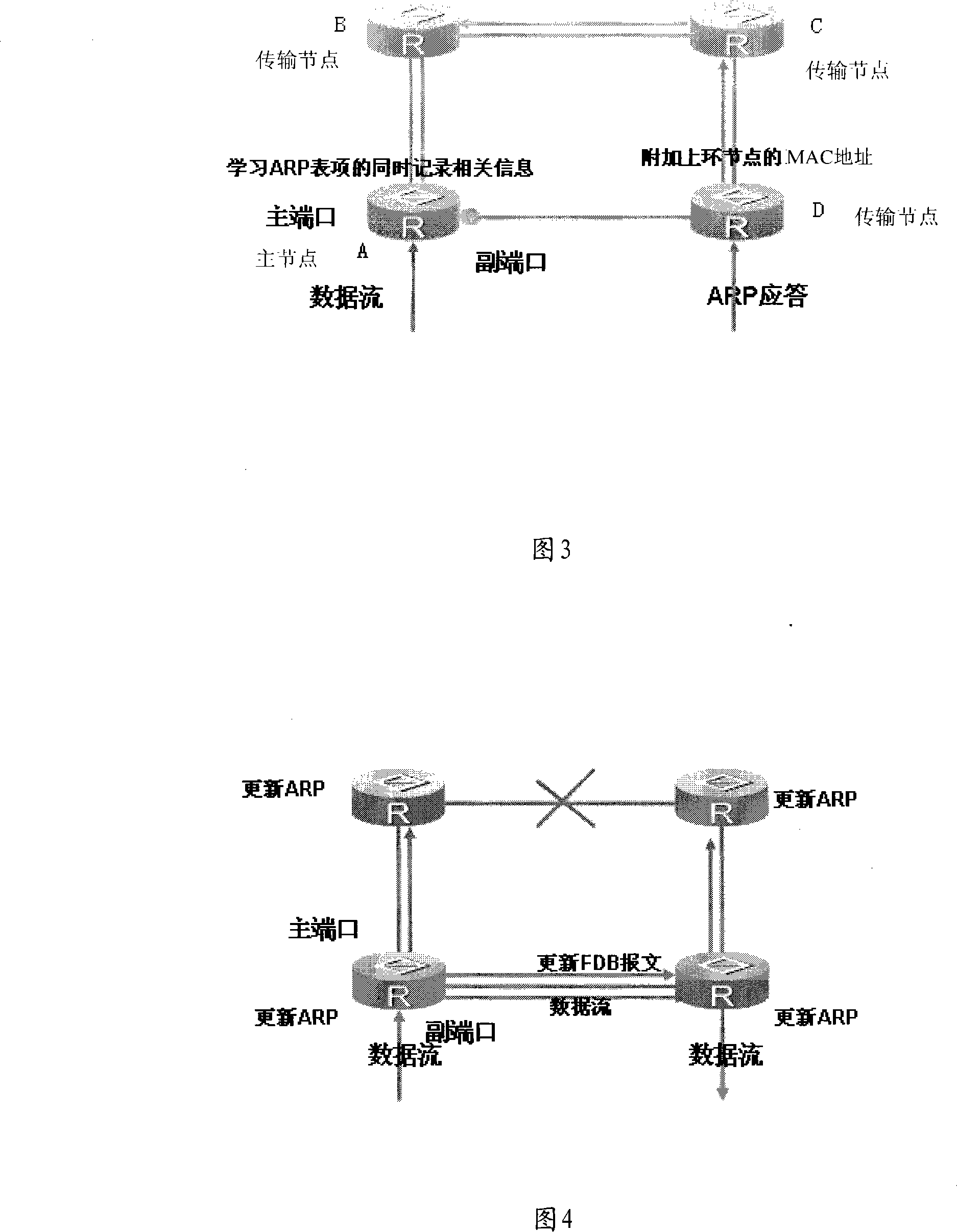
The invention provides a service switching method for a ring network, which is applied in an RRPP (Rapid Ring Protection Protocol) ring composed of transmission nodes and a master node. The method comprises the steps that forwarding relation information is renewed after status transformation information of the rapid ring protection protocol ring is obtained and according to the rapid ring protection protocol ring, an ARP (Address Resolution Protocol) item is renewed according to the renewed forwarding relation information, and the protocol item is analyzed on the basis of the renewed address to perform the forwarding of service message. Through the utilization of the service switching method, the time for renewing the ARP item by the nodes and the delay of the three-level forwarded service switching of the RRPP ring can be reduced.
Owner:HUAWEI TECH CO LTD
Systems and methods to detect and recover from a loop in an ethernet ring protected network
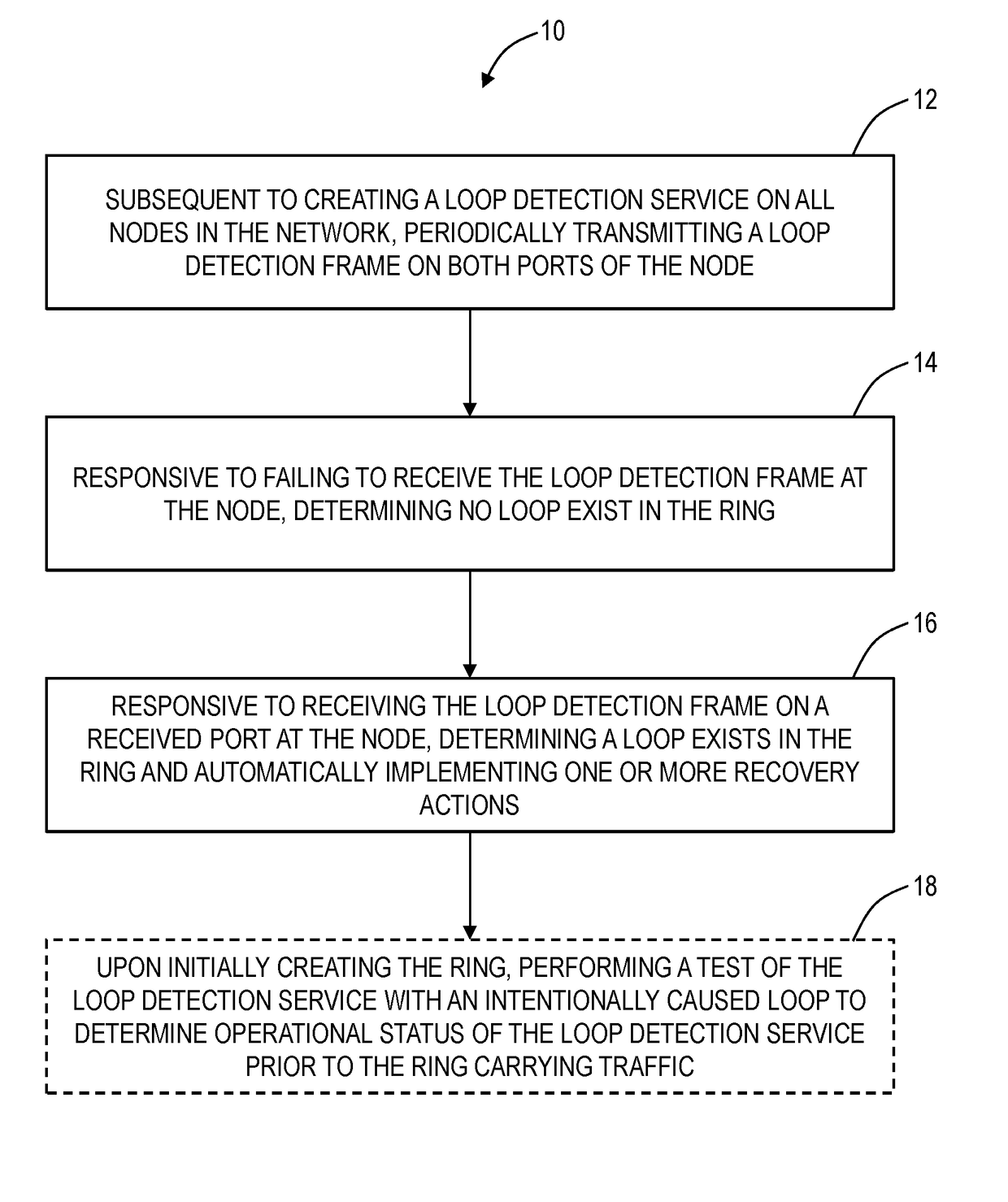
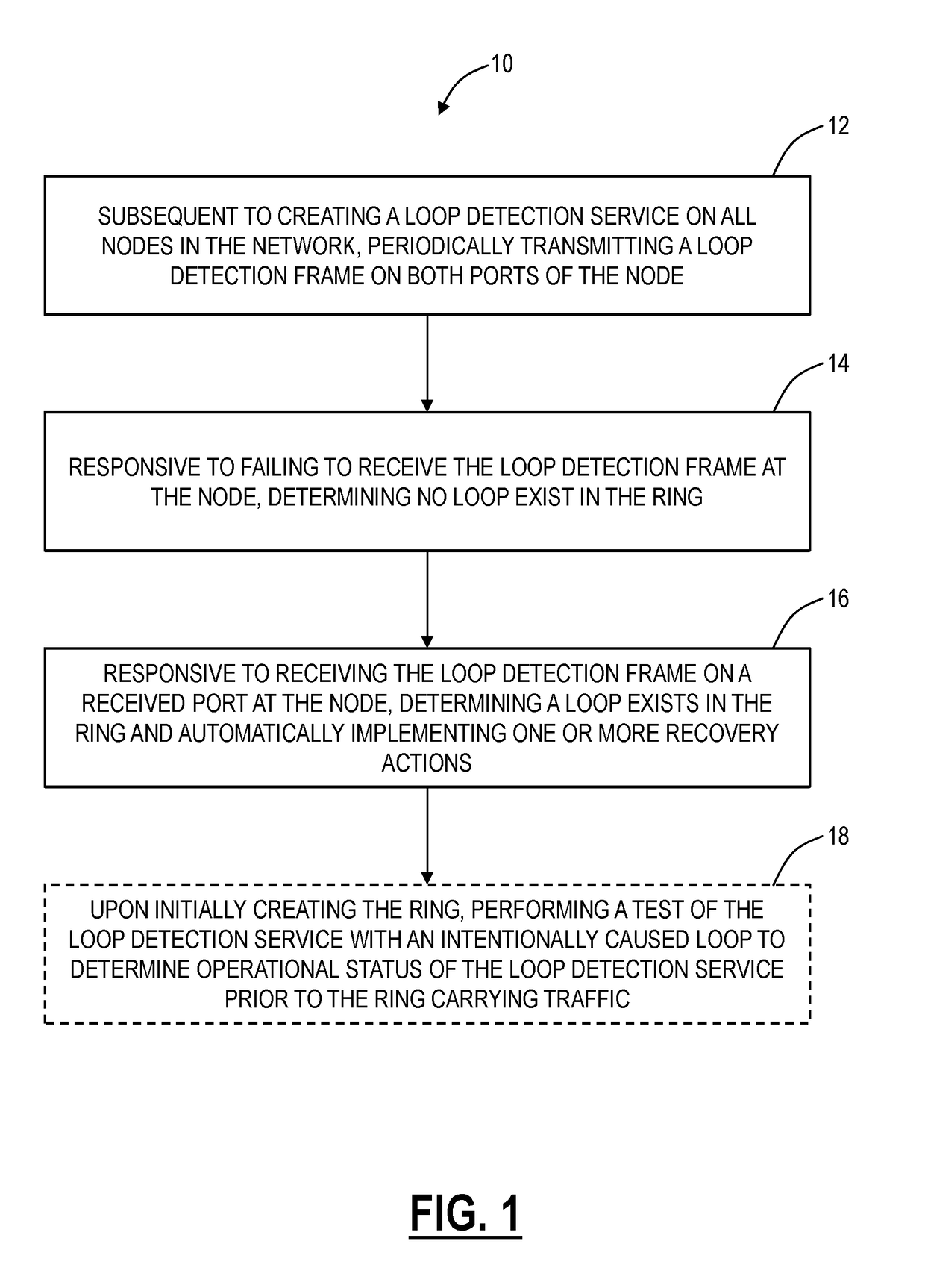
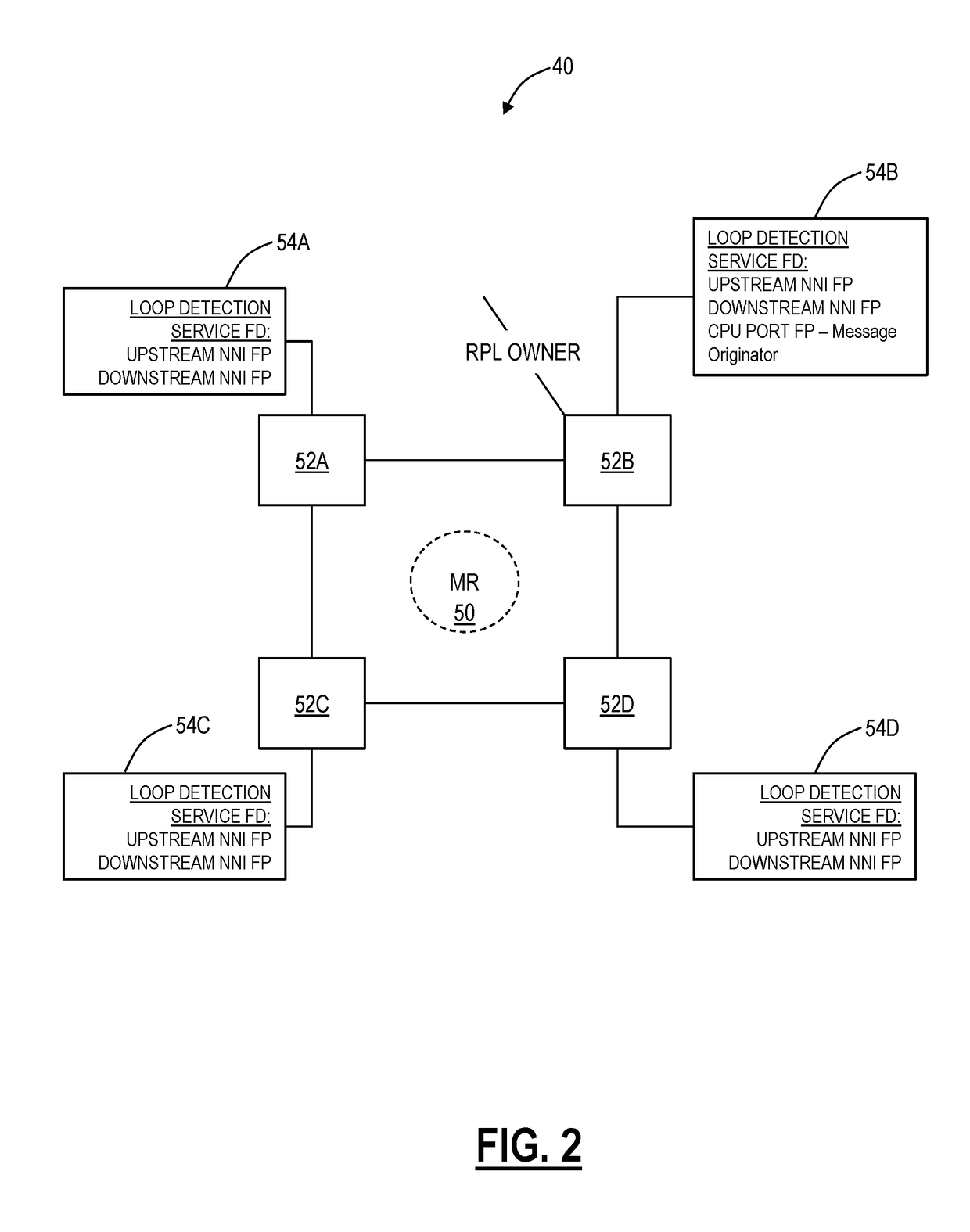
Loop detection systems and methods in an Ethernet Ring Protected network include, subsequent to creating a loop detection service on all nodes in the network, periodically transmitting a loop detection frame on both ports of the node; responsive to failing to receive the loop detection frame at the node, determining no loop exist in the ring; and, responsive to receiving the loop detection frame on a received port at the node, determining a loop exists in the ring and automatically implementing one or more recovery actions.
Owner:CIENA
Crossed ring network protection method, equipment and system
ActiveCN102546425AAchieve protectionIncrease profitMultiplex system selection arrangementsOptical multiplexService informationRing protection
The invention discloses crossed ring network protection method, equipment and system, belongs to the communication field, realizes protection of a crossed ring network with less bandwidth, and improves the bandwidth utilization ratio. The method comprises the following steps: a first crossed node in a crossed node group receives span-ring services and determines the ring setting points of the span-ring services in a second ring according to the service information of the span-ring services; and the first crossed node is not communicated with the ring setting points of the span-ring service in the second ting, and the first crossed node is not the final crossed node, the first crossed node forwards the span-ring services to the second crossed node.
Owner:HUAWEI TECH CO LTD
Method and system for RRPP loop link switching
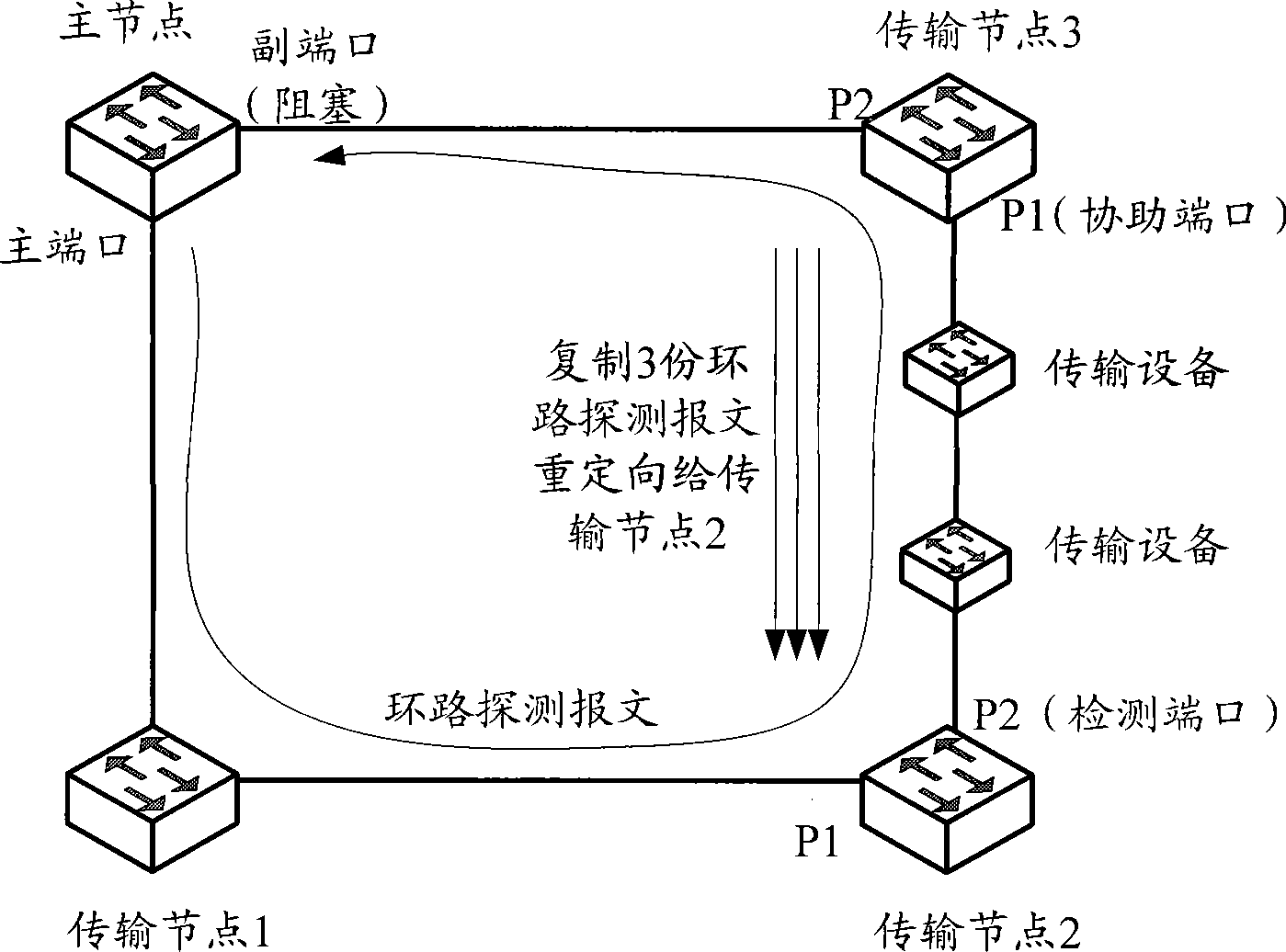
The invention provides a rapid ring protection protocol (RRPP) ring link switching method and a system thereof. Transmission node ports which directly link a RRPP ring and a transmission equipment link are enabled with a fault detection feature, one port of the ports enabled with the fault detection feature, which firstly receives a ring circuit detection message sent from a master node, is used as a detection port, and the other port is used as an assistant port. The method comprises that the transmission node where the assistant port locates forwards a ring circuit detection message after receiving the ring circuit detection message via the assistant port, and copies N ring circuit detection messages and redirects to the detection port via the assistant port, wherein, N is an integer larger than 1; and the transmission node where detection port locates notifies the link fault to the master node if not receiving the ring circuit detection message via the detection port within a set time period after sending the ring circuit detection message via the detection port. The method and the system can reduce traffic interrupting time in the RRPP ring when a fault occurs in the transmission equipment link.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com