Patents
Literature
65 results about "Security kernel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
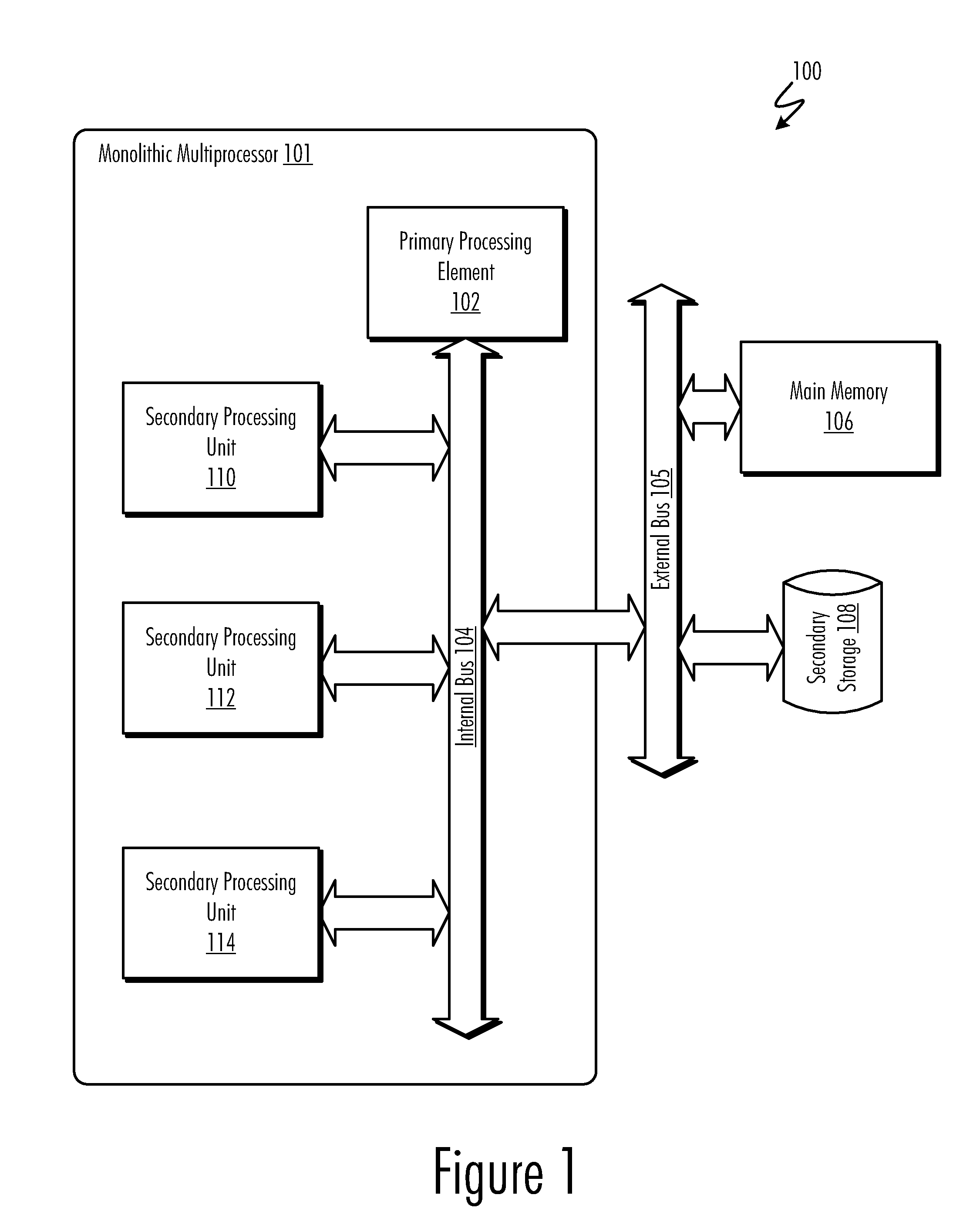
In telecommunication, the term security kernel has the following meanings: In computer and communications security, the central part of a computer or communications system hardware, firmware, and software that implements the basic security procedures for controlling access to system resources. A self-contained usually small collection of key security-related statements that works as a part of an operating system to prevent unauthorized access to, or use of, the system and contains criteria that must be met before specified programs can be accessed. Hardware, firmware, and software elements of a trusted computing base that implement the reference monitor concept.
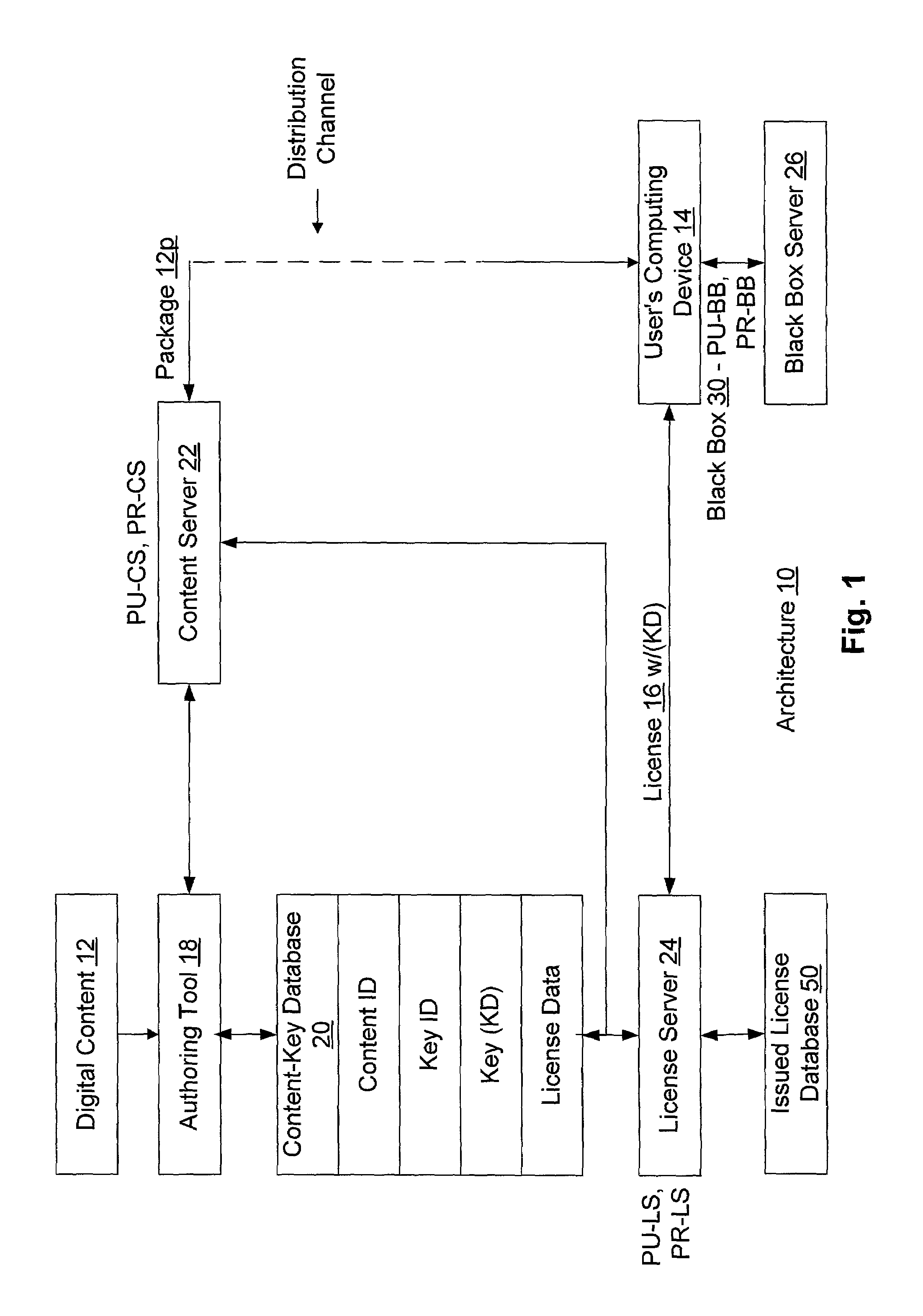
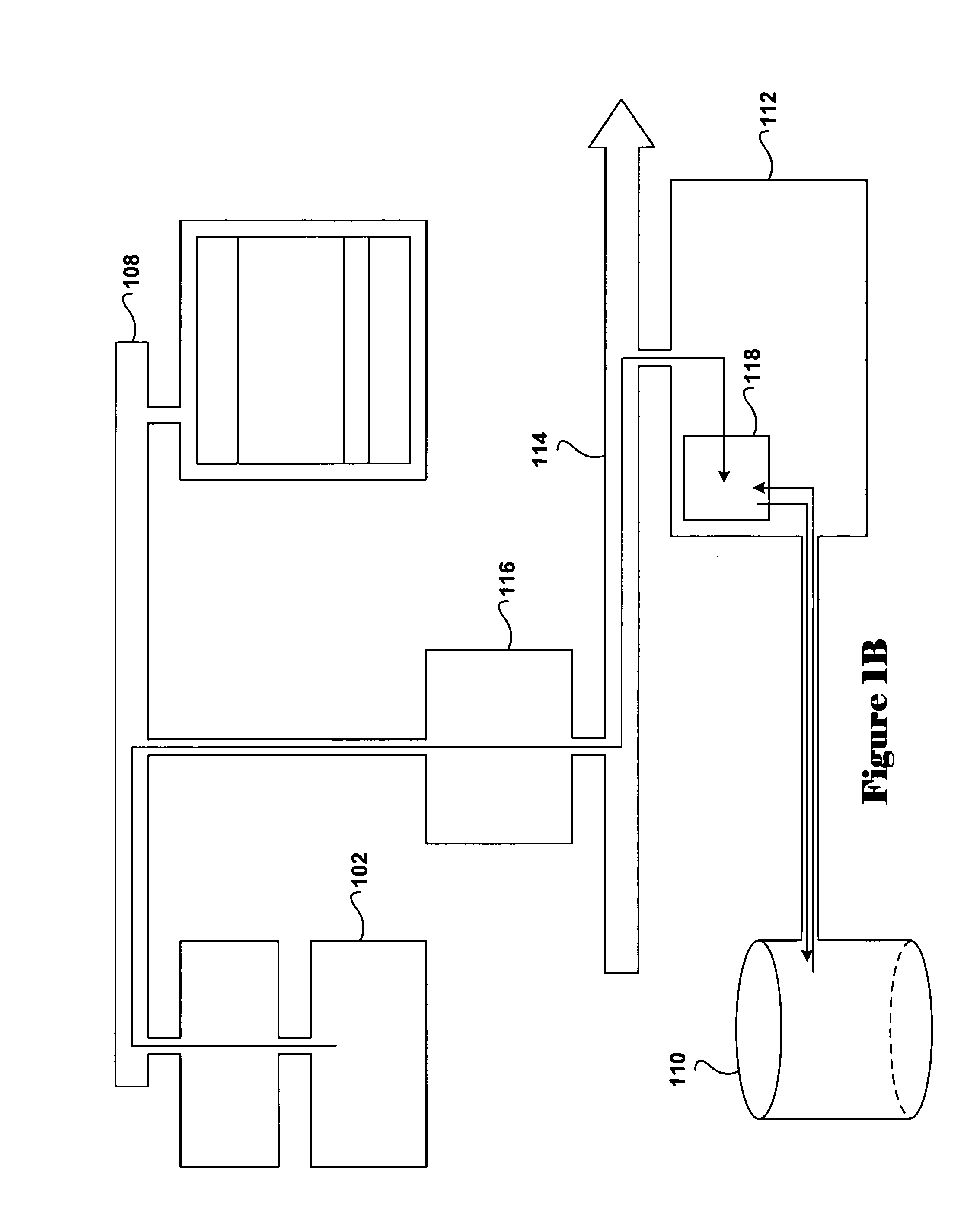
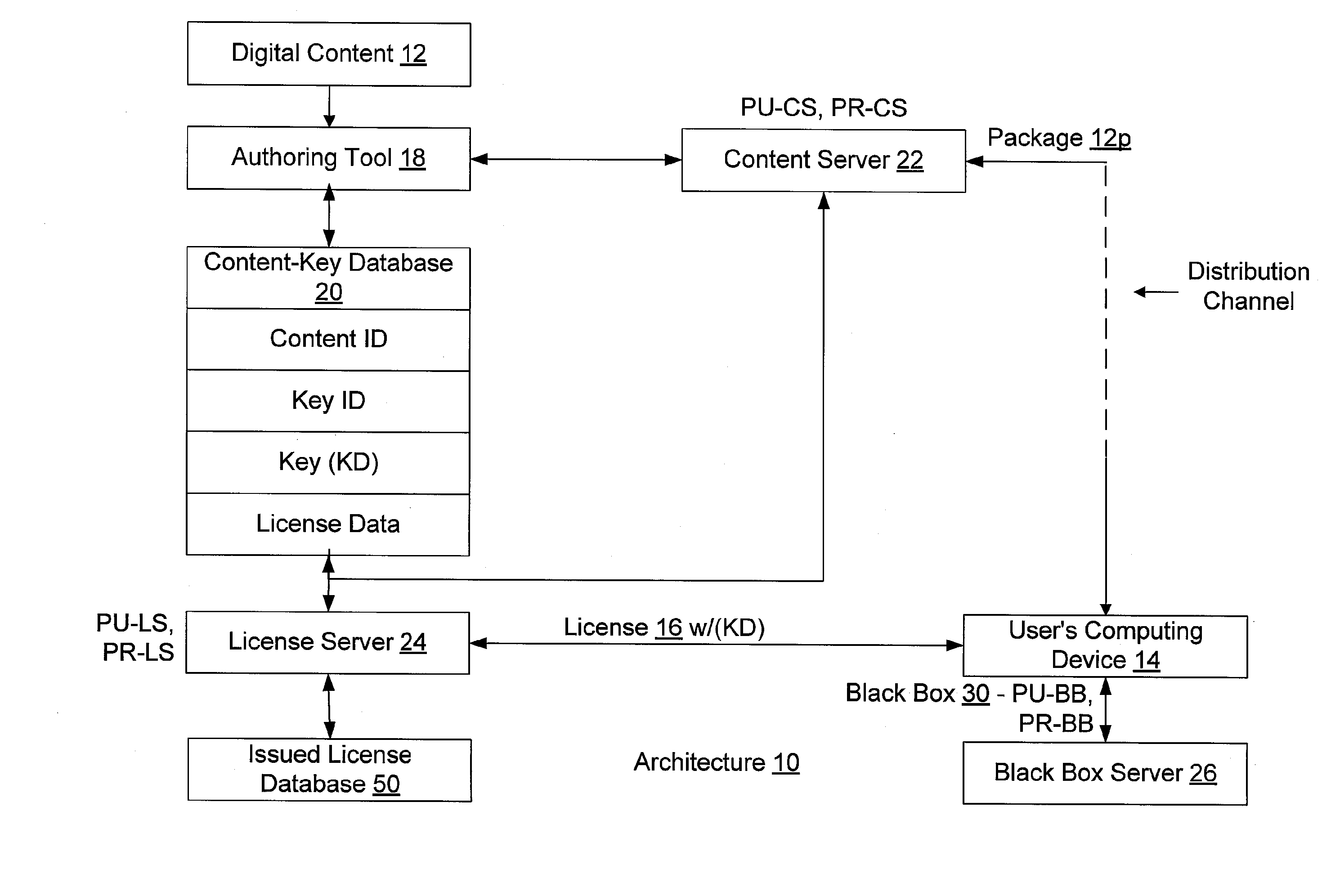
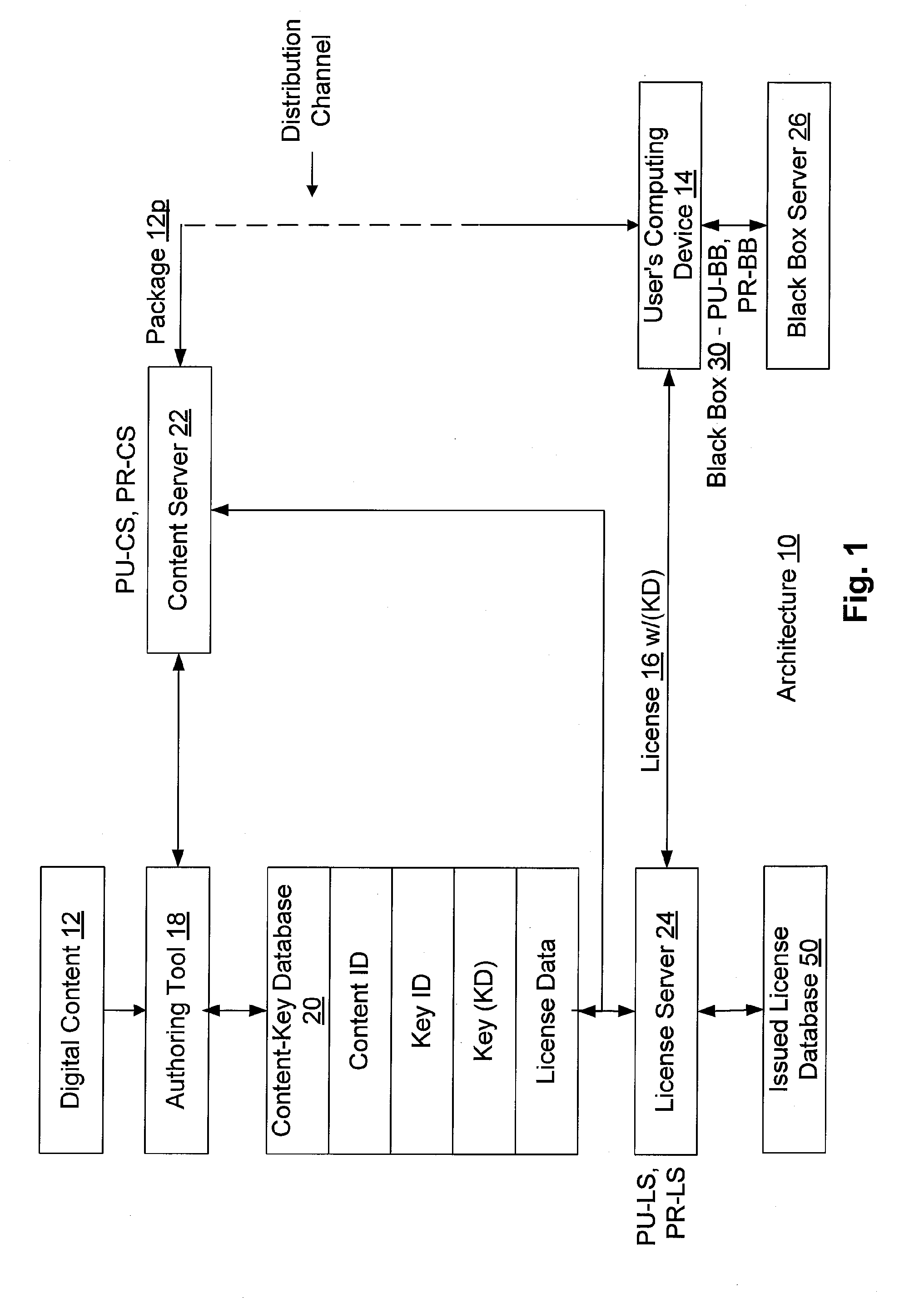
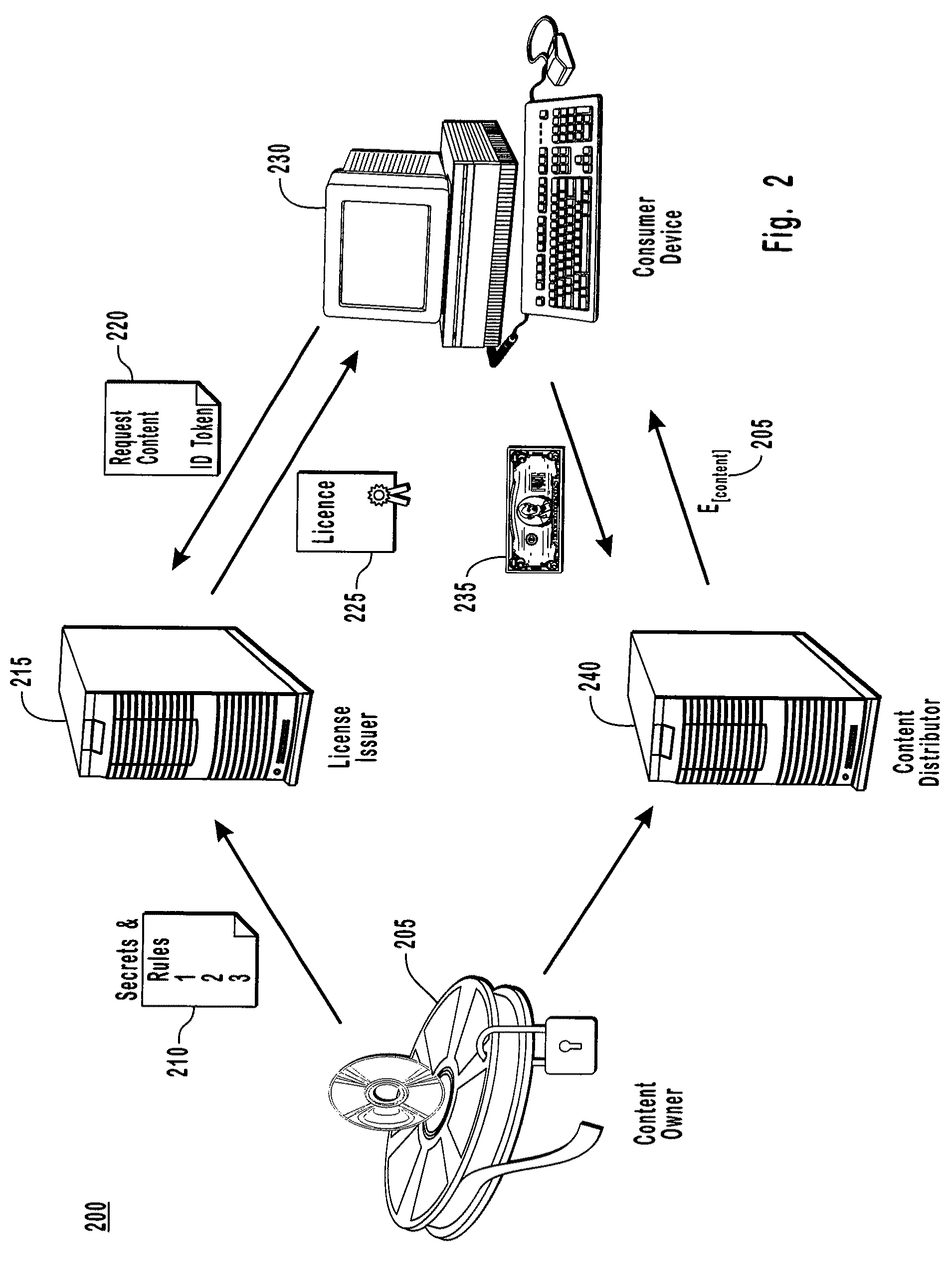
Conditional access to digital rights management conversion
ActiveUS20050182931A1Drying solid materials with heatUser identity/authority verificationSecurity kernelDigital rights management system
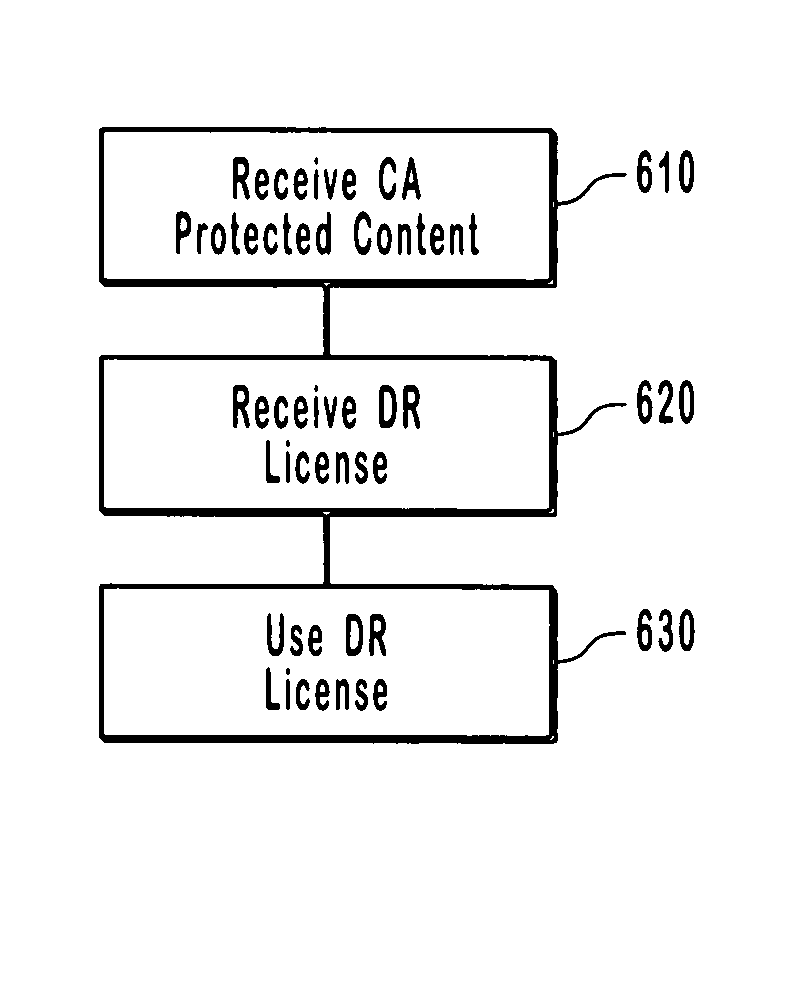
The present invention provides for an interface between two seemingly incompatible and different content protection systems. Accordingly, protected content may be transferred between the respective security kernels of a conditional access (CA) and digital rights management (DRM) systems, while maintaining security of the content and any associated protection information. The transfer and consumption of protected content and the associated content protection information may be achieved by temporarily or permanently binding the respective security kernels of the CA and DRM systems, transcribing content protection information, and potentially transcribing the content.
Owner:MICROSOFT TECH LICENSING LLC
Secure processor architecture for use with a digital rights management (DRM) system on a computing device
InactiveUS7225333B2Digital computer detailsInternal/peripheral component protectionSecurity kernelNormal mode
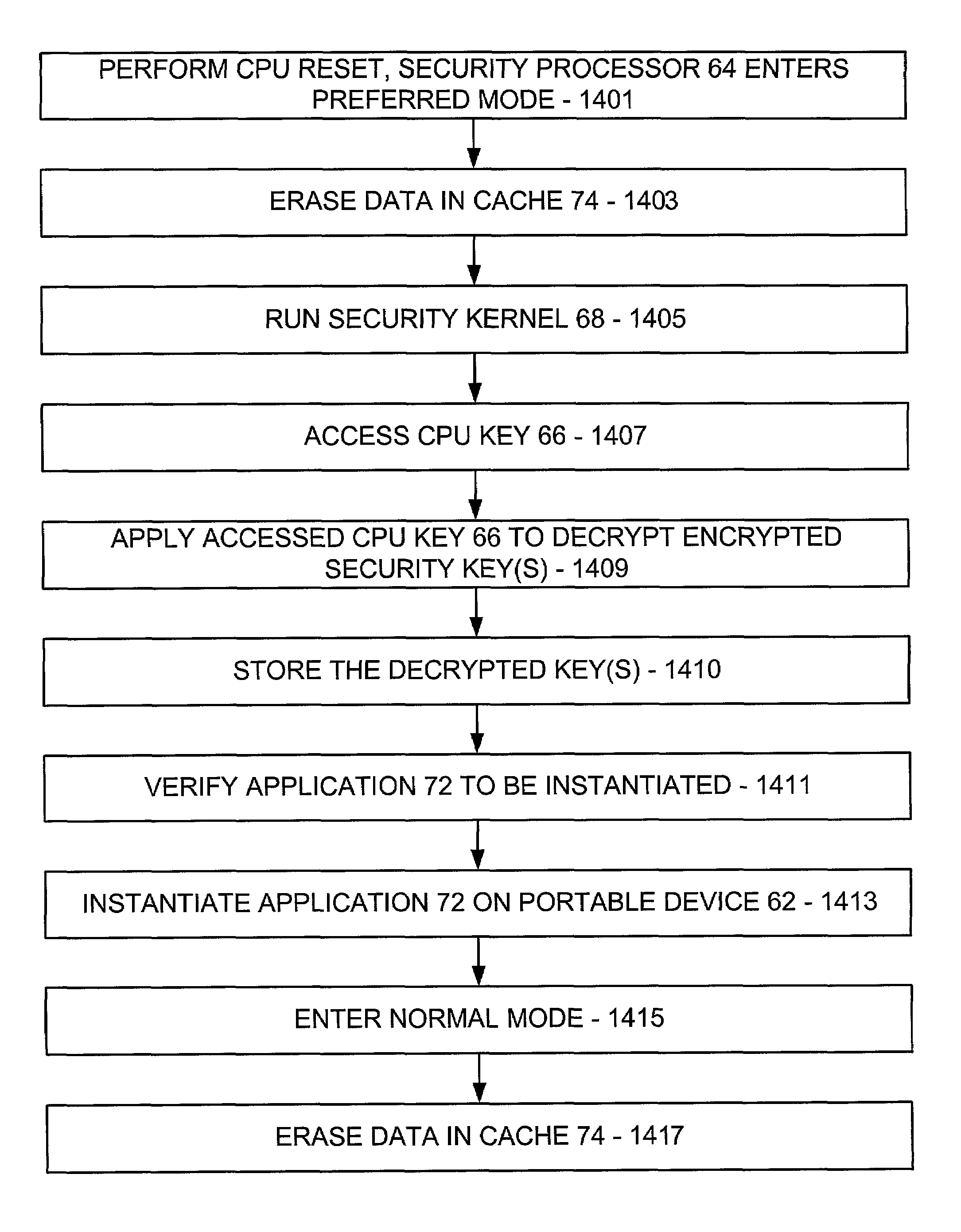
A secure processor is operable in normal and preferred modes, and includes a security kernel instantiated when the processor enters into preferred mode and a security key accessible by the security kernel during preferred mode. The security kernel employs the accessed security key to authenticate a secure application, and allows the processor to be trusted to keep hidden a secret of the application. To instantiate the application, the processor enters preferred mode where the security key is accessible, and instantiates and runs the security kernel. The security kernel accesses the security key and applies same to decrypt a key for the application, stores the decrypted key in a location where the application will expect same, and instantiates the application. The processor then enters the normal mode, where the security key is not accessible.
Owner:MICROSOFT TECH LICENSING LLC
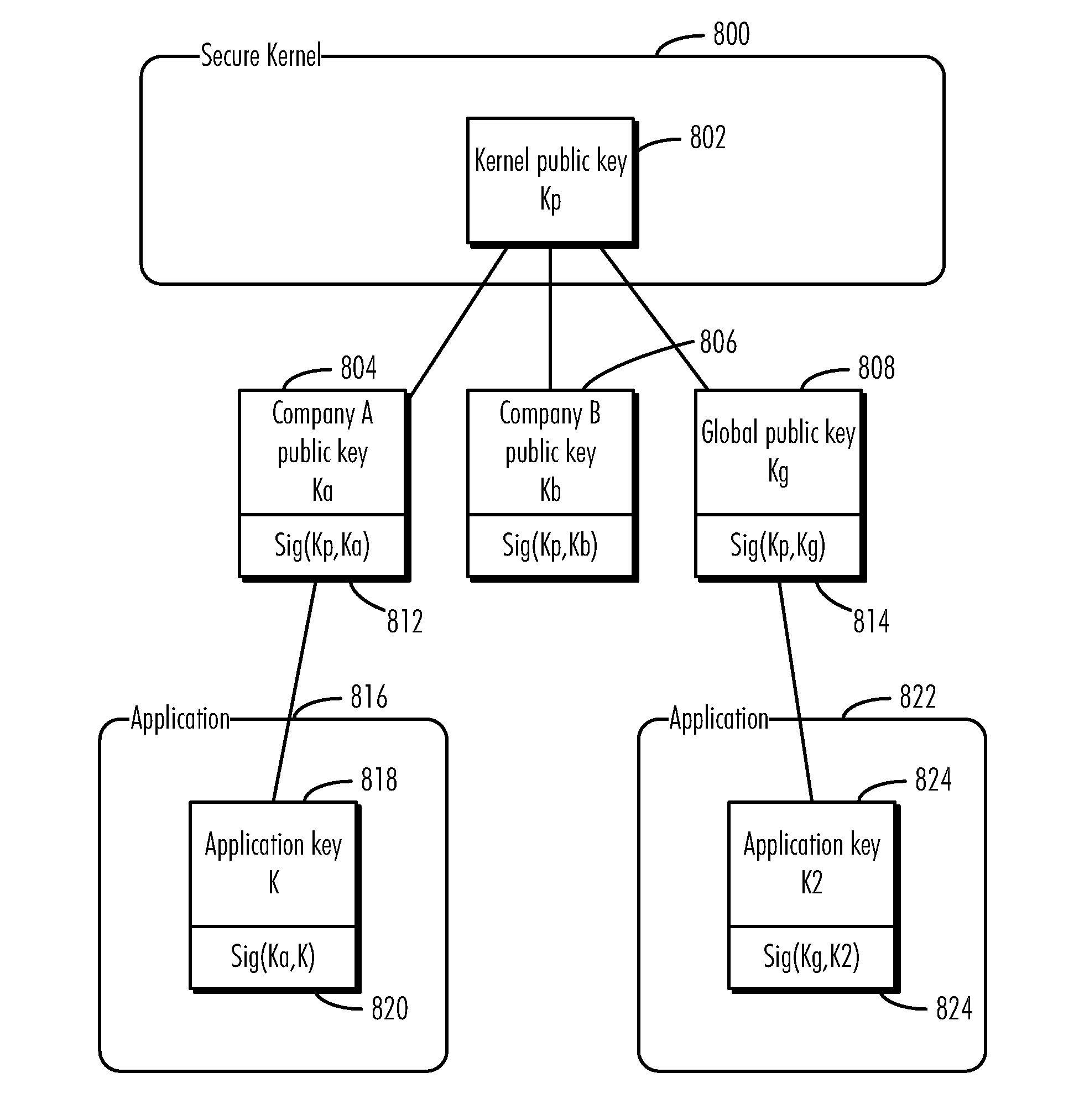
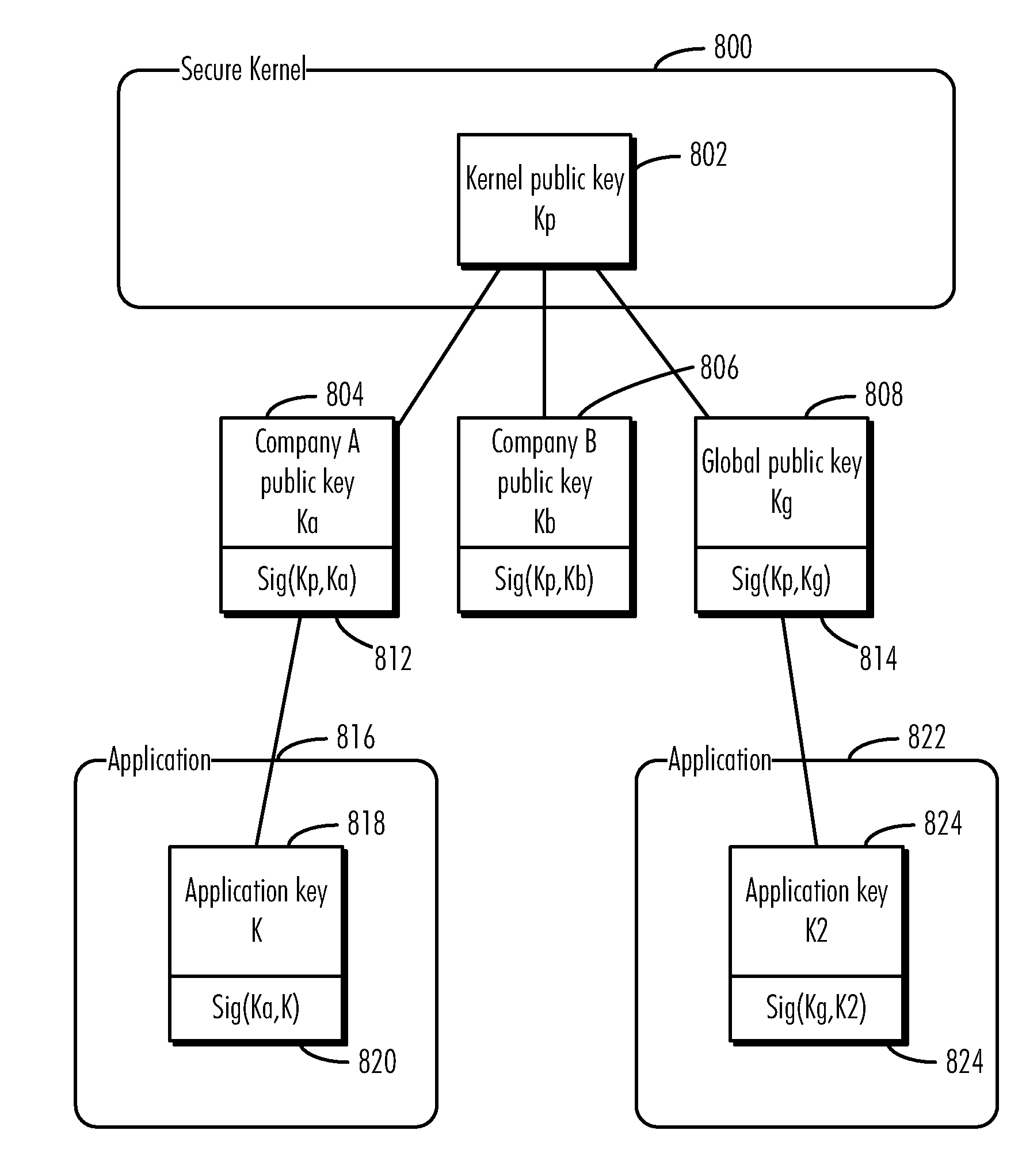
Support for multiple security policies on a unified authentication architecture
ActiveUS8166304B2Digital data processing detailsUser identity/authority verificationData processing systemSecurity kernel
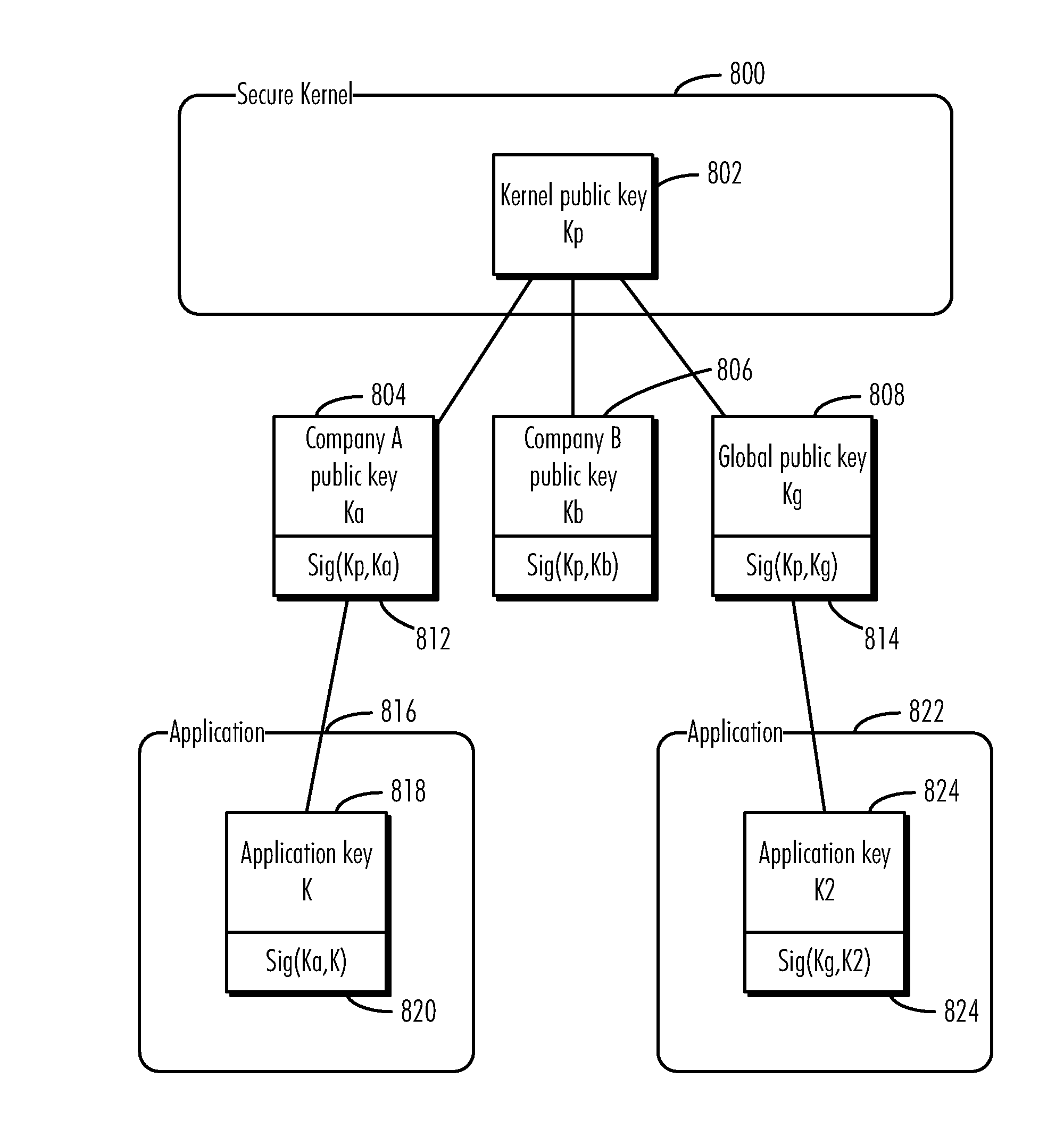
A method, computer program product, and data processing system are disclosed for ensuring that applications executed in the data processing system originate only from trusted sources are disclosed. In a preferred embodiment, a secure operating kernel maintains a “key ring” containing keys corresponding to trusted software vendors. The secure kernel uses vendor keys to verify that a given application was signed by an approved vendor. To make it possible for independent developers to develop software for the herein-described platform, a “global key pair” is provided in which both the public and private keys of the pair are publicly known, so that anyone may sign an application with the global key. Such an application may be allowed to execute by including the global key pair's public key in the key ring as a “vendor key” or, conversely, it may be disallowed by excluding the global public key from the key ring.
Owner:INT BUSINESS MASCH CORP
Secure Policy Differentiation by Secure Kernel Design
InactiveUS20090089579A1Computer security arrangementsSecuring communicationData processing systemSecurity kernel
A method, computer program product, and data processing system are disclosed for ensuring that applications executed in the data processing system originate only from trusted sources are disclosed. In a preferred embodiment, a secure operating kernel maintains a “key ring” containing keys corresponding to trusted software vendors. The secure kernel uses vendor keys to verify that a given application was signed by an approved vendor. To make it possible for users to execute software from independent software developers, an administrative user may disable the above-described vendor key-checking as an option.
Owner:IBM CORP
Method and apparatus for protecting file system based on digital signature certificate
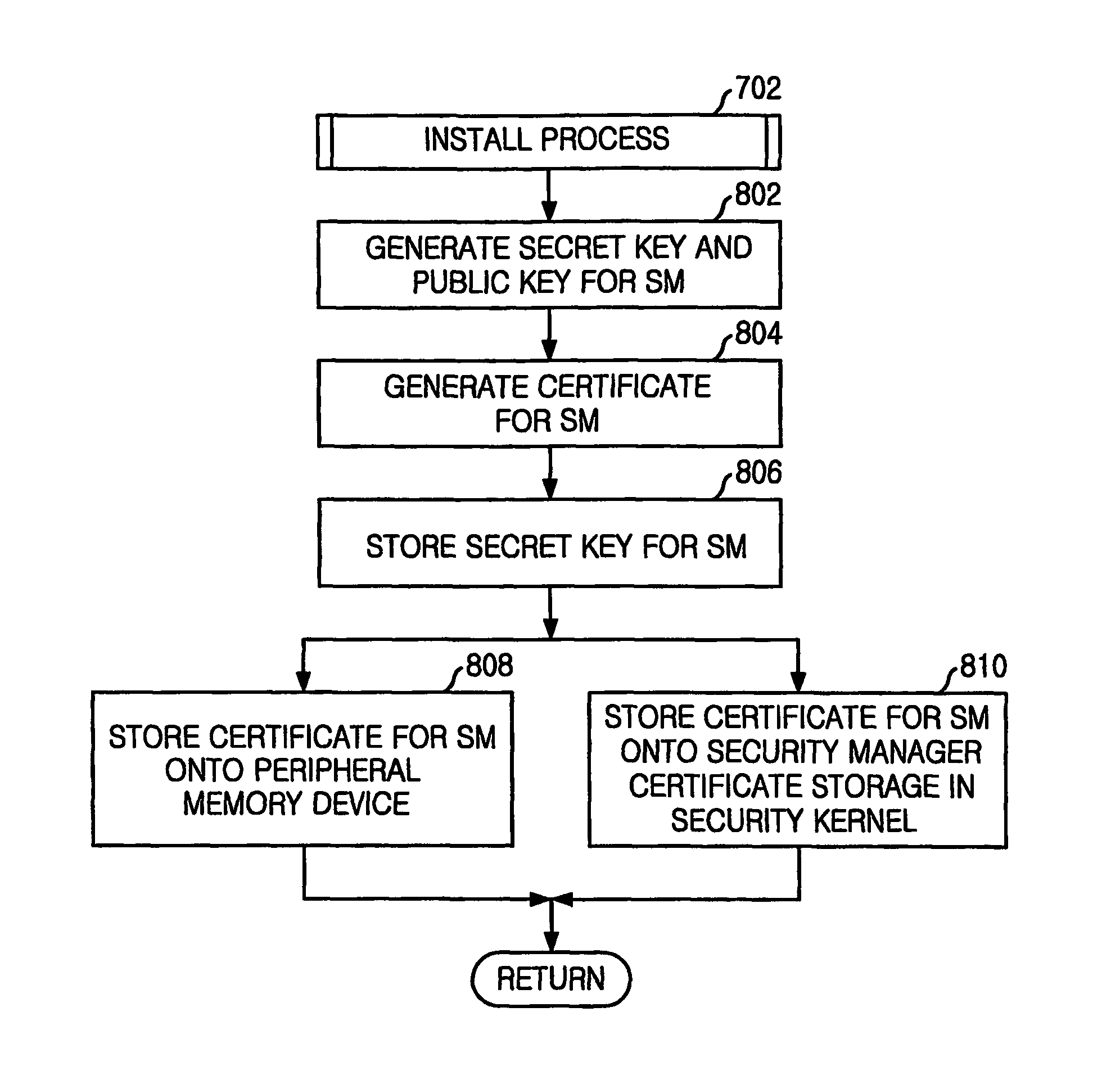
InactiveUS7328341B1Process safety and stabilityDigital data processing detailsUser identity/authority verificationOperational systemDigital signature
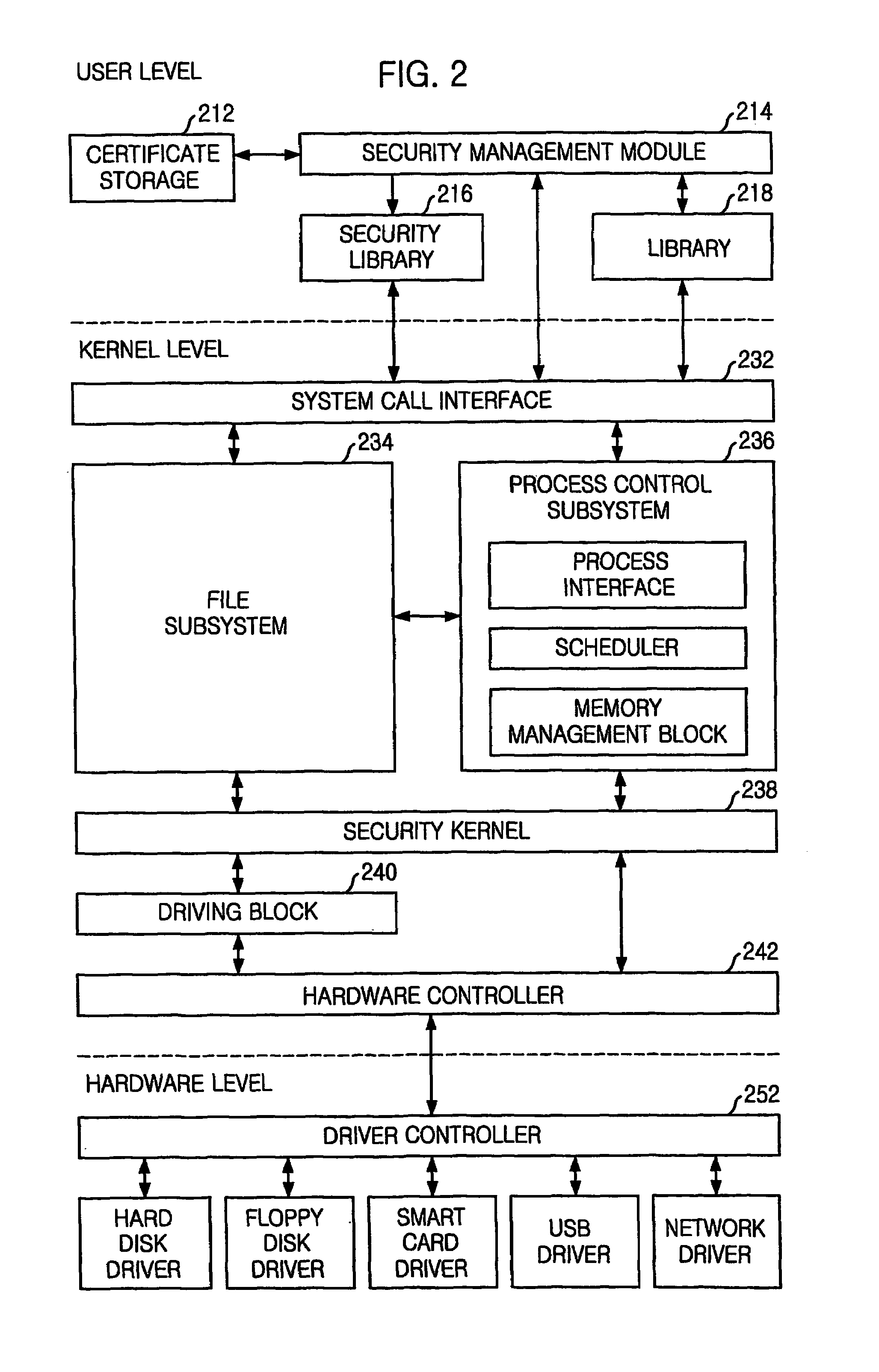
Protection for a file system is provided. The protection includes generating first digital signature keys and a system security manager's certificate for a system security manager. A system security manager's certificate is stored onto a security kernel when installing an operating system on a server computer. Second digital signature keys and a user's certificate are generated for a general user. An access authority of the file system is set. A user is identified through a digital signature authentication method when the user tries to access the file system. The user is given access authority for the file in accordance with an identification result.
Owner:SECUVE
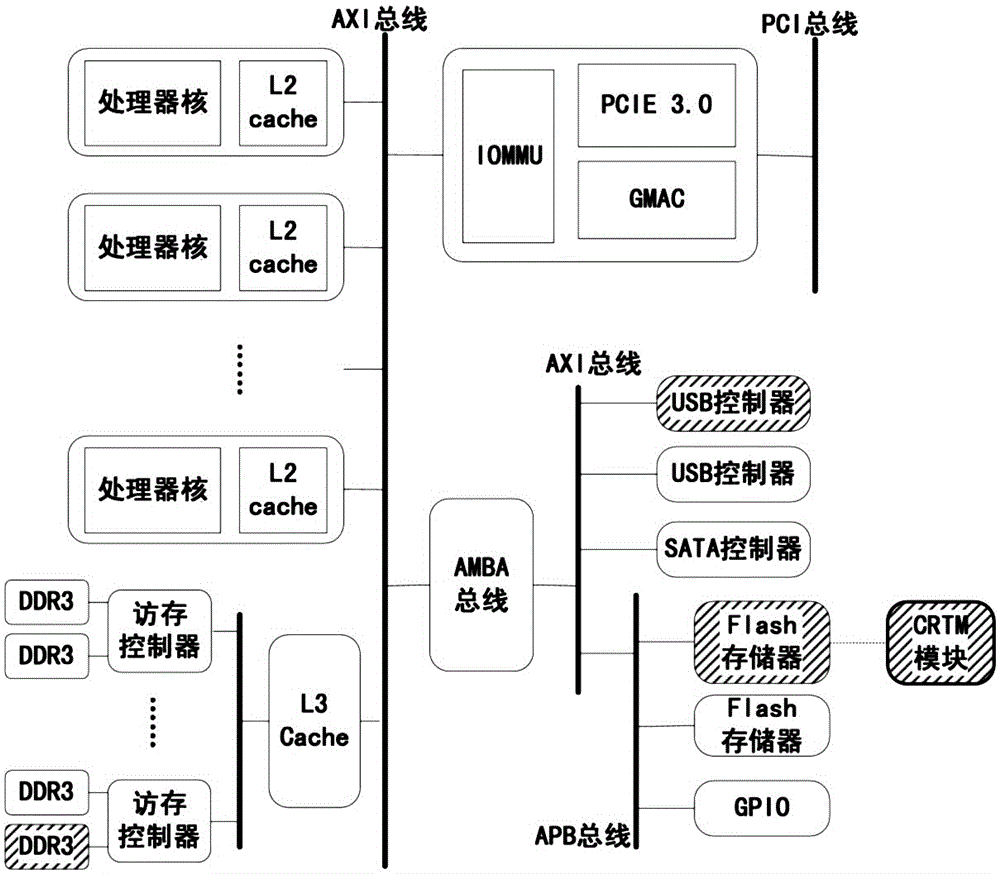
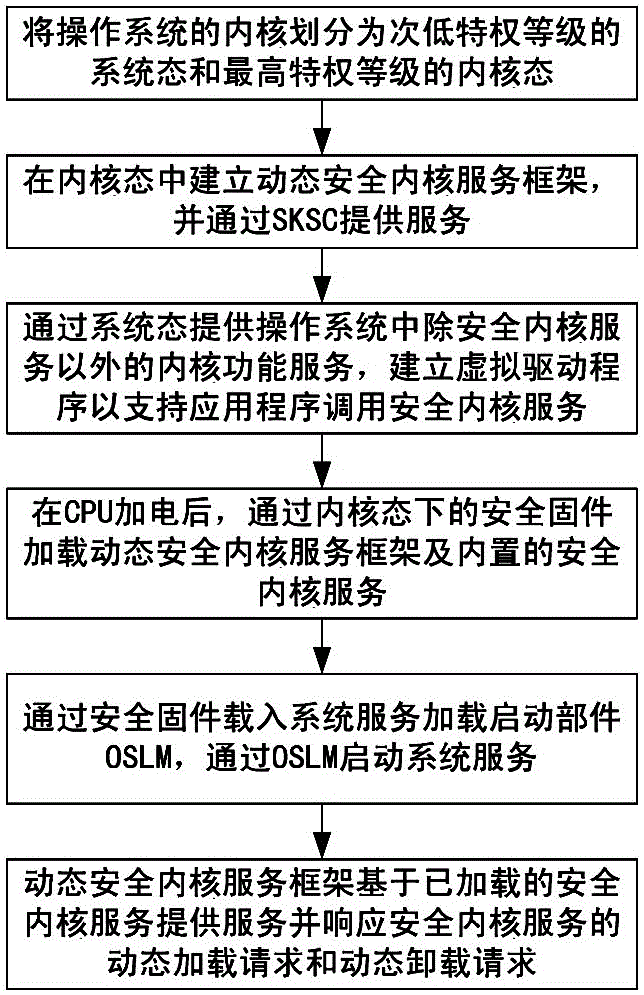
Dynamic running method for security kernel service of tristate operating system in Feiteng CPU
ActiveCN105022954AReduce security risksImprove safety and reliabilityPlatform integrity maintainanceEcological environmentOperational system
The invention discloses a dynamic running method for a security kernel service of a tristate operating system in a Feiteng CPU. The method comprises the steps of: dividing a kernel into a system state and a kernel state of different privilege levels; establishing a service framework in the kernel state to serve as a container for the security kernel service, and establishing a call interface for the security kernel service; establishing a virtual driving interface in the system state to support a user state to call the security kernel service; loading the service framework and the built-in security kernel service after enabling the CPU to be powered on; and loading a loading part of a system service module and starting a system service, wherein the service framework provides the security kernel service and makes a response to a dynamic loading / unloading request of the security kernel service. The dynamic running method can realize security protection on specific hardware resources of the system, realize security access to a core service of the operating system, efficiently support credibility conformation of the system, effectively improve the system security, lower the security risk of traditional kernel bugs and provide an efficient and flexible credible calculating ecological environment for users.
Owner:TSINGHUA UNIV +1
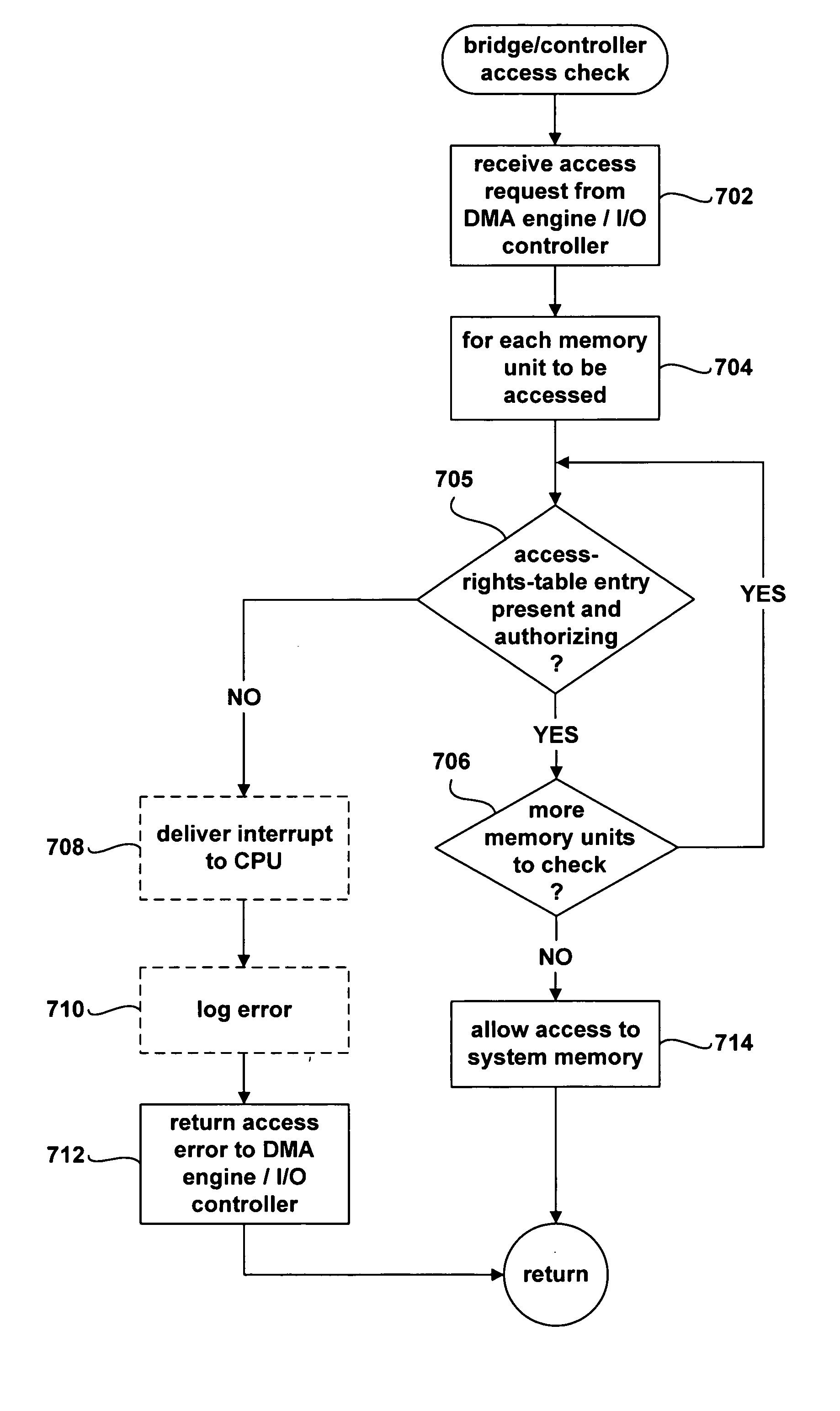
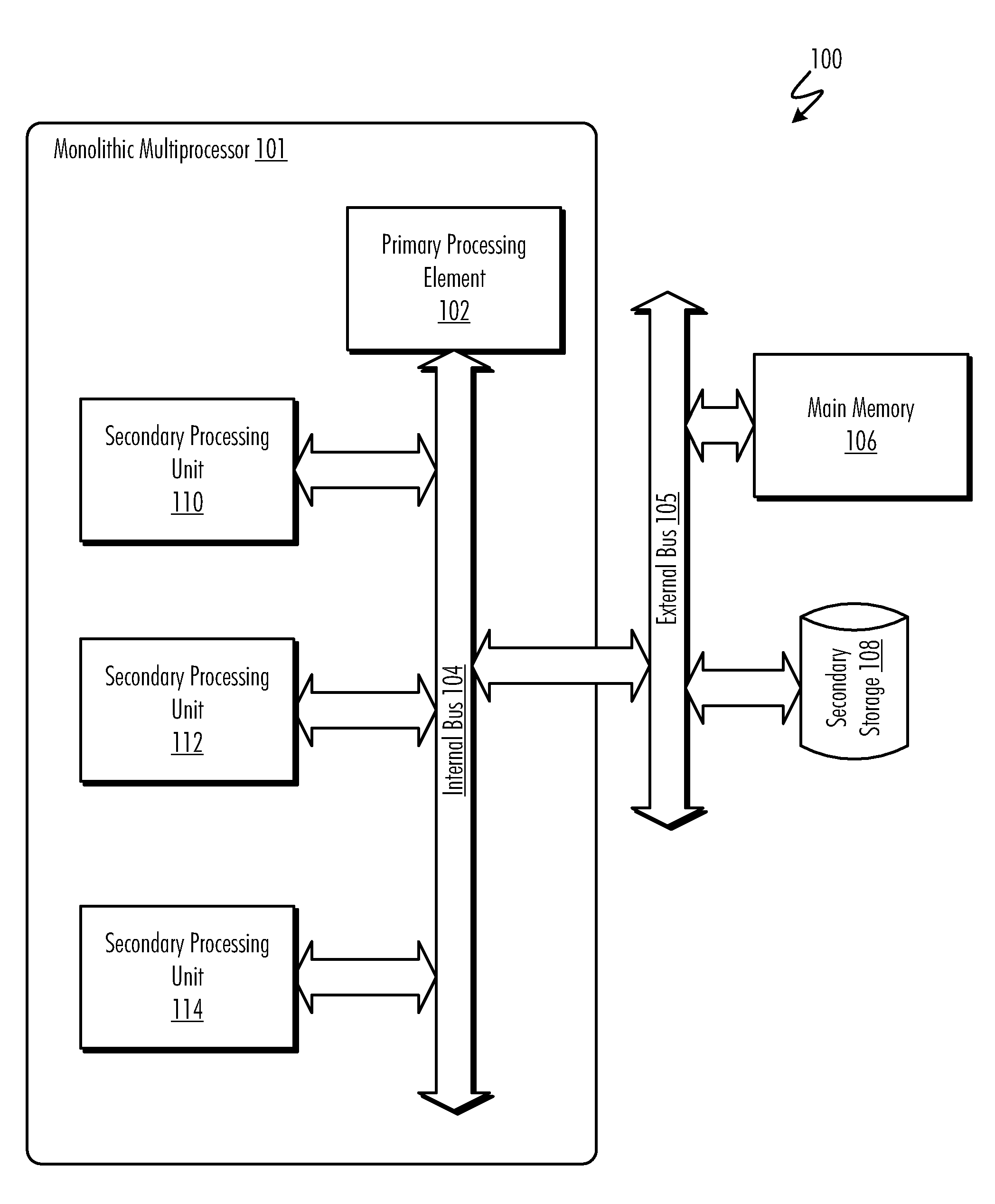
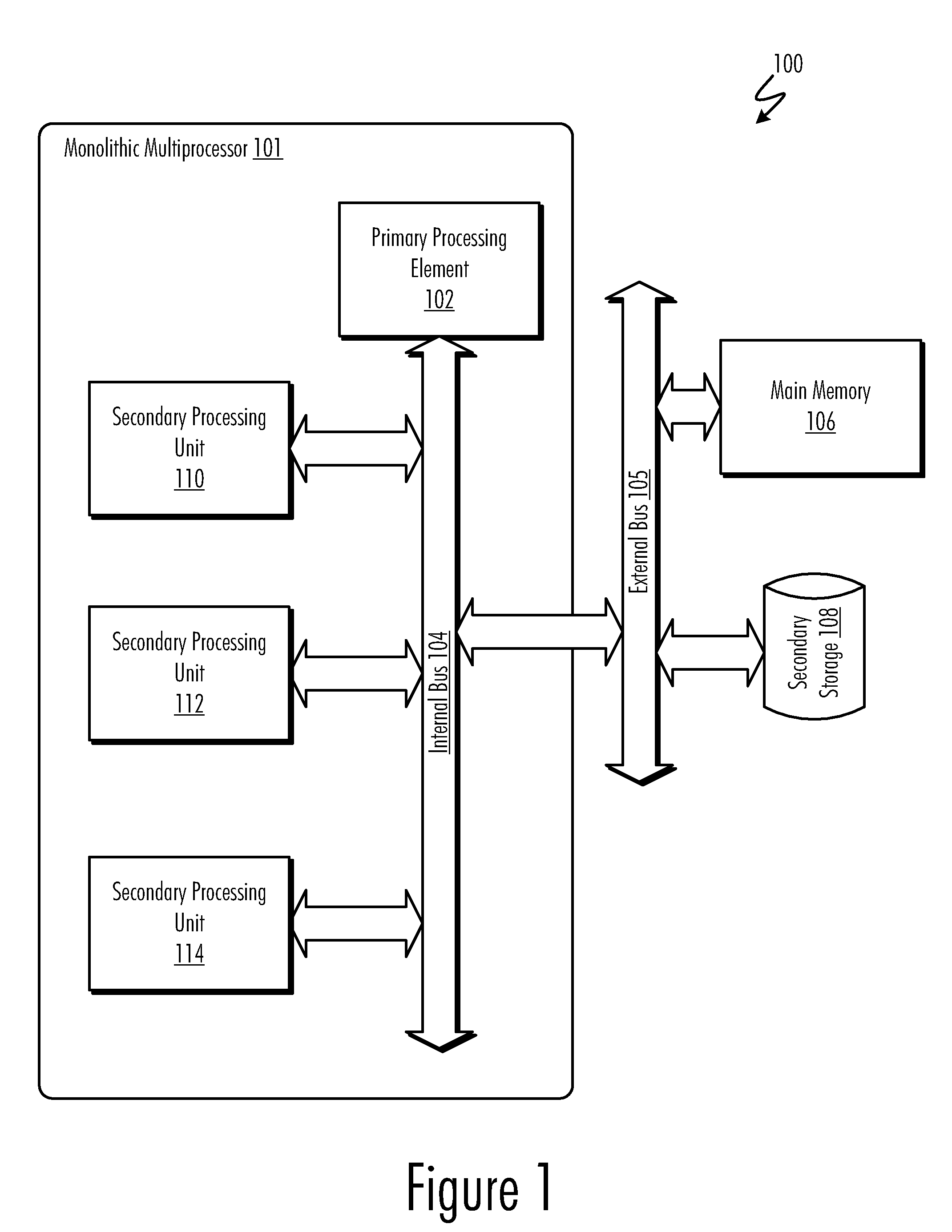
Secure direct memory access through system controllers and similar hardware devices
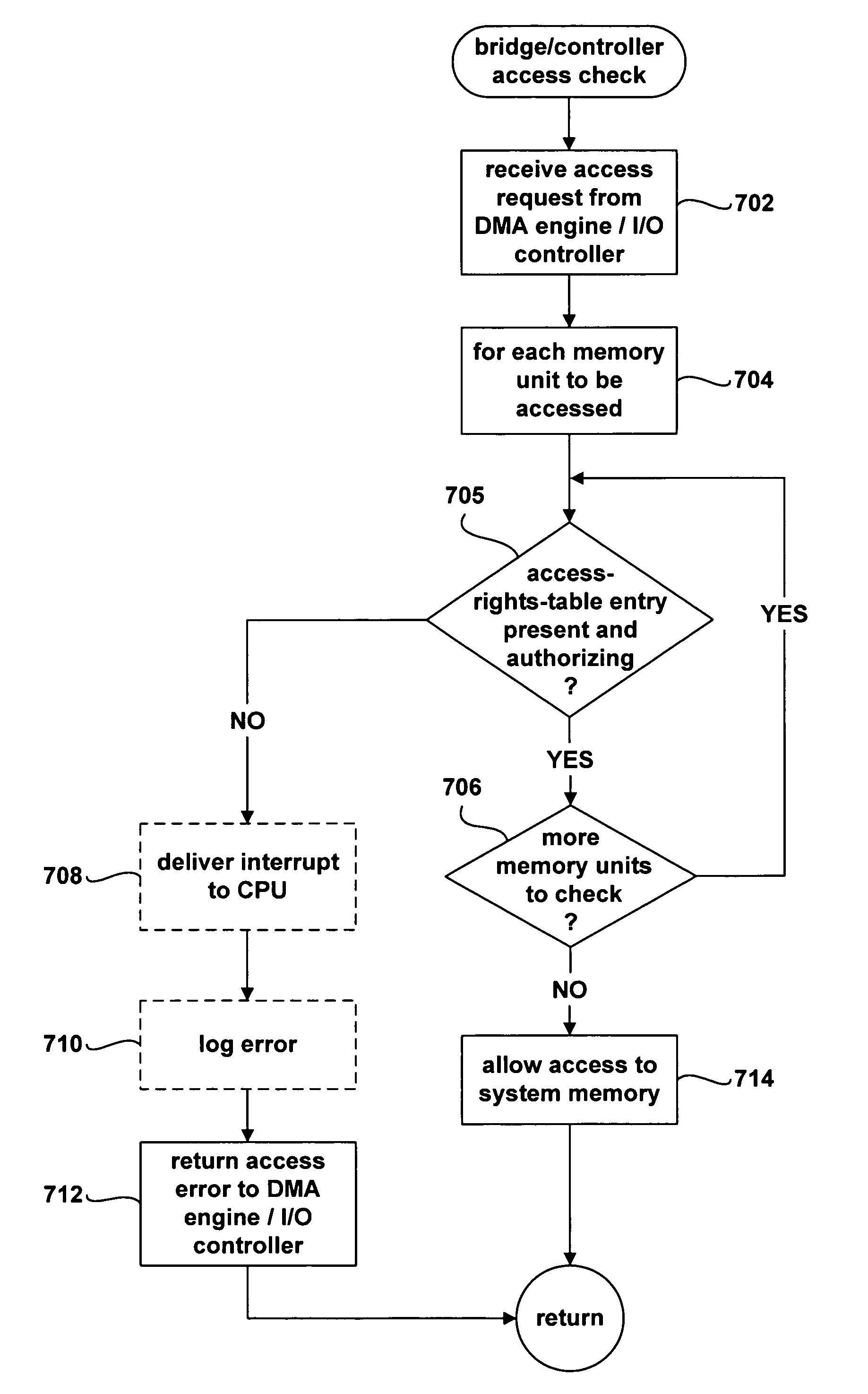
ActiveUS20050165783A1Specific access rightsDigital data processing detailsDirect memory accessSecurity kernel
A method and system for providing secure, direct access to computer system resources, such as system memory, by a non-trusted processing entity running in an unprivileged state that request access to the resource through a device that directly accesses the resource. The device includes access-right-checking logic and is configured to verify access rights of non-trusted processing entities that attempt to access the resource through the device. By checking access rights, the device ensures that non-trusted processing entities access only those particular portions of the resource authorized for access by the secure kernel.
Owner:GOOGLE LLC
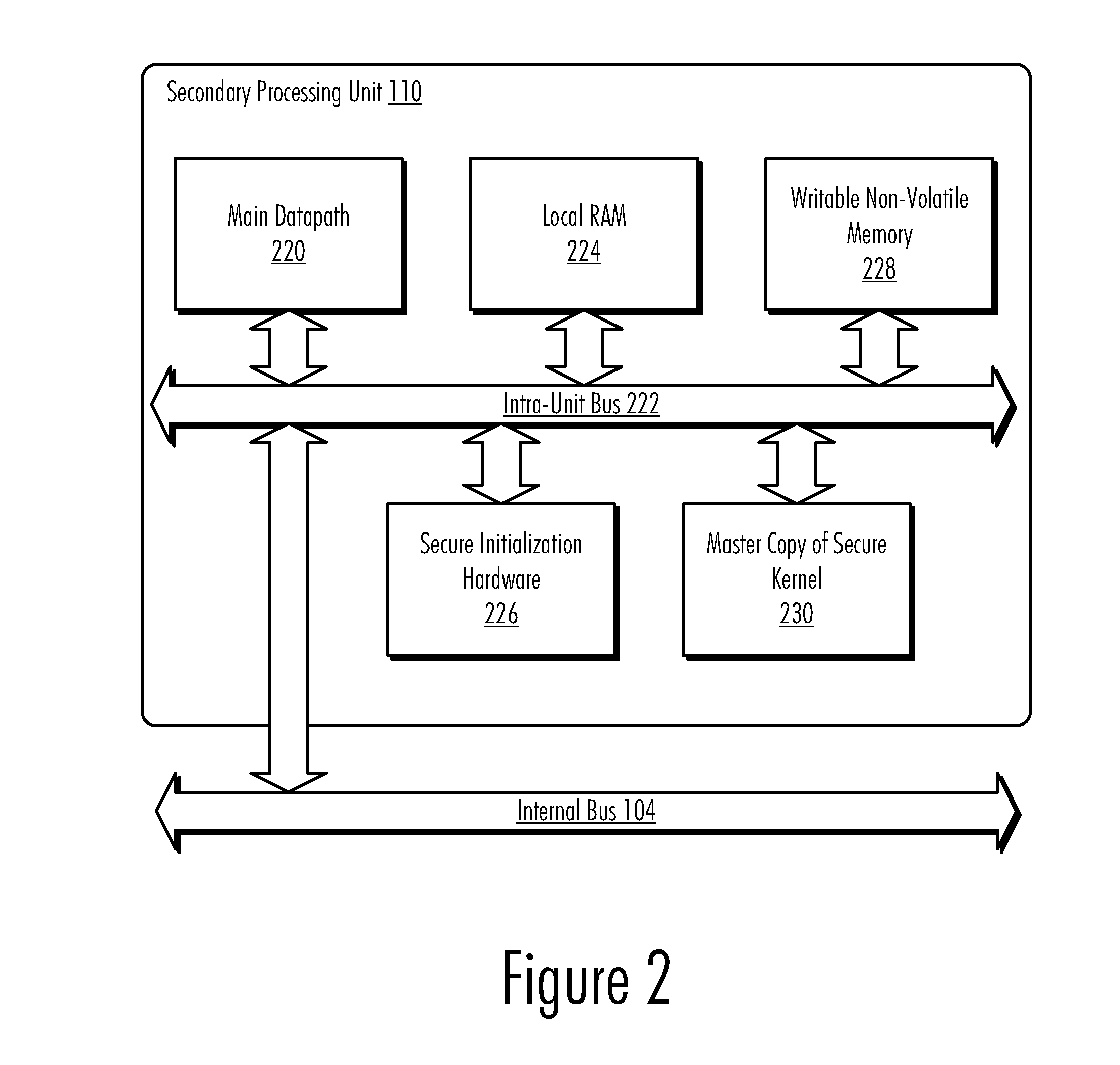
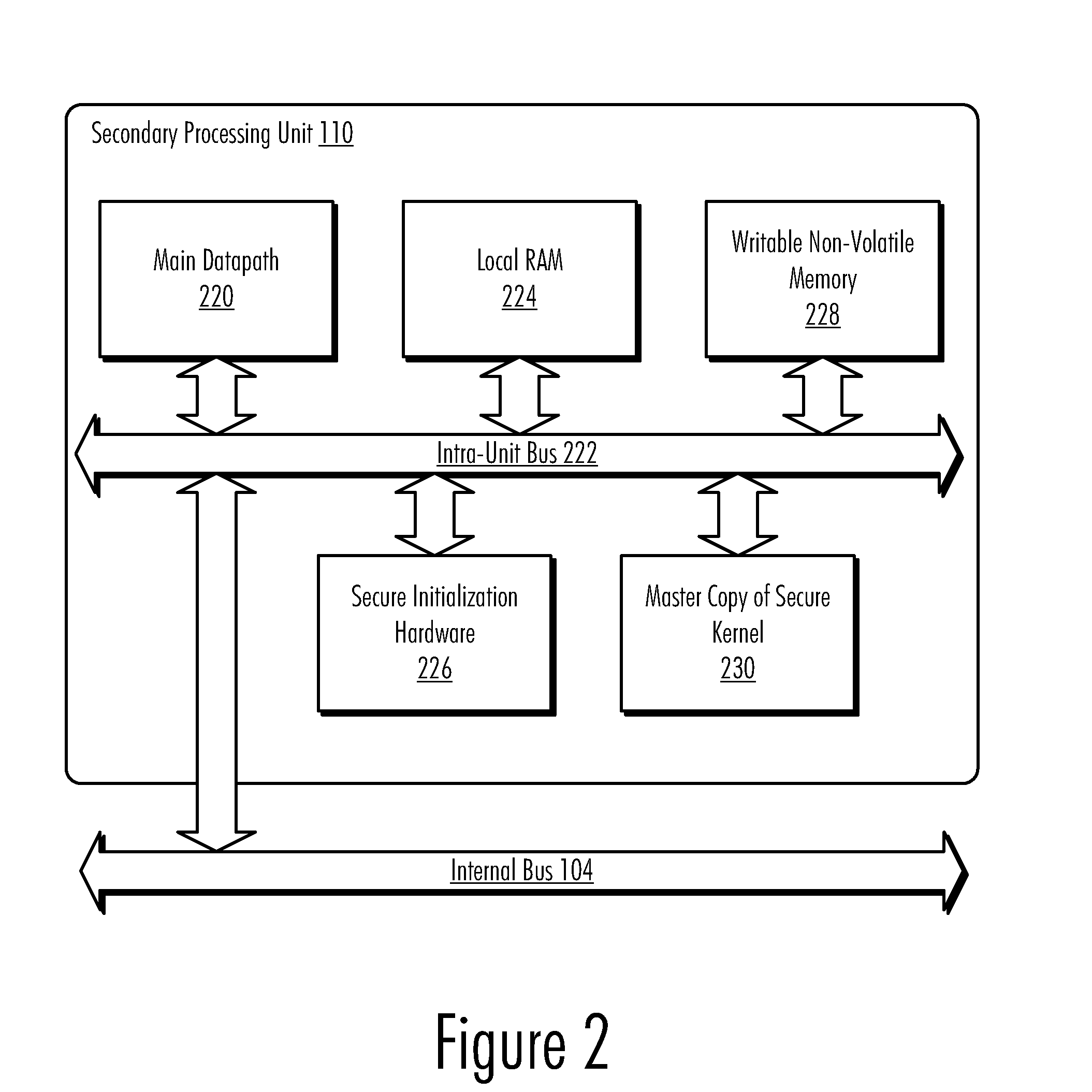
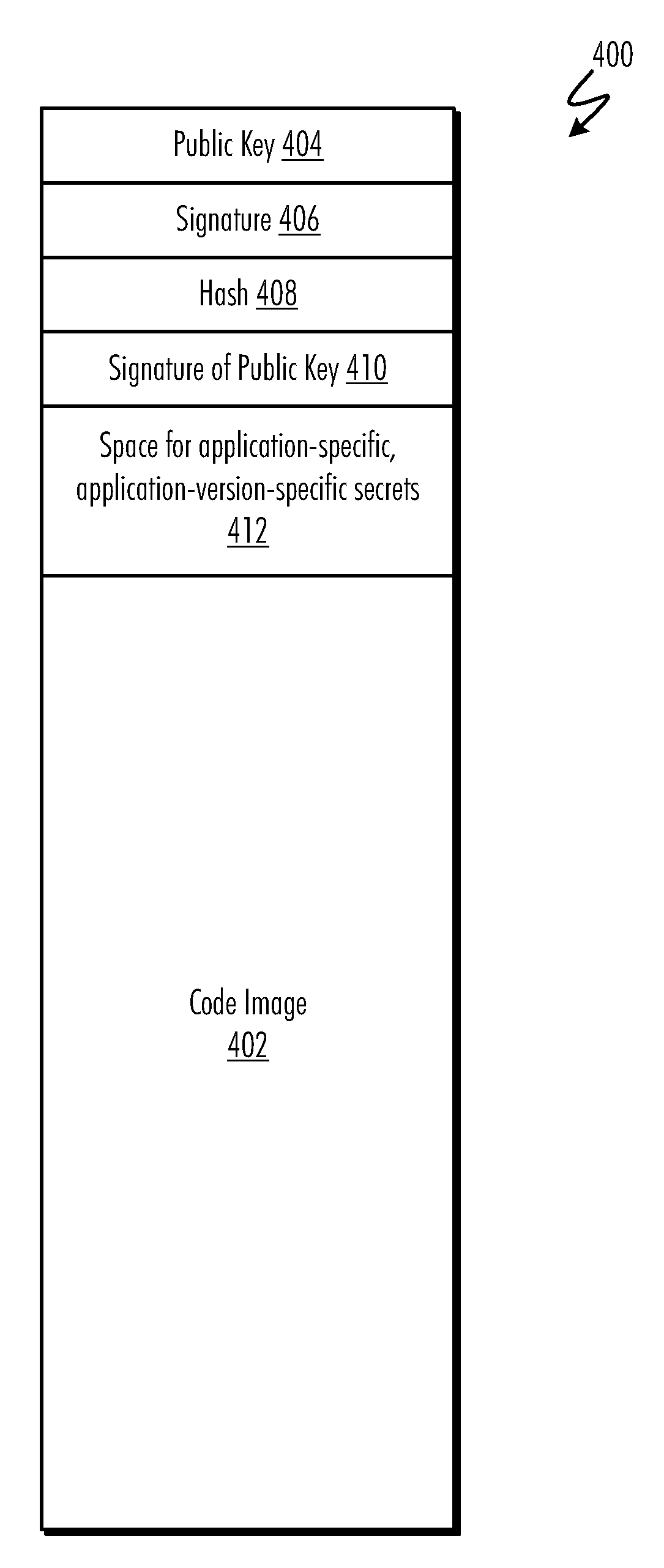
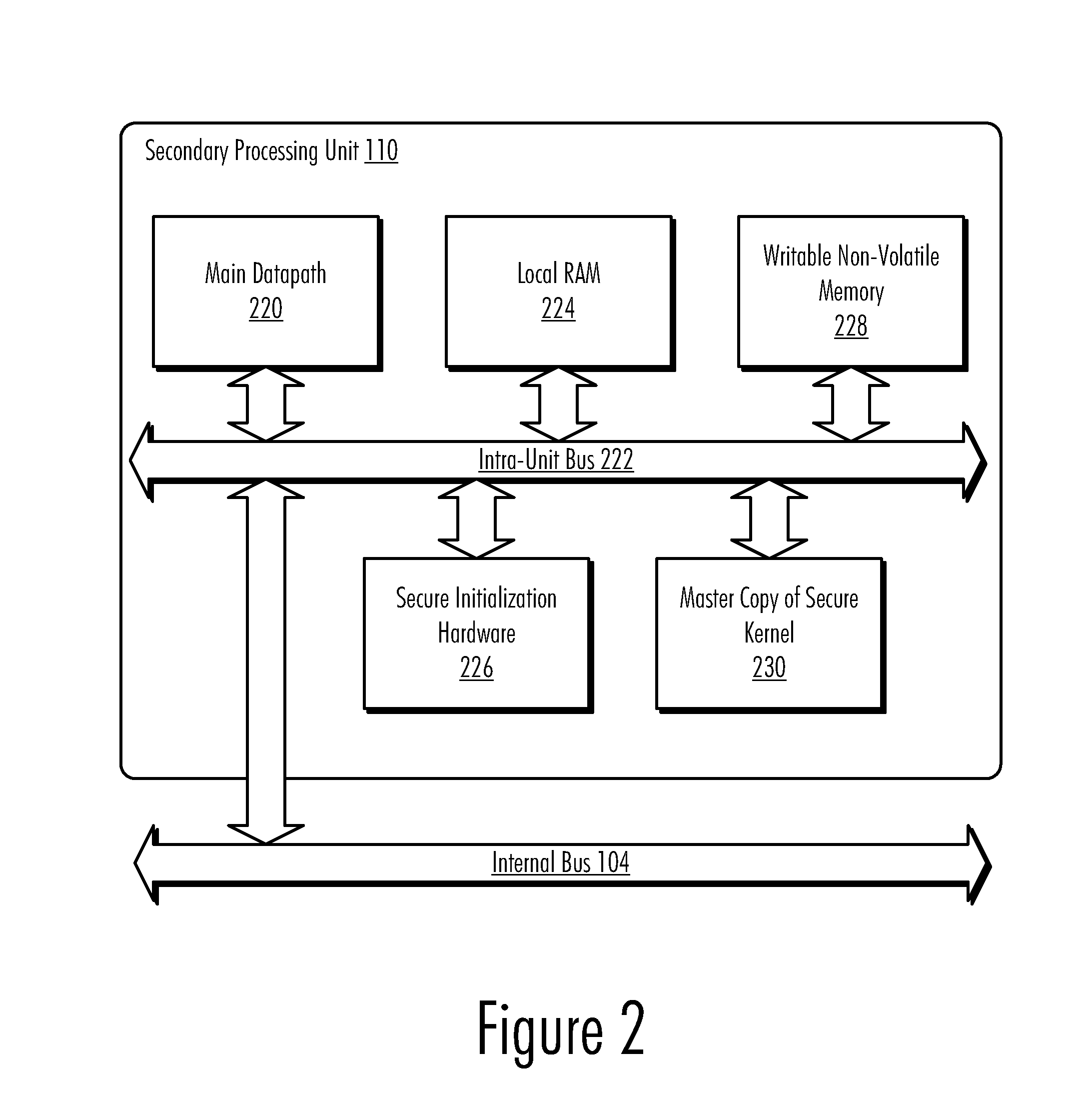
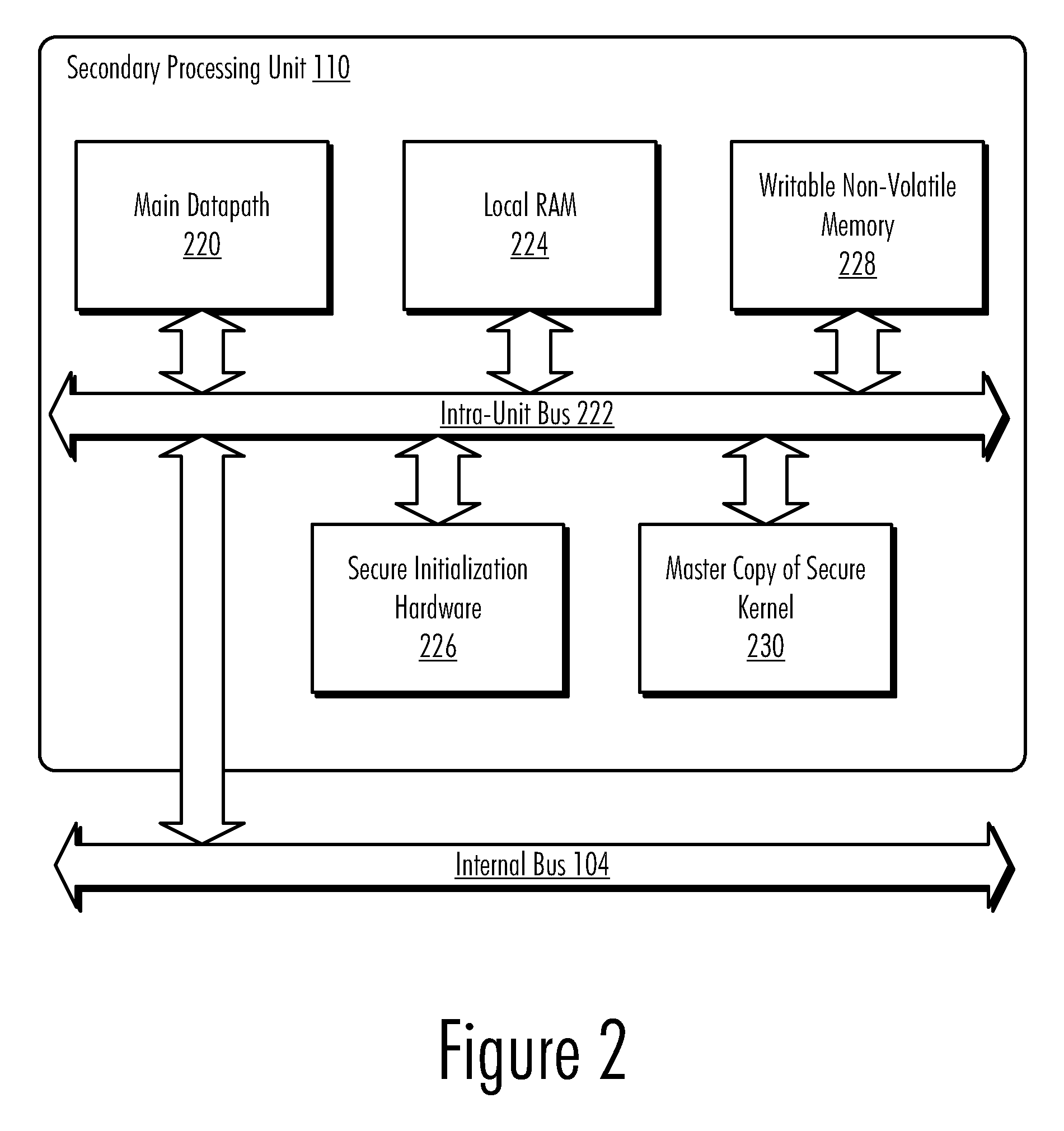
Updateable Secure Kernel Extensions
InactiveUS20080301440A1Volume/mass flow measurementUser identity/authority verificationData processing systemSecurity kernel
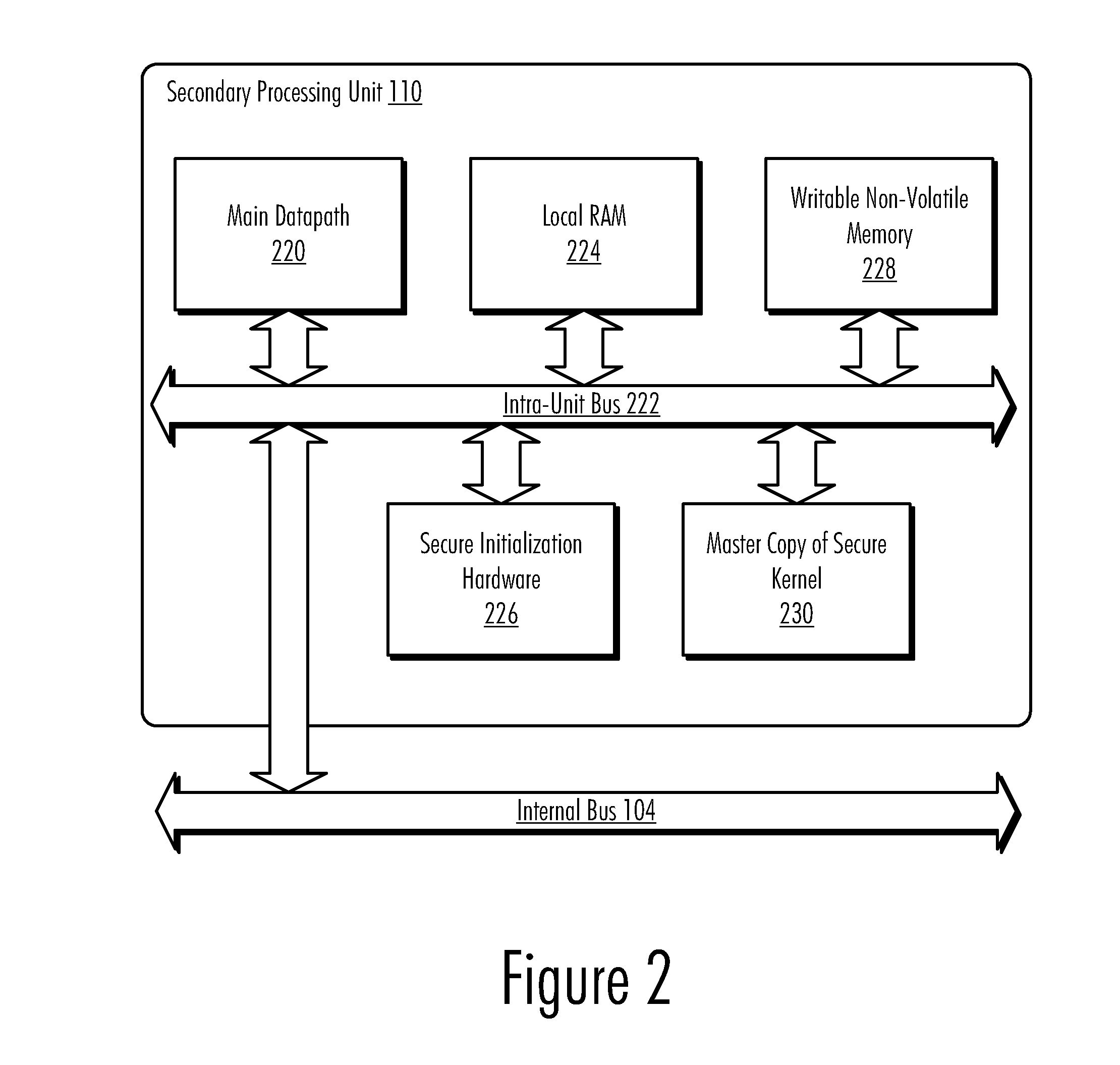
A method, computer program product, and data processing system for providing an updateable encrypted operating kernel are disclosed. In a preferred embodiment, secure initialization hardware decrypts a minimal secure kernel containing sensitive portions of data and / or code into a portion of the processor-accessible memory space, from which the kernel is executed. Most system software functions are not directly supported by the secure kernel but are provided by dynamically loaded kernel extensions that are encrypted with a public key so that they can only be decrypted with a private key possessed by the secure kernel. The public / private key pair is processor-specific. Before passing control to a kernel extension the secure kernel deletes a subset of its sensitive portions, retaining only those sensitive portions needed to perform the task(s) delegated to the kernel extension. Which sensitive portions are retained is determined by a cryptographic key with which the kernel extension is signed.
Owner:IBM CORP
Support for Multiple Security Policies on a Unified Authentication Architecture
ActiveUS20090086974A1Digital data processing detailsPublic key for secure communicationData processing systemSecurity kernel
A method, computer program product, and data processing system are disclosed for ensuring that applications executed in the data processing system originate only from trusted sources are disclosed. In a preferred embodiment, a secure operating kernel maintains a “key ring” containing keys corresponding to trusted software vendors. The secure kernel uses vendor keys to verify that a given application was signed by an approved vendor. To make it possible for independent developers to develop software for the herein-described platform, a “global key pair” is provided in which both the public and private keys of the pair are publicly known, so that anyone may sign an application with the global key. Such an application may be allowed to execute by including the global key pair's public key in the key ring as a “vendor key” or, conversely, it may be disallowed by excluding the global public key from the key ring.
Owner:IBM CORP
Multi-Factor Security System With Portable Devices And Security Kernels
InactiveUS20070283145A1Increase speedPopular acceptanceDigital data processing detailsUser identity/authority verificationTransceiverSecurity kernel
A system for multi-factor security involving multiple secure devices that distribute the secured functions of the system over the different devices, such that the loss or theft of any one of them does not compromise the overall security of the system. Moreover, a configuration of devices is also secure even if one of them has been attacked by malicious software agents, such as “keyboard sniffers”. A novel contactless smart card reader (200) is presented that incorporates a transceiver antenna (220) within a keypad (210) of a device used with contactless smart cards (100). When the card (100) is pressed against the device's keypad (210), the transceiver (220) of the device establishes a session with the smart card (100). A variety of systems are presented, including those using mobile telephones, computer-interfaced card readers, personal digital appliances, and television set-top box remote controllers.
Owner:FORTRESS GB
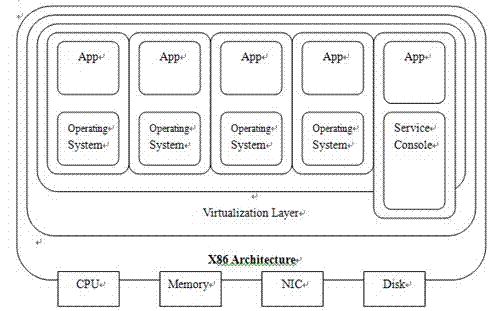
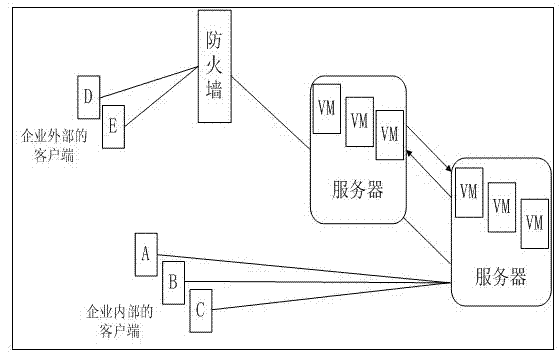
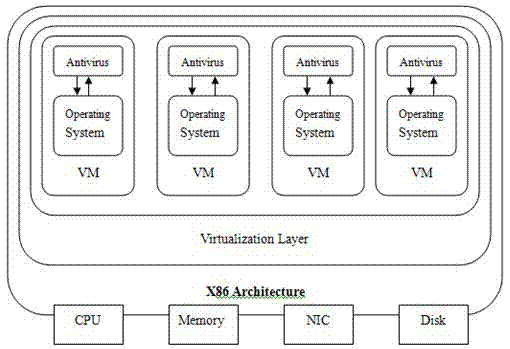
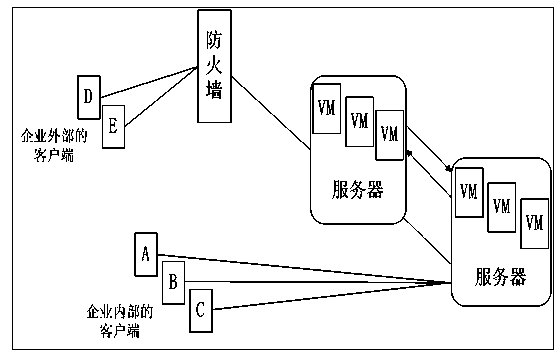
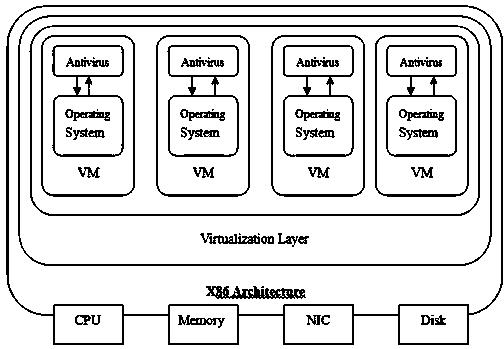
Virtual machine (VM) online antivirus system based on KVM virtualization platform
The invention relates to a computer technology field and provides a virtual machine (VM) online antivirus system based on a KVM virtualization platform. A safety kernel module, a safety control module and a network module are arranged. A function which is used to read memory is added in a KVM kernel module. An interface of a safety kernel module registration hook is provided. The safety kernel module is used to register the hook in the KVM kernel module, emit a scanning command to the safety control module, accept a scanning surveillance result obtained by the safety control module, pause a suspicious process and carry out corresponding processing to the suspicious process. The safety control module calls an antivirus engine to carry out scanning surveillance to the process of all the VMs in the memory of the safety control module and reports the result to the safety kernel module. The network module is formed by a server network module and a client network module.
Owner:北京海云捷迅科技股份有限公司 +1
Secure processor architecture for use with a digital rights management (DRM) system on a computing device
InactiveUS20070226492A1Digital data processing detailsAnalogue secracy/subscription systemsSecurity kernelDigital rights management system
A secure processor is operable in normal and preferred modes, and includes a security kernel instantiated when the processor enters into preferred mode and a security key accessible by the security kernel during preferred mode. The security kernel employs the accessed security key to authenticate a secure application, and allows the processor to be trusted to keep hidden a secret of the application. To instantiate the application, the processor enters preferred mode where the security key is accessible, and instantiates and runs the security kernel. The security kernel accesses the security key and applies same to decrypt a key for the application, stores the decrypted key in a location where the application will expect same, and instantiates the application. The processor then enters the normal mode, where the security key is not accessible.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for secure direct memory access
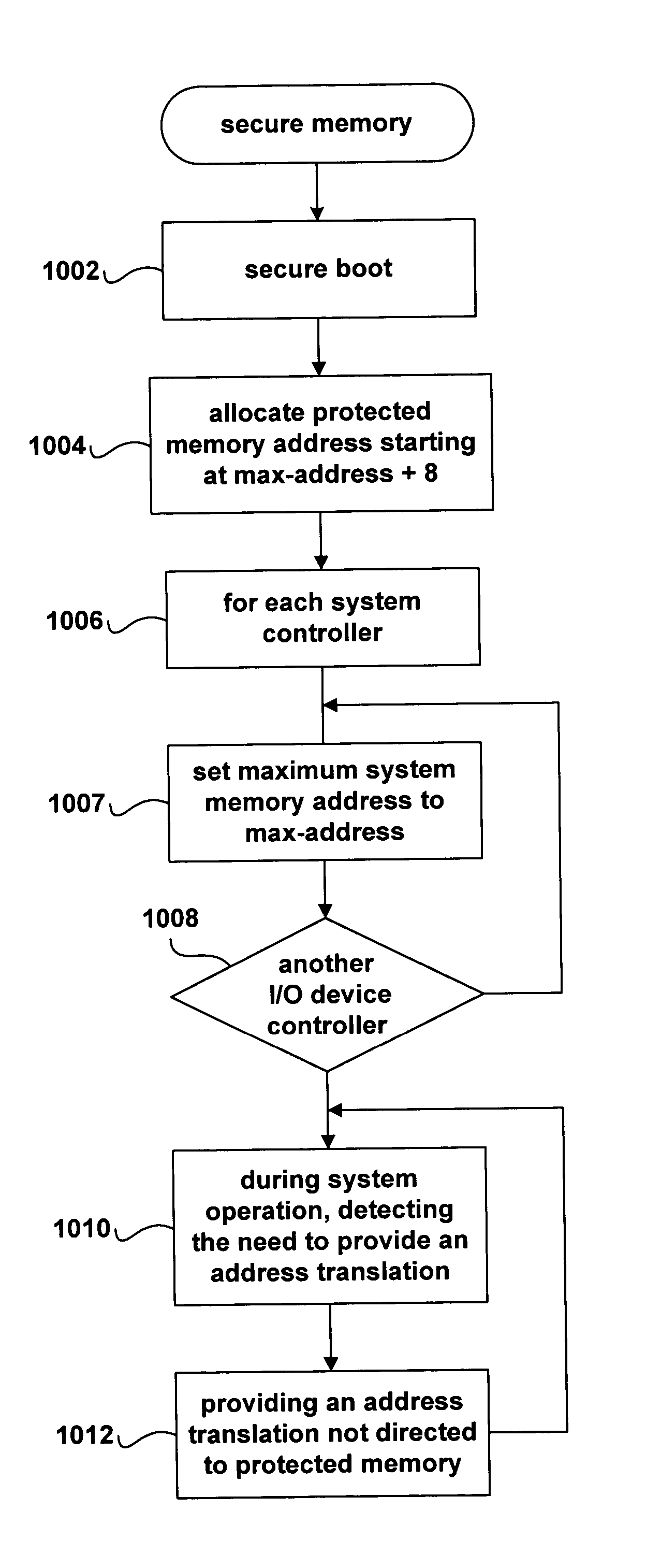
InactiveUS20050033979A1Digital data processing detailsMemory adressing/allocation/relocationMemory addressDirect memory access
Method and system that allows a secure processing entity to allocate a portion of a system resource for use only by the secure processing entity. The portion of the system resource allocated for use only by the secure processing entity is protected from DMA-access by an untrusted processing entity, such as an I / O controller in the control of untrusted software. In one embodiment, a secure kernel may provide address translations to a system controller that result in the system controller returning invalid-memory-address errors to a DMA engine attempting to access a portion of a system memory allocated for use only by a secure kernel. In another embodiment of the present invention, a secure kernel initializes a system controller to contain a view of system-memory address space that does not include a portion of system-memory address space allocated for use only by a secure kernel.
Owner:HEWLETT PACKARD DEV CO LP
Classified management method applied to security baseline software
InactiveCN106055984AImprove securityImprove efficiencyPlatform integrity maintainanceNODALInformation security management
The invention provides a classified management method applied to security baseline software, pertaining to the technical field of host security. The method comprises following respects including nodal point management, strategy management, knowledge base management, resource management, user management, log forms, alarm management and a security center. The classified management method applied to security baseline software has following beneficial effects: the method can be applied to the government, and enterprises and institutions so that comprehensive security kernel configuration services for computer terminals can be provided to help government-related departments set up a system for standardizing terminal security management, thereby obtaining the best management effect. The security and operation and management efficiency of computer terminals can be significantly improved so that security of government information is ensured.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
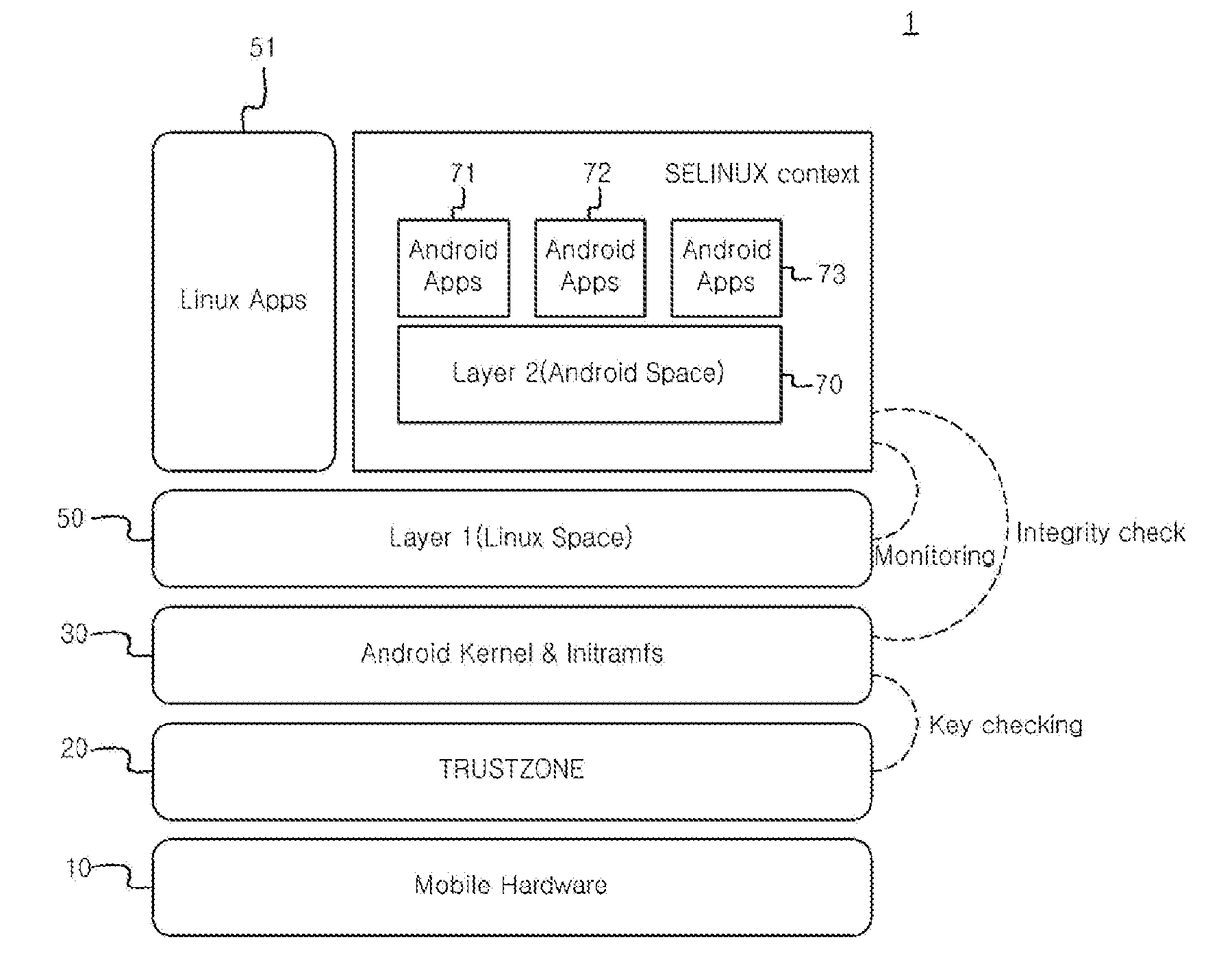
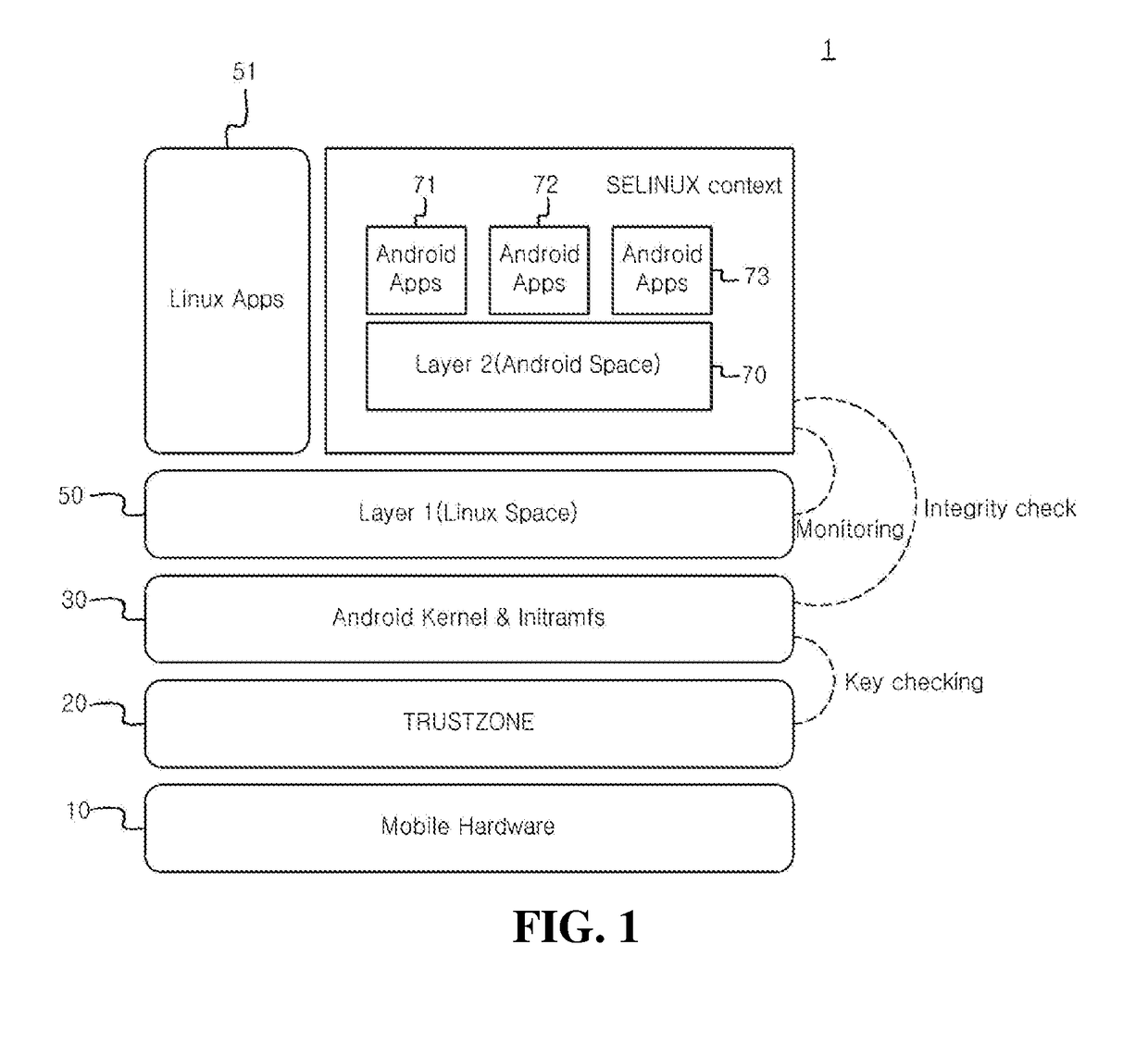
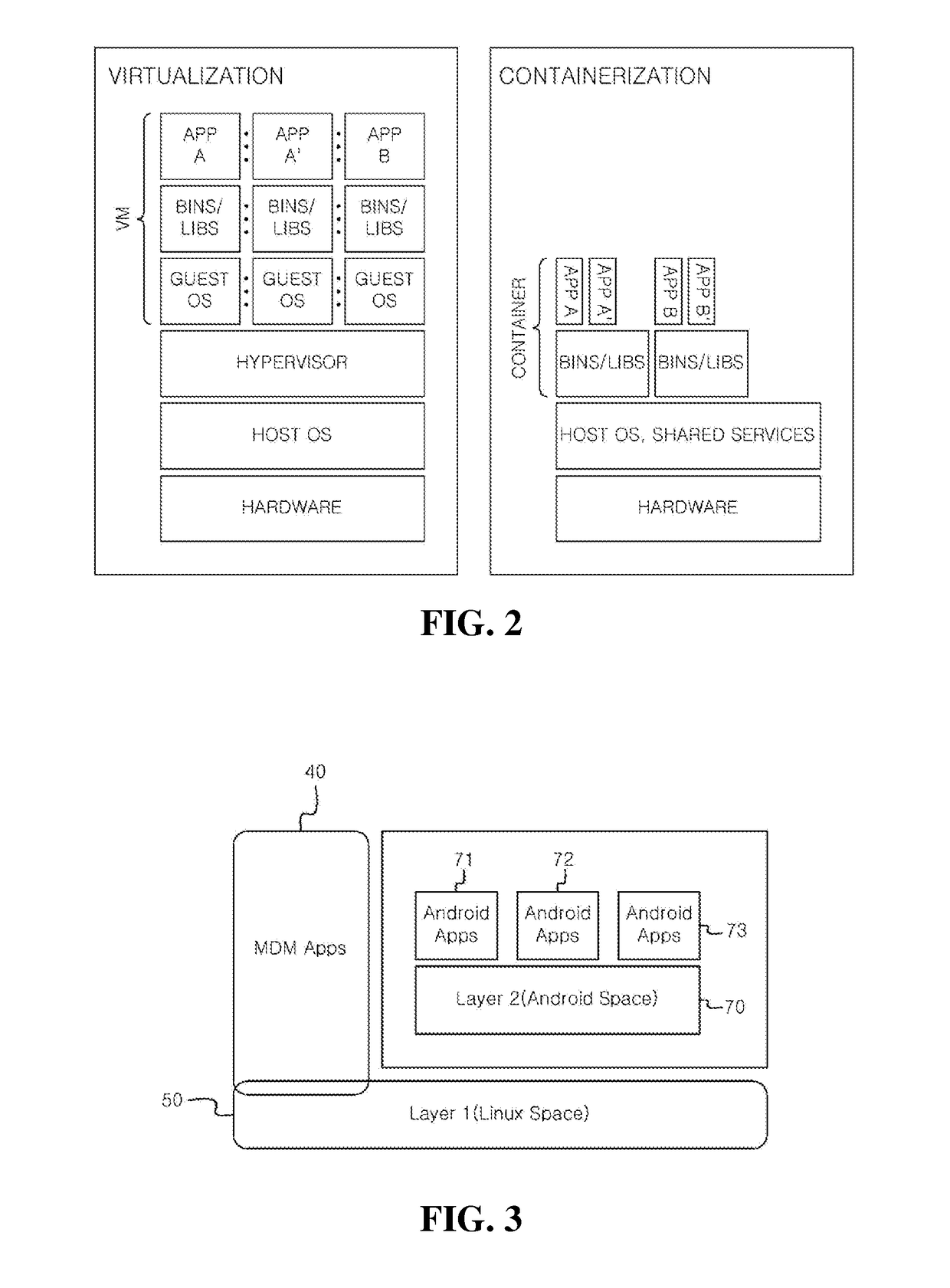
Duo operating system for android security, mobile device having the same, method of securing mobile device having the same
A duo operating system (OS) for Android security is provided. The duo operating system includes an Android kernel providing drivers for a hardware and an interface of a mobile device, a security platform storing a security key of an integrity check when a kernel is booted in a Linux space, a first layer containing a Linux-based operating system executing a mobile device monitoring and a mobile device security examination, and a second layer containing one or more container-based Android operating systems being a user space layer interacting with users through Android applications.
Owner:CROWDSTRIKE
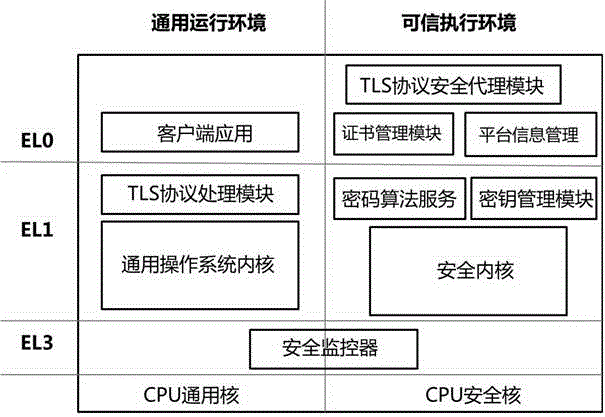
Method for safe improvement of TLS protocol processing based on CPU space-time isolation mechanism
ActiveCN106603487AImprove confidentialityAvoid safety hazardsUser identity/authority verificationOperational systemProtocol processing
The invention discloses a method for the safe improvement of TLS protocol processing based on a CPU space-time isolation mechanism. The method includes, at first, constructing a trusted execution environment for a TLS protocol security agent assembly, that is, a security kernel; secondly, constructing a common running environment for the running of a TLS protocol processing module, that is, a general operating system kernel; and at the end, constructing a security monitor being responsible for the context switching between two running environments and running in the CPU security kernel. The method is advantageous in that the processing flow of a TLS handshake protocol is safely improved, the deficiency of the TLS in the communication platform integrity authentication aspect is expanded, so that the security hidden troubles caused by the high realization level, insufficient independence, and missed platform authentication of the TLS protocol are effectively solved, and the security of data encryption transmission and platform identity authentication of the two parties of the computer communication is improved.
Owner:中软信息系统工程有限公司
Conditional access to digital rights management conversion
InactiveUS20090106850A1Drying solid materials with heatDigital data processing detailsInternet privacyDigital rights management system
The present invention provides for an interface between two seemingly incompatible and different content protection systems. Accordingly, protected content may be transferred between the respective security kernels of a conditional access (CA) and digital rights management (DRM) systems, while maintaining security of the content and any associated protection information. The transfer and consumption of protected content and the associated content protection information may be achieved by temporarily or permanently binding the respective security kernels of the CA and DRM systems, transcribing content protection information, and potentially transcribing the content.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for caller authentication
ActiveUS20050166208A1Error detection/correctionPlatform integrity maintainanceOperational systemSecurity kernel
In various embodiments of the present invention, execution-state transitions occur in a first portion of a system, and a cumulative execution state for each process is maintained by a second portion of the system so that, when a second-portion routine is called, the second-portion routine can determine whether or not the current execution state is suitable for execution of the second-portion routine. In various embodiments, a callpoint log, allocated and maintained for each process, stores the cumulative execution state for the process. In one embodiment, the first portion is an operating system, and the second portion is a secure kernel, with the cumulative execution state used by the secure kernel to prevent unauthorized access by erroneously or maliciously invoked operating-system routines to secure kernel routines. In another embodiment, the cumulative execution state is used as a debugging tool by the second-portion routines to catch errors in the implementation of the first-portion routines.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Central processing unit design method supporting software code data confidentiality and credibility execution
PendingCN110659458AImprove confidentialityImprove integrityDigital data protectionInternal/peripheral component protectionMemory addressData segment
The invention provides a central processing unit design method. Belonging to the field of digital circuits, the method comprises the following steps: 1, processing; dividing and reserving a memory address range for adding a read-only memory and a random access memory in a chip; the instruction in the off-chip memory is limited to be invalid when the content of the on-chip memory is read and written; a private key certificate and a safety kernel code are persistently stored in a chip, memory access is monitored, address monitoring event interruption is triggered, an address monitoring event interruption processing program is written to achieve real-time decryption and encryption of to-be-accessed data, and a to-be-executed instruction is preset to a register and executed from the register.A trusted computing system can be realized on the novel central processing unit, an application program accommodating an encrypted ciphertext form code segment and a data segment can be loaded and executed in real time. Meanwhile, confidential information of the application program is prevented from being accessed unauthorized and leaked to an external bus, and the confidentiality, integrity and authenticity of the confidential information in the application program are protected.
Owner:陈昶宇
Credible application management system and loading method for credible applications
InactiveCN105787353AIncrease flexibilityImprove acceleration performanceComputer security arrangementsExtensibilitySecurity kernel
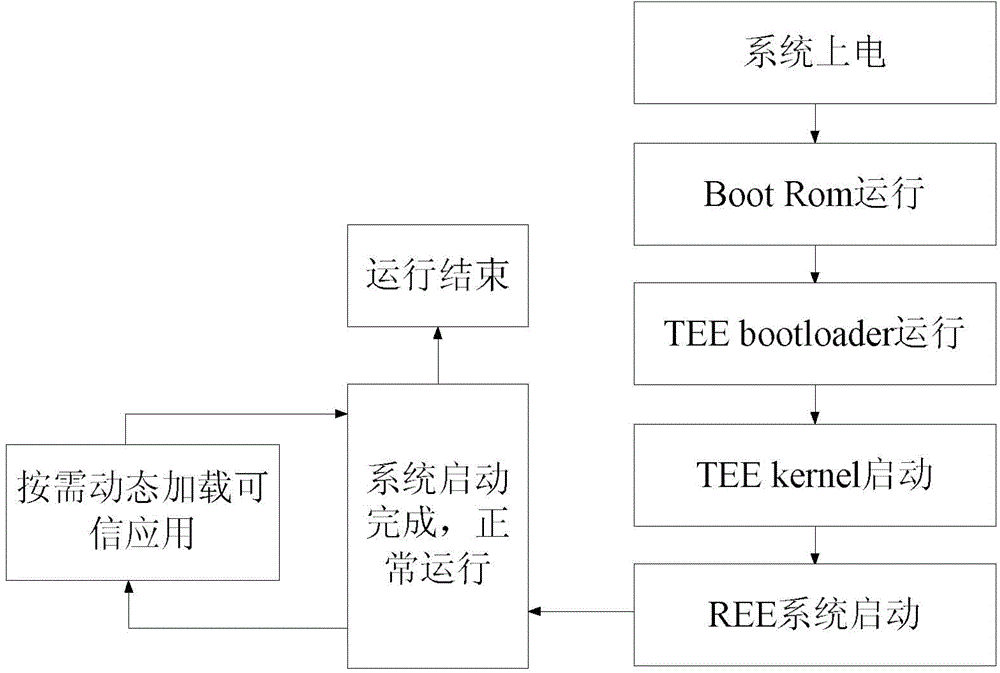
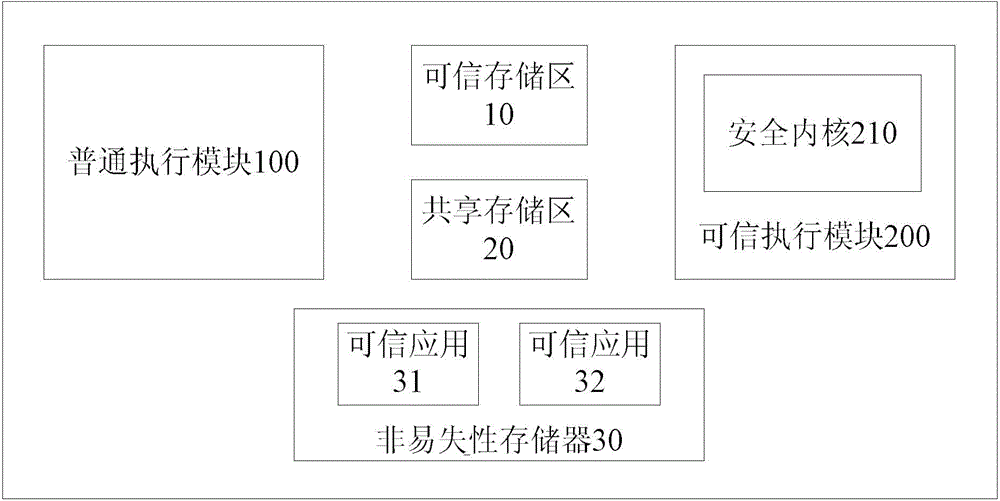
The invention provides a credible application management system. Each credible application serves as a single file, and then a common execution module can dynamically request a desired credible application for a credible execution module during operation; a safe kernel loads the credible application, i.e., loading of the credible application can be performed during operation of the credible application management system, and in this way, the flexibility and the extendibility of the system can be improved, and the run-up time of the system can be shortened. The invention also provides a loading method for the credible applications in order to achieve a dynamic loading process.
Owner:LEADCORE TECH
Method and system for realizing user authentication through biological characteristic information
InactiveCN105868610AImprove reliabilityImprove securityDigital data authenticationTransmissionApplication serverPassword
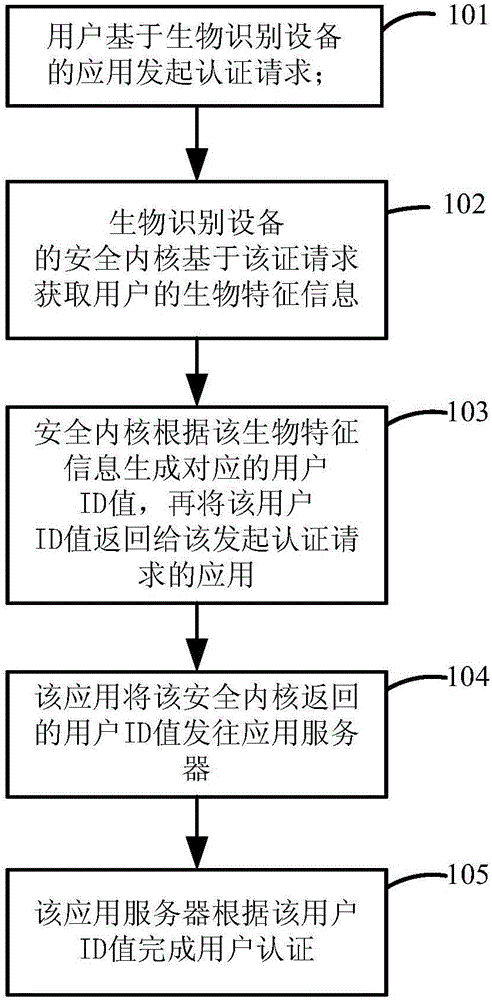
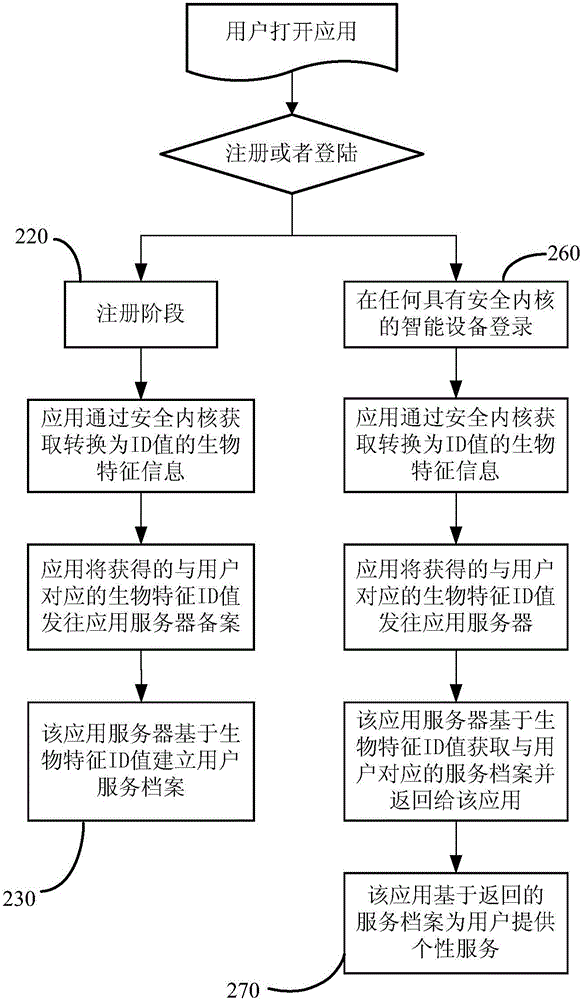
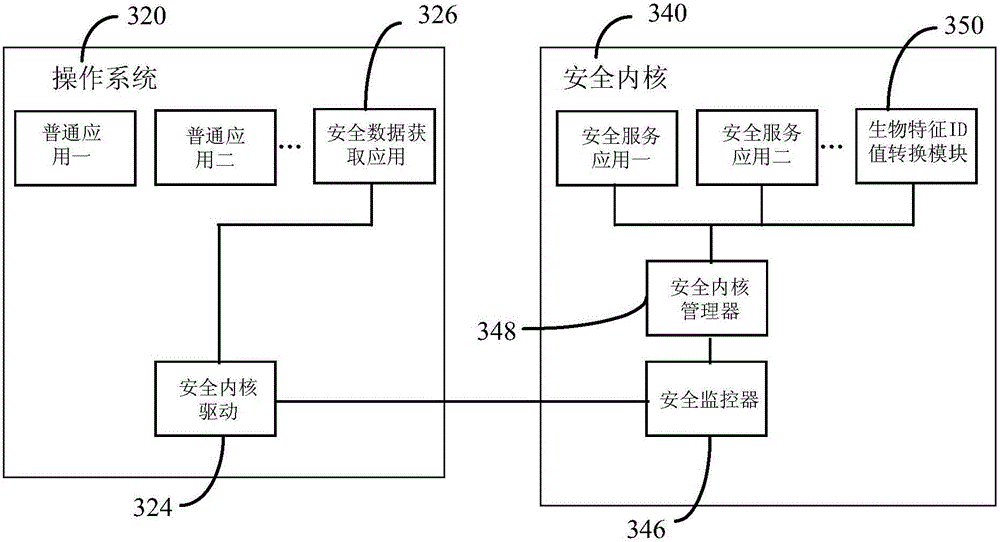
The invention discloses a method and a system for realizing user authentication through biological characteristic information. The method comprises the following steps: a user initiates an authentication request on the basis of an application of biometric identification equipment; a security kernel of the biometric identification equipment acquires the biological characteristic information of the user on the basis of the authentication request, generates a corresponding user ID value according to the biological characteristic information and returns the user ID value to the application initiating the authentication request; the application sends the user ID value returned by the security kernel to an application server, and the application server finishes user authentication according to the user ID value. One novel internet user identity authentication method is provided, so that the user does not need a user name or a password, and the login effect of the user name and the password can be finished on different sets of equipment through simple operation.
Owner:LETV HLDG BEIJING CO LTD +1
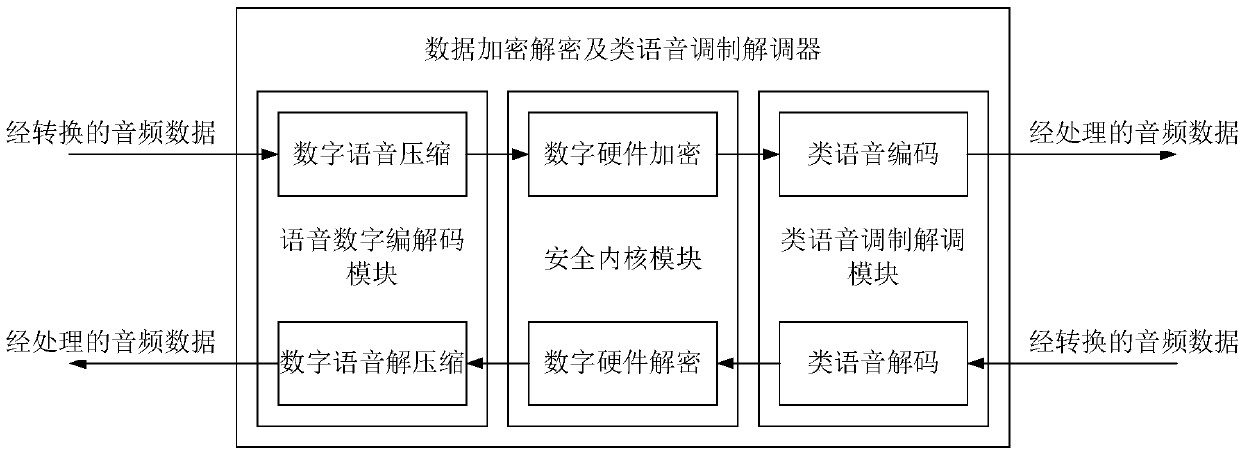
Voice communication information source encryption system for mobile terminal
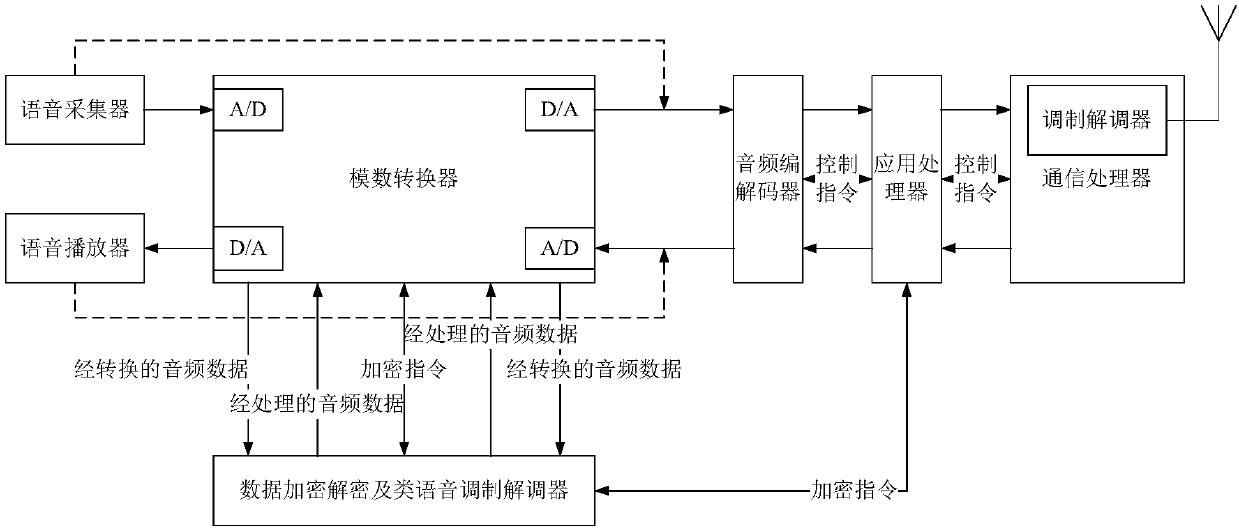
InactiveCN107786574AImplement encryptionPrevent intrusionTransmissionSecurity arrangementModem deviceVoice communication
The invention discloses a voice communication information source encryption system for a mobile terminal, comprising an analog-digital converter and a data encryption and decryption and phonological modem, wherein the analog-digital converter is used for converting an audio analog signal generated by a voice collector into voice data, or used for converting the audio data undergoing phonological encoding into an audio analog signal; the data encryption and decryption and phonological modem comprises a voice digital coding and decoding module, a security kernel module and a phonological modulation and demodulation module, wherein the voice digital coding and decoding module is used for performing digital voice compression on the converted audio data, the security kernel module is used for performing digital hardware encryption on the audio data subjected to digital voice compression, and the phonological modulation and demodulation module is used for performing phonological encoding onthe audio data subjected to digital hardware encryption. According to the invention, under the condition of not changing the voice communication procedure of the existing mobile terminal, voice communication information source encryption of the mobile terminal is realized, the encryption security is high, and the applicability is wide.
Owner:河南芯盾网安科技发展有限公司
Updateable secure kernel extensions
InactiveUS8332635B2Volume/mass flow measurementUser identity/authority verificationData processing systemSecurity kernel
A method, computer program product, and data processing system provide an updateable encrypted operating kernel. Secure initialization hardware decrypts a minimal secure kernel containing sensitive portions of data and / or code into a portion of the processor-accessible memory space, from which the kernel is executed. Most system software functions are not directly supported by the secure kernel but are provided by dynamically loaded kernel extensions that are encrypted with a public key so that they can only be decrypted with a private key possessed by the secure kernel. The public / private key pair is processor-specific. Before passing control to a kernel extension, the secure kernel deletes a subset of its sensitive portions, retaining only those sensitive portions needed to perform the task(s) delegated to the kernel extension. Which sensitive portions are retained is determined by a cryptographic key with which the kernel extension is signed.
Owner:INT BUSINESS MASCH CORP
Secure direct memory access through system controllers and similar hardware devices
ActiveUS7454787B2Specific access rightsDigital data processing detailsDirect memory accessSecurity kernel
A method and system for providing secure, direct access to computer system resources, such as system memory, by a non-trusted processing entity running in an unprivileged state that request access to the resource through a device that directly accesses the resource. The device includes access-right-checking logic and is configured to verify access rights of non-trusted processing entities that attempt to access the resource through the device. By checking access rights, the device ensures that non-trusted processing entities access only those particular portions of the resource authorized for access by the secure kernel.
Owner:GOOGLE LLC
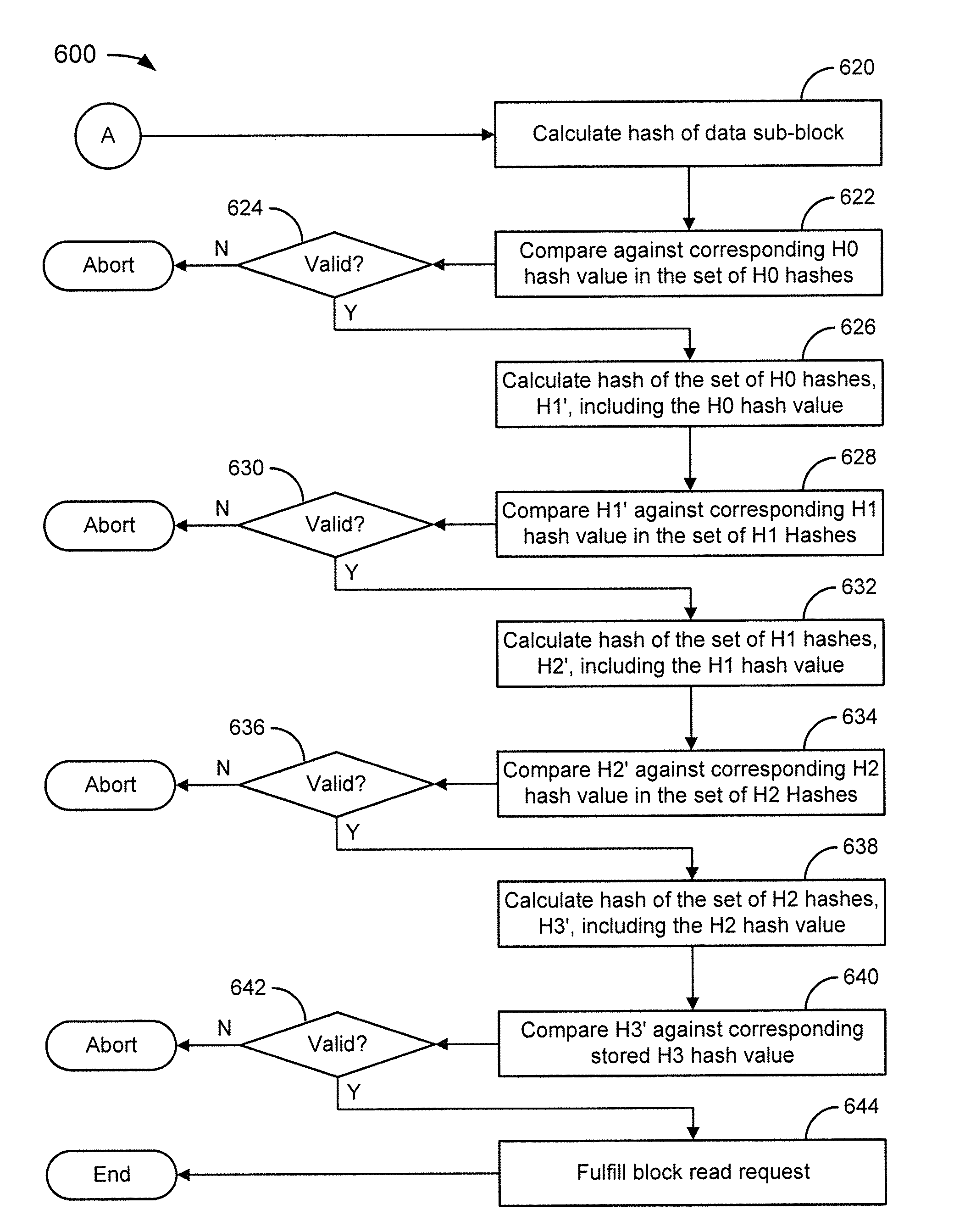
Block-based media content authentication
ActiveUS7991999B2User identity/authority verificationRecord information storageSecurity kernelService module
A technique for security and authentication on block-based media includes involves the use of protected keys, providing authentication and encryption primitives. A system according to the technique may include a secure device having a security kernel with protected keys. A disk drive security mechanism may support authentication of data, secrecy, and ticket validation using the security kernel and, for example, a ticket services module (e.g., a shared service that may or may not be used by other storage devices like flash).
Owner:SAMSUNG ELECTRONICS CO LTD
Internet-of-Things equipment safety protection system and method
ActiveCN113014539APrevent illegal reading and tamperingAvoid security breachesKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSecurity kernelServer appliance
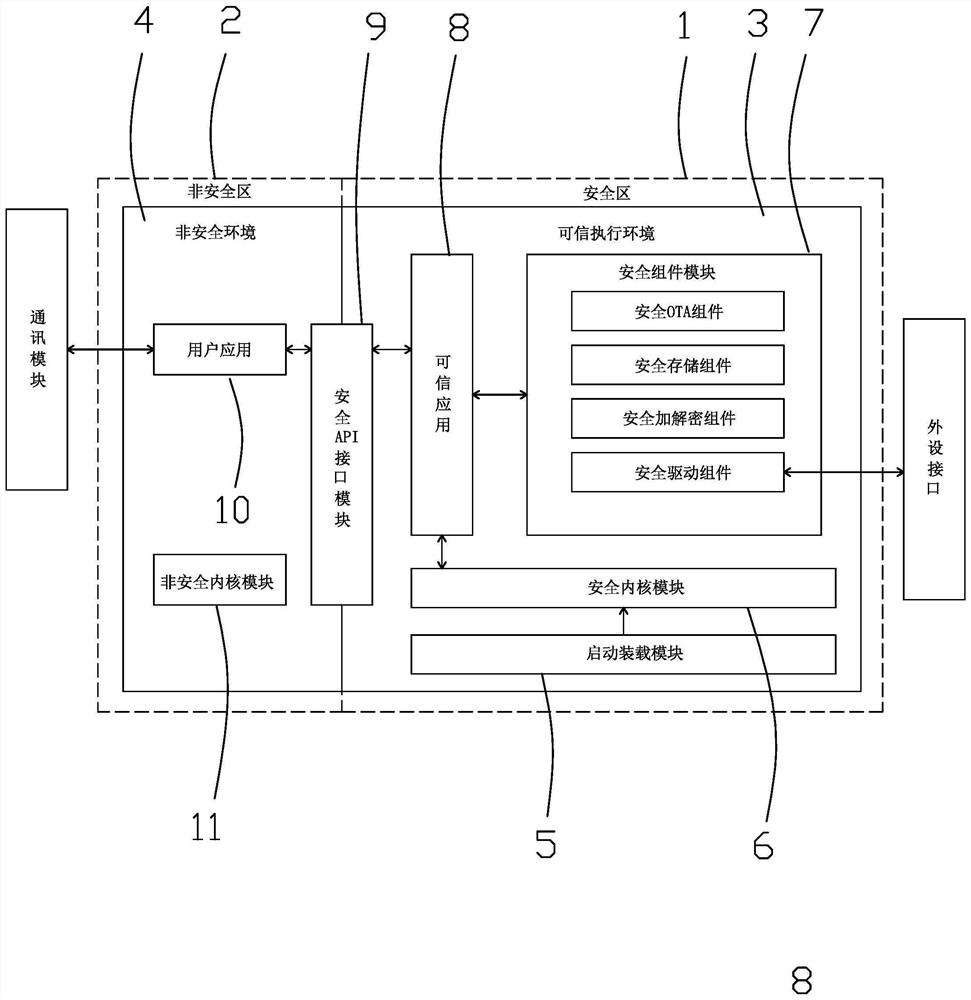
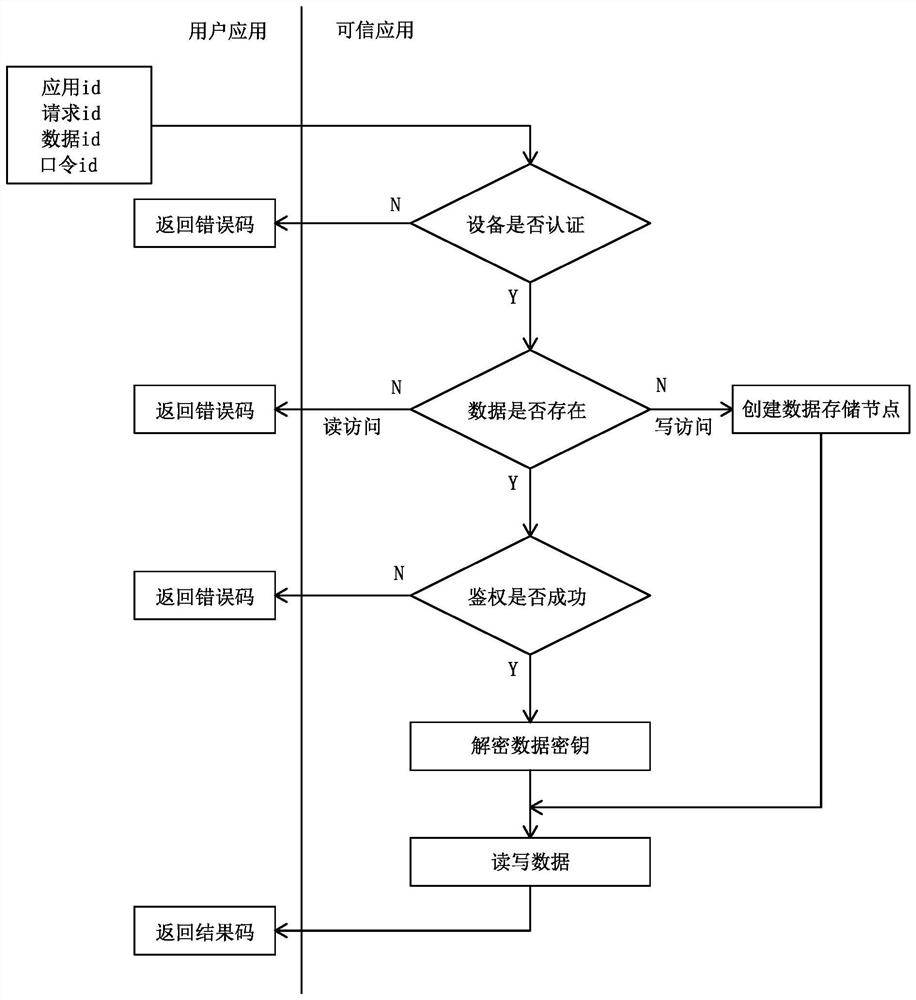
The invention discloses an Internet-of-Things equipment safety protection system and method. The problems that in the prior art, security holes exist in hardware and software of Internet-of-Things equipment, the security of communication encryption and decryption is not high, and the efficiency ratio is low are solved. The system comprises a device and a server, the device comprises an MCU controller, the MCU controller comprises a secure area and a non-secure area, a trusted execution environment is deployed in the secure area, a non-secure environment is deployed in the non-secure area, and a startup loading module, a secure kernel module, a secure component module, a trusted application and a secure API interface module are arranged in the trusted execution environment. A user application and a non-secure kernel module are arranged in the non-secure environment. Sensitive data storage access is protected through three-layer protection measures. Information encryption and decryption between the equipment and the server are verified by adopting an identity token. Security protection is carried out from equipment hardware, software, storage access and communication, and hardware control, software cracking and information stealing are prevented.
Owner:杭州安芯物联网安全技术有限公司
Detecting exploits against software applications
InactiveCN105229652ADigital data protectionPlatform integrity maintainanceSystem verificationSecurity kernel
There is described a method of executing a software application on a device by including a secured cored within the software application, and providing a system verification function within the secured core. The system verification function is used to scan for exploits against the application, for example local exploits seeking to recover cryptographic keys which may be found within the application when executing, with reference to exploit signature data which may be provided by an external server.
Owner:IRDETO ACCESS
Safe kernel structure and safe operation method of satellite-borne computer software
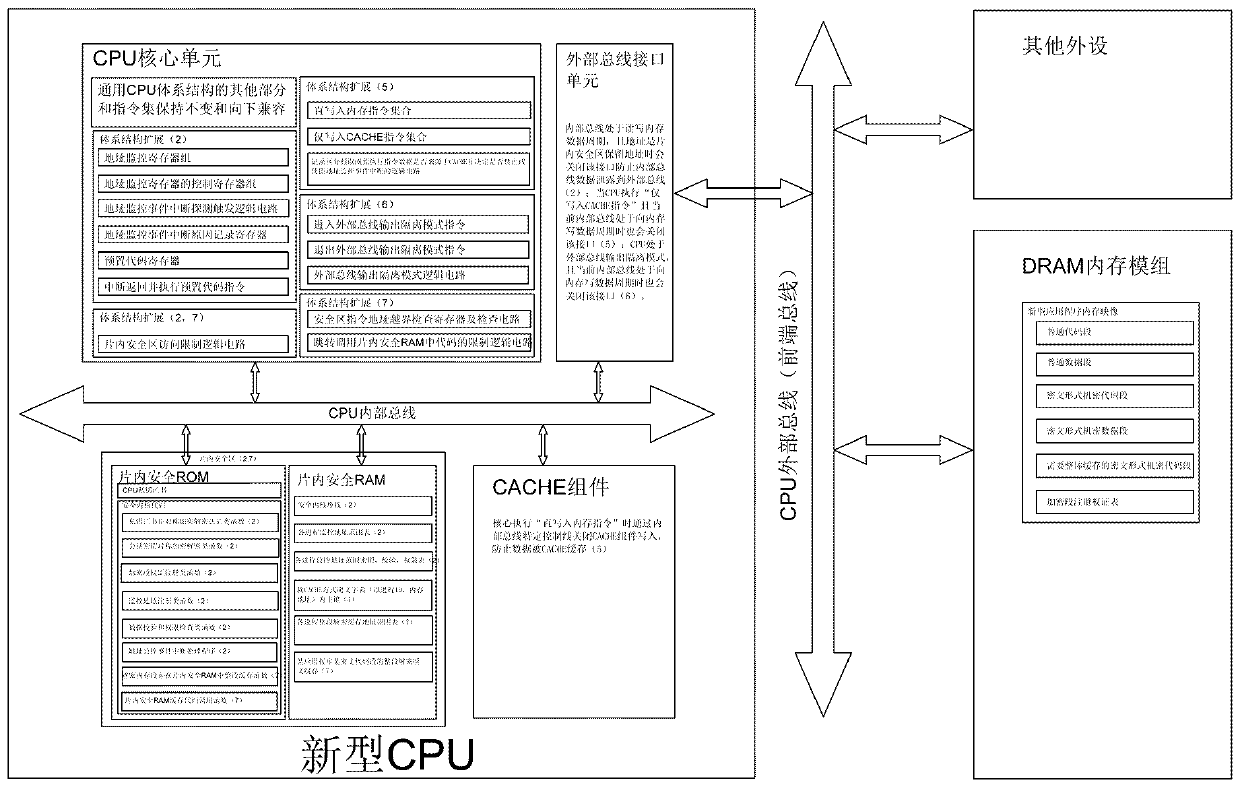
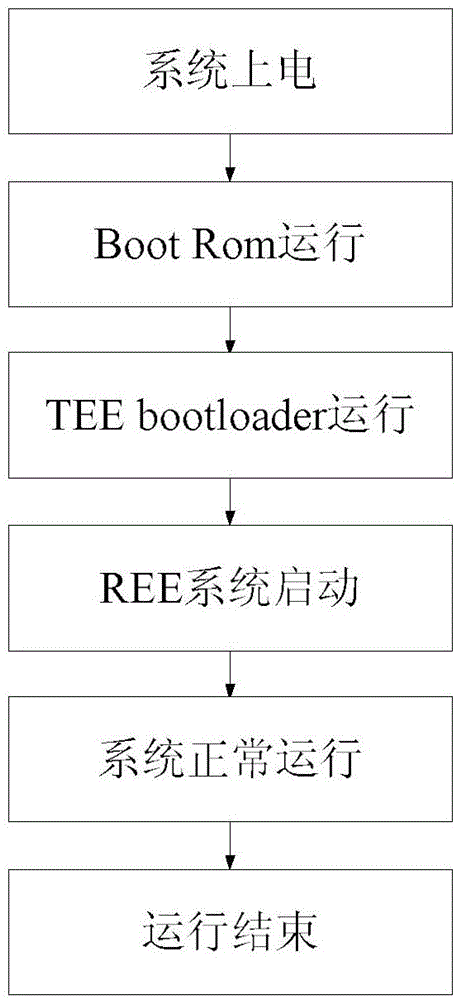
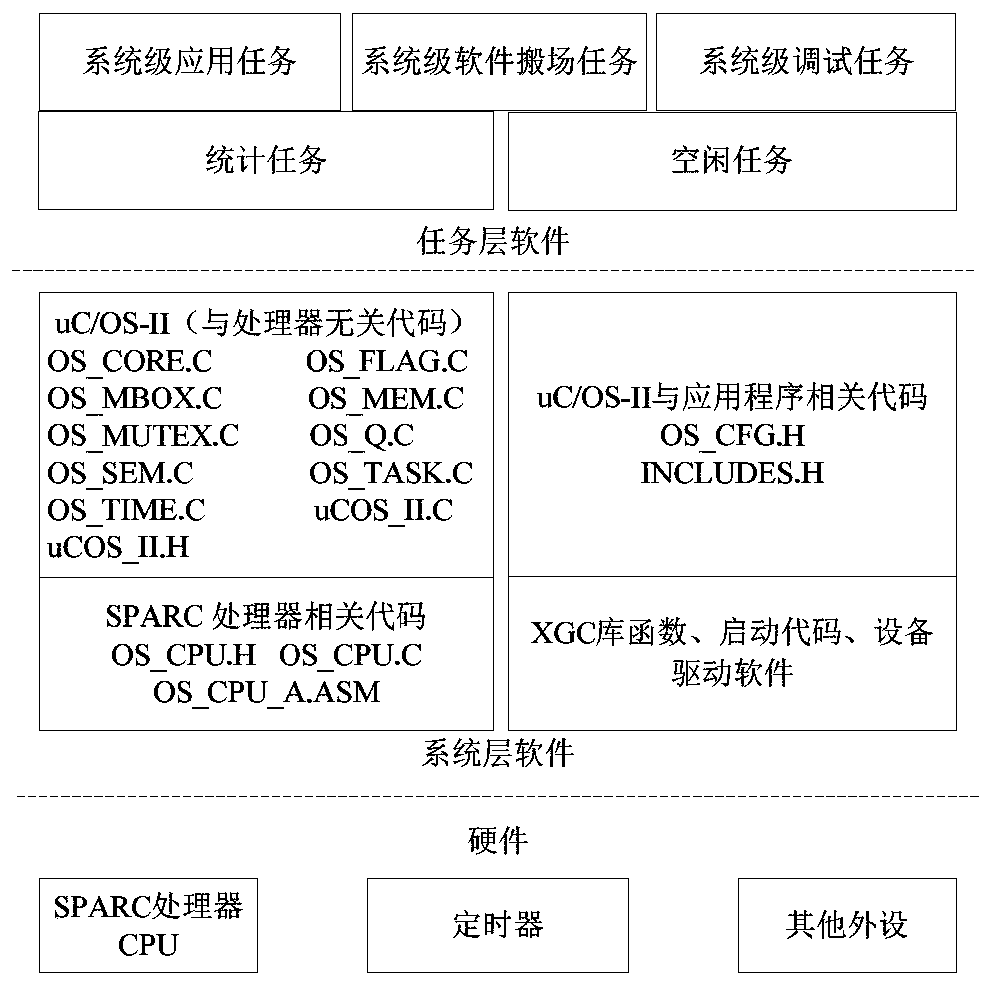
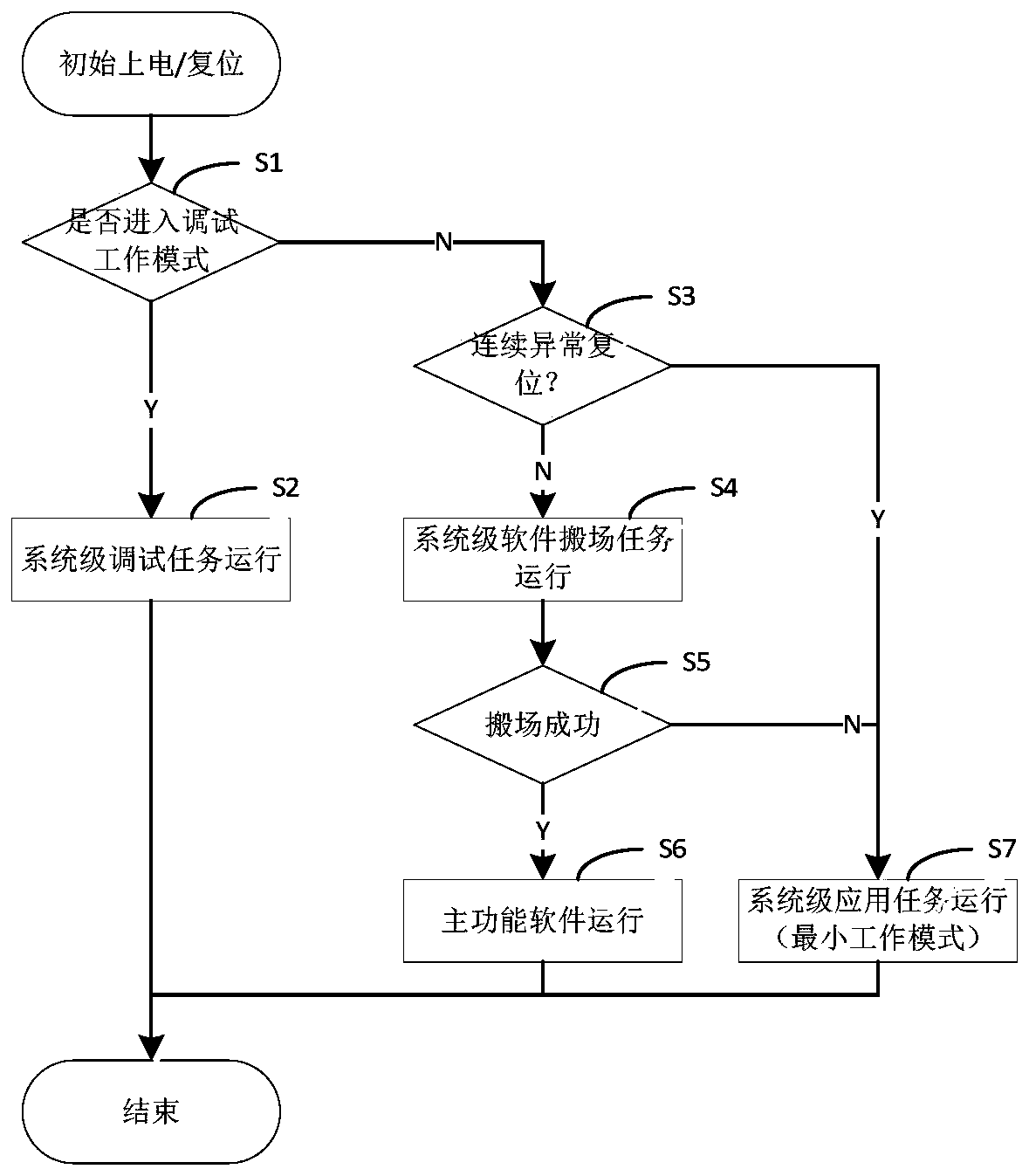
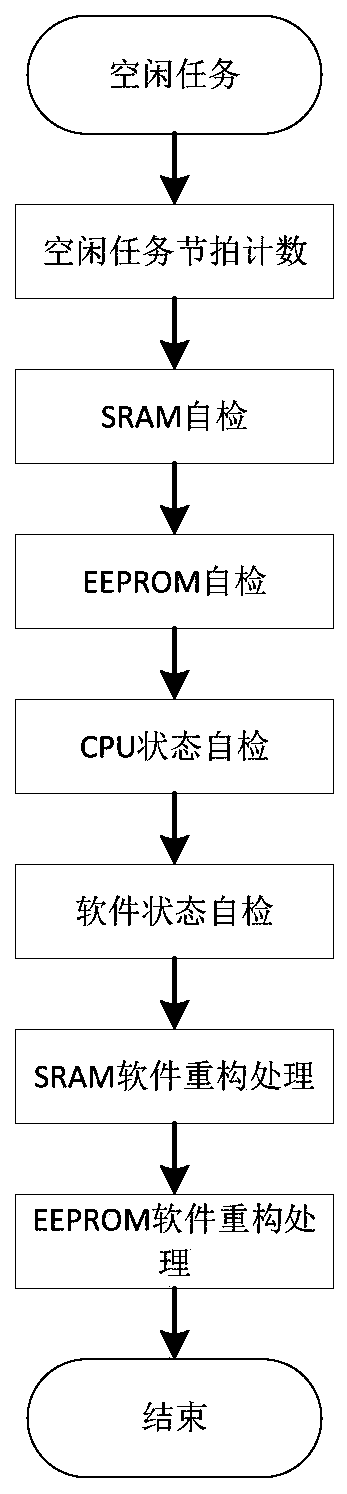
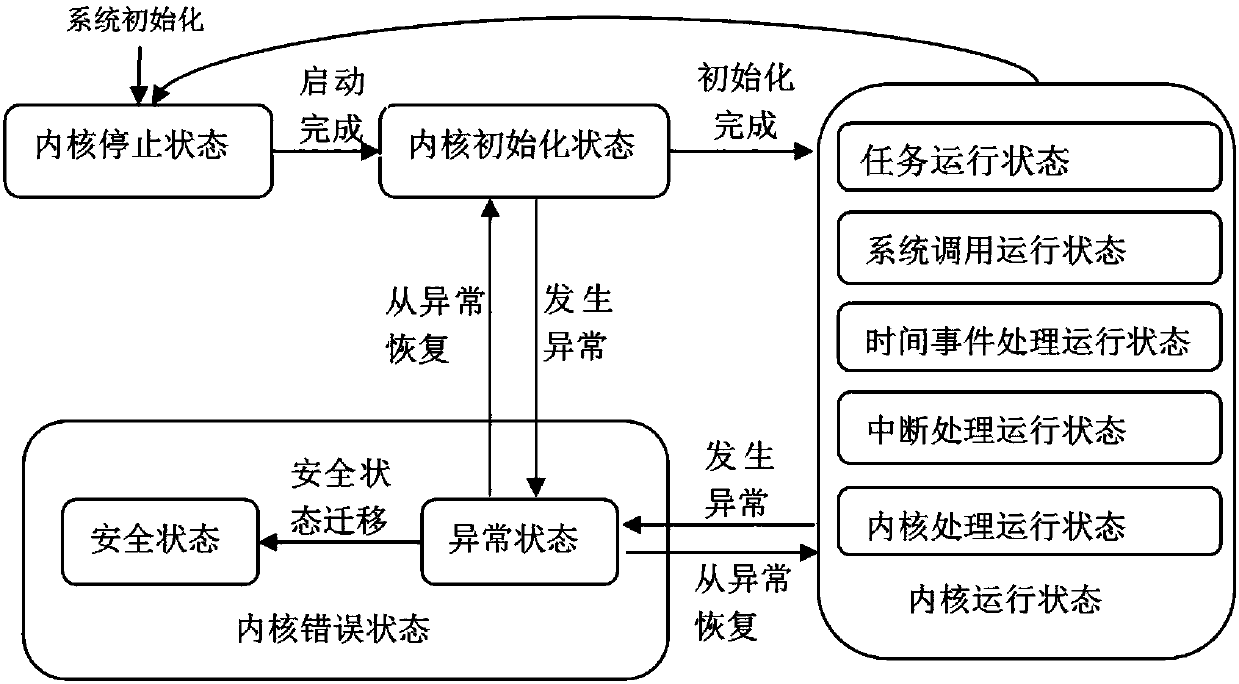
ActiveCN110673975AFunction increaseImprove reconfigurabilityReliability/availability analysisNon-redundant fault processingSecurity kernelEngineering
Owner:SHANGHAI AEROSPACE CONTROL TECH INST
Virtual machine online antivirus system based on kvm virtualization platform
The invention relates to the field of computer technology, and proposes an online virtual machine antivirus system based on a KVM virtualization platform. Set the security kernel module, security control module and network module, add the function of reading memory in the KVM kernel module, and provide the interface of the security kernel module registration hook; the security kernel module is used to register the hook in the KVM kernel module, and send the security control The module sends out a scan command, accepts the scanning and virus checking results obtained by the security control module, suspends the suspicious process, and handles the suspicious process accordingly; the security control module calls the antivirus engine to scan and check for viruses for all virtual machine processes in the memory of the security control module, and Report the result to the security kernel module; the network module is composed of a server-side network module and a client-side network module.
Owner:北京海云捷迅科技股份有限公司 +1
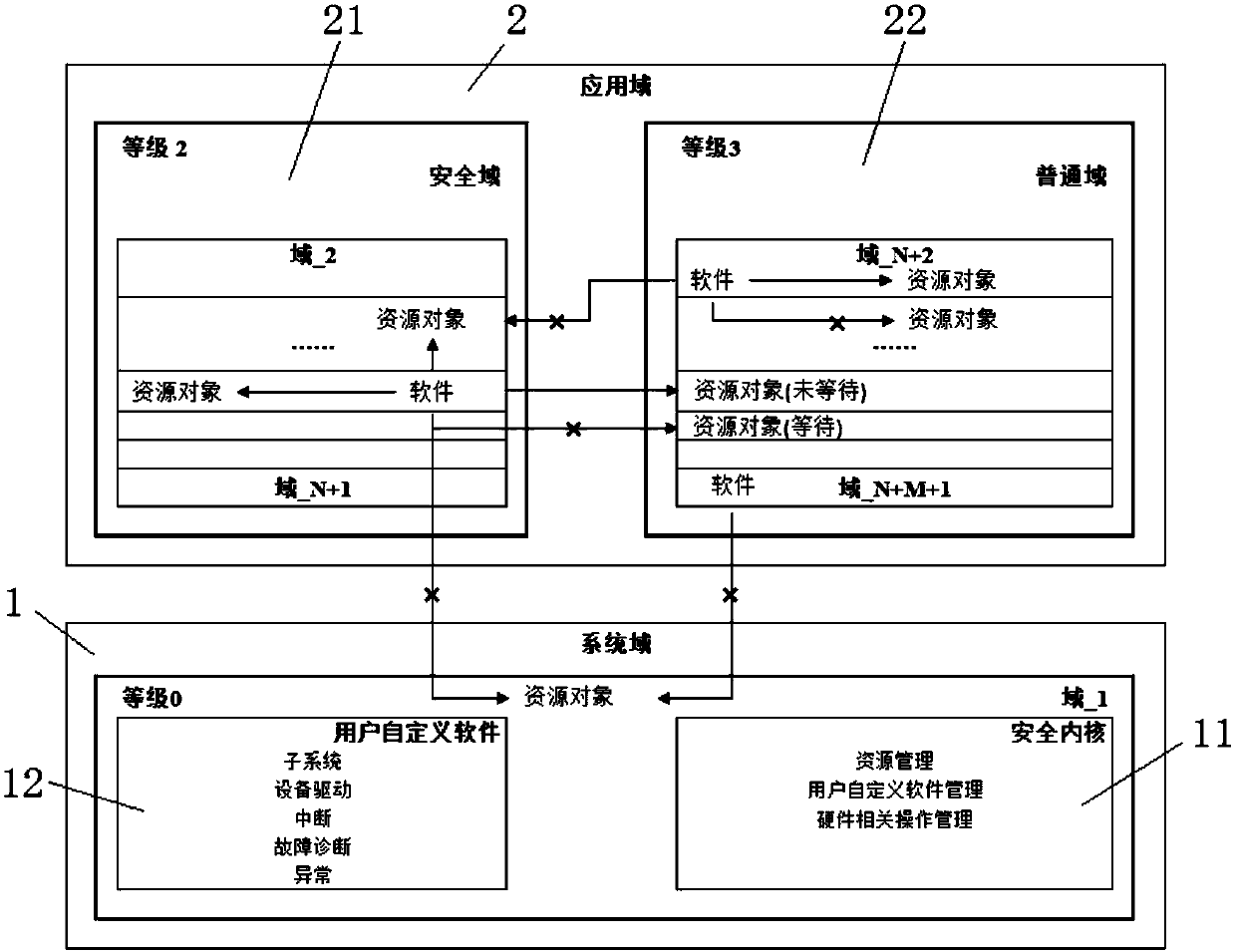
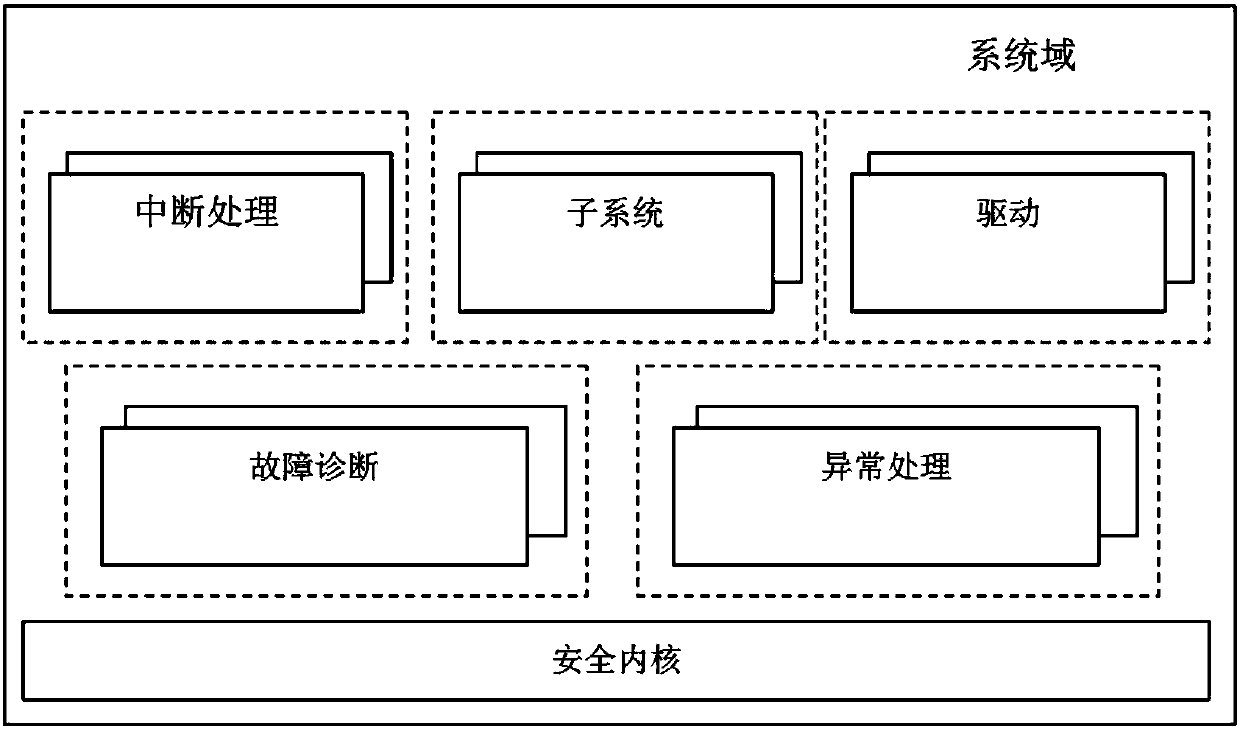
Method and system for establishing security system based on domain mechanism
InactiveCN108021827AFlexible controlReasonable strengthInternal/peripheral component protectionPersonalizationRelevant information
The invention discloses a method and system for establishing a security system based on a domain mechanism. The method includes the following steps of configuring domain management information, setting related information of a resource object, configuring and registering a failure diagnosis routine, starting the failure diagnosis routine, establishing a domain environment, initializing a securitycore, executing scheduling and running software, intersecting a software calling security API of a security domain with the security core, intersecting a software calling ordinary API of an ordinary domain with the security core, and regularly detecting the current system state through the security core. The system comprises system domains and application domains. The application domains include the security domain and the ordinary domain. The smaller the domain value of software is, the higher the authority is; software with high authority can have access to the software itself and resourceswith lower authorities, and software with the same authority can have access to one another. The domain mechanism is sufficiently used, and security isolation is achieved; the individualized securitysystem of different grades can be established; control is flexible, and strength is reasonable; hardware characteristics are not depended on, and portability is high.
Owner:中科开元信息技术(北京)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com