Method and system for realizing user authentication through biological characteristic information
A biometric information, user authentication technology, applied in transmission systems, digital data authentication, electrical components, etc., can solve problems such as user loss, cracking, inconvenience, etc., to improve reliability and security, authentication process safety, and upgrade The effect of operating experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings. Here, the exemplary embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
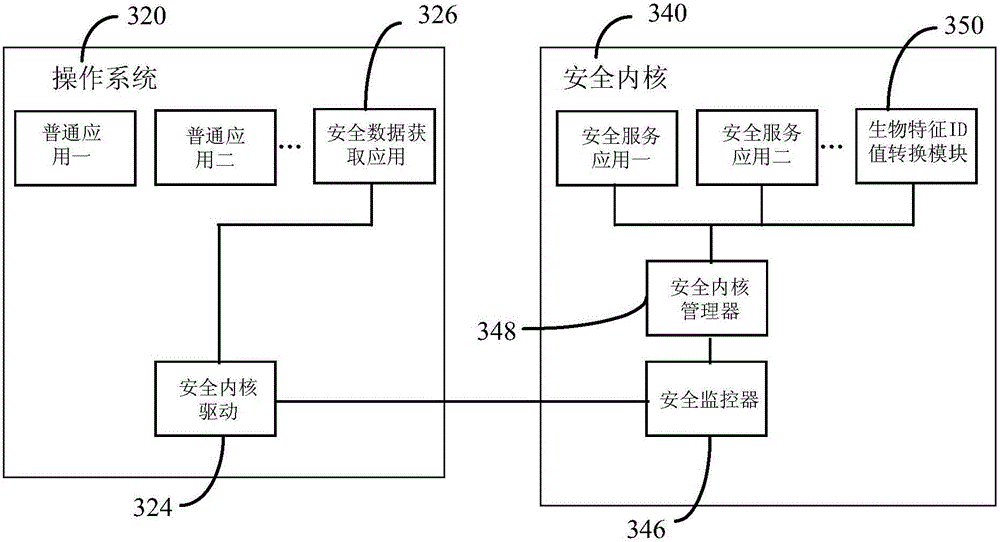
[0031]To facilitate the description of the specific implementation of this embodiment, the biometric information involved in the following takes fingerprint collection as an example, and iris information collection and its ID value conversion are the same as fingerprint collection.
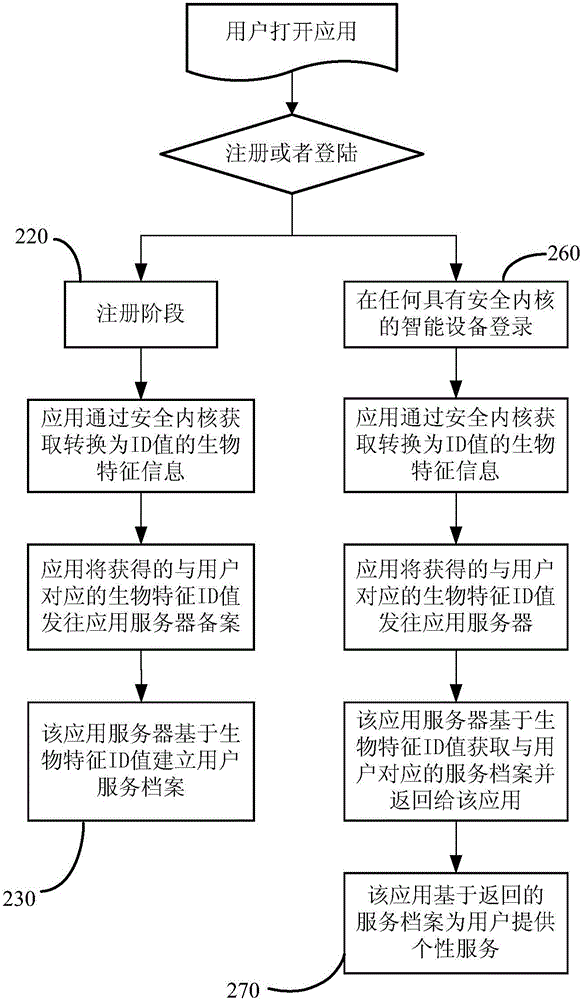
[0032] The embodiment of the present invention provides a new identity authentication method different from the traditional username / password method, that is, a method and system for implementing user authentication using biometric information.
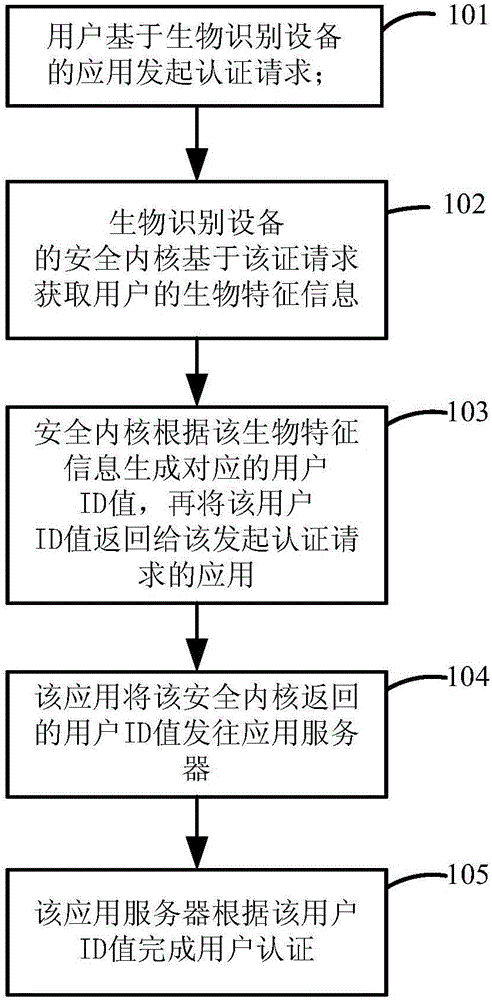
[0033] Please refer to figure 1 As shown,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com