Monitoring method for App behaviors in Android system
A technology for systems and behaviors, applied in instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as inability to intercept, and achieve strong security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
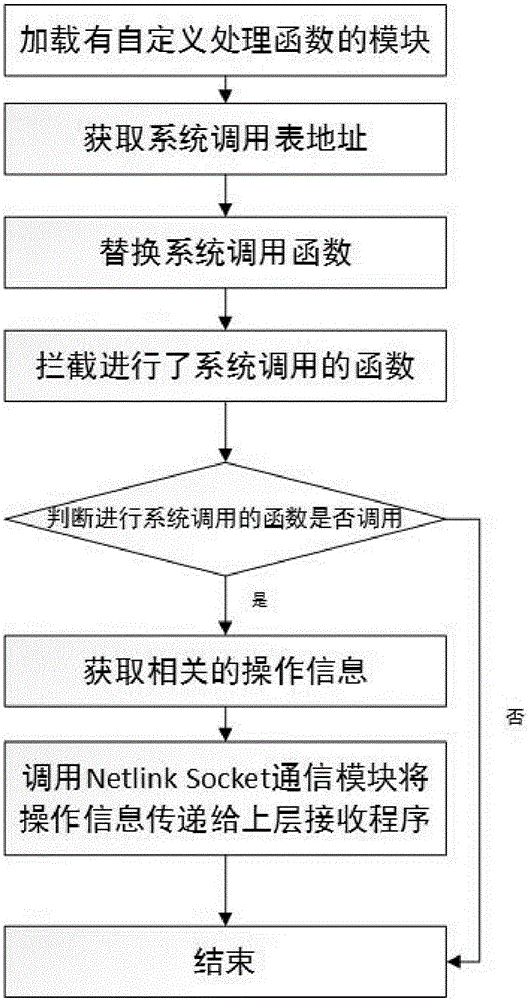
[0028] The invention provides a security kernel implementation method based on Android system App sensitive behavior monitoring, and realizes interception and monitoring of system calls of the entire Android system by adding a module in the Android kernel layer. Specifically, by writing your own Android kernel module, cross-compiling, and then loading the module into the Android system, by intercepting specific functions (such as functions for reading address book and other related information), the corresponding system calls are obtained. information. The system call information includes: the read process (which process reads it), etc. Then return the corresponding record information to the application layer to form a corresponding monitoring log file. The present invention comprises the steps:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com